Classified management method applied to security baseline software
A security baseline, hierarchical management technology, applied in the direction of platform integrity maintenance, etc., to achieve the effect of improving throughput and performance, high access and business volume, security and operational management efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The content of the present invention is described in more detail below:
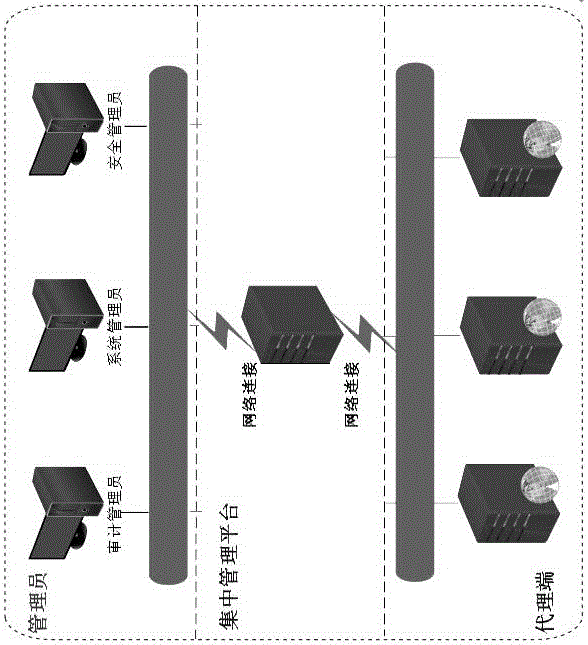
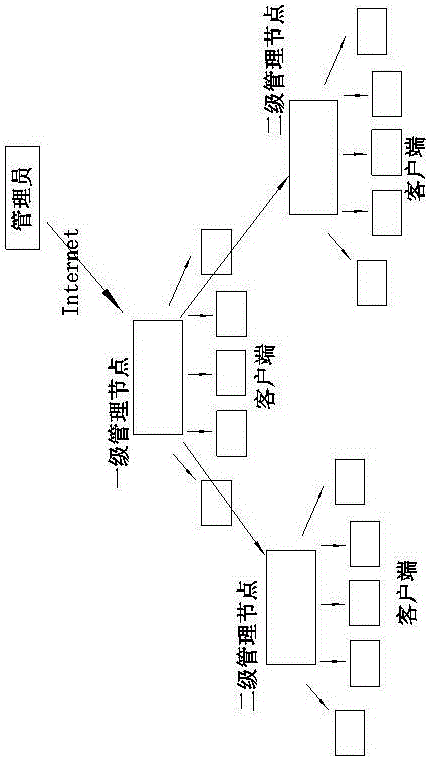
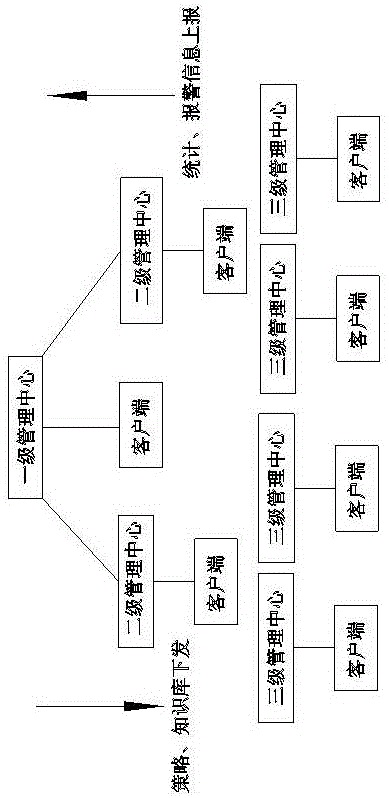
[0030] The security baseline software mainly protects the configuration items of the protected server, and is mainly applied to the operating system and application software running on the protected server. By simply setting scan and repair parameters, the protected server configuration items can be automatically scanned and repaired. The present invention provides a hierarchical management method applied to security baseline software, which supports a multi-layer cascading management mode, and is suitable for centralized management and control of multiple branches of large enterprises, or group management and control. In the cascade management mode, the lower-level centralized management platform can implement the security policy formulated by the upper-level management platform according to the requirements of the management platform; it can also realize timely alarms for important events and ab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com