Credible application management system and loading method for credible applications
An application management and credible technology, applied in the direction of electrical digital data processing, instruments, computer security devices, etc., can solve the problems of destroying TEEkernel trusted applications, upgrade failures, affecting development efficiency, etc., to improve flexibility and scalability , the effect of reducing the start-up time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described in detail below with reference to the accompanying drawings and specific embodiments. The advantages and features of the present invention will become apparent from the following description and claims. It should be noted that, the accompanying drawings are all in a very simplified form and use imprecise ratios, and are only used to facilitate and clearly assist the purpose of explaining the embodiments of the present invention.
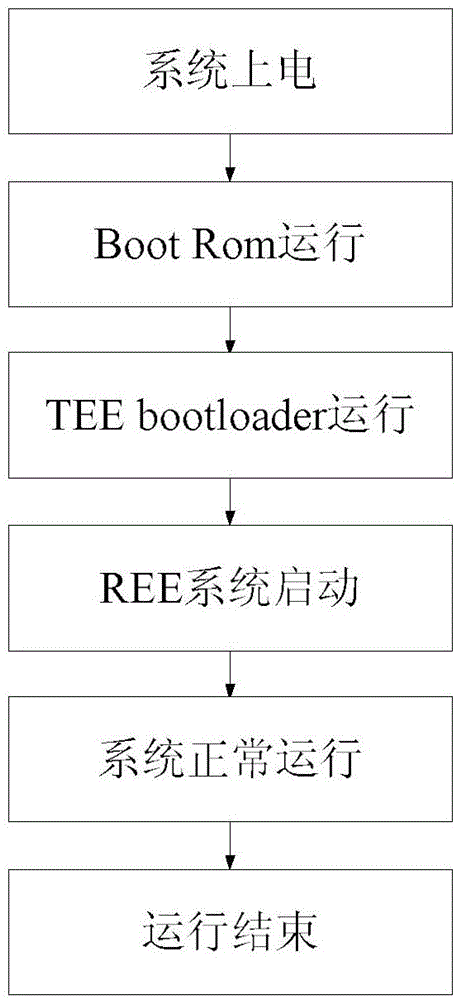
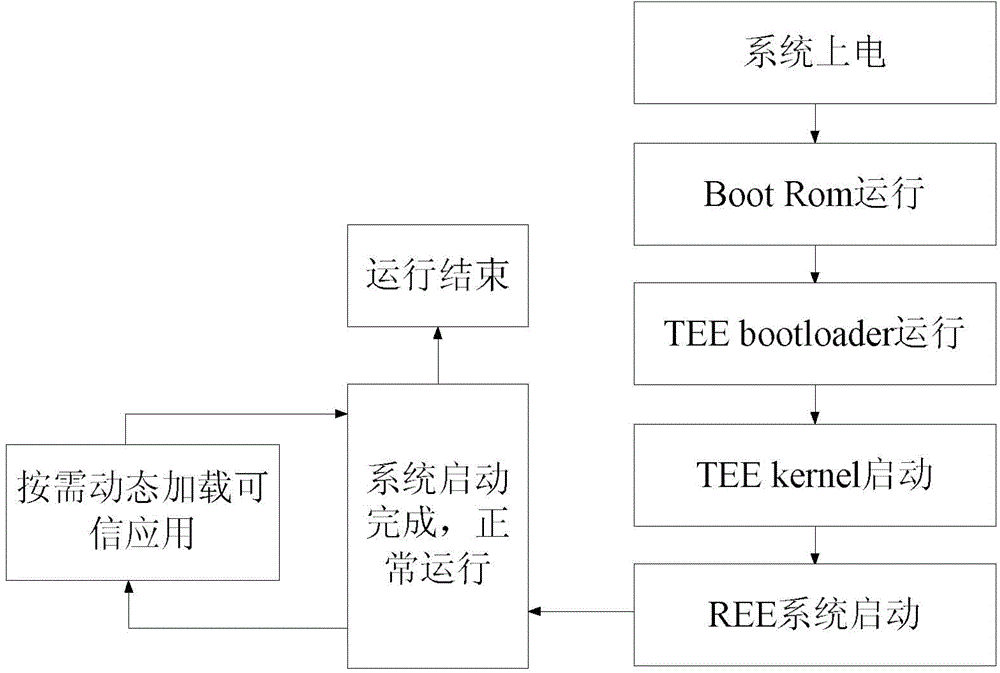
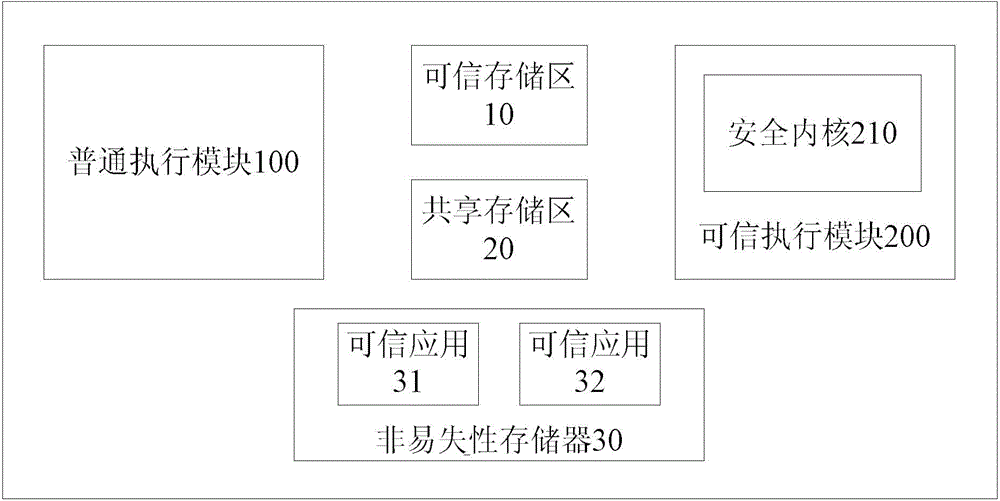
[0032] In view of the problems existing in the prior art, the inventor thought of using each trusted application as a separate file, and proposed a trusted application management system, so that the REE system can dynamically request the trusted application to be used from the TEE system during operation. (TrustedApplication), the security kernel (TEEkernel) loads the trusted application, that is, the loading of the trusted application is performed during the operation of the trusted application ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com