Detecting exploits against software applications
A technology of software application and signature file, which is applied in the direction of program/content distribution protection, instrument, electronic digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
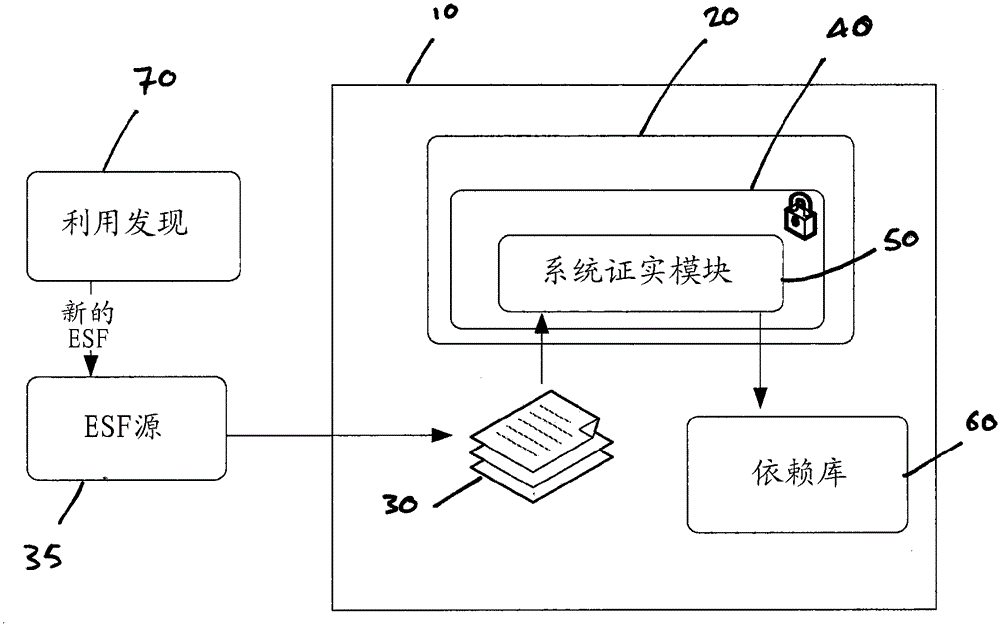
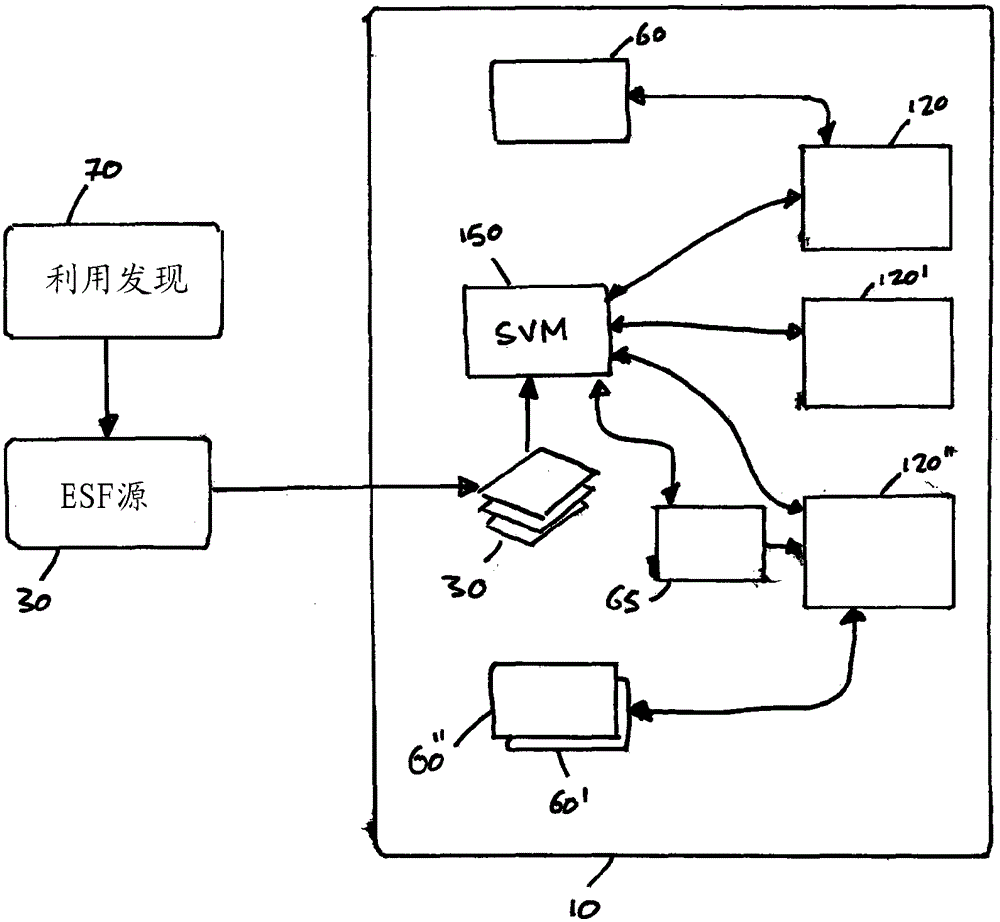
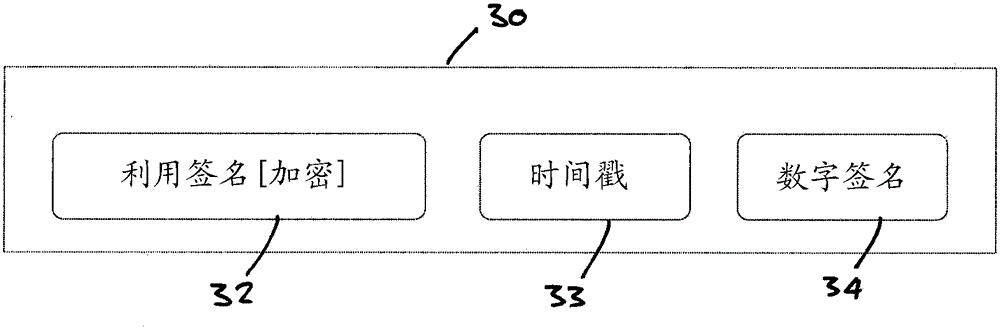
[0032] now refer to figure 1 , the computer device 10 is arranged to execute a software application 20 . The computer device may be, for example, a conventional personal computer, tablet computer, mobile phone or other mobile device, or the like. The invention is typically implemented for a large user base of such computing devices. The software application 20 may typically be stored on a hard drive, a solid state disk, or in some other form of persistent storage for loading into random access memory of the computer device 10 in preparation for execution.
[0033]A known attacker attempted to attack a software application. This may involve, for example, reverse engineering the corresponding executable and / or modifying the executable to access features / functions and / or information that might not normally be available to an attacker. For example, the attacker may not have paid for access to a certain function of the application (for example, if the attacker has not obtained t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com