Multi-Factor Security System With Portable Devices And Security Kernels
a security system and portable device technology, applied in the field of user security authentication, can solve the problems of liable to remain unused in the security system that is not easy and convenient, and achieve the effects of increasing speed, popular acceptance, and increasing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The principles and operation of a method and apparatus according to the present invention may be understood with reference to the drawings and the accompanying description.
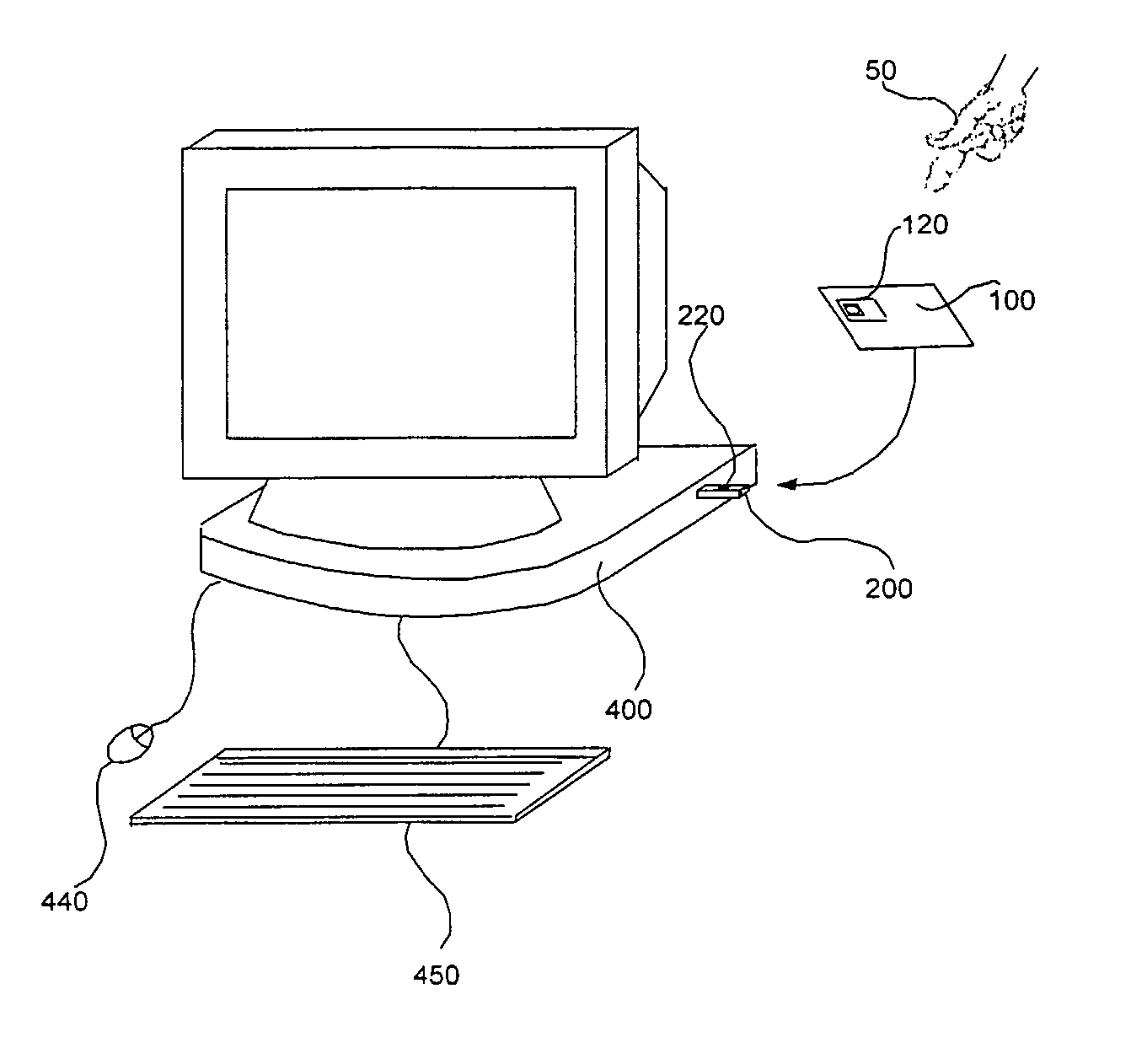
[0060] In the following embodiments of the present invention, a contactless smart card is used in combination with one or more other devices to allow mutual authentication among them.
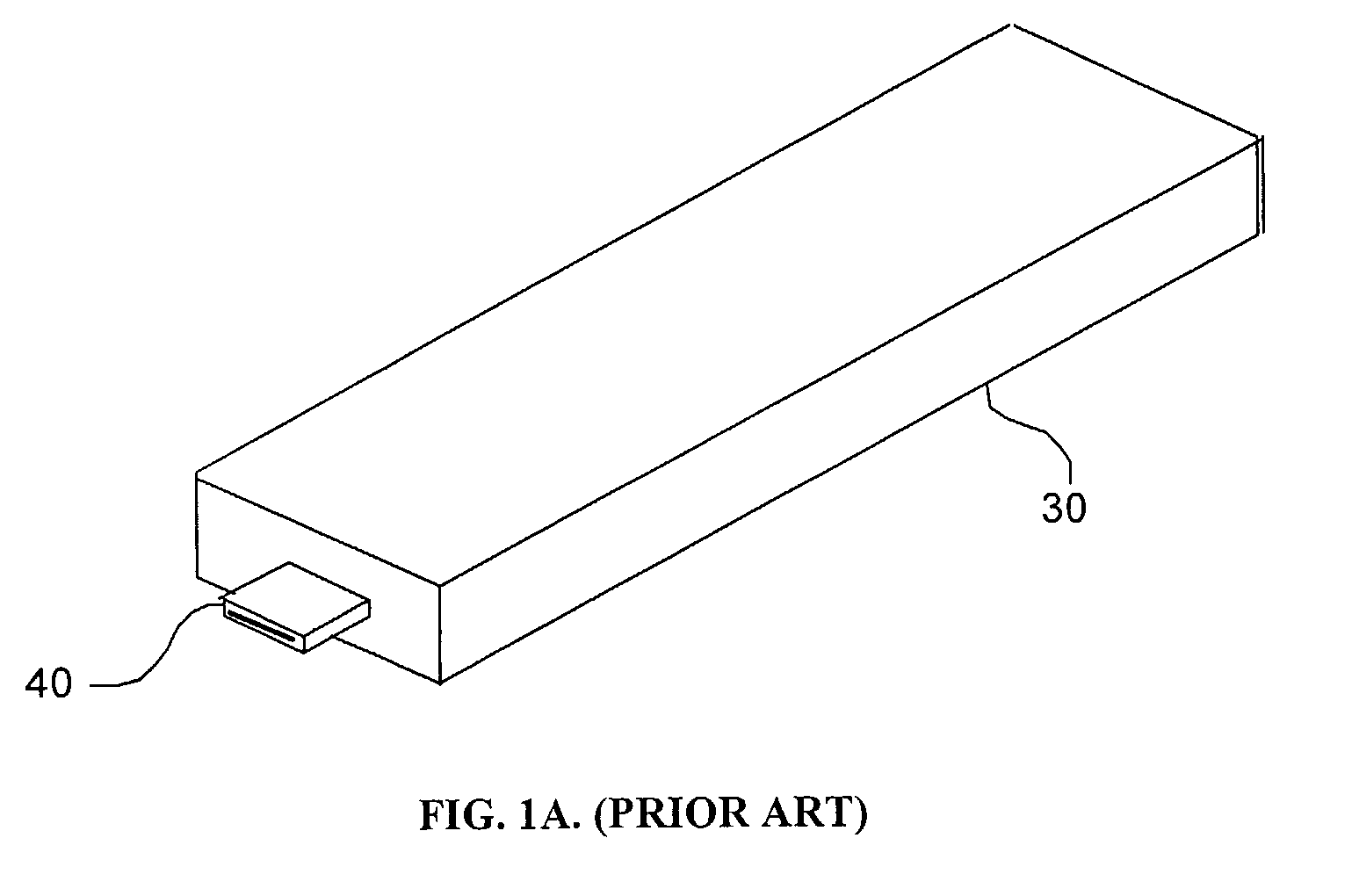
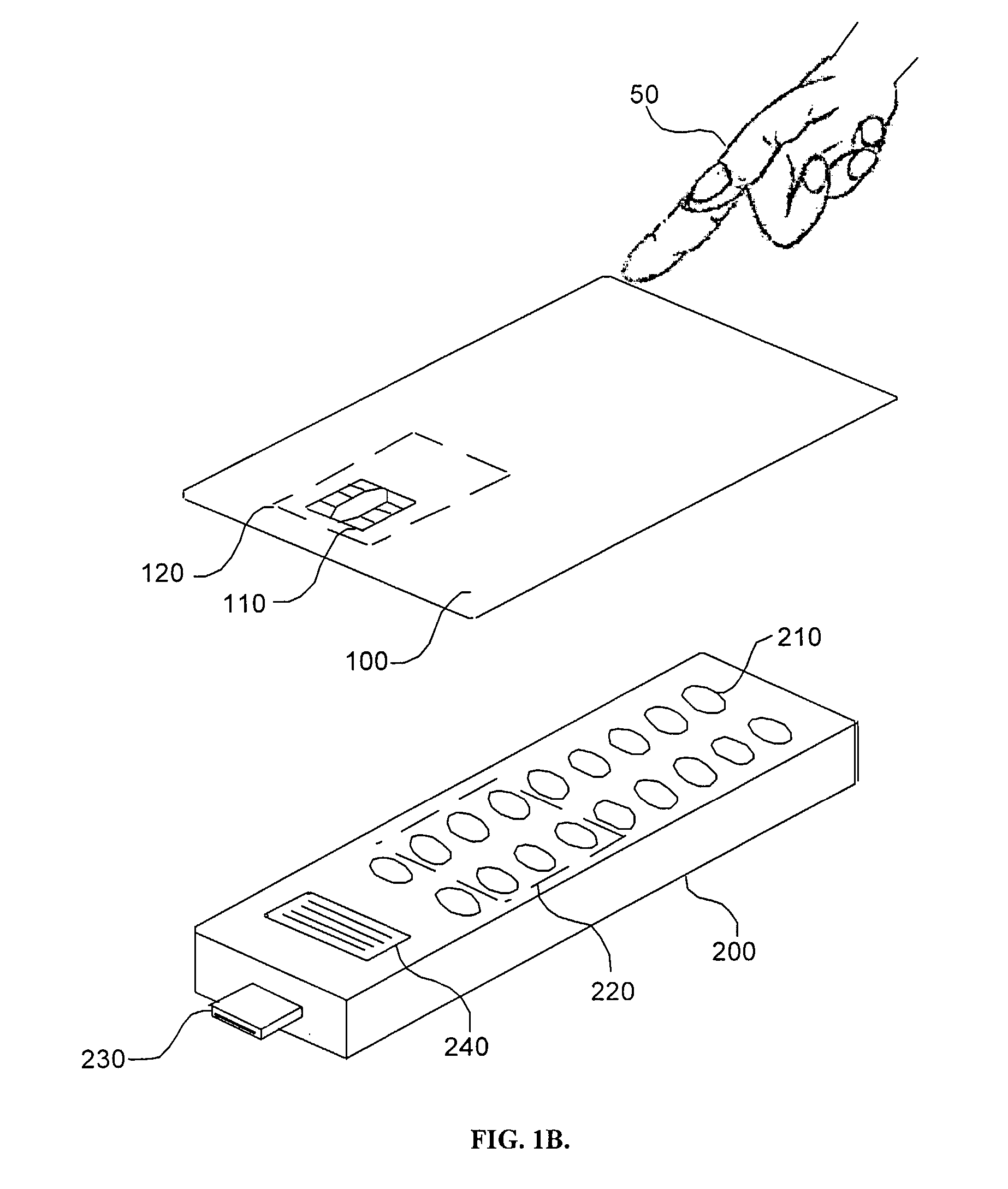
[0061]FIG. 1A is a conceptual diagram of a prior-art computer peripheral device 30 (a mass storage device) with an interface connector 40. FIG. 1B is a conceptual diagram of such a device 200 according to an embodiment of the present invention, wherein device 200 is coupled to a contactless smart card 100 belonging to a user 50. On device 200 is a keypad 210 which communicates directly with an internal secure processor within device 200, without revealing keypad action to the external host computer. Within keypad 210 is an antenna 220 and a transceiver (not shown) for communicating with smart card 100. A connector 230 enables...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com