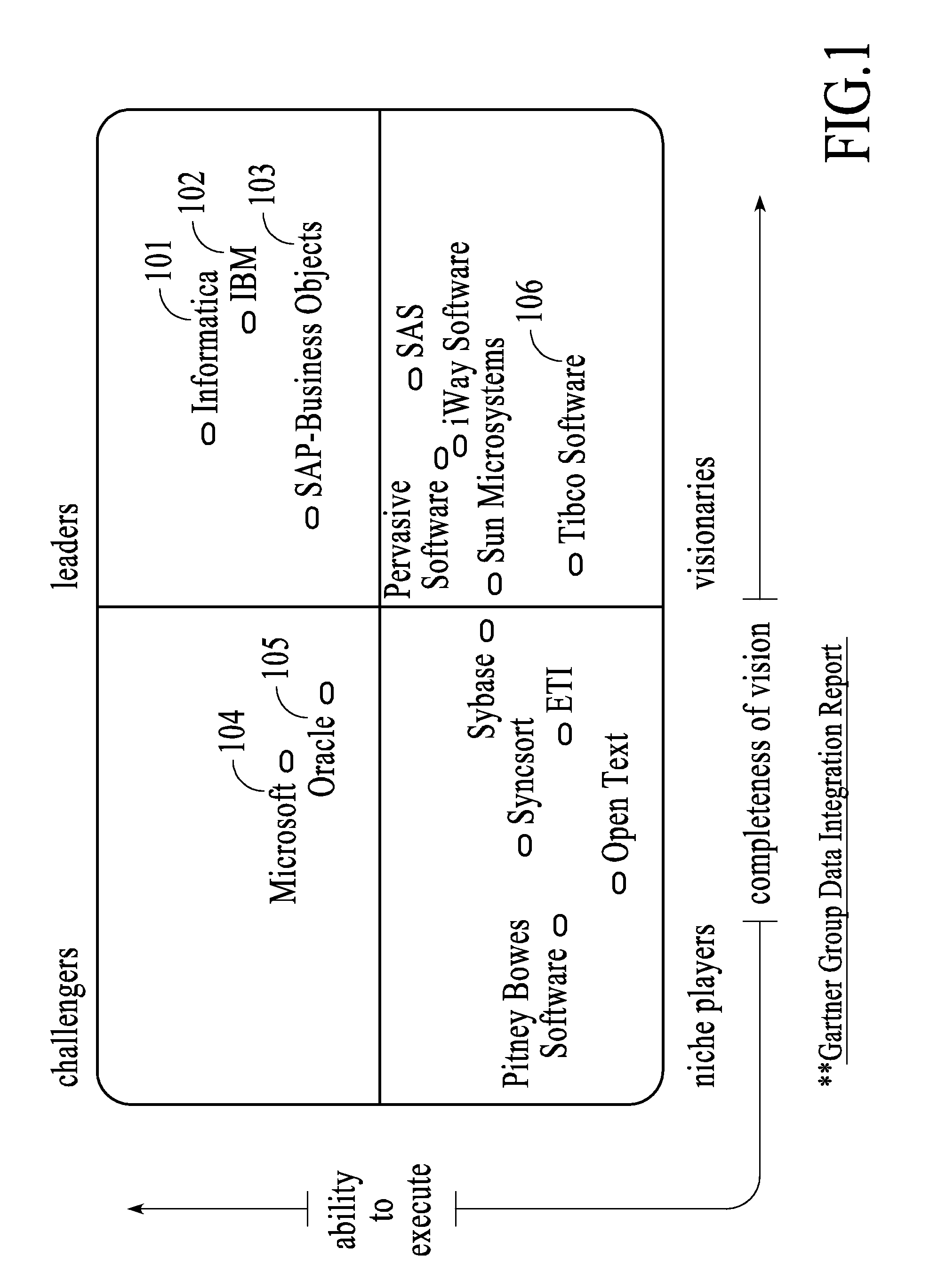
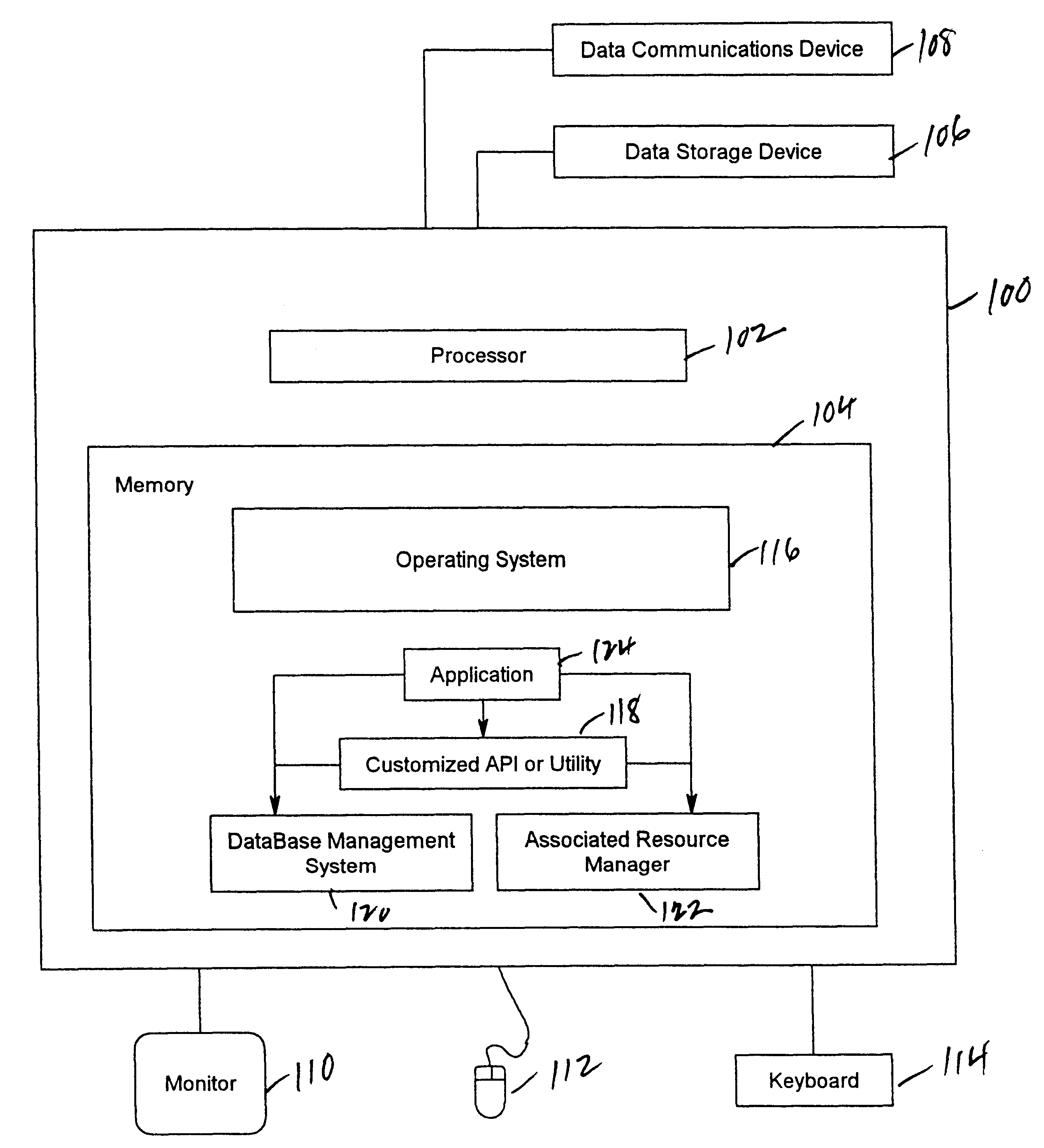
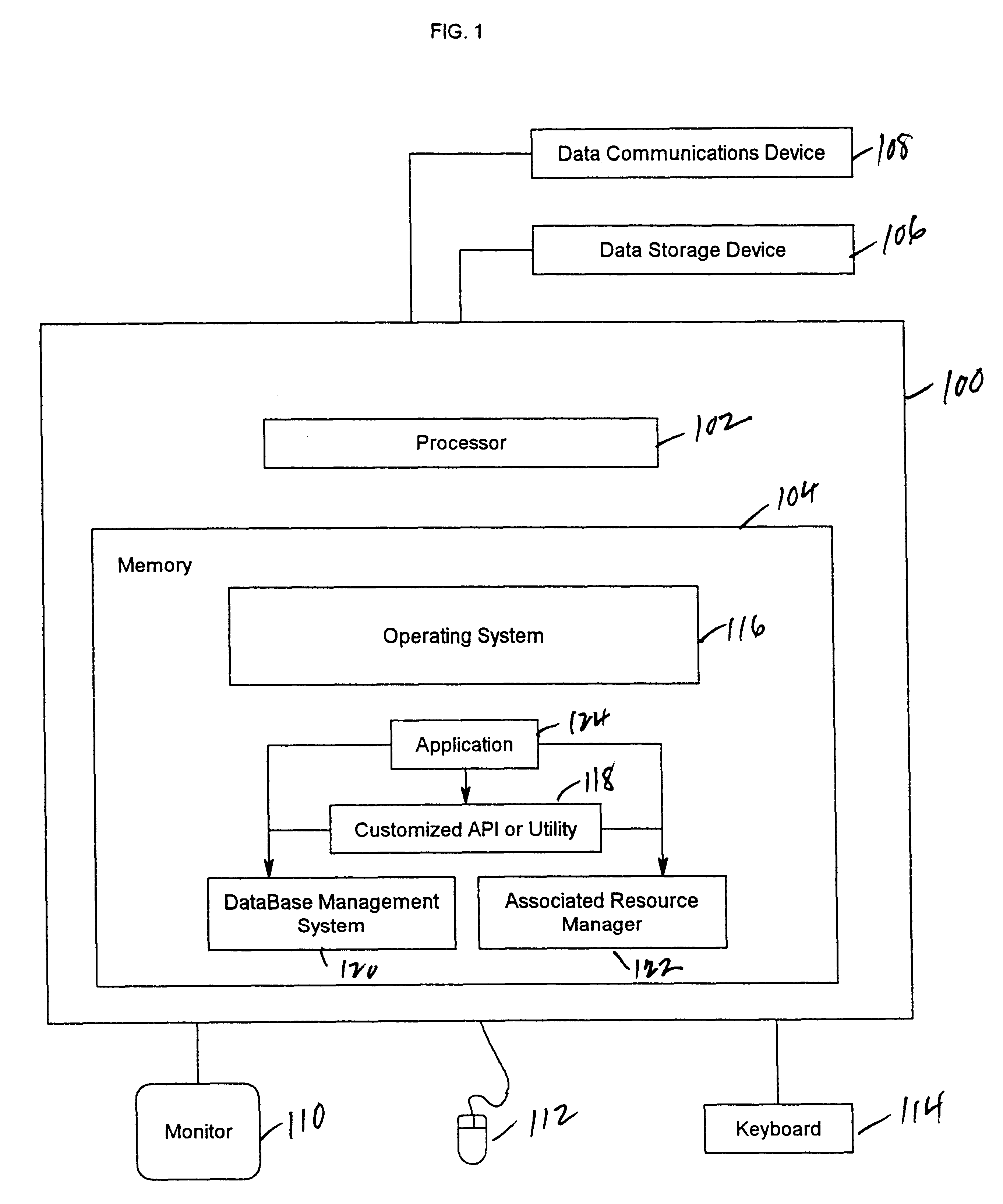
Patents
Literature
317 results about "Operational requirements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Operational requirements. (programming) Qualitative and quantitative parameters that specify the desired capabilities of a system and serve as a basis for determining the operational effectiveness and suitability of a system prior to deployment.
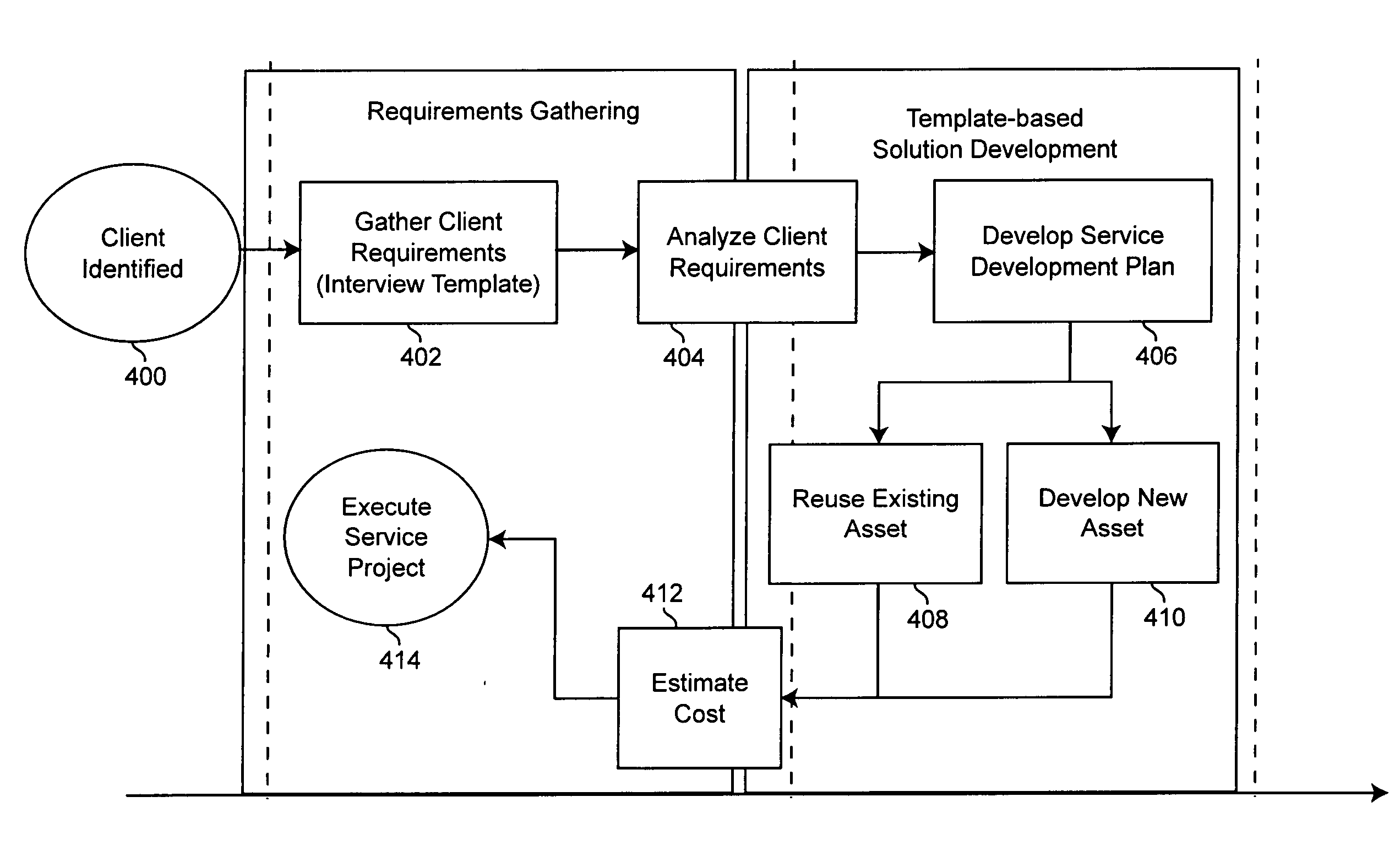
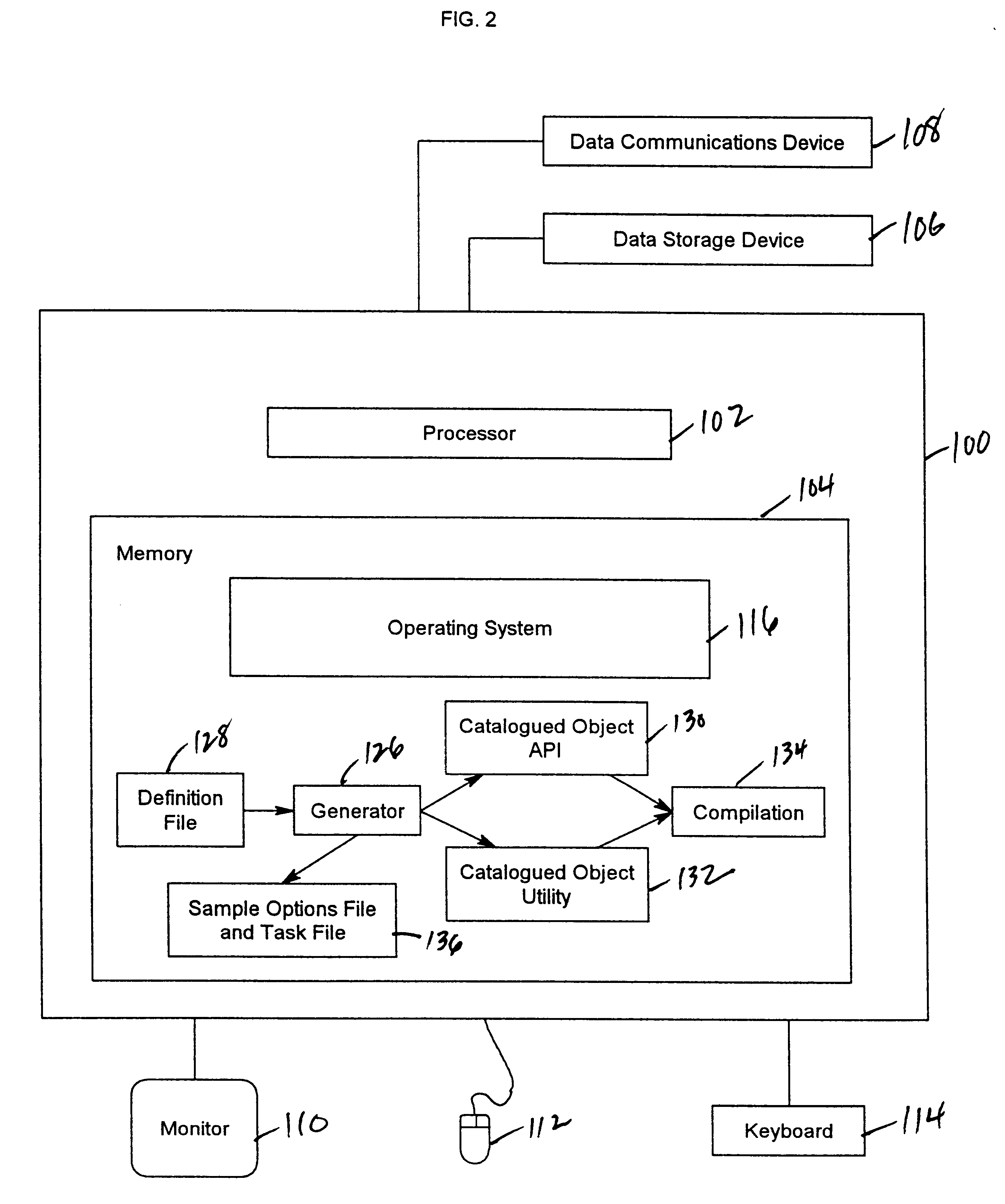
Method and apparatus for model-driven managed business services
InactiveUS20070179793A1Avoid longerAvoid costly service implementationMarket predictionsResourcesSupporting systemTemplate based
A mechanism provides a model-driven solution template-based approach for managed business services. Key assets of the business services are templatized and made configurable. The mechanism implements a metamodel describing standard service offerings that can be configured to meet specific business and operational requirements at a level of business process and system components. A cost and pricing model of service offerings helps assess the service costs and resource requirements based on a client's selection of standard and customized processes and system components. A supporting system solution is developed based upon underlying solution templates and solution artifacts as well as client-specific requirements.
Owner:IBM CORP
System, multi-tier interface and methods for management of operational structured data
ActiveUS20090125796A1Reduce the impactEasy to moveExecution for user interfacesInput/output processes for data processingSubject-matter expertObject based
Owner:AVRO COMPUTING
Application-independent generator to generate a database transaction manager in heterogeneous information systems
InactiveUS6321374B1Easy system integrationFacilitate application/middleware developmentData processing applicationsRelational databasesSystems integratorApplication software
A heterogeneous information system such as a digital library often uses a database manager together with other data resource manager(s), such as an object server or a video server, to manage digital content. Such a system often needs to maintain an application-specific database and / or to handle application-specific operational requirements. To facilitate system integration and application development, an application-independent reusable product is created which generates a custom system component or utility, such as a loader, according to a specification provided by a system integrator or an application developer.
Owner:IBM CORP
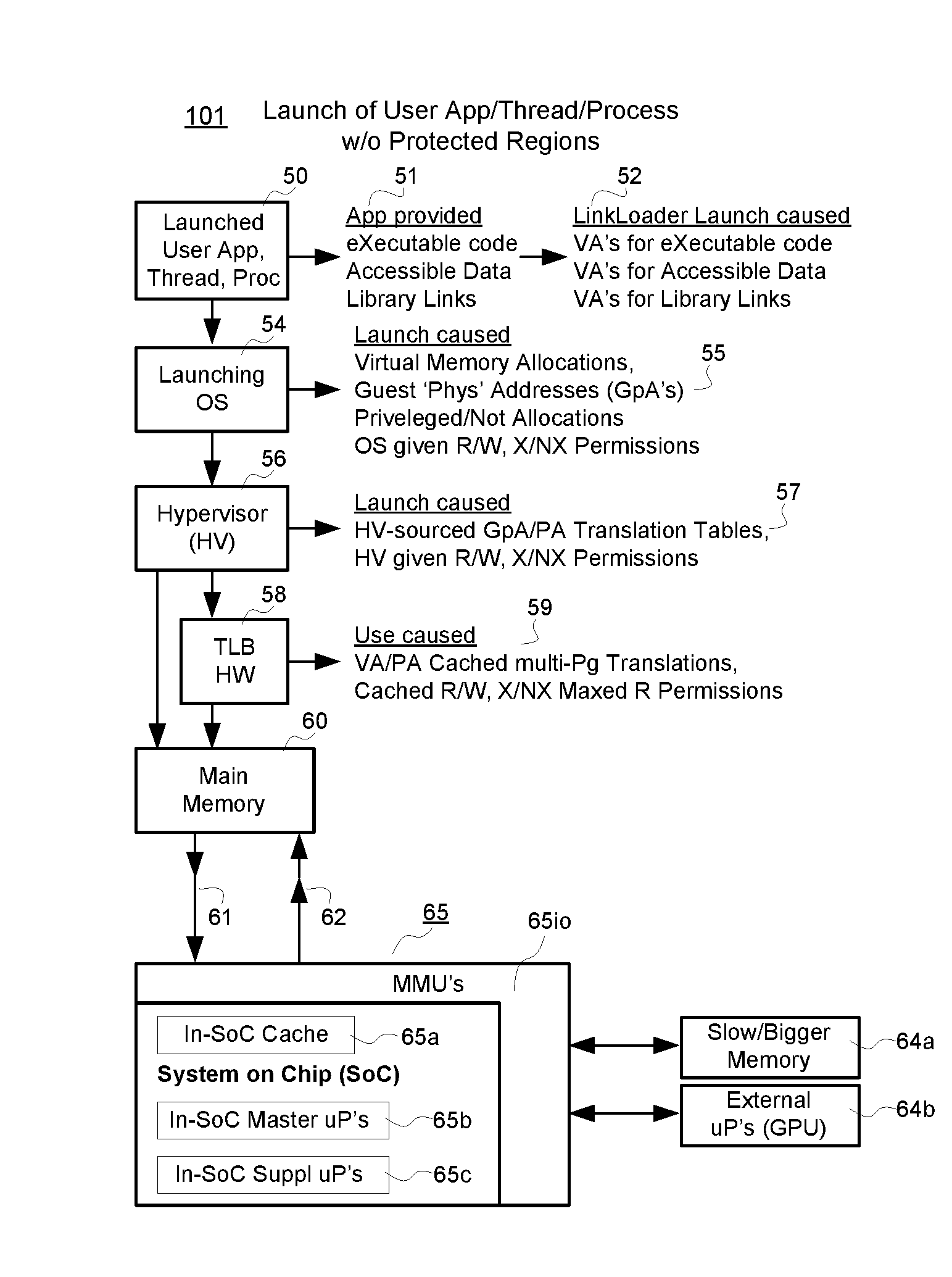
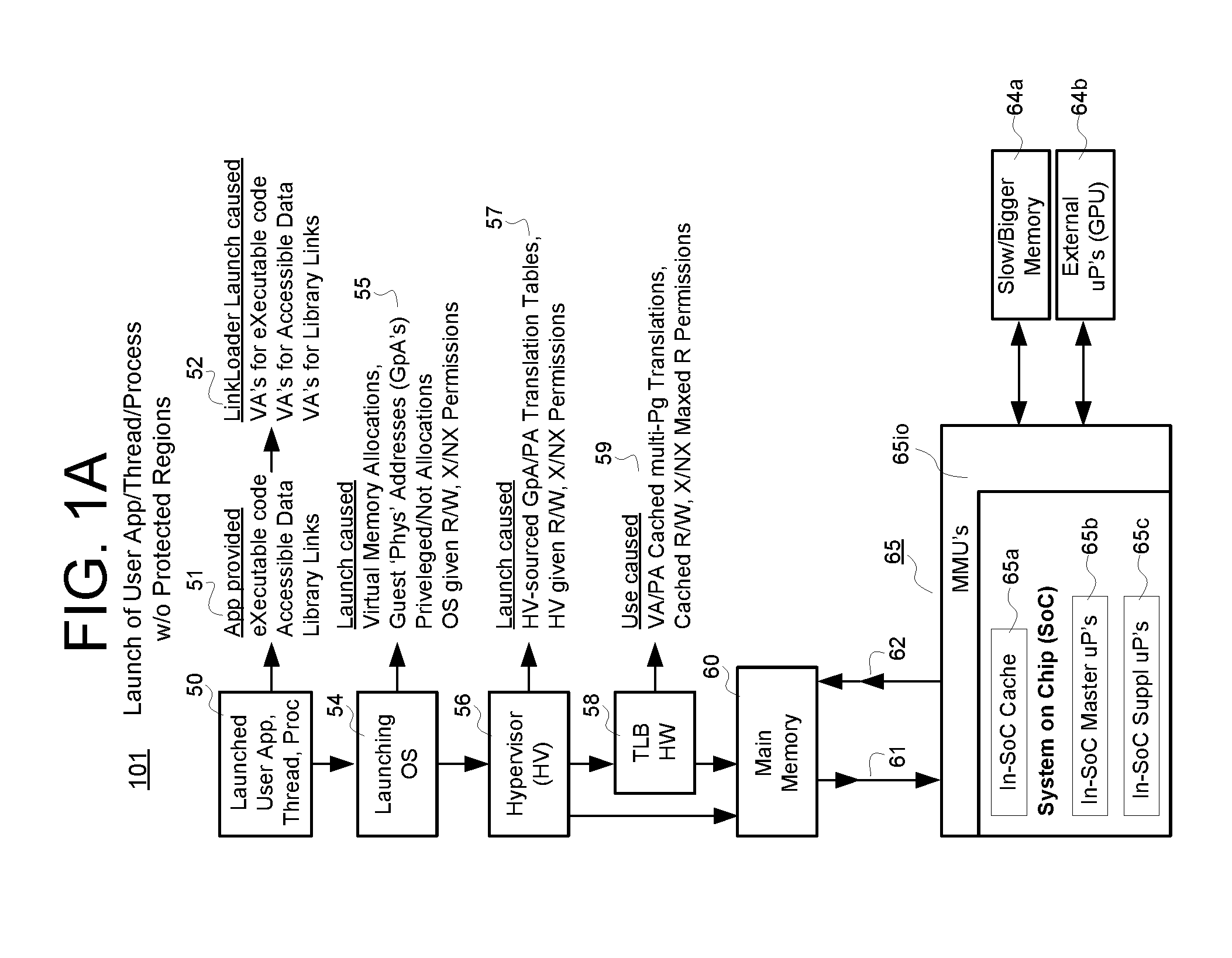
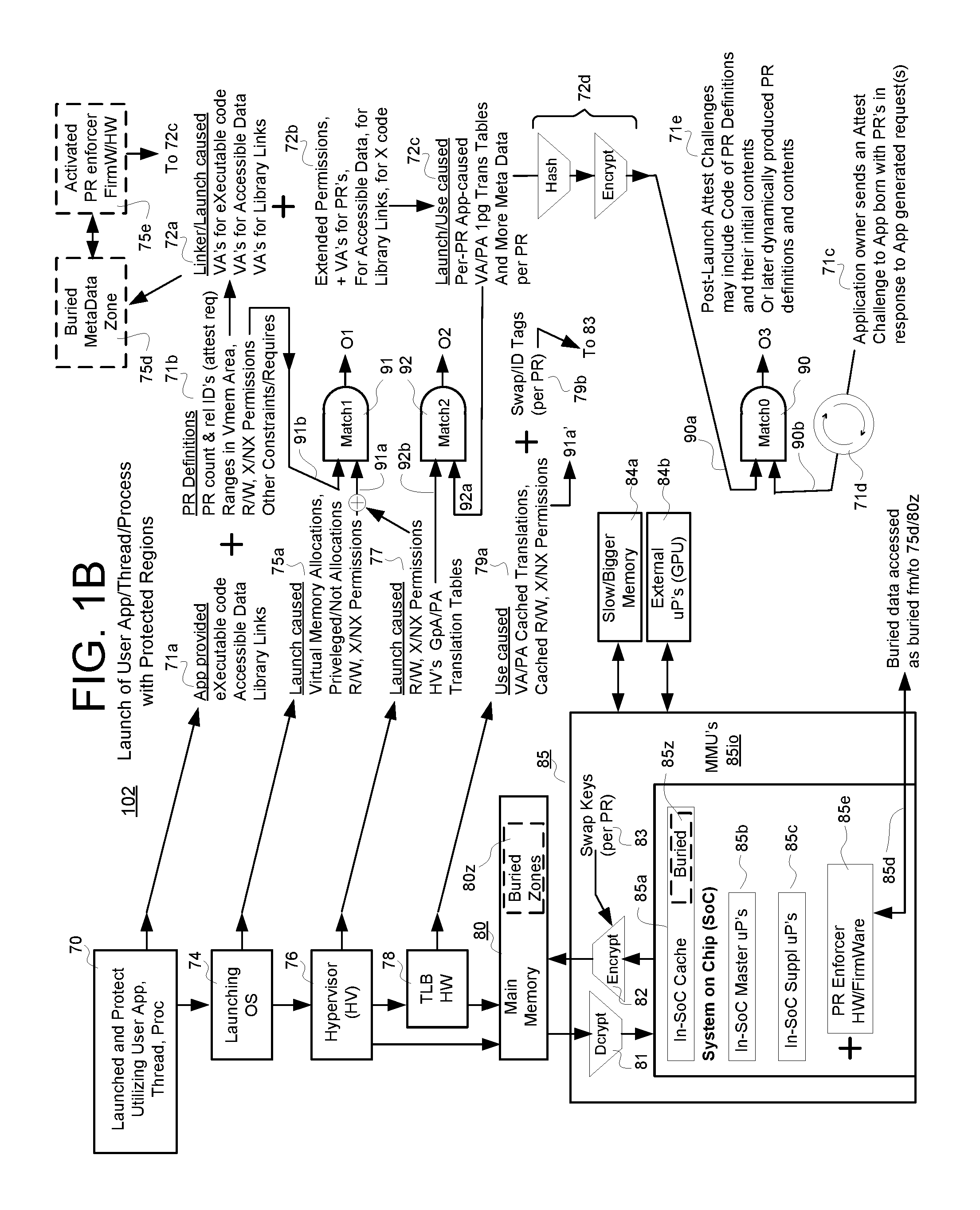
Protected regions
ActiveUS20160371496A1Difficult to compromiseLimit time-windowMemory architecture accessing/allocationUnauthorized memory use protectionOperational systemOperational requirements
A data processing machine is configured to include one or more buried memory zones that are not intelligibly accessible to user software and to operating system software or hypervisor software within the data processing machine. At least one of hardware and firmware are configured to intelligibly access at least one of the buried memory zones so as to store therein, metadata defining one or more extents of a respective one or more protected regions (PR's) that are constituted in other memory areas of the data processing machine. The stored metadata defines constraints for the corresponding PR's including at least one of corresponding operational constraints and / or operational requirements that respectively constrain the operations performed by or on the data of the PR's.
Owner:MICROSOFT TECH LICENSING LLC
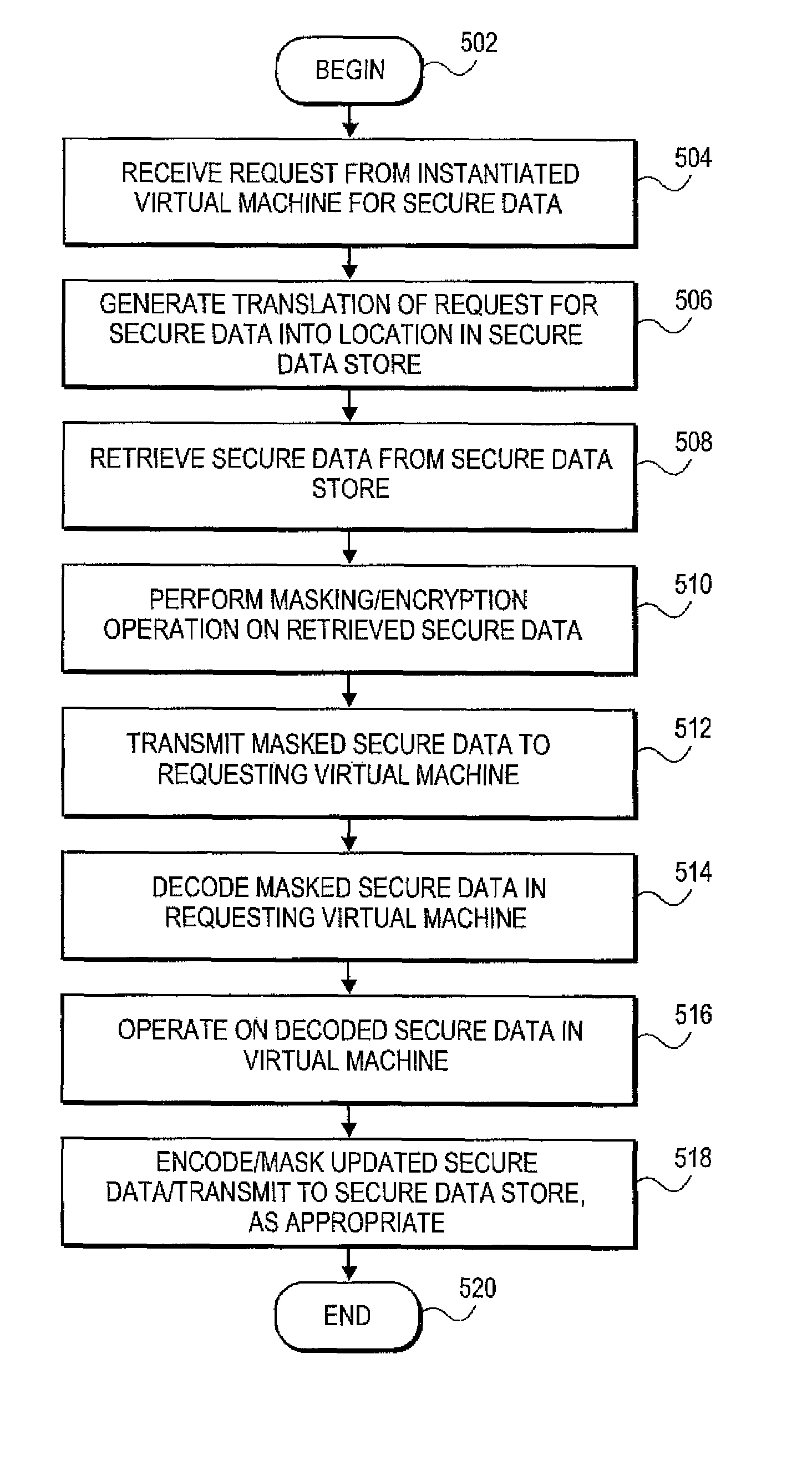
Systems and methods for management of secure data in cloud-based network
ActiveUS8108912B2Digital data processing detailsUser identity/authority verificationCloud baseSocial Security number
Embodiments relate to systems and methods for the management of secure data in a cloud-based network. A secure data store can store sensitive or confidential data, such as account numbers, social security numbers, medical or other information in an on-premise data facility. Regulatory and / or operational requirements may prohibit the migration or unprotected transmission of the secure data to the cloud. An operator can instantiate a set of virtual machines to access and process the secure data, for example to process online purchase transactions. To prevent unauthorized disclosure of the secure data, the secure data store can receive data access requests via a translation module that translates the secure data. The secure data store can retrieve and transmit the secure data using a protection mechanism such as a masking and / or encryption mechanism, avoiding the unprotected transport or exposure of that data to the cloud.
Owner:RED HAT
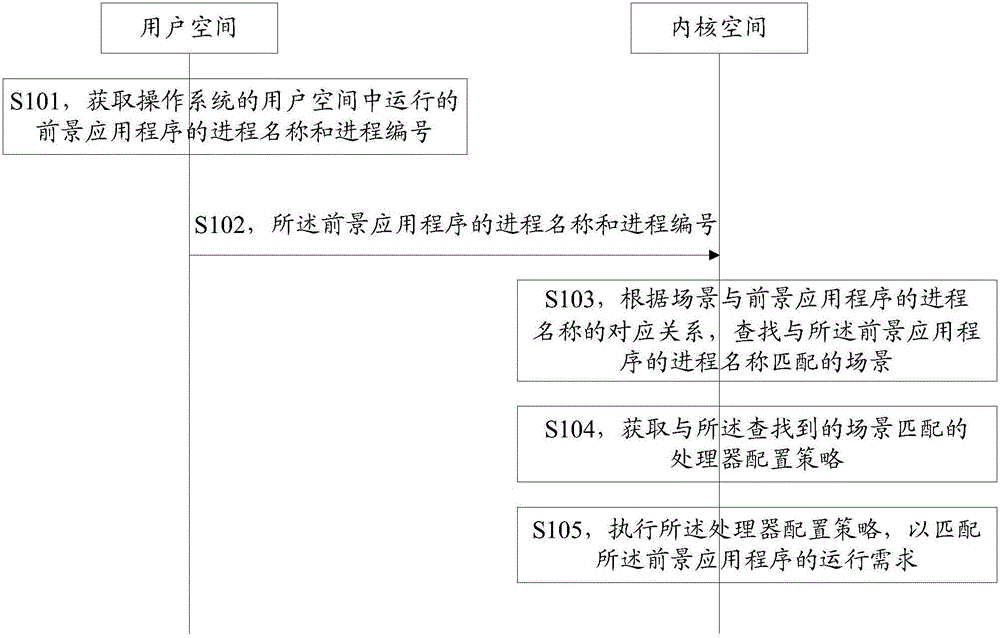
Foreground application program scene synchronization method, apparatus and system
ActiveCN106095592AImprove performanceReduce power consumptionResource allocationProgram synchronisationOperational systemScene matching
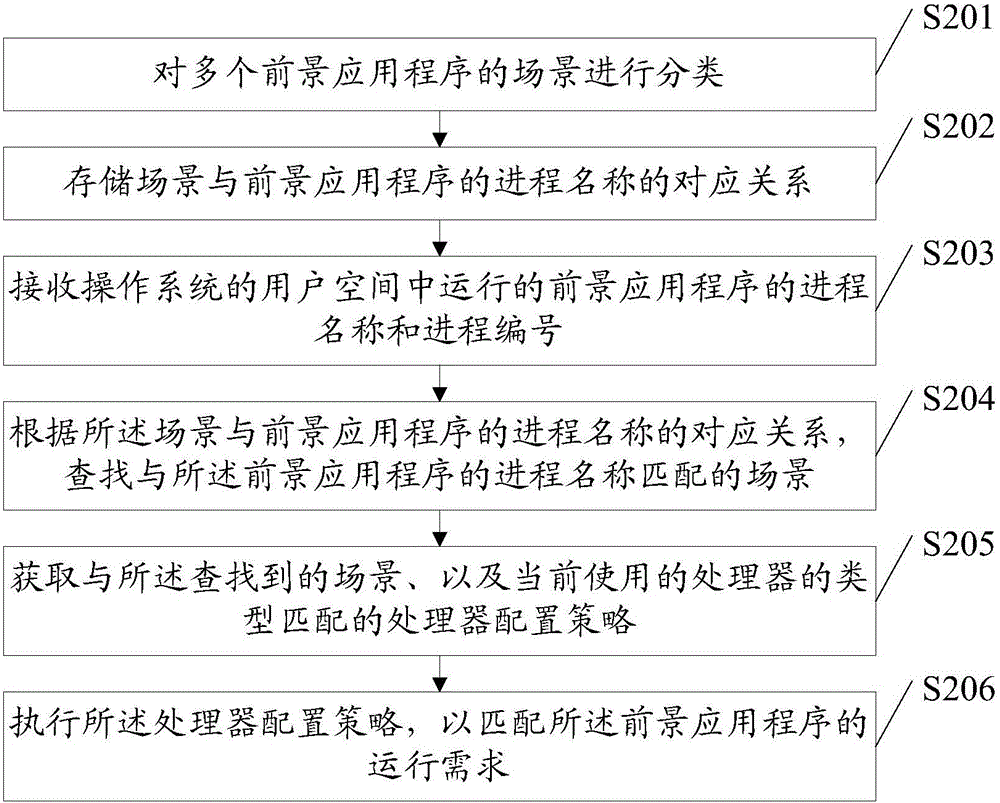
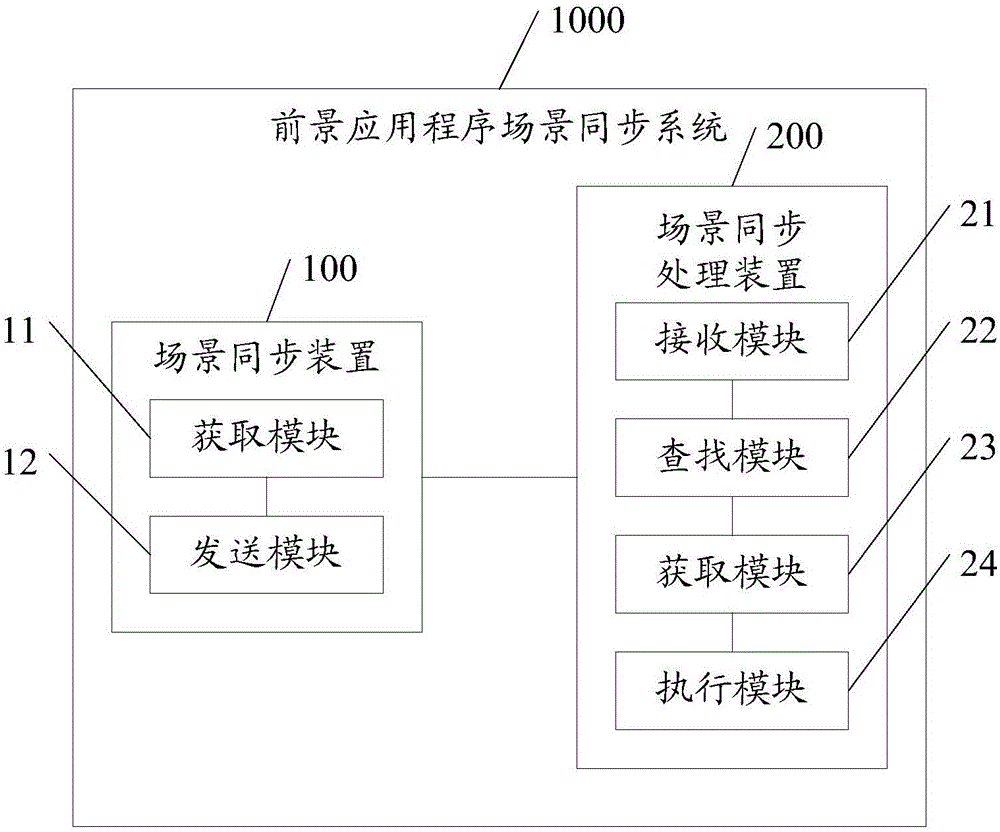
Embodiments of the invention disclose a foreground application program scene synchronization method, apparatus and system. By receiving a process name and a process number of a foreground application program running in the user space of the operating system, the kernel space of the operating system searches a scene matching the process name of the foreground application program according to the corresponding relationship between the scene and the process name of the foreground application program, a processor configuration policy that matches the searched scene is obtained, and the processor configuration policy is executed to match the operational requirements of the foreground application program, so that configuration of the processor can precisely match the operational requirements of the foreground application program, system performance is optimized, and power consumption is reduced.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Scalable transform wideband holographic communications apparatus and methods
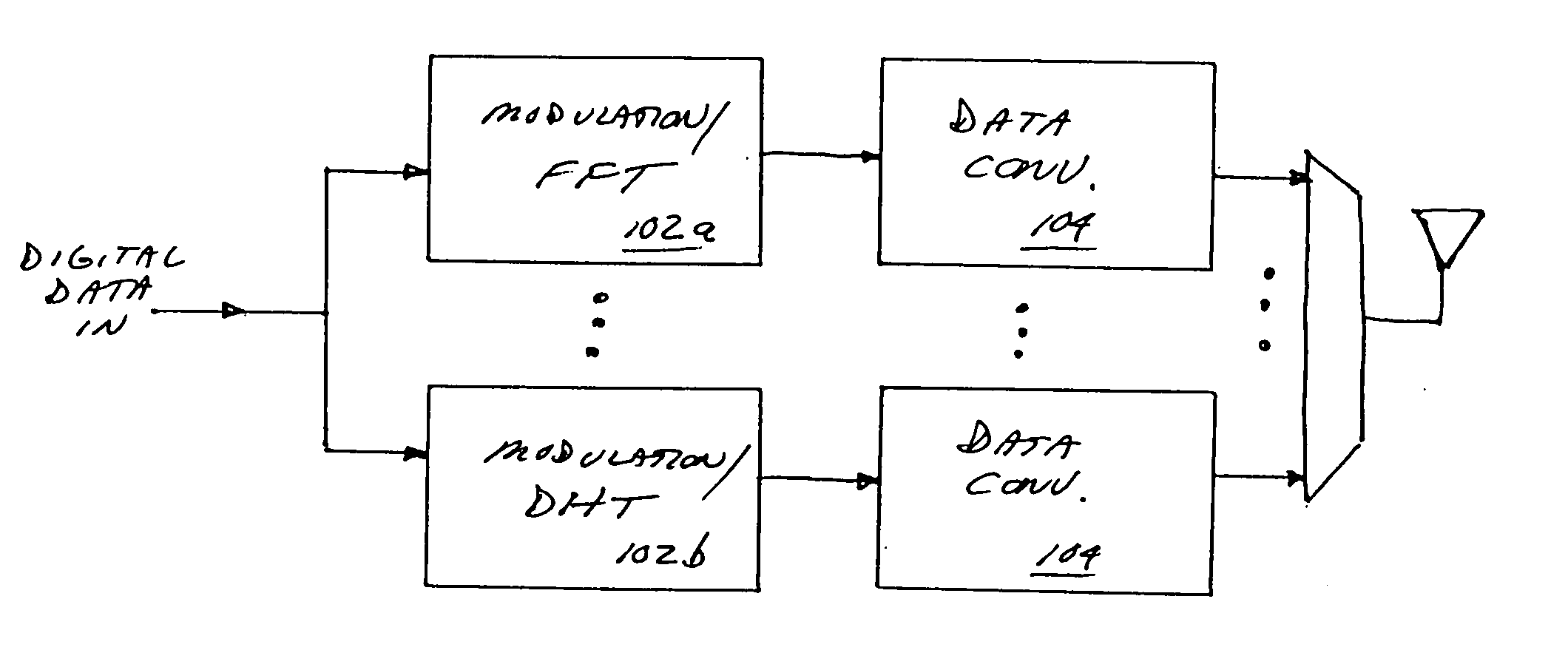
Improved apparatus and methods for utilizing holographic waveforms for a variety of purposes including communication. In one exemplary embodiment, the holographic waveforms are transmitted over an RF bearer medium to provide, inter alia, highly covert and robust communications. The baseband processor(s) are configured to selectively scale their architecture for performing the mathematical transforms (e.g., Fourier) or other operations (such as high speed phase-coding) in order to meet one or more operational requirements, such as reduced power consumption, changes in data rate, etc.
Owner:HOLOWAVE
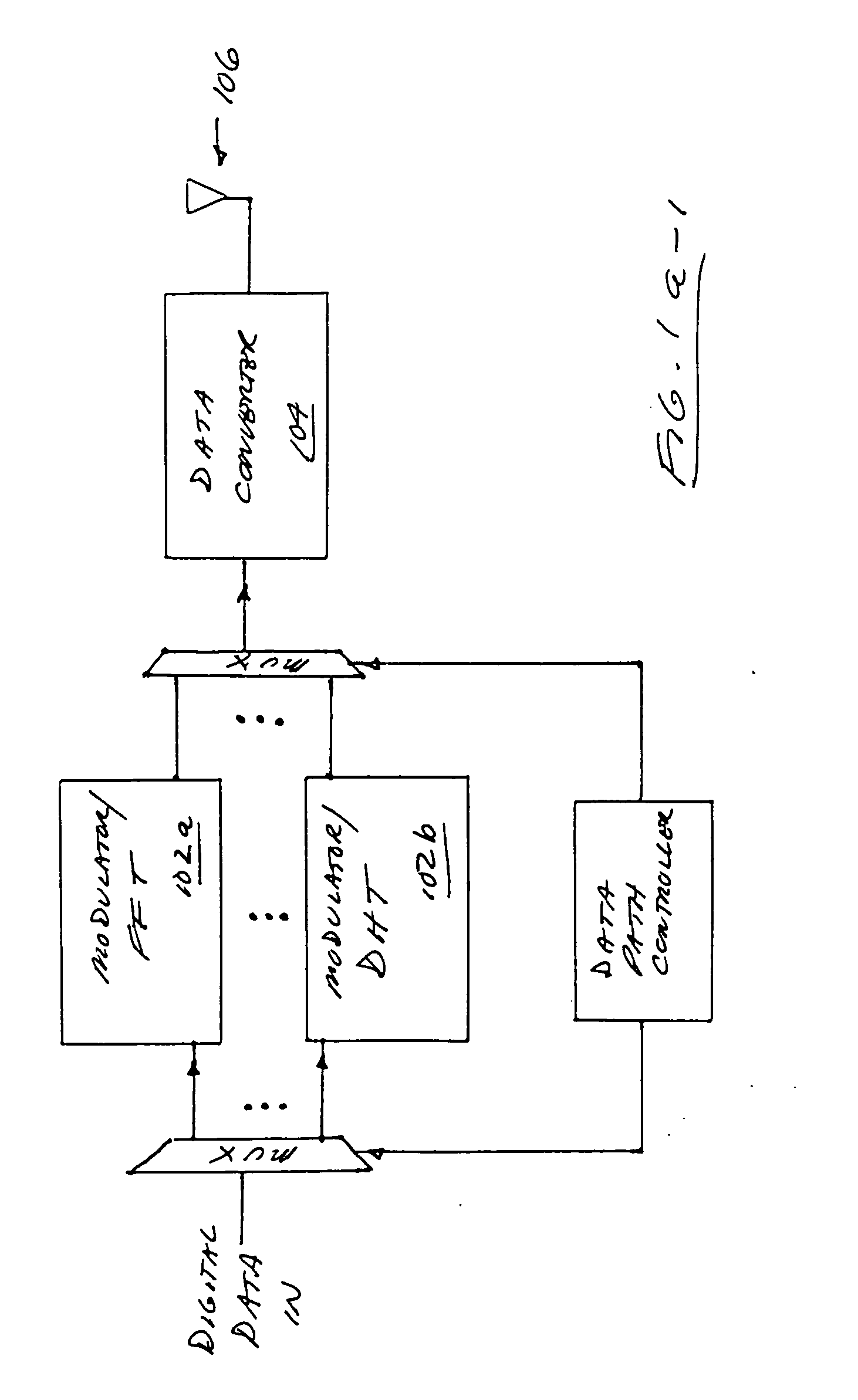
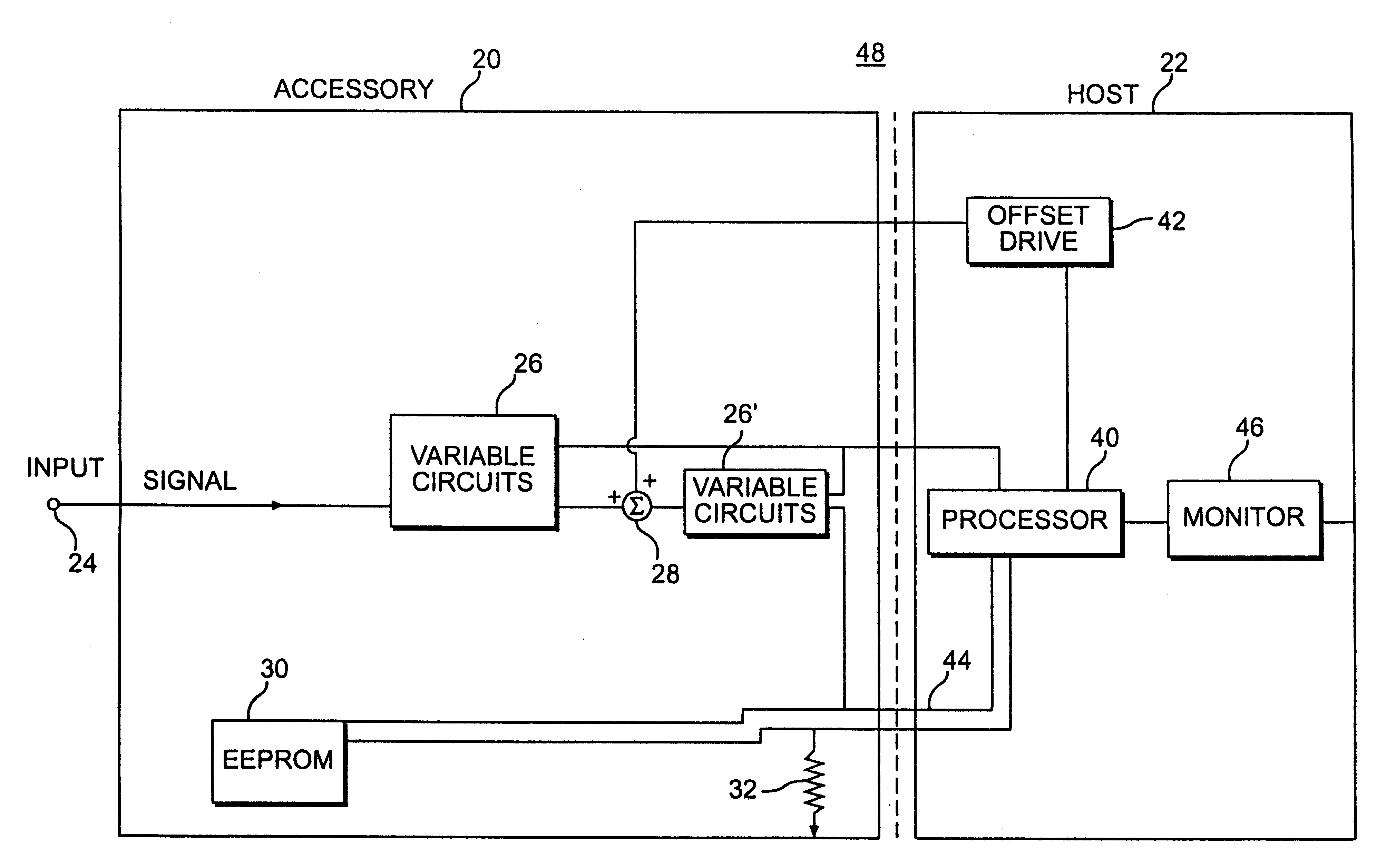
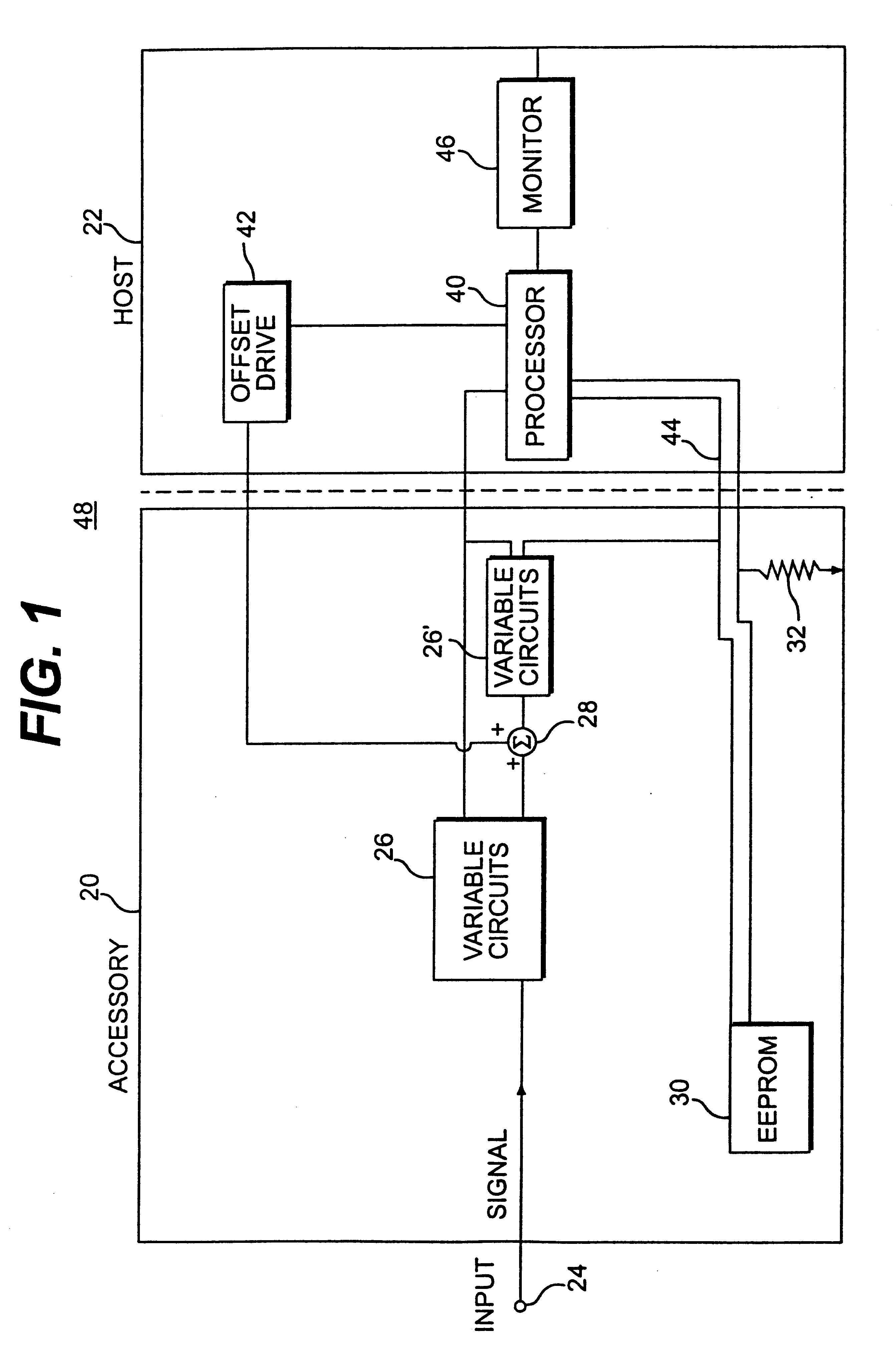
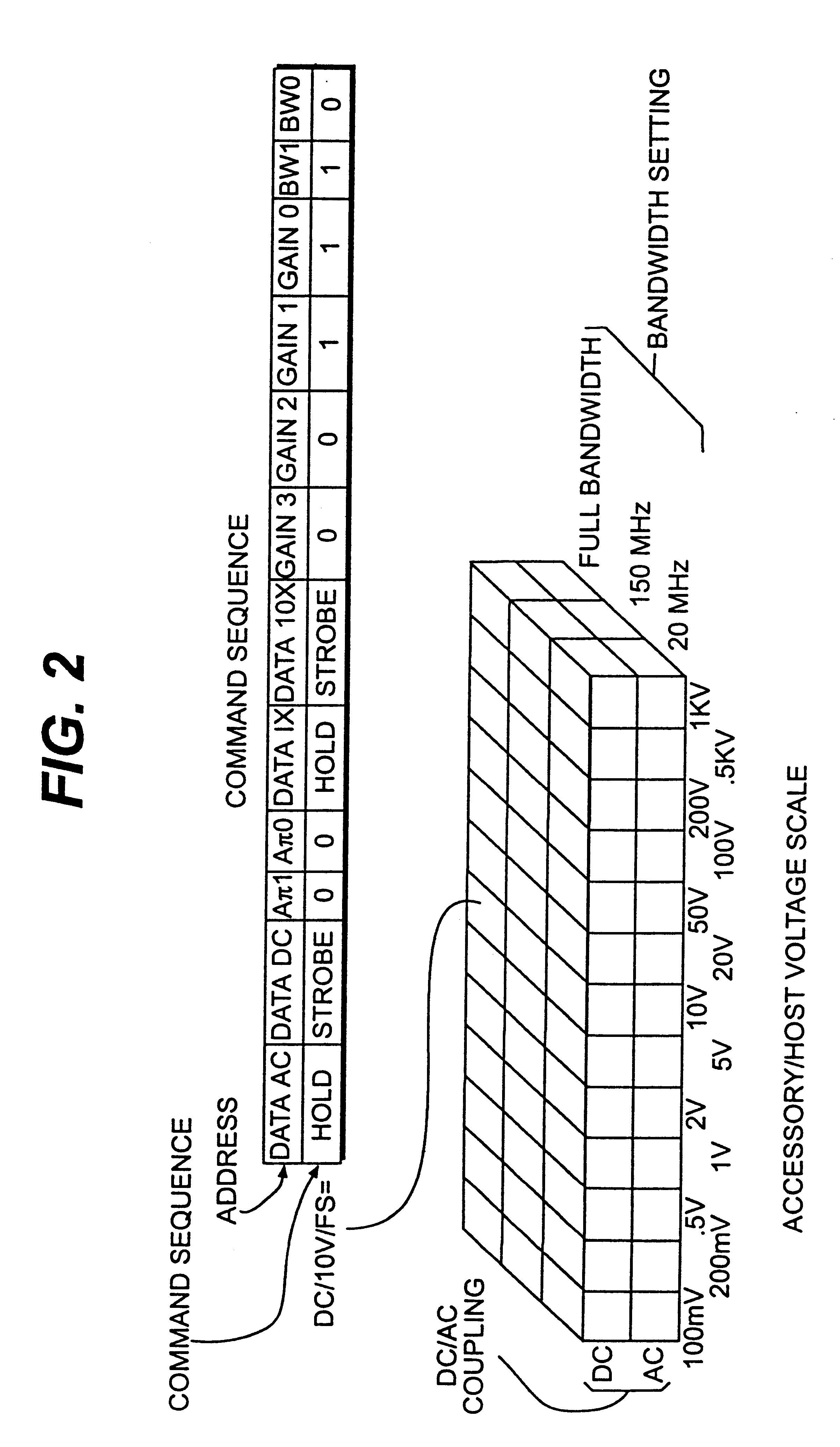
Accessory with internal adjustments controlled by host
InactiveUS6232764B1Special tariff metersElectrical measurement instrument detailsElectronic instrumentOperational capabilities
Owner:TEKTRONIX INC
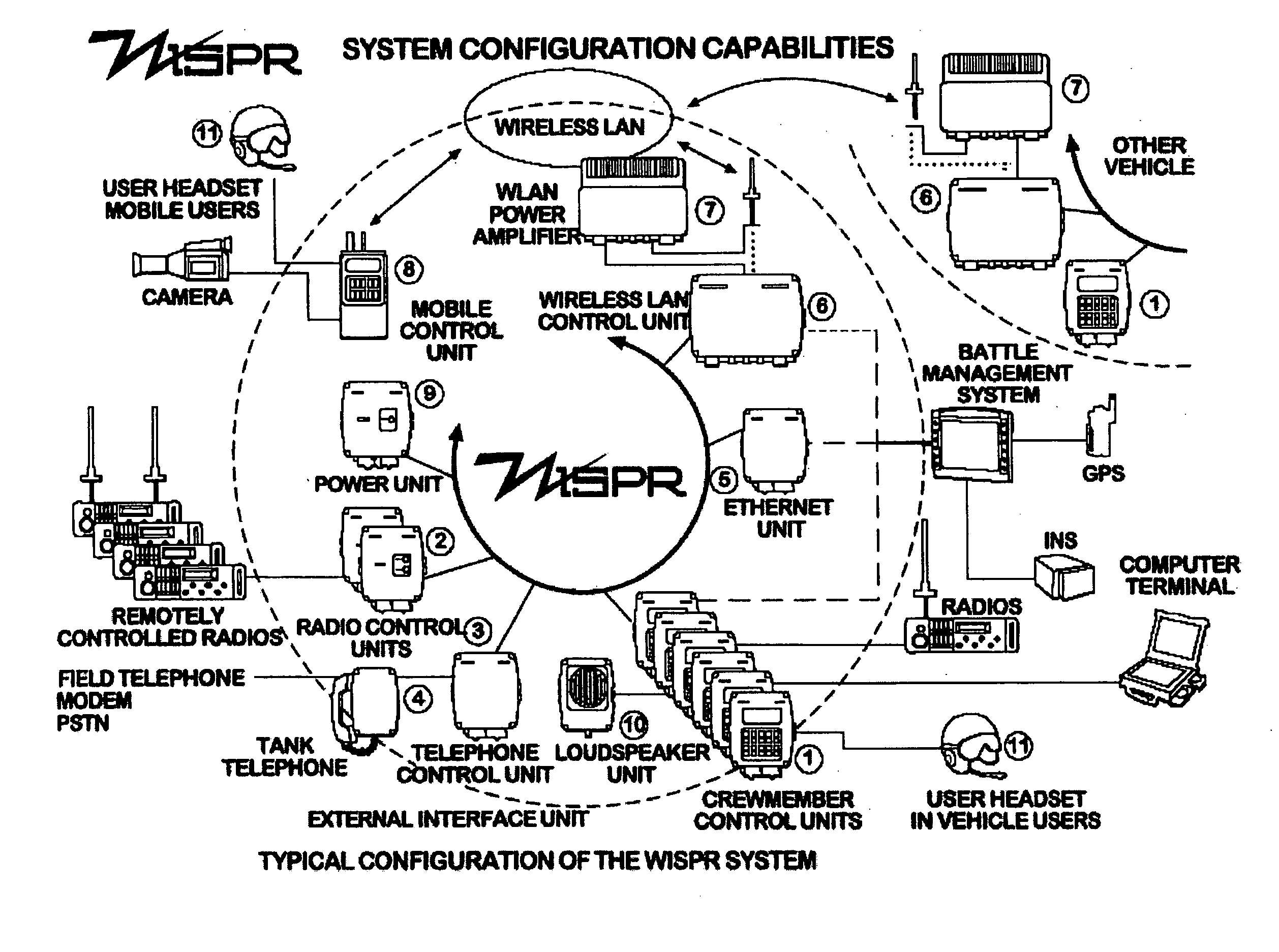
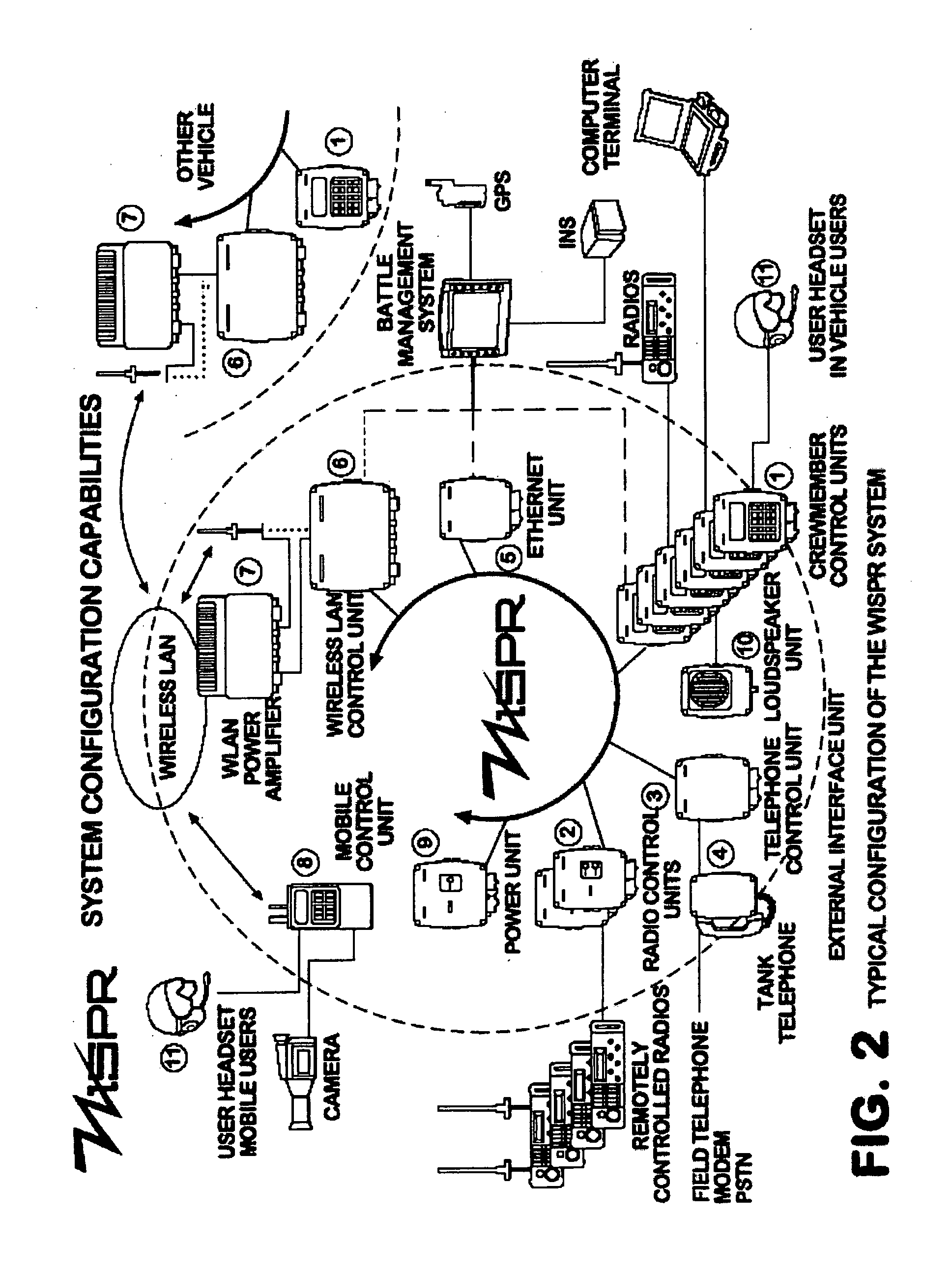
Wideband intercom and secure packet radio (WISPR)
InactiveUS20050232207A1Improve operational capabilitiesHigh degreeTransmission systemsNetwork topologiesAnti jammingSystem configuration
A Wideband Intercom and Secure Packet Radio (WISPR) system includes a state-of-the-art digital, fully programmable communication system that provides internal and external communication to the operators of any type of vehicle. The WISPR system includes a dedicated secure radio with anti-jamming capabilities in order to support a Wireless Local Area Network (WLAN) and is able to provide voice and data communication over radios, analog wires and data / voice over field telephones and tank telephones. The system supports a variety of user specified operational requirements (e.g. hierarchy plans, closed group conference, wired or wireless remote radio control, tactical data reception, independent listen / talk functions) and has the capacity for dynamic adaptation to field requirements and the potential for expansion in order to fulfill the future needs of the Armed Forces. The WISPR system configuration is adaptable according to the type of platform and the particular operational requirements for a specific application.
Owner:INTRACOM DEFENSE ELECTRONICS SYST
Vehicle lighting
A vehicle lighting system is provided where the signal lights are configured so that their performance may be adapted based on ambient conditions and operational requirements. The signal lights are controlled to improve their effectiveness and efficiency.
Owner:EKCHIAN GREGORY J +1
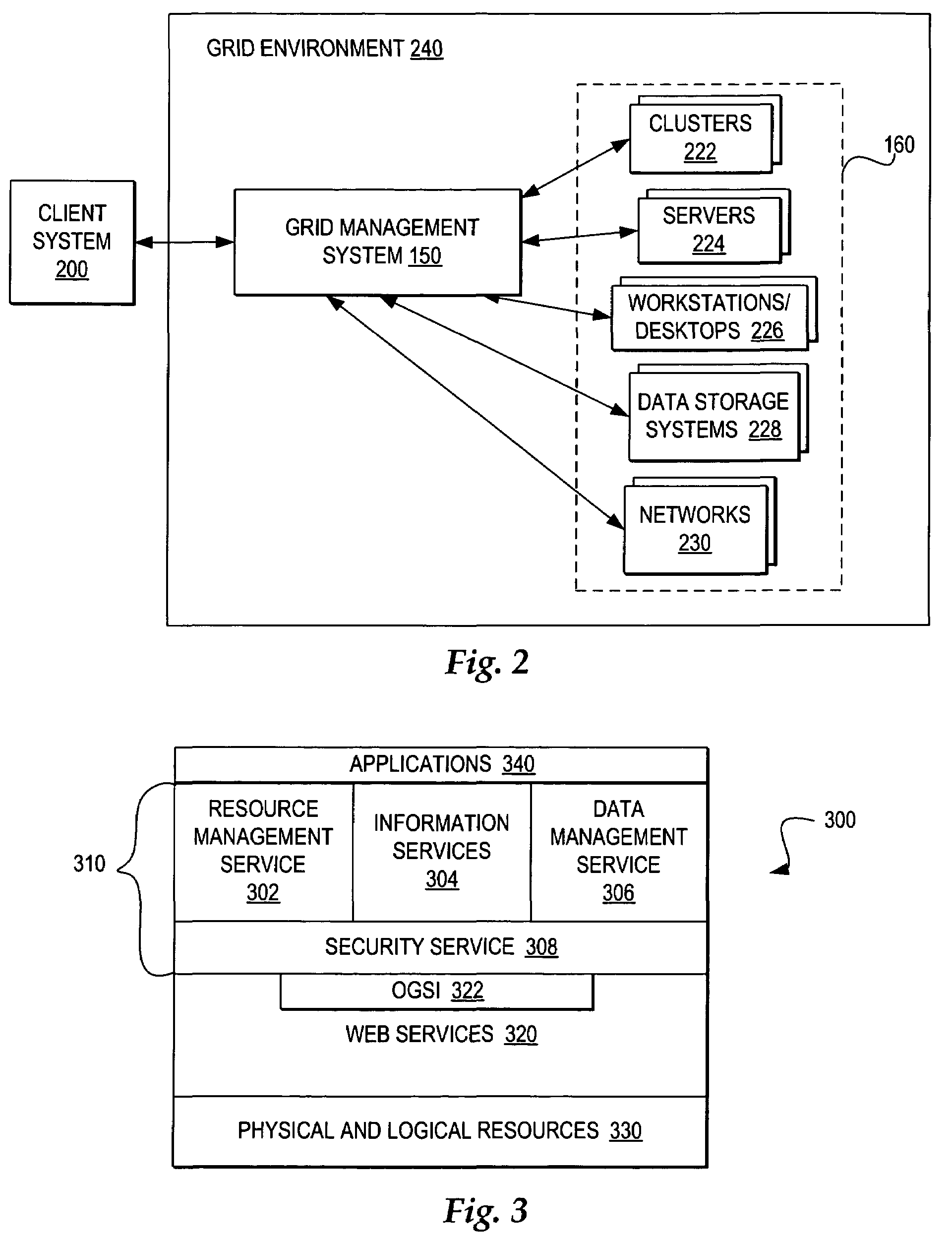
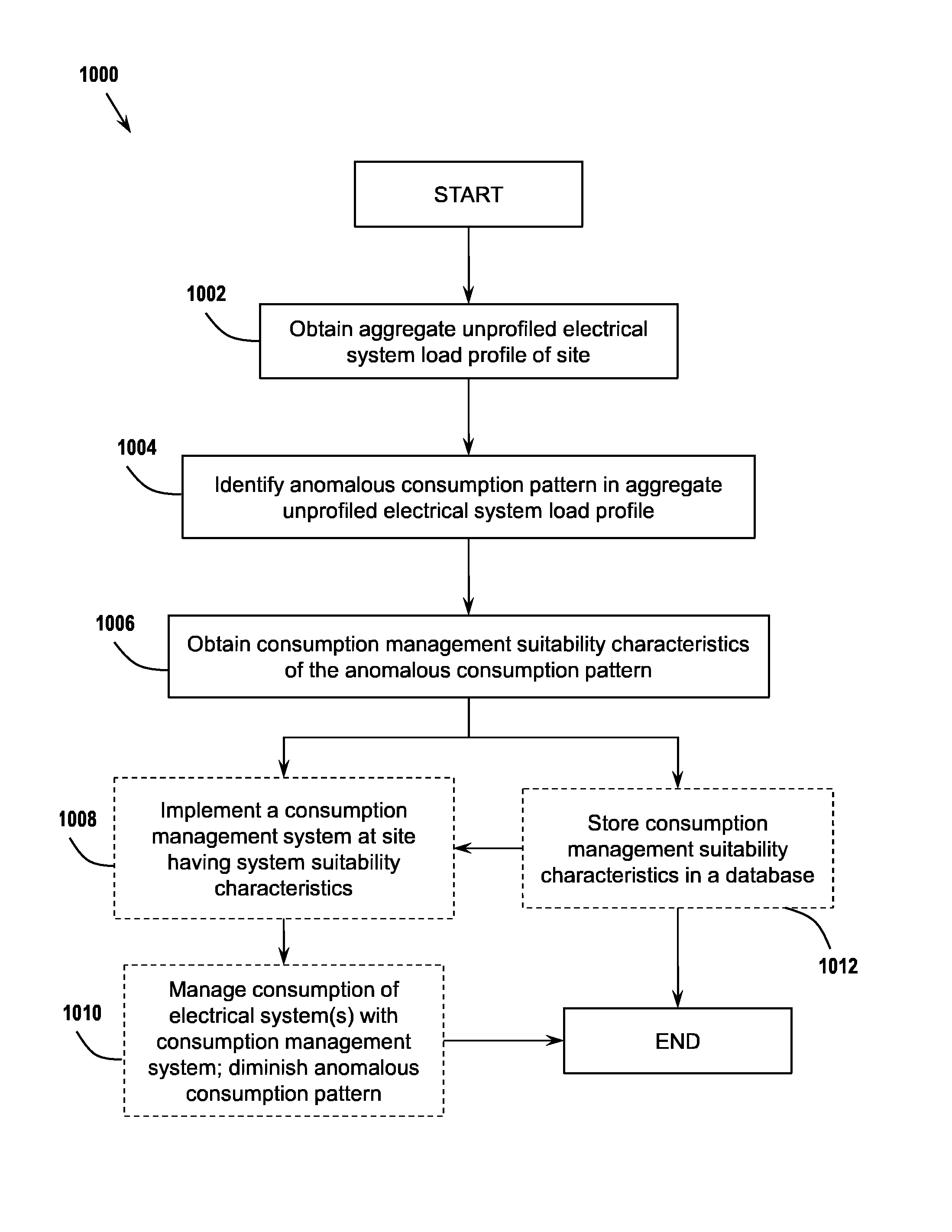
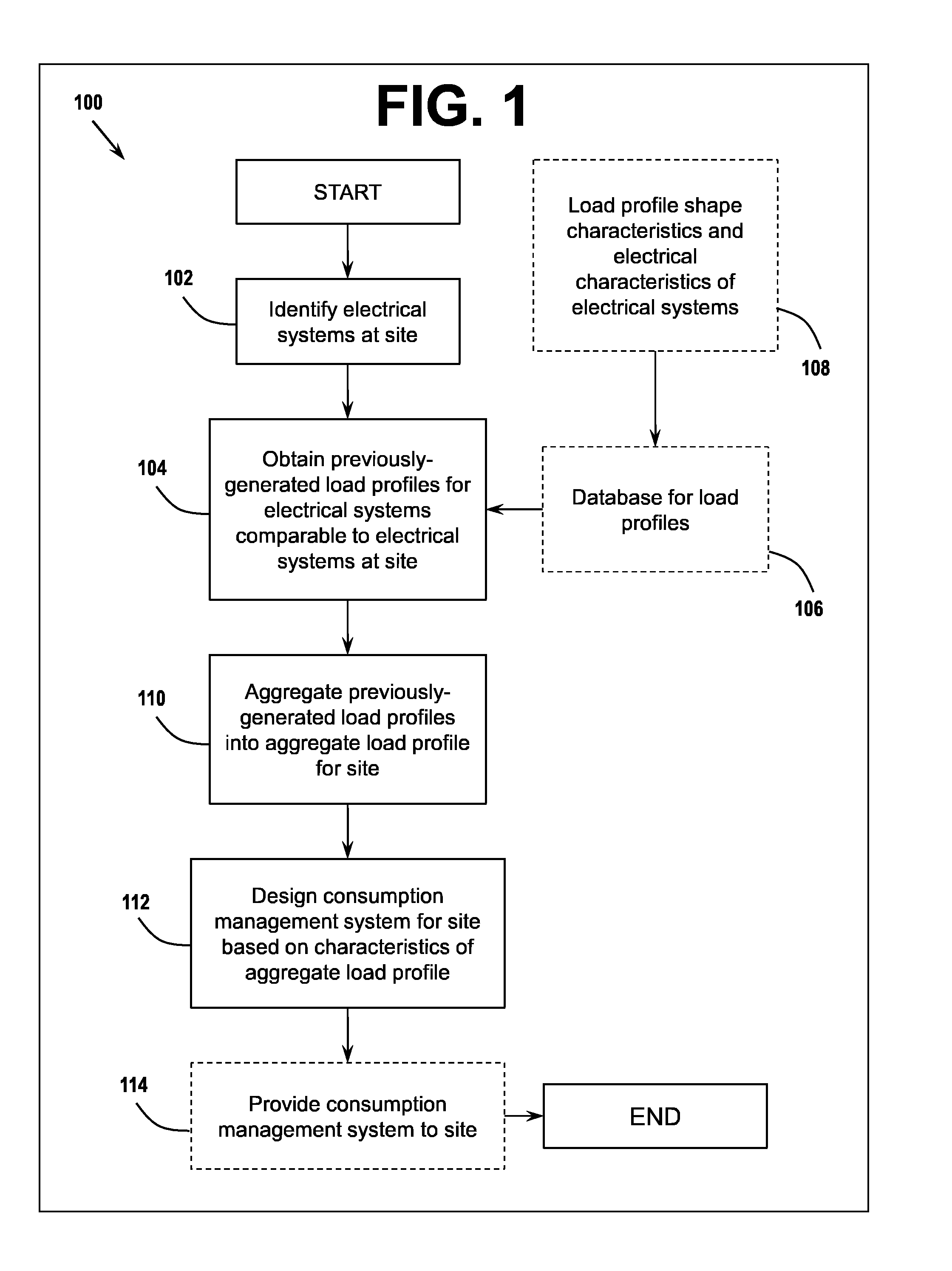
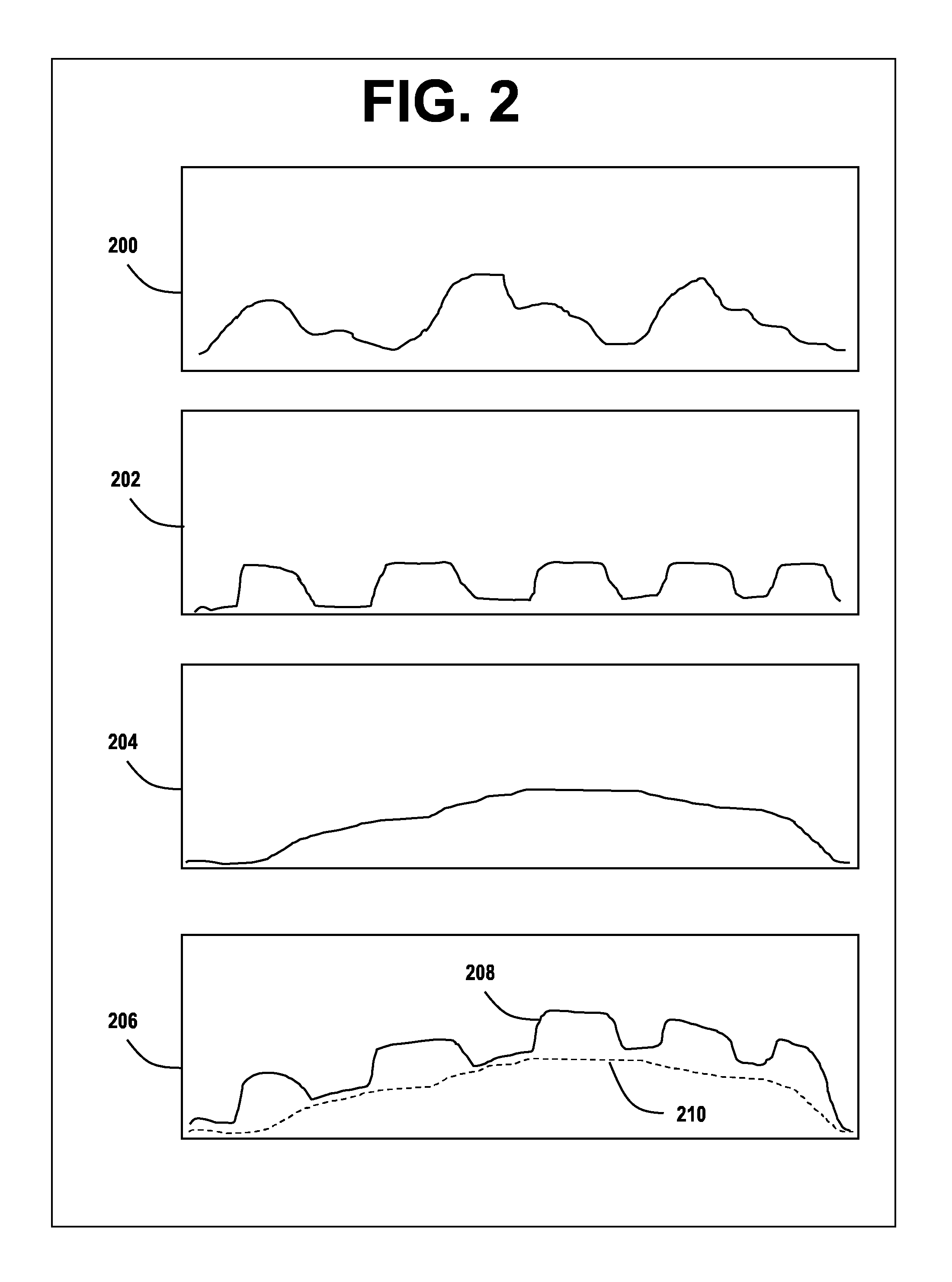
Processing Load Profiles for Consumption Management Systems
ActiveUS20130231790A1Faster and easy energy consumption auditingEffectively manage loadLevel controlVolume/mass flow measurementEngineeringLoad profile
Methods and systems using aggregated electrical system load profiles in determining additional load profiles, and determining consumption management system characteristics, features, and operating requirements at a site are disclosed, along with methods of generating and maintaining databases of load profile information and consumption management system requirements. By using some embodiments of the methods and systems described herein, it is faster and easier to design and implement effective consumption management systems, to determine problematic electrical systems at a site, and to diminish anomalous consumption patterns in an aggregate unprofiled electrical system load profile.
Owner:ENGIE STORAGE SERVICES NA LLC
Electricity-saving method of vehicle-mounted CAN bus network
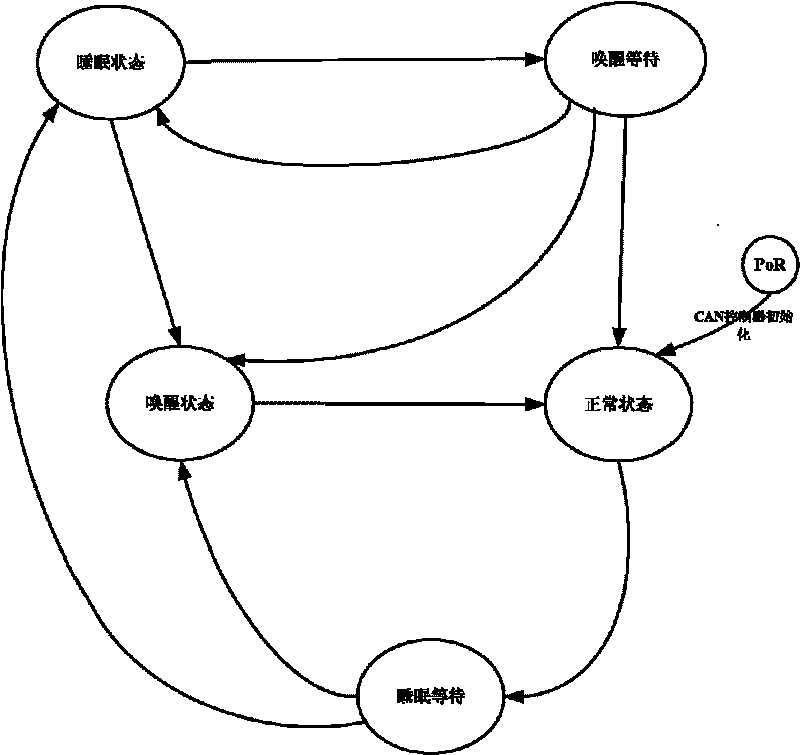
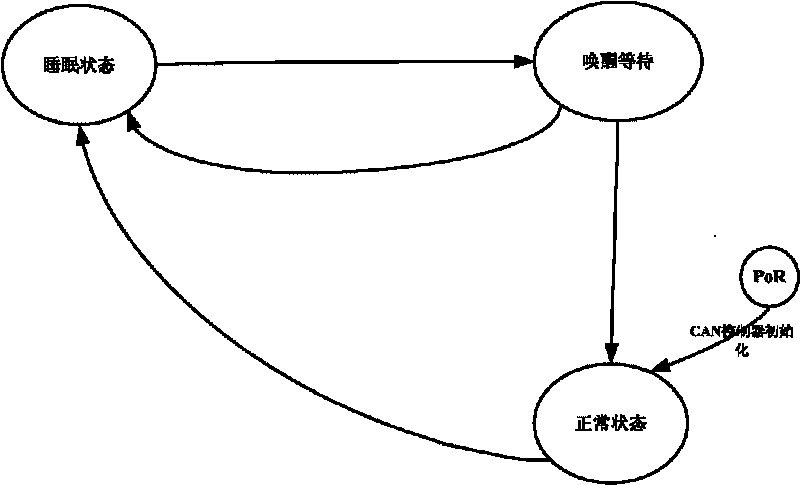
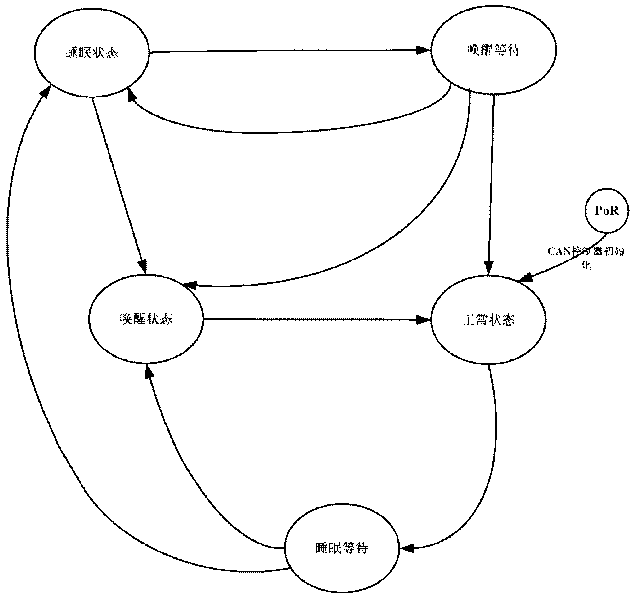
ActiveCN101700762AGuaranteed stabilityAvoid frequent switching transitionsElectric/fluid circuitBus networksElectricityOperational requirements
The invention provides an electricity-saving method of vehicle-mounted CAN bus network, belonging to the electronic technical field. The method solves the problem that electric energy is transported to existing automobile electric equipment no matter the equipment works or not to cause electric energy waste. The electricity-saving method of the vehicle-mounted CAN bus network is as follows: a CAN bus is provided with controller modules used as nodes, and the method can lead the control modules to enter a low power consumption mode in the case of no operational requirement under program setting, can switch each controller module among various states, thereby achieving the electricity-saving purpose when the controller modules are in the low power consumption state in the case of no tasks required to be processed.
Owner:南通迈程汽车技术有限公司
Configurable frame work for testing and analysis of client-side web browser page performance
ActiveUS20110270975A1Detecting faulty hardware by remote testDigital computer detailsComputer resourcesWeb browser
The present invention features methods, computer program products and apparatuses for measuring client-side computer system performance that features identifying one of a plurality of uniform resource locator addresses contained on a server computing system, with each of the uniform resource locator addresses being associated with computing resources. The computing the computing resources associated with any one of the plurality of uniform resource locator addresses being different from the computer resource corresponding to the remaining uniform resource locator addresses. The computing resources are accessible through a web-browser that accesses the same the computing resources associated with the one of the plurality of uniform resource locator addresses. Measured are metrics of the interactions between the web-browser and the computing resources associated with the one of the plurality of uniform resource locator addresses. It is determined whether the metrics satisfy pre-determined operational requirements.
Owner:SALESFORCE COM INC
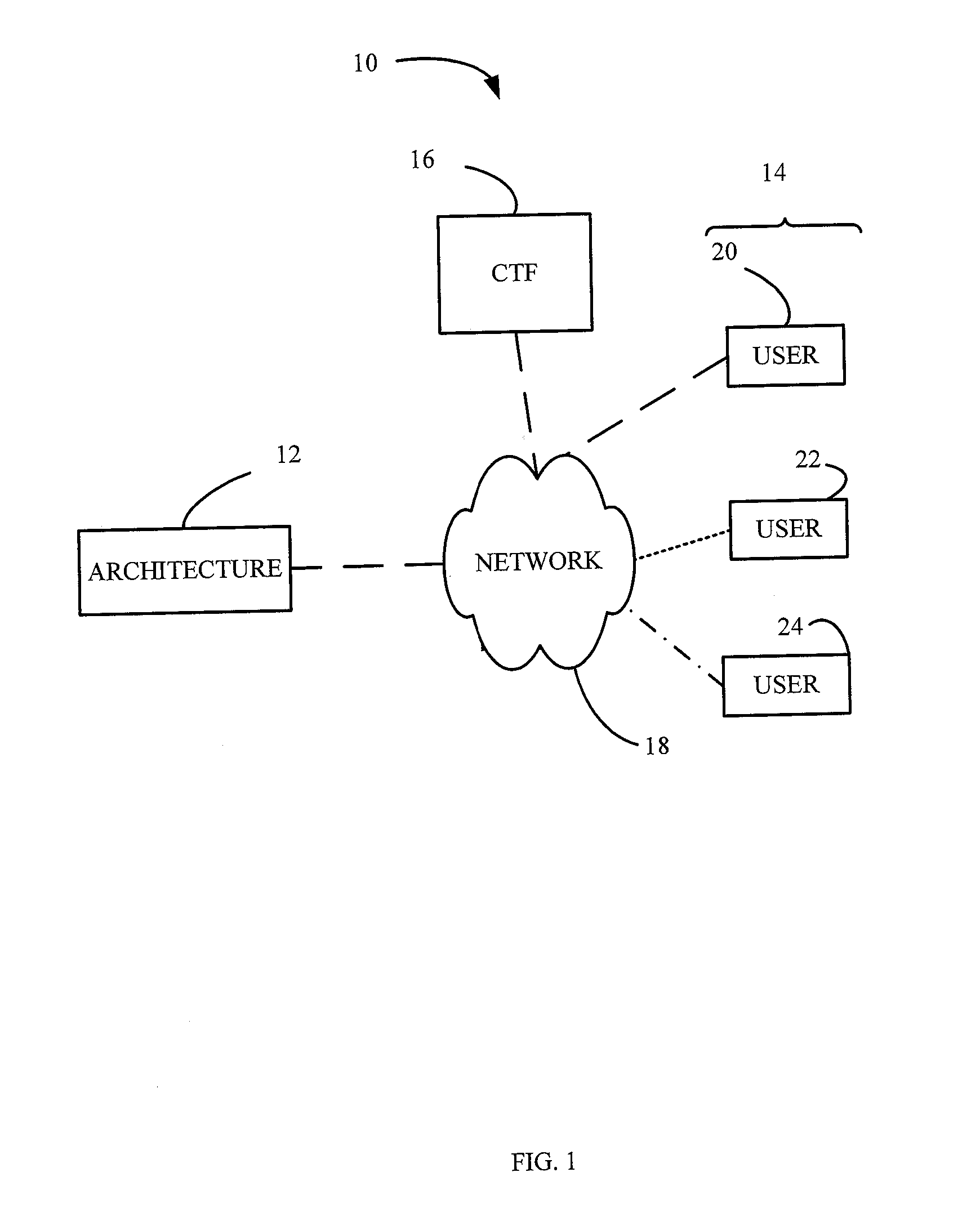
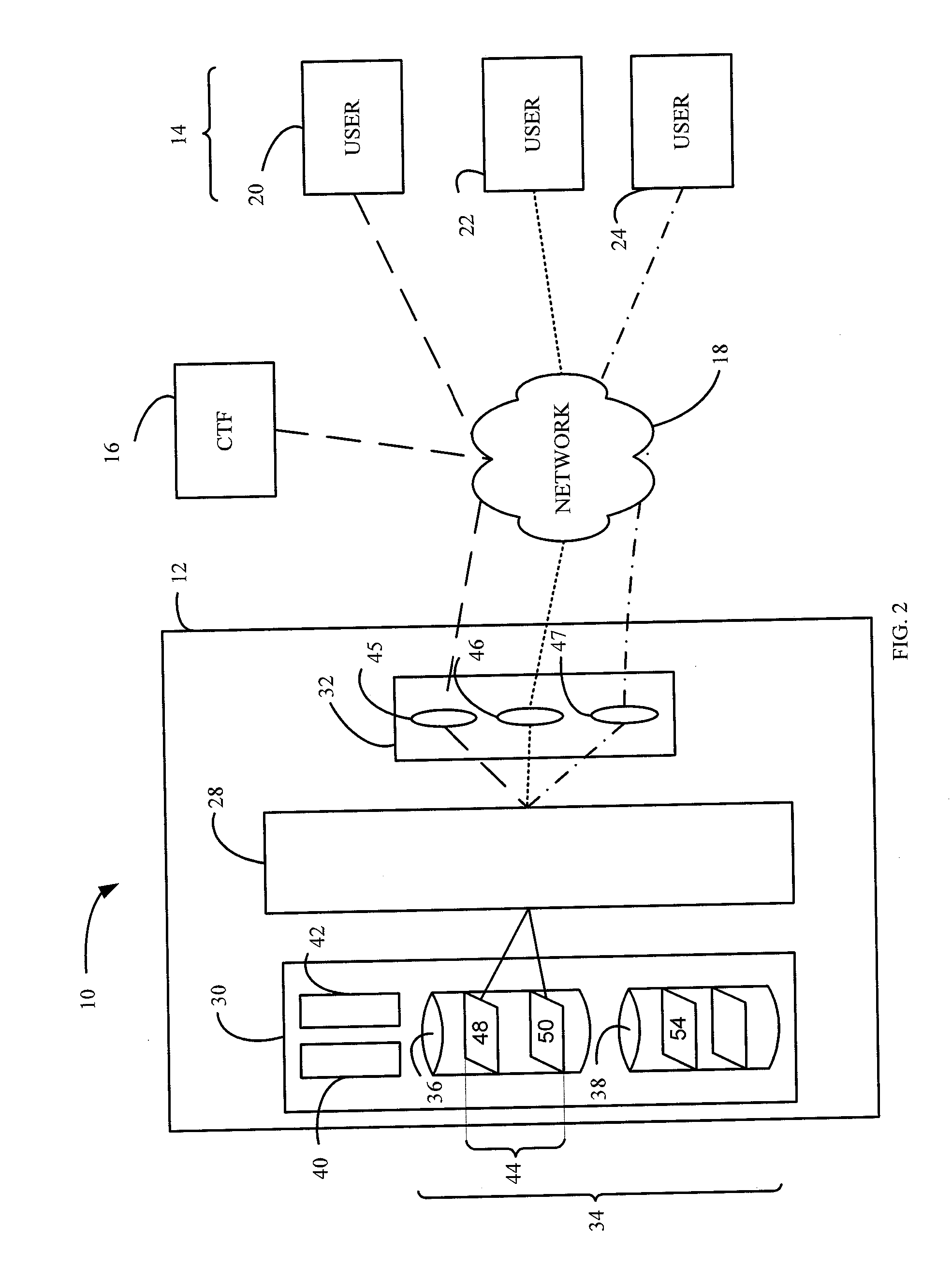
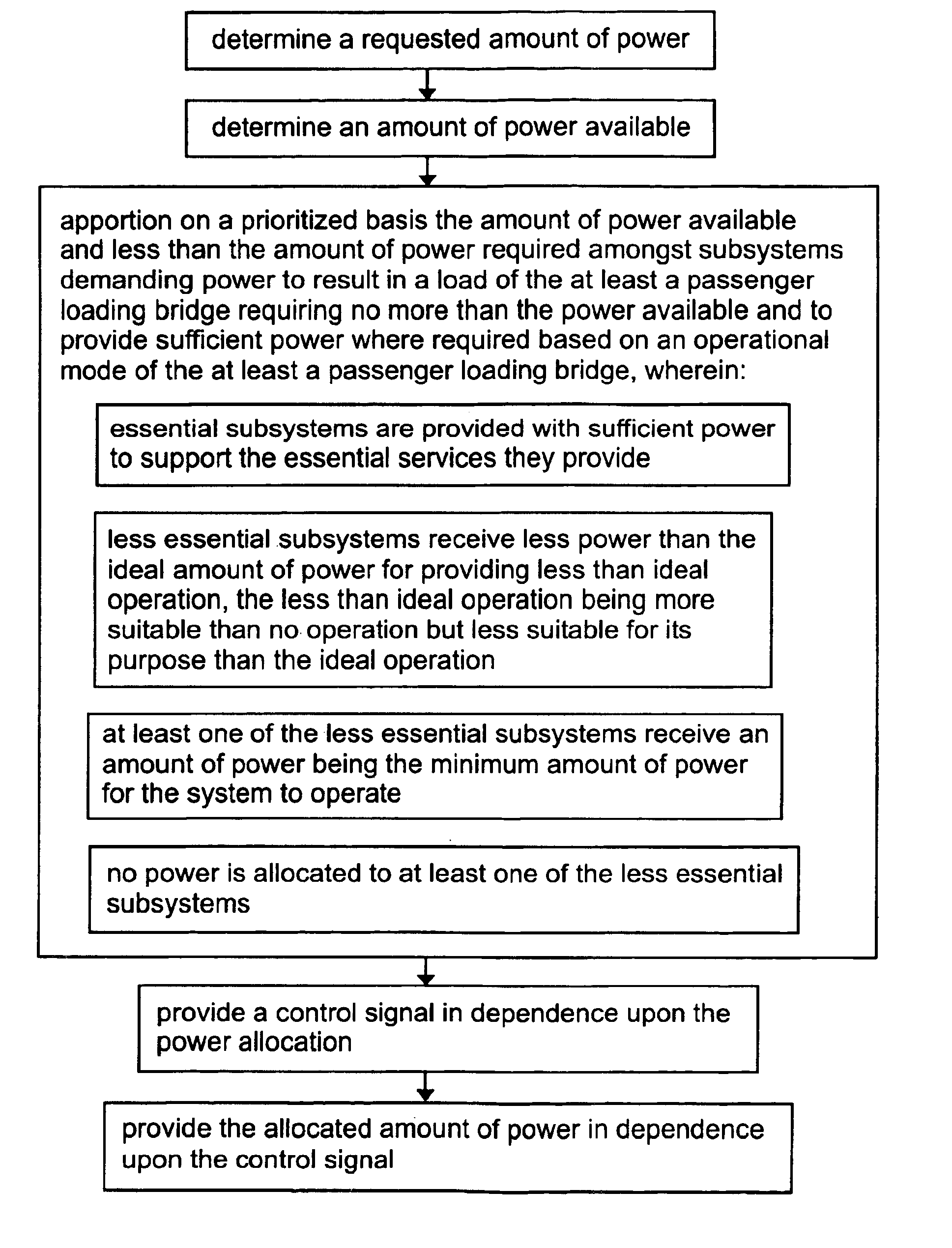
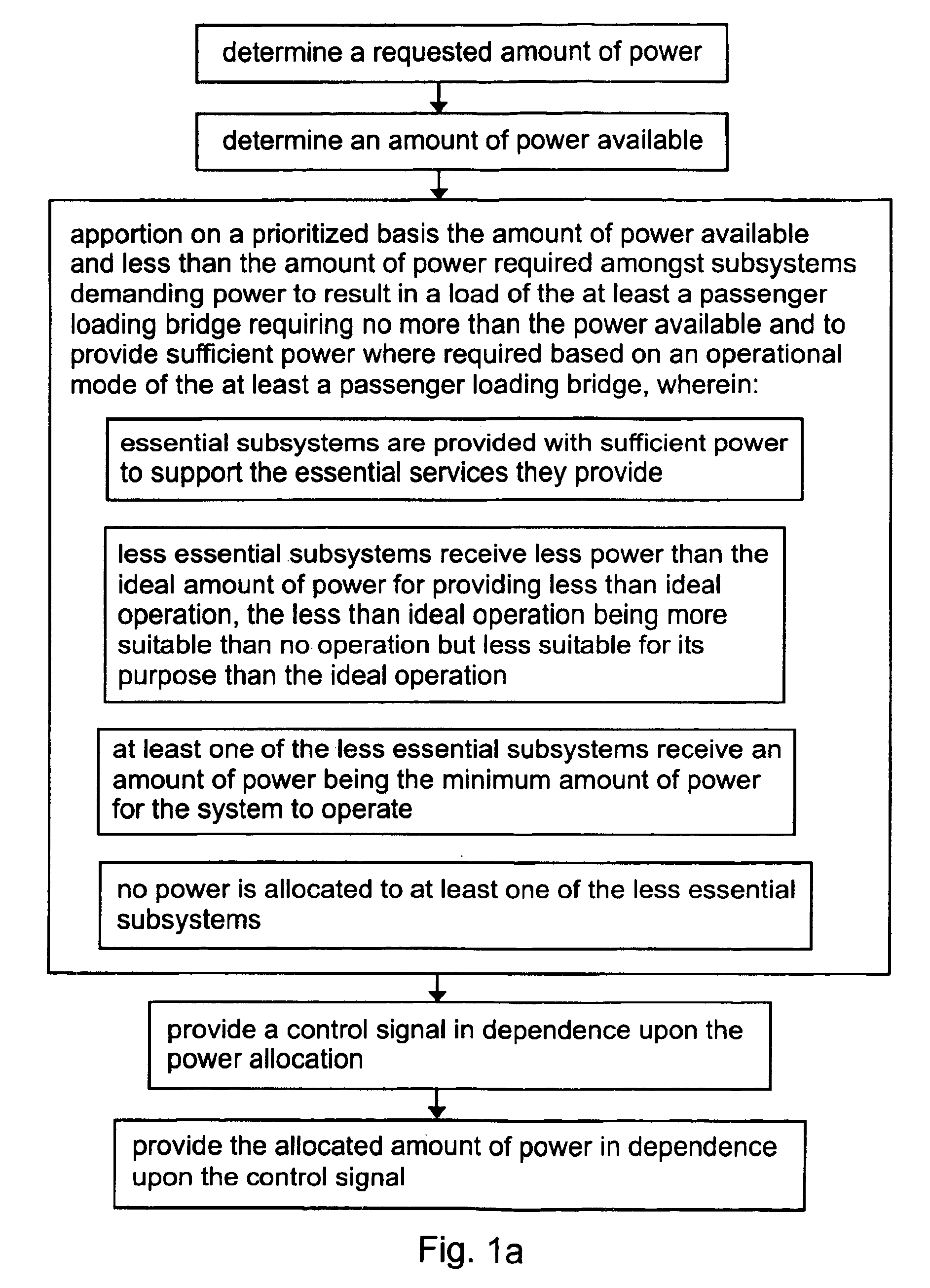
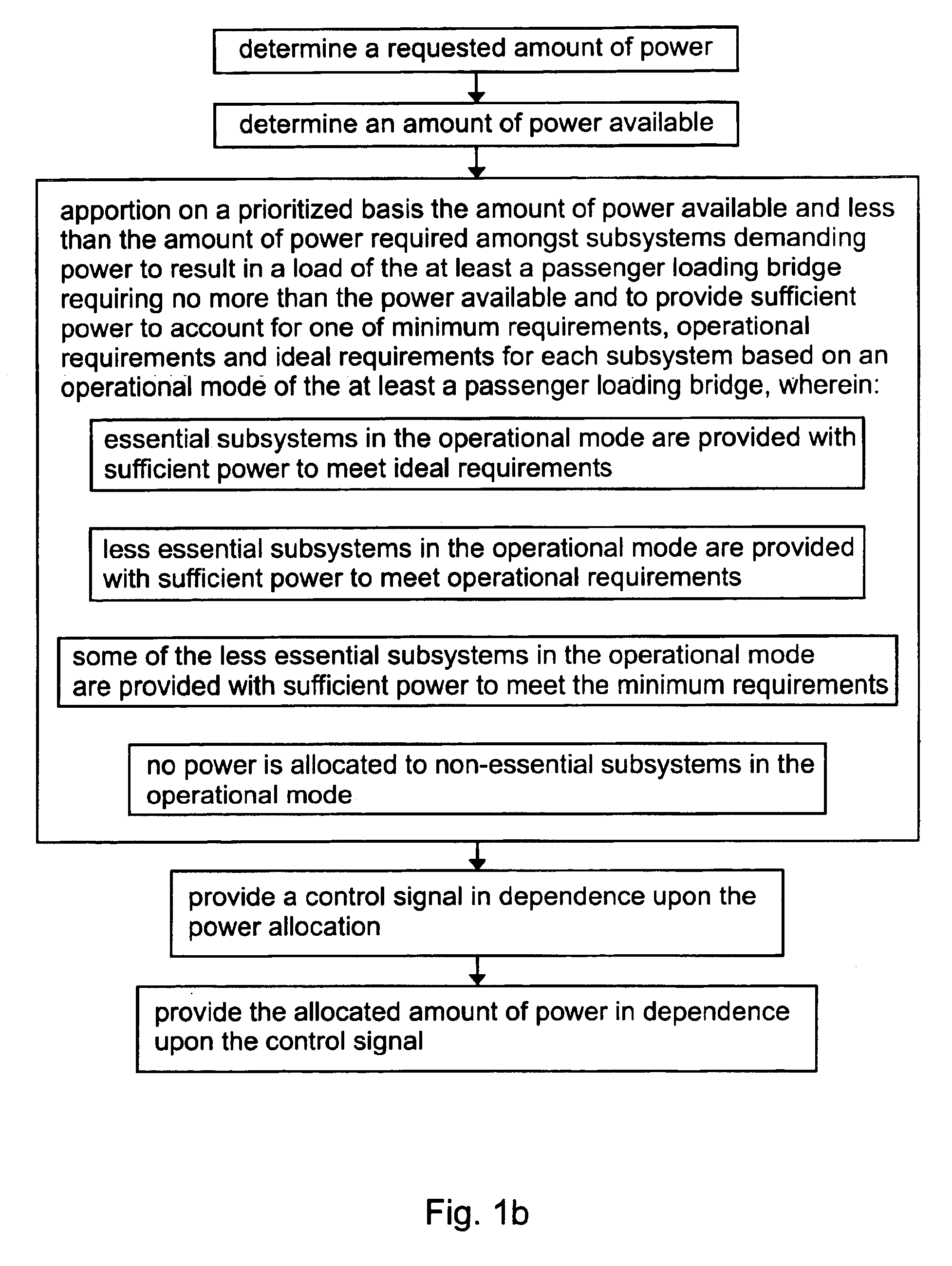
Power allocation control in an overdemand situation of an airport support system
InactiveUS6925363B2Sufficient powerMechanical power/torque controlDc network circuit arrangementsSupporting systemDistribution control
The present invention relates to a method and controller for controlling power allocation in an overdemand situation of at least a passenger loading bridge. A requested amount of power and an amount of power available are determined. The amount of power available and less than the amount of power required is then apportioned on a prioritized basis amongst systems of the at least a passenger loading bridge demanding power to result in a load of the at least a passenger loading bridge requiring no more than the power available and to provide sufficient power to account for one of minimum requirements, operational requirements and ideal requirements for each system based on an operational mode of the at least a passenger loading bridge. The amount of power for provision to each system is determined in dependence upon a priority of the system for the operation of the at least a passenger loading bridge in a predetermined mode of operation.
Owner:AMERIBRIDGE
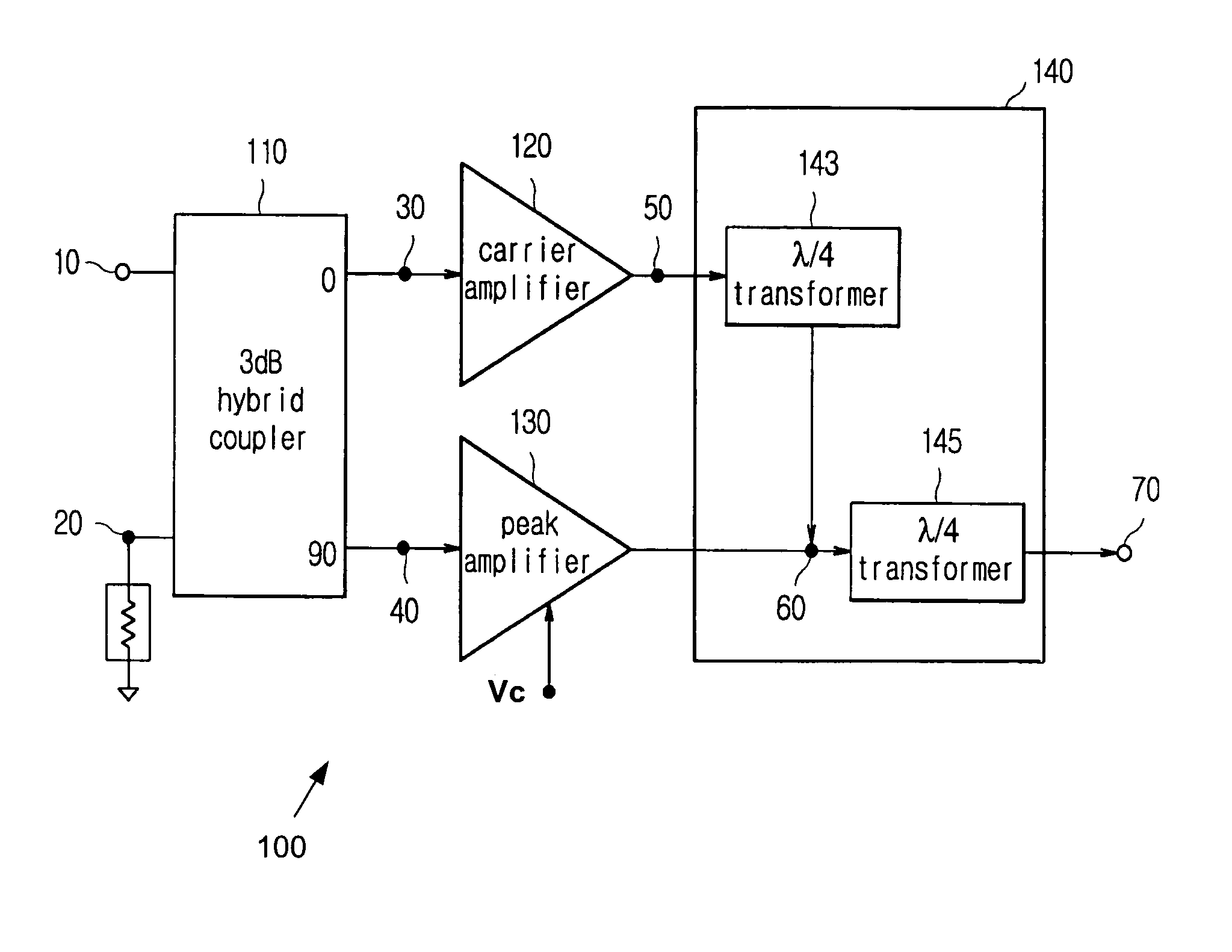
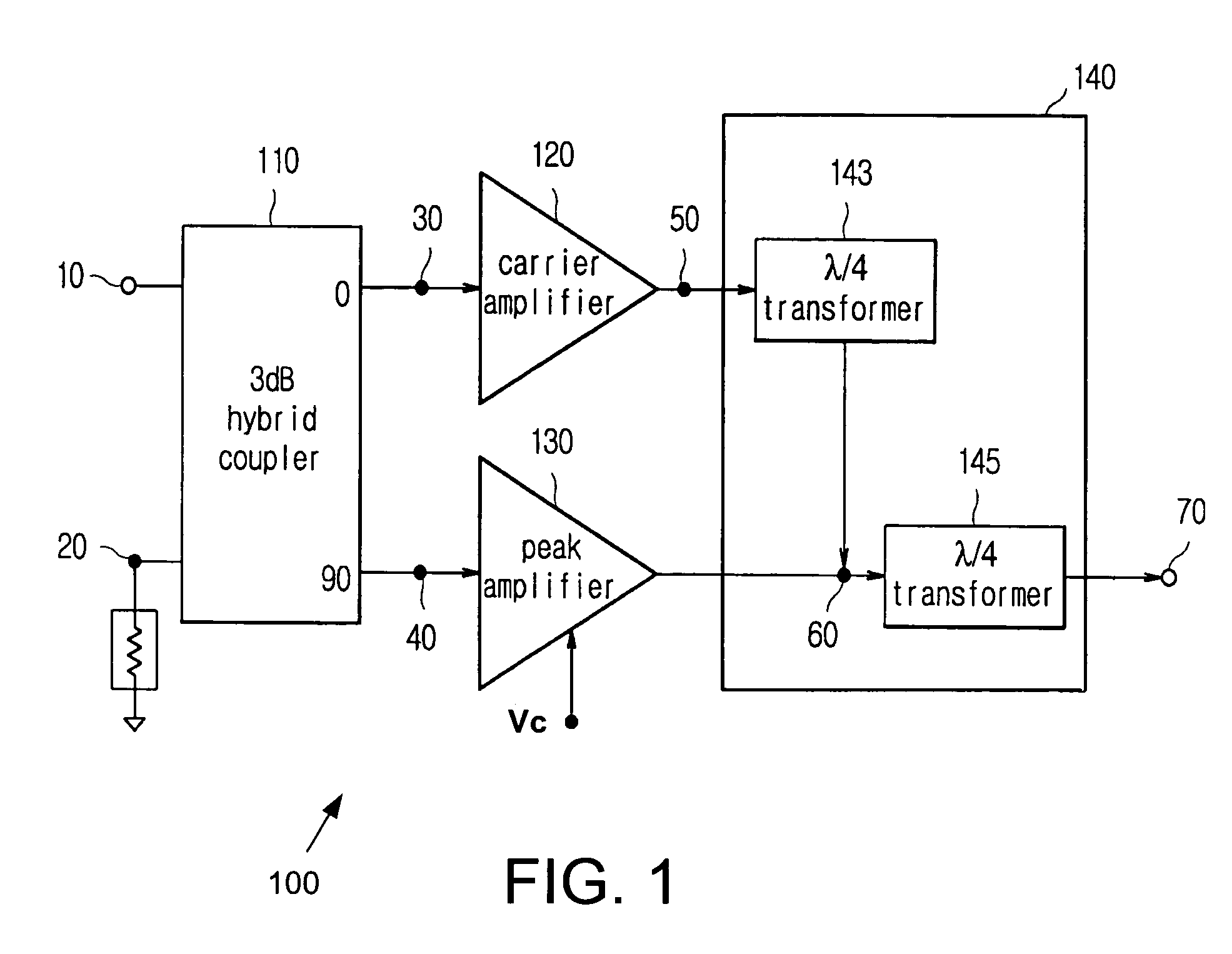
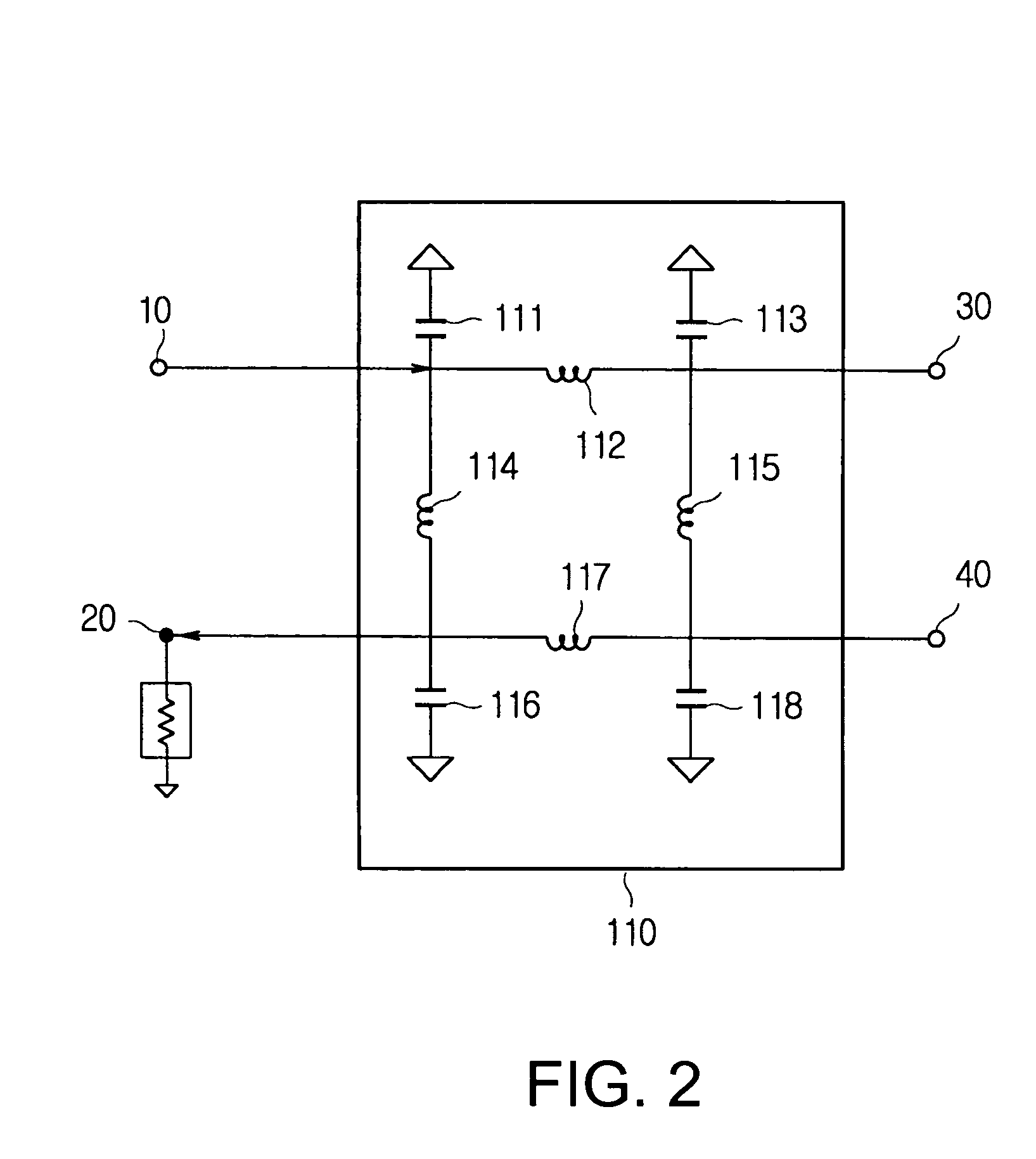
High linearity doherty communication amplifier with bias control
InactiveUS7053706B2Improve efficiencyImprove linearityEnergy efficient ICTAmplifier modifications to reduce non-linear distortionAudio power amplifierClass-D amplifier
The present invention relates to bias control of a power amplification circuit of a mobile device for improving the efficiency and the linearity properties of the power amplifier. In one embodiment, the power amplifier improves these properties by receiving a voltage control signal to bias a supplemental amplifier so that the power amplifier operates in a Doherty mode in a low output power range and in a non-Doherty mode in a high output power range. In the non-Doherty mode, the supplemental amplifier is biased as a class AB amplifier via the received voltage control signal to satisfy the non-linear operational requirements of the power amplifier in the high output power range. The power amplifier generates the voltage control signal based upon power levels of signals received from a remote base station.
Owner:AVAGO TECH KOREA +1
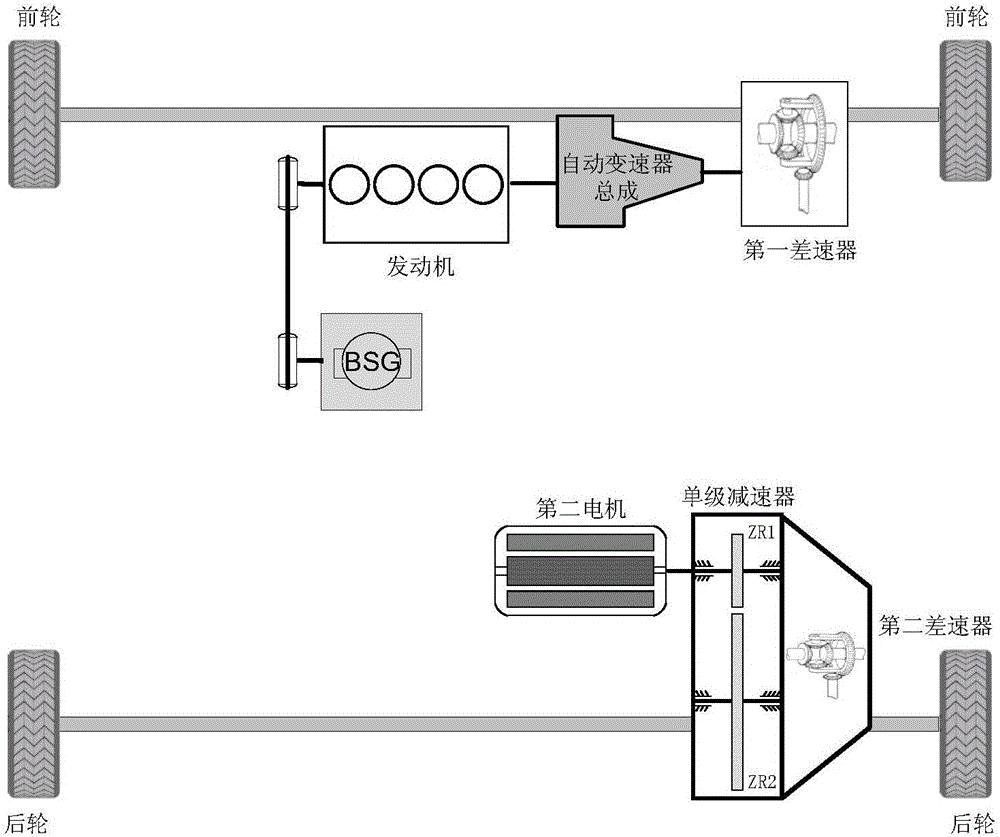
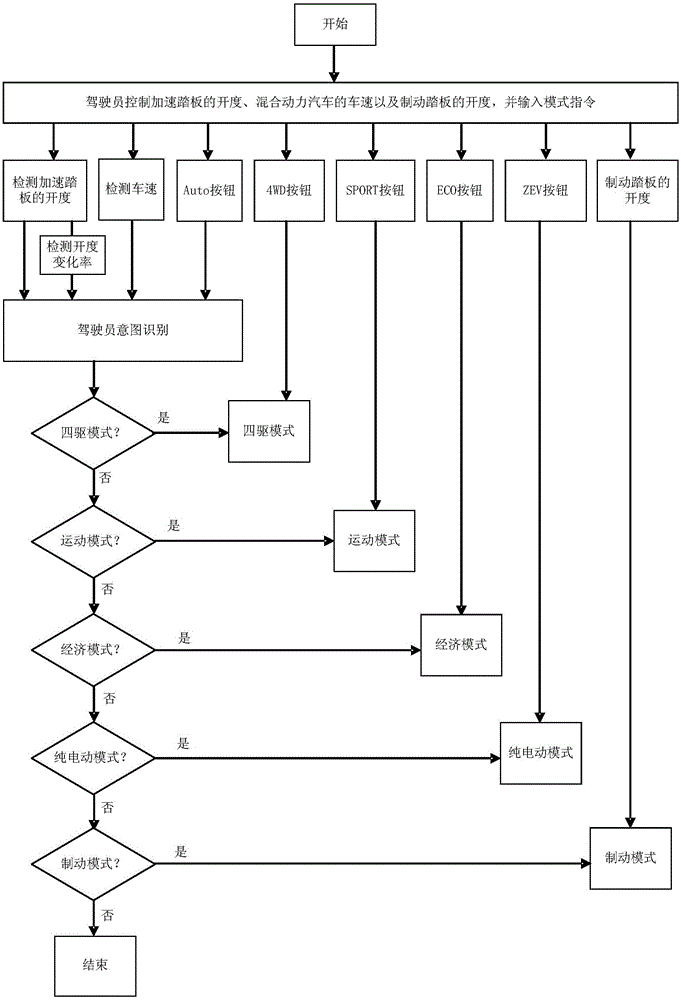
Torque control structure of hybrid vehicle and control system
ActiveCN106696950AImprove securityHybrid vehiclesData processing managementControl systemElectric machine
The present invention discloses a torque control structure of a hybrid vehicle and a control system of the hybrid vehicle provided with the torque control structure. The torque control structure of the hybrid vehicle executes the following steps of detecting the opening degree of an accelerator pedal of the hybrid vehicle and the speed of the hybrid vehicle; controlling the hybrid vehicle to enter the corresponding operation mode according to the opening degree of the accelerator pedal, the speed of the hybrid vehicle and the mode command inputted by a driver; and determining torques of an engine, a first motor and a second motor according to the current operation mode of the hybrid vehicle, and correcting the determined torques according to the active slip prevention strategy and the handling stability strategy, to output target torques. By applying the control structure, the output torques of the engine and the motors meet the operational requirements of the hybrid vehicle under the condition of meeting demand modes of drivers.
Owner:BEIJING BORGWARD AUTOMOBILE CO LTD
Method and system for state-based power management of asset tracking systems for non-statutory assets
ActiveUS9569944B2Reduce power consumptionReduce usageRecord carriers used with machinesBurglar alarm electric actuationEngineeringOperational requirements
A method and system for power consumption management for moveable assets is provided. Various states and modes are defined, in which elements of the system may operate, each state and mode having different power requirements based on different operational requirements and communication paradigms. Various triggers may indicate which state and mode to be in, with the lowest power consumption operating status being selected whenever possible based on the triggers.
Owner:TRAPEZE SOFTWARE
Suction mounted bar code symbol reading system, apparatus and stand
InactiveUS20070017997A1Avoids shortcoming and drawbackSensing by electromagnetic radiationBarcodeEngineering
An improved bar code scanner is equipped with a releasable-attachable base for mounting said bar code scanner to a countertop without modifying said countertop. The releasable-attachable base is provided in the form of a suction-cup apparatus. If the suction-cup apparatus is mounted to the countertop, the bar code scanner becomes fixed to the countertop, alleviating the need for a permanent base, which would require modification to the countertop and irreversible damage to the countertop if the permanent base was ever removed due to an equipment upgrade or a change in operational requirements.
Owner:TALLEY HARRY +1
Loading mechanism with metamorphic function and implementation mechanism thereof
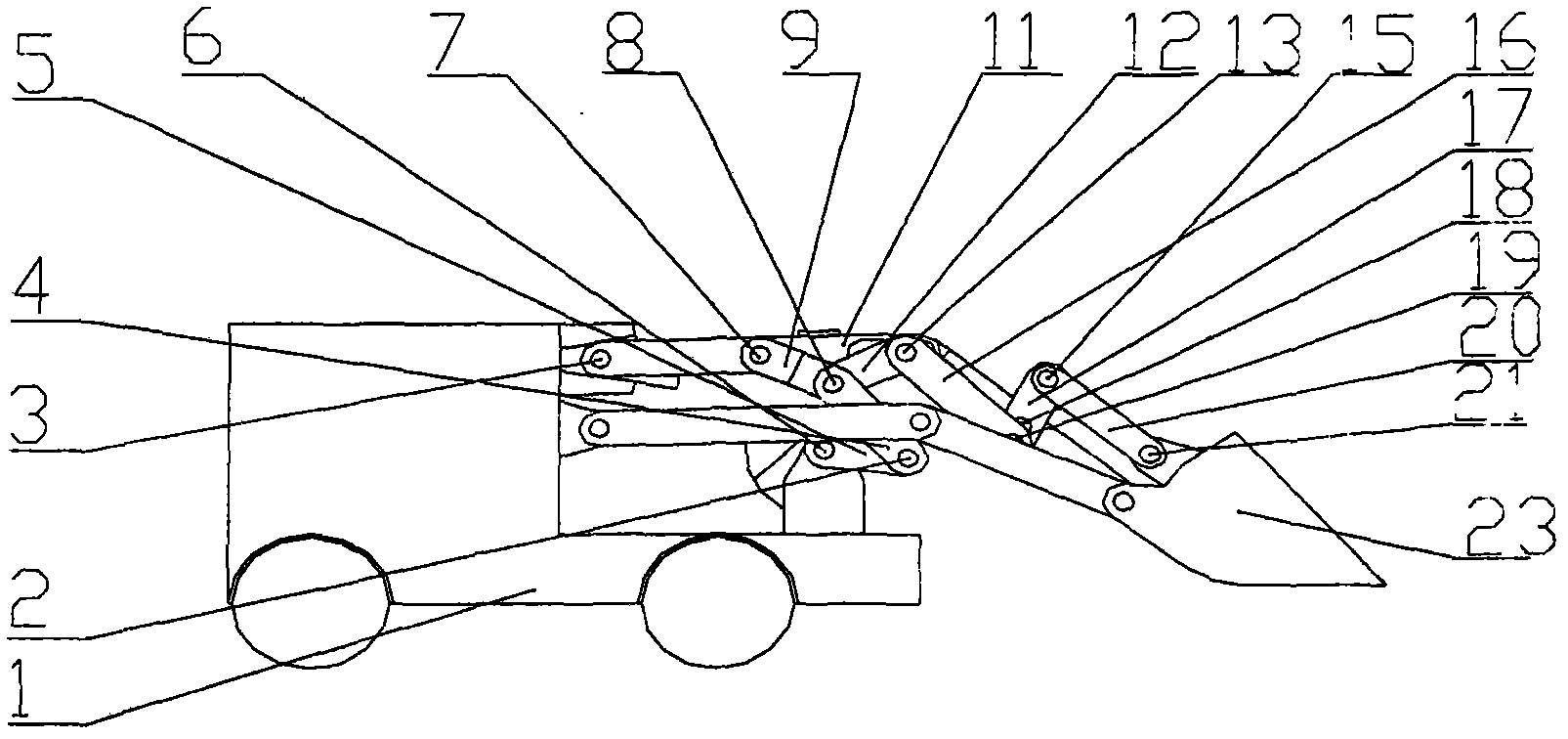
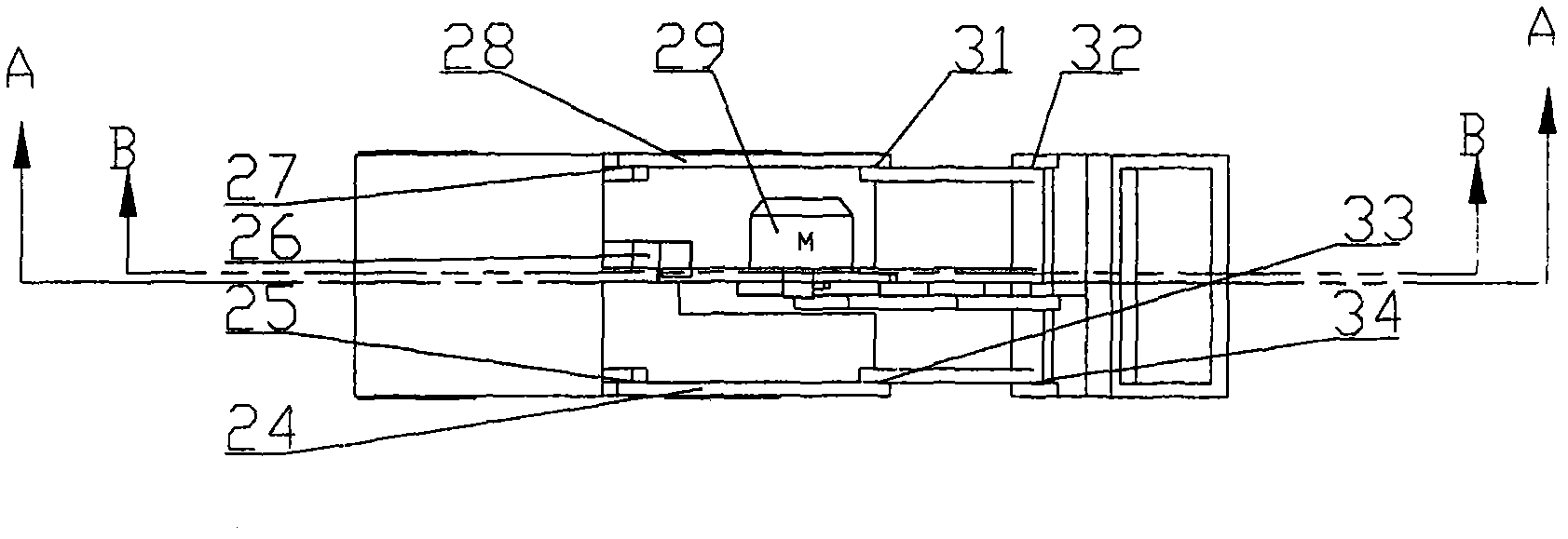
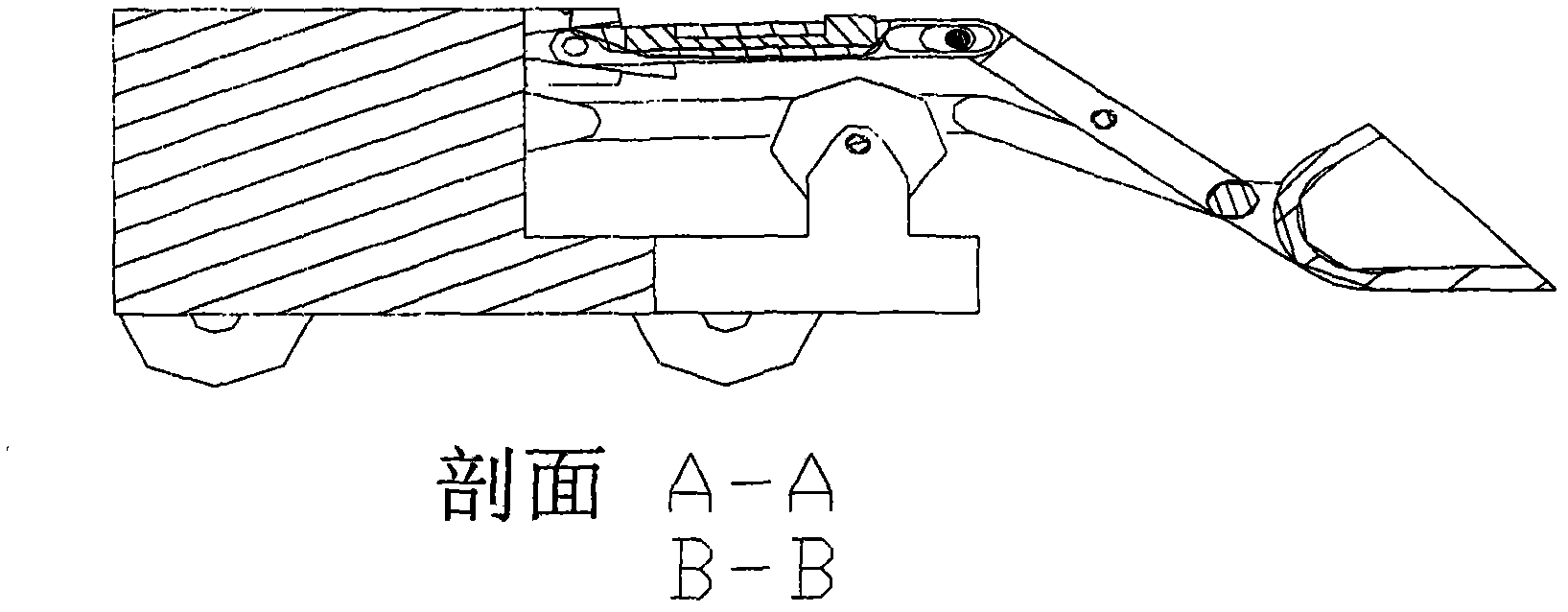
InactiveCN102108717AAdapt to different stages of work requirementsAvoid disadvantagesMechanical machines/dredgersEngineeringWork demand
The invention relates to a loading mechanism with metamorphic function, comprising a bucket overturning mechanism and a bucket lifting mechanism. The topological structure of the loading mechanism is changed as required when a loading task is executed. When the loading structure executes tasks of a bucket loading stage, a bucket overturning stage, a unloading stage and a bucket revolving stage, the topological structure of the loading mechanism is the bucket overturning mechanism; and when the loading mechanism executes the tasks in a bucket lifting stage and a bucket descending stage, the topological structure of the loading mechanism is the bucket lifting mechanism. The loading mechanism can change the topological structure according to the operational requirements in different stages. The loading mechanism can complete the tasks of each stage such as overturning, lifting, loading and unloading by one motor. By applying the loading mechanism disclosed by the invention, the defects that oil of the traditional hydraulic loading mechanism leeks and the reliability is difficult to guarantee; and meanwhile, the manufacturing cost is low, and the loading mechanism is convenient to maintain.
Owner:GUANGXI UNIV
Single actuator controlled rotational flow balance system
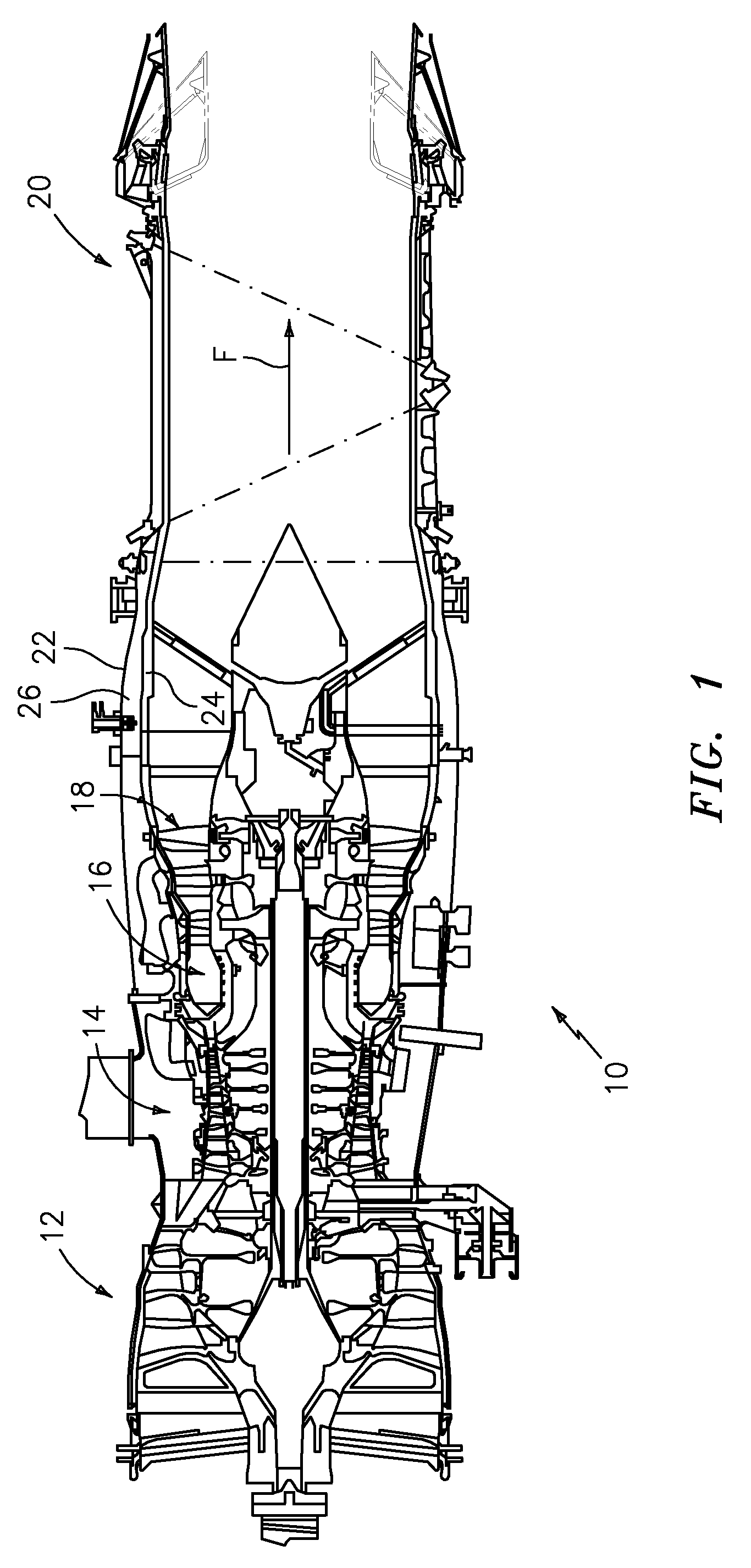
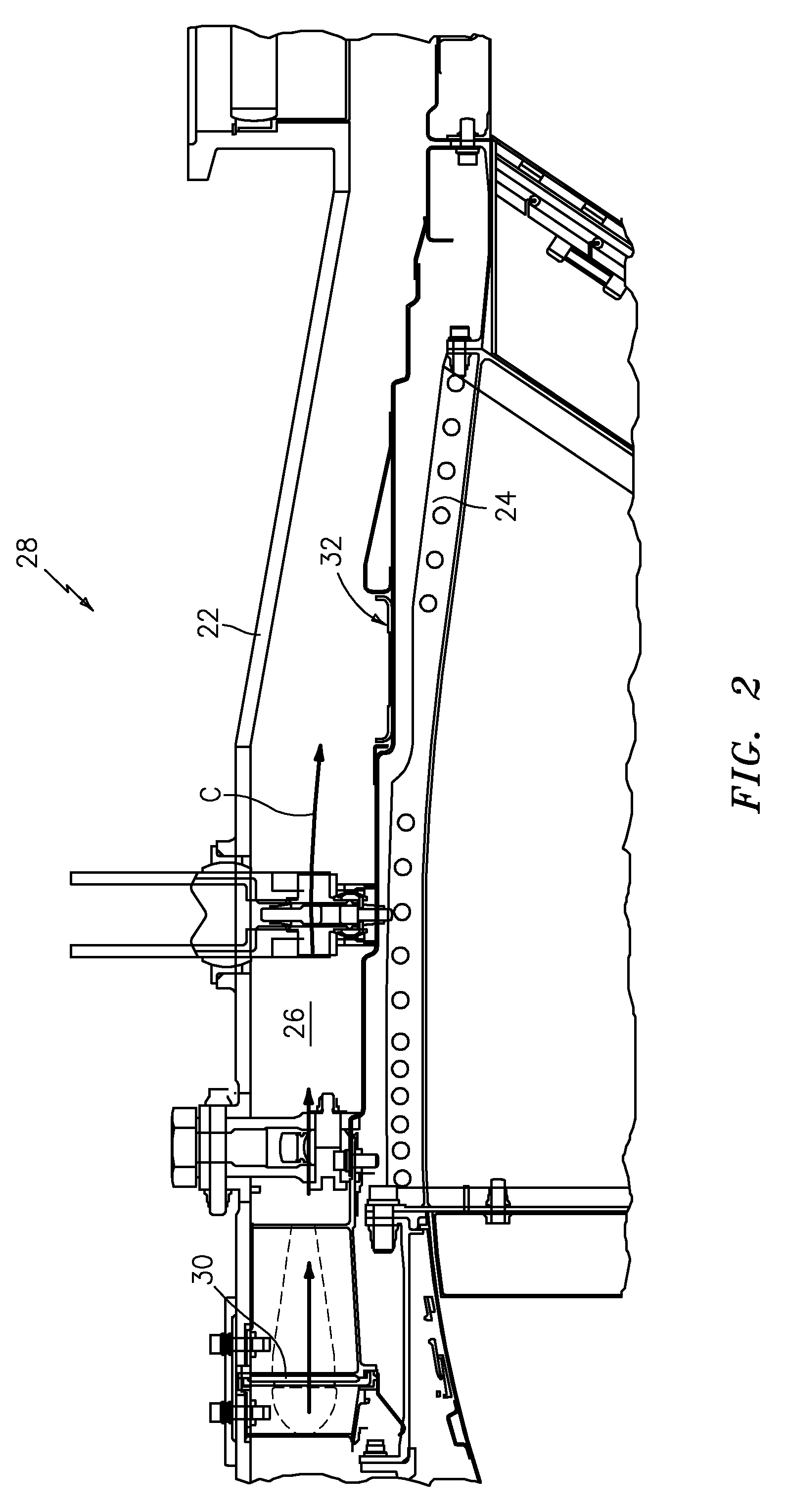
A rotational flow balance system includes an actuator system which controls operation of both a fan duct blocker ring and a modulated exhaust cooling ring through a kinematic system. The kinematic system is controlled by the single actuator system such that the modulated exhaust cooling ring will remain in a fixed position while the fan duct blocker ring can be moved to satisfy operational requirements.
Owner:RTX CORP
Multi-Channel Multiple Access Method Based on Channel Reservation Mechanism in Wireless Ad Hoc Networks
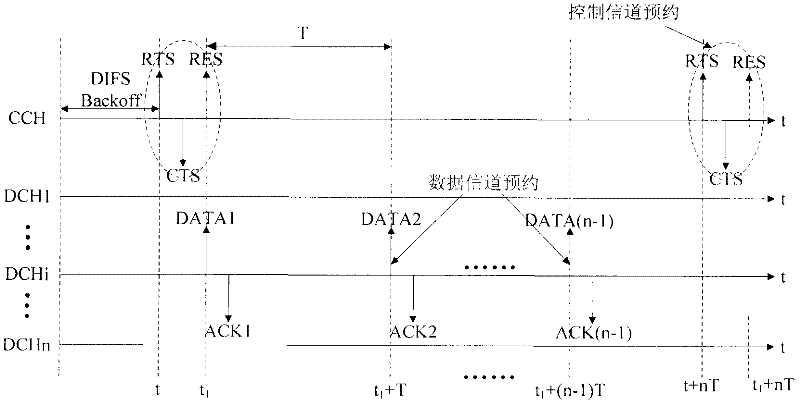
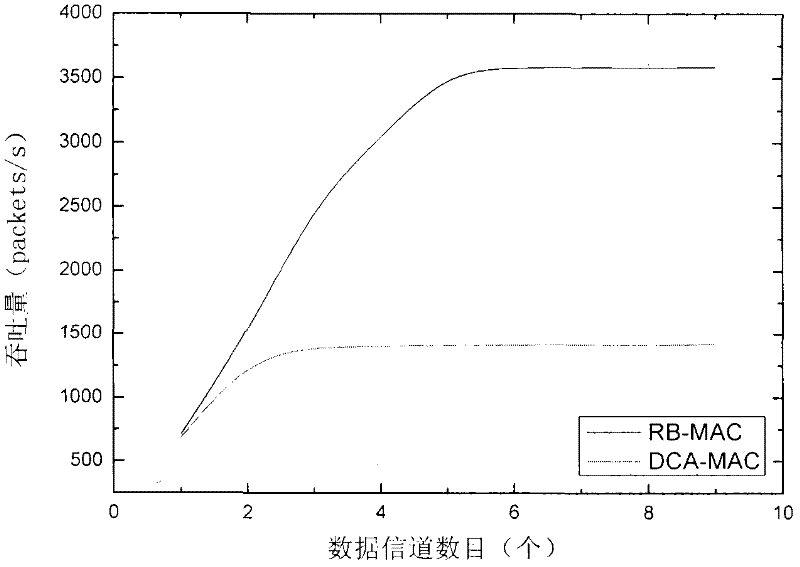
InactiveCN102300257ANo action requiredImprove throughputNetwork traffic/resource managementTransmission protocolWireless ad hoc network
The invention discloses a multi-channel multiple access method based on a channel reservation mechanism in a wireless ad-hoc network. The invention works in a fully distributed network without requiring synchronization of the entire network. In the network using this protocol, the nodes complete the exchange of handshake information on a common channel, and use the reservation mechanism to reserve the sending of a certain number of data packets at the same time as the handshake information is exchanged. The reservation mechanism enables multiple data packets to be sent with only one handshake information exchange, which reduces the load of the public channel and greatly improves the throughput of the network. At the same time, because the time of sending the reserved data packets can be determined, the protocol is particularly suitable for transmission Services that require very high real-time performance, such as video.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Mobile communication terminal and its touch-screen input control method and system
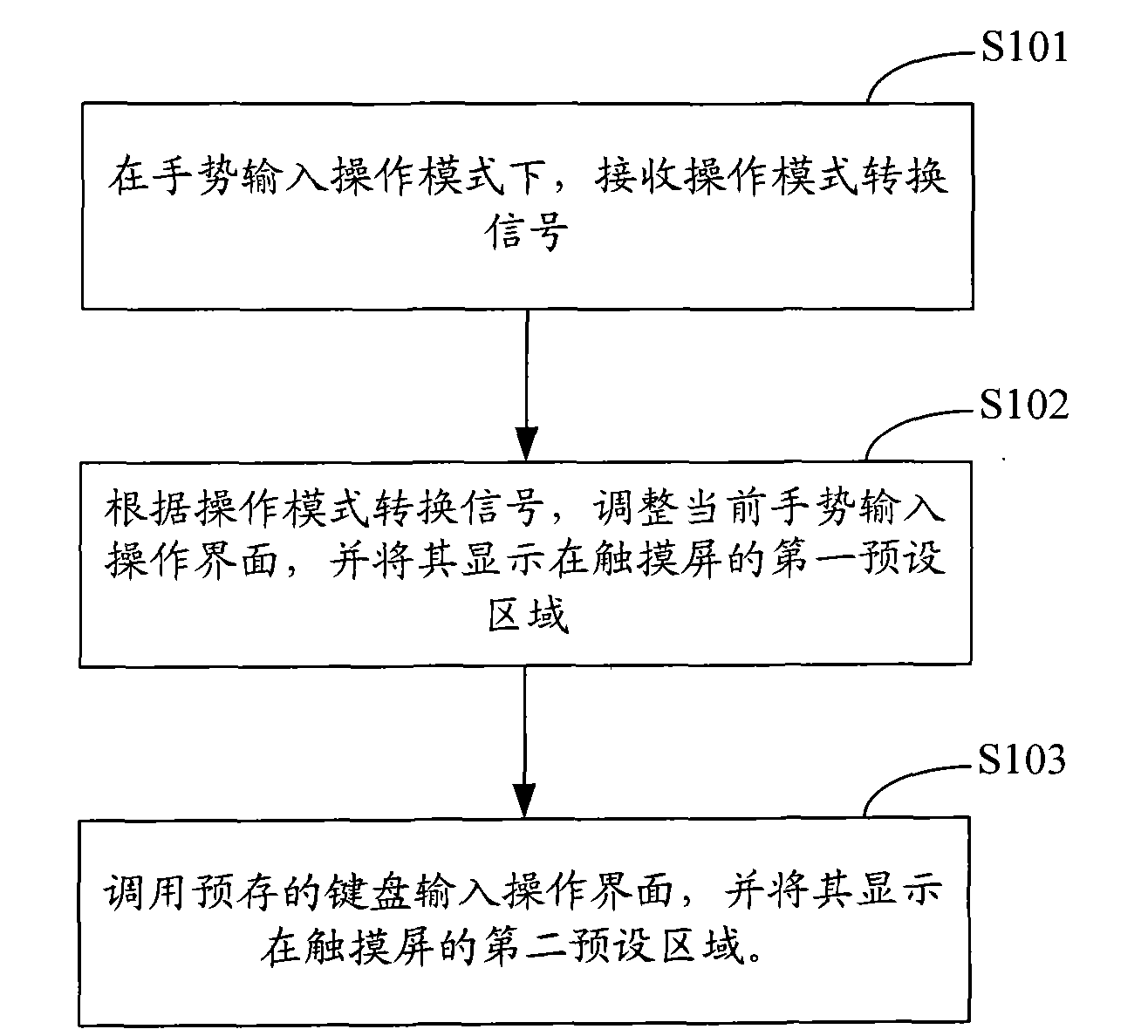
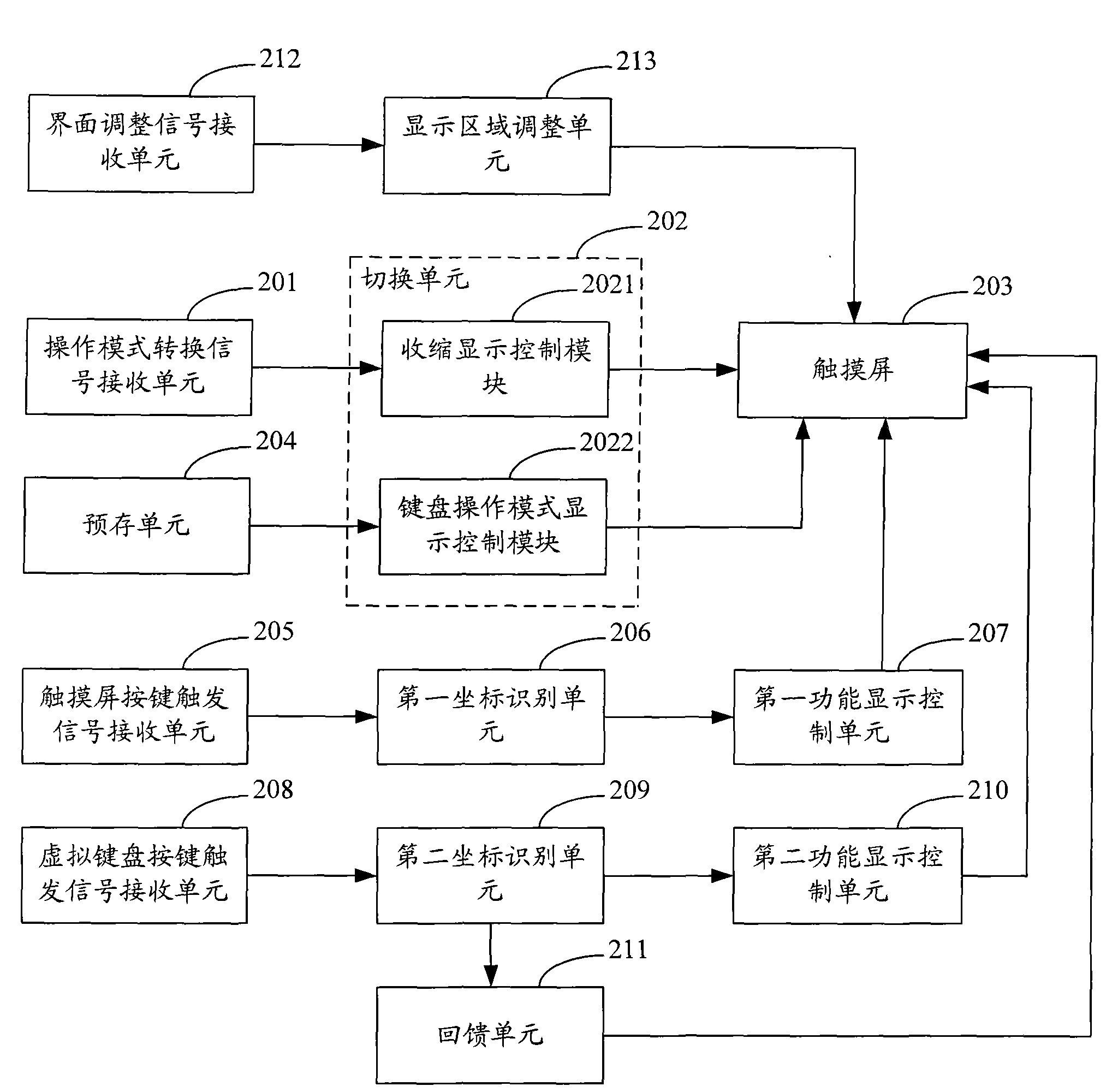
ActiveCN101551727ASmooth operation experienceMeet operational needsSubstation equipmentInput/output processes for data processingInput controlOperation mode
The invention applies to the field of mobile communications technology, provides a touch-screen input control method and system of a mobile communication terminal, wherein, the method includes the following steps: receiving operating mode switching signals in the gesture input operation mode; adjusting the current gesture input interface according to the operating mode switching signals, and displaying them in a first preset area of the touch-screen; calling the prestored keyboard input interface, and displaying it on the second preset area of the touch-screen. The invention simultanously takes care of the keyboard input mode and the touch screen input mode, thereby improving the operational flexibility, enabling operation experience of users to be more smooth, satisfying the operational requirements of users which are accustomed to the keyboard input, and being especially suitable for mobile communication terminals with large-screen touch-screen.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Fluid conduit
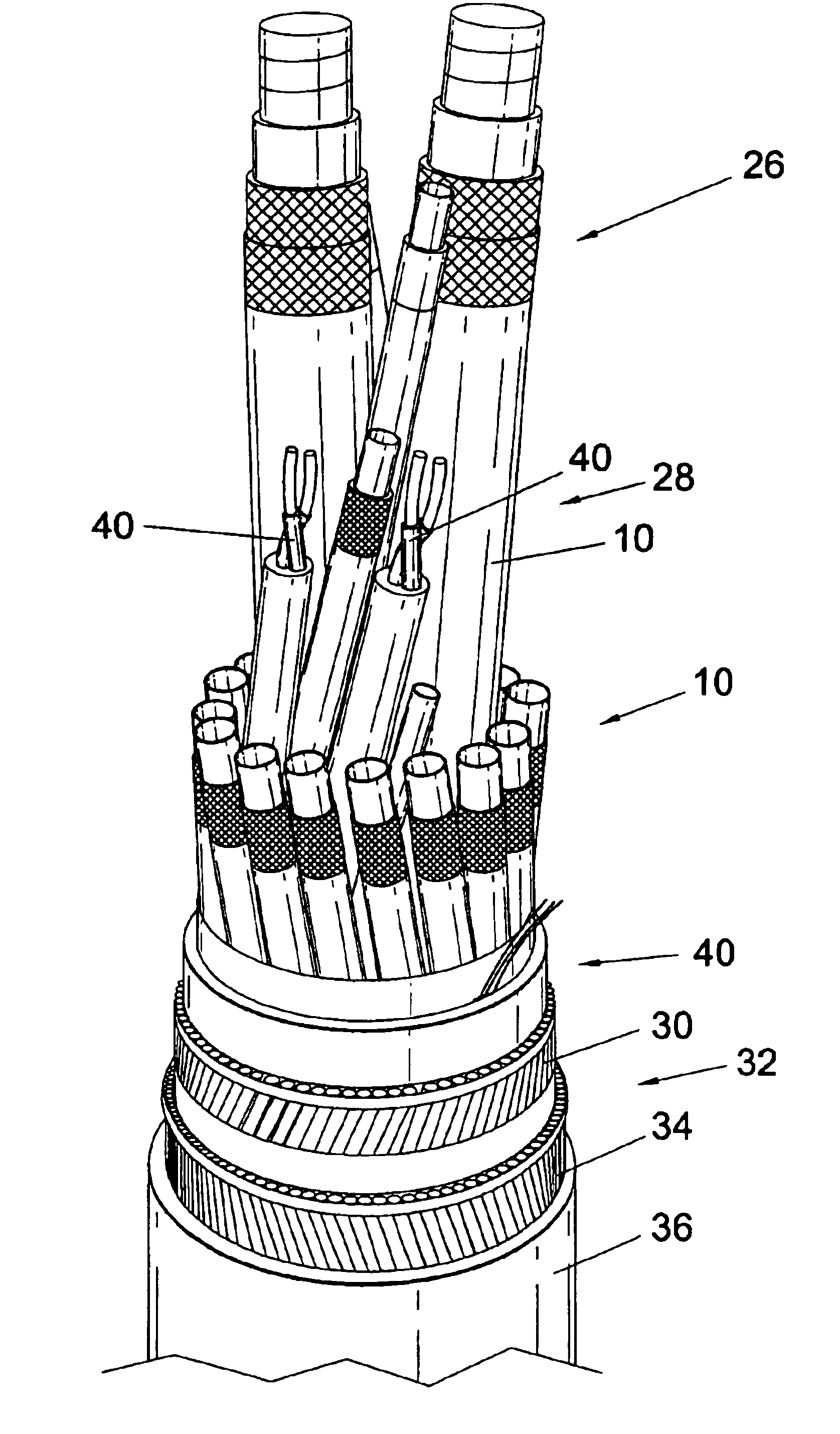
The present invention relates to a fluid conduit, and to a multi-conduit umbilical for use in the transportation of chemicals with small molecular size and shape e.g. methanol ethanol and other hydrocarbon fluids used in the oil industry. The conduit comprises a flexible fluid hose encapsulated by at least one metallized layer which is formed and arranged to minimize permeation of a fluid being transported in the fluid hose. In use in a multi-conduit umbilical the metallised layer minimizes permeation into adjacent fluid hoses containing chemicals. The invention is characterized in that the fluid hose(s) have differing levels of encapsulation and thereby permeation, along a given length according to the operational requirements of the fluid conduit / umbilical. Typically such fluid conduits / umbilicals will have lengths in excess of 100 km.
Owner:OCEANEERING INT SERVICES
Oil well blowout containment device
InactiveUS8555980B1Easy to anchorGuaranteed uptimeDrilling rodsAdjustable jointsWell drillingMarine engineering
A blowout containment system is permanently positioned on the wellhead. The blowout containment system is relatively inexpensive, is always available and in place, it does not interfere with normal drilling operations, will capture all of the oil and gas emitted by the blowout, does not require special or unique sea surface or underwater apparatus or vessels, does not have any operational requirements that are different than those which drilling crews normally use and are already familiar, and is activated the using actions are similar to those used by drilling crews for well drilling and completion.
Owner:POWELL JOHN
Operationally adaptable chemical-biological mask
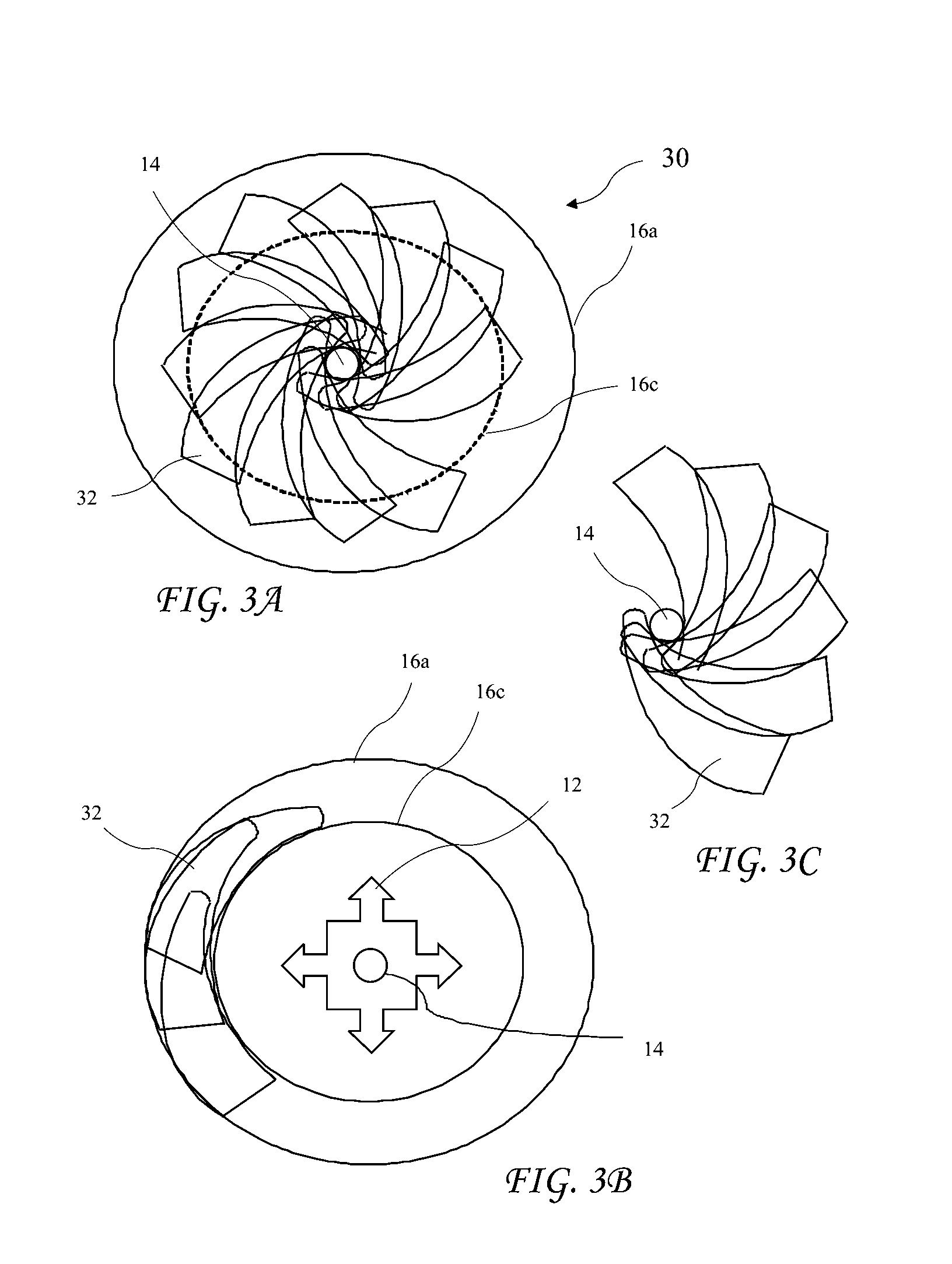
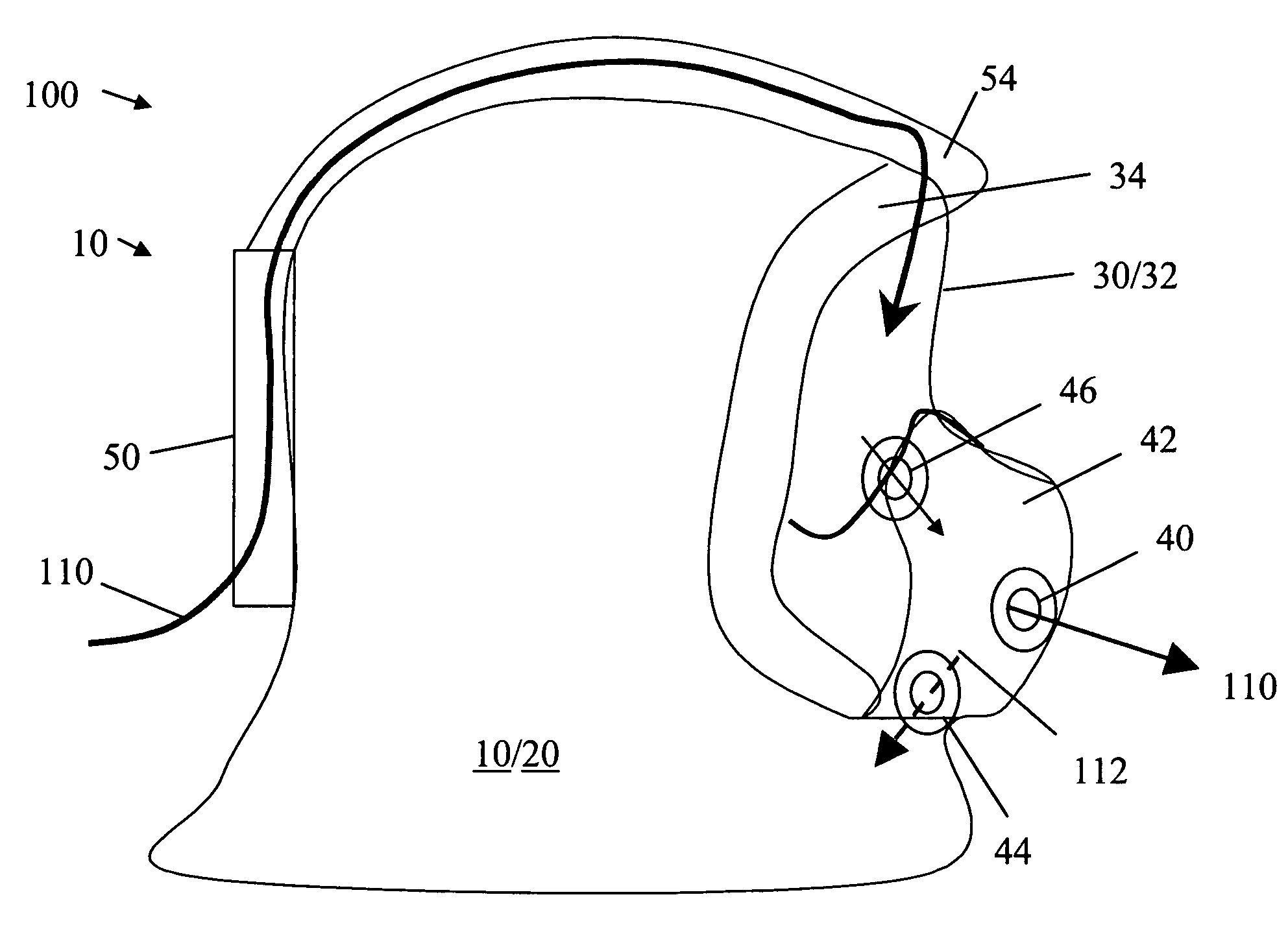
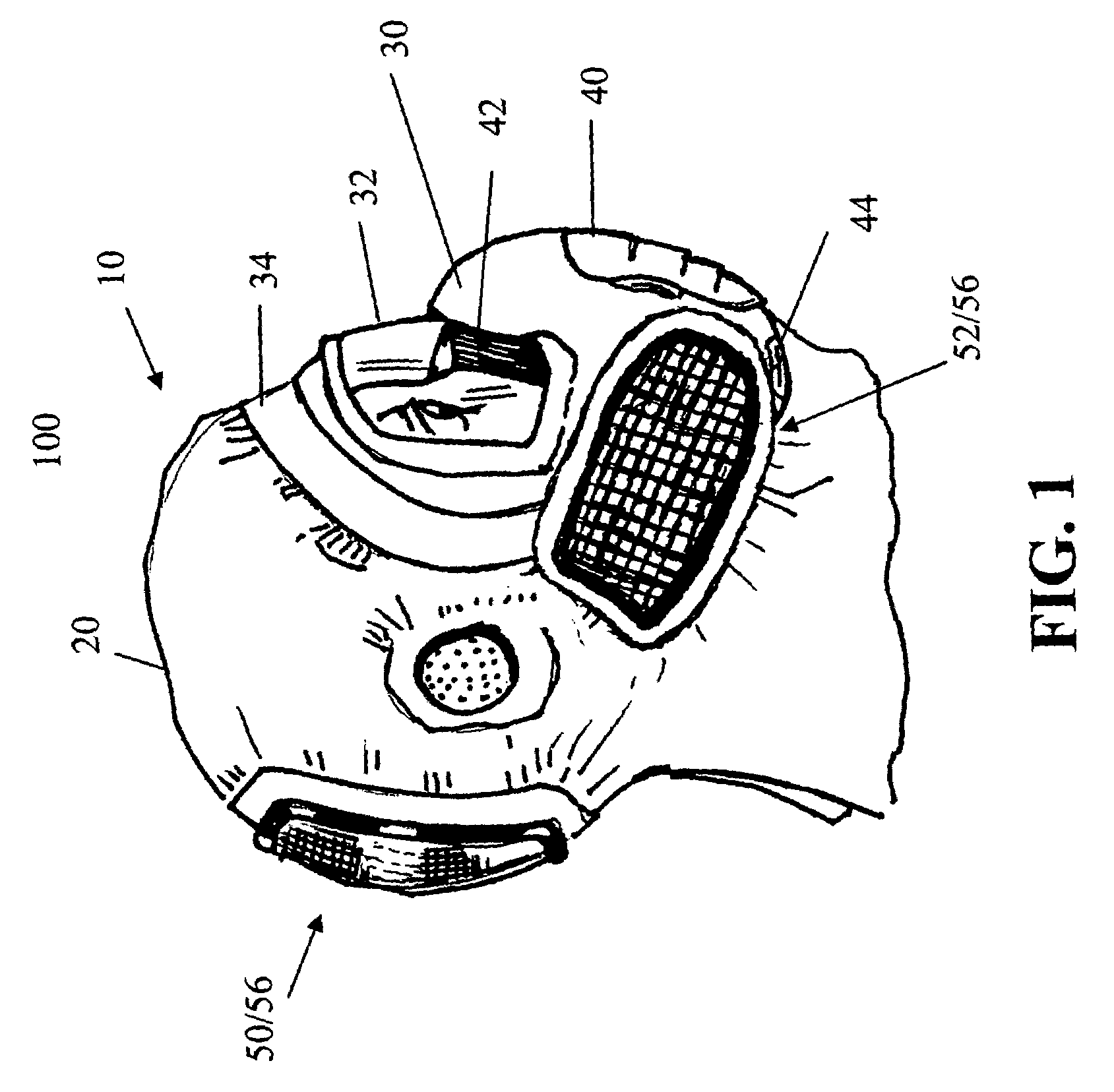
InactiveUS7028688B1Increases comfort and balance and visual field-of-viewChemical protectionHeat protectionFiltrationFilter system
A chemical-biological protective mask having a weight distribution that imparts a balanced center-of-gravity to the wearer of the mask, and is adaptable for different operational requirements by adjusting or altering the air flow through the mask. The protective mask includes a head covering to fully cover the wearer's head including a hood, a face piece having a visor contoured to the wearer's face, ducting within the mask connected to a filtering system mounted at the rear of the head covering and a purge airflow through the hood. Additional side or front mounted filters can be added to provide either parallel or series filtration with the rear mounted filters. A blower system may also be used to impart an airflow into the mask and improve breathing resistance.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
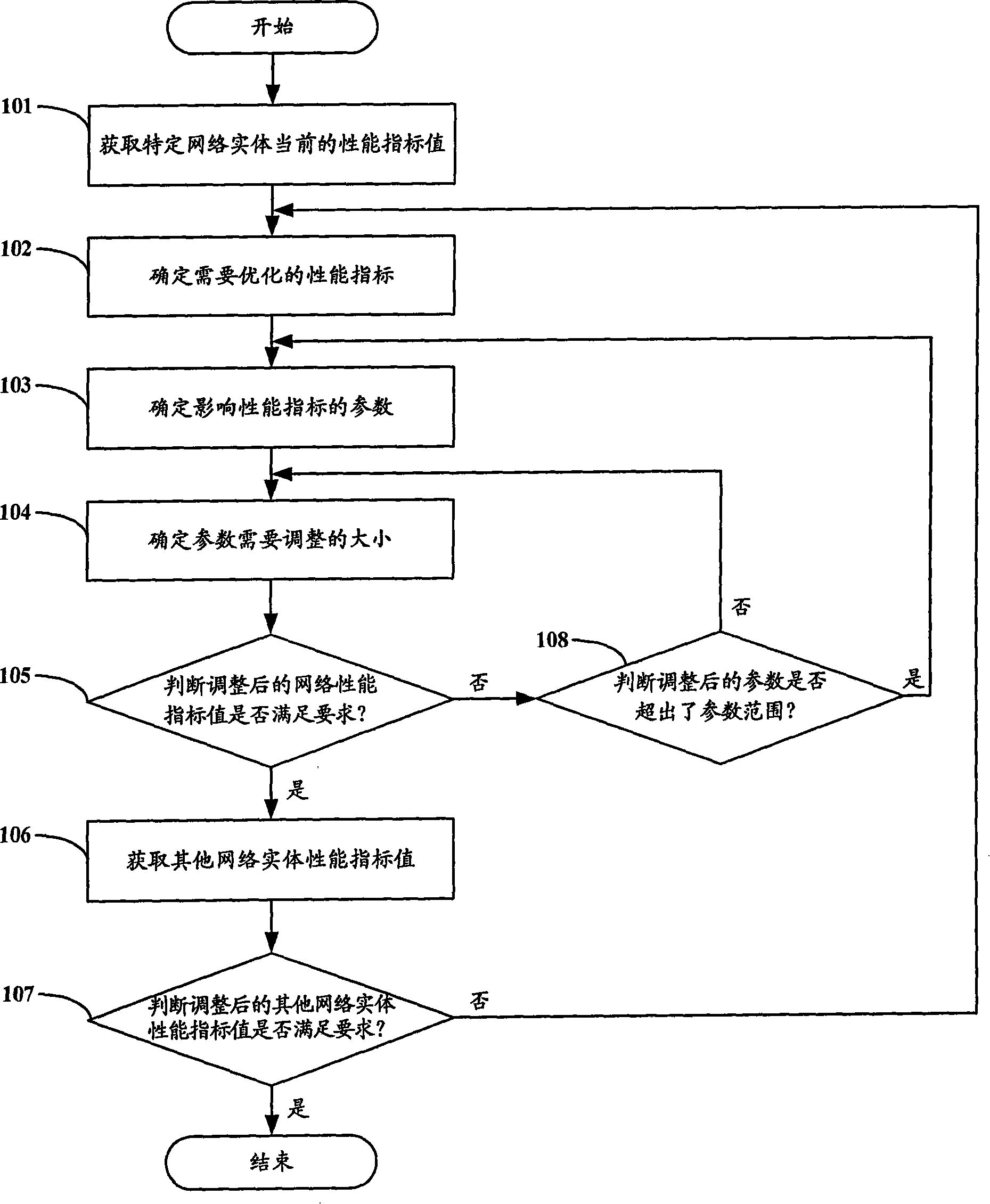
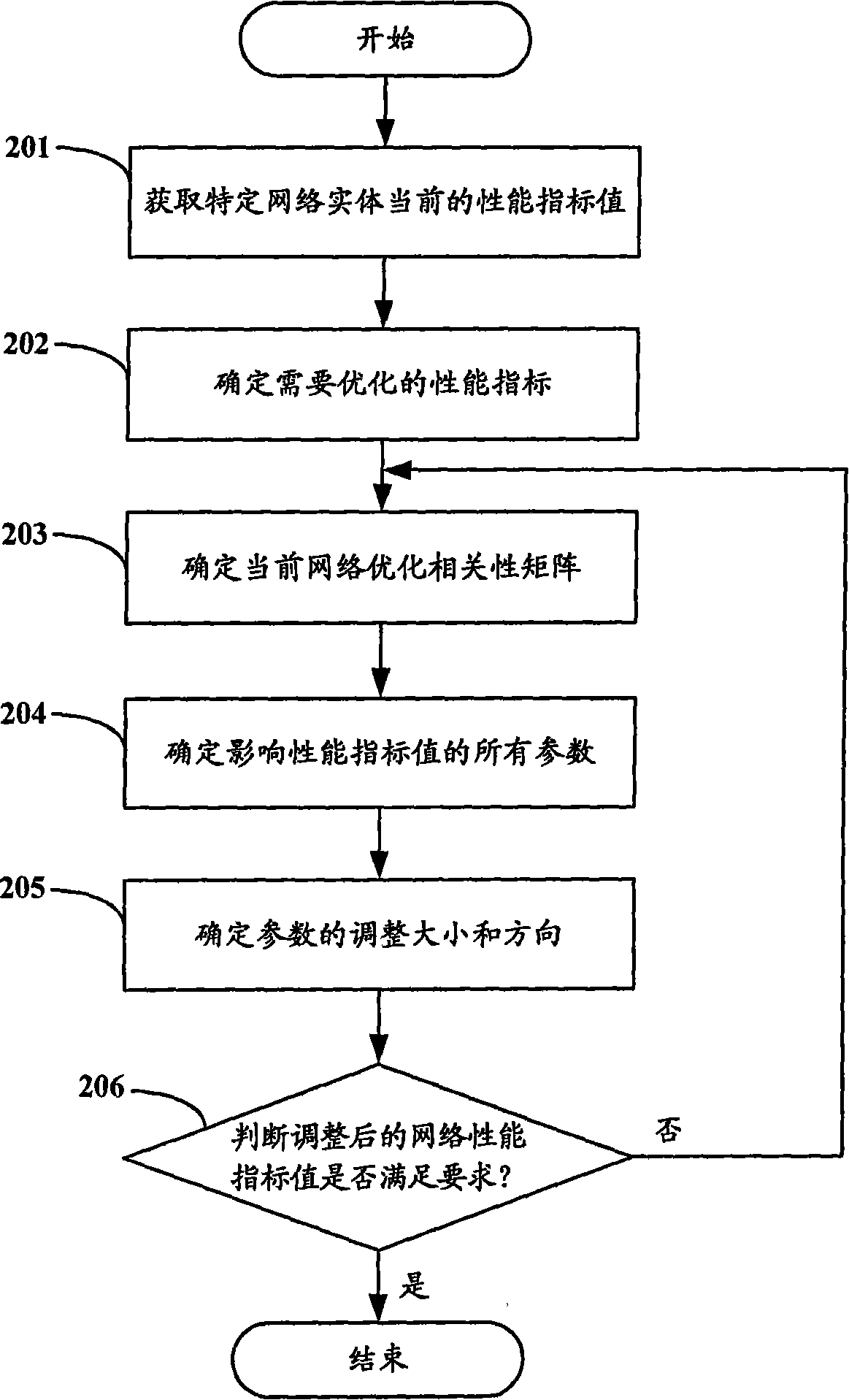
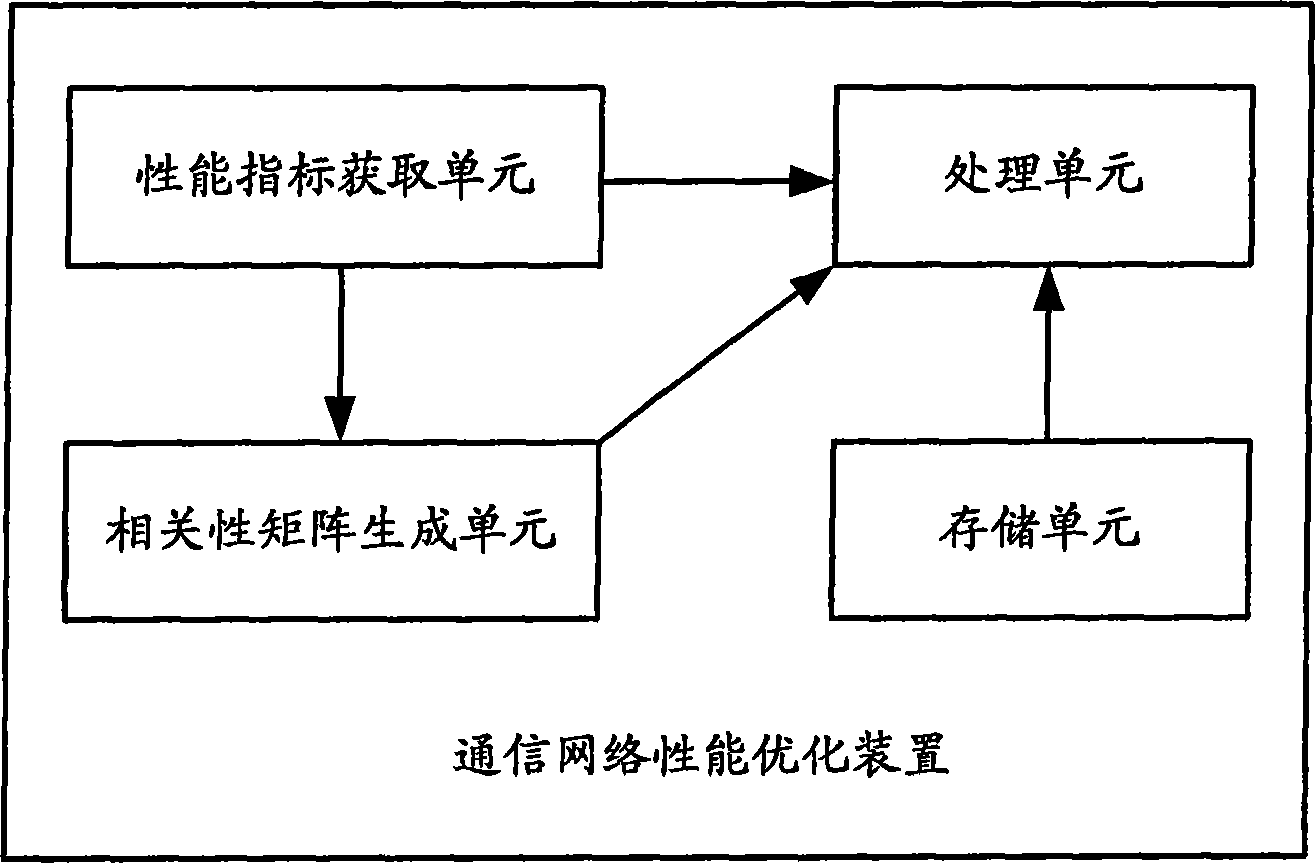
Communication network performance optimization method and device
ActiveCN101159586AEasy to judgeSure easyData switching by path configurationCommunications systemPerformance index
The invention discloses a method for optimizing communication network performance, which comprises: (a) setting and storing a history network optimization correlation matrix according to the design and operational requirement of the communication network; (b) determining a current network optimization correlation matrix by using the current parameter values and performance index values of the network entity in the communication network; (c) determining the parameters required for the adjustment to reach the target value of network entity performance index, according to the corresponding relationship in parameter and performance index between the current network optimization correlation matrix and the history network optimization correlation matrix; and (d) comparing the correlation values between the current network optimization correlation matrix and the history network optimization correlation matrix, and adjusting the parameters to be adjusted based on the predetermined parameter adjustment strategy. The invention also discloses a device for optimizing the communication network performance. With the invention, the service provider can easily judge and determine the parameter target required for the optimization to improve the network performance index, and the network optimization is automatically implemented.
Owner:CHINA MOBILE GROUP DESIGN INST
Method for controlling the operation of high-voltage bypass in thermal generator set
ActiveCN101825005ARunning wellGuaranteed uptimeBoiler controlSteam engine plantsStart timeThree stage
The invention relates to a method for controlling the operation of a high-voltage bypass in a thermal generator set, which is characterized in that operational modes of the high-voltage bypass are divided into the following four modes according to the operational states of the thermal generator set: a set starting mode, a set normal operation tracking mode, a mode of shutdown without blowing-out and a blowing-out mode, wherein the set starting mode is divided into three stages according to different operational requirements of a boiler: a first set starting mode, a second set starting mode and a third set starting mode. By using the method, the opening / closing of a high-voltage bypass valve and the opening of a valve position can be controlled according to different operational stages of the set, so that main recovery pressure of the boiler is ensured to ascend smoothly, operate stably and descend smoothly; and simultaneously, the boiler can also be controlled to improve the recovery temperature quickly, so that the recovery temperature is matched with the metal temperature of a gas turbine cylinder quickly and adapt to a combined mode of fixed pressure operation and sliding pressure operation of the set, so that the starting time of the set is shortened, steam exhausting towards air is reduced, the life loss of the steam turbine is reduced, and the optimal starting of the set is realized.
Owner:CHINA SHENHUA ENERGY CO LTD +2
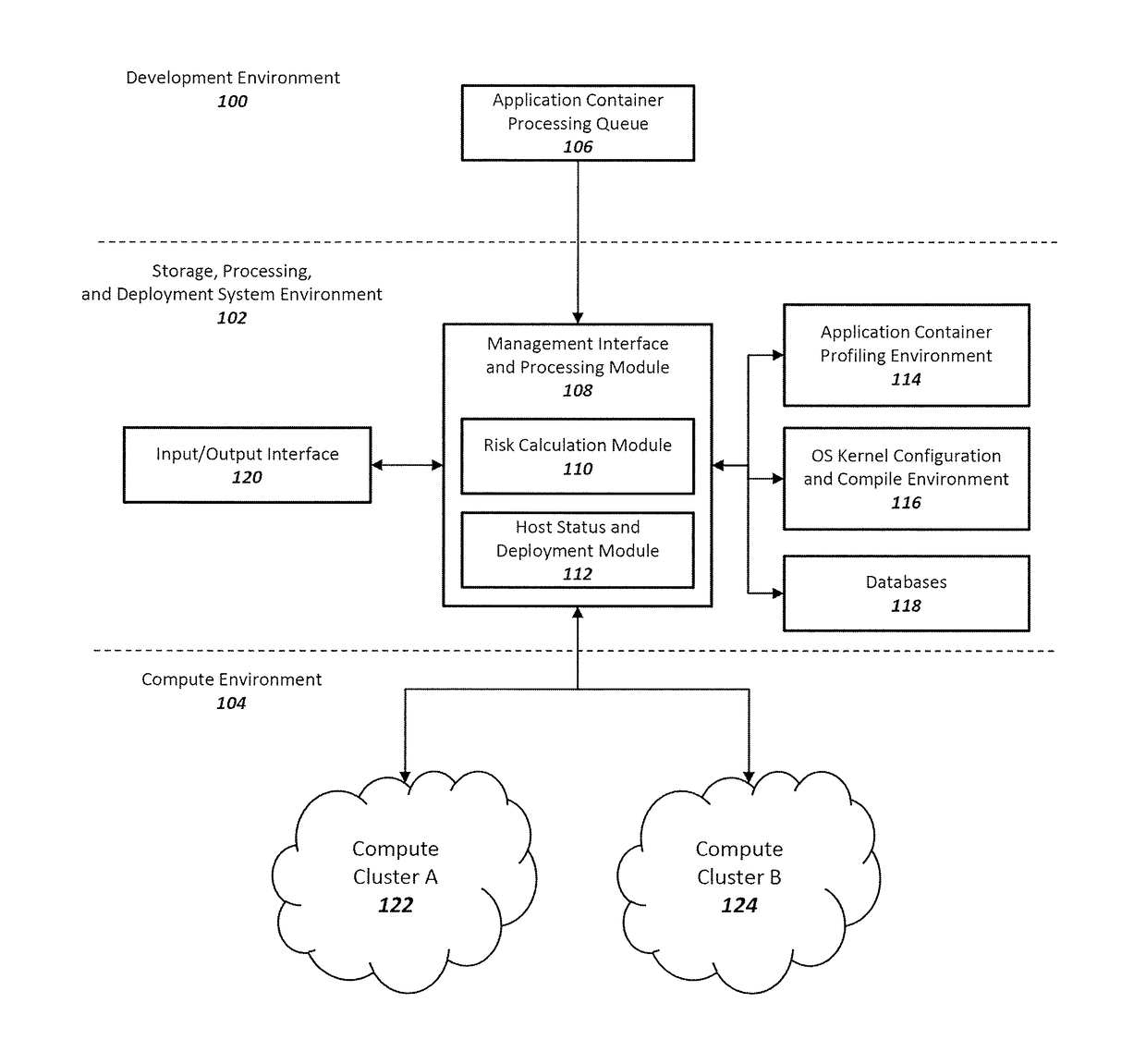
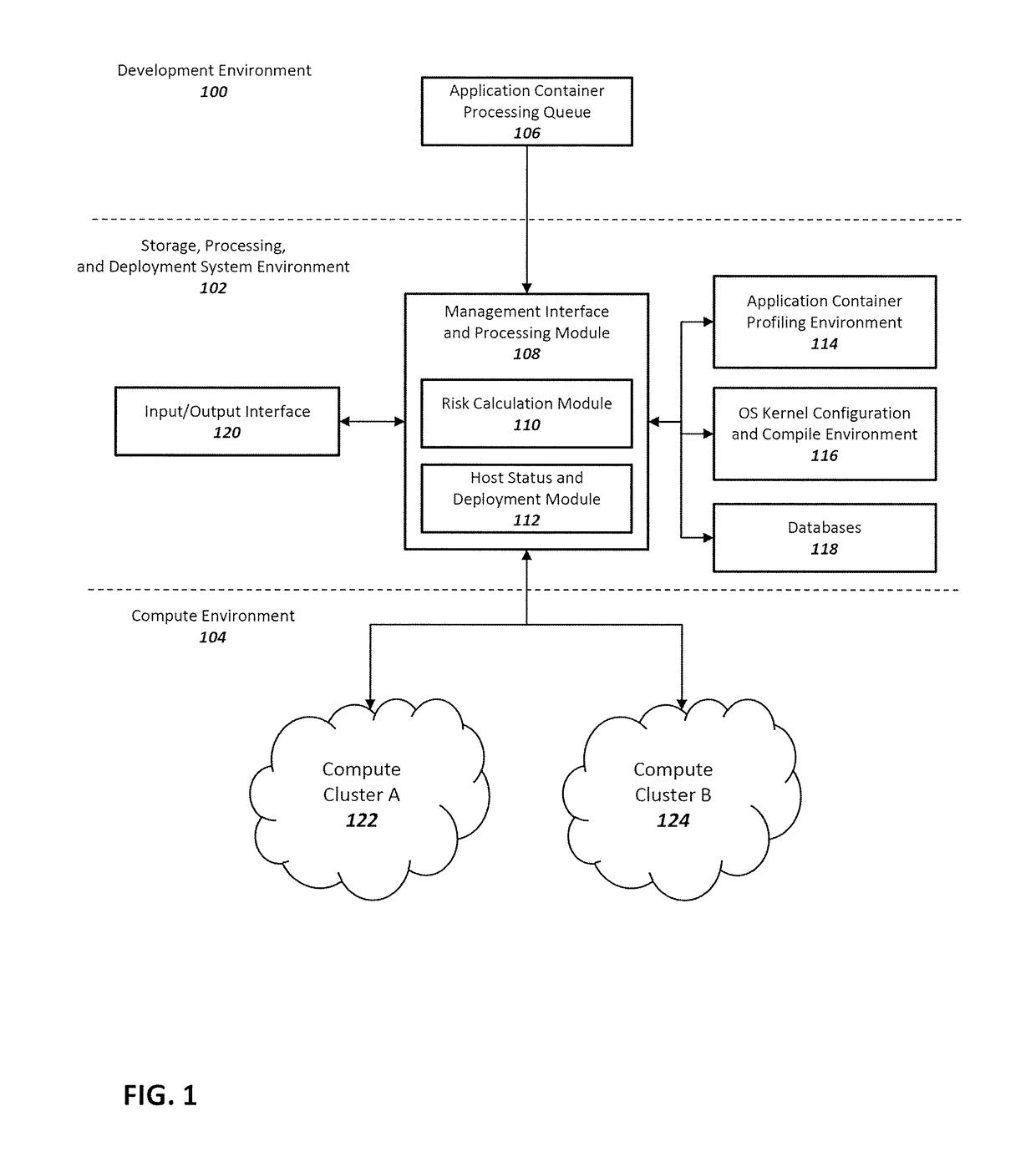
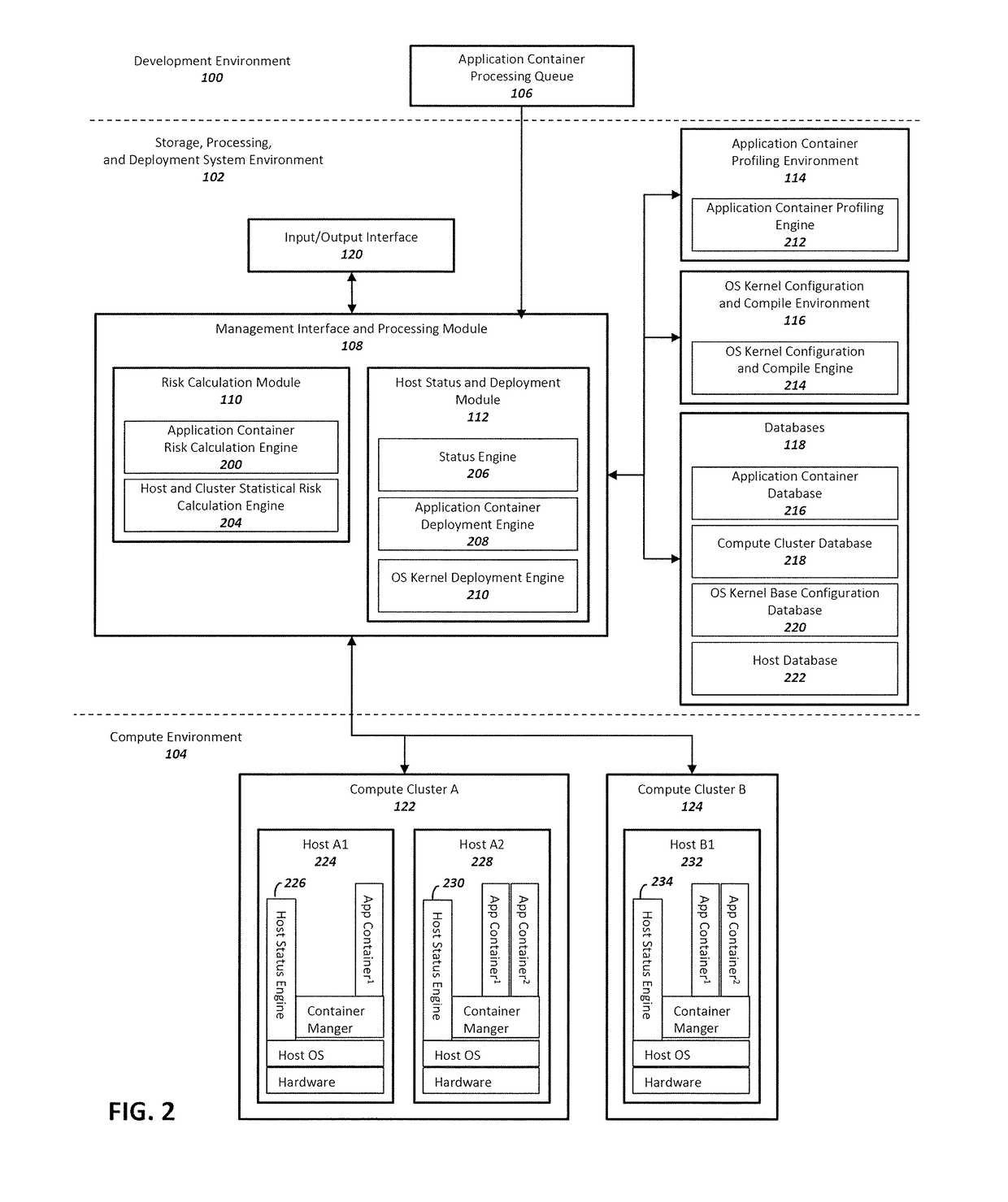
Method and system for enhancing application container and host operating system security in a multi-tenant computing environment
ActiveUS20180046457A1Reliability/availability analysisSoftware testing/debuggingOperating system securityComputerized system
A system for application container security comprising an application container processing and deployment computer system configured to receive an application container, determine operating system kernel requirements of the application container, calculate a risk value based on the operating system kernel requirements of the application container, determine availability of a host computer to host the application container, by determining if the operating system kernel of the host computer meets operational requirements of the application container. The operational requirements including the risk value for the application container. When the operating system kernel of the host computer is determined to meet the operational requirements, pair the application container with the operating system kernel of the host computer. When the operating system kernel of the host computer is determined to not meet the operational requirements, configure and compile a container-specific operating system kernel that meets the operational requirements.
Owner:MAXISIQ INC
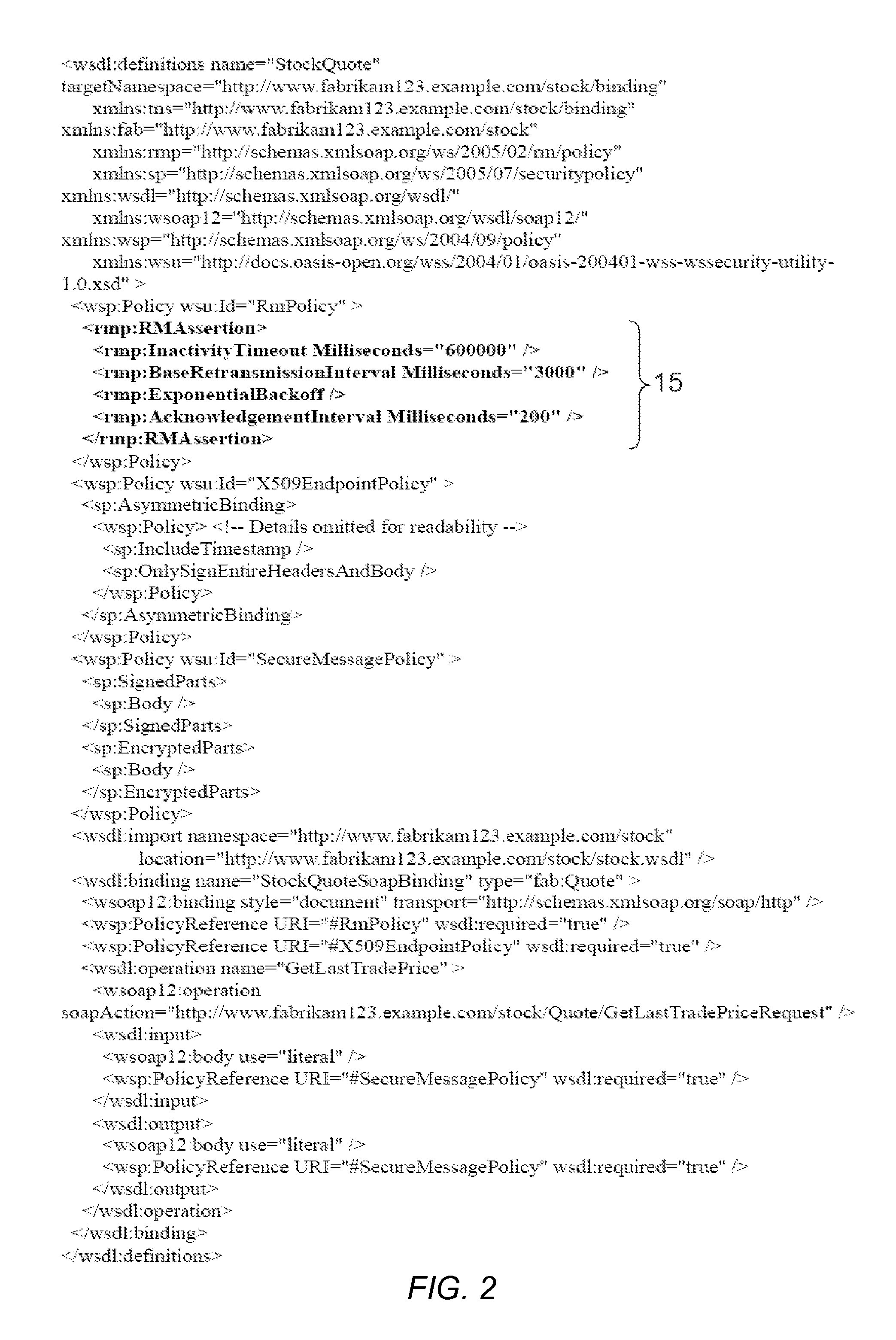
Managing operational requirements on the objects of a service oriented architecture (SOA)
ActiveUS20080229195A1Simple definitionShortens overall definition timeRequirement analysisTransmissionService-oriented architectureFunctional requirement
A registry for a service oriented architecture (SOA) comprising a plurality of processing objects. The registry may include a plurality of non-formalized operation requirements for the plurality of SOA objects, a plurality of technical assertions for the plurality of SOA objects, and a plurality of links, linking each non-formalized operation requirement to at least one technical assertion of the registry.
Owner:SOFTWARE AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com