Patents
Literature
119 results about "Social Security number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the United States, a Social Security number (SSN) is a nine-digit number issued to U.S. citizens, permanent residents, and temporary (working) residents under section 205(c)(2) of the Social Security Act, codified as 42 U.S.C. § 405(c)(2). The number is issued to an individual by the Social Security Administration, an independent agency of the United States government. Although the original purpose for the number was for the Social Security Administration to track individuals, the Social Security number has become a de facto national identification number for taxation and other purposes.
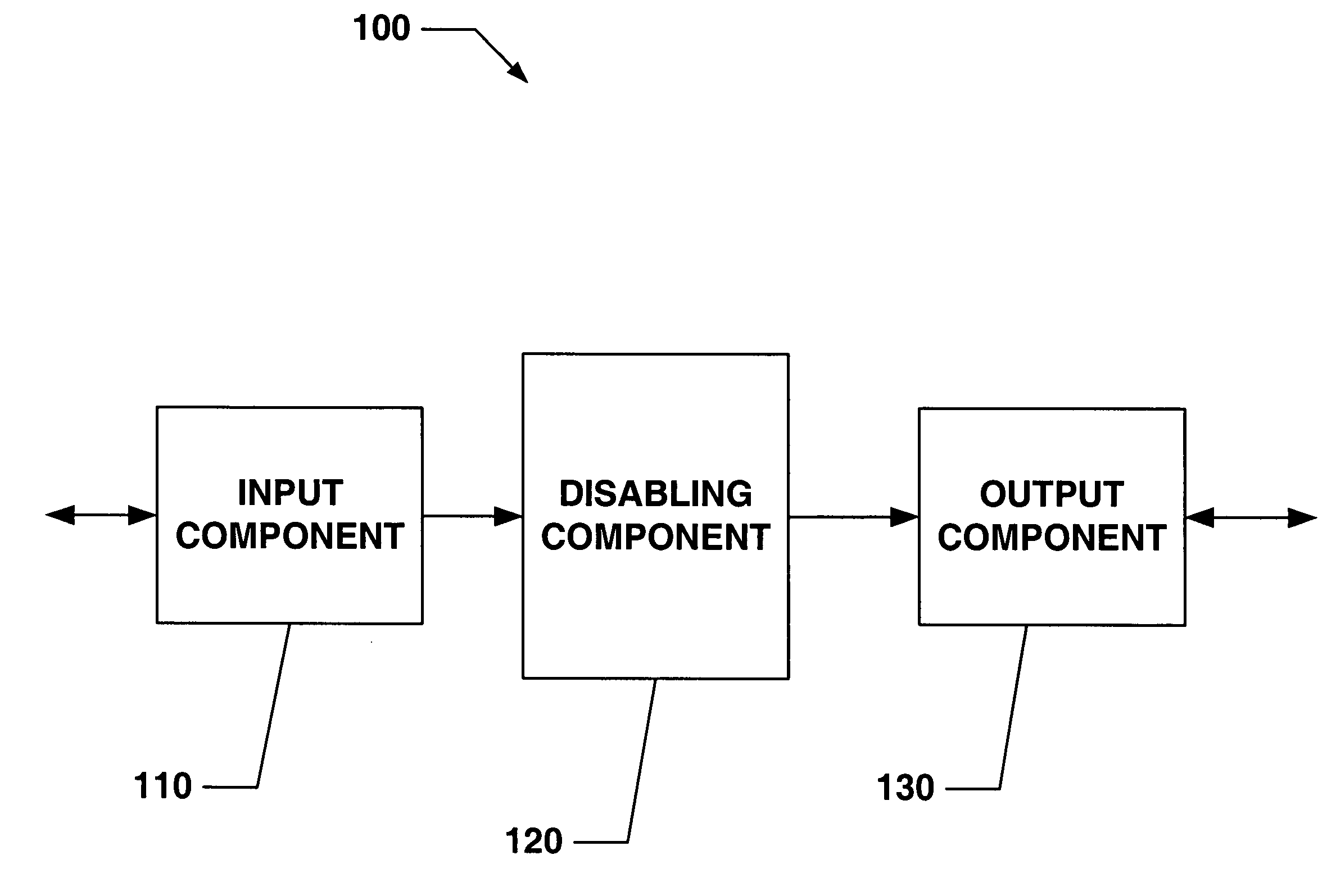
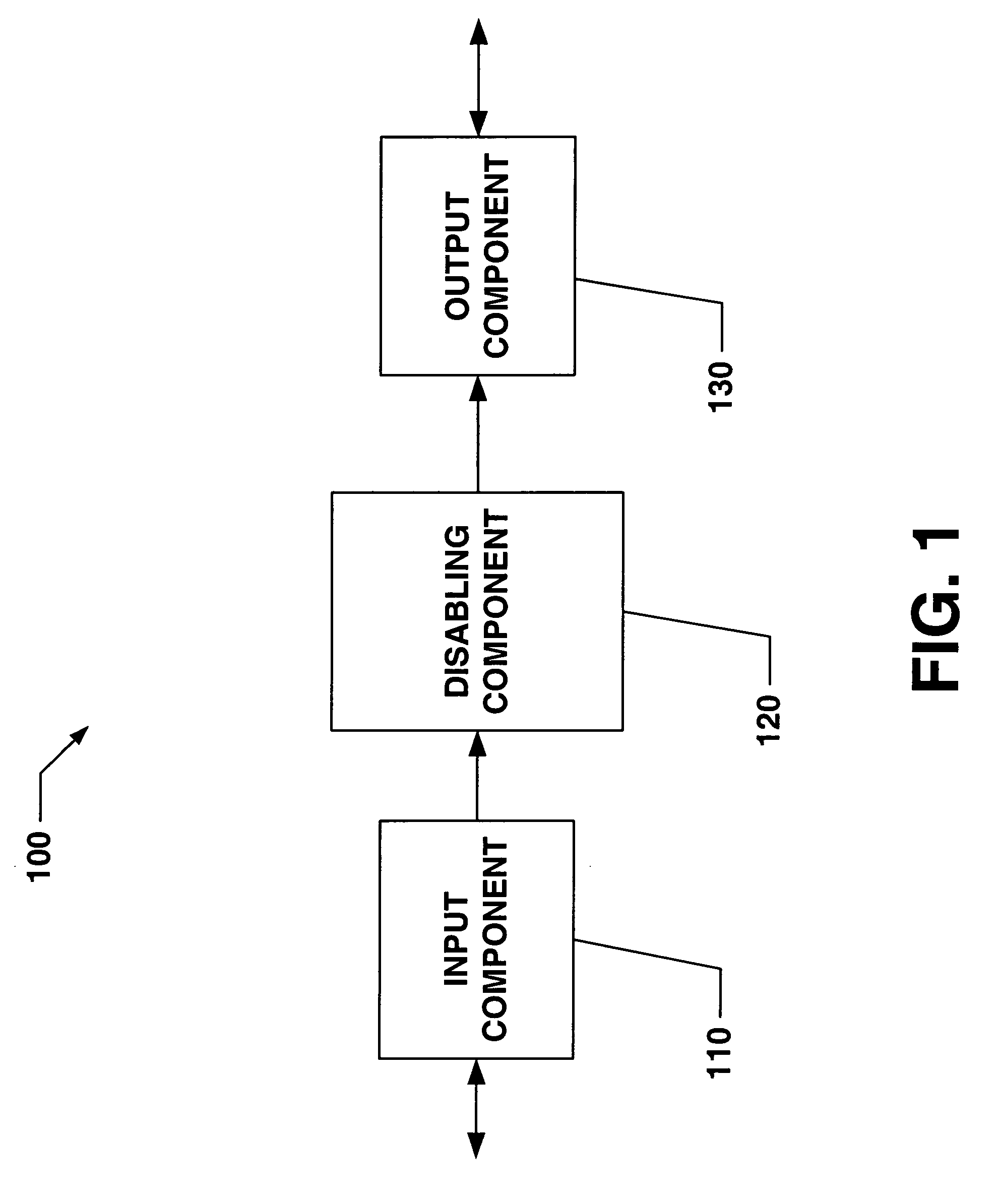
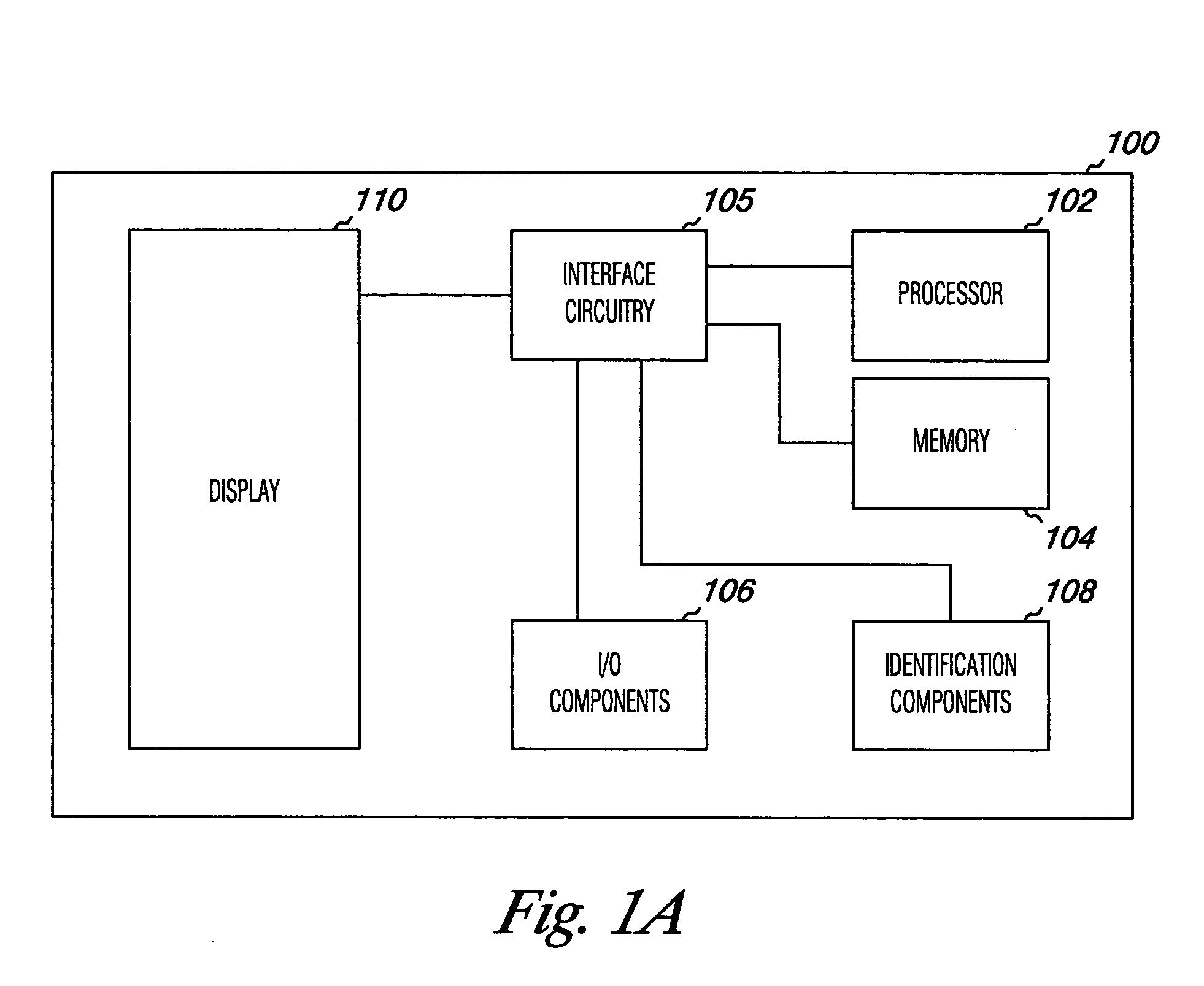
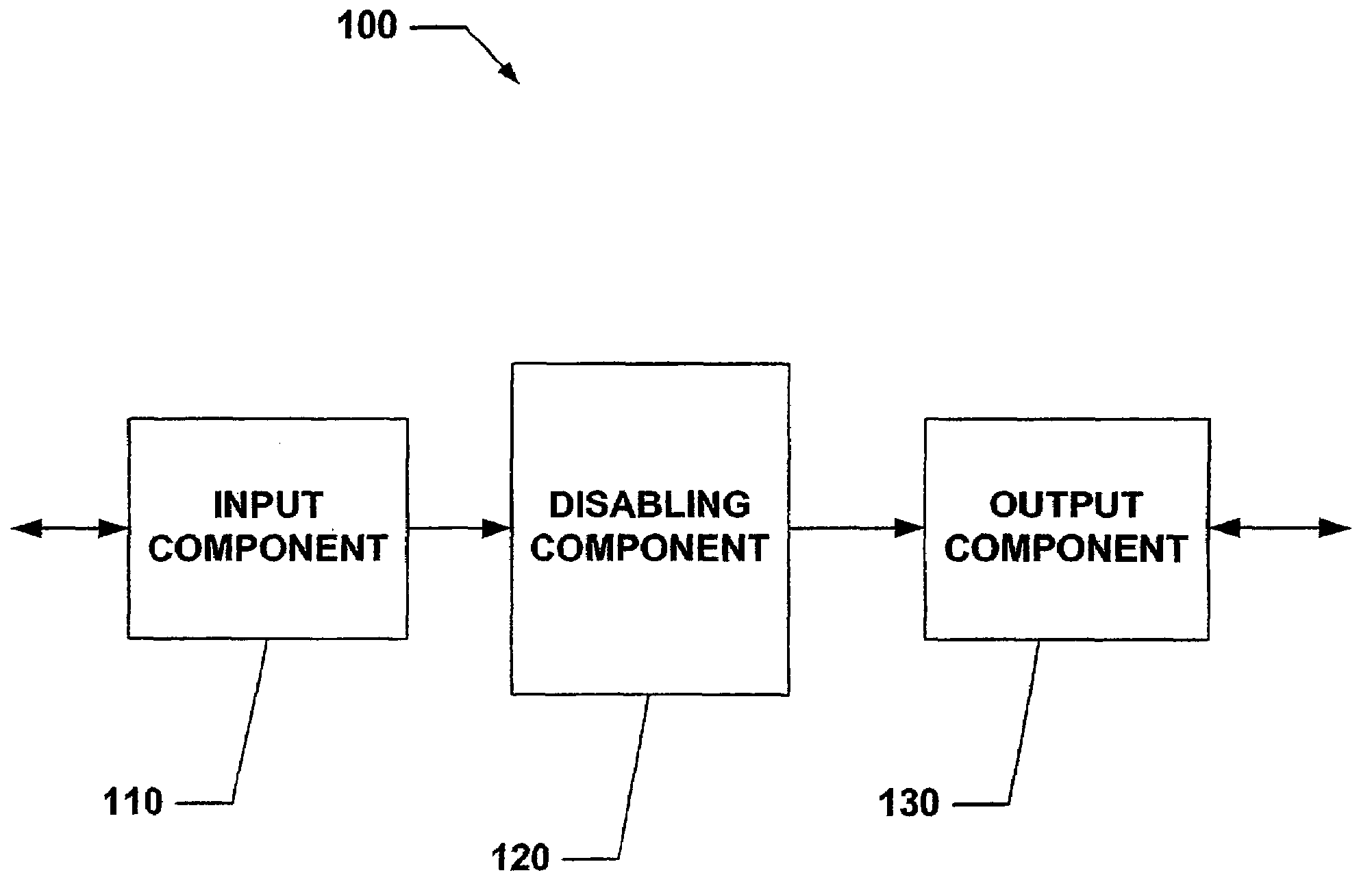
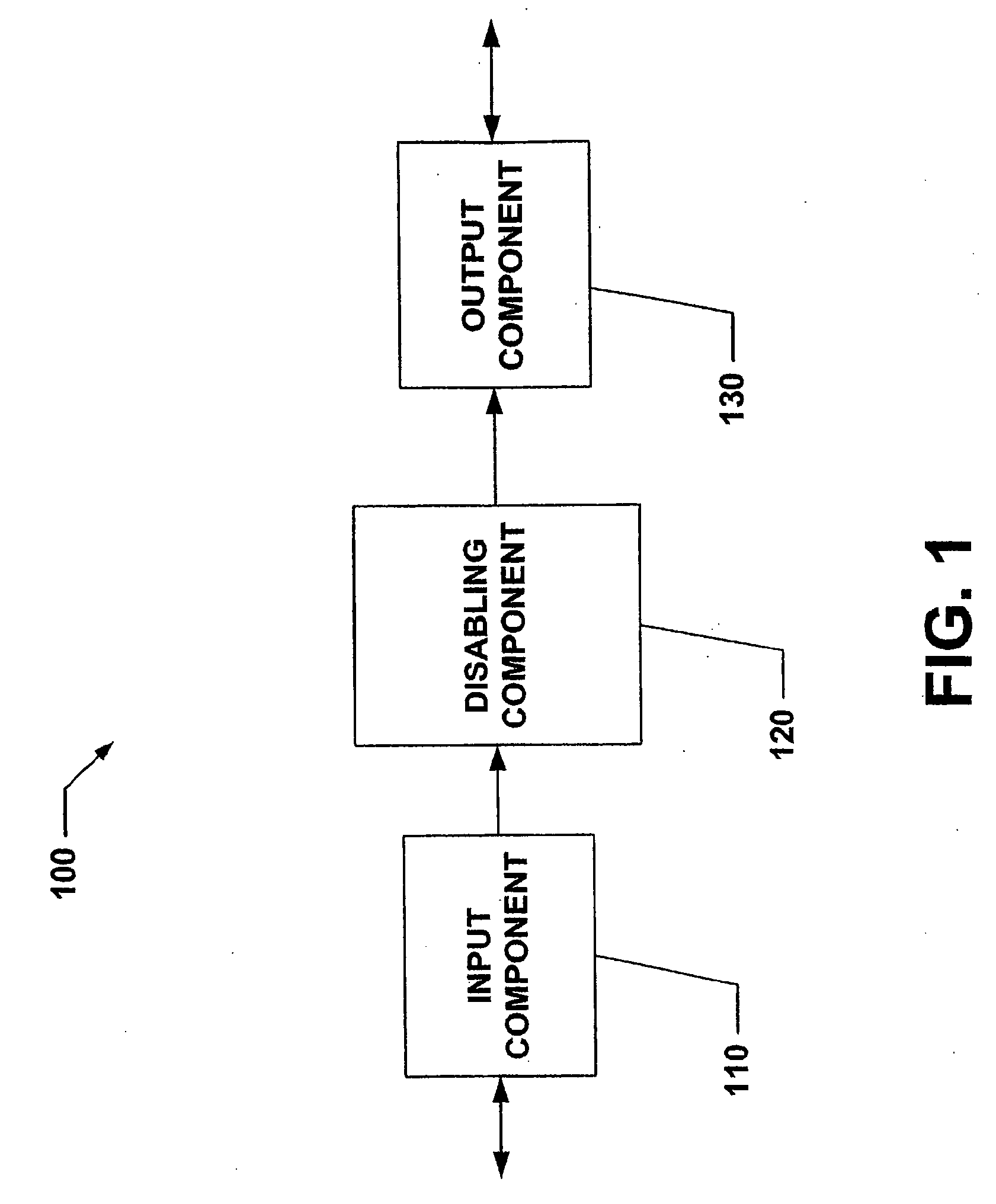
Systems and methods that provide user and/or network personal data disabling commands for mobile devices
InactiveUS20050186954A1Reduce harmPrevent unauthorized accessUnauthorised/fraudulent call preventionUnauthorized memory use protectionCredit cardInternet privacy
The present invention relates to systems and methods that employ various mechanisms to selectively disable mobile device functionality. In general, mobile devices can be utilized to store personal and / or highly sensitive information such as bank account numbers, social security numbers, credit card numbers and the like. If the mobile device is lost or stolen, data stored within the device can be accessed by an unauthorized user; and, thus, any personal and / or highly sensitive information can be obtained. In order to mitigate unauthorized access, the subject invention provides a disabling component that communicates with the lost or stolen device to render data stored thereon inaccessible. Further, the data can be stored in local or remote locations to backup stored information, thereby creating a more robust and reliable method of storing information important to the device owner. These features provide enhancements over conventional mobile device security techniques.
Owner:NOKIA CORP
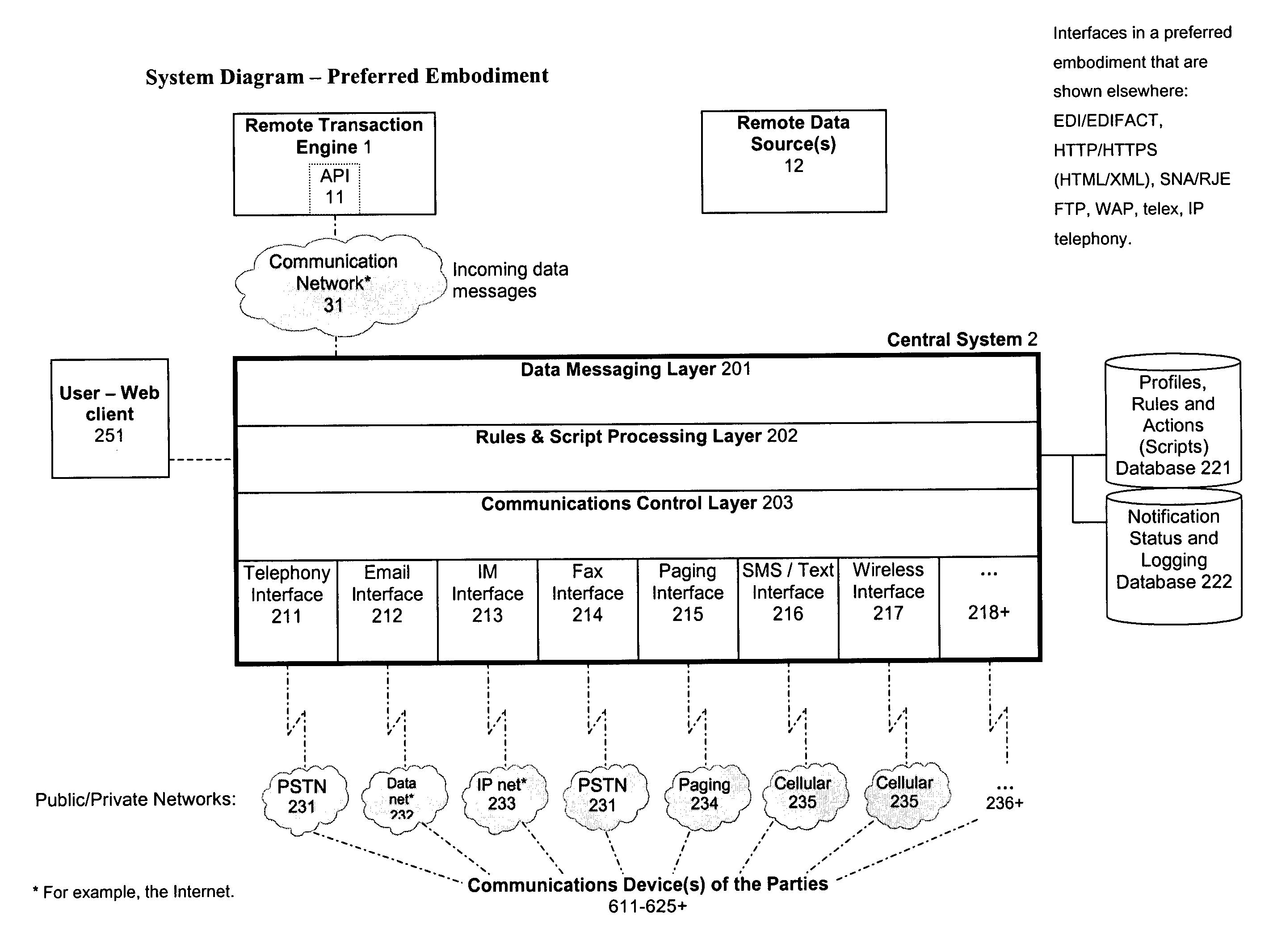
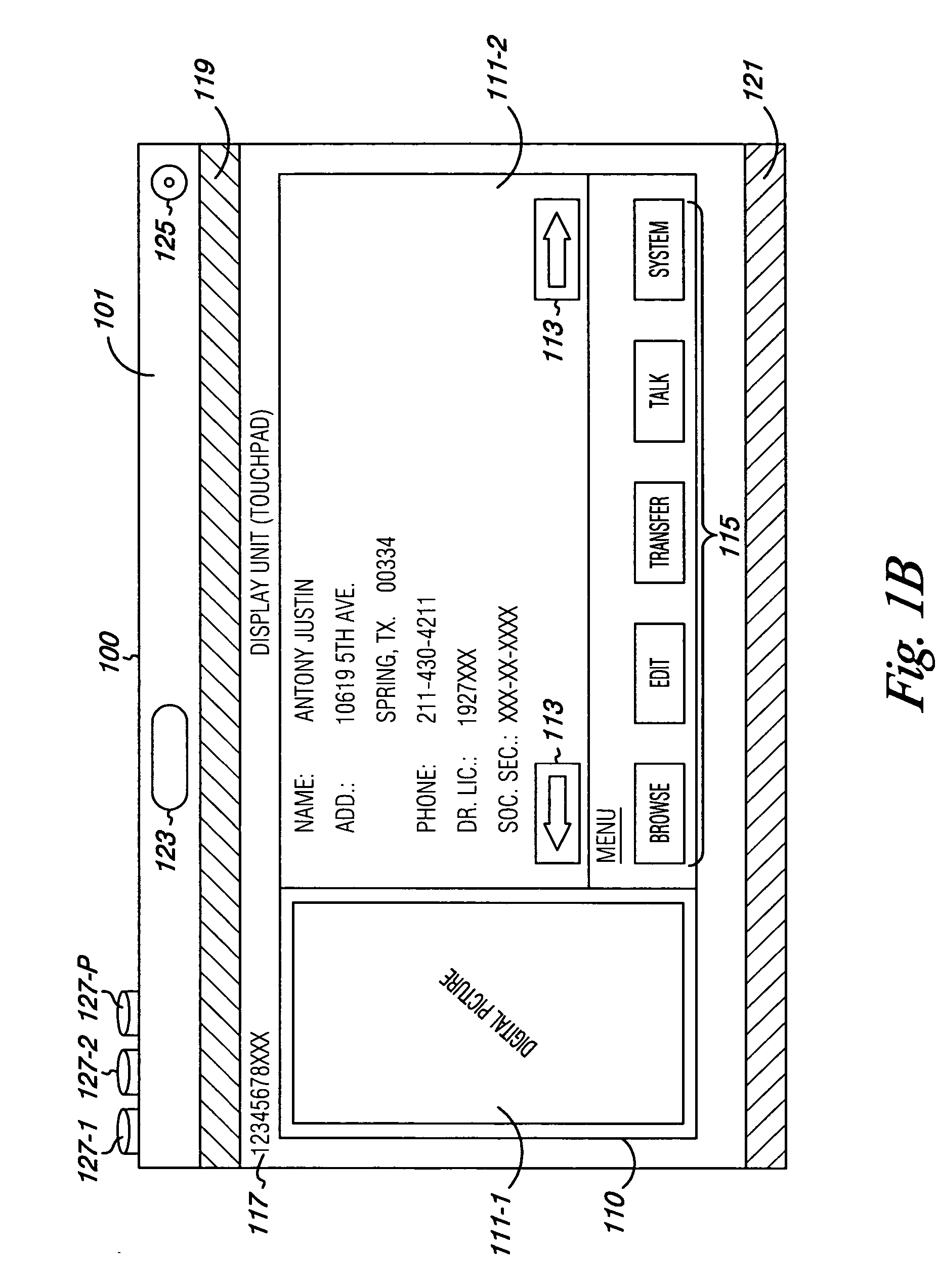
System and method for verification, authentication, and notification of a transaction
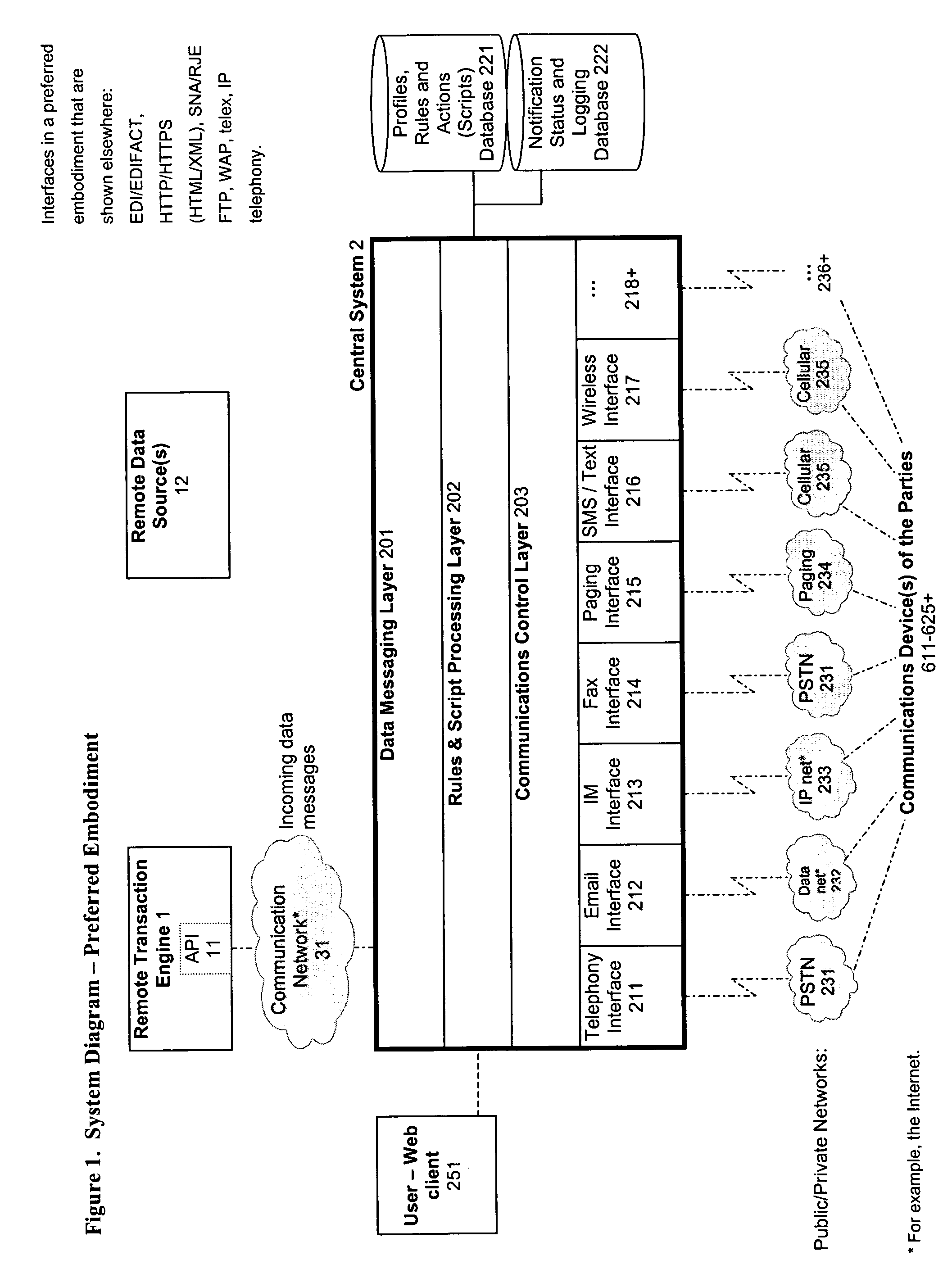
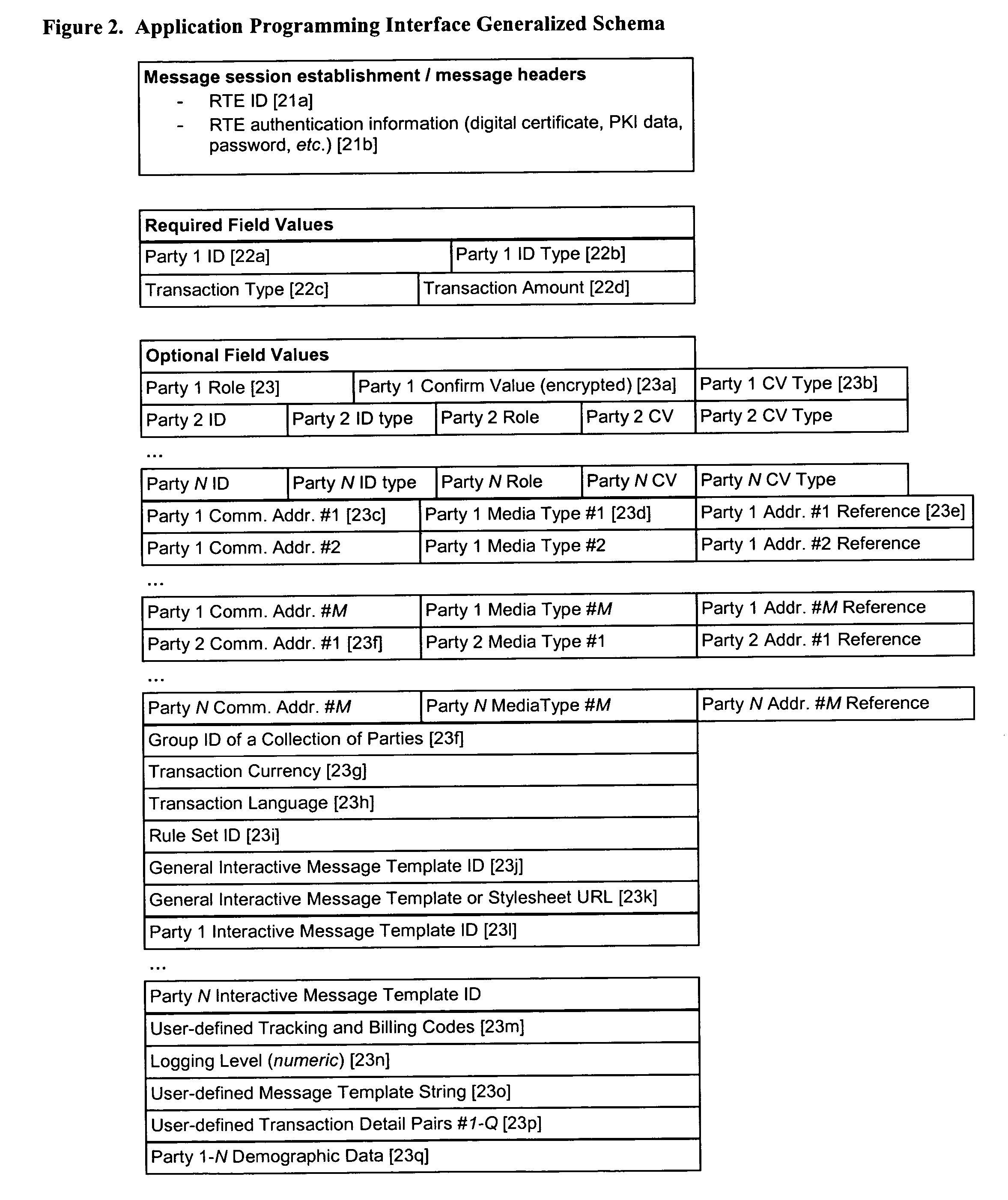
ActiveUS20040078340A1Increase valueFinanceBuying/selling/leasing transactionsTelecommunications linkSocial Security number
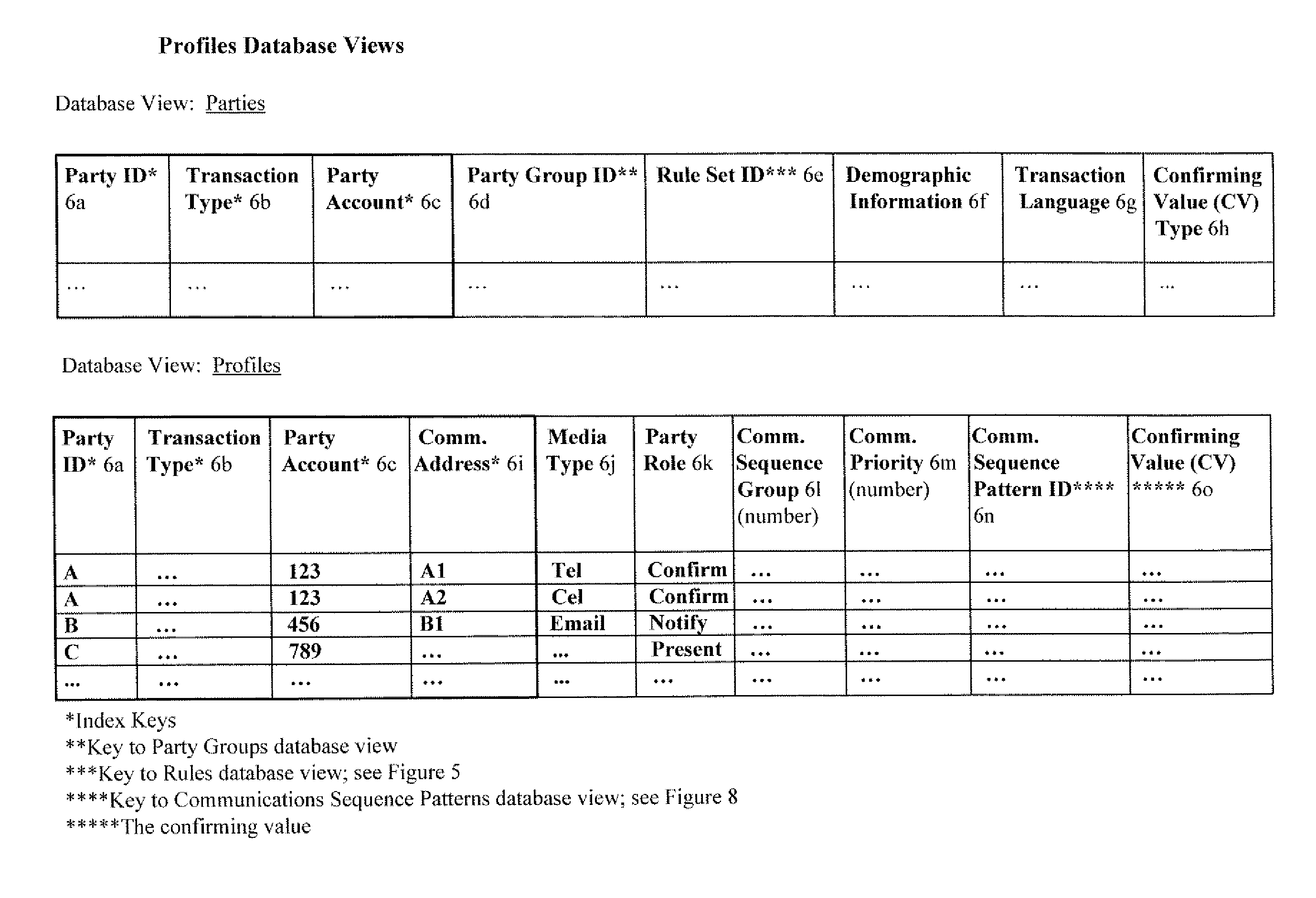
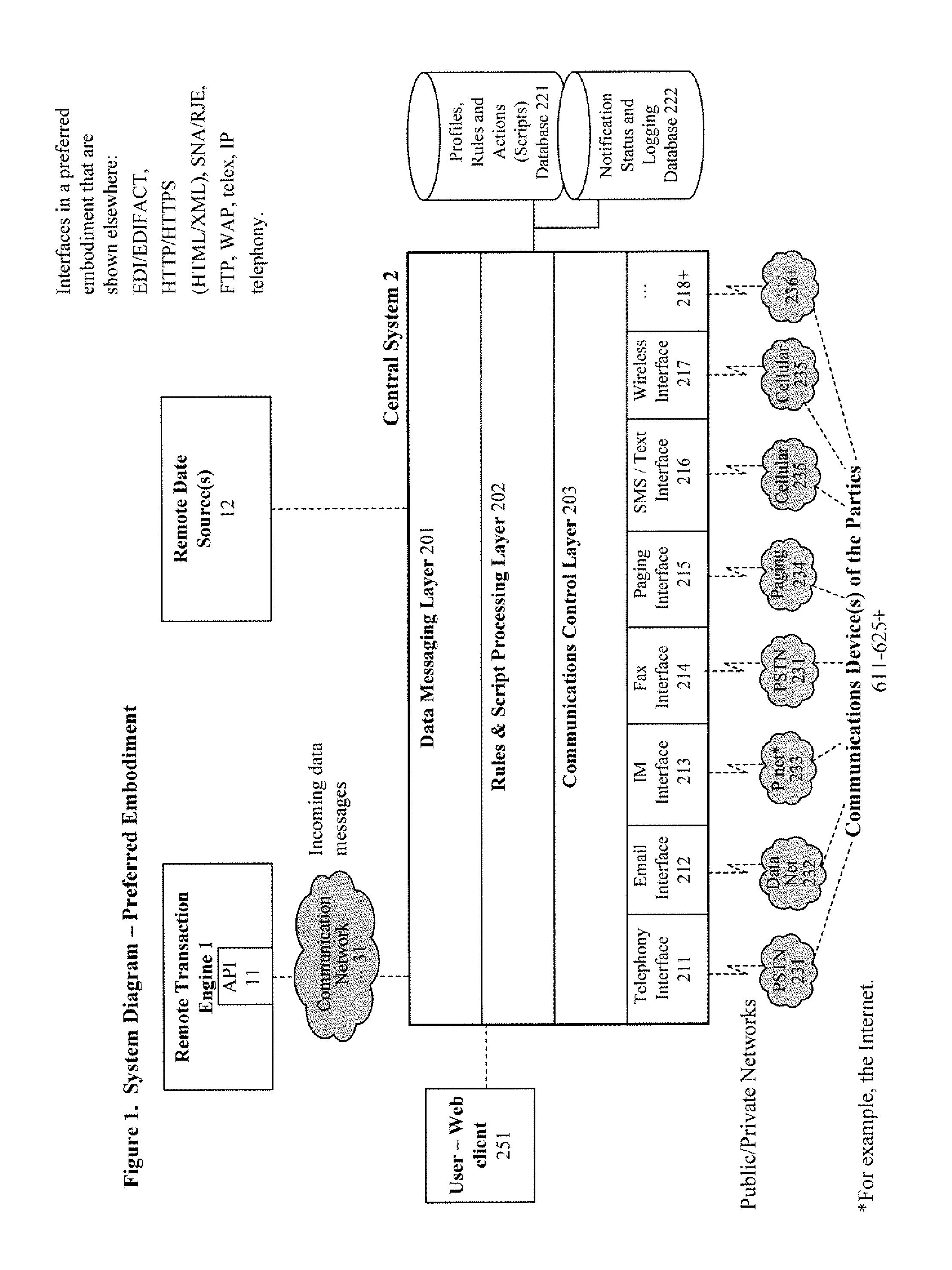
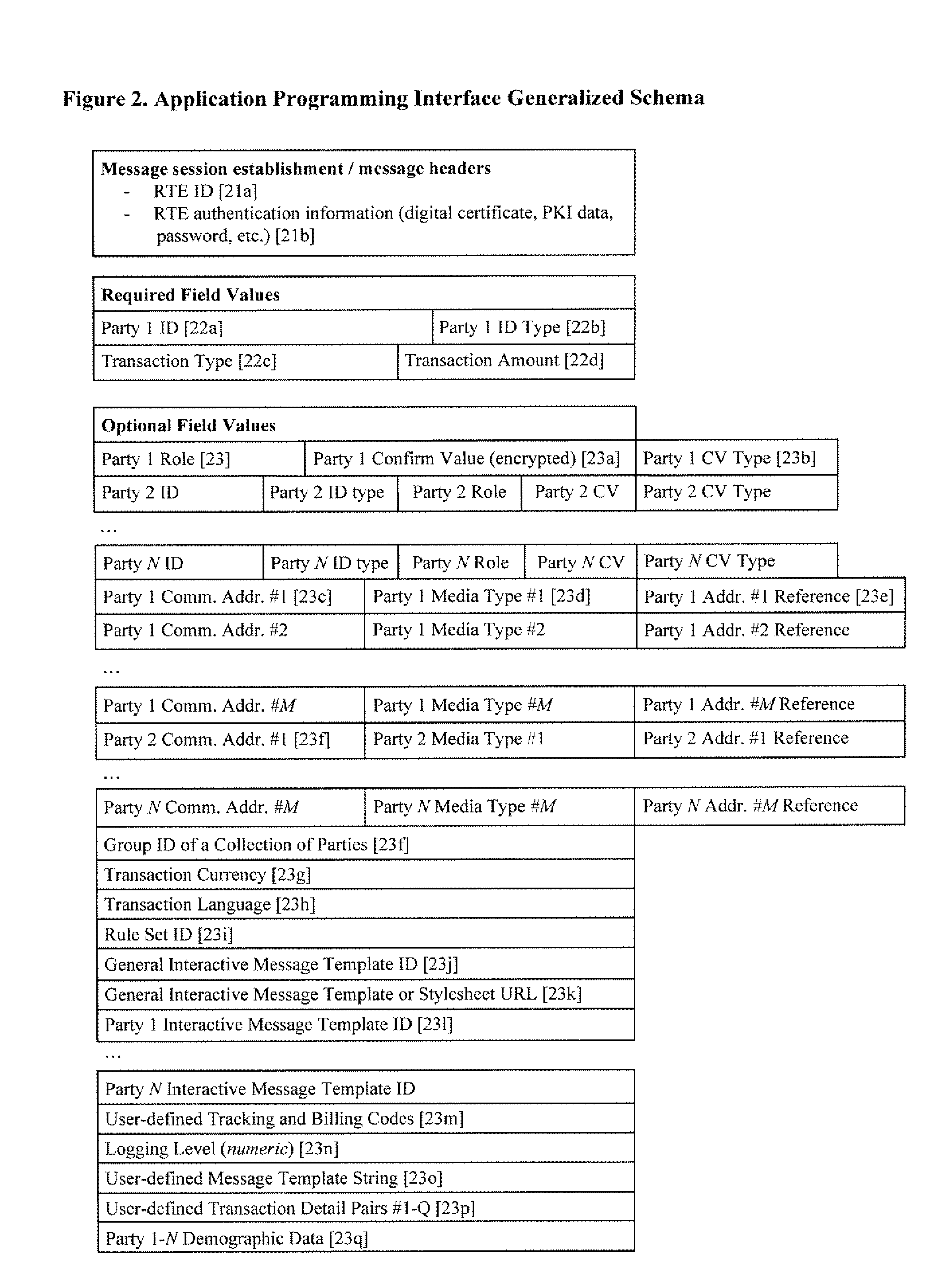
A system and method for verifying, authenticating, and providing notification of a transaction, such as a commercial or financial transaction, with and / or to at least one party identified as engaging in the transaction and / or identified as having a potential interest in the transaction or type of transaction, are provided. A central system accepts information regarding a transaction, including information about at least one party identified as engaging in the transaction, such as by a credit account number or Social Security number or merchant account number, and / or identified as having a potential interest in the transaction. Based on the information regarding the transaction and any supplemental information the central system determines, the central system communicates with and / or to at least one party and / or additional or alternative parties, via at least one communications device or system having a communications address, such as a telephone number or Short Message Service address, predetermined as belonging to the at least one party and / or additional or alternative parties. Via said communications, at least one party having an interest or a potential interest in the transaction may be notified of it, and may further be enabled or required to supply additional verifying or authenticating information to the central system. If the transaction was initiated or engaged in via a communications link, such as via the Internet, said communications preferably occur over at least one different communications link and / or protocol, such as via a wireless voice network. The central system may then compute a result based on the outcomes of said communications, and may then transmit the result to the user and / or to a second system or device.
Owner:ST ISIDORE RES
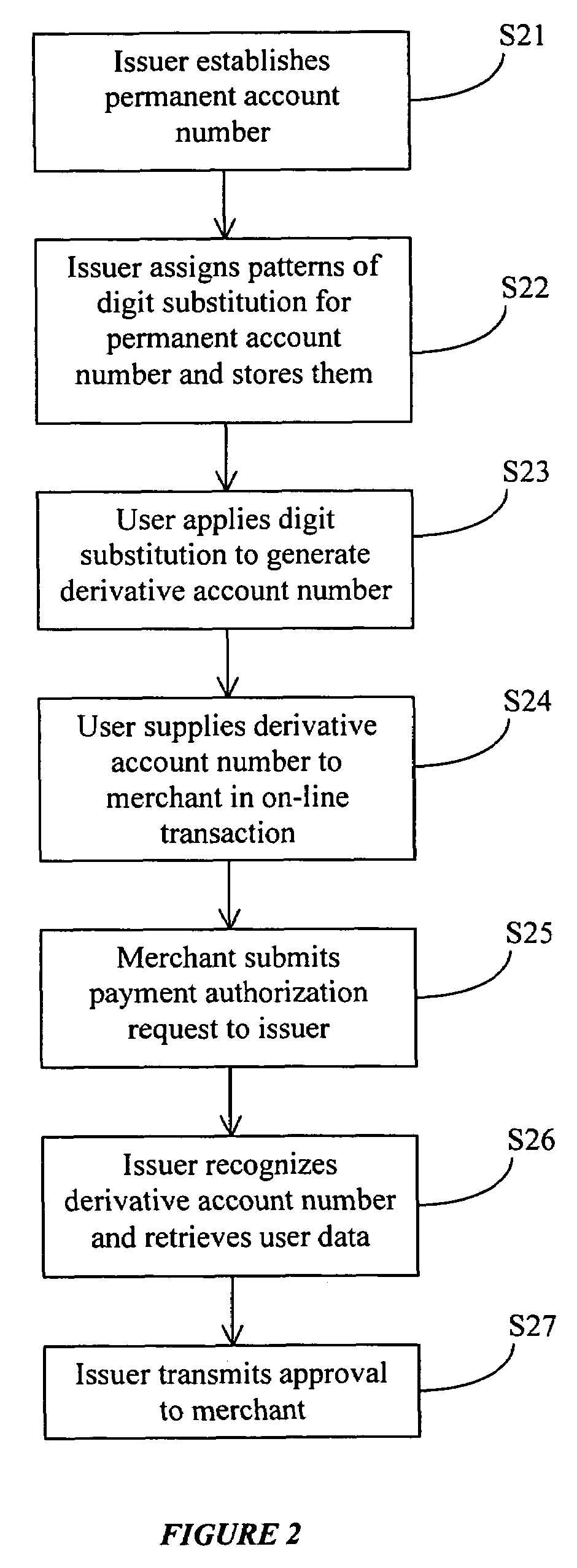
Payment card authentication system and method
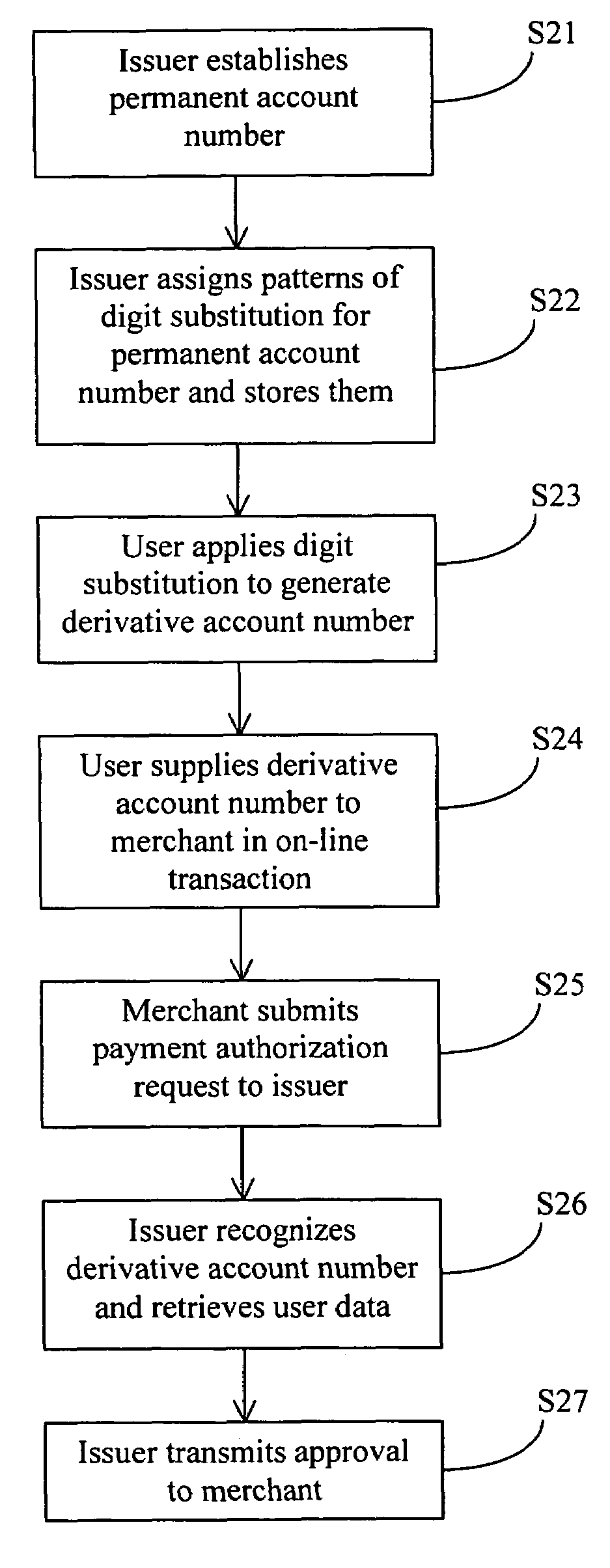
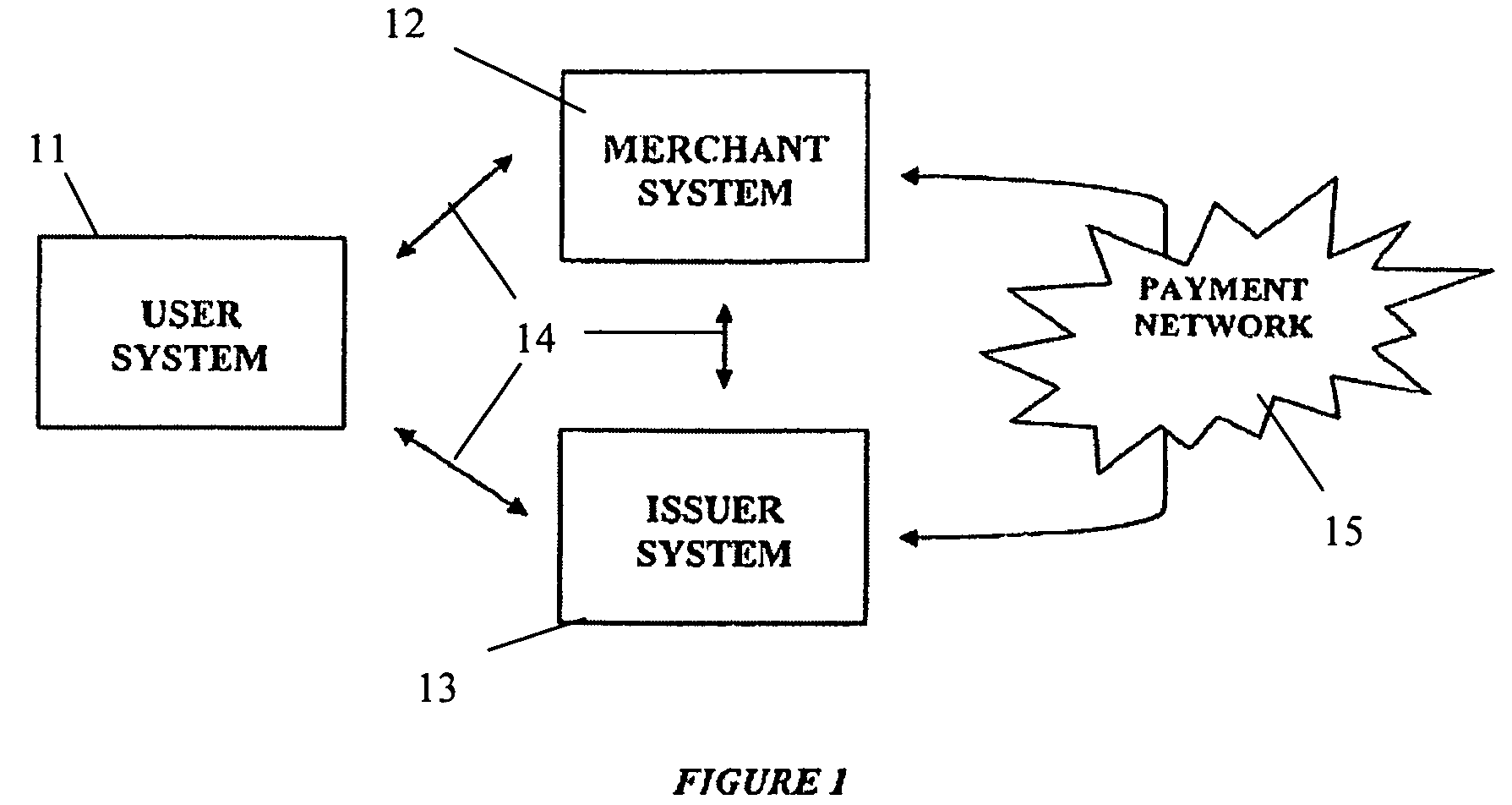
A system and method for authenticating payments are described. In a registration and activation step, an issuer issues to a user one or more patterns of digit substitution associated with a permanent account number. The patterns of digit substitution can then be used to generate derivative account numbers based on the permanent account number. During a commerce transaction, the user interacts with a merchant and specifies a derivative account number. The merchant transmits the derivative account number and other transaction information to the issuer for approval. Based on the derivative account number, the issuer retrieves the permanent account number and processes an approval. By using this method, a user's actual permanent account number is not revealed or transmitted via an unsecure network, which protects it from being stolen. The method may be used in various transactions to protect other personal identification information such as social security numbers, driver license numbers, etc.
Owner:FRIEDMAN MAURY SAMUEL
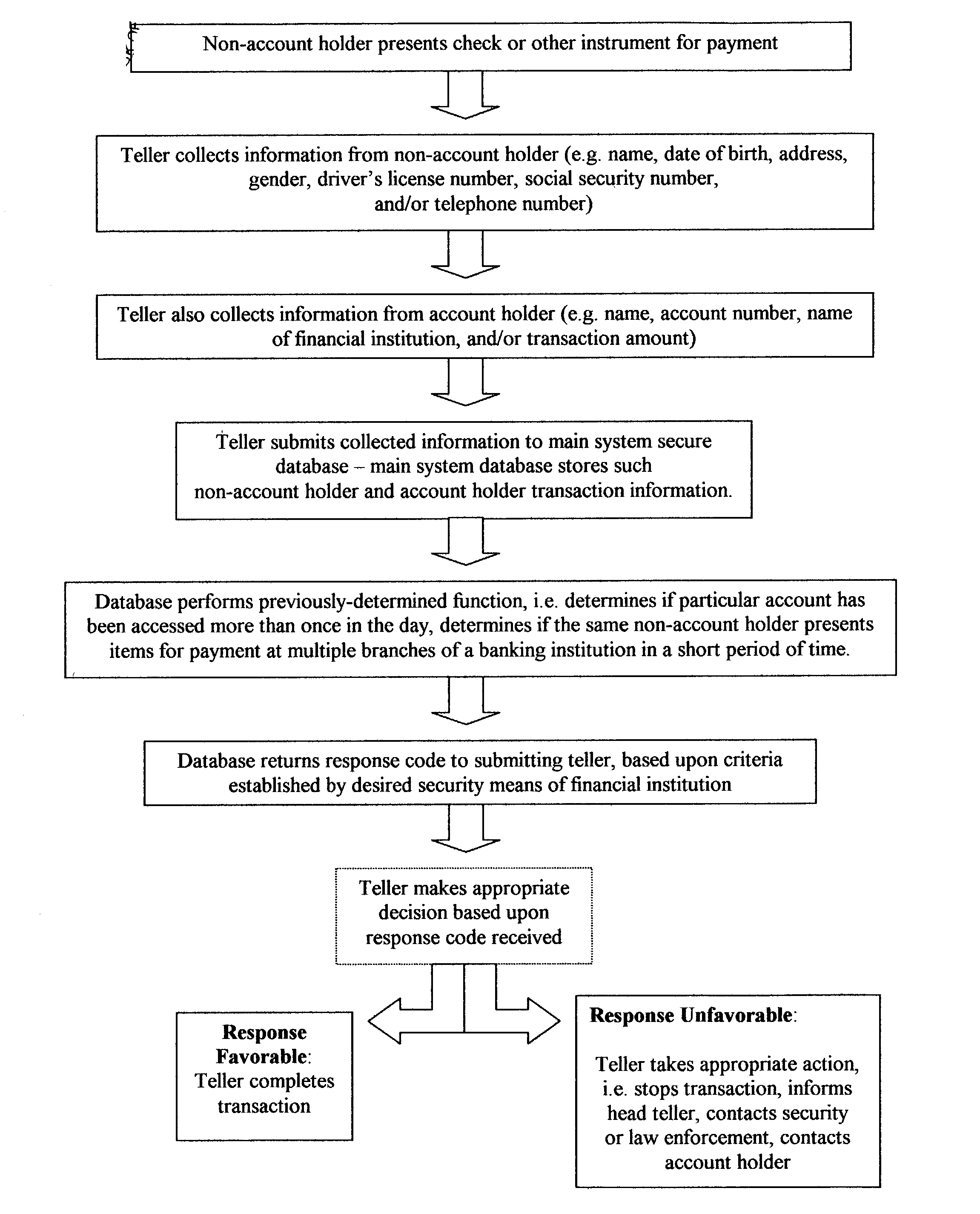
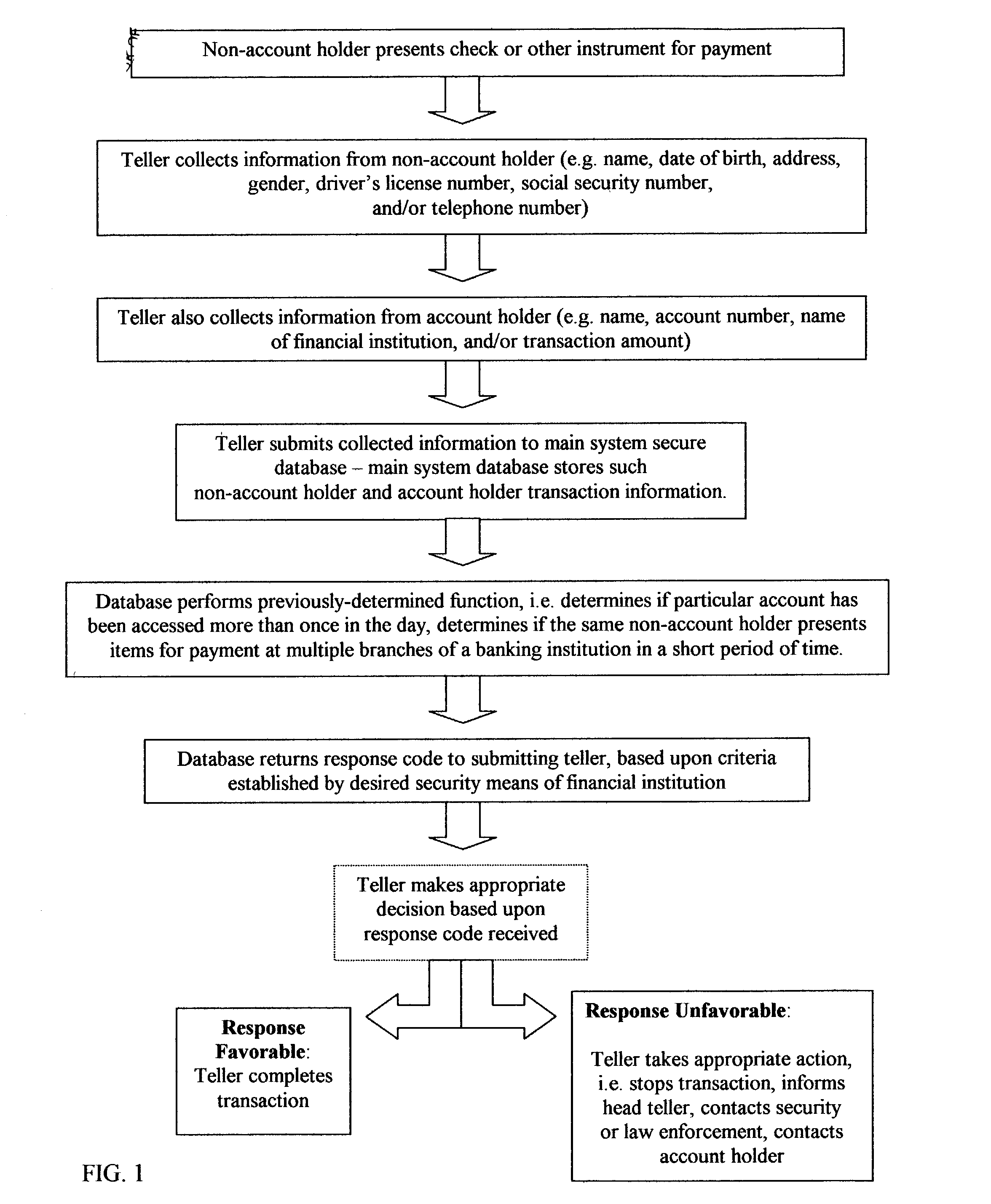
Fraud detection and security system for financial institutions
InactiveUS20030182214A1Limit losses to individual FIsAvoid checkingFinancePayment circuitsSocial Security numberCheque
A fraud detection and security system for financial institutions utilizes a secure database of information relating to financial transactions of non-account holders who present checks and other instruments for payment. The system collects and tracks the frequency of particular aspects of the subject's behavior, and flags deviations from such norms for the purpose of indicating that fraudulent or criminal behavior may be occurring. At such time, the teller or other employee with whom the subject is dealing may stop the transaction, to the benefit of the financial institution and account holder. The system also allows for law enforcement to detect related transactions, or a string of criminal activity from the same perpetrator. In the preferred mode, the system includes a teller collecting information from the non-account holder, including name, date of birth, address, gender, driver's license number, social security number, and / or telephone number. At the time of the transaction, such data is submitted to the system database and the database returns a response code based upon criteria established by the financial institution's desired security measures, accomplished by installation of new software or by integration of a custom program. The system alerts tellers to suspicious activity, such as when a particular account is accessed more than once in a day, or when the same non-account holder presents items for payment at multiple branches of a banking institution in a short period of time.
Owner:TAYLOR MICHAEL K
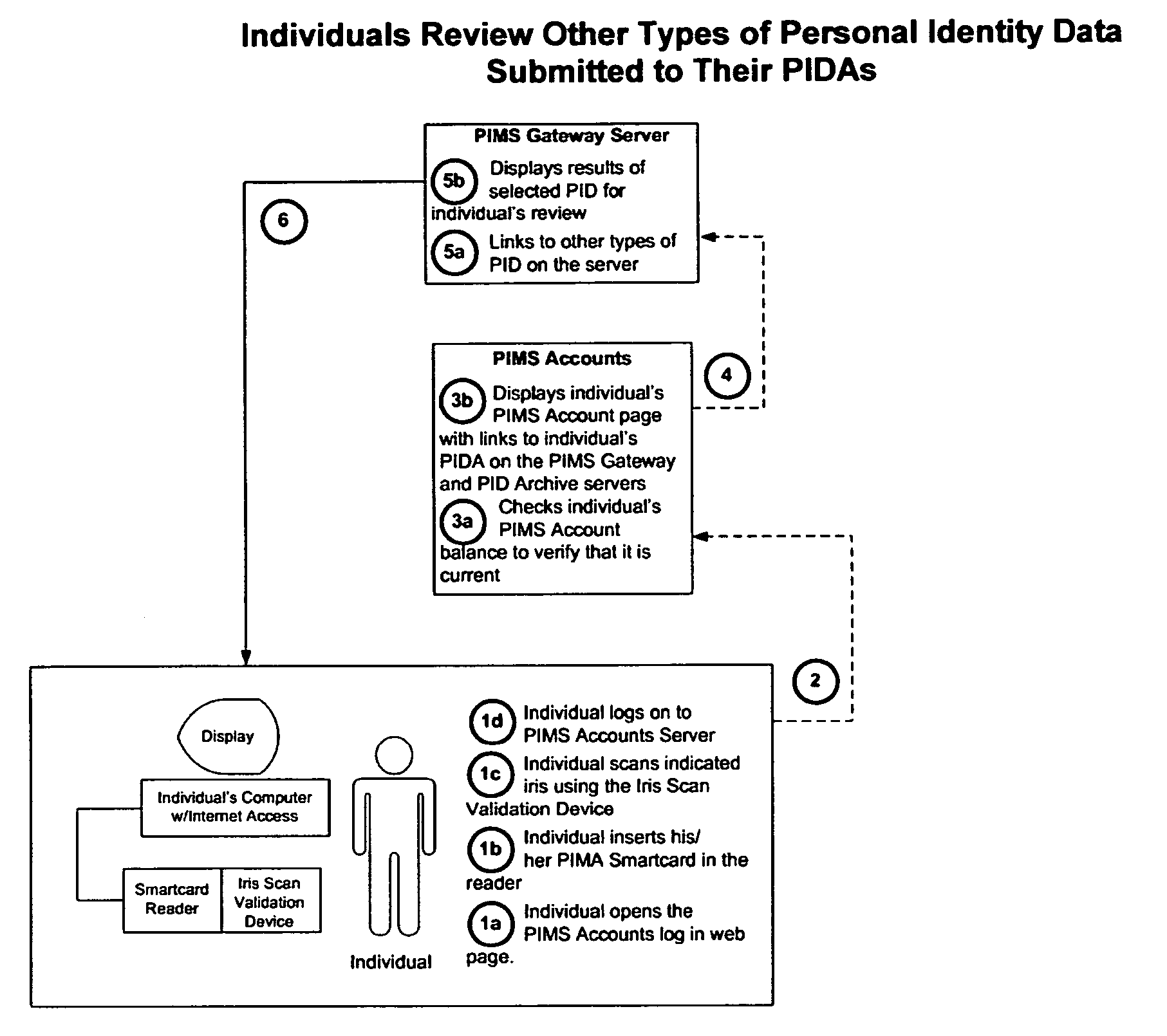
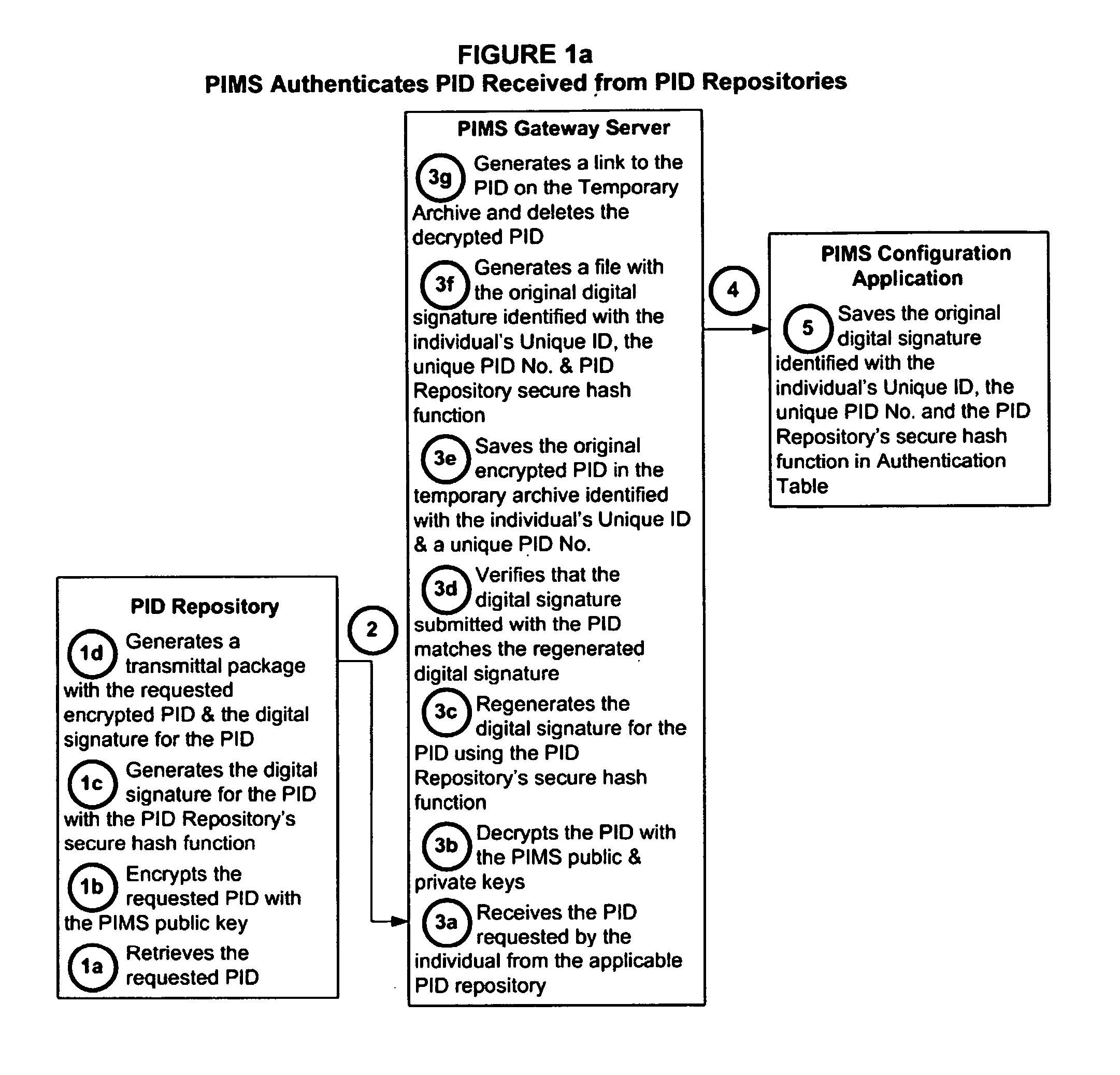
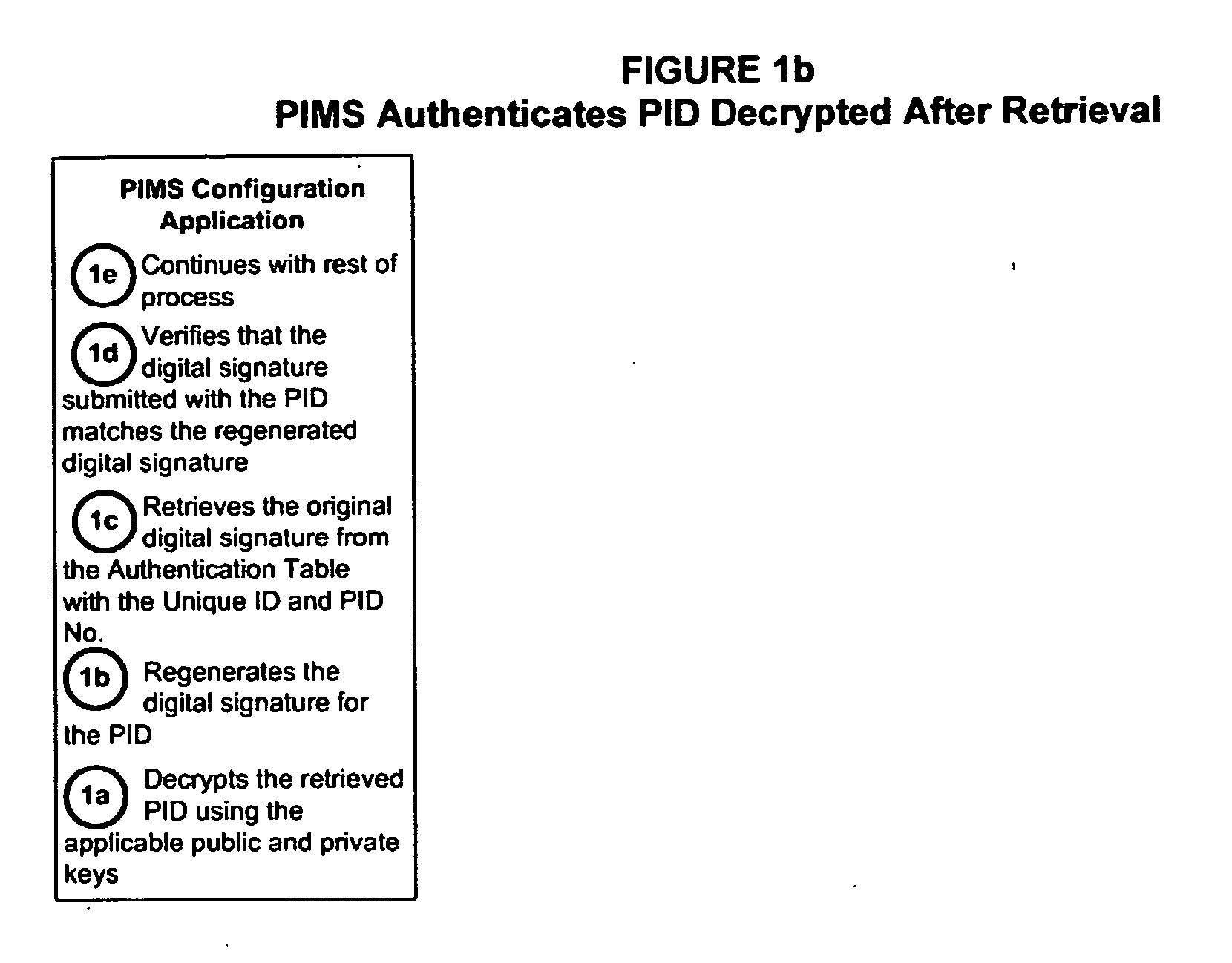
Personal identity data management
InactiveUS20060034494A1Public key for secure communicationUser identity/authority verificationSocial Security numberSmart card
Systems, methods and apparatus for personal identity data management permit individuals to manage their criminal background, credit history, employment, demographic and educational information, for example, to establish their credentials and to help protect their good names. All access to this personal identity data, including the biometrics that uniquely establish the individuals' identity, is under the personal control of the individuals, with access limited to others only with their specific authorization. The subject systems, methods and apparatus include at least two separate archives that store encrypted data about individuals that can be accessed only via the individuals' biometrics specific to the archives and unique Identification Numbers. The Identification Numbers are encrypted when they are associated with the individuals' demographic data, which includes their names, Social Security Numbers and the Unique Identifiers assigned by the system to each of the individuals. Public / private key encryption is used to encrypt the Personal Identity Data maintained in the archives and the Identification Numbers maintained in a Personal Identity Management Service configuration application server that links the rest of the system to the archives. To permit the private keys to be securely retained for use in regenerating a. Smartcard in case of loss or damage, separate segments of the private key are stored on different servers each of which requires submittal of a different biometric, which must match the biometric associated with the private key segment.
Owner:NAT BACKGROUND DATA
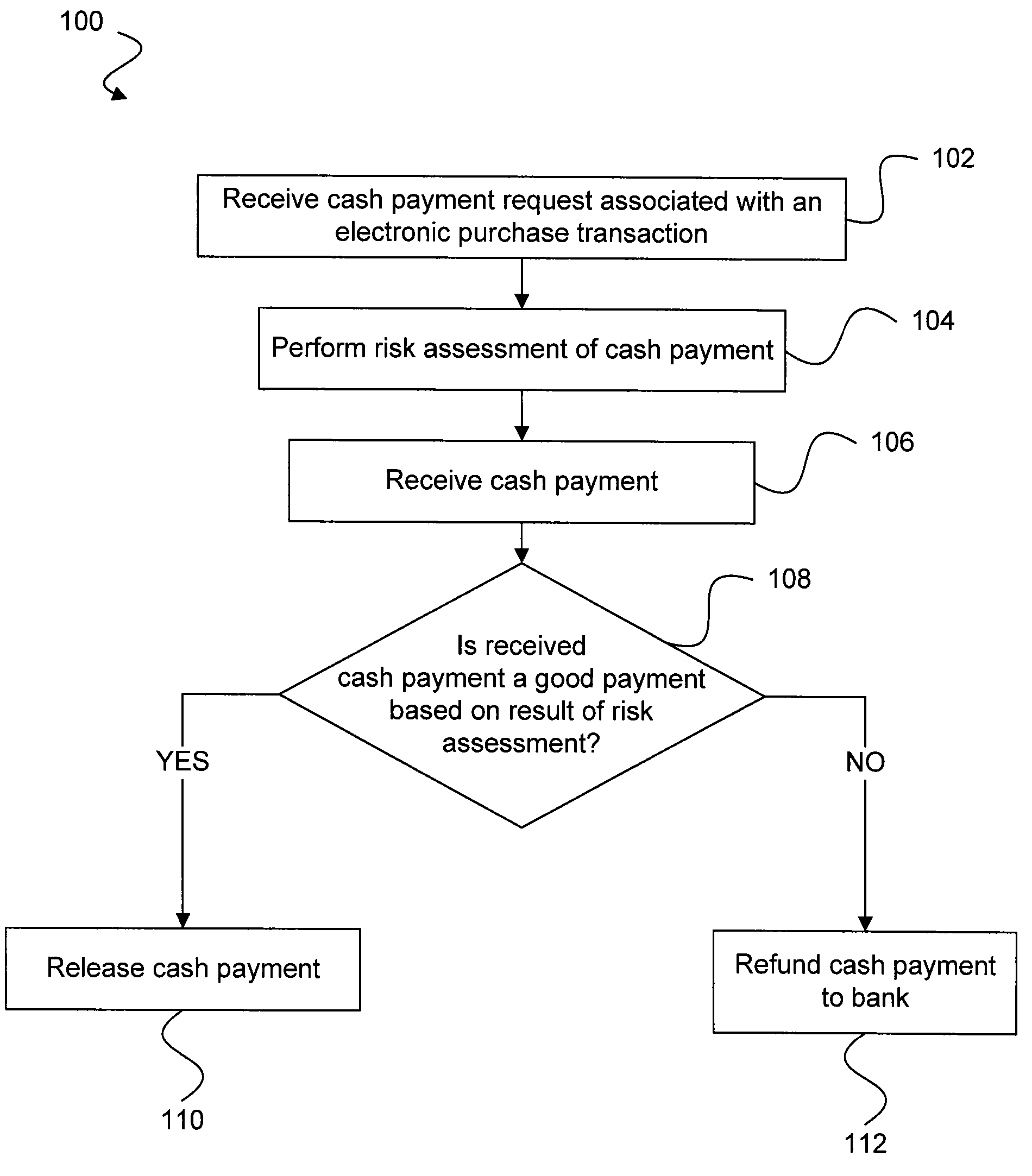
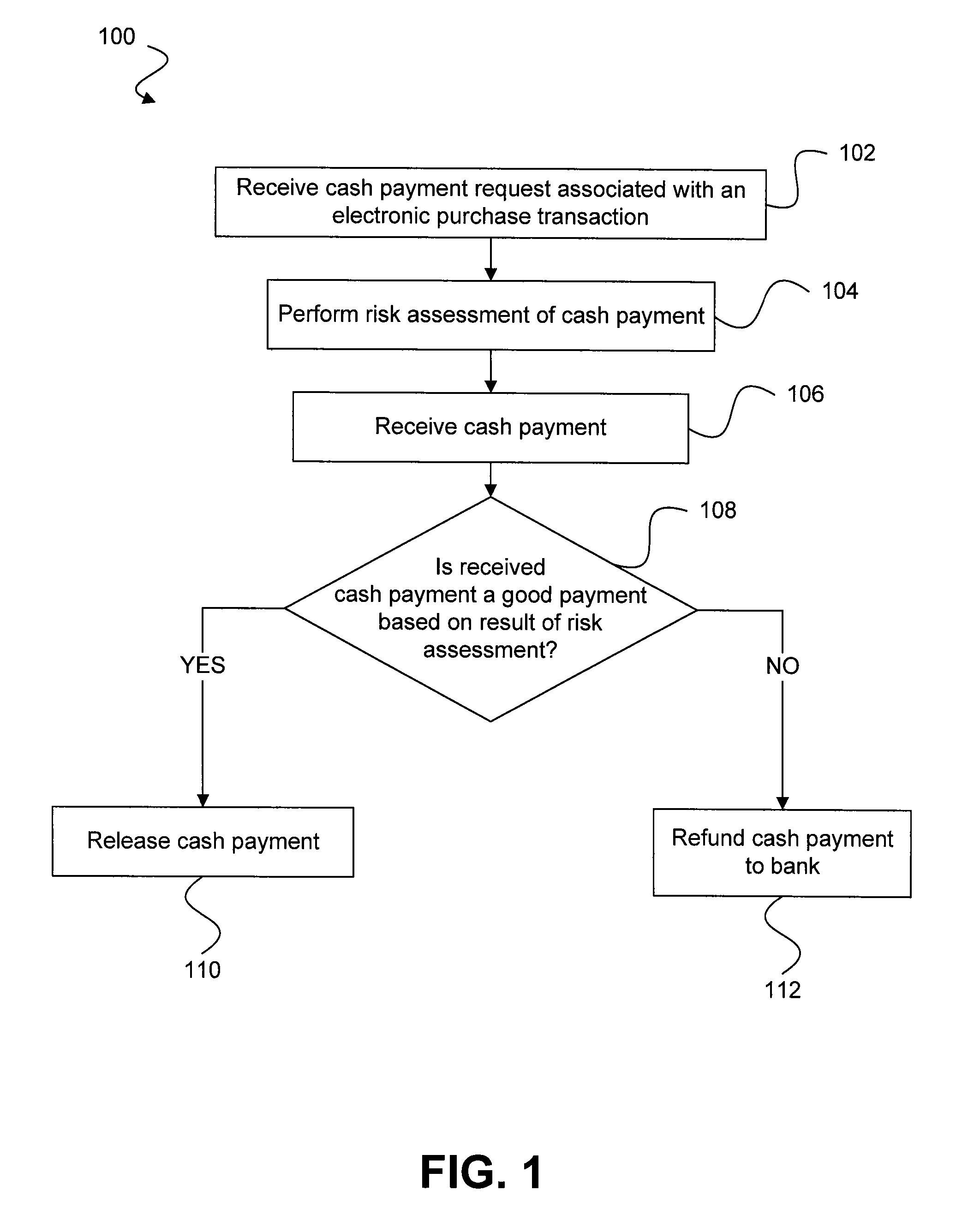
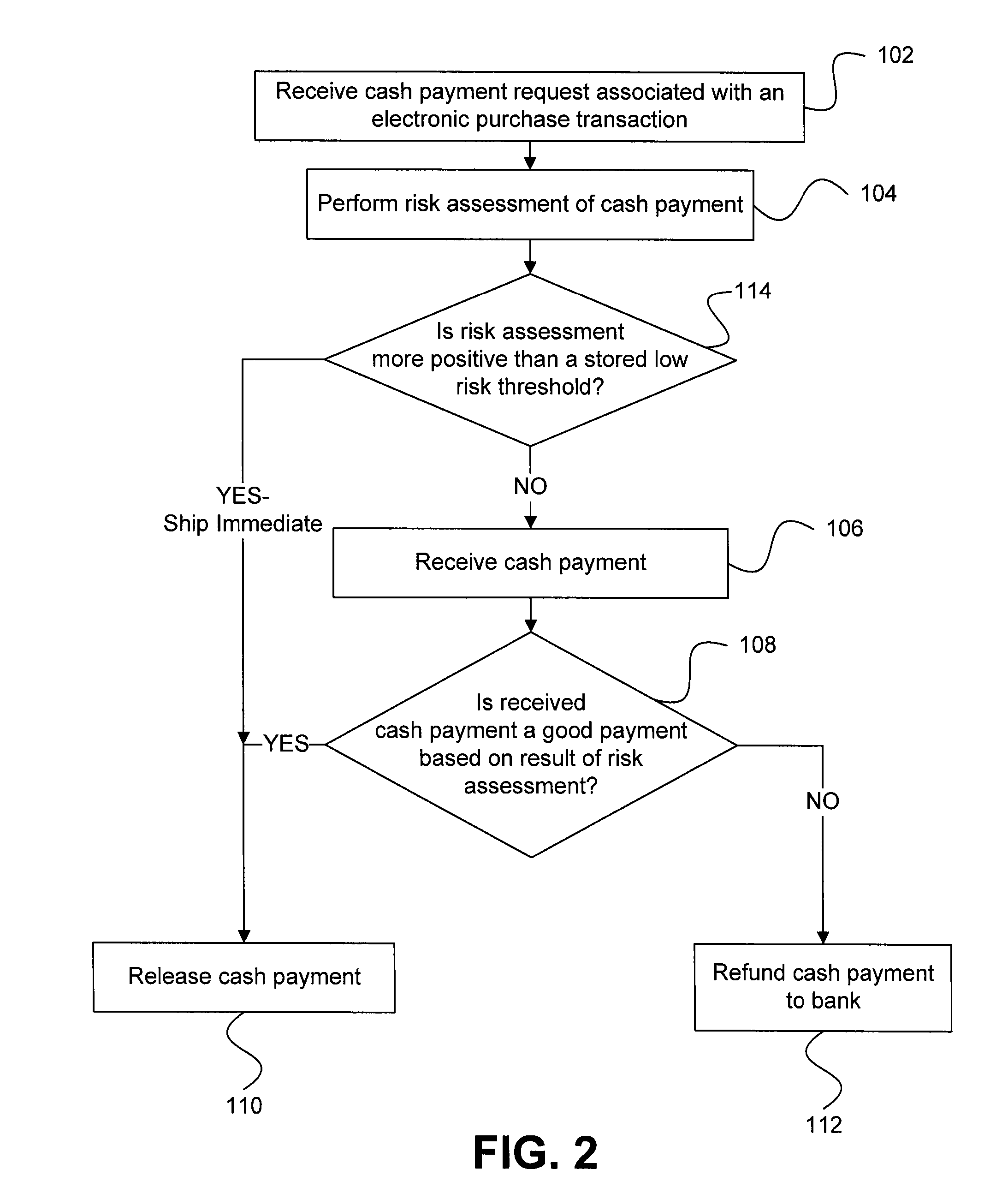
Risk detection and assessment of cash payment for electronic purchase transactions
A system and methods are provided which allow consumers to pay for ecommerce transactions through online bill payment and for merchants to determine that payments are not fraudulent. The system and methods do not rely on personal or confidential customer information relating to credit-cards and / or bank account routing information, date of birth and / or social security number. A risk manager can perform risk assessment for the cash payment based on order information and non-confidential purchaser information included in a cash payment request. In response to receiving an indication of the cash payment from the purchaser, a determination is made whether the cash payment is a good payment based on the risk assessment. The cash payment is released to a merchant in response to a determination that the cash payment is a good payment.
Owner:WESTERN UNION FINANCIAL SERVICES
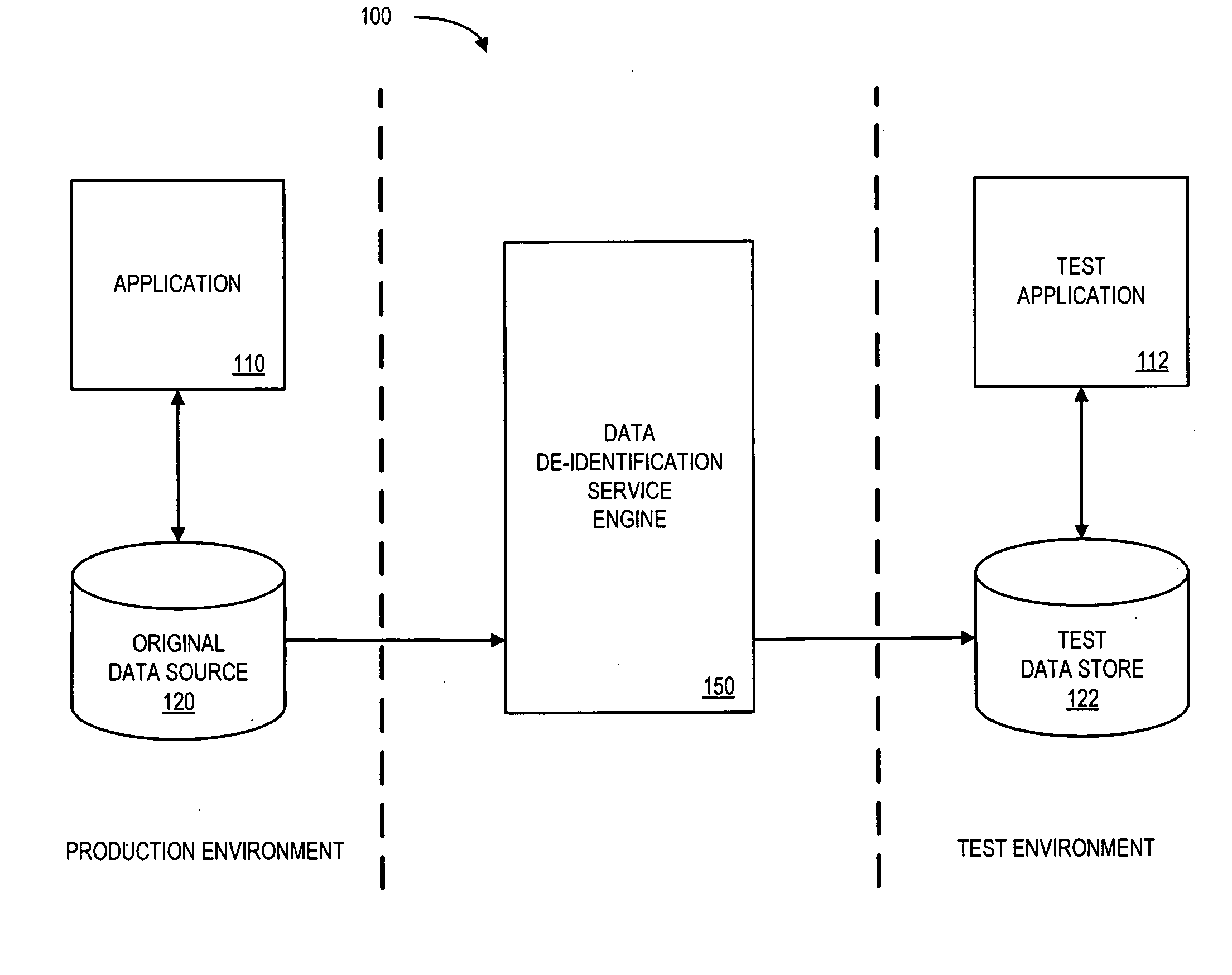
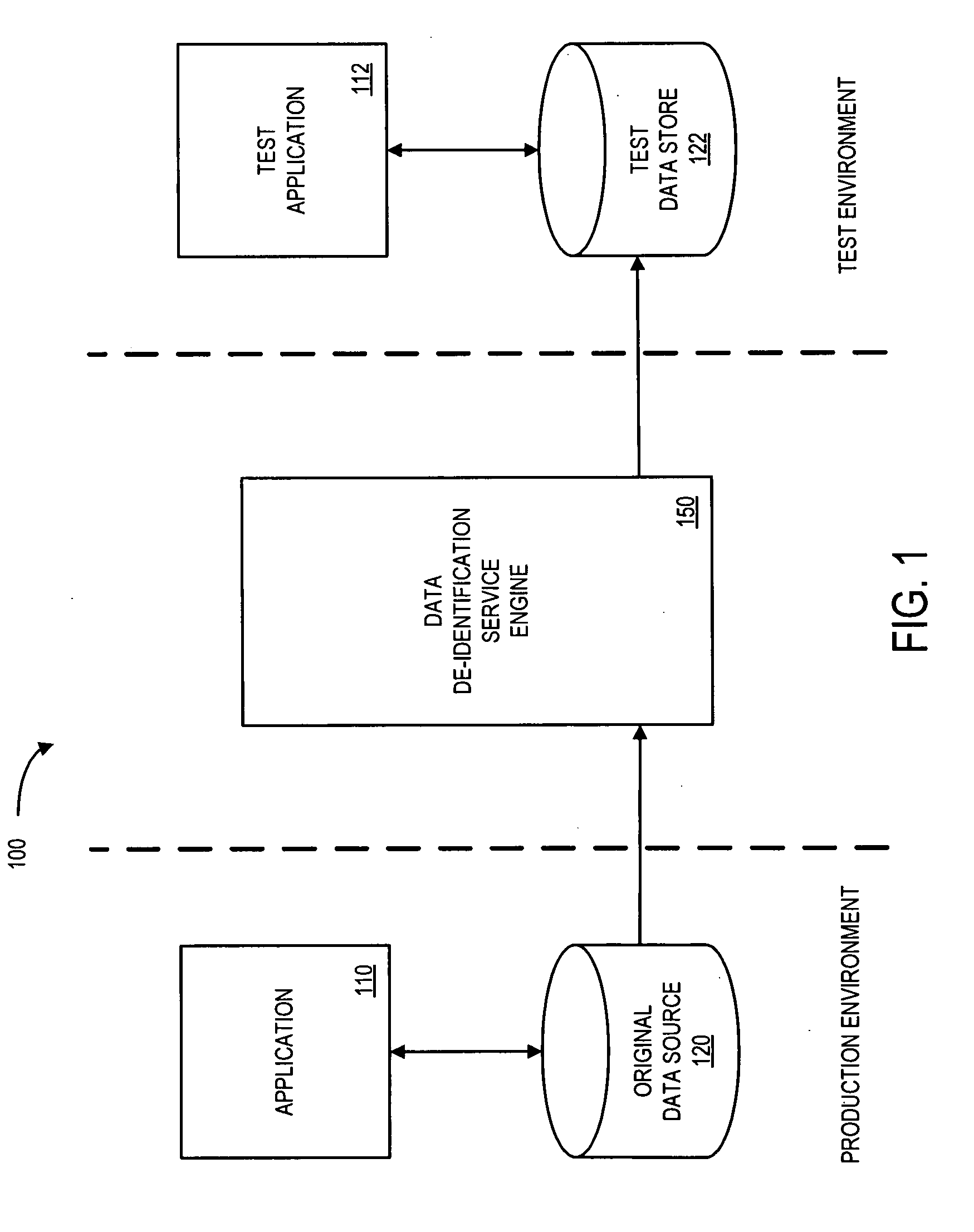
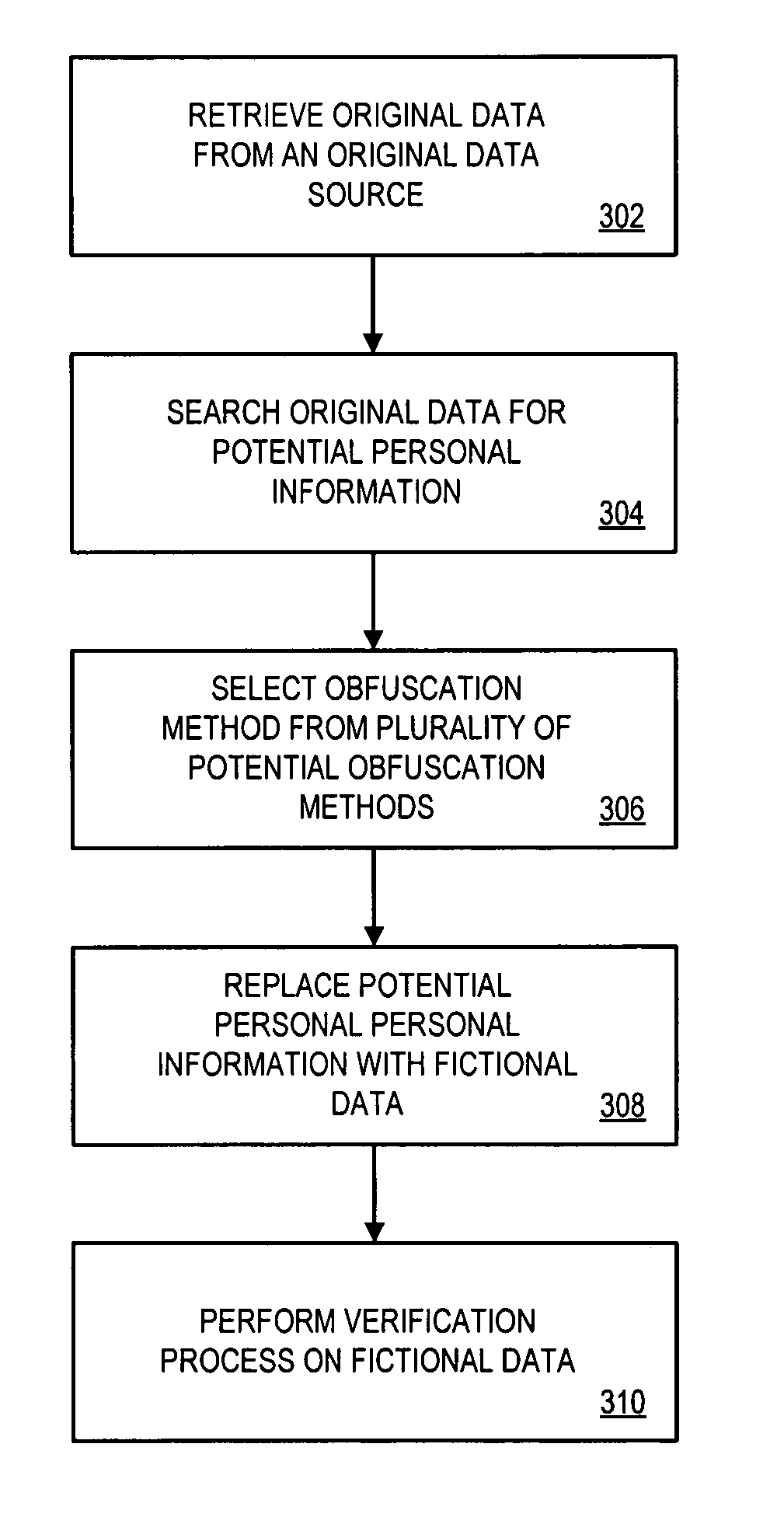
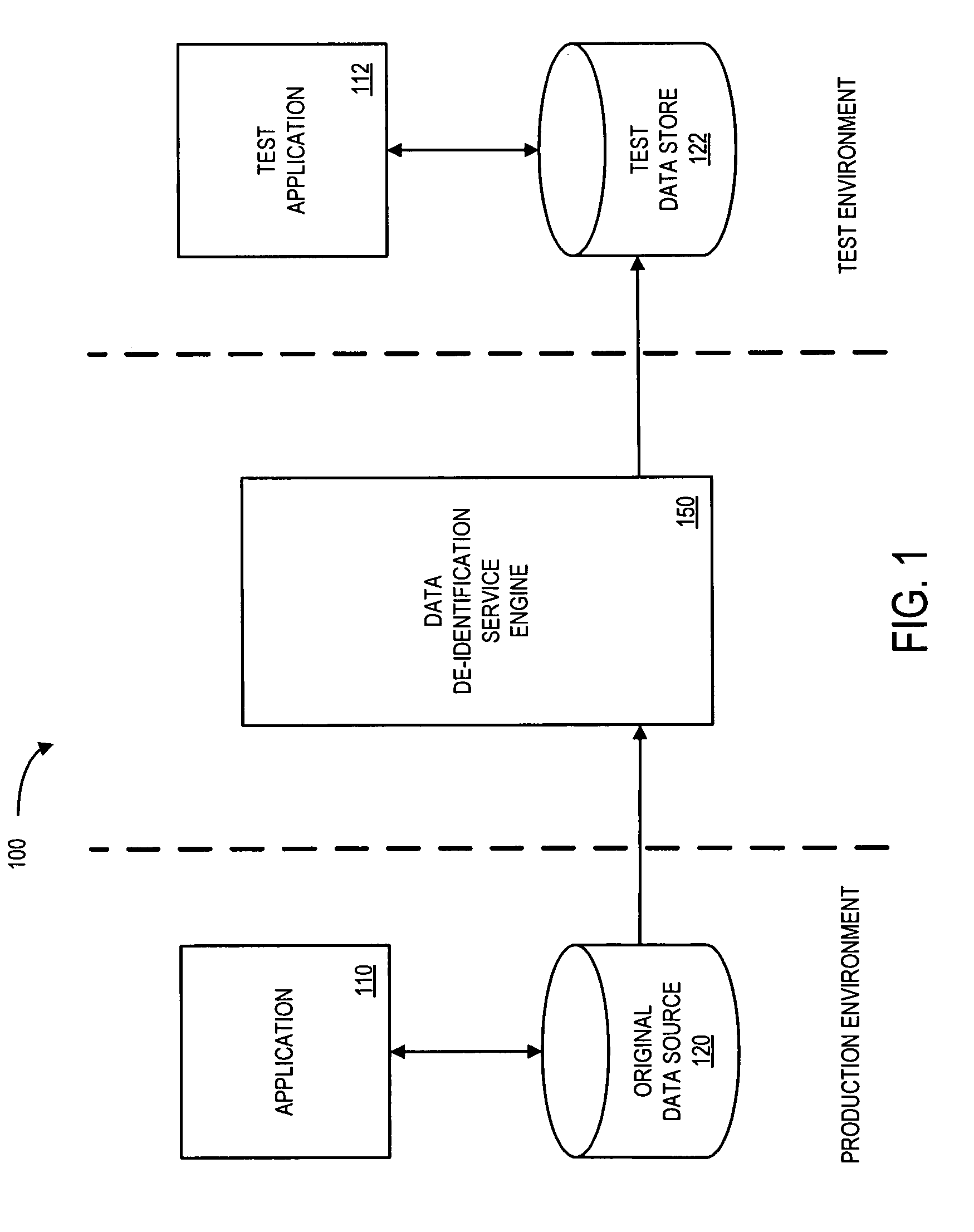
Systems and methods for de-identification of personal data
According to some embodiments, original data is retrieved from an original data source. The original data may be automatically searched for potential personal information, such as a person's name, address, or Social Security number. An obfuscation method may be selected from a plurality of potential obfuscation methods. The potential personal information in the original data may then be automatically replaced with fictional data in accordance with the selected obfuscation method.
Owner:HARTFORD FIRE INSURANCE
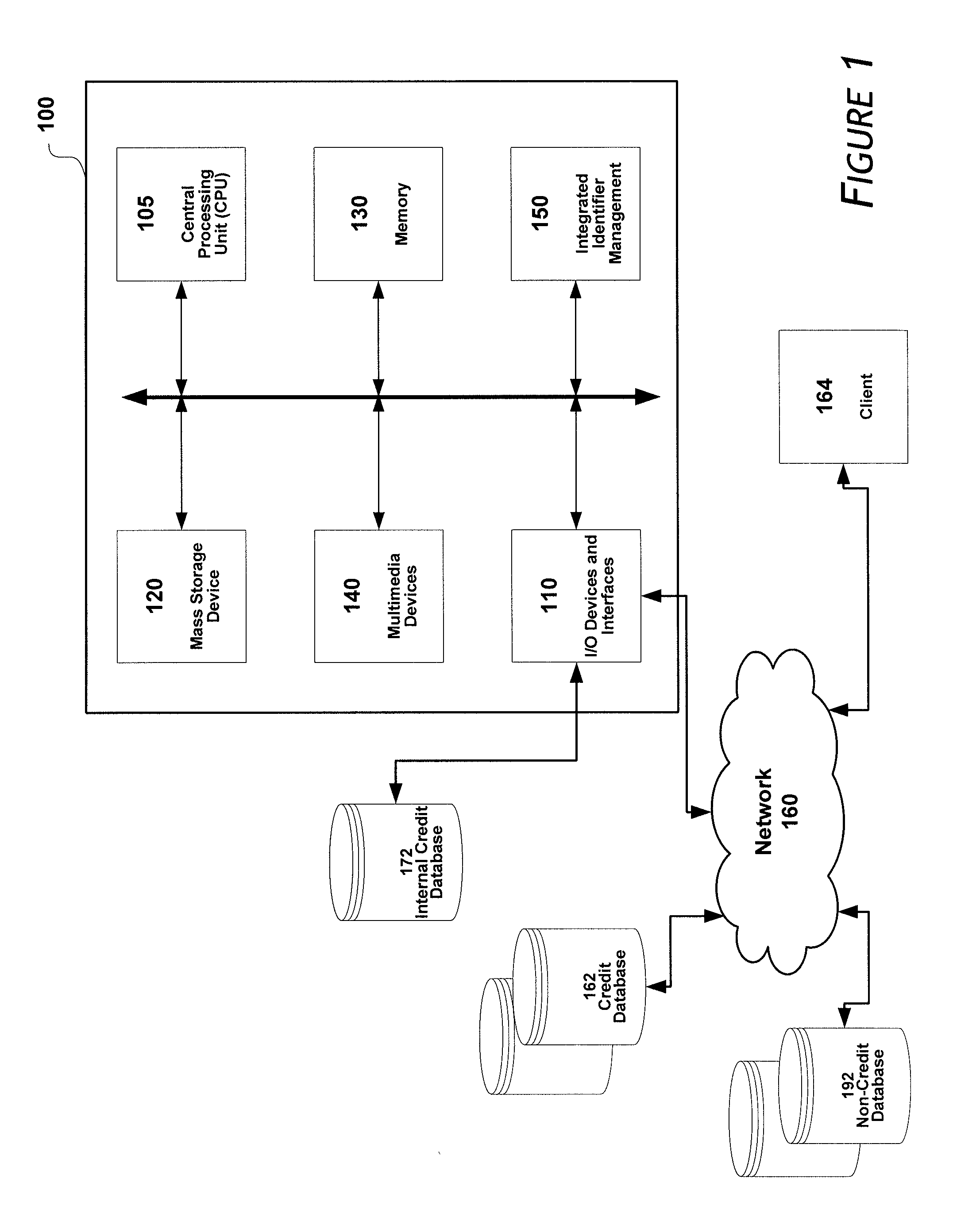
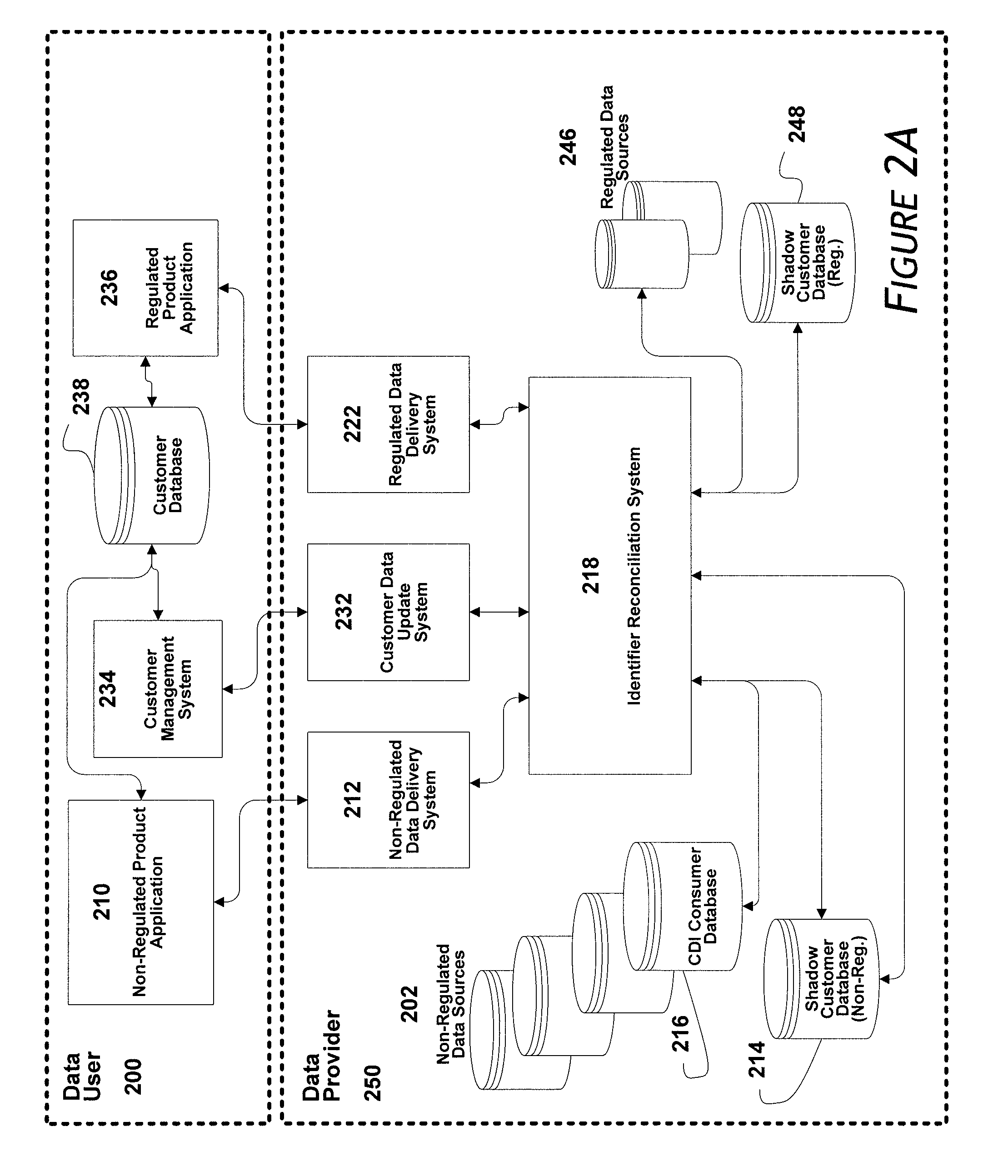
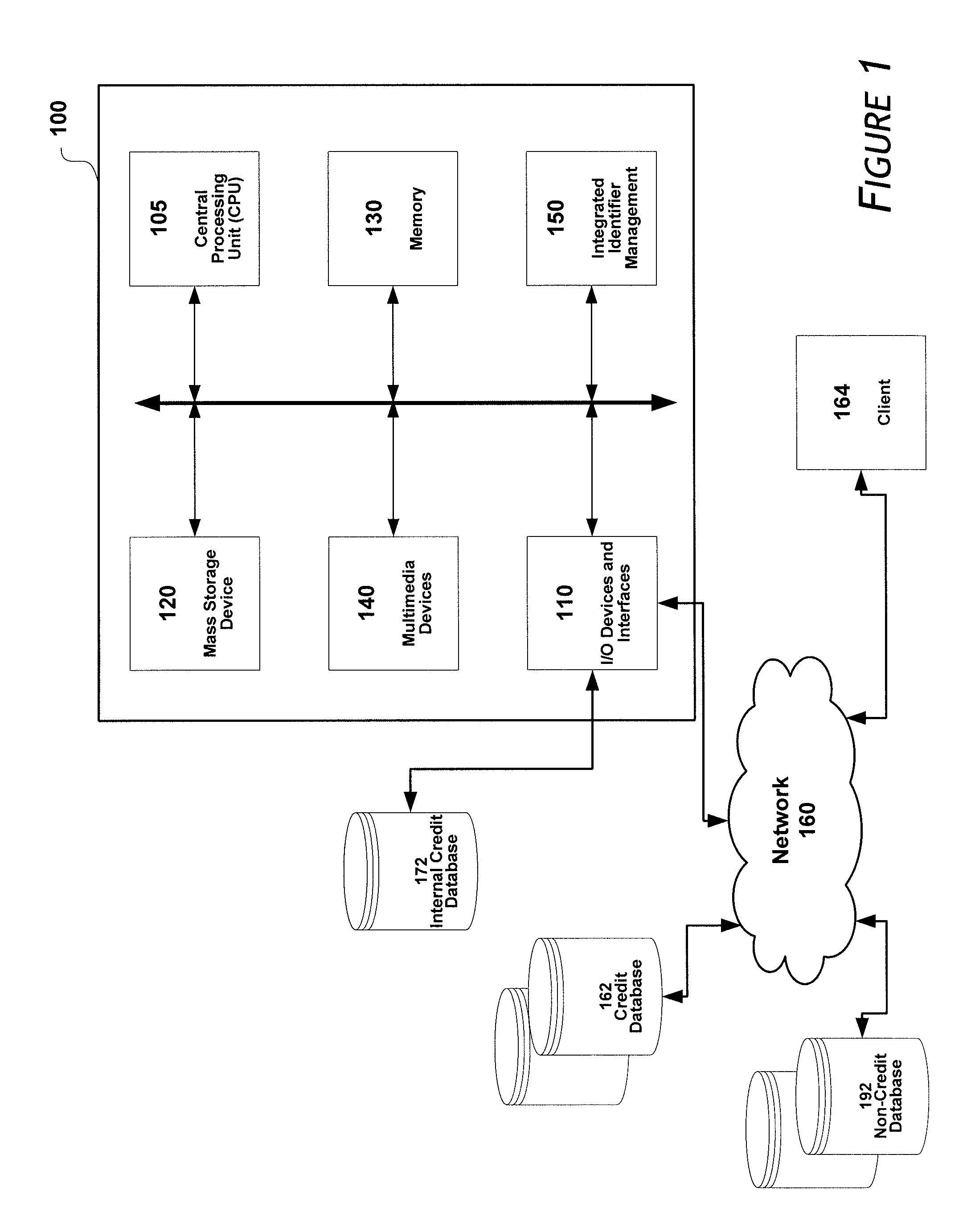
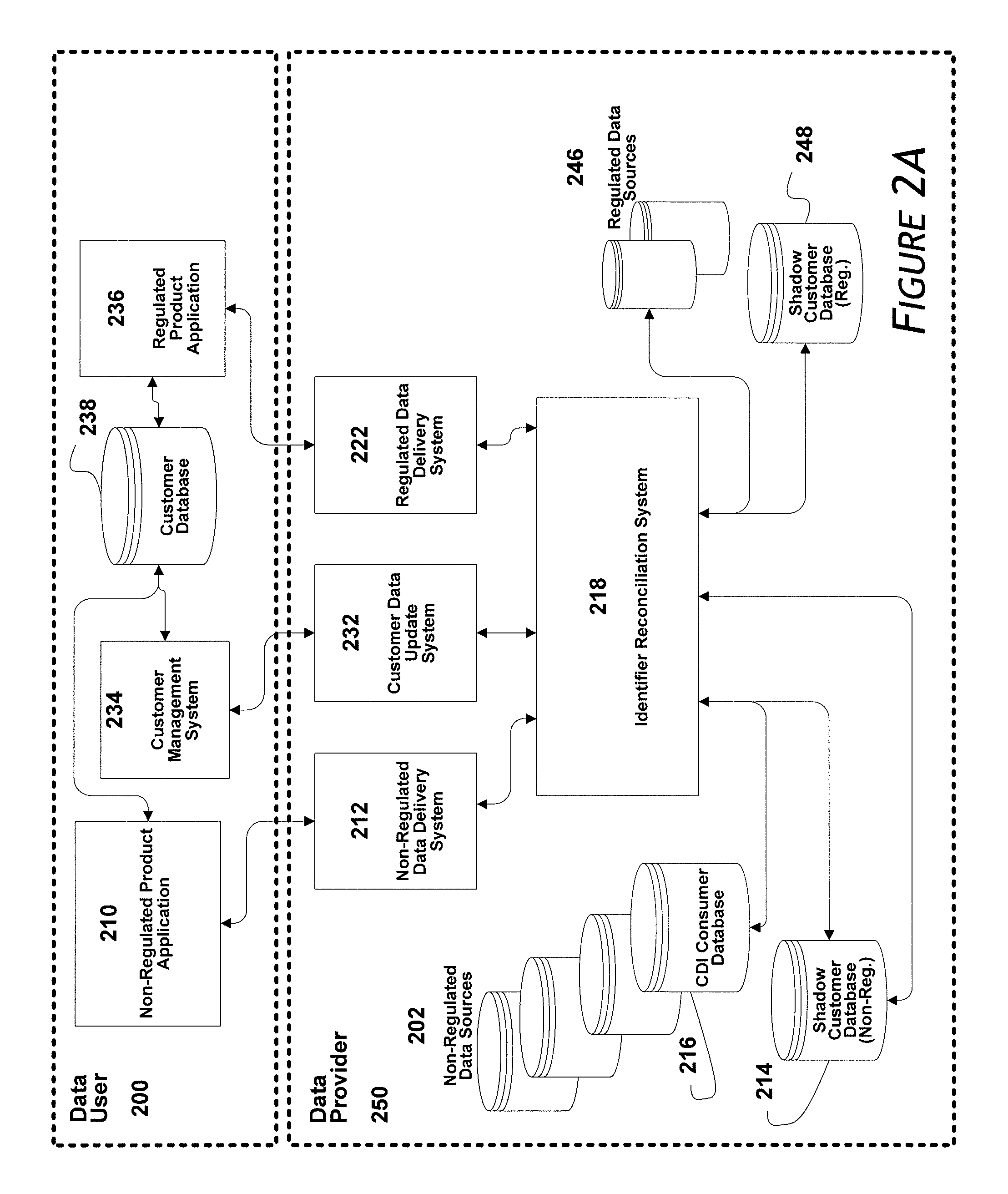
Systems and methods for providing an integrated identifier
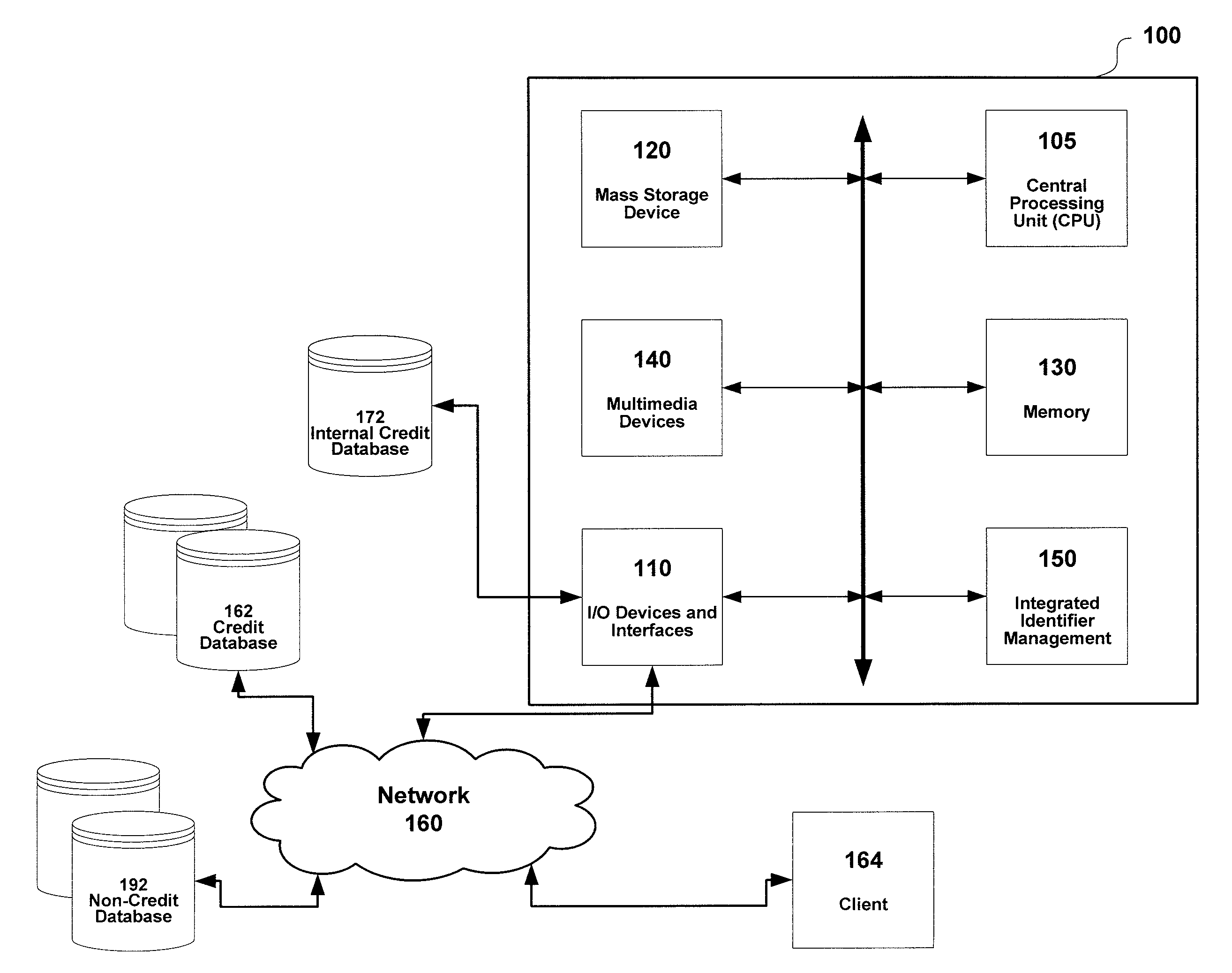
ActiveUS8312033B1Reduce eliminateDigital data processing detailsRelational databasesSocial Security numberInternet privacy
Owner:EXPERIAN MARKETING SOLUTIONS
Information card
ActiveUS20050211784A1Facilitate easy recognitionEasy and efficientRecord carriers used with machinesSpecial data processing applicationsInformation CardBank account
An information card and method of use in connection with external devices and networks is provided. One method embodiment includes storing a variety of user information including a social security number, a driver license record, and a bank account record in a memory on the card. The method further includes selectably communicating the variety of user information in a manner detectable external to the card. And, the method includes selectably updating the variety of user information stored on the card based on user input.
Owner:HEWLETT PACKARD DEV CO LP
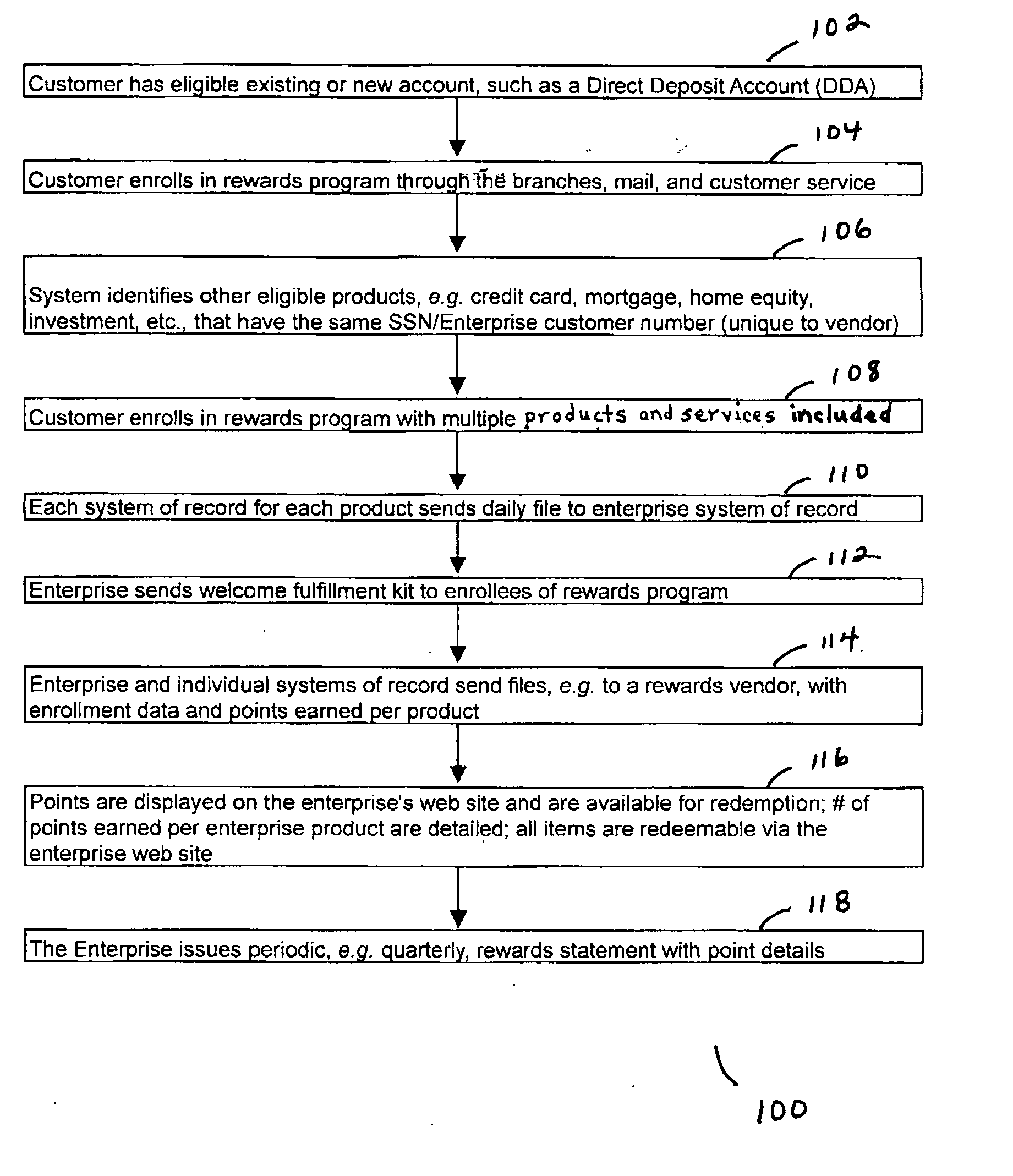
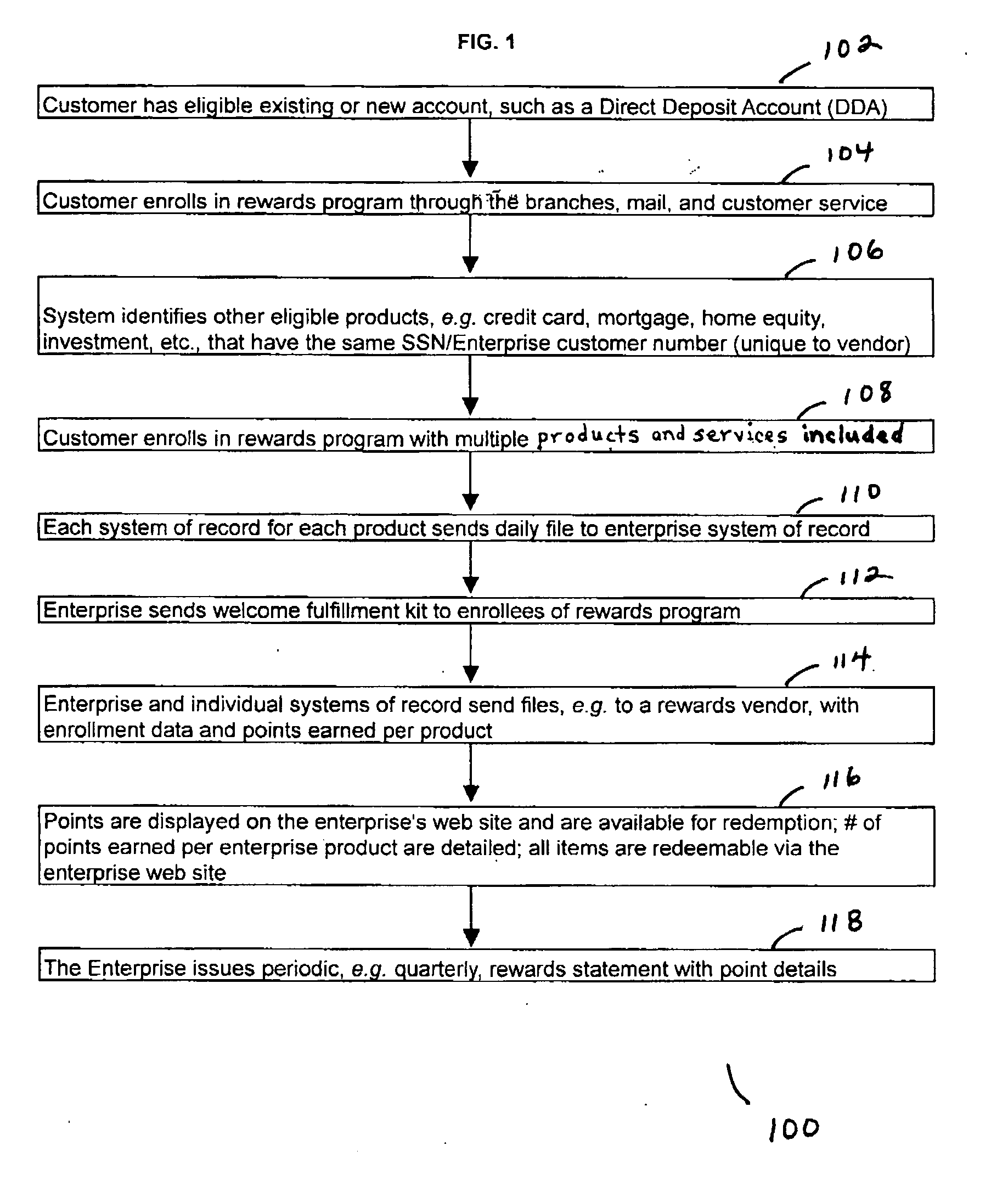
Combined rewards system and process
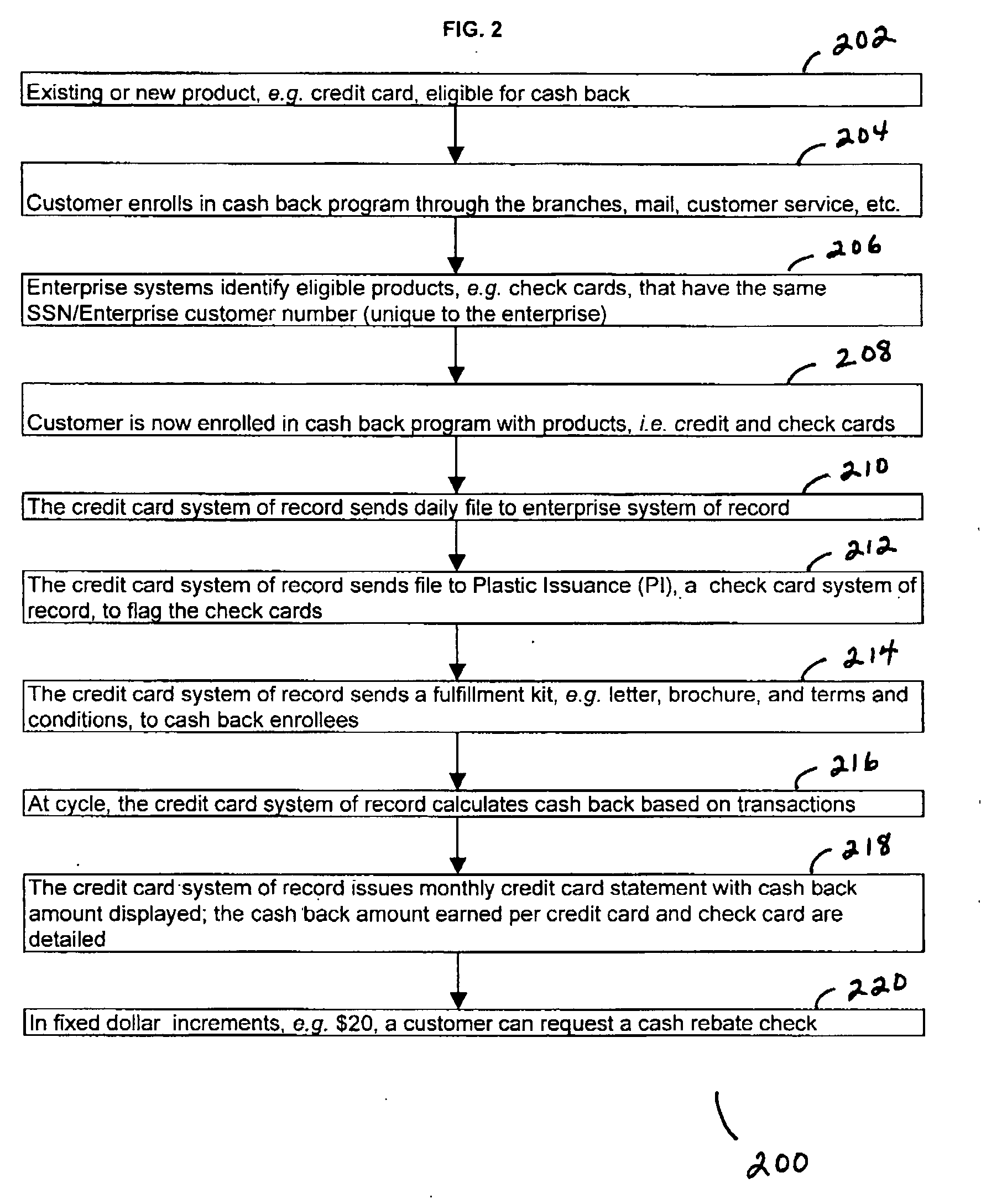
A system and process that awards rewards currency, e.g. cash back rebate or rewards points, for credit card and check card purchases and that provides rewards for a customer's enterprise relationship is provided. Further provided is a methodology for enrollment into the combined rewards program or the relationship rewards program. Further provided is a methodology to show total combined points or cash earned where the points or amount of cash earned are parsed into the various accounts and purchases. Further provided is a methodology to communicate the currency earned by providing customers with periodic statements and newsletters, data online, and data through customer service representatives. Further provided is a mechanism by which to systematically enroll eligible products or services as defined by the enterprise, e.g. where the eligibility may be based on social security numbers or other unique customer numbers.
Owner:WELLS FARGO BANK NA
Methods and apparatus for recovering keys
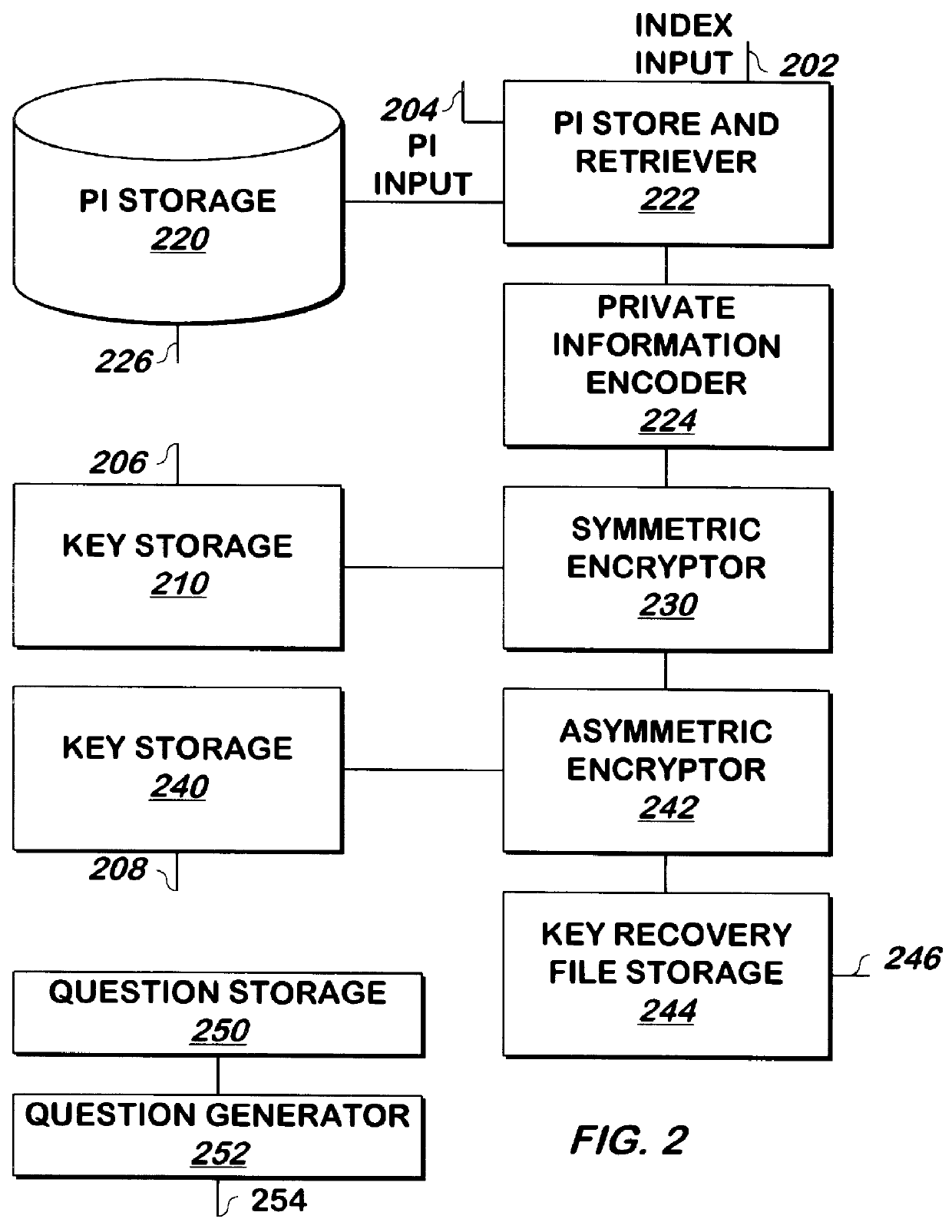
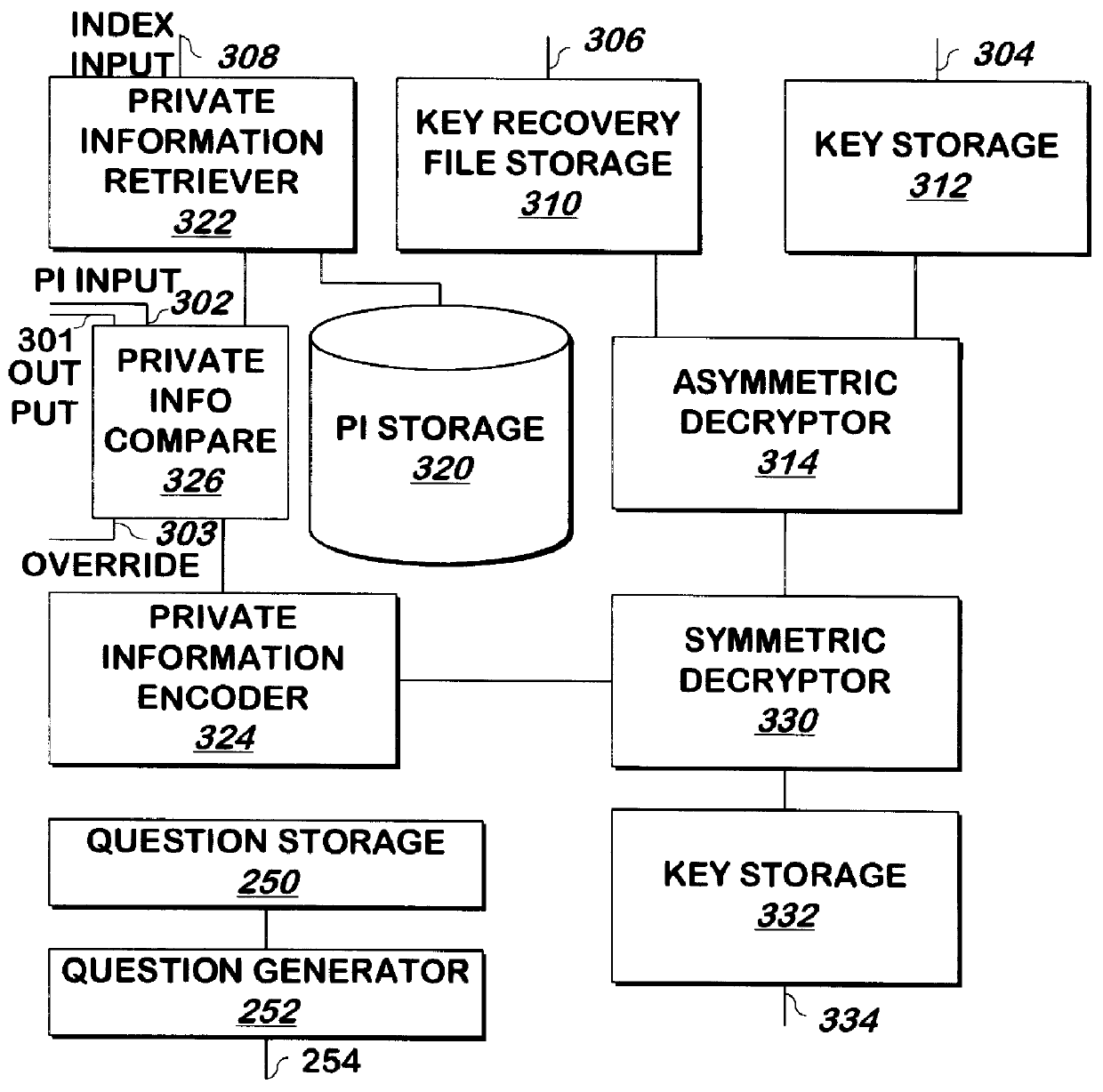
A key such as a private key or key password of a private key is encrypted for storage, and may be decrypted if the private key becomes lost or unavailable. The key is encrypted by encoding, for example, by hashing, private information such as mother's maiden name and social security number, and the result is used as a key to encrypt the private key using DES or another symmetric encryption technique. The encrypted key is again encrypted, for example using asymmetric encryption, using the public key of a trusted party such as the certificate authority that generated the private key. The result may be stored as a key recovery file by the principal of the private key or another party. To decrypt the key recovery file, the private key corresponding to the public key used to encrypt the key recovery file is used to decrypt the key recovery file, for example by asymmetric decryption. The result is symmetrically decrypted using a key obtained by encoding, for example, by hashing, the private information in the same manner as was used to encrypt the key. The result of this decryption is the key.
Owner:ORACLE INT CORP
System and method for distributed tokenization using several substitution steps
ActiveUS20110213807A1Reduce disadvantagesReduce problemsAcutation objectsDigital data processing detailsCredit cardSocial Security number
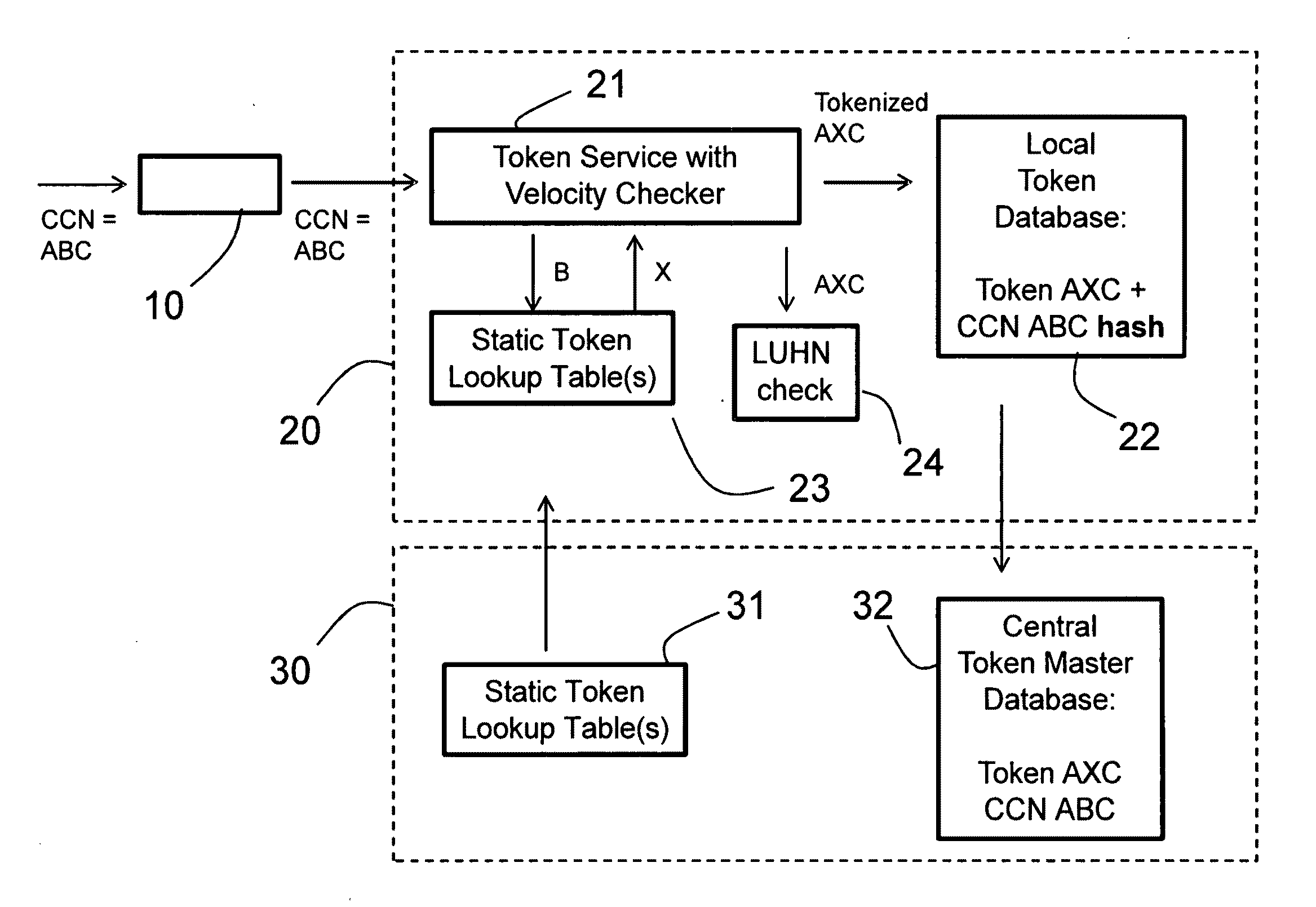
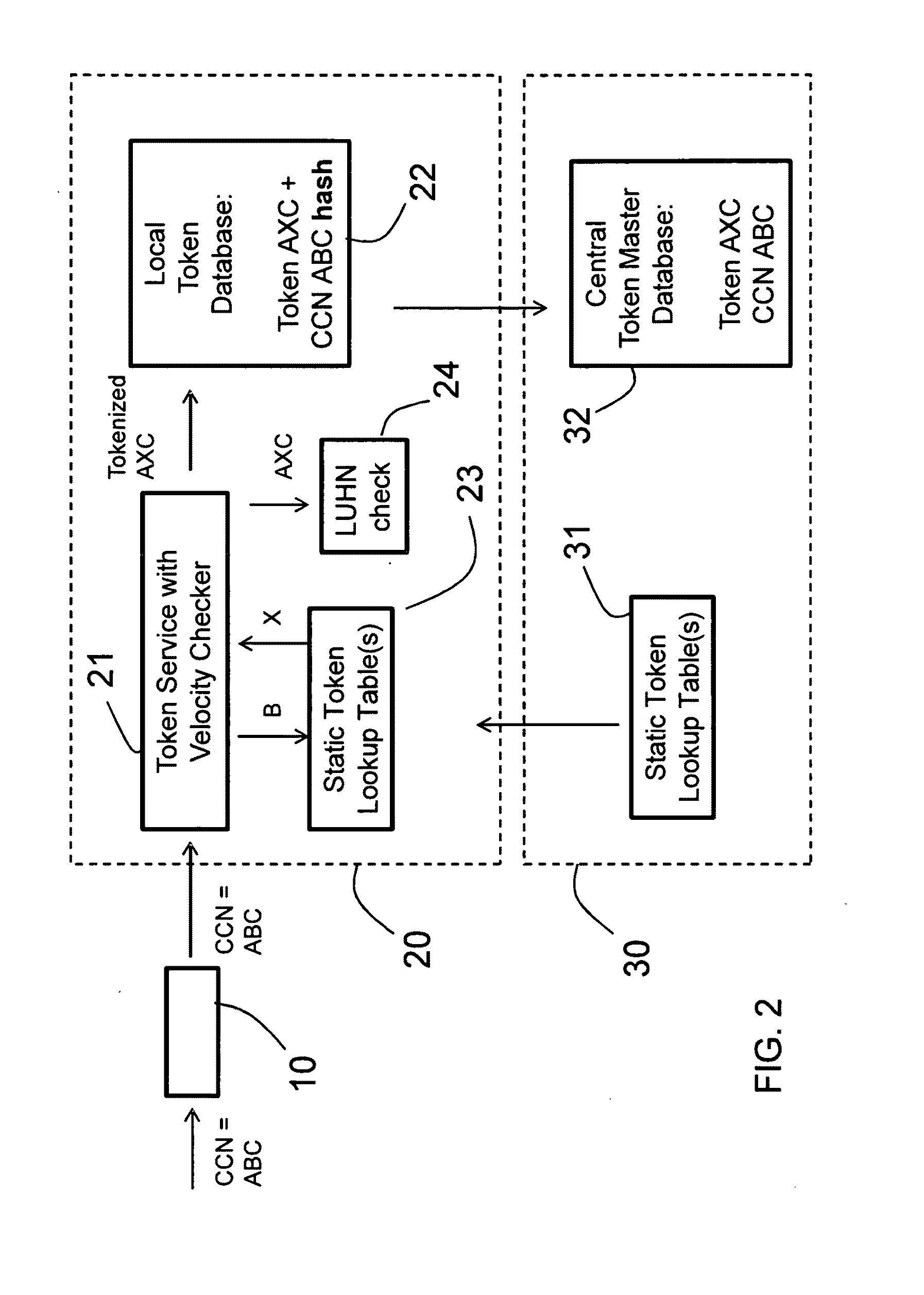
A method for distributed tokenization of sensitive strings of characters, such as social security numbers, credit card numbers and the like, in a local server is disclosed. The method comprises the steps of receiving from a central server at least one, and preferably at least two, static token lookup tables, and receiving a sensitive string of characters. In a first tokenization step, a first substring of characters is substituted with a corresponding first token from the token lookup table(s) to form a first tokenized string of characters, wherein the first substring of characters is a substring of the sensitive string of characters. Thereafter, in a second step of tokenization, a second substring of characters is substituted with a corresponding second token from the token lookup table(s) to form a second tokenized string of characters, wherein the second substring of characters is a substring of the first tokenized string of characters. Optionally, one or more additional tokenization steps is / are used.
Owner:PROTEGRITY CORP
Systems and methods for providing an integrated identifier
ActiveUS8954459B1Reduce eliminateDigital data processing detailsDigital computer detailsSocial Security numberInternet privacy
Owner:EXPERIAN MARKETING SOLUTIONS
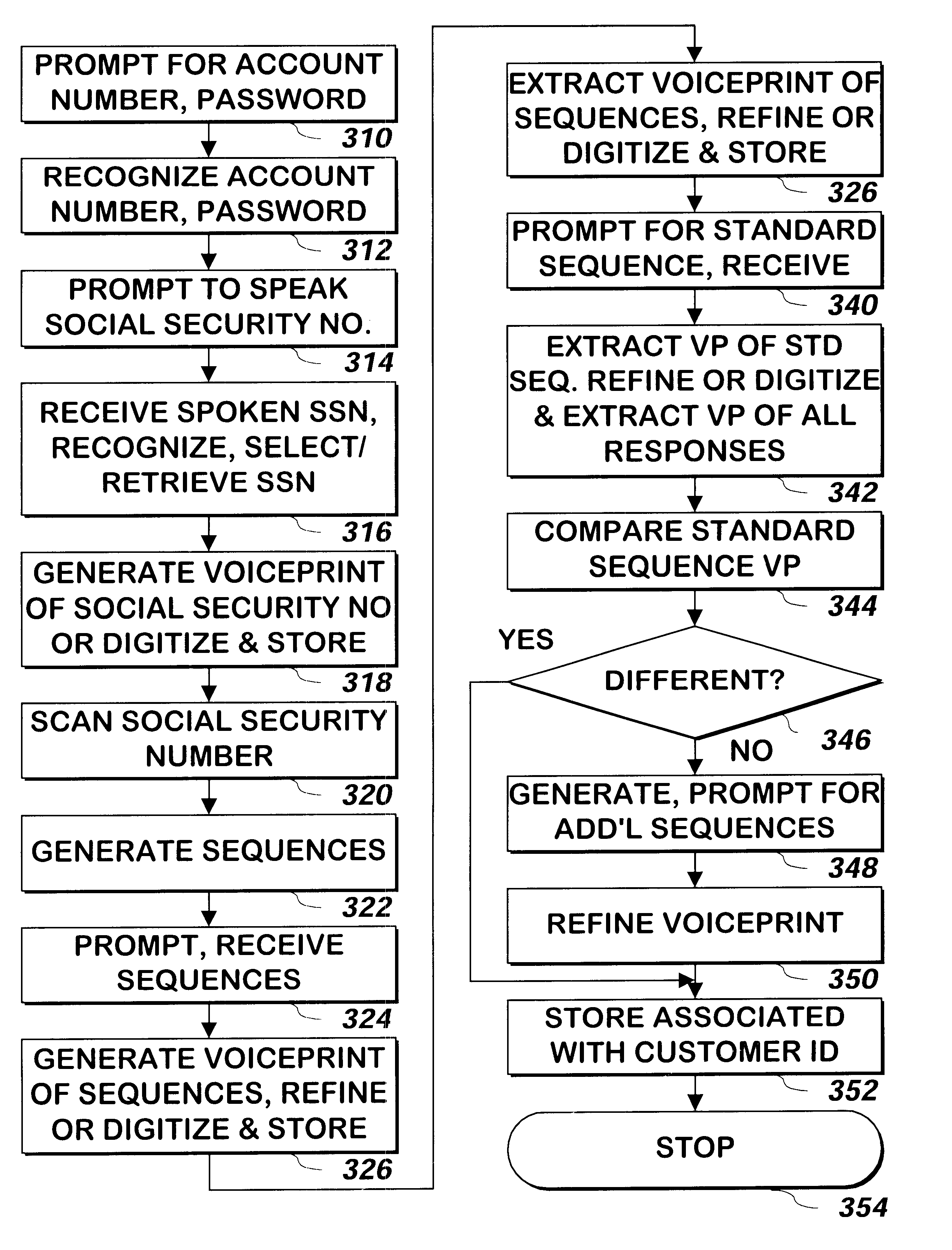
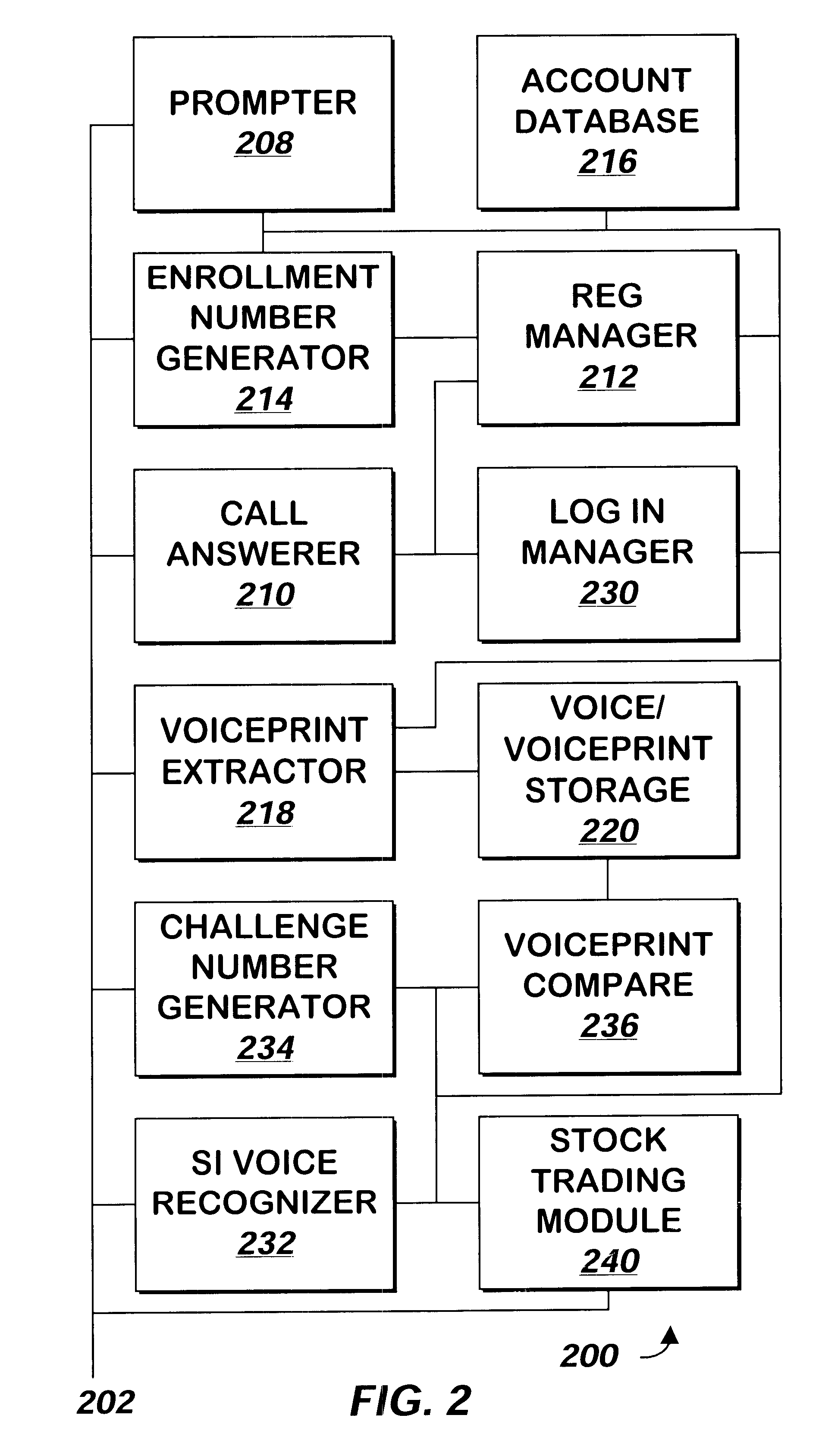
Method and apparatus for enrolling a user for voice recognition
InactiveUS6681205B1Secure and accurate verificationSpeech recognitionSocial Security numberSpeech identification
A method and apparatus enrolls a user for voice recognition by prompting the user to speak a social security number or other number. A voiceprint is extracted from the social security number. Additional sequences of numbers are generated so that the total number of times each decimal digit appears in the social security number or the additional sequences meets or exceeds a threshold value. The user is then prompted to speak the additional sequences and the voiceprint extracted from the social security number is refined to include the additional information received from the responses to the prompts for the sequences. A standard sequence may also be prompted and a voiceprint of the standard sequence compared with the voiceprints of other users speaking the same standard sequence to identify the level of differentiation between the user's voice and other user's voices. If the comparison determines the level of differentiation is low, the user may be prompted to speak his or her social security number again and / or the same or additional sequences and the user's voiceprint further refined from these additional responses.
Owner:CHARLES SCHWAB & CO INC
System and Method for Limiting Mobile Device Functionality.
ActiveUS20080233919A1Reduce harmPrevent unauthorized accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCredit cardInternet privacy
The present invention relates to systems and methods that employ various mechanisms to selectively disable mobile device functionality. In general, mobile devices can be utilized to store personal and / or highly sensitive information such as bank account numbers, social security numbers, credit card numbers and the like. If the mobile device is lost or stolen, data stored within the device can be accessed by an unauthorized user; and, thus, any personal and / or highly sensitive information can be obtained. In order to mitigate unauthorized access, the subject invention provides a disabling component that communicates with the lost or stolen device to render data stored thereon inaccessible. Further, the data can be stored in local or remote locations to backup stored information, thereby creating a more robust and reliable method of storing information important to the device owner. These features provide enhancements over conventional mobile device security techniques.
Owner:NOKIA TECH OY
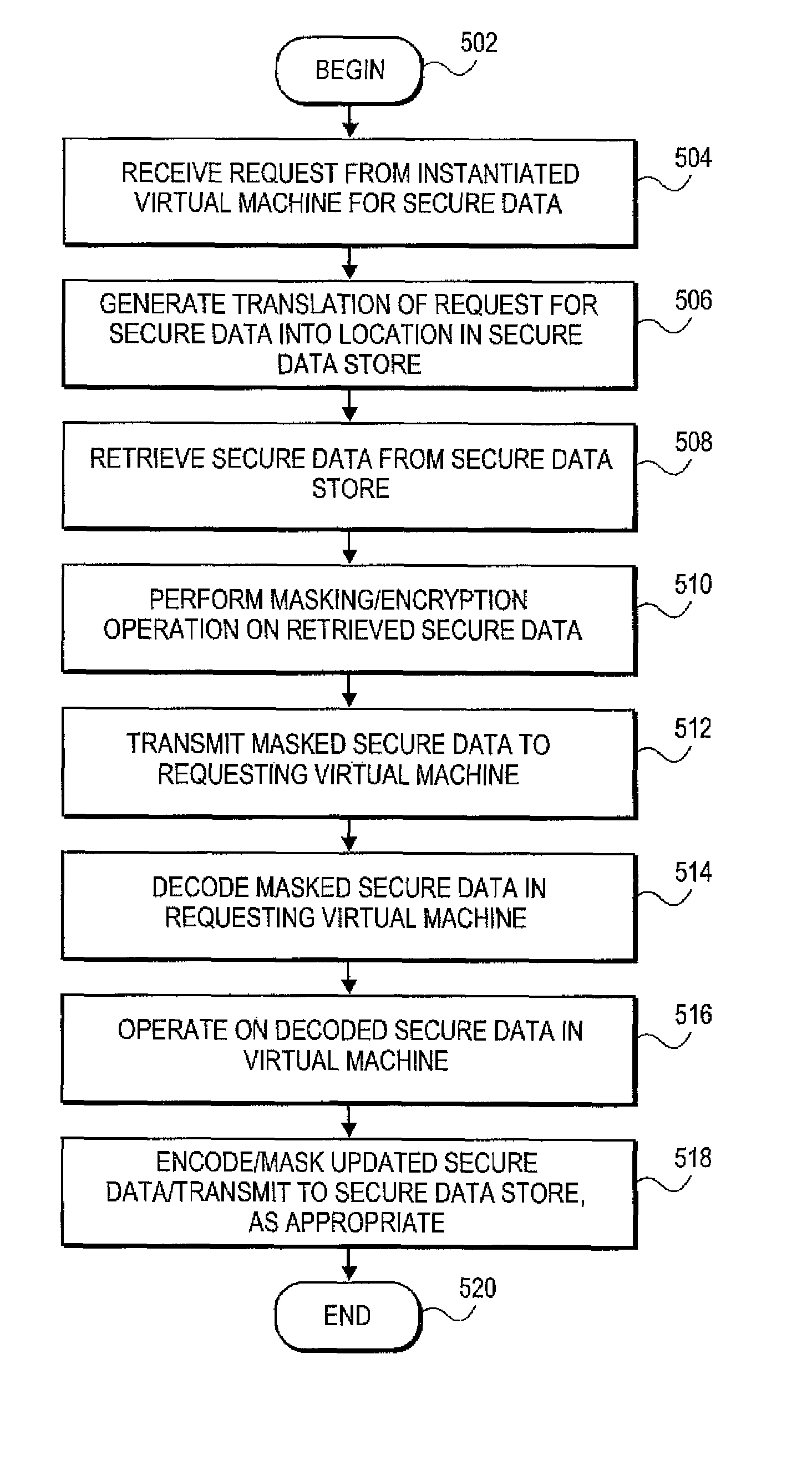
Systems and methods for management of secure data in cloud-based network
ActiveUS8108912B2Digital data processing detailsUser identity/authority verificationCloud baseSocial Security number
Embodiments relate to systems and methods for the management of secure data in a cloud-based network. A secure data store can store sensitive or confidential data, such as account numbers, social security numbers, medical or other information in an on-premise data facility. Regulatory and / or operational requirements may prohibit the migration or unprotected transmission of the secure data to the cloud. An operator can instantiate a set of virtual machines to access and process the secure data, for example to process online purchase transactions. To prevent unauthorized disclosure of the secure data, the secure data store can receive data access requests via a translation module that translates the secure data. The secure data store can retrieve and transmit the secure data using a protection mechanism such as a masking and / or encryption mechanism, avoiding the unprotected transport or exposure of that data to the cloud.
Owner:RED HAT
Deferred payment and selective funding and payments
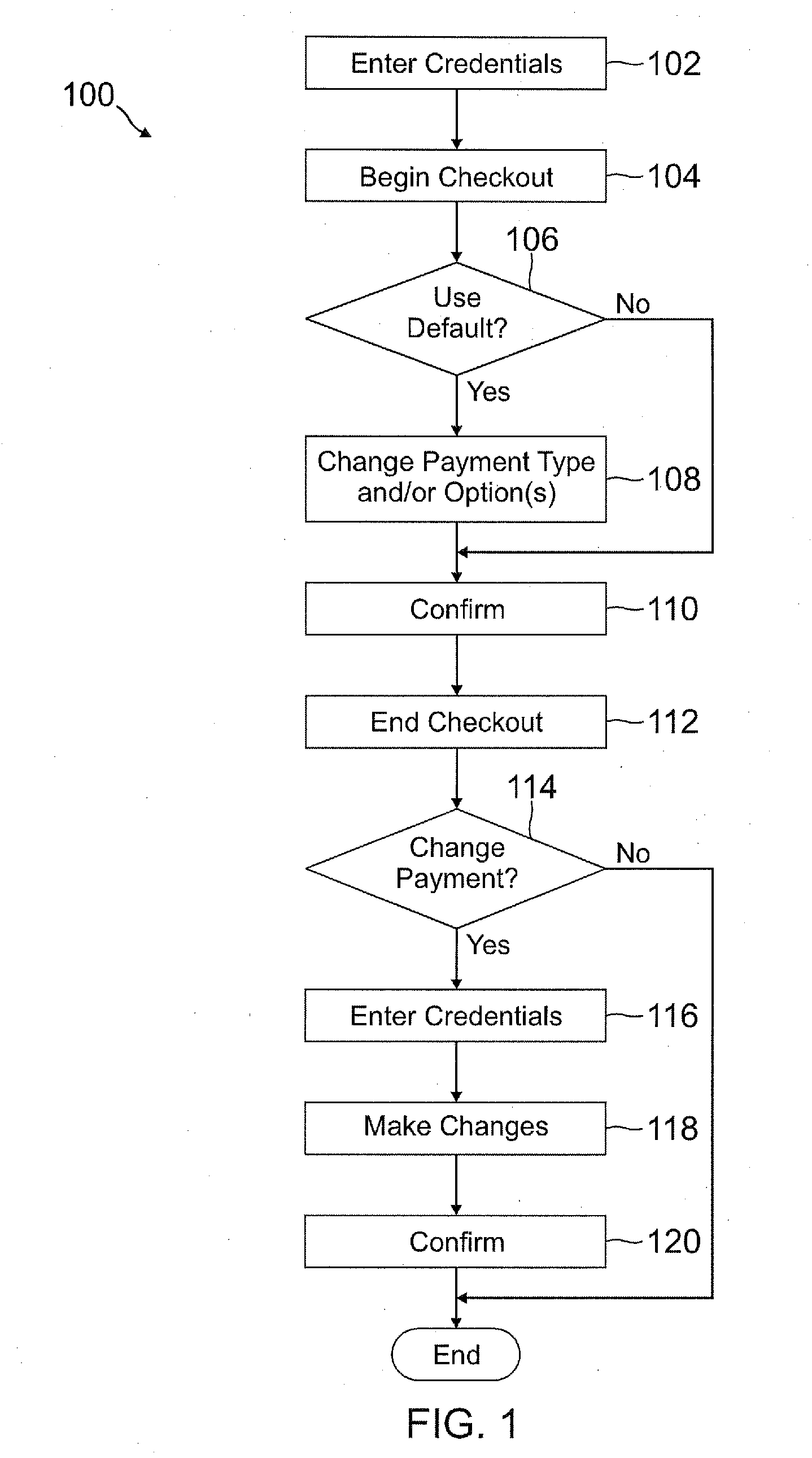
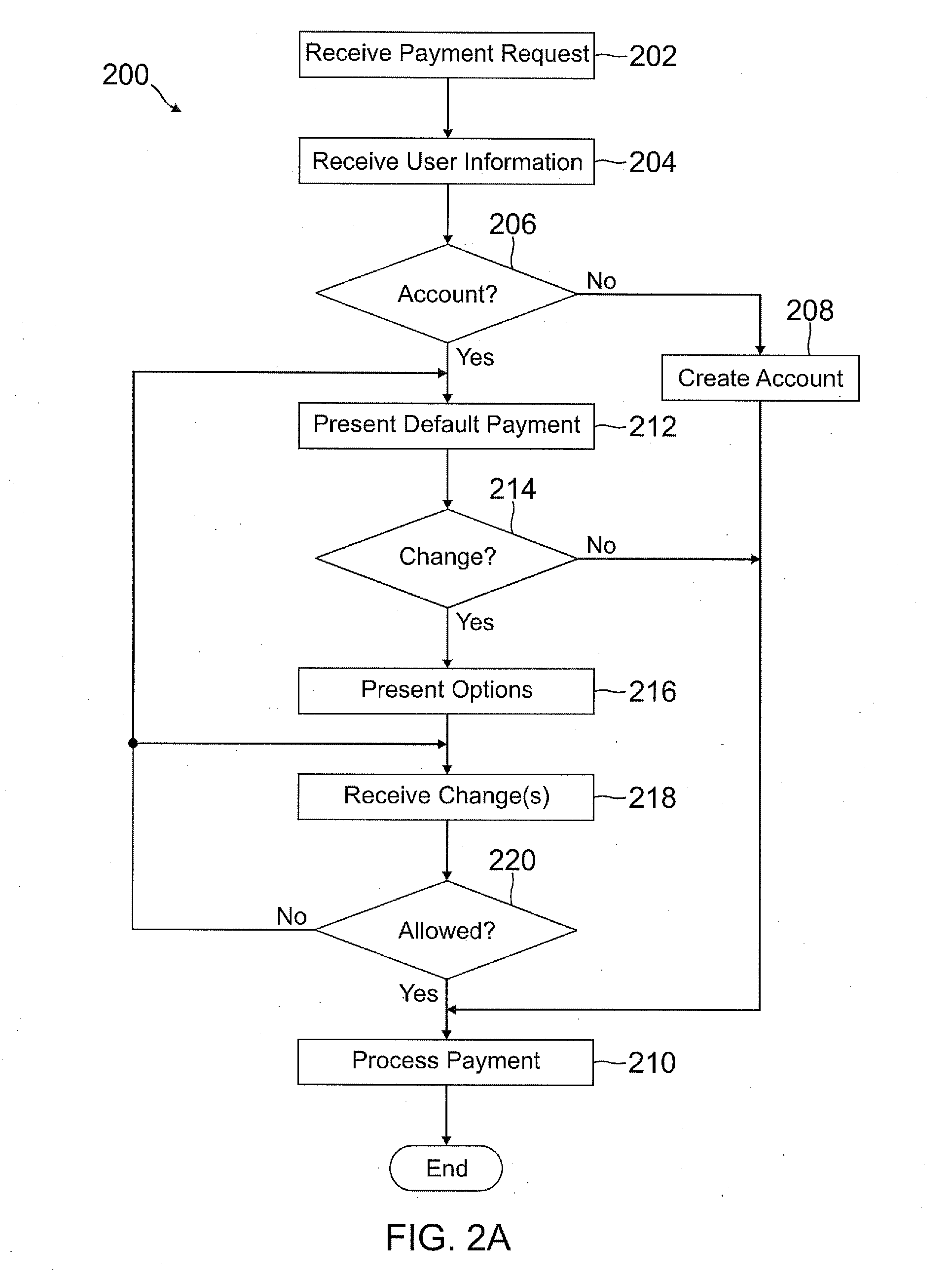
InactiveUS20120166311A1Increase flexibilityEasy to controlPayment architectureBuying/selling/leasing transactionsPaymentEmail address
A user is able to change one or more payment options after payment has already been made to a merchant. A payment provider processes a payment request during a transaction with the merchant with default or selected payment options. After the transaction with the merchant is completed and the merchant has been paid, the user may change one or more of the payment options, such as funding source(s) and terms / conditions of payment (e.g., deferment period, installment period / amount, etc.). During the transaction, the user may make a purchase through the payment provider even if the user does not have an account with the payment provider by providing user information, such as name, address, phone number, email address, and date of birth, but not a social security number or funding source information.
Owner:PAYPAL INC
Method for communicating confidential, educational information
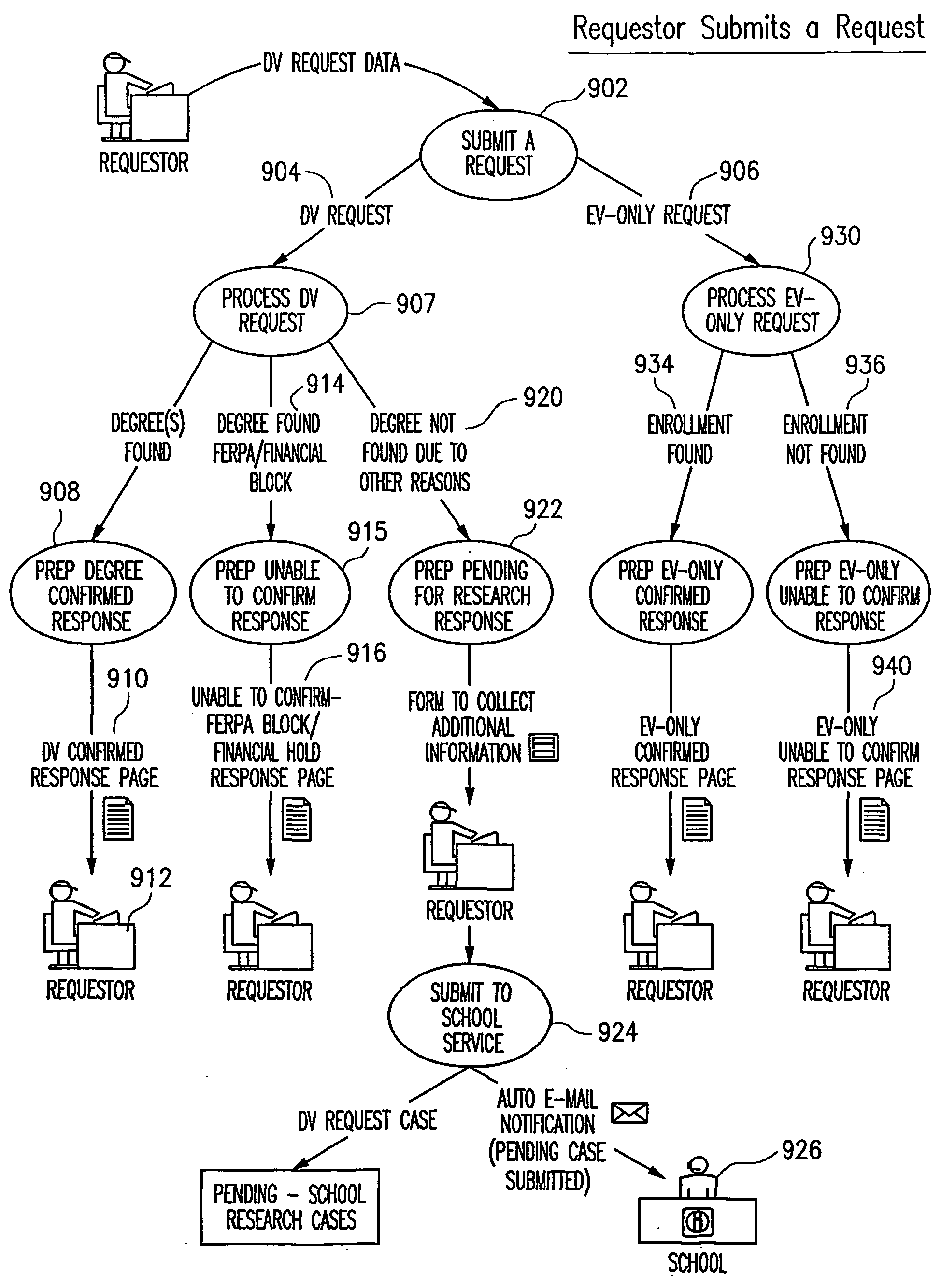
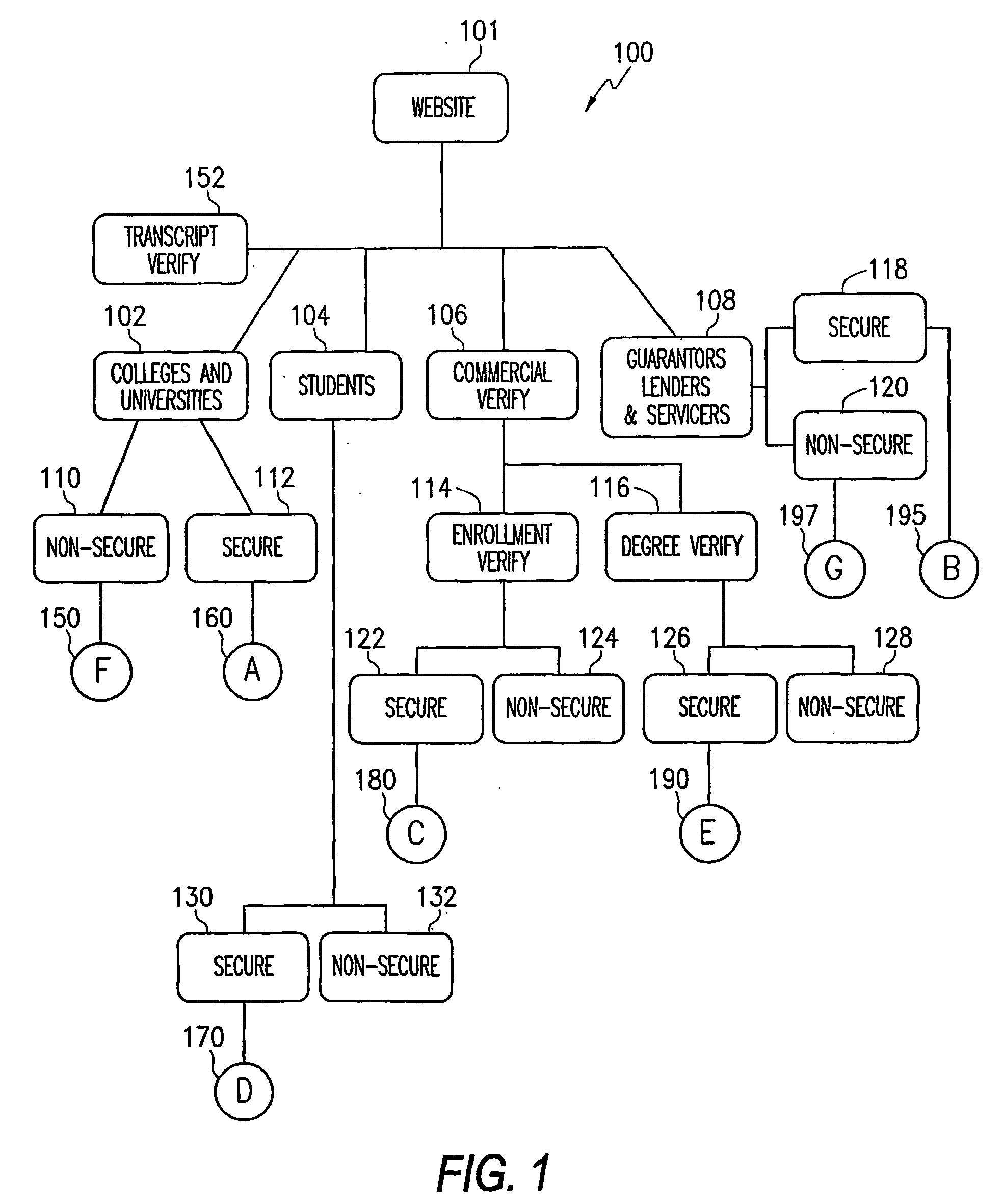
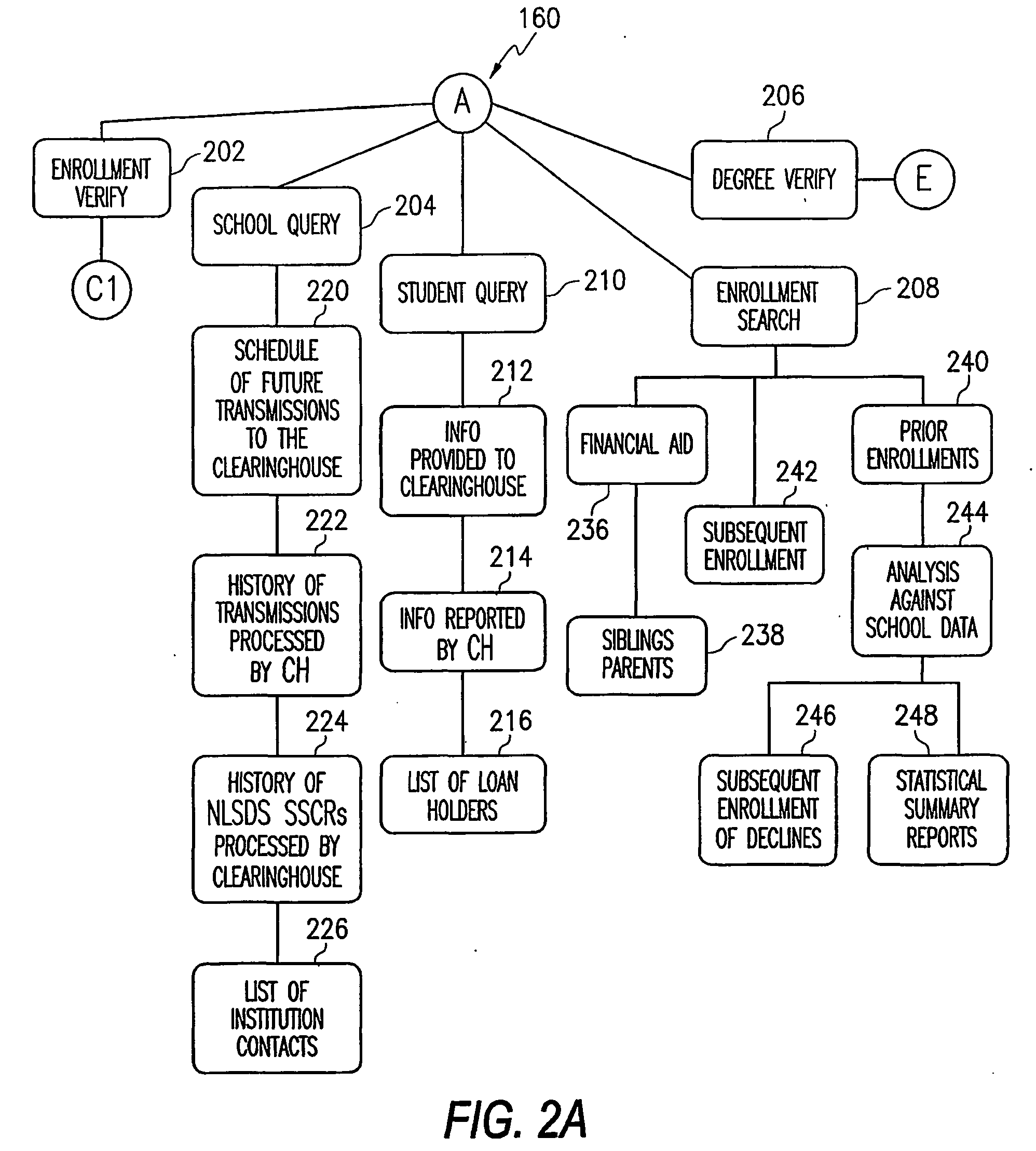
InactiveUS20080208873A1Significant burdenFraud and misrepresentation will be avoidedInterconnection arrangementsGraded-service arrangementsTrademarkSocial Security number
A method for receiving, processing, and responding to requests relating to educational degree, enrollment, transcript, and loan information via secured and non-secured channels. In a disclosed embodiment, a requestor submits an order to verify degree or enrollment information consisting of a student's first name, last name, and / or social security number. A computer at a Clearinghouse matches the order with data compiled from participating educational institutions and generates a response. Enrollment information can include both current attendance and historical information. Optionally, degree information can be maintained in a separate database. Requestors can also order up-to-date student transcripts via the Clearinghouse.
Owner:BOEHMER DANIEL R
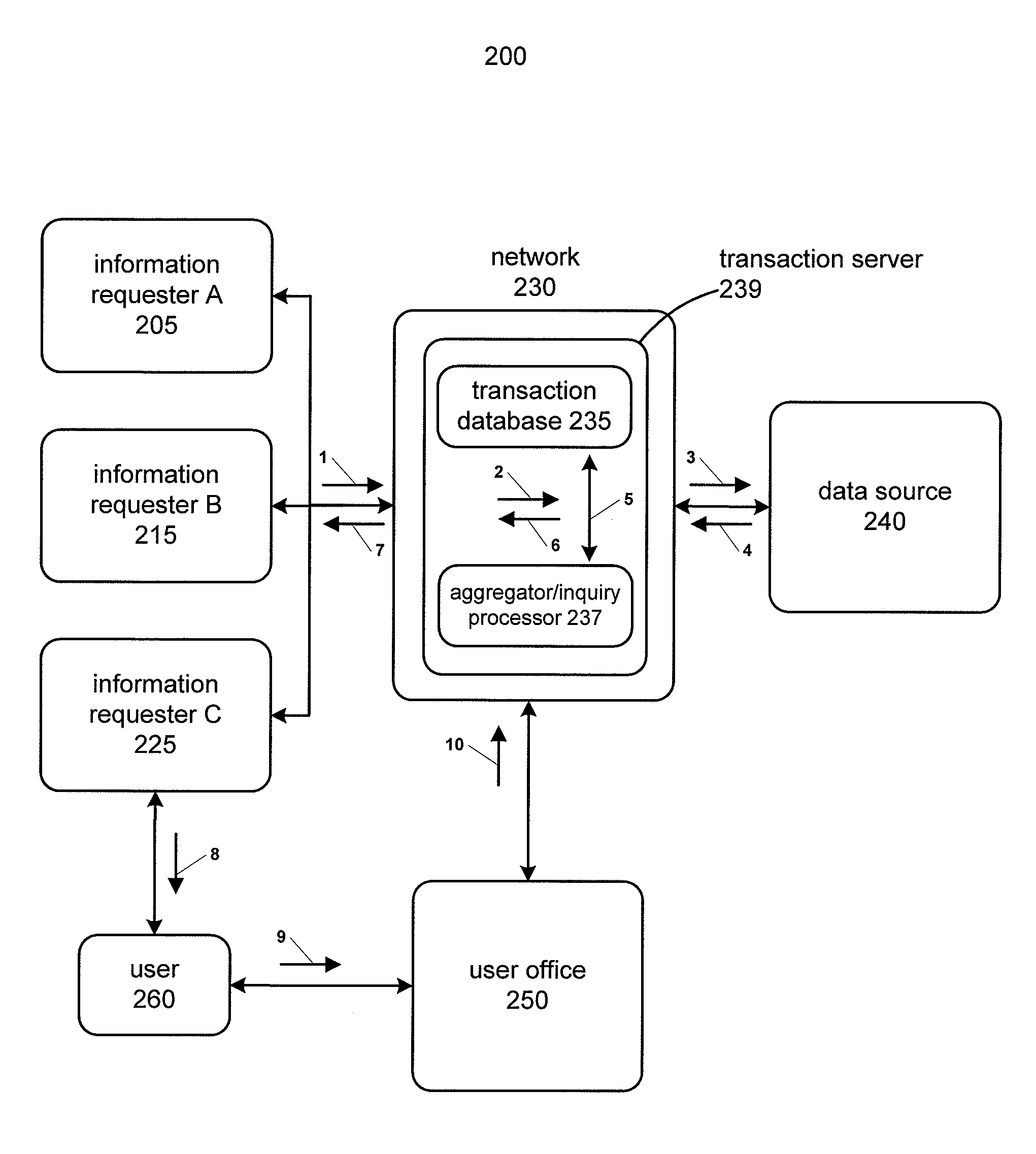
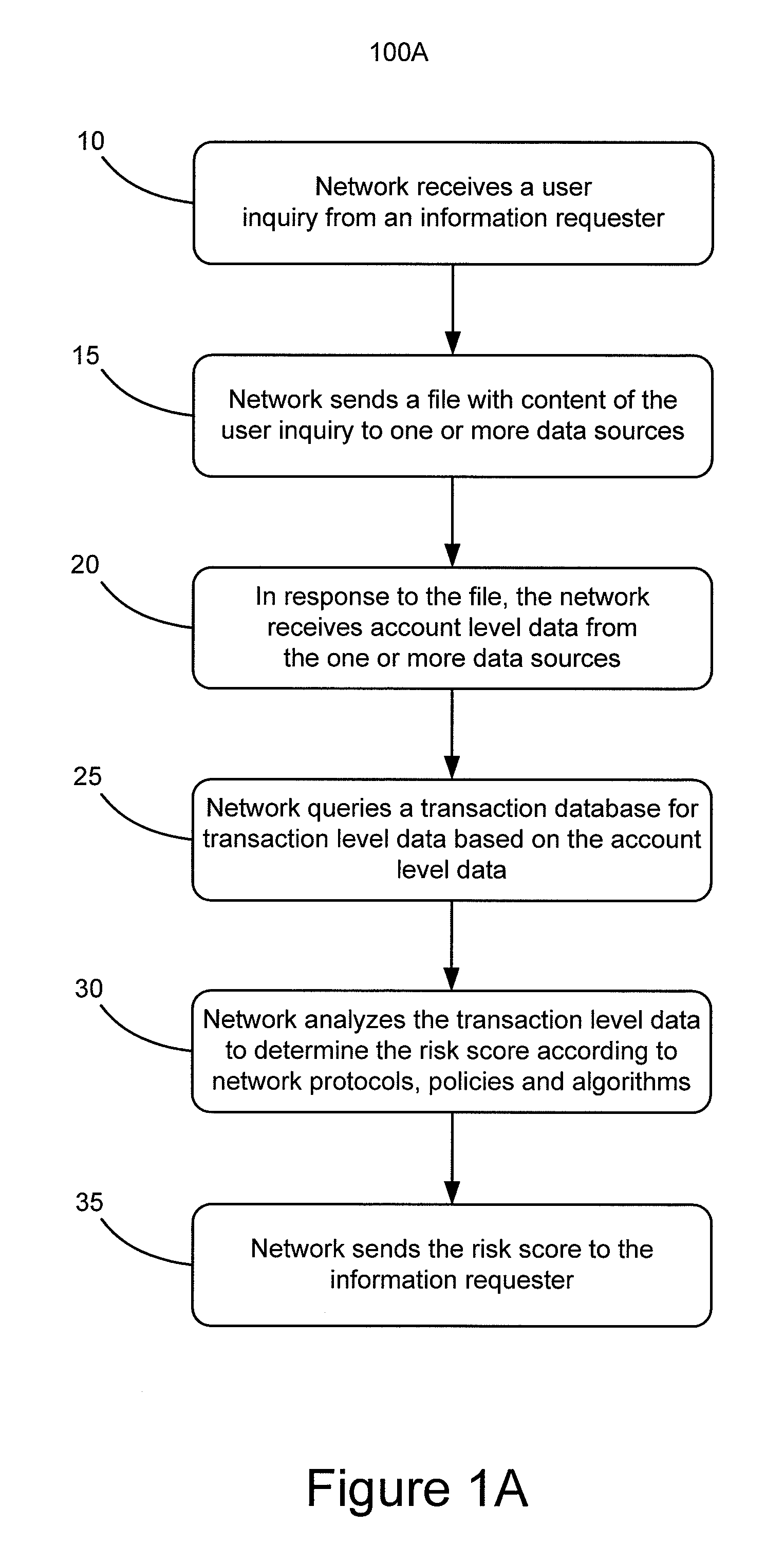
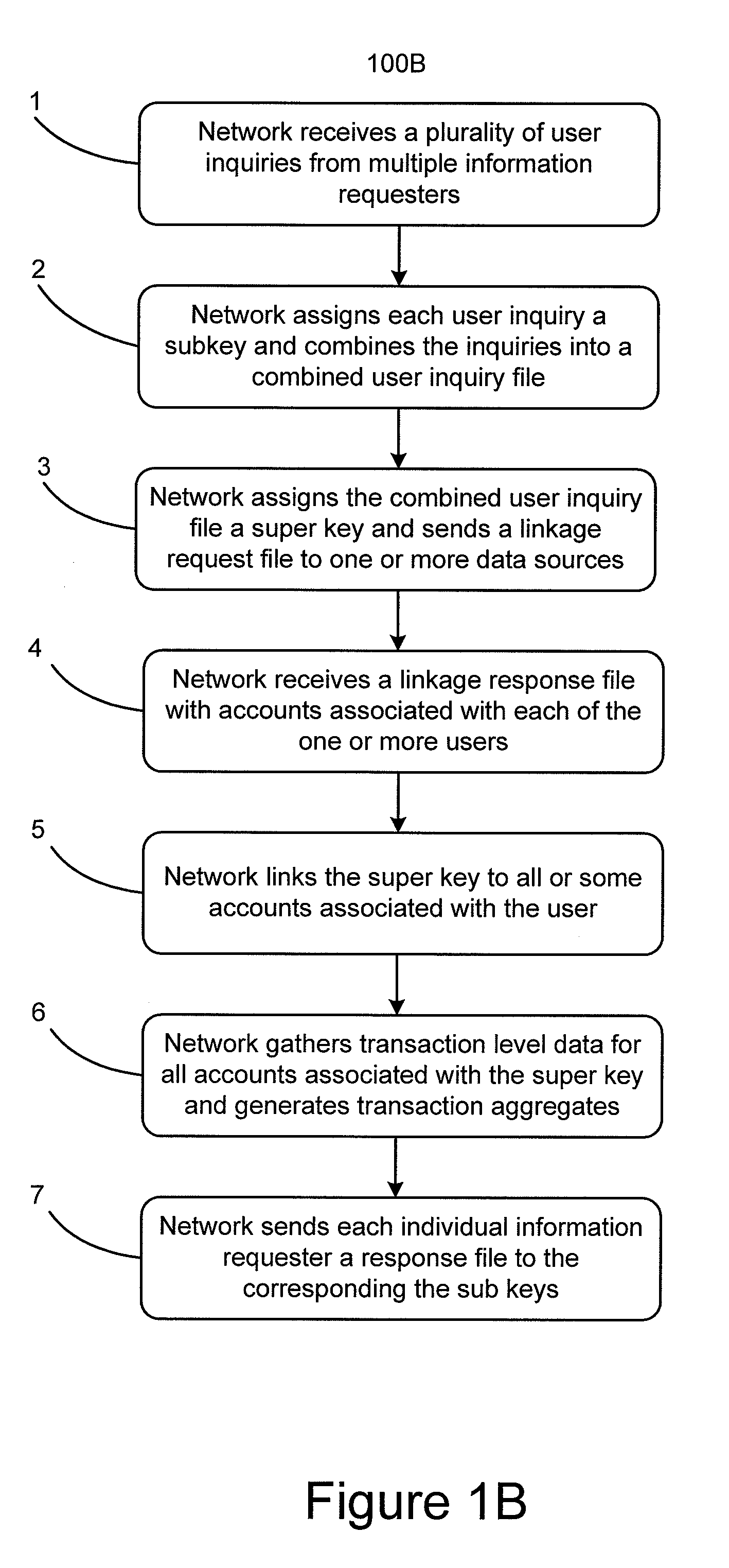
System and method using superkeys and subkeys
Systems and methods for providing aggregated transaction level data for a particular user to multiple information requesters are disclosed. Subkeys are assigned to user inquiries from multiple information requesters and a super key is assigned to those subkeys to link them to one or more user identifiers such as a username or Social Security number. Account level data is provided based on the super key and the user identifiers. Duplicate requests for aggregated transaction level data contained in the user inquiries can be deleted. User inquiry response files containing transaction level aggregate data can be sent to the information requesters based on the assigned subkeys.
Owner:VISA INT SERVICE ASSOC
Data conversion environment
ActiveUS20080301162A1Collision detectionDigital data information retrievalSpecial data processing applicationsInformation typeEmployee number
Converting data from a first format to a second format may be used to merge two databases having different formatting. Conversion maps may be defined for pairs of formats and may be used to convert data between the pair of formats. Data may further be transformed from one information type or format into another information type or format. In one example, a first format may allow storage of a social security number while a second format might not. Thus, a social security number stored in the first format may be converted to an employee number for storage in the second format. Collisions between pieces of data may be detected and managed by generating an identifier for the pieces of data (e.g., data records) and merging the pieces of data into a single piece or portion of data (e.g., a single data record) corresponding to the assigned identifier.
Owner:BANK OF AMERICA CORP
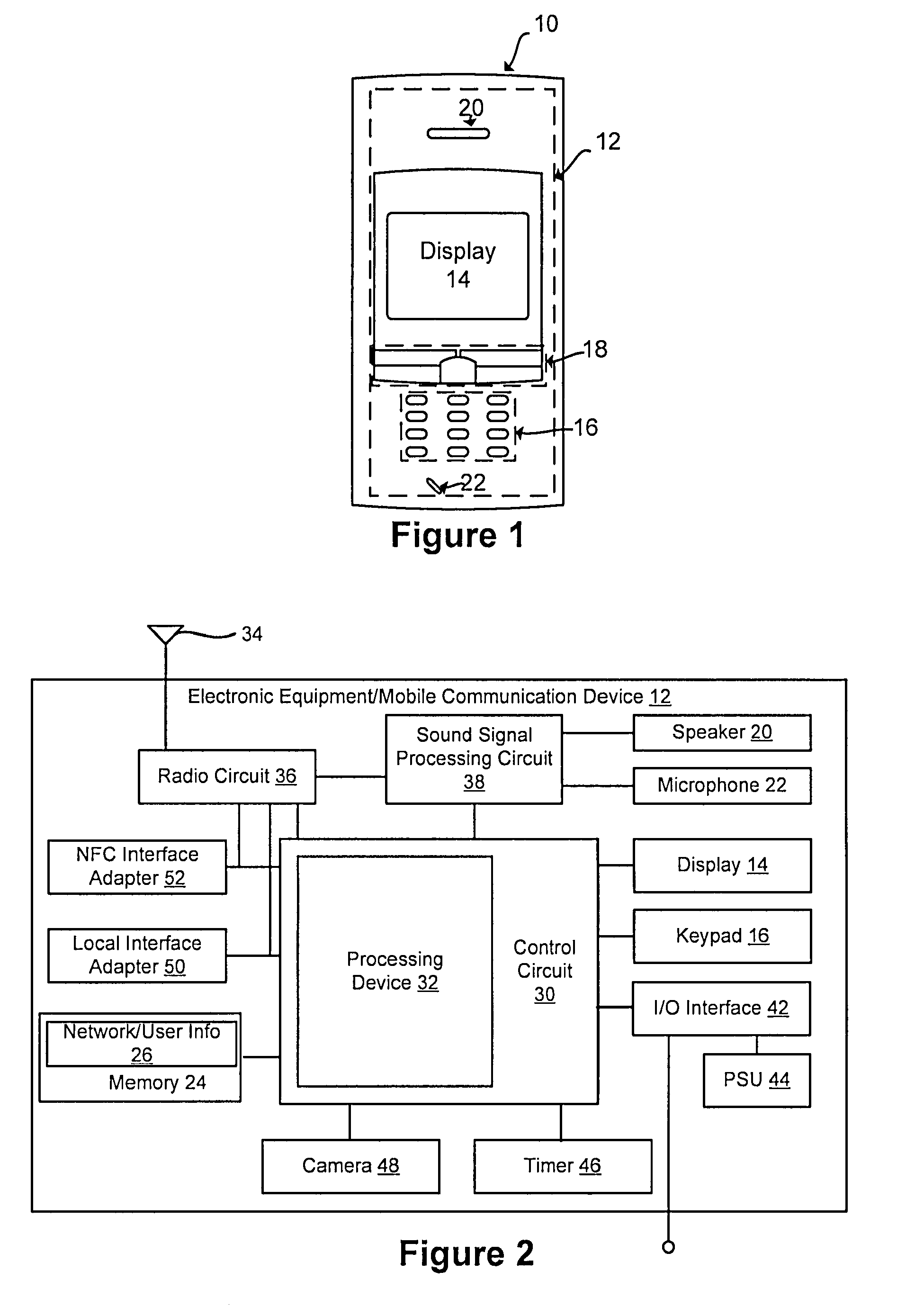
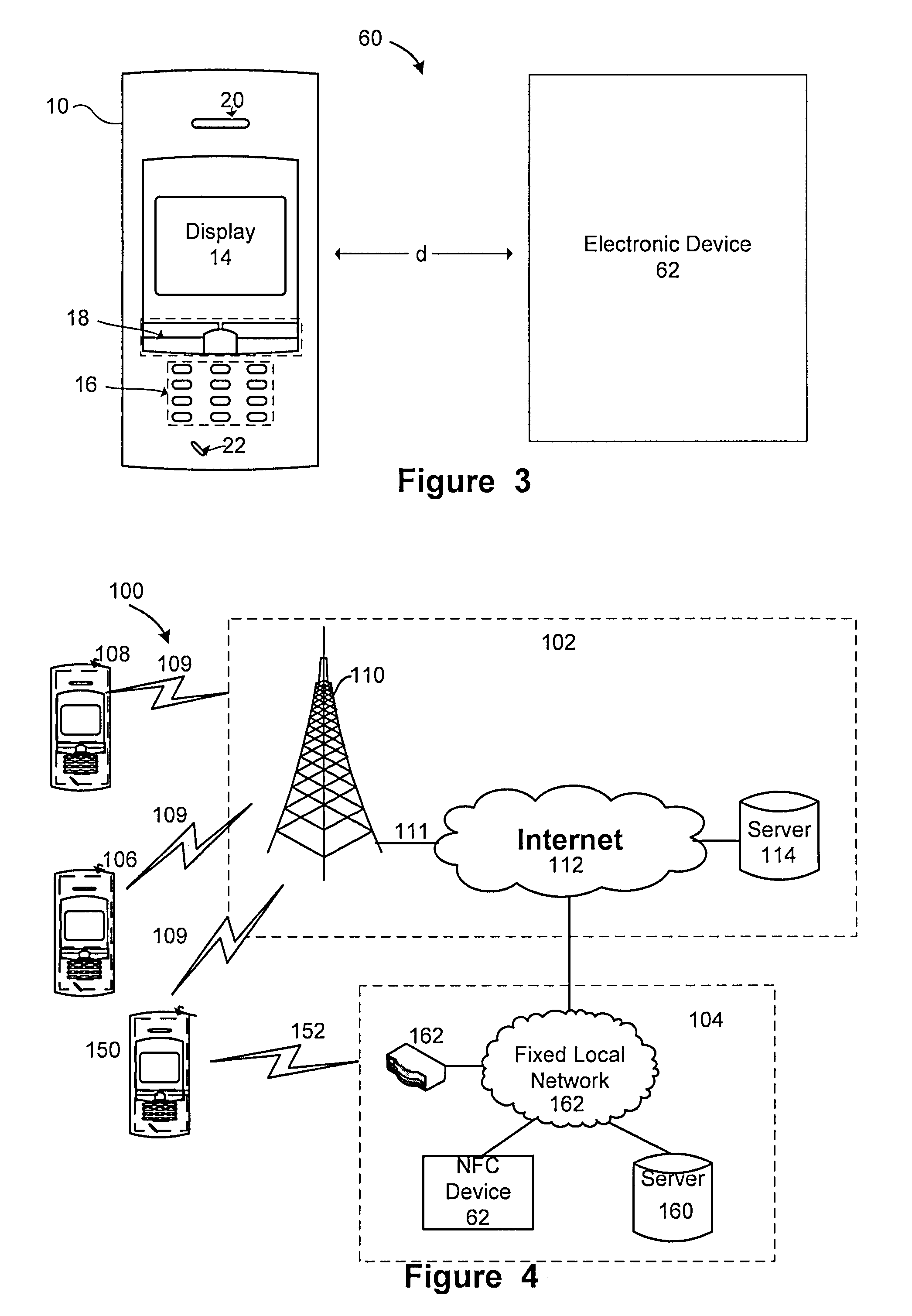
Near field communication for profile change in switching network acess
Disclosed is a system and method that utilizes near field communications (NFC) for establishing and / or controlling the routing of communications in a fixed mobile convergence environment. Electronic equipment is provided with an NFC adapter and a storage element (e.g., memory, disk drive, etc.) that has user's identity specific information (e.g., user's identity information, social security number, user's identity identification number, virtual target network (VPN) settings, etc.) stored in a suitable electronic format for transmission to a NFC reader that is coupled to a fixed local network (e.g., corporate enterprise network). The fixed local network authenticates the user and fixed mobile convergence is realized between a wide area communication network and the fixed local area network.
Owner:SONY ERICSSON MOBILE COMM AB
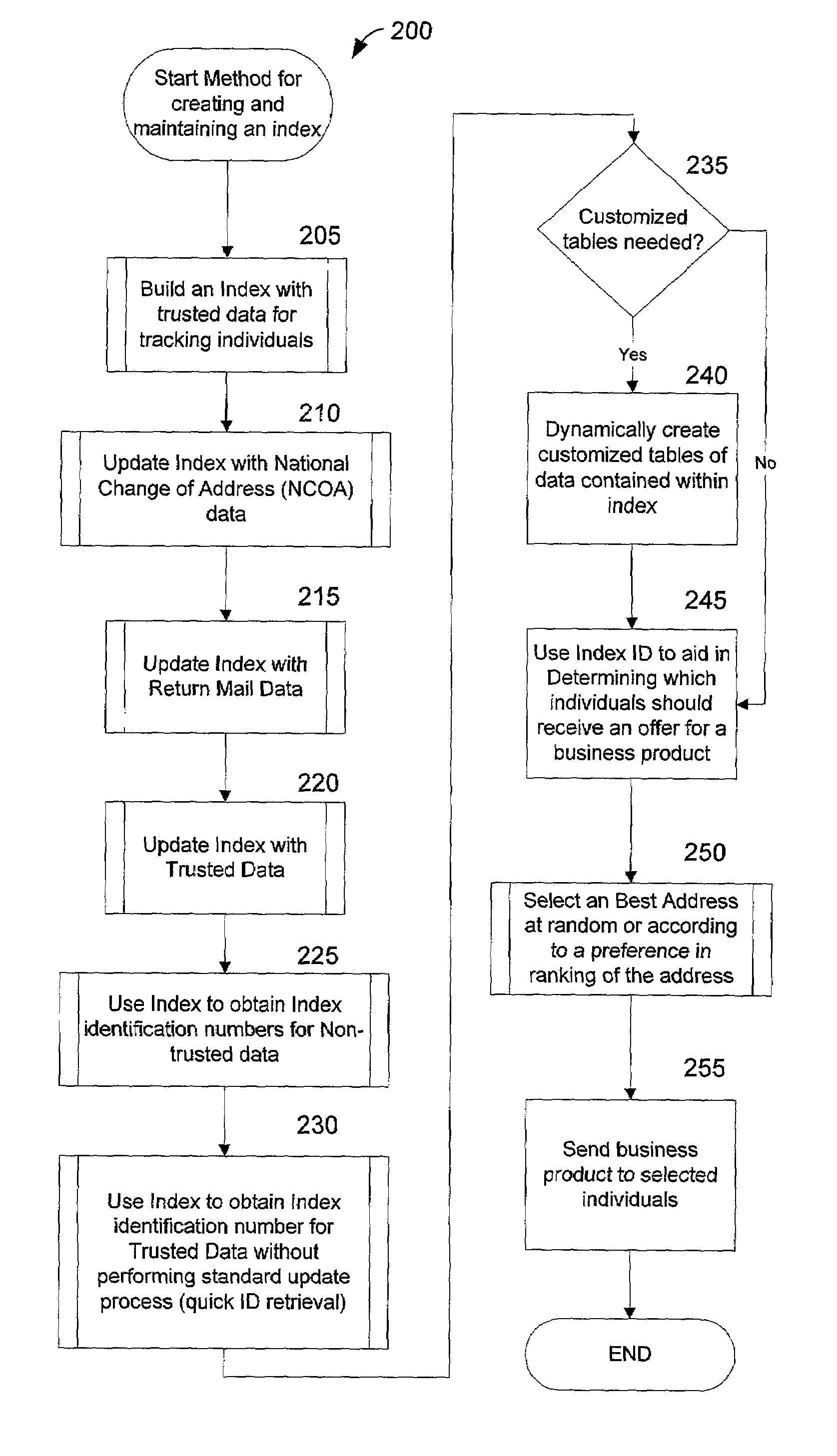
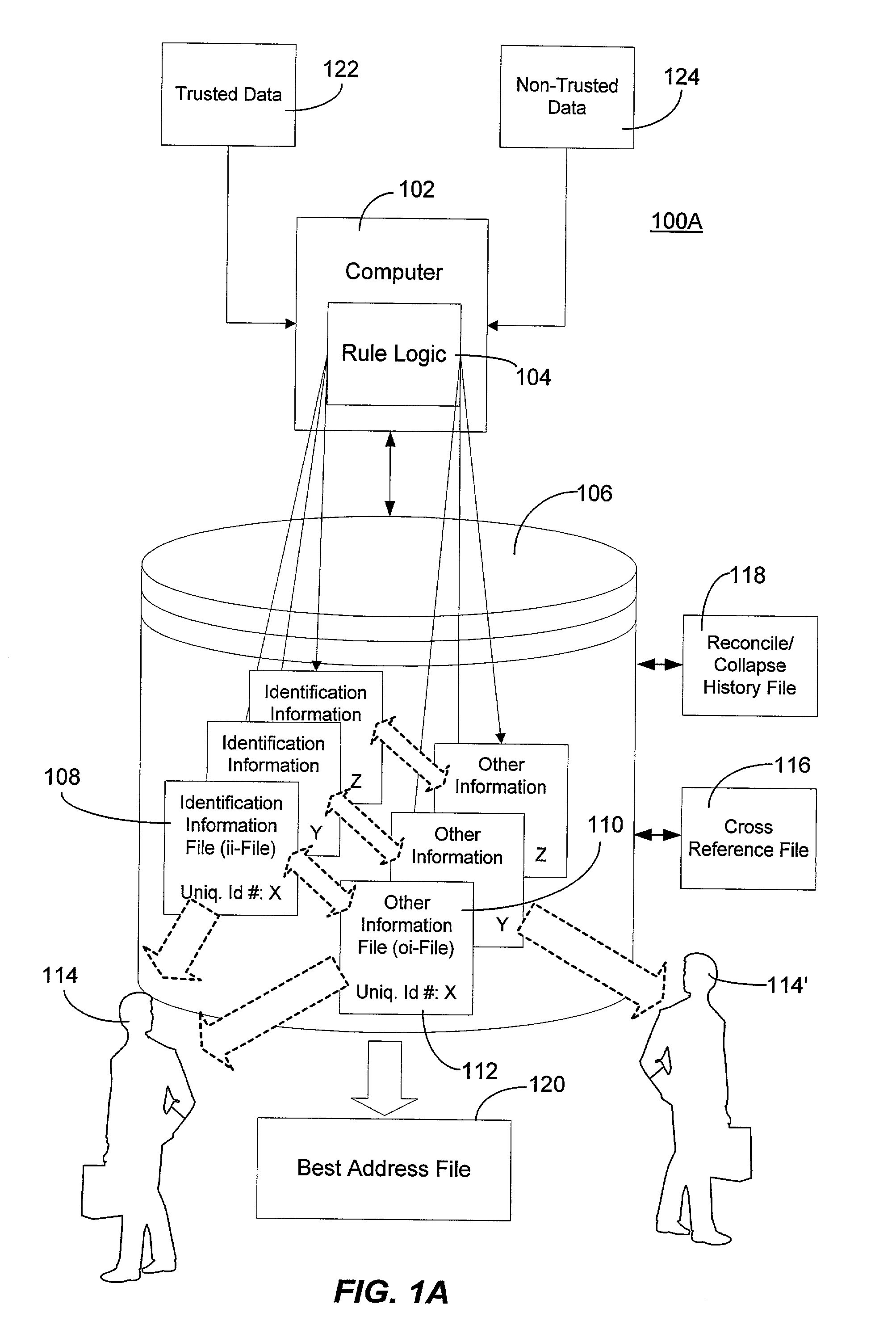
Method and system for creating and maintaining an index for tracking files relating to people
InactiveUS6968348B1Easy accessEasy to manufactureFinanceDigital data processing detailsFile allocationSocial Security number
A computer system creates and maintains an index for tracking information relating to individuals. Such information can include, but is not limited to, social security numbers, names, address information, credit bureau identification numbers, and credit history information on individuals. The invention employs logical rules to this information in order to create and maintain a set of files for each individual. The logical rules can include social security rules, geography rules, and address ranking rules. The invention is designed to evaluate slight variations in information very carefully in order to insure that appropriate files are assigned the same index identification number or that appropriate records are assigned separate and different index identification numbers as a situation warrants. The present invention is designed to maintain numerous files for each individual being tracked instead of merging and purging files as is done in the conventional art.
Owner:PROVIDIAN FINANCIAL CORP +1
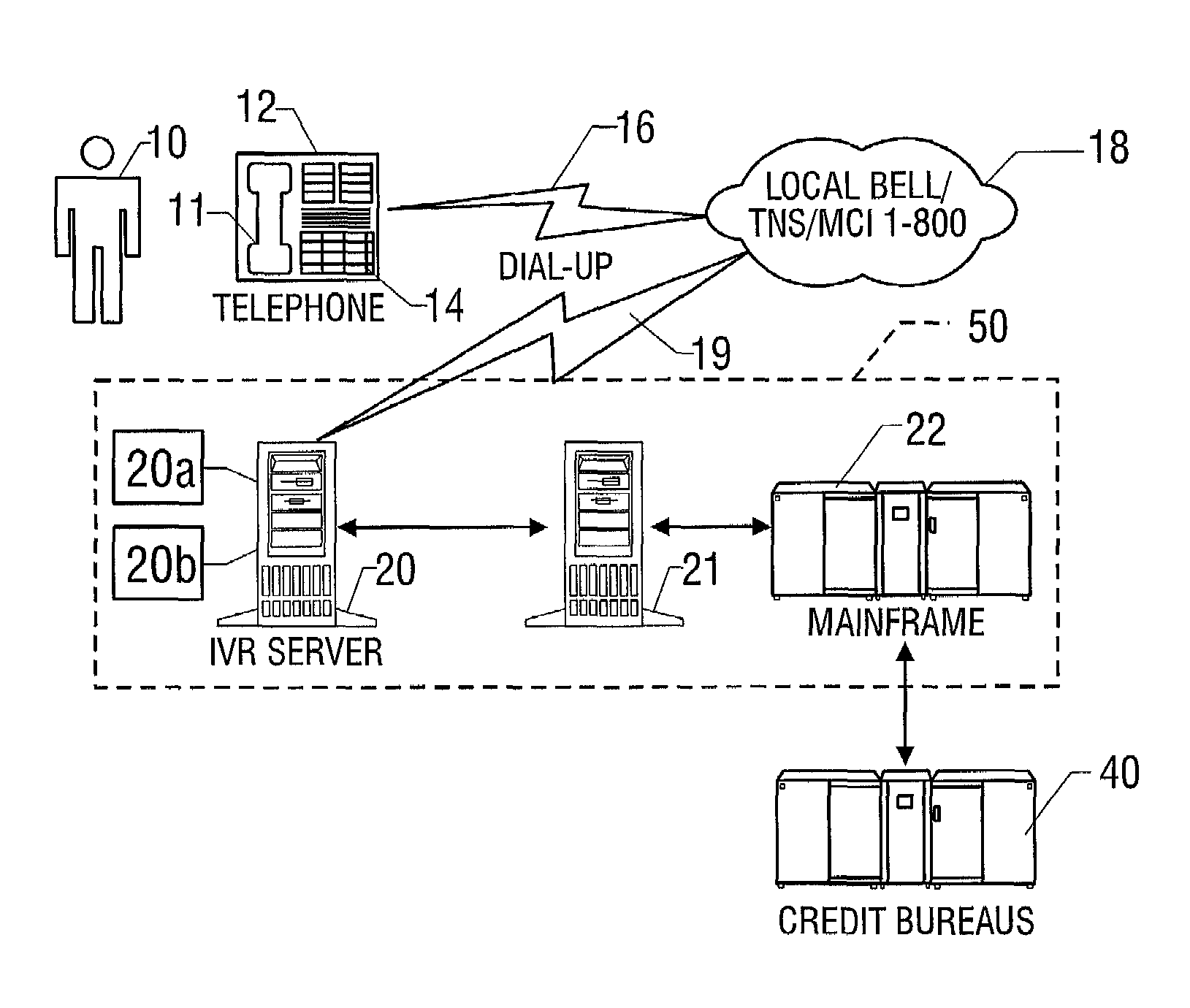
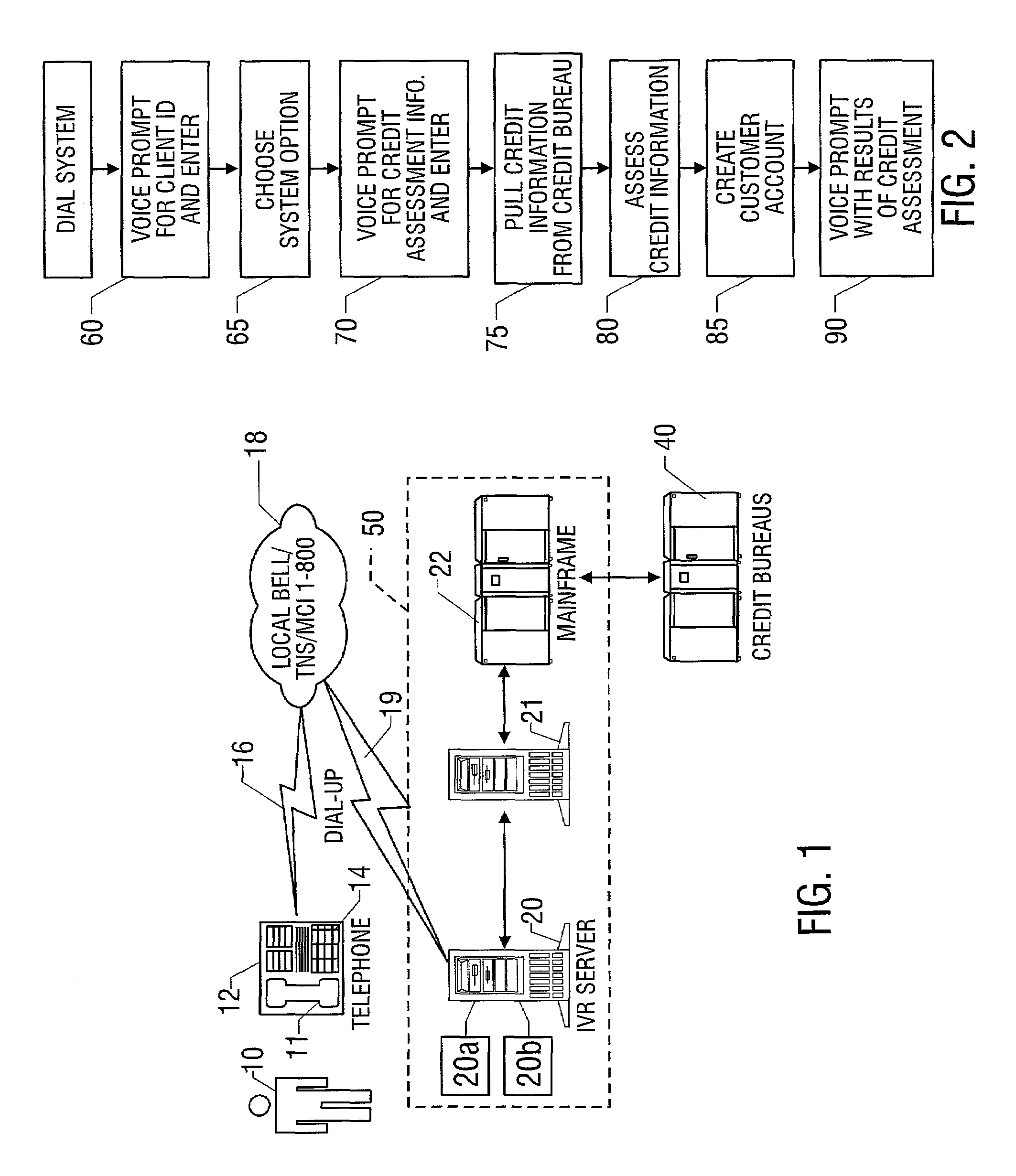
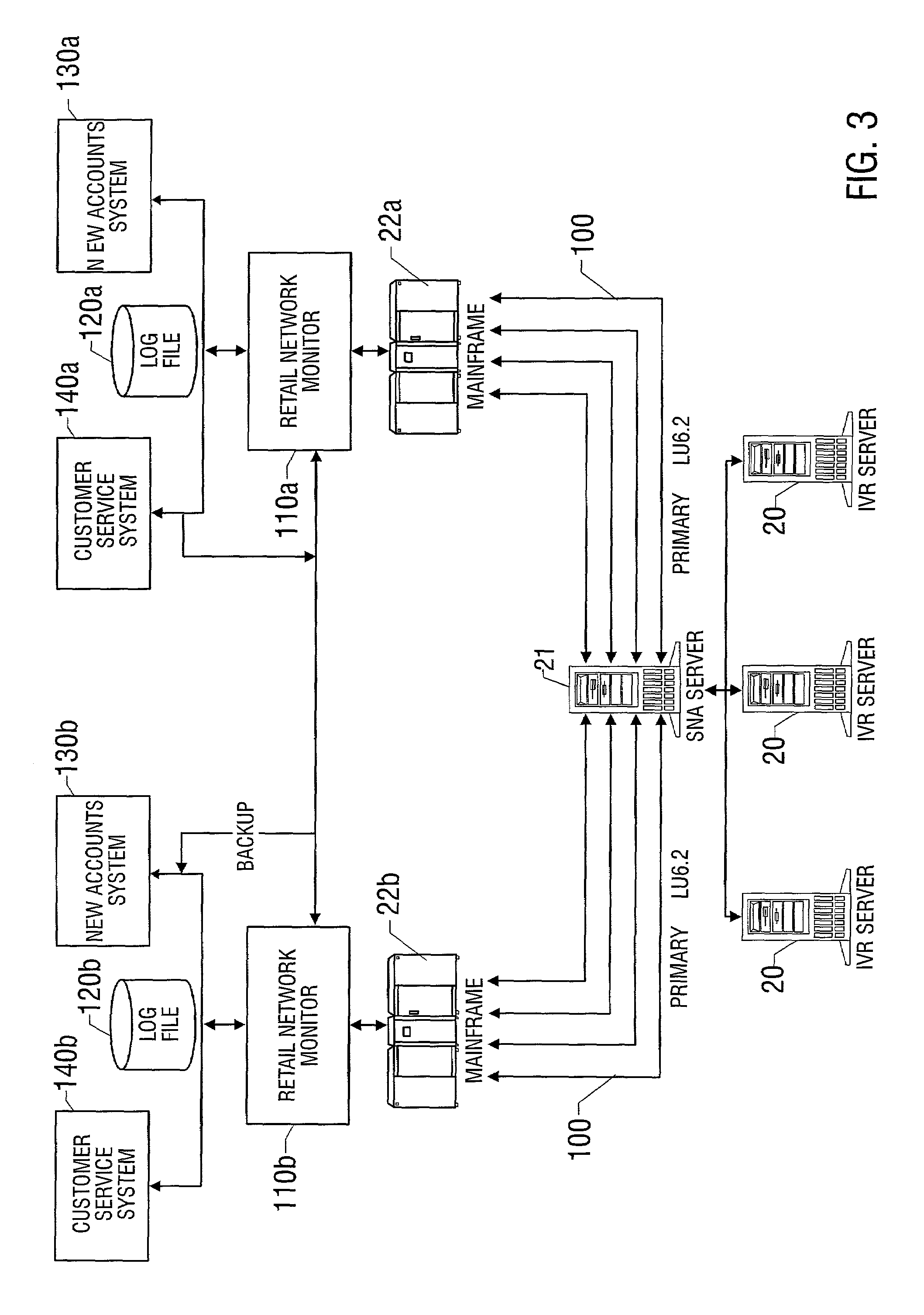
Interactive voice response quick credit system and associated methods
A system and method for applying for a credit card, preferably at a point of sale, is disclosed. The system employs an automated interactive voice response system preferably sponsored by a credit card issuer. The user calls into the system using a standard telephone, and enters credit assessment information about the customer using the key pad of the telephone in response to verbal questions posed by the system. In one embodiment, only numeric information concerning the customer is entered, such as the customer's social security number. This credit assessment information is used to retrieve a credit report or score from a credit bureau database, which is used by the system to electronically decide whether to issue credit and to what extent and to establish a customer account. The system verbally provides information to the user regarding the credit assessment so that the customer's credit purchase can be quickly consummated.
Owner:BREAD FINANCIAL PAYMENTS INC
Method of preventing fraud
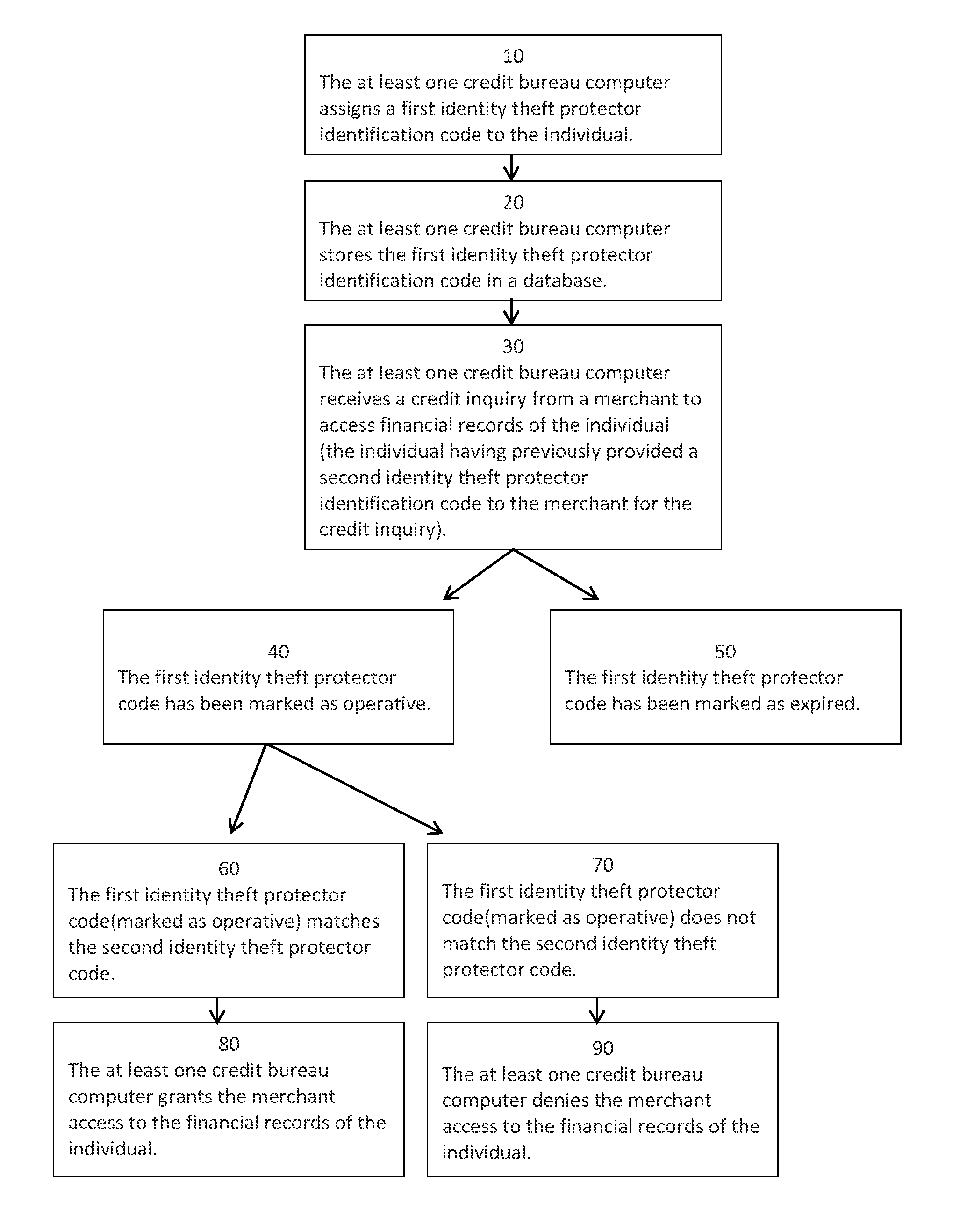
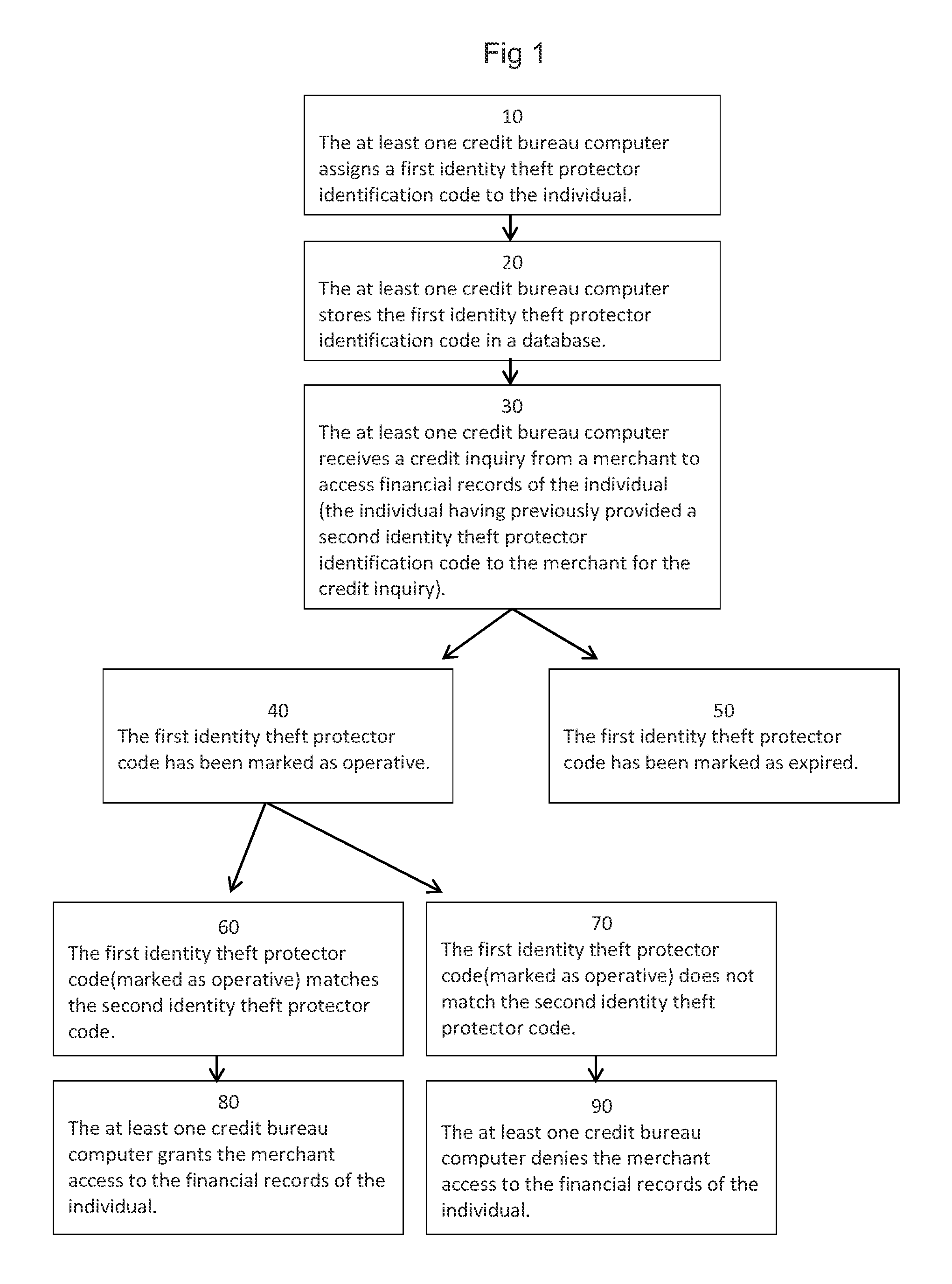
ActiveUS7860769B2Reduce usageFinanceDigital data processing detailsSocial Security numberIdentity theft
An identification verification system designed to prevent identity theft and financial fraud. Individuals are given or select identification codes which replace the commonly used social security numbers (SSNs). In order to access an individual's credit report or other financial records or open a credit account, the individual's identification code must be provided. Individuals, therefore, no longer have to provide their SSN in order to verify their identity. An individual's identity is verified only if the identification code submitted by the individual matches their identification code as found in a database. Individuals may choose to have their identification codes automatically changed periodically, or may choose to change their identification codes themselves as often as they wish. Identification codes are preferably changed upon each access to the individual's credit report or credit account opening.
Owner:BENSON TRACEY M
Systems and methods for de-identification of personal data
According to some embodiments, original data is retrieved from an original data source. The original data may be automatically searched for potential personal information, such as a person's name, address, or Social Security number. An obfuscation method may be selected from a plurality of potential obfuscation methods. The potential personal information in the original data may then be automatically replaced with fictional data in accordance with the selected obfuscation method.
Owner:HARTFORD FIRE INSURANCE
Method of preventing fraud
An identification verification system designed to prevent identity theft and financial fraud. Individuals are given or select identification codes which replace the commonly used social security numbers (SSNs). In order to access an individual's credit report or other financial records or open a credit account, the individual's identification code must be provided. Individuals, therefore, no longer have to provide their SSN in order to verify their identity. An individual's identity is verified only if the identification code submitted by the individual matches their identification code as found in a database. Individuals may choose to have their identification codes automatically changed periodically, or may choose to change their identification codes themselves as often as they wish. Identification codes are preferably changed upon each access to the individual's credit report or credit account opening.
Owner:BENSON TRACEY M
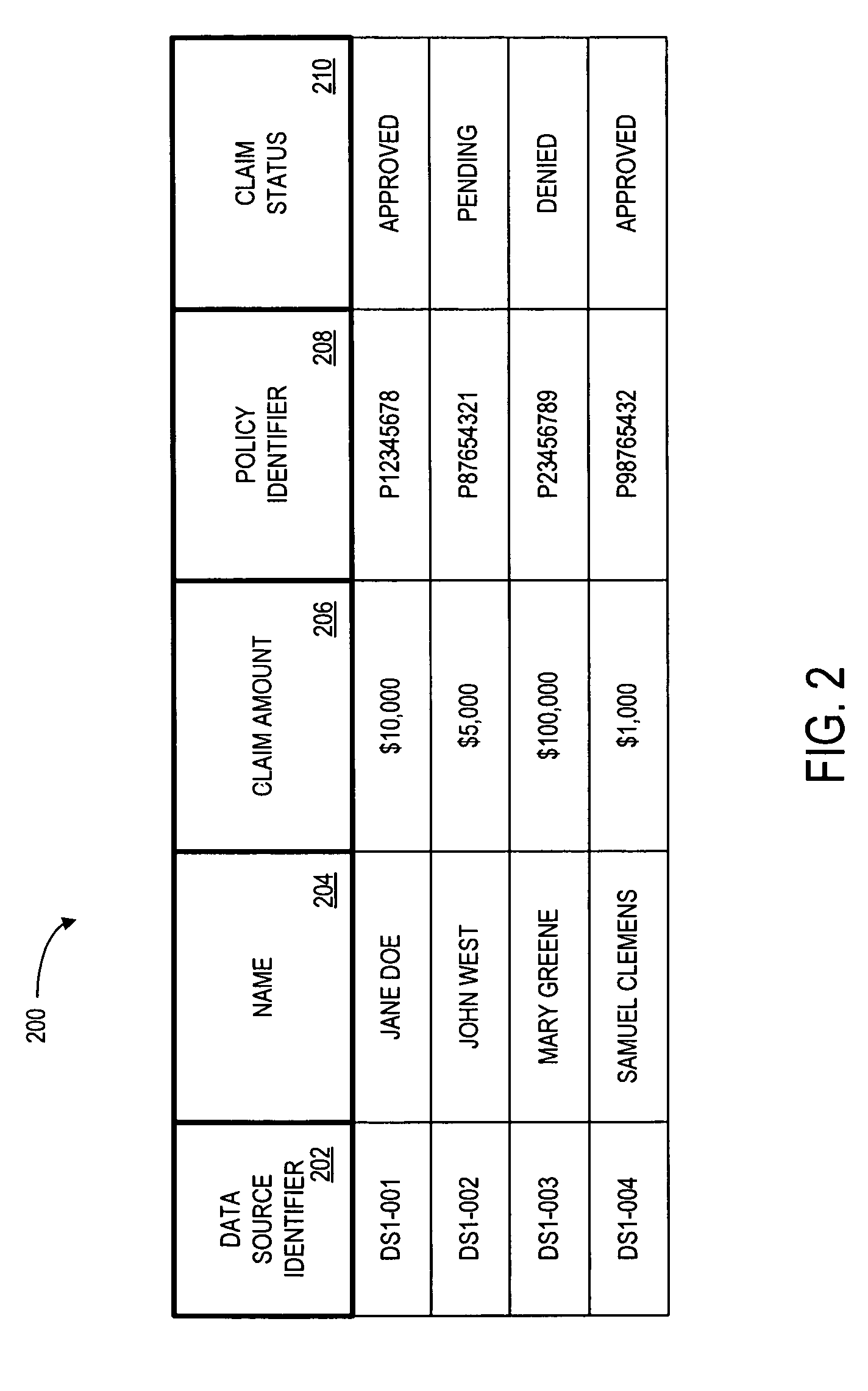
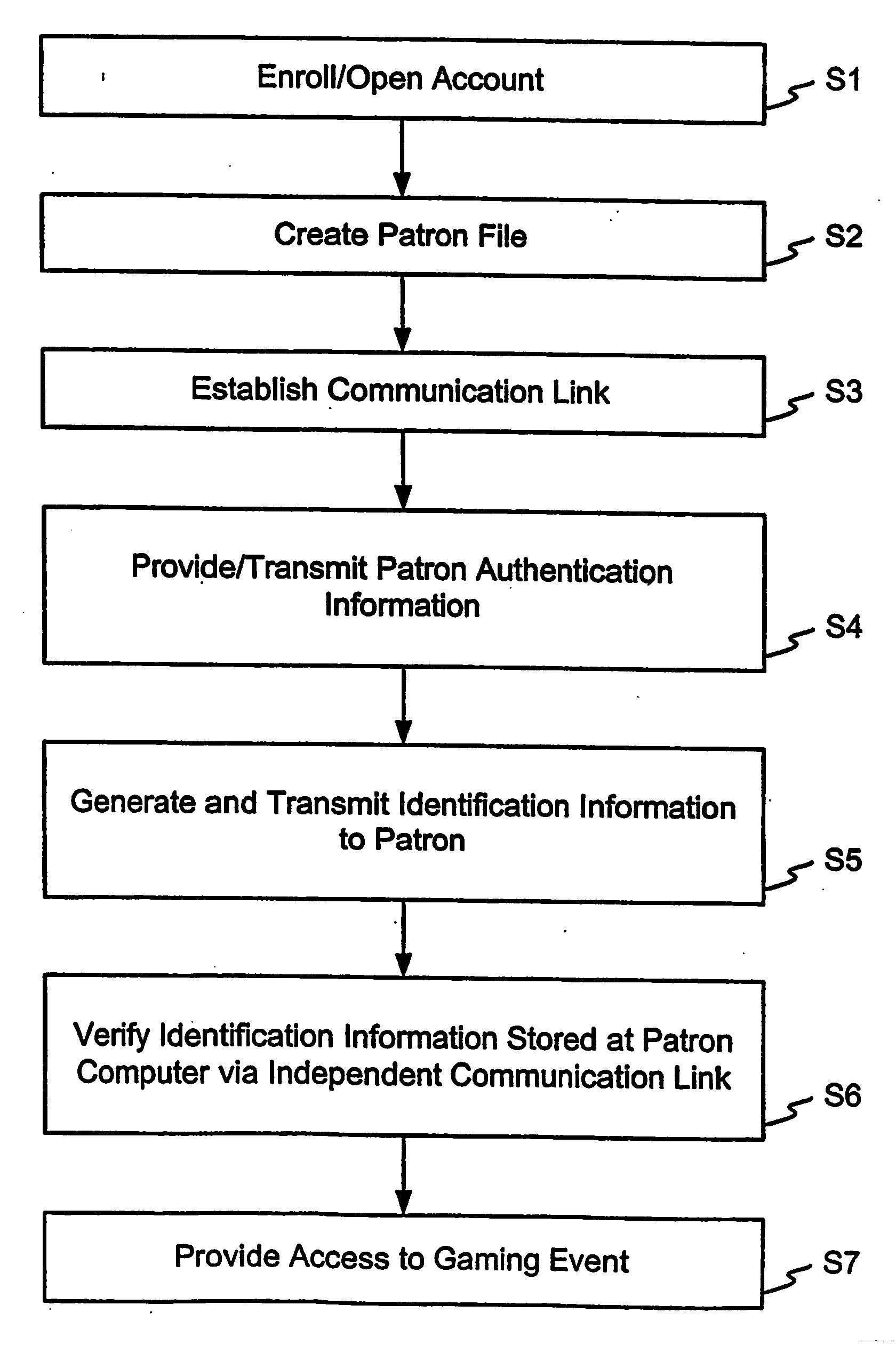
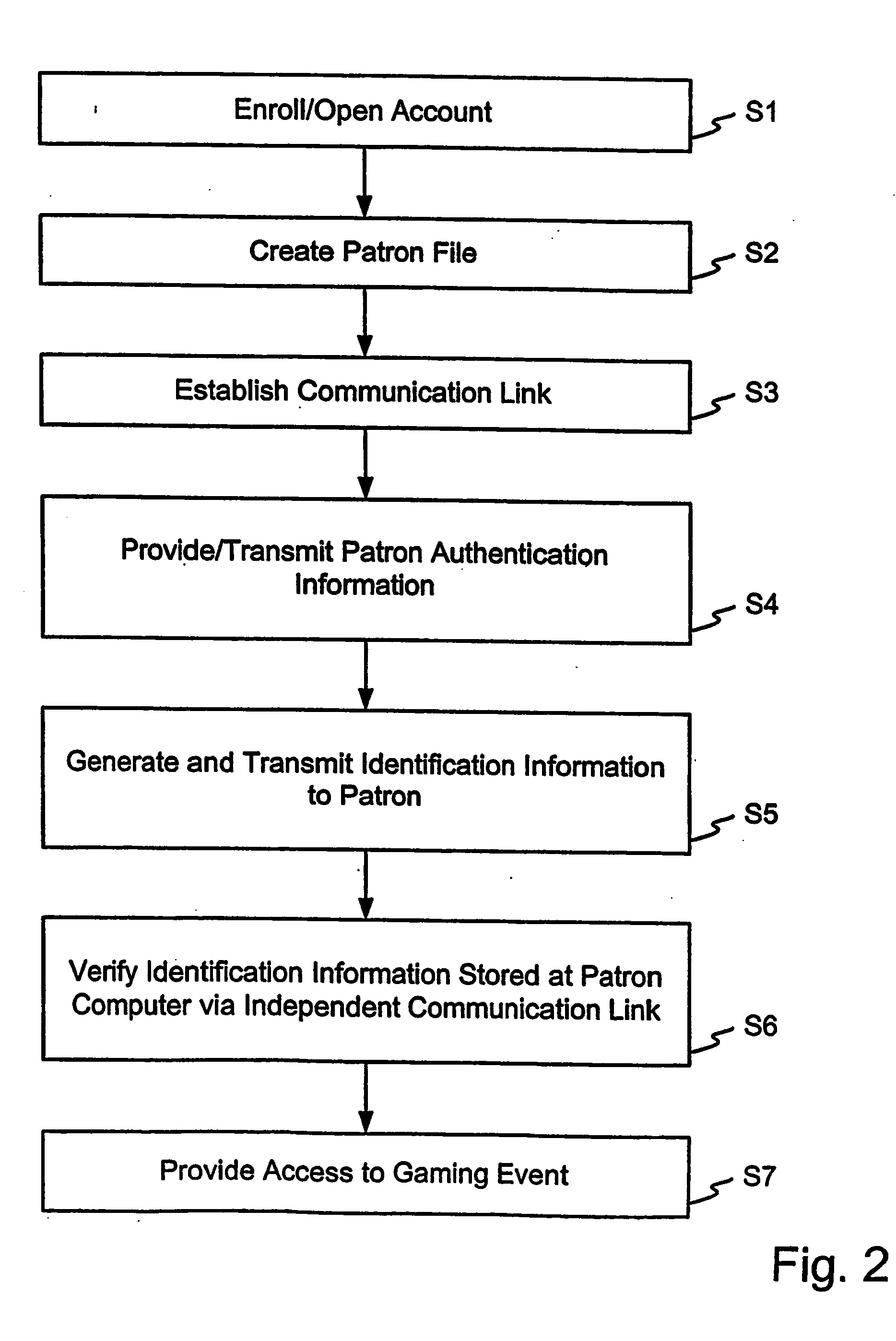
Method of verifying entitlement to participate in a gaming event from a remote location
InactiveUS20050005127A1Computer security arrangementsApparatus for meter-controlled dispensingTelecommunications linkSocial Security number
In a first step (S1), a prospective gaming patron preferably enrolls to establish entitlement to participate in a gaming event. This step includes the patron providing a variety of information, including identification information. Preferably, this information is of a nature which permits the gaming event provider to verify the patron's identity. For example, the patron may provide a state drivers license, a federal Social Security number or card, birth certificate, passport or the like for the purpose of ensuring that the individual who is enrolling is the person they purport to be. In a step (S2), a file is created regarding the patron. Generally, this file will only be created in the event the patron is determined to meet the requirements for participating in a gaming event. In a step (S3), the player establishes communication with the game server. In a step (S4), the user transmits authentication information to the game server. The authentication information is compared to authentication information contained in the file or files corresponding to the patron. In a step (S5), the game server preferably generates identification information and transmits it to the patron, such as by sending the information to the patron's computer for storage in memory. In a step (S6), the game server established, preferably via a separate communication link or pathway, that the identification information is present at the patron's computer. In a step (S7), the patron is provided access to the game server for participating in one of more gaming events.
Owner:IGT
Global identity protector E-commerce payment code certified processing system
InactiveUS20120331557A1Digital data processing detailsAnalogue secracy/subscription systemsMedical recordCredit card
An identity theft protection system and method which employs several security features to prevent identity theft on all levels. The protection system database employs a member's address and telephone number as a numeric identity protector, security code and lock for Social Security numbers. Preventing the issuing of identity theft credit cards, and e-commerce address billing payment code numbers, and e-commerce telephone number billing payment code numbers. The locking address also prevents account hijacking, preventing checks from being mailed to identity thieves. The system employs a computer generated photo copy of the member's ID or drivers license, to prevent fraud on all big ticket items, and preventing identity theft bank fraud on checking accounts and medical records providing photo match and verify, identity theft prevention verification. The system protects its members against stolen and counterfeit checks. The G.I.P. computer database will ID the owner of the checking account at the cash register. The ID can also prevent cyber identity theft, also known as account hijacking.
Owner:WASHINGTON KEITH ANTHONY
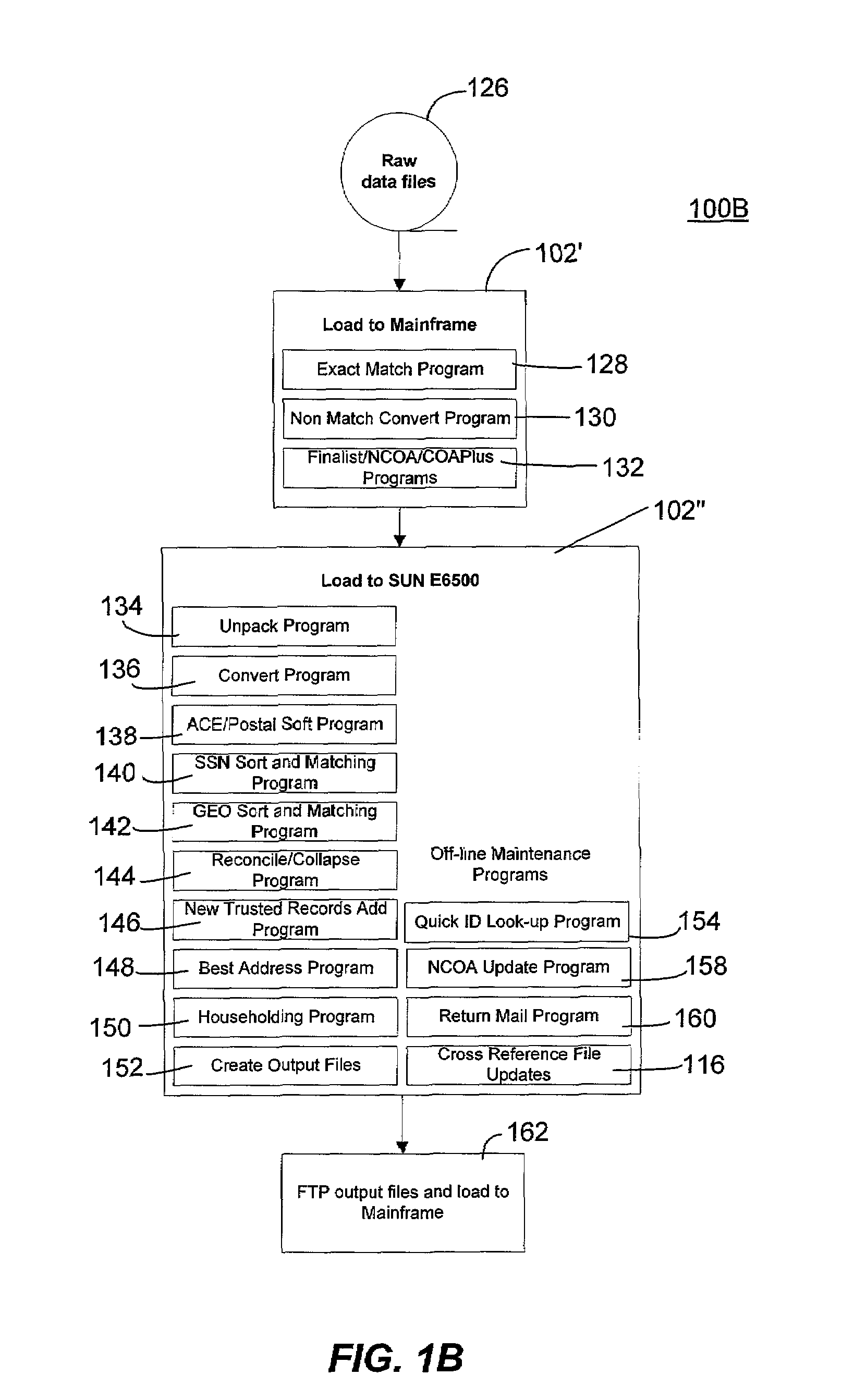
System and method for verification, authentication, and notification of transactions
InactiveUS20110016050A1Facilitate communicationIncrease likelihoodFinanceBuying/selling/leasing transactionsTelecommunications linkShort Message Service
A system and method for verifying, authenticating, and providing notification of a transaction, such as a commercial or financial transaction, with and / or to at least one party identified as engaging in the transaction and / or identified as having a potential interest in the transaction or type of transaction, are provided. A central system accepts information regarding a transaction, including information about at least one party identified as engaging in the transaction, such as by a credit account number or Social Security number or merchant account number, and / or identified as having a potential interest in the transaction. Based on the information regarding the transaction and any supplemental information the central system determines, the central system communicates with and / or to at least one party and / or additional or alternative parties, via at least one communications device or system having a communications address, such as a telephone number or Short Message Service address, predetermined as belonging to the at least one party and / or additional or alternative parties. Via said communications, at least one party having an interest or a potential interest in the transaction may be notified of it, and may further be enabled or required to supply additional verifying or authenticating information to the central system. If the transaction was initiated or engaged in via a communications link, such as via the Internet, said communications preferably occur over at least one different communications link and / or protocol, such as via a wireless voice network. The central system may then compute a result based on the outcomes of said communications, and may then transmit the result to the user and / or to a second system or device.
Owner:EVANS ALEXANDER WILLIAM
System and method for enhanced fraud detection in automated electronic credit card processing
InactiveUSRE38572E1Efficient detectionImproving fraud detectionComplete banking machinesFinanceInternet privacySocial Security number
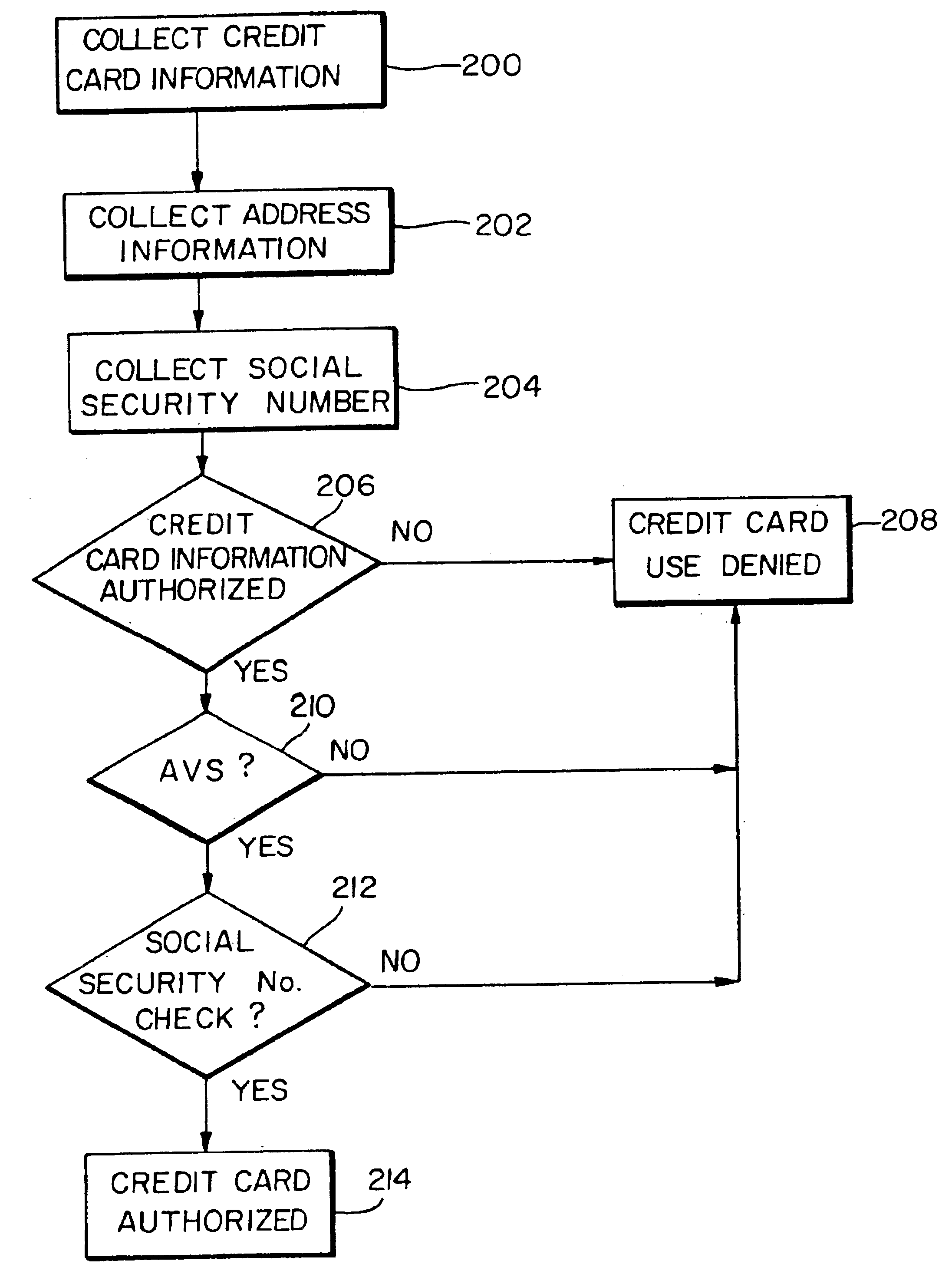
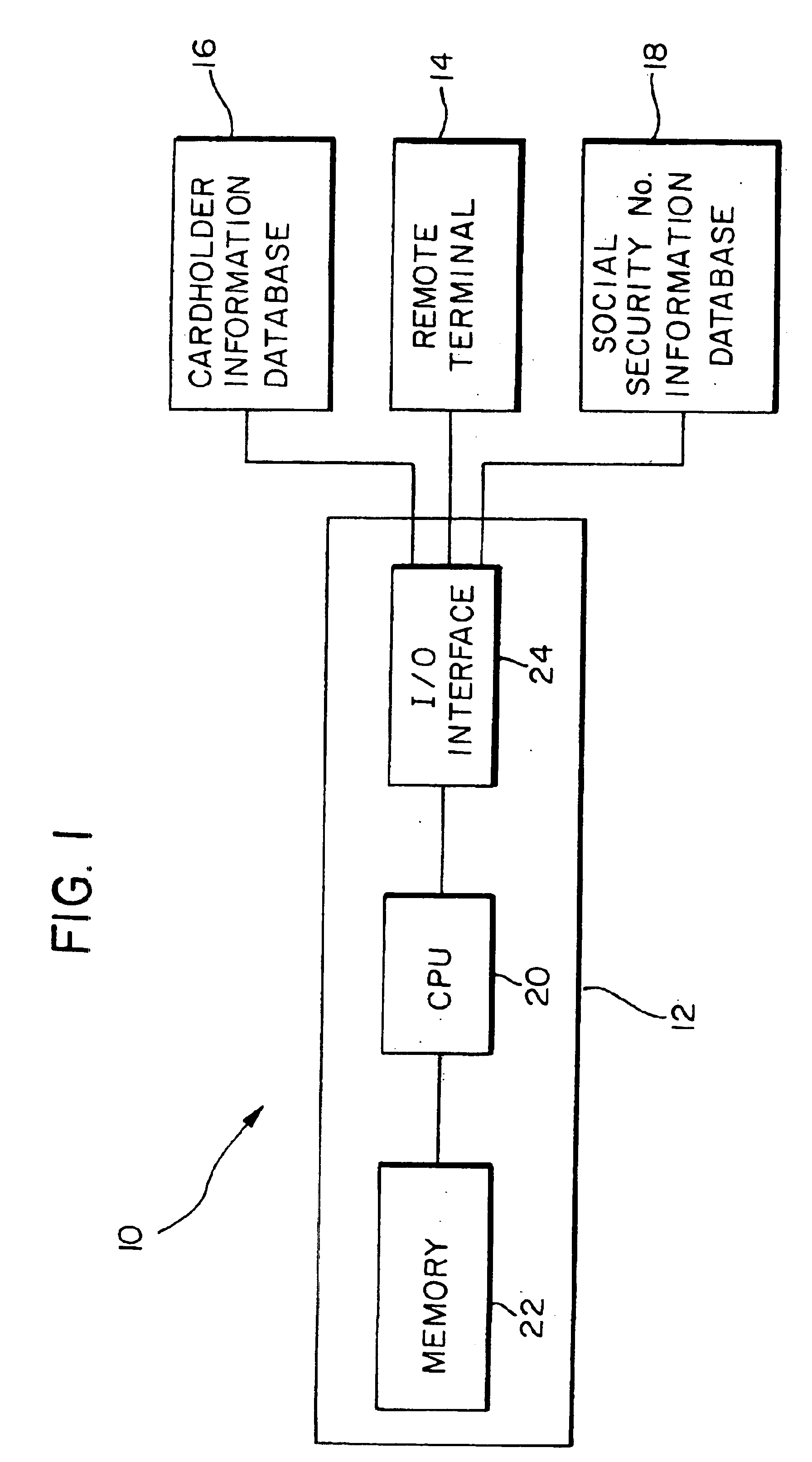
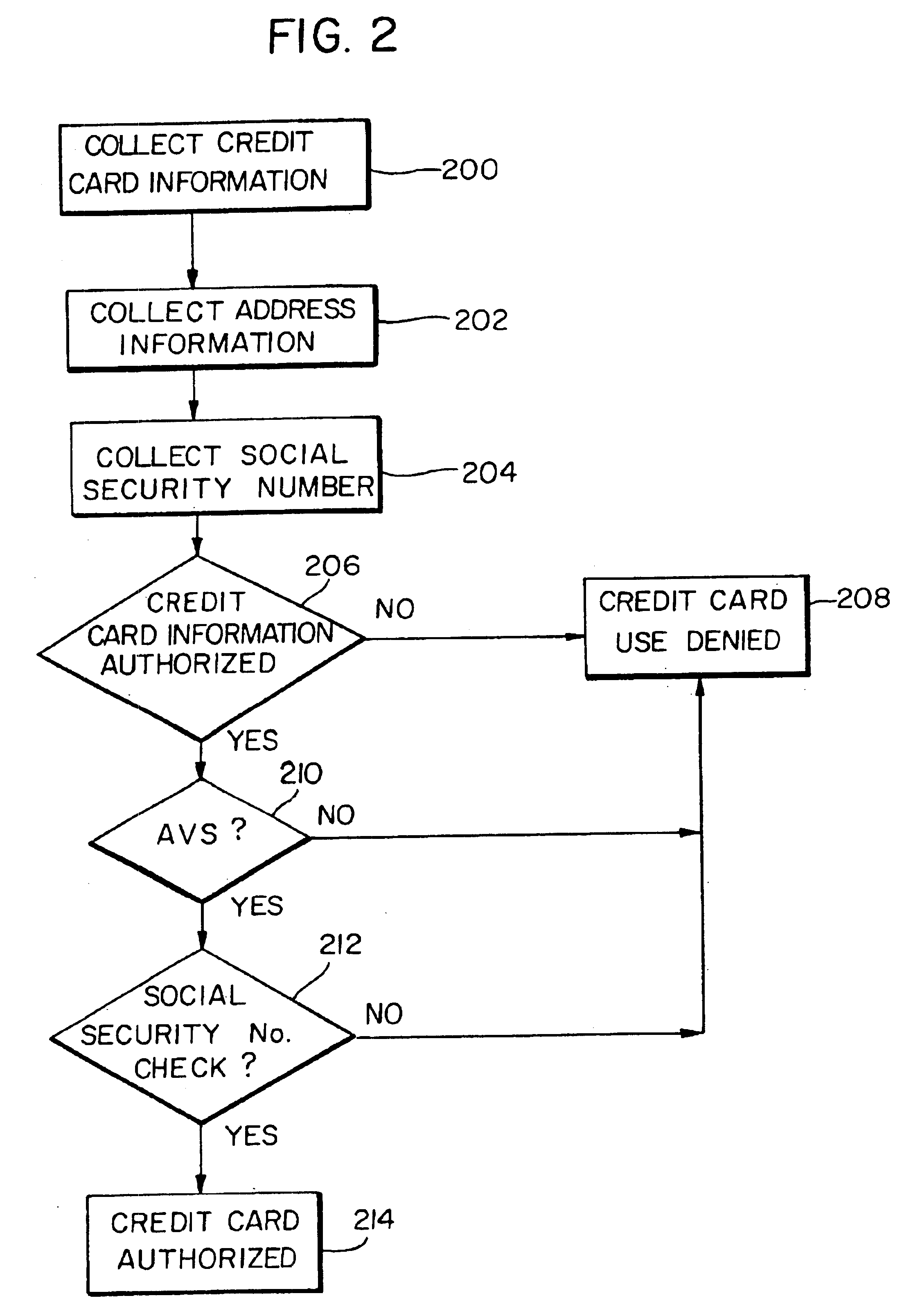
A method and system for authorizing an electronic credit card transaction having enhanced measures for detecting fraudulent transactions. A user .[.at a remote terminal attempting to conduct an electronic credit card transaction.]. is prompted to input the user's credit card information, address, and social security number. .[.The information input by the user is retrieved and used for identification purposes..]. Initially, the input credit card information is submitted to an issue of the user's credit card to determine whether the input credit card information is valid. The social security number .[.input by the user.]. is next checked .Iadd.against a separate social security number database .Iaddend.to determine if it corresponds to the user. .[.A database having a stored list of social security numbers is accessed, wherein each of the stored social security numbers includes at least one address stored therewith corresponding to an address of an individual identified by the respective social security number..]. The addresses stored in association with the input social security number are retrieved and compared with the input address to determine if the input address corresponds to any of the retrieved stored addresses. If the input credit card information has been confirmed by the issuer as being valid and the address input by the user matches any of the retrieved address stored in association with the input social security number, the electronic credit card transaction is authorized .[.and allowed to transpire. The social security number database is stored and accessed separately from the issuer's credit card information database to provide an added measure of protection against a person fraudulently gaining access to one of the database, since access to the information in both databases is required to complete the financial transaction..].
Owner:TETRO DONALD +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com