System and method using superkeys and subkeys
a technology of superkeys and subkeys, applied in the field of system and method using superkeys and subkeys, can solve the problems of not being able to provide customized reports or analysis of transaction level data according to internal needs, and the current risk assessment network cannot provide transaction level data aggregates across multiple accounts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
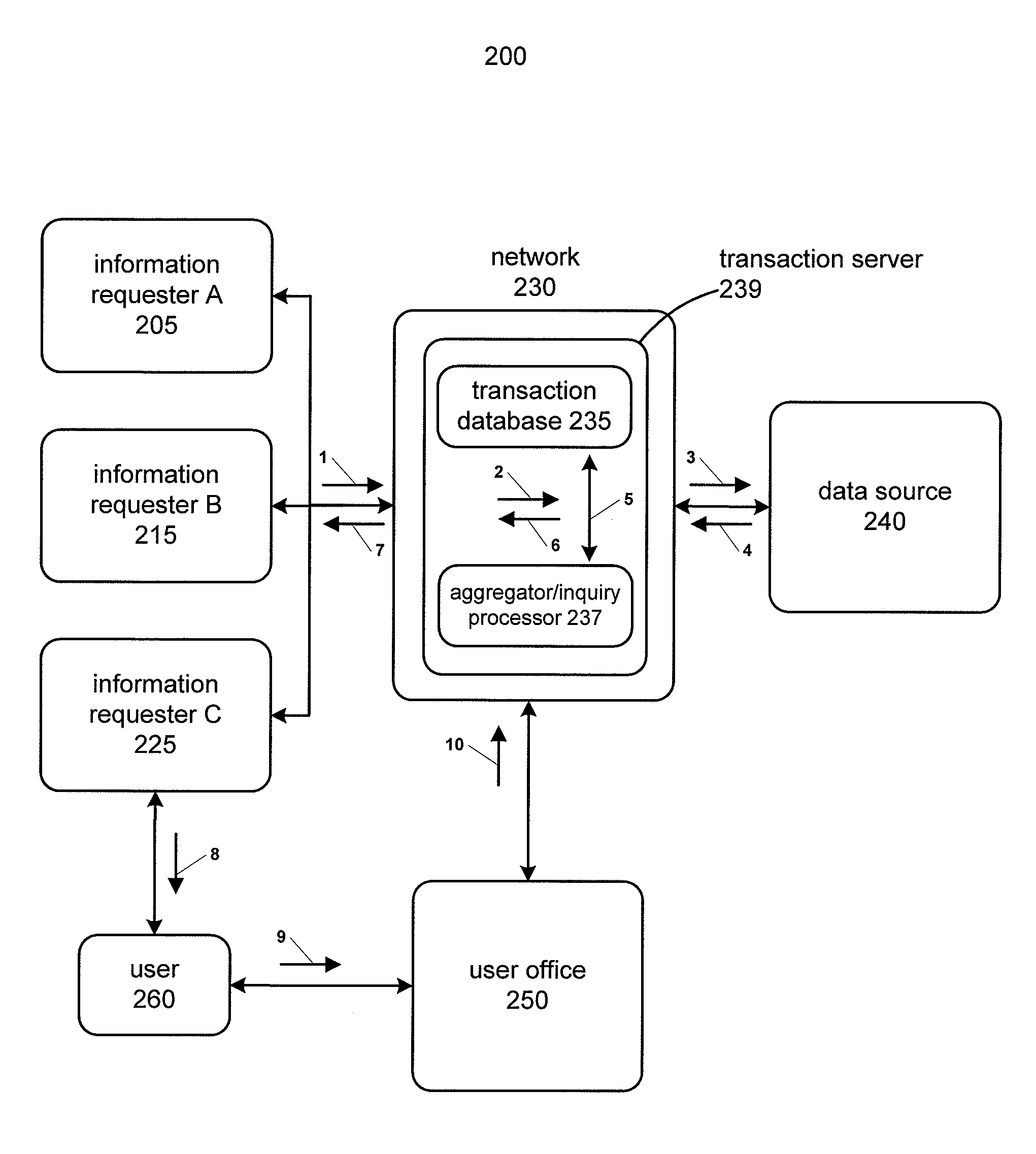
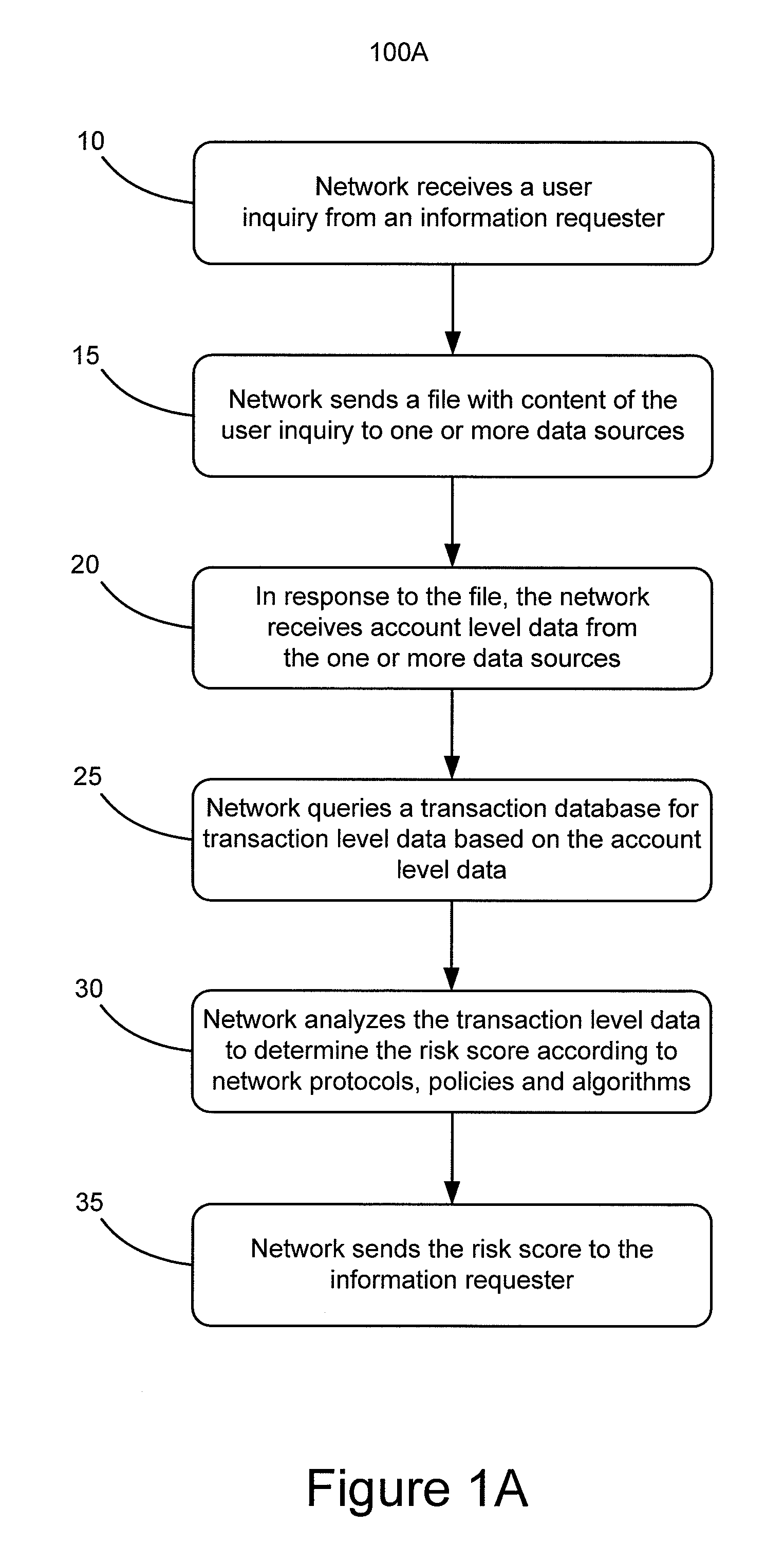
[0019]The present invention is directed to systems and methods for efficiently and cost-effectively reporting aggregated user, account and transaction level information to multiple information requesters. For example, embodiments of the present invention can be used to report user information and aggregated transaction data to multiple credit account issuers for the purpose of anticipating or managing the risk of user bankruptcy or other account risks.
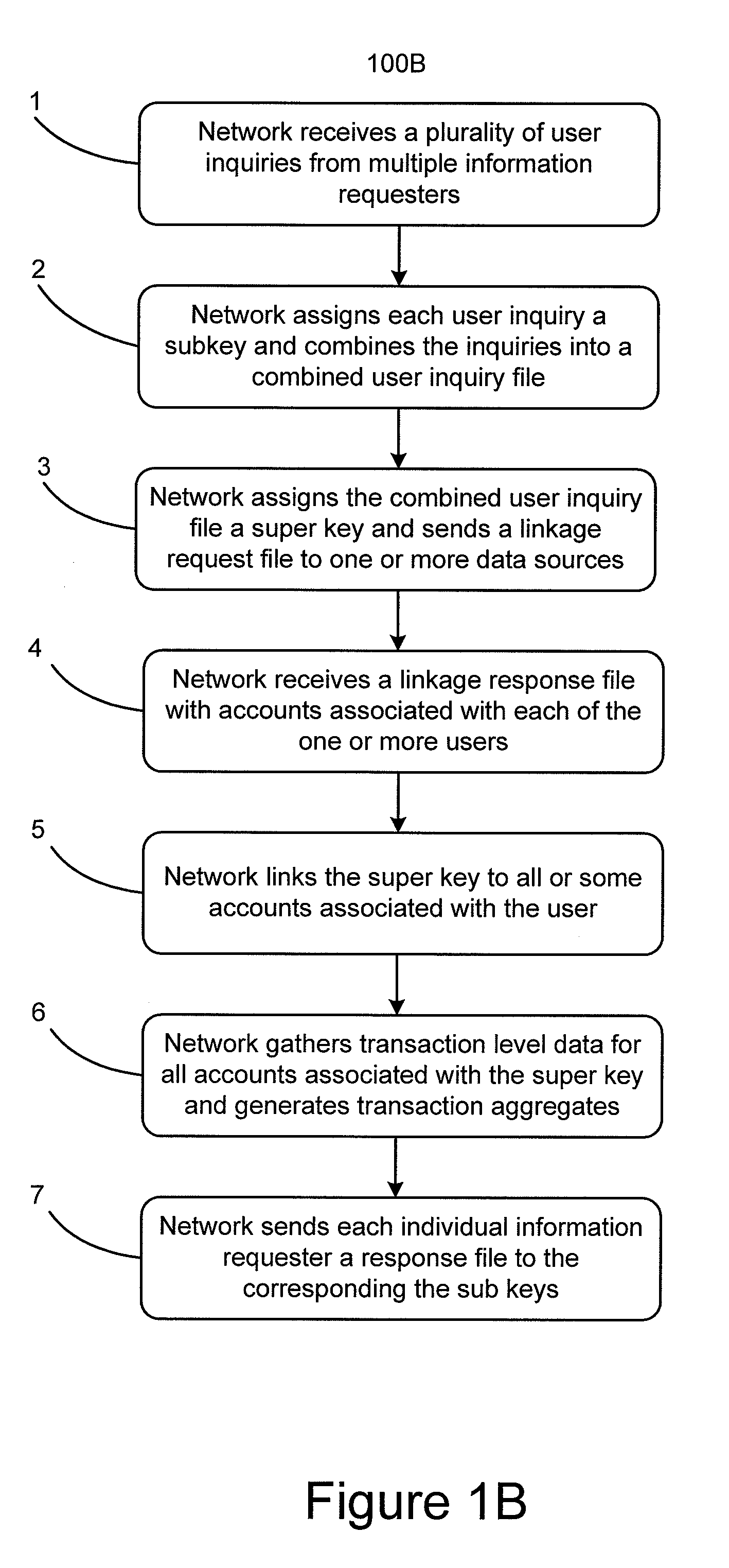
[0020]FIG. 1B depicts a flow chart of a method 100B for processing user inquiries from multiple information requesters according to one embodiment of the present invention. Method 100B can be performed by any appropriate computer or server system running appropriate computer readable code in a network for processing account applications and / or transactions. In step 1, the network receives a plurality of user inquiries from multiple information requesters. As examples, information requesters can be banks or other credit issuing institut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com