Patents
Literature
157results about How to "Avoid checking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
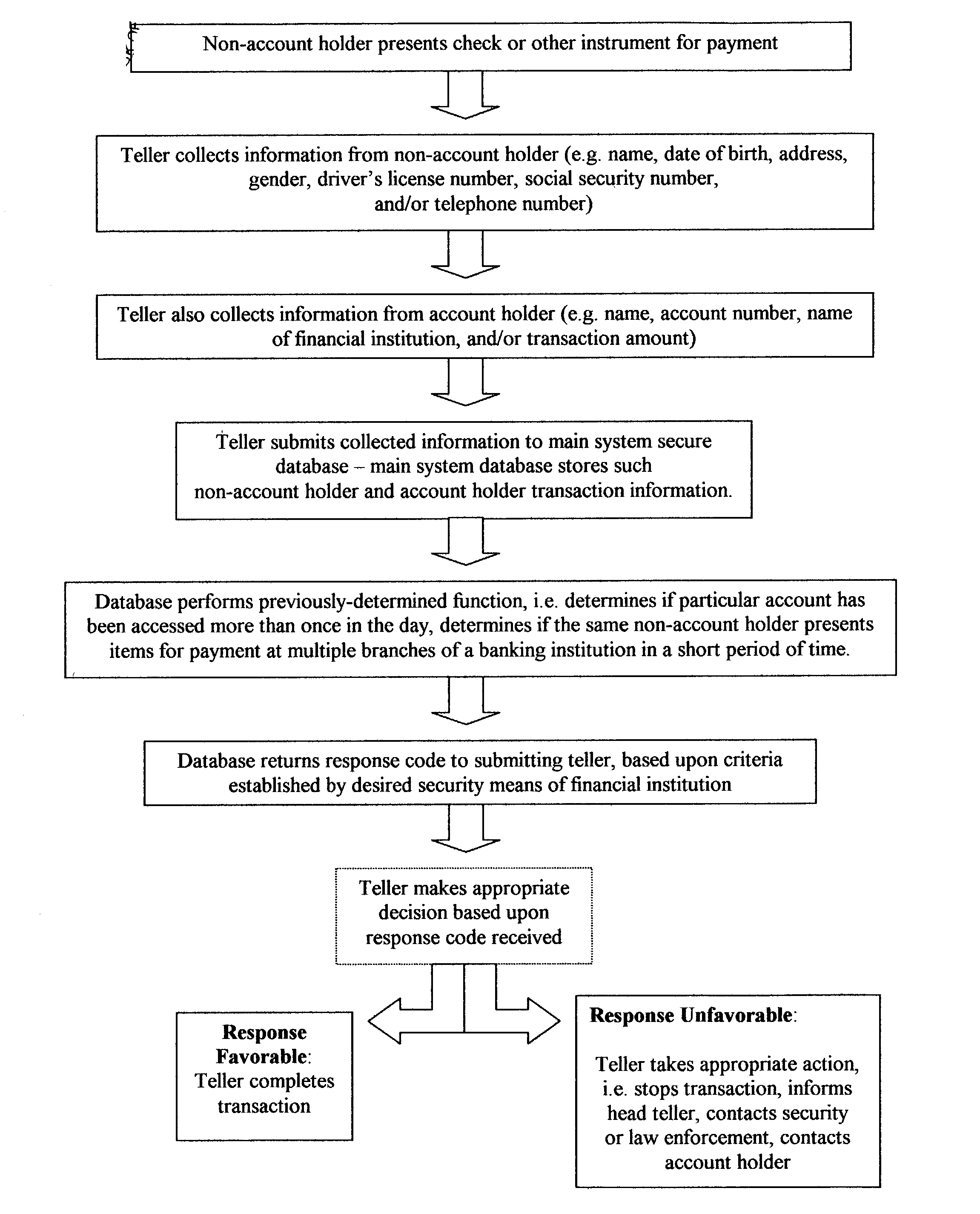
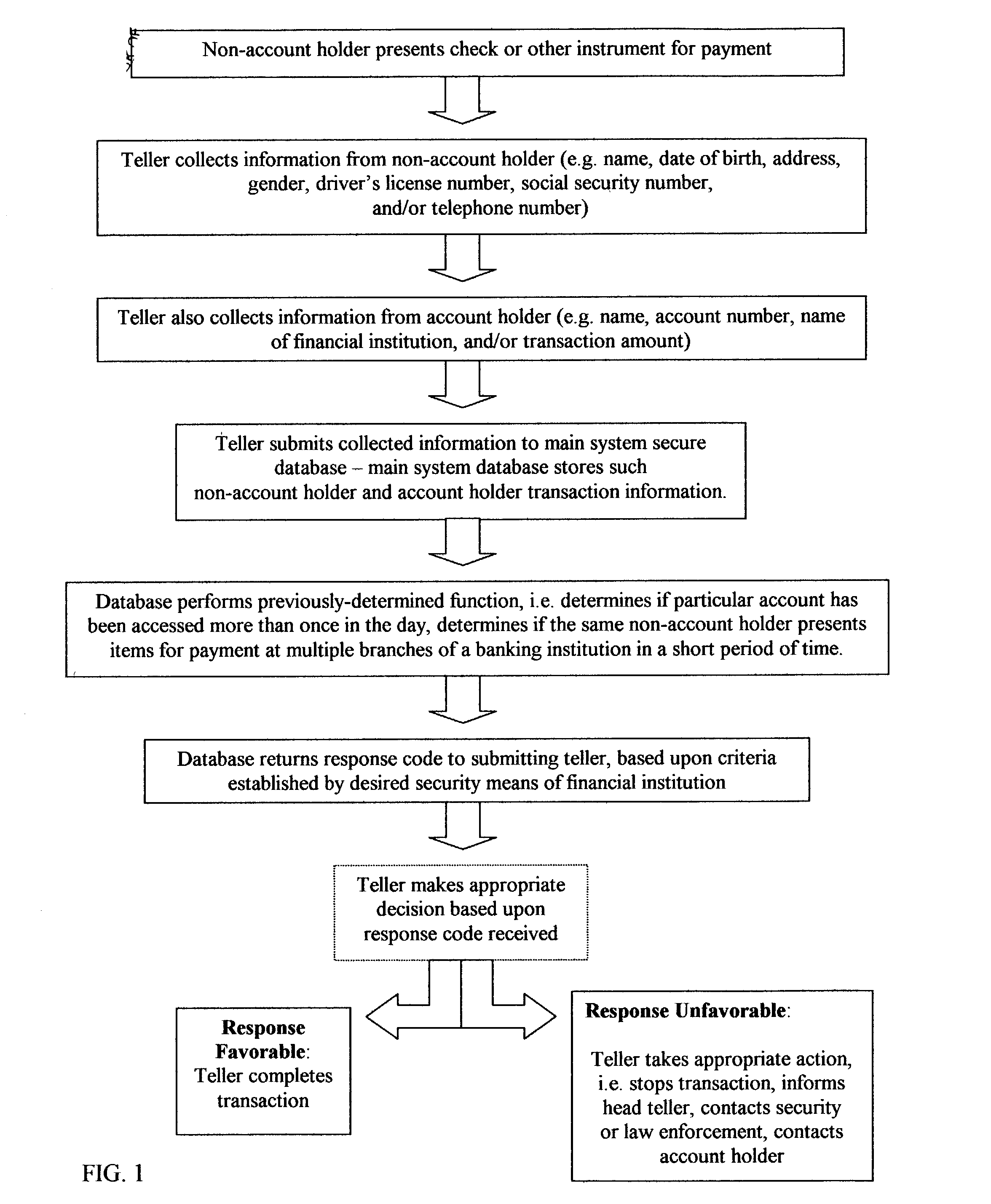
Fraud detection and security system for financial institutions
InactiveUS20030182214A1Limit losses to individual FIsAvoid checkingFinancePayment circuitsSocial Security numberCheque
A fraud detection and security system for financial institutions utilizes a secure database of information relating to financial transactions of non-account holders who present checks and other instruments for payment. The system collects and tracks the frequency of particular aspects of the subject's behavior, and flags deviations from such norms for the purpose of indicating that fraudulent or criminal behavior may be occurring. At such time, the teller or other employee with whom the subject is dealing may stop the transaction, to the benefit of the financial institution and account holder. The system also allows for law enforcement to detect related transactions, or a string of criminal activity from the same perpetrator. In the preferred mode, the system includes a teller collecting information from the non-account holder, including name, date of birth, address, gender, driver's license number, social security number, and / or telephone number. At the time of the transaction, such data is submitted to the system database and the database returns a response code based upon criteria established by the financial institution's desired security measures, accomplished by installation of new software or by integration of a custom program. The system alerts tellers to suspicious activity, such as when a particular account is accessed more than once in a day, or when the same non-account holder presents items for payment at multiple branches of a banking institution in a short period of time.
Owner:TAYLOR MICHAEL K
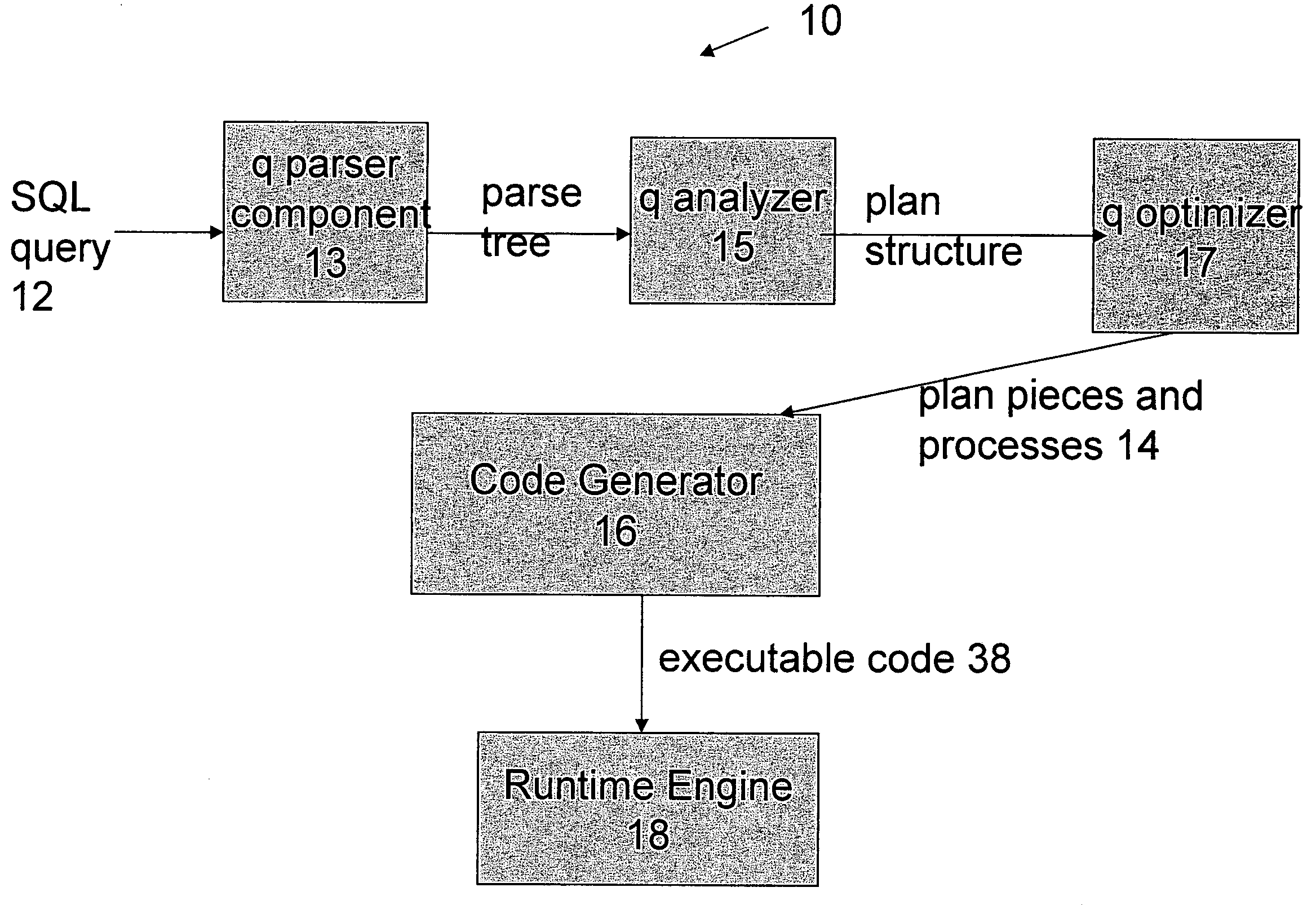
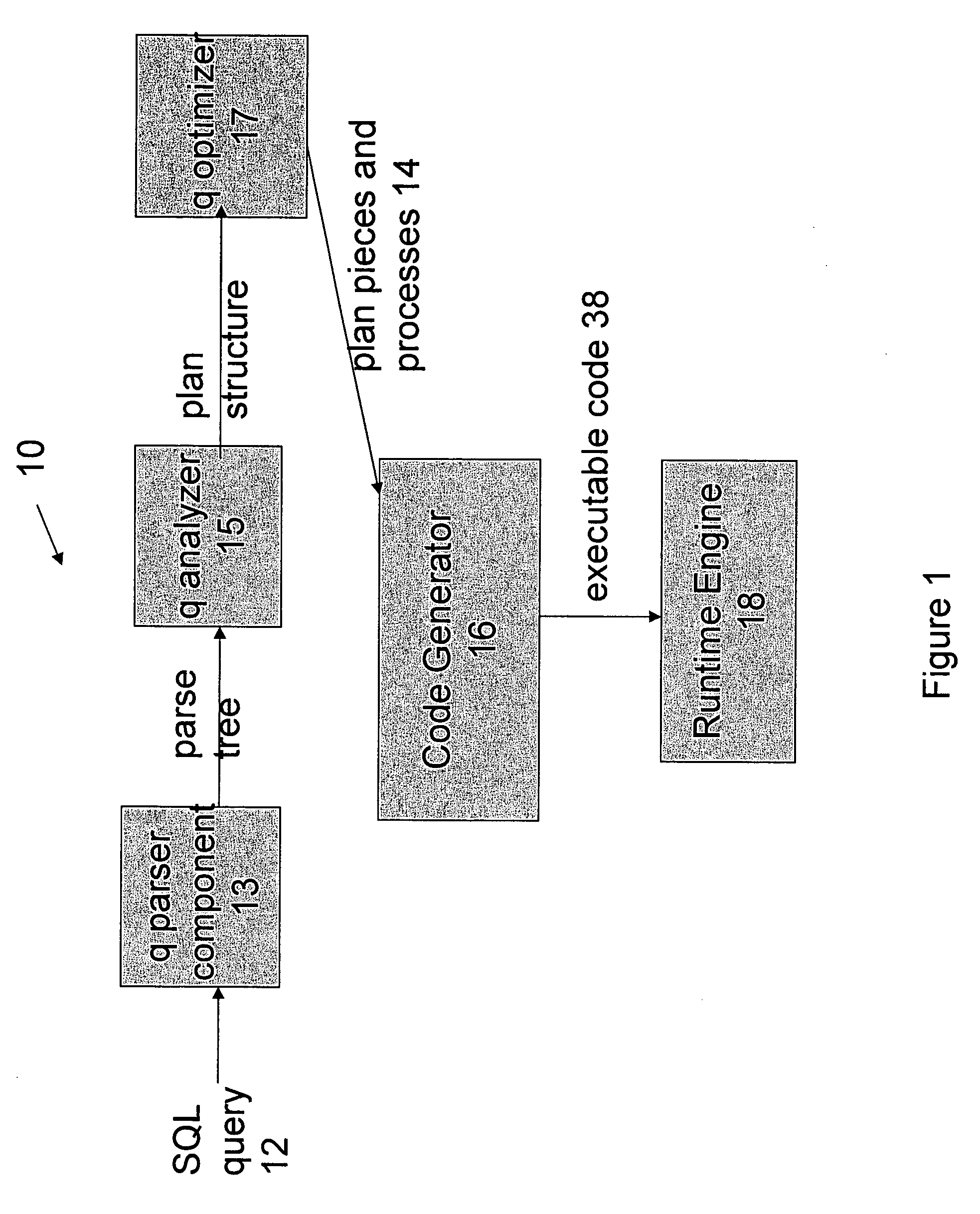
Optimized SQL code generation
ActiveUS20050027701A1Reduce and minimize compilation timeReduce and minimize execution timeDigital data information retrievalData processing applicationsExecution planSQL
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. The present invention provides a method for generating executable machine code for query execution plans, that is adaptive to dynamic runtime conditions, that is compiled just in time for execution and most importantly, that avoids the bounds checking, pointer indirection, materialization and other similar kinds of overhead that are typical in interpretive runtime execution engines.
Owner:IBM CORP
Protective coating
InactiveUS20070197686A1Improve waterproof performanceImparts flexibility and ductilityFireproof paintsPigmenting treatmentInorganic particleInorganic particles
Fire-protective coatings comprising a water-soluble alkali metal silicate binder, at least one inorganic particulate material which endothermically releases a nonflammable gas in the presence of heat, and an inorganic filler and / or a polymeric binder are disclosed.
Owner:AMERICAN THERMAL HLDG CO
Physiological parameter management monitoring system and method based on internet of things
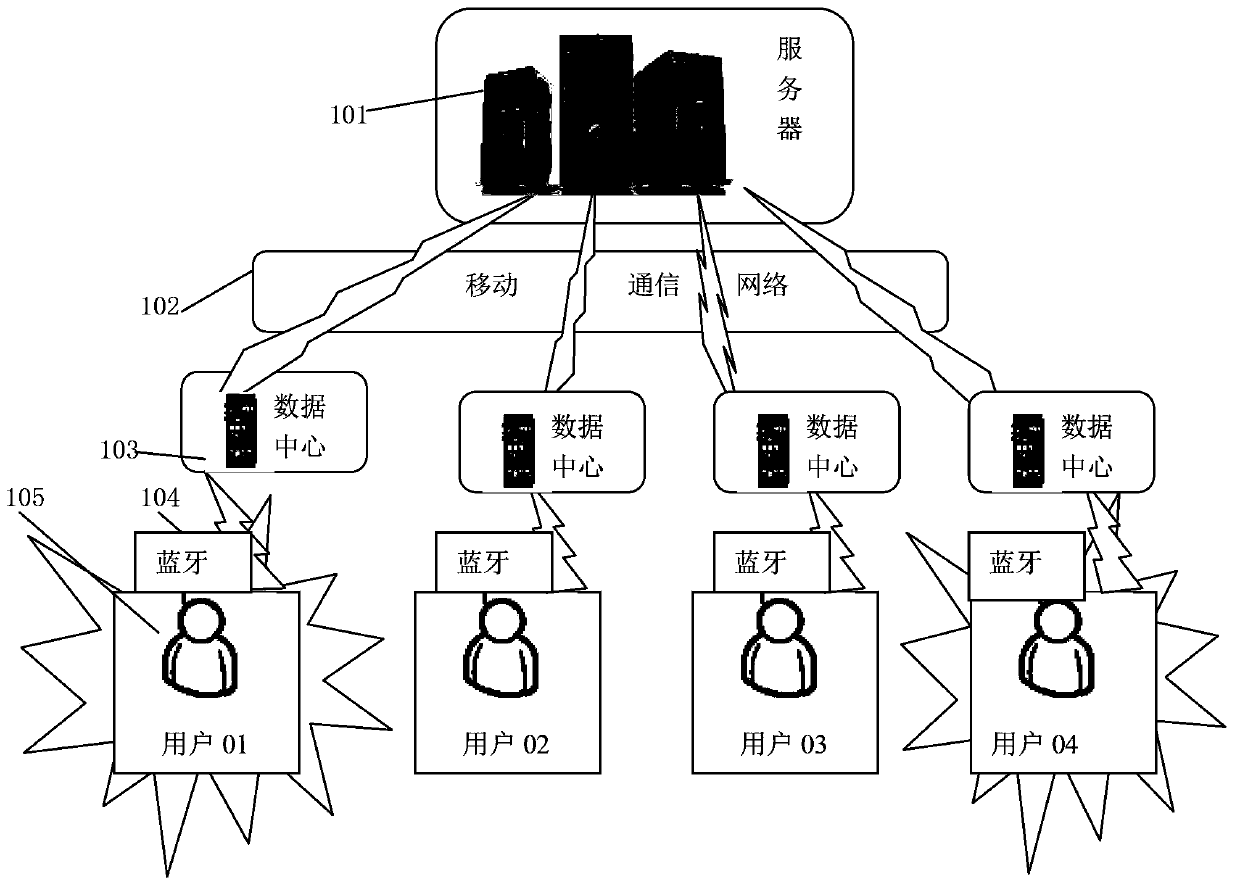
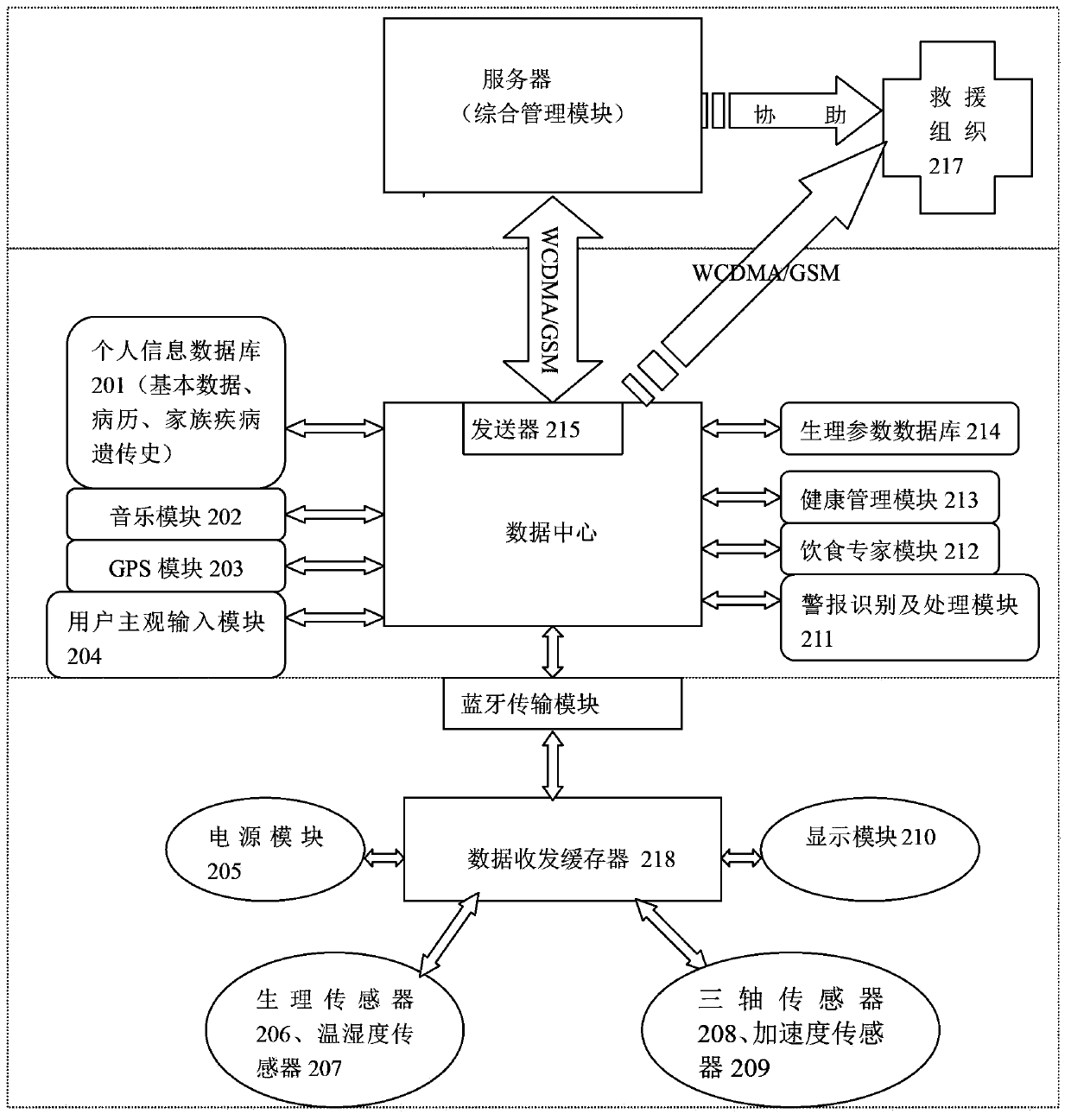
InactiveCN103417195AAccurately grasp the physical condition in real timeAvoid checkingTransmission systemsDiagnostic recording/measuringData centerThe Internet
The invention discloses a physiological parameter management monitoring system and method based on the internet of things. The system comprises a user terminal device worn on a tested object, a data center and a server for achieving physiological parameter management monitoring. The user terminal device is connected with the data center through a bluetooth transmission module in a data communication mode, and the data center is connected with the server through a wireless network in a data communication mode. Physical conditions of the tested object are detected and managed in real time through the internet of things, a physiological parameter sensor collects physiological data periodically and transmits the physiological data to the data center through the bluetooth transmission module, and the data is processed, handled, stored and transmitted to a mobile communication network to be managed and monitored by the server. According to the system and method, the device worn on the tested object is simple and low in cost and power consumption, can monitor the physical conditions of the tested object in real time and is intelligent and good in practicality.
Owner:JIANGSU UNIV
Using security levels to improve permission checking performance and manageability
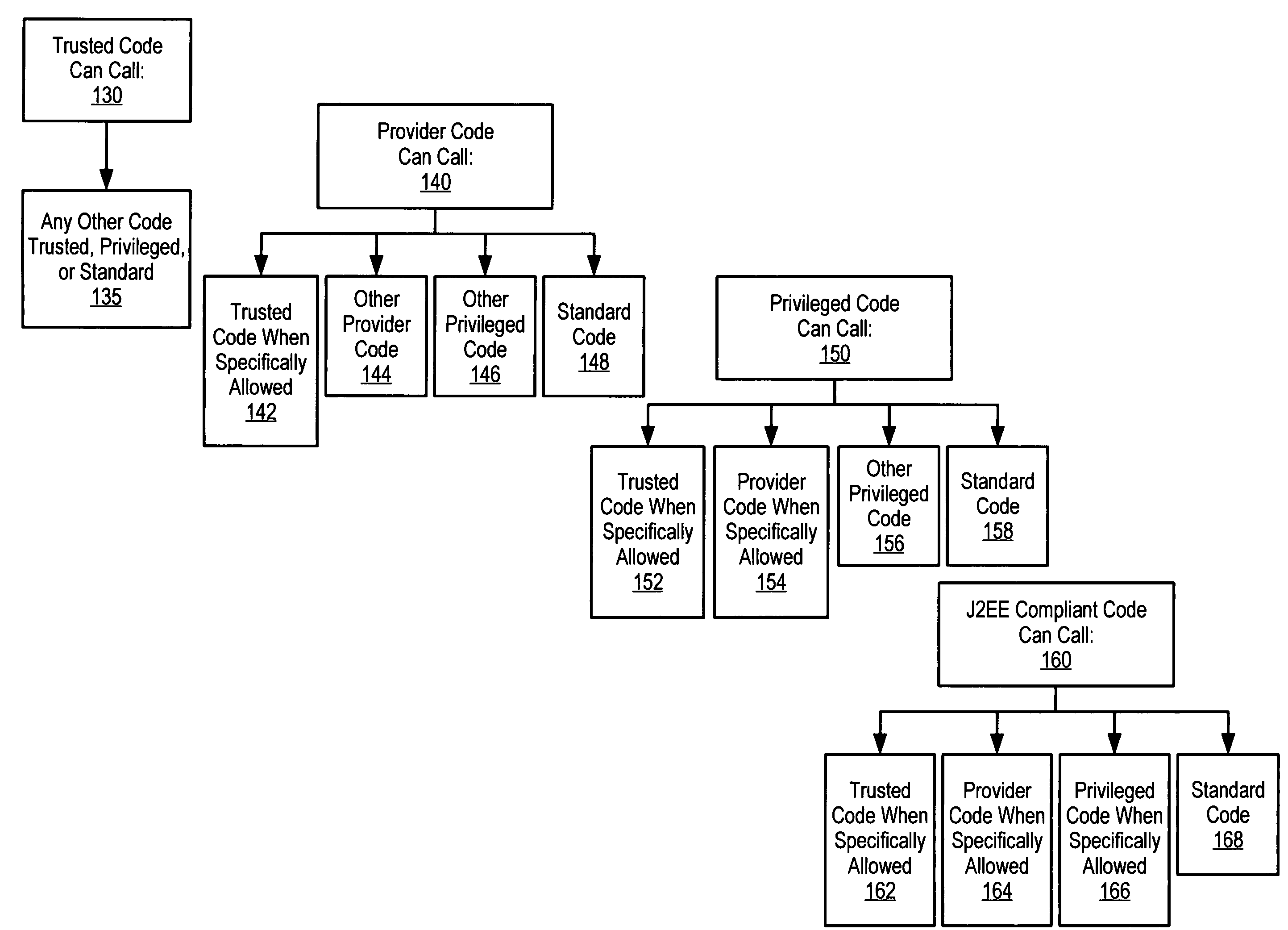
InactiveUS7475431B2Improve performanceAvoid checkingDigital data processing detailsAnalogue secracy/subscription systemsComputer hardwareSecurity level
Complexity is reduced and performance is improved when enforcing security restrictions on the execution of program code in a runtime environment. Units of executable code, such as methods or functions, are classified by “security level.” Code units belonging to a “trusted” security level may call any other code unit in the runtime environment, but other security levels are restricted in the code units they can call. Code units may also have “instance permissions” to allow them to have permission to call other individually-specified code units that they would normally be precluded from calling, due to their security level. The security level scheme described herein reduces the complexity of establishing permissions with respect to different code units in the runtime environment. This security level scheme also improves runtime performance by making it unnecessary to check individually-defined permissions in many cases.
Owner:INT BUSINESS MASCH CORP
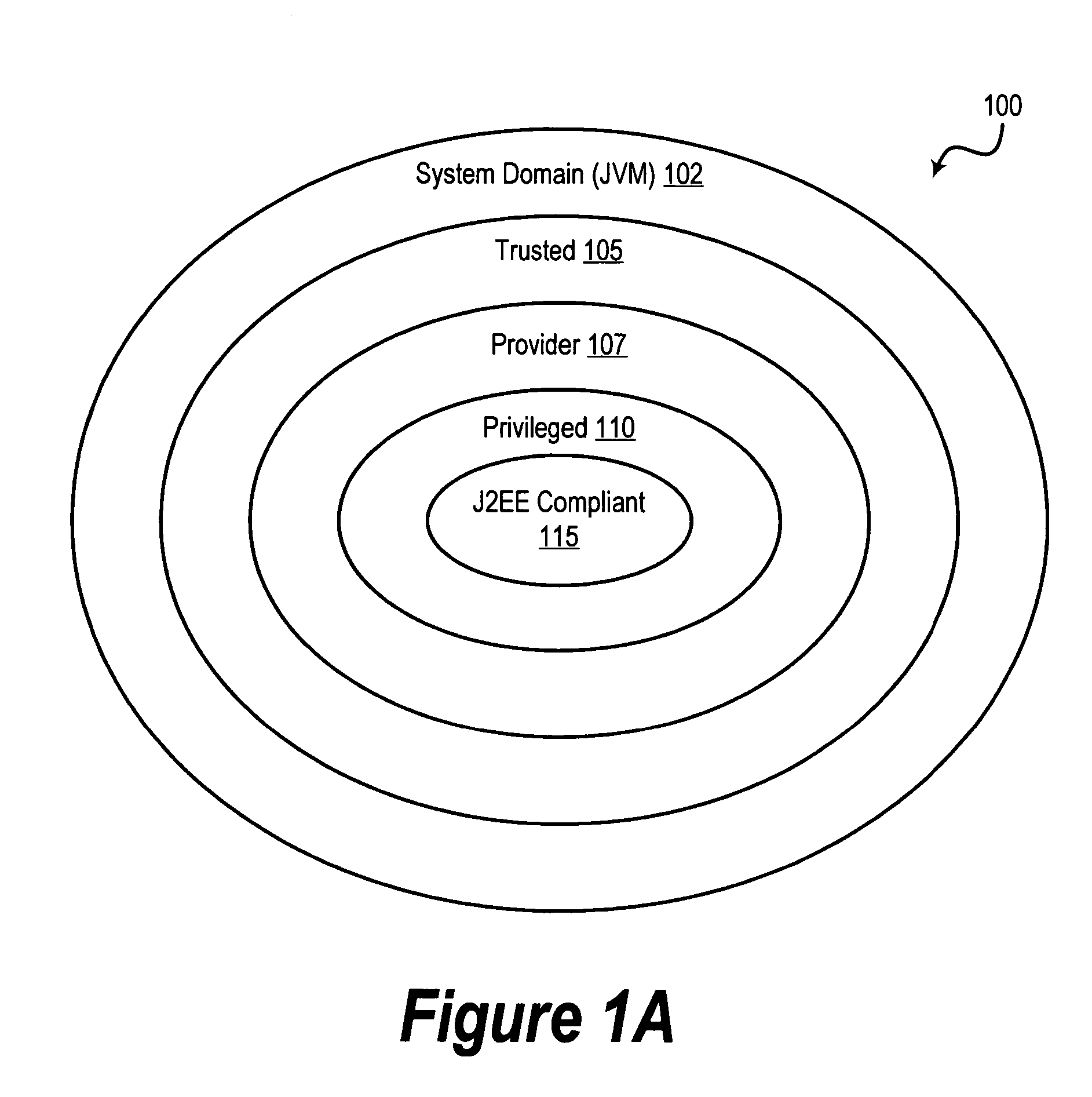
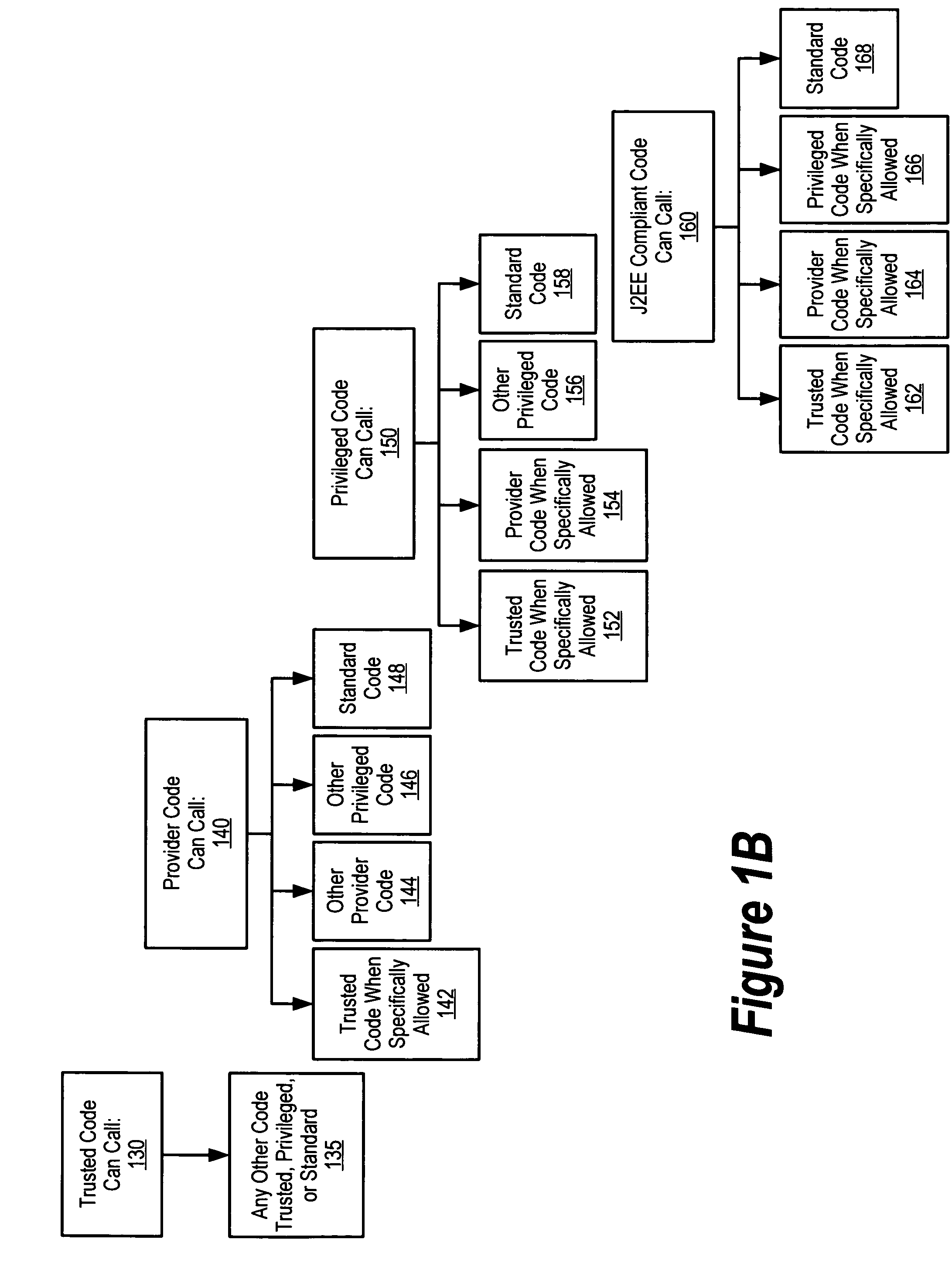
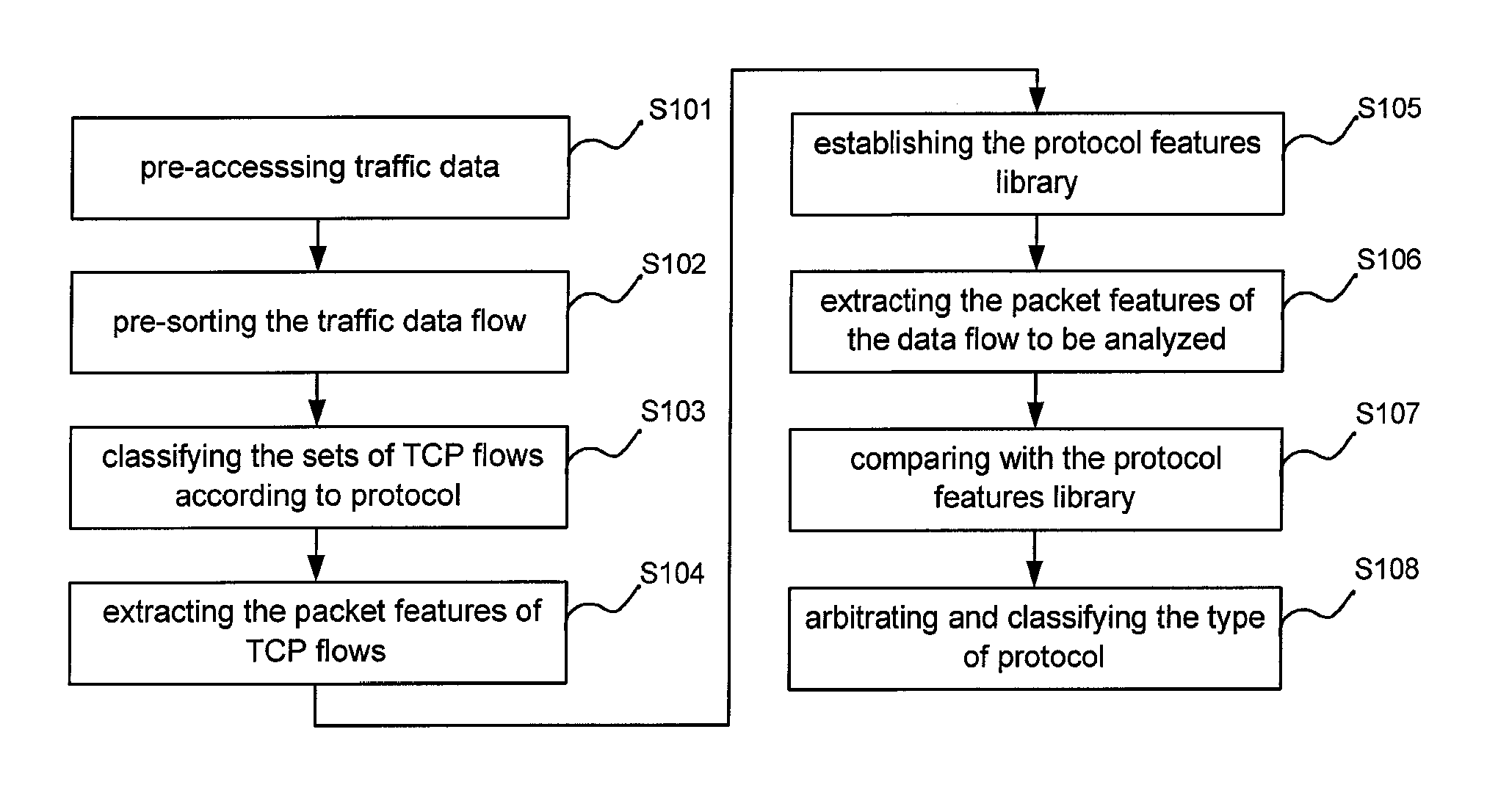
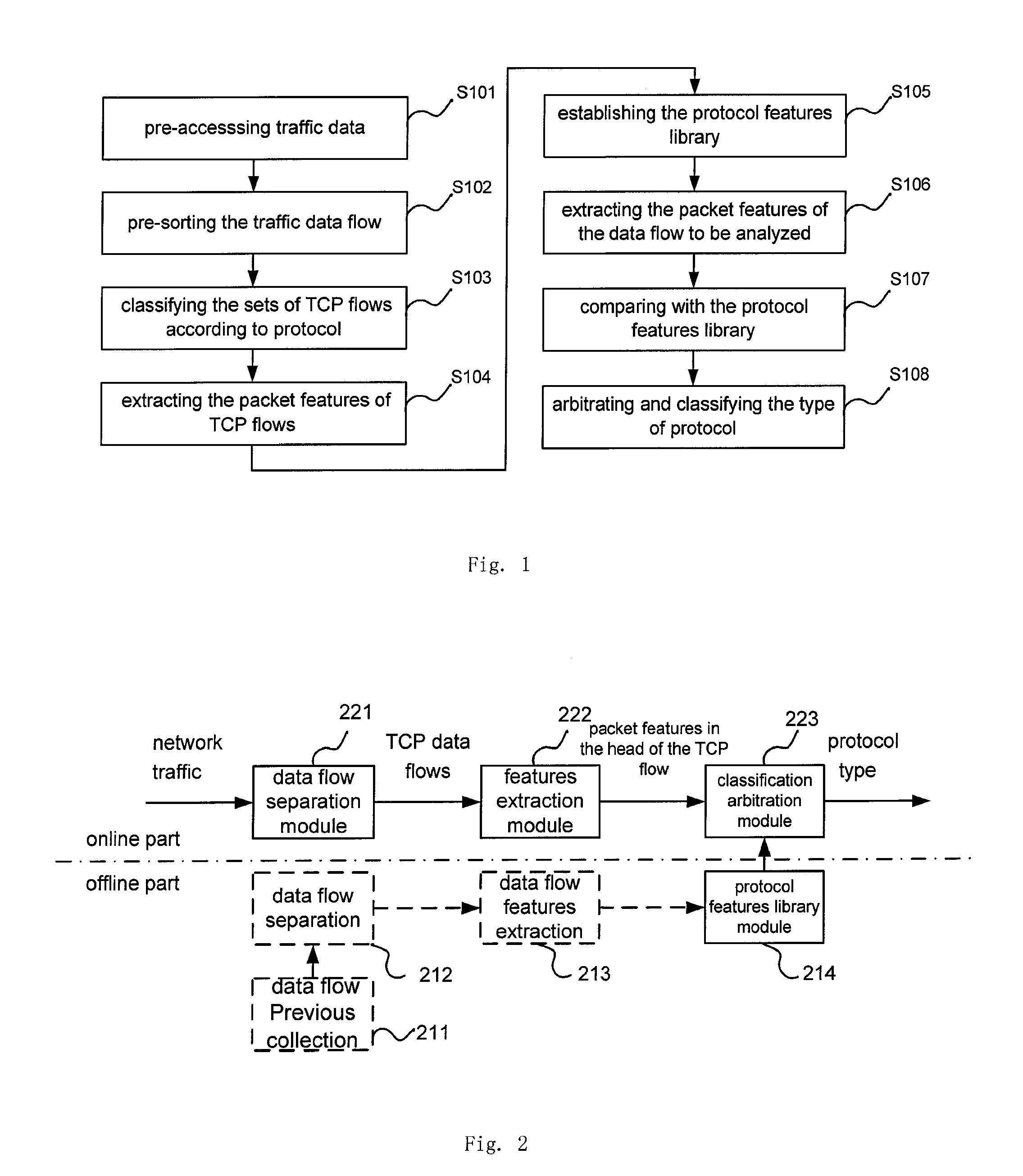
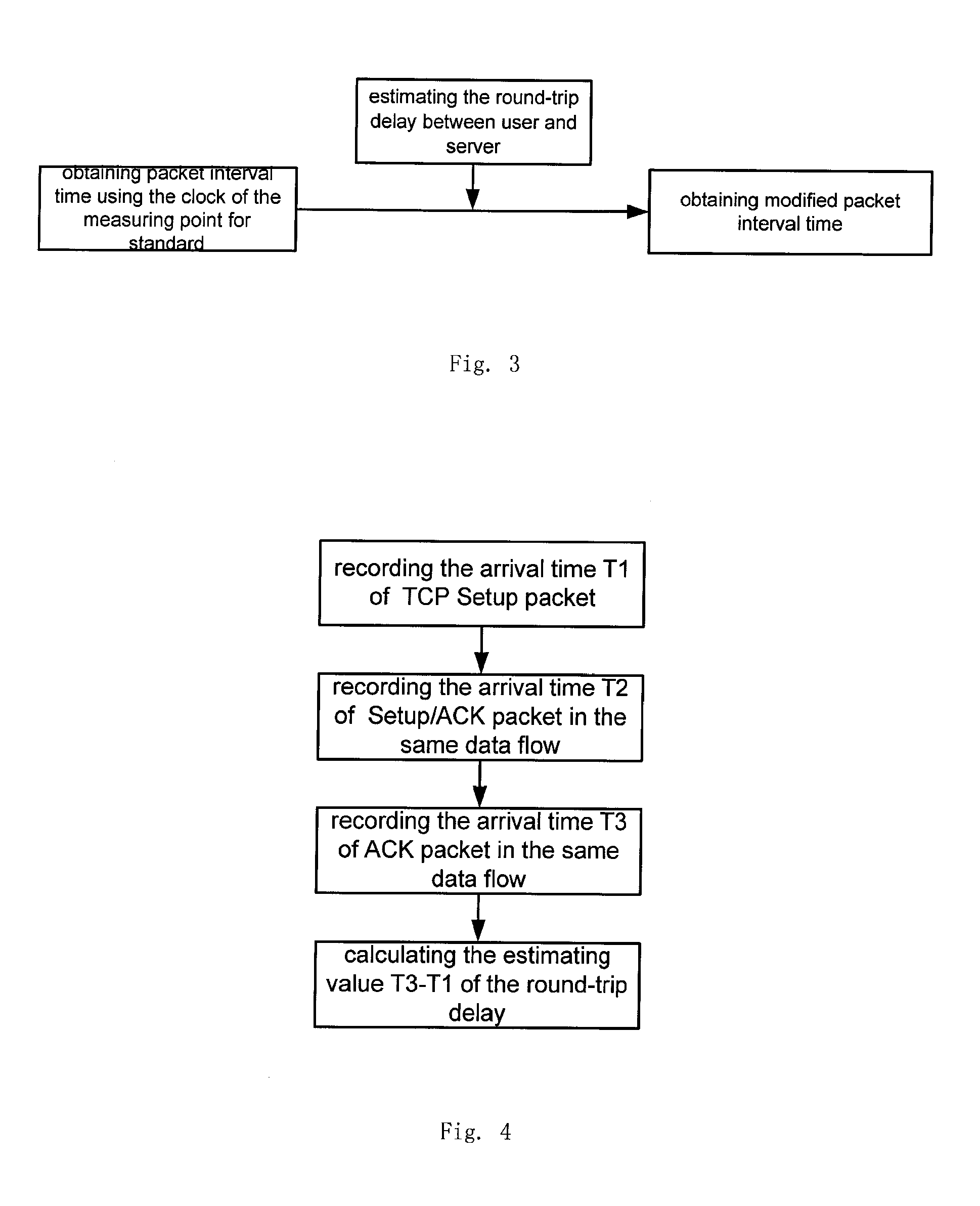
Method and its devices of network TCP traffic online identification using features in the head of the data flow
InactiveUS20120099465A1Avoid checkingEasy to identifyError preventionTransmission systemsTraffic volumeTraffic capacity
Owner:BEIJING UNIV OF POSTS & TELECOMM
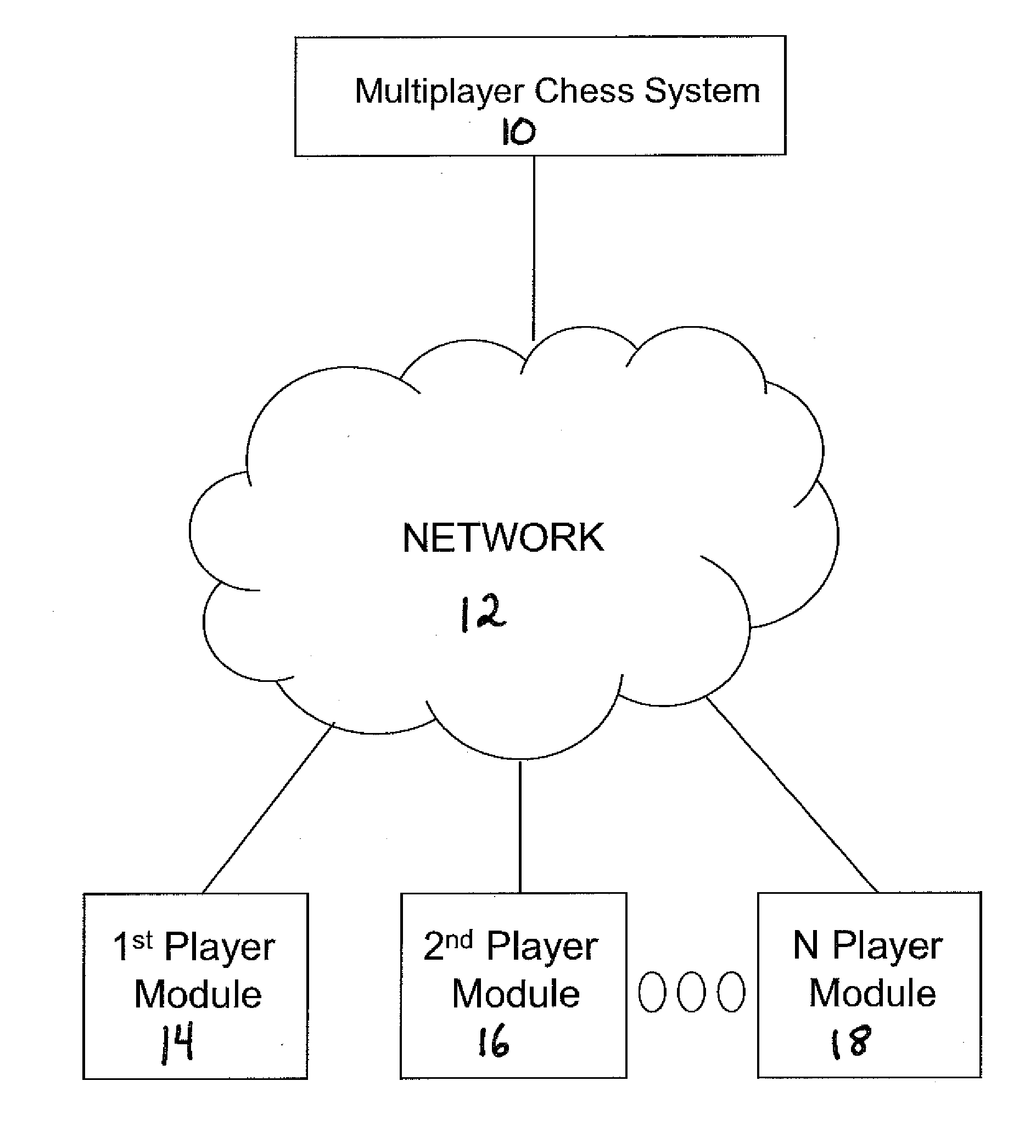
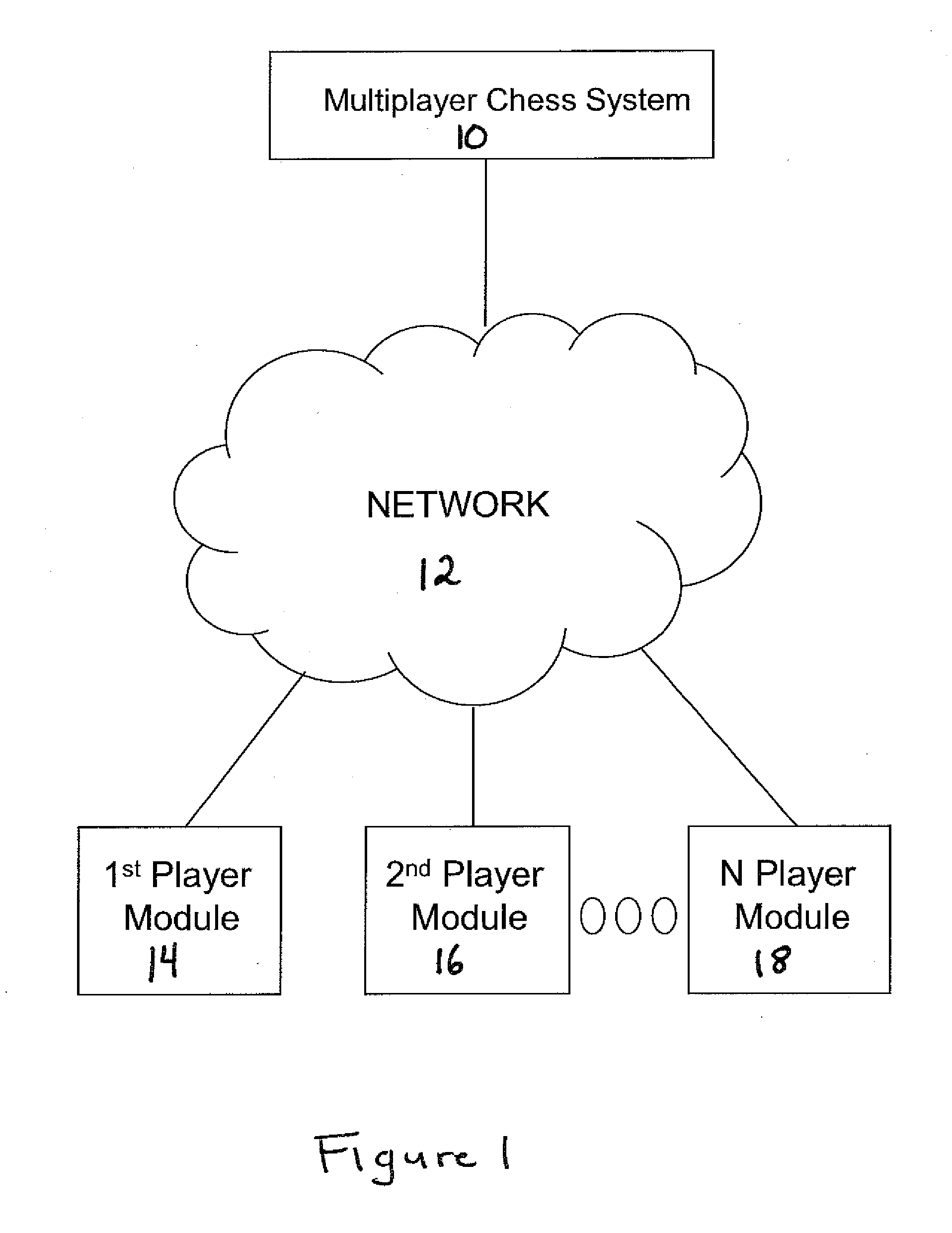
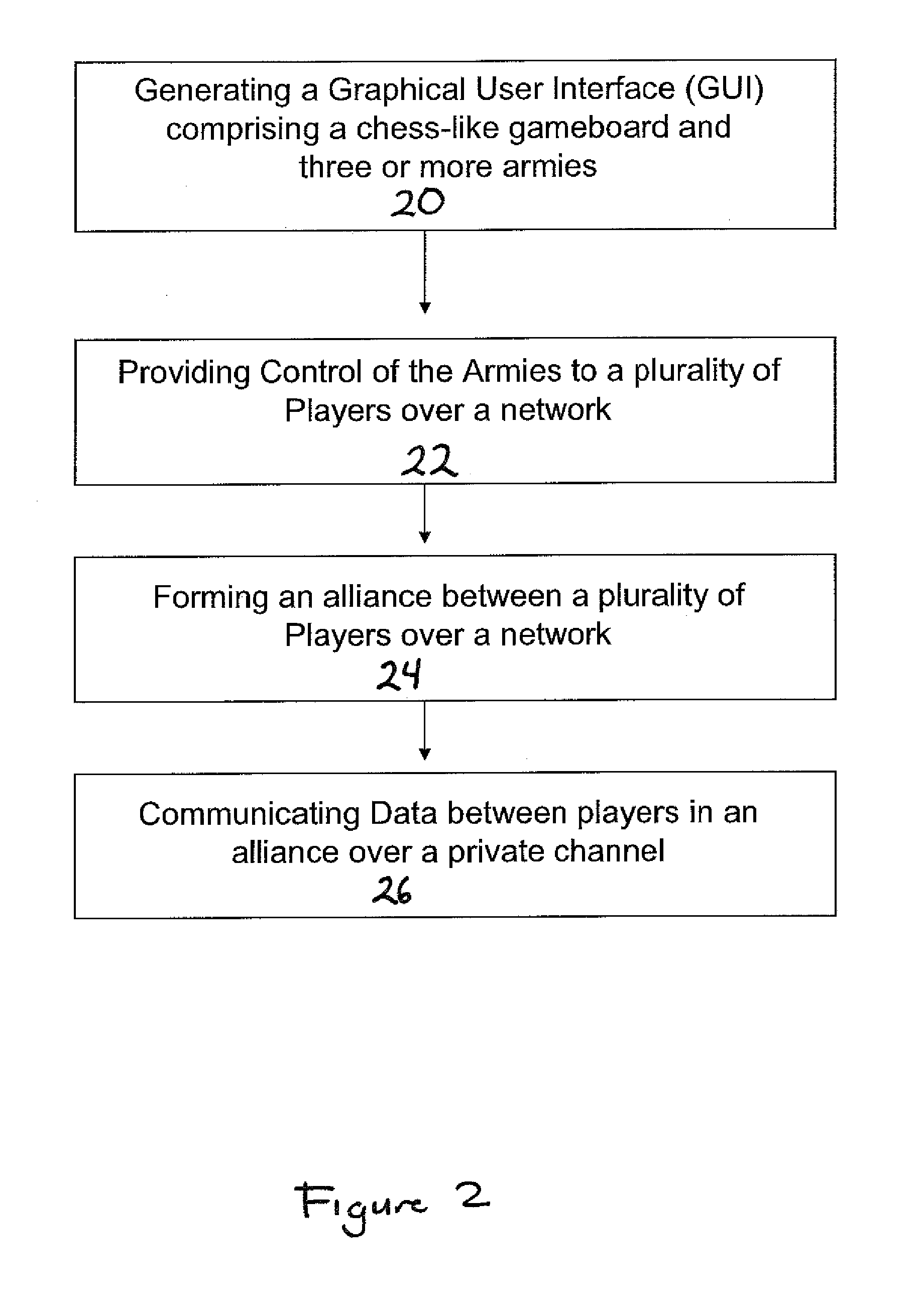
System and method for playing chess with three or more armies over a network
InactiveUS20080045343A1Avoid captureAvoid checkingBoard gamesApparatus for meter-controlled dispensingGraphicsGraphical user interface
A system and method for playing chess with three or more armies over a network comprising the steps of: generating a graphical user interface, according to a first mode, including: a virtual gameboard including a plurality of substantially square-shaped playing spaces; a first, second and third army; wherein the first army, the second army, and the third army are associated with the plurality of substantially square-shaped playing spaces; providing control of the first, second, and third armies to one or more players over a network; forming an alliance according to a second mode among players. The system and method further comprise altering the rule of game play upon the formation of an alliance between the first player and the second player.
Owner:SAUBERMAN HERMINA
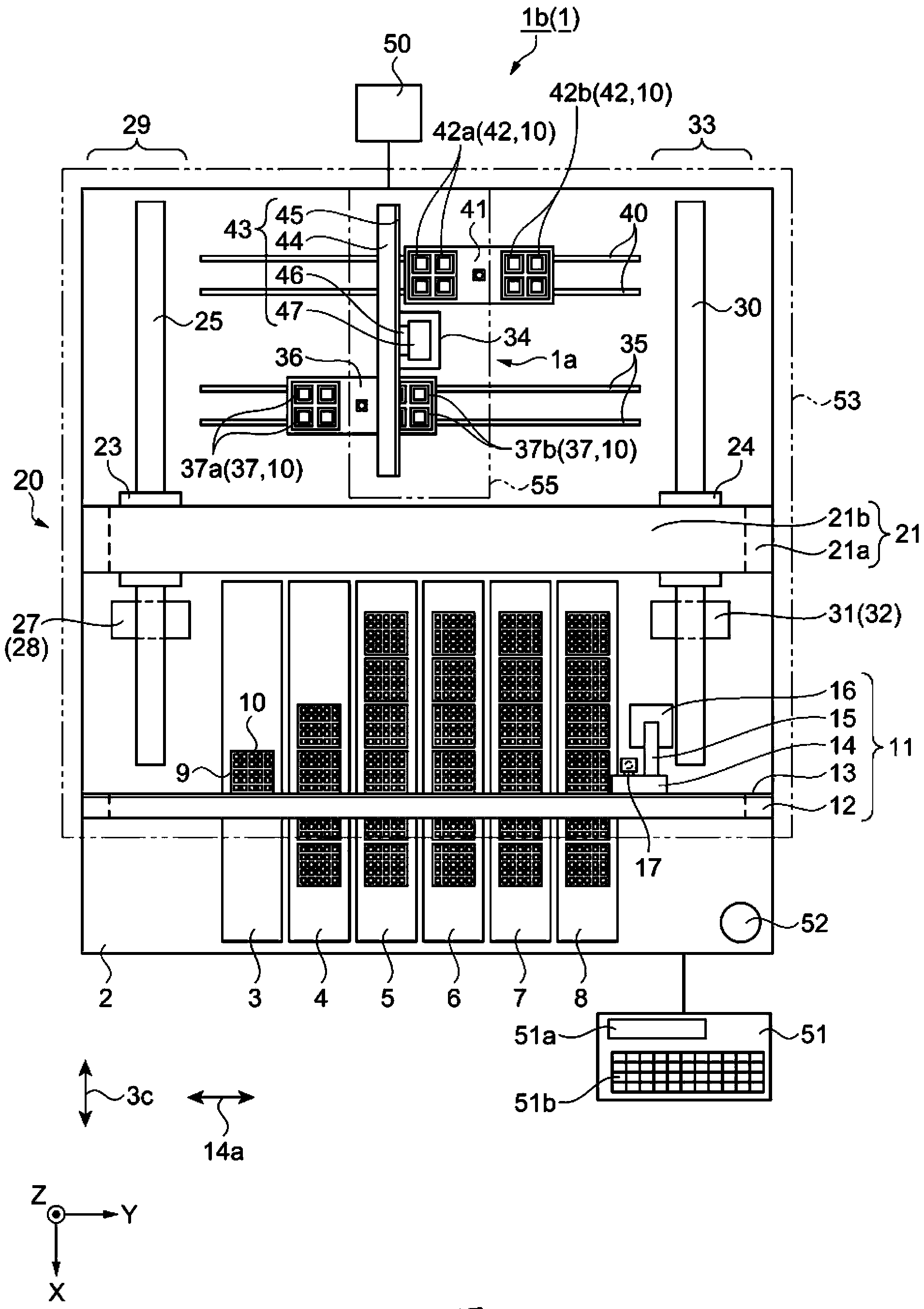
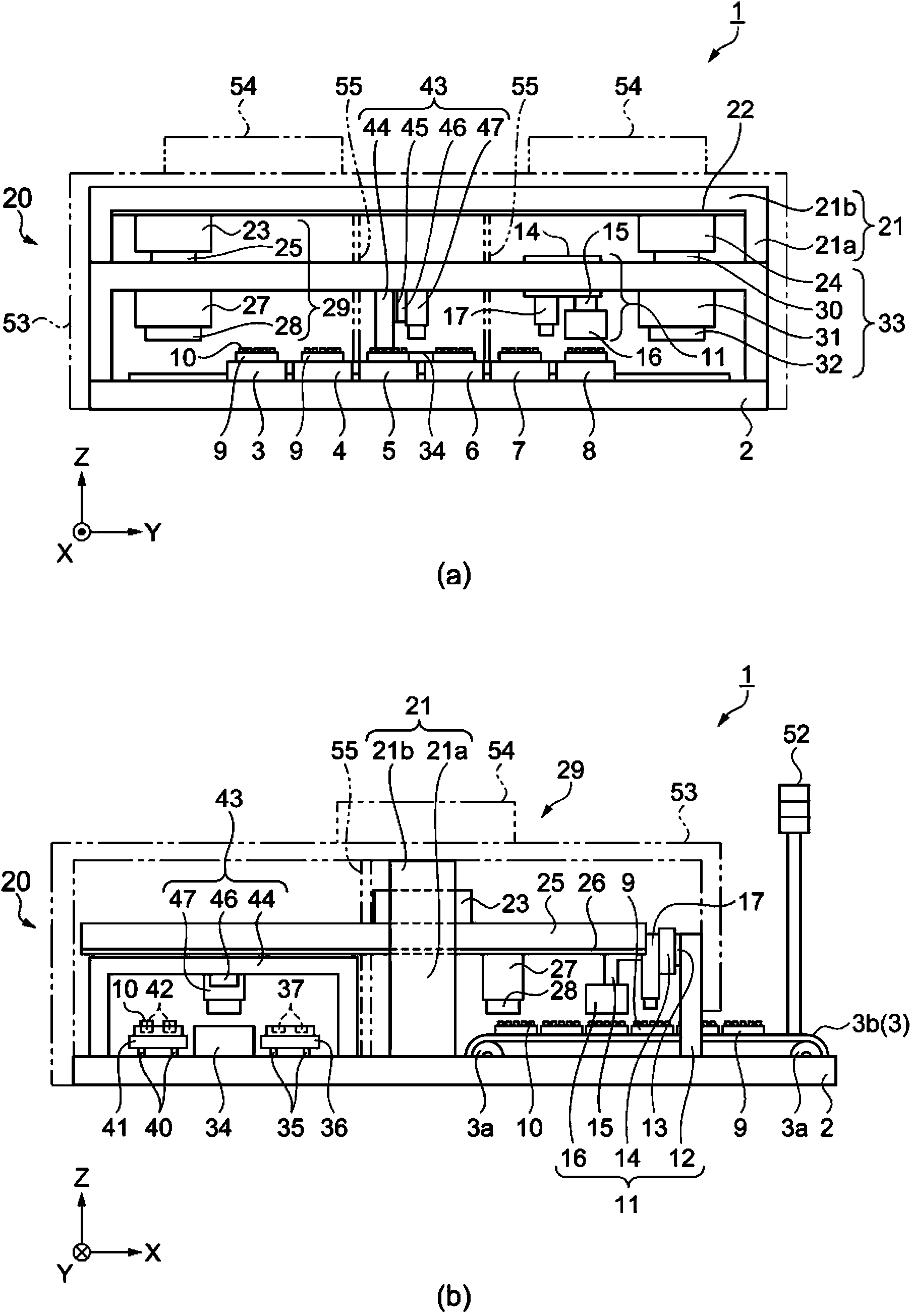
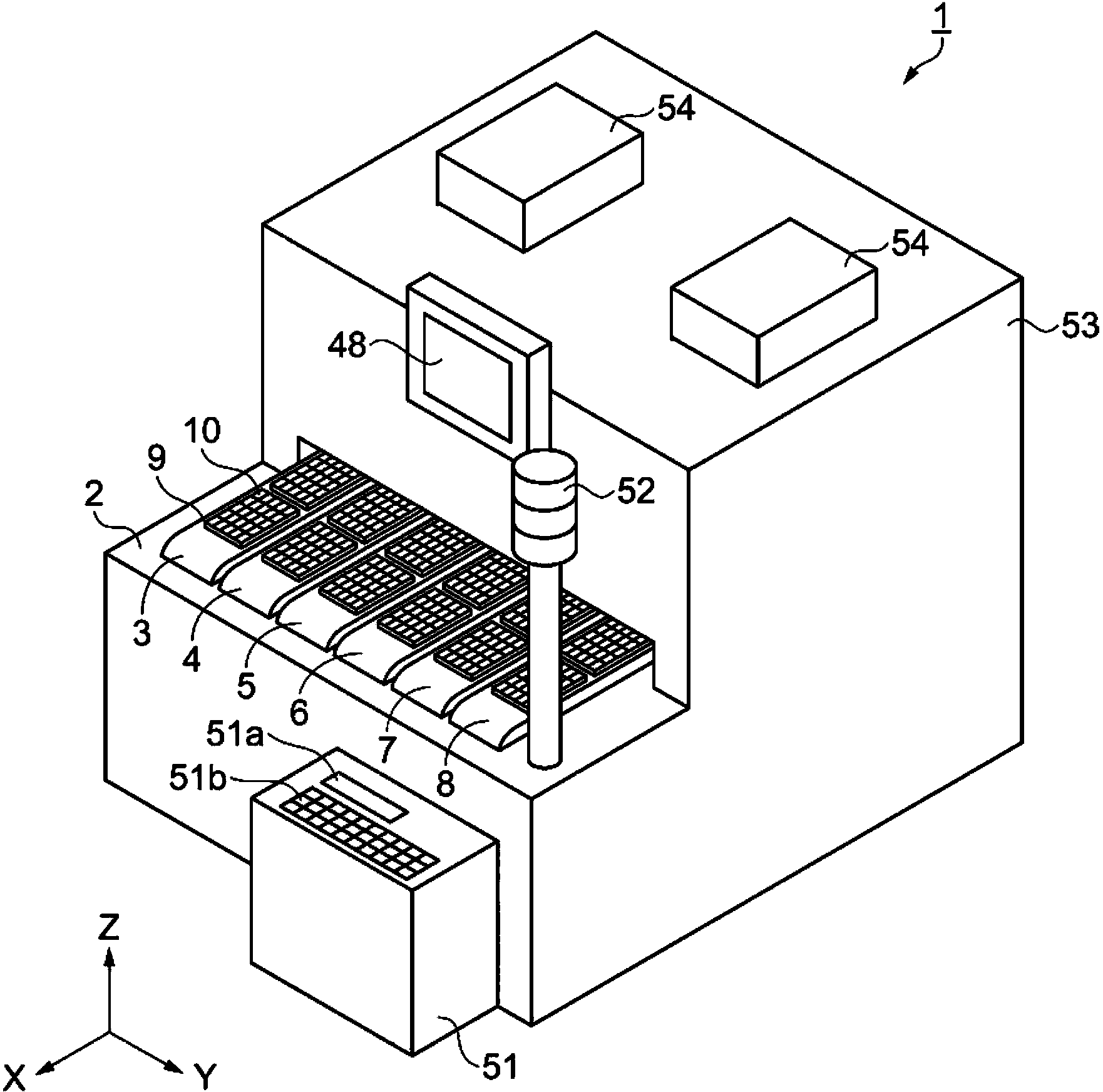
Electronic component carrying device and electronic component testing device
InactiveCN103569624AAvoid checkingControl devices for conveyorsCharacter and pattern recognitionEngineeringElectronic component
The present invention provides an electronic component carrying device and an electronic component testing device. The electronic component carrying device has: a first conveyor for enabling a tray carrying an electronic component to move along a first direction; a shooting device for detecting an individual recognition number arranged on the electronic component; a tray carrying part for enabling the shooting device to move along a second direction crossed with the first direction; and an individual recognition number operating part for using the individual recognition number to operate recognition information of the electronic component.
Owner:SEIKO EPSON CORP
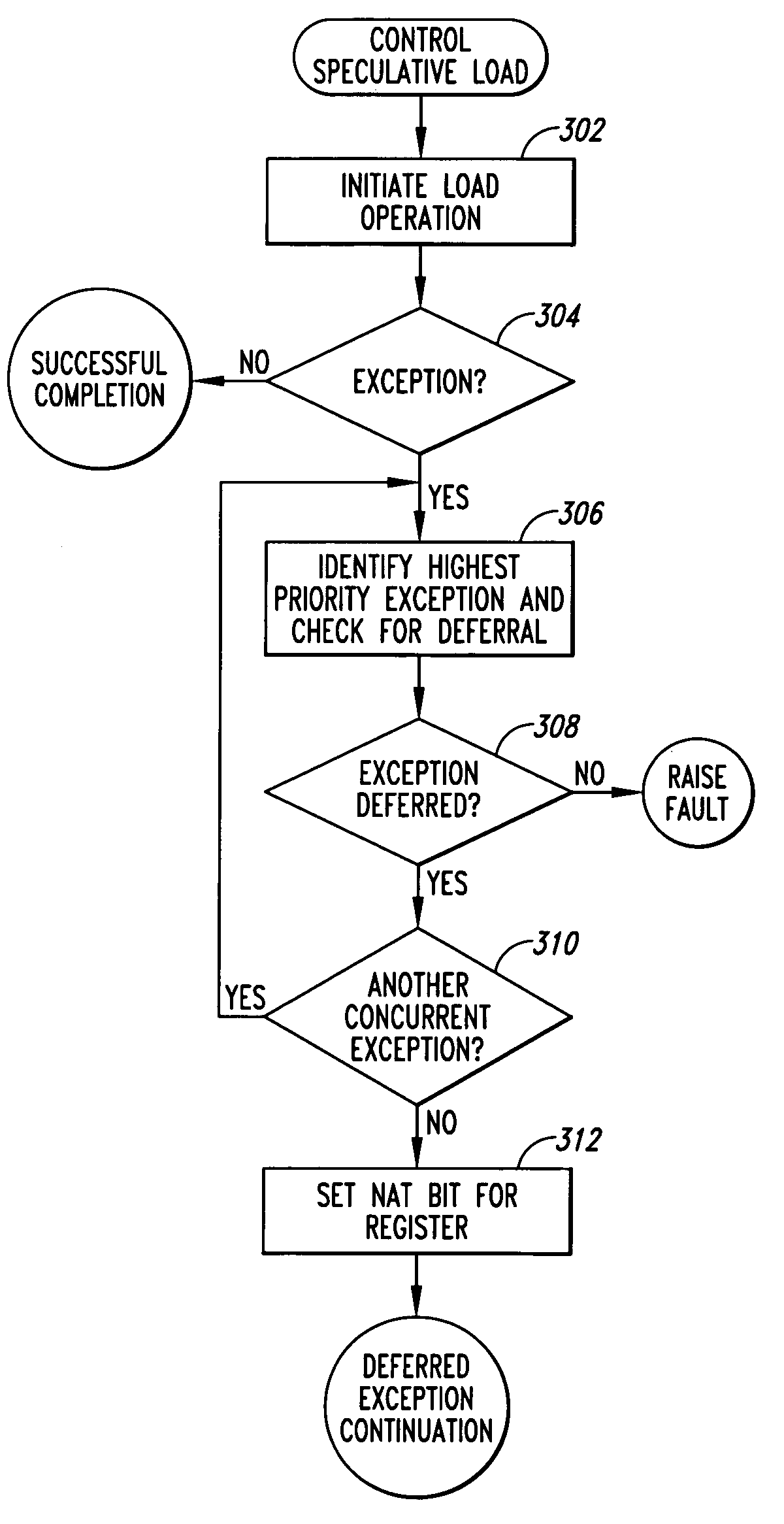
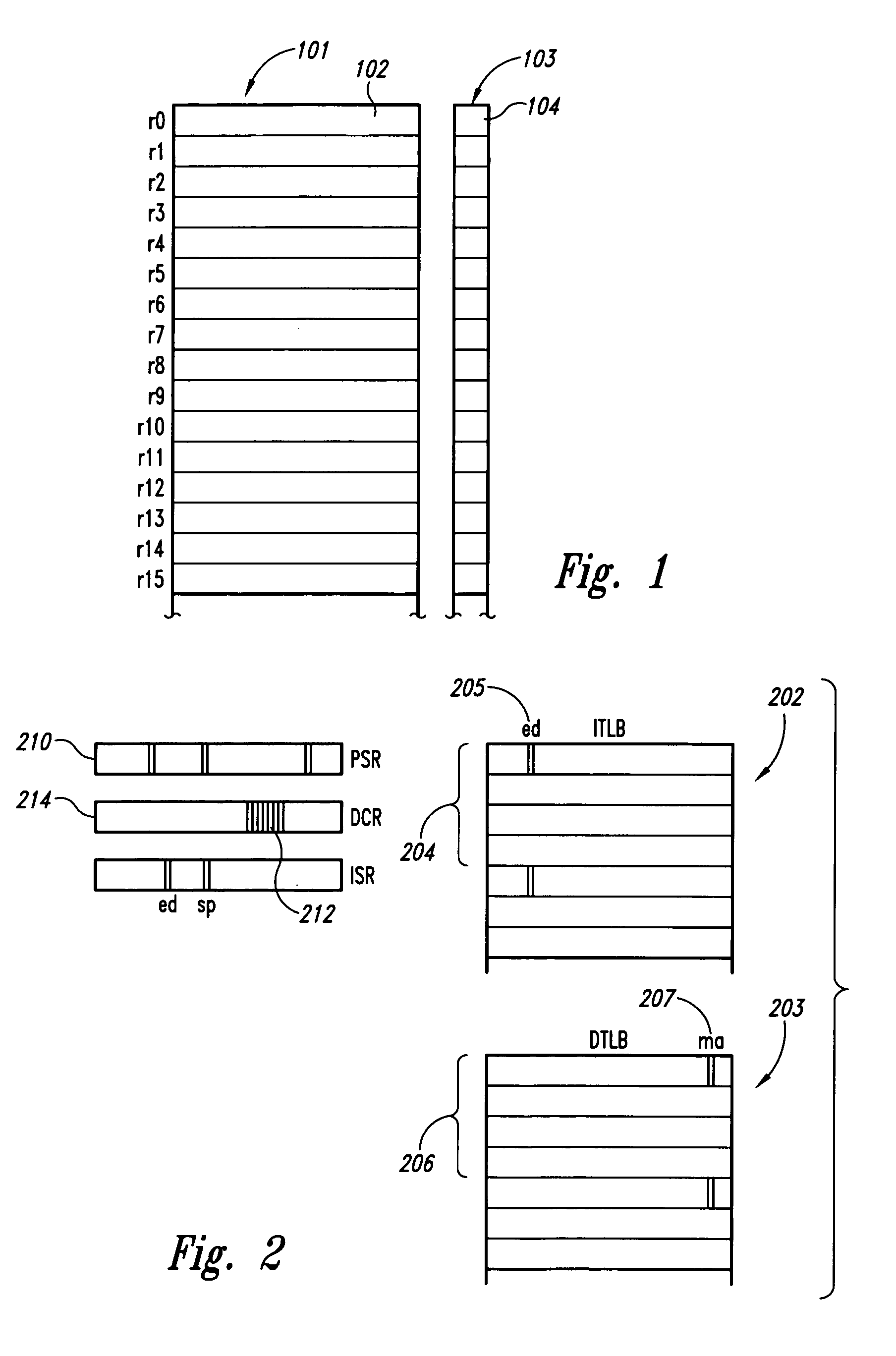
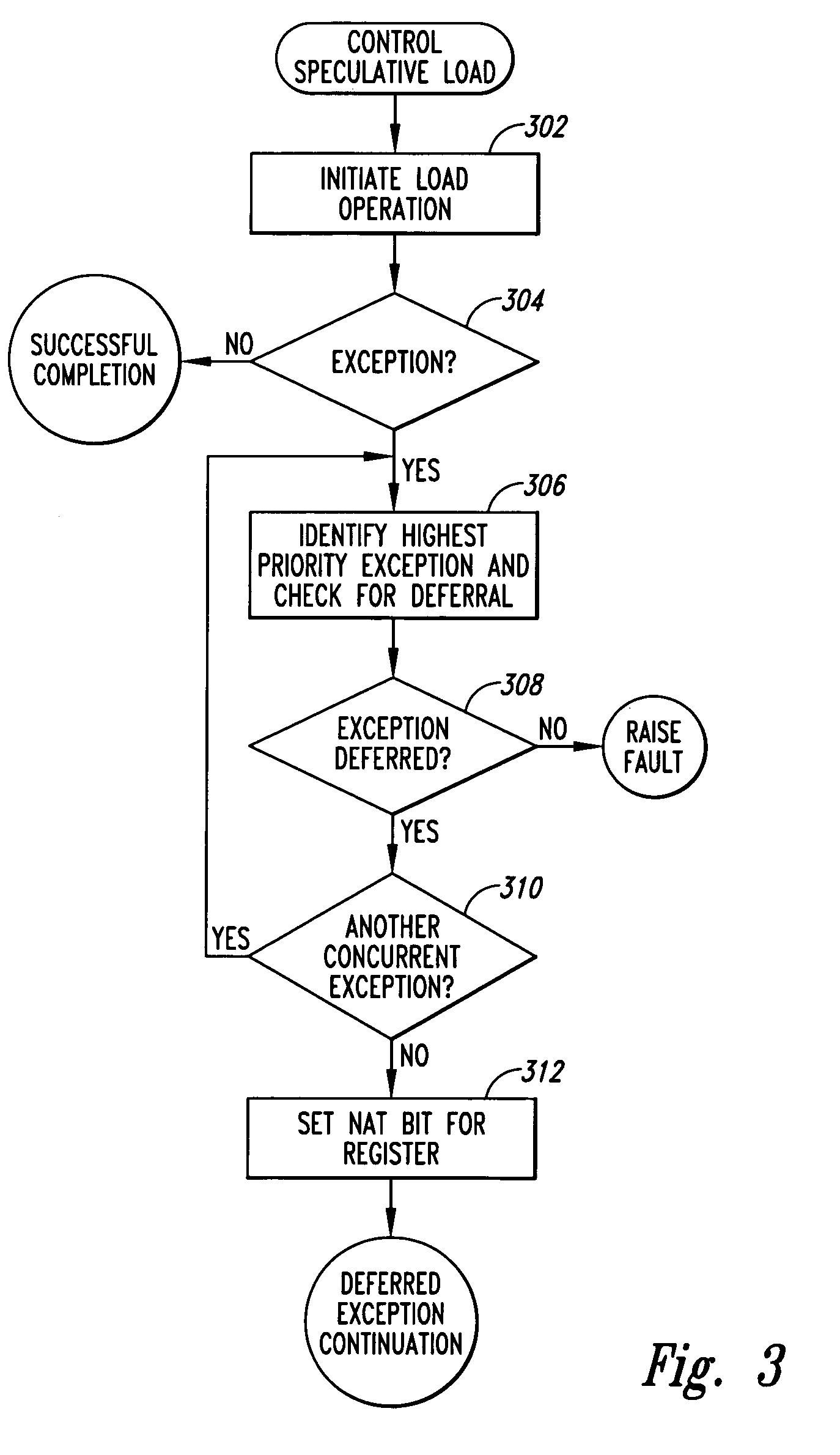
Method and system for using machine-architecture support to distinguish function and routine return values
ActiveUS7051238B2Avoid checkingError preventionError detection/correctionGeneral purposeLoad instruction
A method and system for nearly immediately trapping a failure-to-check-a-return-value error in a computer program. Modern processor architectures, such as the Intel® IA-64 processor architecture, provide for control speculation of load instructions, including 1-bit NAT registers, associated with general registers, that indicate occurrences of deferred exceptions arising during execution of control-speculative load instructions targeting the corresponding general registers. One embodiment of the present invention employs the NAT registers associated with general-purpose registers to distinguish special values, often indicating error conditions, stored in general-purpose registers serving to store the return values of functions and routines.
Owner:VALTRUS INNOVATIONS LTD +1
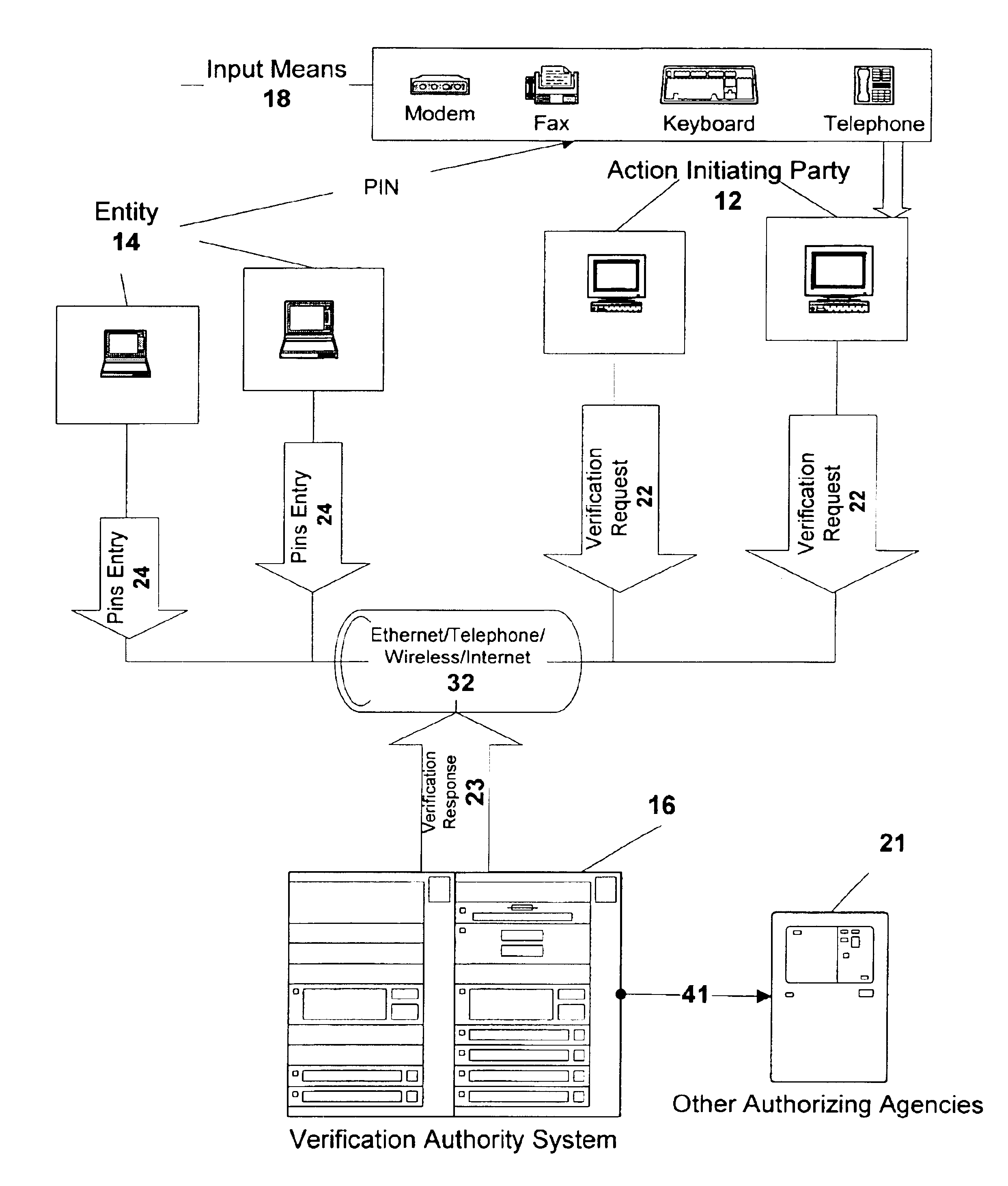
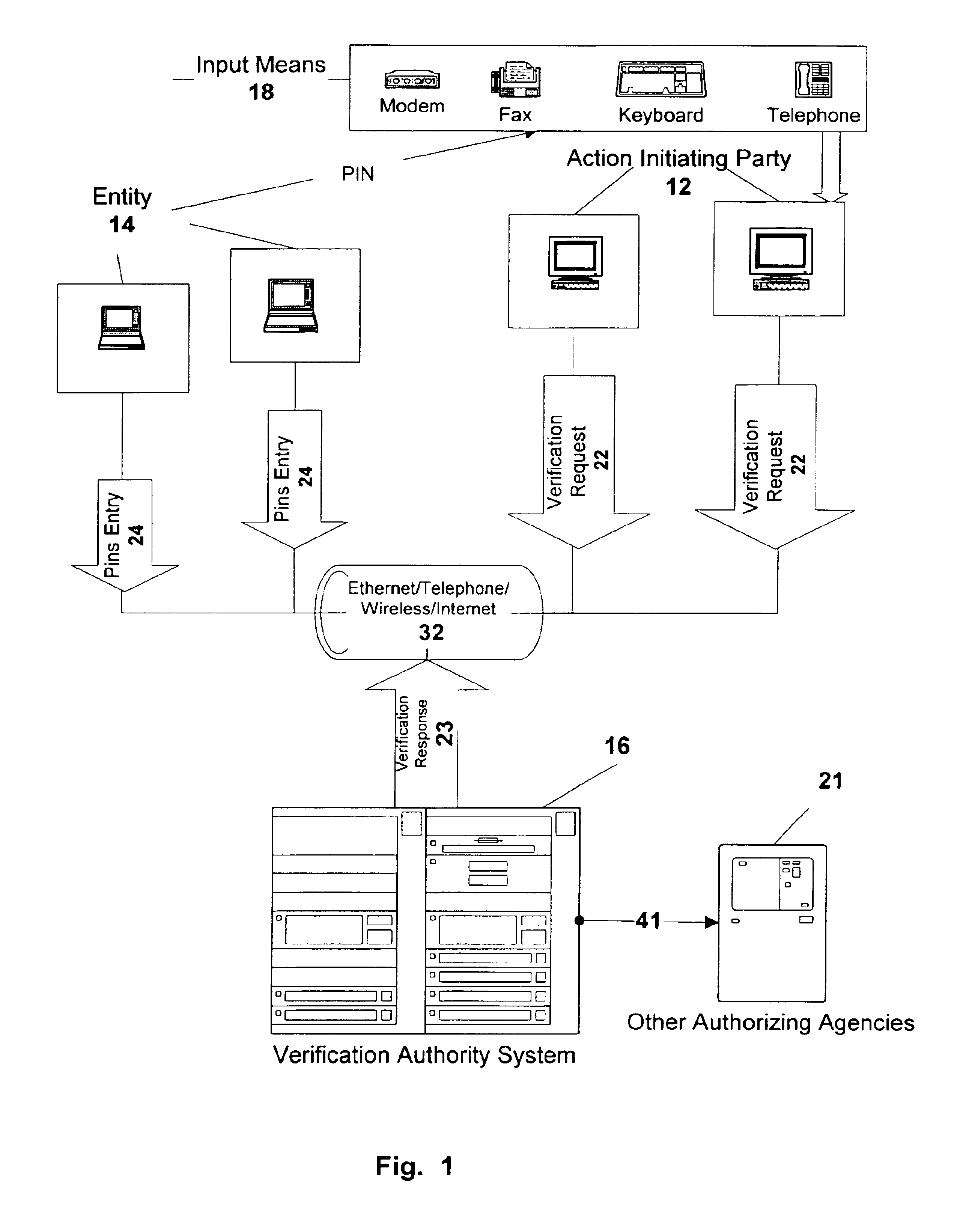
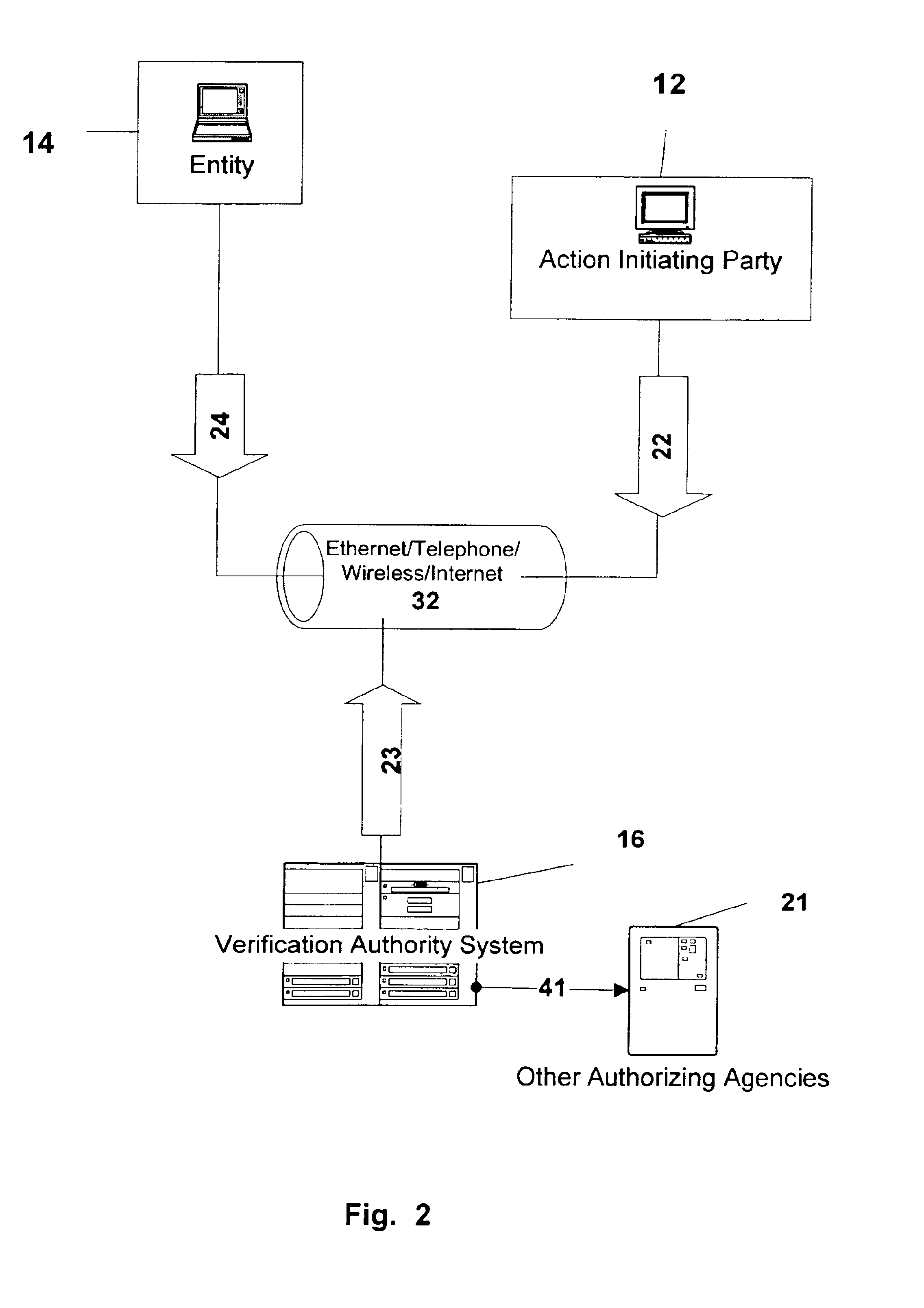
Action verification system using central verification authority
InactiveUS6954740B2Avoid checkingPublic key for secure communicationSecret communicationPersonal identification numberE-commerce
Architecture for central e-commerce authorization and verification using multiple Keys / Pins storage and central action verification means. Action Verification is provided between Action Initiating Party (12) and a central Verification Authority (16), wherein action includes a transaction, message, command, approval, identification request, financial transaction and data transmittal. Wherein action is authorized and initiated by an Entity (14) which can be an individual, company, vendor or other organization, which authorizes by giving a PIN, the execution, processing or delivering of an action. The action can be requested and / or transmitted and / or delivered electronically or mechanically. Verification information is stored in a Verification Authority system, accessed by Entities and the Action Initiating parties. The Entity stores in the Verification Authority sets of Personal Identification Numbers (PINS / Keys), and as a verification option, personal data parameters. The Entity is also able to generate automatically multiple Entity PINs / Keys. Verification includes validation of Entity's identity and the authorization of an action by comparing action PINs / Keys to a PIN / Key stored in the Verification Authority.
Owner:TALKER ALBERT ISRAEL
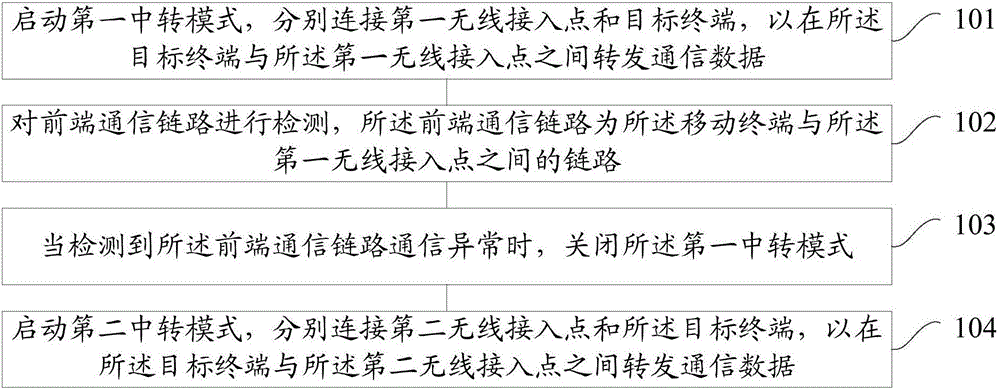
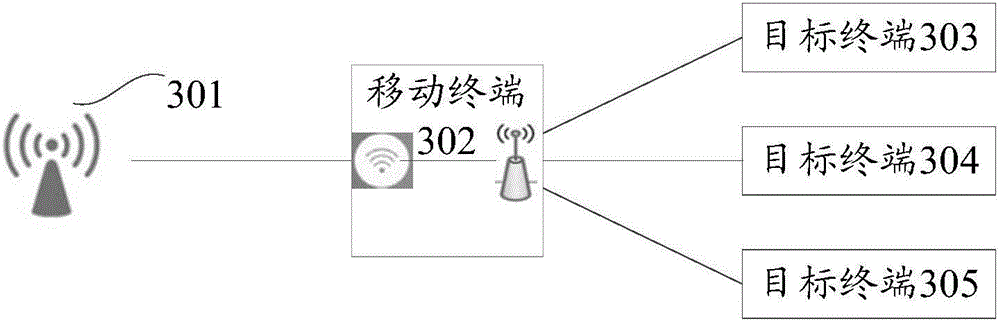
Link switching method and device
ActiveCN106535238AAvoid checkingLower technical barriersWireless communicationTelecommunicationsTelecommunications link
Embodiments of the present invention provide a link switching method and a device, wherein the method and the device are applied to a mobile terminal. The method comprises the steps of turning on a first transfer mode, and respectively connecting a first wireless access point with a target terminal so as to transmit communication data between the target terminal and the first wireless access point; detecting a front-end communication link, wherein the front-end communication link is a link between the mobile terminal and the first wireless access point; upon detecting the abnormal communication state of the front-end communication link, turning off the first transfer mode; turning on a second transfer mode, and respectively connecting a second wireless access point with the target terminal so as to transmit communication data between the target terminal and the second wireless access point. According to the embodiments of the invention, the anomaly detection and repair is automatically realized. Therefore, a user is prevented from manually checking the mobile terminal of a transfer node. The technical threshold is reduced and the convenience of operation is improved.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
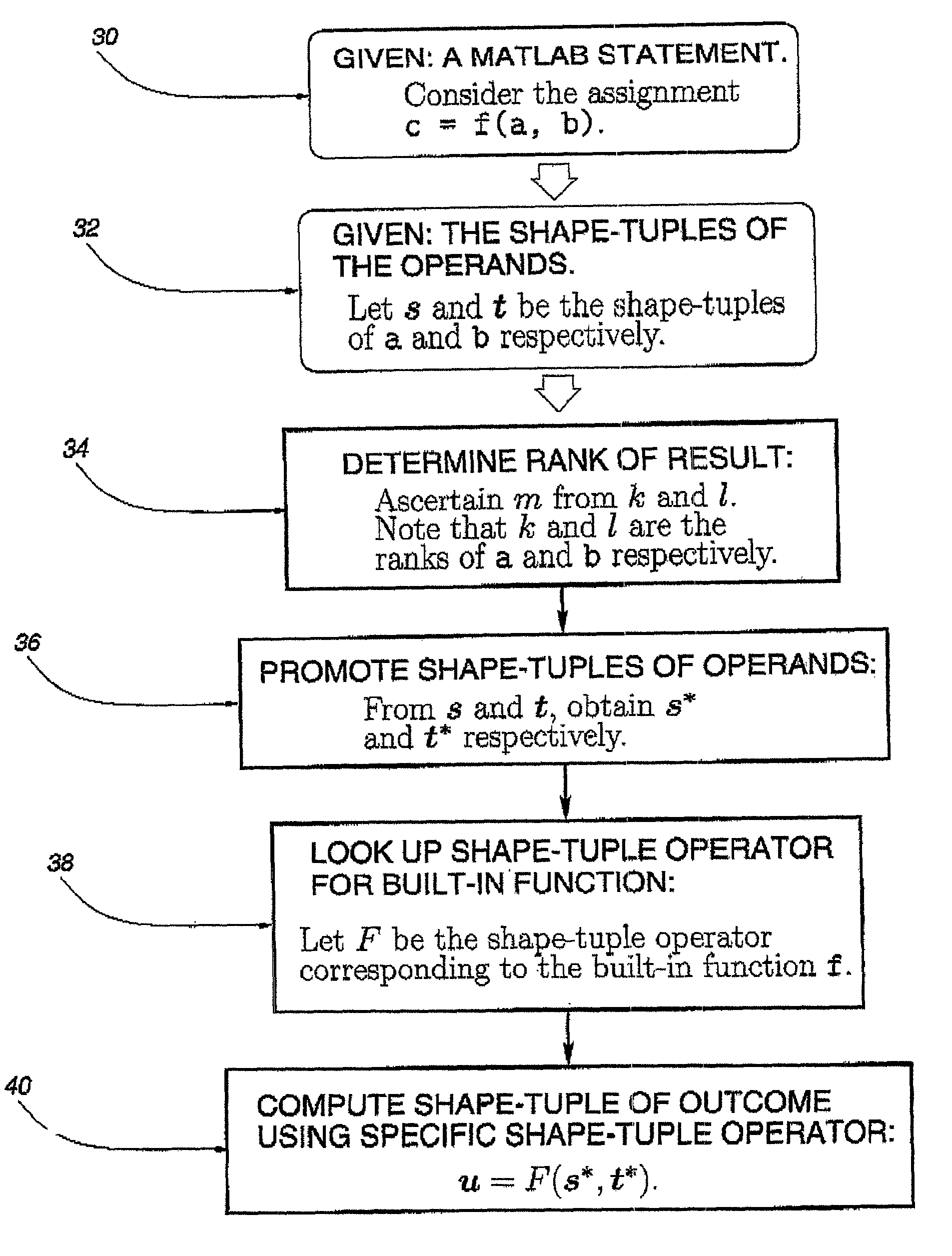
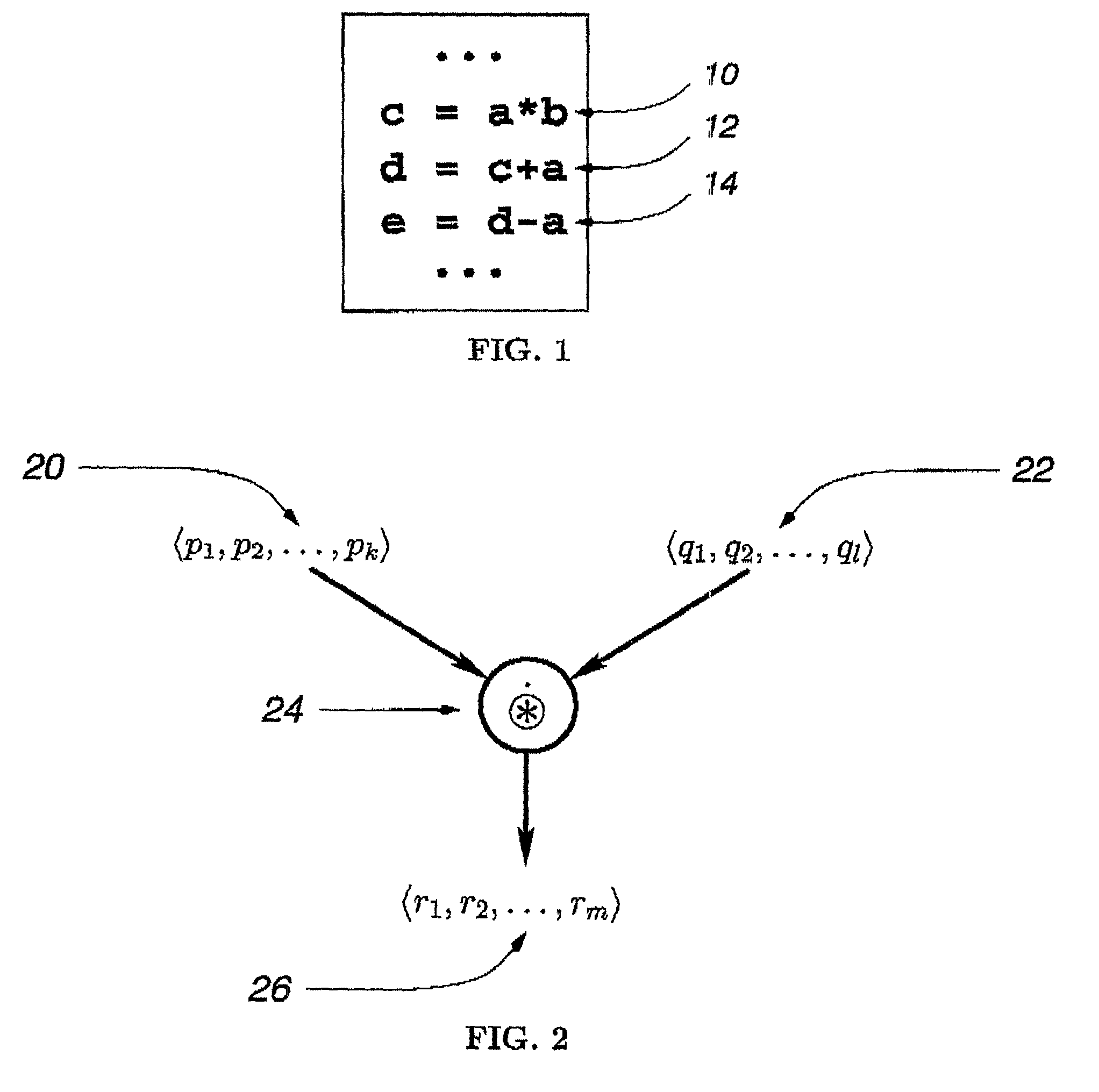
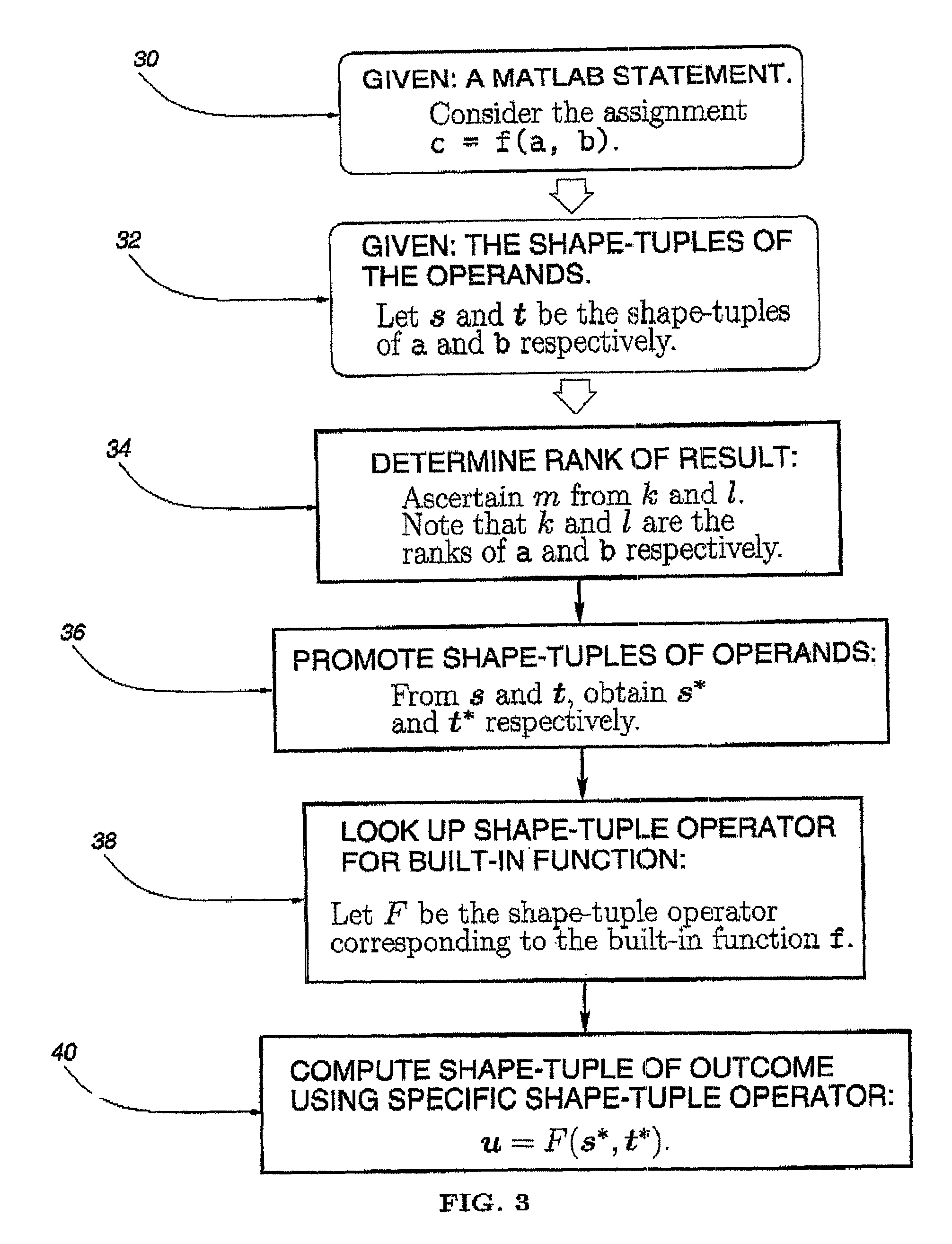
Method for array shape inferencing for a class of functions in MATLAB
InactiveUS7086040B2Optimize allocationOptimal codeSoftware engineeringProgram controlArray data structureTheoretical computer science
A method for inferring the shape and dimension of arrays for high-level, array-based languages such as MATLAB is presented. The method uses the algebraic properties that underlie MATLAB's shape semantics and infers the shape that the program expression assumes. In one embodiment, a shape-tuple of the result of a program expression is inferred by creating a shape-tuple expression comprising the shape-tuples of the operands and the shape-tuple operator.
Owner:NORTHWESTERN UNIV
Multi-layer adhesive closure
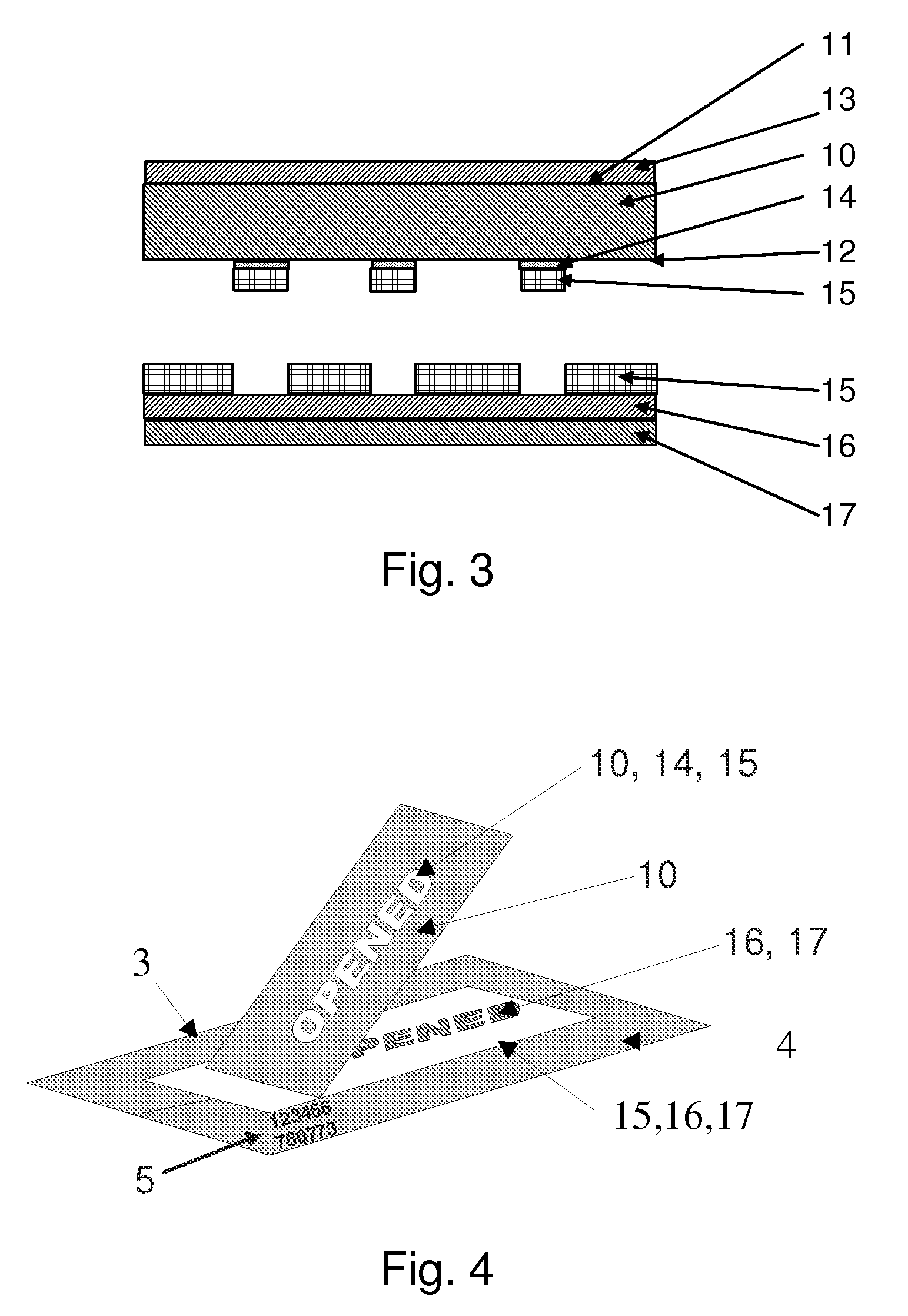
The present invention relates to a multi-layer adhesive closure having a backing and an adhesive layer disposed over the full area beneath the backing, at least the following layers being disposed between backing and adhesive layer: a) a first layer applied not over the full area—marking layer; b) a second layer applied over the full area—contrast layer. It is proposed that an individual identifier be included for verification.
Owner:TESA SE
Method and system for maintaining connections between surfaces and objects in a graphics display system
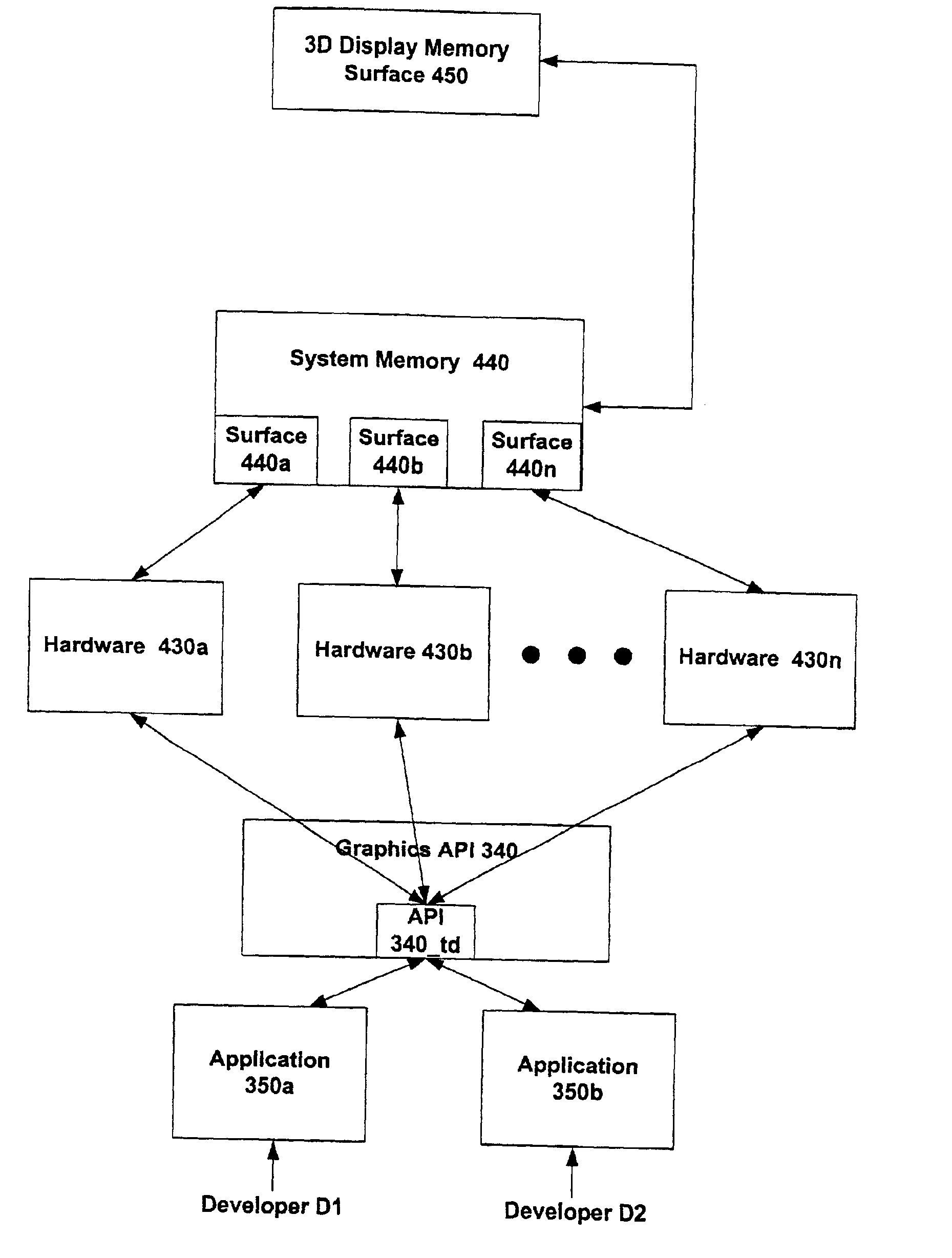
InactiveUS6874150B2Avoid previous inefficient useDemand for overall computing resourceMultiprogramming arrangementsProgram loading/initiatingGraphicsGraphic system
A method and system are provided for controlling the algorithmic elements in 3D graphics systems via an improved 3D graphics API and for managing computing resources utilized in connection with the maintenance of connections between surfaces and objects. When multiple applications are running simultaneously, it is possible that the demand for overall computing resources may exceed supply; and it is possible that a connection between a surface and object may be lost for one or more applications. In accordance with the present invention, a check for the persistence of a connection between surface space and object space is made substantially at the time of a present function call, and thus multiple redundant checks are avoided. In one embodiment, checks made incident to function calls other than a present function call are spoofed or bypassed in order to avoid previous inefficient use of computing resources.
Owner:MICROSOFT TECH LICENSING LLC
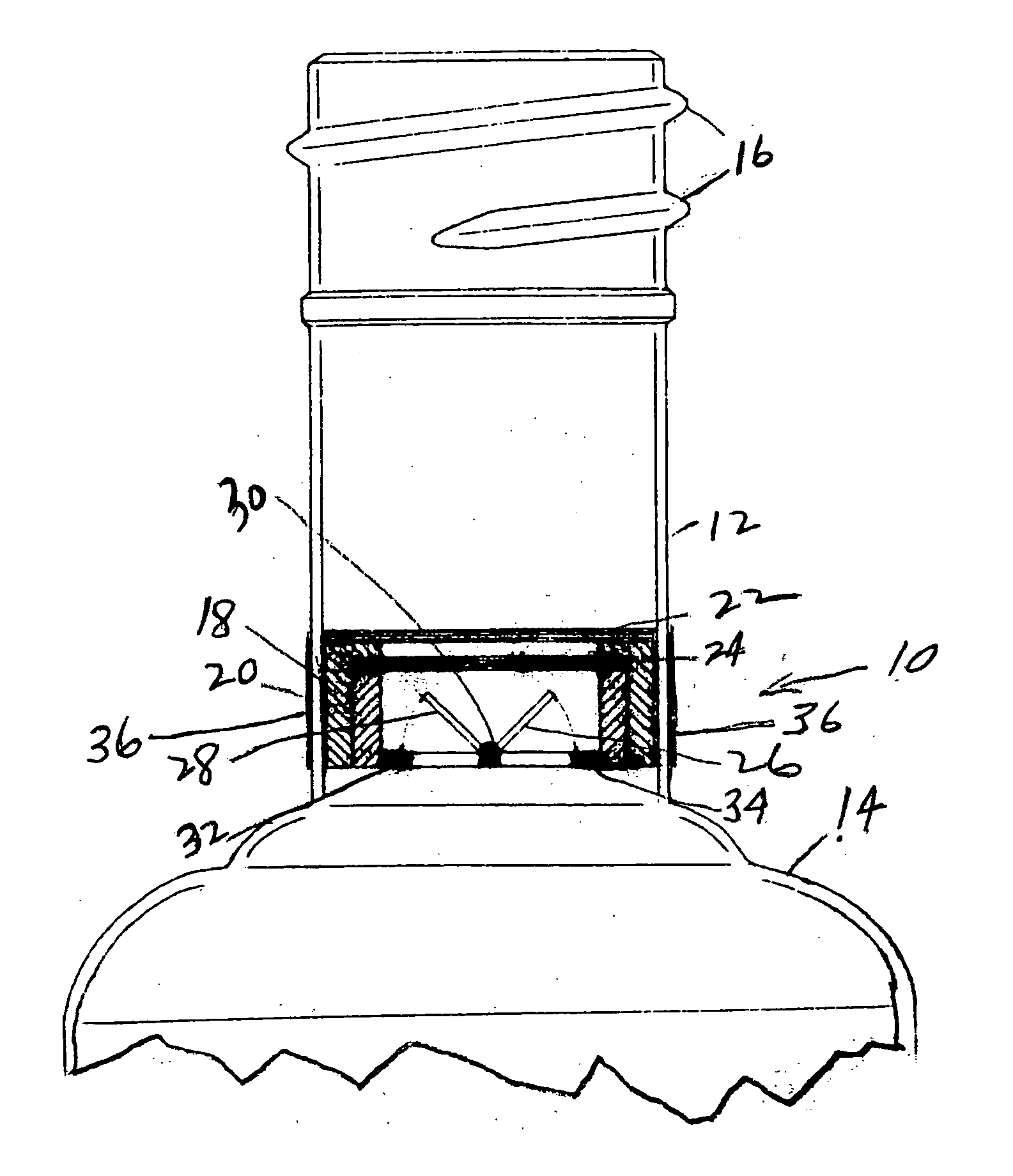
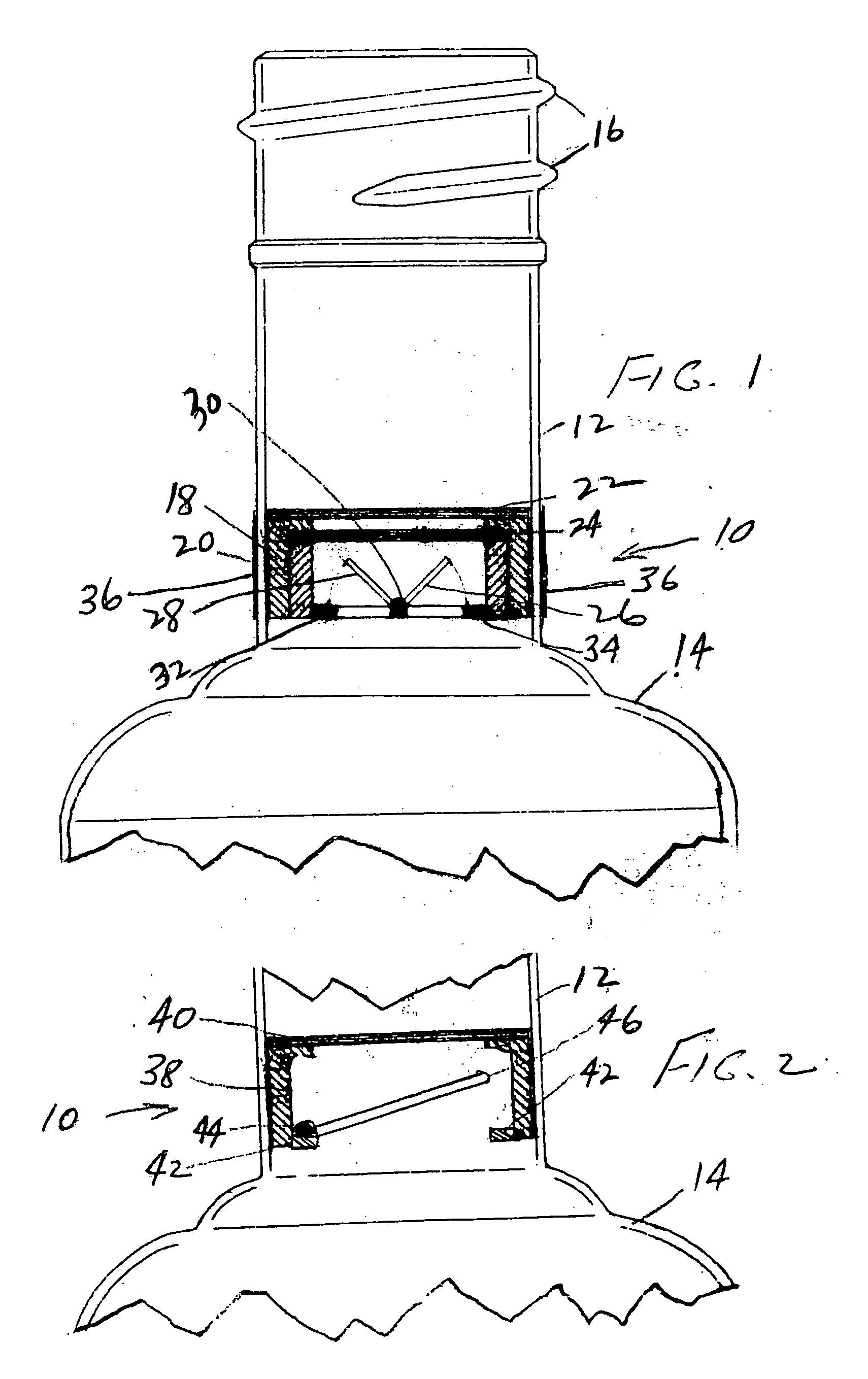
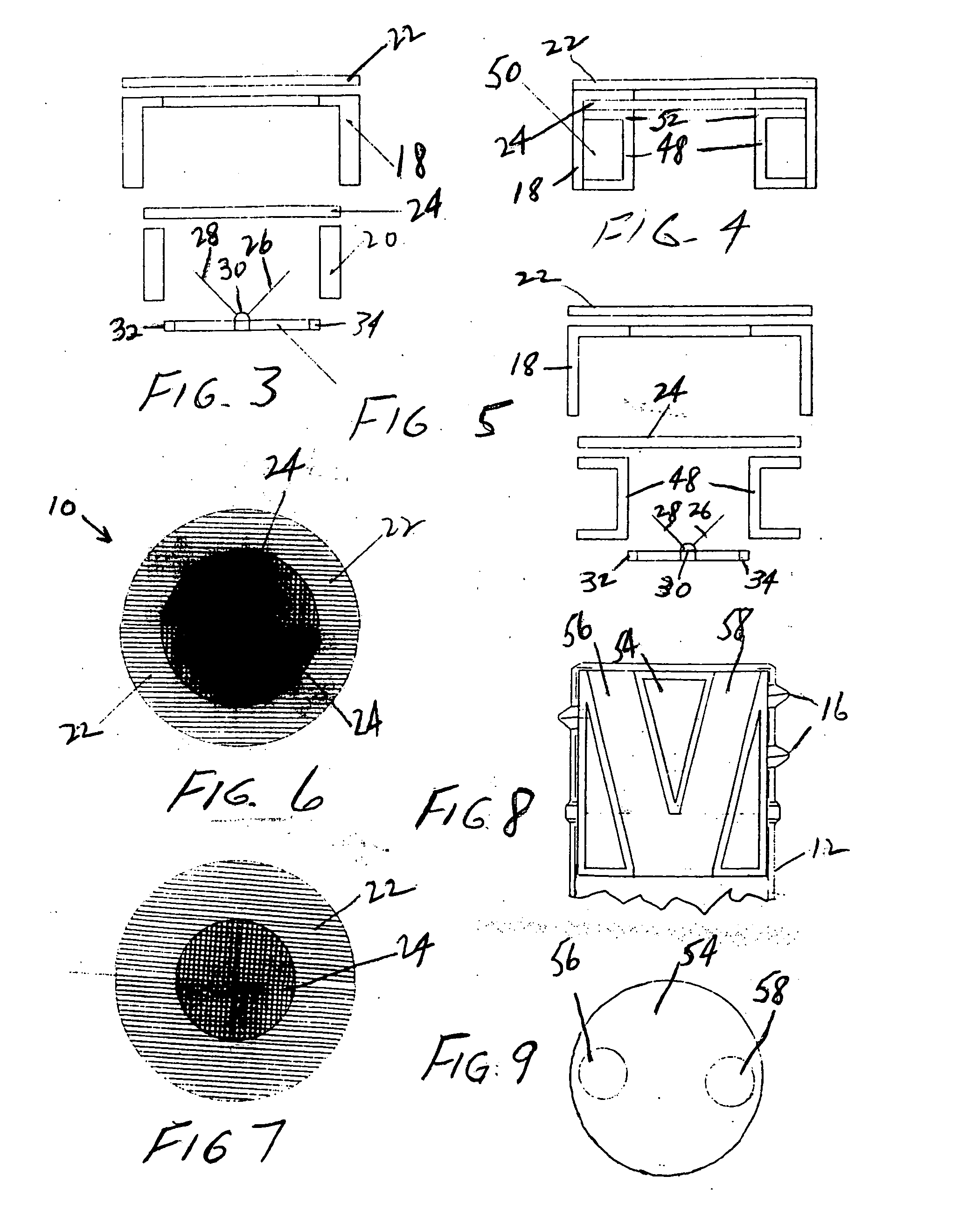
Tamper evident check valve apparatus for use in a beverage bottle and method of use
InactiveUS20070262042A1Prevent adulterationAvoid substitutionClosures to prevent refillingEngineeringBottle
Disclosed is an apparatus and method for preventing the adulteration or substitution of beverages such as premium liquors disposed in bottles having a neck. The apparatus preferably comprises the use of a check valve which is protected from manipulation or tampering by screens and / or by lodging the apparatus loosely in the neck of the bottle so that tampering will result in its being dislodged and falling into the beverage bottle and / or by the use of a frangible reservoir containing a harmless dye to discolor the beverage in the event of tampering. The invention also contemplates the method of preventing the adulteration or substitution of beverages including the steps manufacturing the apparatus, filling the beverage bottle with the beverage, inserting the apparatus to prevent adulteration or substitution in the neck of the bottle, closing the bottle, disposing external indicia on the bottle to call the consumer's attention to the protective apparatus, and publicity associated with educating the public concerning same.
Owner:PAREJA MICHAEL R
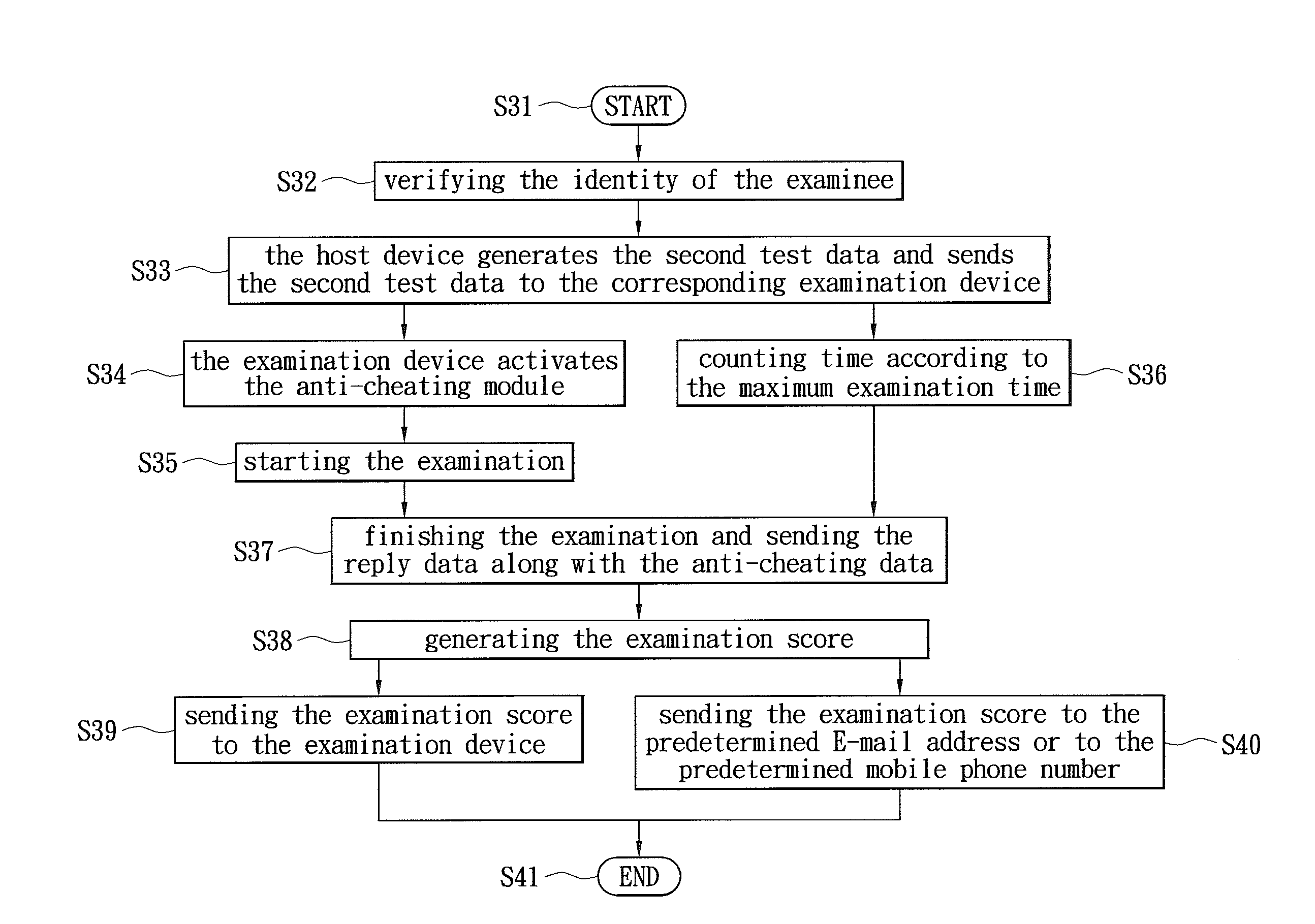
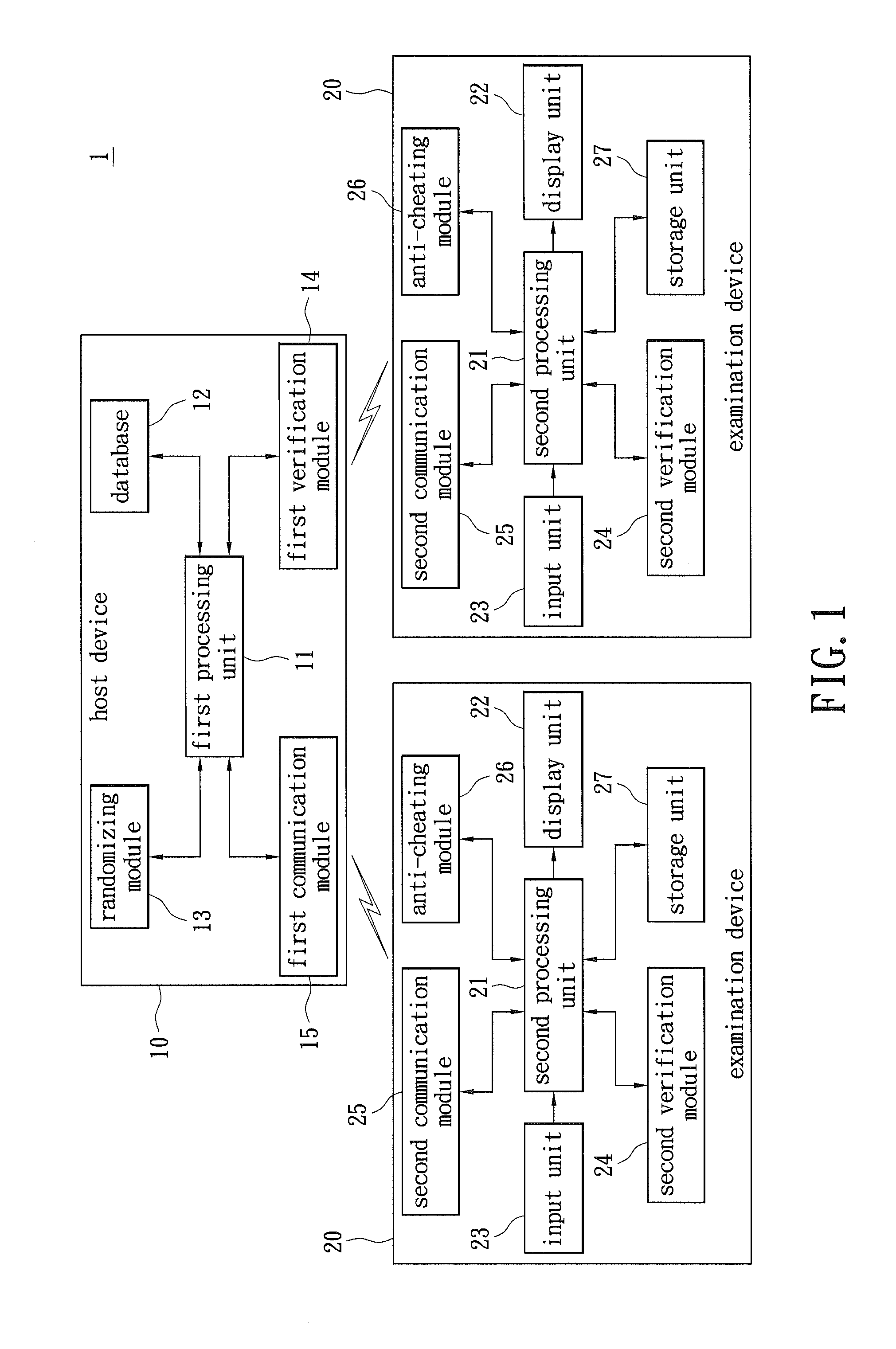
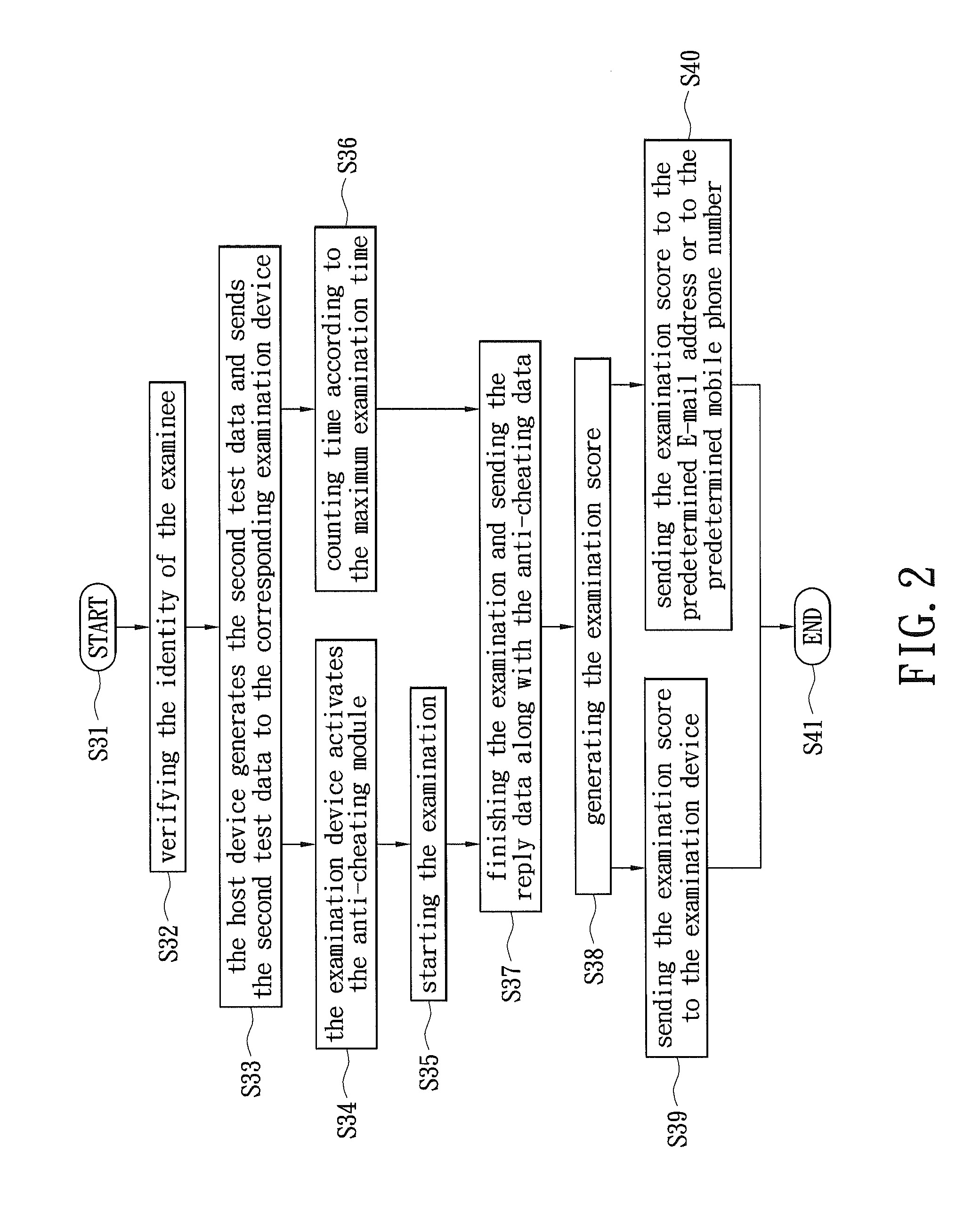
Examination system and method thereof
InactiveUS20110217687A1Avoid checkingElectrical appliancesElectronic clinical trialsExamination methodComputer science
An examination system and an examination method are disclosed. The examination method includes: generating a first test data by a host device, in which the first test data has a plurality of questions; rearranging the questions of the first test data in order to generate a second test data; and sending the second test data to a corresponding examination device for taking the examination. An anti-cheating module is provided for detecting distances between the examination devices or detecting a deviation angle of a character image of the examinee. When the distance is less than a predetermined value or the deviation angle is greater than a predetermined value, an anti-cheating signal is then generated for avoiding cheating actions.
Owner:E INK HLDG INC
Check valve
ActiveUS20160097486A1Improve integrityAvoid checkingPositive displacement pump componentsCheck valvesEngineeringCheck valve
A check valve supplies fluid to a system and includes a fluid barrier protects the sealing elements and surfaces of the check valve preventing degradation from any backflow of gas and debris from the system to which fluid is supplied.
Owner:ROYS CURTIS
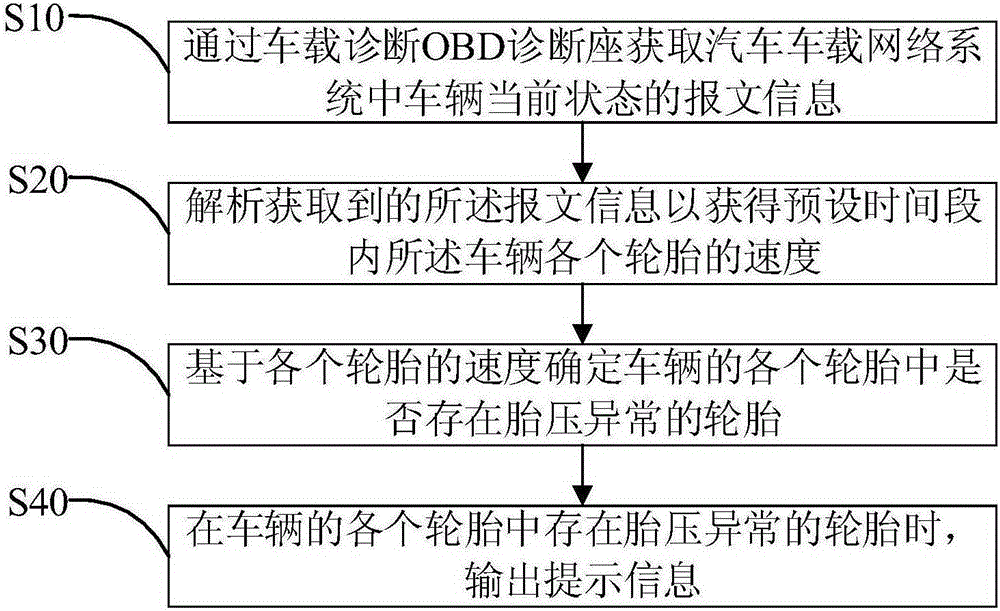
On-board diagnostic (OBD) diagnosis base-based tire pressure abnormity monitoring method and device
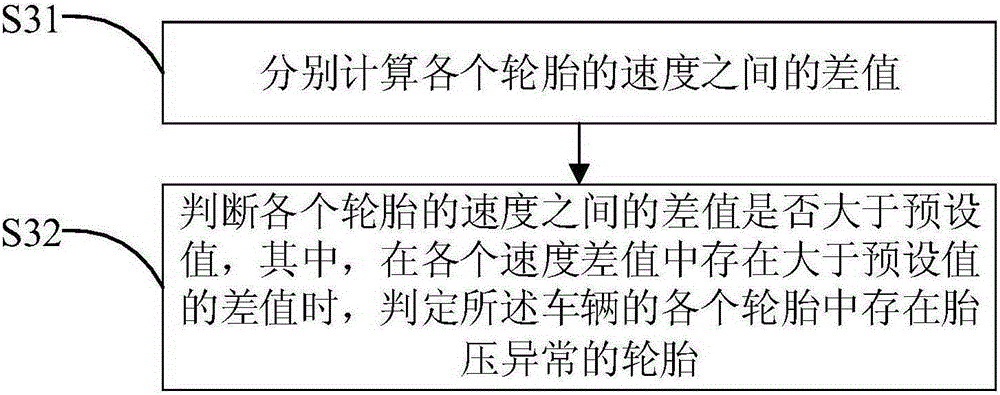
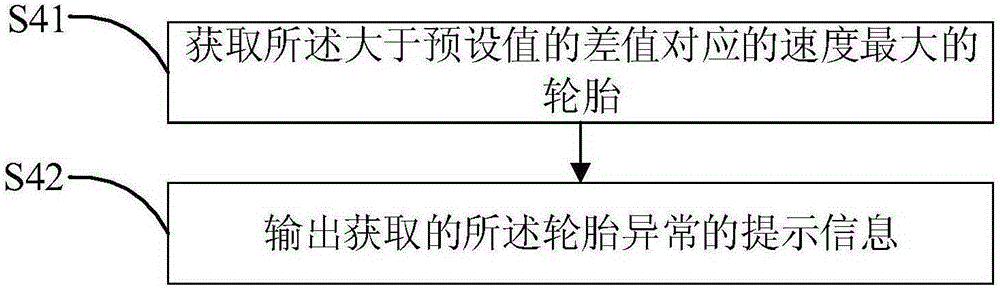
The invention discloses an on-board diagnostic (OBD) diagnosis base-based tire pressure abnormity monitoring method. The method comprises acquiring report information of a current state of an automobile in an automobile-mounted network system by an OBD diagnosis base, carrying out analysis on the report information to obtain rates of tires of the automobile in a preset time stage, determining if the tires of the automobile comprise a tire with abnormal tire pressure according to the rates of the tires of the automobile, and outputting prompt information when the tires of the automobile comprise a tire with abnormal tire pressure. The invention also discloses an OBD diagnosis base-based tire pressure abnormity monitoring device. The method and device realize tire pressure monitoring based on rates of tires of a vehicle, can output prompt information to give a tire abnormity prompt for a user when the tire pressure is low, are free of tire pressure detection by a pressure transducer installed in a tire and reduce a vehicle tire pressure monitoring cost.
Owner:LAUNCH SOFTWARE DEV
Vehicle Suspension Control System With High Flow Exhaust Mechanization
ActiveUS20170267046A1Simple designCompact and inexpensive to manufactureResilient suspensionsVehicle springsAir suspensionCheck valve
An air management system for a vehicle. The air management system includes at least one air spring. A compressor is provided for filling the air spring. A central air line is fluidly connected to the air spring and the compressor. At least one spring air line extends between the central air line and the air spring. At least one suspension valve is disposed along the spring air line. At least one auxiliary air line extends between the spring air line and the central air line. At least one high flow exhaust valve is disposed along the auxiliary air line. At least one isolation check valve is disposed in series with the high flow exhaust along the spring air line. The isolation check valve allows air to pass through therethrough from the air spring to the central air line while preventing air from passing therethrough from the central air line to the air spring.
Owner:BEIJINGWEST INDUSTRIES
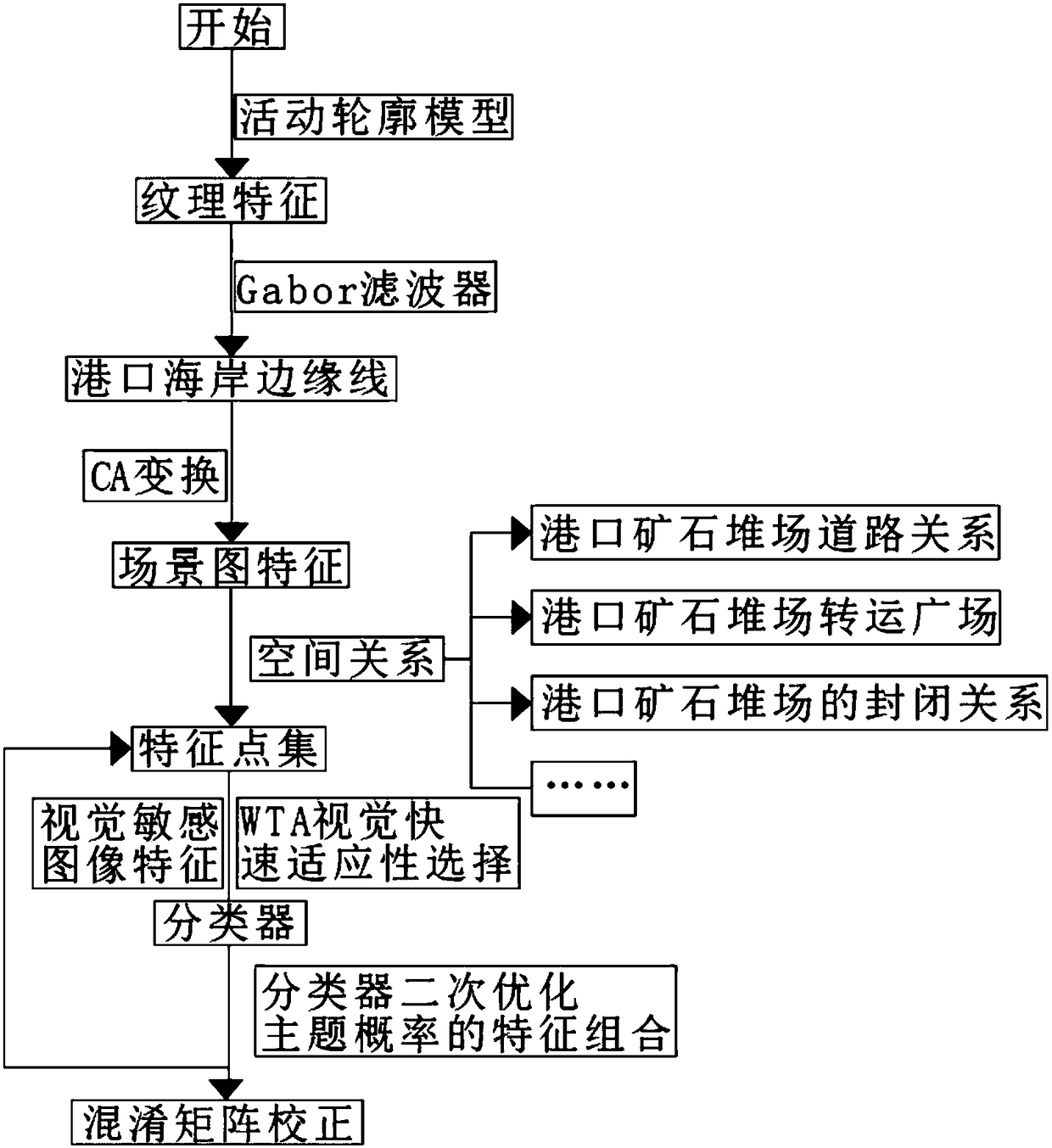
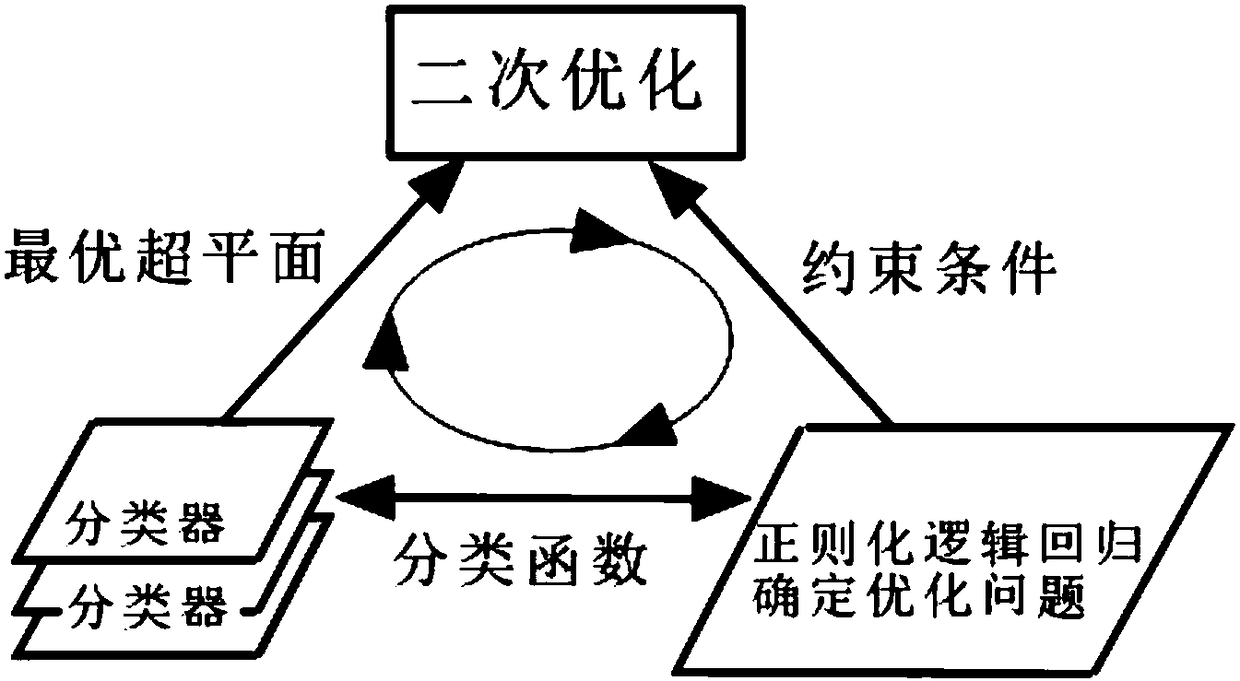
Port ore stockyard identification method based on remote sensing screen classification
The invention discloses a port ore stockyard identification method based on remote sensing screen classification. The method comprises the following steps of firstly, performing texture characteristicidentification on a random area of a remote sensing image, and extracting a port coast edge line; secondly, performing classification based on CA change through different scene picture characteristicdifferences; based on accurate identification to an ore stockyard spatial relation characteristic, extracting an association relation of the ore stockyard, and forming a characteristic point set by the identified to-be-analyzed ore stockyard; finally, establishing a classifier through regular logic regression, and performing secondary optimization through a classifier for obtaining a constrainedcondition; combining a theme probability characteristic and performing scene classification by means of a vector classifier for identifying the ore stockyard; extracting an original attribute througha texture characteristic, eliminating impurity data, and obtaining a scene picture characteristic after layering capability obtainment through CA conversion. The port ore stockyard identification method has relatively high pertinence and can calibrate data in real time, thereby performing data updating identification according to a field condition and realizing high accuracy.
Owner:TRANSPORT PLANNING & RES INST MINIST OF TRANSPORT
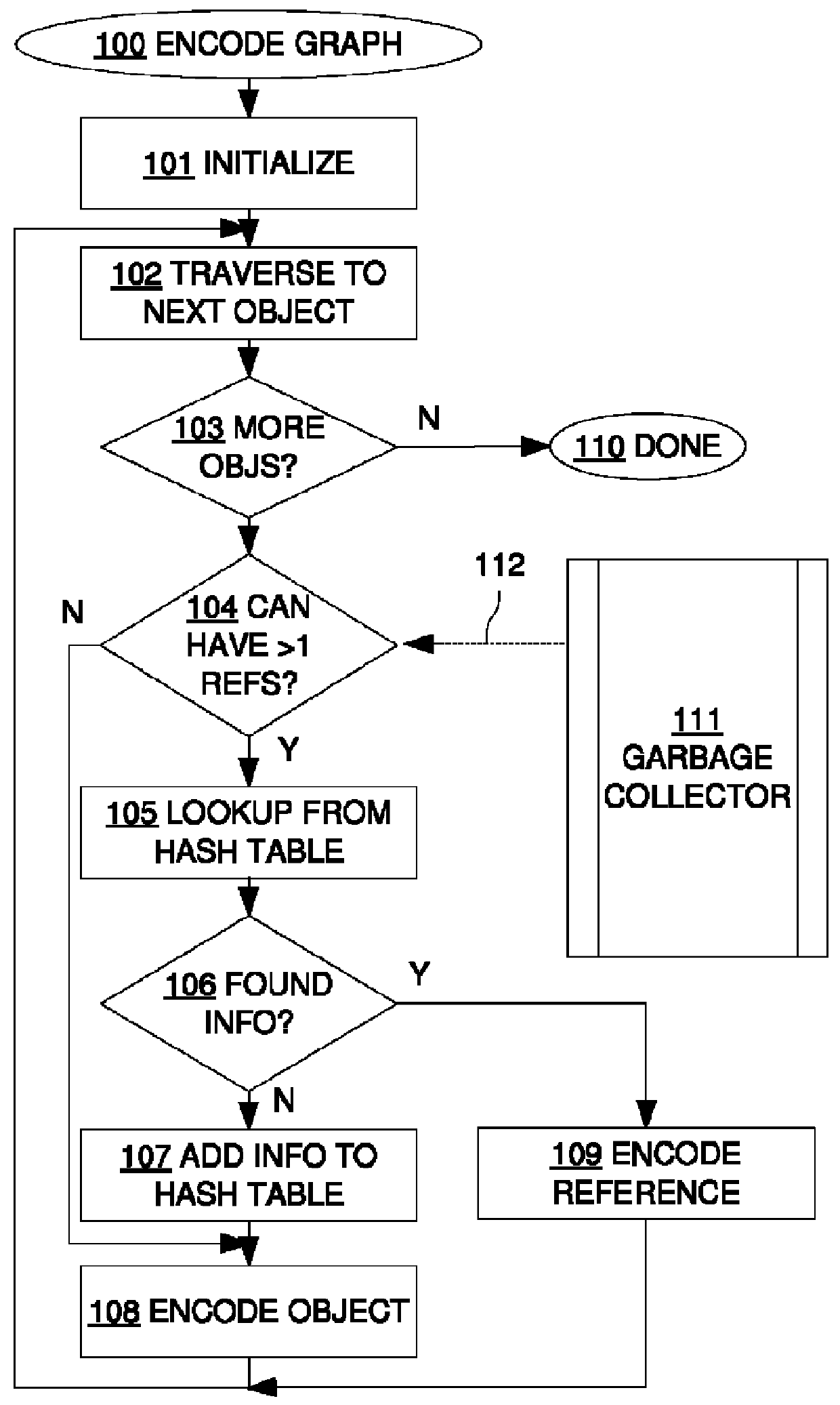
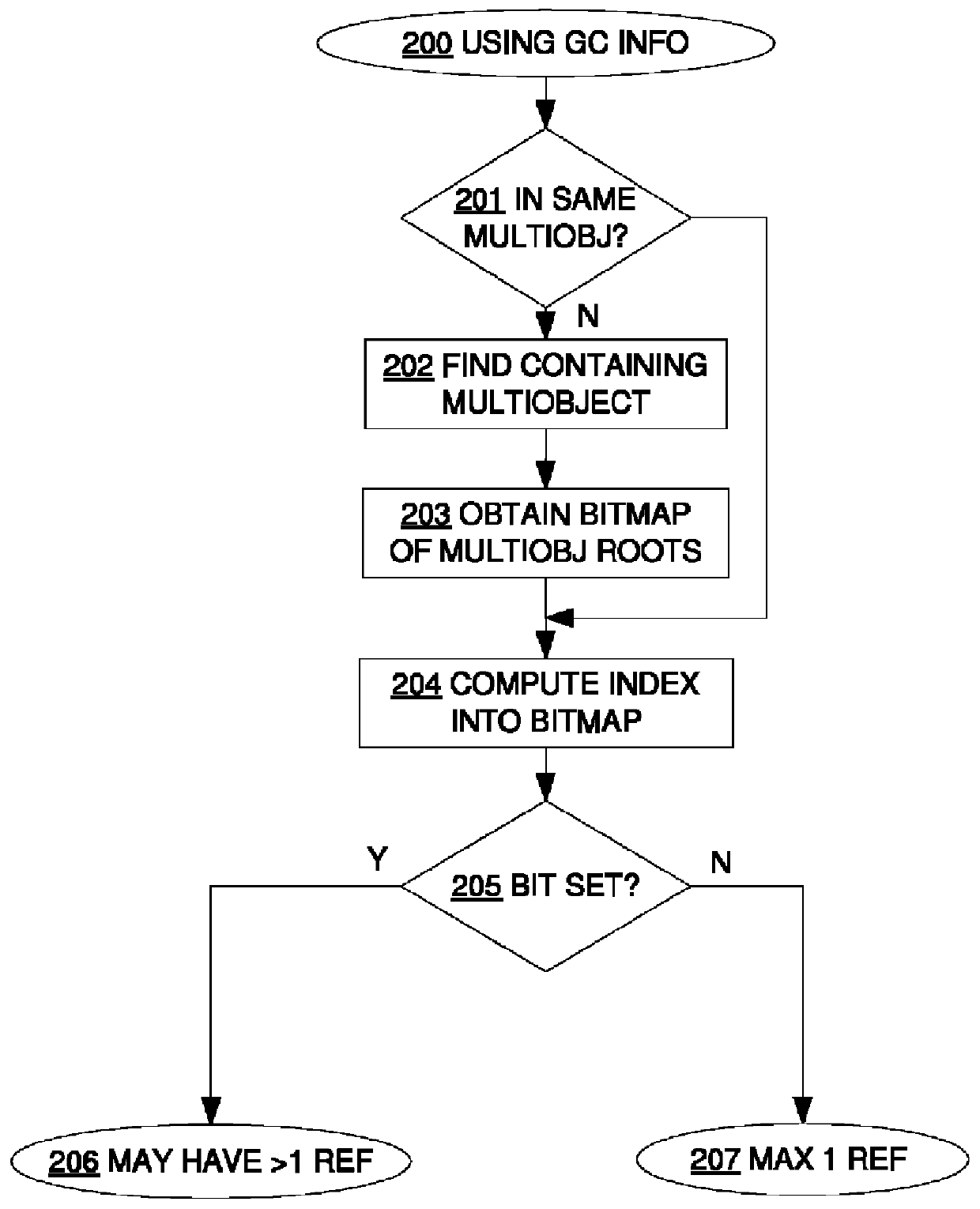
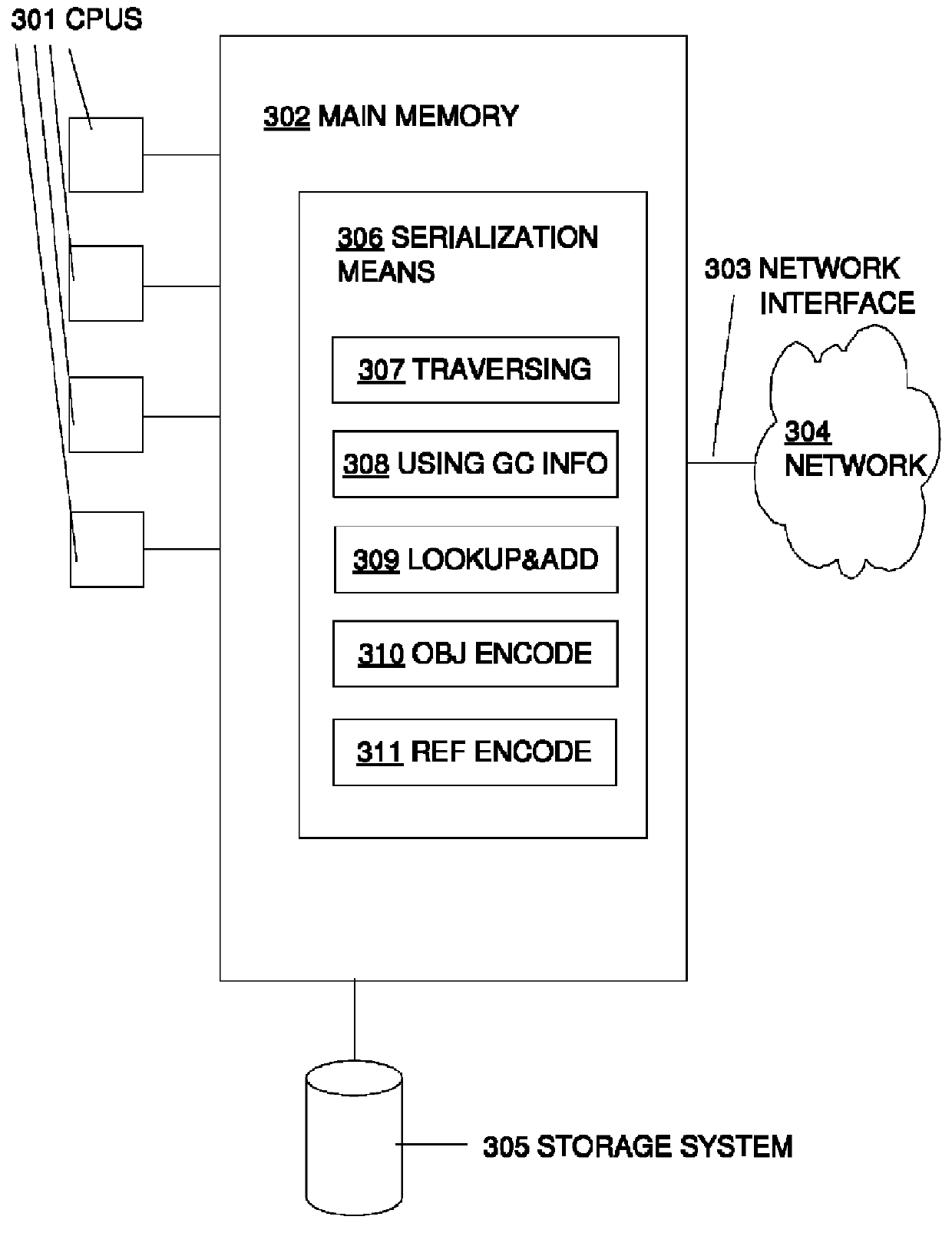
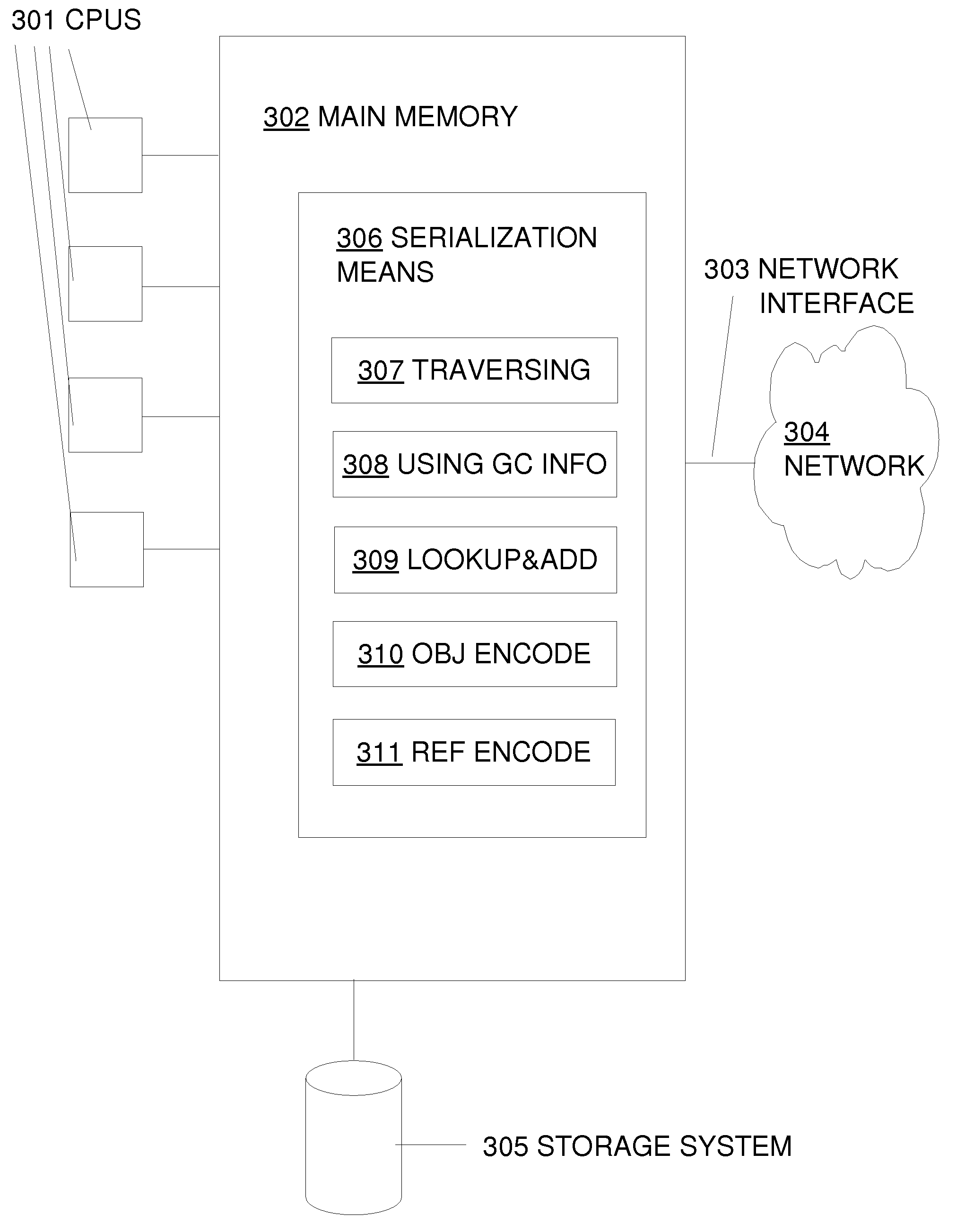
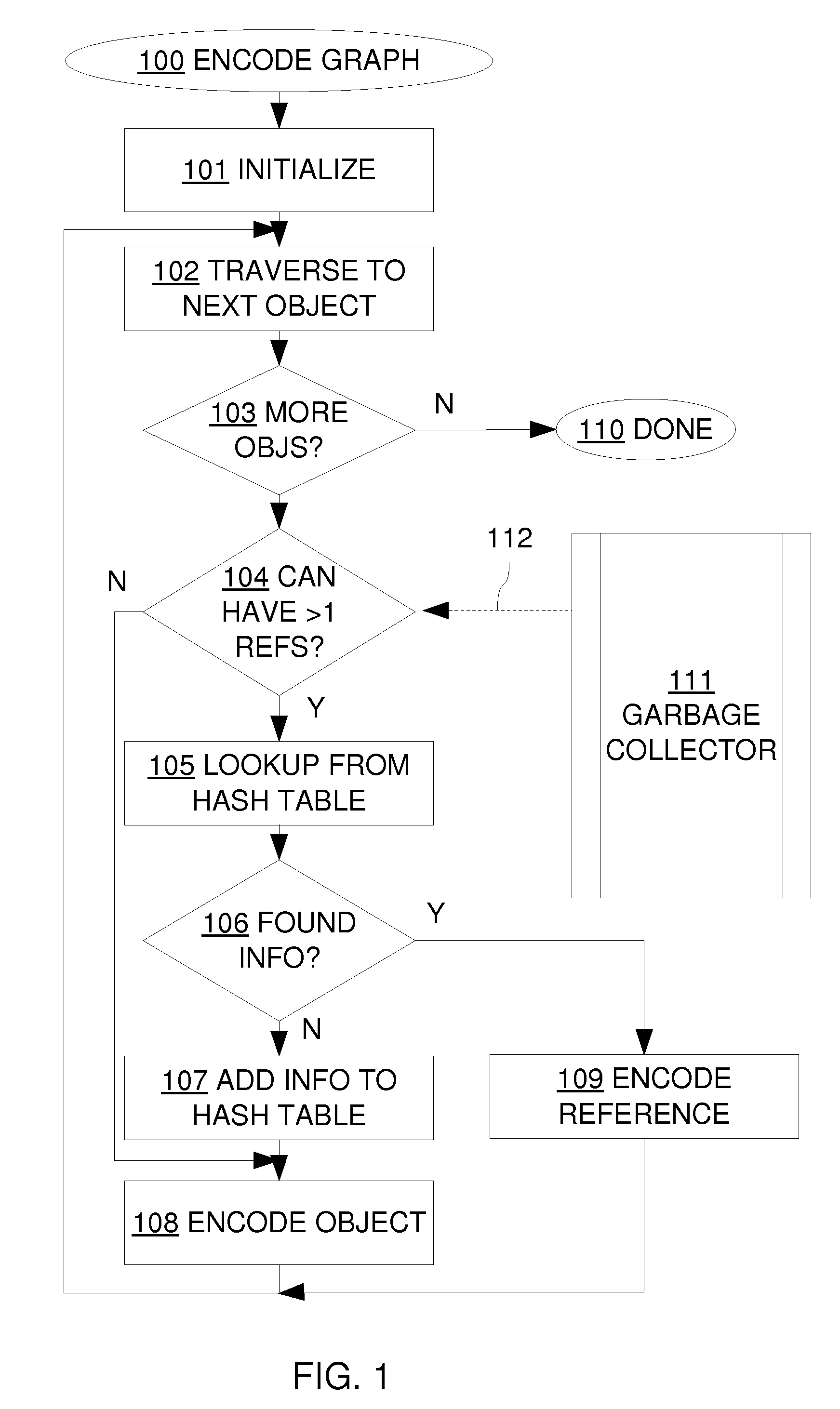
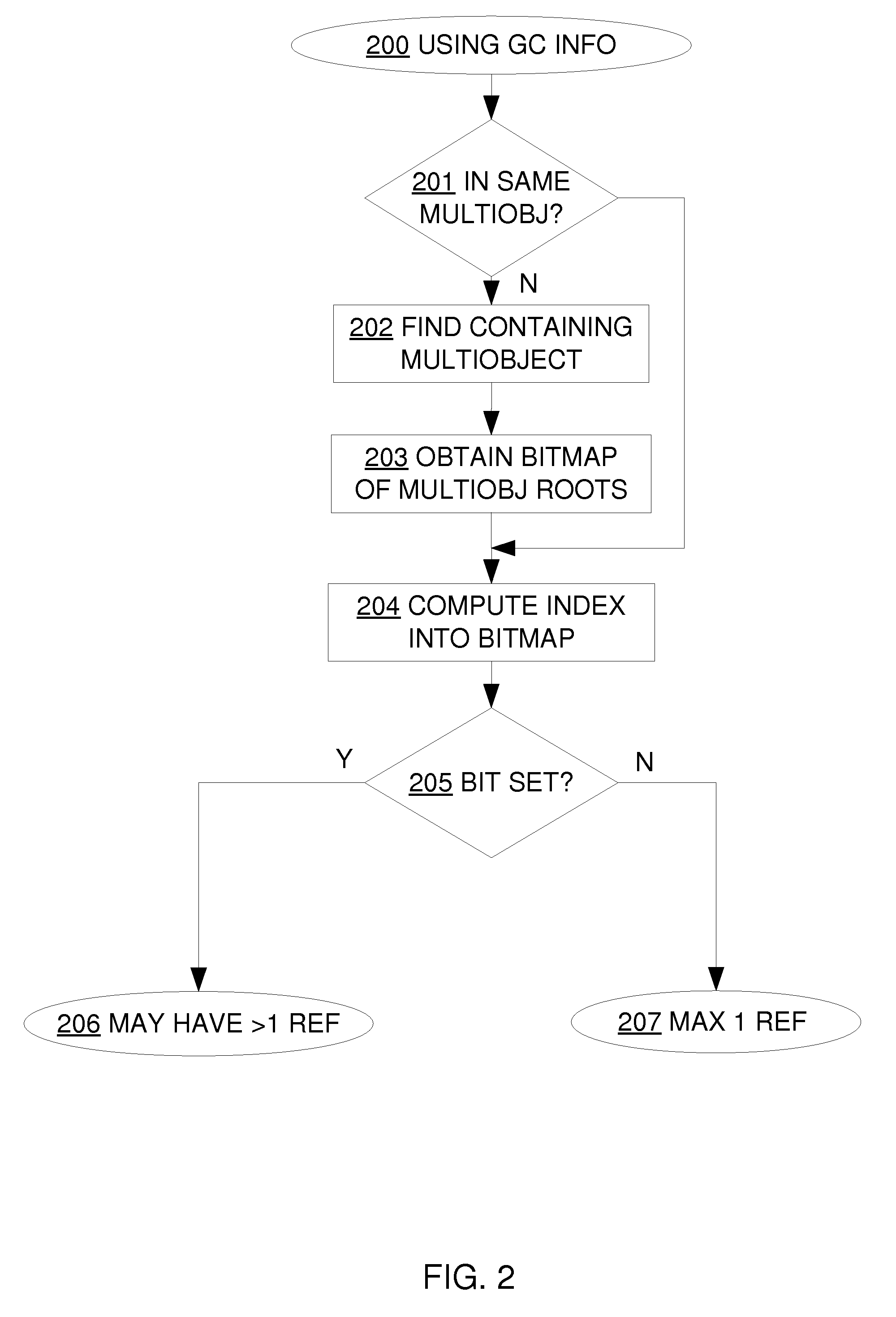
Utilizing information from garbage collector in serialization of large cyclic data structures
ActiveUS8396904B2Avoid checkingImprove performanceDigital data processing detailsObject oriented databasesSerializationComputer science
A method for serializing cyclic or shared data structures using information from the garbage collector to determine that some objects in the data structure being serialized cannot have more than one reference.
Owner:POSTQ IPR OY
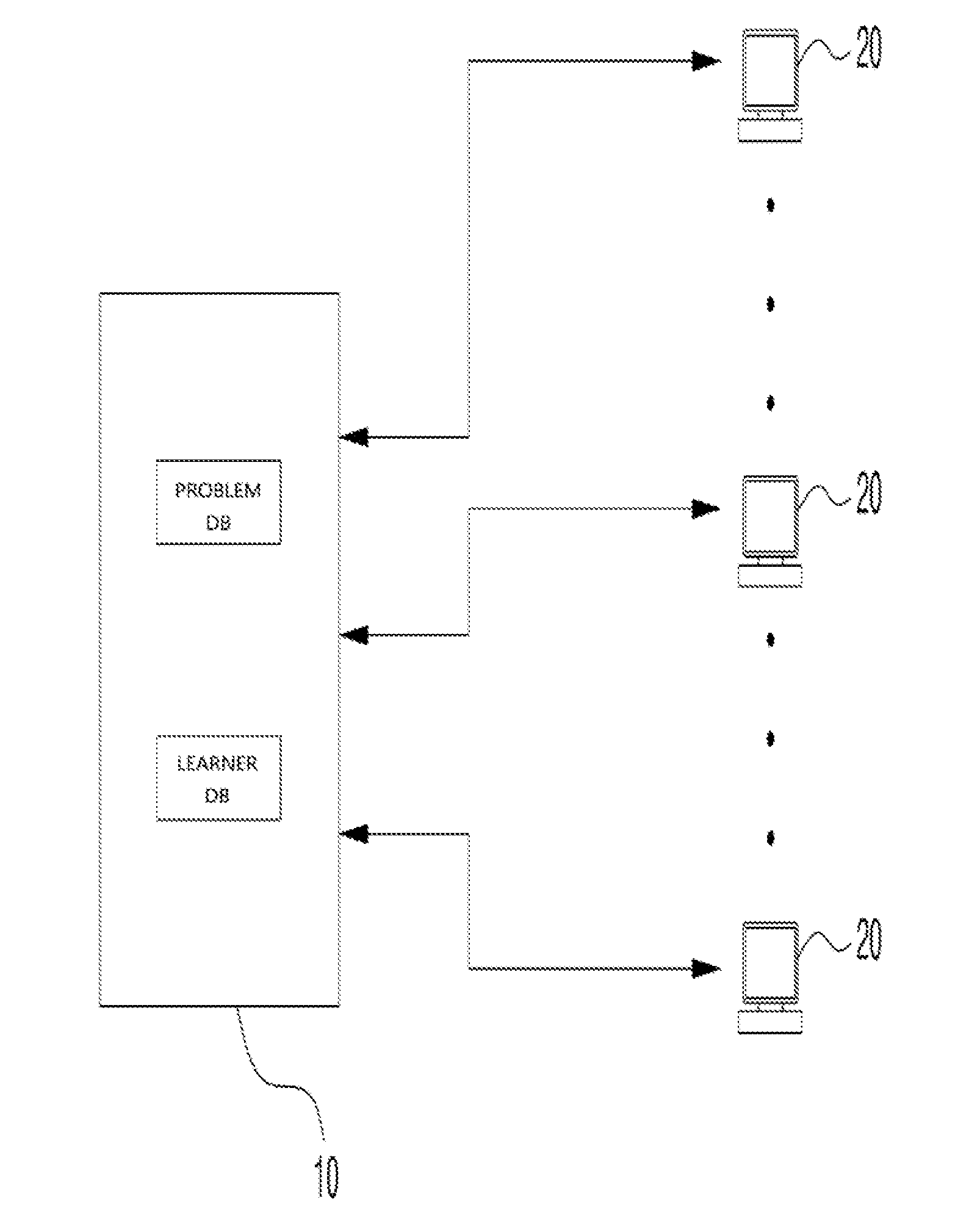
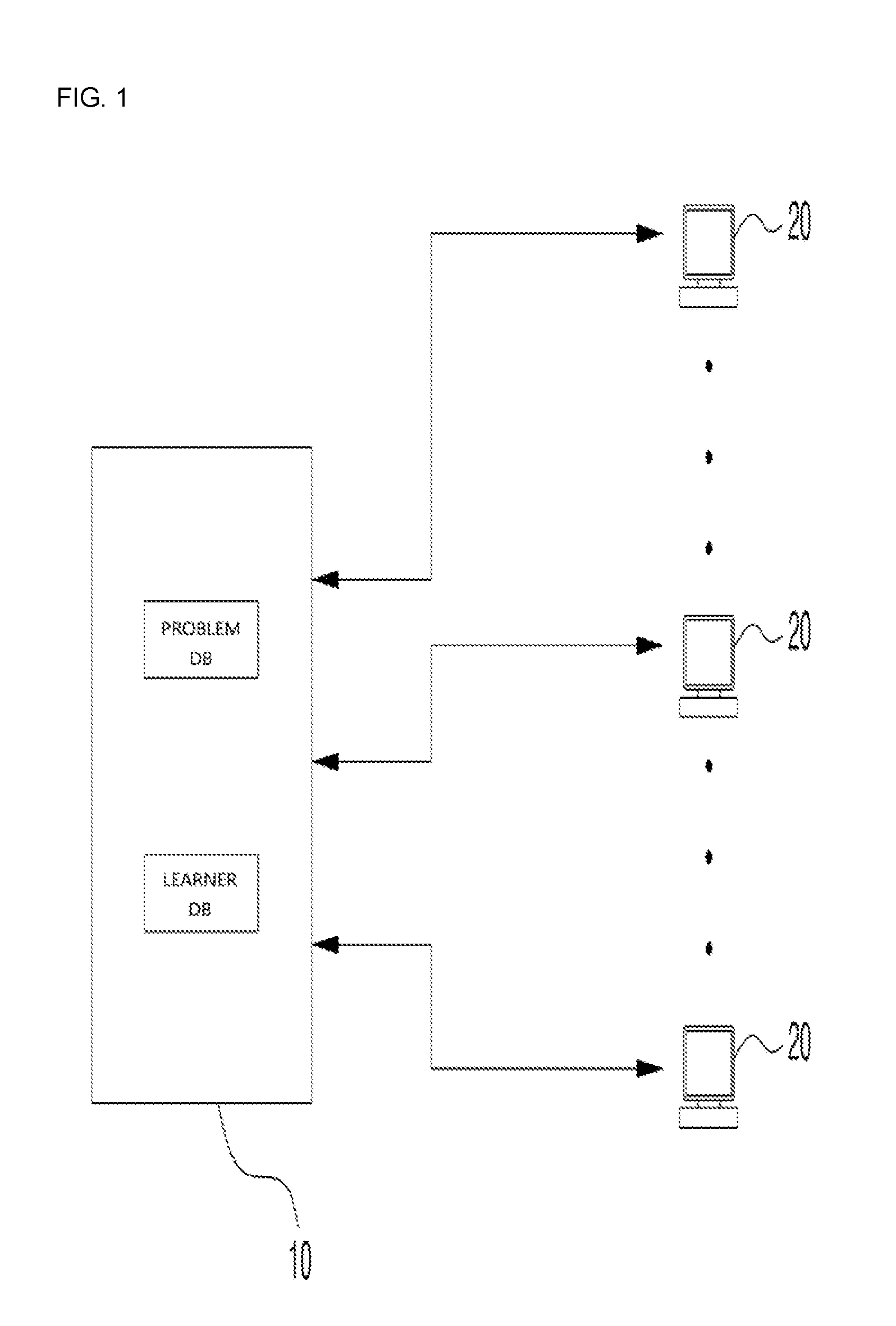
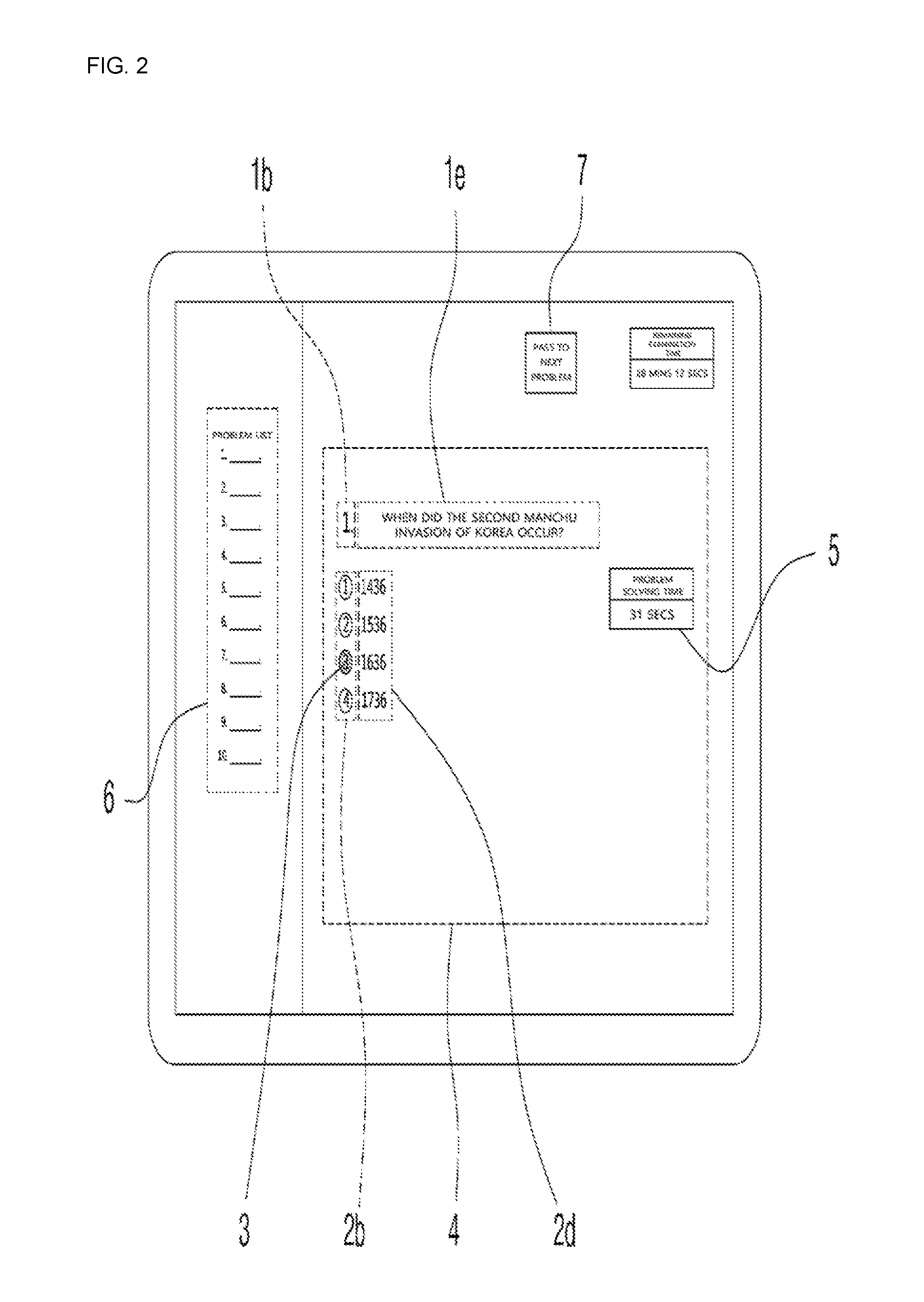
Individually customized online learning system
InactiveUS20160314702A1Resolve mental stressResolve physical painData processing applicationsWeb data indexingOnline learningKnowledge management
Disclosed is an individually-customized online learning system which, when respective learners make online connections using terminals belonging to the learners, automatically discloses learning problems on the terminals of respective learners, which instructs the learners to solve the learning problems using the terminals, which receives the learner's answers through the terminals and evaluates the students' grades, which additionally provides information regarding time taken to solve each problem, information regarding answers to respective problems, and information regarding solving of respective problems, and which can automatically adjust the difficulty level of the automatically disclosed problems using information regarding time taken to solve each problem and to submit the answer and information regarding erroneous answers to corresponding problems, thereby disclosing problems according to the learning level of learners.
Owner:PARK HYUNG YONG
Protective coating
InactiveUS7652087B2Improve waterproof performanceImparts flexibility and ductilityFireproof paintsPigmenting treatmentInorganic particlePhysical chemistry
Fire-protective coatings comprising a water-soluble alkali metal silicate binder, at least one inorganic particulate material which endothermically releases a nonflammable gas in the presence of heat, and an inorganic filler and / or a polymeric binder are disclosed.
Owner:AMERICAN THERMAL HLDG CO
Utilizing information from garbage collector in serialization of large cyclic data structures
ActiveUS20100185632A1Improve performanceAvoid checkingDigital data processing detailsObject oriented databasesSerializationData structure
A method for serializing cyclic or shared data structures using information from the garbage collector to determine that some objects in the data structure being serialized cannot have more than one reference.
Owner:POSTQ IPR OY
Access control in a web application using event filtering
ActiveUS20050262099A1Prevent them from checkAvoid checkingDigital data processing detailsMultiple digital computer combinationsReceiptComputer program
A web application is described that is capable of assuming a plurality of states and being arranged to process a received event from among a predeterminable set of events to change from one state to another. A permission record defines a set of permitted or forbidden events and the web application comprises an event filter arranged to consult the permission record on receipt of an event in order to determine whether to permit or not permit the event to be processed. Related methods of access control and computer program products are also described.
Owner:MARQETA
Process and composition for treating wood
InactiveUS20060269583A1Low costNot increase corrosion aspectFibreboardBiocideEnvironmental chemistryAluminium
The invention relates to a method for reducing the rate of deterioration of wood by providing an aqueous wood preservative composition having dissolved aluminum and dissolved and / or suspended silica, in which the concentration of aluminum as alumina is between about 300 mg Al2O3 / L and 20000 mg Al2O3 / L and the concentration of aluminum as alumina is at least two times the concentration of silica, and injecting the aqueous wood preservative composition into wood. Advantageously, the pH of the injected wood preservative composition is below about 3. Such a formulation is an effective wood preservative that is free of environmentally sensitive compounds such as copper, organic insecticides, and the like. However, such environmentally sensitive compounds can be used with the process of this invention, in some cases to bolster the biocidal effect.
Owner:CALYCLE RES
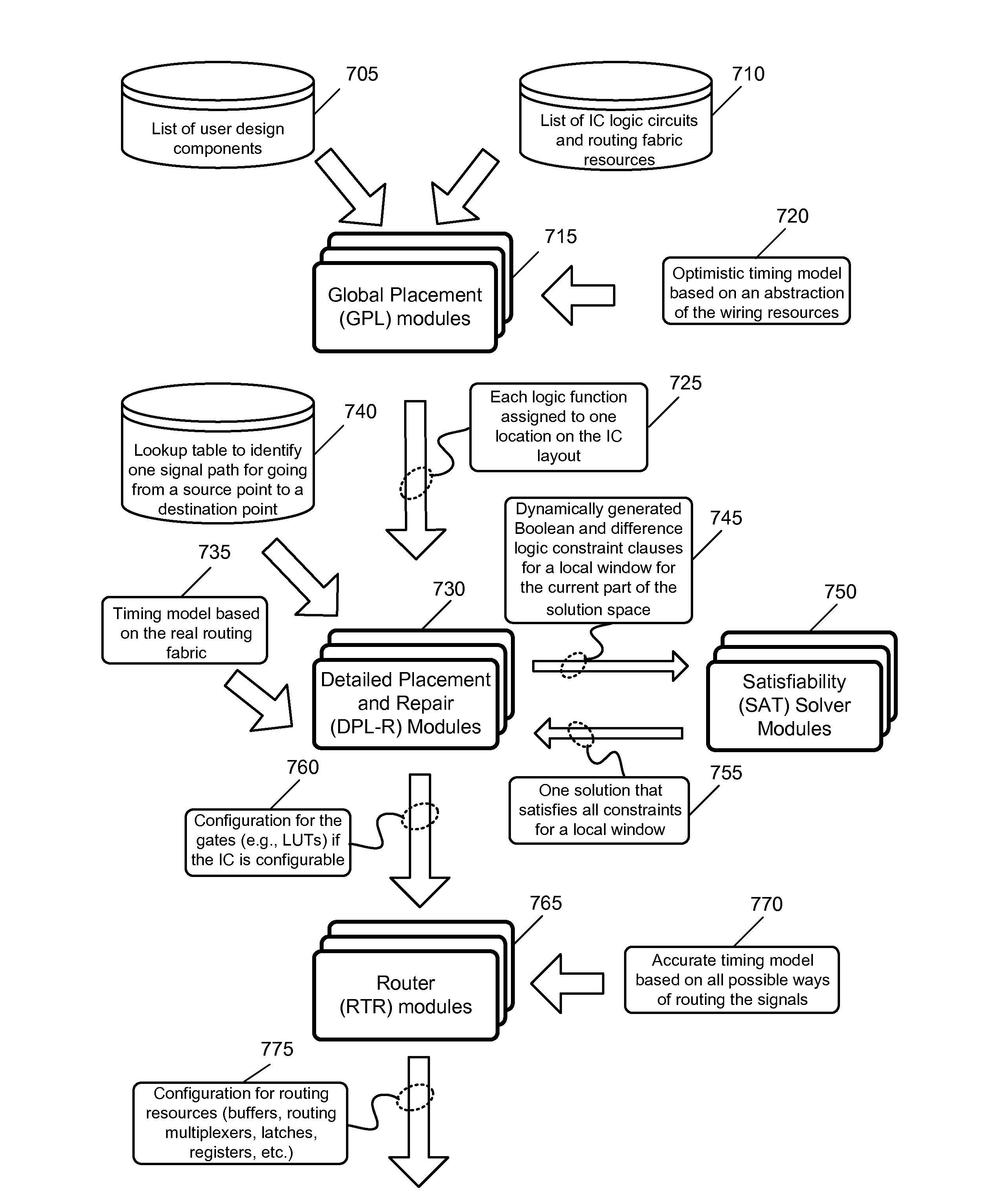
Detailed Placement with Search and Repair
ActiveUS20150220674A1Avoid checkingReduce in quantityDesign optimisation/simulationConstraint-based CADSatisfiabilitySolver
A method of detailed placement for ICs is provided. The method receives an initial placement and iteratively builds sets of constraints for placement of different groups of cells in the IC design and uses a satisfiability solver to resolve placement violations. In some embodiments, the constraints include mathematical expressions that express timing requirements. The method in some embodiments converts the mathematical expressions into Boolean clauses and sends the clauses to a satisfiability solver that is only capable of solving Boolean clauses. In some embodiments, the method groups several cells in the user design and several sites on the IC fabric and uses the satisfiability solver to resolve all placement issues in the group. The satisfiability solver informs placer after each cell is moved to a different site. The method then dynamically builds more constraints based on the new cell placement and sends the constraints to the satisfiability solver.
Owner:ALTERA CORP
Bypass filter apparatus and method
A filter sub apparatus comprising a housing configured to contain a filter and a bypass mechanism is provided. The bypass mechanism may be actuated upon debris buildup on the filter resulting in a load applied to the bypass mechanism rising above a predetermined lower level. A method to prevent chemical injection process failures may also be provided. The method may comprise the steps of providing a filter sub prior to a check valve. The filter sub may include a filter and a bypass mechanism. Another step may be passing fluid through the filter. In addition, the steps may also include containing at least some debris on a side of the filter such that the debris is prevented from reaching the check valve. A further step may be actuating the bypass mechanism after the debris builds up to a level in which a resulting load applied to the bypass mechanism exceeds a lower limit.
Owner:SCHLUMBERGER TECH CORP
Debugging System, Debugging Method, and Program
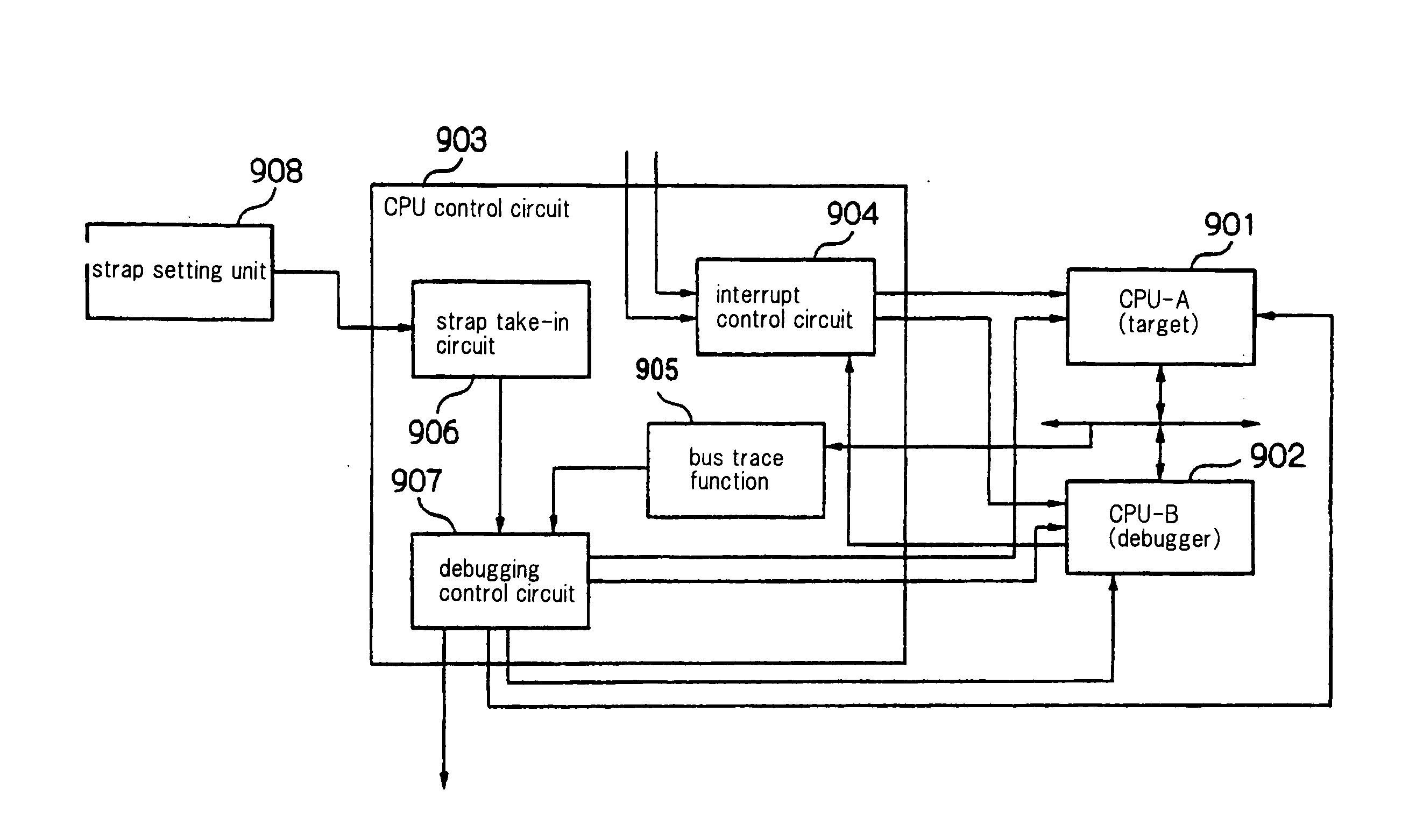
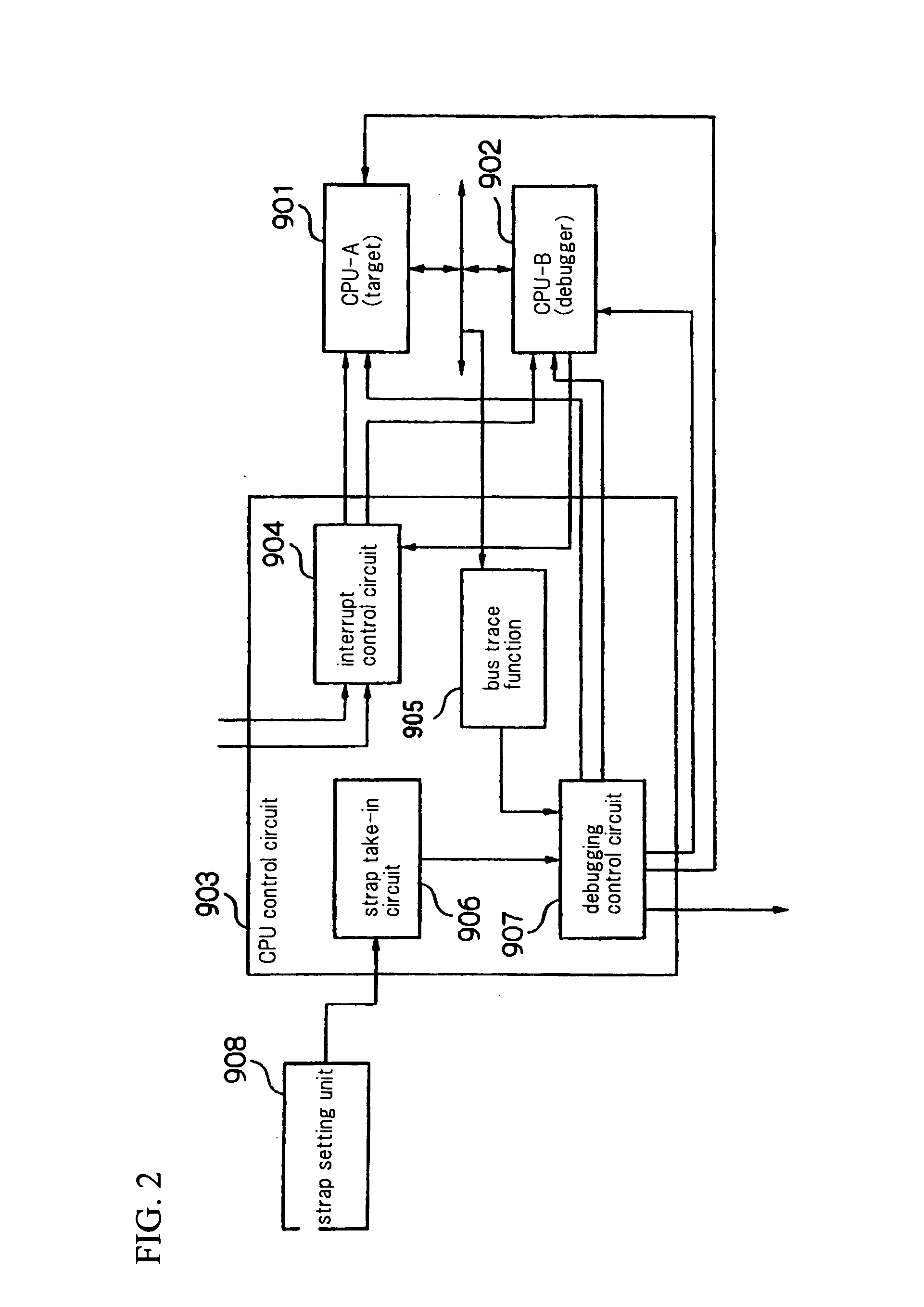
InactiveUS20090235233A1Avoid it happening againAvoid checkingSoftware testing/debuggingSpecific program execution arrangementsParallel computingExecution unit
Upon receiving debugging program activation instructions sent from a communication port (1), debugging program activation instruction distribution units (61 and 71) distribute the received debugging program activation instructions to execution units designated by these activation instructions. Debugging program activation units (62 and 72) are provided for each execution unit (A and B) and, based on the activation instructions distributed by the activation instruction distribution units (61 and 71), activate debugging programs (63 and 73) on the execution units designated by these activation instructions.
Owner:NEC CORP
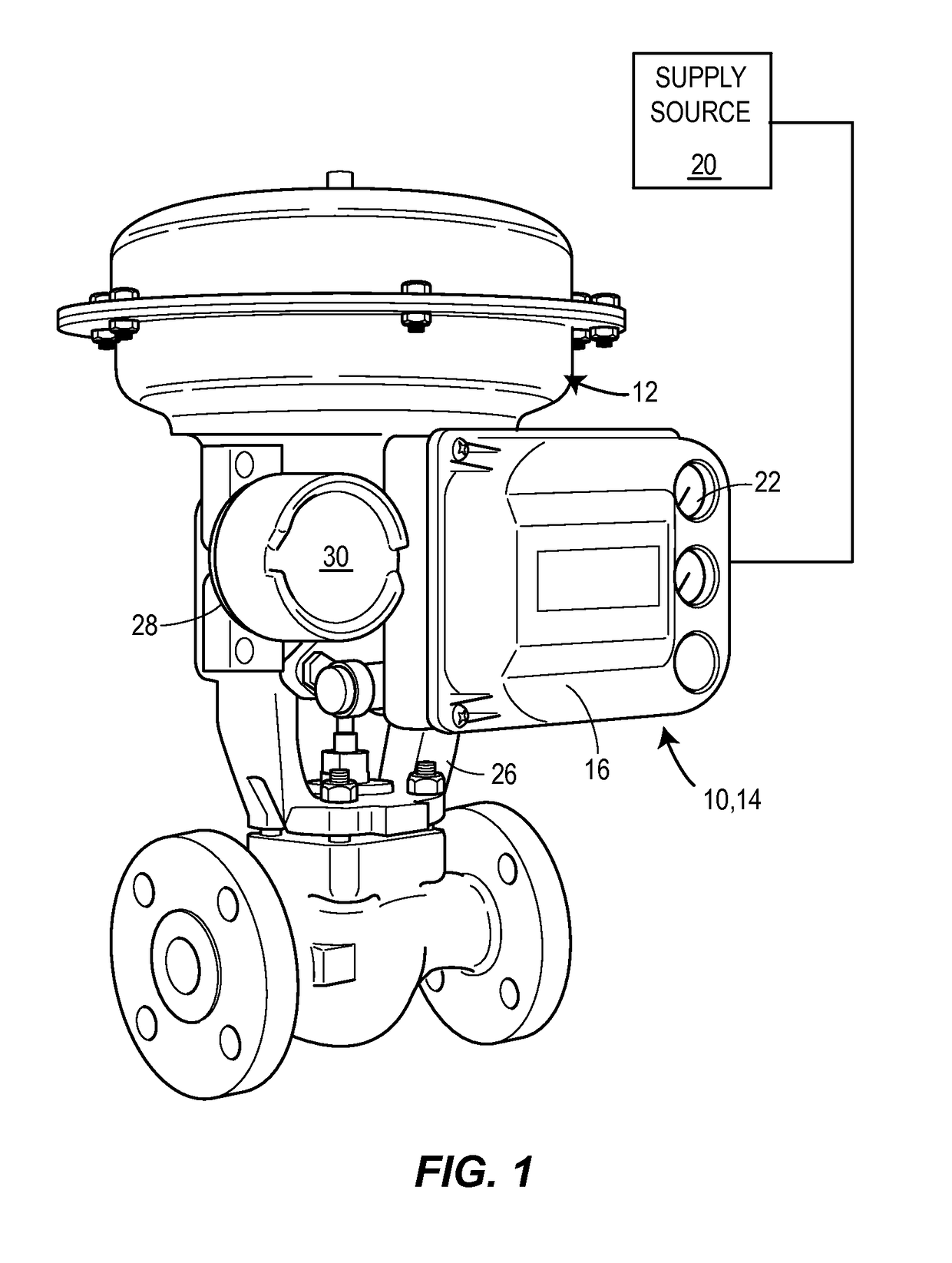
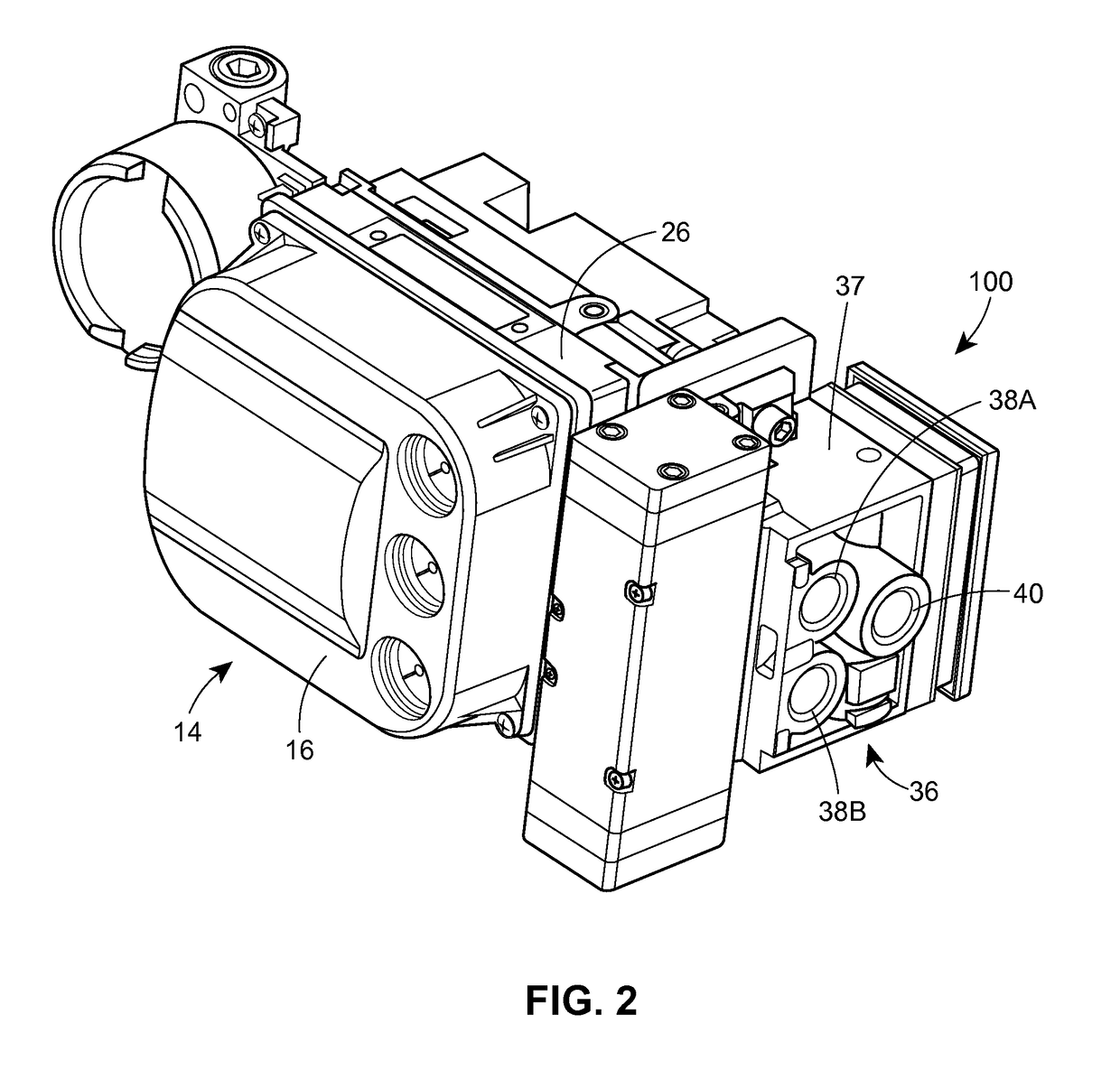
Vent assembly and method for a digital valve positioner
ActiveUS9989159B2Reduce assemblyReduce the soundOperating means/releasing devices for valvesCheck valvesEngineeringActuator
A digital valve positioner for use with an actuator. The digital valve positioner includes a housing, at least one exhaust port opening formed in the housing, and a vent assembly operatively coupled to the at least one exhaust port opening. The vent assembly includes a body having a bore, a valve seat surrounding the bore, and a check valve disposed within the bore. The check valve is arranged to shift from a closed position seated against the valve seat to an open position disposed away from the valve seat. A plurality of barriers is disposed around and positioned to enclose the check valve. The plurality of barriers is arranged to prevent an external medium from entering the check valve and to provide a tortuous flow path for the exhaust medium reducing sound through the vent assembly.
Owner:FISHER CONTROLS INT LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com