Patents
Literature
74 results about "Date of birth" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
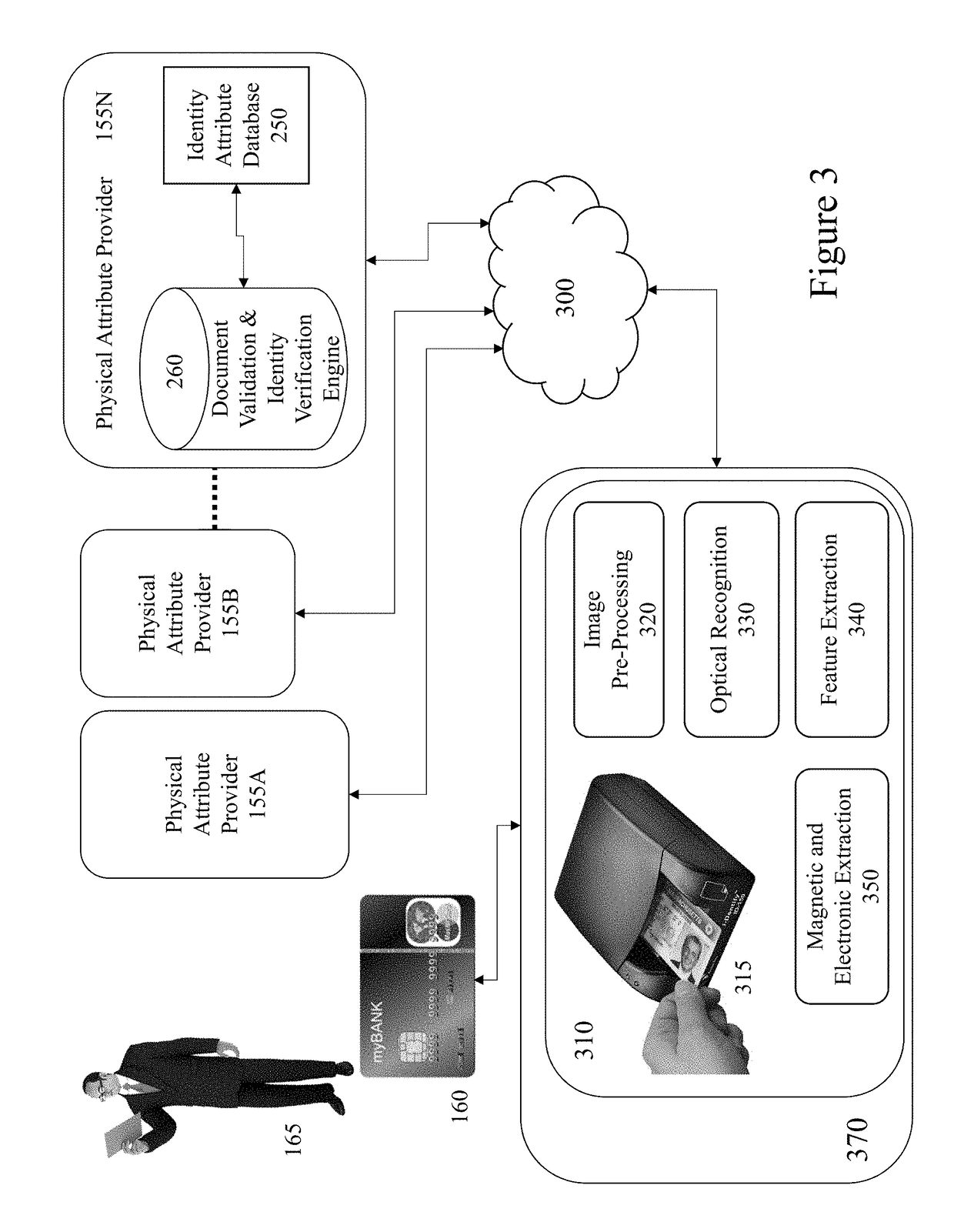
Fraud detection and security system for financial institutions
InactiveUS20030182214A1Limit losses to individual FIsAvoid checkingFinancePayment circuitsSocial Security numberCheque
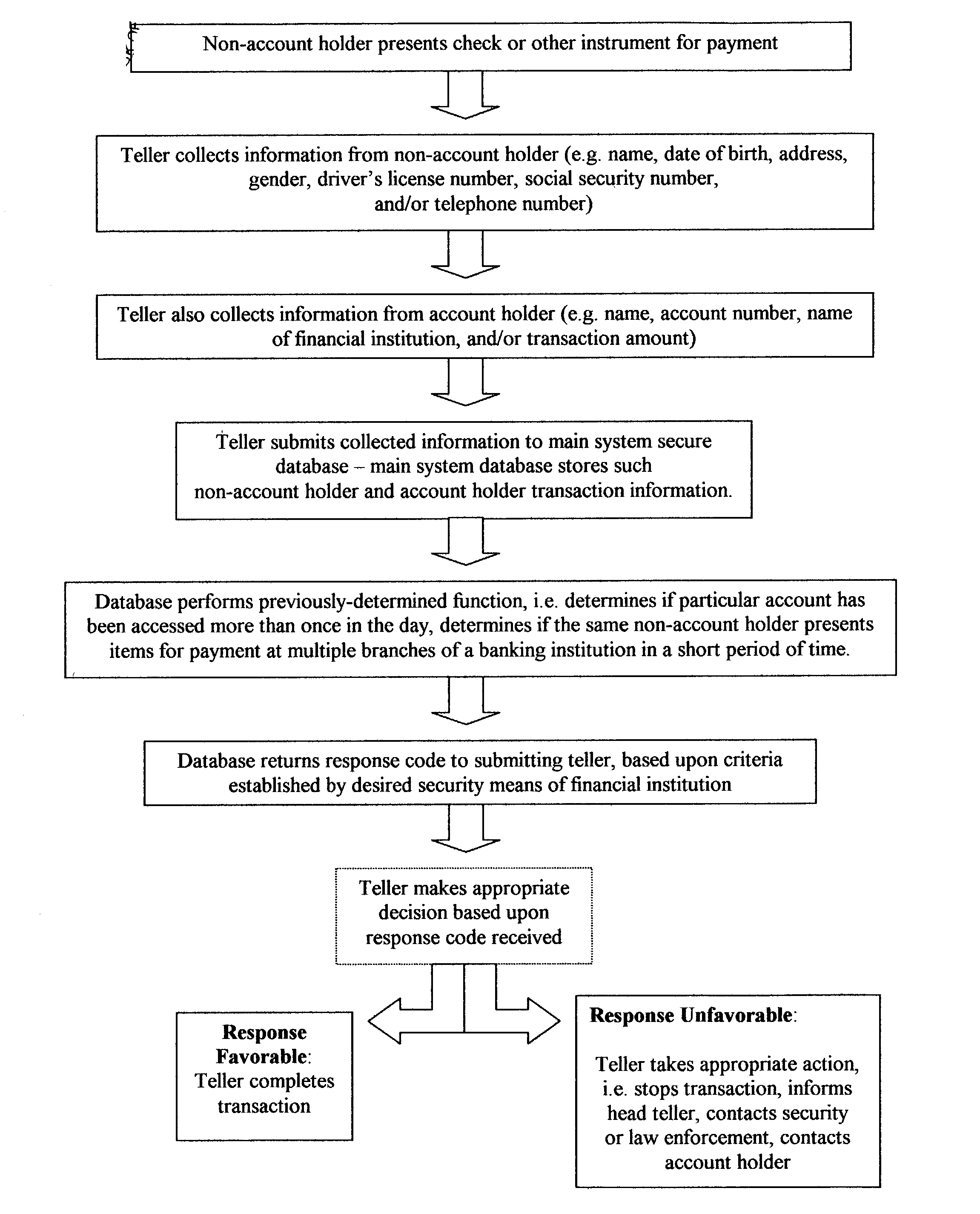
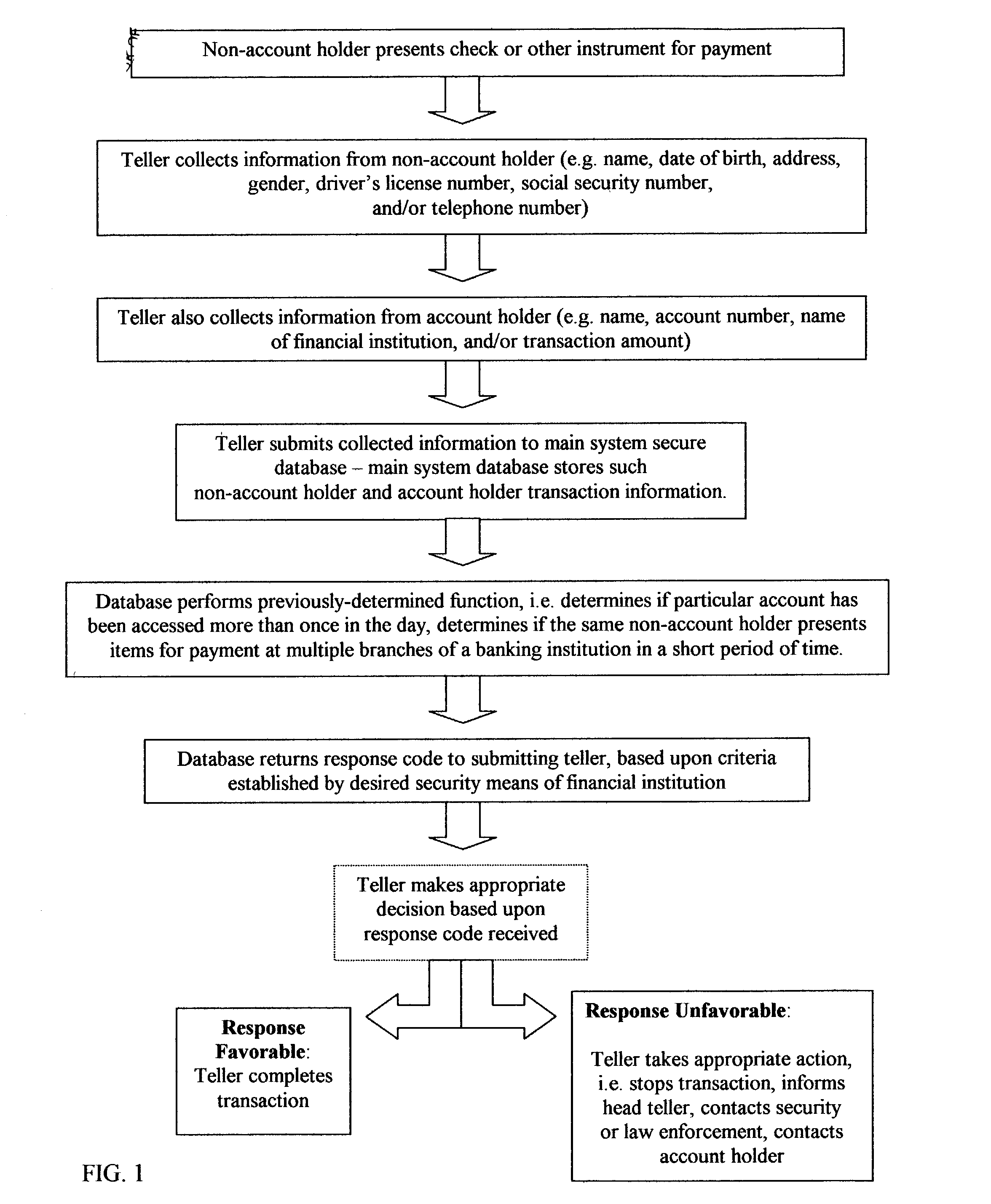
A fraud detection and security system for financial institutions utilizes a secure database of information relating to financial transactions of non-account holders who present checks and other instruments for payment. The system collects and tracks the frequency of particular aspects of the subject's behavior, and flags deviations from such norms for the purpose of indicating that fraudulent or criminal behavior may be occurring. At such time, the teller or other employee with whom the subject is dealing may stop the transaction, to the benefit of the financial institution and account holder. The system also allows for law enforcement to detect related transactions, or a string of criminal activity from the same perpetrator. In the preferred mode, the system includes a teller collecting information from the non-account holder, including name, date of birth, address, gender, driver's license number, social security number, and / or telephone number. At the time of the transaction, such data is submitted to the system database and the database returns a response code based upon criteria established by the financial institution's desired security measures, accomplished by installation of new software or by integration of a custom program. The system alerts tellers to suspicious activity, such as when a particular account is accessed more than once in a day, or when the same non-account holder presents items for payment at multiple branches of a banking institution in a short period of time.
Owner:TAYLOR MICHAEL K
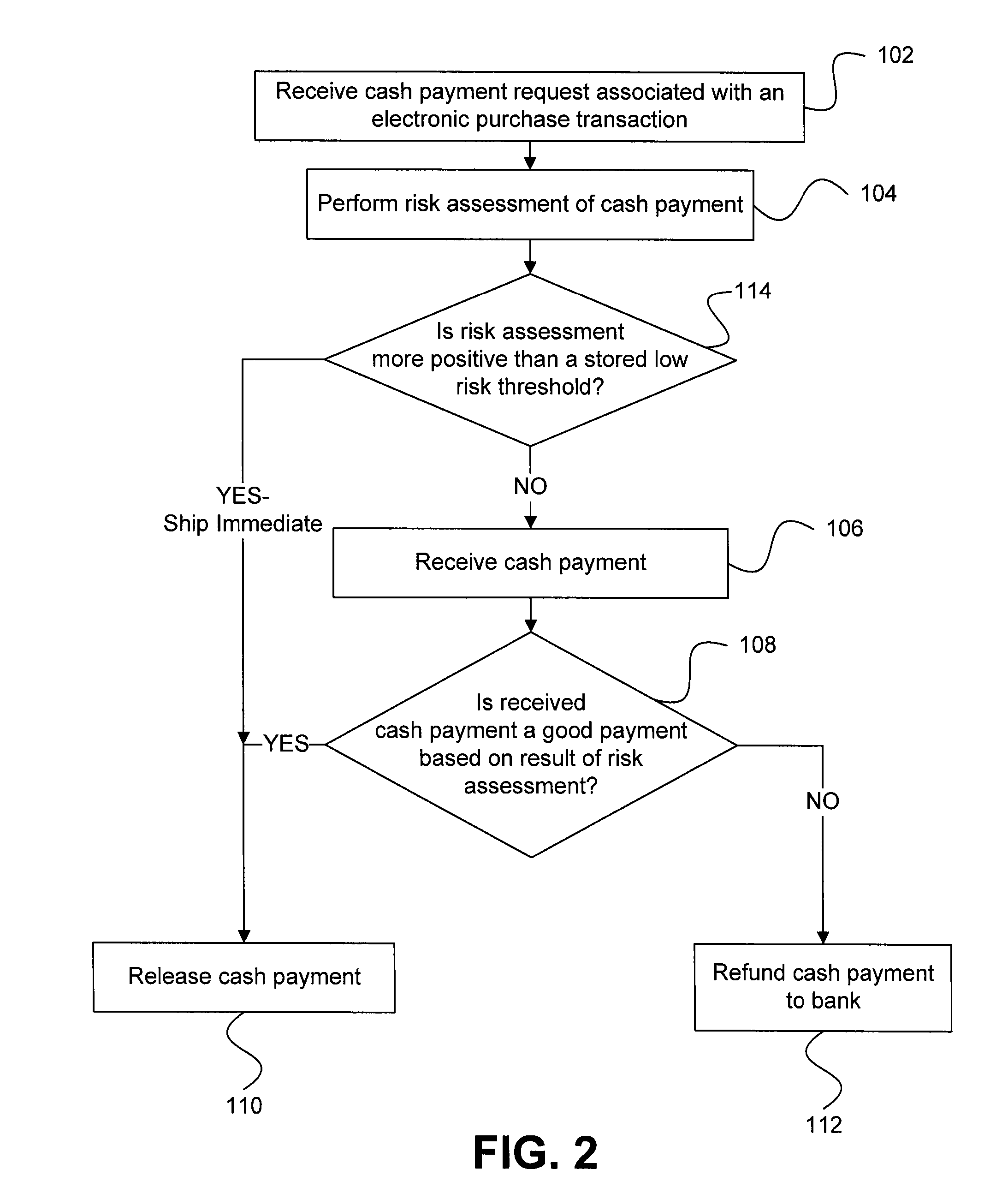
Risk detection and assessment of cash payment for electronic purchase transactions
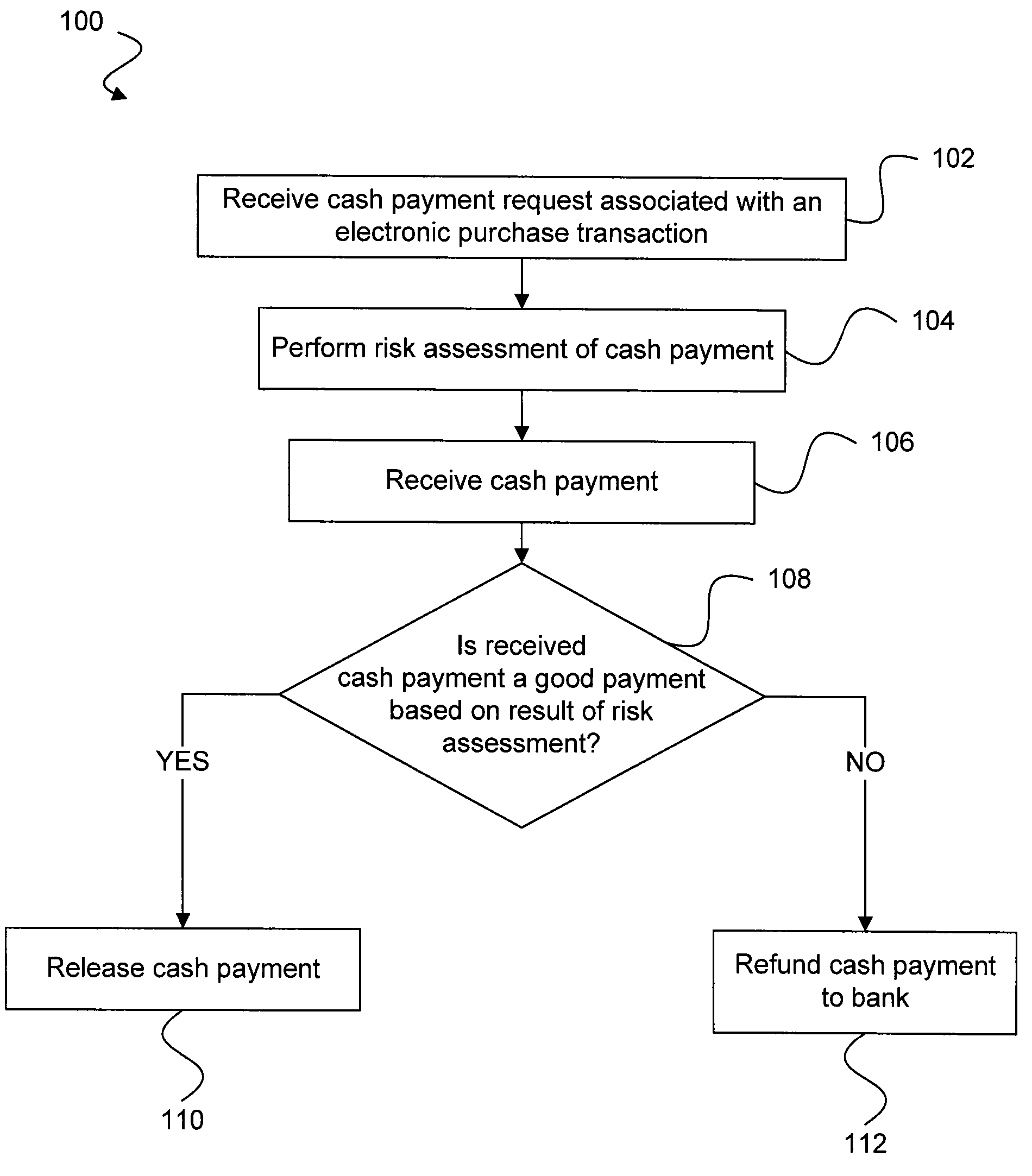
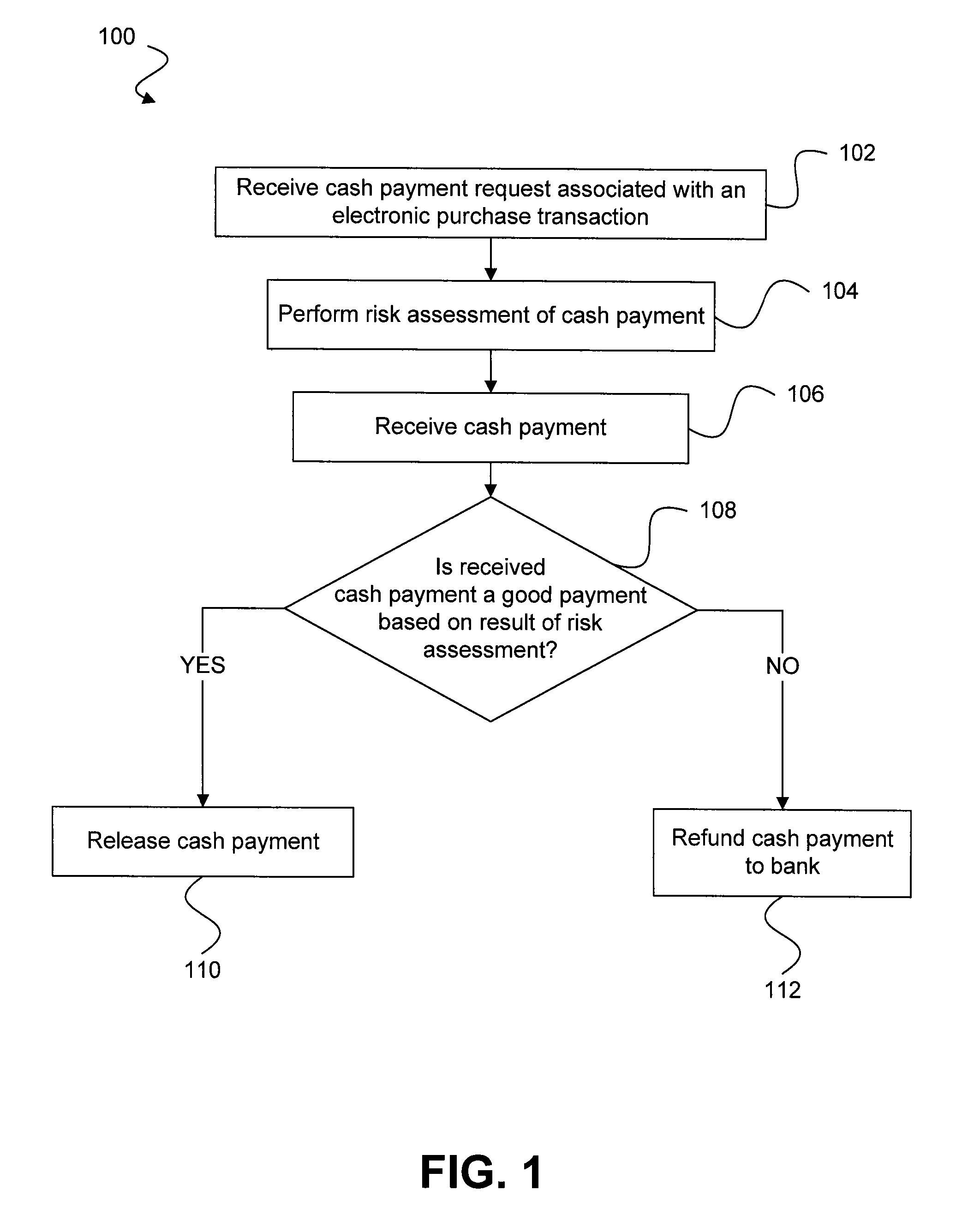
A system and methods are provided which allow consumers to pay for ecommerce transactions through online bill payment and for merchants to determine that payments are not fraudulent. The system and methods do not rely on personal or confidential customer information relating to credit-cards and / or bank account routing information, date of birth and / or social security number. A risk manager can perform risk assessment for the cash payment based on order information and non-confidential purchaser information included in a cash payment request. In response to receiving an indication of the cash payment from the purchaser, a determination is made whether the cash payment is a good payment based on the risk assessment. The cash payment is released to a merchant in response to a determination that the cash payment is a good payment.
Owner:WESTERN UNION FINANCIAL SERVICES
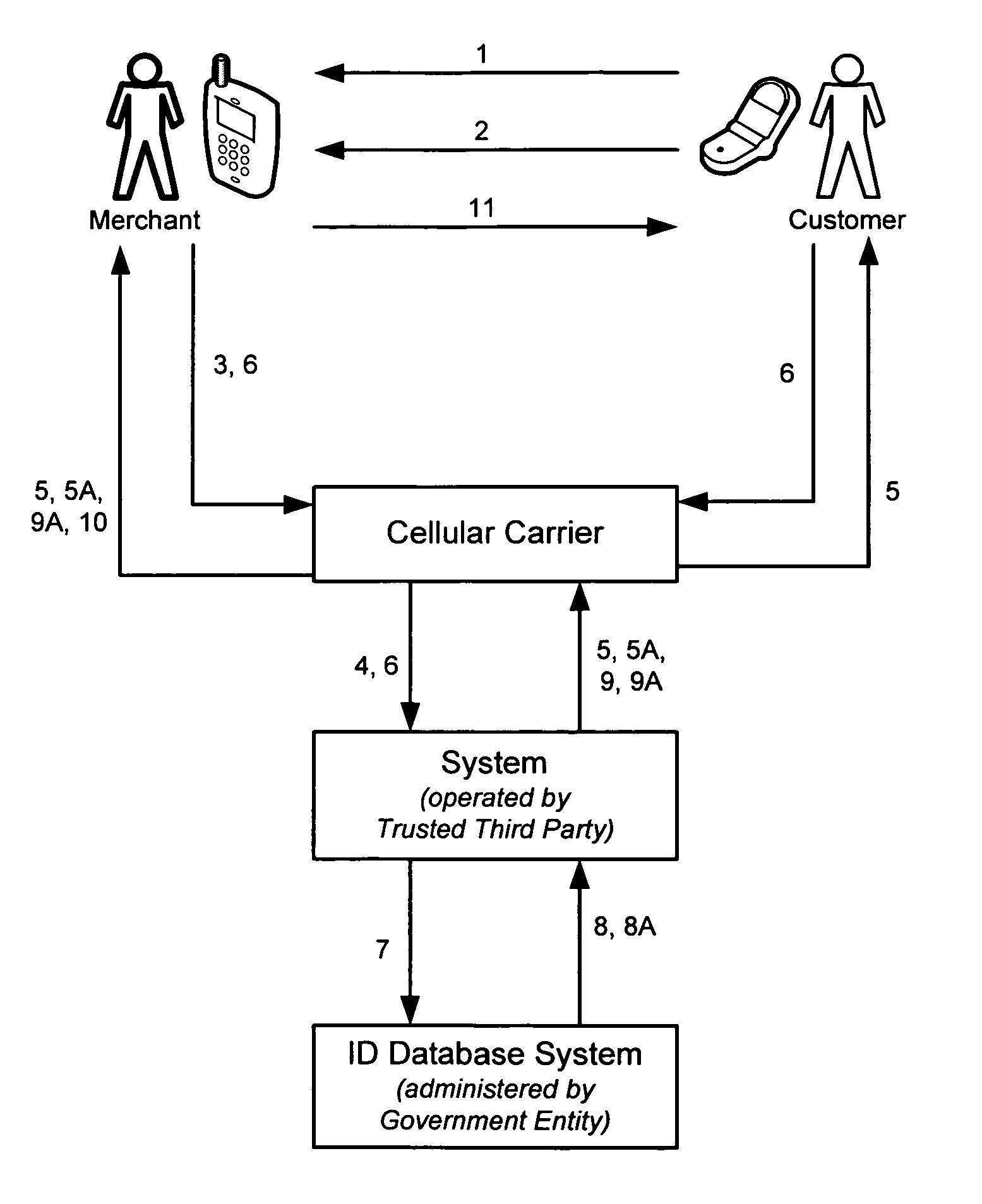
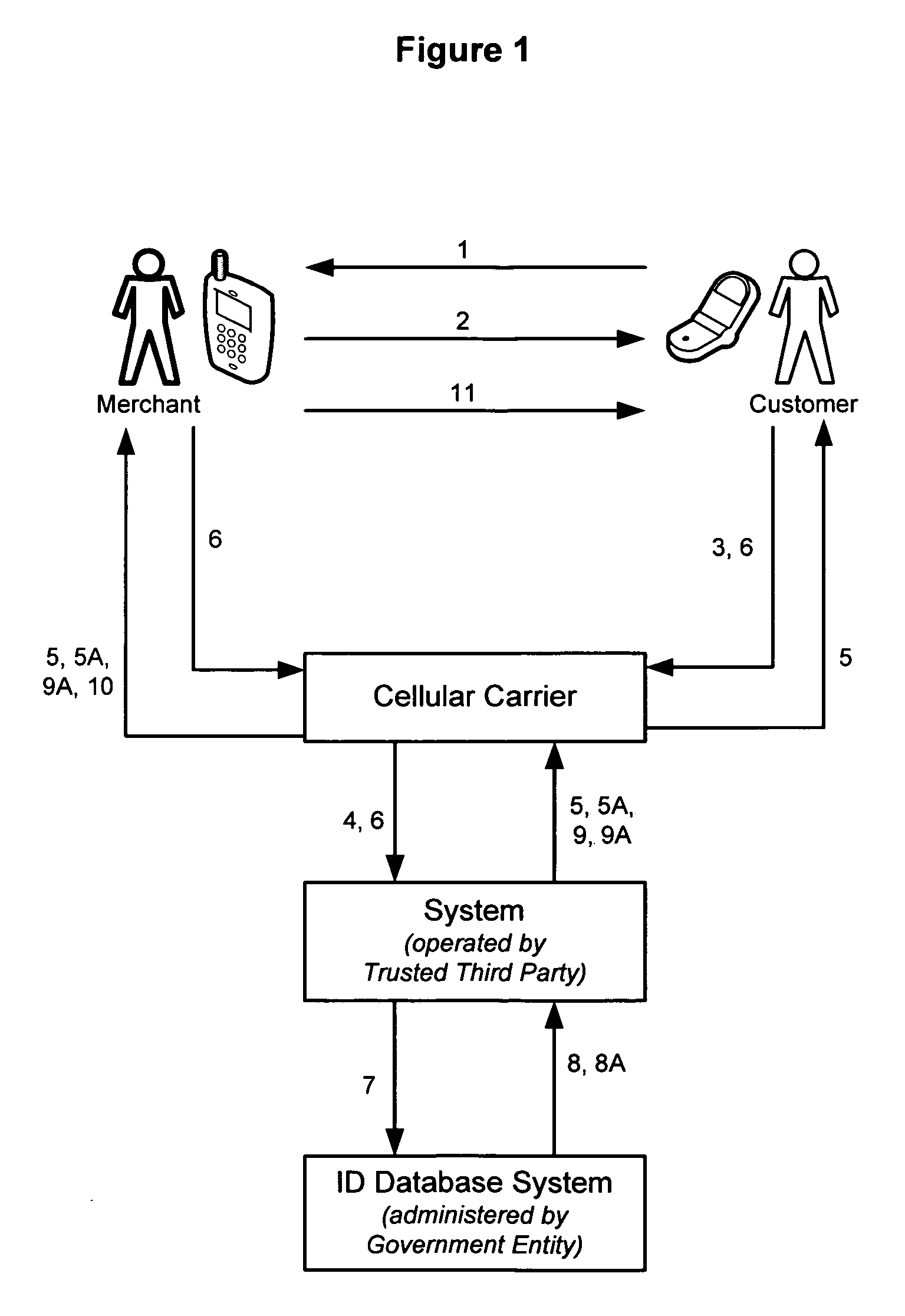
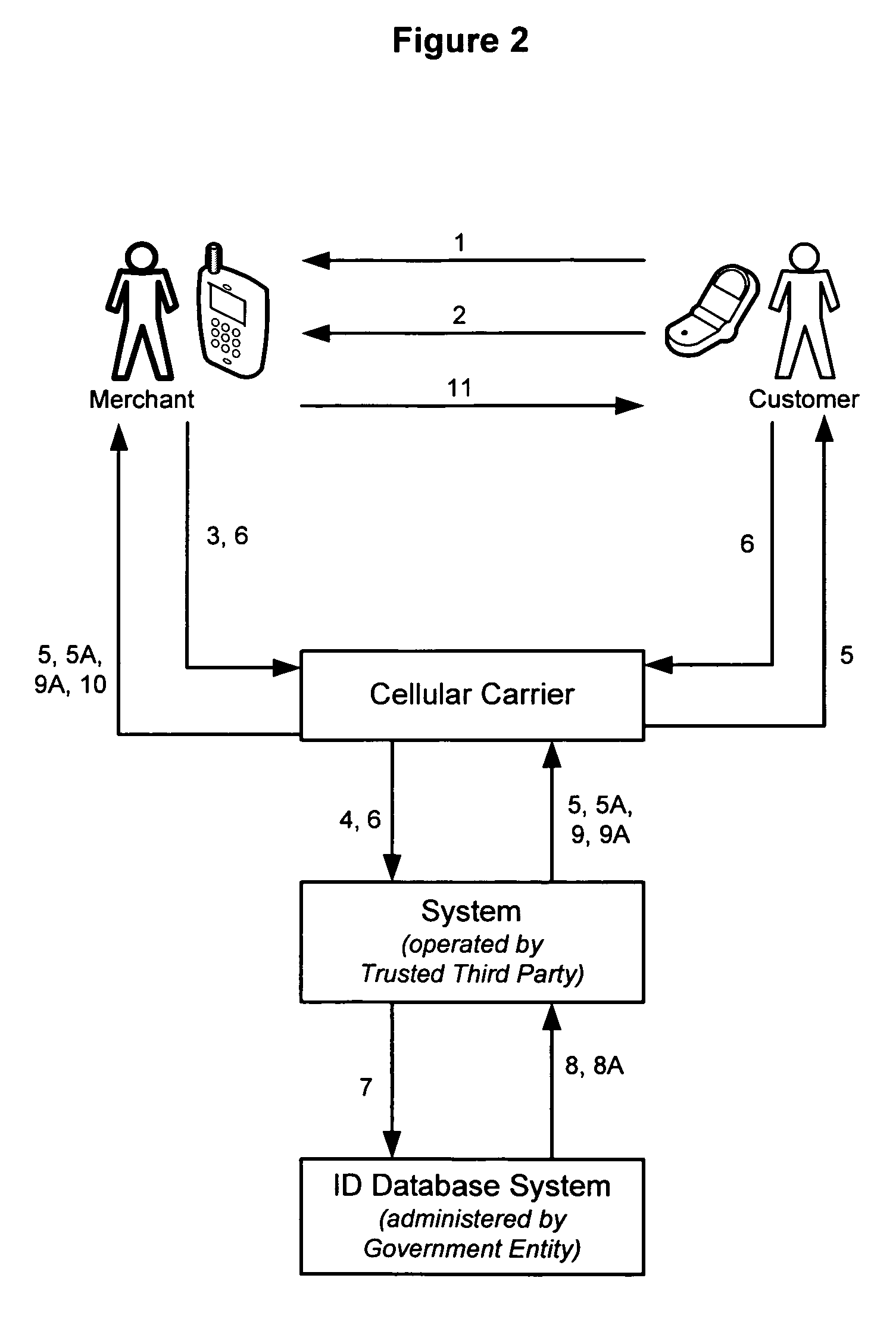
System and method for establishing or verifying a person's identity using SMS and MMS over a wireless communications network
Individuals asked to present two forms of picture identification face a problem as individuals usually only have one form of picture ID, that form of identification generally being a state-issued driver's license. The disclosed invention is a system and method for a party, generally a Customer or Patron, to establish proof of identification to another party, generally a Merchant or Agent, via a mobile phone using the mobile communications networks. The invention thereby provides the Merchant or Agent with an additional capability to verify the identity of Customers, including verification of the date of birth of the Customer. In a preferred embodiment, the invention uses the Short Message Service (“SMS”) and Multimedia Messaging Service (“MMS”) features available on mobile phones, or other wireless communication devices, to establish the identity of a Customer after communicating a request for such identification to a government administered identification database system.
Owner:MPOWER MOBILE
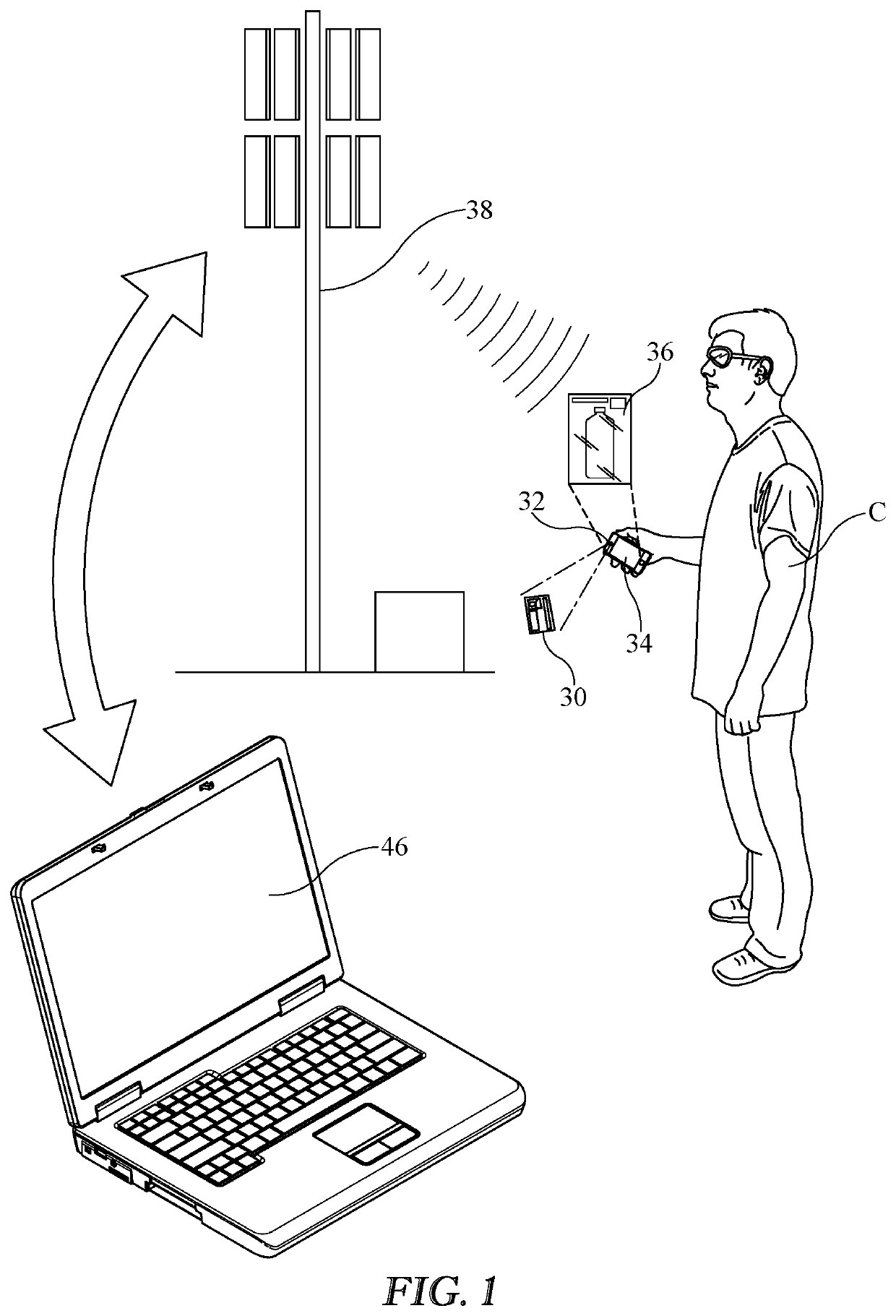
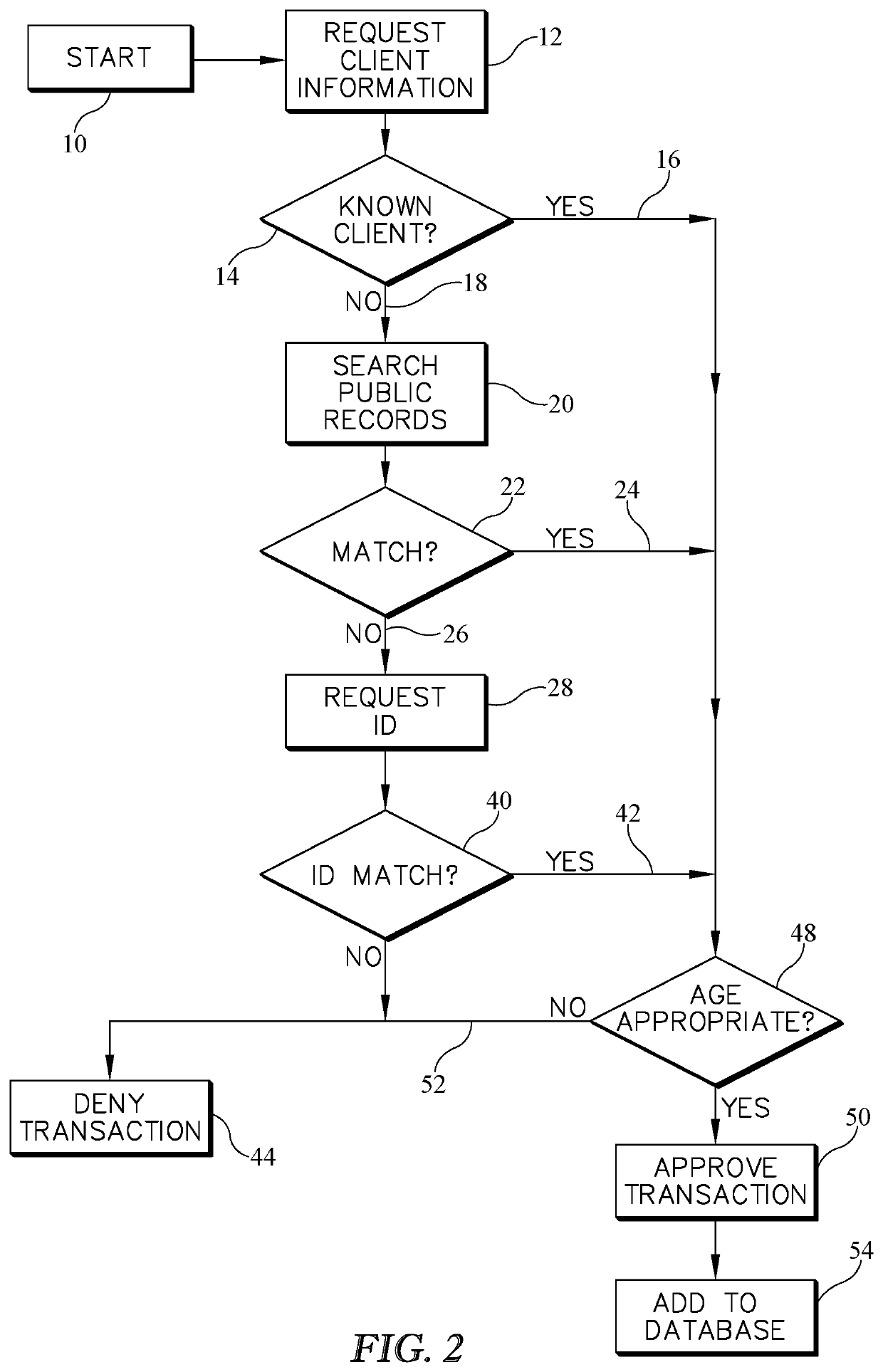
Network based age verification method
ActiveUS10984458B1Easily and quickly checkSimple subroutineWeb data indexingCharacter and pattern recognitionWeb sitePhoto identification
A method whereby the date of birth (age) of a consumer engaging in e-commerce over the Internet is verified. The present invention is launched from a merchant's website when an age sensitive transaction—alcohol or tobacco purchase, access to an adult web site, etc., —is being undertaken. The system first checks to see if the consumer is a known entity with a known date of birth. If the consumer is not known to the system, then the system checks public records from information supplied to the system by the consumer. If the date of birth is still unknown after such a check, the consumer uploads an image of photo identification which is checked for date of birth either via software or manually. Once the date of birth is known, the transaction is approved or denied based on the totality of the facts of the transaction.
Owner:BANKCARD USA MERCHANT SERVICES INC
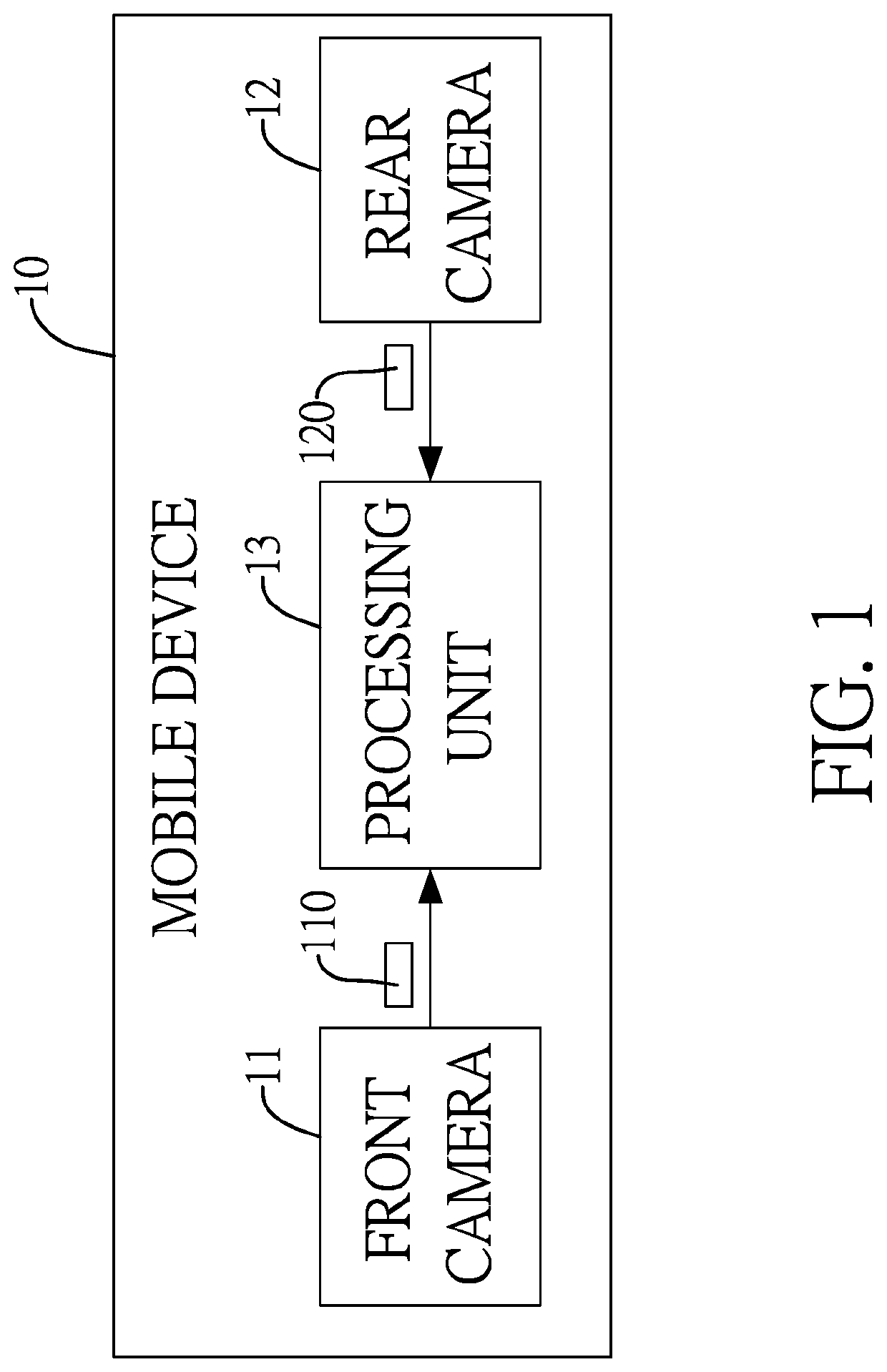
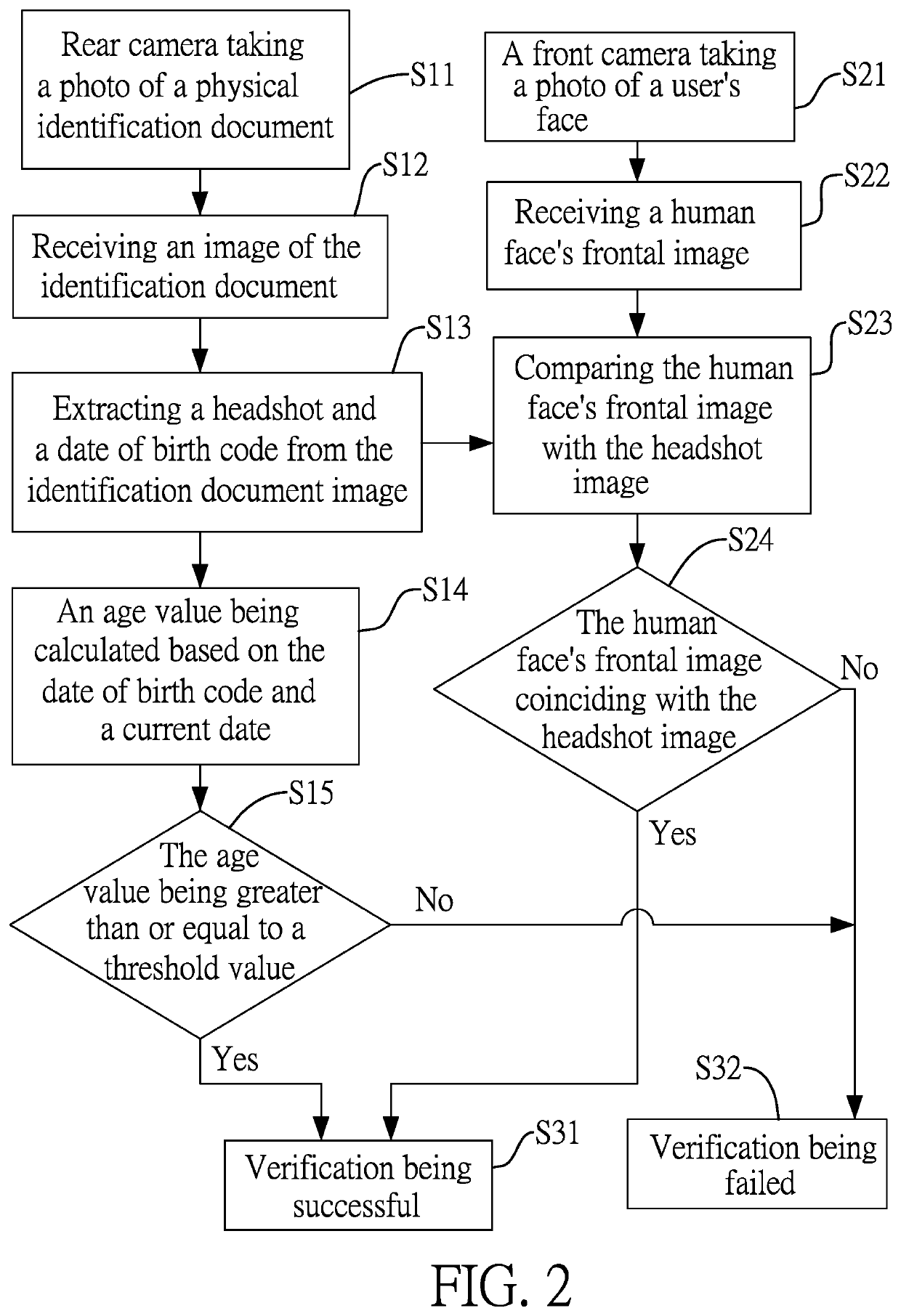
Method for verifying user identity and age
InactiveUS20190362169A1Prevent fraudAvoid identificationBuying/selling/leasing transactionsMultiple biometrics useComputer visionDate of birth
A method for verifying user identity and age includes: using a front camera to receive a frontal image of a human face; using a rear camera to receive an image of an identification document, from which a headshot and a date of birth code are extracted; determining whether there is a coincidence or not by comparing the face image and the headshot; determining whether an age value, calculated by comparing the date of birth code and a current date, is greater than or equal to a threshold value; when the face image coincides the headshot and the age value is larger than or equal to the threshold value, the verification is passed and an online transaction proceeds; when the face image is not consistent with the headshot or the age value is smaller than the threshold value, the verification fails and the online transaction is terminated.
Owner:GOOD COURAGE LTD
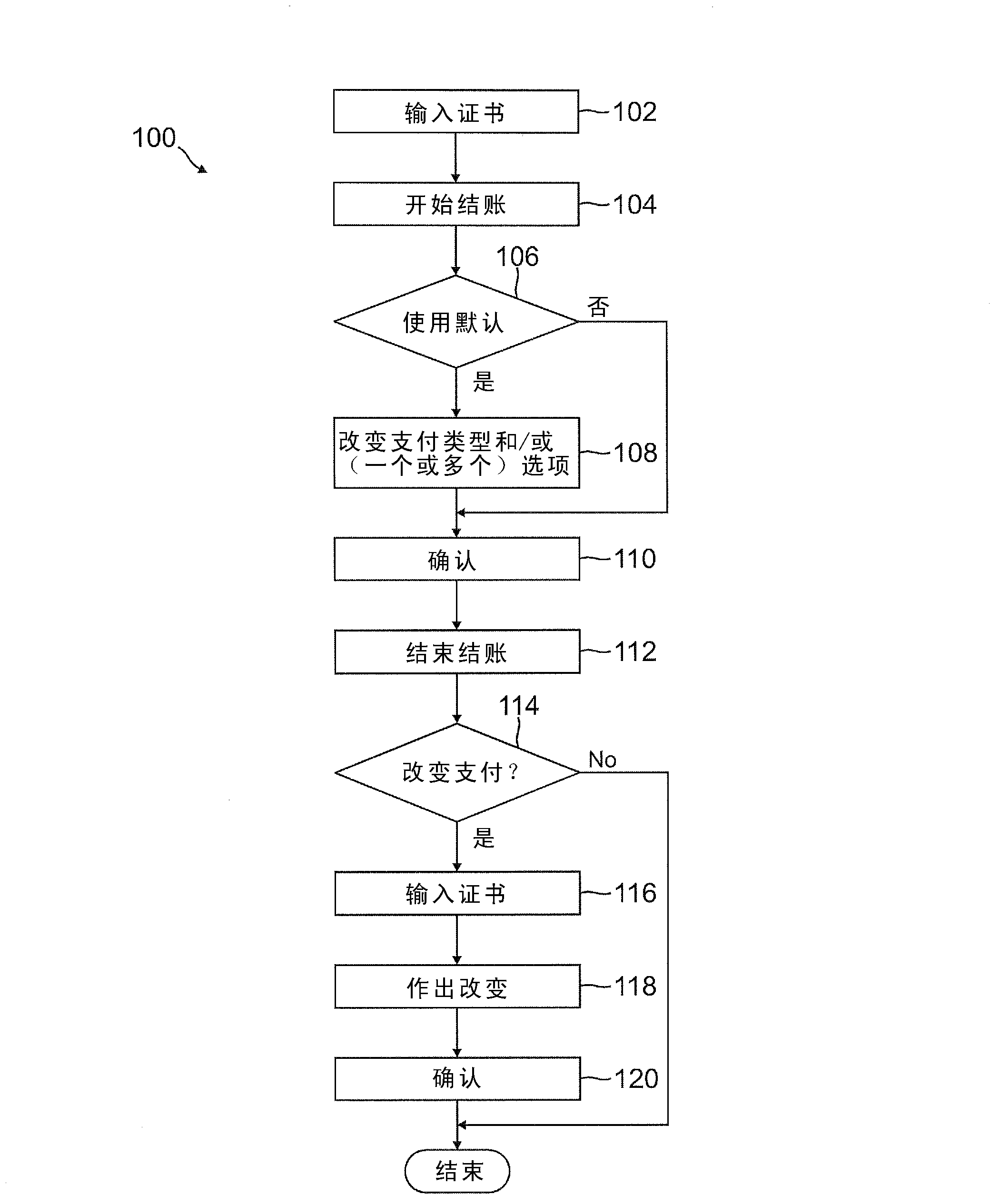
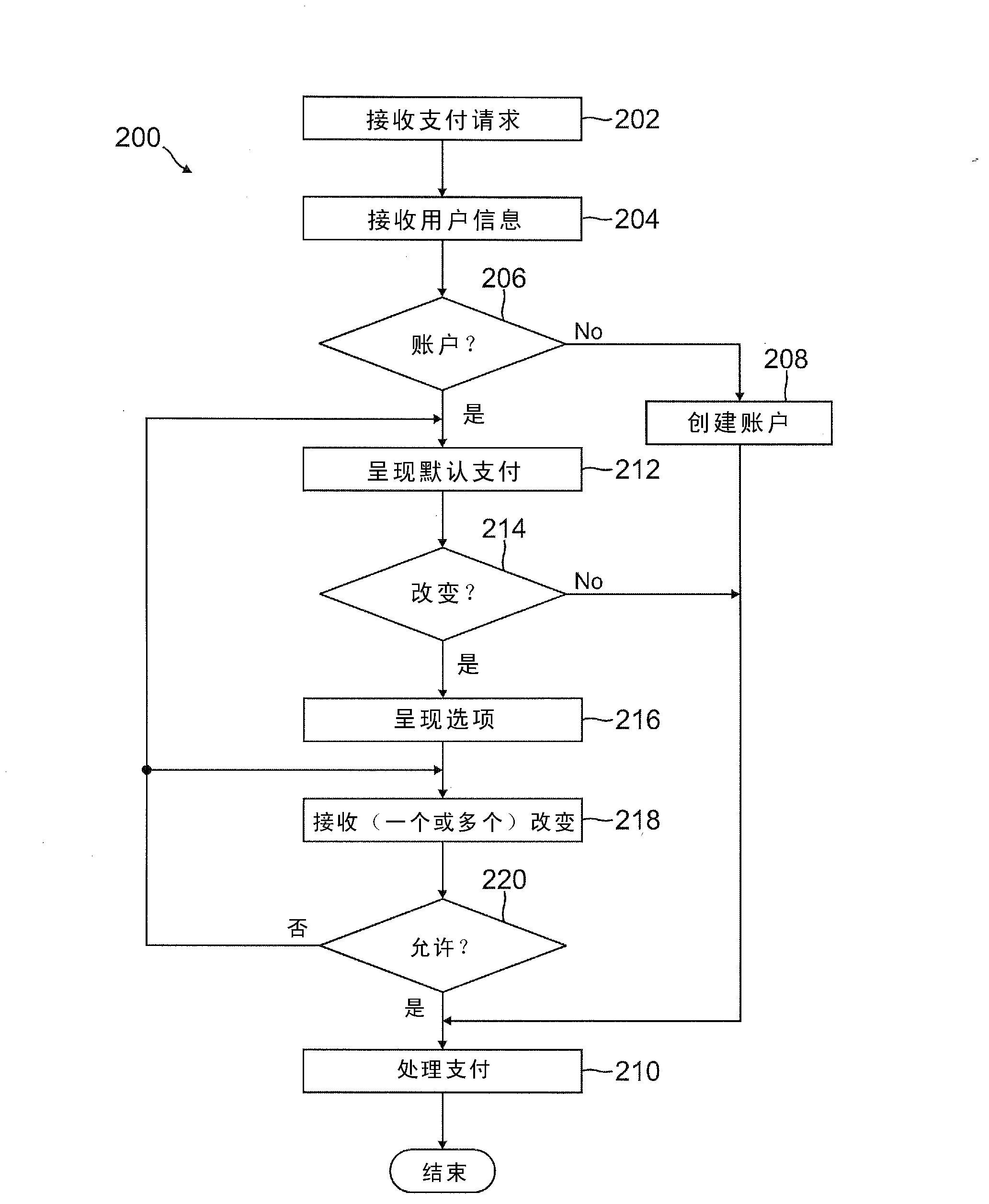
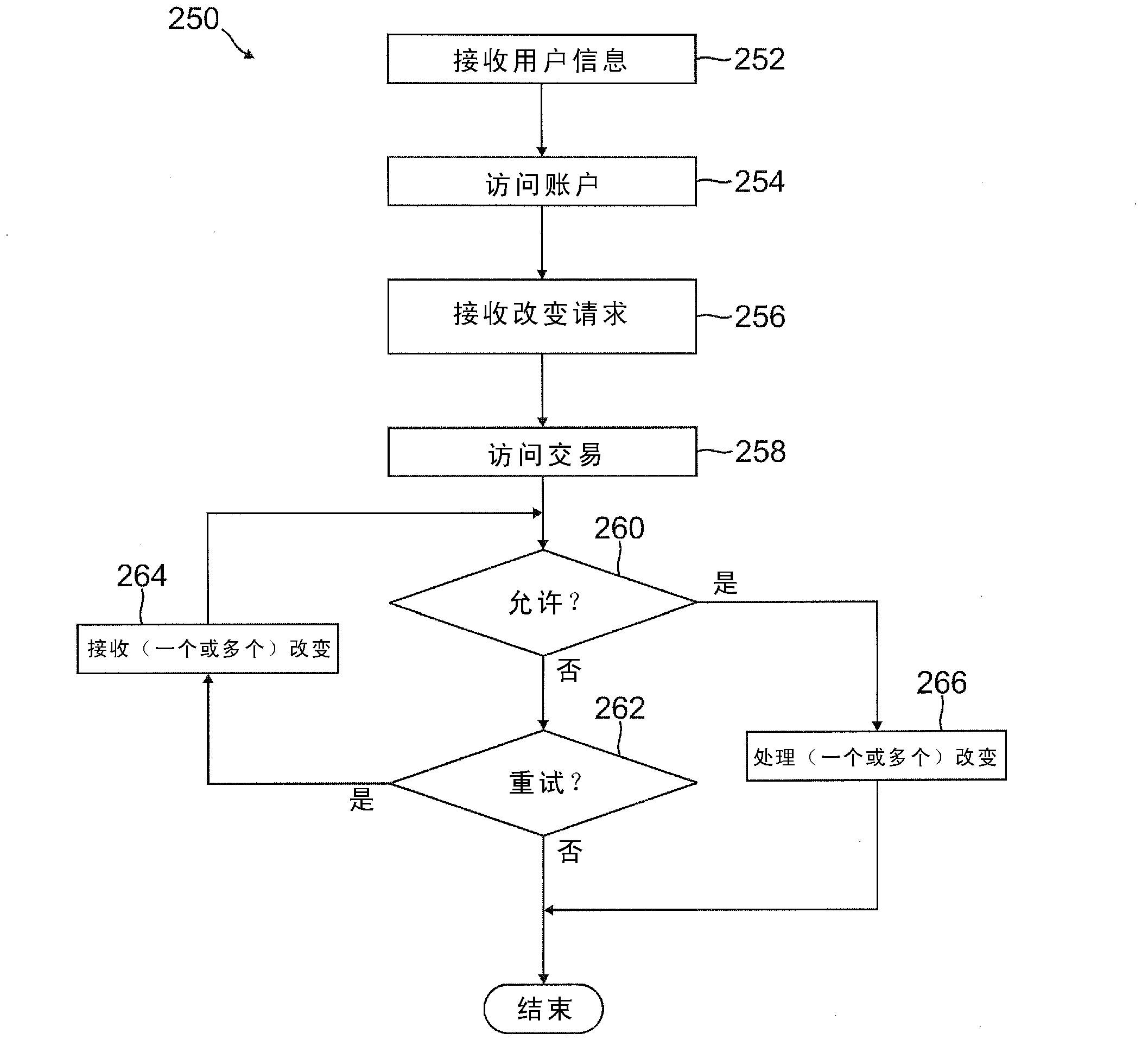
Deferred payment and selective funding and payments
InactiveUS20120166311A1Increase flexibilityEasy to controlPayment architectureBuying/selling/leasing transactionsPaymentEmail address
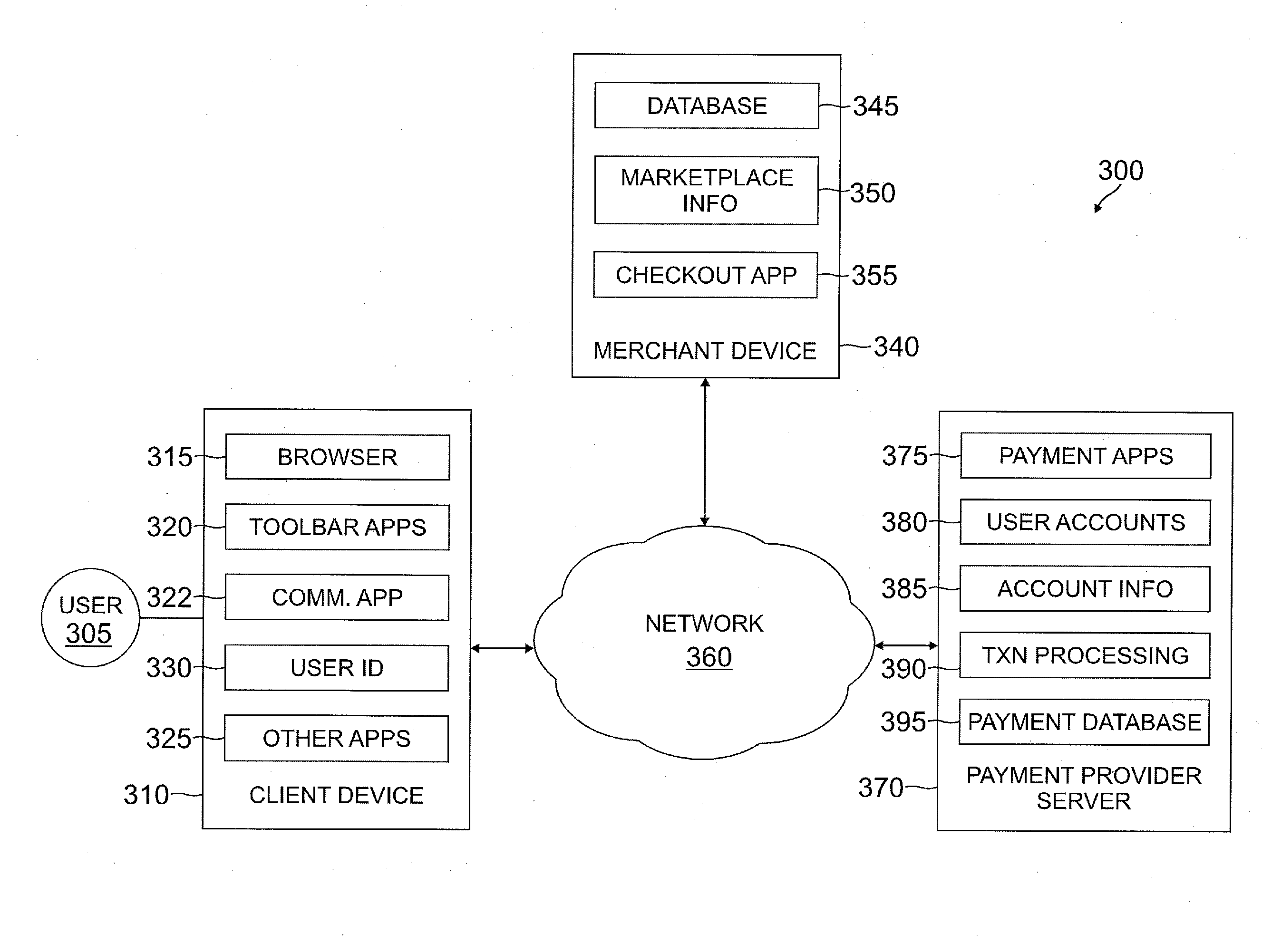
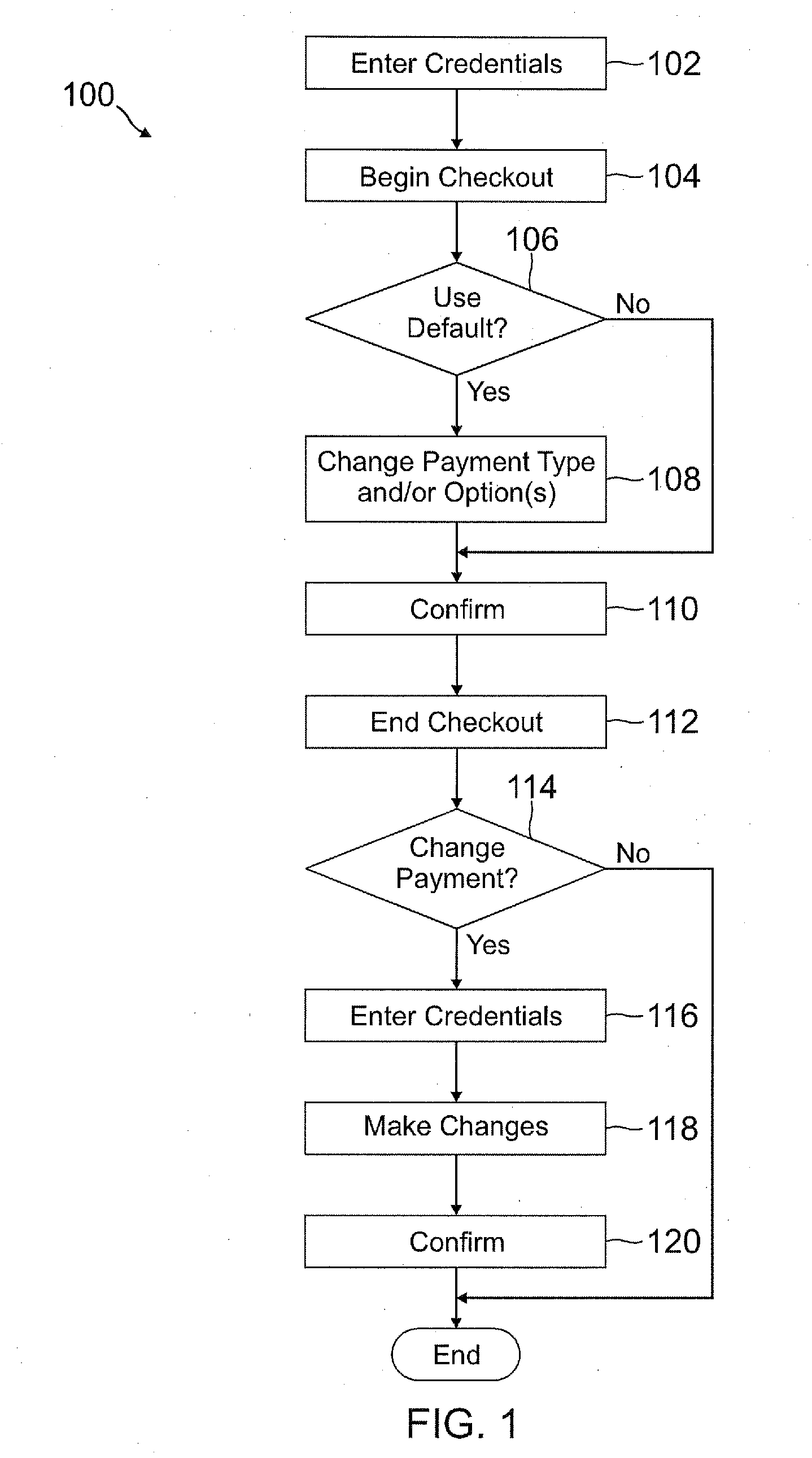
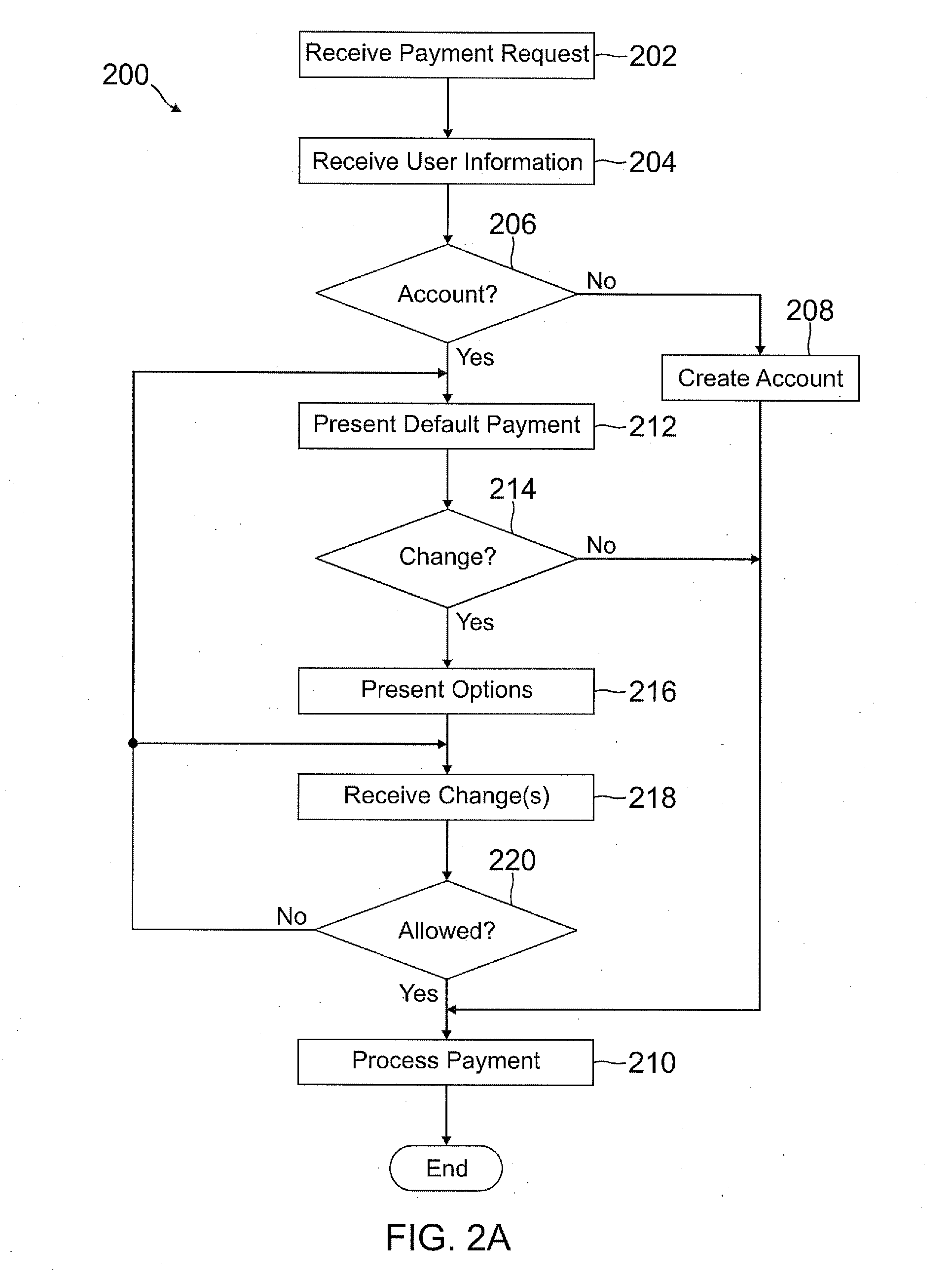
A user is able to change one or more payment options after payment has already been made to a merchant. A payment provider processes a payment request during a transaction with the merchant with default or selected payment options. After the transaction with the merchant is completed and the merchant has been paid, the user may change one or more of the payment options, such as funding source(s) and terms / conditions of payment (e.g., deferment period, installment period / amount, etc.). During the transaction, the user may make a purchase through the payment provider even if the user does not have an account with the payment provider by providing user information, such as name, address, phone number, email address, and date of birth, but not a social security number or funding source information.
Owner:PAYPAL INC
On-line anonymous age verification for controlling access to selected websites
InactiveUS20080033740A1Additional safetyImprove securityDigital data processing detailsCommerceBirth certificateService provider
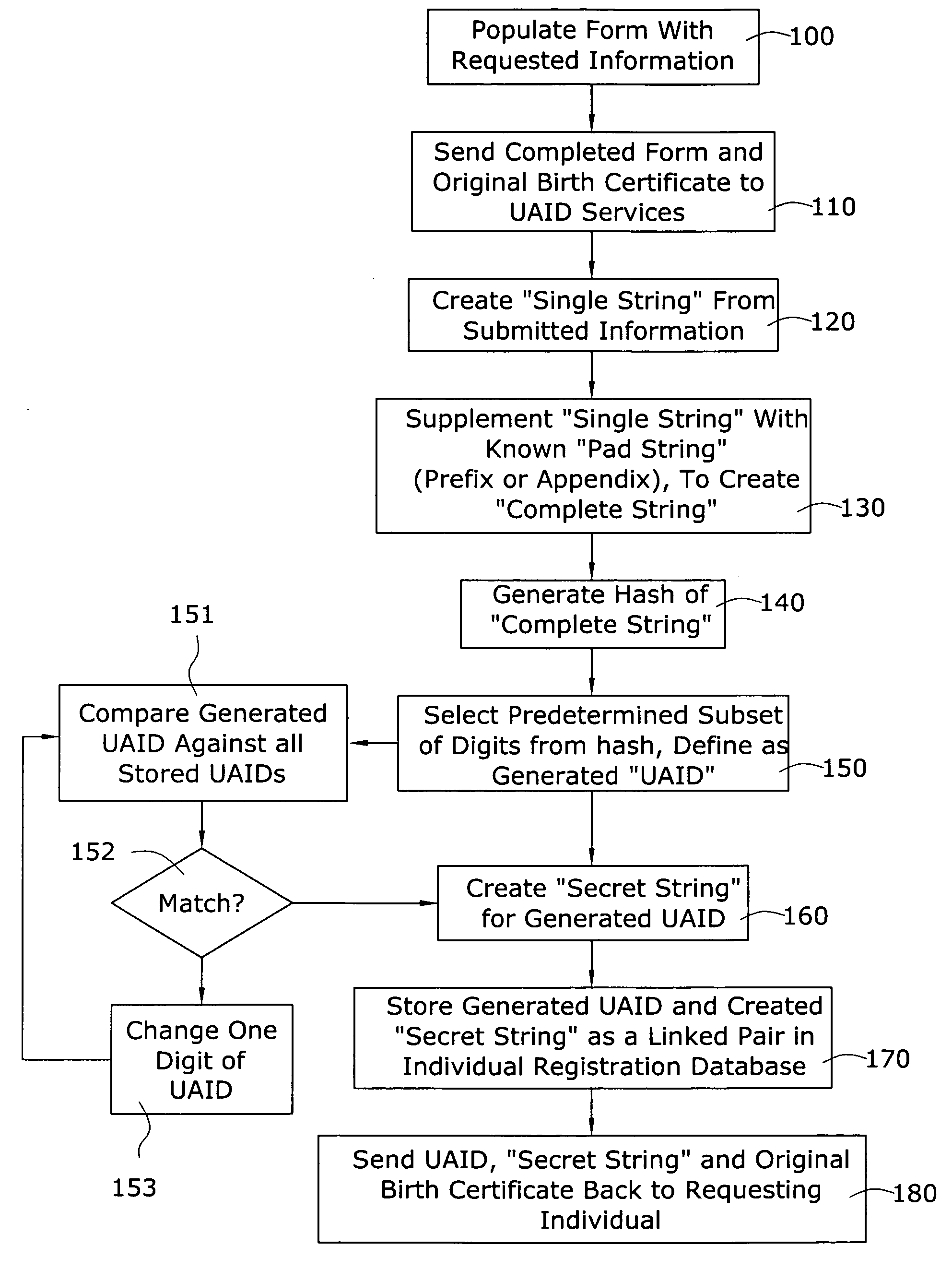
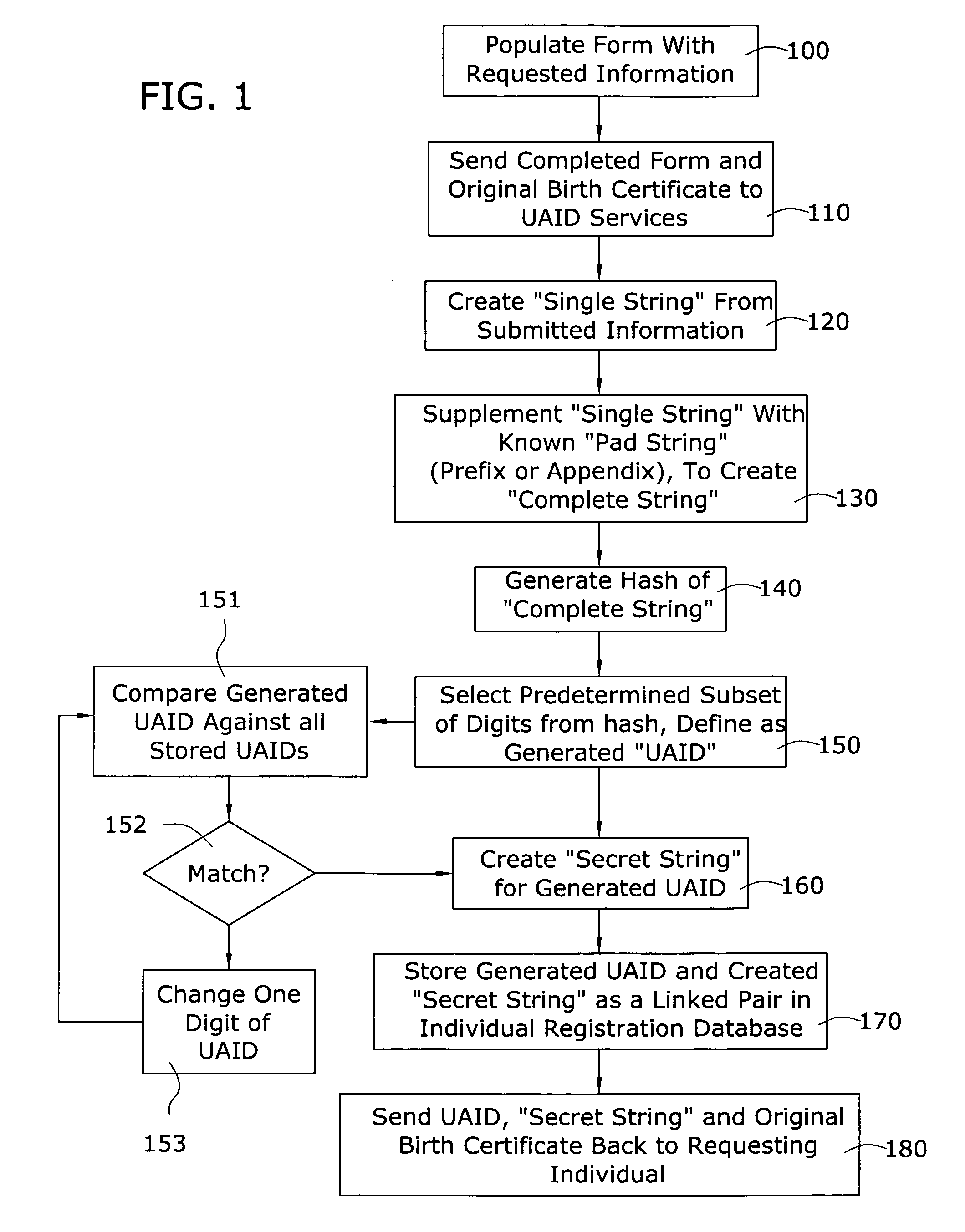
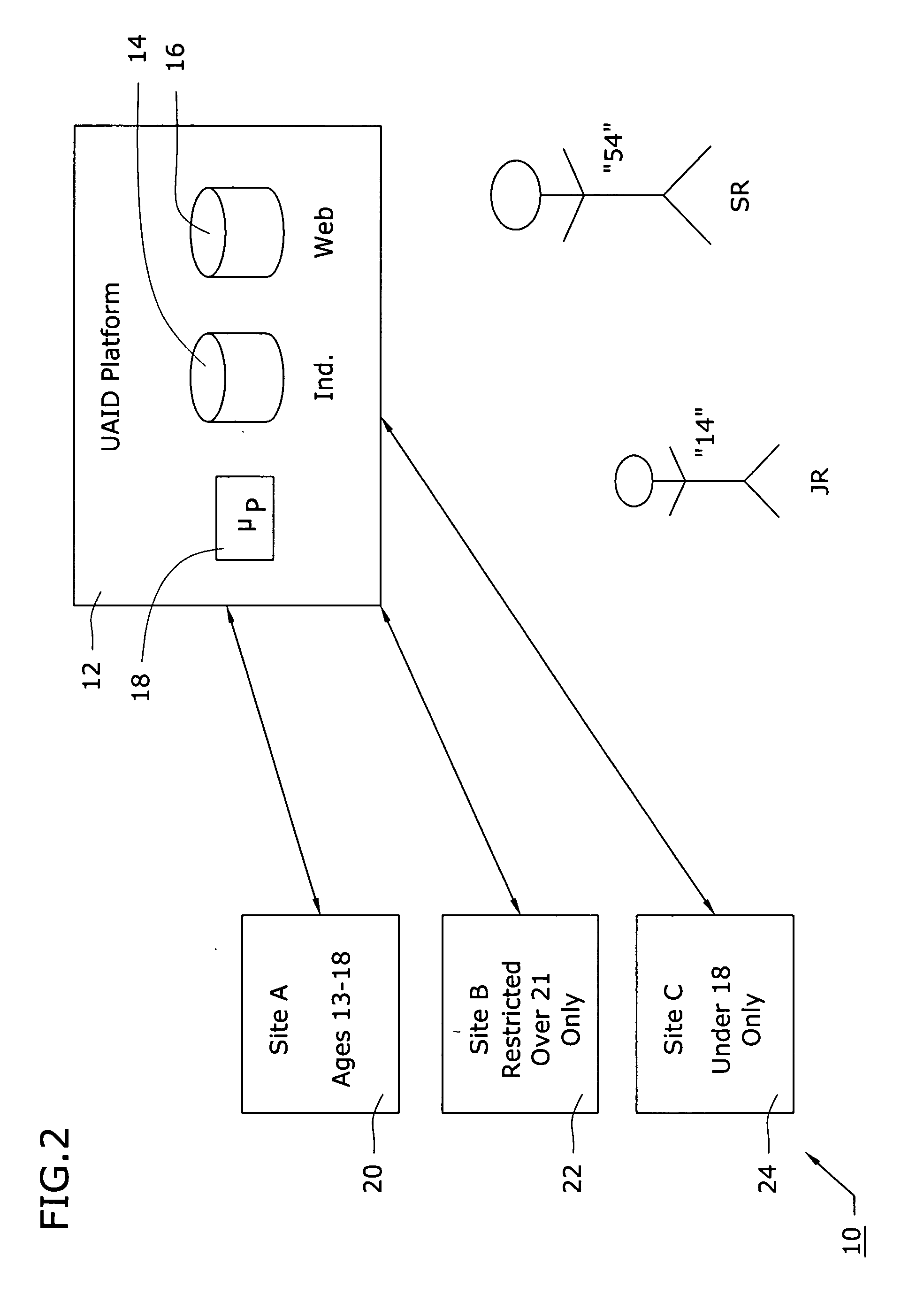
A universal age verification service is provided where individuals initially register with the service by submitting their birth certificate or other “legally authentic” documentation of age and gender (such as required to obtain a passport) to obtain a “universal ID” comprising a string of alphanumeric digits selected from a hash function that is performed on a string of information including individual's name, gender, birth date and birth location. The string is preferably supplemented by a secret, proprietary pad string known only to the service provider. A selected number of digits from the hash (preferably, at least 9 digits, and possibly, more) is then defined as the individual's “universal age / gender verification ID”. The original documentation papers and generated UAID are then conveyed by mail, in person, or otherwise, to the individual, along with a password. Once registered, the individual's UAID is used to control entry to various websites that have registered with the universal age / gender verification service.
Owner:ALBRIGHT ASSOCS
Video player and video playback method of a video player having an audio-visual restriction capability
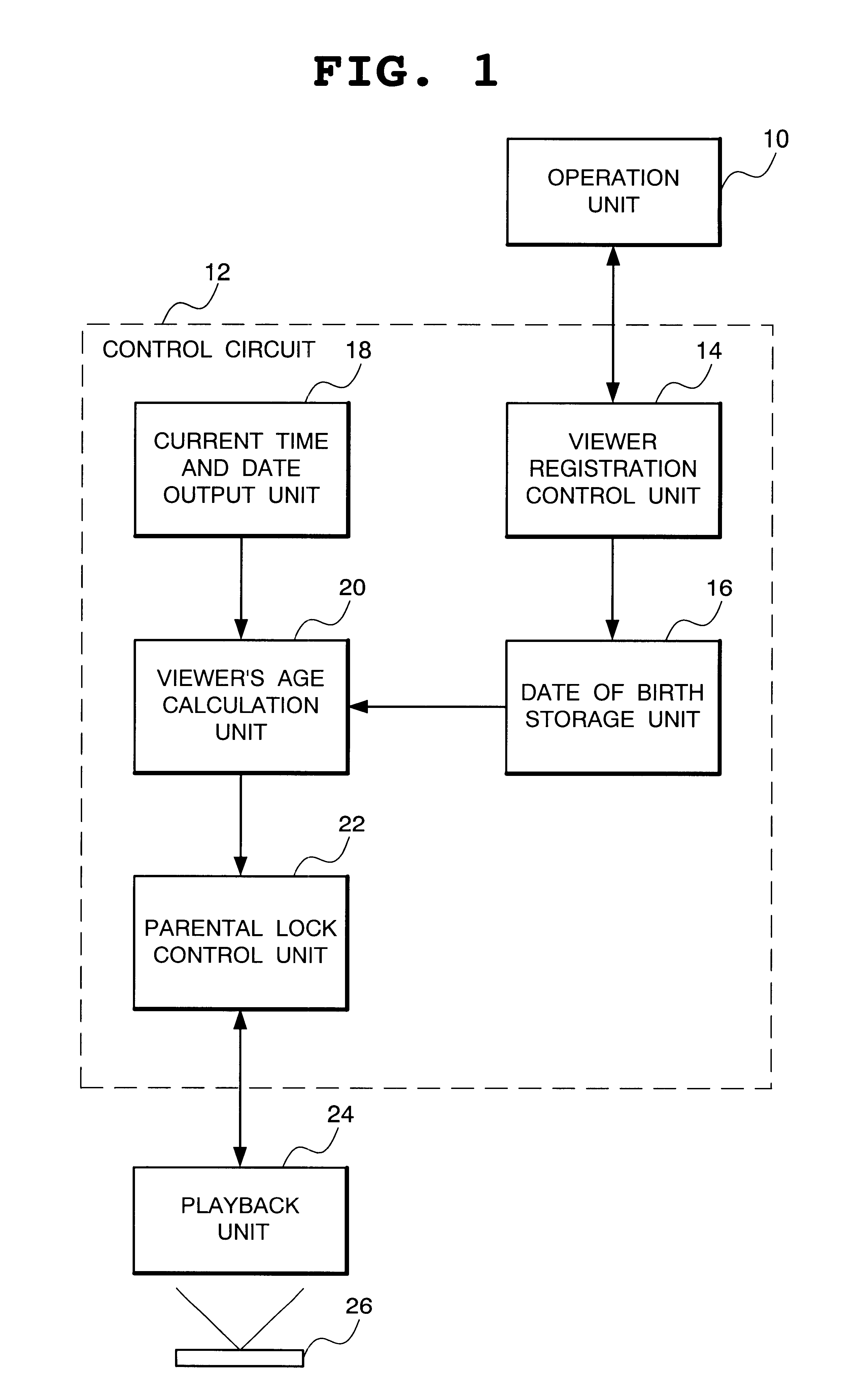
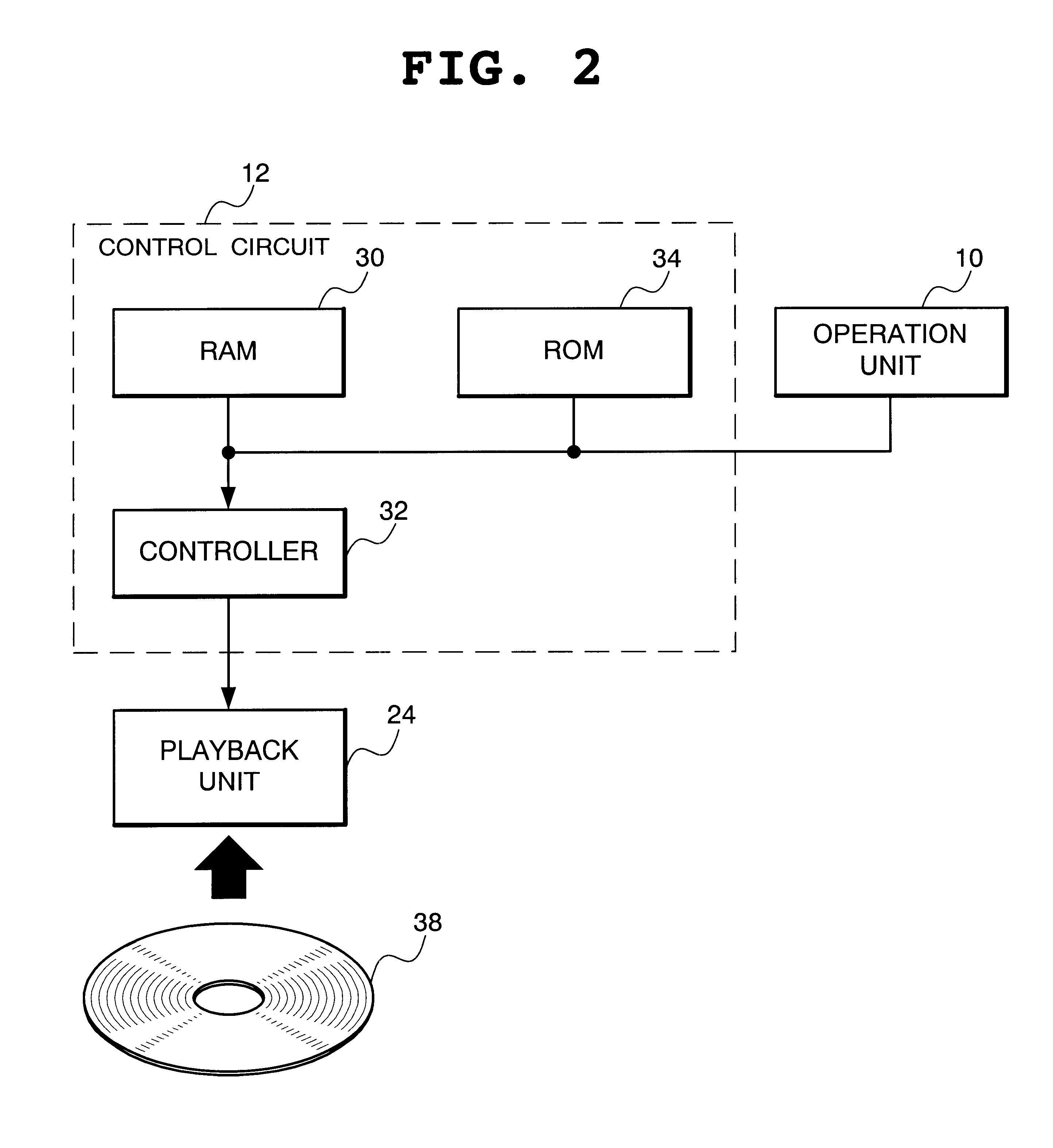
InactiveUS6847777B1Improve the inconvenienceExhibit optimumTelevision system detailsColor television signals processingVideo playerVideo record
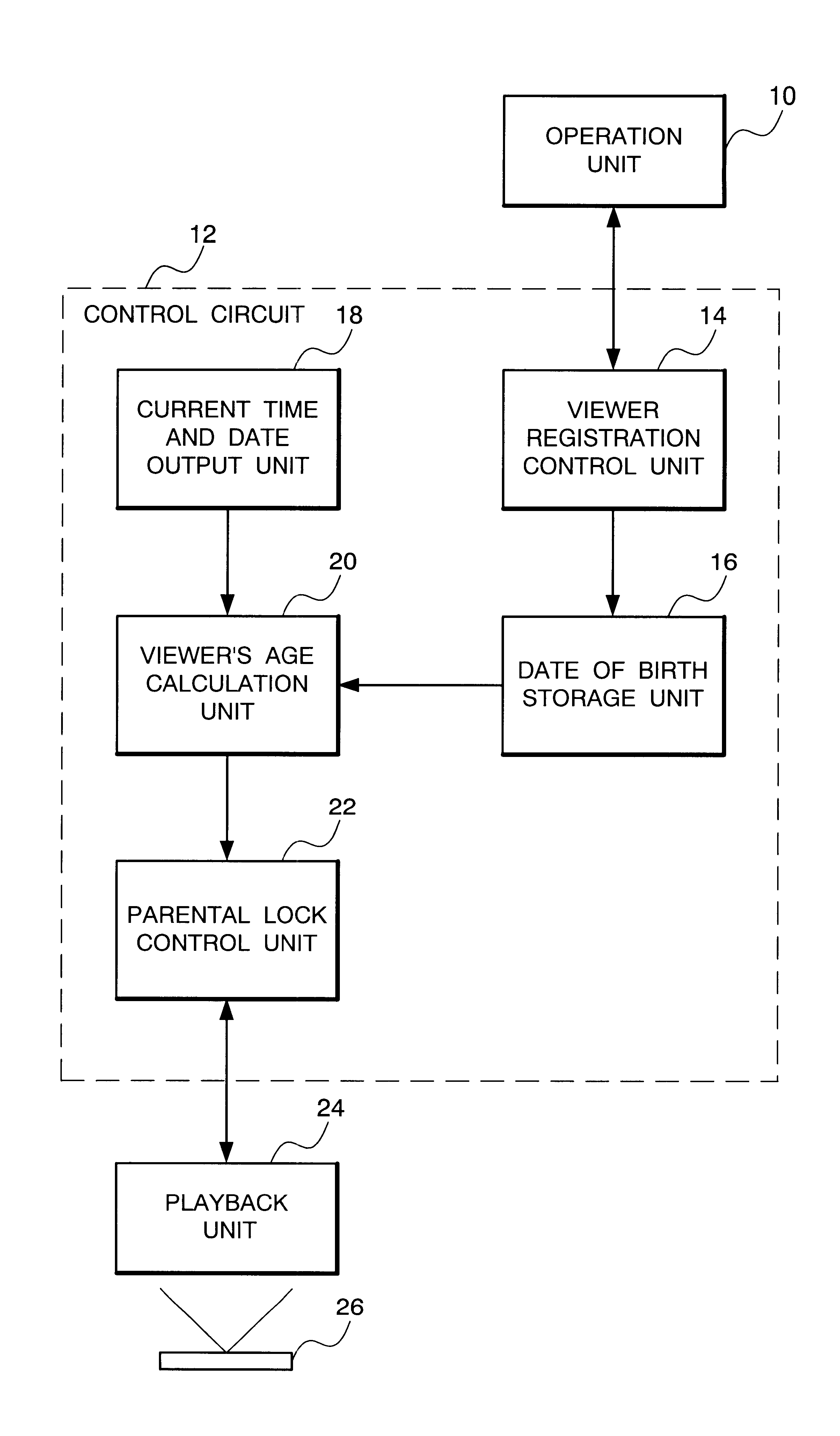
A video player including playback means for playing back a video recording medium, control means for controlling the playback means in response to external input, as well as externally outputting a video signal played back by the playback means, and operation means for inputting setting data input by a user to said control means, as well as externally displaying setting data output from the control means, said control means including a current time and date output unit for outputting current time and date, a date of birth storage unit for storing a date of birth of each viewer input through said operation means, a viewer's age calculation unit for calculating an age of each viewer based on a date of birth stored in said date of birth storage unit and current time and date output by said current time and date output unit, and a parental lock control unit for determining allowance / non-allowance of playback by said playback means based on parental lock information stored in advance in said video recording medium and an age calculated by said viewer's age calculation unit.
Owner:HTC CORP
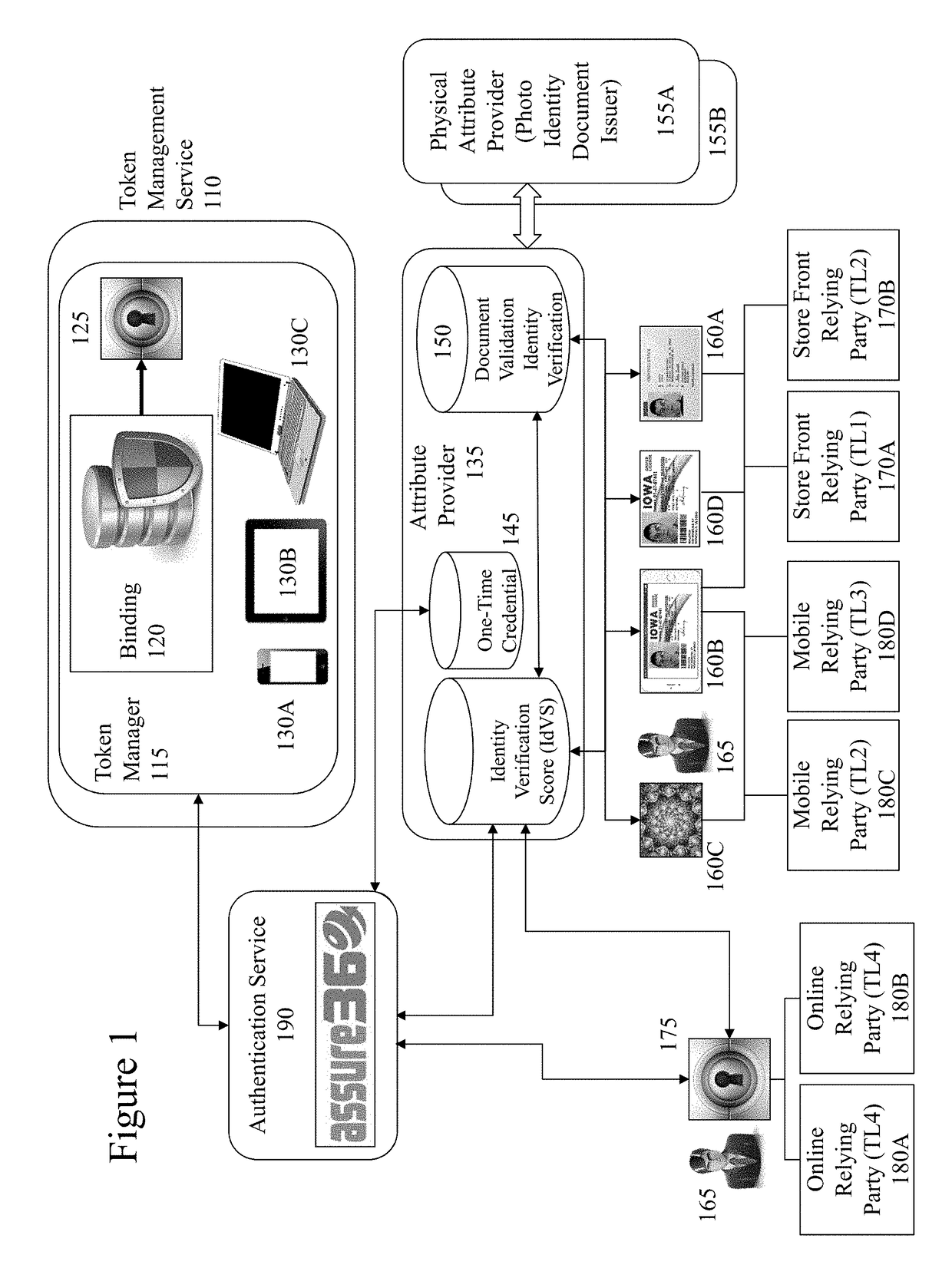
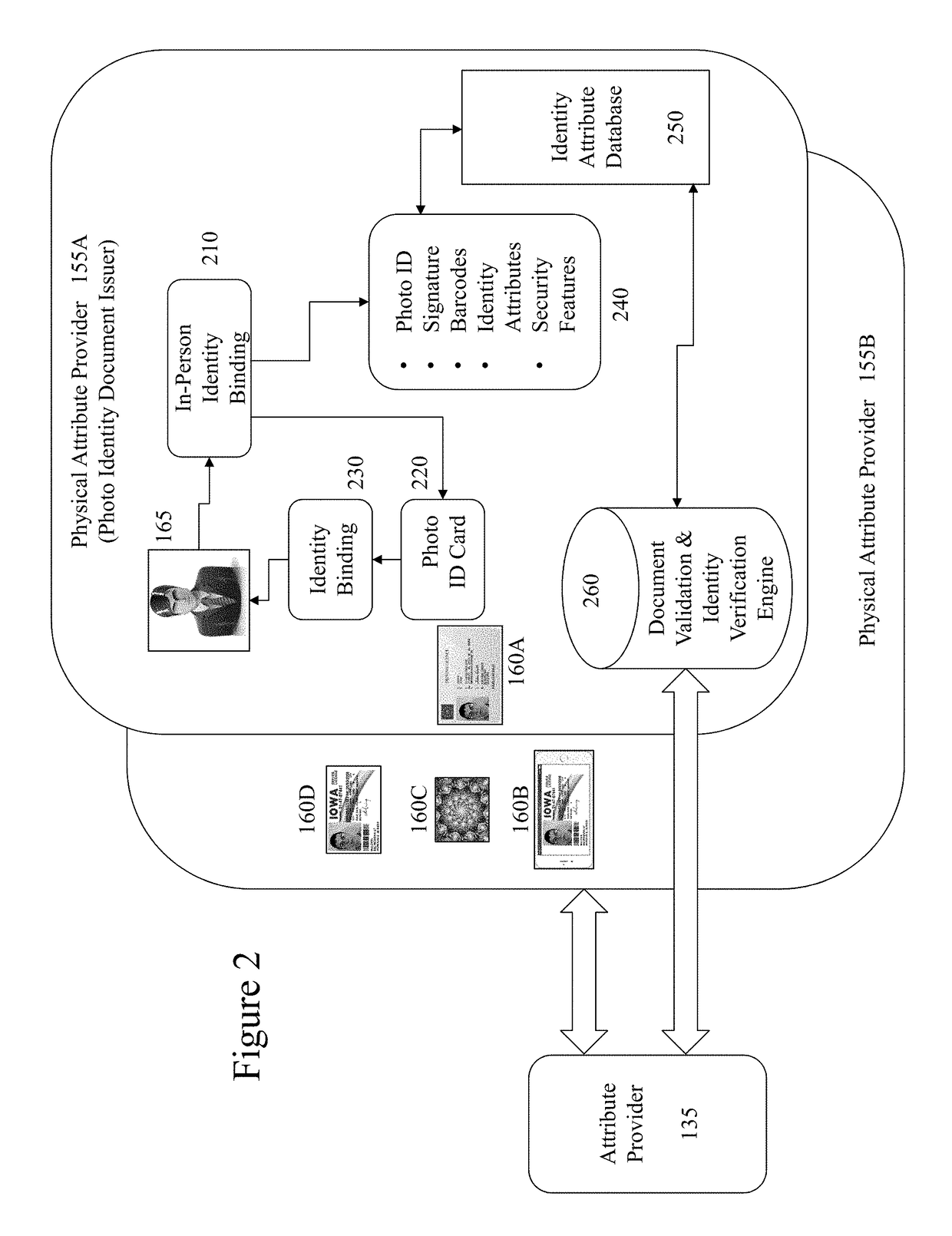
Portable verifiable credentials and methods thereof
InactiveUS20170324750A1Reduce restrictionsUser identity/authority verificationSecurity arrangementElectronic documentDocument preparation
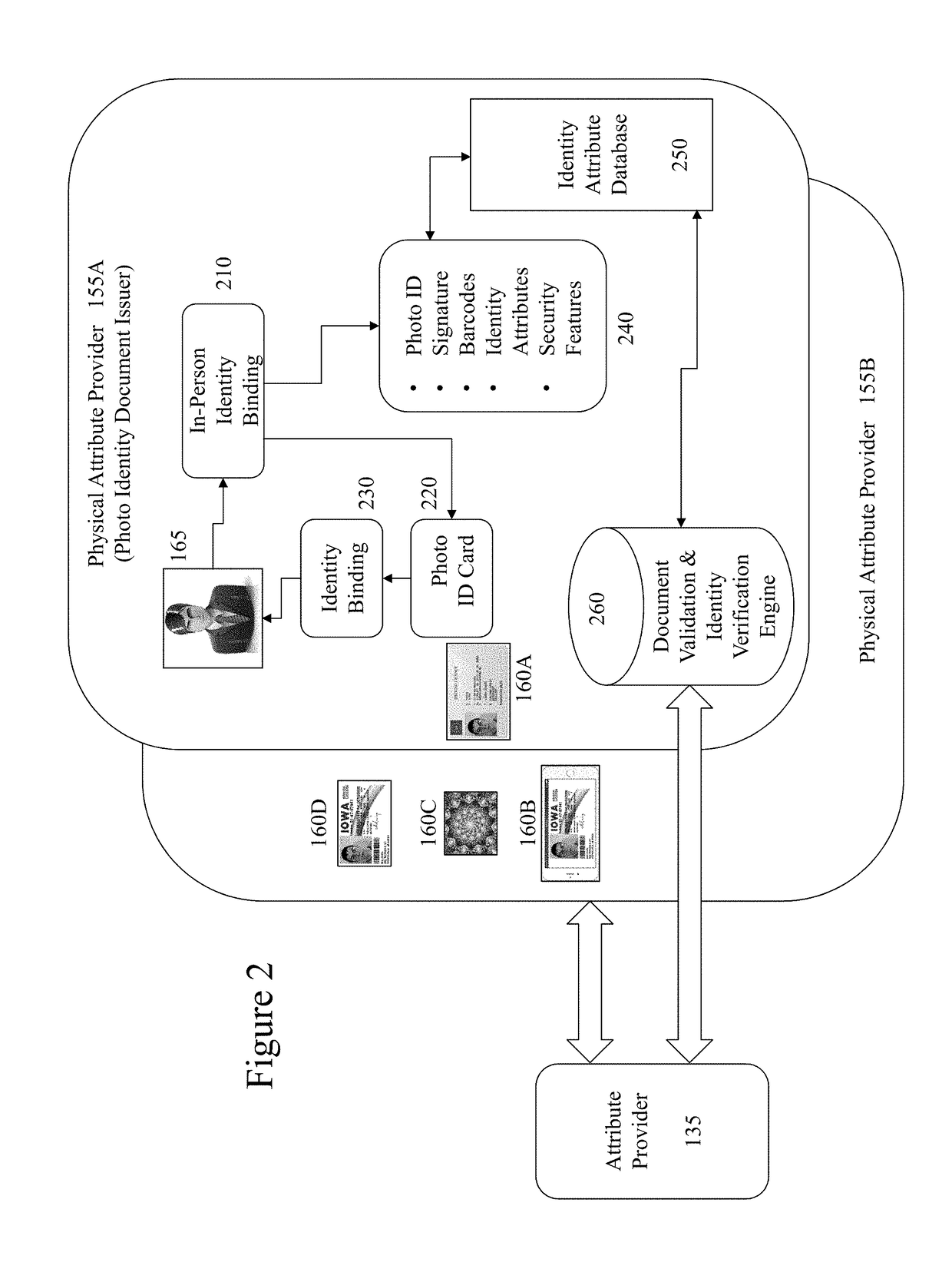
The migration of identity documents, such as driving licenses, from physical documents to electronic documents creates new problems for those seeking to verify the identity of an individual based upon the electronic document they provide. However, the inventors have established a means of binding electronic documents and electronic representations of physical documents to individuals at issuance of the document(s). Accordingly, the inventors address identity verification by providing to those seeking to verify the individual's identity data allowing them to verify the presented electronic ID document. For example, a police officer requesting a driving license can obtain on their own electronic device through the methods of the invention the issued driving license associated with identifier information on the license provided by the individual. As such tampering with the license to change a name, date of birth, photo etc. will result in a visible mismatch to the police officer in comparing them.
Owner:KHAN SAL
System and method for uniquely identifying persons
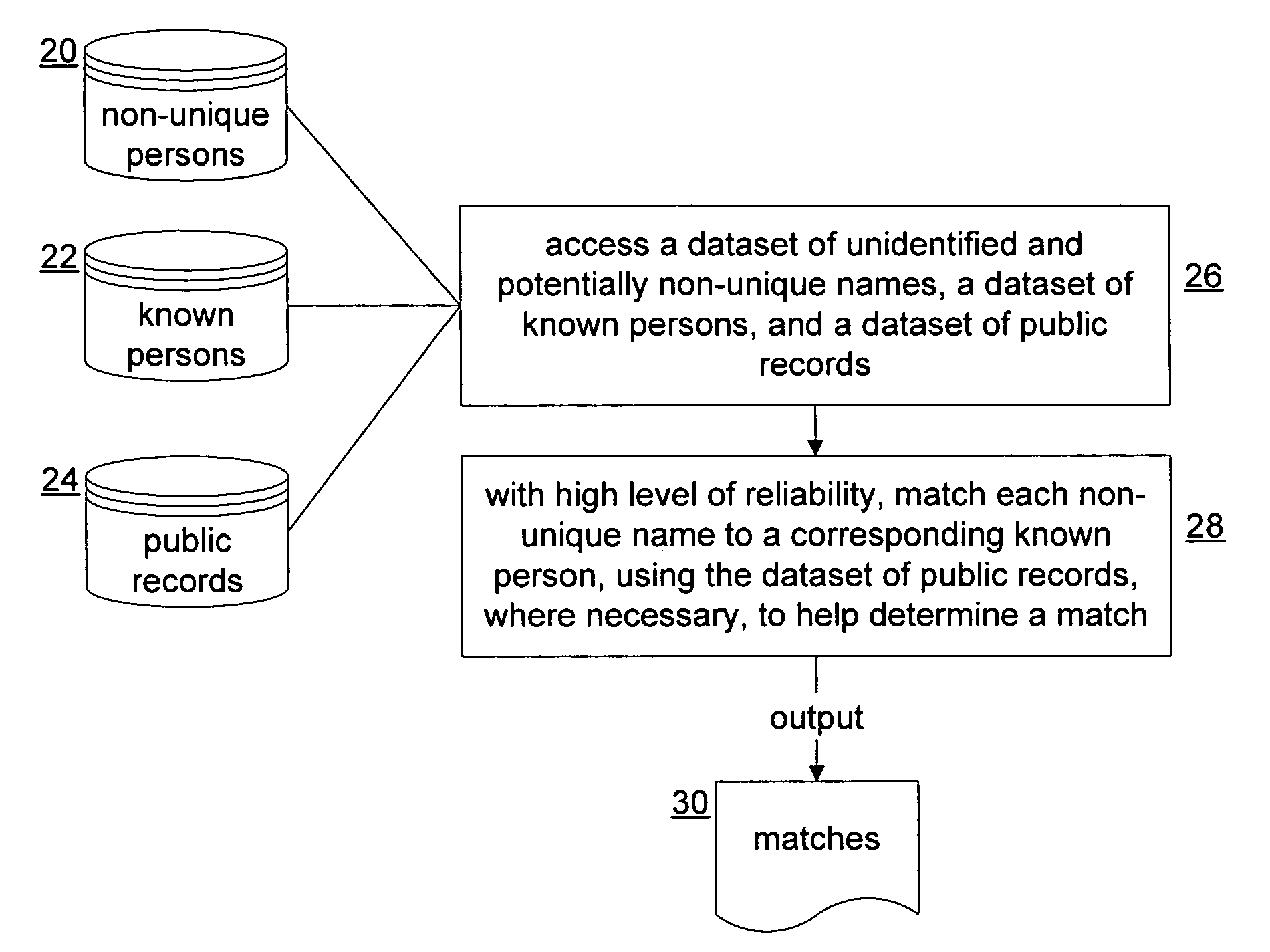
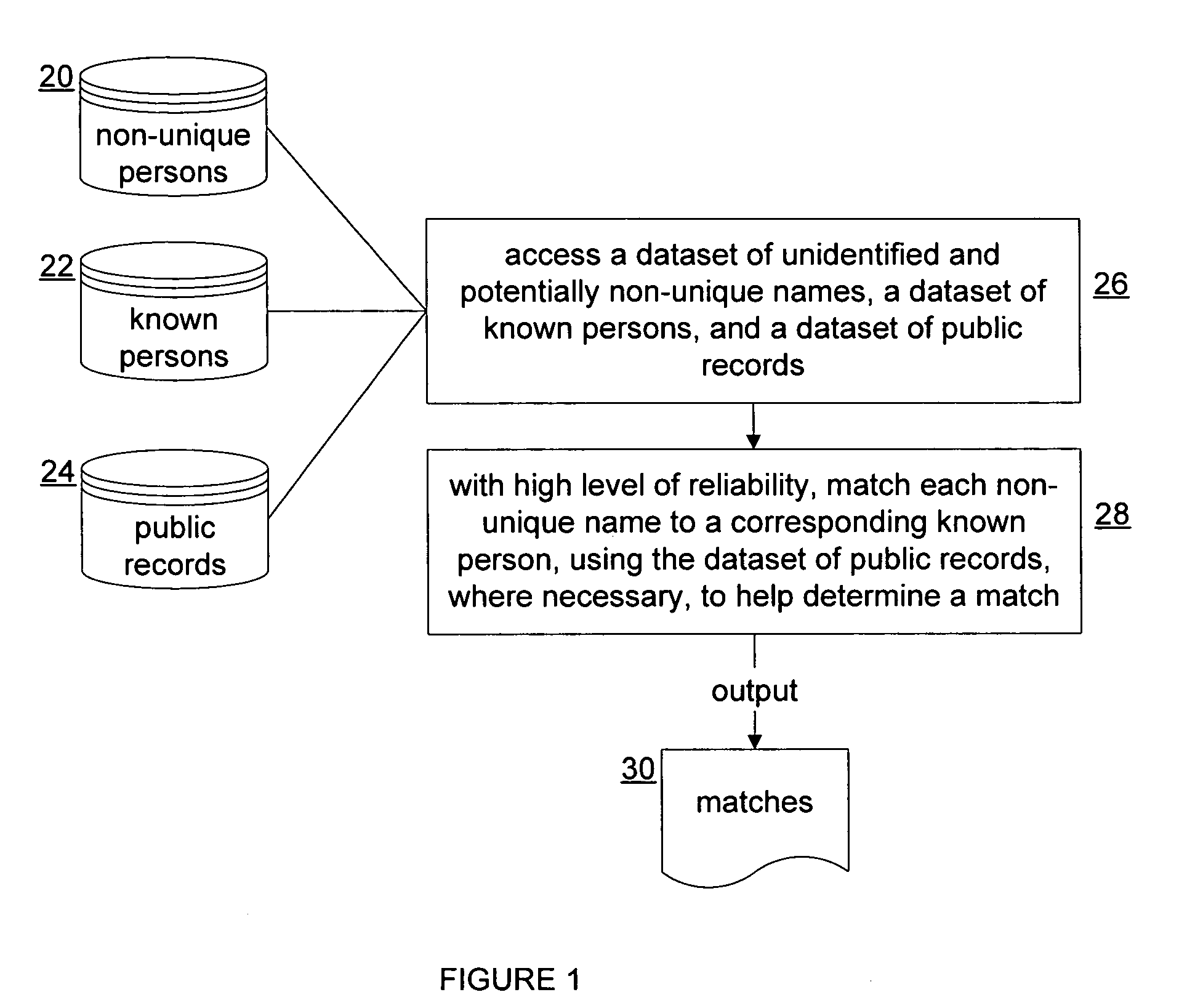
InactiveUS20050149527A1Data processing applicationsDigital data processing detailsData setUnique identifier
A system that determines whether a non-uniquely identified name substantially corresponds to a uniquely identified person. A source dataset of uniquely identified persons is accessed, where the source dataset has records including, for each uniquely identified person, a source name, a source unique identifier, a source date of birth, and a source address. A target dataset of non-uniquely identified persons is also accessed, where the target dataset has records that include, for each non-uniquely identified person, a target name, and either (1) a target age and a target age-date indicating an exact or approximate date of the target age, or (2) a target address. For a particular source person in the source dataset, whether the particular source person corresponds to a particular target person in the target dataset is determined automatically in accordance with the accessing.
Owner:INVESTIGATIVE CONSULTANTS
Method for credit card payment settlement and system for same
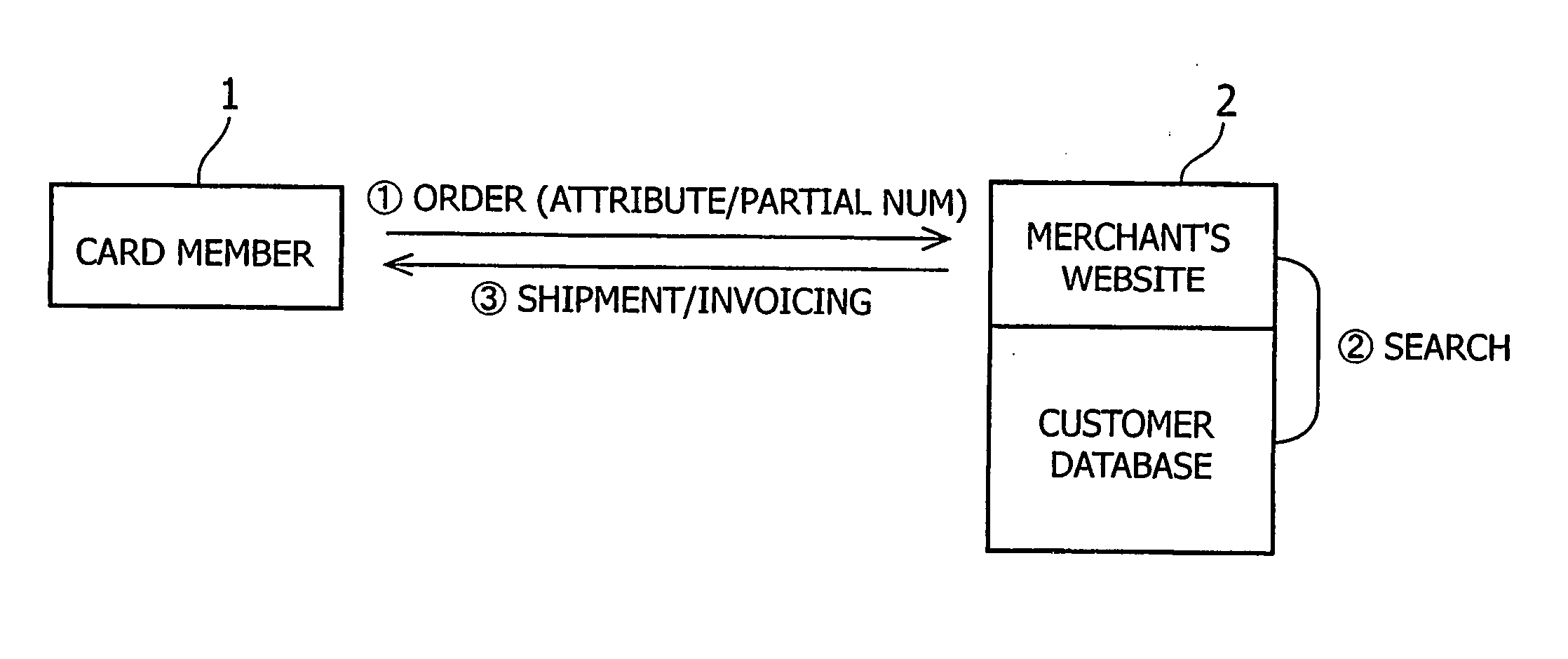
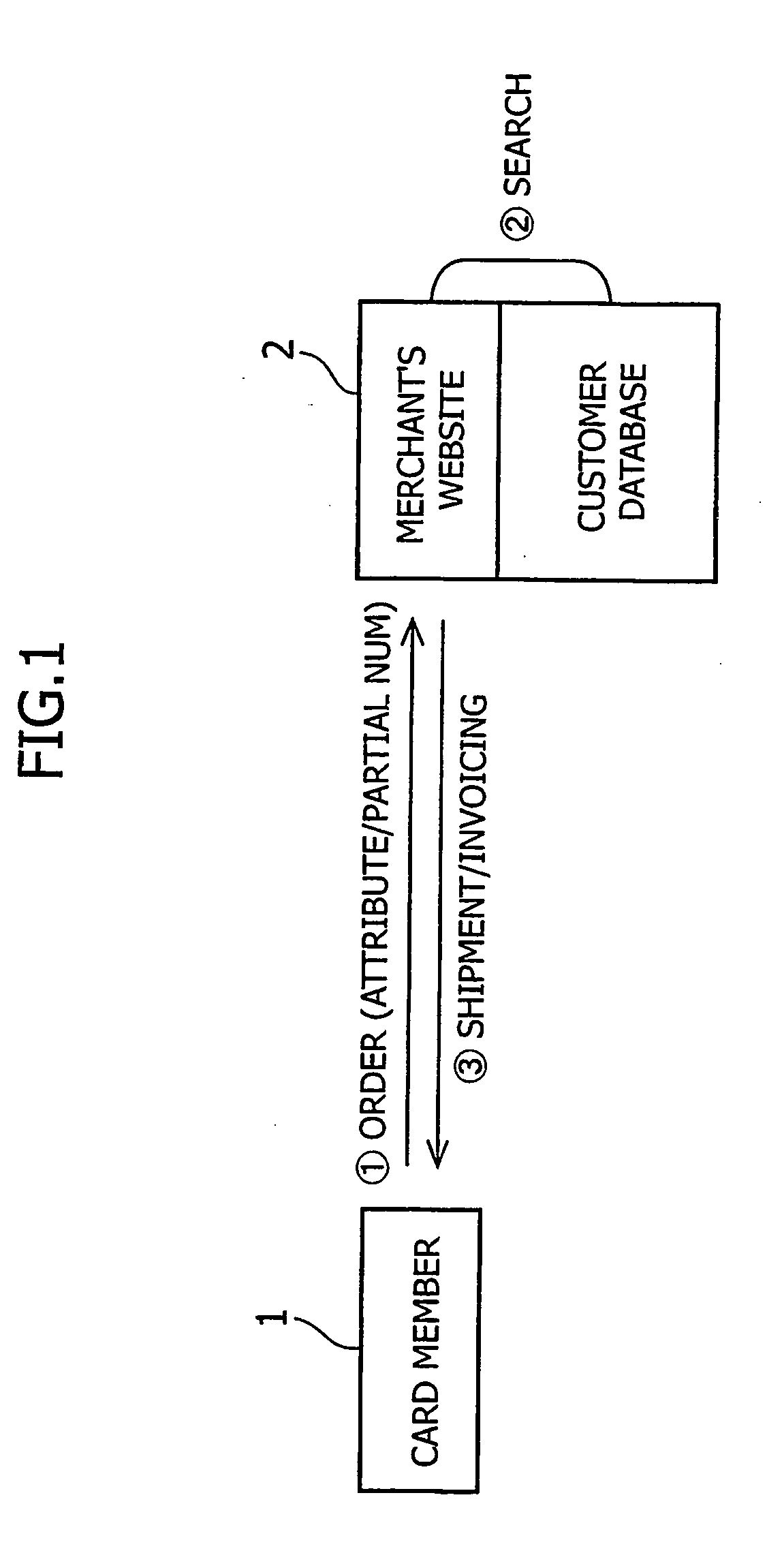
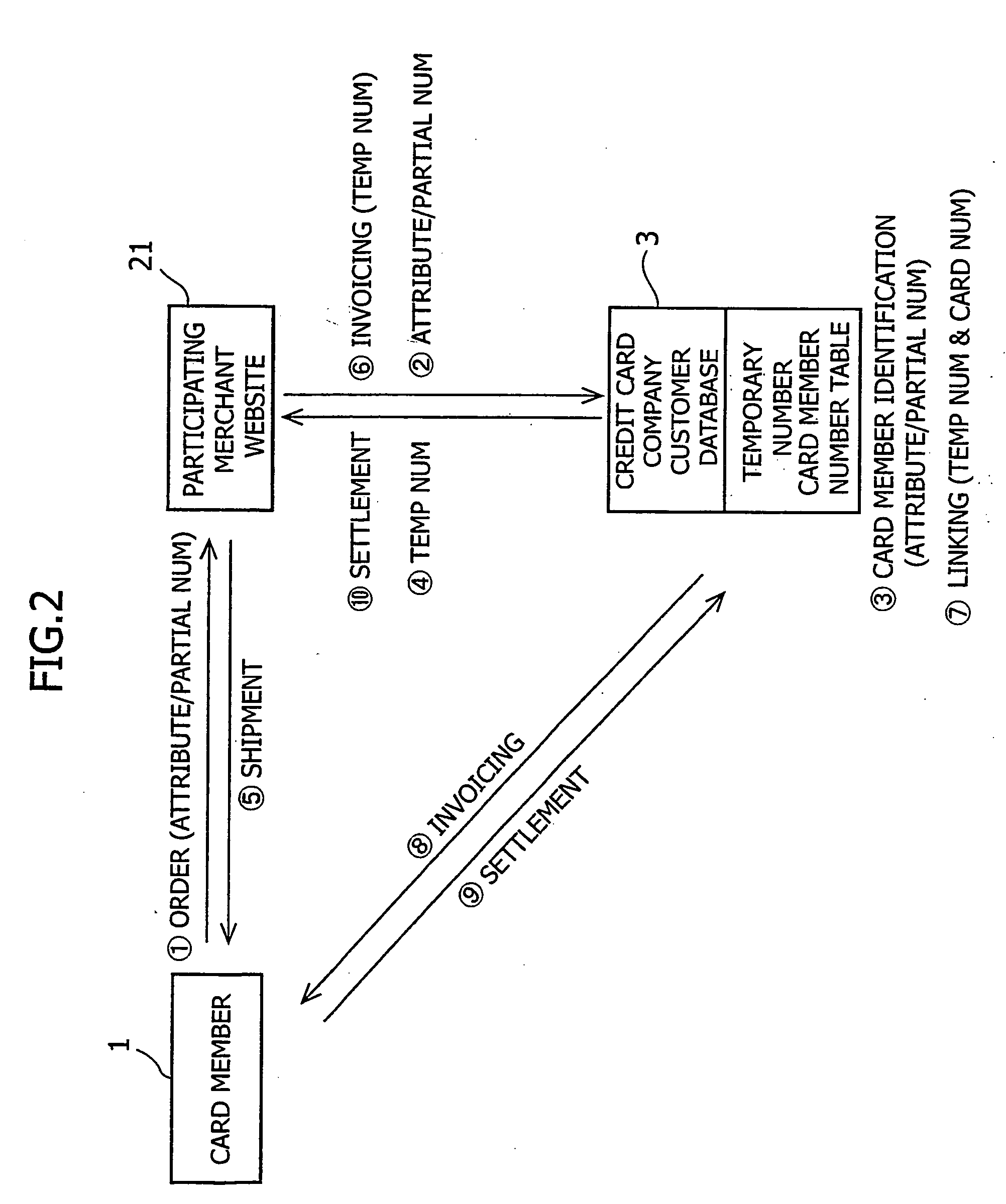
InactiveUS20050246181A1Simplifying ordering site (participating merchant) managementSimplifying transactionFinancePayment circuitsDate of birthApplication software
In a method and system for credit card payment settlement at an ordering site accepting via the Internet an order for a product or an application for a service of a credit card participating merchant, input of a part of the numerals of the card member number and input of attribute information, such as the name, date of birth, and address of the card member or user are accepted and these are used to identify whether or not the user matches with any credit card member, and in the case in which there such identification, invoicing for payment is performed with respect to the person responsible for payment of the card member's card.
Owner:KAWAHARA HIROSHI
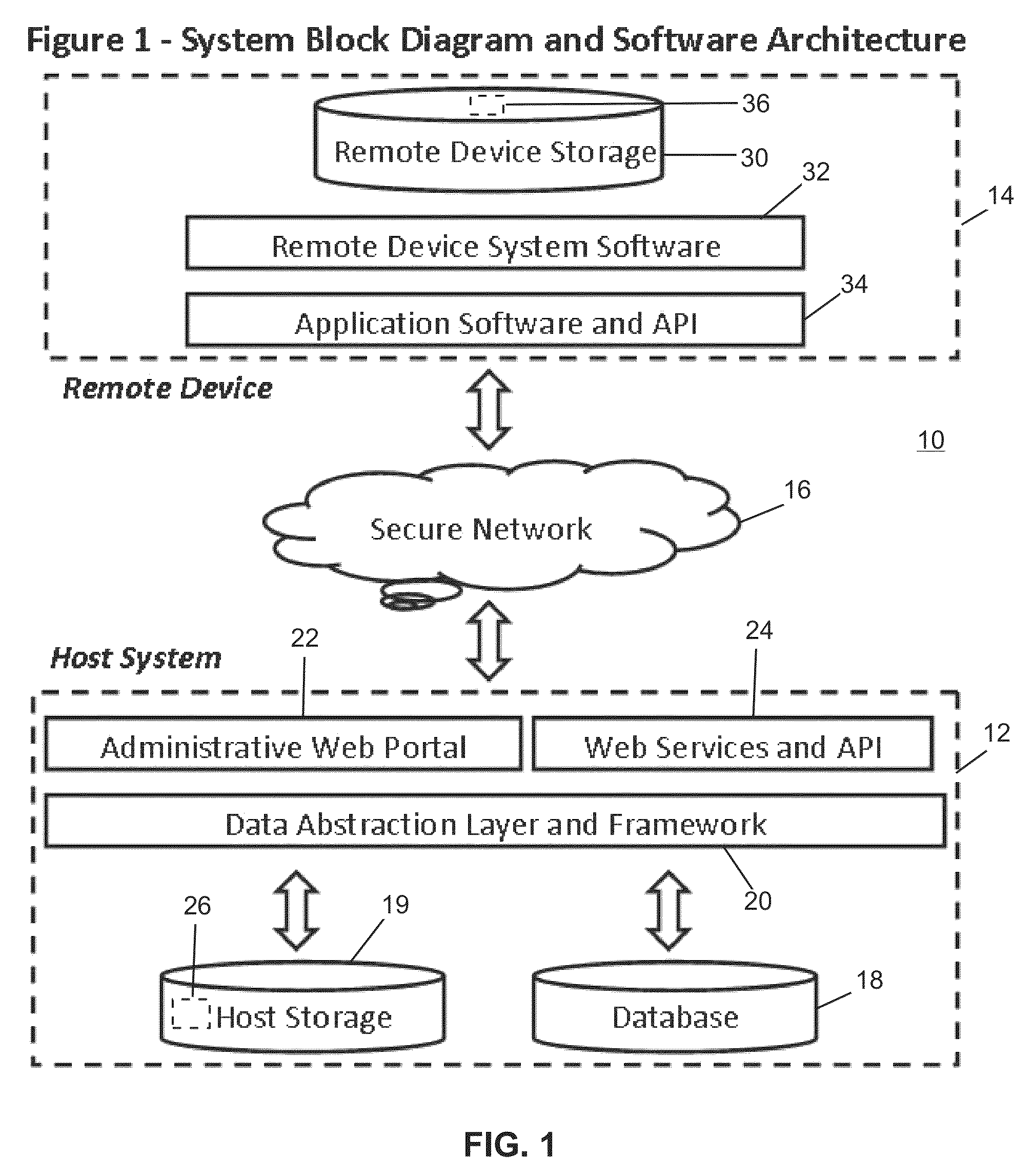
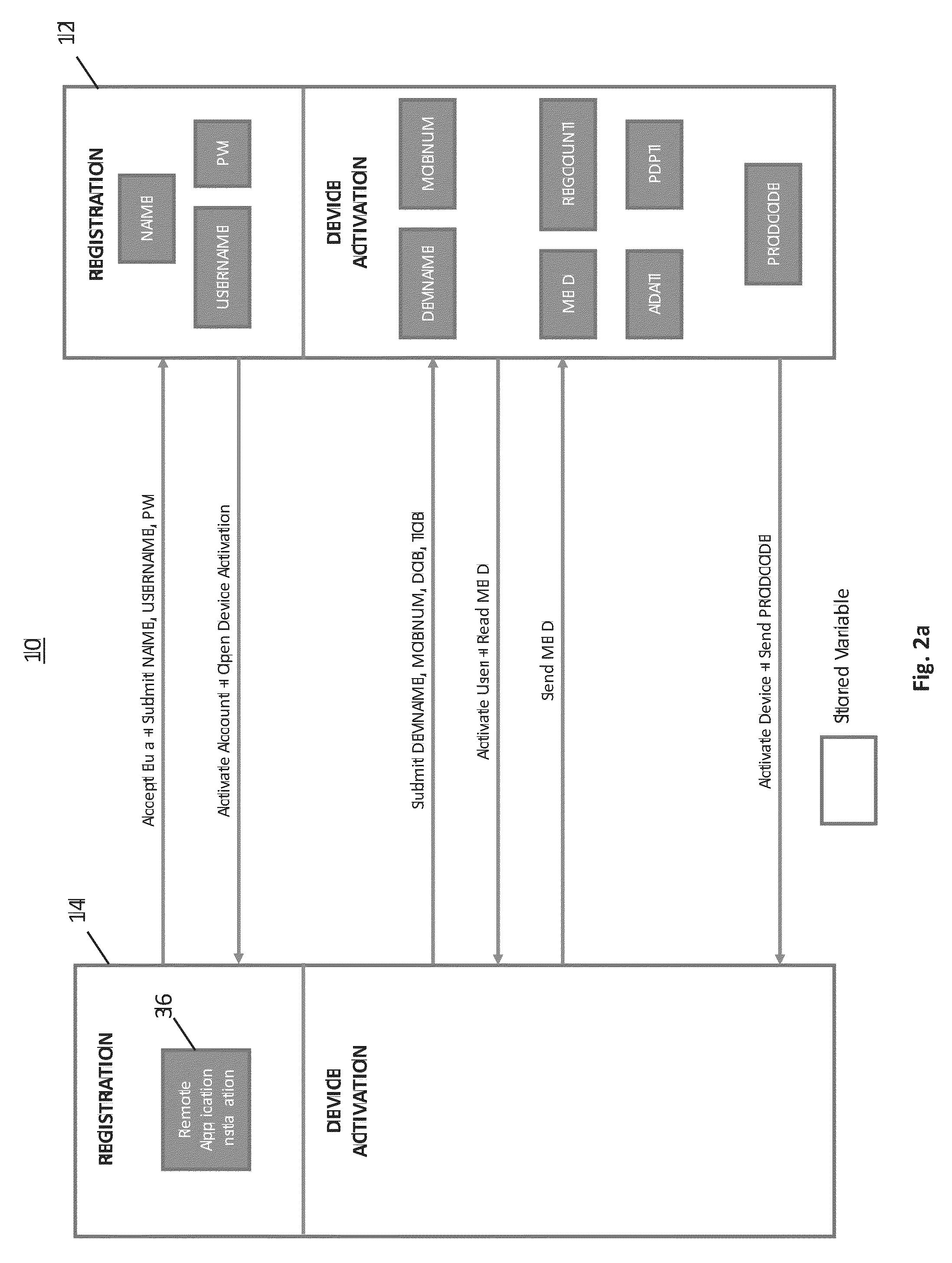
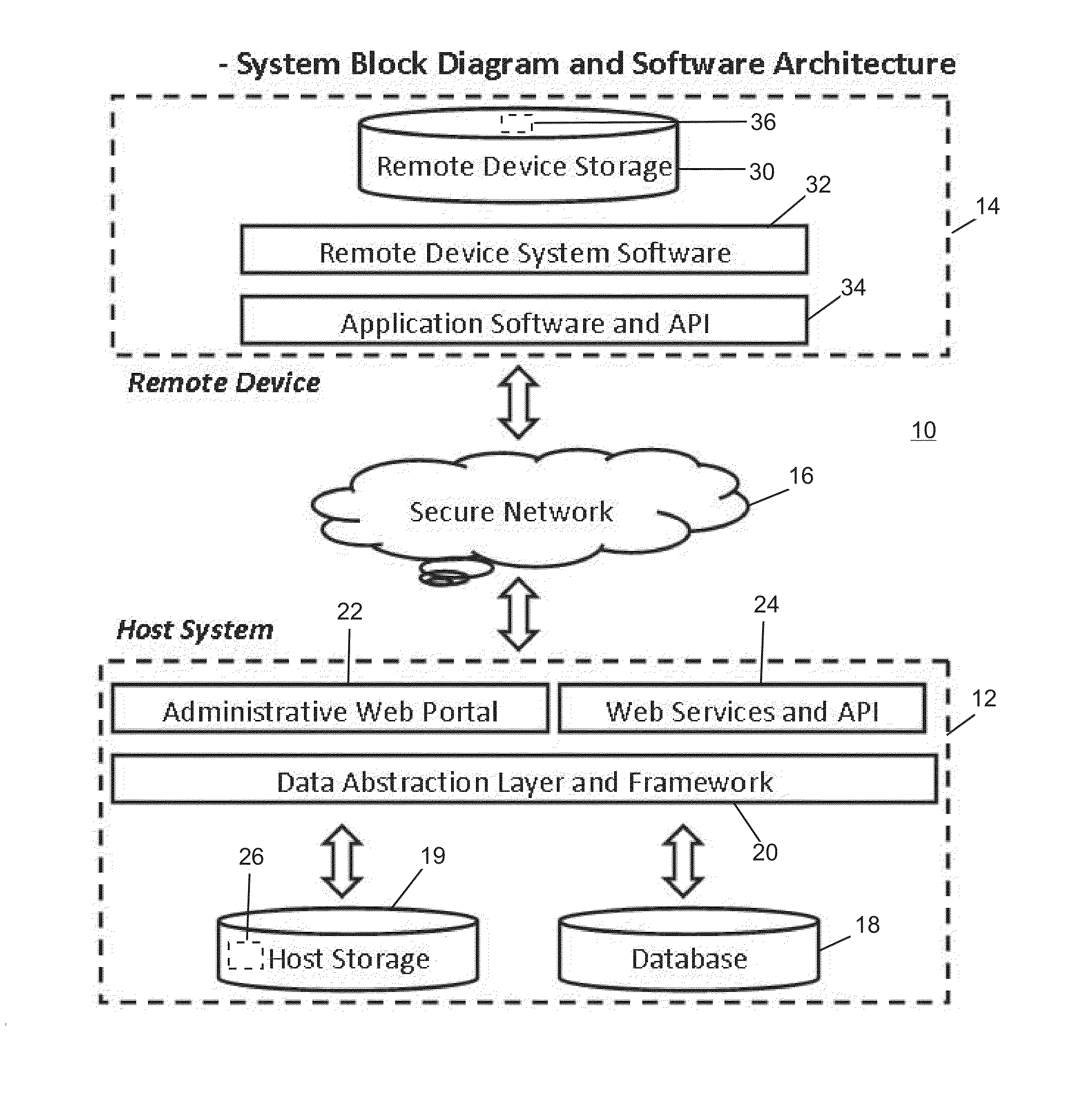
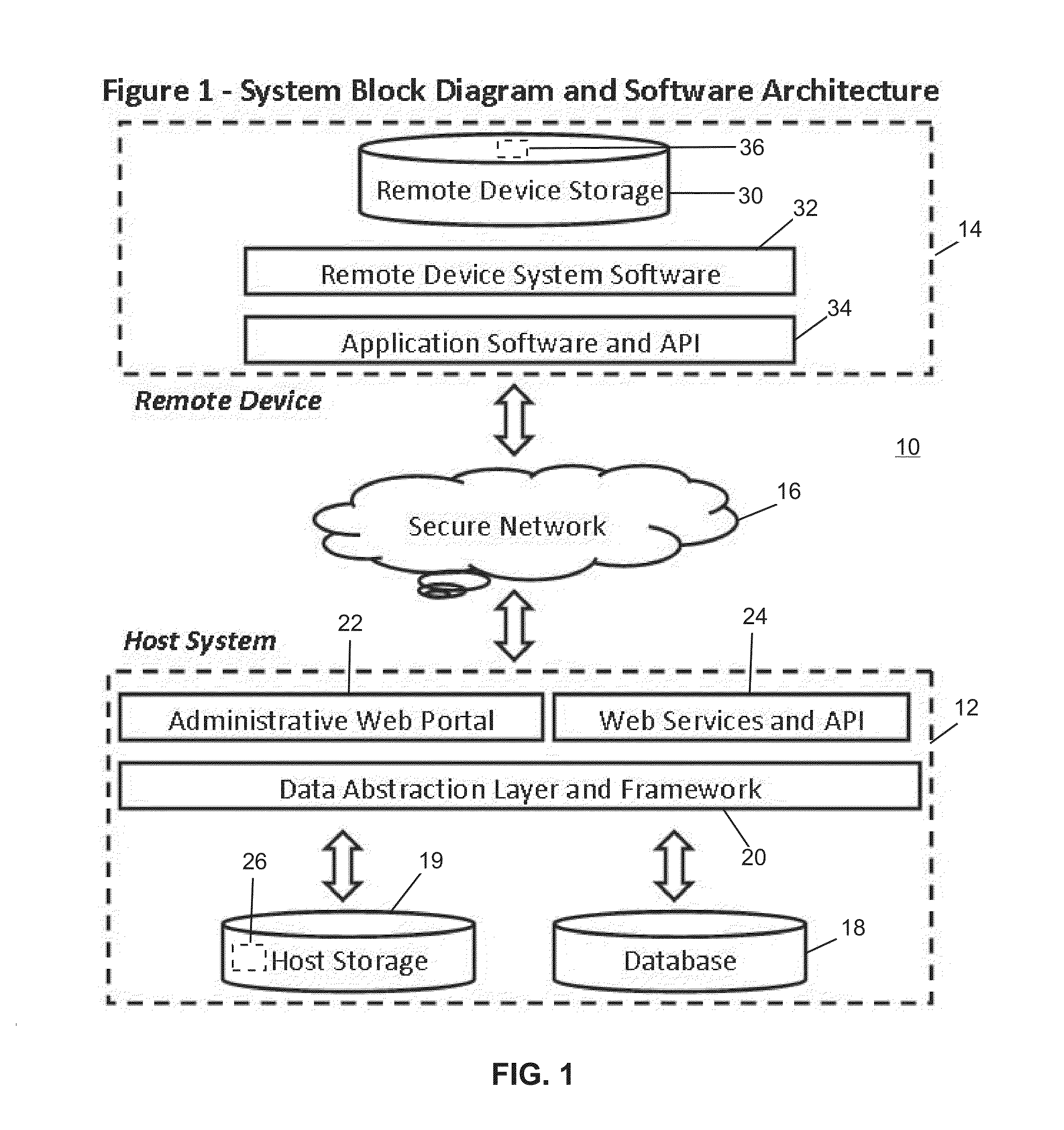
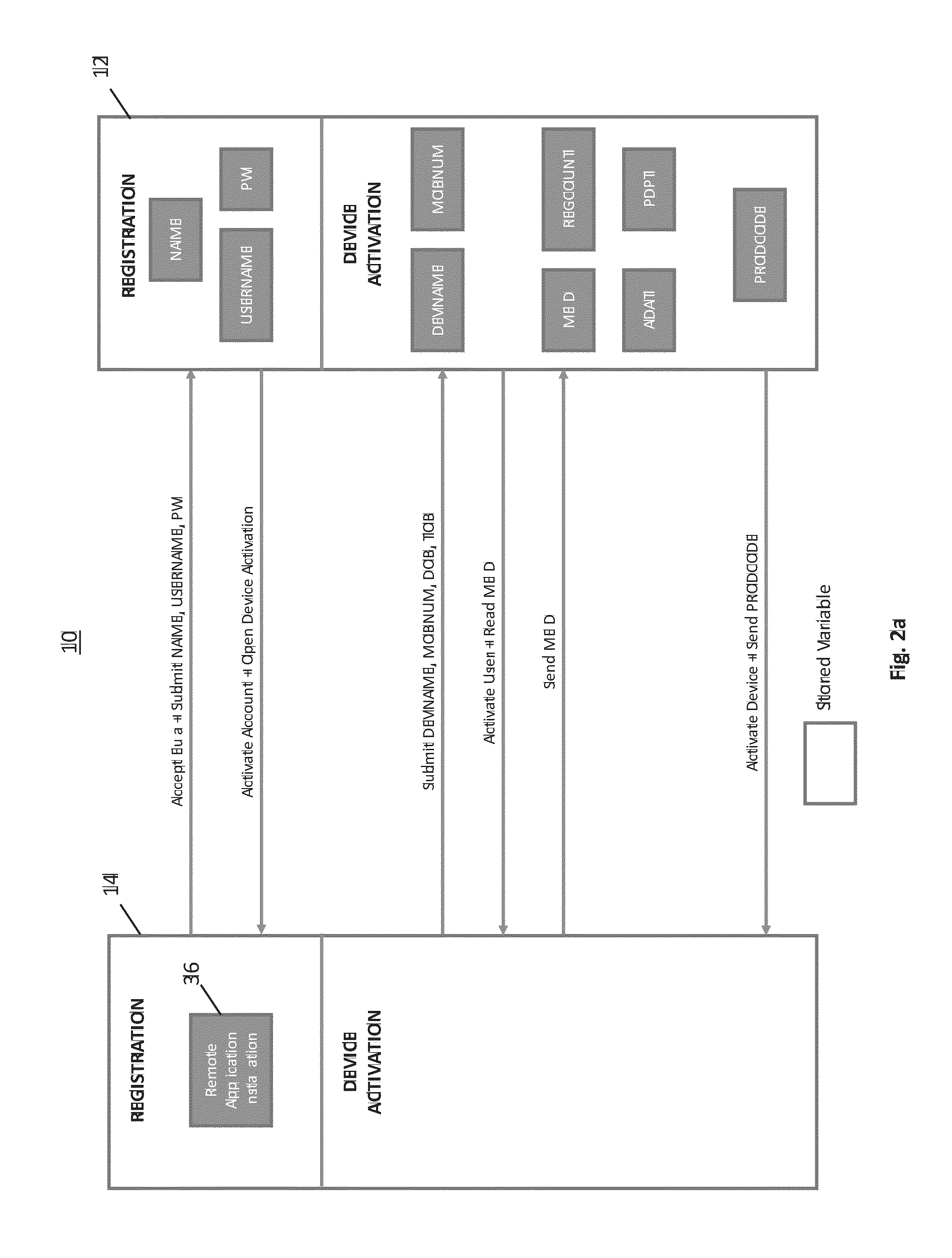
Remote device secure data file storage system and method
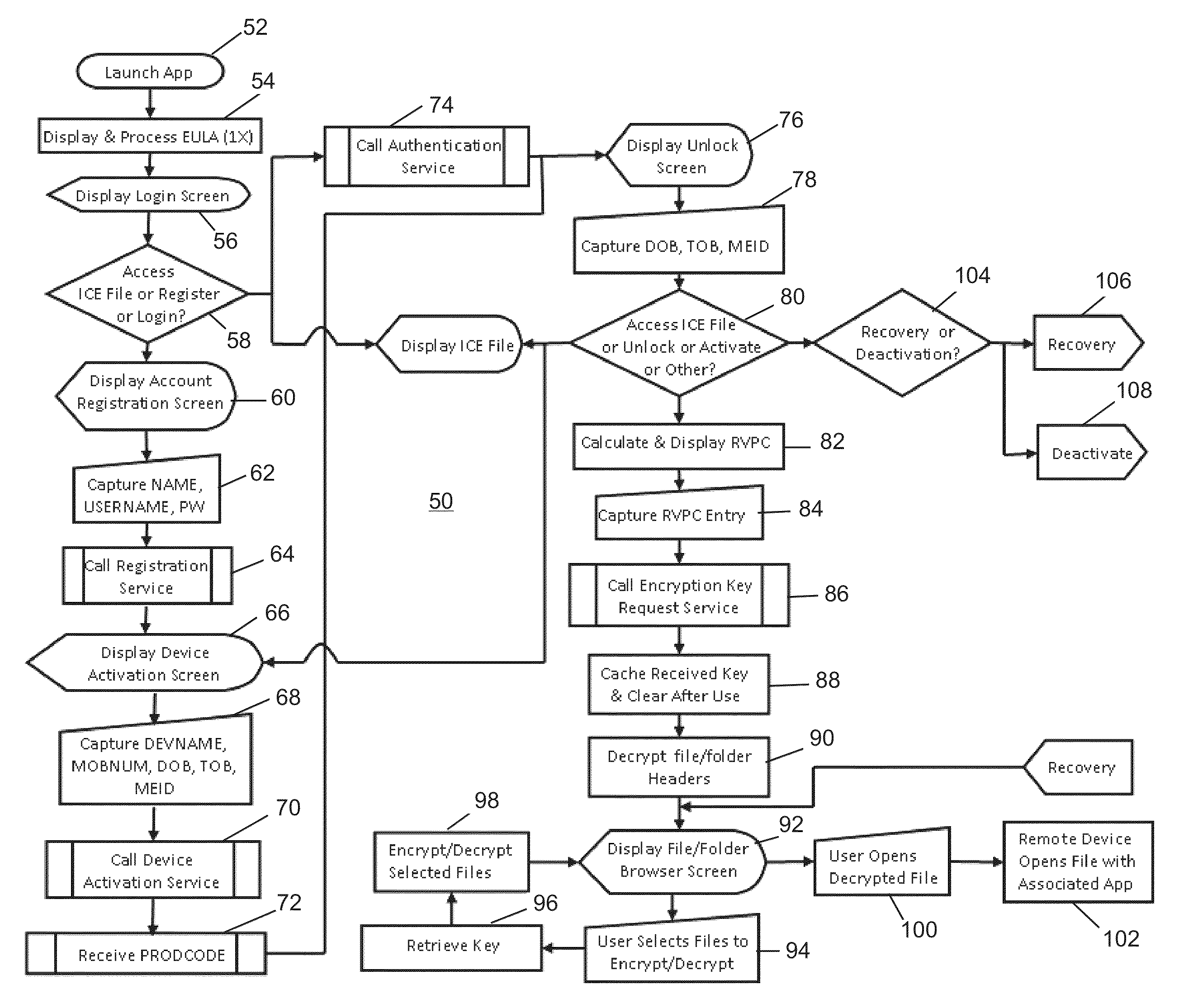
ActiveUS8930700B2Low costKey distribution for secure communicationSynchronising transmission/receiving encryption devicesData fileInitialization vector
A remote device secure data file storage system and method of securely storing data files at a remote device, includes a host system having a database and a plurality of remote devices, each connected with the host system by a communication network. Each remote device and the host system is programmed with a time-based cryptography system that generates an encryption key (RVK) and initialization vector (IV) for encrypting and decrypting data on the remote device. The time-based cryptography system generates the encryption key (RVK) as a function of a parameter (PDPT) that is a function of a personal date (PD) and personal time (PT) of the user. The personal date and personal time of the user being a function of personal data entered by the user on the remote device. The personal date (PD) is a function of the date of birth (DOB) of the user and the personal time (PT) is a function of the time of birth (TOB) of the user.
Owner:WIELOPOLSKI RICHARD J
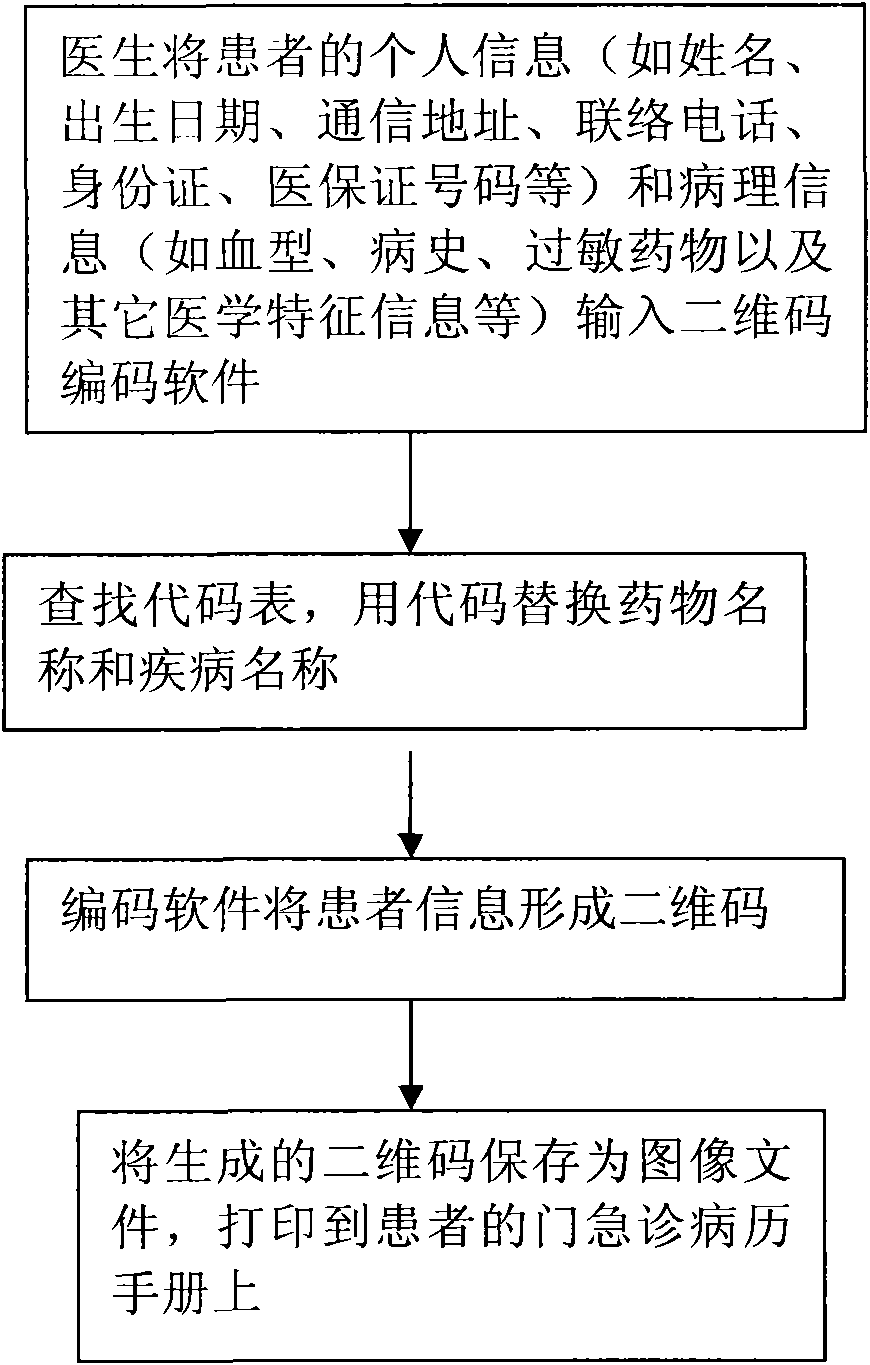
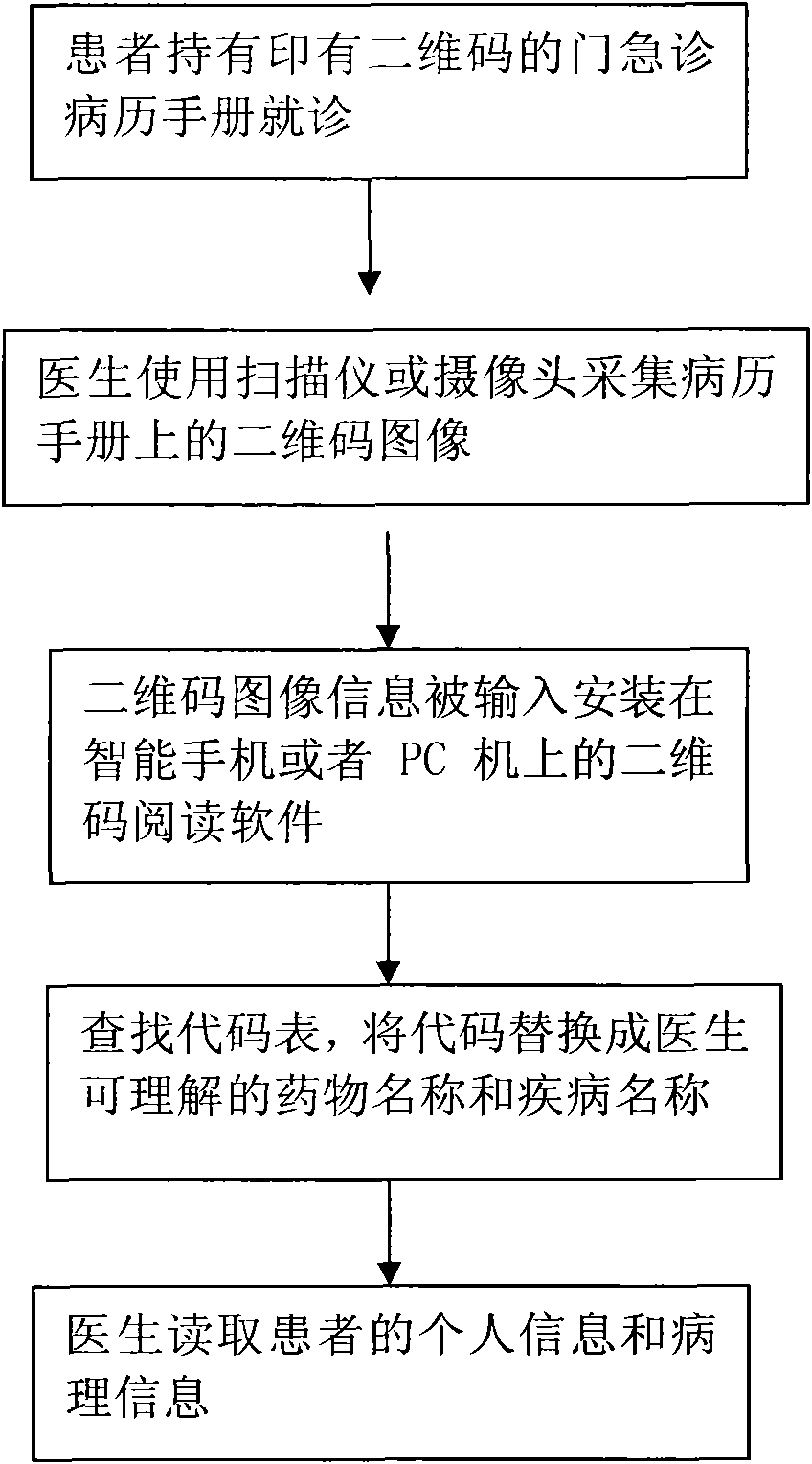
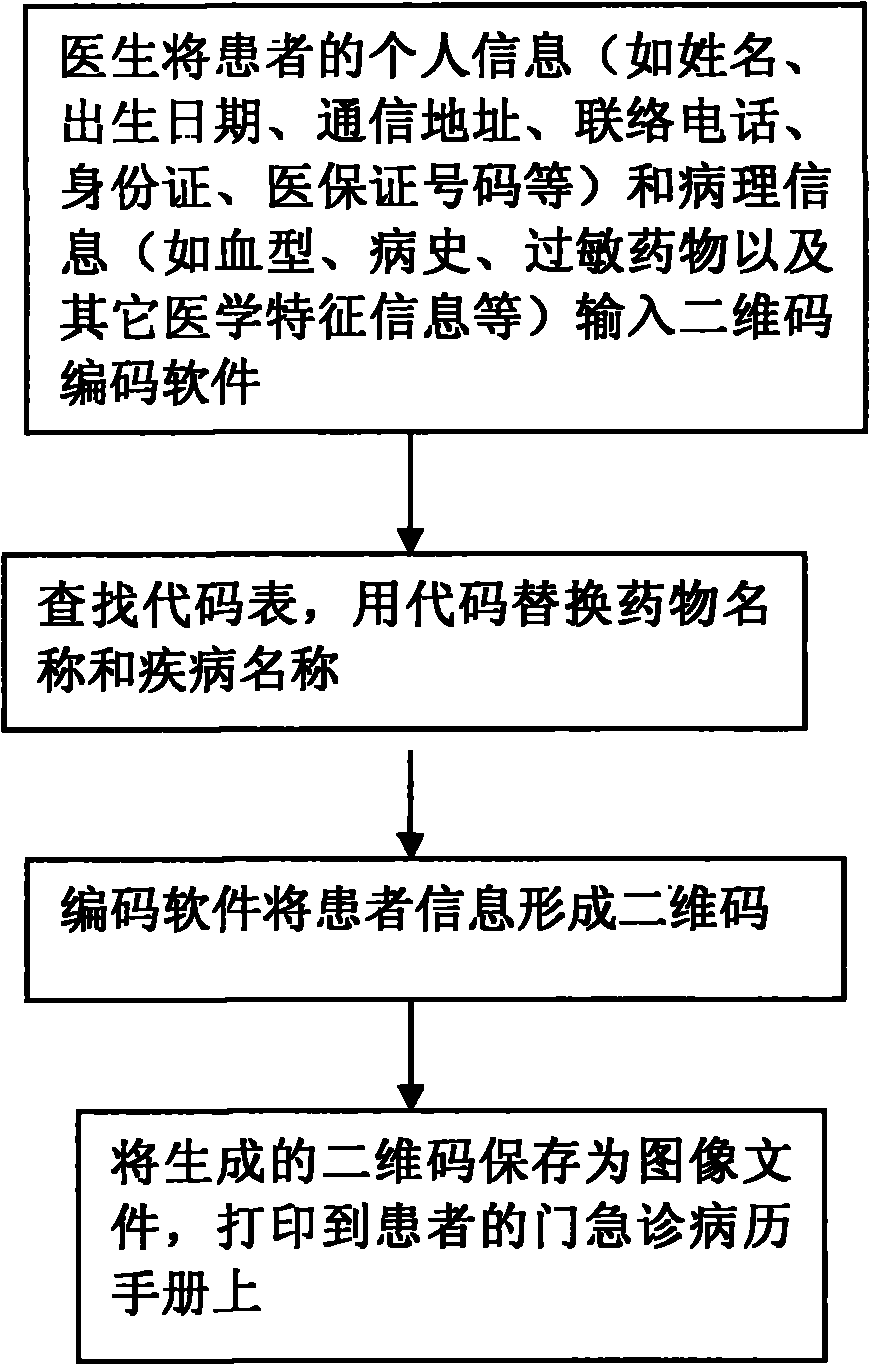
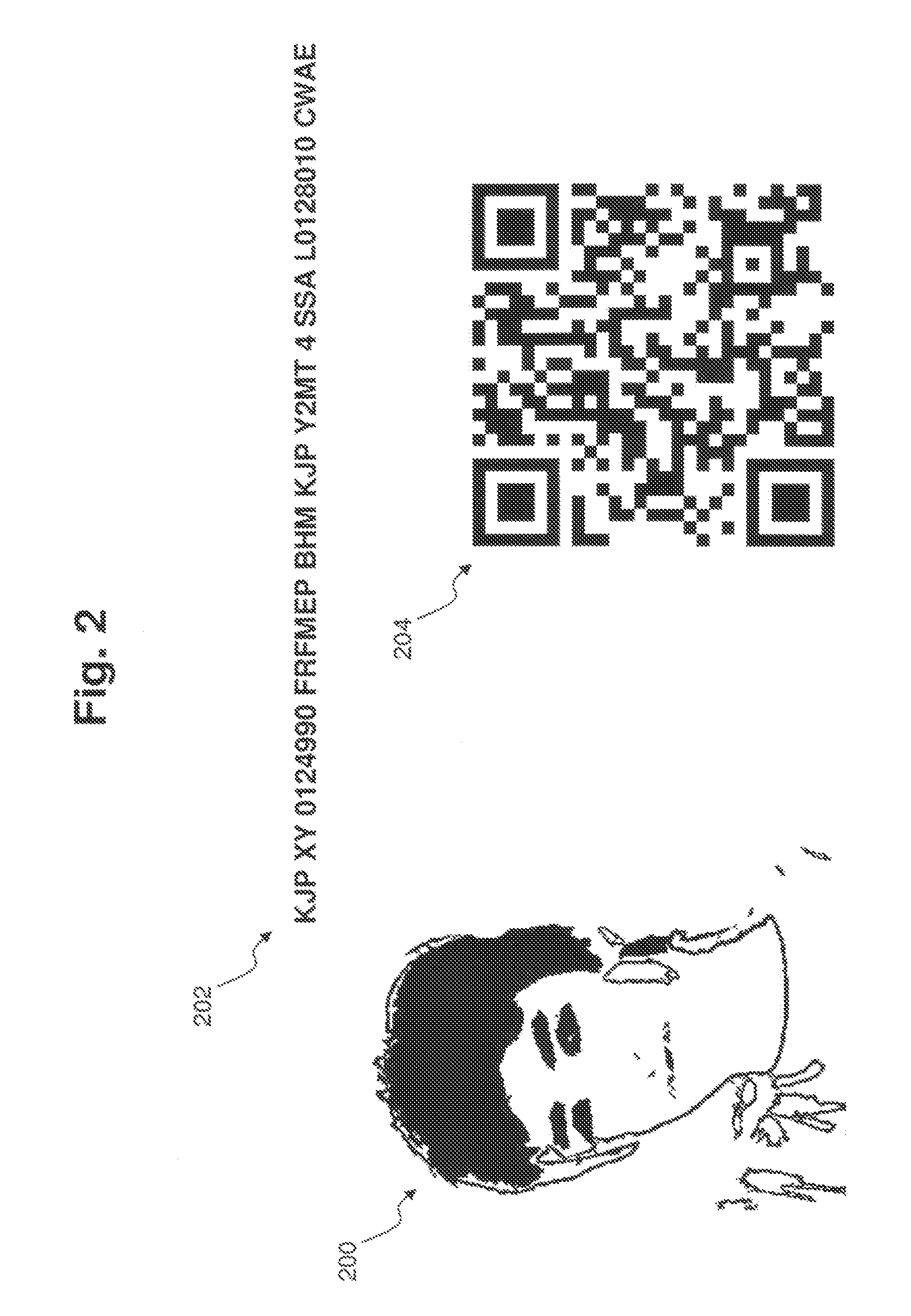
Medical record information management method based on two-dimensional code technology
InactiveCN101976329AData processing applicationsPatient-specific dataMedical recordMedical diagnosis
The invention relates to a medical record information management method based on the two-dimensional code technology, which comprises the steps of leading personal information (such as name, date of birth, mailing address, telephone number, identity card, number of medical insurance certificate and the like) of patients and pathological information (such as blood type, medical history, allergy drugs and other medical characteristic information) to form two-dimensional codes by utilizing two-dimensional code encoding software, saving as image files and printing on outpatient and emergency medical record manuals. When the patient holds the outpatient and emergency medical record manual printed with the two-dimensional codes to see a doctor in any medical institution, the doctor needs to use a scanning instrument or a camera head to collect the two-dimensional code images on the medical record manual, and then the information of the patient can be displayed through a computer or an intelligent mobile phone equipped with two-dimensional code reading software. Therefore, the method can not only save information inquiry time, but also avoid the embarrassment of inquiring privacy information face to face, facilitate medical diagnosis and information sharing, realize the protection of personal privacy and not increase additional economic burden on the patients.
Owner:刘彤
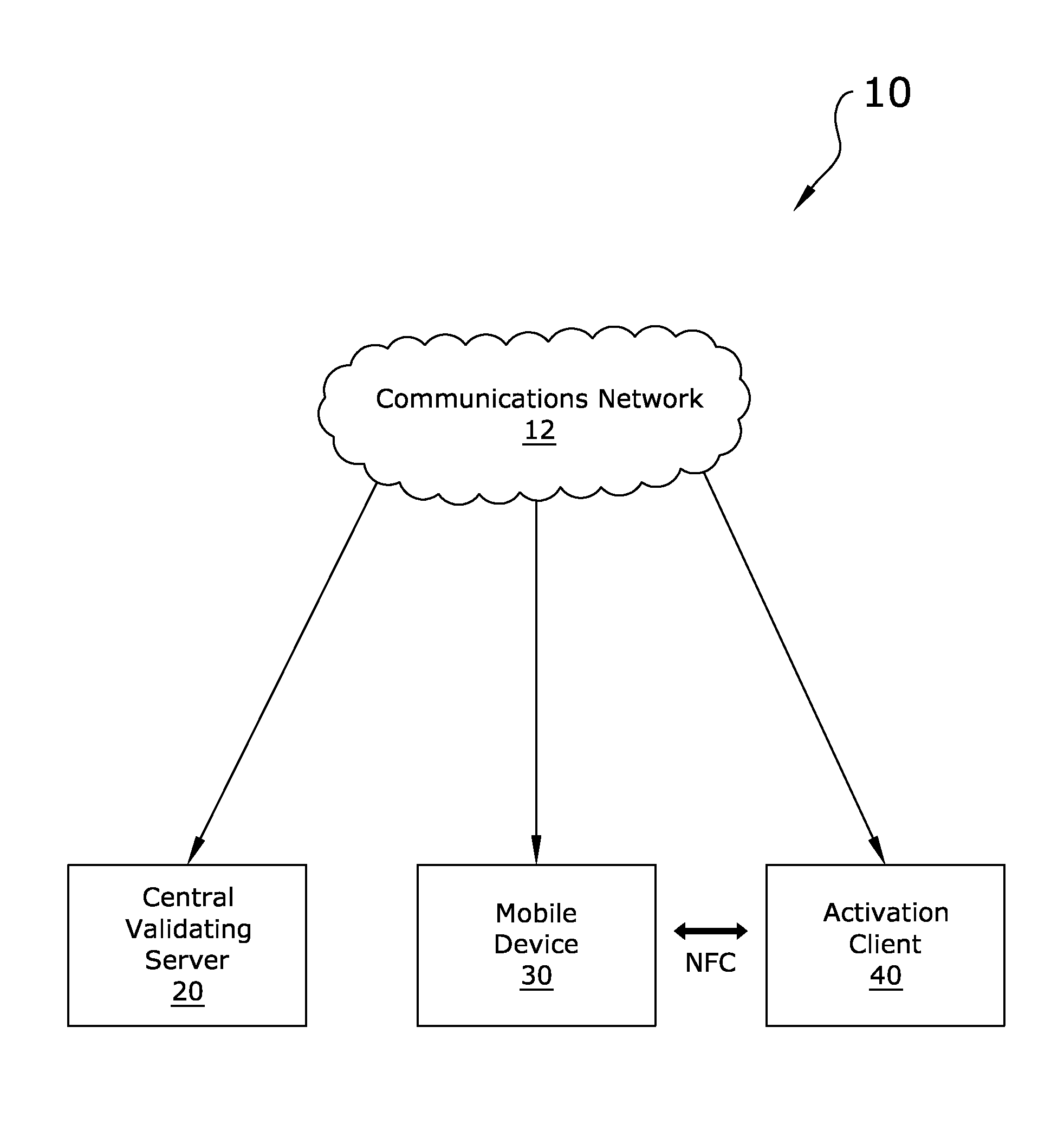
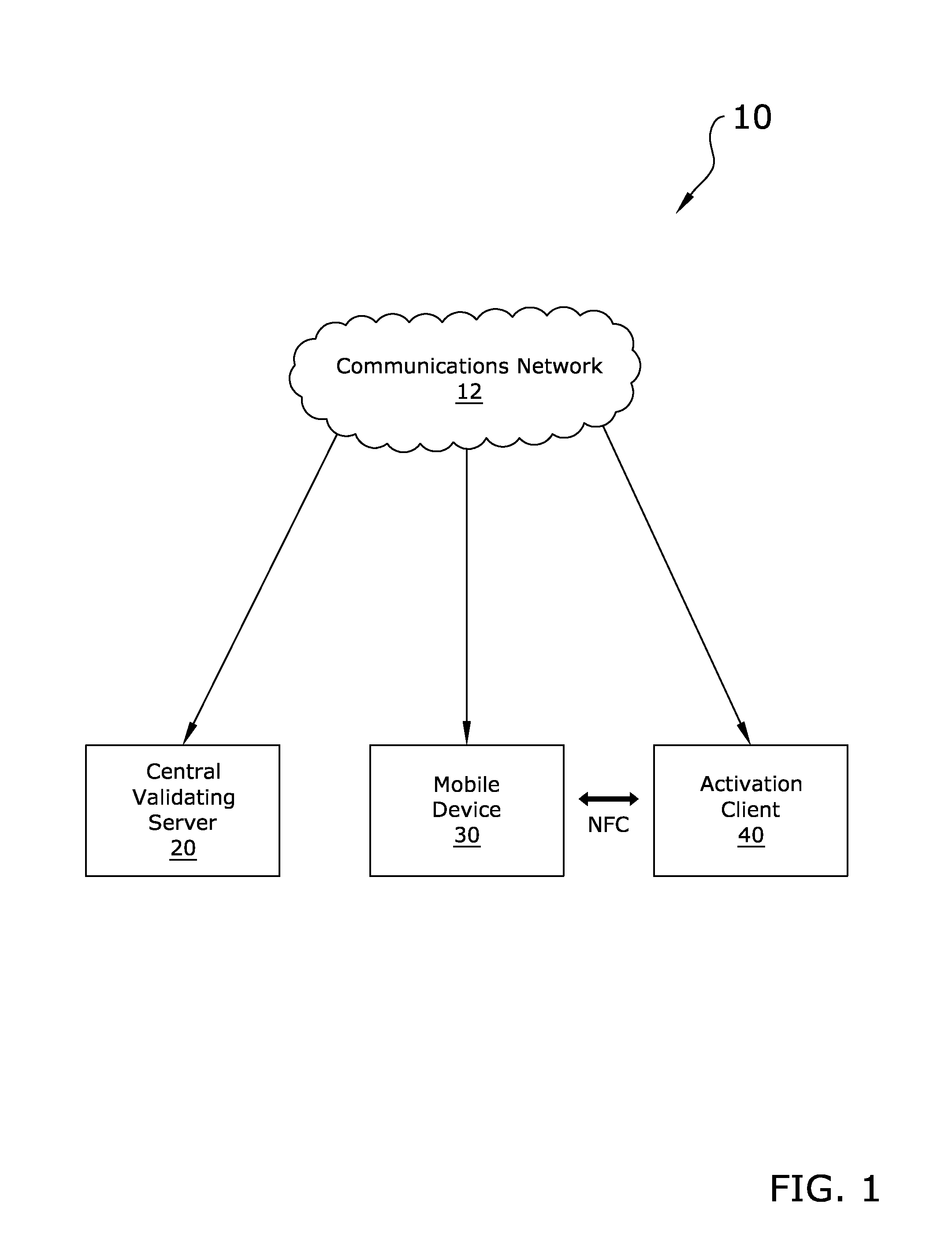
System and Method for Data Verification Using a Smart Phone
ActiveUS20140335824A1Convenient verificationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsBiometric dataData information
A system and method for data verification using a smart phone which verifies data and biometric identity information using only locally stored biometric information. The system and method for data verification using a smart phone generally includes a mobile device, a central validating server, and an activation client. The validating server and activation client are utilized upon initial activation of the mobile device to verify data information (i.e. name, date of birth, social security number, etc.) and / or biometric data regarding an individual and then flag the mobile device as activated and verified. The biometric data is not stored in any location other than the memory of the mobile device. The activated and verified mobile device may then be utilized in combination with a wide range of verification clients to easily verify data information and / or biometric data of an individual.
Owner:ABRAHAM DENNIS THOMAS
Computer Based Method of Pricing Equity Indexed Annuity Product with Guaranteed Lifetime Income Benefits
A computer-based method for determining a set of equity-indexed crediting parameters E for a lifetime-income equity-indexed deposit product provided to a set of owners having a set of dates of birth B, a rider charge C, a lifetime income percentage scale L, a set of profitability requirements R, a principal amount P, and an account value A. The method can include the steps of: establishing the values of C, L, R, P, A and E at a time when said deposit product is purchased; generating a set of yield curve and equity index scenarios consistent with valuation parameters; setting a trial value Ei for E; calculating the observed distribution D of profitability; comparing D with R; and, computing a revised trial value Ei+1 for E, where the steps of establishing, generating, setting, calculating, comparing, and computing are performed by at least one general purpose computer.
Owner:GENESIS FINANCIAL PRODS
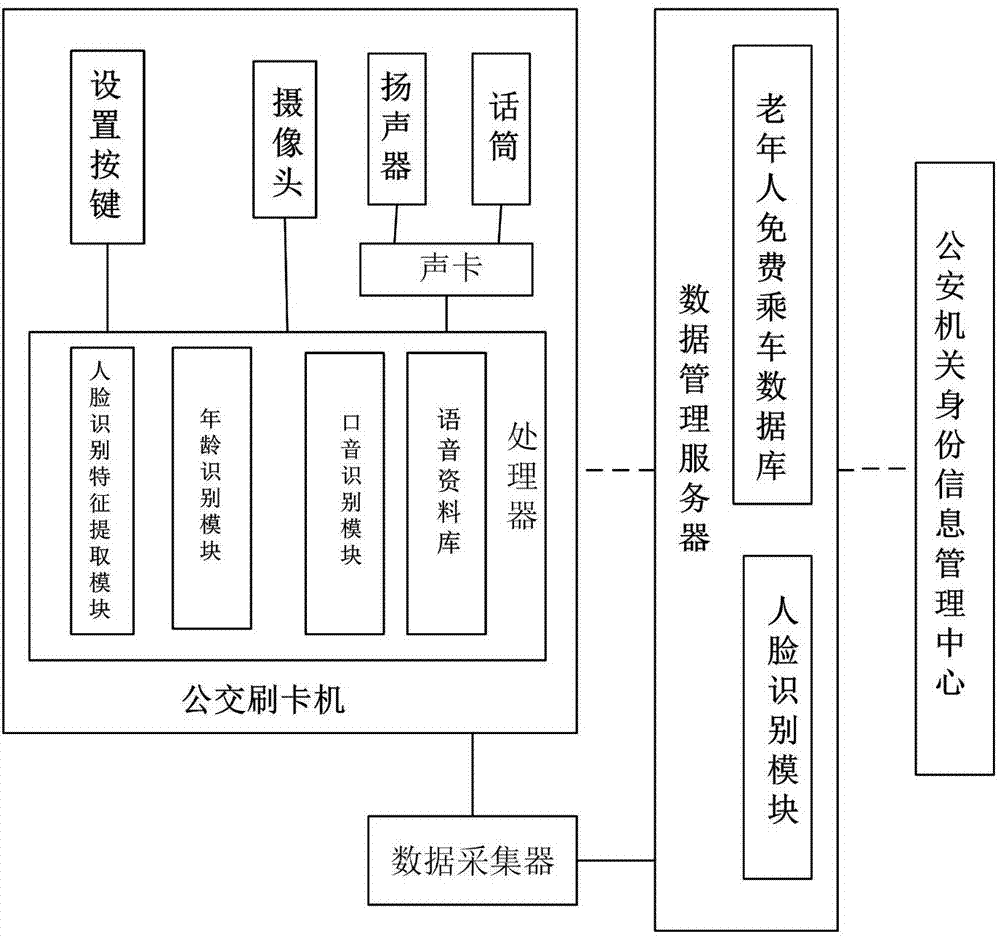
Intelligent bus payment system with specific people recognition function and implementing method of intelligent bus payment system
The invention discloses an intelligent bus payment system with a specific people recognition function and an implementing method of the intelligent bus payment system. The system comprises a bus card swiping machine, wherein the bus card swiping machine is connected with a data management server through a data acquirer or a wireless network and is also connected with a camera, a receiving loudspeaker and a sound card of a microphone; a human face recognition feature extracting module is inlaid in the bus card swiping machine; an age recognition module based on human faces and an accent recognition module based on voice are also inlaid in the bus card swiping machine; the data management server is provided with an old people zero fare database which is used for storing personal identity information containing face feature information; the data management server can keep contact with an identity information management center of a local public security organization through a network; and identity information of old people who can take a bus free in a local place in real time according to dates of birth can be transmitted to the local bus data management server so as to update the old people zero fare database. The old people who can take the bus free do not need to take identity cards, and the intelligent bus payment system is convenient.
Owner:建湖联众智慧科技有限公司
Remote device secure data file storage system and method
ActiveUS20140164777A1Low costKey distribution for secure communicationSynchronising transmission/receiving encryption devicesData fileInitialization vector
A remote device secure data file storage system and method of securely storing data files at a remote device, includes a host system having a database and a plurality of remote devices, each connected with the host system by a communication network. Each remote device and the host system is programmed with a time-based cryptography system that generates an encryption key (RVK) and initialization vector (IV) for encrypting and decrypting data on the remote device. The time-based cryptography system generates the encryption key (RVK) as a function of a parameter (PDPT) that is a function of a personal date (PD) and personal time (PT) of the user. The personal date and personal time of the user being a function of personal data entered by the user on the remote device. The personal date (PD) is a function of the date of birth (DOB) of the user and the personal time (PT) is a function of the time of birth (TOB) of the user.
Owner:WIELOPOLSKI RICHARD J
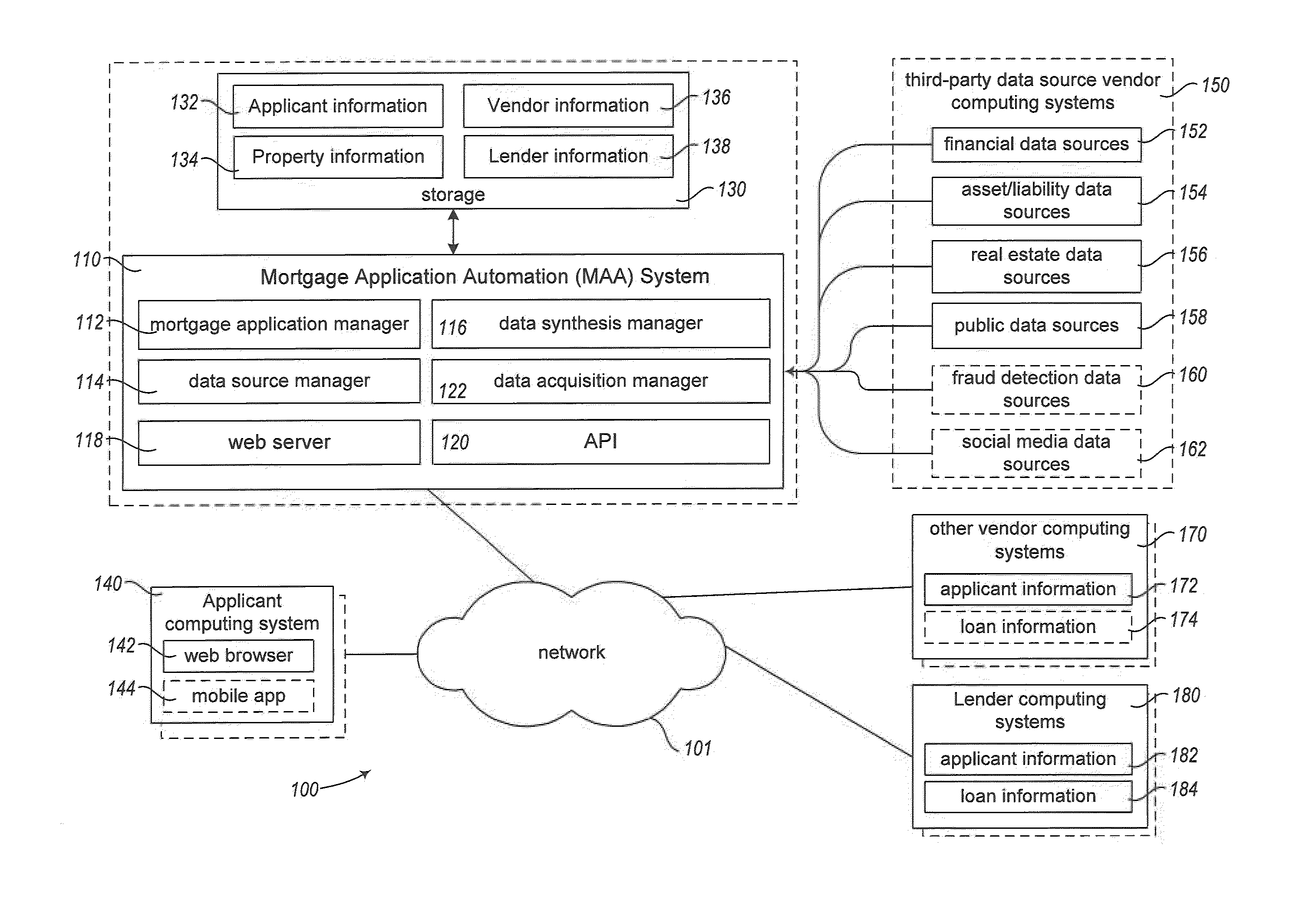
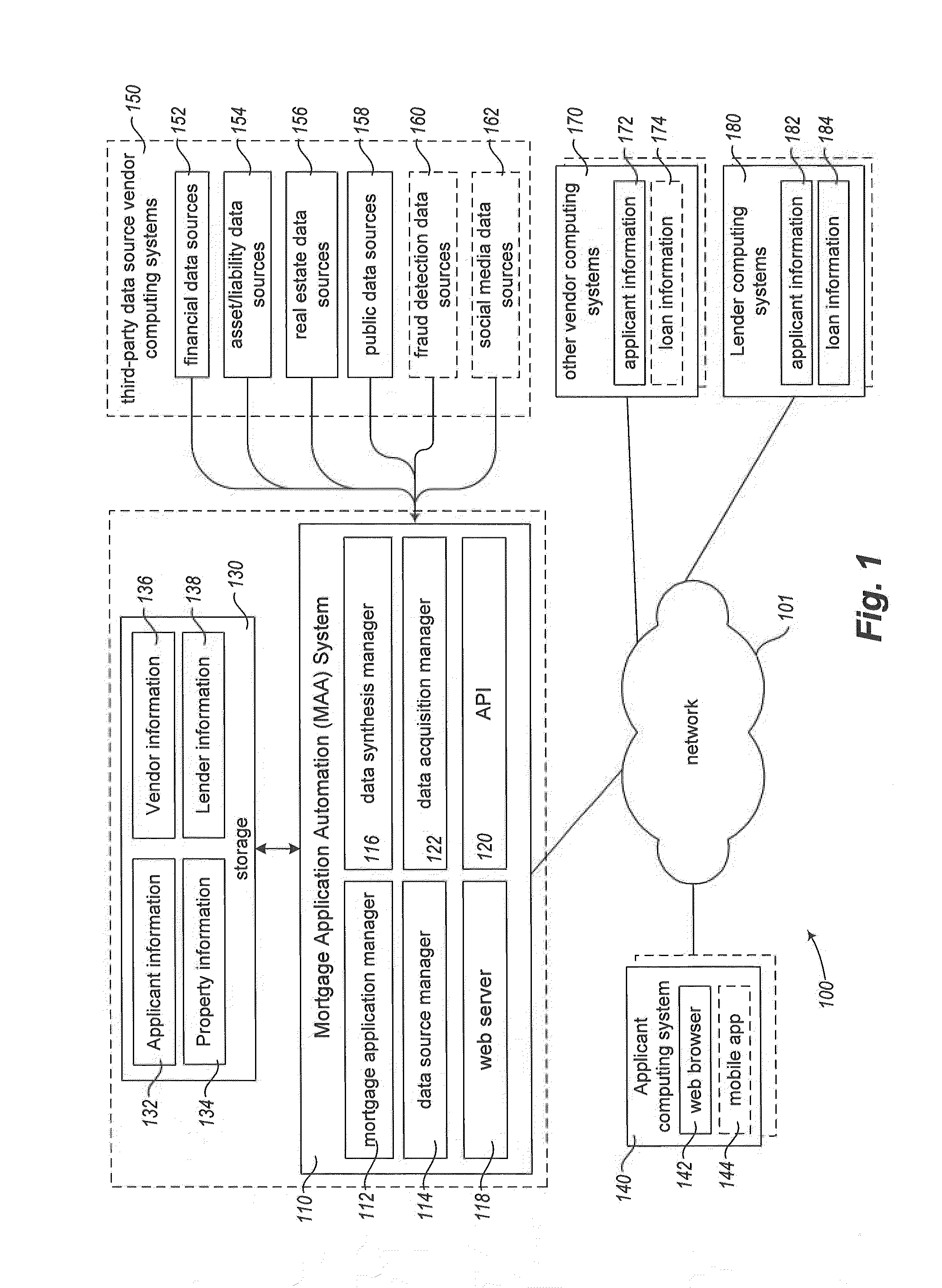
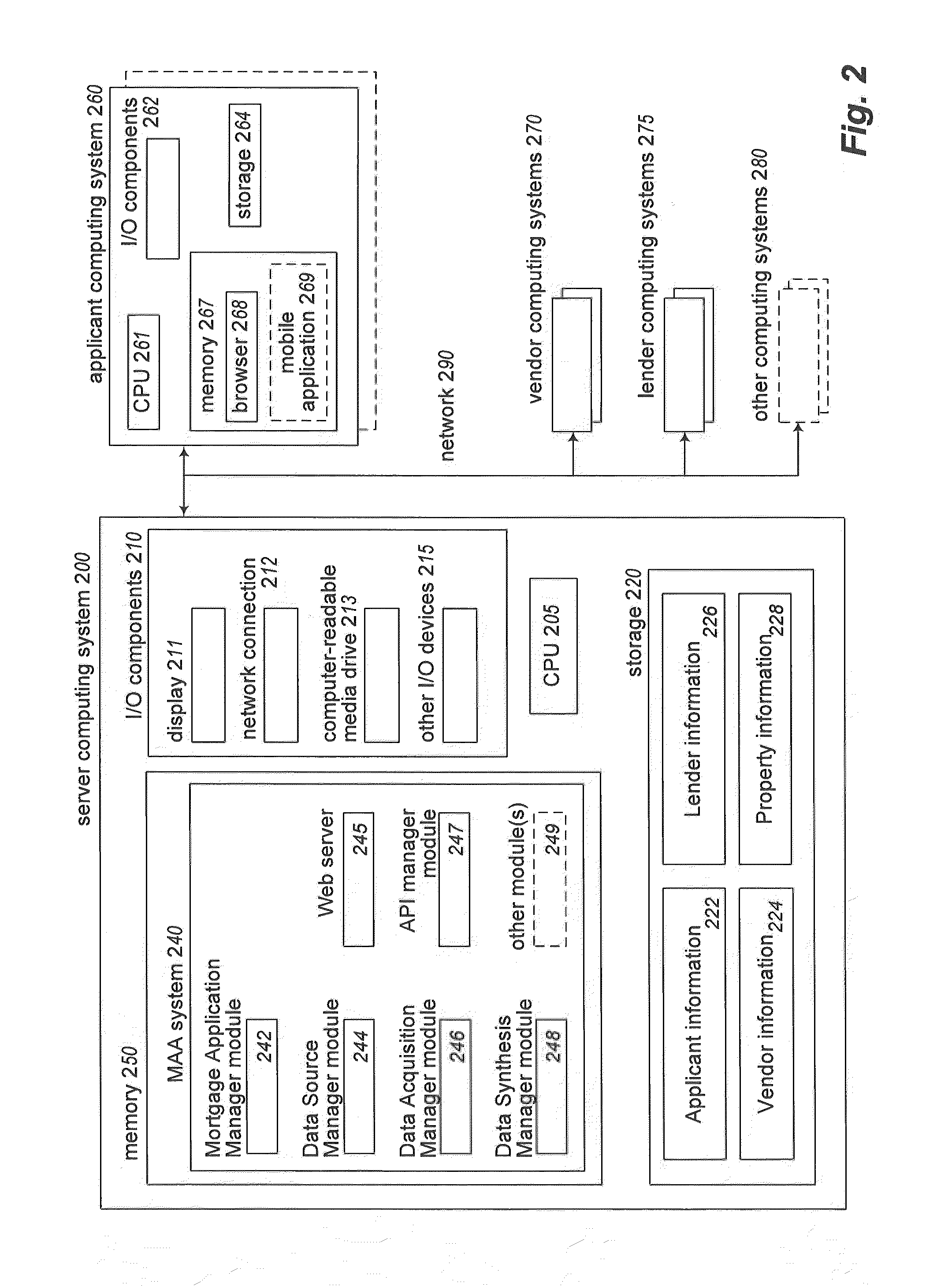
Mortgage synthesis and automation
Owner:BESMARTEE
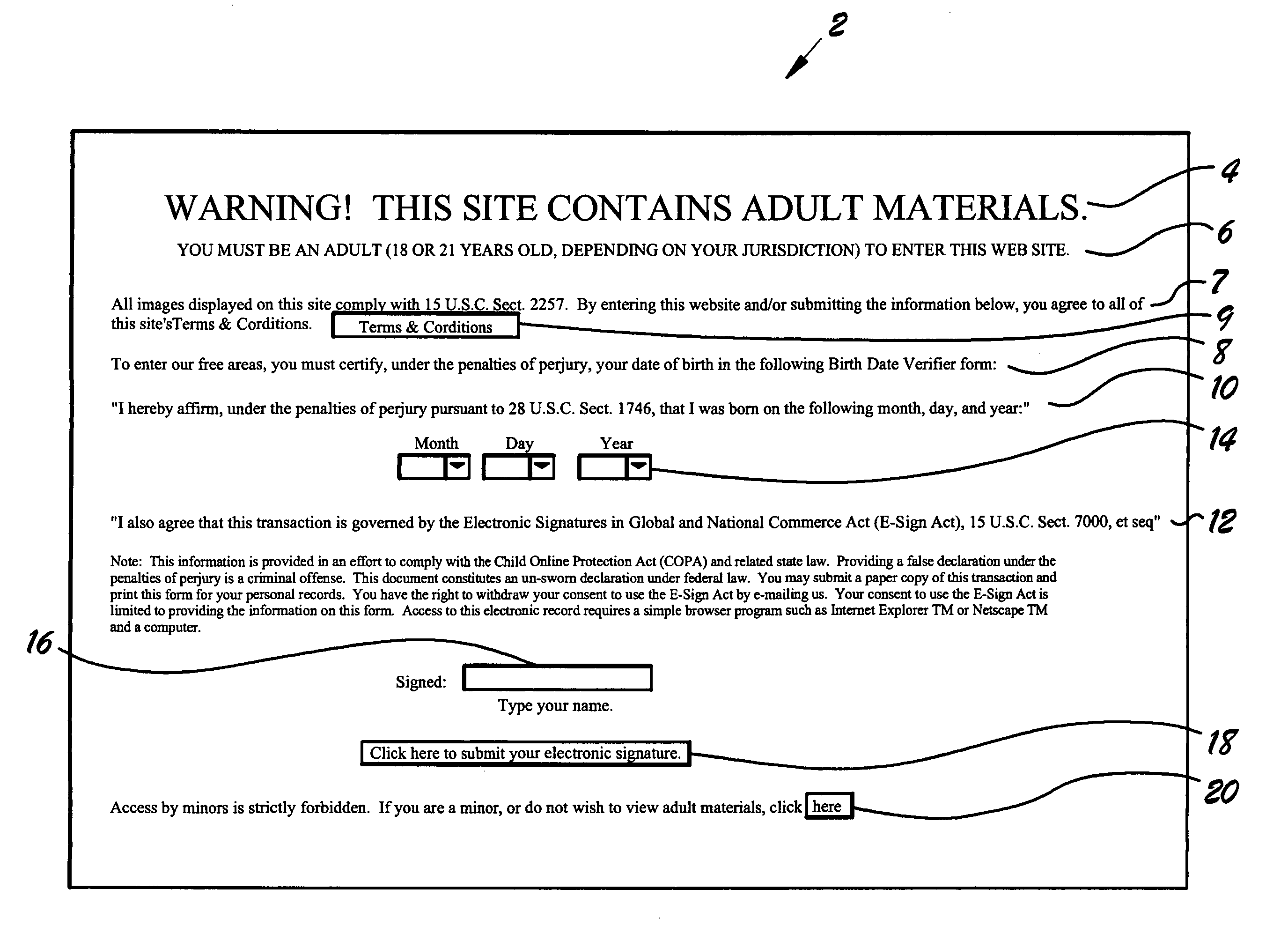
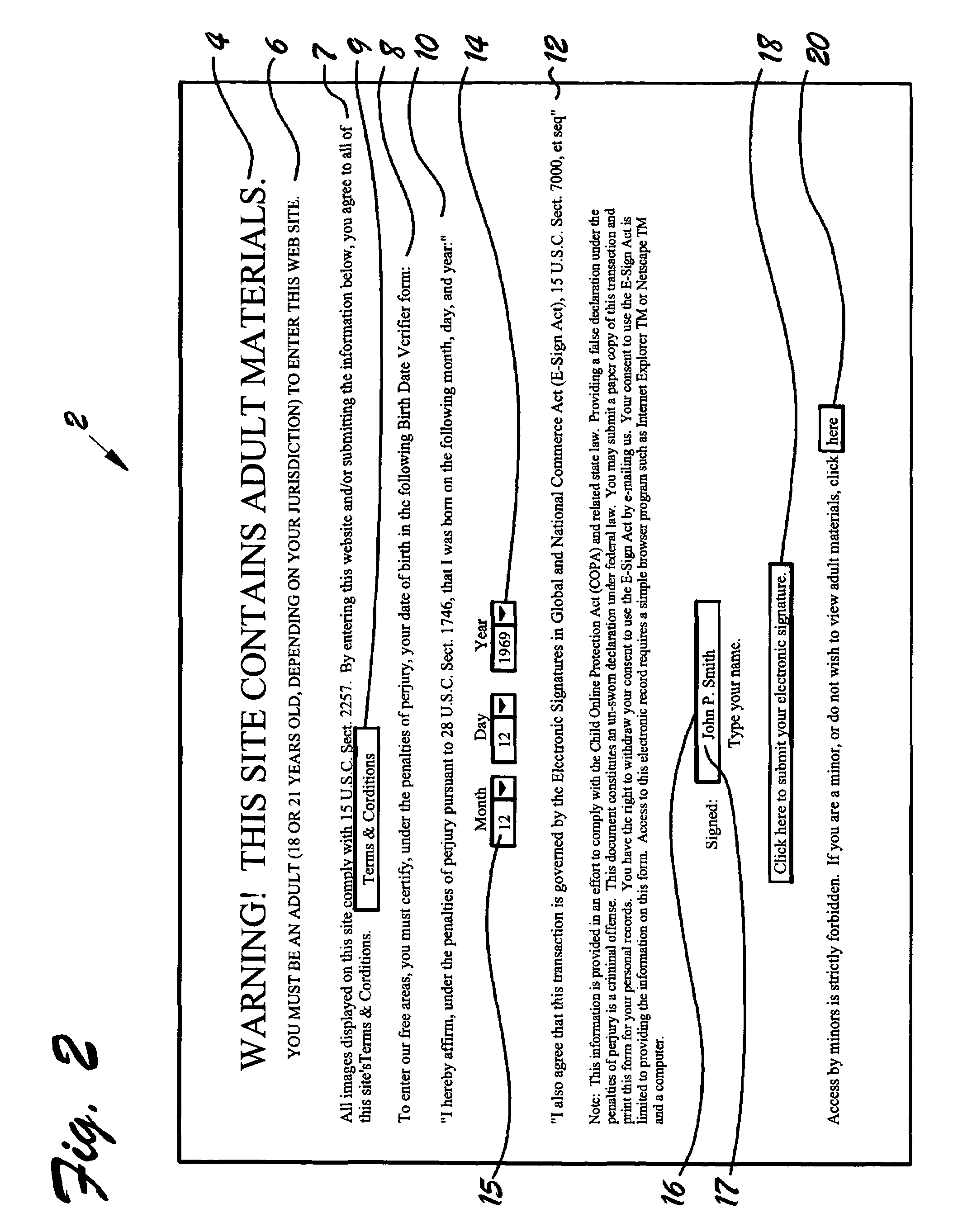
Method of age verification for electronic media
InactiveUS6959861B1Improve certaintyReduce the possibilityOffice automationData sortingValidation methodsIp address
A method of age verification for electronic media. The method includes the step of displaying a gateway page containing one or more of the following: a warning, user age limitation, terms and conditions, completion instructions, sworn statement, E-Sign Act statement, date of birth block, signature block, and activation button. User age and name are entered in the date of birth block and signature block. Upon clicking the activation button, software associated with the gateway page calculates each user's age by determining the difference between the current date and the user's date of birth. If the user's age thus calculated equals or exceeds a threshold age, access to the site is provided. If the user's name does not meet or exceed the threshold age, access to the site is denied. Names, dates of birth, times and dates of attempted access, and IP addresses may be stored in an access attempts record.
Owner:METRO INNOVATIONS
Integrated medical software system with patient pre-approvals
InactiveUS20110246225A1Cost-effective to implementCost-effective to maintainMedical report generationPatient personal data managementSocial Security numberPatient registration
An integrated medical software system with a patient registration software component executed by a processor of the system to capture patient information is disclosed. The system and method comprise a section where demographic data is input for the patient, said demographic data including at least one of a digital photograph, a name, an address, a date of birth, a social security number, and a sex of the patient; a section where financial data is input for the patient, said financial data including at least one of financial responsibility, outstanding balances, insurance coverage, insurance claims currently being processed, and account information of the patient; and a section where administrative data is input for the patient, said administrative data including at least one of scheduling information, reminders and alerts, visit check-in and check-out, and system preferences for the patient, wherein the patient is pre-approved for at least one of a referral, a hospital admission, a clinician's order, a medical procedure, or a medication that would otherwise require prior approval based on at least one of the demographic data, the financial data, and the administrative data.
Owner:GREENWAY MEDICAL TECH
Deferred payment and selective funding and payments
InactiveCN103270523AIncrease flexibilityEasy to controlPayment architectureCommercePaymentEmail address
A user is able to change one or more payment options after payment has already been made to a merchant. A payment provider processes a payment request during a transaction with the merchant with default or selected payment options. After the transaction with the merchant is completed and the merchant has been paid, the user may change one or more of the payment options, such as funding source(s) and terms / conditions of payment (e.g., deferment period, installment period / amount, etc.). During the transaction, the user may make a purchase through the payment provider even if the user does not have an account with the payment provider by providing user information, such as name, address, phone number, email address, and date of birth, but not a social security number or funding source information.
Owner:PAYPAL INC
Computer based method of pricing equity indexed annuity product with guaranteed lifetime income benefits
A computer-based method for determining a set of equity-indexed crediting parameters E for a lifetime-income equity-indexed deposit product provided to a set of owners having a set of dates of birth B, a rider charge C, a lifetime income percentage scale L, a set of profitability requirements R, a principal amount P, and an account value A. The method can include the steps of: establishing the values of C, L, R, P, A and E at a time when said deposit product is purchased; generating a set of yield curve and equity index scenarios consistent with valuation parameters; setting a trial value Ei for E; calculating the observed distribution D of profitability; comparing D with R; and, computing a revised trial value Ei+1 for E, where the steps of establishing, generating, setting, calculating, comparing, and computing are performed by at least one general purpose computer.
Owner:GENESIS FINANCIAL PRODS
International alpha-numeric demographic identity code
InactiveUS20110101115A1Data processing applicationsRecord carriers used with machinesBirth parentsPlace of birth
A universal system and apparatus for the creation, storage, management, manipulation and display of a unique human biometric signature containing both static and dynamic coded information regardless of background or nationality, comprising a user interface to receive data regarding life statistics, a first set of mappings correlating each life statistic with a coded representation for the life statistic, a second set of mappings correlating the coded representation with one of a series of linear positions. Coded life statistics comprise current name, sexual identity, date of birth, country of birth, place of birth, maiden name of the birth mother, name at birth, ethnic and tribal classification, blood type, occupation, country and location of residence. Ethnic classifications are combined from birth parents. Location codes are derived from International Civil Aviation Organization codes. The biometric signature is displayed as an alphanumeric string read from left to right and / or as a two-dimensional barcode.
Owner:OJARALI SYST LLP
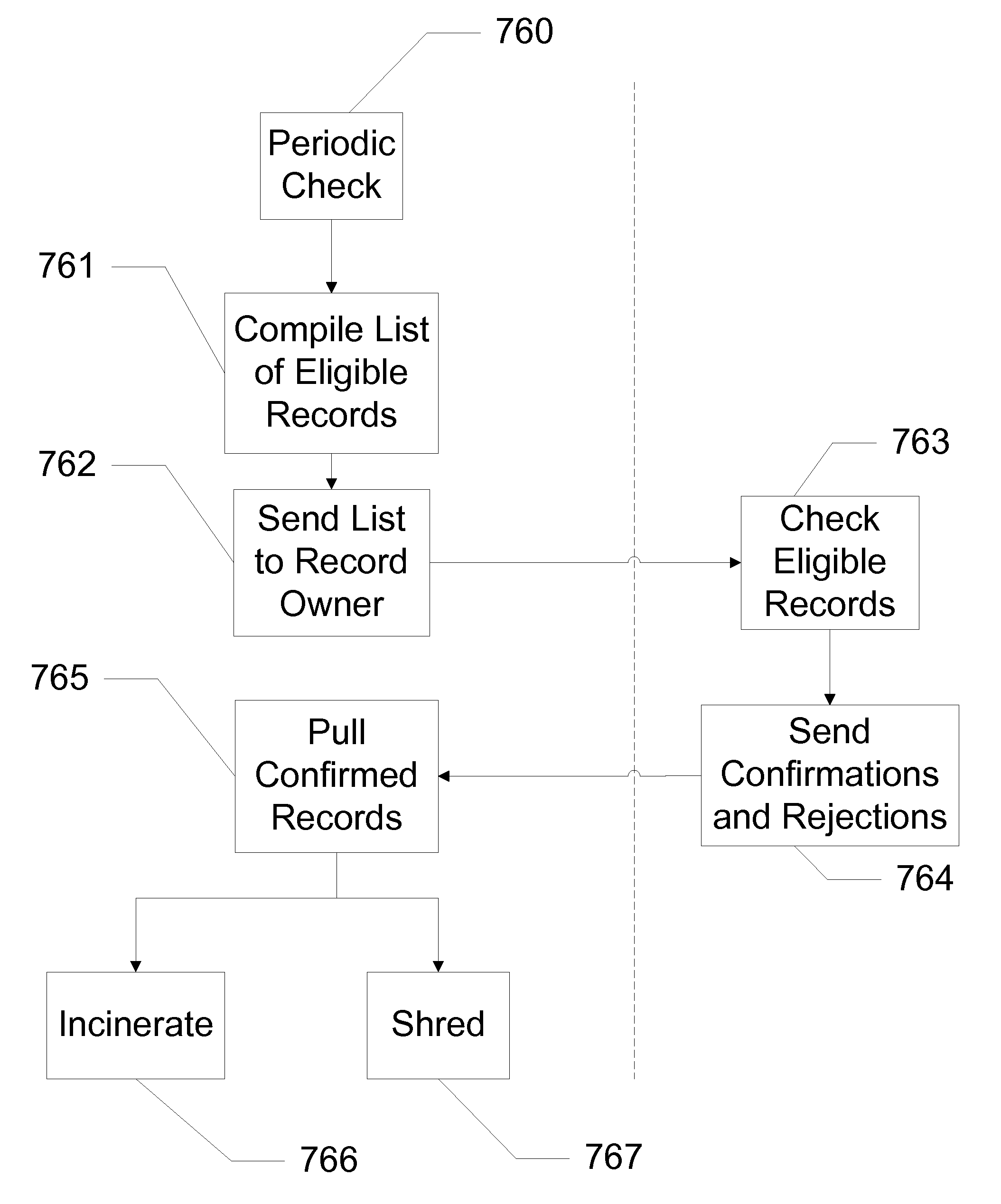
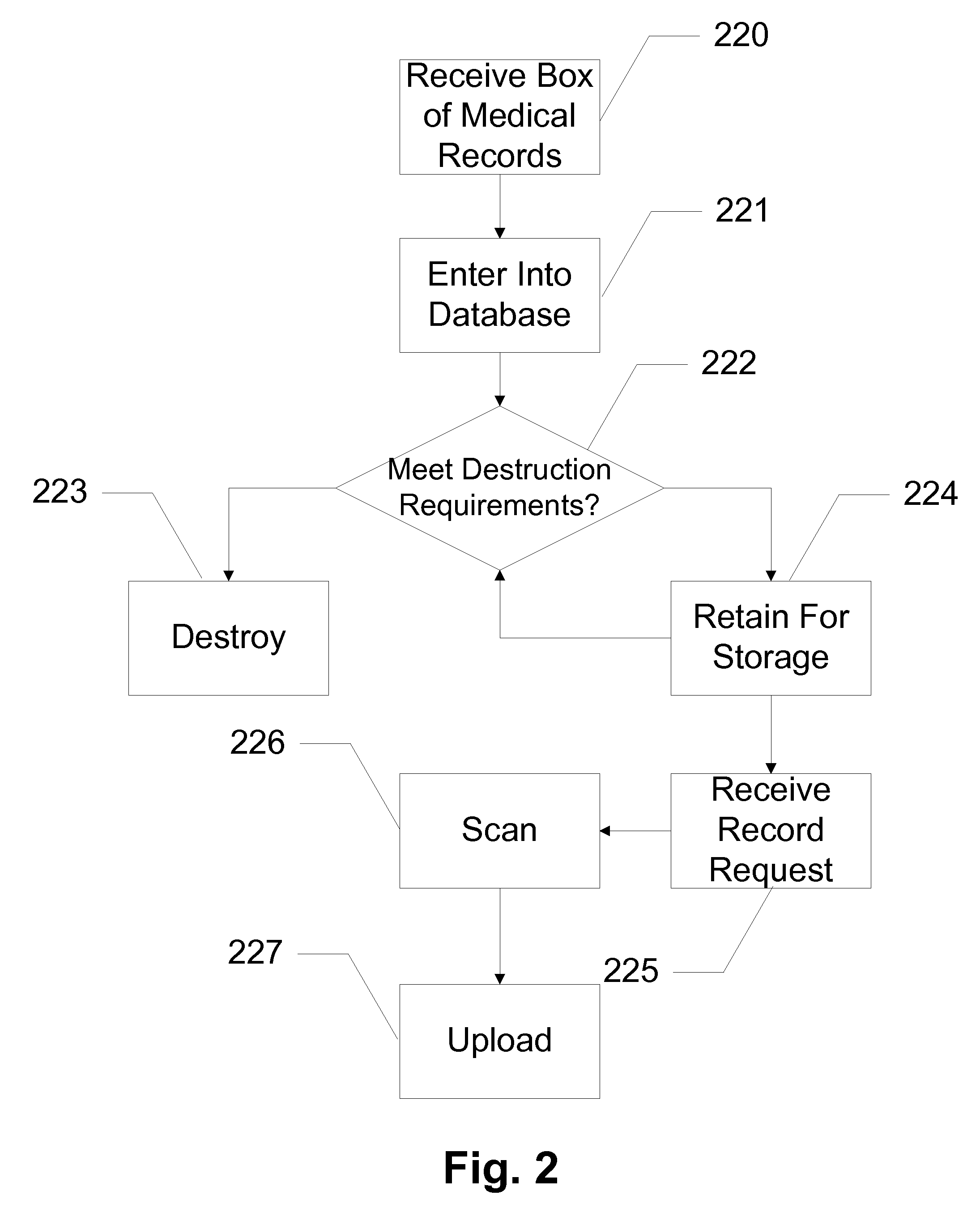
Systems and Methods for Maintaining Records
InactiveUS20100169296A1Improving medical record retrievalImprove destruction efficiencyDigital data processing detailsMemory adressing/allocation/relocationCatalogingDate of birth
Systems and methods are disclosed which relate to collecting, cataloguing, reproducing, and destroying records. Medical, legal, and other records from hospitals, medical offices, law offices, etc. are sent to a storage facility. Entry fields, such as name, record number, date of service, and date of birth, from each record are entered into a database. The database catalogues each record as well as the box the record is in and where the box is located. The system allows professionals to search the database over a secure connection. Multiple search fields allow a professional to search the database using any of a plurality of criterion. Search logic enables a cross-field search for a specific query. When professionals request a record, the record is pulled at the storage facility and physically or electronically sent to the professional. The system also keeps track of records eligible for destruction as well as those destroyed. Files eligible for destruction are destroyed after the requisite permission is given.
Owner:EVRICHART
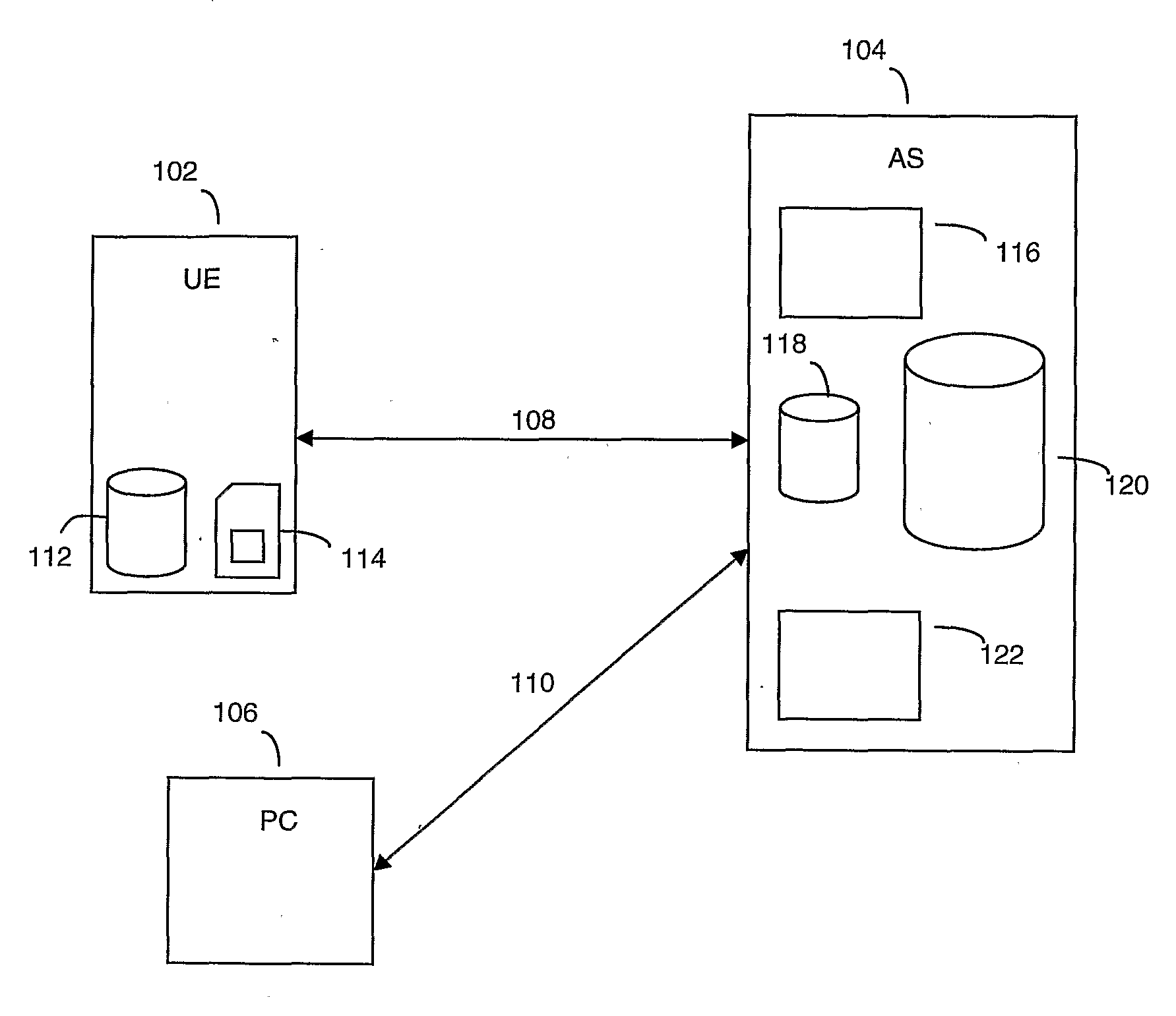
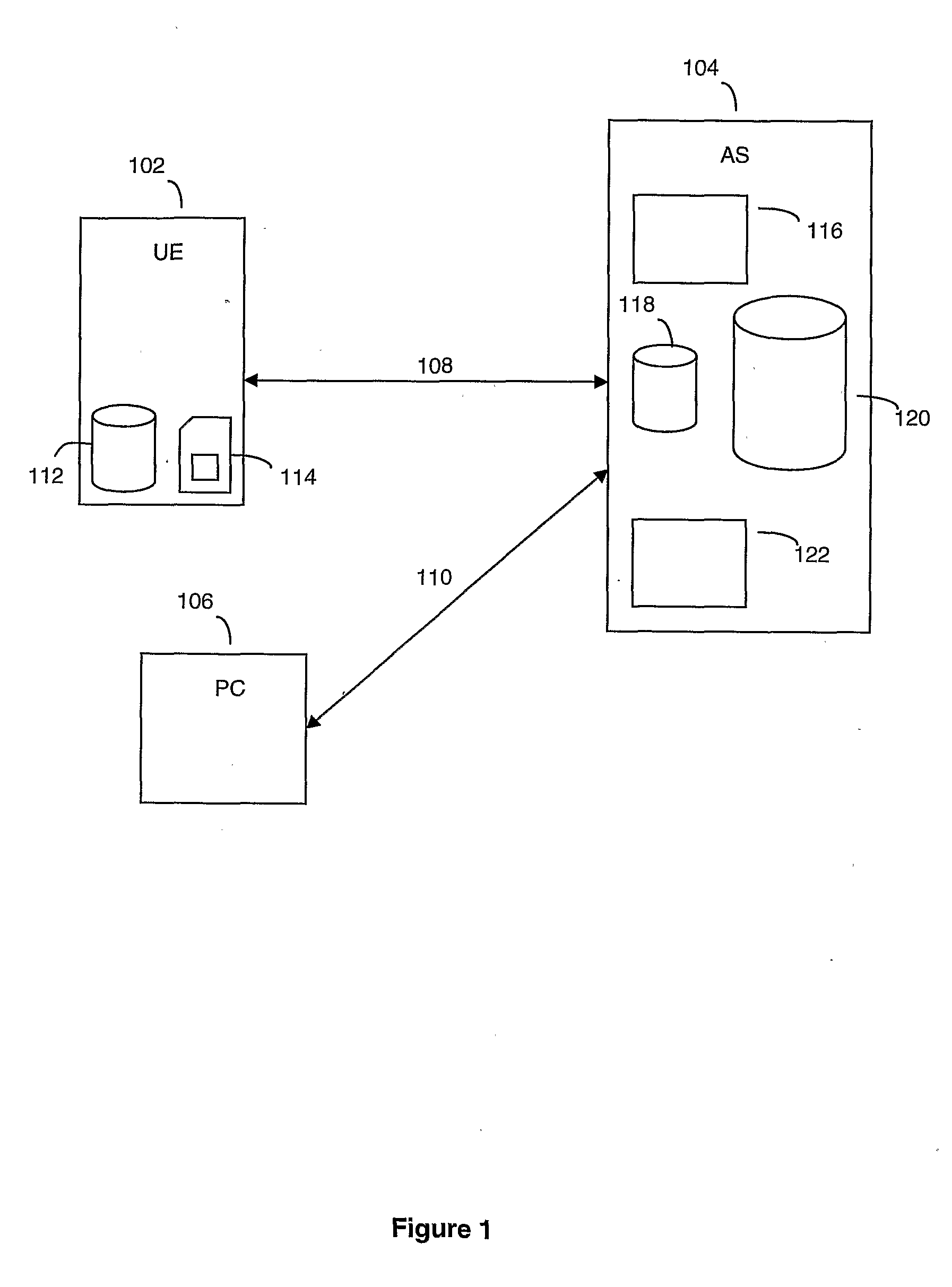
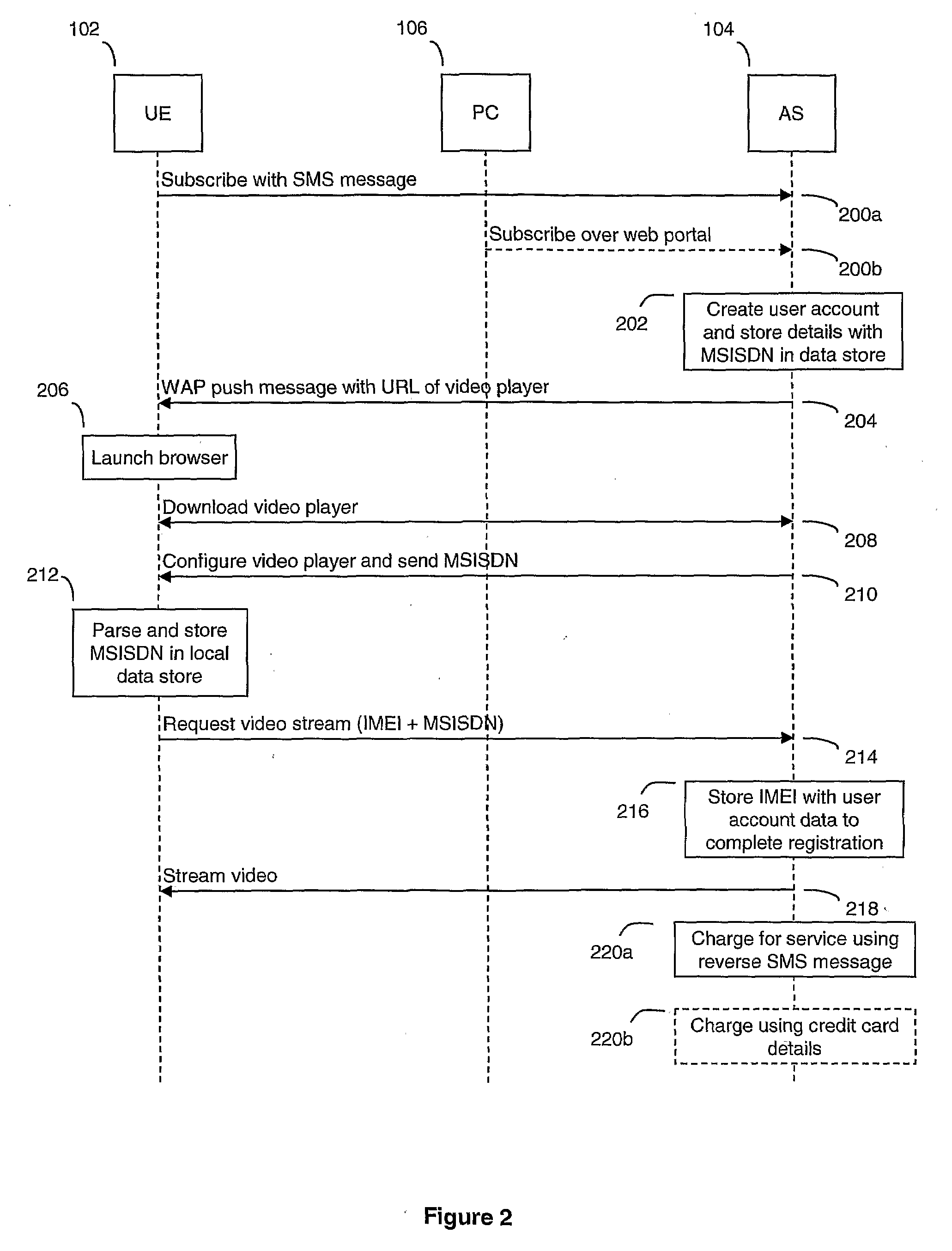
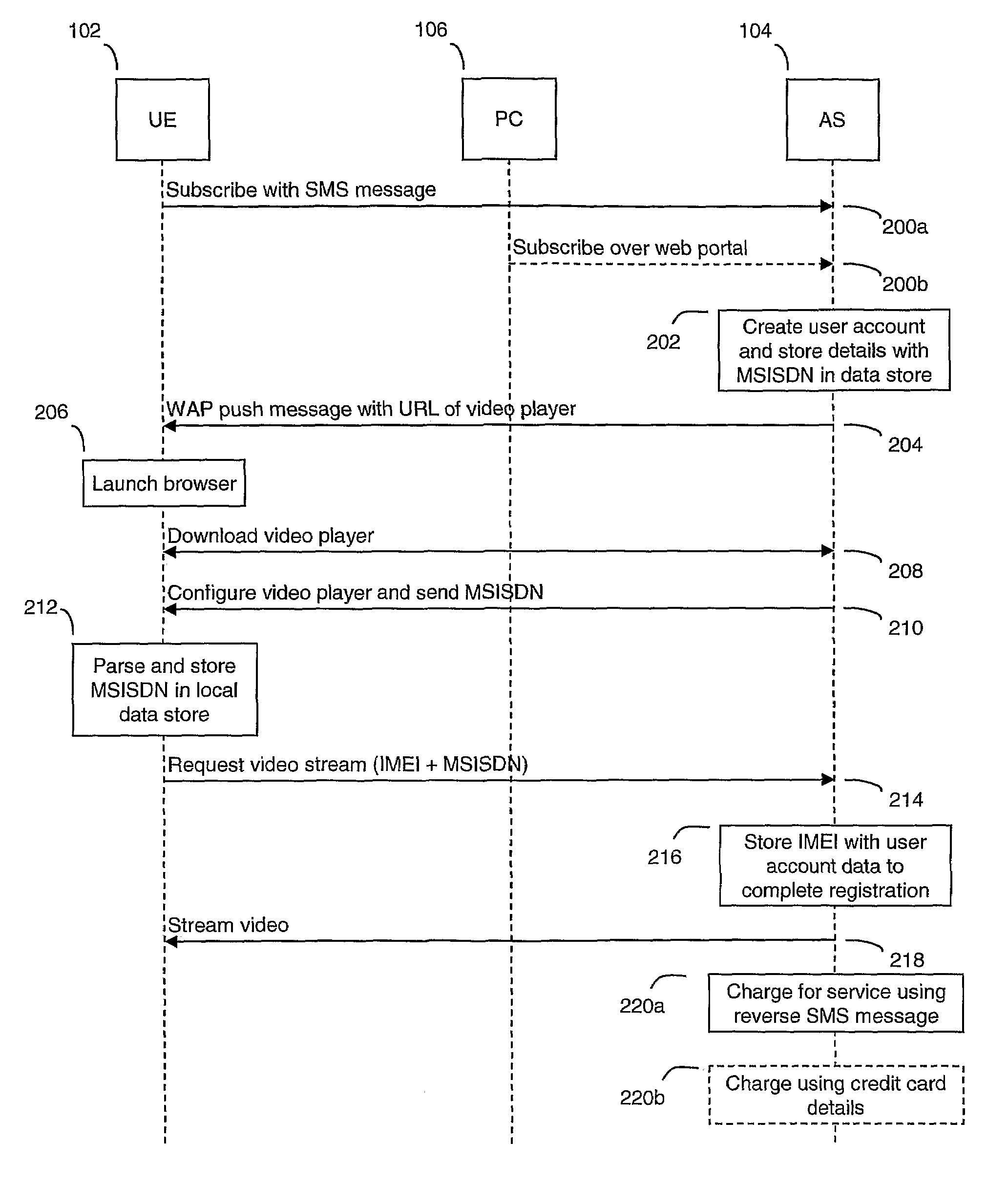
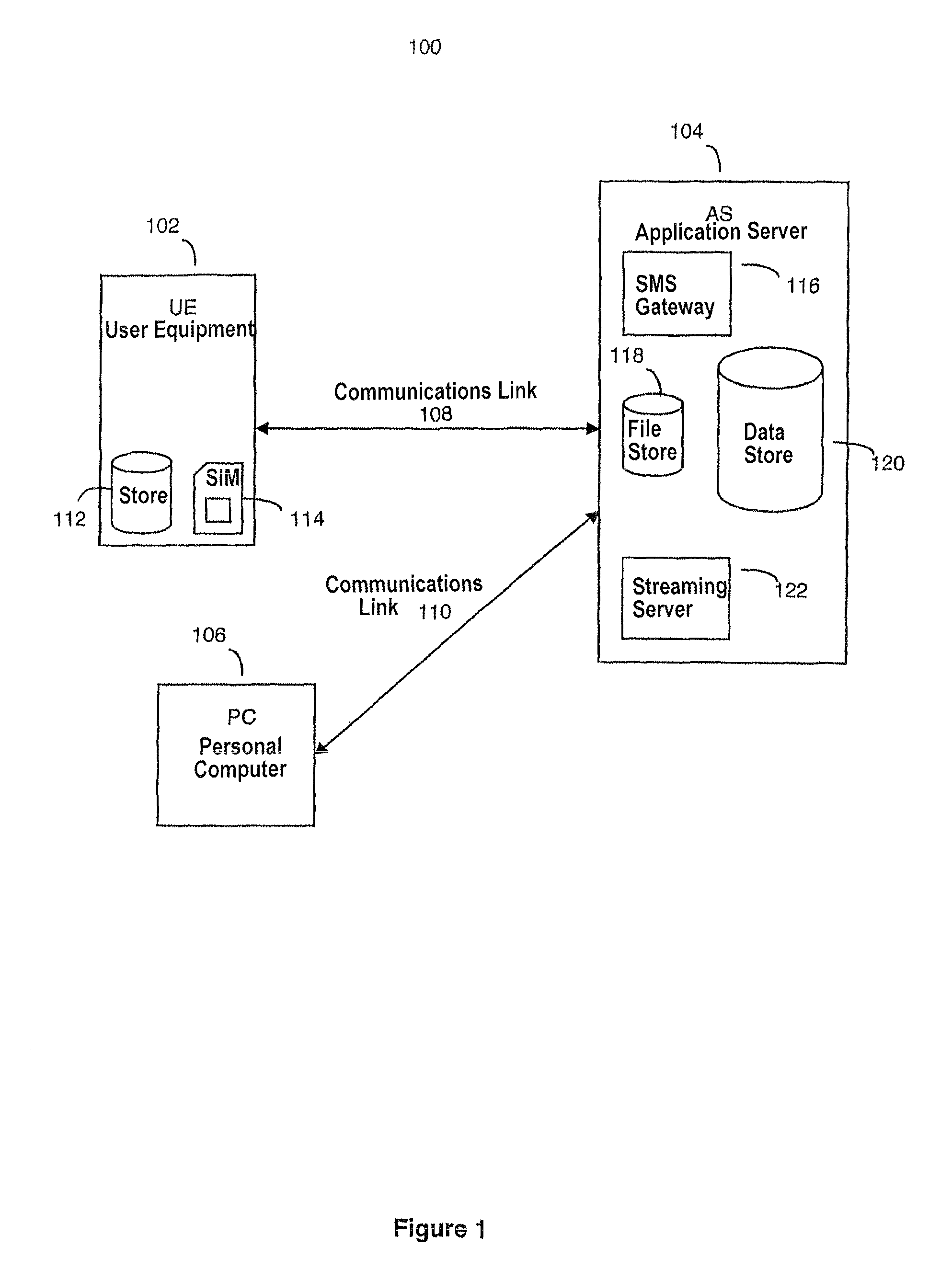
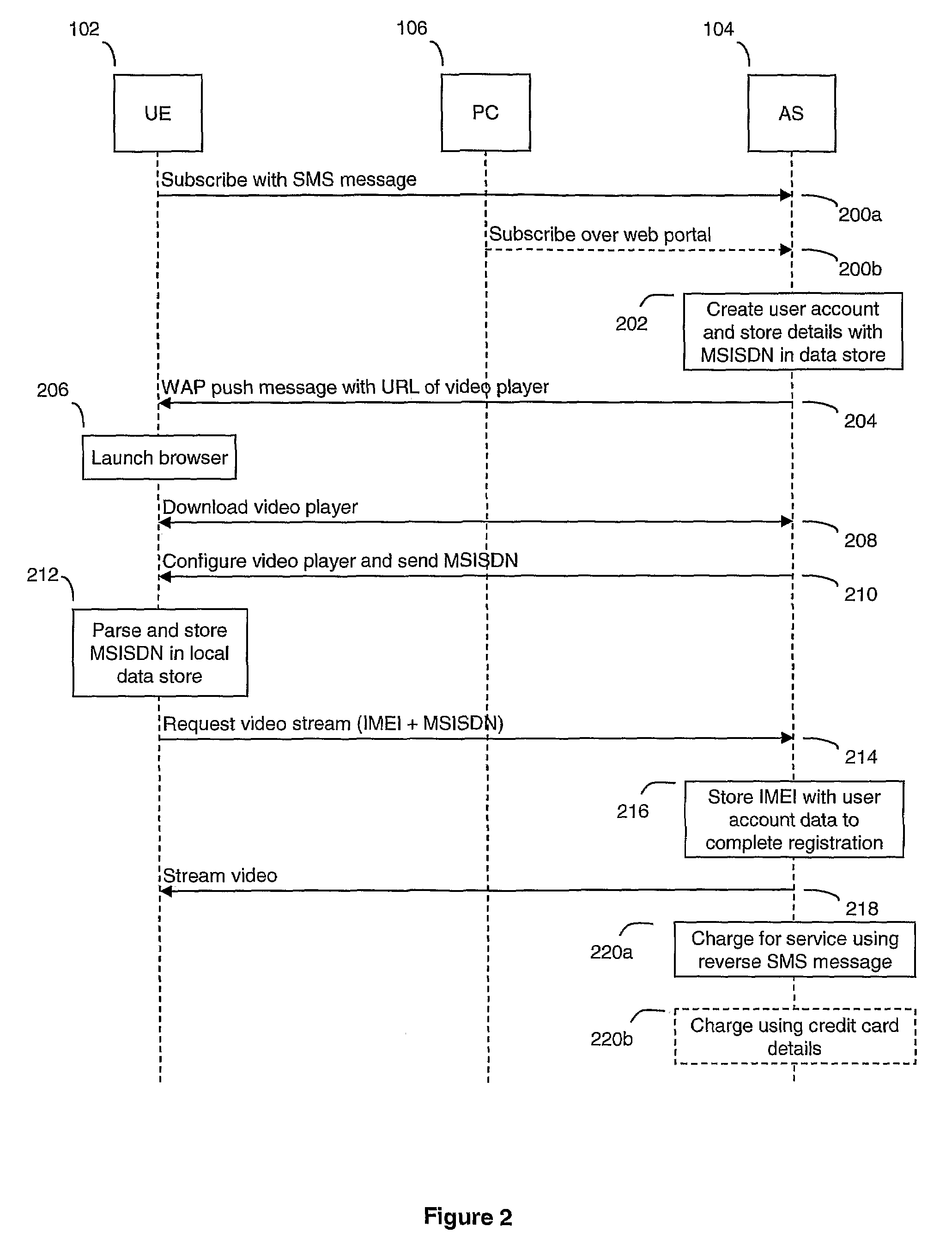
Automated User Registration
ActiveUS20080320573A1Simple methodEasy to useDigital data processing detailsUser identity/authority verificationAccess networkPassword
For users to access network services such as video streaming from a device, users usually have to register themselves with the service first. Most registration mechanisms require a user to input a username, password, date of birth and other details. When implemented through a web interface, this mechanism is relatively easy for the service provider to provision. However, the problem is that users are required to manually enter significant amounts of information which can be both time consuming, especially on a mobile device where there usually no QWERTY input device, and susceptible to unintentional errors. The present invention proposes an automated registration process that does not require a user to enter any details manually except for the initial request to subscribe to a service. The process gathers information automatically about the user and the device used, which is then stored and used for user authentication during subsequent service requests following the initial subscription request. The subsequent requests for service also do not require the user to manually input any user data.
Owner:BRITISH TELECOMM PLC
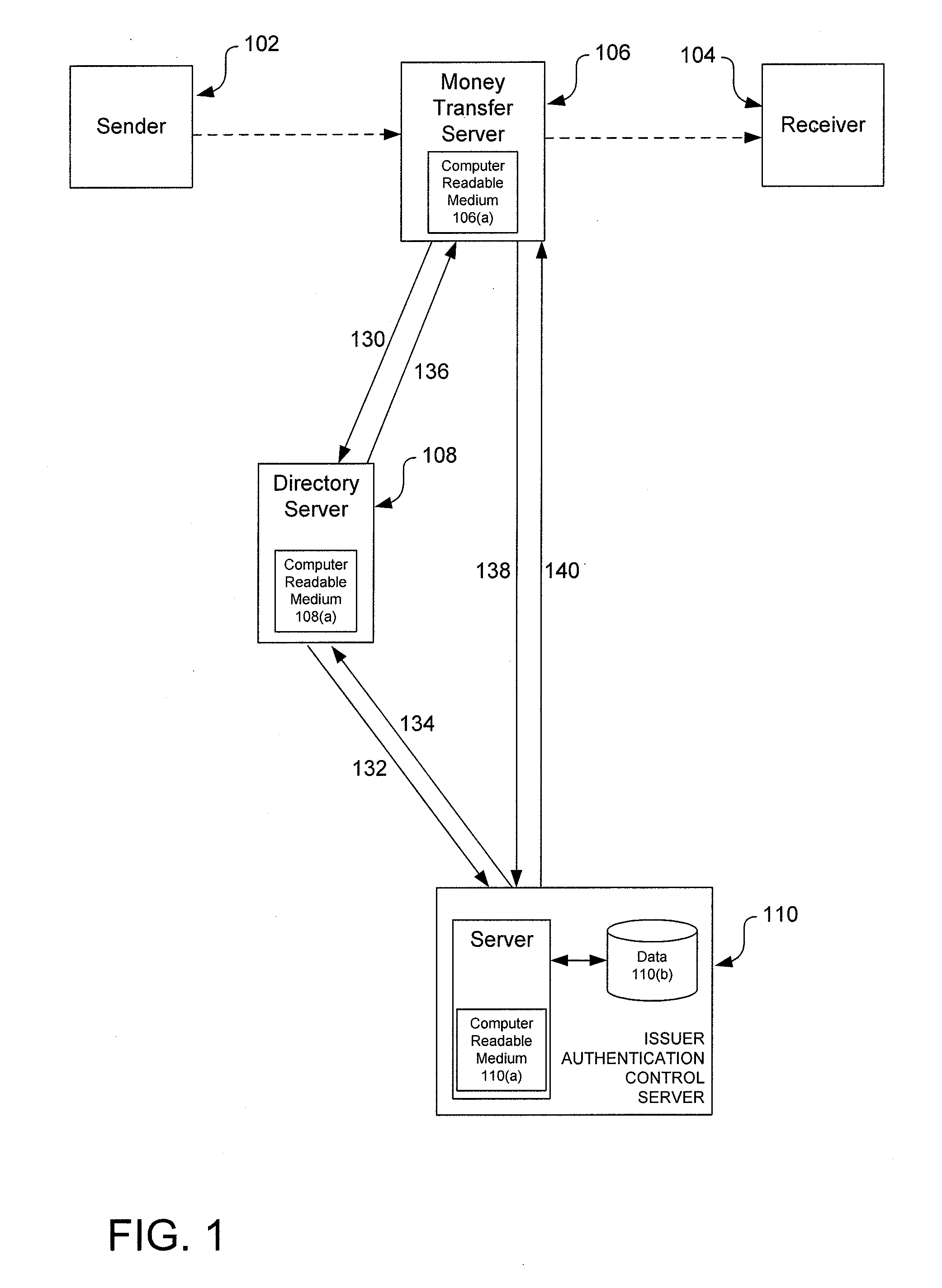
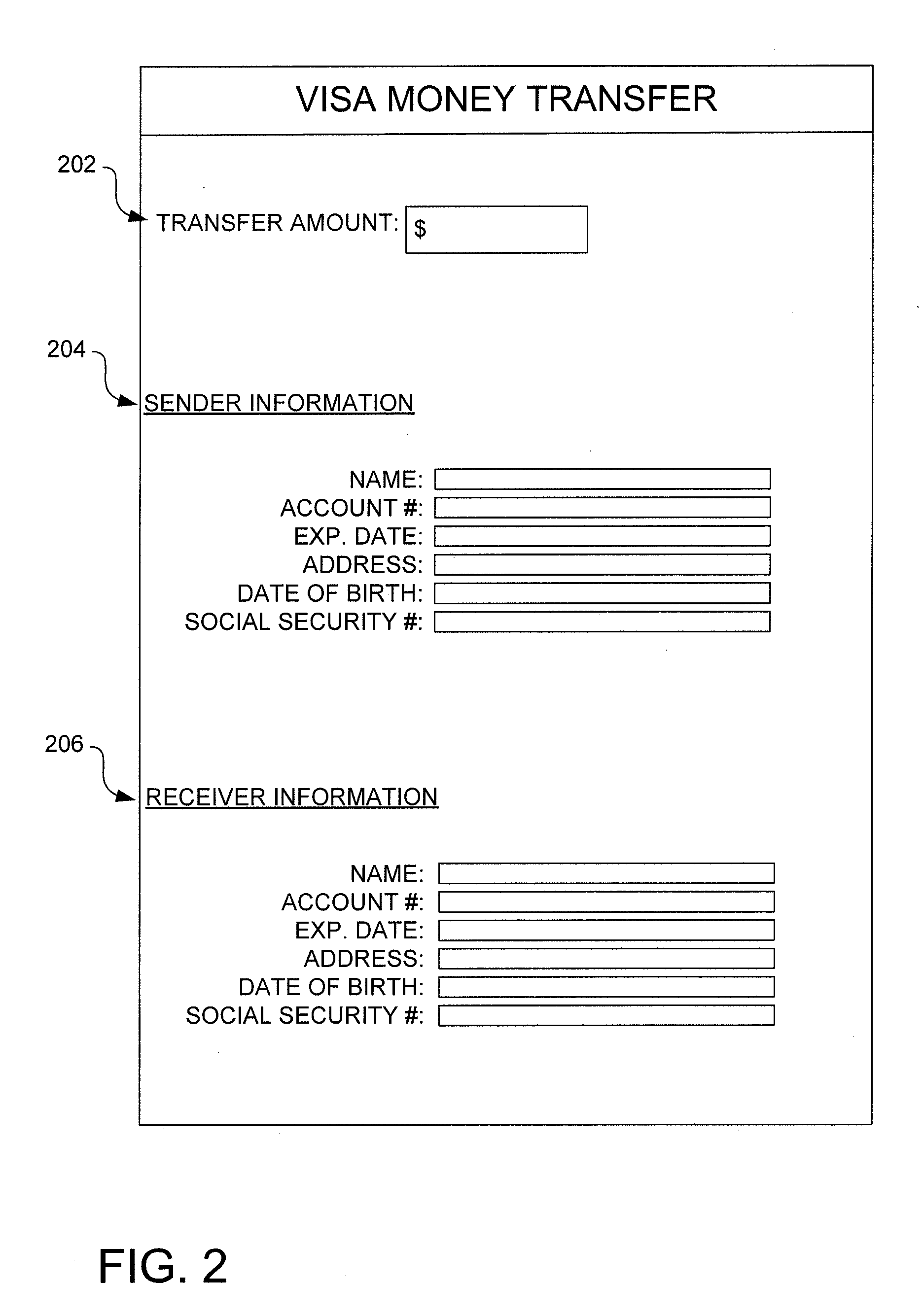
Authentication framework extension to verify identification information
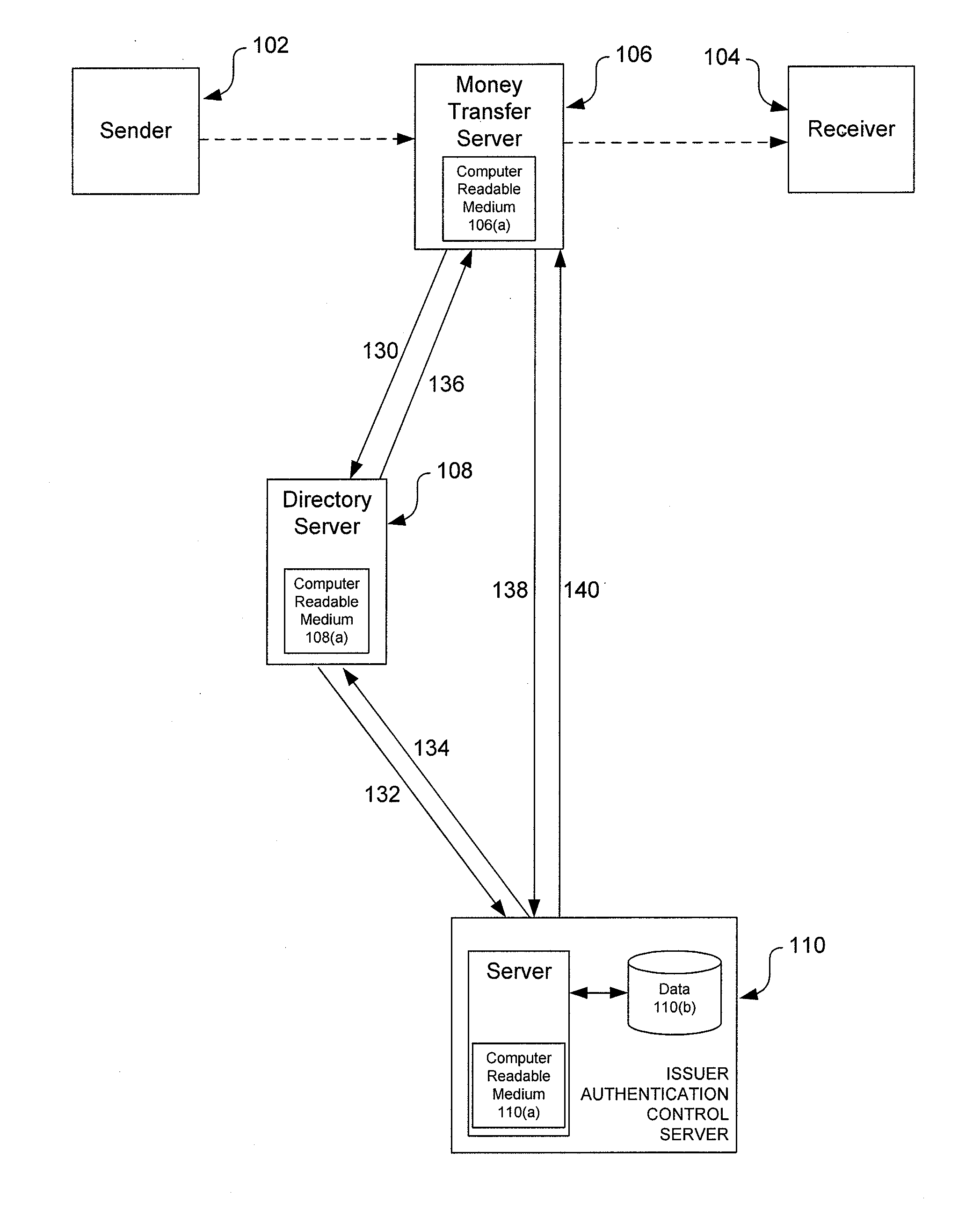
Systems and methods for authenticating parties involved in a transaction are disclosed. Some embodiments of the disclosure are directed to systems and methods for authenticating various identification attributes of a participant in a transaction. The attributes can include items such as the participant's name, address, social security number, date of birth, or any other identifying attributes. In some embodiments, all participants in a transaction may have identification information authenticated. The 3-D Secure protocol and framework is extended and enhanced to provide the ability to authenticate the identification details of participants in transactions.
Owner:VISA INT SERVICE ASSOC
System and method for protecting the privacy of identity and financial information of the consumer conducting online business
InactiveUS10171476B2Reduce restrictionsUser identity/authority verificationSecurity arrangementElectronic documentOnline business
The migration of identity documents, such as driving licenses, from physical documents to electronic documents creates new problems for those seeking to verify the identity of an individual based upon the electronic document they provide. However, the inventors have established a means of binding electronic documents and electronic representations of physical documents to individuals at issuance of the document(s). Accordingly, the inventors address identity verification by providing to those seeking to verify the individual's identity data allowing them to verify the presented electronic ID document. For example, a police officer requesting a driving license can obtain on their own electronic device through the methods of the invention the issued driving license associated with identifier information on the license provided by the individual. As such tampering with the license to change a name, date of birth, photo etc. will result in a visible mismatch to the police officer in comparing them.
Owner:KHAN SAL
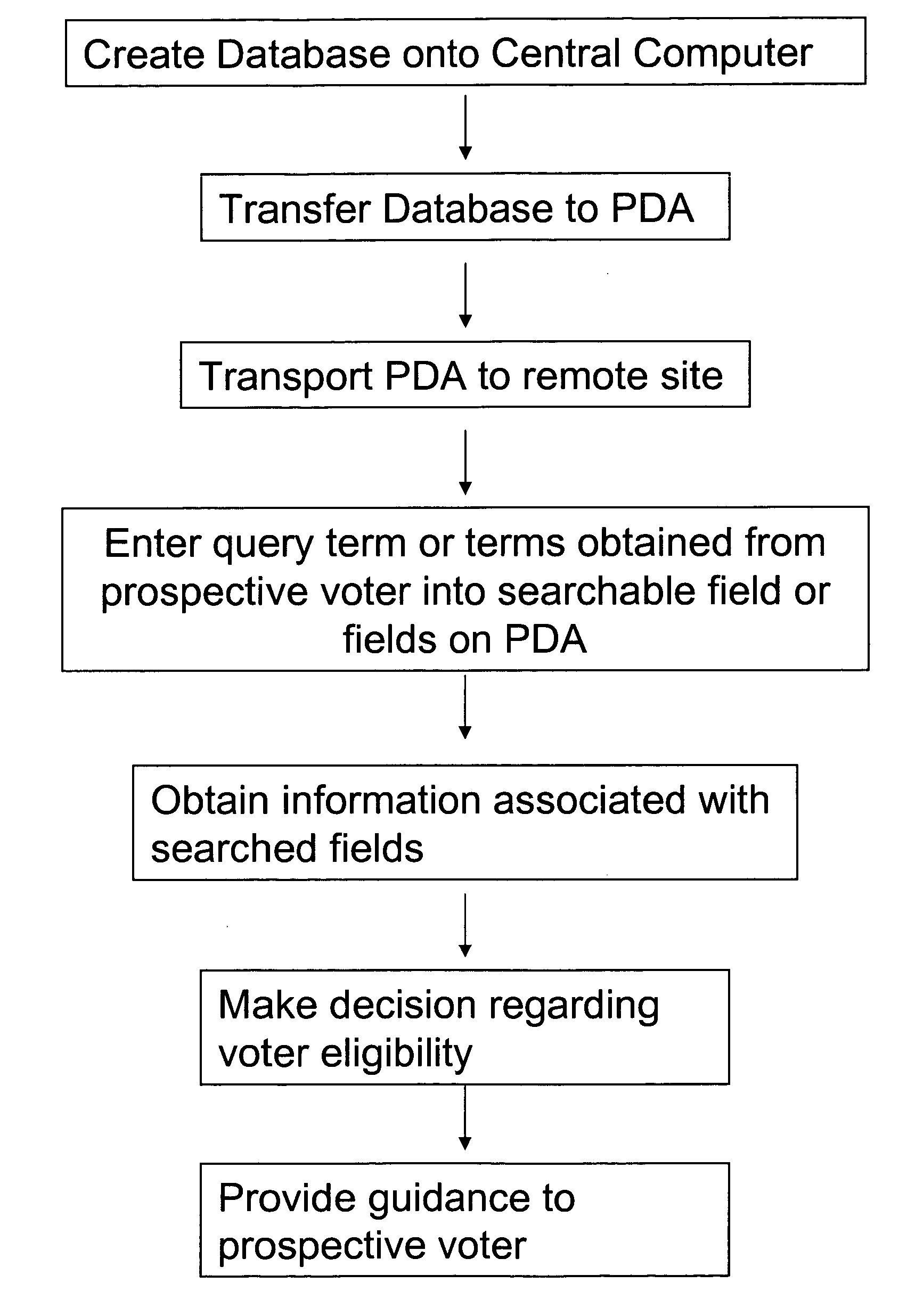
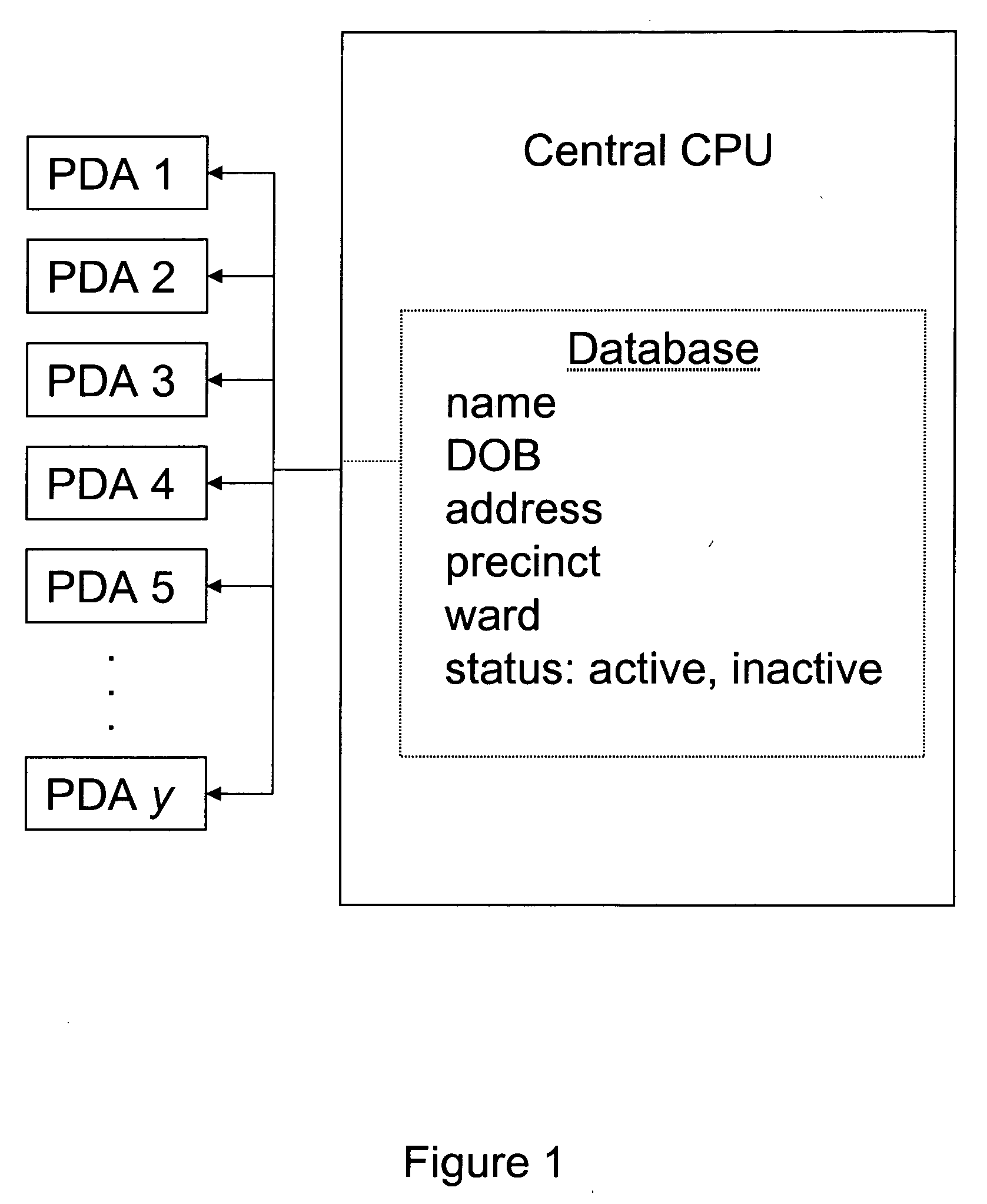
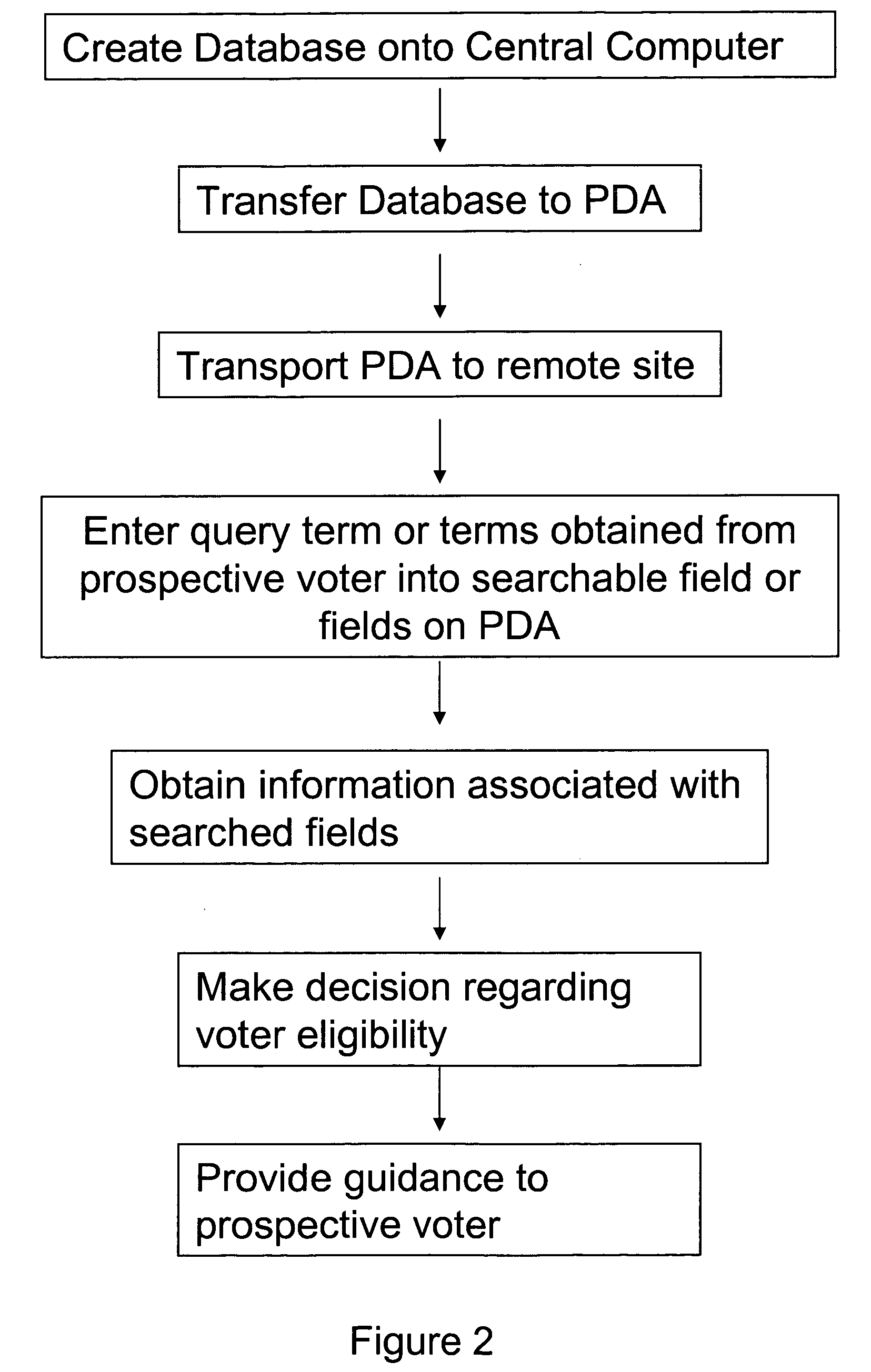
Electronic voter registration system and method
InactiveUS20060036481A1Improve accuracyImprove efficiencyVoting apparatusError detection/correctionData miningDate of birth
A system and a method for facilitating an election. A database containing voter registration information is downloaded from a central computer to a portable computer that is accessible at a polling station. The database can be searched by a proctor or official at the polling station to determine whether a prospective voter is eligible to vote at the polling station. The name or name and date of birth of the prospective voter is entered into a search field of the portable computer and the database is searched. If and when a matching record is found, additional information is displayed on a second screen and the proctor or official can make a determination whether the prospective voter is eligible to vote at the polling place.
Owner:ELECTION ADMINISTATORS
Automated user registration
ActiveUS8370912B2Simple methodEasy to useDigital data processing detailsUser identity/authority verificationUser authenticationMinutiae
Owner:BRITISH TELECOMM PLC
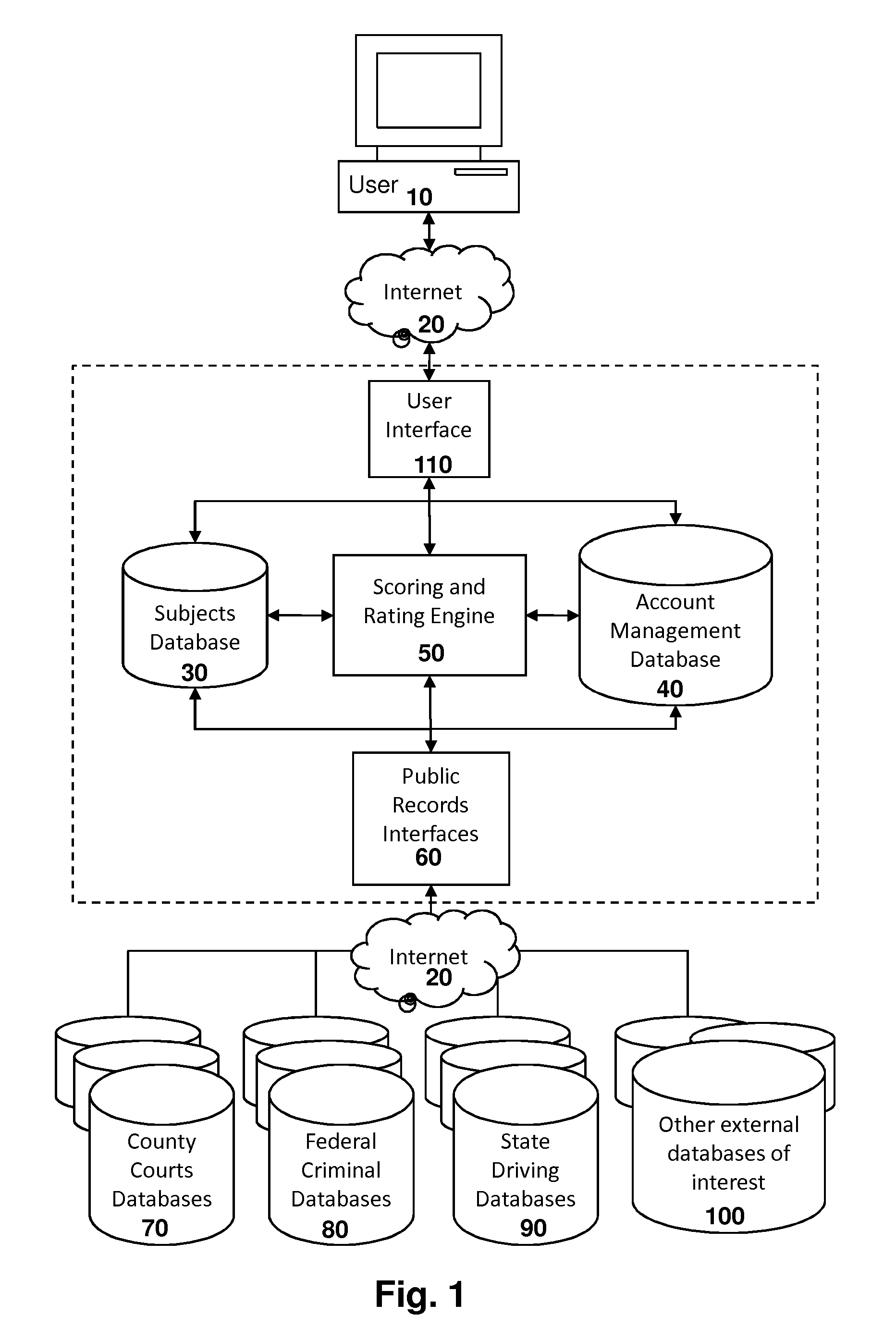
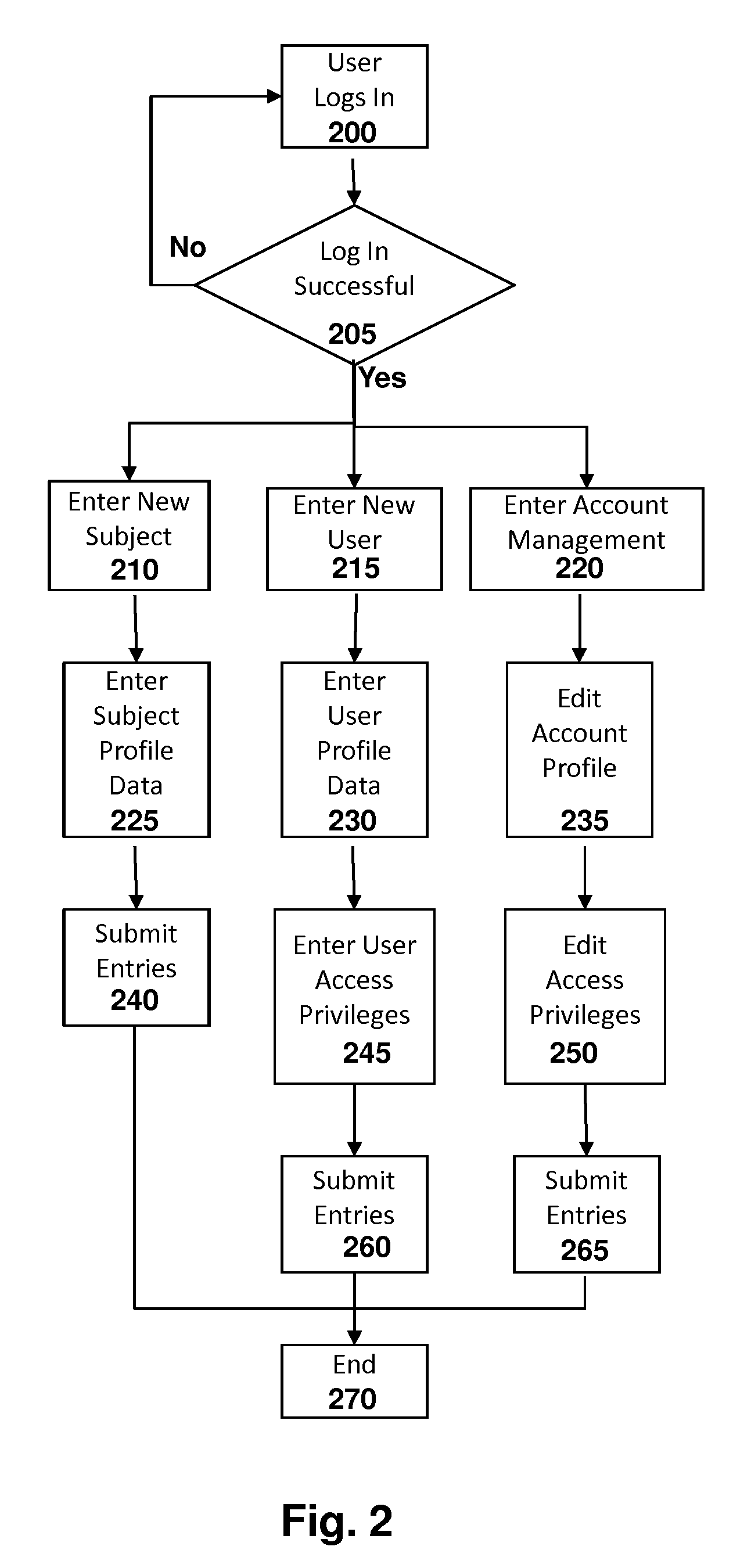
System for Conducting Persistent Periodic Common Weighted Background Investigations
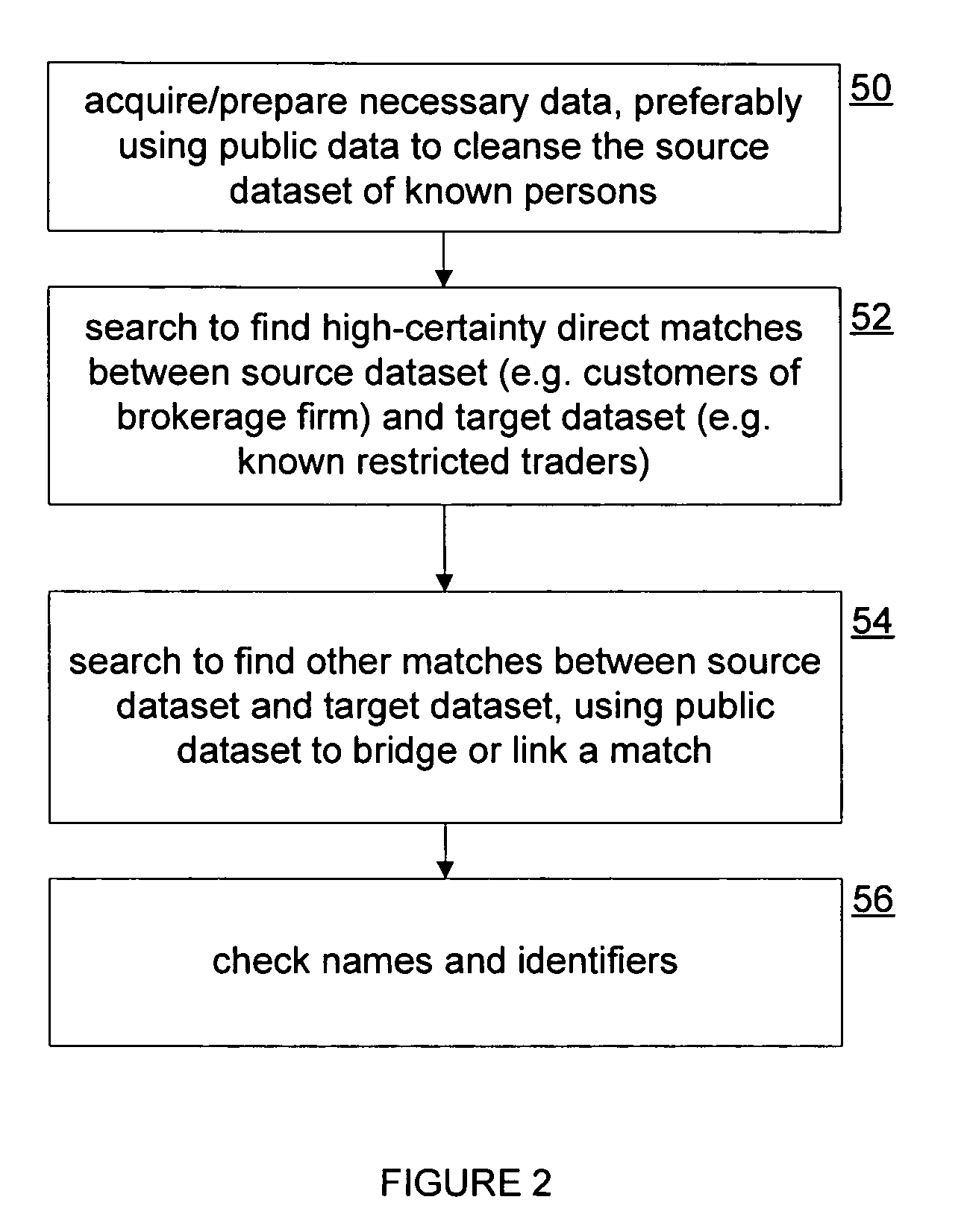
A system for conducting persistent common weighted personnel background investigations. An investigator enters the subject's known applicable information that includes the subject's name, address, social security number, date of birth into the system. Once entered into the system, a report on background investigation findings is automatically generated and provided to the investigator. The report also contains a risk score and rating for the subject based on a common weighted set of evaluation criteria. Periodically afterward, a report of any new background investigation findings is automatically provided to the investigator along with the updated risk score. Reports continue to be generated periodically until the subject's name is removed from the system.
Owner:GRAY ANTHONY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com