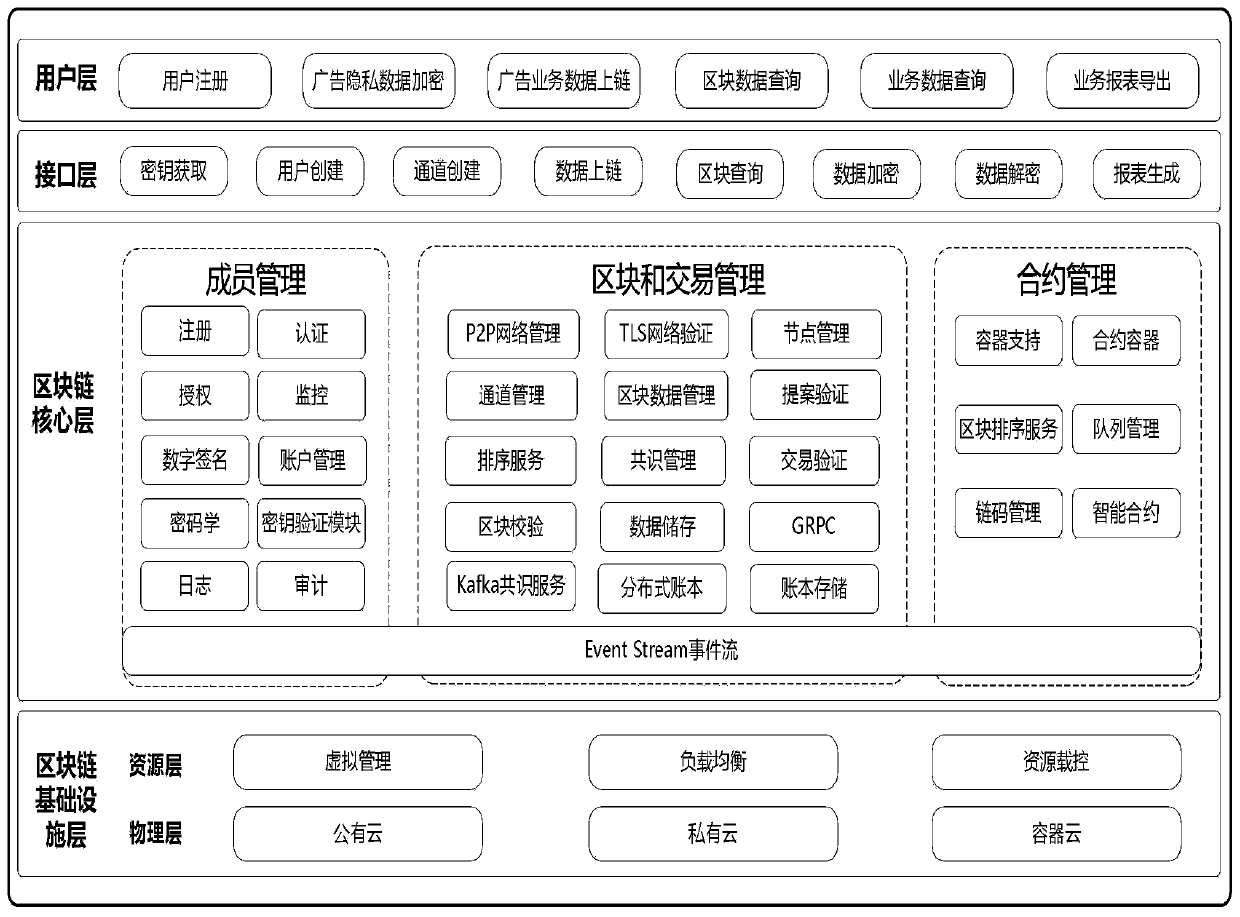
Patents
Literature
240results about How to "Avoid substitution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
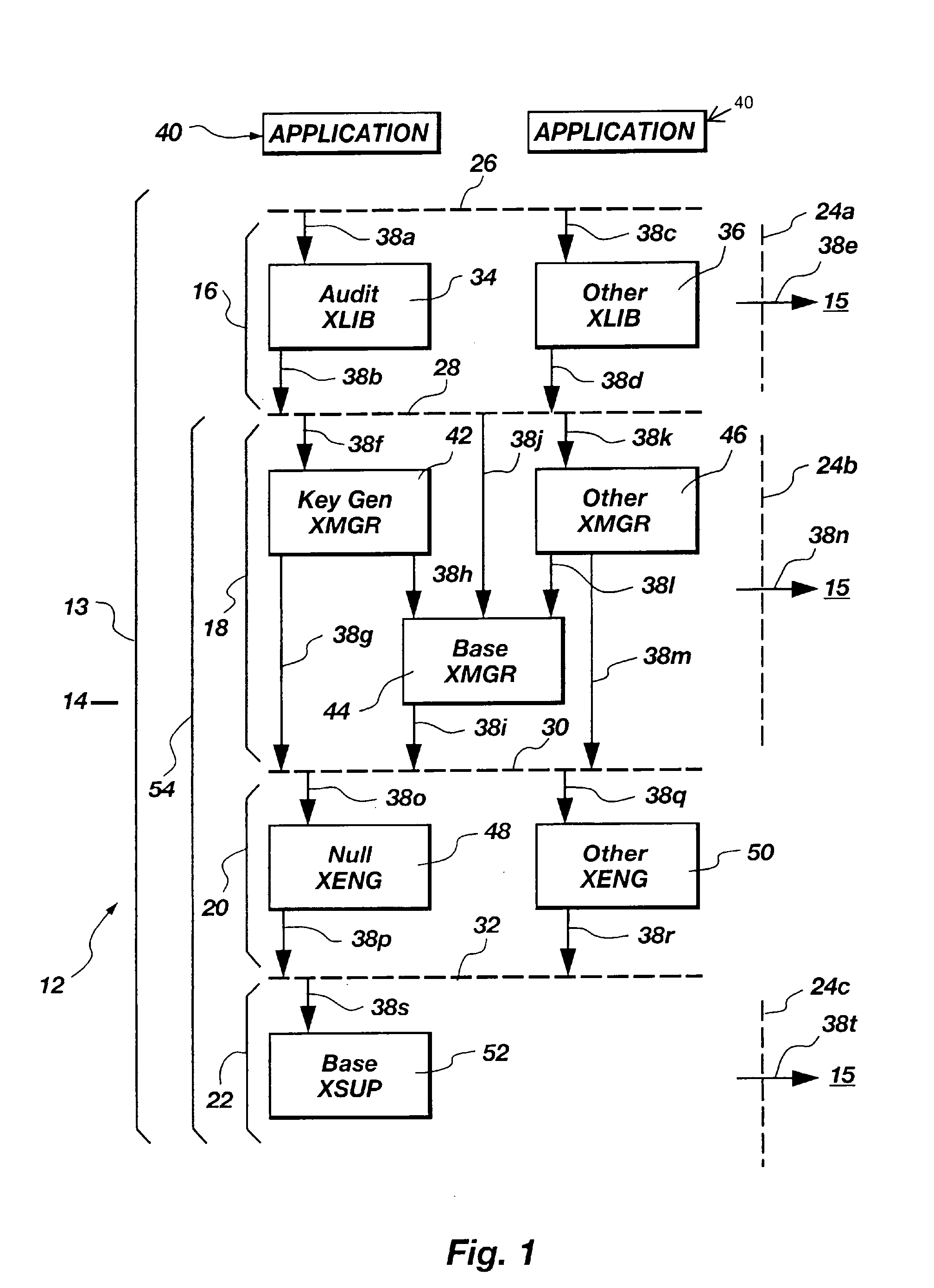
Double connector for medical sensor
InactiveUS7083480B2Firmly connectedReduce in quantityElectrocardiographyElectric discharge tubesCardiography impedanceMedical treatment
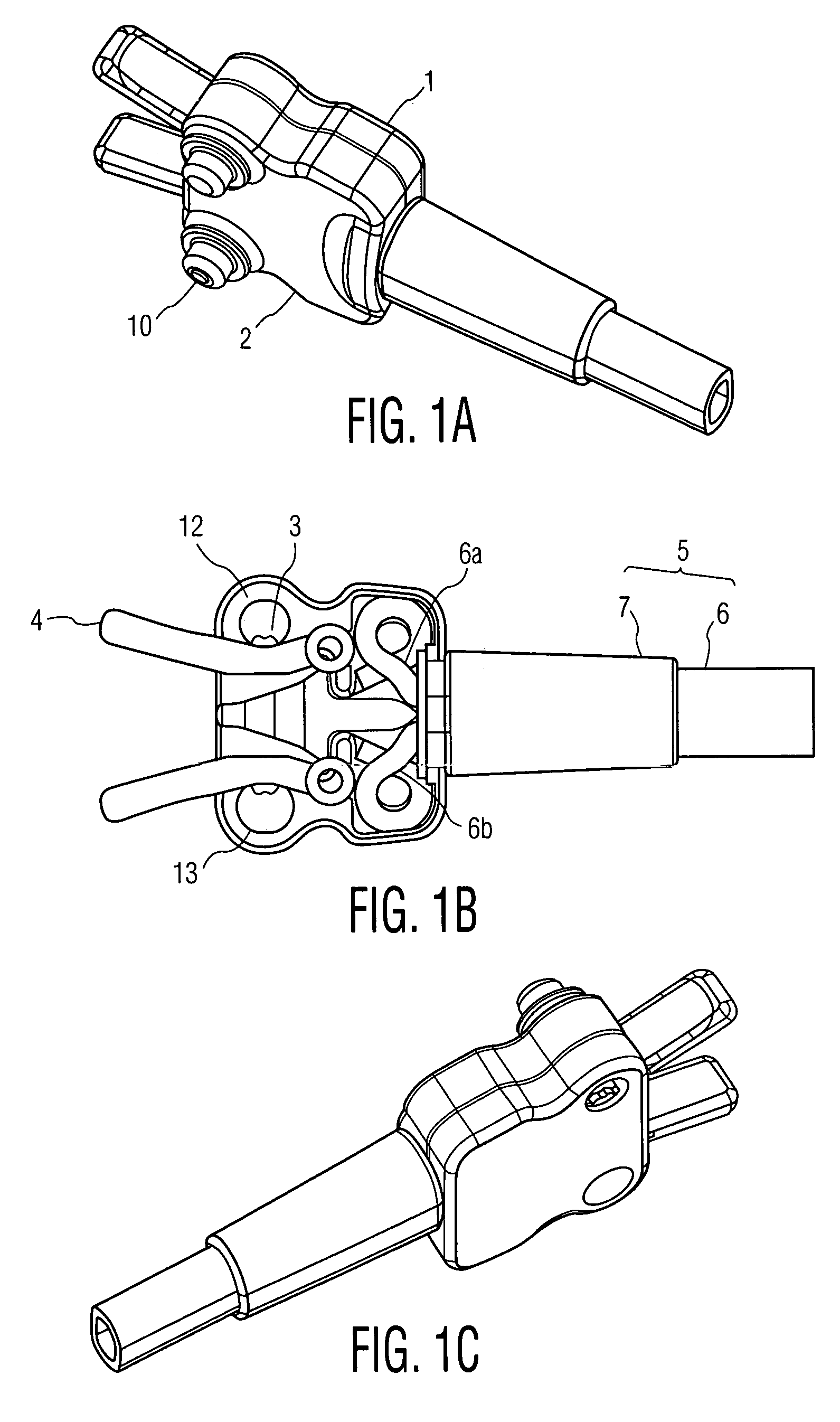
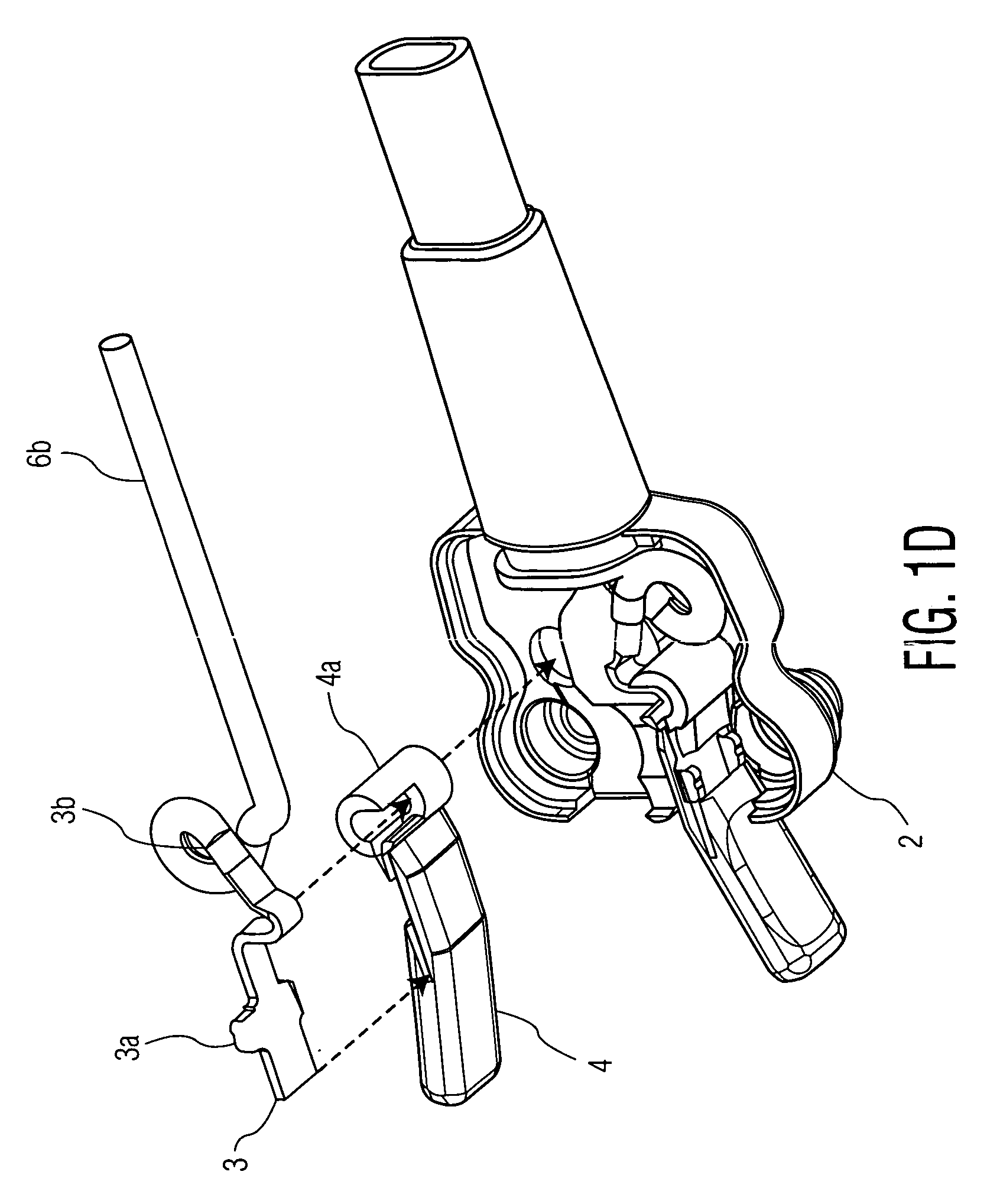
A double electrode connector for connecting to medical electrodes preferably in an impedance cardiography system includes a connector housing comprising a base having two holes therein of predetermined diameters arranged at predetermined location in the housing, with a first of the two holes associated with a first connector and a second of the two holes associated with a second connector of the double-electrode connector; a pair of biasing elements arranged along a surface of the housing so that each one of the pair of biasing elements is adapted for biasing against an electrode stud inserted in a respective hole of the two holes in the housing; a cable assembly including a twin wire cable and a bend relief, wherein each one of the pair of metal lugs is connected to one of the first connector and second connector, and the bend relief is arranged in a hole in the base to flexibly connect the twin wire cable to respective metal lugs of the pair of metal lugs. The biasing means may include handles to assist with attaching the double connector to two electrodes with a near-zero insertion force towards a patient.
Owner:KONINK PHILIPS ELECTRONICS NV
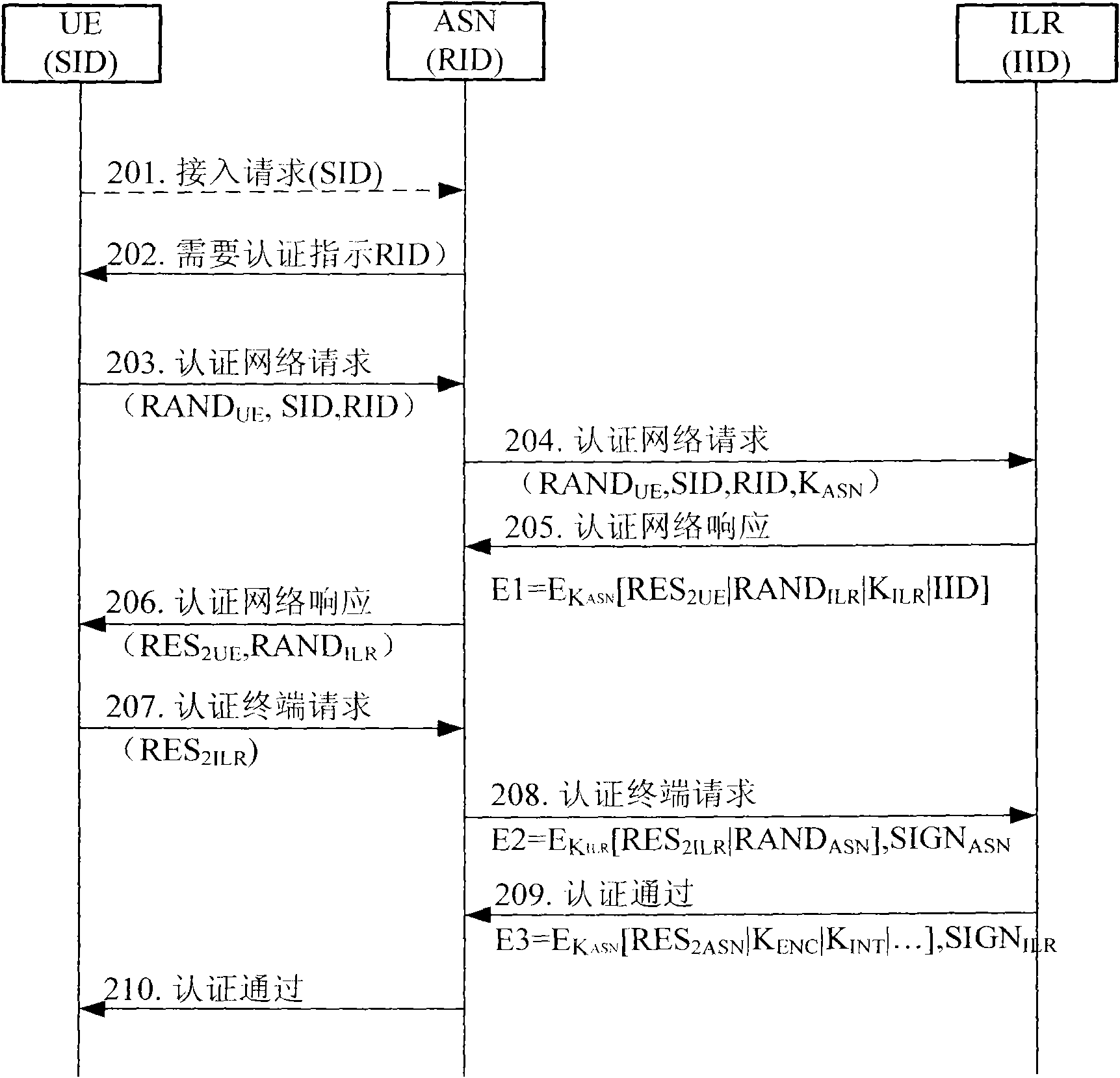
Access authentication method and system in mobile communication network
InactiveCN102036242AAvoid attackArrived without errorUser identity/authority verificationSecurity arrangementMan-in-the-middle attackDigest access authentication
The invention discloses an access authentication method in a mobile communication network. The method comprises the following steps that: a user terminal generates a random number RANDUE, and acquires a random number RANDILR generated by route identification (RID) and an identity location register (ILR) of an access service node (ASN) in a network when needing to perform authentication; the user terminal calculates to obtain an authentication result RES2ILR by using a pre-shared key K1 and sends the RES2ILR to the ASN; the ASN generates a random number RANDASN and sends the RES2ILR and the random number RANDASN to the ILR; and the ILR calculates to obtain an authentication result XRES2ILR by using the pre-shared key K1 and compares the XRES2ILR with the received RES2ILR; and if the XRES2ILR is consistent with the RES2ILR, the access authentication is successful. Correspondingly, the invention also provides a system for implementing the method. Through the method and the system, Man-in-the-Middle attacks caused by an unreliable network can be effectively avoided.
Owner:ZTE CORP
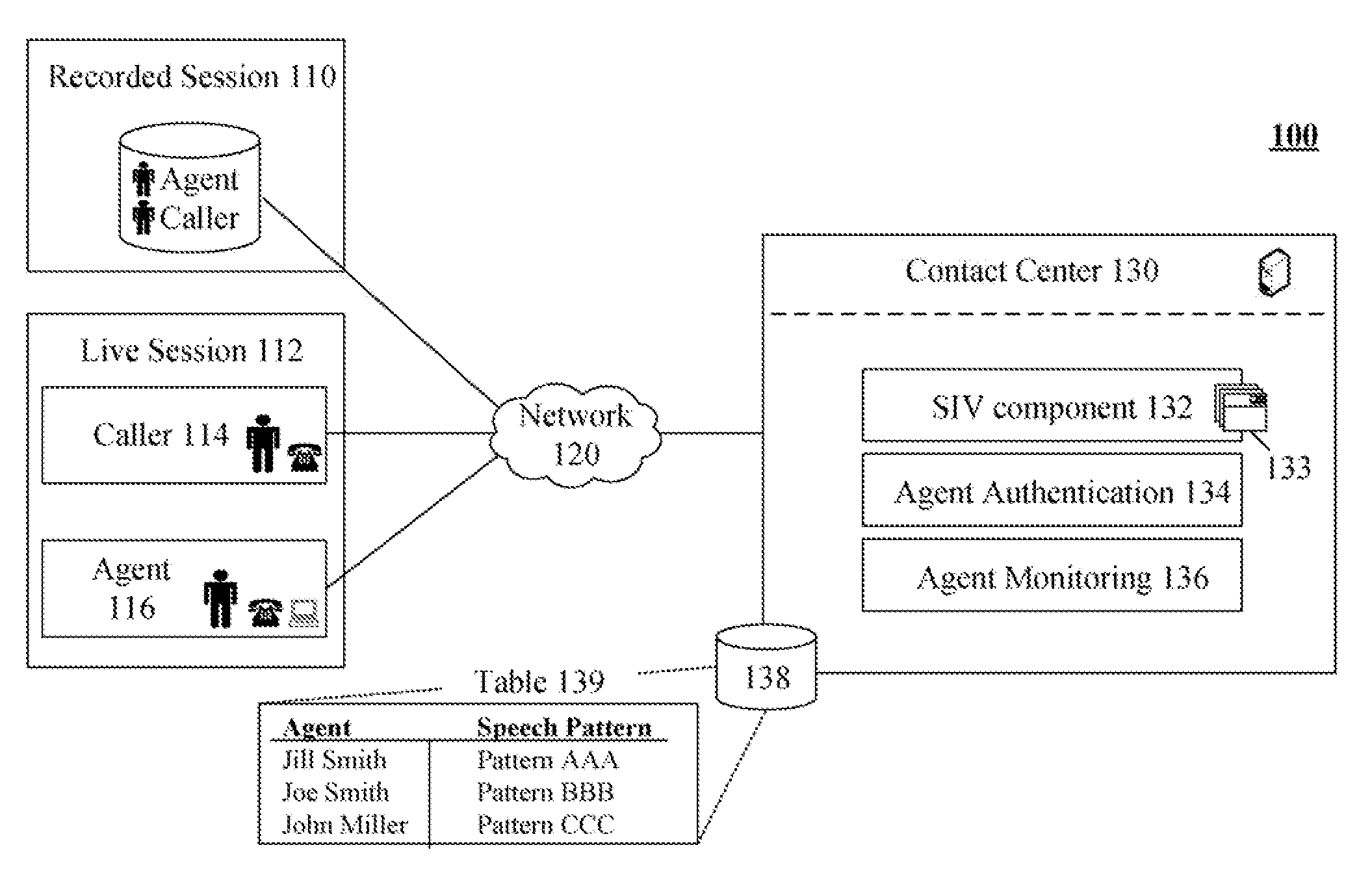
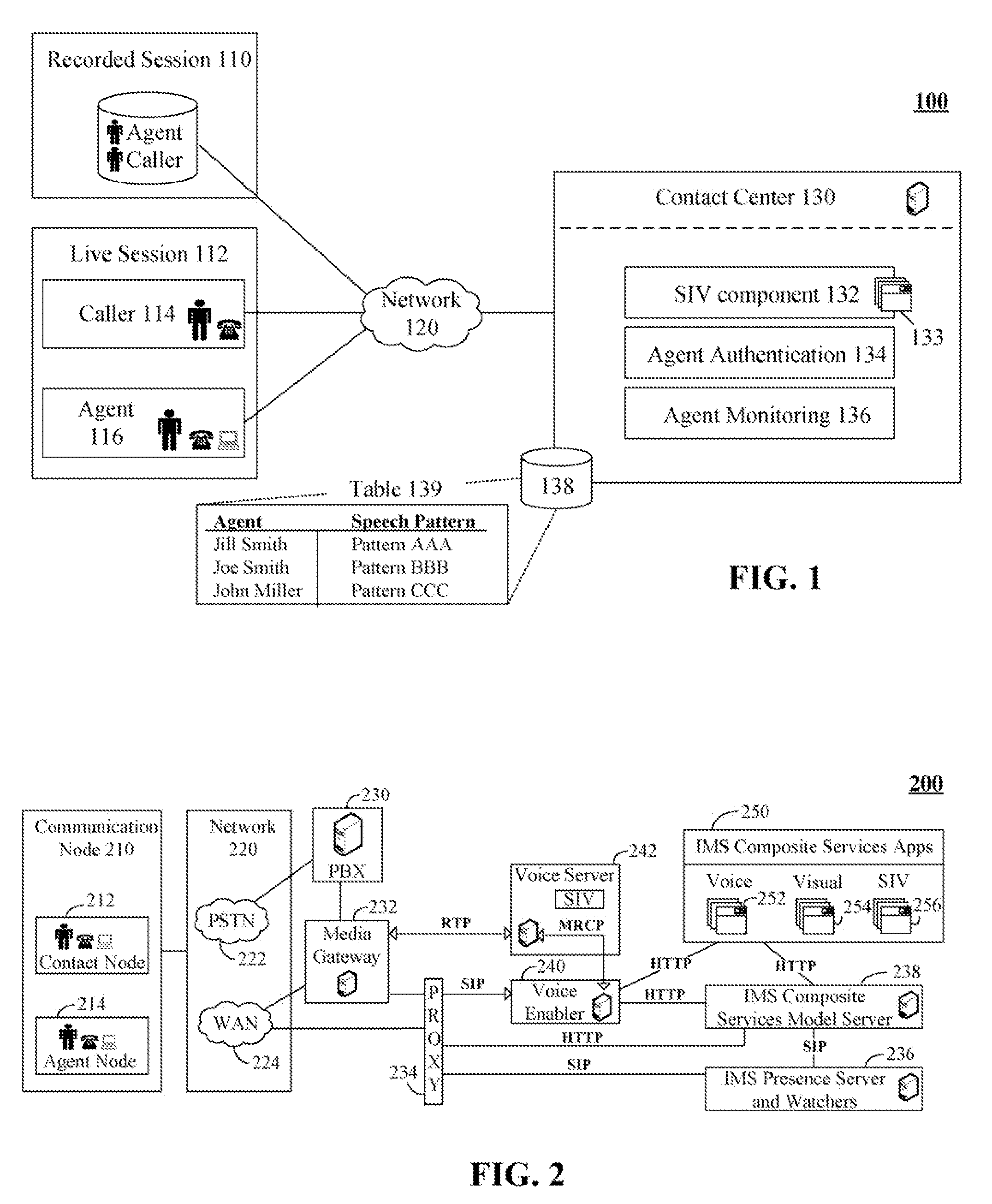
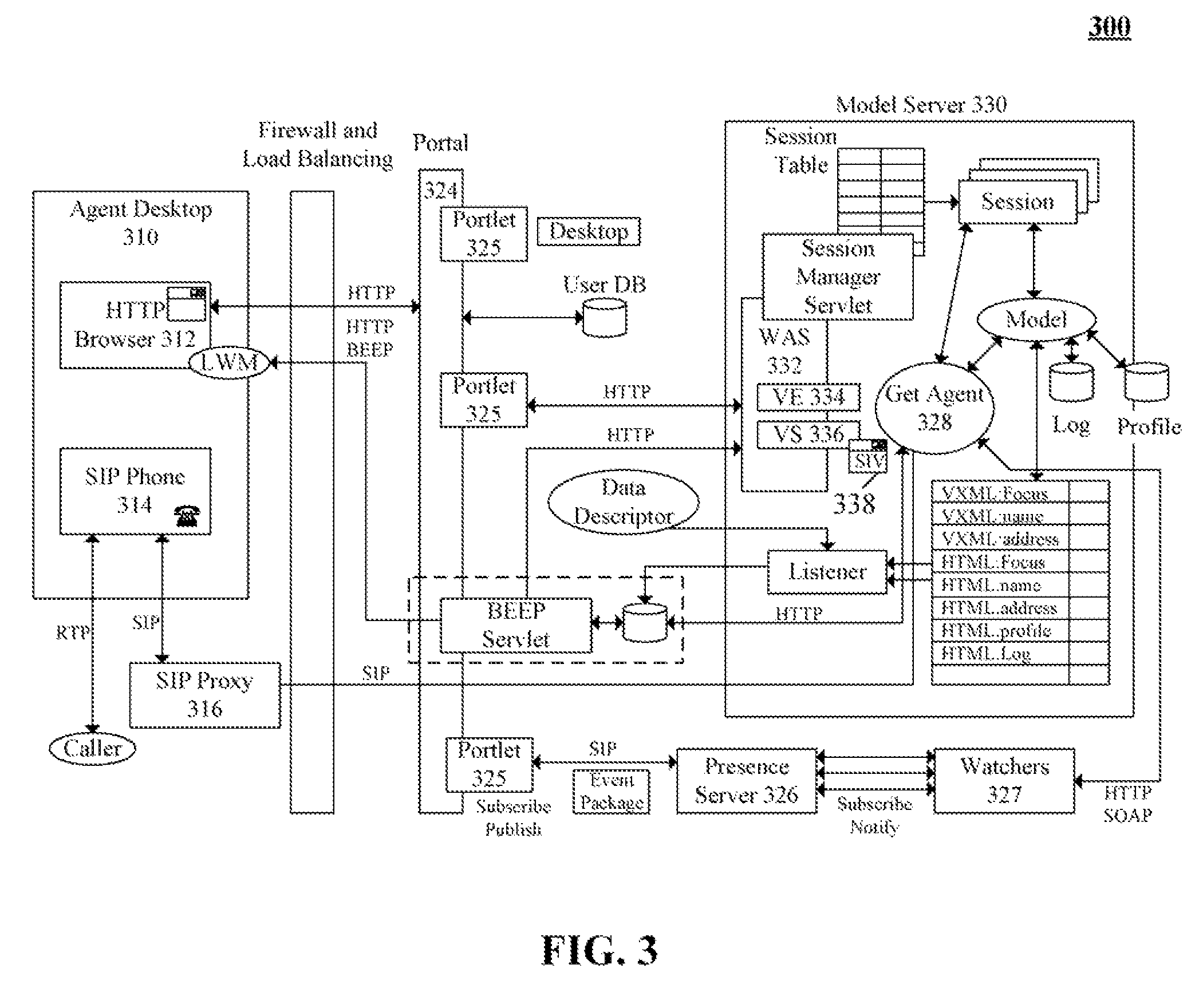
Identifying contact center agents based upon biometric characteristics of an agent's speech
ActiveUS20080205624A1Improve recognition accuracyAvoid substitutionSpecial service for subscribersManual exchangesContact centerSpeech sound
The present invention discloses a contact center with speaker identification and verification (SIV) capabilities. In the invention, a set of contact center components can provide automated interactive communications with callers, can provide queue management for callers waiting to communicate with live agents, and can provide skills based routing for assigning live agents to callers. The SIV component can analyze speech utterances to determine a speaker identify based upon biometric characteristics of the analyzed speech utterances. Additionally, the SIV component can process speech from contact center sessions. In one embodiment, the SIV component can prevent agent substitutions from occurring of which the call center is unaware. The SIV component can also be used to distinguish whether communication session content was spoken by a contact center agent or a caller.
Owner:IBM CORP
Operation and maintenance safety auditing method and system
InactiveCN106330919AAvoid substitutionGuarantee authenticityCharacter and pattern recognitionTransmissionCorrelation analysisComputer science
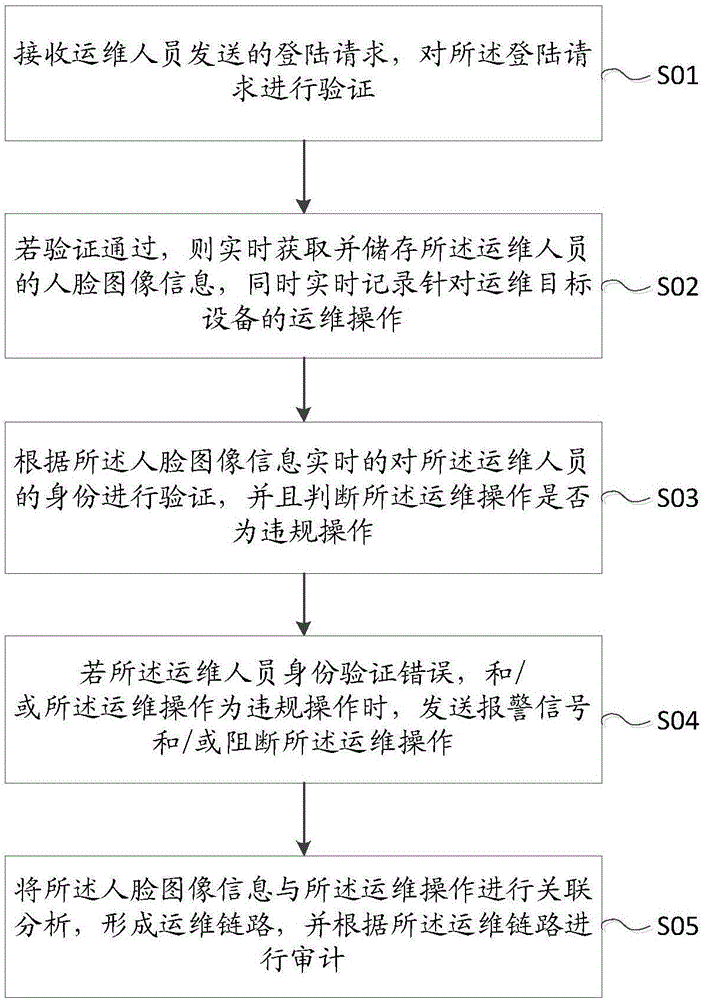
The invention discloses an operation and maintenance safety auditing method. The operation and maintenance safety auditing method comprises the following steps: receiving a login request sent by operation and maintenance personnel, and verifying the login request; if the verification is passed, obtaining and storing face image information of the operation and maintenance personnel in real time, and meanwhile recording an operation and maintenance operation on operation and maintenance target equipment in real time; verifying the identity of the operation and maintenance personnel in real time according to the face image information, and judging whether the operation and maintenance operation is an illegal operation; if the verification of the identity of the operation and maintenance personnel is wrong, and / or the operation and maintenance operation is the illegal operation, sending an alarm signal and / or interrupting the operation and maintenance operation; and carrying out correlation analysis on the face image information and the operation and maintenance operation, forming an operation and maintenance link, and carrying out audit according to the operation and maintenance link. Identity authentication can be carried out on the identity of the IT operation and maintenance personnel in an operation and maintenance personnel process, and the illegal operation and maintenance operation can be found in time. The invention further discloses an operation and maintenance safety auditing system.
Owner:STATE GRID CORP OF CHINA +2
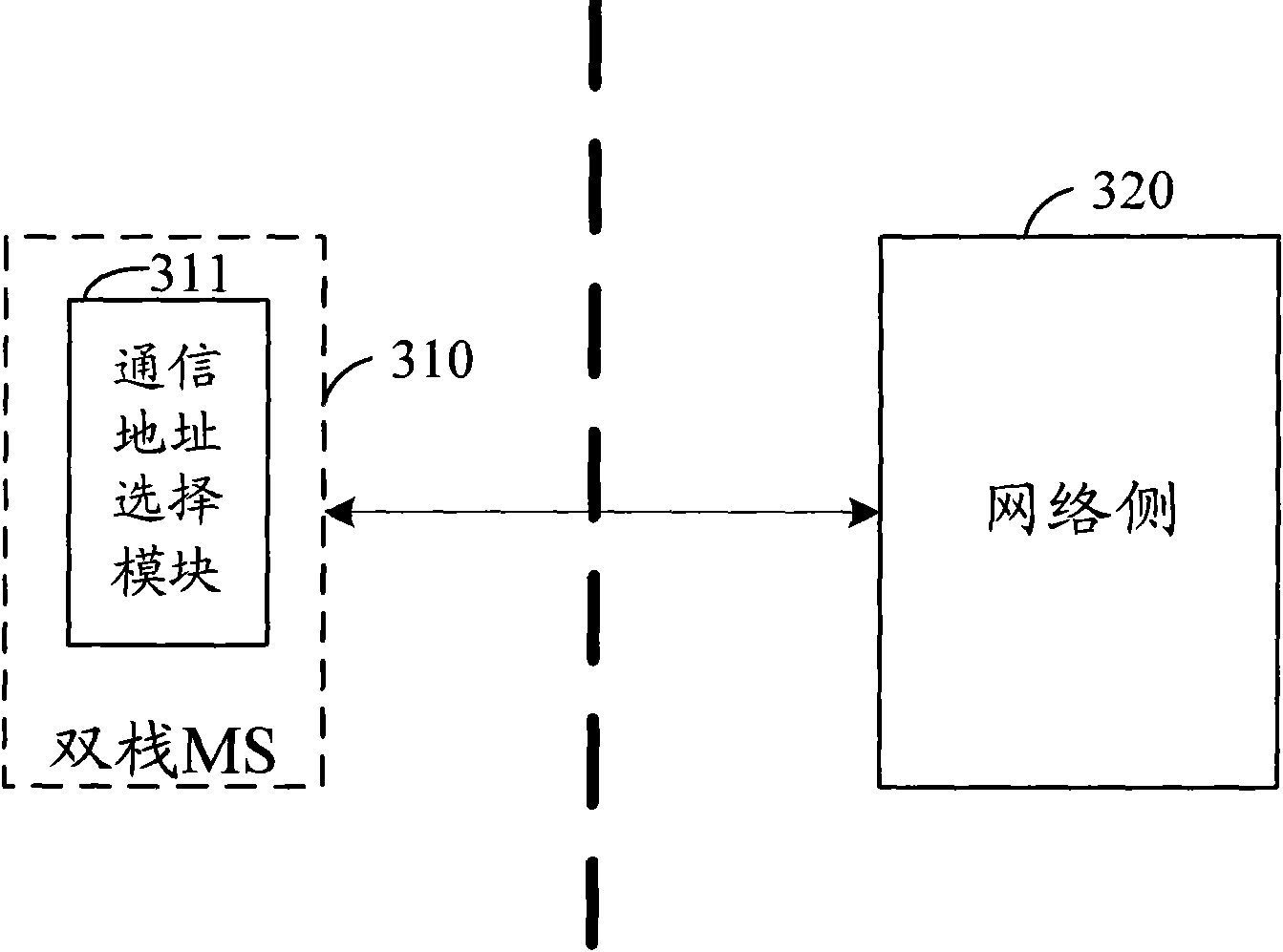
Method and system for accessing addresses, mobile terminal and application method thereof
InactiveCN101997934AAvoid overwritingAvoid substitutionTransmissionBiological activationDistributed computing
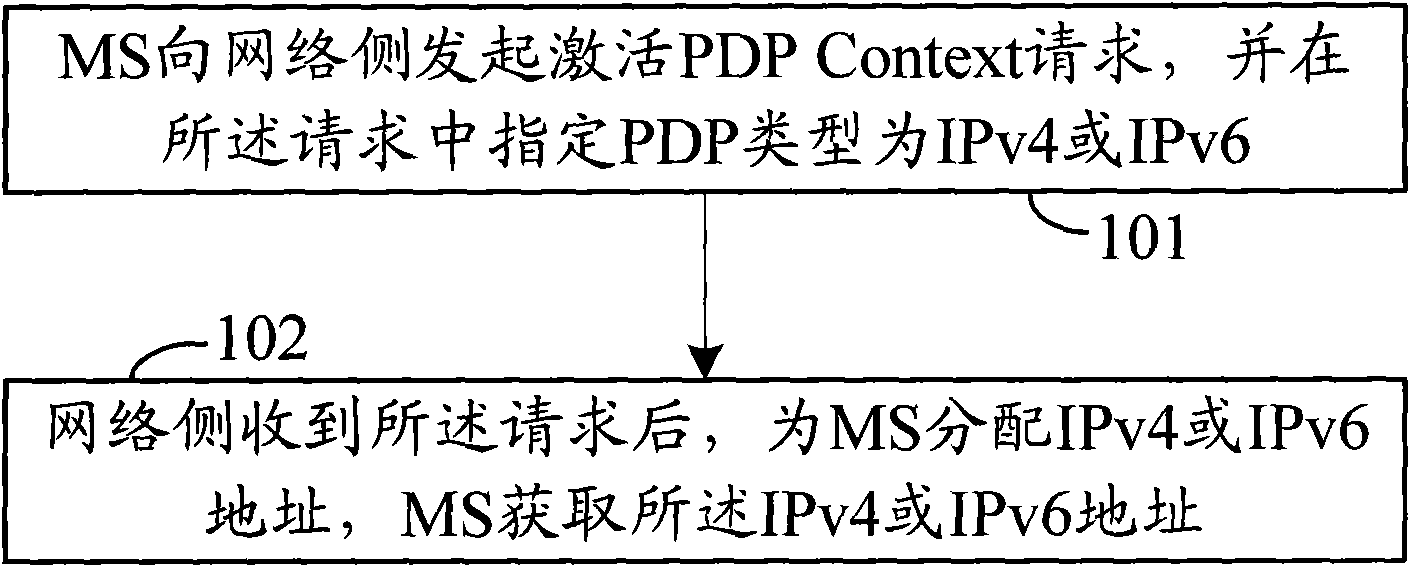
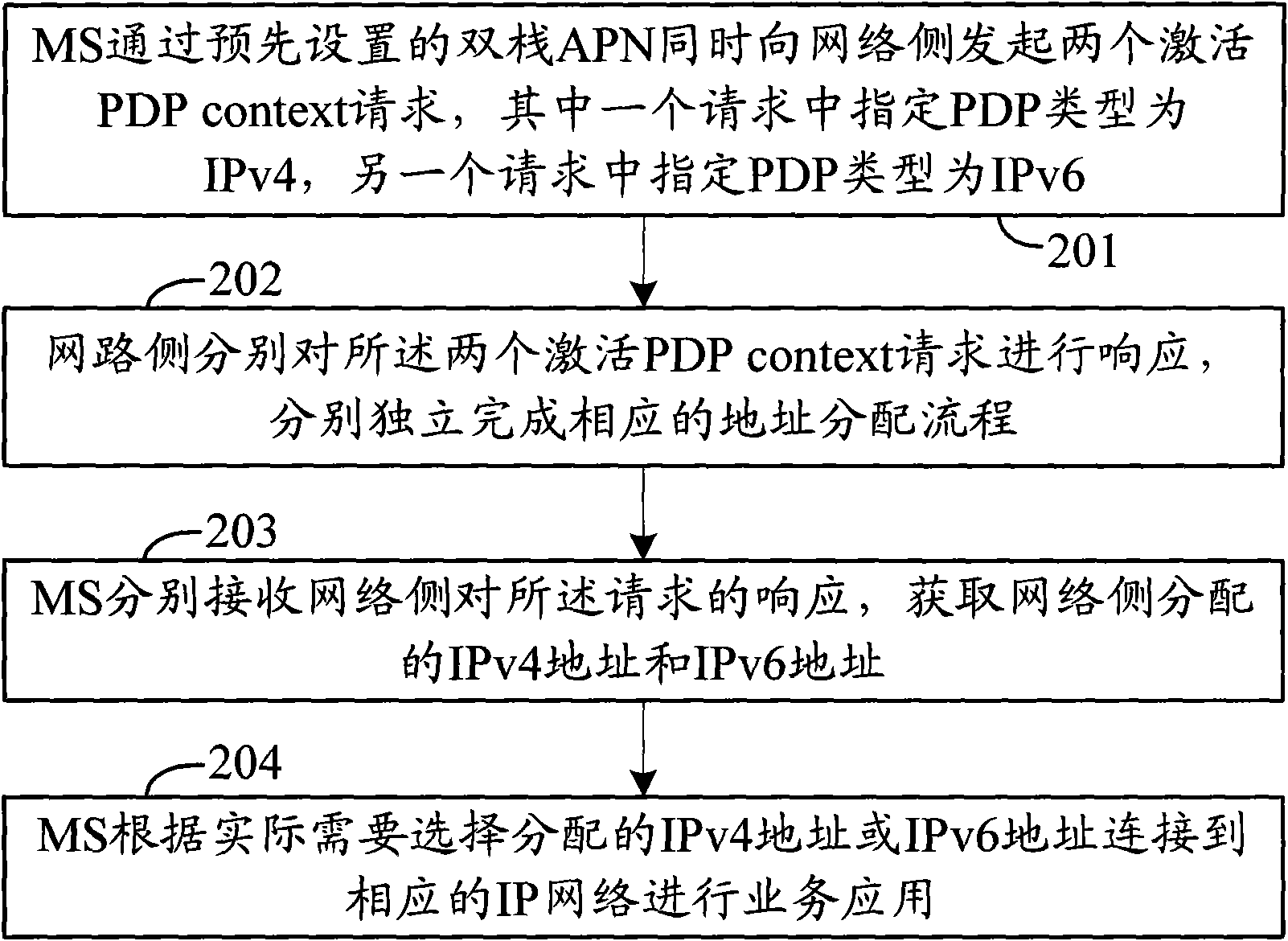
The invention discloses a method for accessing addresses, comprising the following steps: a mobile terminal (MS) simultaneously launches two activation packet data protocol (PDP) context requests to a network side through a preset dual-stack access point name (APN) in advance, wherein the PDP type specified in one request is IPv4, and the PDP type specified in the other request is IPv6; the network side respectively responds to the two activation PDP context requests to finish the address allocation flows corresponding to the requests; and the MS receives the responses of the network side to the requests to access the an IPv4 address and an IPv6 address allocated by the network side. The invention also provides the MS and an application method thereof. According to the method and system for accessing addresses in the embodiment of the invention, two activation PDP context requests are simultaneously launched to the network side, and the network side respectively responds to the two activation PDP context requests to finish the address allocation flows, thereby simultaneously accessing the IPv4 address and the IPv6 address.
Owner:CHINA MOBILE COMM GRP CO LTD
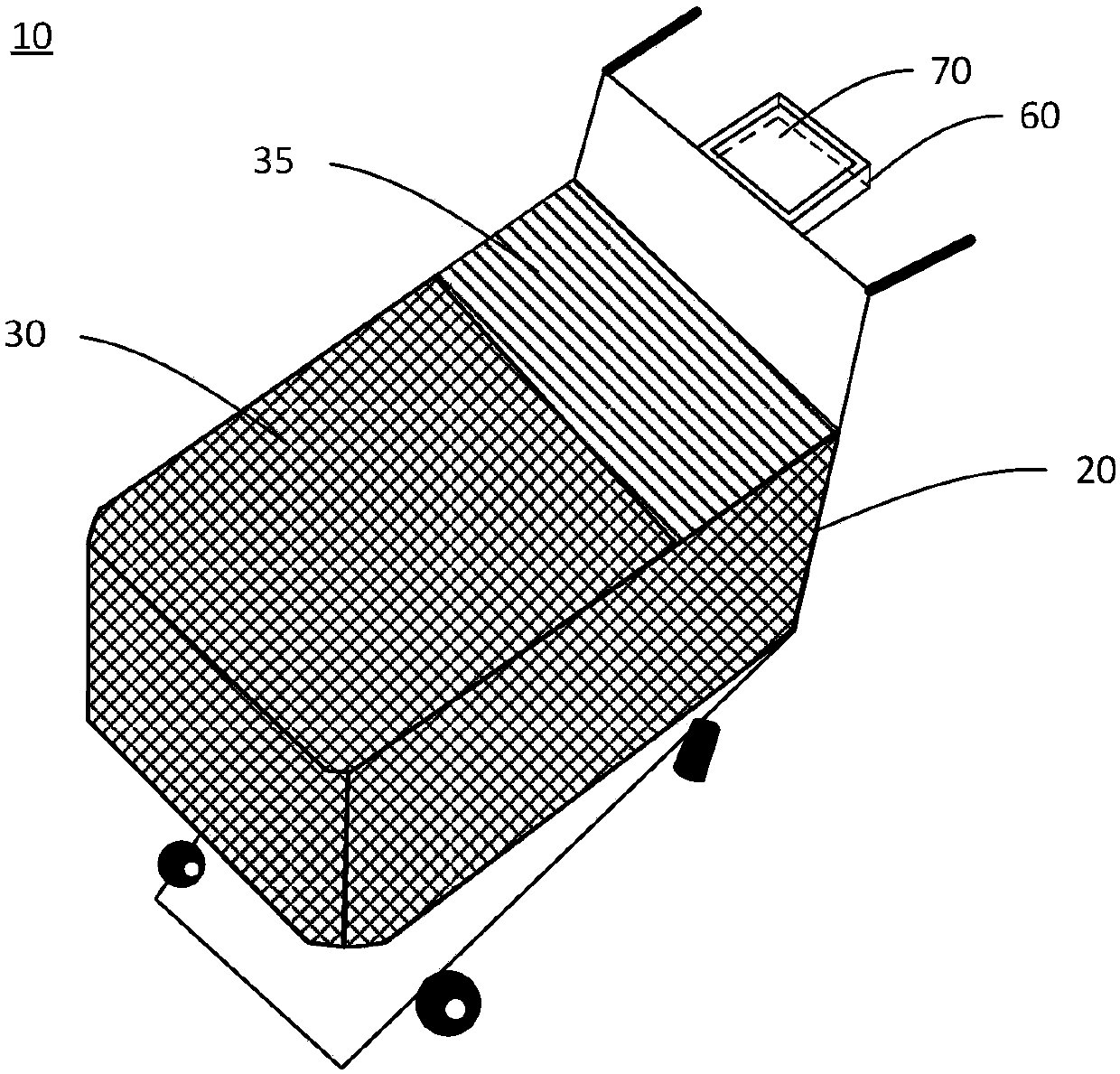
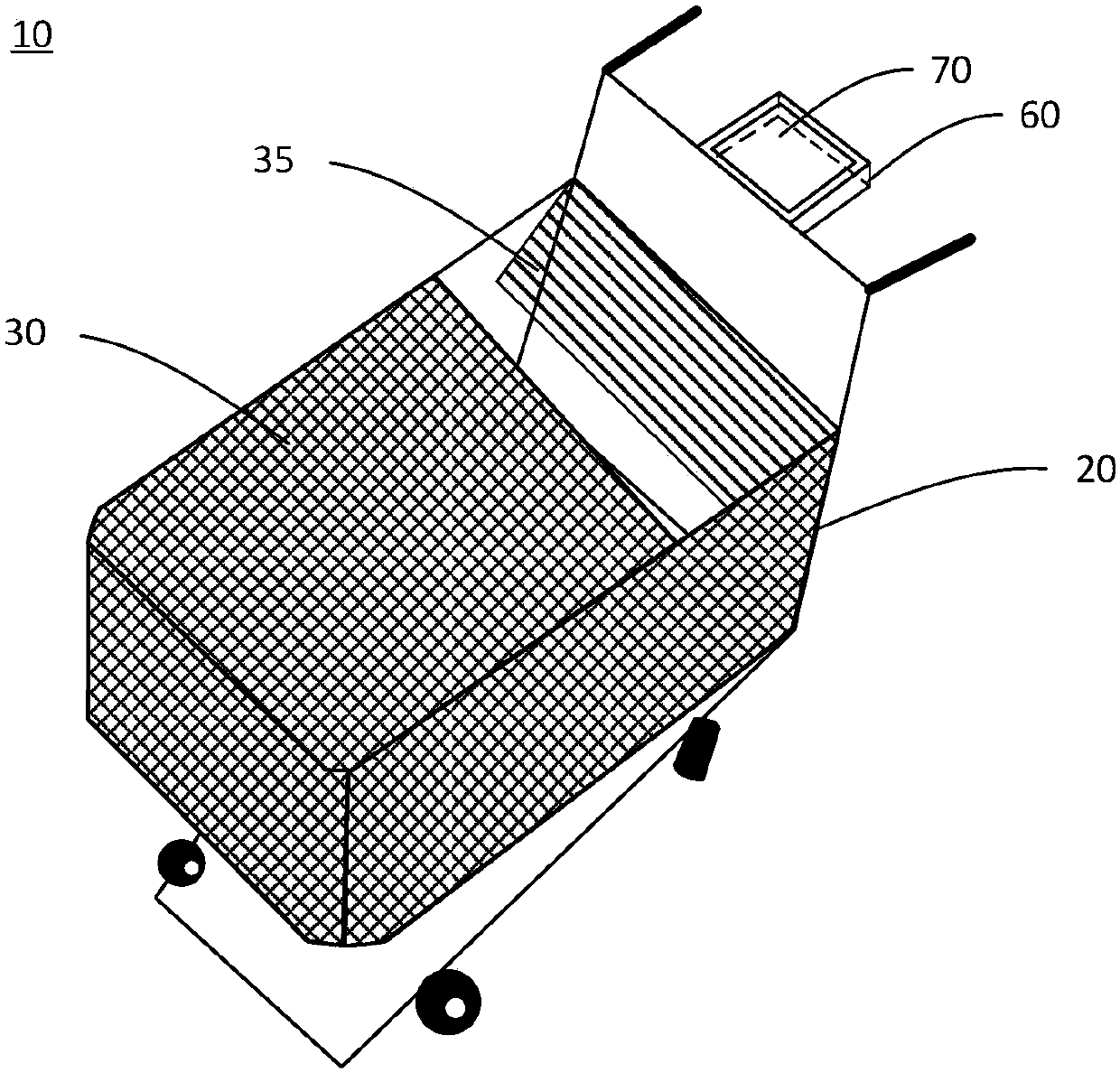
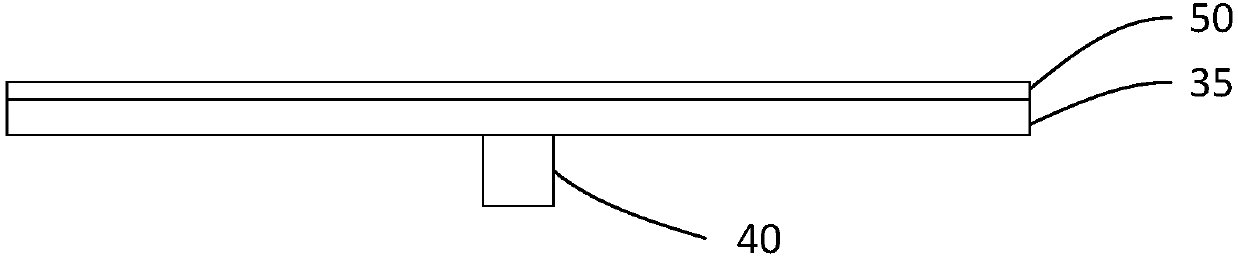
Intelligent shopping cart and intelligent shopping system including same
ActiveCN107767129ARealize autonomous settlementAvoid substitutionSupporting partsCo-operative working arrangementsShopping basketBarcode
The invention discloses an intelligent shopping cart. The shopping cart includes a body and a shopping basket arranged in the body. A cover plate which can be tilted to the inside of the shopping basket to form a commodity entrance is arranged on the shopping basket. The shopping cart also includes a scanning unit, which scans a barcode of a commodity placed on the cover plate, and acquires a nameand a unit price of the commodity; a first weighing unit, which measures weight of the commodity on the cover plate; a settlement unit, which generates settlement information of the commodity on thebasis of the name and the unit price of the commodity, adds the same to a settlement list, and updates the settlement list; and a display unit, which displays the settlement list. The invention also discloses an intelligent shopping system including the above-mentioned shopping cart. According to the system, voluntary settlement is carried out through the shopping cart, a settlement speed is increased, and accuracy of a settlement process is guaranteed.
Owner:BOE TECH GRP CO LTD
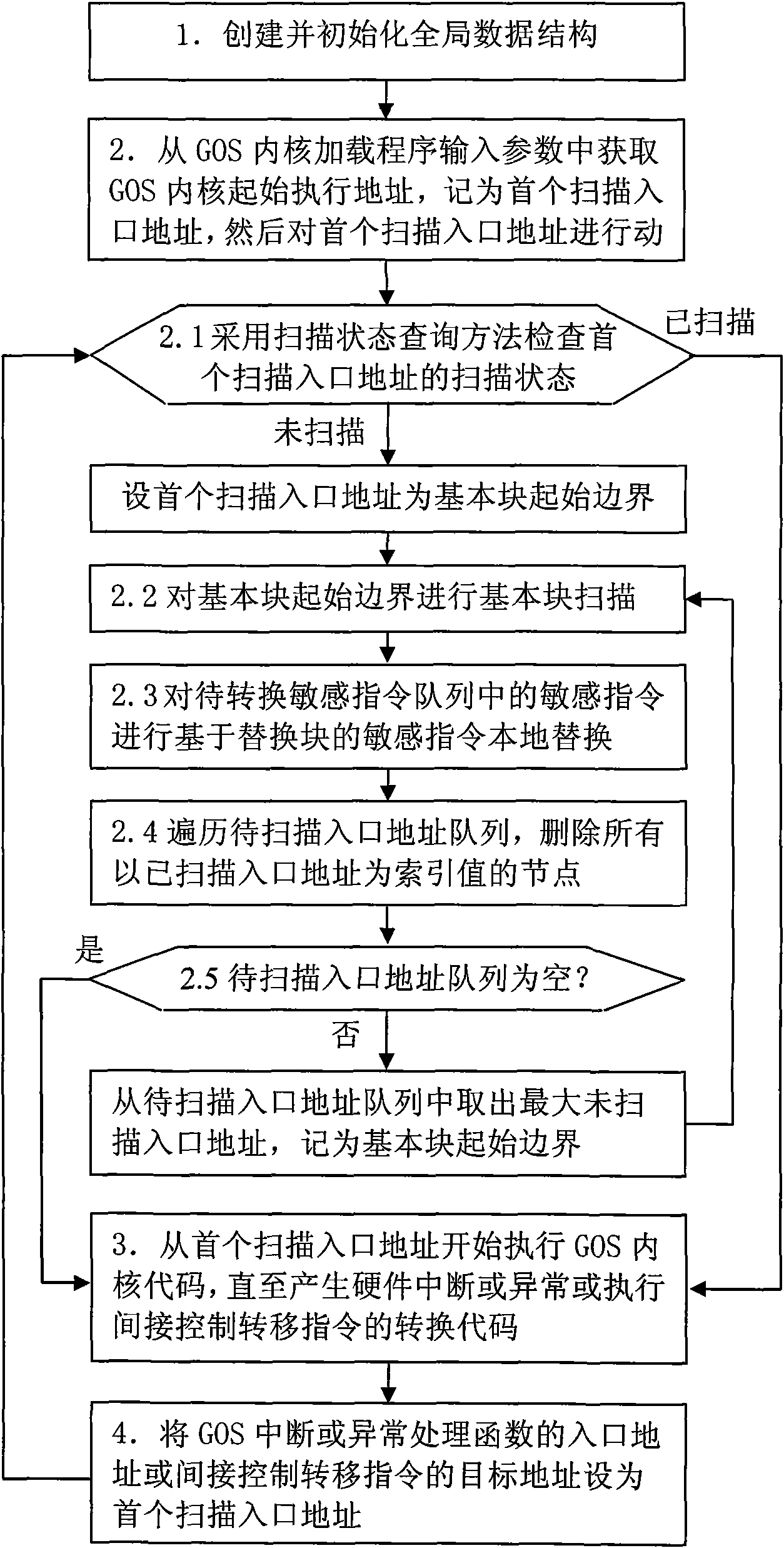
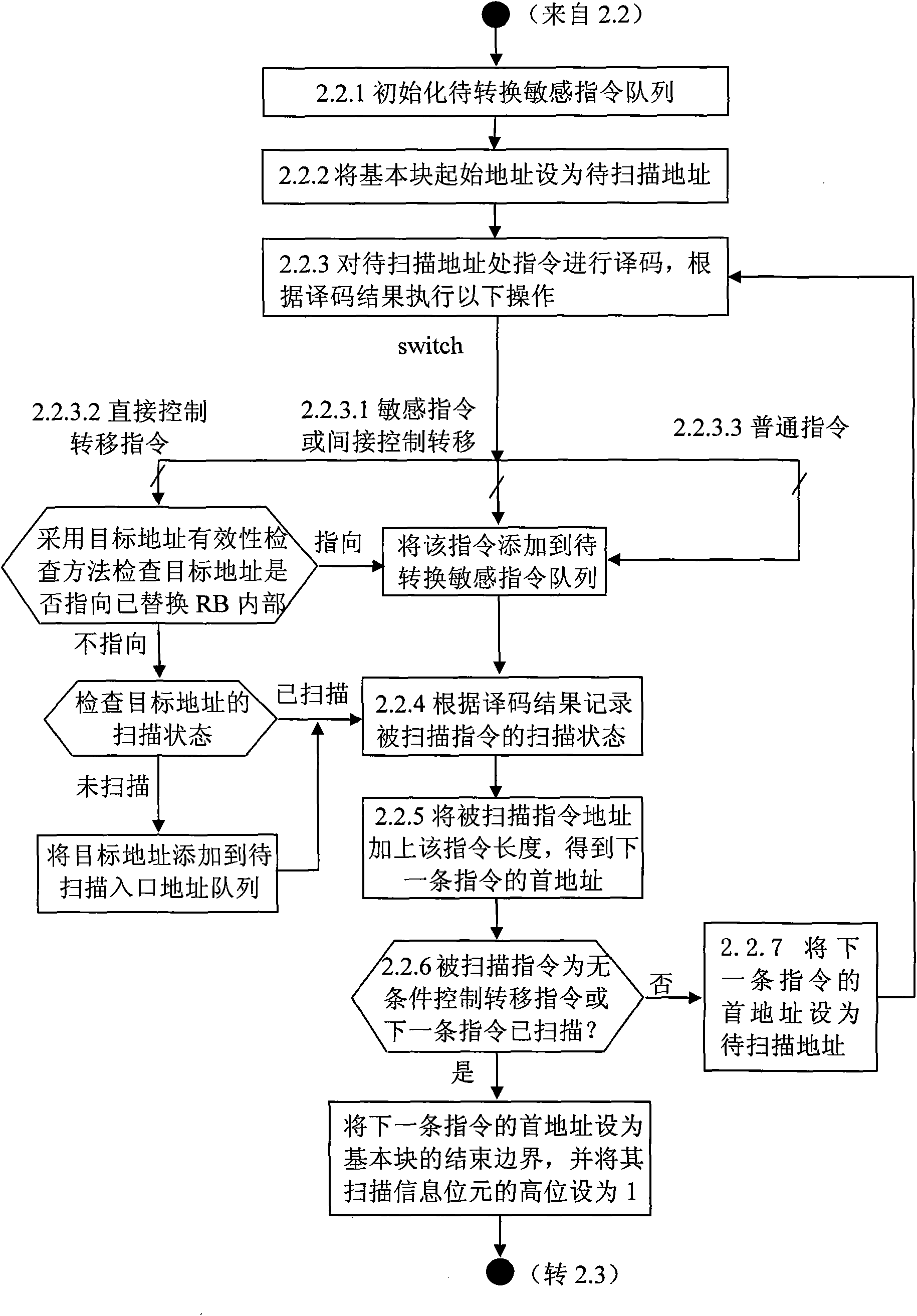
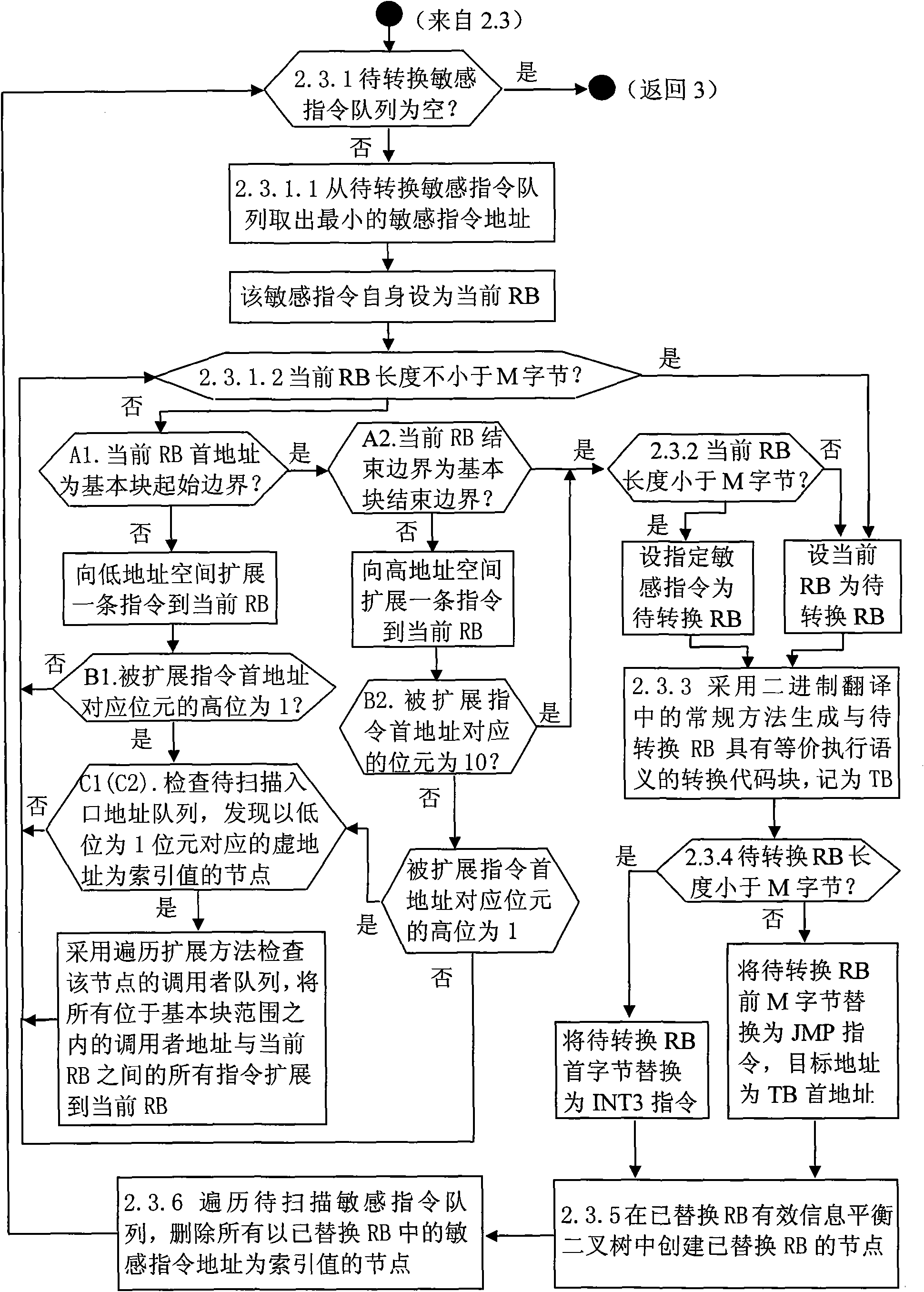
Block-based method for scanning object code and replacing sensitive instruction
InactiveCN101630269AAvoid substitutionImprove virtualization performanceSoftware simulation/interpretation/emulationSpecial data processing applicationsVirtualizationObject code
The invention discloses a block-based method for scanning object code and replacing sensitive instruction, aiming to provide a method of searching a minimum object code block which contains an sensitive instruction and is longer than JMP and using JMP to replace the minimum object code block when the sensitive instruction is shorter than JMP. The invention has the technical scheme that the method carries out dynamic scanning to a first scanning entry, wherein, the dynamic scanning mainly comprises basic block scanning for the initial boundary of a basic block and local sensitive instruction replacement for the sensitive instruction in a sensitive instruction queue to be transformed; the method executes GOS kernel code from the first scanning entry address until hardware interrupt or abnormal phenomena happens, or transforming code of an indirect control and transform instruction is executed; the entry address for GOS interrupt and abnormal exception handler or the destination address for indirectly controlling and transmitting instructions can be set as the first scanning entry address to circularly carry out the dynamic scanning. By adopting the block-based method, using INT0 / INT3 instruction for replacement can be avoided to the maximum extent, and the BT virtualization performance can be effectively improved.
Owner:NAT UNIV OF DEFENSE TECH
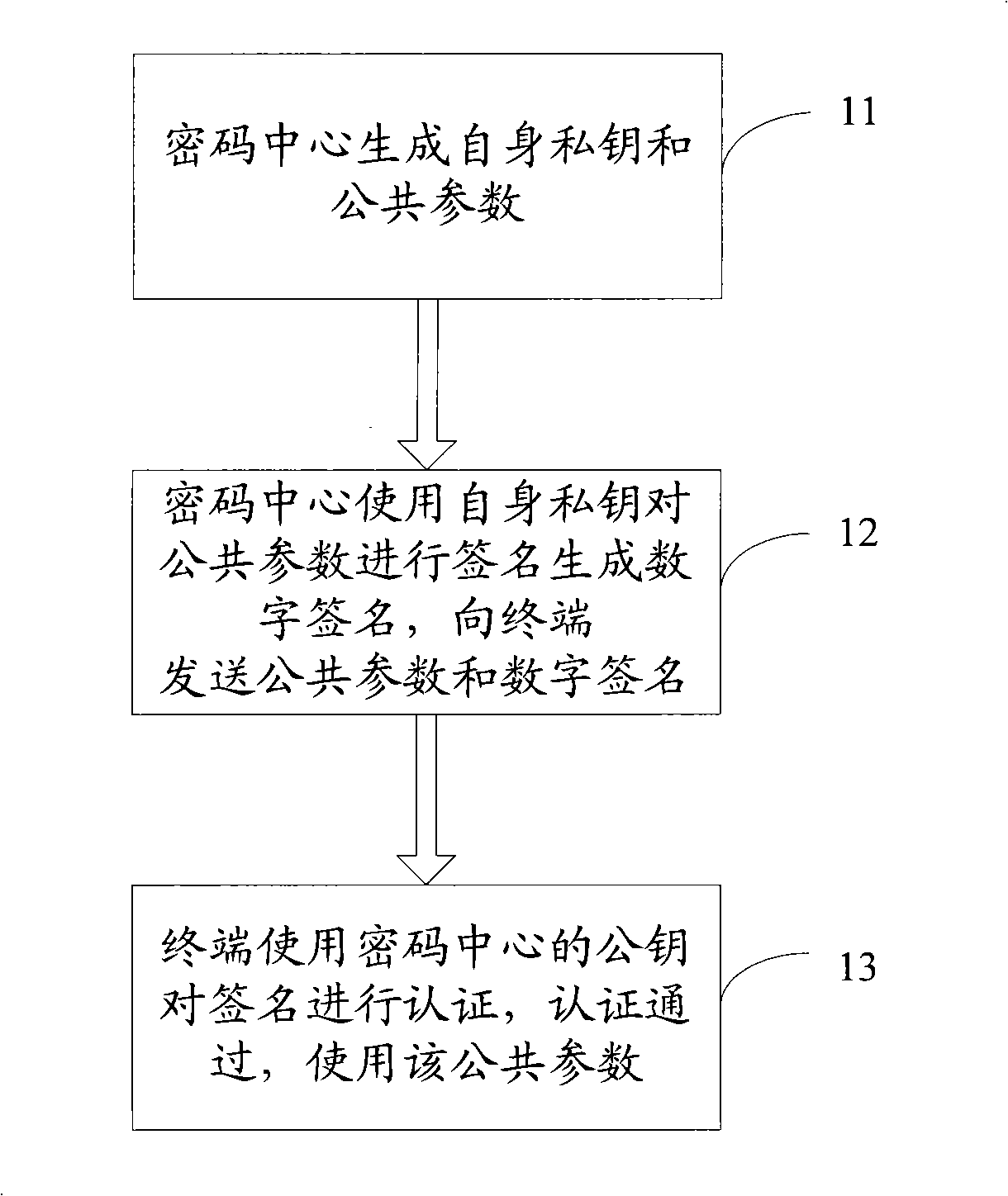
Enciphered data transmission method and system
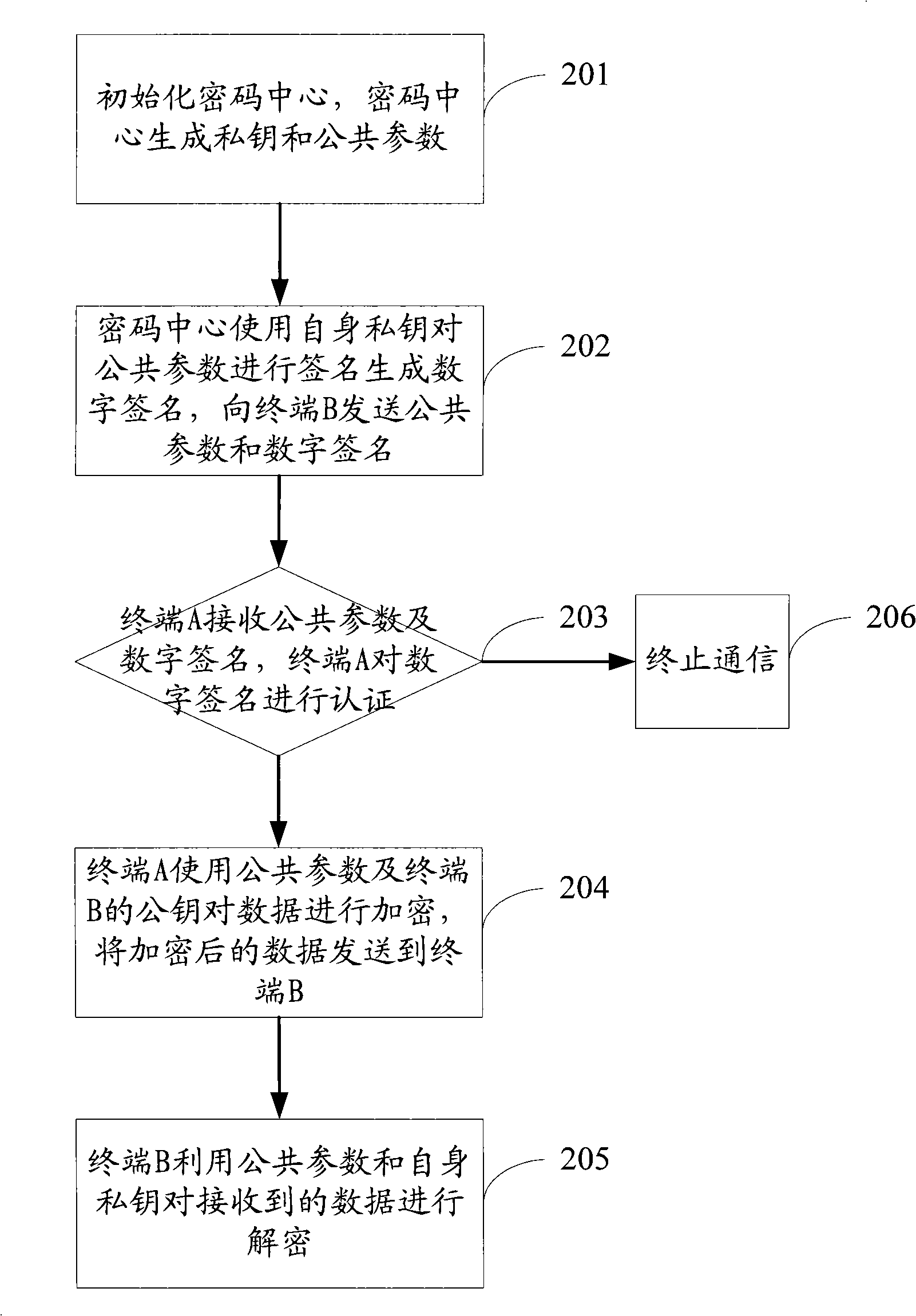
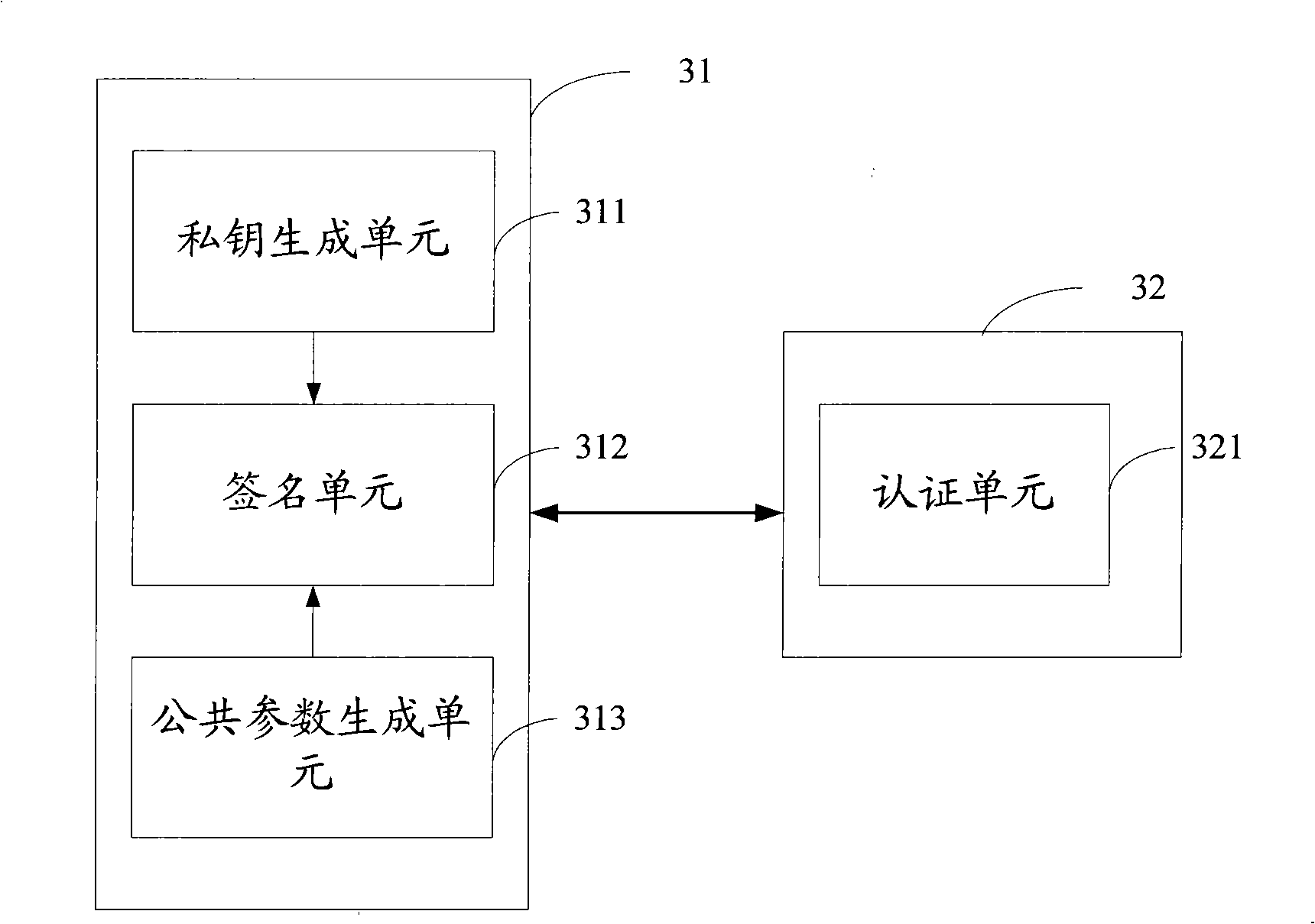
InactiveCN101296083AGuaranteed sourceIntegrity guaranteedKey distribution for secure communicationUser identity/authority verificationDigital signaturePassword
The invention discloses a method for transmitting encrypted data, which comprises the following steps of: receiving common parameters and digital signatures and authenticating the digital signatures, wherein, the common parameters are generated by a password center and the digital signatures are generated by signing the common parameters by the password center using a private key thereof; the common parameters are used for encrypting and transmitting the data needing to be transmitted after passing through the authentication. The method of the embodiment of the invention can guarantee the sources and completeness of the common parameters, prevent an attacker from replacing and amending the common parameters, and enhance the security of the transmitting of the common parameters by signing the common parameters.
Owner:HUAWEI TECH CO LTD
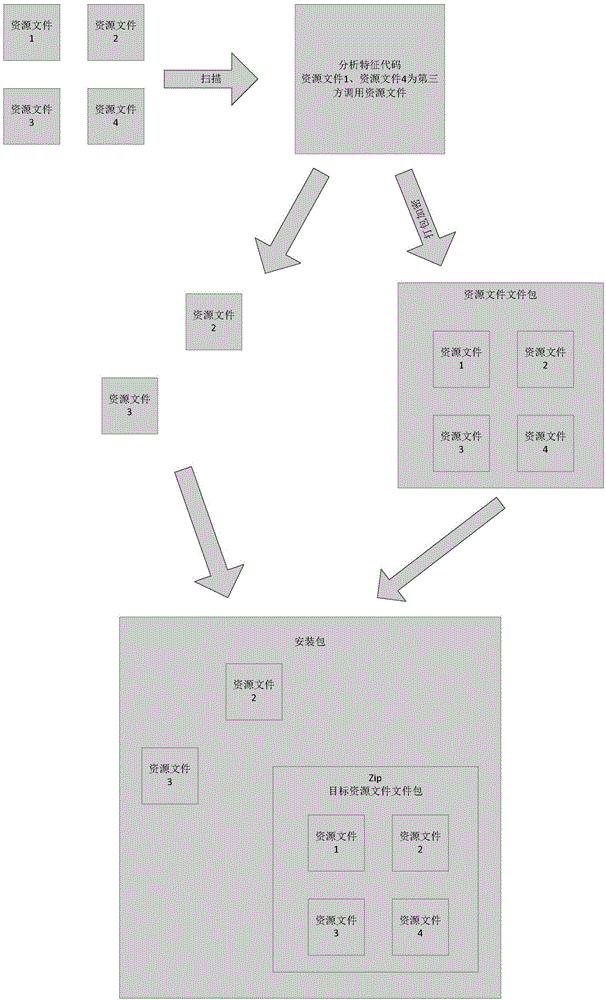
Resource file processing method, apparatus and system
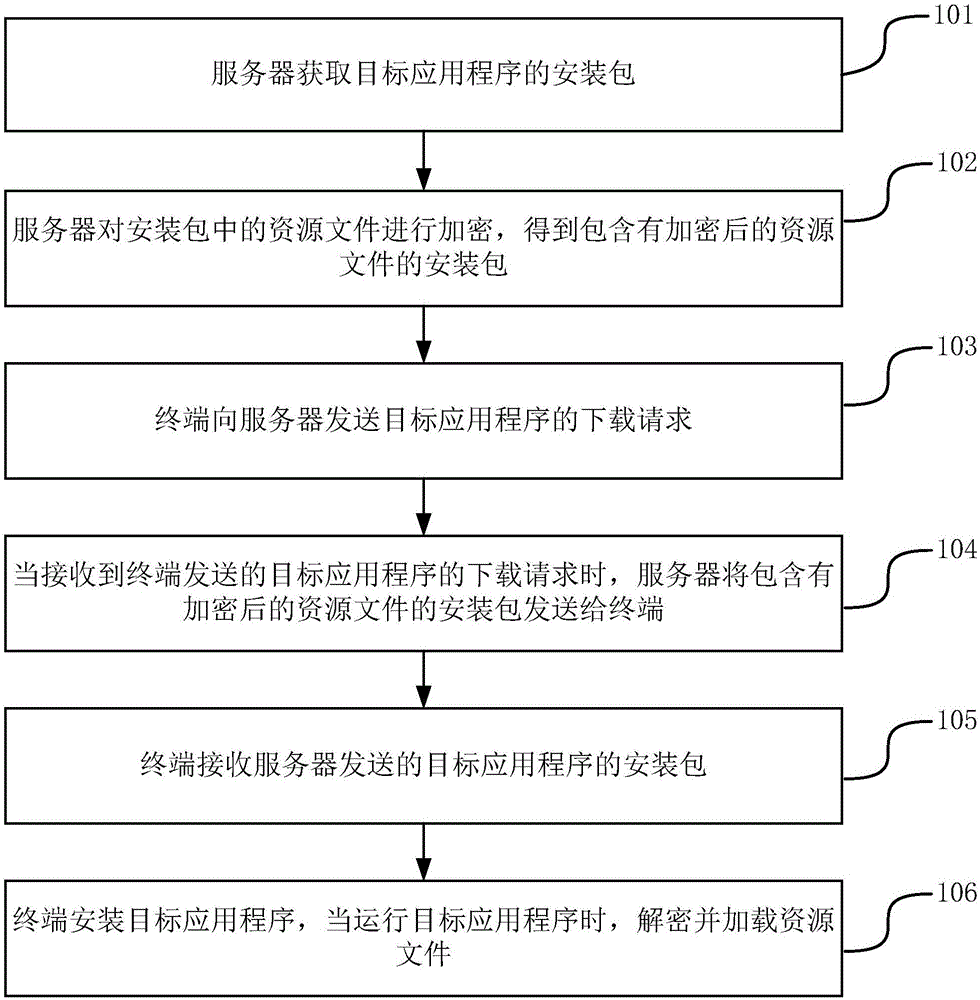
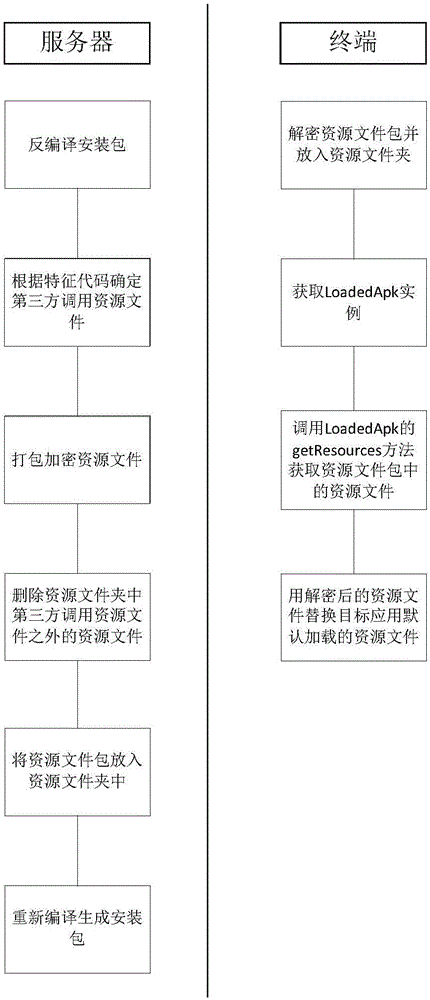
ActiveCN106598584APrevent modification or substitutionImprove securityProgram documentationProgram loading/initiatingApplication softwareApplication security
The invention discloses a resource file processing method, apparatus and system, and belongs to the technical field of computers. The method comprises the steps of obtaining an installation package of a target application; encrypting resource files in the installation package to obtain an installation package containing the encrypted resource files; and when a downloading request used for the target application and sent by a terminal is received, sending the installation package containing the encrypted resource files to the terminal. By adopting the method, the apparatus and the system, the application security can be improved.
Owner:GUANGZHOU HUADUO NETWORK TECH
Double connector for medical sensor
InactiveUS20060068649A1Firmly connectedReduce in quantityElectrocardiographyCoupling device detailsCardiography impedanceMedical treatment
A double electrode connector for connecting to medical electrodes preferably in an impedance cardiography system includes a connector housing comprising a base having two holes therein of predetermined diameters arranged at predetermined location in the housing, with a first of the two holes associated with a first connector and a second of the two holes associated with a second connector of the double-electrode connector; a pair of biasing elements arranged along a surface of the housing so that each one of the pair of biasing elements is adapted for biasing against an electrode stud inserted in a respective hole of the two holes in the housing; a cable assembly including a twin wire cable and a bend relief, wherein each one of the pair of metal lugs is connected to one of the first connector and second connector, and the bend relief is arranged in a hole in the base to flexibly connect the twin wire cable to respective metal lugs of the pair of metal lugs. The biasing means may include handles to assist with attaching the double connector to two electrodes with a near-zero insertion force towards a patient.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Team organizing video method, device and system used in team organizing game
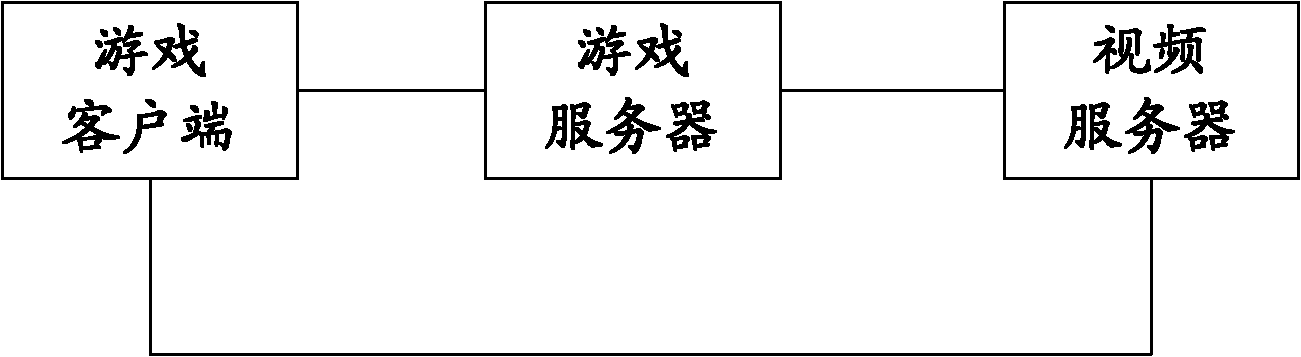
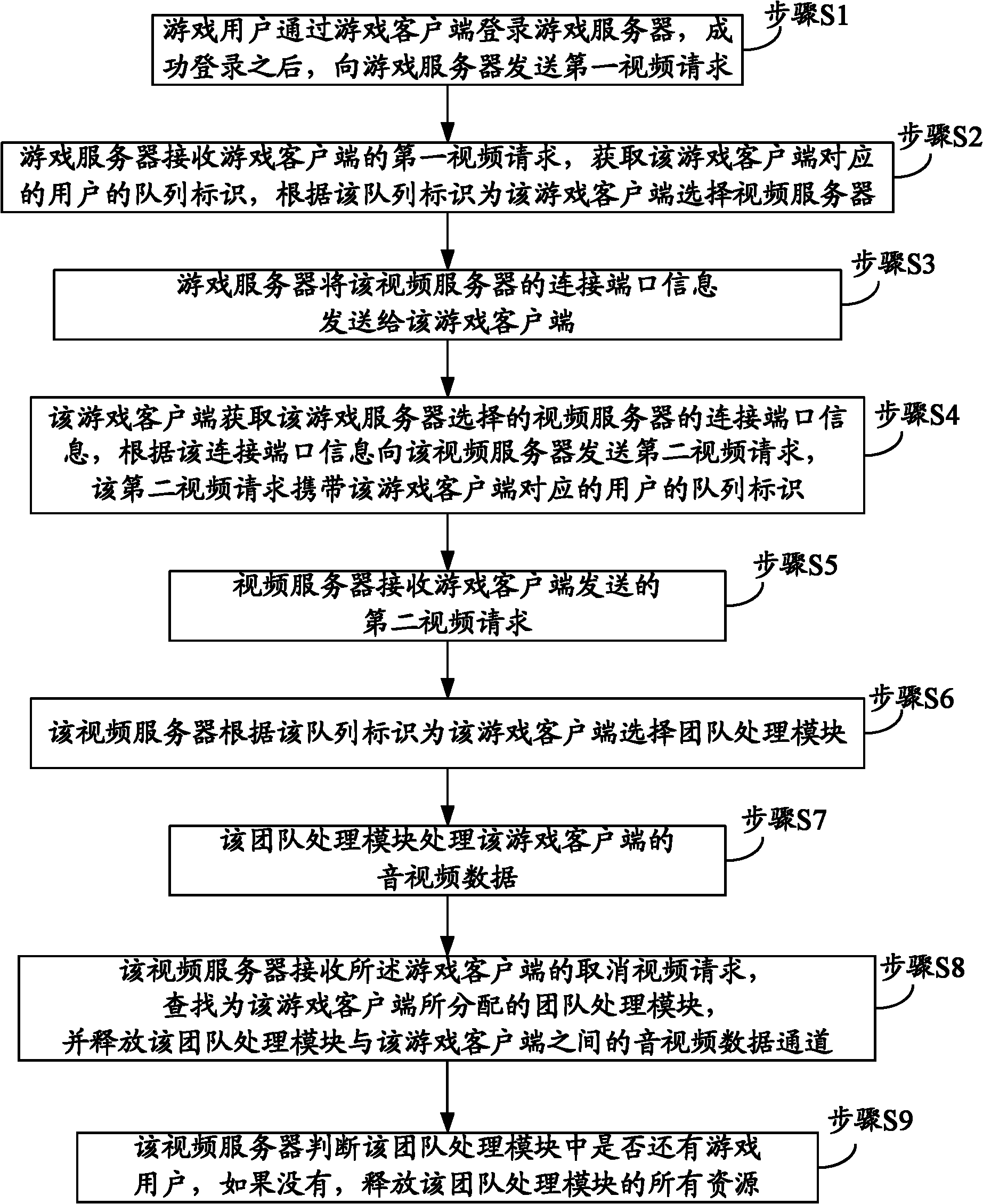
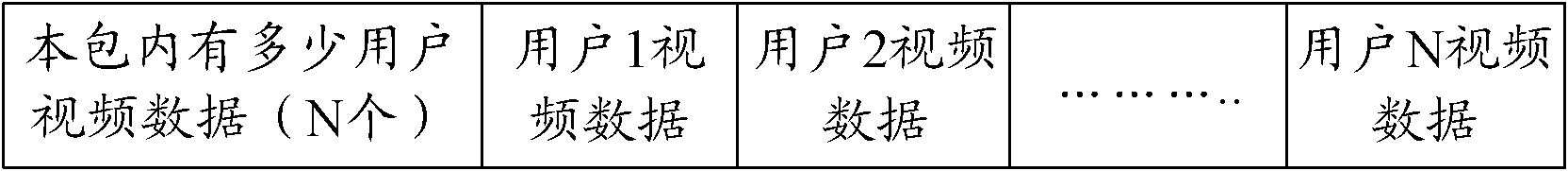
ActiveCN102185856AImprove interactivityTroubleshoot game interruptionsTransmissionSelective content distributionClient-sideGame server
The invention discloses a team organizing video method, a team organizing video device and a team organizing video system used in a team organizing game, aiming at reducing the waste of network resources and facilitating management. The team organizing video system used in the team organizing game comprises a game client terminal, a game server and a video server, wherein the game client terminal is used for sending a first video request to the game server, obtaining connecting port information of the video server selected by the game server, and sending a second video request to the video server according to the connecting port information; the second video request carries the queue identification of a user corresponding to the game client terminal; the game server is used for receiving the first video request of the game client terminal, obtaining the queue identification of the user corresponding to the game client terminal, and selecting the video server for the game client terminal according to the queue identification; and the video server is used for receiving the second video request sent by the game client terminal, and selecting a team processing module for the game client terminal according to the queue identification to process audio / video data of the game client terminal.
Owner:贵阳语玩科技有限公司
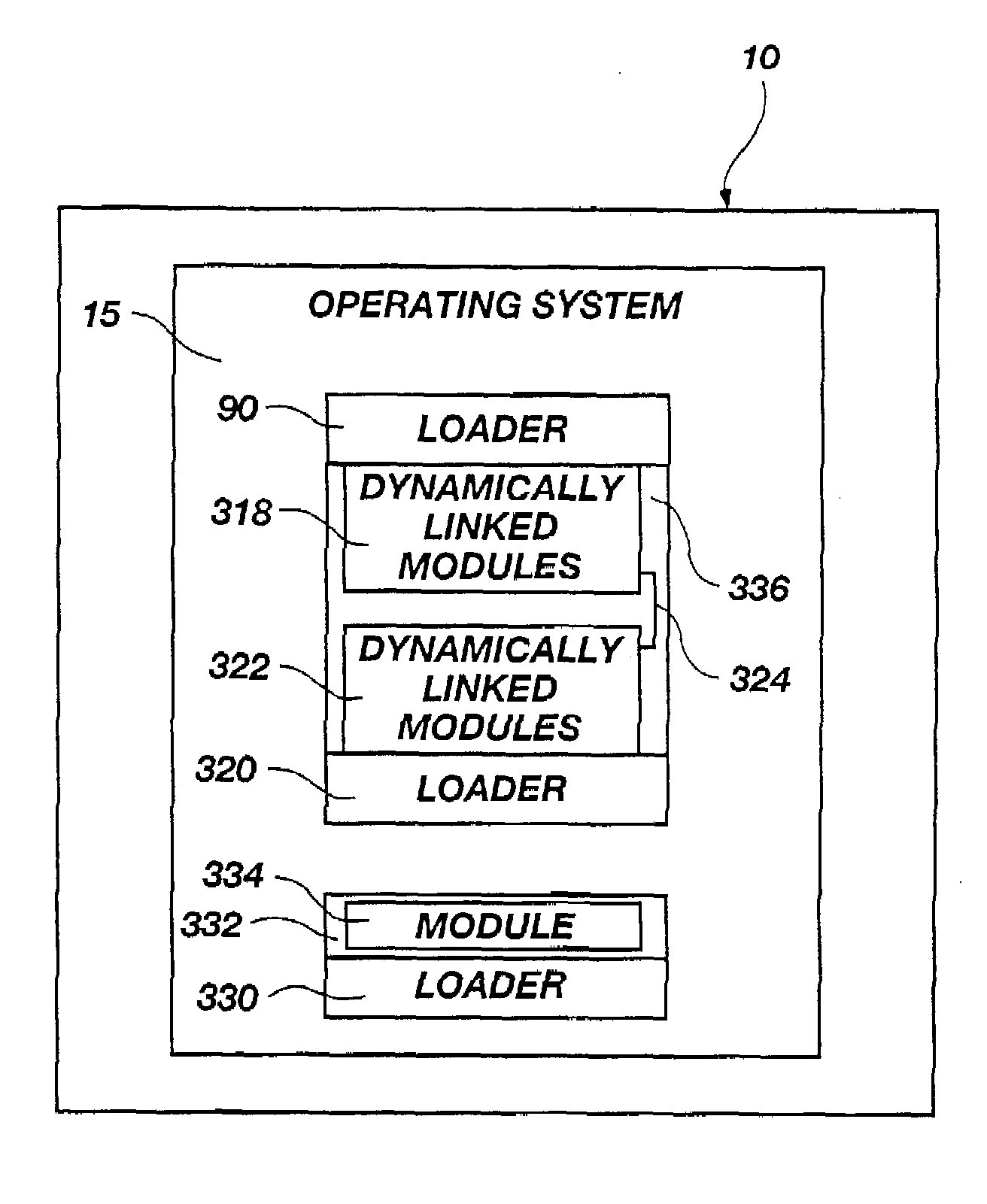
Nested strong loader apparatus and method
InactiveUS7383442B2Reduce probability being decipheredSufficient complexityMultiple keys/algorithms usageUser identity/authority verificationComputer moduleModularity
An apparatus and method provides one or more controlled, dynamically loaded, modular, cryptographic fillers. Fillers may be loaded by a single loader, multiple independent loaders, or nested loaders. Loaders may be adapted to load other loaders, within cryptographic controls extant and applicable thereto. Integration into a base executable having one or more slots, minimizes, controls, and links the interface between the fillers and base executables. The filler may itself operate recursively to load another filler in nested operations, whether or not the fillers are in nested relation to one another. An ability of any filler to be loaded may be controlled by the base executable verifying the integrity, authorization, or both for any filler. The base executable may rely on an integrated loader to control loading and linking of fillers and submodules. A policy may limit each module function, access, and potential for modification or substitution. Dynamically loaded modules (loaders, other fillers, and submodules thereof), typically represent a relatively small portion of the overall coding required by the base executable, and may provide strong controls limiting integration by providing access that is nested, layered, or both between modules excluding direct access to or by them from the base executable or supported applications.
Owner:EMC IP HLDG CO LLC
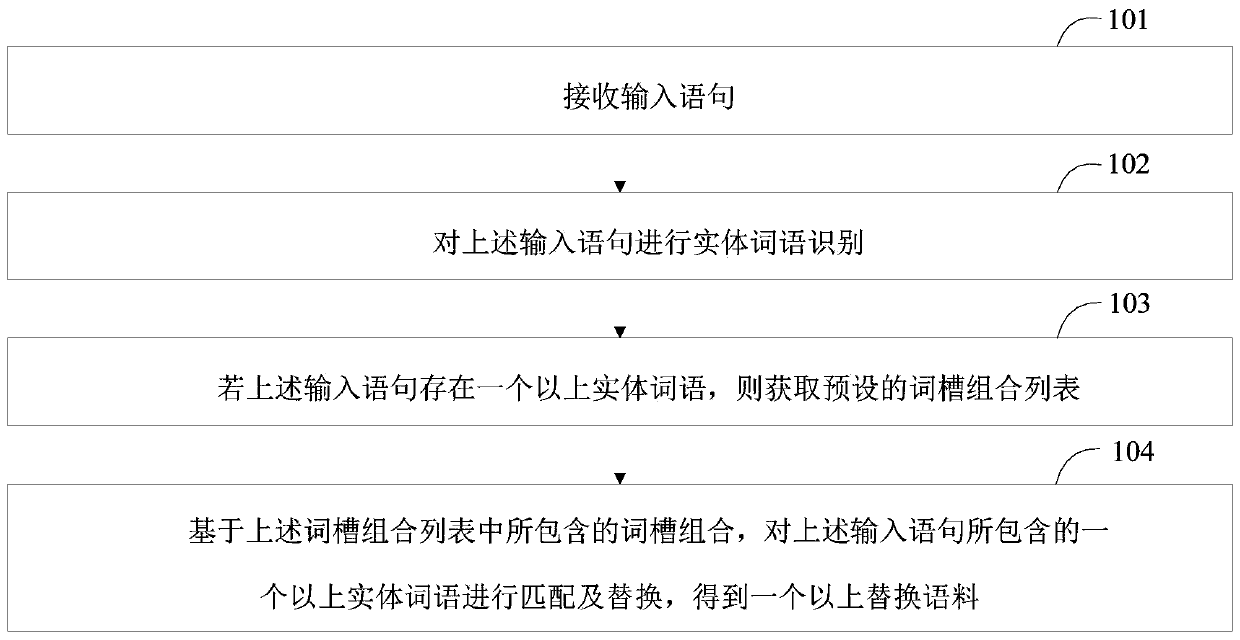
Corpus generation method, corpus generation device and intelligent equipment
PendingCN111178077AImprove processing efficiencyReduce generationNatural language data processingProgramming languageNatural language processing
The invention discloses a corpus generation method, a corpus generation device, intelligent equipment and a computer readable storage medium. The method comprises the steps: receiving an input statement; performing entity word recognition on the input statement; if more than one entity words exist in the input statement, a preset word slot combination list is obtained, the word slot combination list comprises more than one word slot combination, and each word slot combination at least comprises one word slot; and based on word slot combinations contained in the word slot combination list, matching and replacing more than one entity words contained in the input statement to obtain more than one replacement corpus. According to the scheme, word slot replacement is limited through the presetword slot combination list, it is avoided that word slot replacement is conducted on the input statement through invalid word slot combinations, generation of wrong replacement corpora can be reducedto a certain extent, and the subsequent replacement corpus processing efficiency is improved.
Owner:UBTECH ROBOTICS CORP LTD
Digital work ticket management and control system and method for power industry
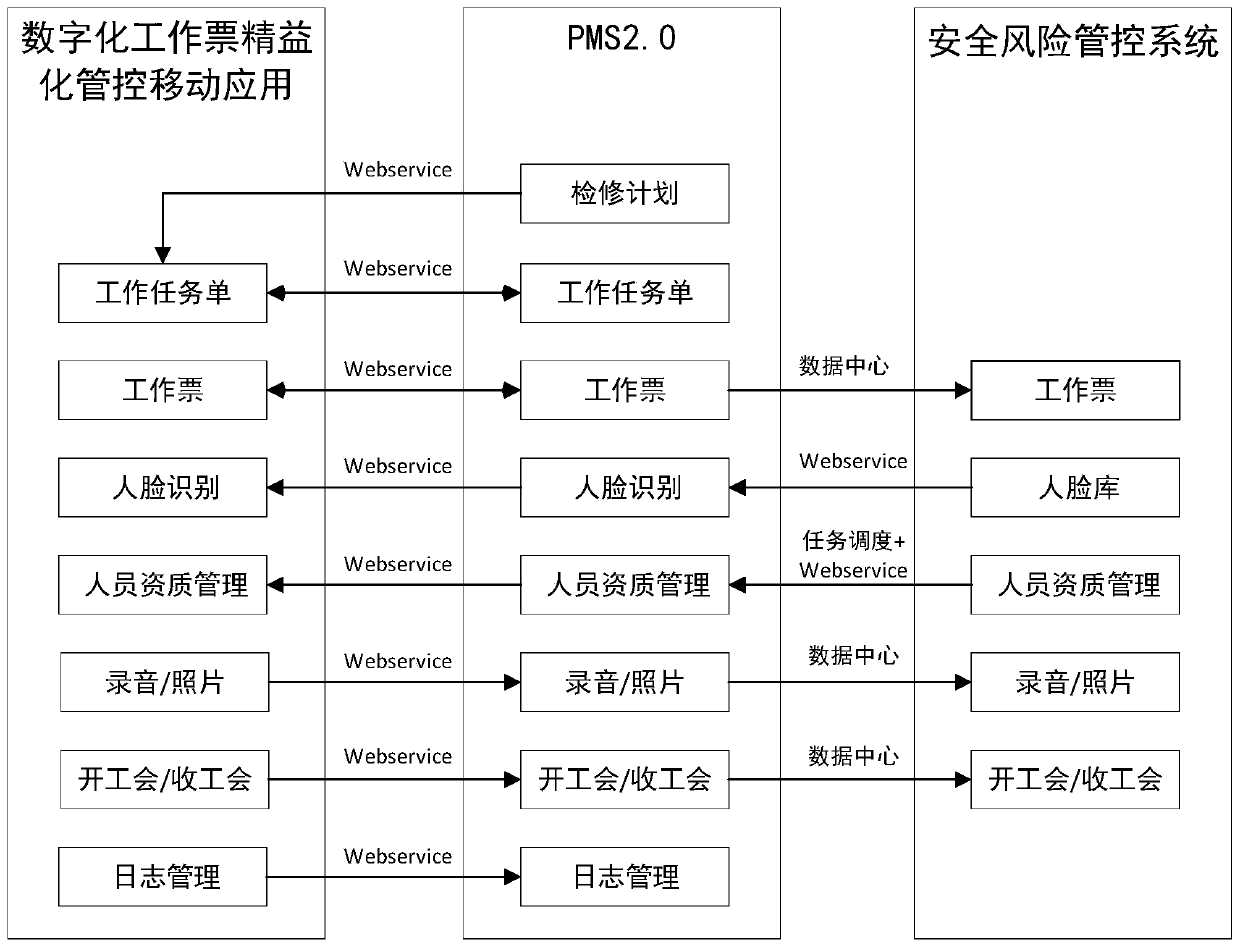
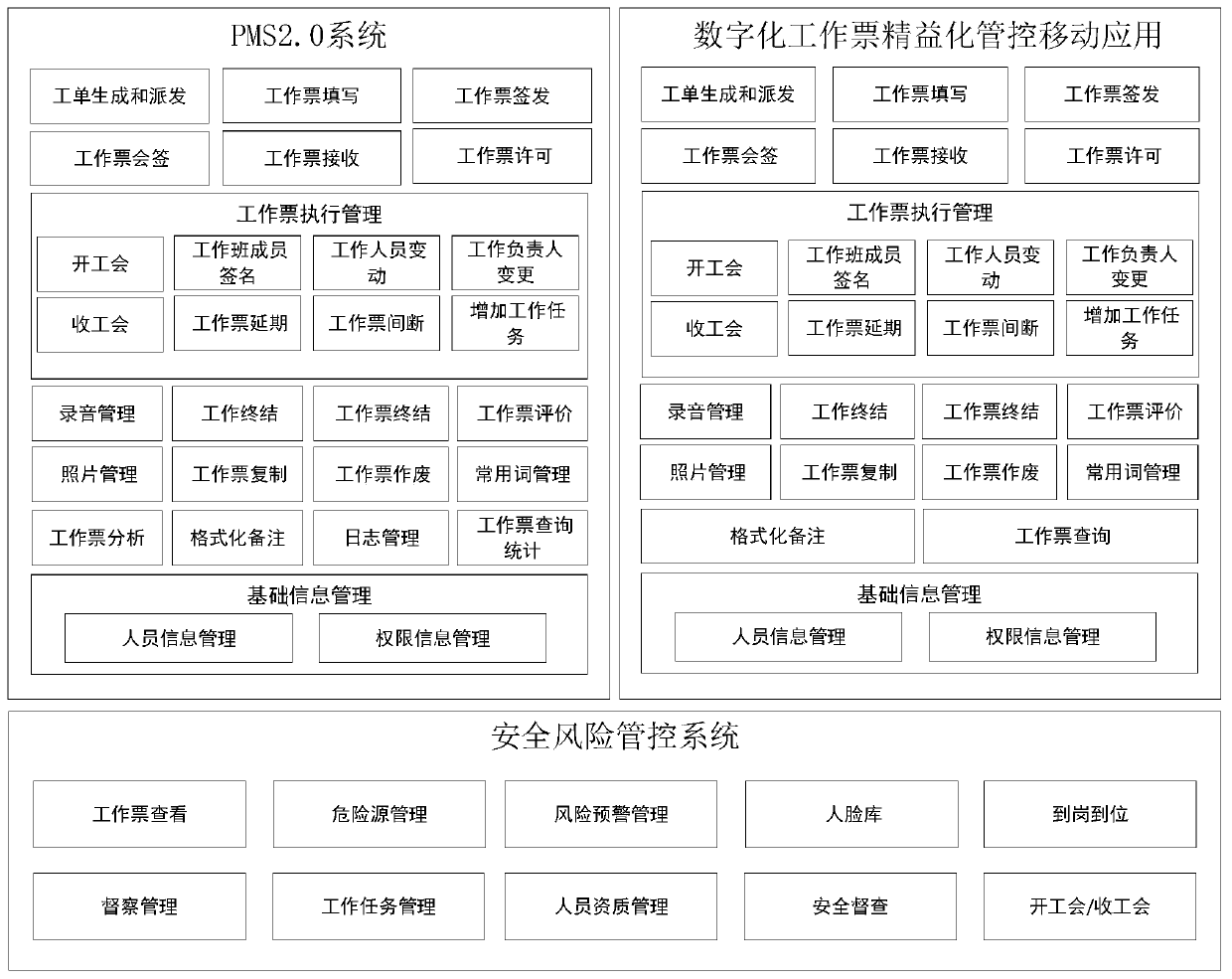
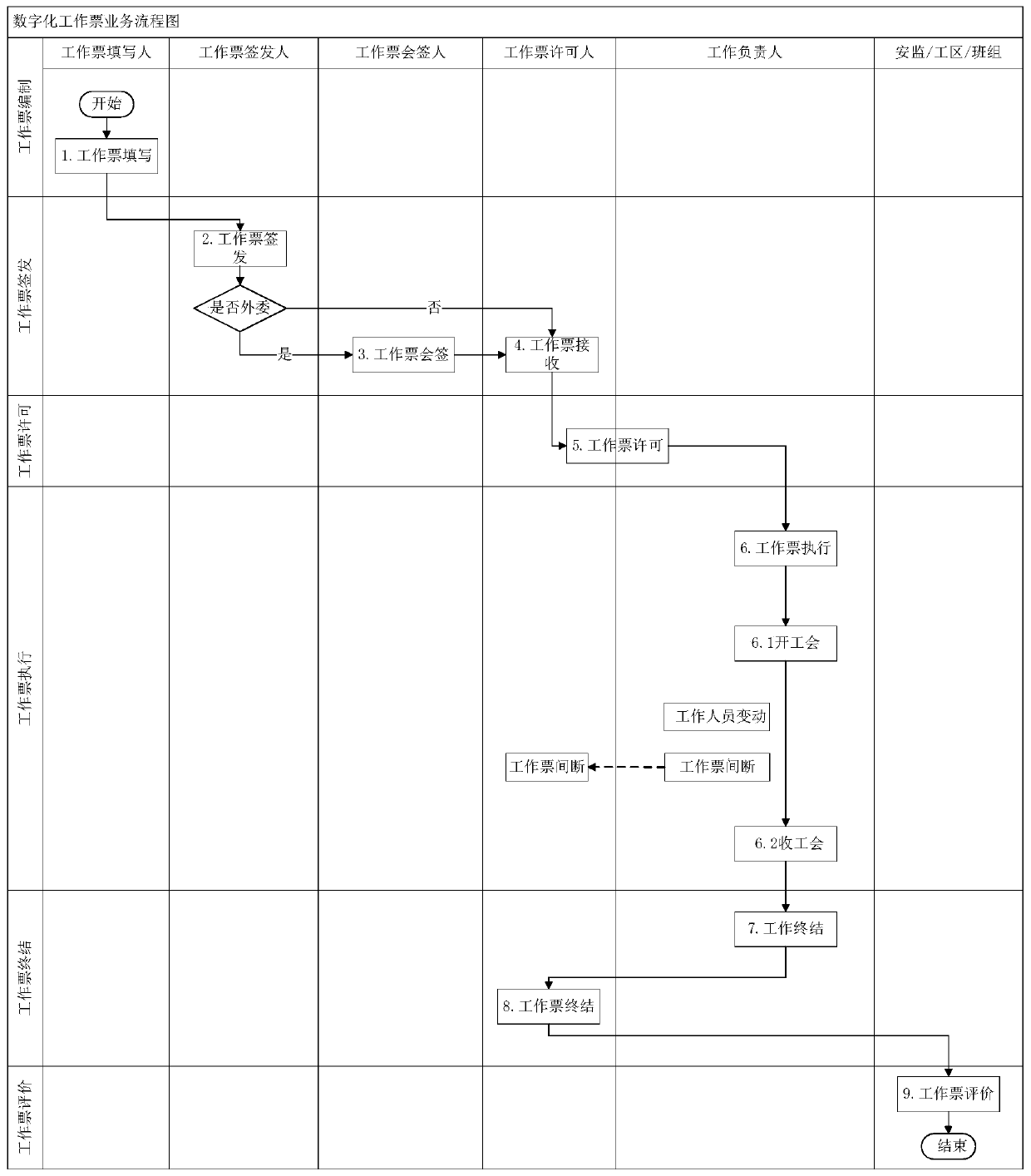
PendingCN111091304ASolve electronic problemsAvoid time-consuming and laborious communicationOffice automationResourcesTicketControl system
The invention discloses a digital work ticket management and control system and method for the power industry. The system comprises a work ticket management and control subsystem which generates a work order according to a received maintenance task, generates a work ticket according to the work order, performs electronic signature and personnel qualification judgment on the work ticket to executeissuing and permission, sends an electronic signature verification and personnel qualification judgment request to a PMS subsystem, and synchronizes the work ticket to the PMS subsystem; the PMS subsystem calls a face library and face recognition judgment logic of the safety risk management and control subsystem; an electronic signature verification result is obtained, personnel qualification information of the safety risk management and control subsystem is called regularly, the electronic signature verification result and the personnel qualification information are sent to the work ticket management and control subsystem, and the work ticket is synchronized to the work ticket management and control subsystem; and the safety risk management and control subsystem is used for storing the face library, the face recognition judgment logic and the personnel qualification information, receiving the work ticket synchronized by the PMS subsystem for storage, and realizing integration with thePMS 2.0 system and the safety risk management and control platform.
Owner:金现代信息产业股份有限公司
Security certification system based on broadcast television one-way transmission network
InactiveCN104506503AAvoid substitutionPrevent operabilityUser identity/authority verificationSecure transmissionData source
The invention discloses a security certification system based on a unidirectional transmission broadcast television network. The security certification system comprises a data source server end, a signature encryption and certificate management system and a data receiving end, and solves several security problems that the broadcast television network currently faces. On one hand, secure and reliable certification is provided for secure data transmission of a broadcast television server side, on the other hand, illegal operations that files are tampered, replaced, maliciously replaced and the like in the transmission process of the unidirectional network are effectively prevented, and meanwhile television advertisements are also prevented from being replaced by criminals with profitable advertisement of the criminals.
Owner:BEIJING BUPT GUOAN TECH
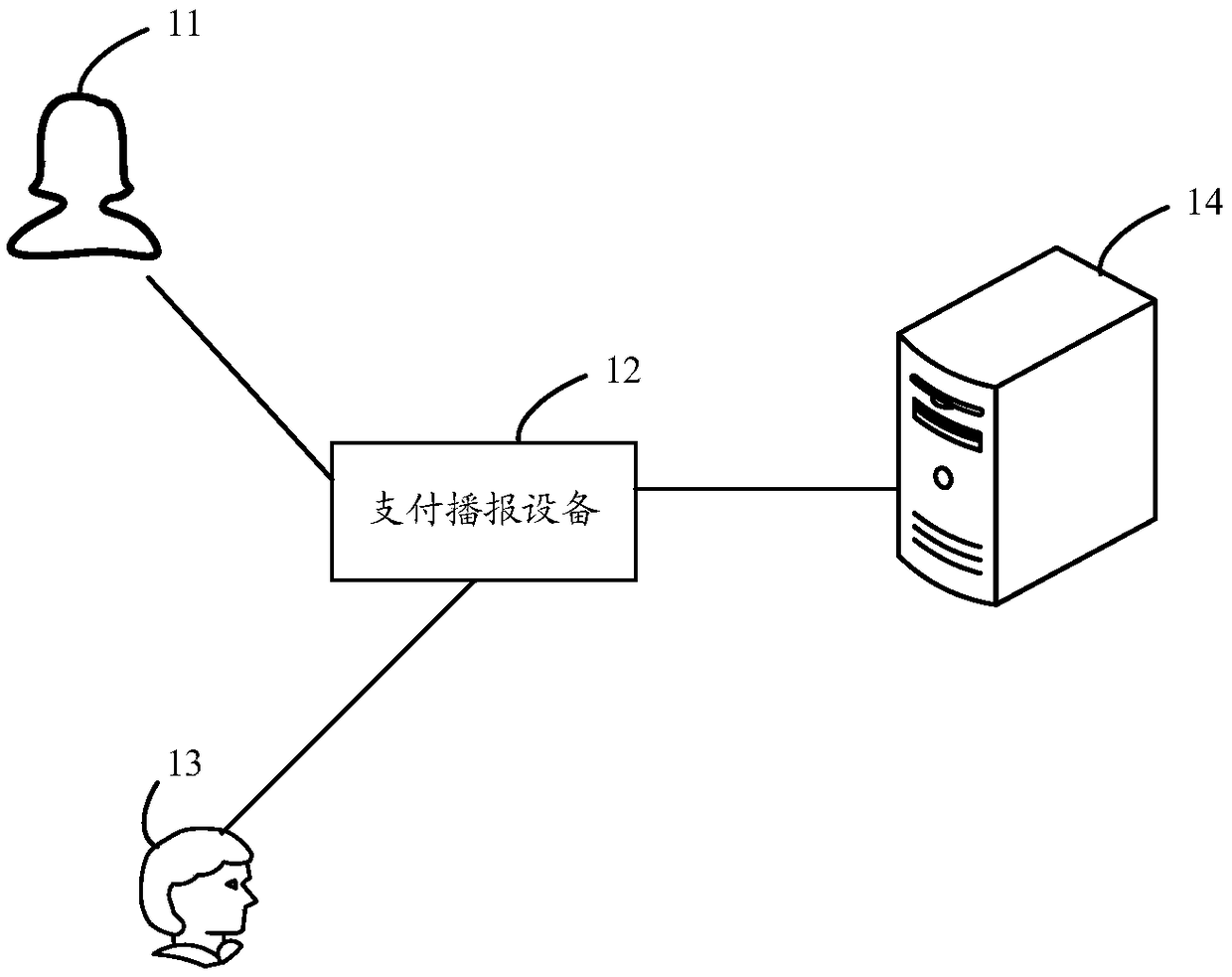
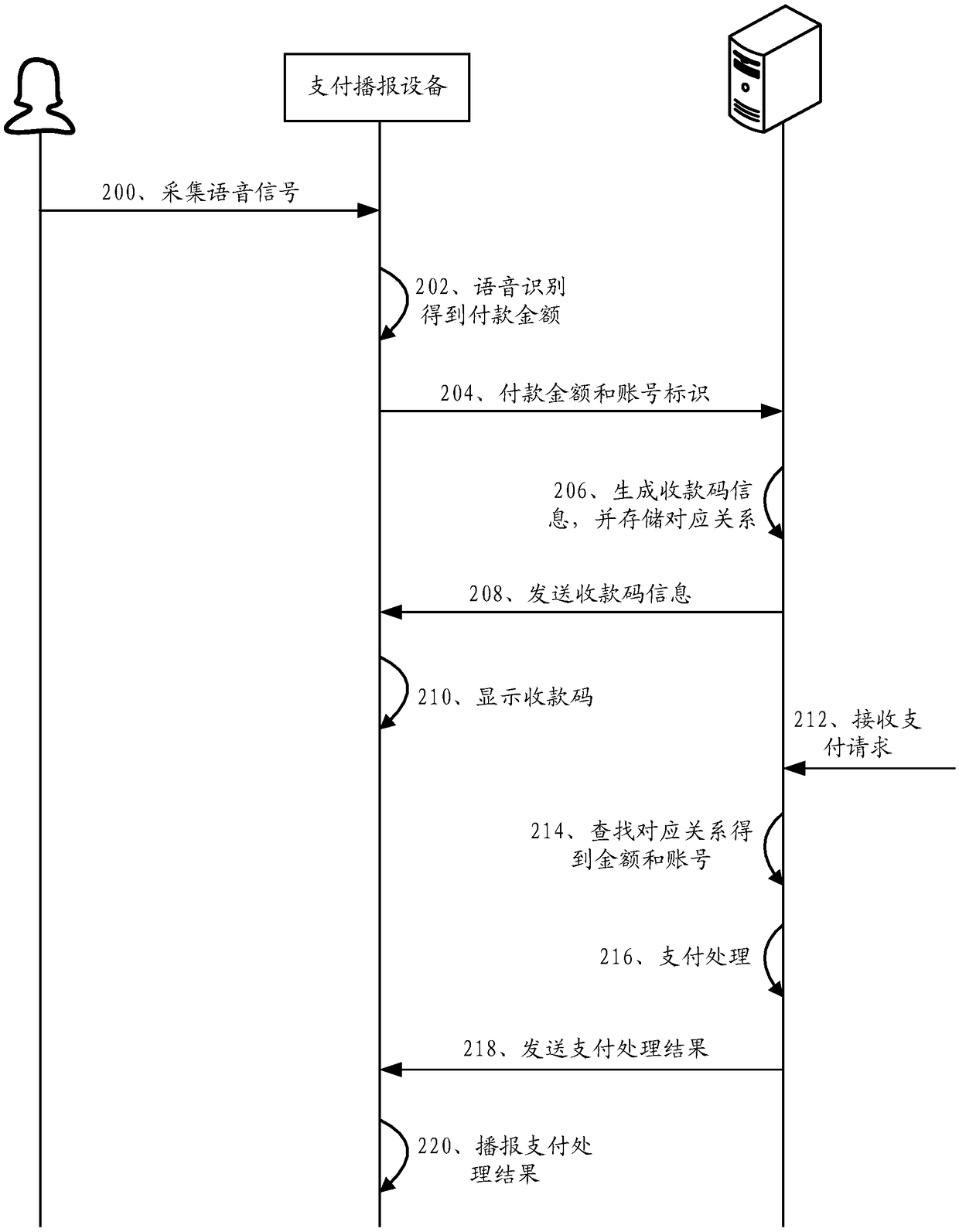
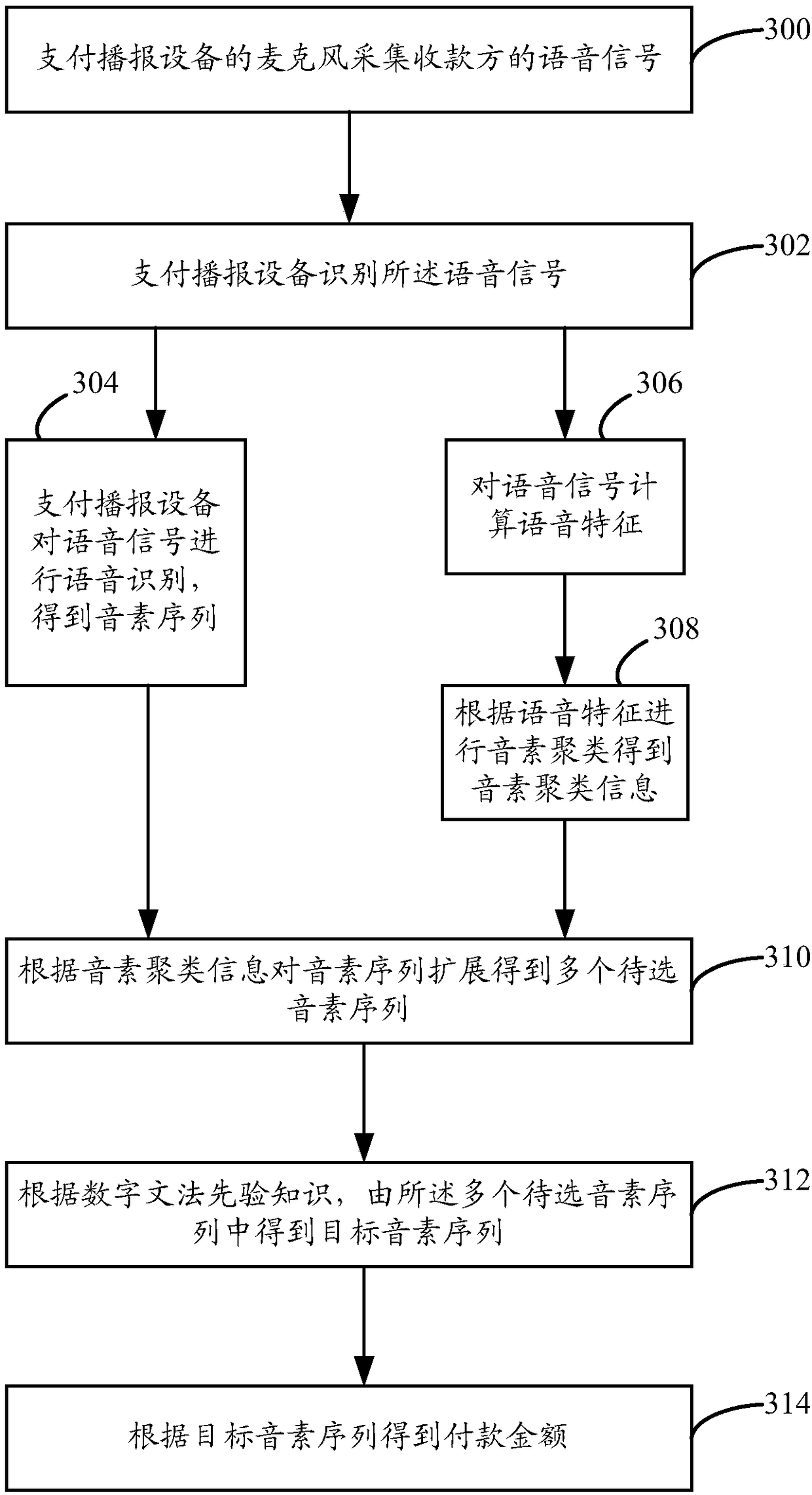
A payment processing method and device
InactiveCN109377202AImprove convenienceAvoid substitutionPayment architectureSpeech recognitionPaymentInformation finding
The embodiment of the specification provides a payment processing method and device, wherein, the method comprises the following steps: a payment broadcasting device collects a voice signal of a payee, wherein the voice signal is a payment amount to be paid by the payee at an input payer; The payment broadcasting device recognizes and analyzes the voice signal to obtain the payment amount, and sends the payment amount and the account number identification of the payee to the payment server. The payment server generates corresponding collection code information according to the payment amount and the account number identification; the collection code information is sent to the payment broadcasting device; The payment broadcasting device displays a collection code corresponding to the collection code information; When receiving the payment request, the payment server searches for the corresponding payment amount and the account number identification according to the collection code information in the payment request, and performs payment processing.
Owner:ADVANCED NEW TECH CO LTD
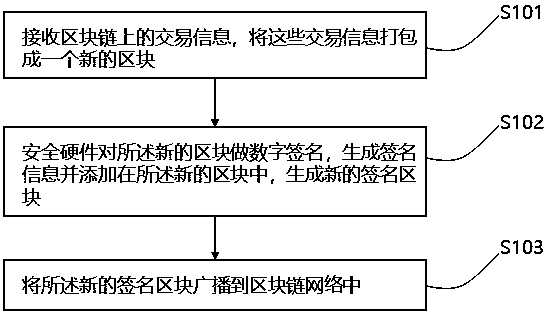
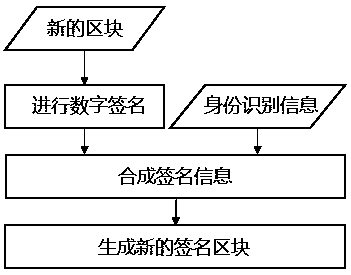
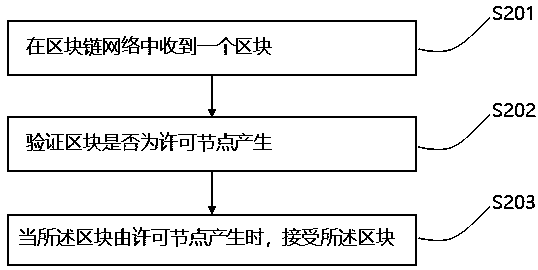
Block sending method and device for block chain
InactiveCN109560939AAvoid duplicatesEnsure safetyFinanceUser identity/authority verificationIdentity recognitionTransaction data
The invention discloses a block sending method and device for a block chain. The block sending method comprises the steps that interaction data on a block chain network is received and packaged into anew block; security hardware signs the new block by using an identity recognition private key packaged inside and adds the signature information to the new block so as to generate a new signature block; and the new signature block is sent to the block chain network. By using the method and device disclosed by the embodiment of the invention, the identity recognition private key packaged inside the security hardware of a block sending node of the block chain cannot be extracted, so that the non-duplication and uniqueness of identity recognition information of the block sending node are ensured, and thus the witch attack performed by the block sending node by using the duplication is avoided; and a receiving node on the block chain can determine the identity of a block sender by verifying the signature information in the new signature block so as to judge whether the block is generated by a license node or not.
Owner:张超
Data security protection method and data security protection device
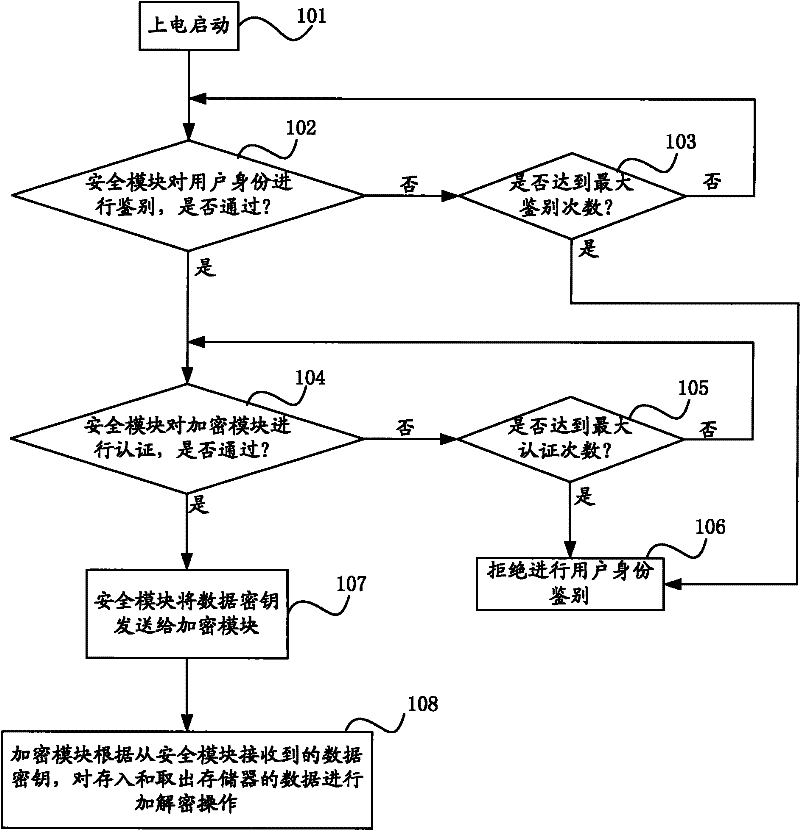
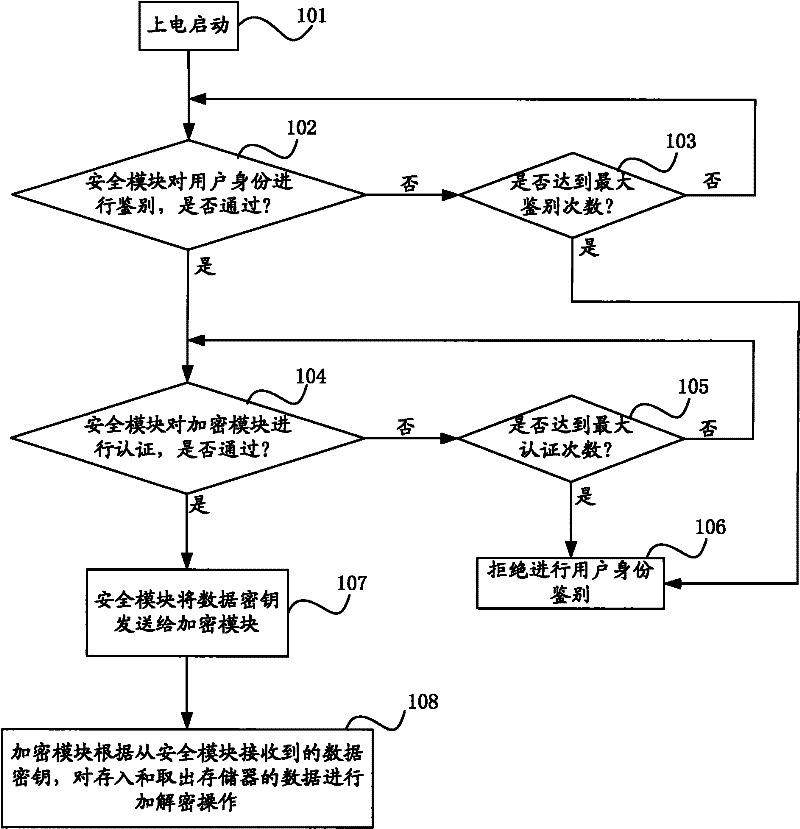
ActiveCN102236607AGuaranteed reliabilityEnsure safetyUnauthorized memory use protectionInternal/peripheral component protectionComputer memoryMobile phone
The invention relates to a data security protection method and a data security protection device for protecting data security in a computer memory. The method comprises the following steps that: while starting computer equipment, a security module respectively distinguishes and authenticates a user identity and an encryption module, after passing through the distinguishing and the authentication, the security module transmits a data key to the encryption module, in the following use, the encryption module encrypts the memory data for protection, and if the distinguishing and the authentication are not passed, the computer cannot be started. The device comprises the security module and the encryption module, which are arranged in computer equipment, such as a PC host, a PDA, a mobile phone, a PMP or a digital photo frame and the like, and are connected with each other. The method and the device implement the transparent encryption for the memory data of computer equipment and the distinguishing of user identity, and simultaneously, separately store a key and an encryption algorithm, thereby implementing higher security.
Owner:NATIONZ TECH INC
Data storage method, scheduling device, system and device and storage medium
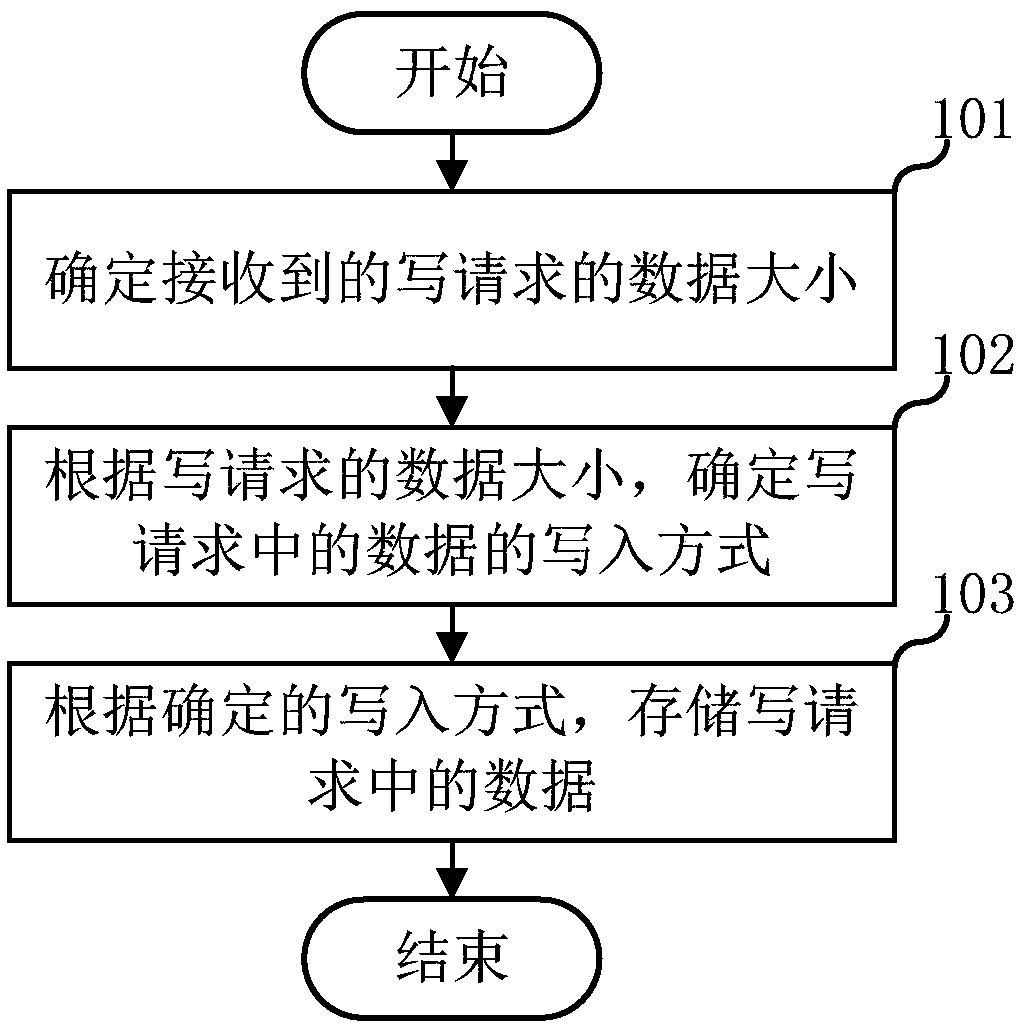
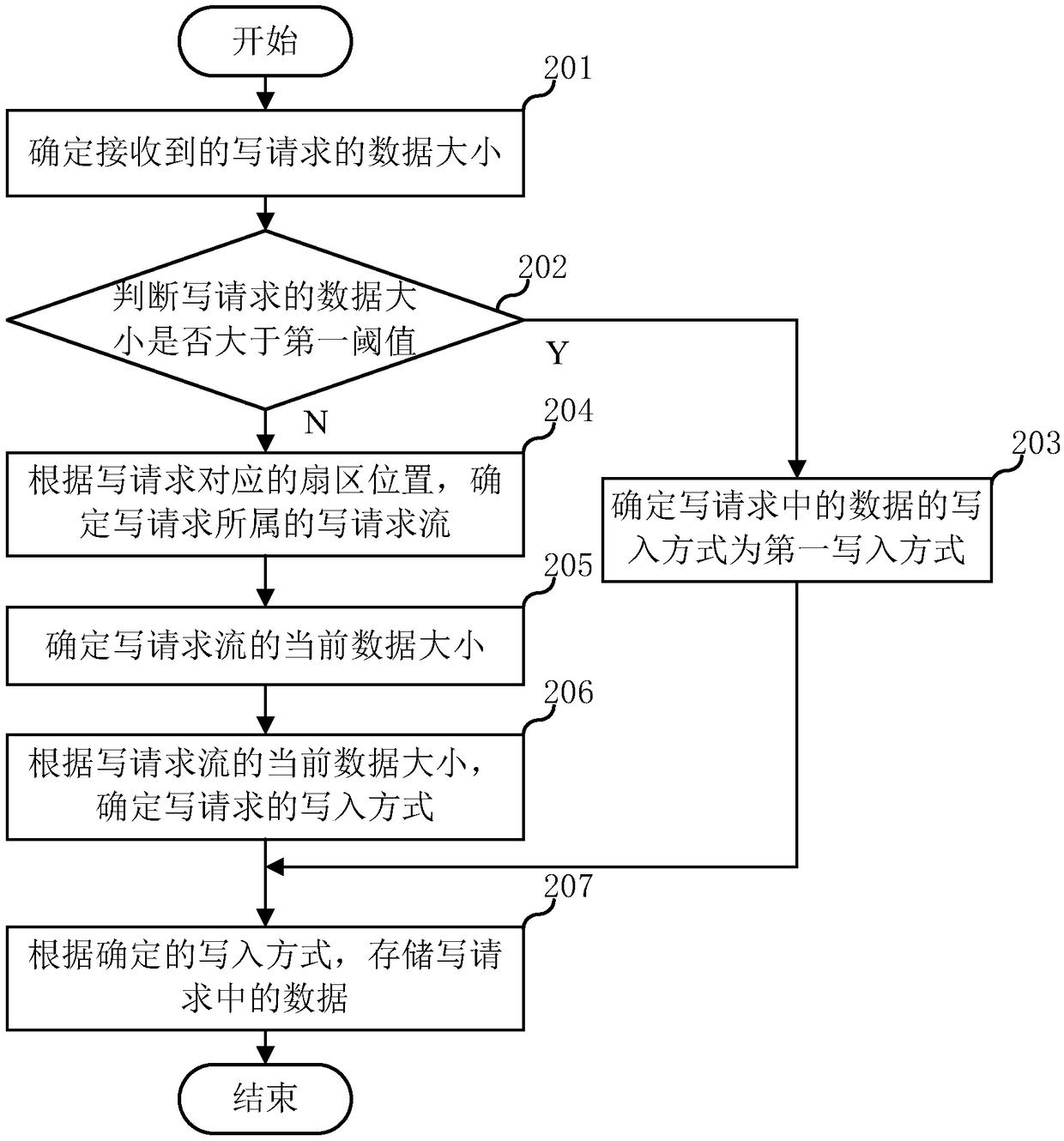
ActiveCN109375868AAvoid substitutionReduce performance consumptionInput/output to record carriersIOPSThroughput
The embodiment of the invention relates to the field of data storage, and discloses a data storage method, a scheduling device, system and device and a storage medium. In the invention, the data storage method comprises the following steps: determining the data size of the received write request; determining a write mode of data in the write request according to the data size of the write request;Wherein the writing mode comprises a first writing mode; Wherein the first write mode is to directly store the data in the write request into the memory; The data in the write request is stored according to the determined write mode. According to the data size of the write request, the write mode of the data storage system to the data in the write request is flexibly adjusted, so that the data storage system has high IOPS performance and high throughput performance.
Owner:深圳爱捷云科技有限公司
Method and device for guaranteeing security of POS machine firmware
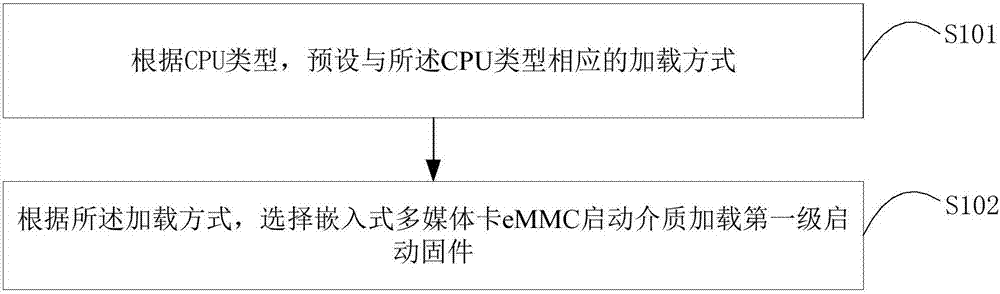
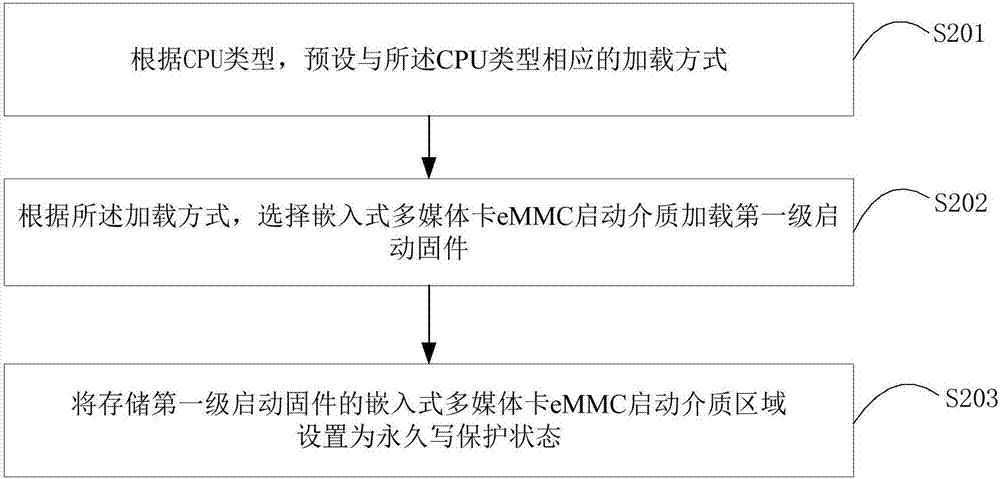
ActiveCN107330333ALow costAvoid substitutionCash registersPlatform integrity maintainanceFirmwareComputer terminal
The invention is suitable for the technical field of terminals, and provides a method and device for guaranteeing the security of POS machine firmware. The method includes the steps that according to the type of a CPU, a loading mode corresponding to the type of the CPU is preset, and according to the loading mode, first stage starting firmware is loaded by selecting an embedded multi-medium card e MMC starting medium. With the method, loading from other starting media capable of being connected with the exterior can be avoided; it is prevented that through the starting media, the firmware in a POS machine is replaced or tampered, and therefore it is guaranteed that the POS machine meets the requirement for security.
Owner:PAX COMP TECH SHENZHEN
Physical distribution piece tracking system based on GSM (Global System for Mobile Communications) and RFID (Radio Frequency Identification) technology
InactiveCN102184437APrevent off-dutyAvoid substitutionData processing applicationsCo-operative working arrangementsInformation processingData center
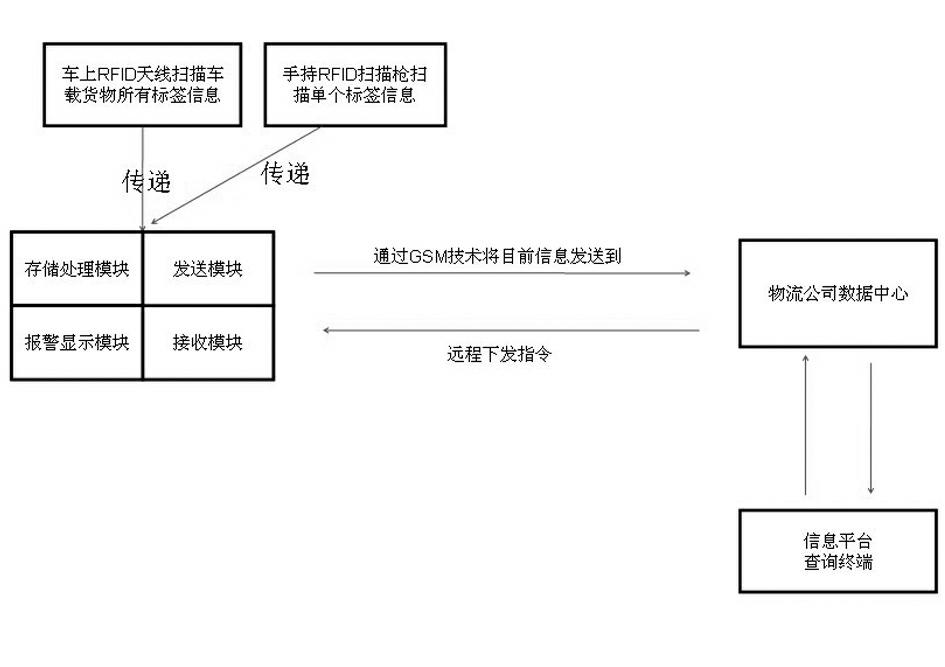
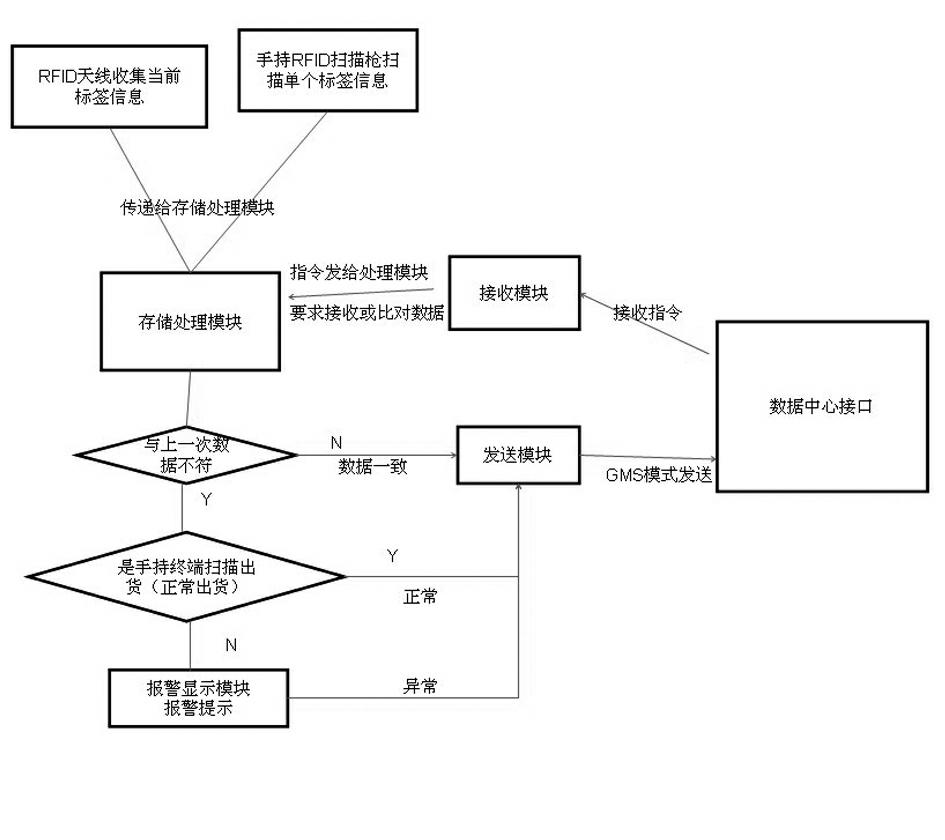
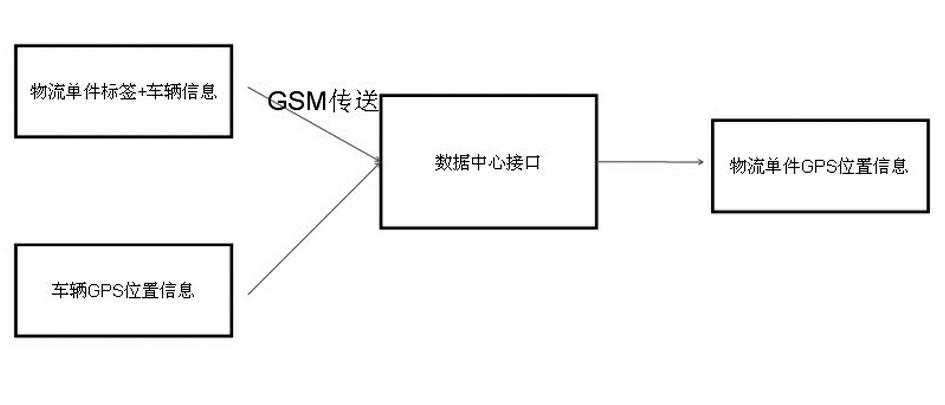
The invention relates to a physical distribution piece tracking system based on a GSM (Global System for Mobile Communications) and RFID (Radio Frequency Identification) technology. The physical distribution piece tracking system is characterized by comprising an information processing flow, a vehicular terminal information processing flow and a data processing center flow, wherein the information processing flow comprises the following steps that: a vehicular RFID antenna scans all label information of the vehicular goods and a handhold scanning gun scans single label information; all the label information of the vehicular goods scanned by the RFID antenna and the single label information scanned by the handhold scanning gun are transmitted to a processing center module; the processing center module sends the current information to a data center of the physical distribution company through the GSM technology; and the data center of the physical distribution company sends an instruction to the processing center module in remote and is communicated with an information platform inquiring terminal. The physical distribution piece tracking system has the following advantages that: the label information is sent back through the vehicular RFID; the drivers are prevented from leaving the pose, and replacing the goods; and during the vehicle transportation procedure, the system can timely alarm when the goods is accidentally lost.
Owner:SHANGHAI XINYE NETWORK TECH
Aircraft engine and mouse cage type bearing structure thereof
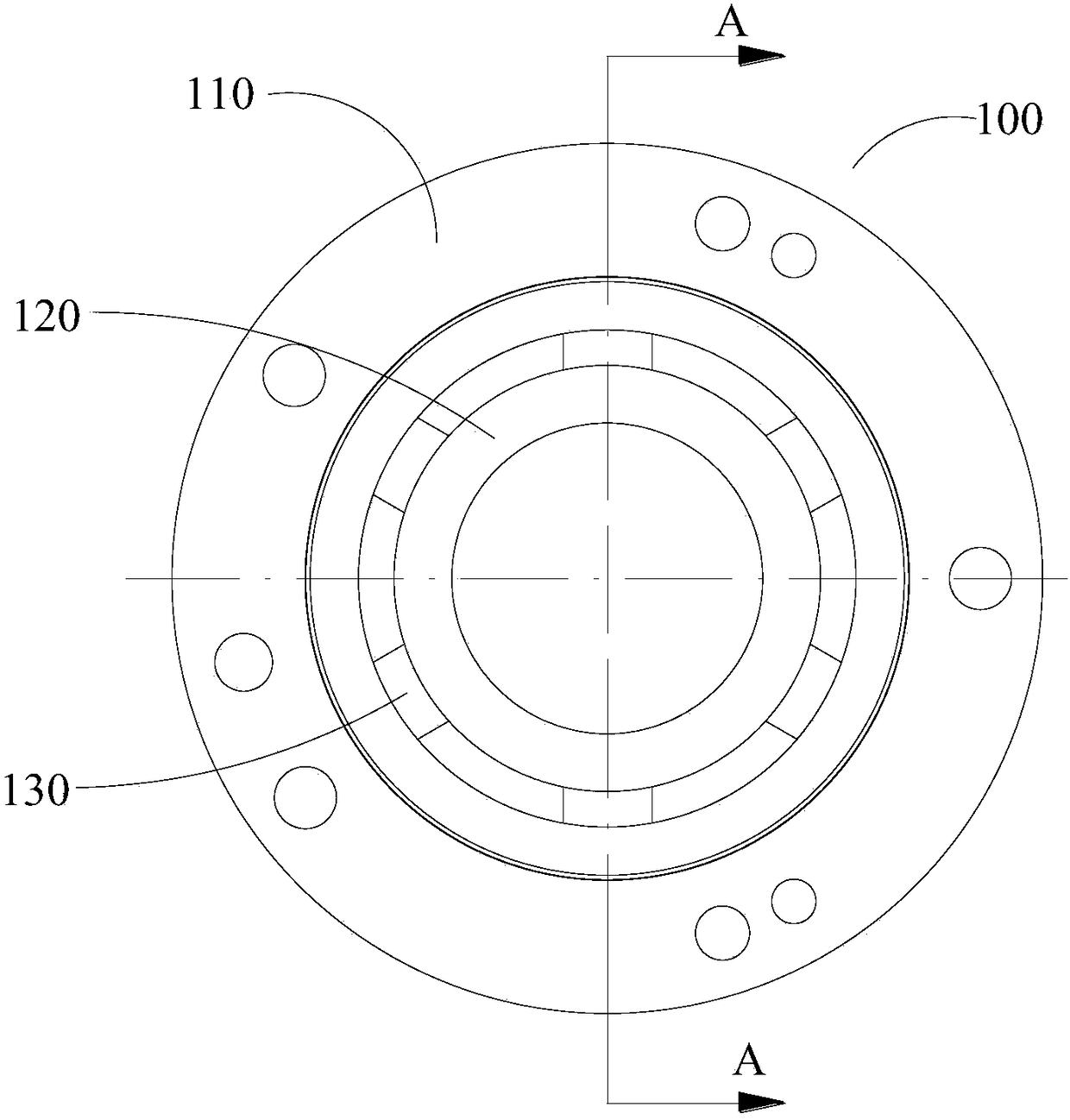
ActiveCN108691893AImprove performanceImprove reliabilityElastic bearingsBearing unit rigid supportAircraft noiseAero engine
The invention provides a mouse cage type bearing structure. The mouse cage type bearing structure comprises a mouse cage body, a bearing and a regulating fixing part, wherein the inner part of the mouse cage body is provided with a bearing placing cavity and a regulating cavity; the bearing is arranged in the bearing placing cavity; the length, in the axial direction, of the bearing is smaller than that, in the axial direction, of the bearing placing cavity; the regulating fixing part can be axially and movably arranged in the regulating cavity; the regulating fixing part can regulate the position, in the bearing placing cavity, of the bearing, and fixes the bearing; the regulating fixing part regulates the position, in the bearing placing cavity, of the bearing, so that the axial positionof the bearing is adjustable, the distance from the bearing to the end part of the mouse cage body is changed, the problem that the bearing position is non-adjustable as the bearing and the mouse cage are integrated is effectively solved, and the rigidity of the mouse cage type bearing structure is conveniently changed. Meanwhile, the mouse cage body and the bearing are two parts, so that the cost can be reduced, and design and processing are convenient. The invention further provides the aircraft engine.
Owner:TSINGHUA UNIV
Detection system for detection of concrete test block and traceability anti-cheating method
ActiveCN108090531AAvoid taking by mistakeAvoid detection implementationImage enhancementImage analysisImage acquisitionTraceability
The disclosure provides a detection system for detection of a concrete test block and a traceability anti-cheating method. The detection system is composed of a detection machine, an identity information acquisition device, an image acquisition device, and a processor. The front end of the image acquisition device is aligned at a direction of a concrete test block of the detection machine. The processor coupled to the detection machine, the identity information acquisition device, and the image acquisition device electrically performs the following control operations: the identity informationacquisition device determines an identity of a current test block; according to the identity of the current test block, a detection task related to the current test block is searched; after the detection machine carries out detection corresponding to the detection task on the current test block, a detection result is obtained; when mould breaking of the concrete test block is detected, the image acquisition device is controlled to obtain a mould breaking picture of the concrete test block; and the detection result, the mould breaking picture, and the identity of the current test block are associated and are stored. Therefore, the links with high cheating feasibility are reduced; the cheating cost is lowered; and the authenticity of the concrete detection is improved truly.
Owner:北京金科汇智科技有限公司 +1
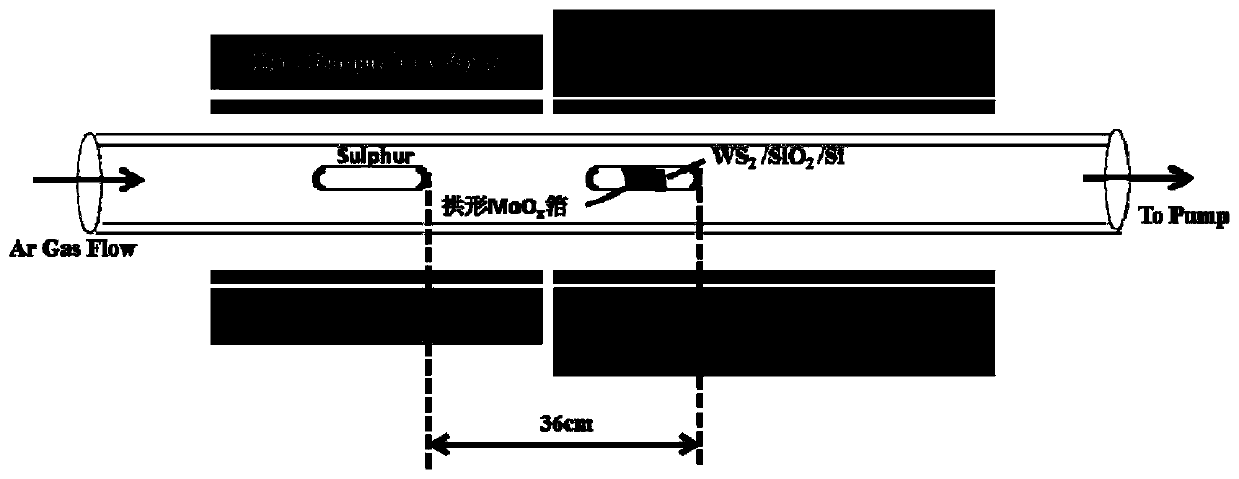
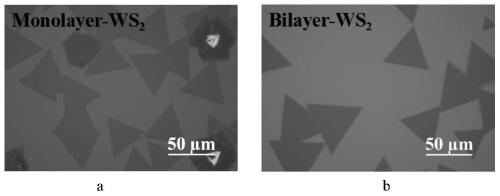
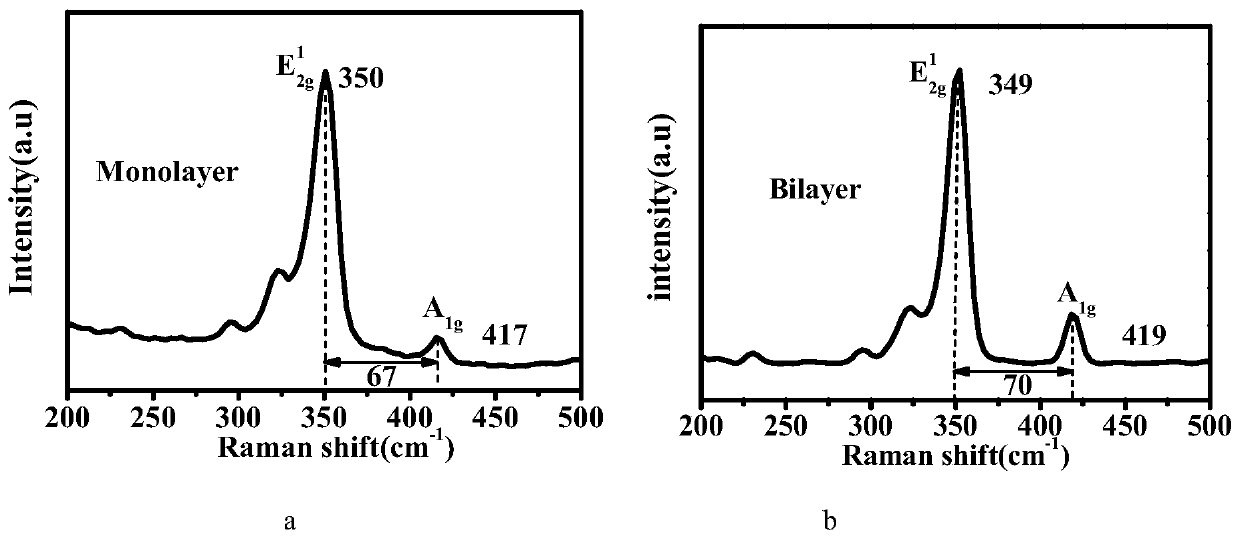
Preparation method for MoS2/WS2 vertical heterojunction
ActiveCN111349907AEasy molybdenum sulfur ratioControl Molybdenum Sulfur RatioSurface reaction electrolytic coatingChemical vapor deposition coatingAnodic oxidationTungsten
The invention discloses a preparation method for a MoS2 / WS2 vertical heterojunction. The preparation method comprises the following steps that WO3 and powdered sulfur are used as precursors, large-size high-quality single-layer tungsten disulfide is prepared on a SiO2 / Si substrate, a multivalent molybdenum oxide foil (MoOx) is prepared by using an electrochemical anodic oxidation method of Mo foil, and under the conditions of low pressure and low temperature, molybdenum disulfide grows on the surface of the tungsten disulfide by using the molybdenum oxide foil and the powdered sulfur as the precursors, so that the MoS2 / WS2 vertical heterojunction is prepared. The method is high in controllability and repeatability and has great significance in preparation of other transition metal sulfideheterojunctions.
Owner:XIAMEN UNIV
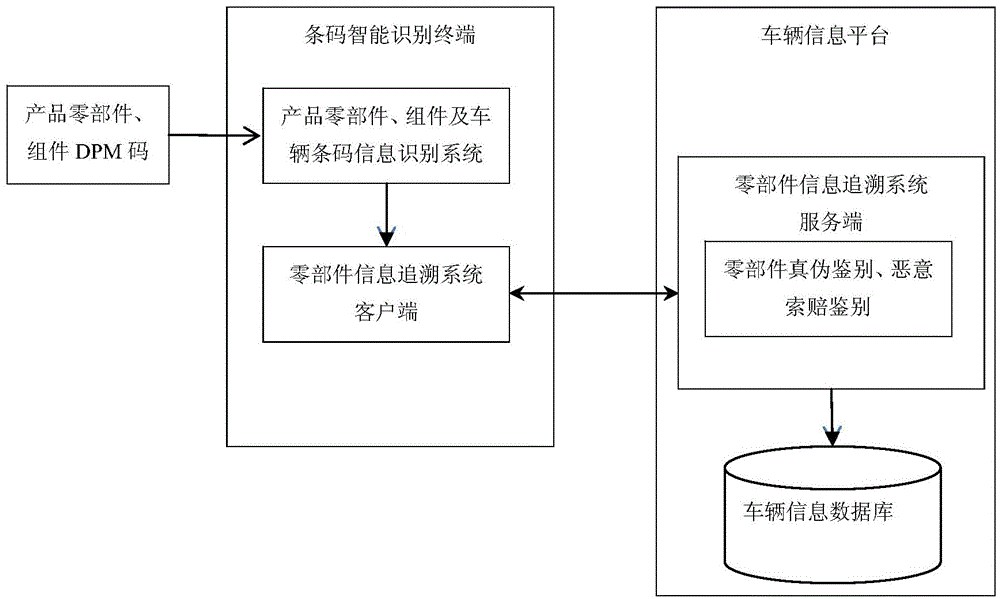
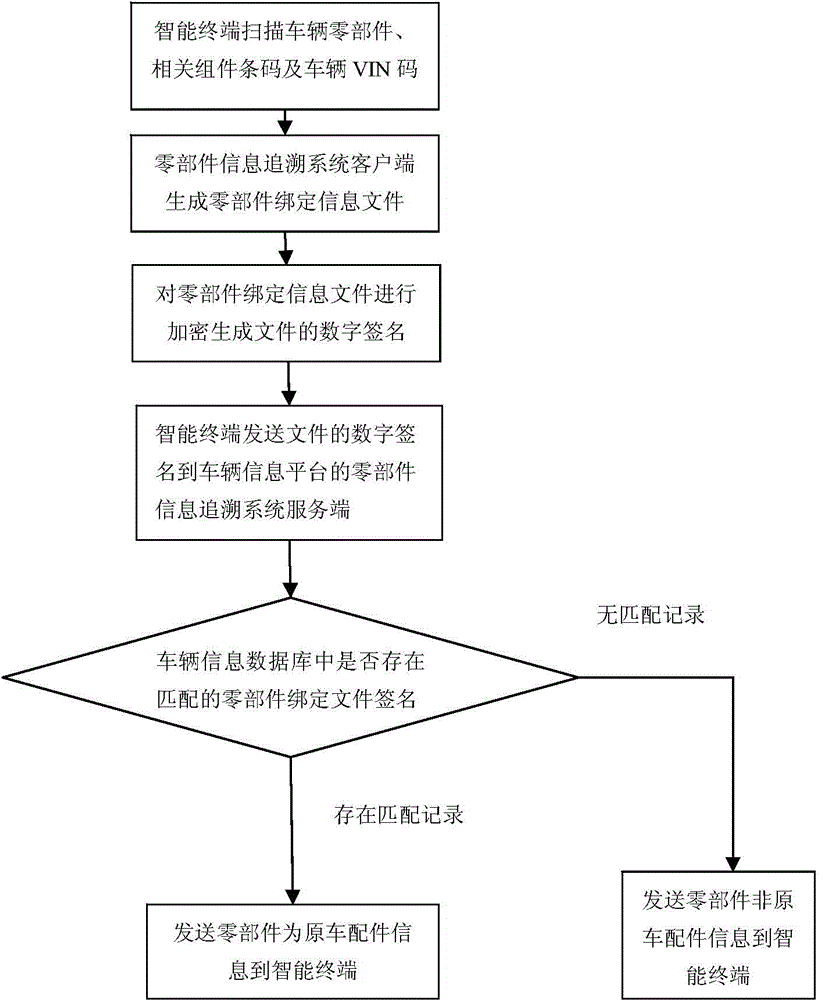
Tracing and discriminating method for anti-counterfeiting information of vehicle component
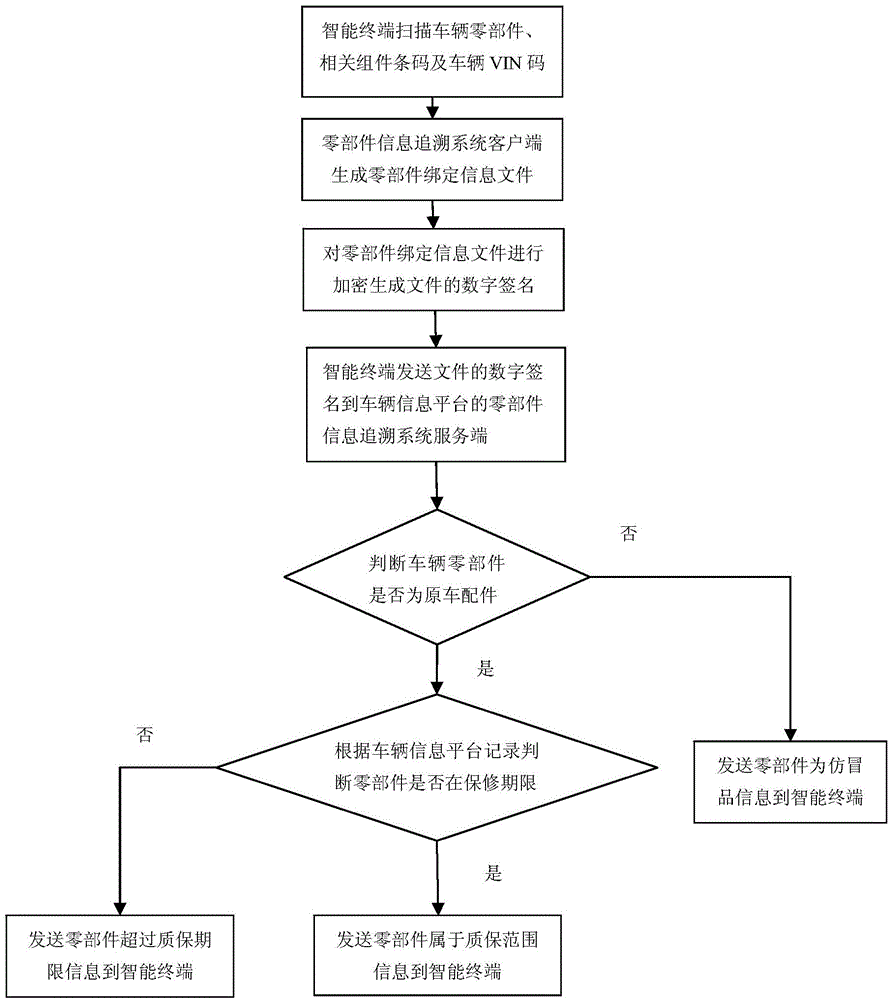
ActiveCN104424570AEasy to parseConvenient queryCommerceSensing by electromagnetic radiationDigital signatureBarcode
The invention relates to a tracing and discriminating method for anti-counterfeiting information of a vehicle component. The method comprises the following steps that: a barcode intelligent terminal scans or inputs component barcode identifier information; the barcode intelligent terminal generates an XML-format file from the collected component barcode identifier information according to level binding relation, carries out encryption on the file to obtain a digital signature, and sends the digital signature to a vehicle information platform; the vehicle information platform queries whether the digital signature exists in the database of the vehicle information platform; if so, the component belongs to the original vehicle fittings; if not, the component does not belong to the original vehicle fittings; and the query result is fed back to the barcode intelligent terminal. According to the invention, authenticity identification and information query of the vehicle as well as the main components and parts of the vehicle for the consumers can be realized and thus the vehicle components can be prevented from being replaced; and a discriminating method for malicious claims beyond the warranty and the fraud of the vehicle with warranty can be provided.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
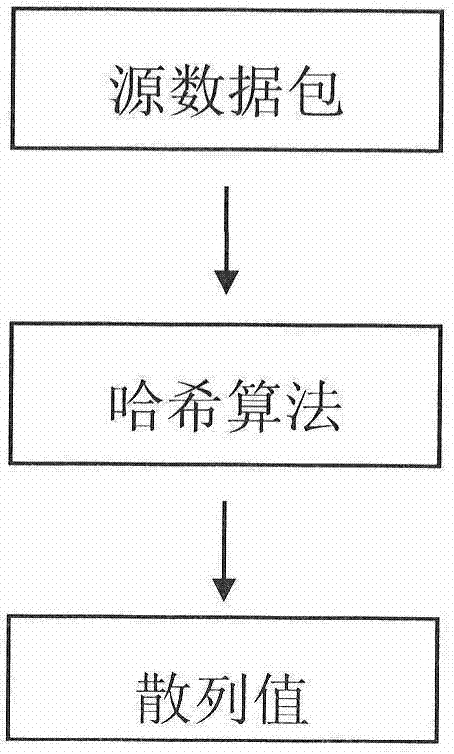
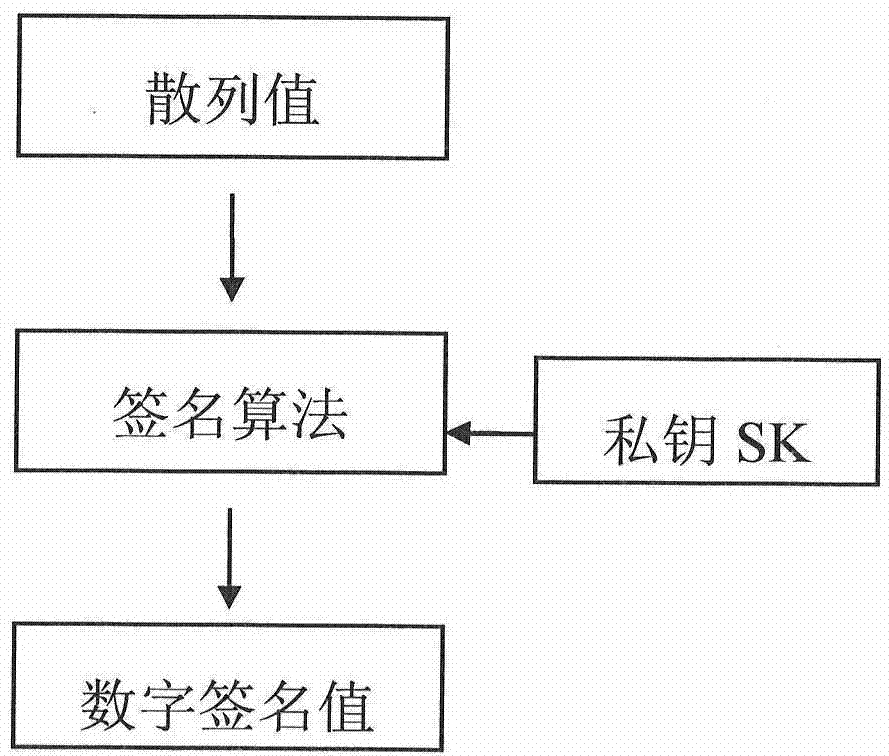
Sign device and method of digital sign
InactiveCN1794631APrevent tamperingAvoid substitutionUser identity/authority verificationInstruction unitTransfer procedure
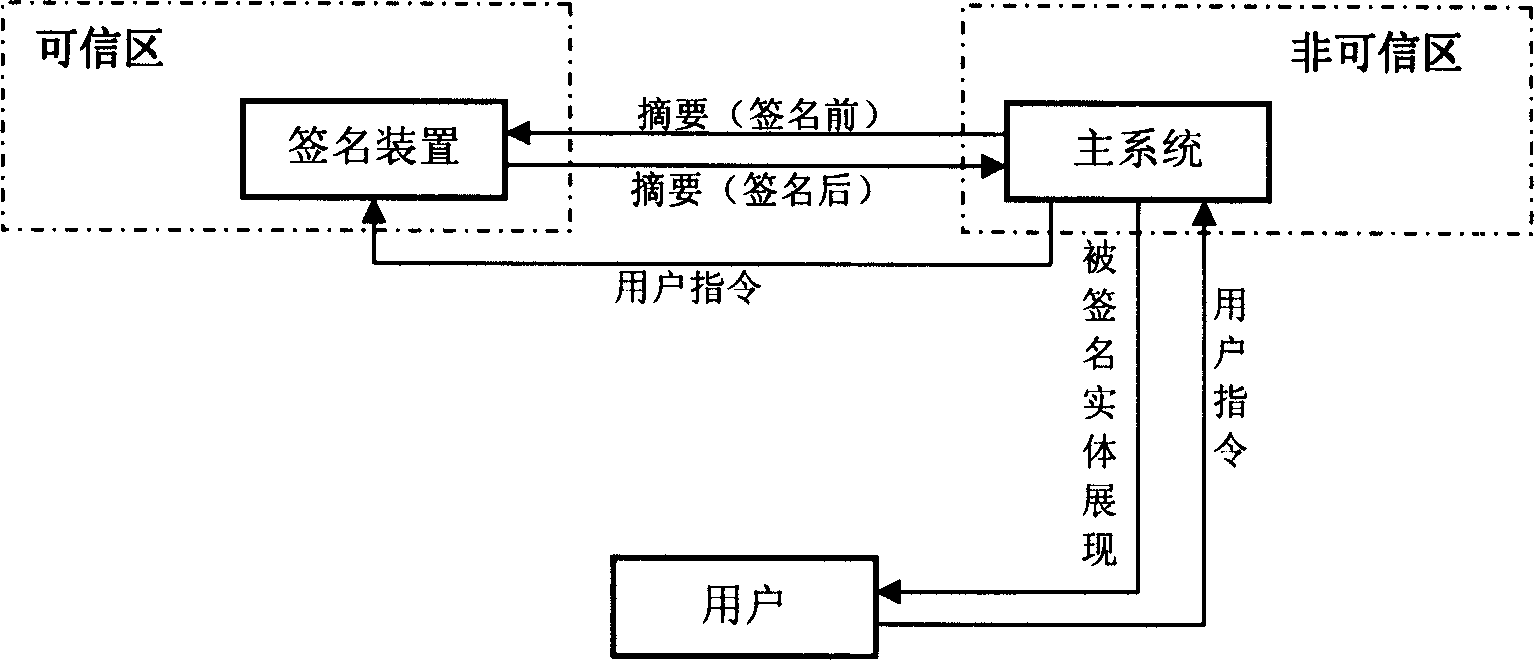
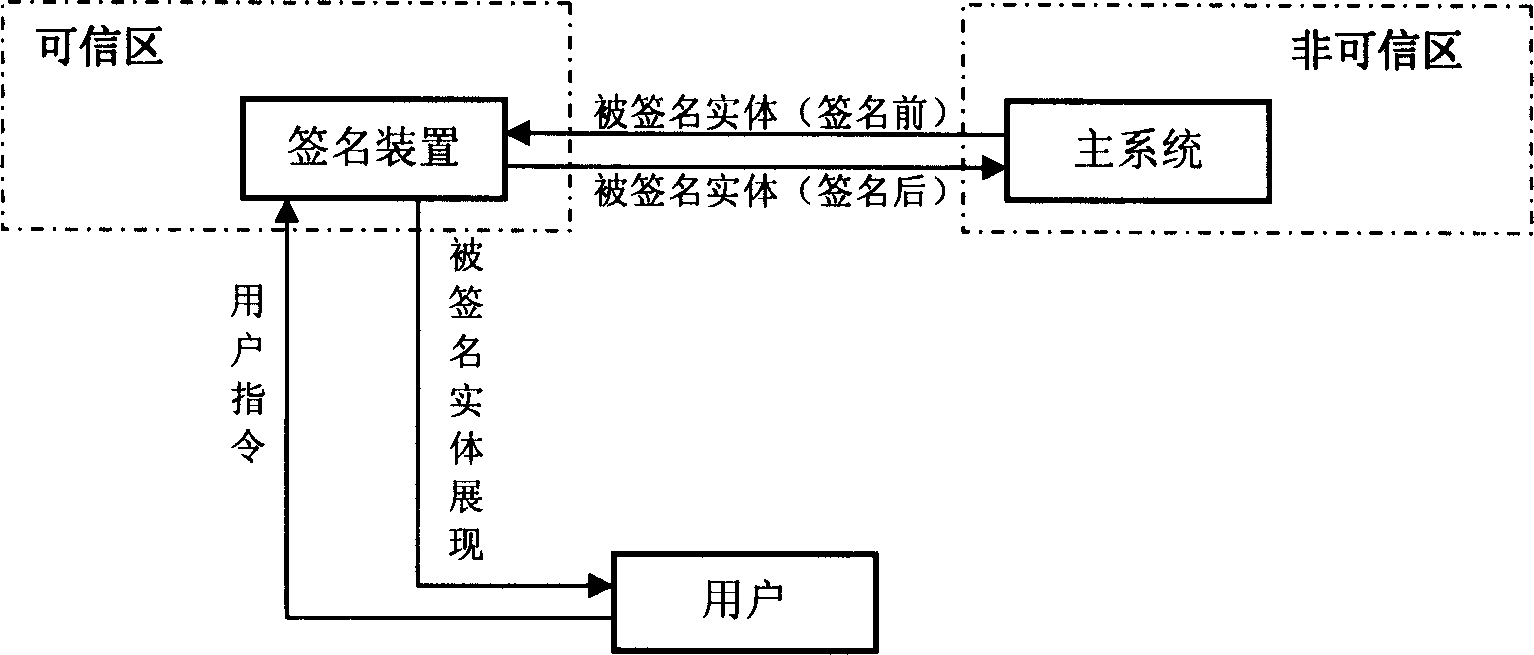
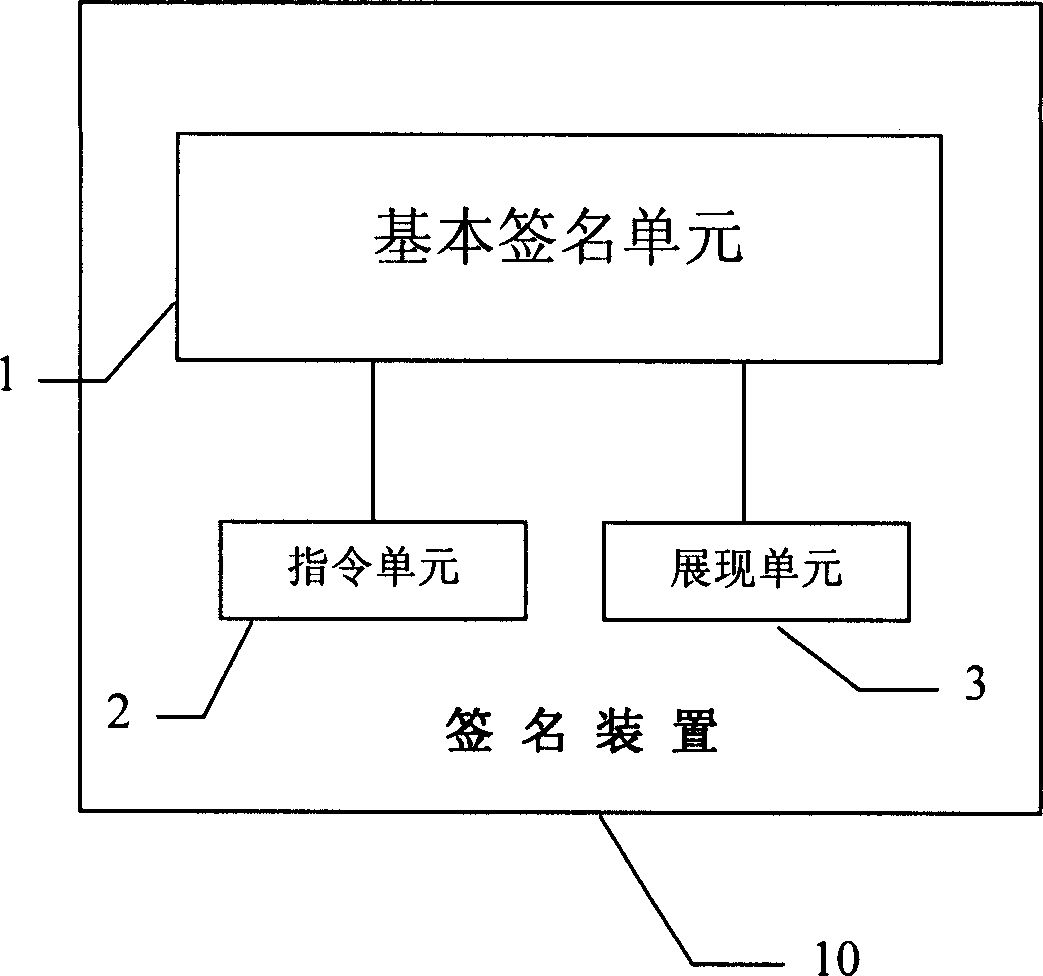
This invention provides a signature device and a method for digital signature, in which, said device includes basic signature unit, which is a digital signature device signing names digitally for signed entities, in which, said device also includes an instruction unit used in receiving instructions of signing or refusing signature and sending said instruction to the basic signature unit, which operates according to the instruction and the sending of the instruction, generation of the abstracts and the display of the signed entity are put up in trust regions completely.
Owner:李代甫
Advertisement media business data credible storage system based on block chain
InactiveCN110022217AProtection securityRealize depositUser identity/authority verificationMarketingTamper resistanceBusiness data
The invention discloses an advertisement media service data credible storage system based on a block chain, which can more comprehensively protect the safety of advertisement media service data. The method comprises the following steps: firstly, selectively encrypting advertisement media business privacy data through a symmetric encryption algorithm; secondly, storing the data in the block chain,permanently storing important data in the chain, meanwhile, ensuring the tamper resistance of the advertisement media service data stored in the chain by combining an elliptic curve algorithm of the block chain, and meanwhile, ensuring the privacy of the advertisement media service privacy data. The method can effectively prevent the advertisement media business data from being tampered, has the advantage of high security, and provides a credible evidence storage method for the advertisement media business data.
Owner:深圳大通实业股份有限公司
A replaceable glass mold bulkhead
The invention discloses a replaceable glass mold bulkhead which comprises a fixed base and a bulkhead core body, wherein the bulkhead core body is arranged at the lower part of the fixed base; a cavity is formed in the middle of the fixed base; the cavity includes a bolt mounting hole extending downwards from the top of the fixed base and a core body matching hole extending upwards from the bottom of the fixed base; two threaded holes are formed in the upper surface of a cylinder; two bolts corresponding to the threaded holes are arranged inside the bolt mounting hole; the bolts penetrate through a kidney-shaped hole and fix the cylinder in the core body matching hole. According to the replaceable glass mold bulkhead provided by the invention, the fixed base is made of cast iron, so that the cost and processing difficulty are low; the bulkhead core body adopts nickel alloy or high-temperature resistant stainless steel, so that the glass mold bulkhead is high in strength and good in durability; in addition, the bulkhead core body can be separated from the fixed base and replaced, so that the production cost is reduced.
Owner:CHANGSHU HONGZHOU MOLD
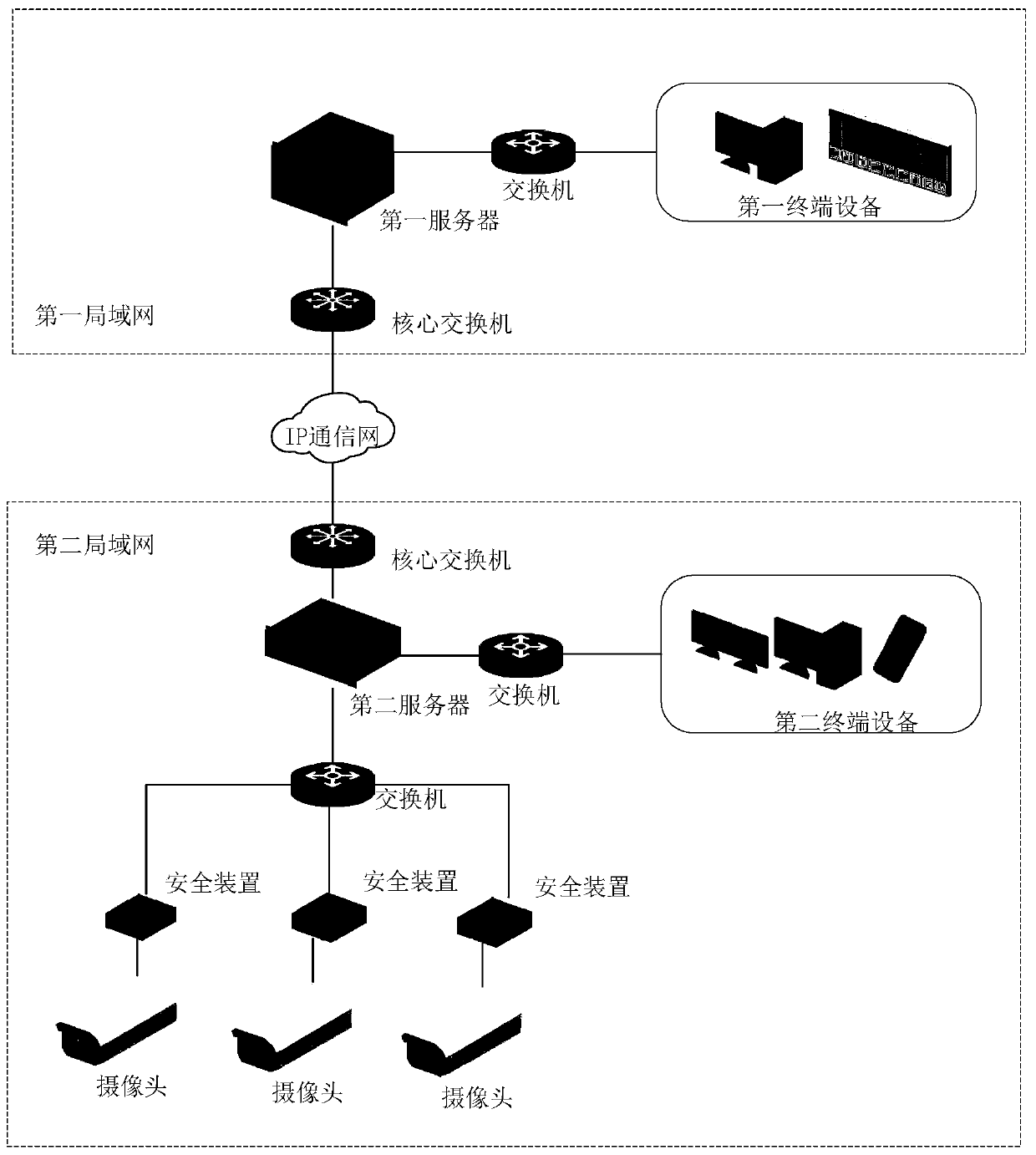
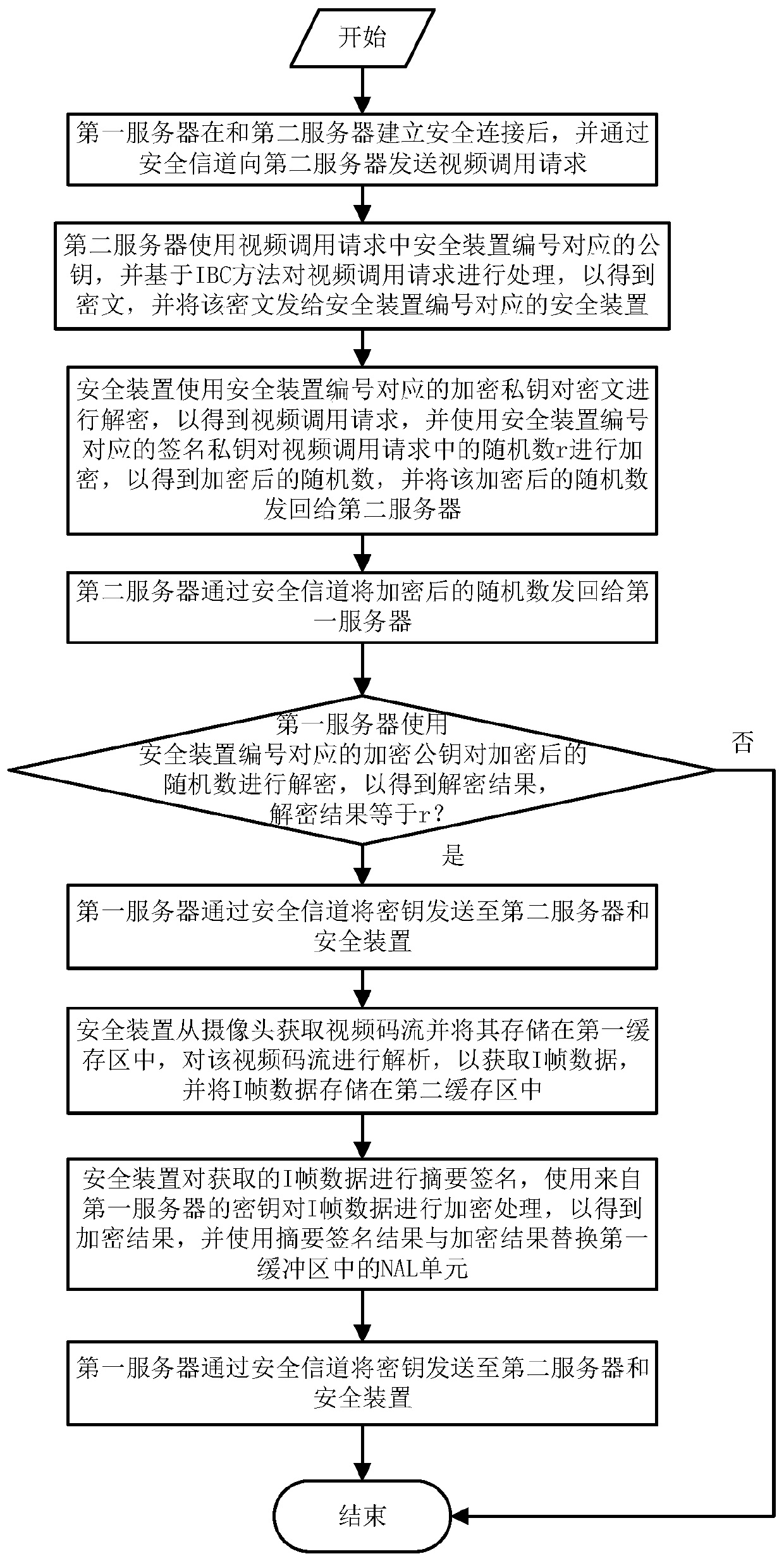
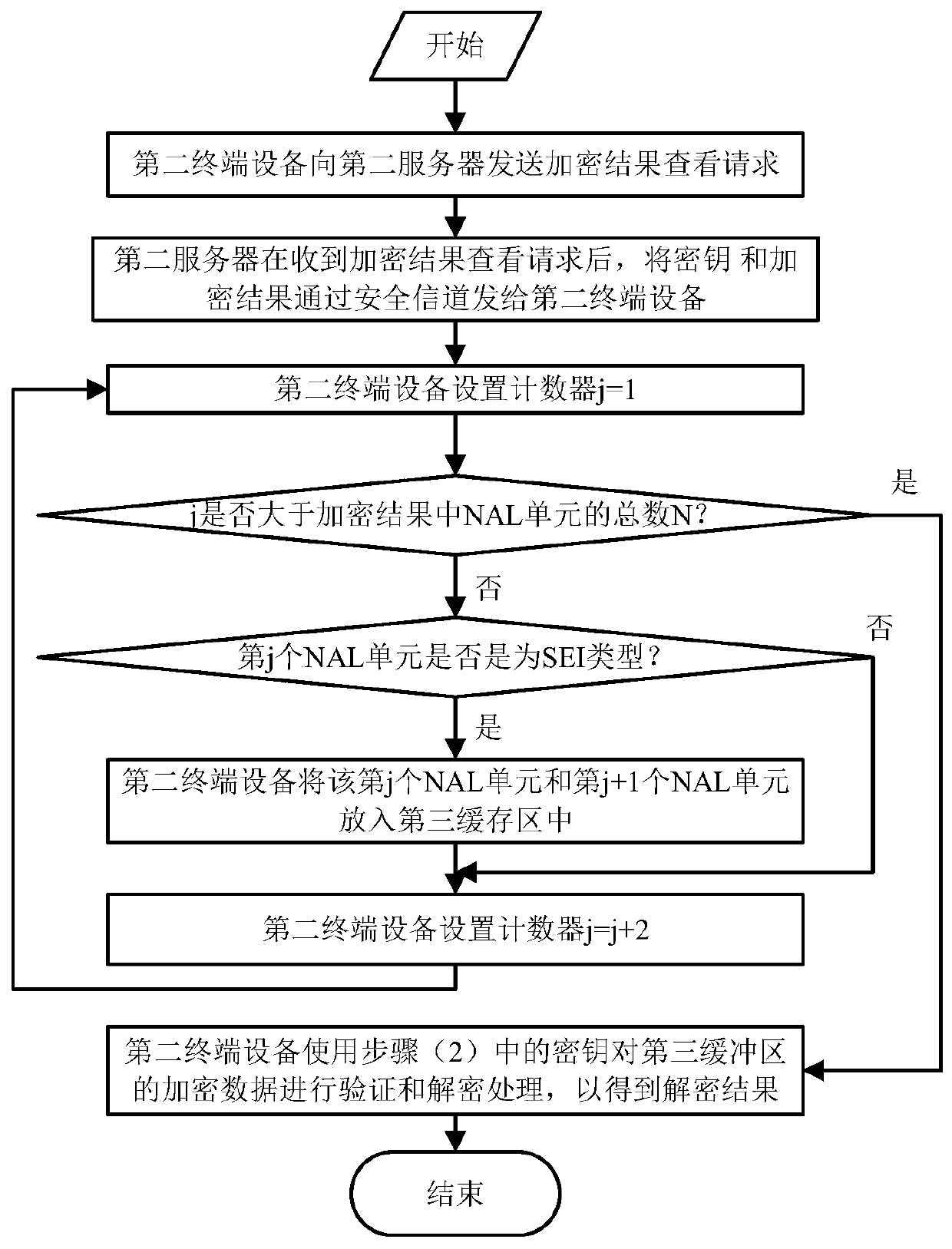
Encryption and decryption method for realizing safe video transmission of power monitoring system
ActiveCN110427762APrevent tamperingAvoid substitutionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesVideo monitoringVideo transmission
The invention discloses an encryption method for realizing safe video transmission of a power monitoring system. The encryption method comprises the following steps: after establishing a secure connection between a first server and a second server, a video calling request is sent to the second server through a secure channel, and the second server uses a public key corresponding to the security device number in the video call request; the video calling request is processed based on an IBC method; consequently, ciphertext can be obtained, and the ciphertext is sent to the safety device corresponding to the safety device number; and the security device decrypts the ciphertext by using an encryption private key corresponding to the security device number to obtain a video call request, encrypts a random number in the video call request by using a signature private key corresponding to the security device number to obtain an encrypted random number, and sends the encrypted random number back to the second server. According to the invention, a security protection mechanism can be designed for the characteristics and security threats of the video monitoring system, so that the security and reliability of the video monitoring system are ensured.
Owner:湖南匡安网络技术有限公司
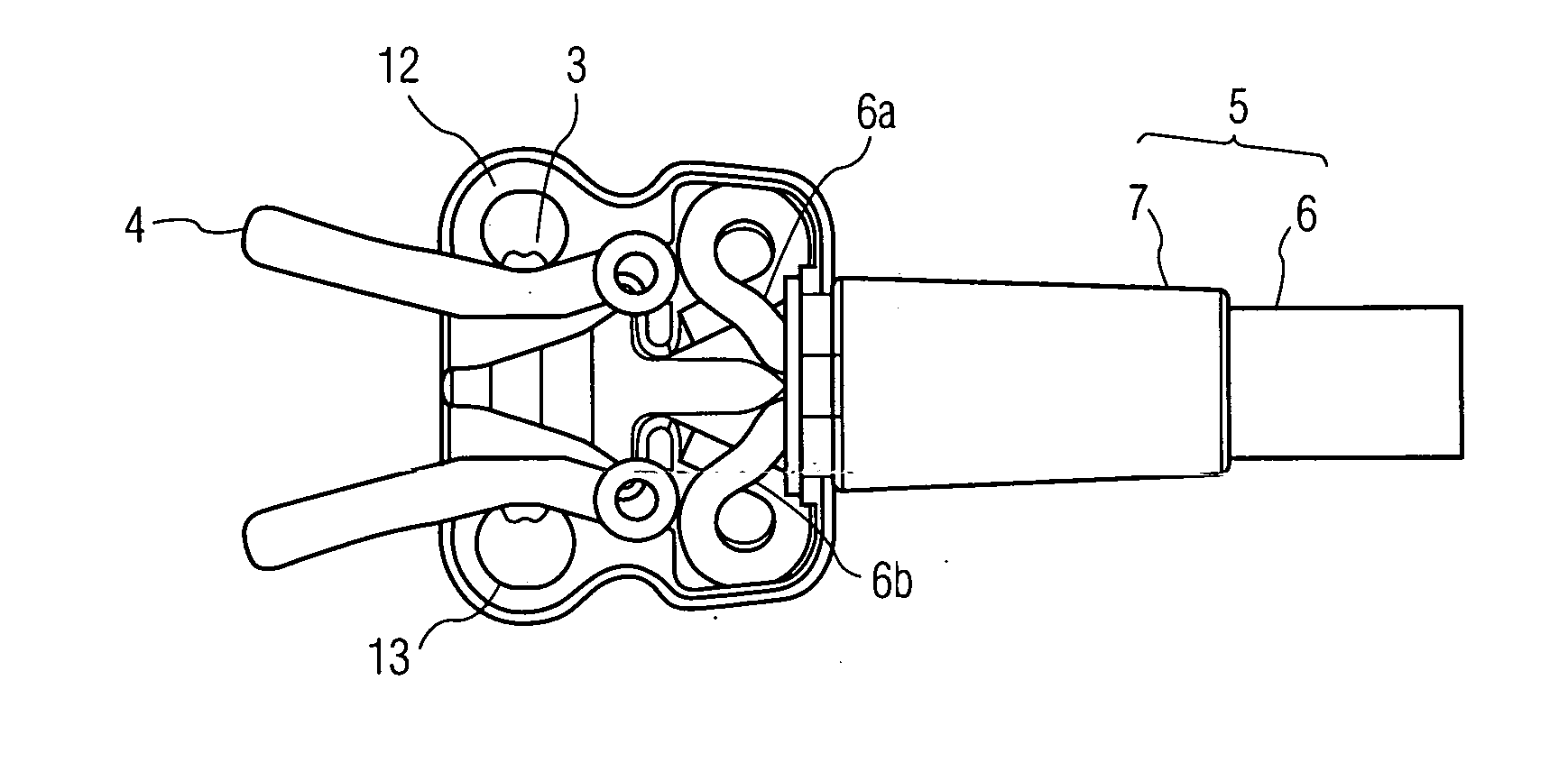
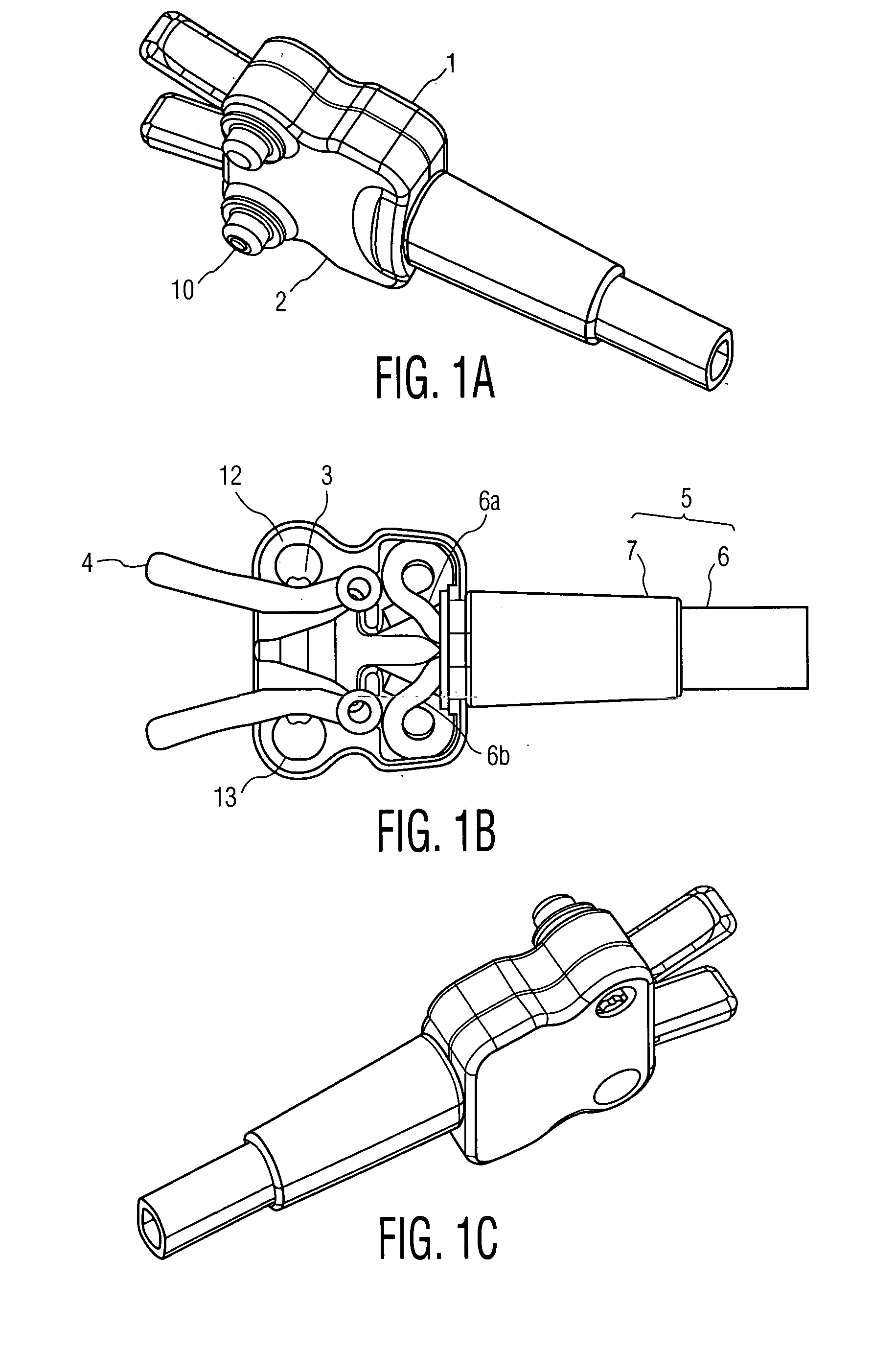
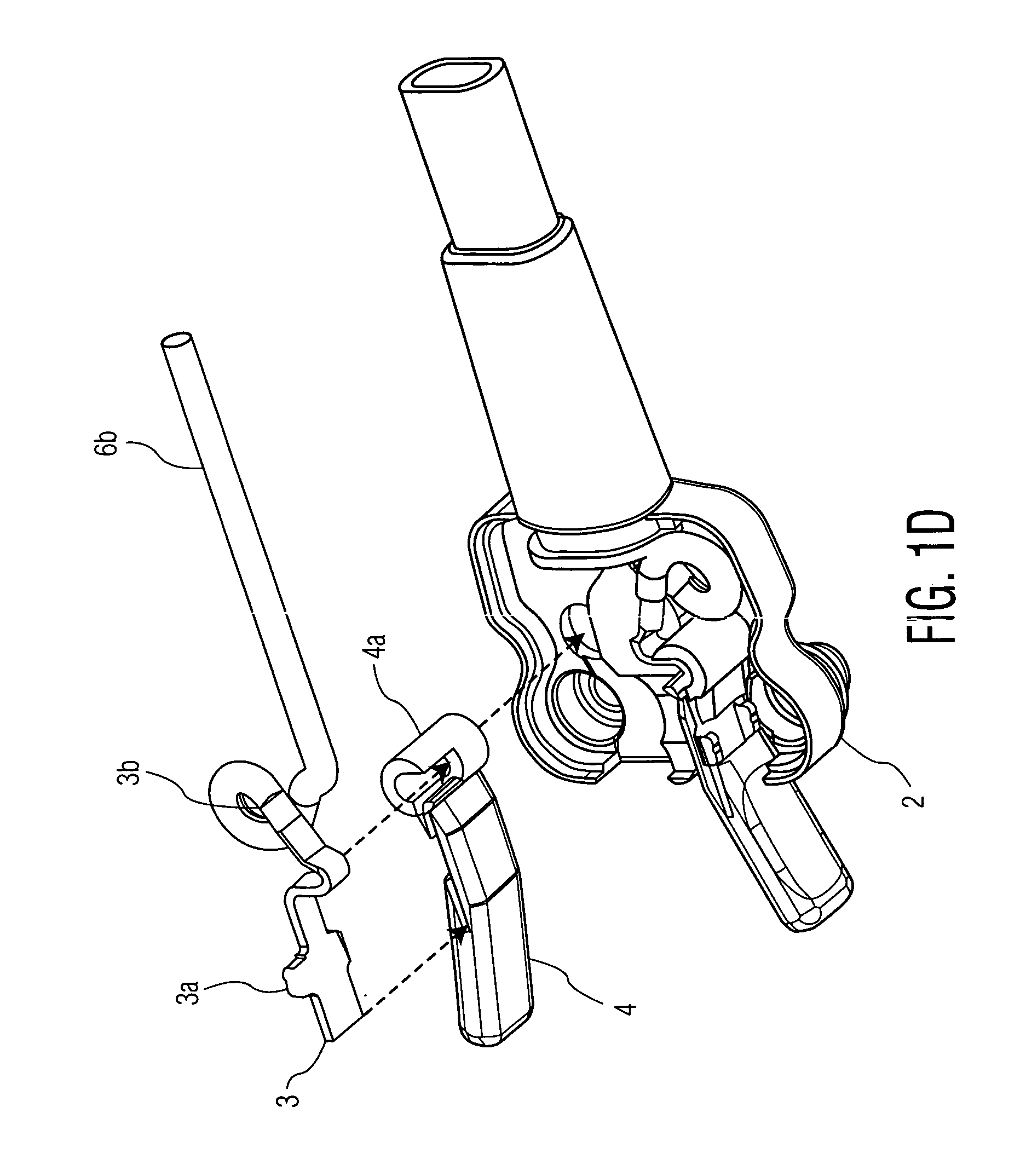
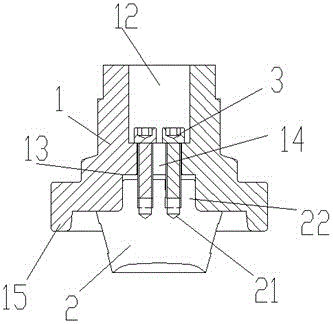
Battery connector and method for mounting it on battery
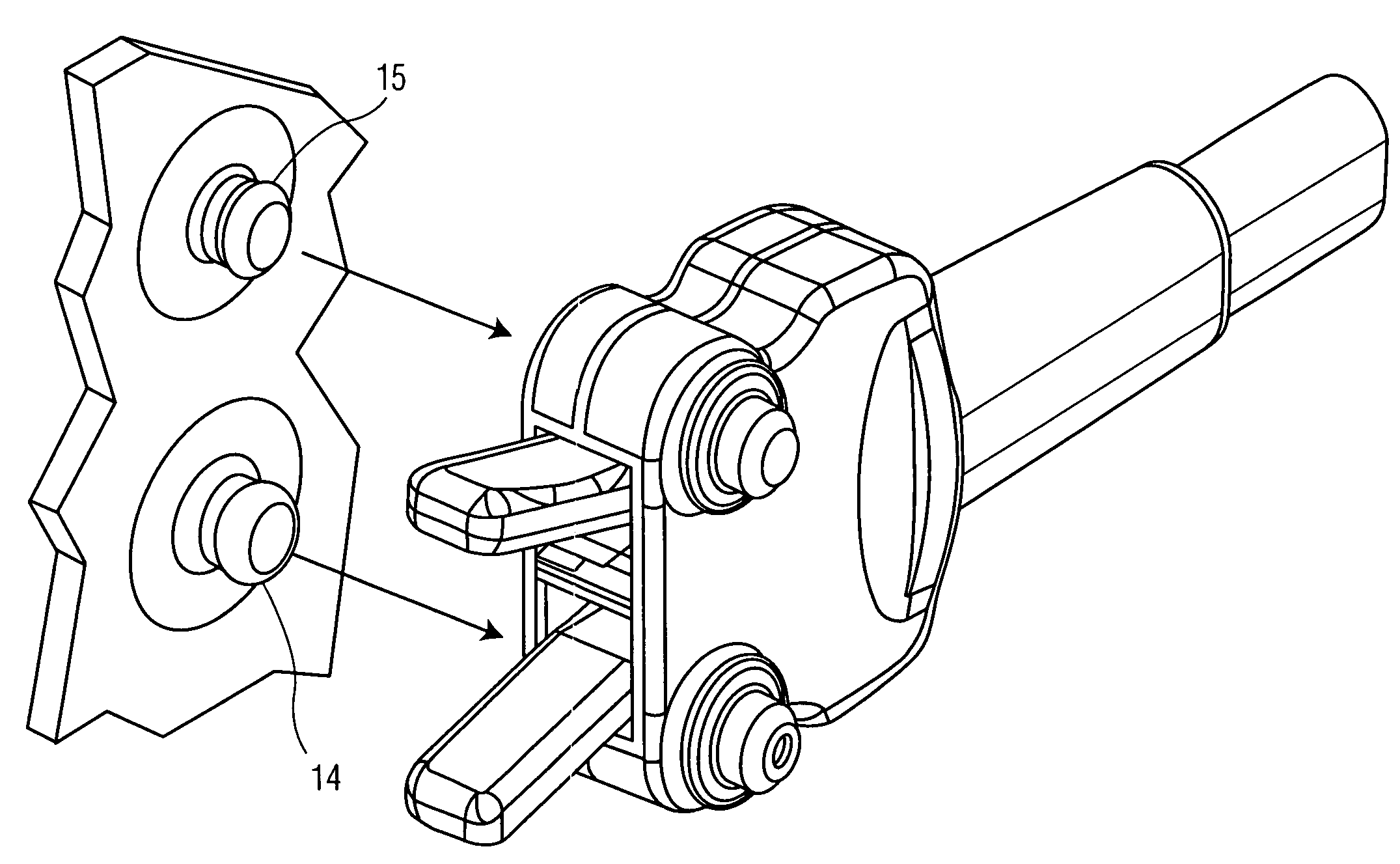
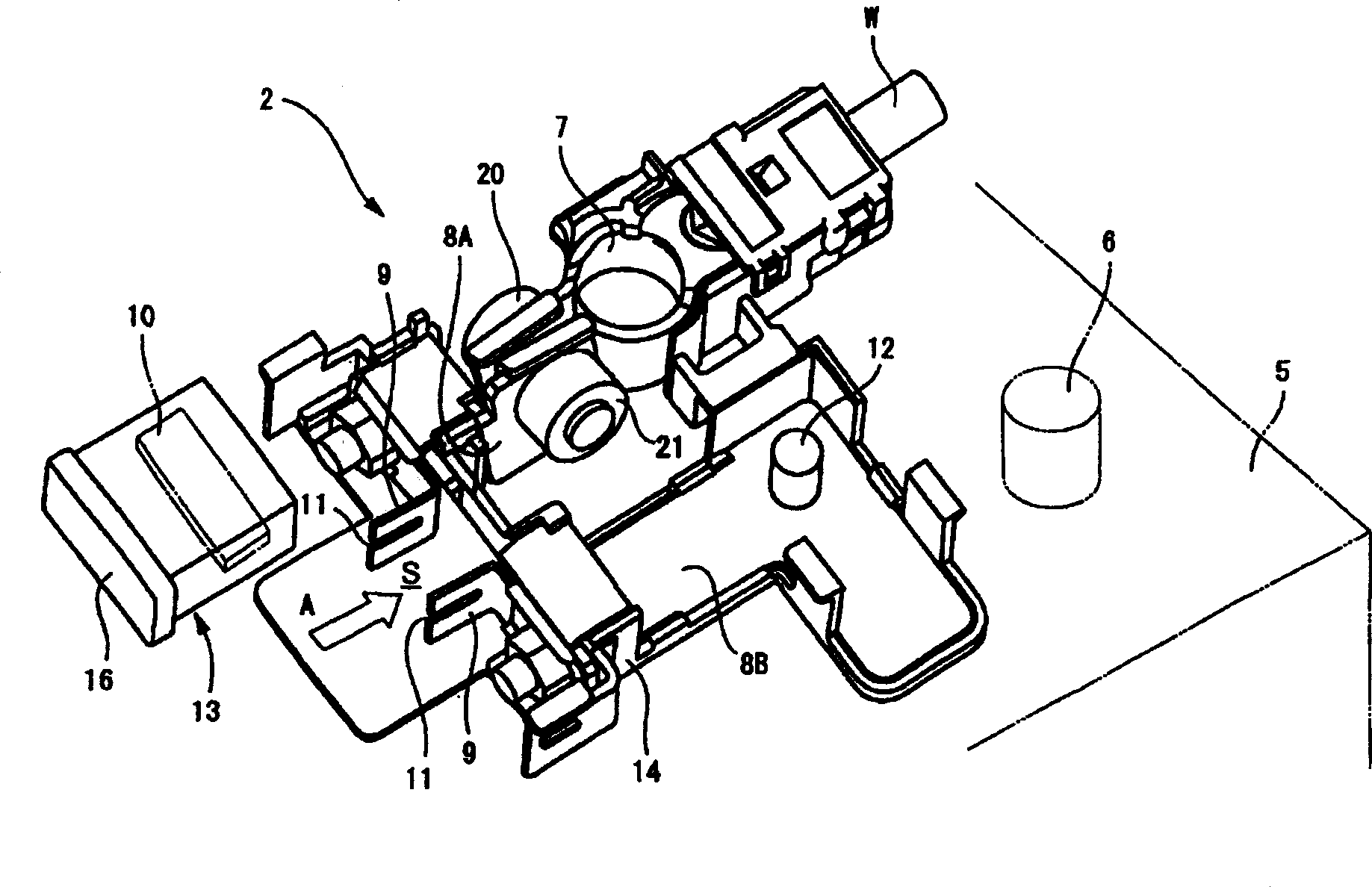
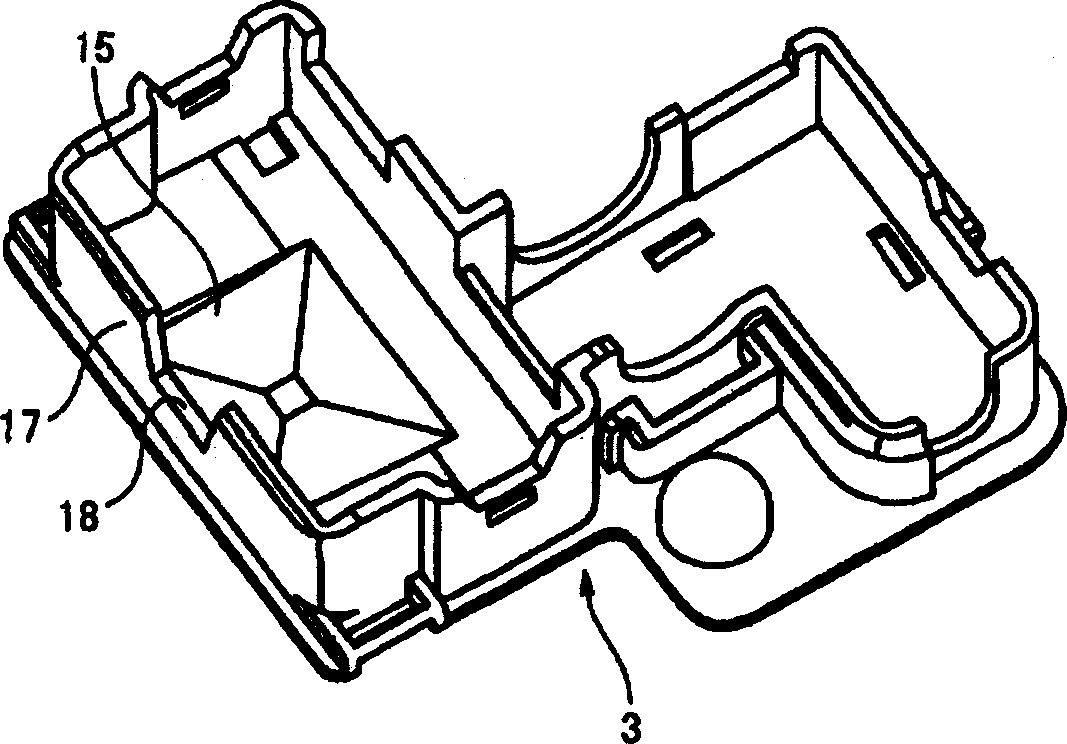
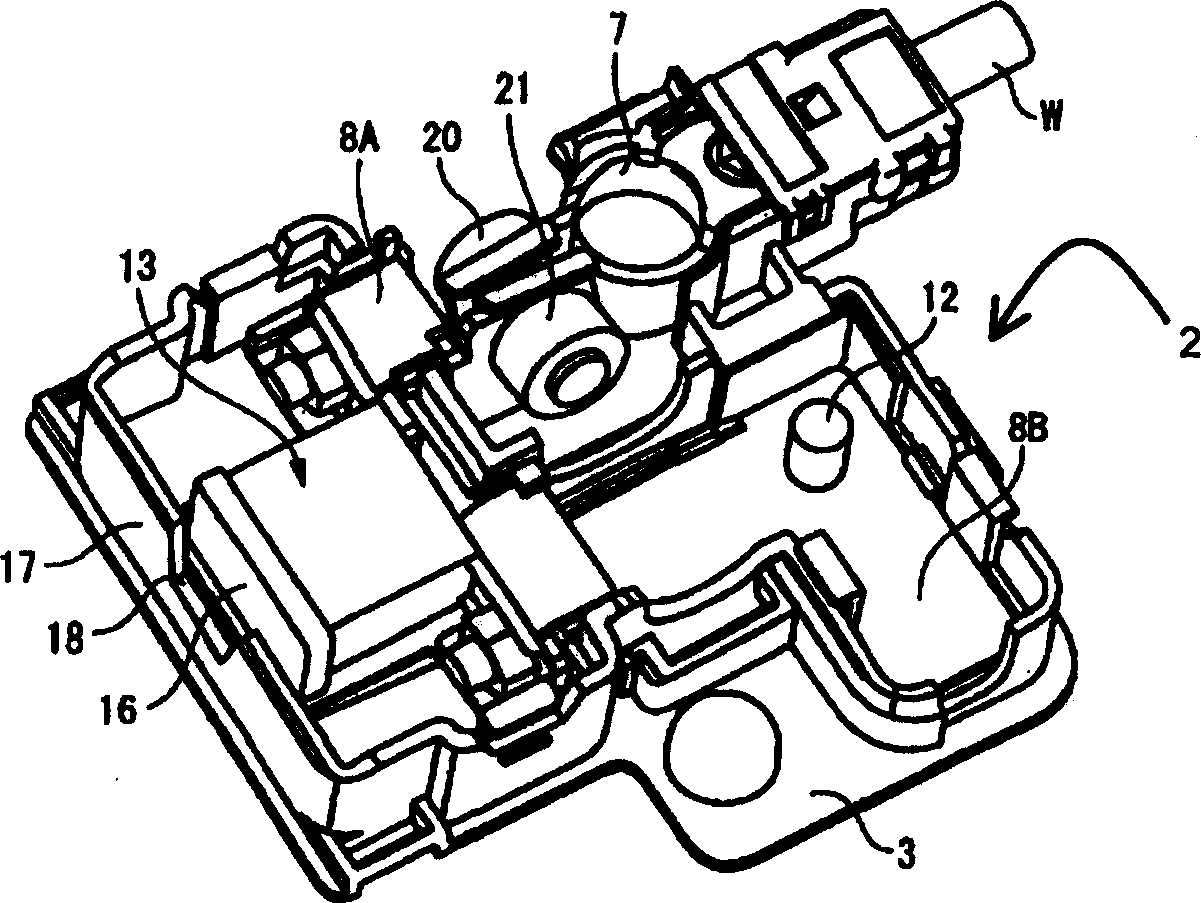
A battery-connecting member (1) has a base (2) for accommodating a fuse (10) and a casing (3) for accommodating the base (2). The base (2) includes a battery terminal (7), busbars (8A, 8B) and the fuse (10). A box-accommodating portion (15) is provided in the casing (3) for accommodating the fuse (10) and is provided with an operation space closing portion (17) at a side toward which the fuse (10) is detached. Thus, the fuse (10) cannot be detached unless the battery-connecting member (1) is detached from a battery (5) and the casing (3) and the base (2) are separated.
Owner:SUMITOMO WIRING SYST LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com