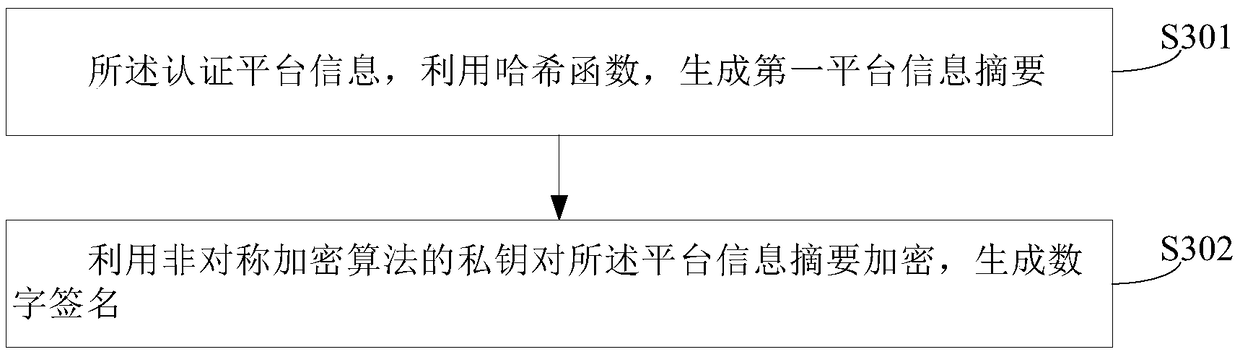
Patents
Literature
73results about How to "Prevent Malicious Use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
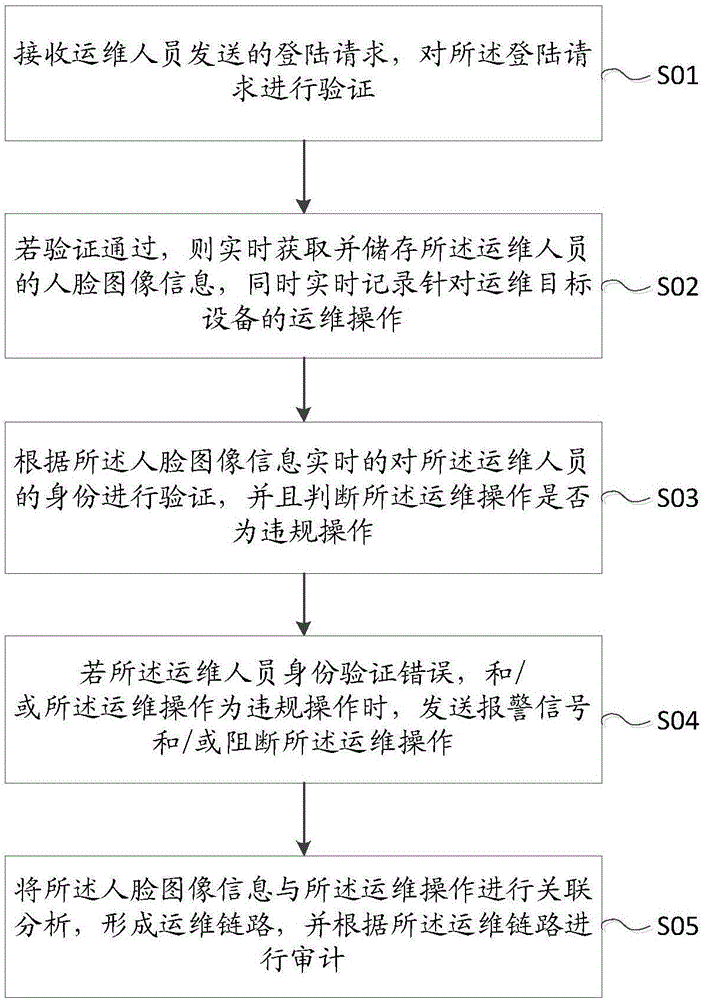
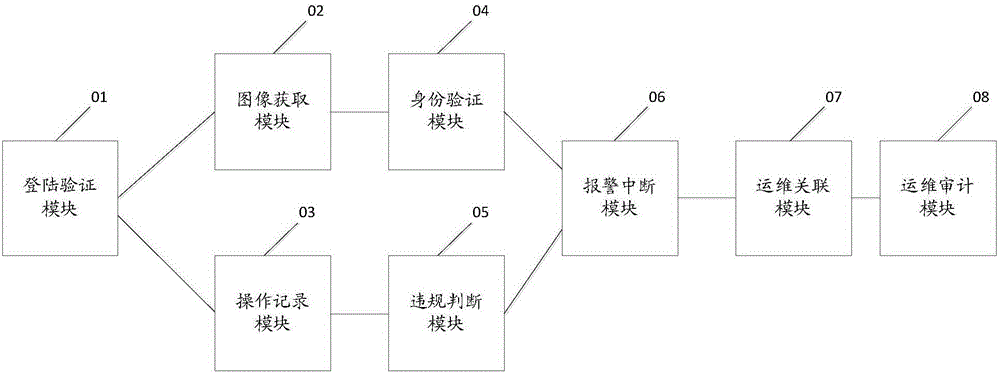
Operation and maintenance safety auditing method and system
InactiveCN106330919AAvoid substitutionGuarantee authenticityCharacter and pattern recognitionTransmissionCorrelation analysisComputer science
The invention discloses an operation and maintenance safety auditing method. The operation and maintenance safety auditing method comprises the following steps: receiving a login request sent by operation and maintenance personnel, and verifying the login request; if the verification is passed, obtaining and storing face image information of the operation and maintenance personnel in real time, and meanwhile recording an operation and maintenance operation on operation and maintenance target equipment in real time; verifying the identity of the operation and maintenance personnel in real time according to the face image information, and judging whether the operation and maintenance operation is an illegal operation; if the verification of the identity of the operation and maintenance personnel is wrong, and / or the operation and maintenance operation is the illegal operation, sending an alarm signal and / or interrupting the operation and maintenance operation; and carrying out correlation analysis on the face image information and the operation and maintenance operation, forming an operation and maintenance link, and carrying out audit according to the operation and maintenance link. Identity authentication can be carried out on the identity of the IT operation and maintenance personnel in an operation and maintenance personnel process, and the illegal operation and maintenance operation can be found in time. The invention further discloses an operation and maintenance safety auditing system.
Owner:STATE GRID CORP OF CHINA +2
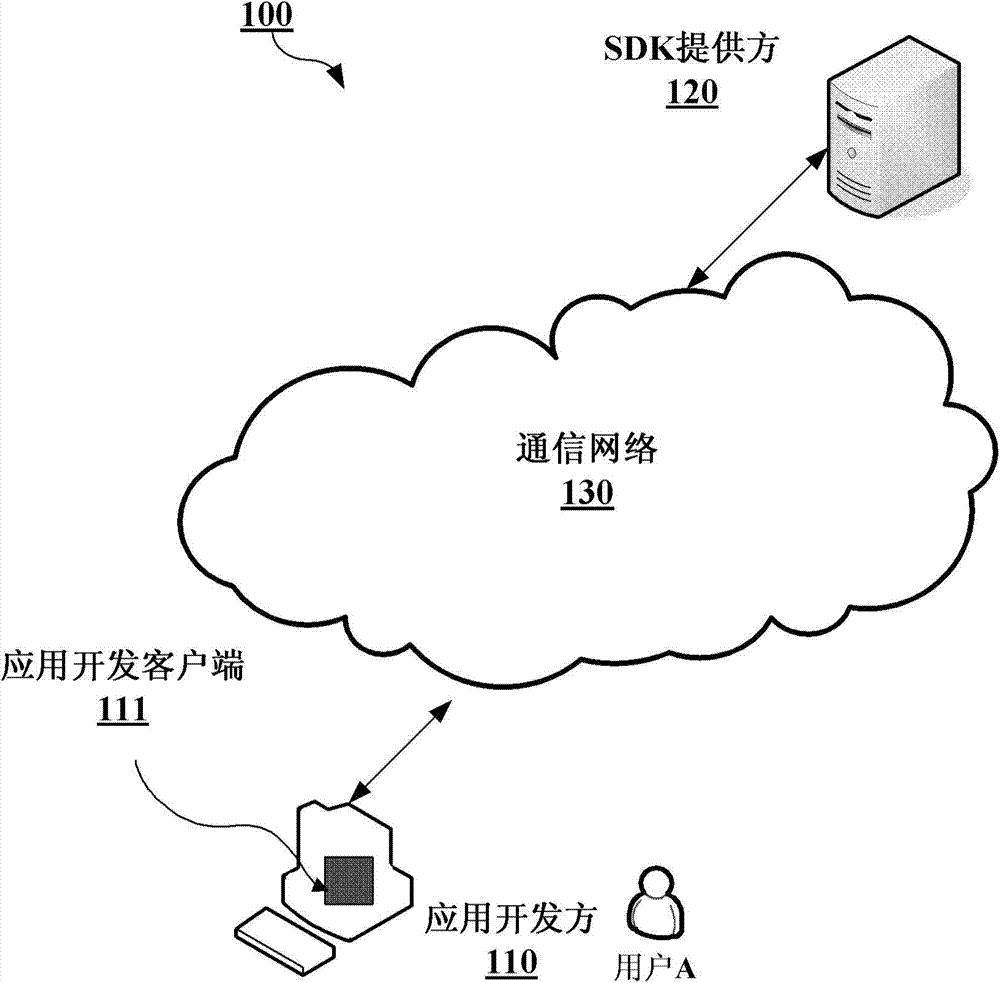
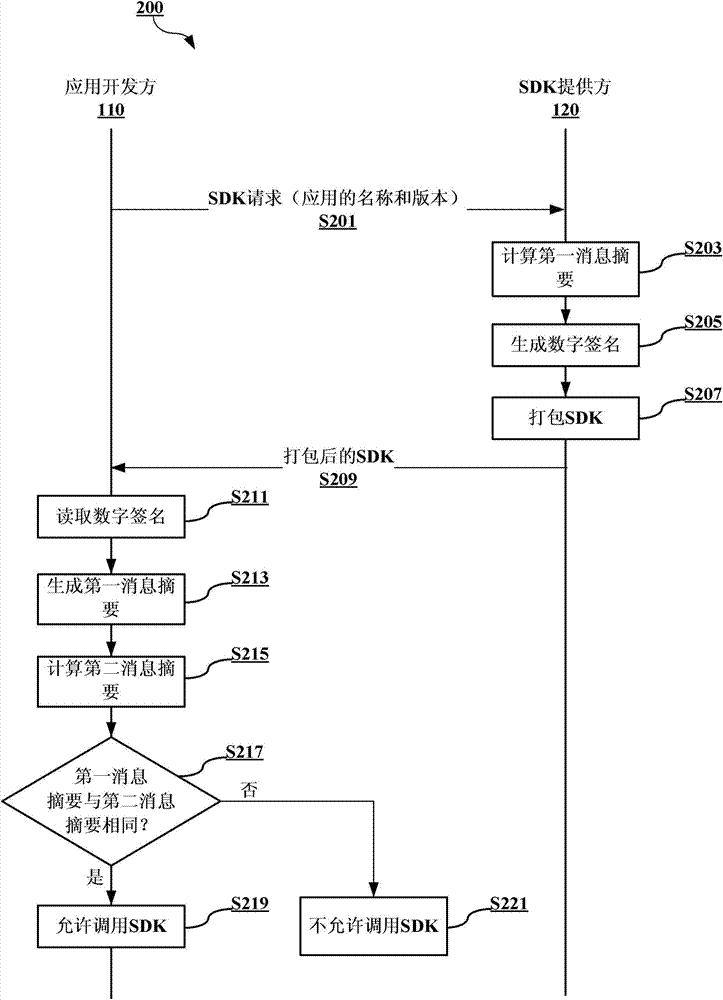
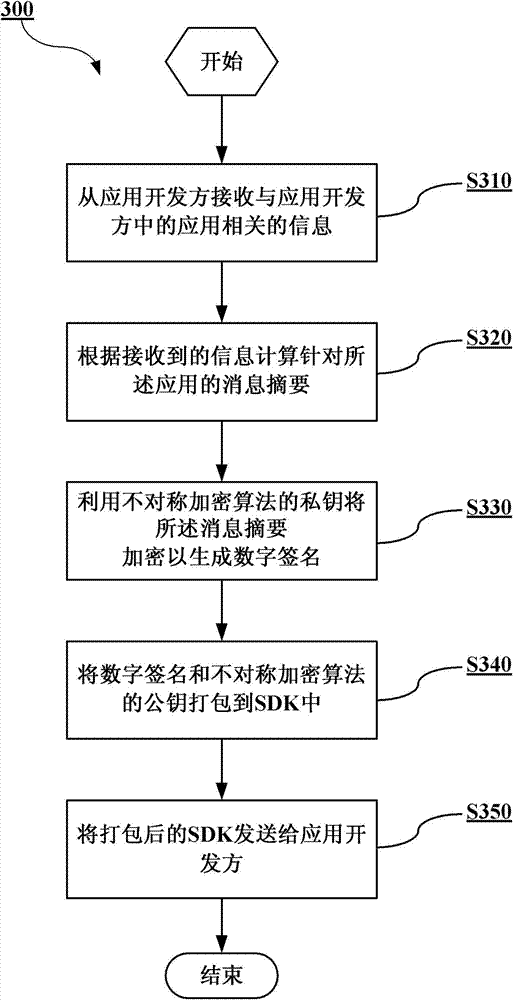
SDK providing and invoking method and associated device
InactiveCN103617394APrevent Malicious UseDigital data protectionPlatform integrity maintainanceDigital signatureSoftware development
The invention provides a software development kit SDK providing method and a device. An SDK is provided by an SDK providing direction application developer. The method comprises the following steps of receiving information related to application of the application developer from the application developer; calculating information abstract on the application according to received information; utilizing a private key of a symmetric encryption algorithm to encrypt the information abstract so as to generate a digital signature; packing the digital signature and a public key of the symmetric encryption algorithm into the SDK; sending the packed SDK to the application developer for SDK invoking by the application. The invention further provides an SDK invoking method and a device.
Owner:BEIJING NETQIN TECH
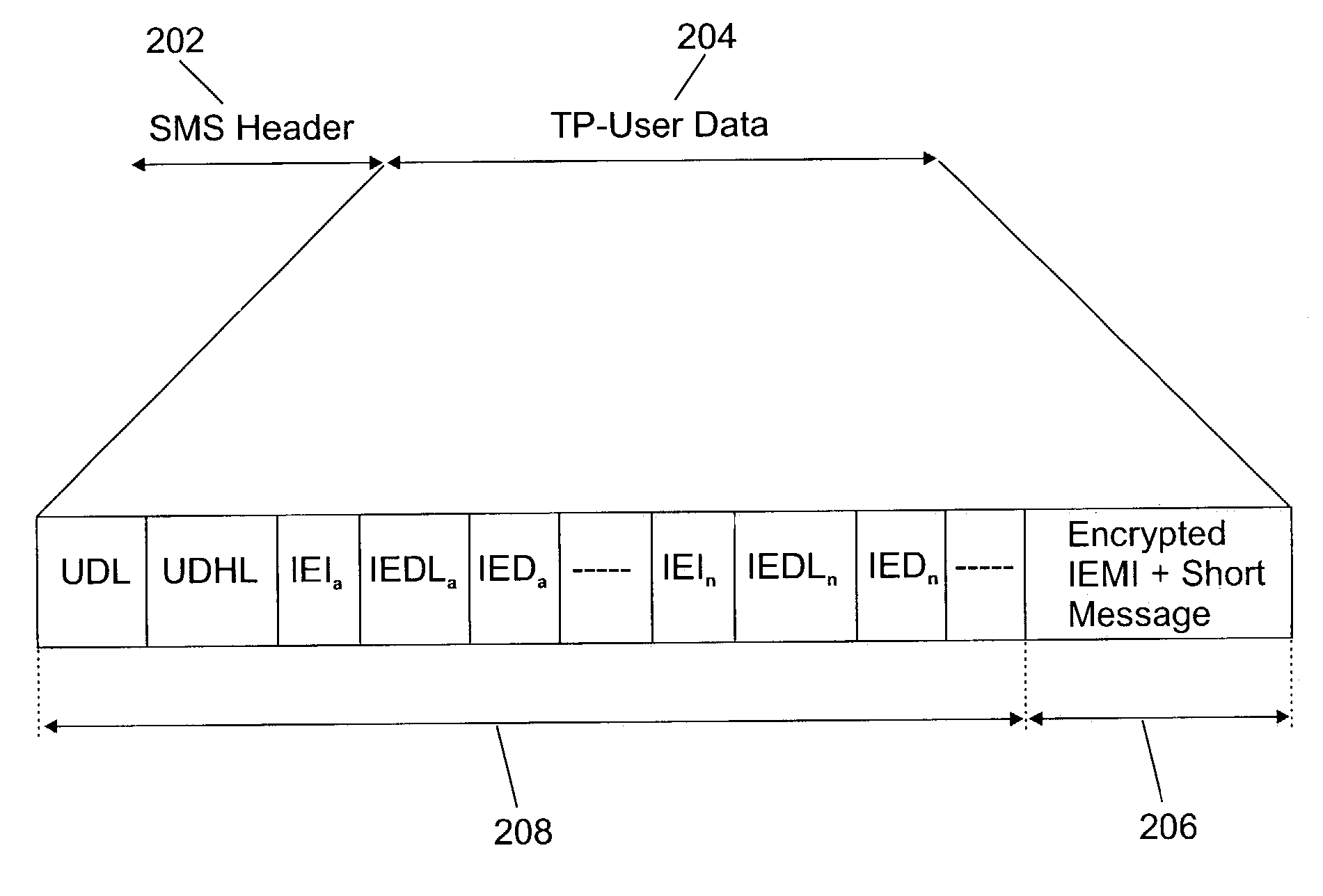
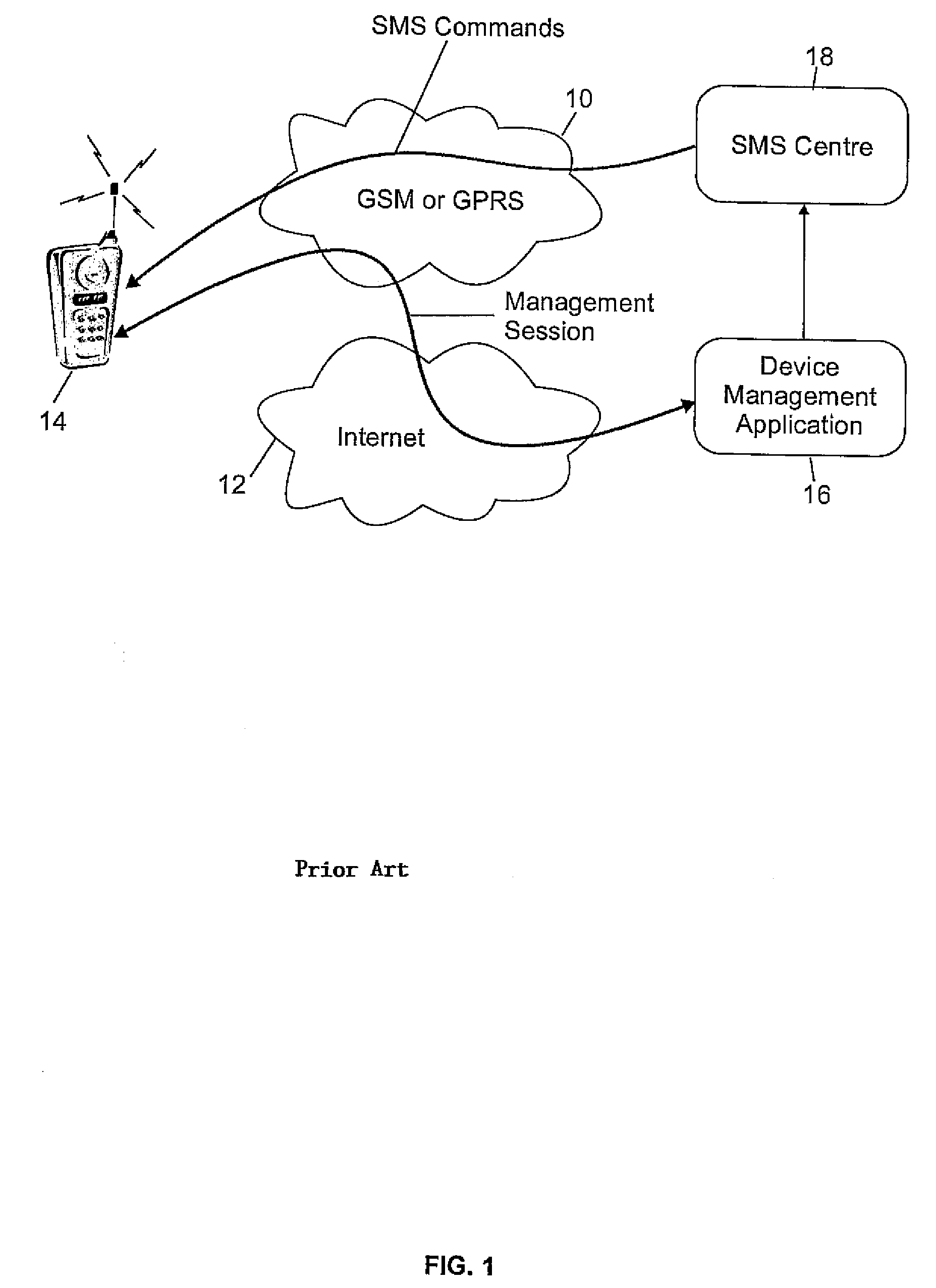
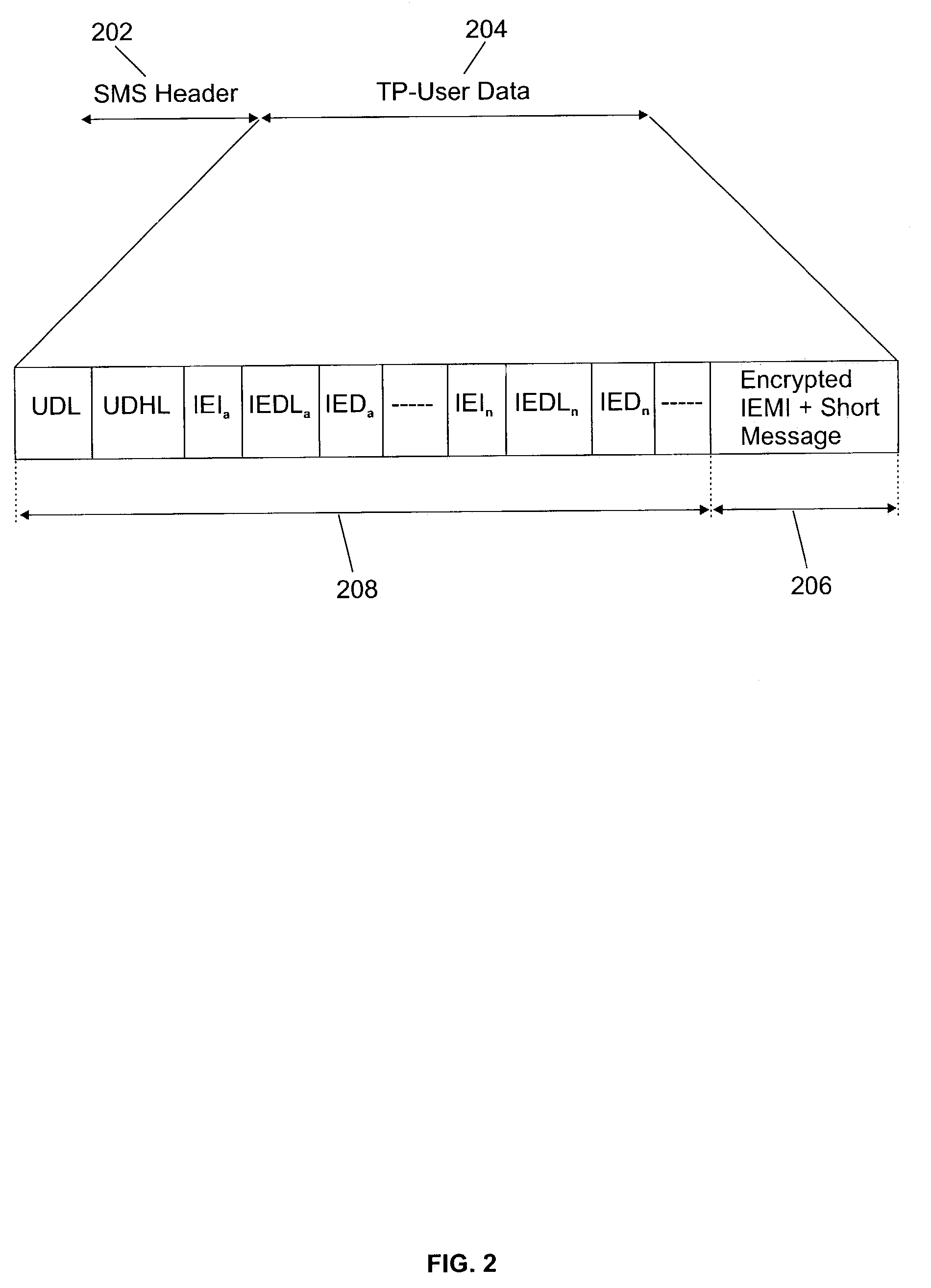
System and method for SMS authentication
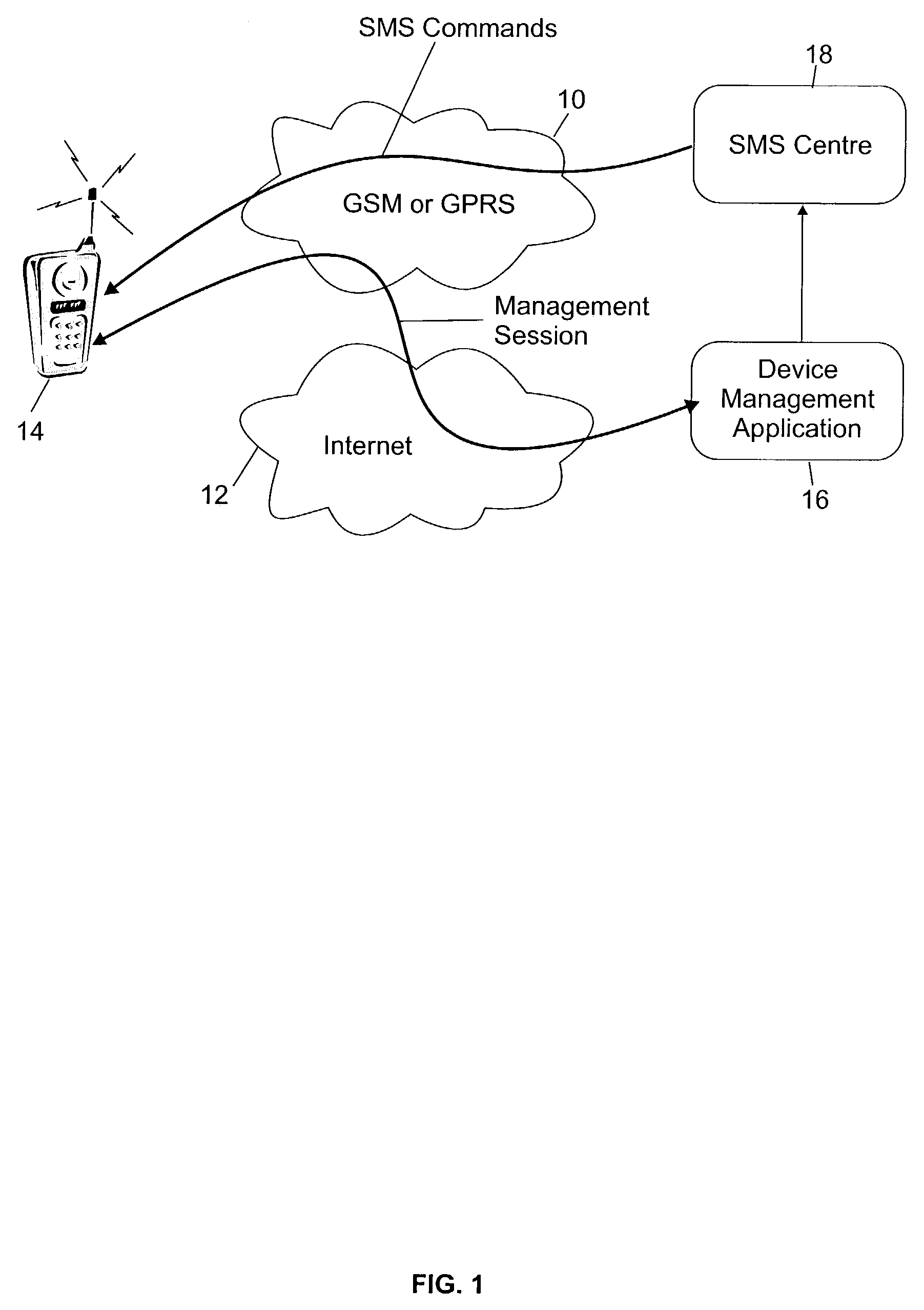
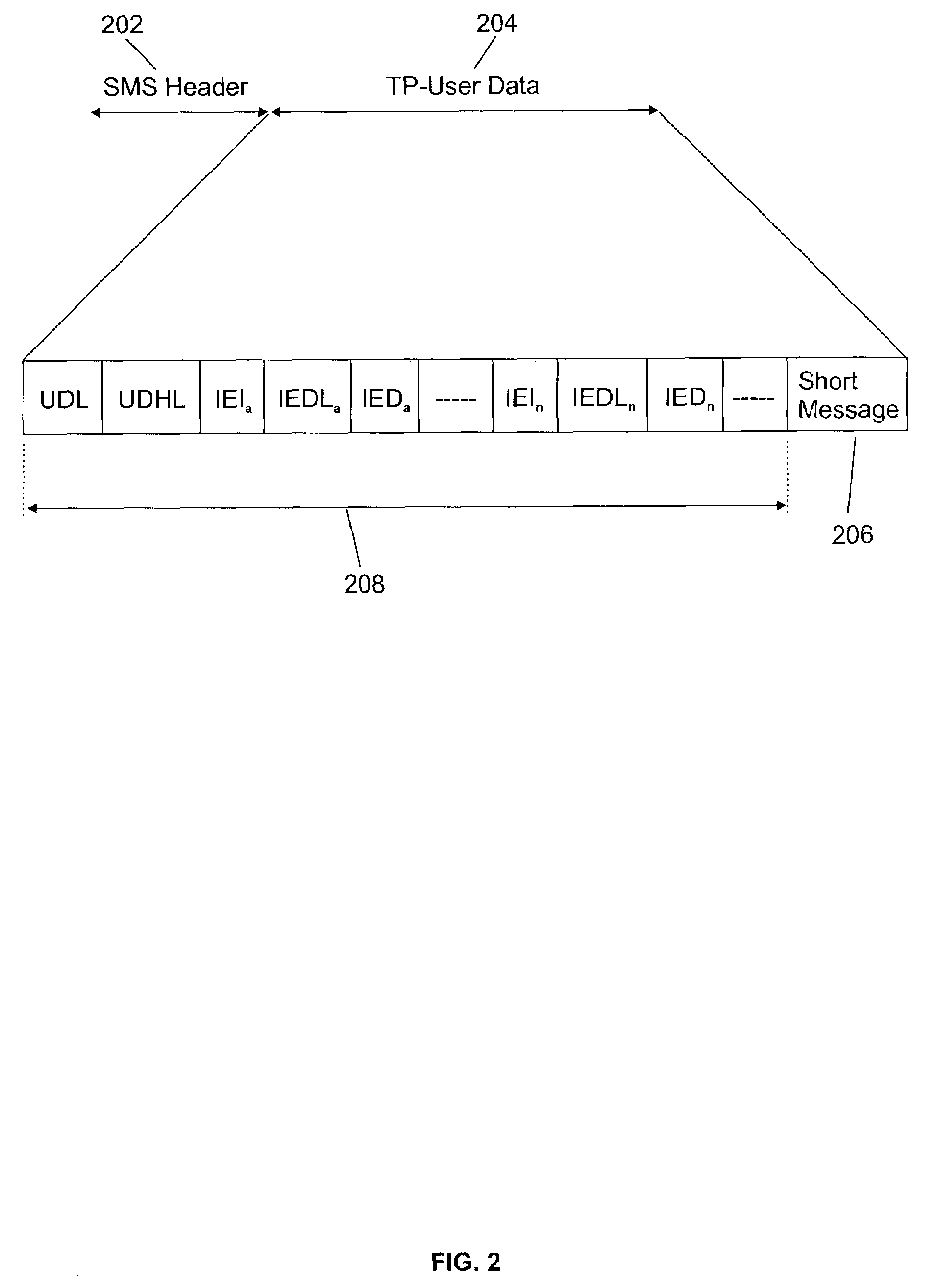
ActiveUS7296156B2Easy to usePrevent Malicious UseKey distribution for secure communicationUser identity/authority verificationProcess configurationKey generation
The disclosed invention allows security of configuration SMS messages through the use of encryption computed with the International Mobile Equipment Identity (IMEI) as a key. Particularly, a text messaging system having the ability to send SMS messages to remotely managed wireless terminal equipment comprises means to generate an encrypted bit string based on the IMEI shared key and to signal use of the security mechanism in available Information Element fields of the TP-User Data of the SMS message. The receiving wireless terminal equipment is configured to process configuration SMS messages encrypted using the IMEI as a key.
Owner:TREND MICRO INC
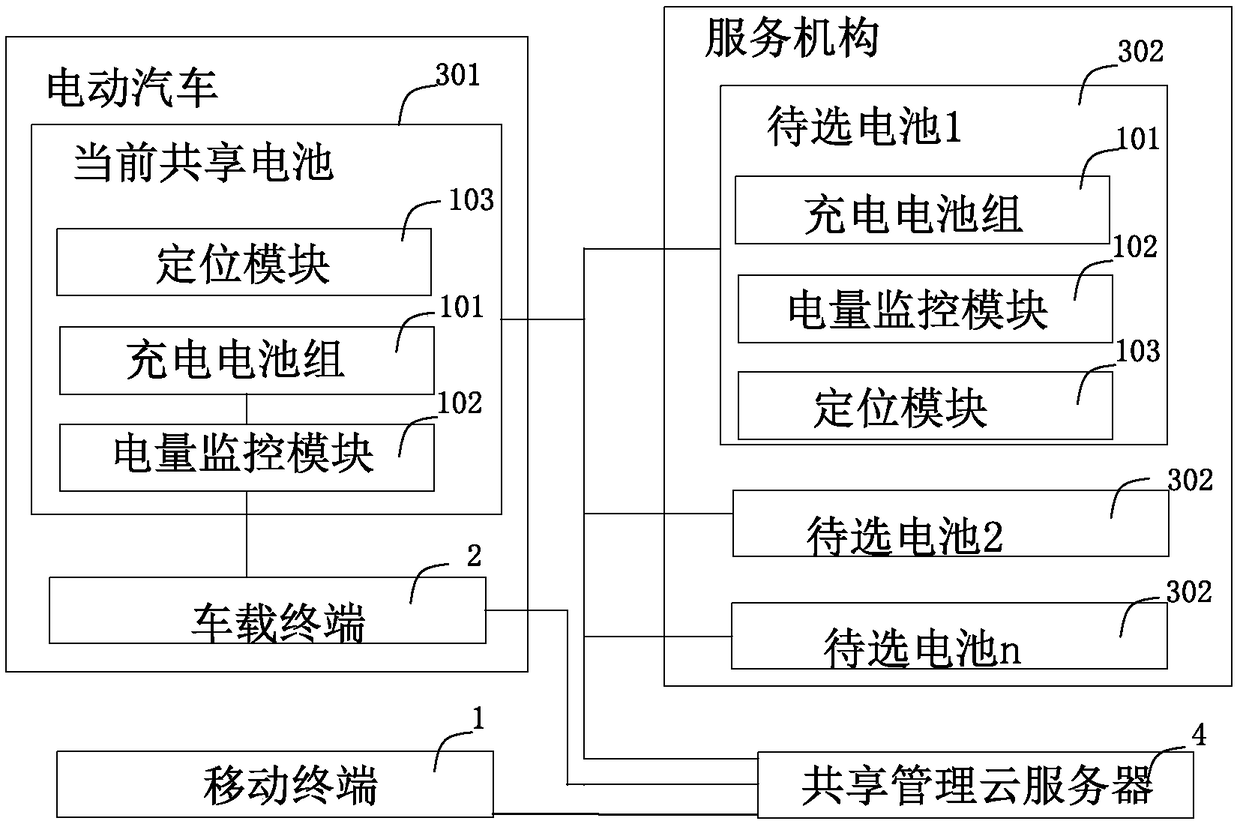
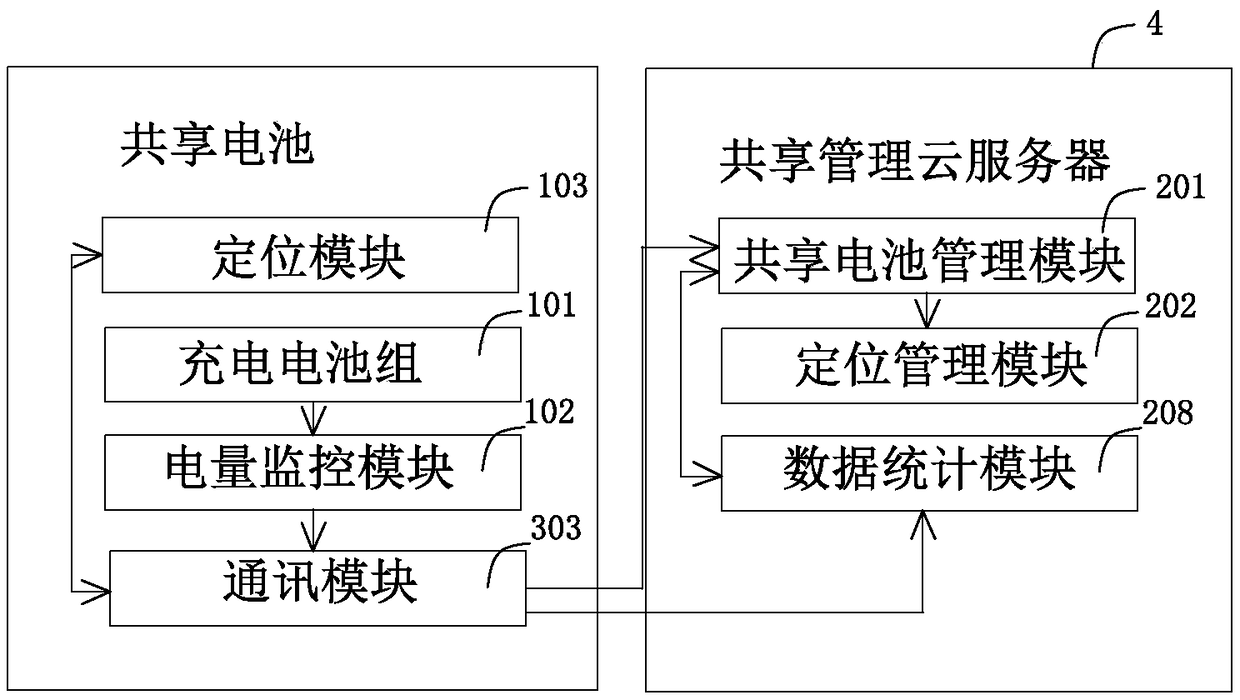
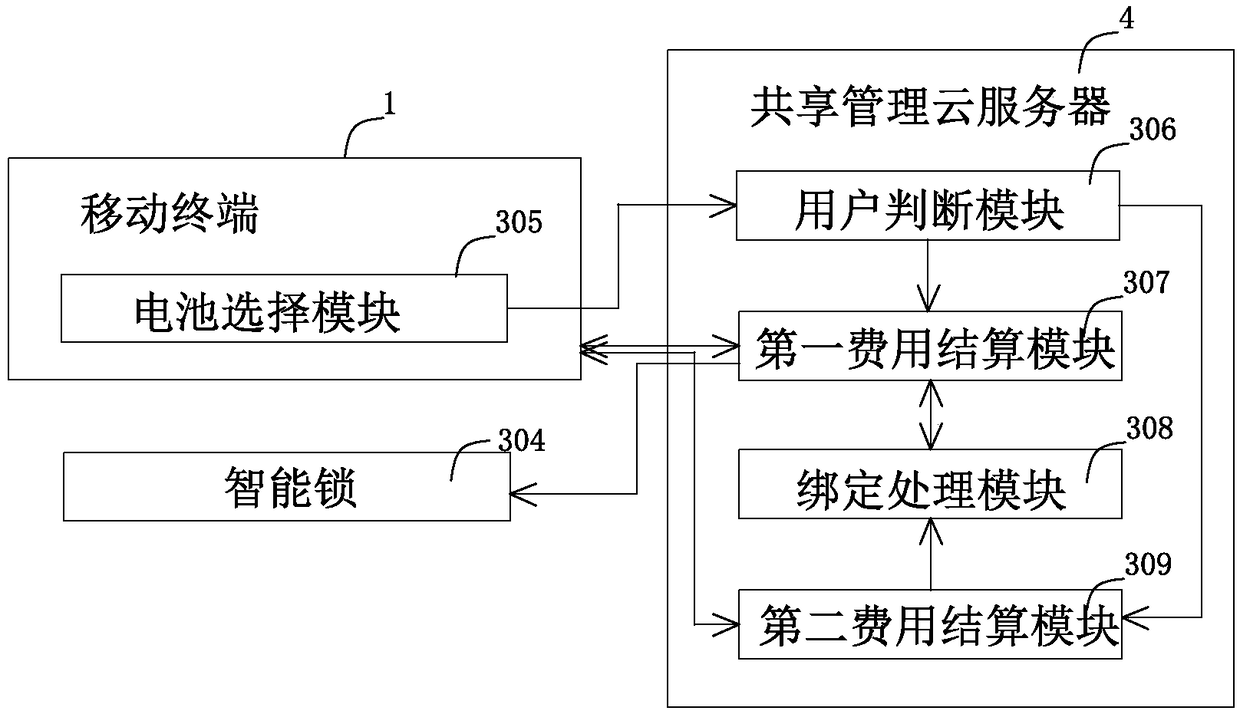
Electric automobile battery sharing system
ActiveCN108629663AGood for healthImprove stabilityCharging stationsReservationsAutomotive batteryElectrical battery
The invention relates to an electric automobile battery sharing system and a sharing method. The electric automobile battery sharing system comprises a mobile terminal, a vehicle-mounted terminal, a shared battery and a battery service platform. The battery service platform comprises a plurality of service mechanisms and a shared management cloud server. The shared battery comprises an electric quantity monitoring module. The electric quantity monitoring module is used for monitoring the electric quantity of a rechargeable battery pack located in an electric automobile and is in communicationwith the vehicle-mounted terminal. The vehicle-mounted terminal receives the residual electric quantity A of the battery. When the residual electric quantity A of the battery reaches a threshold valueA1, the vehicle-mounted terminal automatically searches pre-selected service mechanisms which can arrive before the electric quantity of the battery is exhausted. Meanwhile, a list of the selected pre-selected service mechanisms is formed and displayed by the vehicle-mounted terminal. When the number B of searched pre-selected service mechanisms is smaller than a preset threshold value B1, the vehicle-mounted terminal sends out the alarm information. According to the invention, by adopting the electric automobile battery sharing system and the sharing method thereof, the shared battery is monitored, and the driving state of a user is fully considered. Therefore, more reasonable selectable service mechanism recommendations can be provided for the user, and a better user experience is provided for the user.
Owner:北京安泰创业新能源科技有限公司
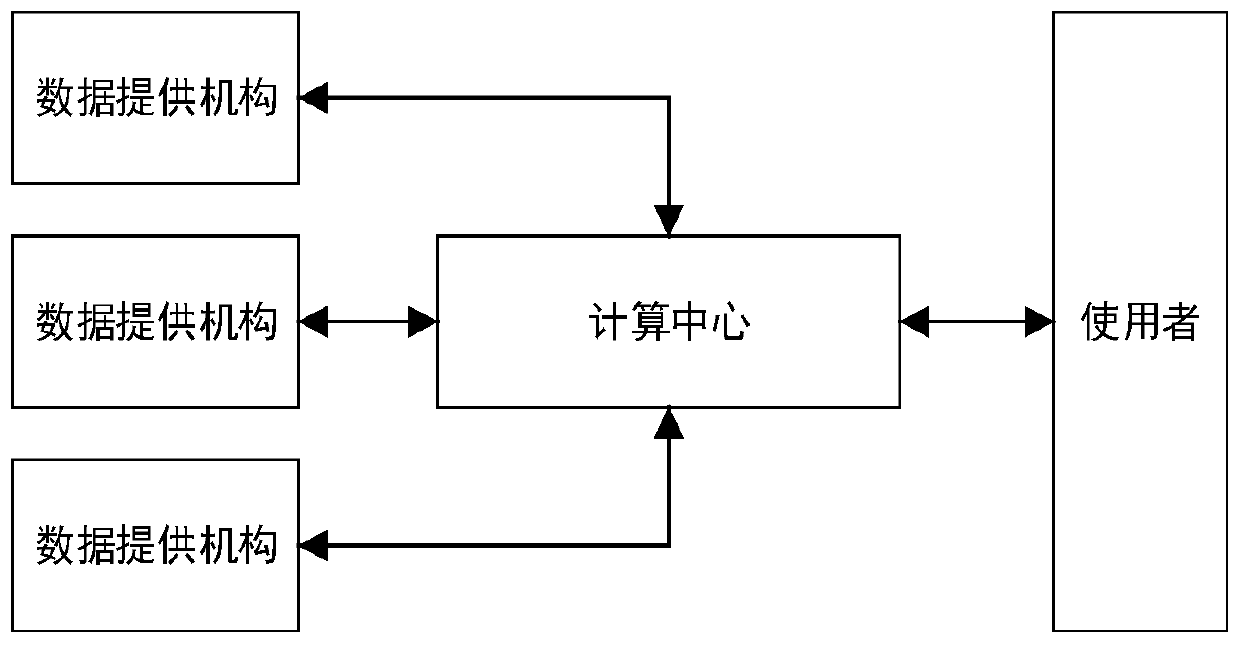
Privacy protection multi-mechanism data classification method based on homomorphic encryption
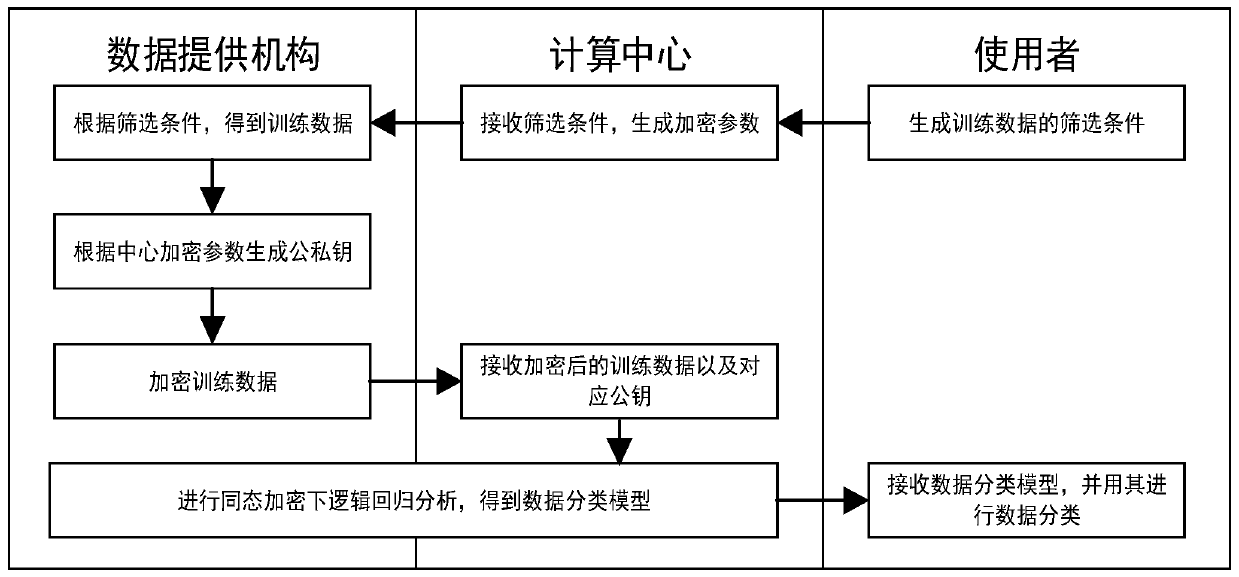
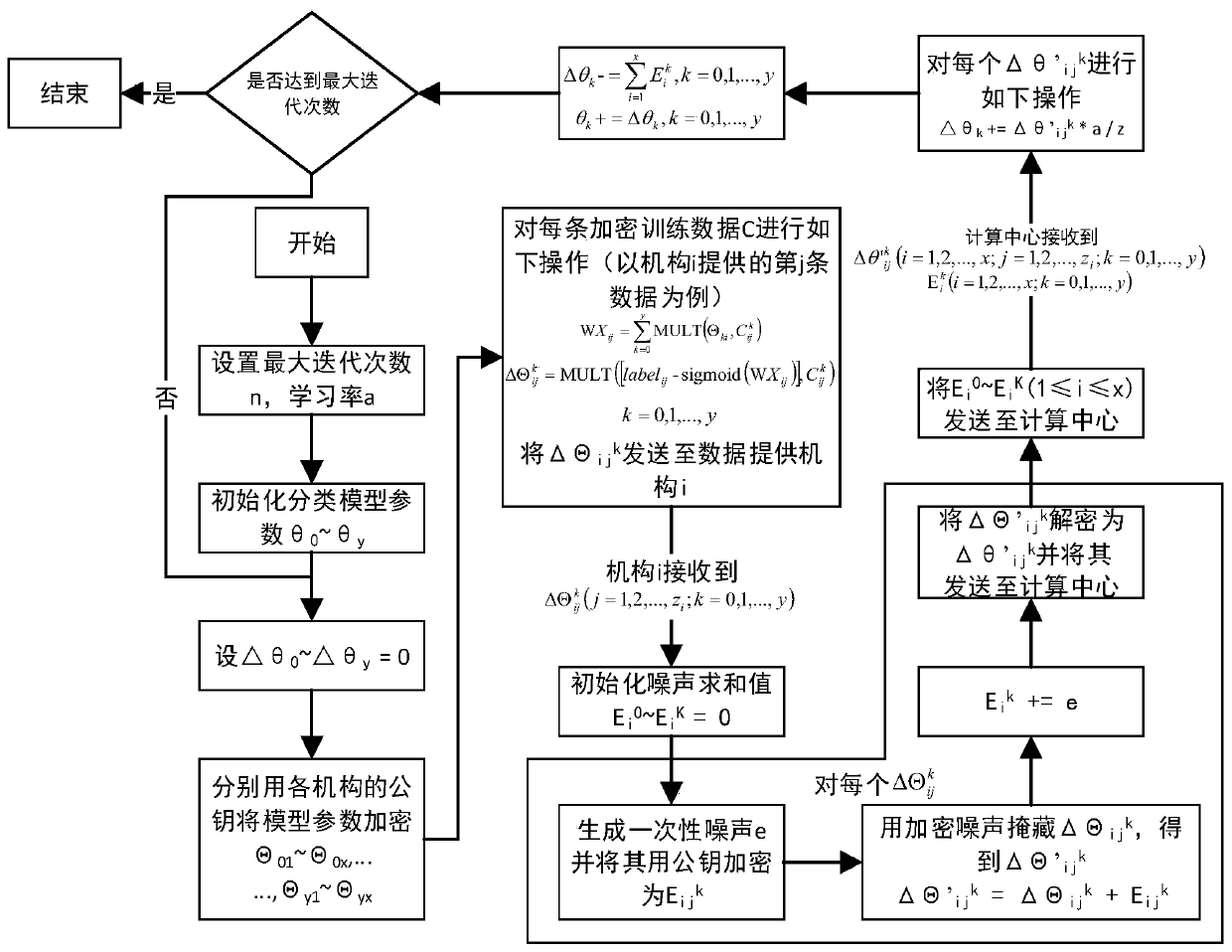
ActiveCN110190946APrevent leakagePrevent Malicious UseCharacter and pattern recognitionCommunication with homomorphic encryptionComputing centerUser input
The invention discloses a privacy protection multi-mechanism data classification method based on homomorphic encryption. Firstly, a user generates a screening condition of training data and sends thescreening condition to a computing center; a computing center generates encryption parameters by using a homomorphic encryption algorithm and sends the encryption parameters to each data providing mechanism; each data providing mechanism screens the local data marked with the classification tags to obtain training data, generates respective public key and private key by utilizing a homomorphic encryption algorithm according to the encryption parameters, encrypts the training data through the public key and sends the training data to the computing center; a computing center and each data providing mechanism jointly execute logistic regression analysis under homomorphic encryption to obtain a data classification model and send the data classification model to a user; and a user inputs the to-be-classified data into the data classification model to obtain a classification result. Compared with the prior art, the method has higher safety in practical application, personal privacy is effectively protected, benefit loss possibly generated by a data providing mechanism is avoided, and development of multi-mechanism data analysis is promoted to a great extent.
Owner:ZHEJIANG LAB
System and method for digital signature authentication of SMS messages
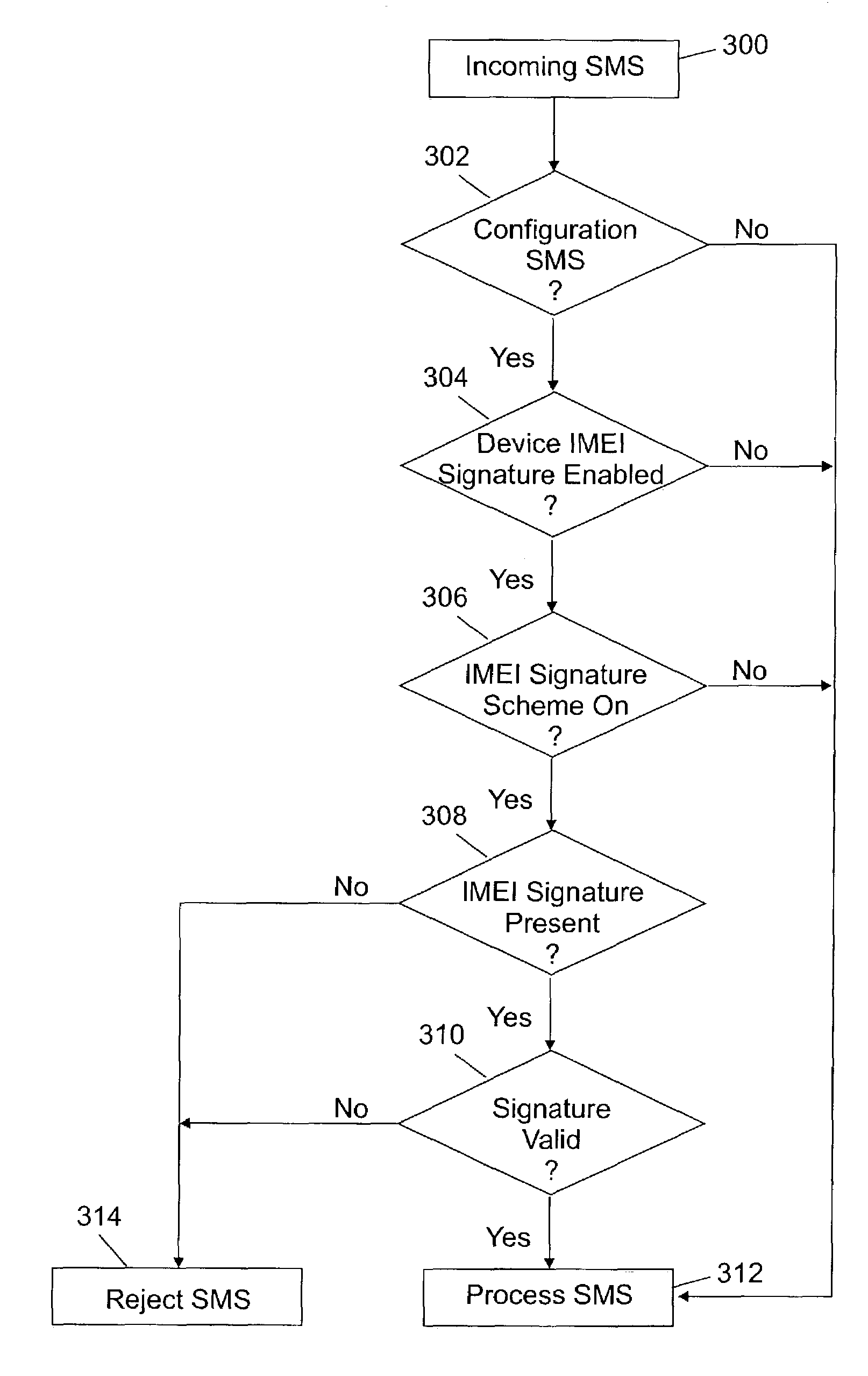
ActiveUS7353394B2Easy to usePrevent Malicious UseDigital data processing detailsUser identity/authority verificationDigital signatureTerminal equipment
The invention allows SMS messages authentication through the use of a digital signature computed with the International Mobile Equipment Identity (IMEI) as a key. Particularly, a text messaging system having the ability to send SMS messages to remotely managed wireless terminal equipment is disclosed and includes a system to generate such digital signature and to store it in available Information Element fields of the TP-User Data of the SMS message. Receiving wireless terminal equipment that are configured for IMEI-based signature security, still keep the option to process both SMS messages having the IMEI-based signature or not. Receiving wireless terminal equipment not enabled for IMEI-based signature security process the SMS normally.
Owner:TREND MICRO INC
Method for transmitting data service and equipment thereof
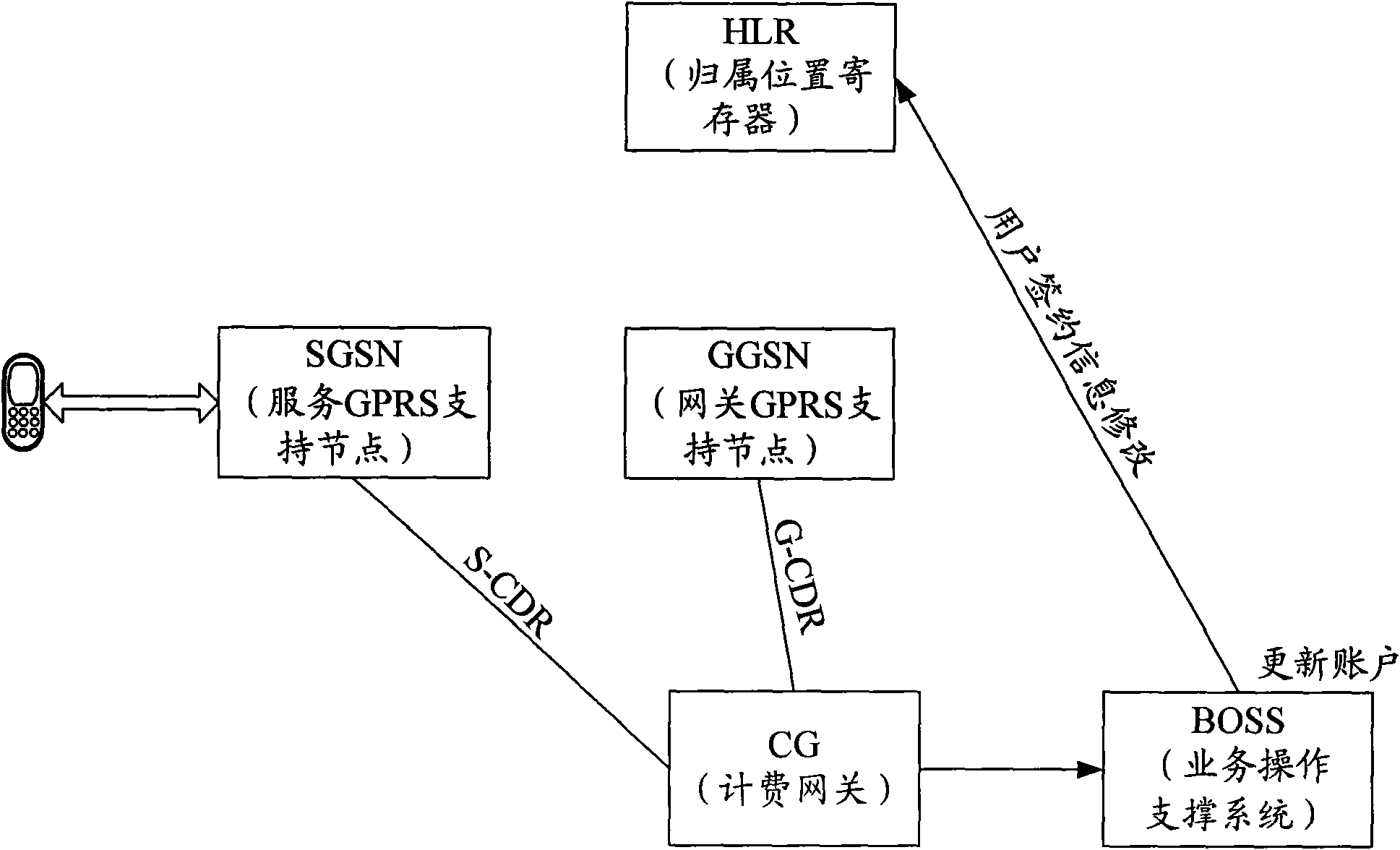
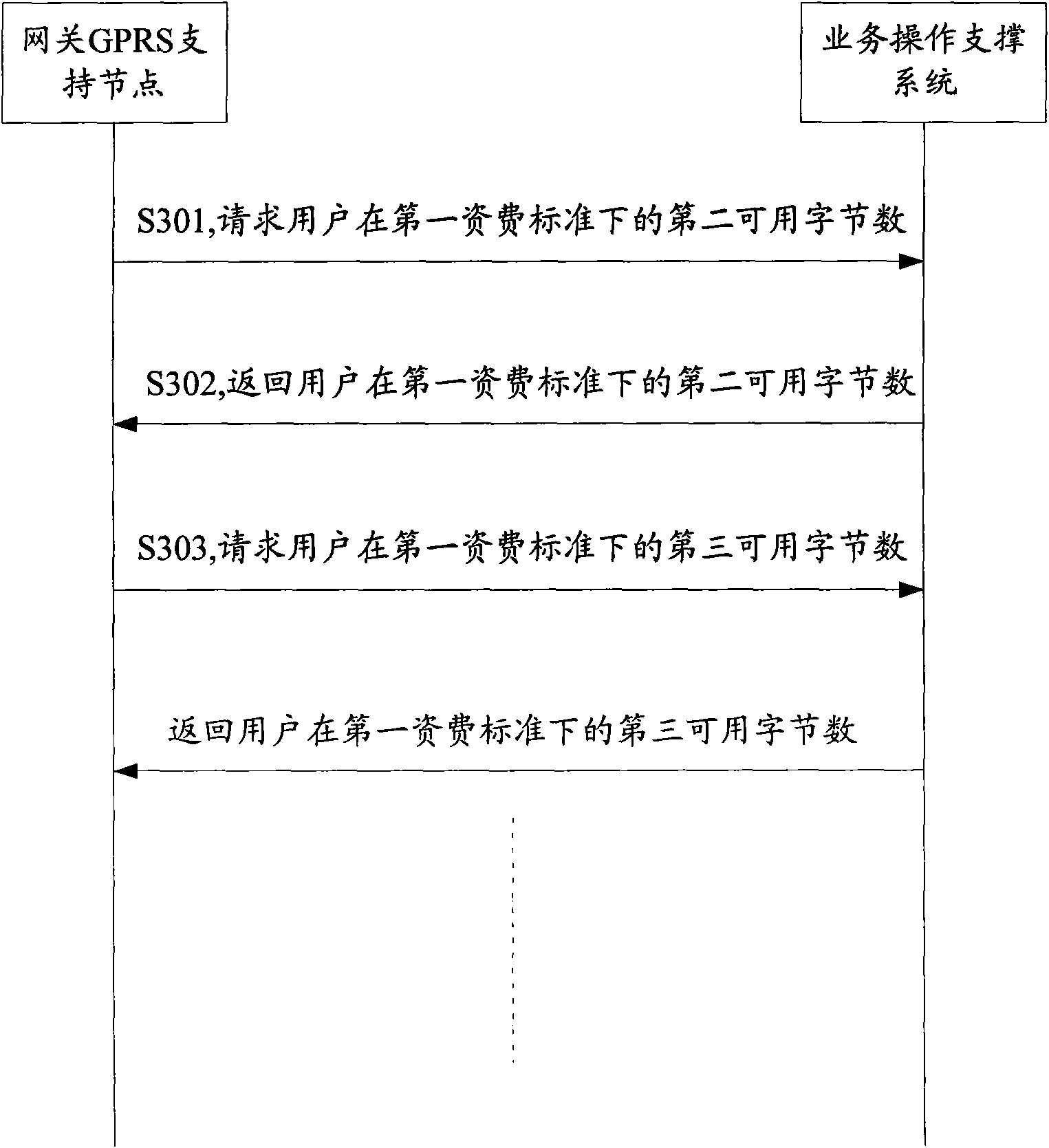
ActiveCN101616009AReduce the risk of arrearsPrevent Malicious UseMetering/charging/biilling arrangementsAccounting/billing servicesComputer networkByte
The invention discloses a method for transmitting data service and equipment thereof, which aims to solve the problem that the prior GGSN cannot carry out transmission control on data service requested by a user. The method comprises the following steps that: a BOSS screens a transmission control user in a mobile communication network according to set time or cycle, sets an available sum for the transmission control user and determines a corresponding available byte number of data service requested by the user according to the available sum of the transmission control user; and a GGSN transmits the data service requested by the user according to the available byte number indicated by the BOSS. The technical scheme ensures that the GGSN can carry out transmission control on data service requested by a user and control the amount of consumption of the user within an available sum, thereby preventing the user from using PS domain data service viciously and reducing user arrearage risks.
Owner:CHINA MOBILE COMM GRP CO LTD
Connecting method and system for wireless fidelity network
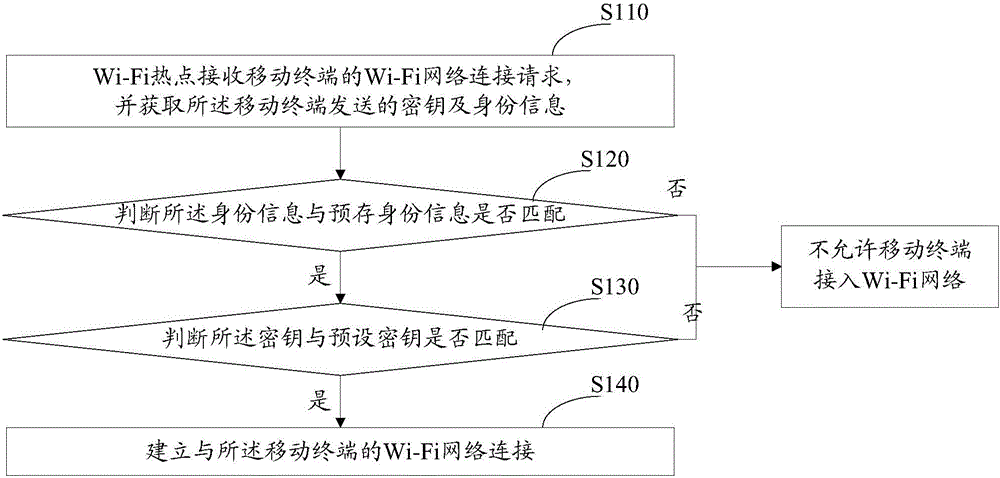
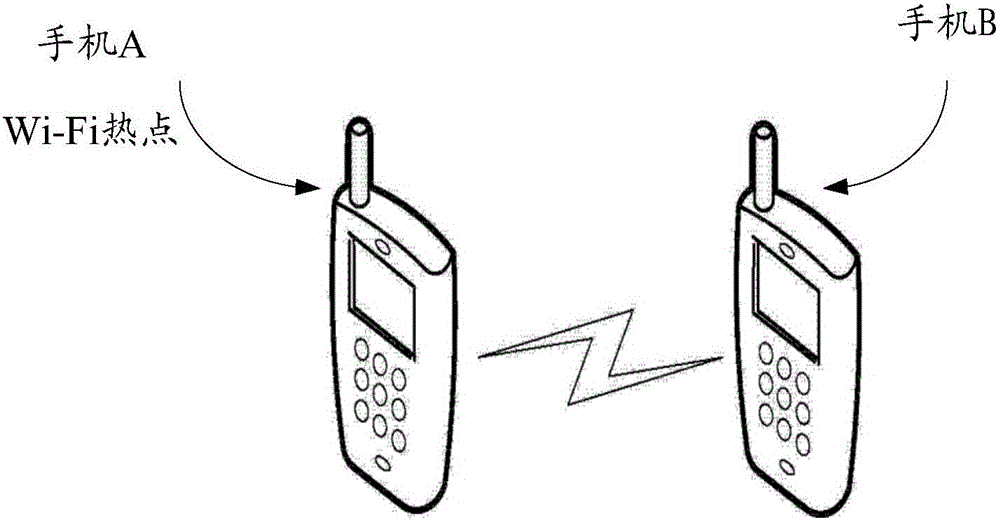
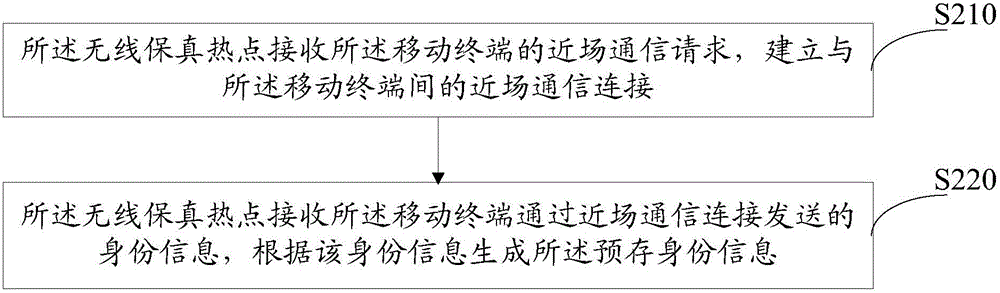
ActiveCN105072615AImprove securityImprove experienceConnection managementTransmissionWi-FiNetwork connection
The invention relates to a connecting method and system for a wireless fidelity network. The method comprises the steps that a wireless fidelity hotspot receives a wireless fidelity network connecting request of a mobile terminal, and acquires a secret key and identity information sent by the mobile terminal; the wireless fidelity hotspot judges whether the identity information is matched with prestored identity information, and judges whether the secret key is matched with a prestored secret key; and if the identity information is matched with the prestored identity information, and the secret key is matched with the preset secret key, the wireless fidelity hotspot establishes a wireless fidelity network connection with the mobile terminal. Due to dual authentication mechanisms of identity information and secret key, the Wi-Fi network connection security is sharply improved, the Wi-Fi hotspot can be effectively prevented from being cracked maliciously, the data traffic of the user is prevented from being used maliciously, and the user experience is further improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Intelligent goods taking system and control method
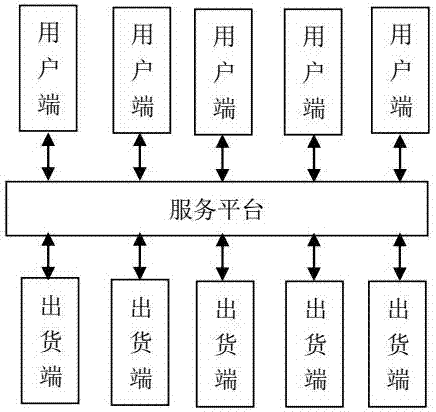
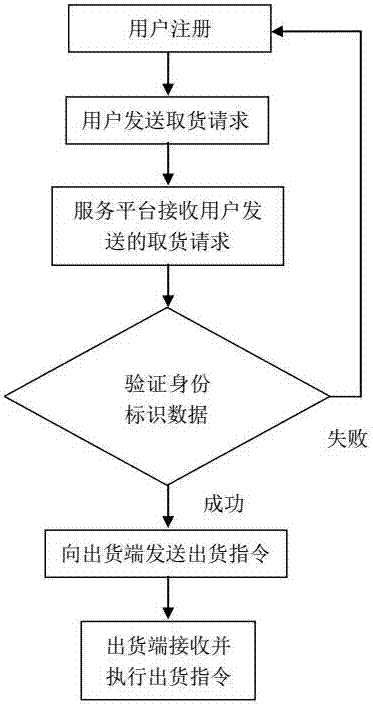
InactiveCN107025735AGet goodPrevent Malicious UseDigital data authenticationApparatus for meter-controlled dispensingData matchingService provision
The invention provides an intelligent goods taking system and a control method. The system comprises a service platform and a goods delivery terminal, wherein the service platform is used for receiving and verifying a goods taking request sent by a user through a user side or goods delivery terminal and sending a goods delivery instruction to the goods delivery terminal after the goods taking request is successfully verified, and the condition of successful verification of the goods taking request is as follows: user identity identification data in the goods taking request are successfully matched with identity identification data of any registered user of designated programs; the goods delivery terminal is used for receiving and executing the goods delivery instruction sent by the service platform. Output and / or opening of related products and / or services are / is determined by verifying whether users are the registered users of the designated programs (official accounts), and the intelligent goods taking system and the control method can not only be used for promoting designated programs (official accounts), but also provide great convenience for users who want to get related products and / or use related services.
Owner:HEFEI LONGTUTEM INFORMATION TECH CO LTD
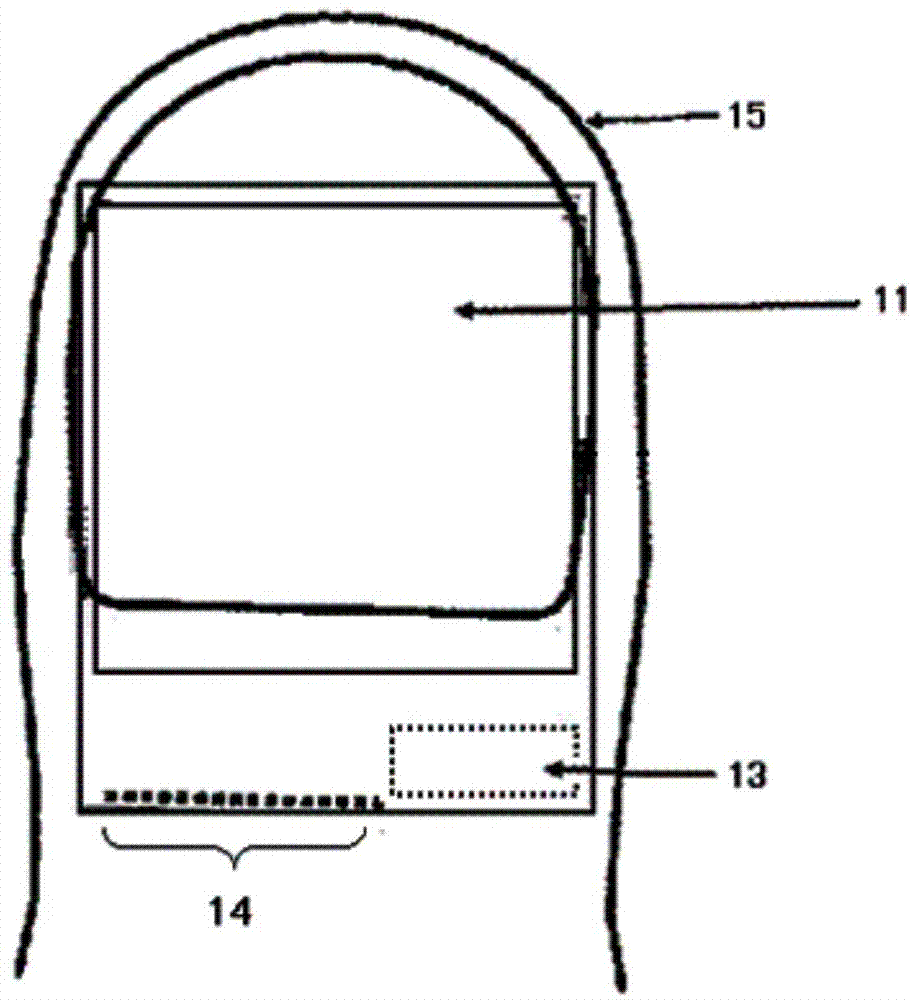
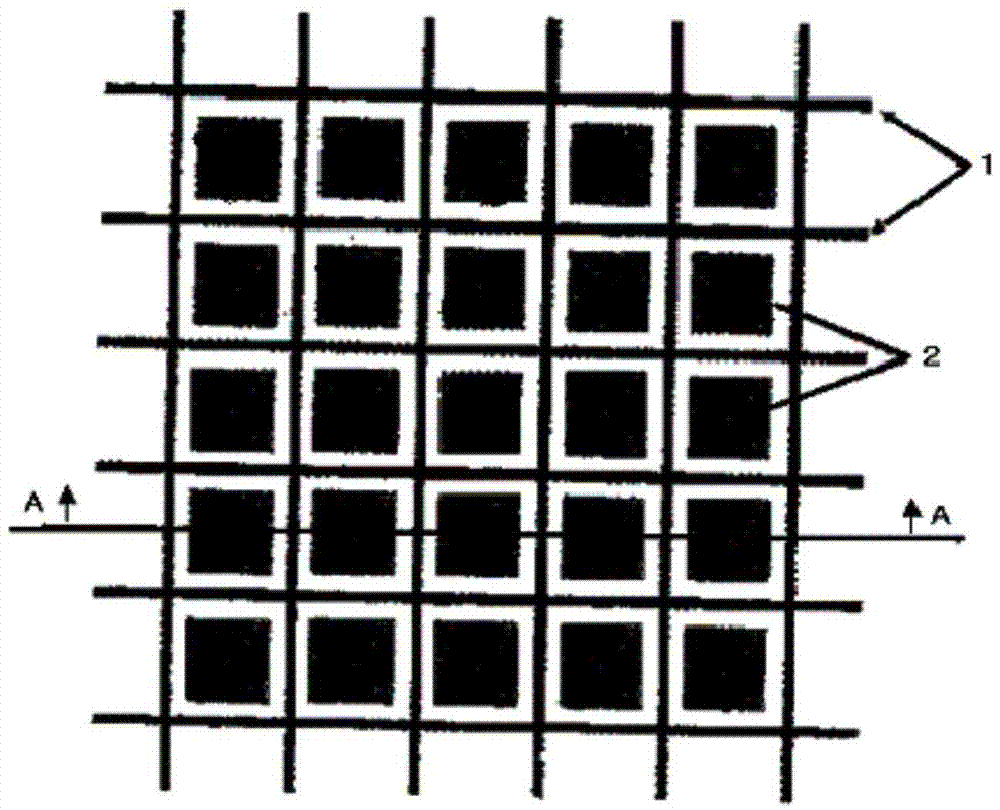
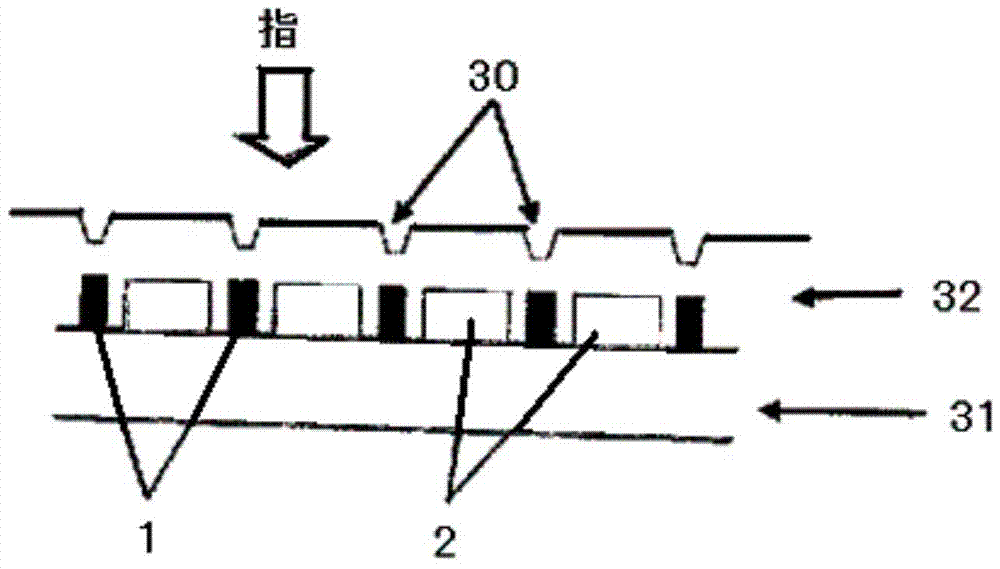
Fingerprint reading sensor capable of removing residual fingerprints
InactiveCN103793698APrevent Malicious UseCharacter and pattern recognitionCoated surfaceTitanium oxide
The invention provides a fingerprint reading sensor capable of removing residual fingerprints. The fingerprint reading sensor capable of removing the residual fingerprints comprises a semiconductor fingerprint reading sensor body, wherein a fingerprint reading part of the semiconductor fingerprint reading sensor body comprises electrodes distributed in an array and meshes between the electrodes, the semiconductor fingerprint reading sensor body is coated with a coating, and grooves are engraved in the surface of the coating along the meshes in the longitudinal direction or the transverse direction of the meshes. Alternatively, an anatase type titanium oxide thin film can be arranged on the surface the coating in a lamination mode, and then grooves are engraved in the thin film. The fingerprint reading sensor capable of removing the residual fingerprints has the advantages that sweat drops which form the residual fingerprints are made to flow away along the grooves, the graphic trace of the residual fingerprints is damaged, and therefore malicious use of the residual fingerprints is prevented.
Owner:JIANGSU HENGCHENG HI TECH INFORMATION TECH
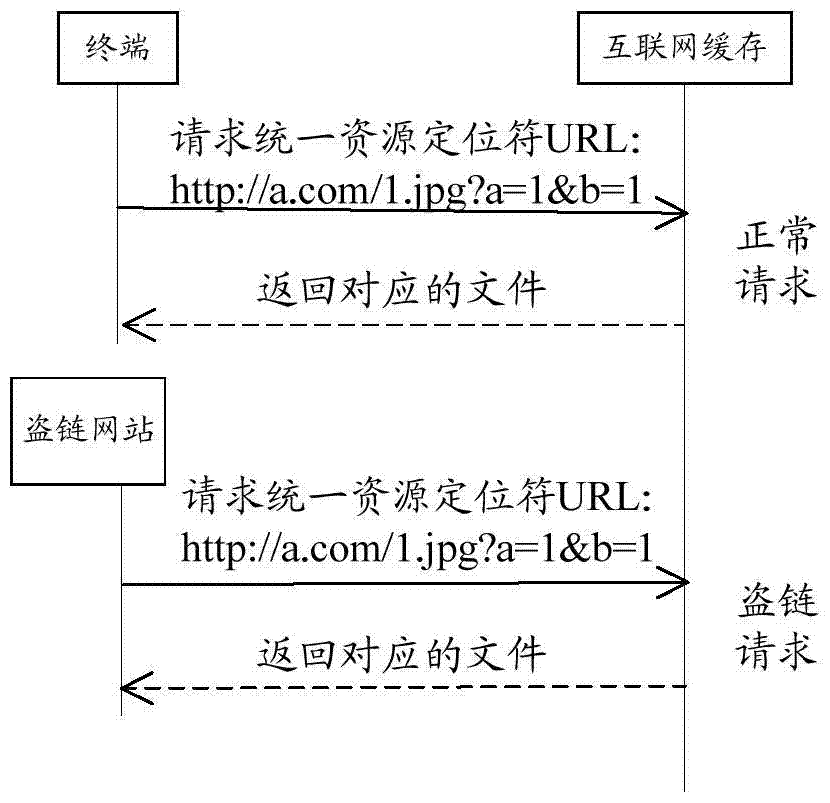
Internet cache and anti-stealing link method based on internet cache
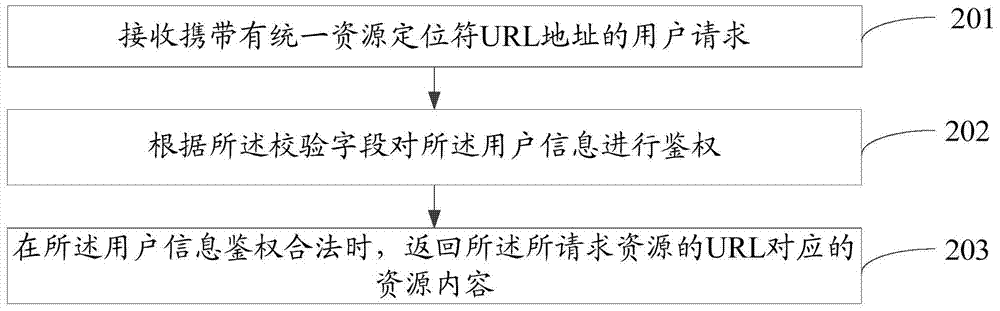
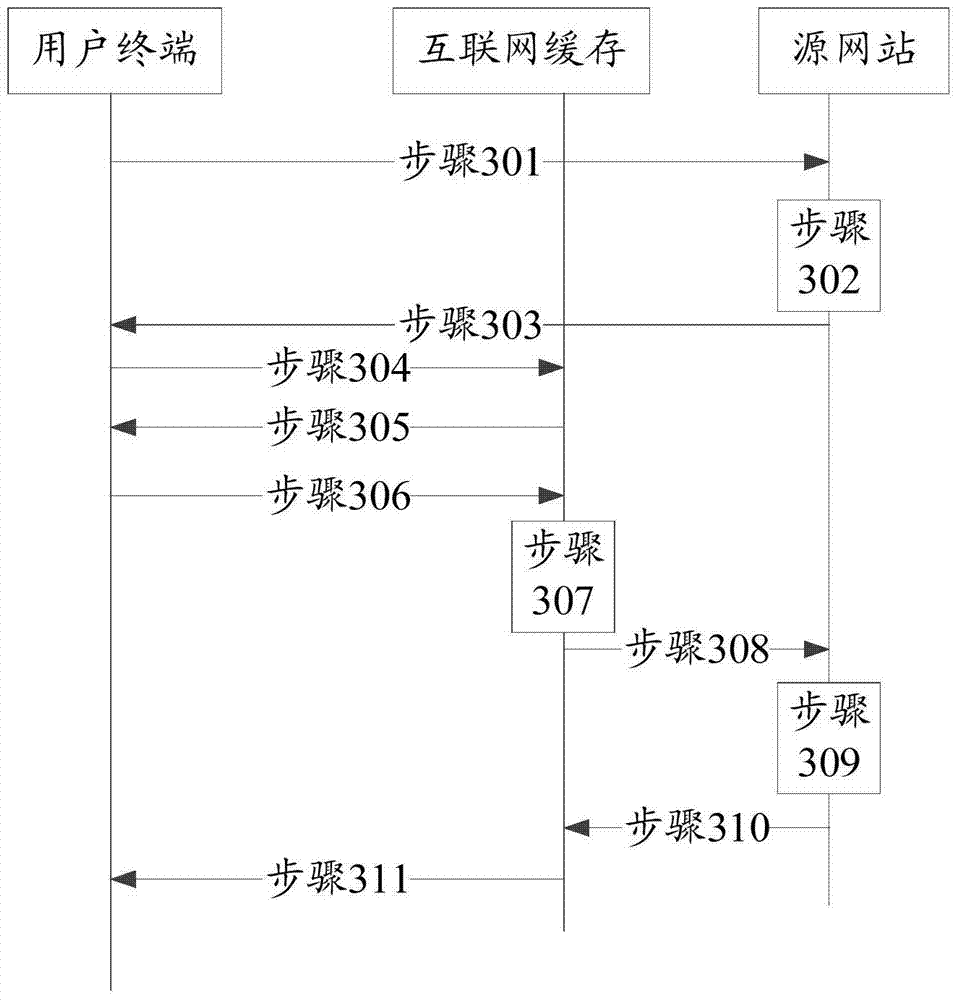
ActiveCN107026828ARealize the anti-theft chain functionPrevent malicious useTransmissionThe InternetUniform resource locator
The embodiment of the invention discloses an anti-stealing link method based on an internet cache. The method comprises the following steps: receiving a user request with a uniform resource locator URL address, wherein the URL address comprises user information, the URL of a requested resource and a check field; authenticating the user information according to the check field; and returning resource content corresponding to the URL of the requested resource when the user information authentication is legal. The embodiment of the invention further discloses the internet cache.
Owner:LIAONING MOBILE COMM
Processing method for electronic equipment and system
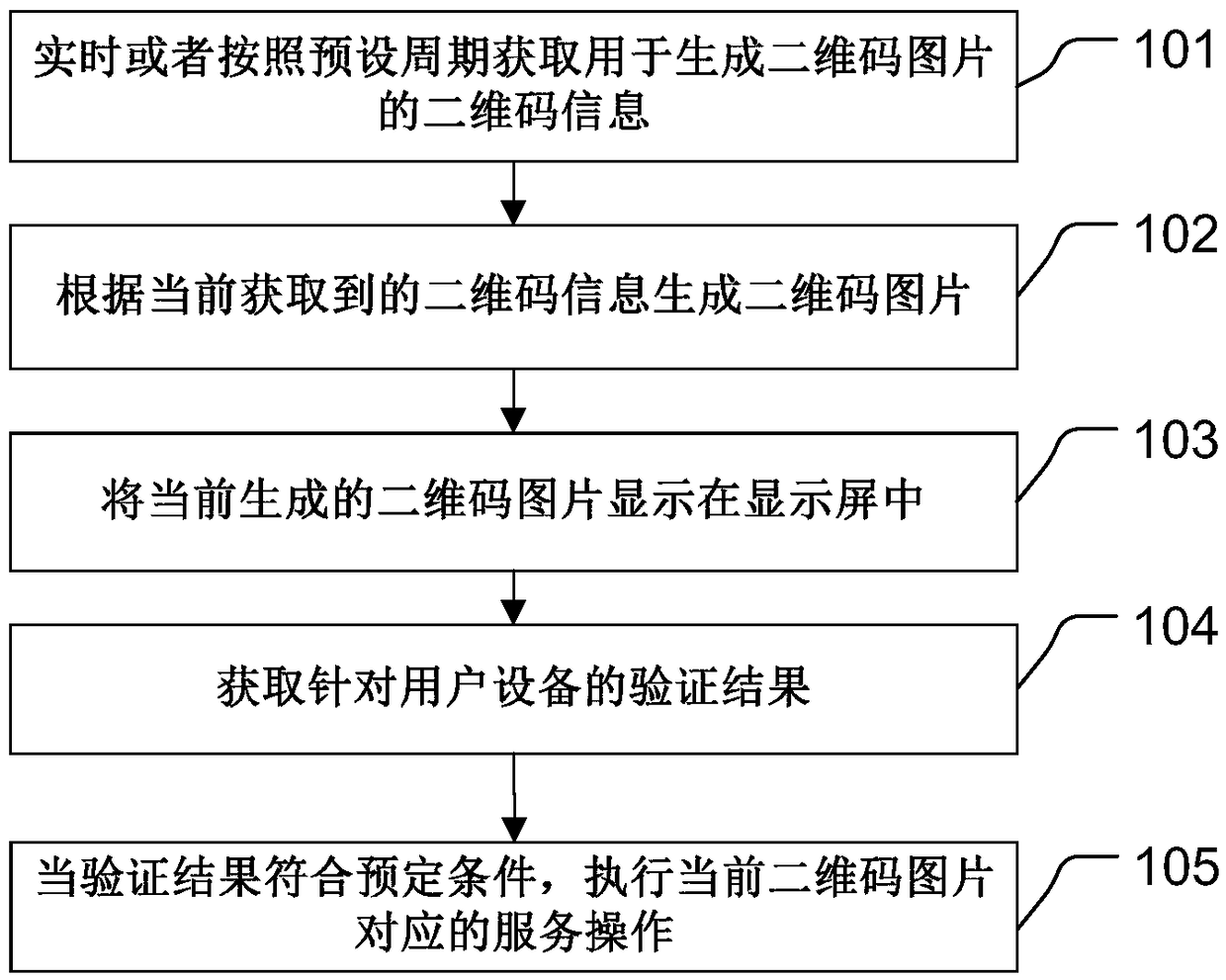
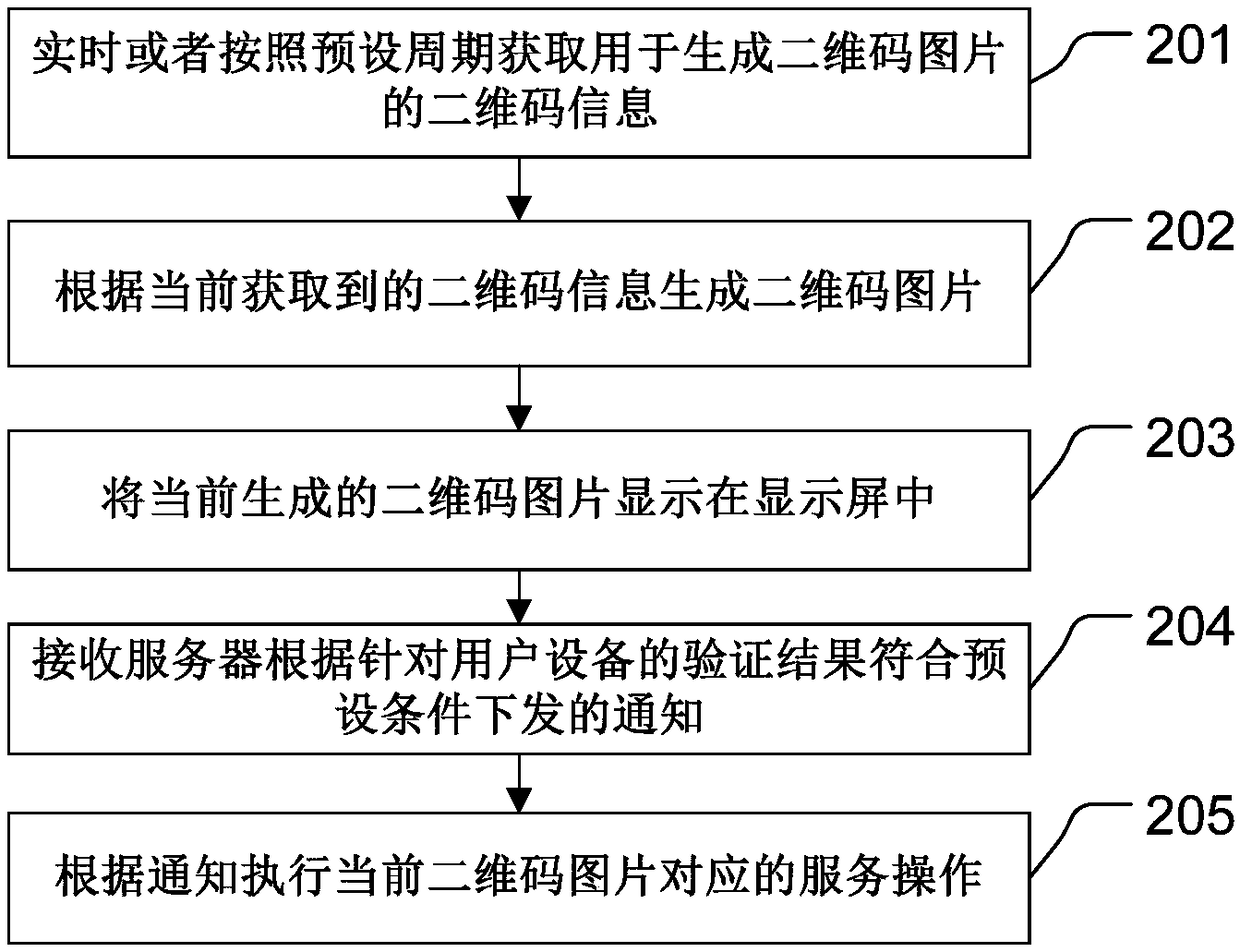
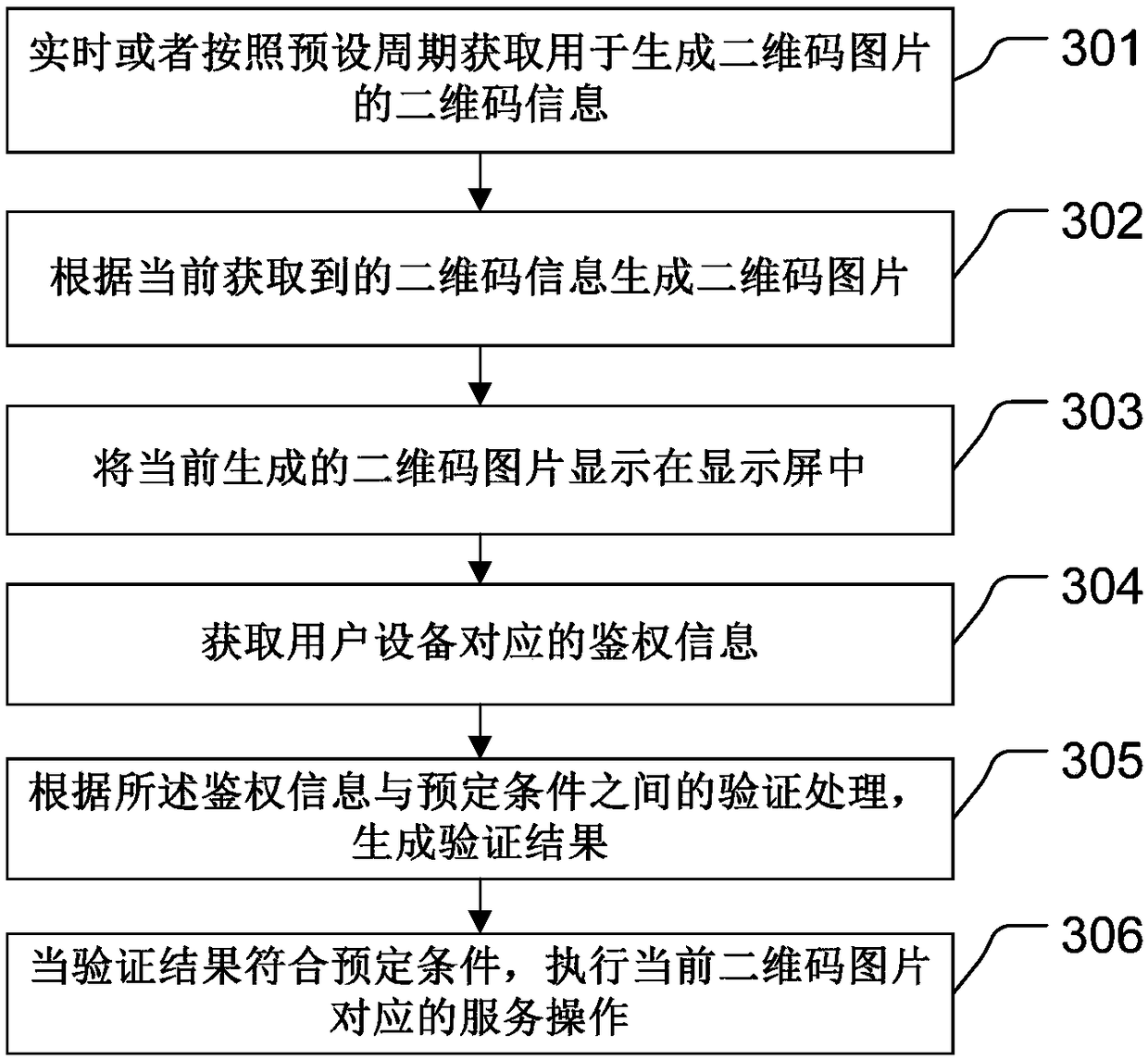
ActiveCN108733992APrevent Malicious UseImprove securityDigital data authenticationDynamic displayBarcode
The invention discloses a processing method for electronic equipment and a system. The method comprises the steps of obtaining two-dimensional bar code information for generating a two-dimensional barcode image in real time or according to a preset period; generating the two-dimensional bar code image according to the currently obtained two-dimensional bar code information; displaying the currently generated two-dimensional bar code image in a display screen; obtaining a verification result for user equipment; and performing service operation corresponding to the current two-dimensional bar code image when the verification result is consistent with a preset condition. Through application of the method, the two-dimensional bar code image can be dynamically displayed on the display screen and verification operation is carried out on the user equipment, the defect that a static two-dimensional bar code image is broken or artificially and maliciously tampered can be avoided, the electronic equipment also can be prevented from being used by a malicious user, and the security of the electronic equipment is further improved.
Owner:深圳市图灵奇点智能科技有限公司 +1
Emergency call based authentication method, device and system
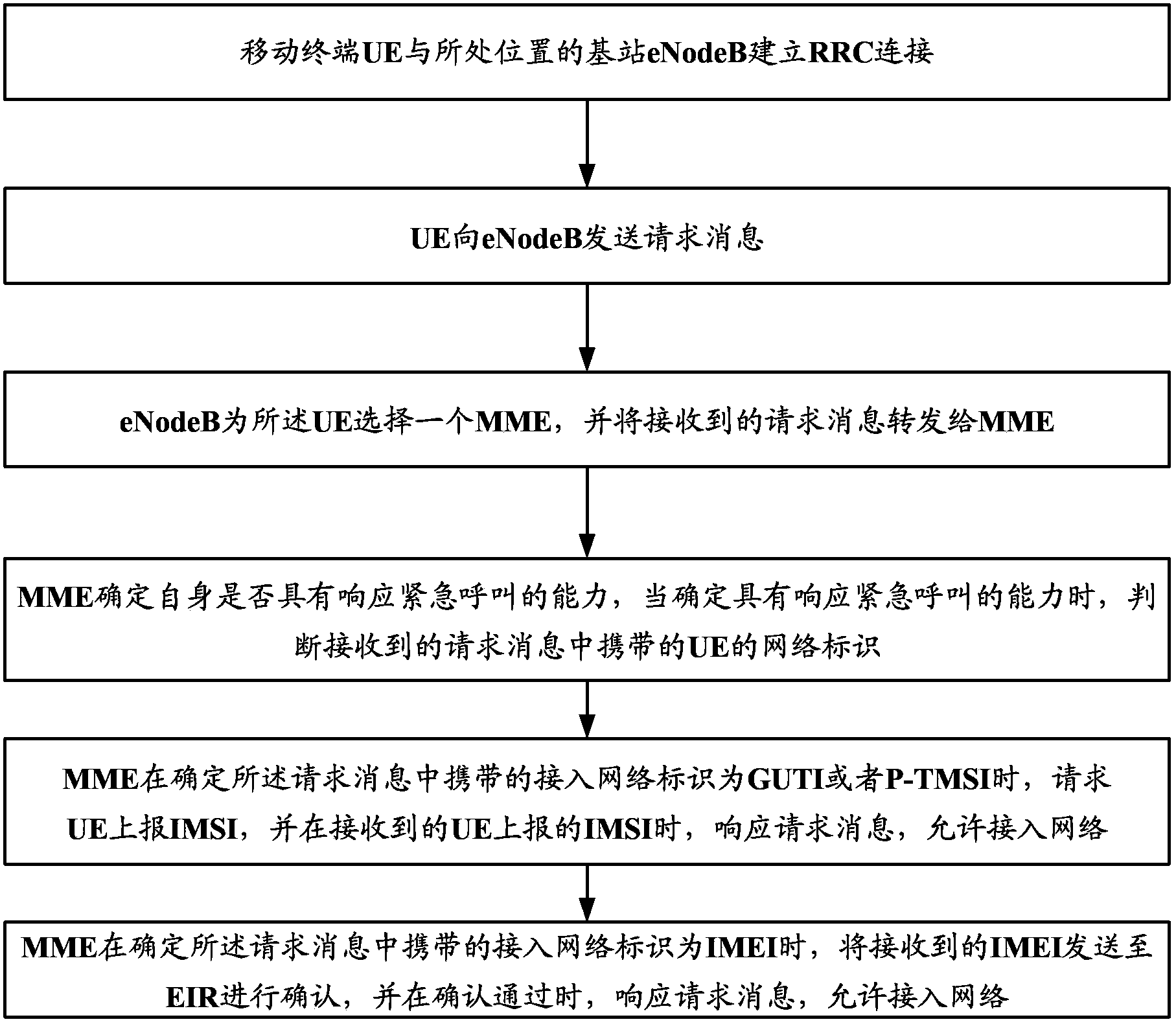
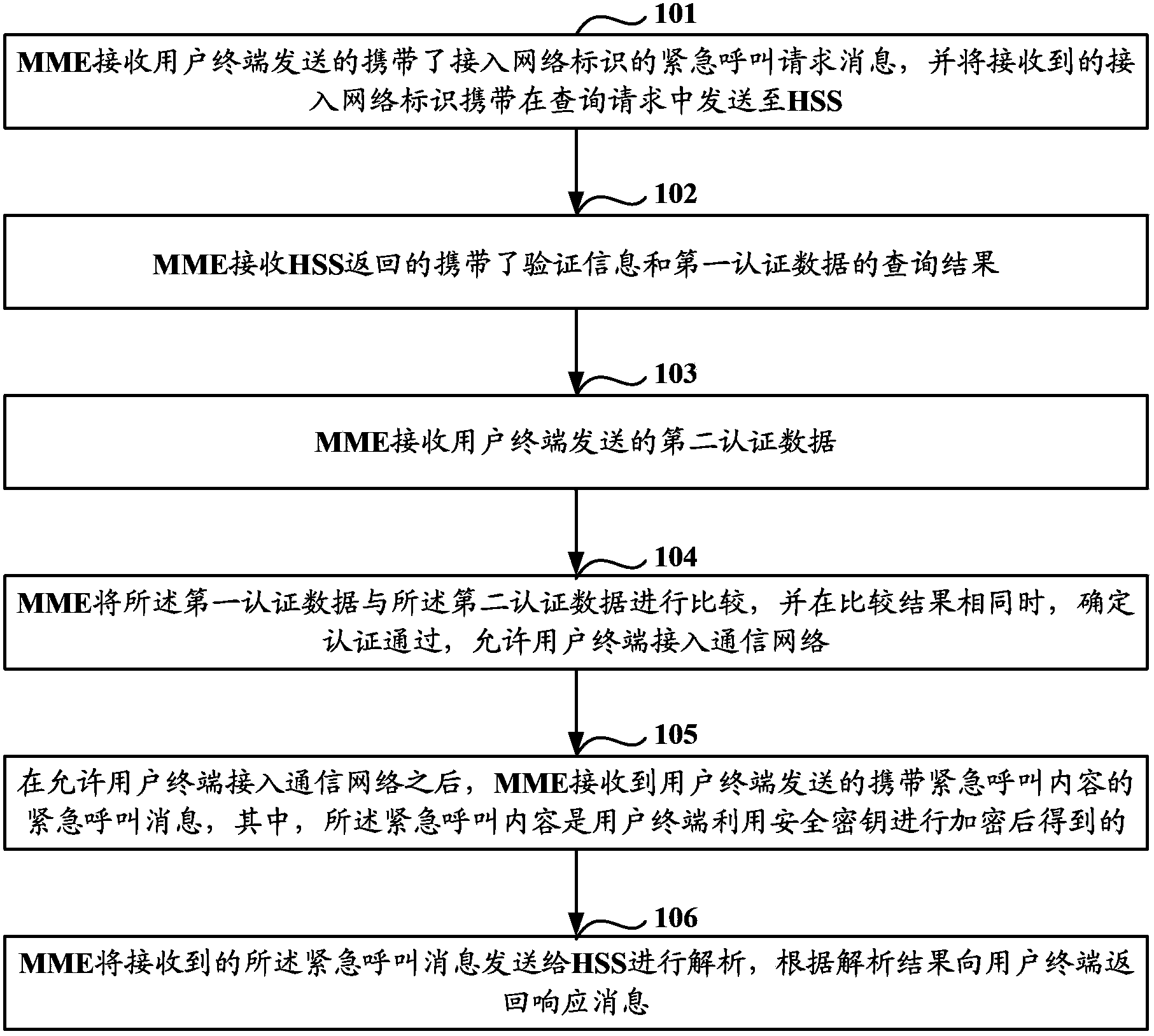
ActiveCN103686651AImprove securityEnsure safetyConnection managementWireless commuication servicesApplication securityComputer science
The invention discloses an emergency call based authentication method, device and system. The main content of the authentication method comprises the following steps: respectively storing corresponding relation between an IMEI of a user terminal and an equipment key in the user terminal side and an HSS side, obtaining a safe key containing the equipment key from the HSS by an MME when the user terminal sends an emergency call request message to the MME, carrying out operation to random verification information to obtain first authentication data, receiving second authentication data which is obtained by computing the locally stored safe key and the received authenticated message and transmitted by the user terminal, comparing the first authentication data with the second authentication data; when the comparison results are the same, confirming that the authentication passes, and permitting that the user terminal accesses the communication network. Therefore, that the illegal user terminal accesses the communication network by the emergency call manner malignantly can be avoided, the security of the emergency call can be promoted, and the application security of the communication network can be ensured.
Owner:ZTE CORP
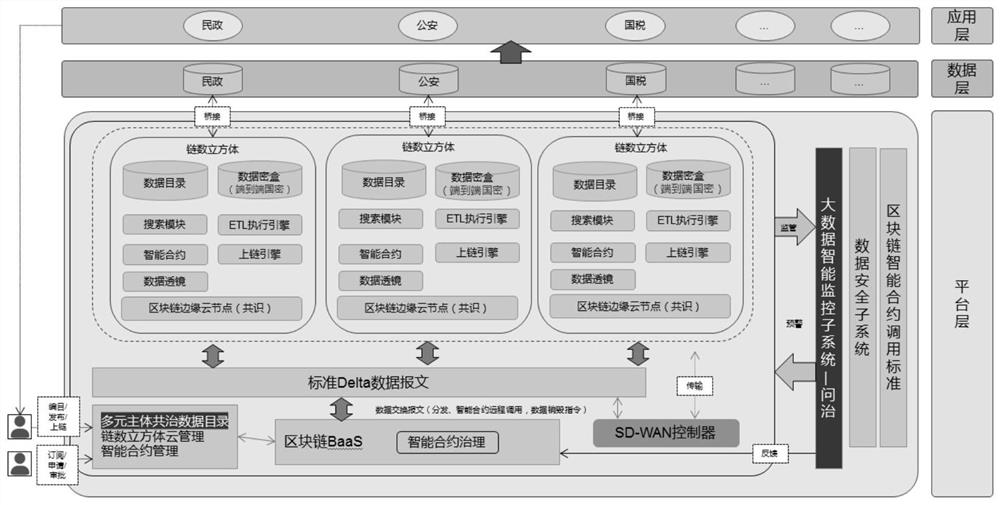
Big data management application system based on chain number cube
ActiveCN112527873AEfficient and convenient authorization access processConnectableDatabase management systemsFinanceThe InternetData access
The invention relates to the technical field of block chain information sharing, and particularly discloses a big data management application system based on a chain number cube. The system comprisesa plurality of chain number cubes, a user achieves data encryption, data storage, data uplink and data access through the chain number cubes, and the chain number cubes perform data interaction through data messages; each chain number cube comprises a data directory, a search module, a data secret box, an intelligent contract, an ETL execution engine, a data lens, an uplink engine and a block chain edge cloud node. According to the technical scheme, the data integration ETL process is combined with the block chain to form a chain type data internet, the problems that data is unknown and uncontrollable are solved, and data integration, data circulation and the like are credible and controllable.
Owner:成都无右区块链科技有限公司
Method for user security management of important system
InactiveCN103051447APrevent Malicious UseImprove securityUser identity/authority verificationMessaging/mailboxes/announcementsSoftware systemPassword
The invention relates to a method for user security management of an important software system, which aims at solving the current situation that users of a traditional system are lack of security awareness and hardly voluntarily change user passwords. The method is characterized in that for the important software system, after a user logs in the system every time, the system generates a verification code in real time and transmits the verification code onto a mobile phone of the user through a background management program, and then the user inputs the verification code to verify, so that a purpose for security management of the user password can be realized.
Owner:ZHENJIANG JINGYING SOFTWARE TECH
Key factor generation method of root key
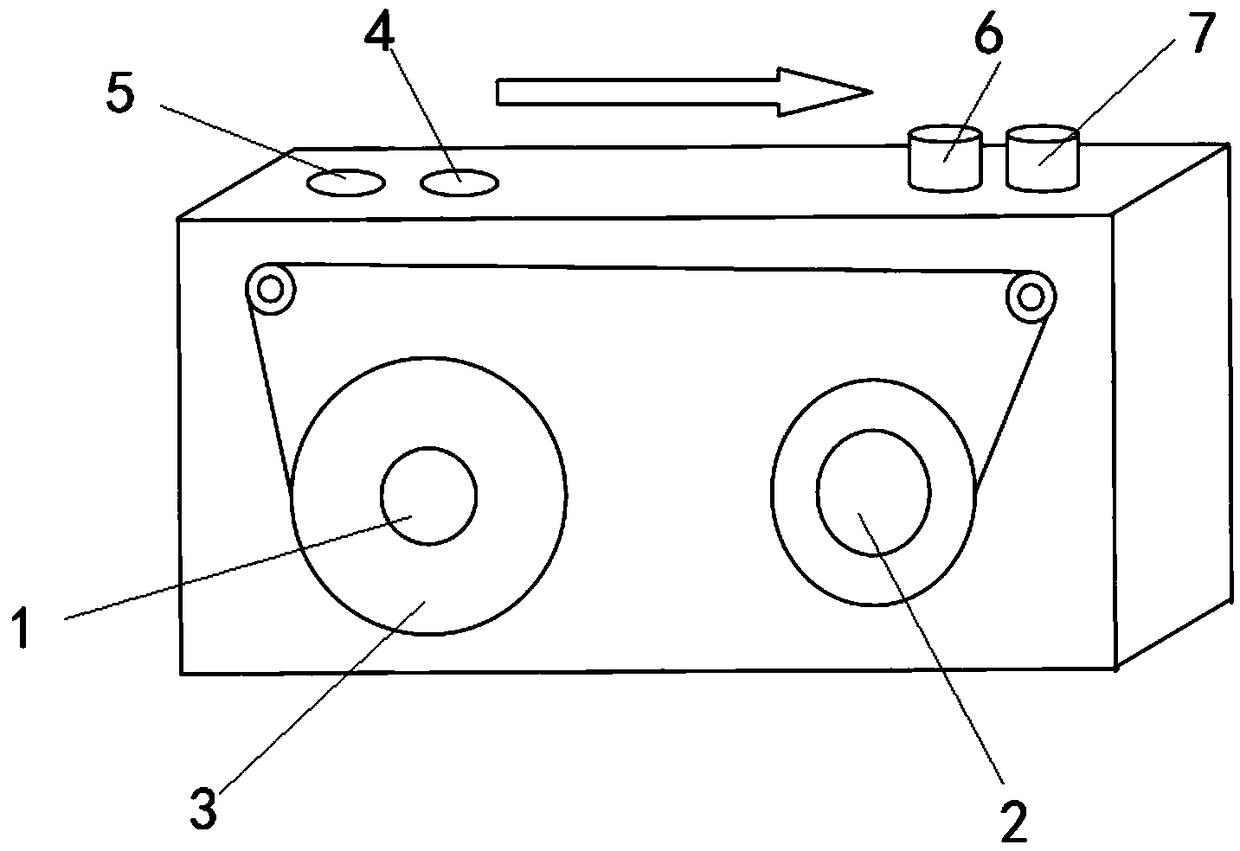
InactiveCN108923921APrevent malicious useImprove securityKey distribution for secure communicationUser identity/authority verificationPaper tapeEngineering
The invention relates to a key factor generation method of a root key. Key factors are generated one by one by a key factor generation device and are input into an encryption machine, the key factor generation device comprises an opaque rectangular box, a first axle and a second axle are arranged in the rectangular box side by side, a paper tape coil printed with continuous characters is installedon the first axle, a starting end of the paper tape coil is wound on the second axle, a first button and a second button, and a first hole and a second hole aligned to the upper side of the first axle are arranged on a top face of the rectangular box, the first hole just exposes one character on the paper tape coil, and the second hole exposes a blank part between the character aligned to the first hole and the next character. Compared with the prior art, the method provided by the invention has the advantages that the sufficient randomness of the key factors of the root key is determined bymultiple randomness, it can be ensures that the root key and all keys are established without anyone knowing the factor values, and meanwhile a mechanism is provided to guarantee that the root key canbe rebuilt when a disaster occurs.
Owner:上海声联网络科技股份有限公司
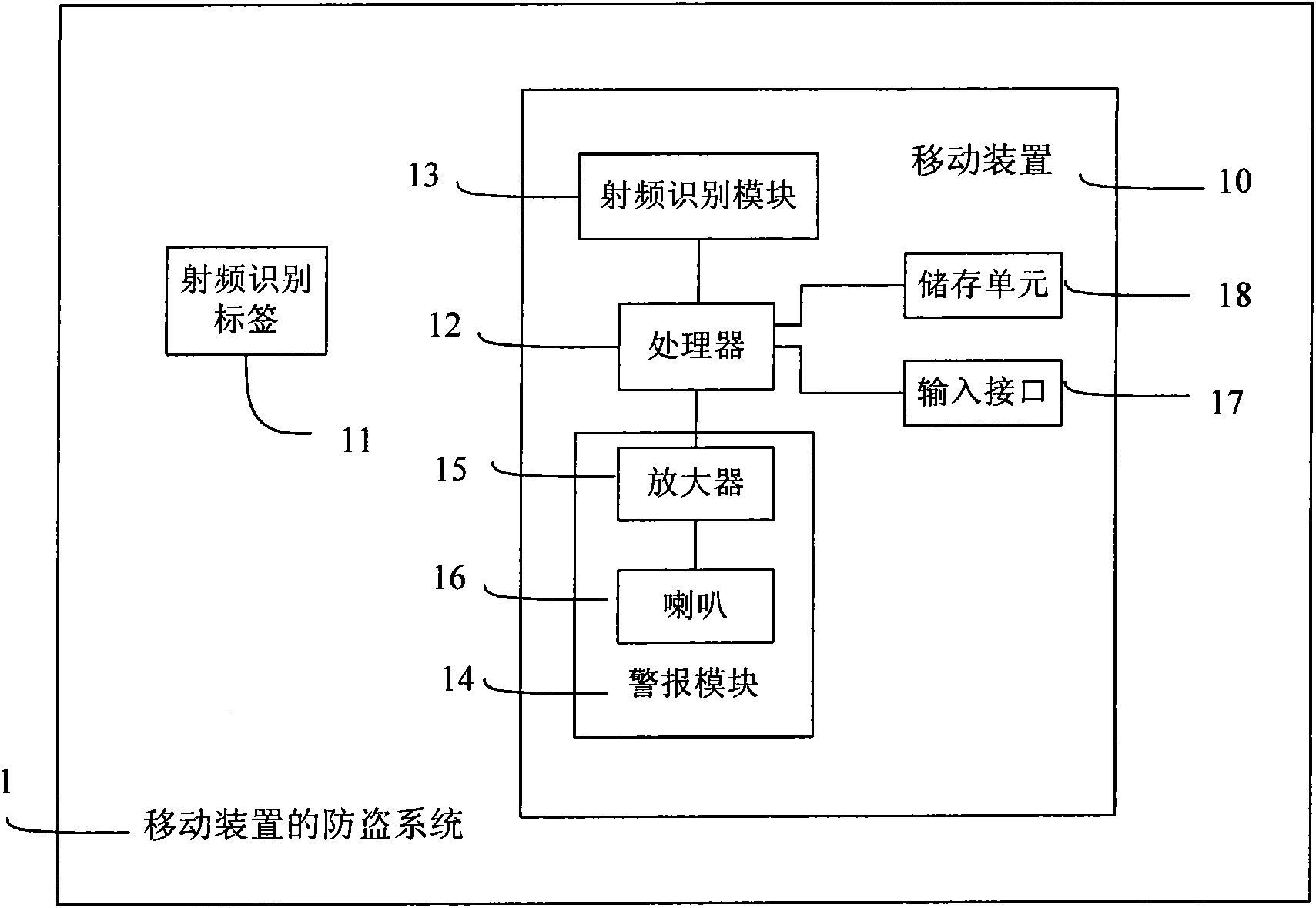
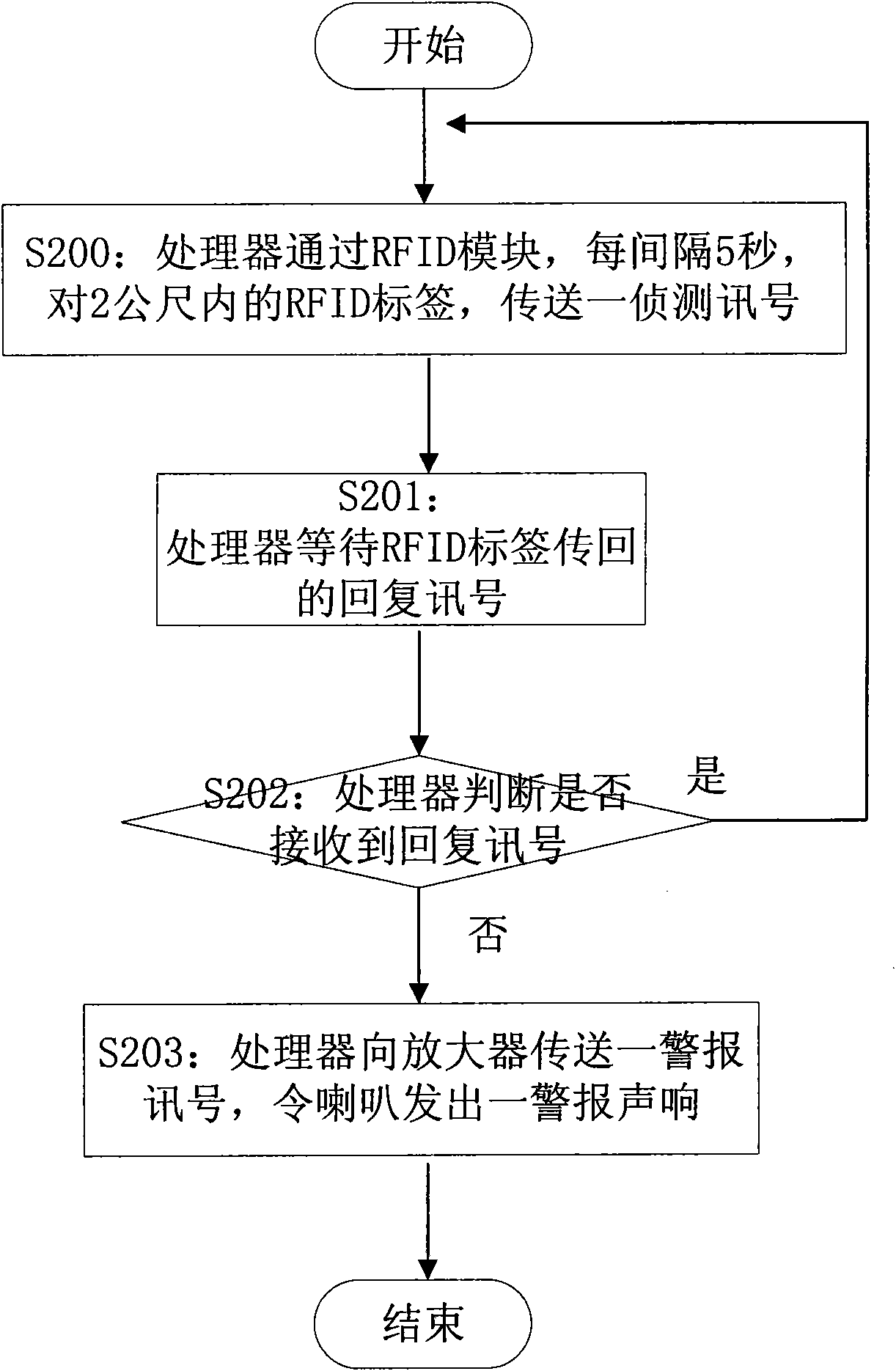
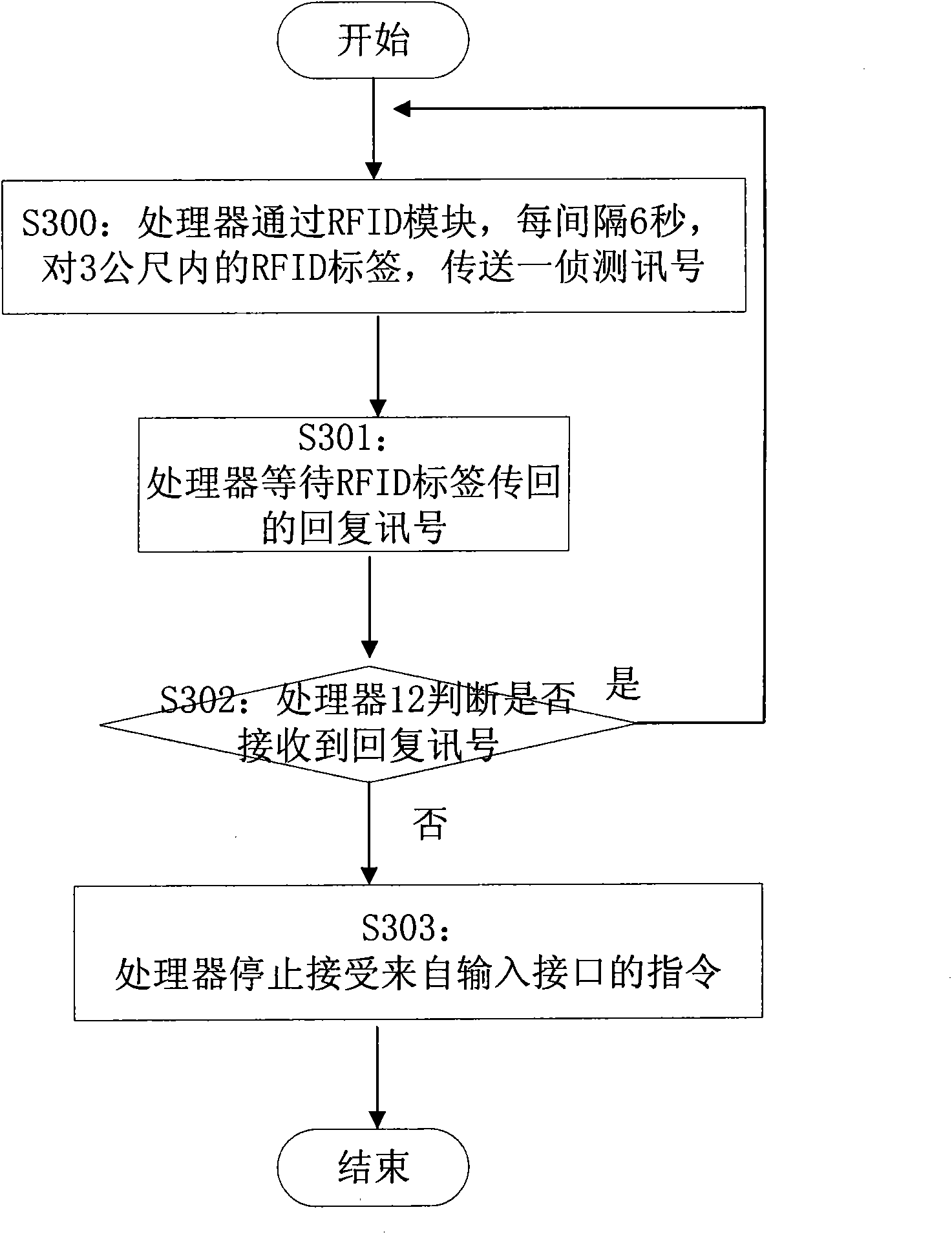
Theft-proof system of mobile device
ActiveCN101625788APrevent theftImprove information securitySubstation equipmentSensing record carriersComputer moduleMobile device
The invention discloses a theft-proof system of a mobile device, which comprises the mobile device and a radio-frequency identification label. The mobile device comprises a radio-frequency identification module, a processor and an alarm module, wherein the processor is connected with the radio-frequency identification module, and can emit a detection signal by using a first predetermined time as a period in a surrounding predetermined range through the radio-frequency identification module; and the alarm module is connected to the processor. The radio-frequency identification label can transmit a response signal to the radio-frequency identification module after receiving the detection signal; and when the processor does not receive the response signal in the period of the first predetermined time through the radio-frequency identification module after emitting the detection signal through the radio-frequency identification module, the processor carries out an emergency processing program. The theft-proof system can effectively prevent the mobile device from being stolen or lost, prevent the mobile device from being embezzled, and simultaneously protect the individual privacy from being invaded.
Owner:INVENTECSHANGHAI TECH
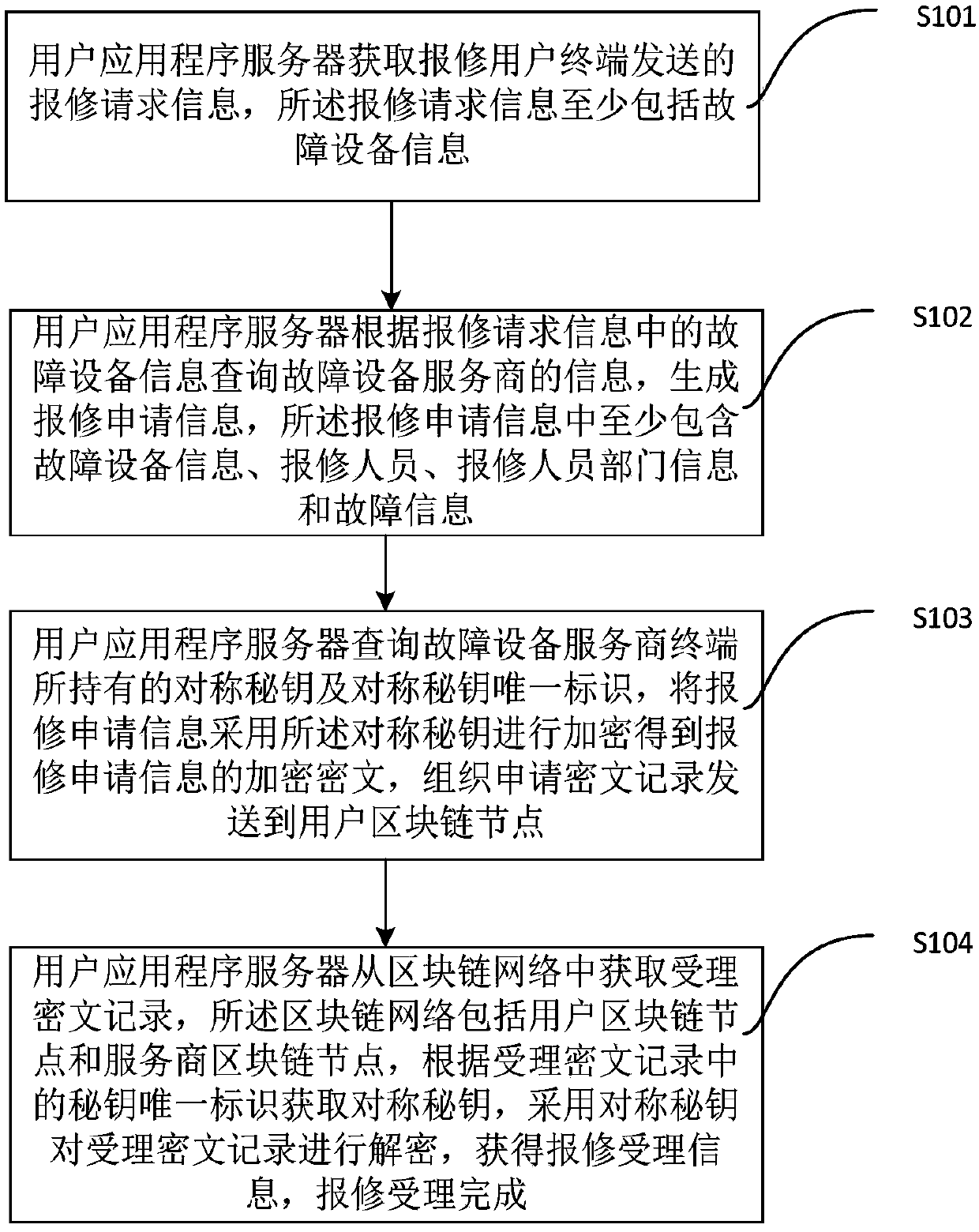
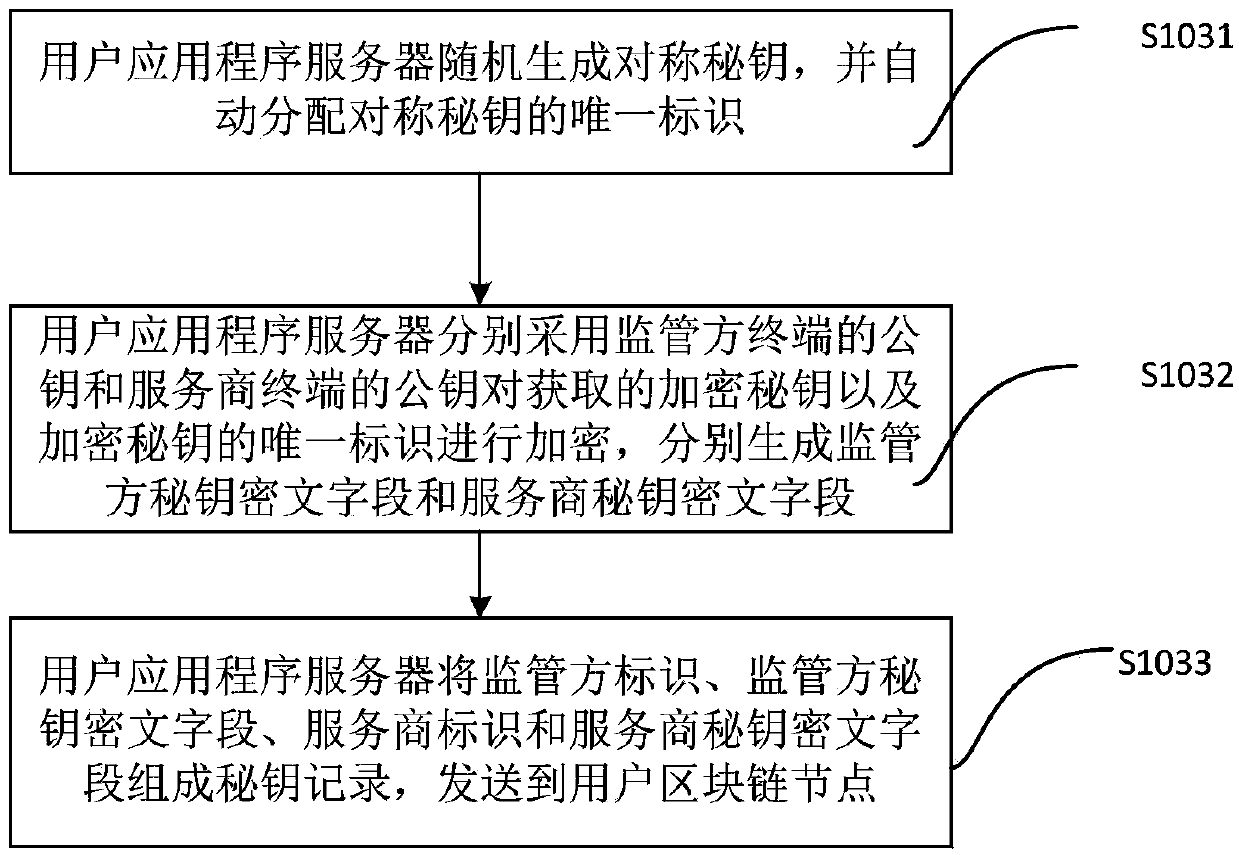
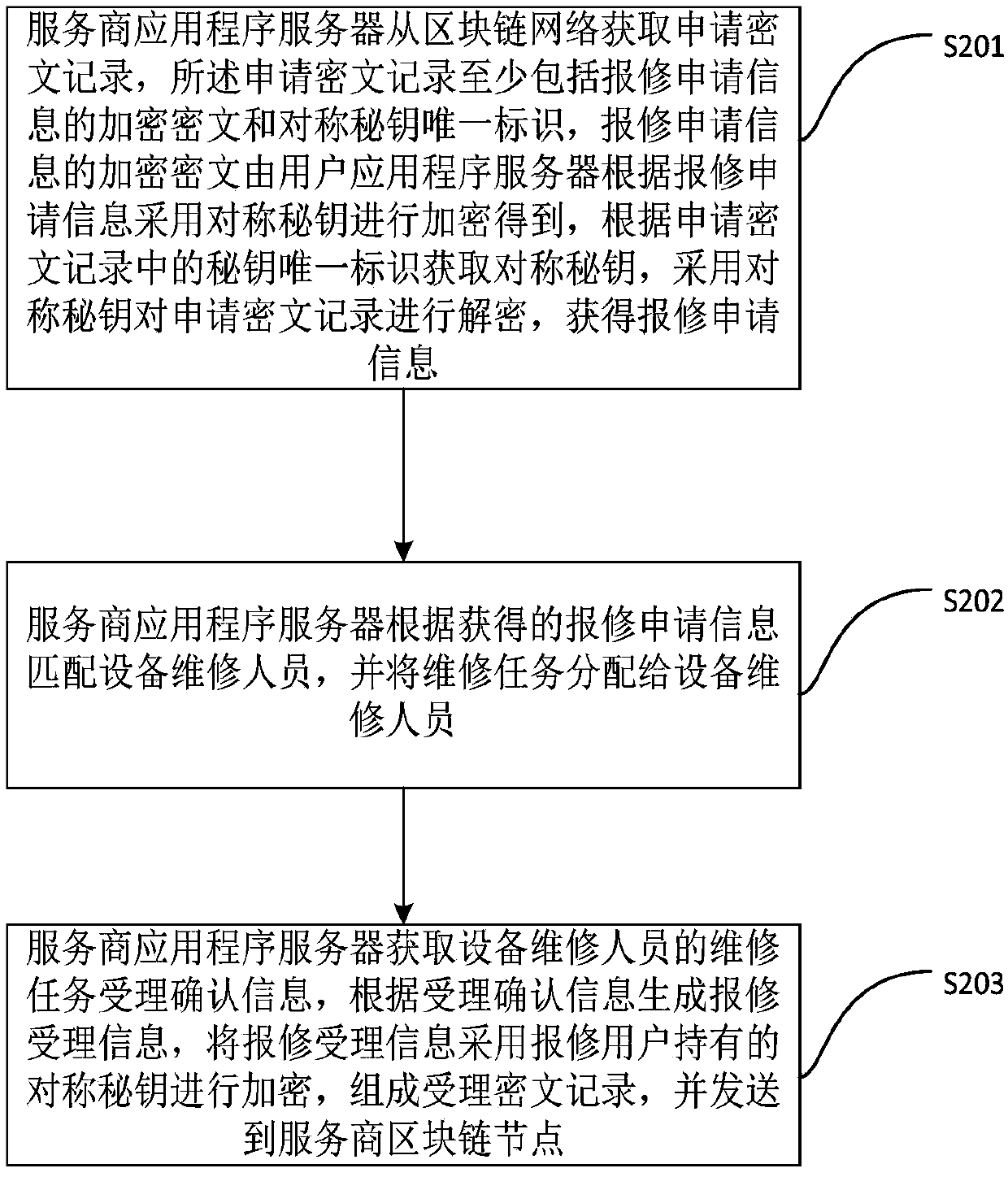
User equipment repair method, server, system and medium capable of protecting privacy
ActiveCN109523040AProtect data privacyAvoid malicious use and tamperingDigital data protectionChain networkApplication server
The user equipment repair method capable of protecting privacy disclosed by the invention is applicable to a user terminal, and comprises the following steps that: a user application program server acquires repair request information sent by a repair user; Inquiring information of a faulty equipment service provider according to faulty equipment information in the repair request information to generate repair application information; Inquiring a symmetric key and a unique identifier of the symmetric key held by a faulty equipment service provider, encrypting the repair application informationby adopting the symmetric key to obtain an application ciphertext record, sending the application ciphertext record to a user block chain node, and performing information synchronization of each blockchain node by the block chain network through a consensus algorithm; And obtaining the accepted ciphertext record from the block chain network, decrypting the accepted ciphertext record by adopting the symmetric key, obtaining repair acceptance information, and finishing repair acceptance. The data of each party is encrypted through the encryption algorithm, the possibility that the data is maliciously utilized and tampered is avoided, the data privacy of each participant is protected, and the security is high.
Owner:南京荣链科技有限公司
Radio-frequency multi-functional intelligent card
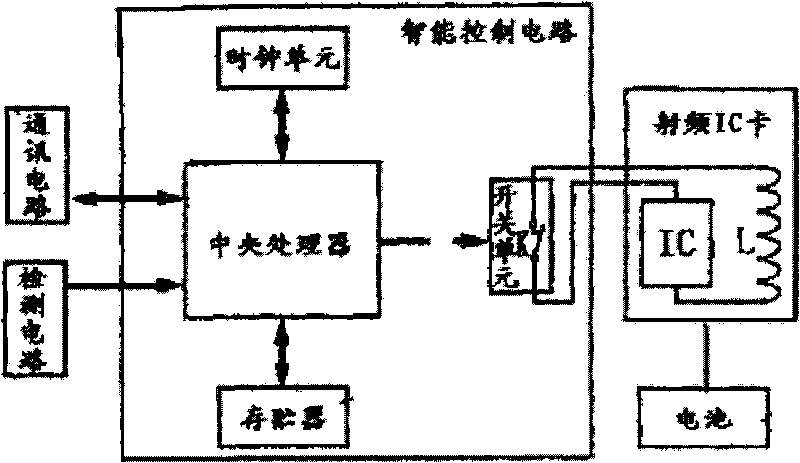
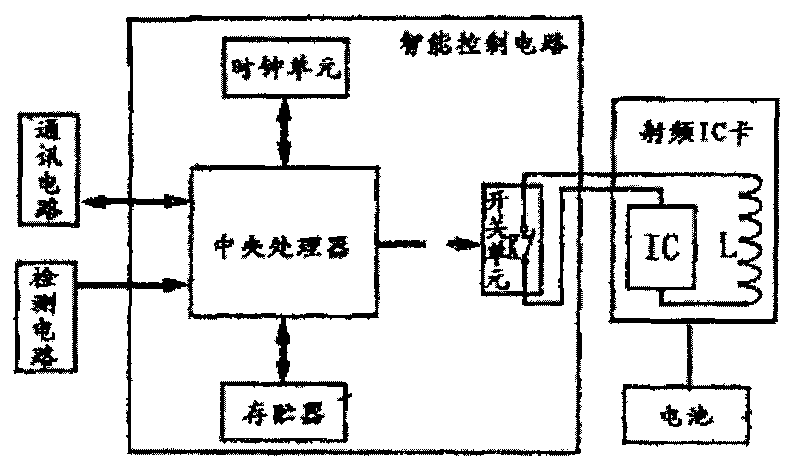
InactiveCN101706881ASimple structureEasy to makeRecord carriers used with machinesRadio frequencyIntegrated circuit
The invention provides a radio-frequency multi-functional intelligent card which relates to an IC card, in particular to a combined type radio-frequency IC card of which the working state is controlled in an intelligent way. Because the working state of the prior radio-frequency IC card can not be controlled, the prior radio-frequency IC card can not meet certain special applications. The invention aims to provide a novel radio-frequency IC card which combines an intelligent control circuit and a traditional radio-frequency IC card into a whole. The intelligent control circuit, a communication circuit, a detection circuit and the radio-frequency IC card are combined into a whole, the radio-frequency IC card comprises two parts: a coil and an integrated circuit, and the coil is also an antenna of the radio-frequency IC card and is used for transmitting and receiving electronic data.
Owner:王倩
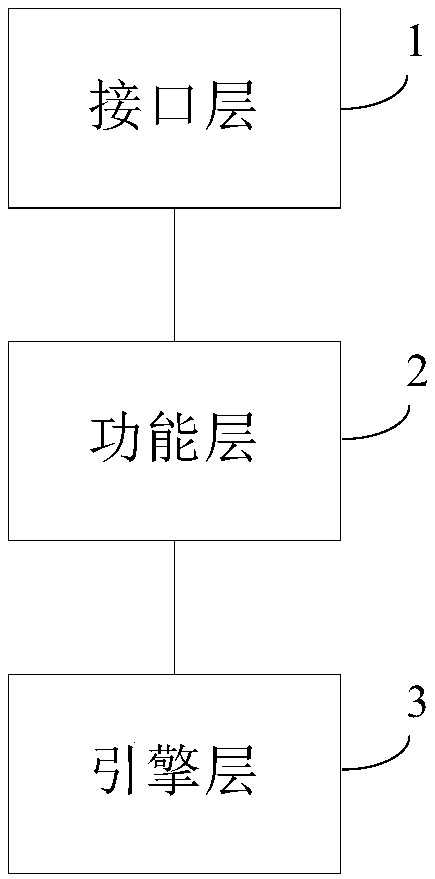
A security network middleware for identity authentication, and a method and apparatus for implementing the same
ActiveCN109492359APrevent Malicious UsePrevent theftDigital data protectionDigital data authenticationCheck markThird party
The invention discloses a security network middleware for identity authentication, a method and apparatus for implementing the same. The middleware comprises an interface layer, a function layer and an engine layer. The interface layer is located on top of the function layer and is used for providing a channel for the client to call the middleware. The function layer is located on top of the engine layer, and is used for providing service interface to the interface layer, and is responsible for service realization of the middleware. The service includes signature, check mark, encryption and decryption. The engine layer comprises a national secret algorithm engine, an OpenSSL algorithm engine and a hardware algorithm engine. The middleware of the application is a front terminal of the authentication platform for collecting user information, which provides protection for safely collecting user identity information and avoids malicious use of the user identity information after the third-party network application collects the user identity information. At the same time, the user identity information is avoided to be stolen in the transmission process from the client to the authentication platform and from the authentication platform to the third-party network application.
Owner:北京庚金科技有限公司
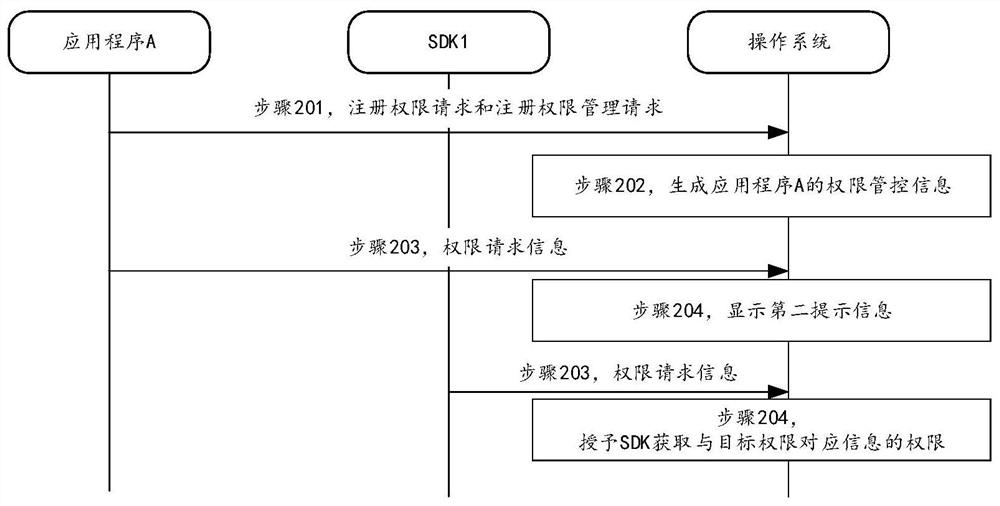
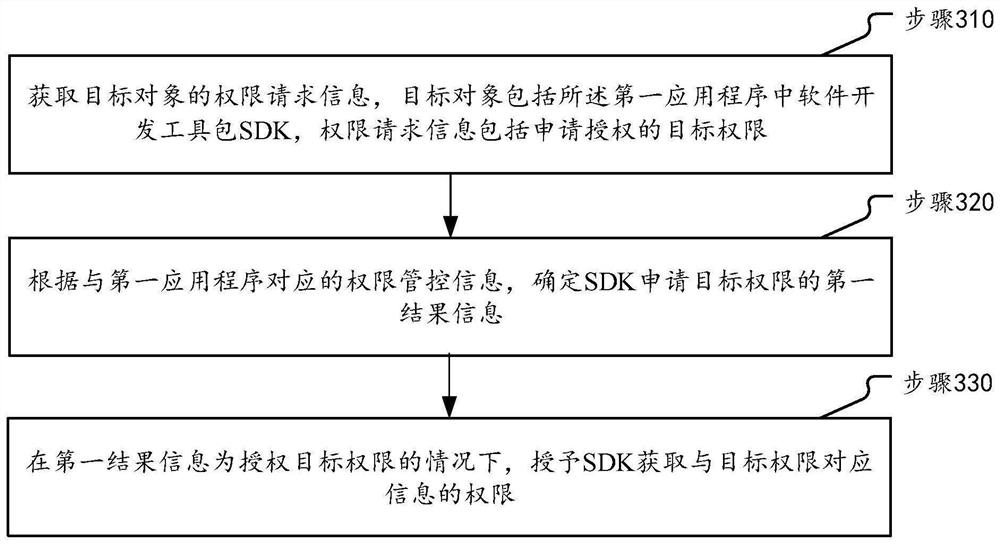
Authority management method and device and electronic equipment
PendingCN113569288AImprove management and control efficiencyRest assuredDigital data protectionSoftware engineeringSoftware development
The invention discloses an authority management method and device and electronic equipment, and belongs to the technical field of communication. The method mainly comprises the steps of obtaining permission request information of a target object, wherein the target object comprises a software development kit SDK in a first application program, and the permission request information comprises target permission applying for authorization; according to authority control information corresponding to the first application program, determining first result information that the SDK applies for the target authority; and under the condition that the first result information is to authorize the target authority, granting the SDK to obtain the authority of the information corresponding to the target authority.
Owner:VIVO MOBILE COMM HANGZHOU CO LTD
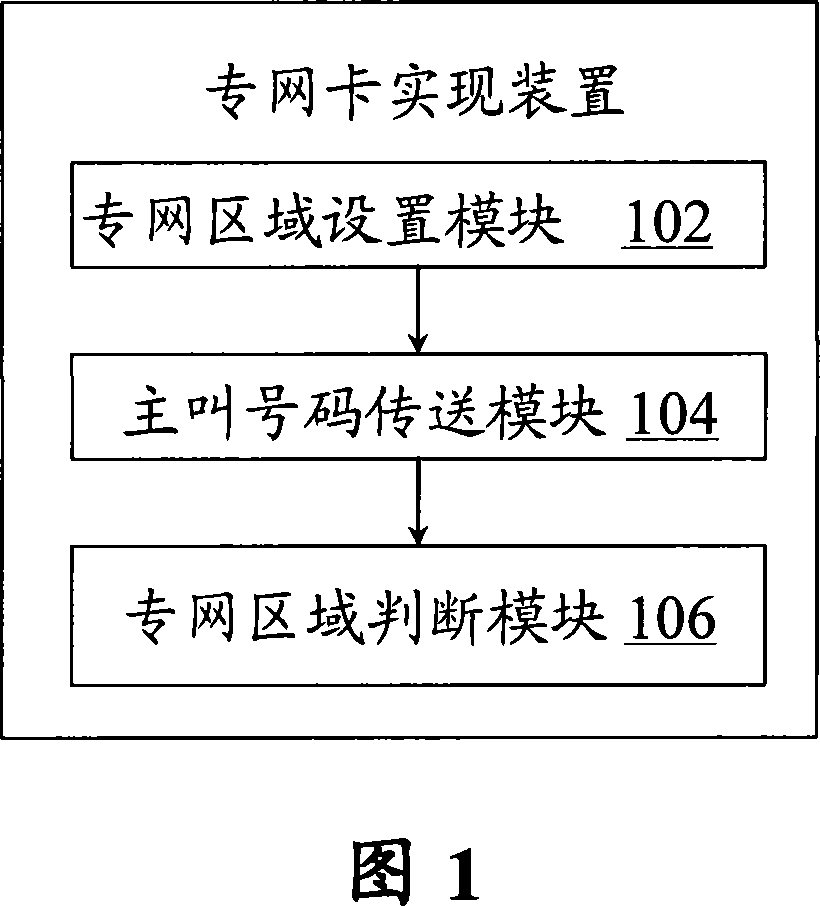
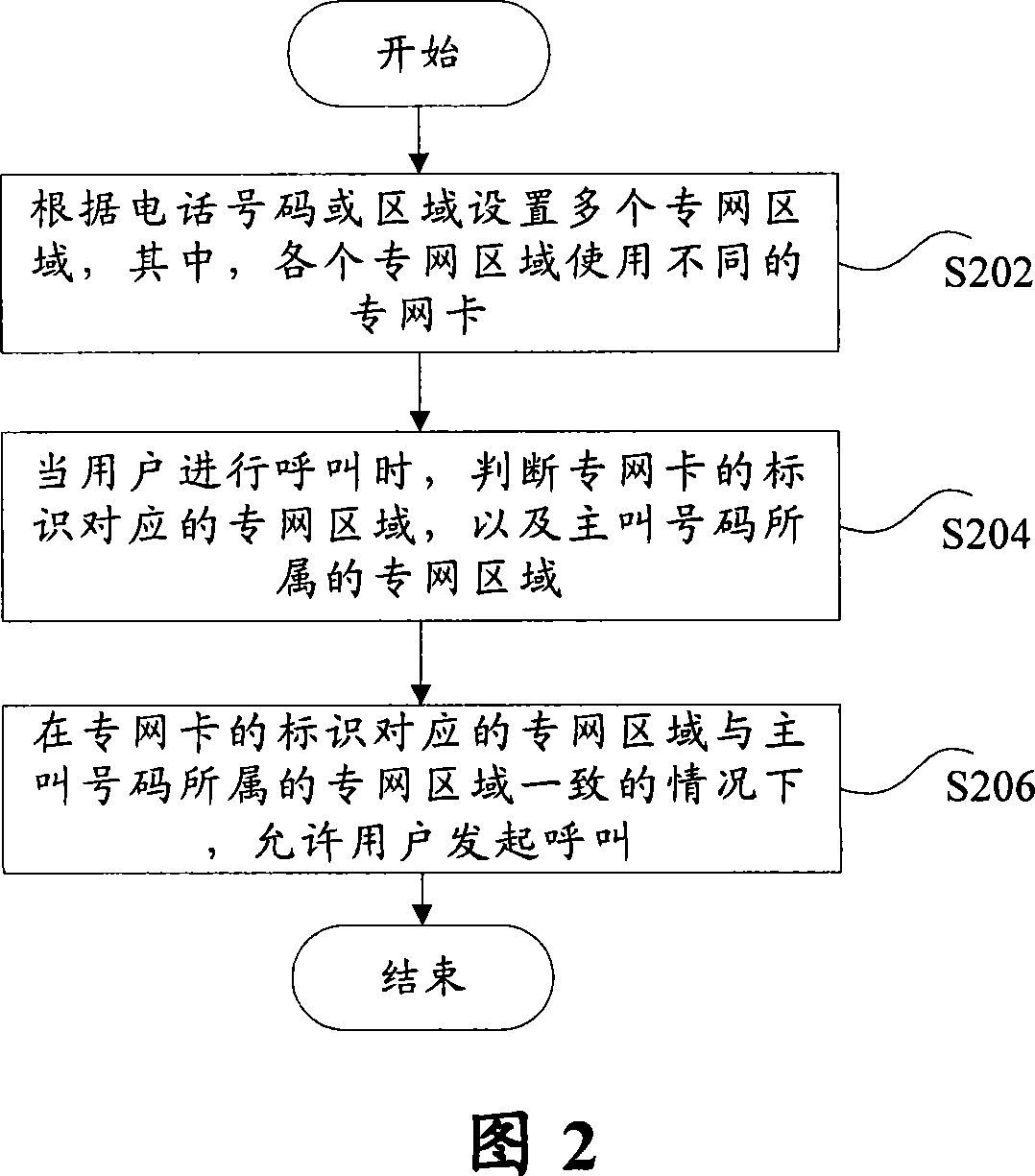
Special network card implementation device and method
InactiveCN101056471APrevent Malicious UseUse balanceUnauthorised/fraudulent call preventionRadio/inductive link selection arrangementsComputer hardware
Owner:ZTE CORP
Collection system based on three-dimensional bar codes
ActiveCN107657021AMalicious modification cannotGuaranteed correctnessData processing applicationsCo-operative working arrangementsCollection systemWeb page
The invention discloses a collection system based on three-dimensional bar codes. The system comprises the following information collection processes that 1), a plurality of three-dimensional bar codes are generated, wherein the three-dimensional bar codes at least comprise reporting three-dimensional bar codes, and copy-prevention areas are set on the reporting three-dimensional bar codes; 2), users scan the reporting three-dimensional bar codes through terminals, the users verify the authenticity of the reporting three-dimensional bar codes through matching of preset rules and the copy-prevention areas, and if the reporting three-dimensional bar codes are verified successfully, the users send reporting requests; 3), after the system receives the reporting requests, the system carries outunique numbering on the users and displays preset declaration information web pages on the terminals of the users; and 4), the users fill out the declaration information web pages and submit the declaration information web pages, and the system receives form item information of the declaration information web pages filled out by the users, carries out preliminary verification on the form item information according to preset rules and uploads the form item information and unique serial numbers to a cloud platform after the preliminary verification is successful.
Owner:CN3WM XIAMEN NETWORK TECH CO LTD
Pre-ordering management method, device and system
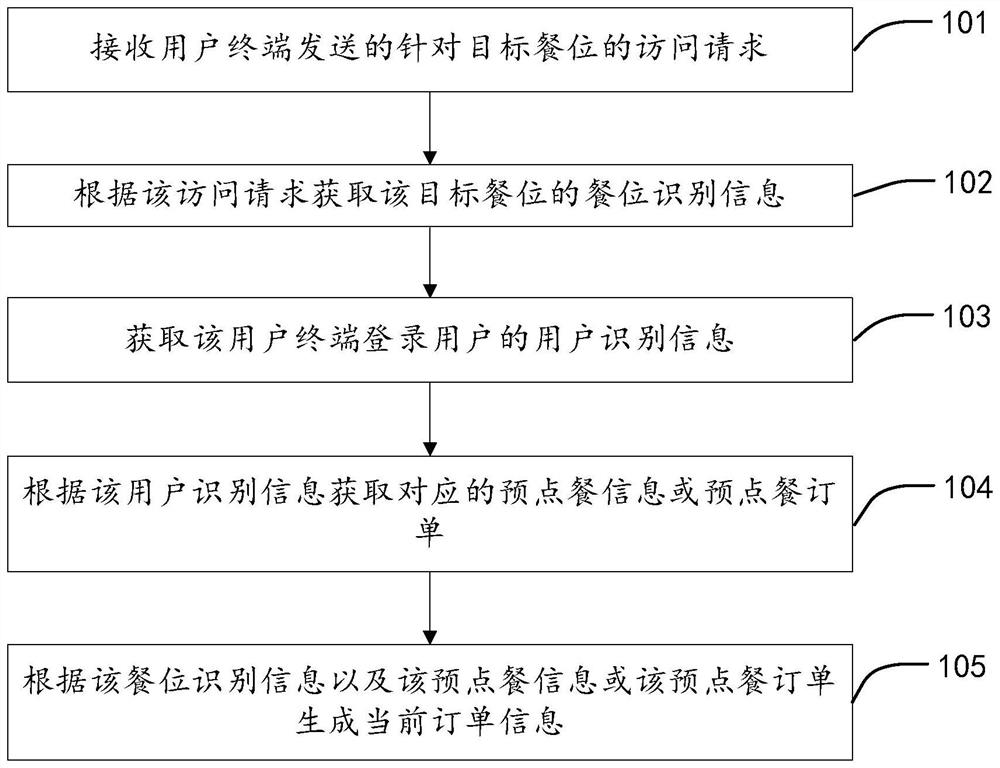
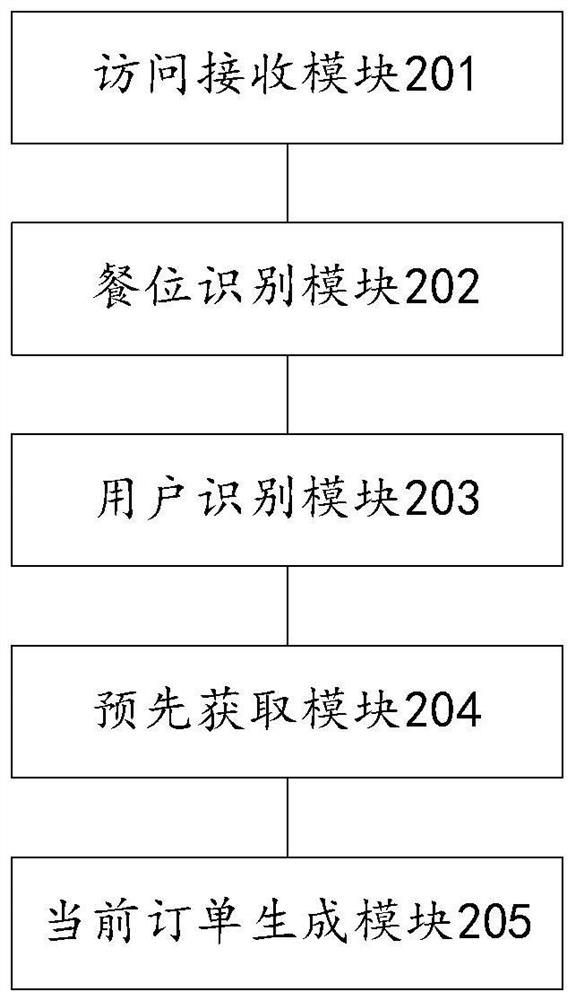
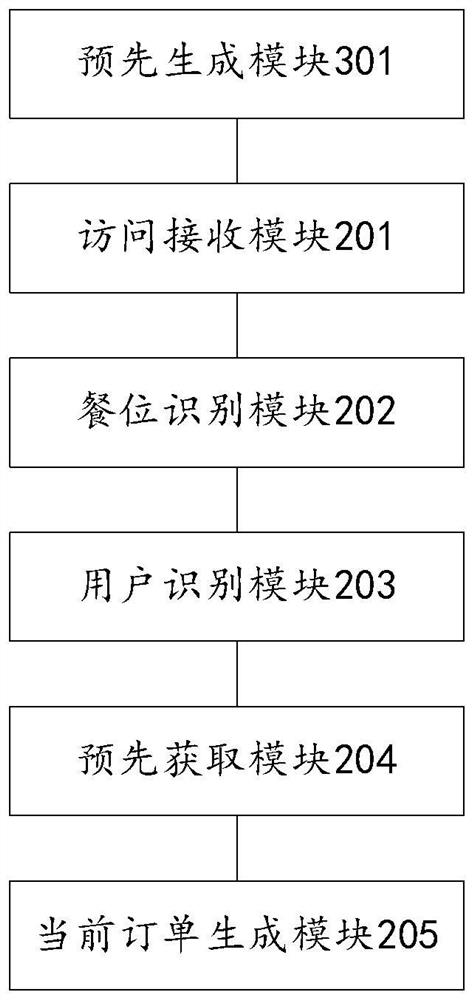
PendingCN111738471ASave ordering timePrevent Malicious UseReservationsDigital data authenticationEngineeringData mining
The invention discloses a pre-ordering management method, device and system. The method comprises the following steps: receiving an access request for a target dining seat sent by a user terminal; acquiring dining seat identification information of the target dining seat according to the access request; acquiring user identification information of a login user of the user terminal; acquiring corresponding pre-ordering information or a pre-ordering order according to the user identification information; and generating current order information according to the dining seat identification information and the pre-ordering information or the pre-ordering order. According to the method, the pre-ordering information or the pre-ordering order pre-generated by the ordering user is effectively applied to the target meal position, so the rapid ordering operation is realized, and the ordering time is saved.
Owner:刘高峰
Exclusive vehicle-mounted GNSS (Global Navigation Satellite System) signal compensation device and positioning system and method
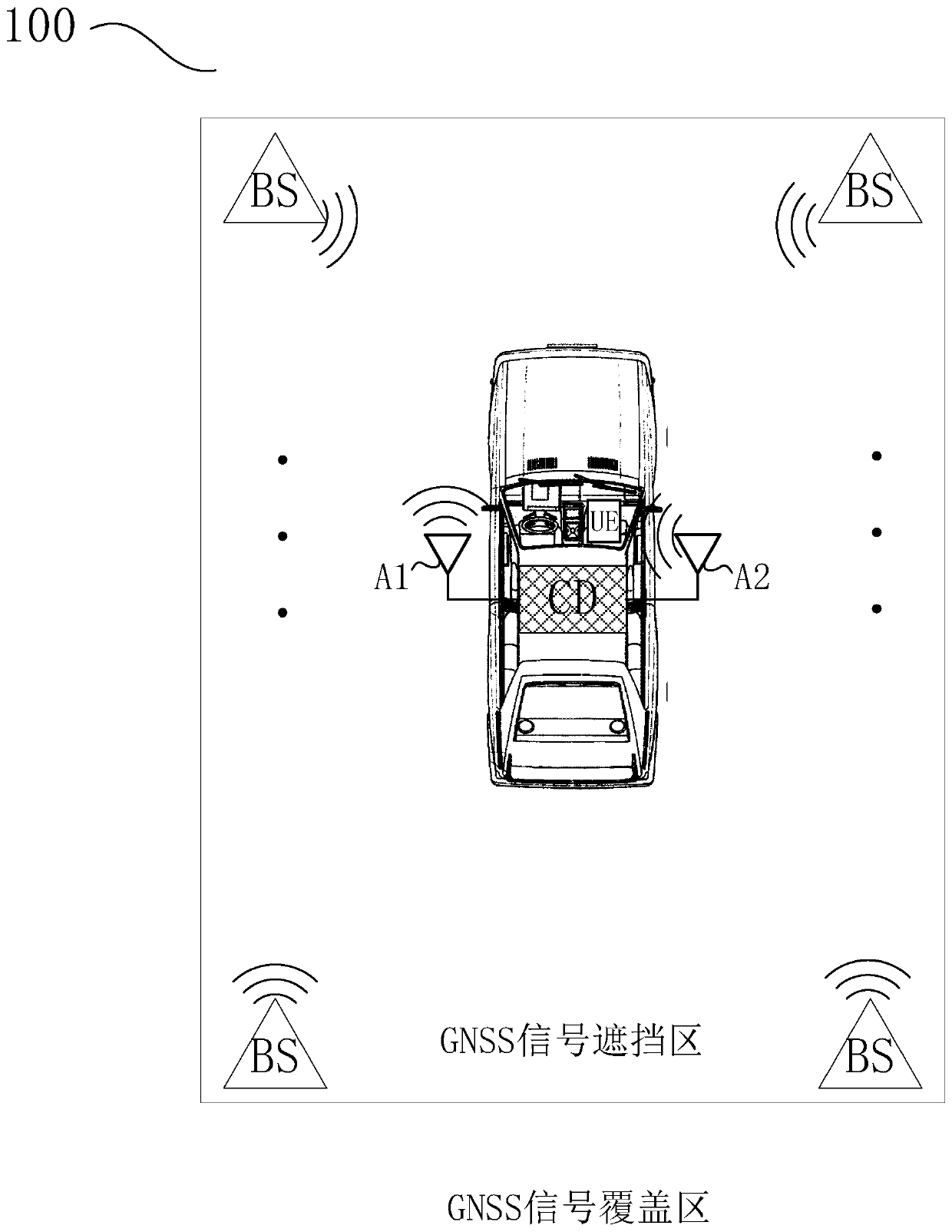
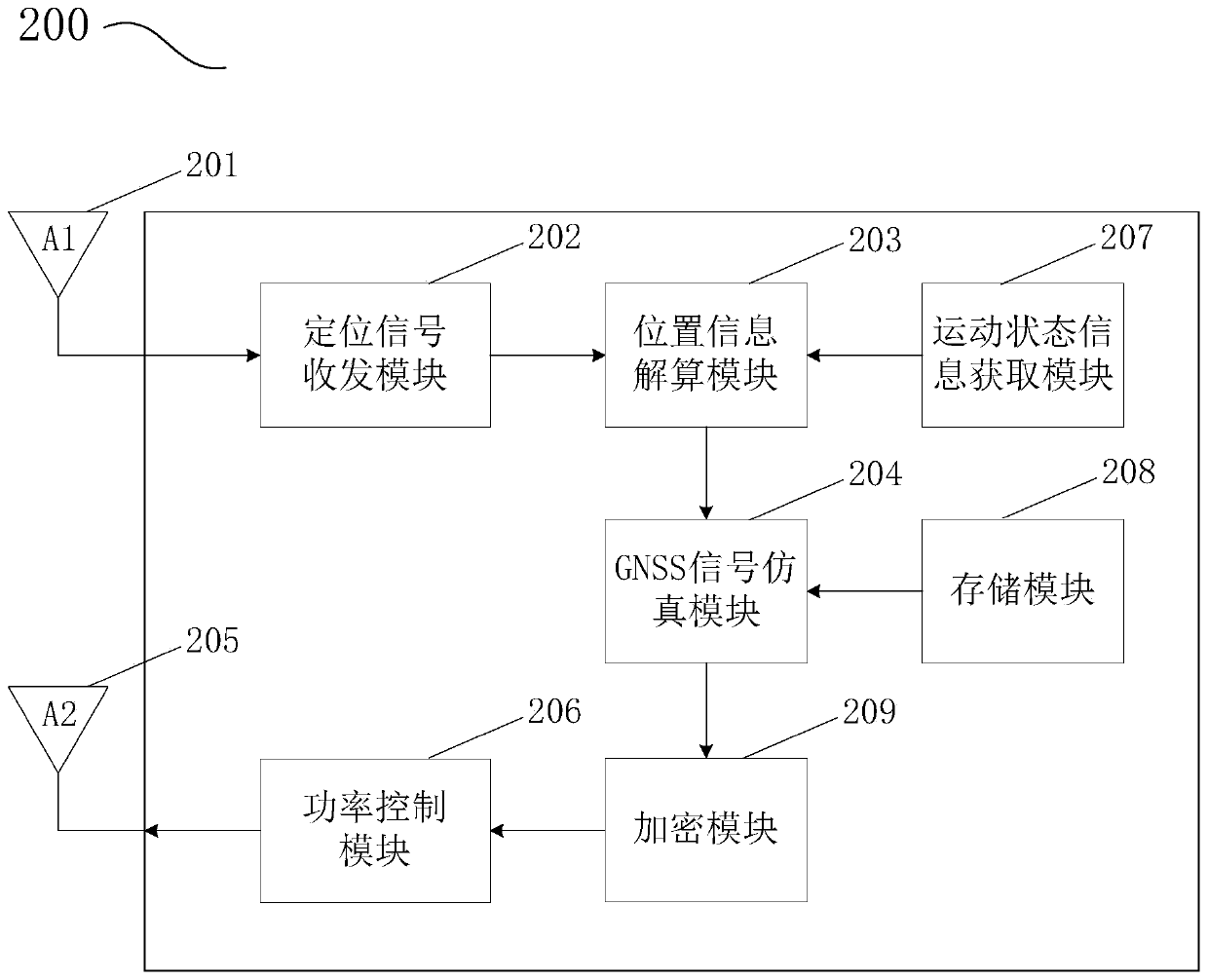
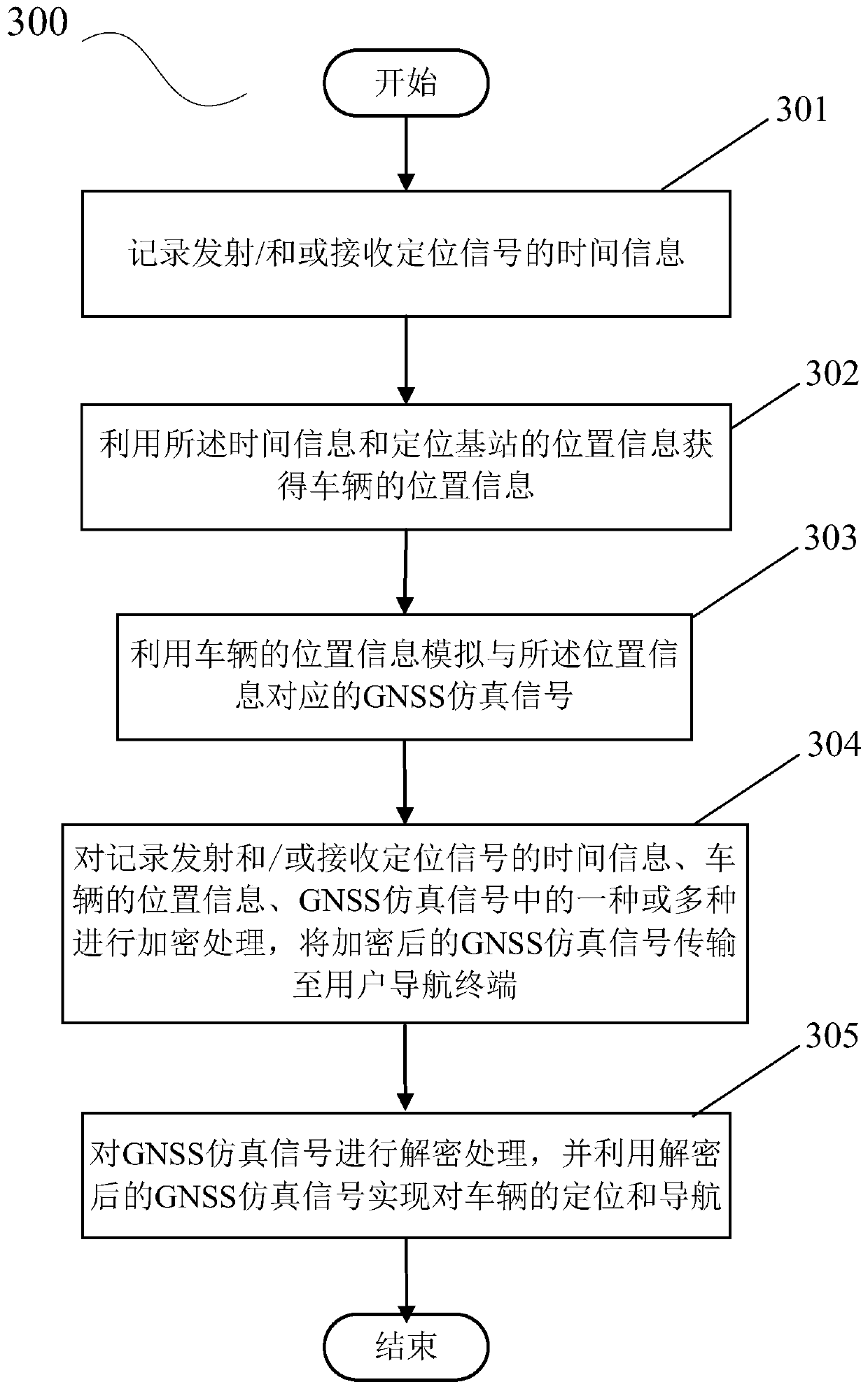
ActiveCN110632631AThe problem of poor implementation experienceImprove experienceSatellite radio beaconingHigh level techniquesTime informationComputer terminal
The invention discloses an exclusive vehicle-mounted GNSS (Global Navigation Satellite System) signal compensation device and an exclusive vehicle-mounted GNSS signal blind compensation positioning system and method. The exclusive vehicle-mounted GNSS signal compensation device solves the position information of a vehicle through a self-built positioning system and simulates a corresponding GNSS simulation signal. The exclusive vehicle-mounted GNSS signal compensation device comprises an encryption module, wherein the encryption module is used for encrypting one or more of time information forrecording the transmission and / or reception of a positioning signal, position information of the vehicle, the GNSS simulation signal and a GNSS satellite signal, and then radiating the encrypted information to a navigation terminal in the vehicle. According to the scheme disclosed by the invention, the information is encrypted, and only the specified application program can realize decryption processing through pre-stored decryption information, so that malicious use of an unauthorized terminal or application program is avoided, and the practical benefits of positioning system manufacturers and cooperative application program merchants are further guaranteed.
Owner:KUNCHEN TECH CO LTD
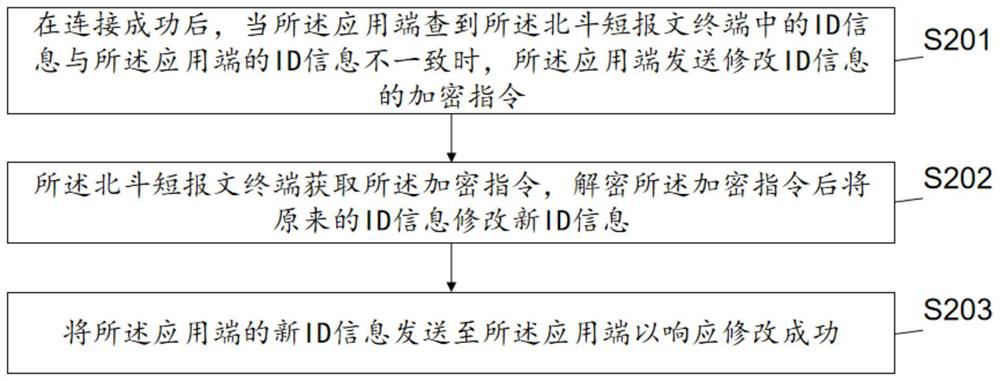
Security verification method and system for Beidou short message terminal
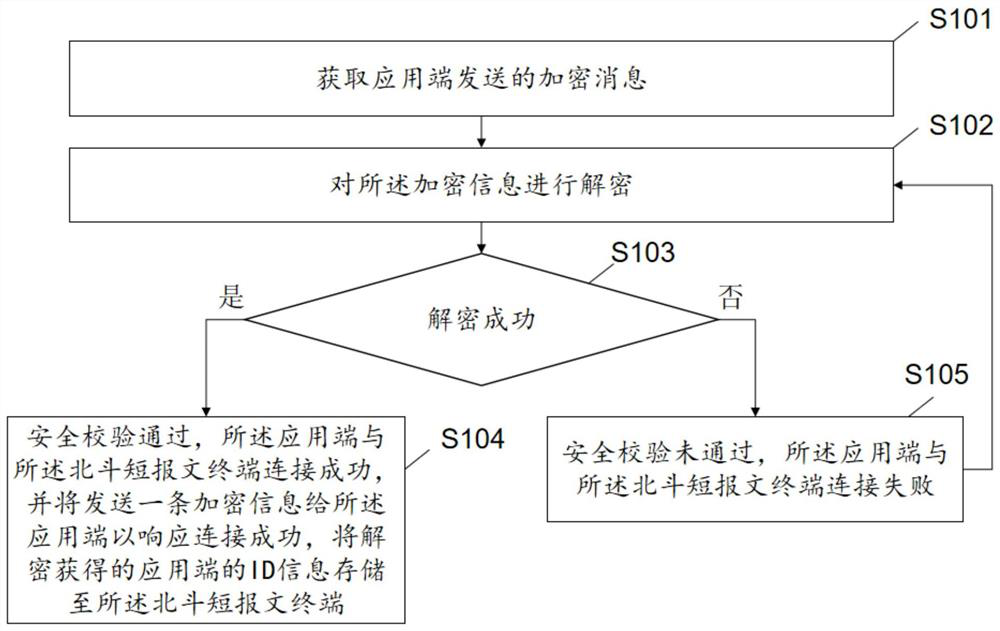
ActiveCN113099446APrevent Malicious UseImprove securityConnection managementSecurity arrangementThird partyTerminal equipment
The invention discloses a safety verification method for a Beidou short message terminal. The method comprises the following steps: acquiring an encrypted message sent by an application end; decrypting the encrypted information; judging whether decryption is successful or not: if yes, passing safety verification, determining that the application end is successfully connected with the Beidou short message terminal, sending a piece of encryption information to the application end to respond to successful connection, and storing the ID information, obtained through decryption, of the application end in the Beidou short message terminal; if not, not passing safety verification, determining that the connection between the application end and the Beidou short message terminal fails, so the Beidou terminal equipment can be prevented from being maliciously used by a third party, and verifying, binding and perfecting the security of a Beidou communication link through the terminal equipment end. The invention further discloses a safety verification system of the Beidou short message terminal. According to the invention, the Beidou terminal equipment can be prevented from being maliciously used by a third party, and the security of a Beidou communication link is improved through verification and binding of the terminal equipment end.
Owner:广东海聊科技有限公司
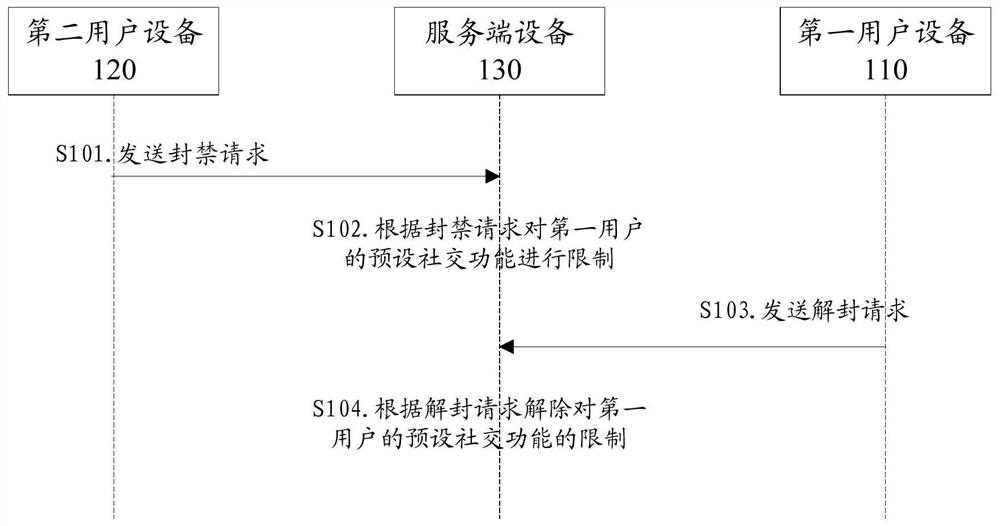
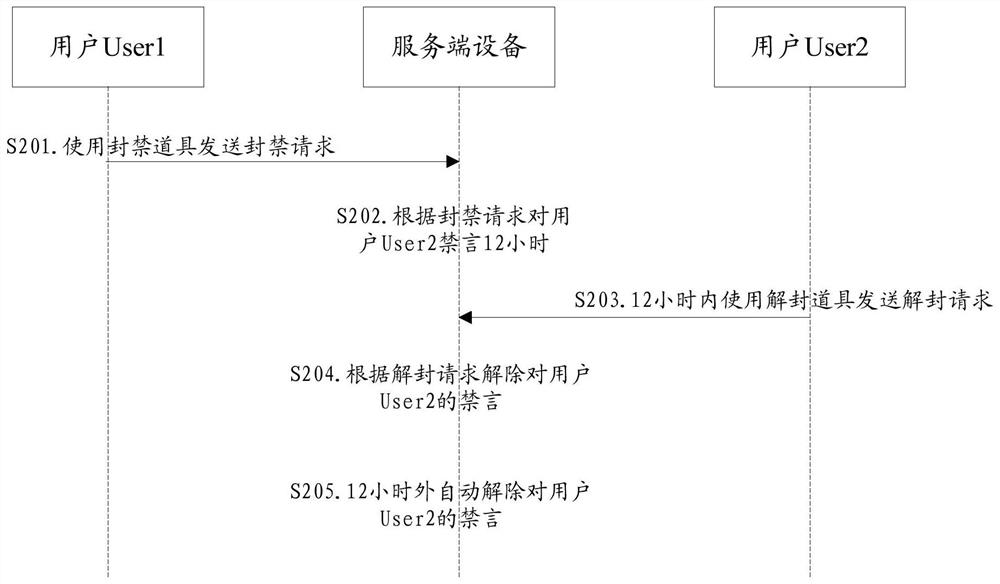
User social function adjustment method and device and computer readable medium
PendingCN111951118AImprove experienceBalance RequestsData processing applicationsWebsite content managementComputer securitySocial function
According to a user social function adjustment scheme provided by the invention, a user can request to limit the preset social functions of other users without waiting for auditing, user experience isimproved, the limited user can also request to release the limit, and the server equipment balances the request times of the two users by controlling the number of issued props, so that the user experience is improved. When bad users can be effectively controlled, malicious use of judgment and processing rights is avoided.
Owner:SHANGHAI LIANSHANG NETWORK TECHNOLOGY CO LTD
Bidding informatization management system with confidentiality function
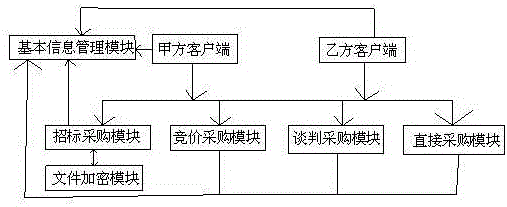
InactiveCN105869042AEasy to useReduce error rateFinanceDigital data protectionInformatizationConfidentiality
The invention discloses a bidding informatization management system with a confidentiality function. The system comprises a basic information management module, a bidding procurement module, a file encryption module, a bidding procurement module, a negotiation procurement module and a direct procurement module. All the modules are connected with a first client and a second client through a network, client information of the first client and client information of the second client are checked, and the information is judged and then enters the corresponding modules. By means of the system, the system is provided with the procurement modules in various modes, switching in multiple systems is not needed, and use is more convenient. The system automatically judges which procurement module is used by the clients, and compared with manual judgment, the error rate is reduced. Meanwhile, confidentiality measures are added for unpublished biding documents, and justice and equity of bidding are ensured.
Owner:CHENGDU CHENYUE CONSTR PROJECT MANAGEMENT CO LTD
Method for preventing system short message service from being stolen
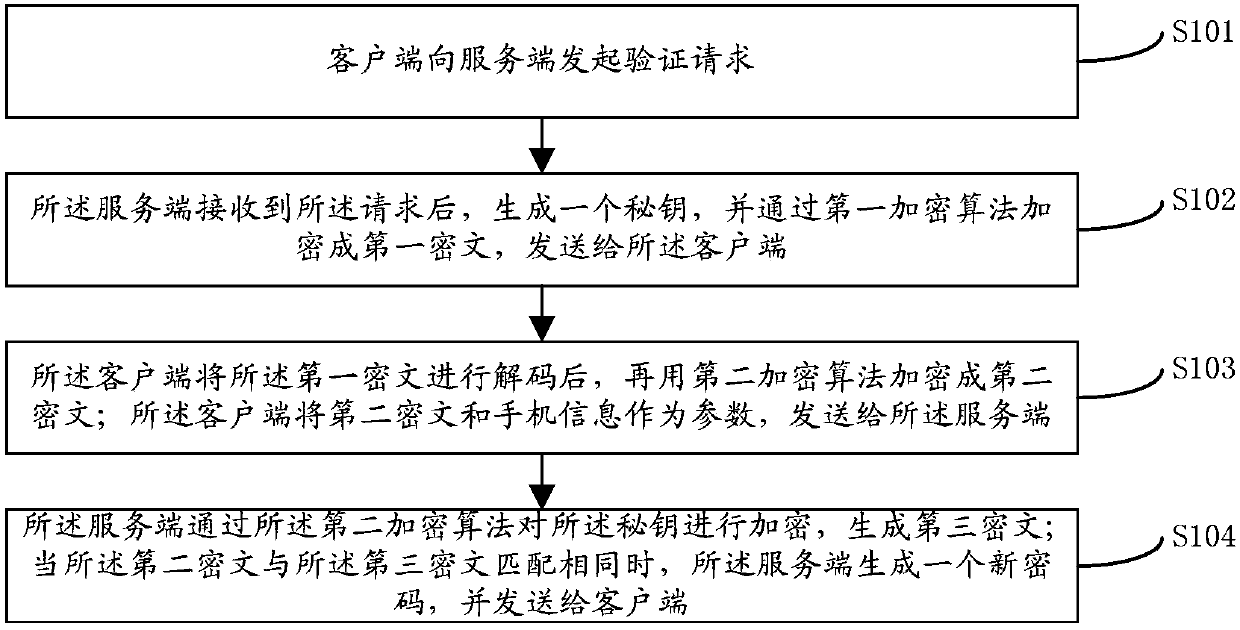
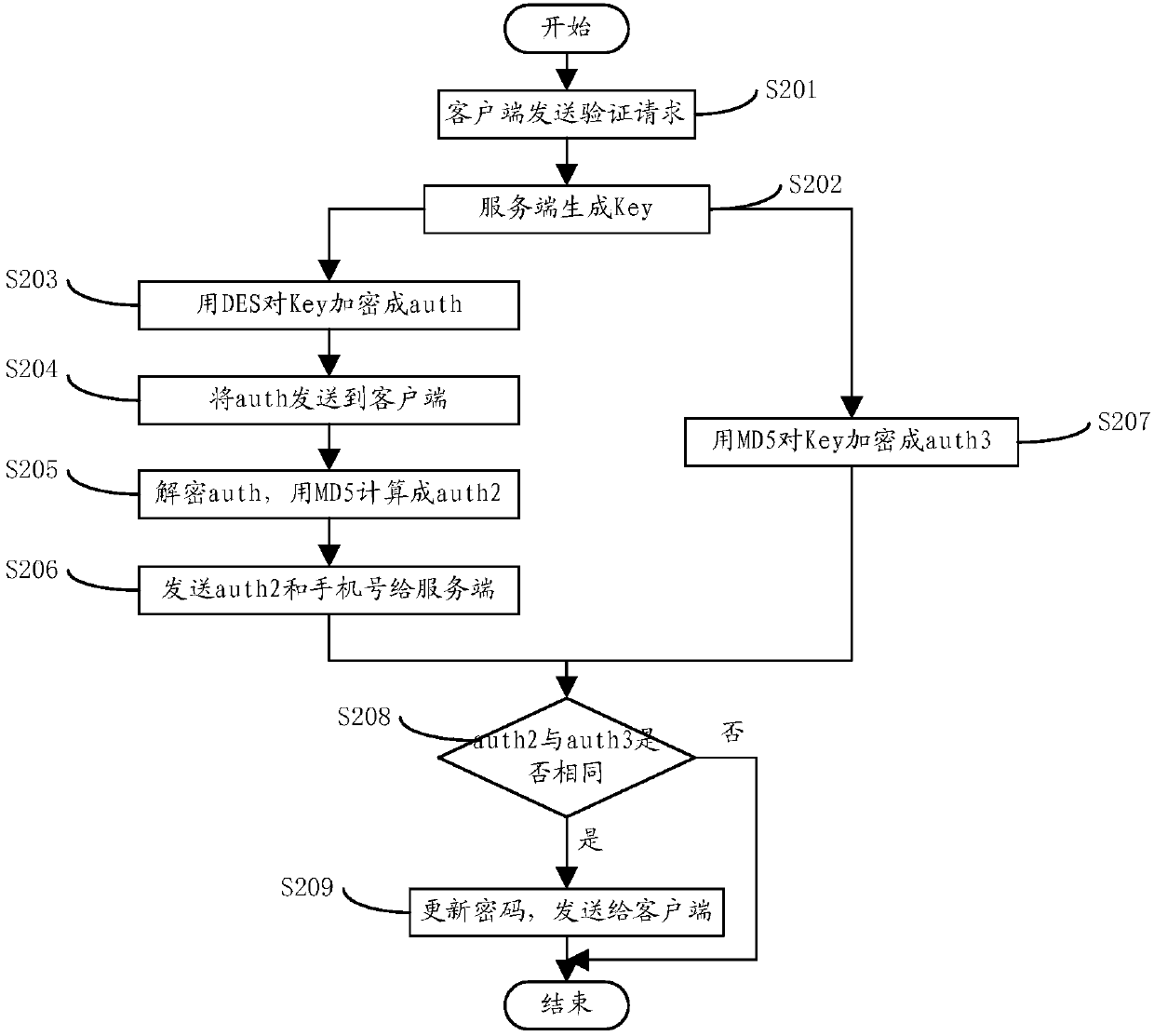
InactiveCN107864136AEnsure safetyPrevent Malicious UseKey distribution for secure communicationUser identity/authority verificationClient-sideText message
The invention relates to a method for preventing a system short message service from being stolen. The method comprises the steps as follows: a client initiates a verification request to a server; after receiving the request, the server generates a secret key, encrypts the secret key into a first ciphertext via a first encryption algorithm, and sends the first ciphertext to the client; after decoding the first ciphertext, the client encrypts the decoded ciphertext into a second ciphertext via a second encryption algorithm; the client uses the second ciphertext and user information as parameters, and sends the parameters to the server; the server encrypts the secret key via the second encryption algorithm to generate a third ciphertext; and when the second ciphertext is matched with the third ciphertext, the server generates a new password, and sends the new password to the client. According to the method provided by the invention, the secret key generated by the server after being encrypted by the client is matched with that after being encrypted by the server, for ensuing that a short message is sent by a user himself; and matching times and matching time are set, so that the system short message service is prevented from being used maliciously.
Owner:BEIJING KUWO TECH
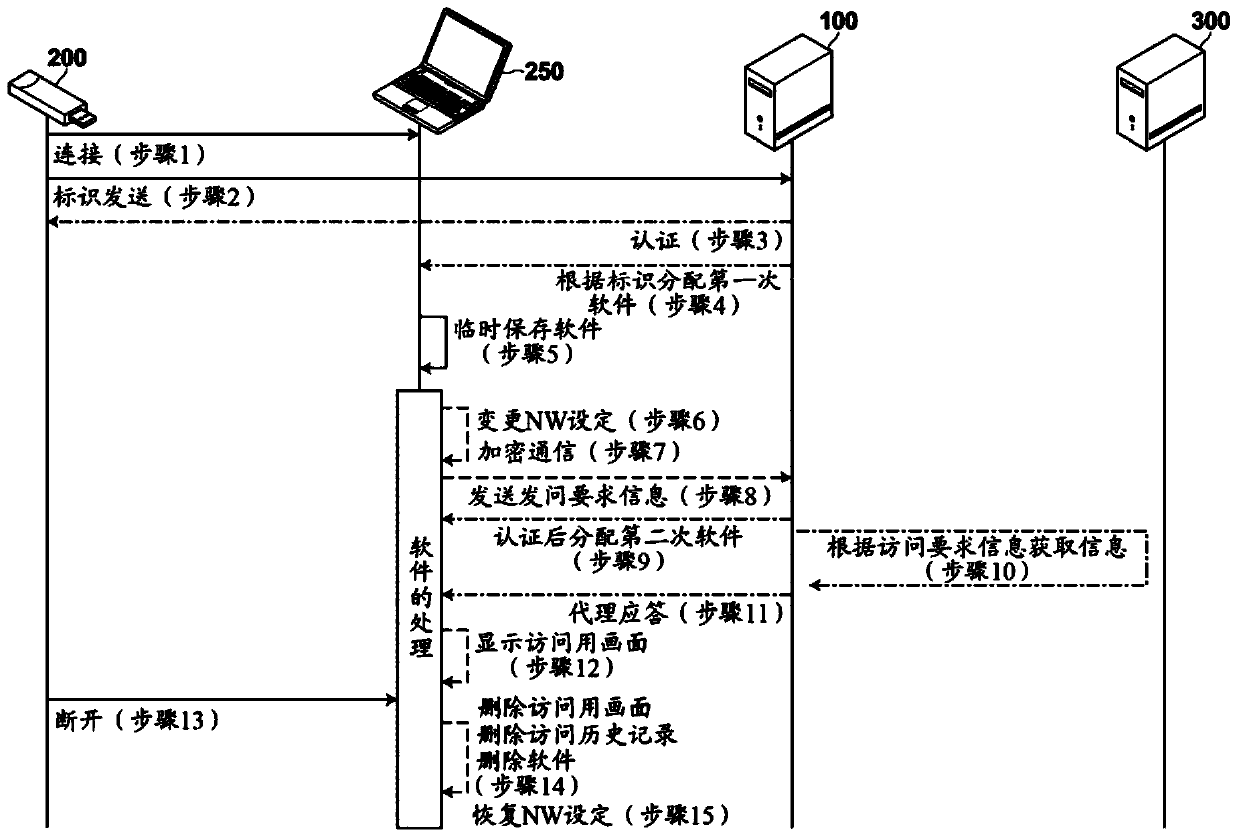
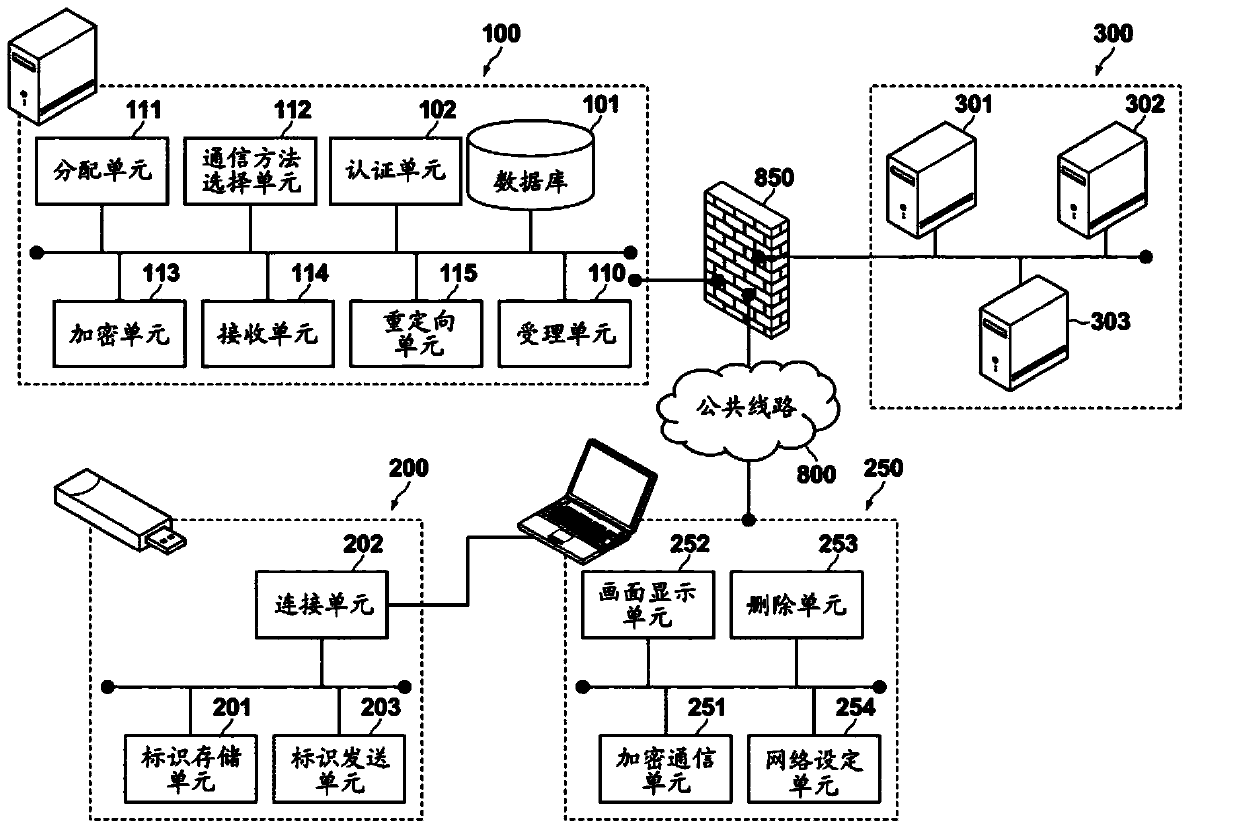
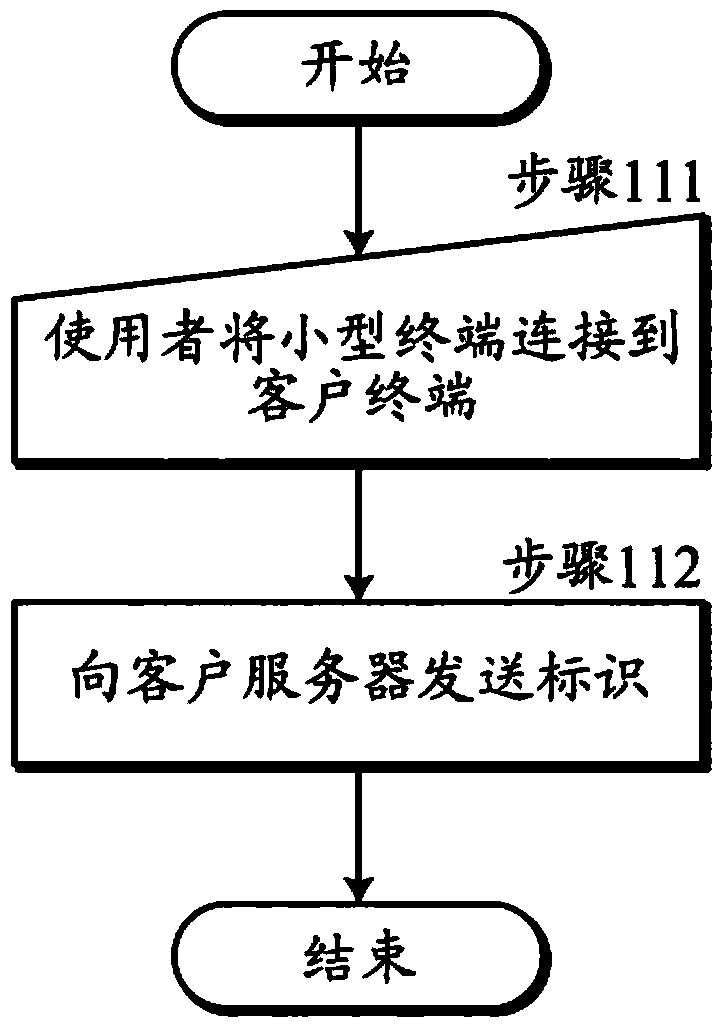
Virtual network building system, virtual network building method, small terminal, and authentication server
InactiveCN103731410ASetting omittedPrevent malicious useEncryption apparatus with shift registers/memoriesNetworks interconnectionNetwork Communication ProtocolsAuthentication server
The invention discloses a virtual network building system, a virtual network building method, a small terminal, and an authentication server. The virtual network building system of the invention includes a small terminal and an authentication server. The small terminal includes an identifier transmission unit automatically transmitting an identifier to the authentication server via a client terminal in a state in which a connection unit is connected to the client terminal. The authentication server includes an authentication unit performing authentication on the basis of the identifier of the small terminal, a distribution unit distributing software for encrypting communication to the client terminal according to selected communication protocol and encryption method, a reception unit receiving access request information regarding a request for access to the target apparatus, which is automatically transmitted from the distributed software, and a redirect unit making a proxy response of access of the client terminal to the target apparatus in response to the received access request information.
Owner:UKD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com