Pre-ordering management method, device and system
A management method and pre-ordering technology, applied in reservations, data processing applications, instruments, etc., can solve the problems of not providing pre-ordering methods, affecting restaurant benefits, and reducing seat utilization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
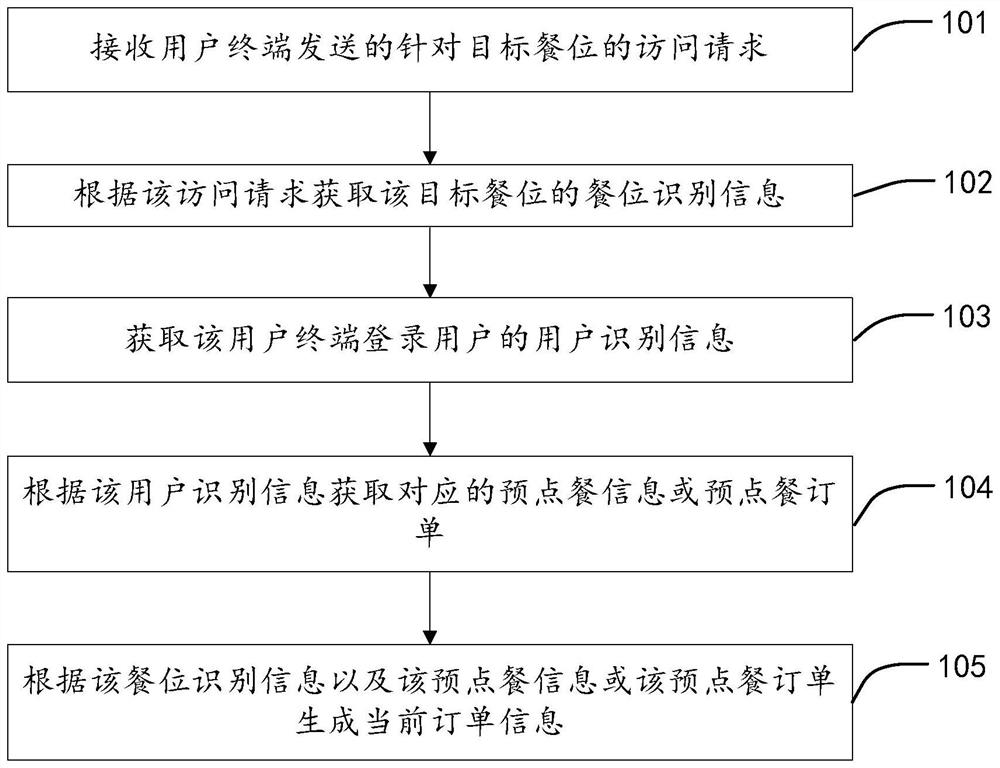
[0171] Specifically, the ordering server obtains the seat identification information of the target seat according to the access request, which may include various implementation methods, for example:
[0172] In one embodiment, the access request includes the seat identification information, and the meal ordering server acquires the seat identification information from the access request.
[0173] In one embodiment, the association relationship between the associated information and the seat identification information is established in advance, and if the access request contains the associated information associated with the seat identification information, then according to the association information in the association relationship Obtain the seat identification information in . For example, a relationship between a unique character string and seat identification information of the target seat is pre-established, that is, the associated information is the unique character st...
Embodiment approach 1
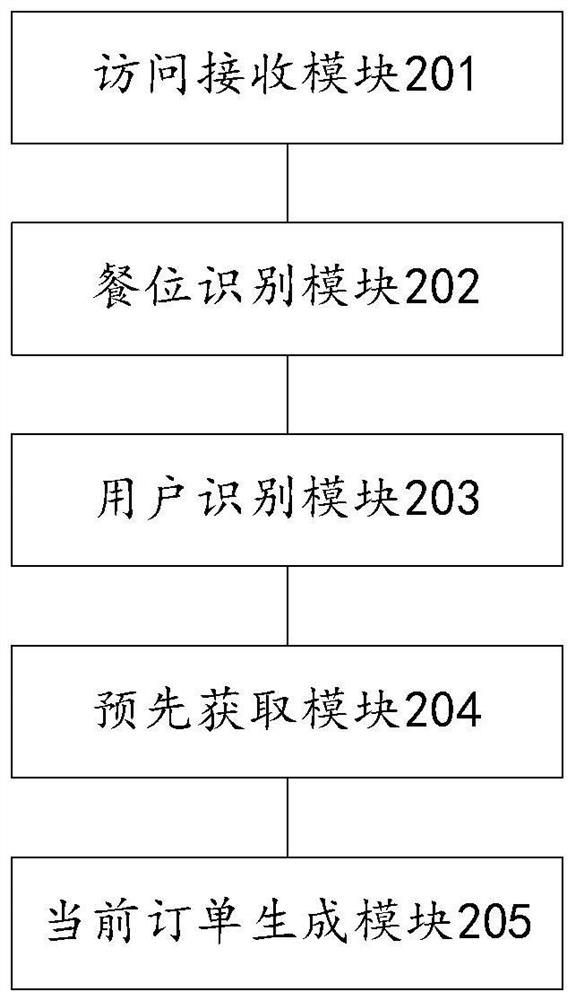
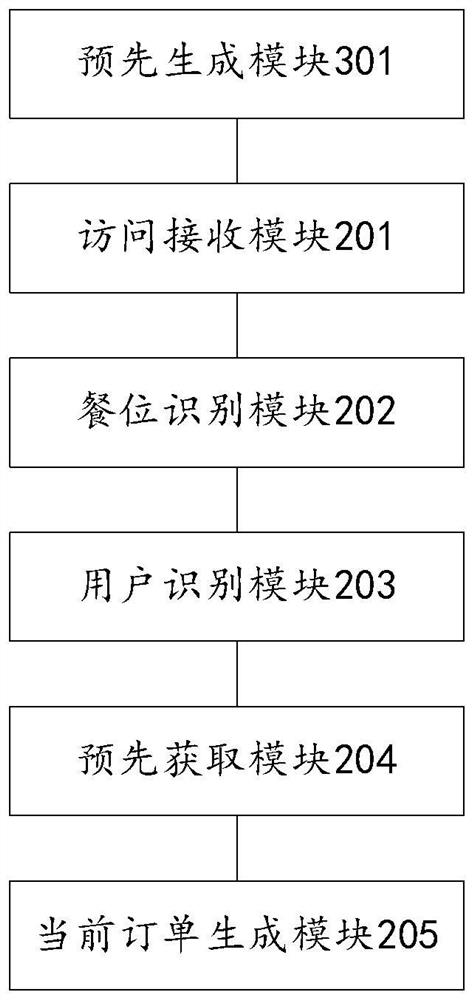
[0212] Embodiment 1: Step 105 is executed after confirmation by the merchant terminal.
[0213] The specific process of confirmation by the merchant terminal may include:
[0214] The ordering server generates prompt information corresponding to the target seat, and the prompt information is used to indicate whether the merchant terminal agrees to apply the login user's pre-order information or pre-order order to the target seat. The prompt information includes the user information of the logged-in user. For example, if the corresponding user information is set for the user in the ordering server, then the corresponding user information is obtained according to the user identification information, and the corresponding user information is the logged-in user. For another example, if the login user is a WeChat login user or Alipay login user, call the interface service provided by the WeChat or Alipay open platform, and obtain the user information of the login user after o...
Embodiment approach 2
[0218] Embodiment 2: Security verification is performed on the user terminal, and step 105 is performed if the user terminal passes the security verification.
[0219] Perform security verification on the user terminal, the specific process may include:
[0220] Generate the safety verification information corresponding to the seat identification information, for example, randomly generate a character string, and set the character string as the safety verification information corresponding to the seat identification information. Preferably, the randomly generated character string is four to six pure numbers of bits;
[0221] Inform the ordering user of the security verification information. For example, when the ordering user orders food, the restaurant staff will obtain the security verification information corresponding to the target seat through the merchant terminal, and the restaurant staff will inform the ordering user of the security verification information. u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com