Method for preventing system short message service from being stolen
A short message and server-side technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as malicious use of system short message services, and achieve the effect of preventing malicious use and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
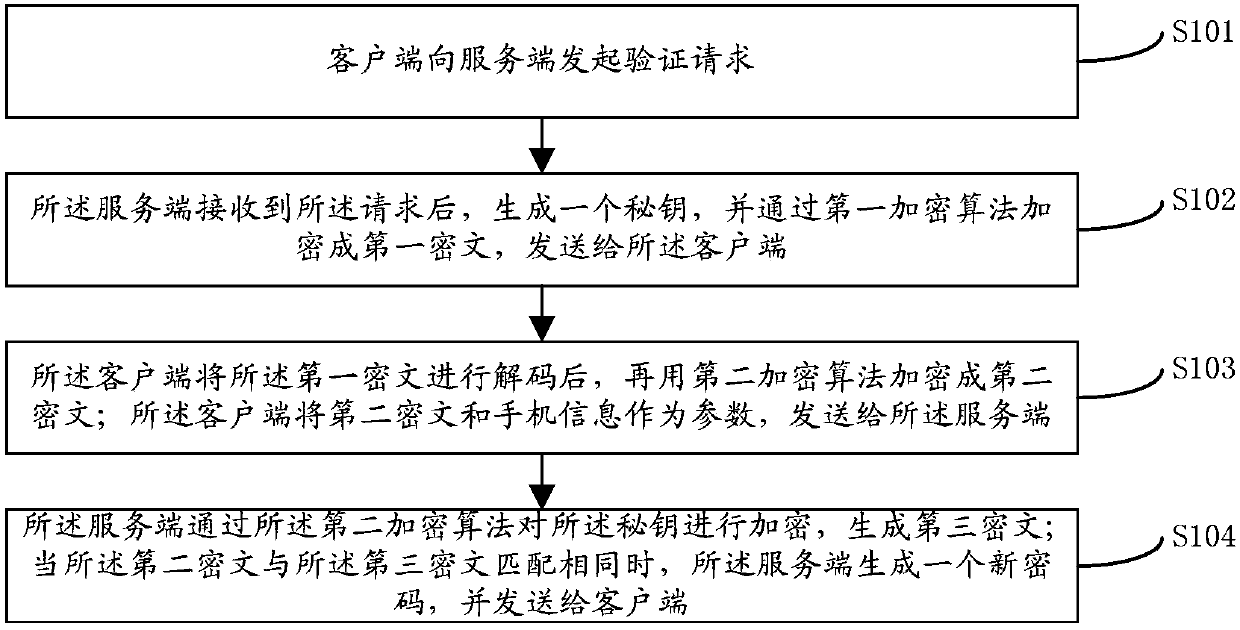
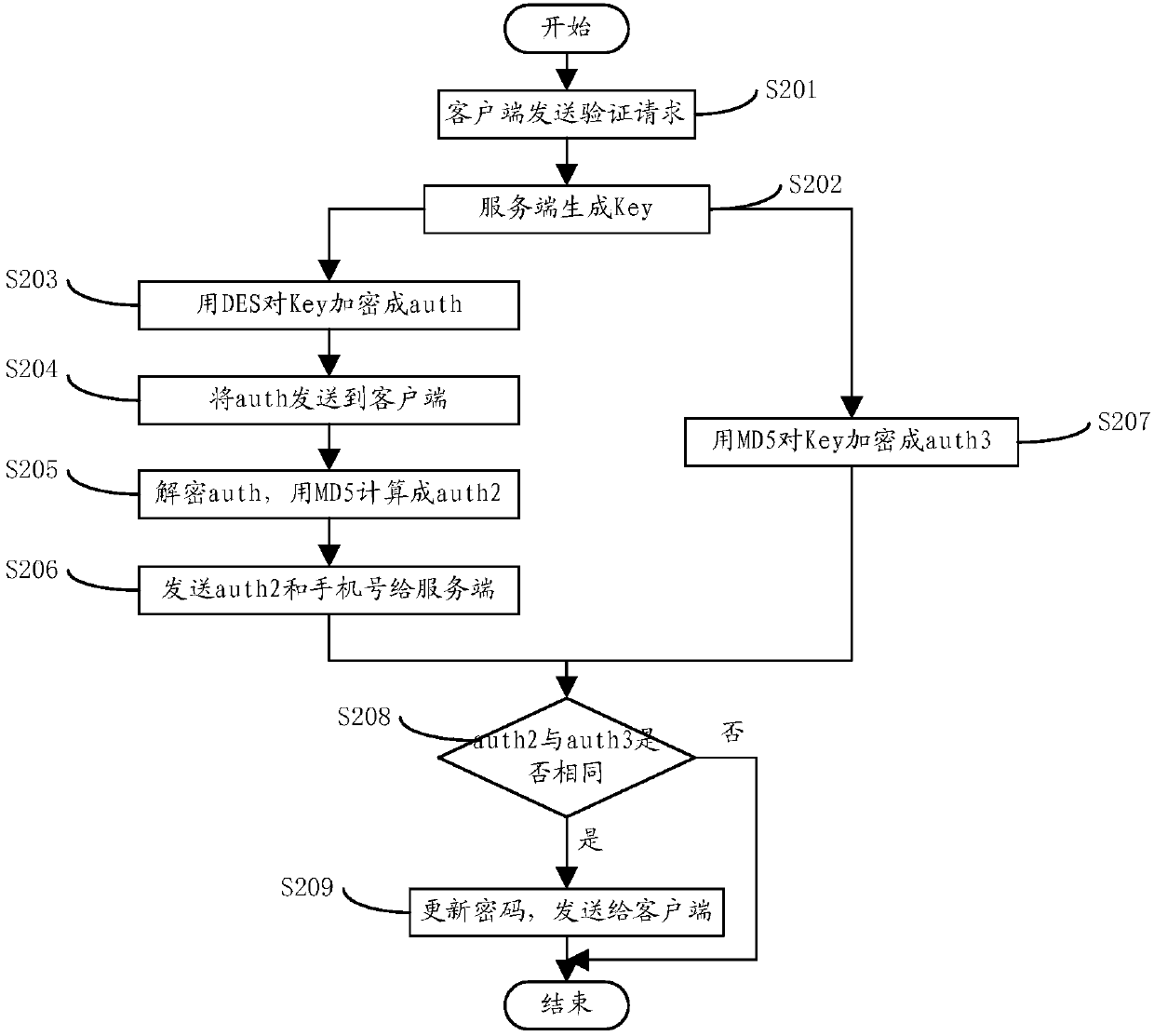
[0021] figure 1 It is a flow chart of the method for preventing the short message service of the system from being stolen in the present invention. Such as figure 1 As shown, the present invention proposes a method for preventing system short message service from being stolen, and the specific steps include:
[0022] Step 101, the client initiates a verification request to the server.
[0023] Specifically, when the user forgets the client login password, etc., the user needs to enter the mobile phone number for user verification, and the client sends a verification request to the server.
[0024] Step 102, after receiving the request, the server generates a key, encrypts it into a first ciphertext through a first encryption algorithm, and sends it to the client.
[0025] Specifically, after receiving the request sent by the client, the server randomly generates a key according to the received mobile phone number. In order to send security, the server encrypts the key befo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com