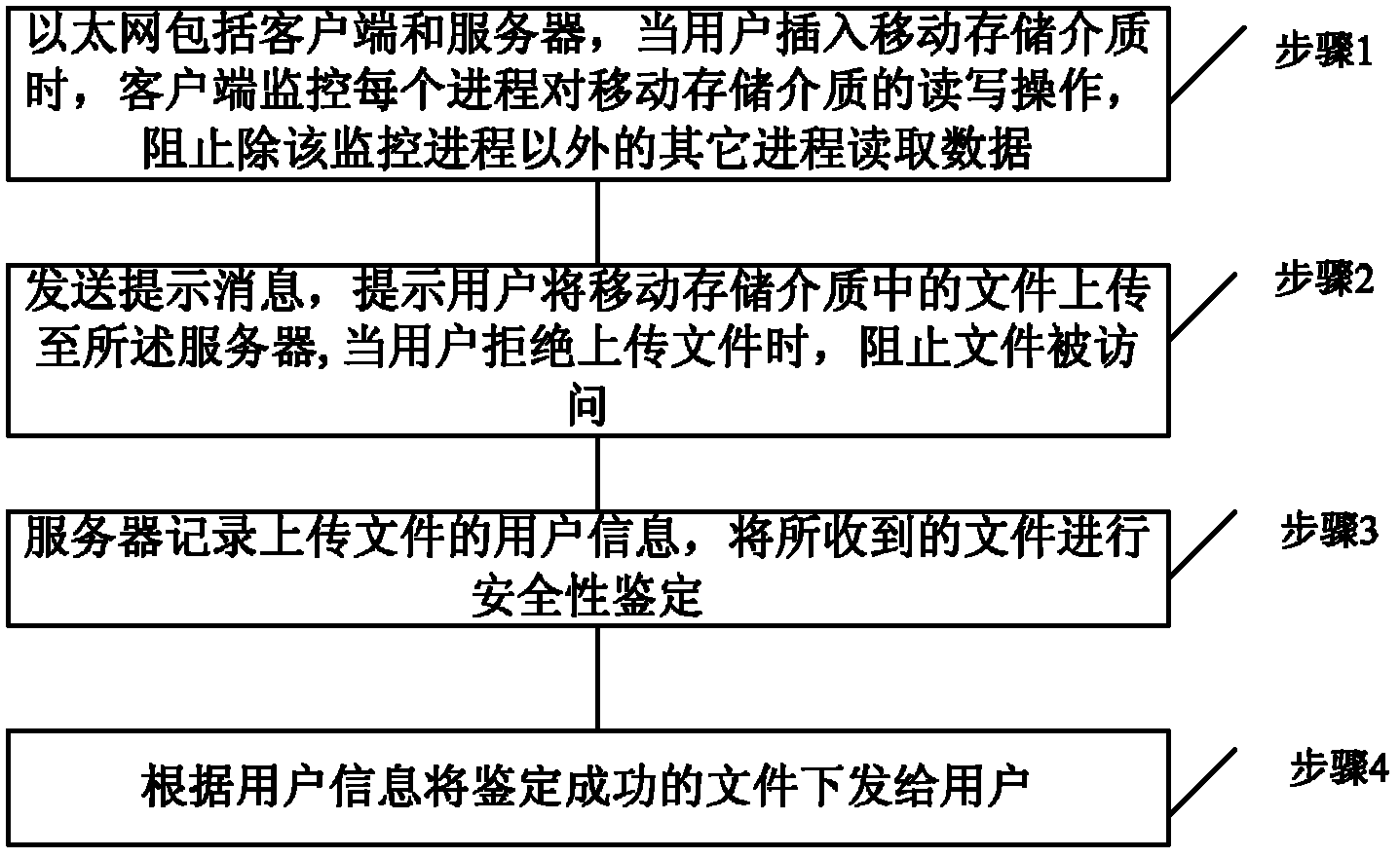
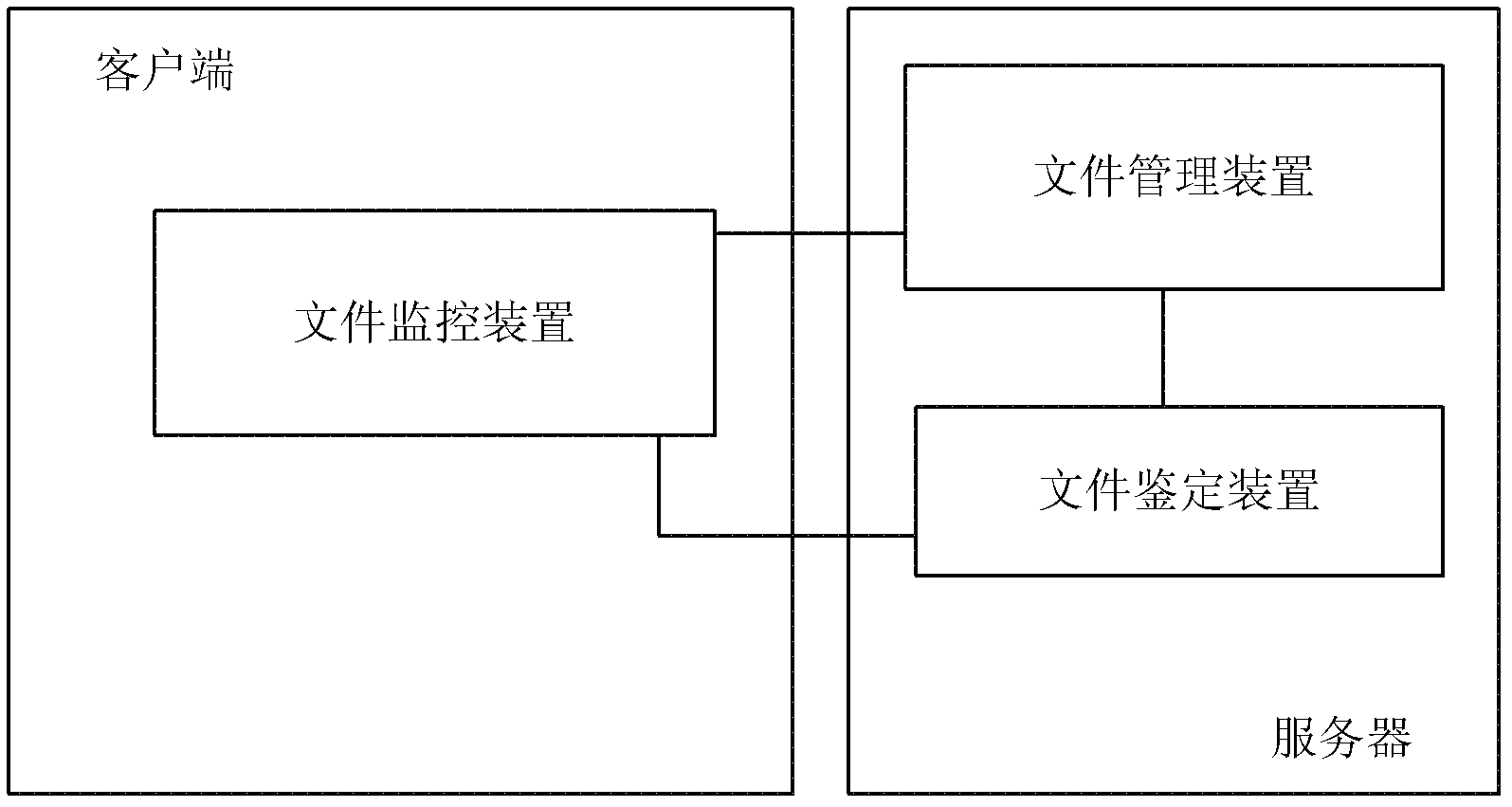
Patents
Literature
94results about How to "Easy to audit" patented technology
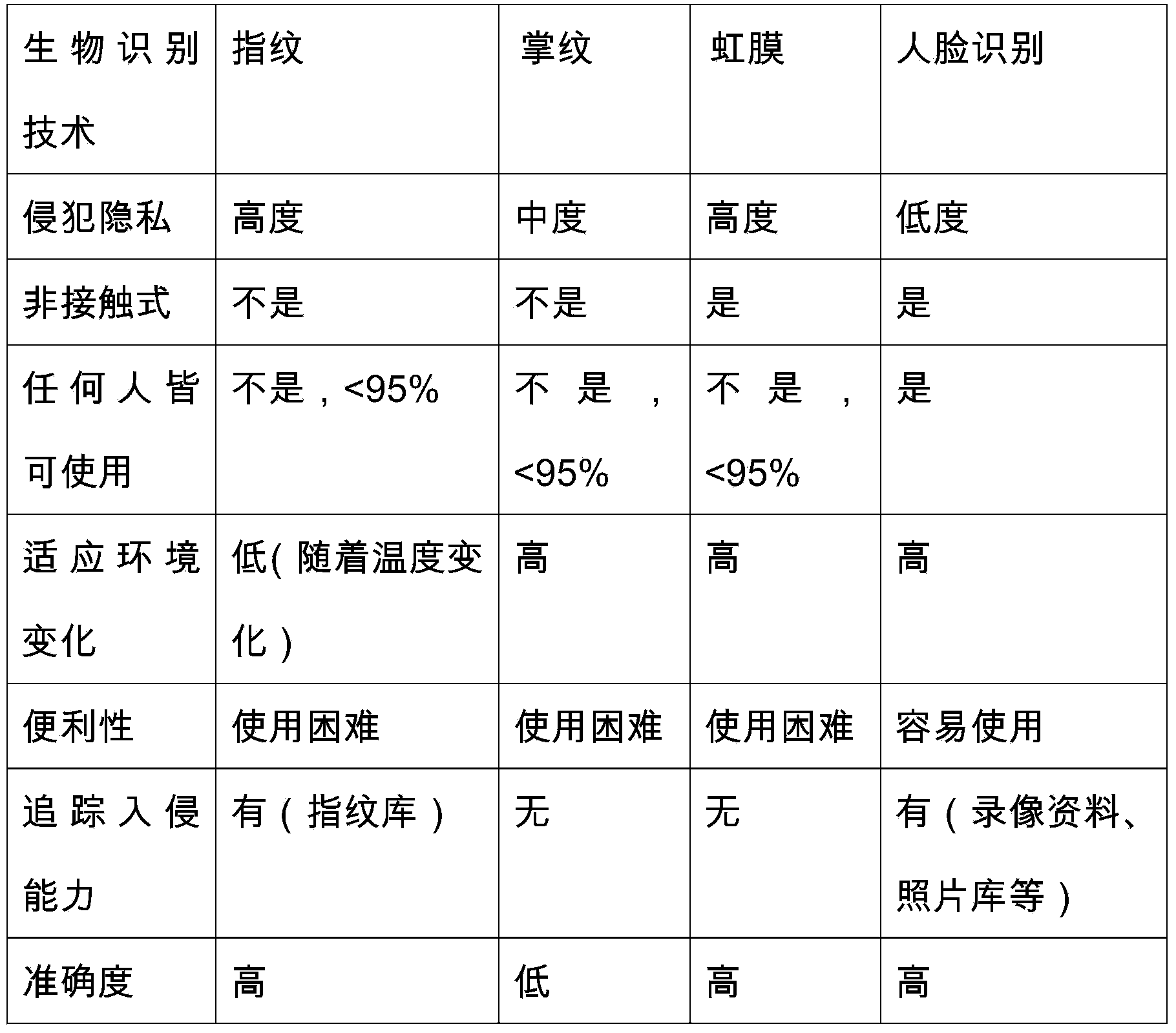
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
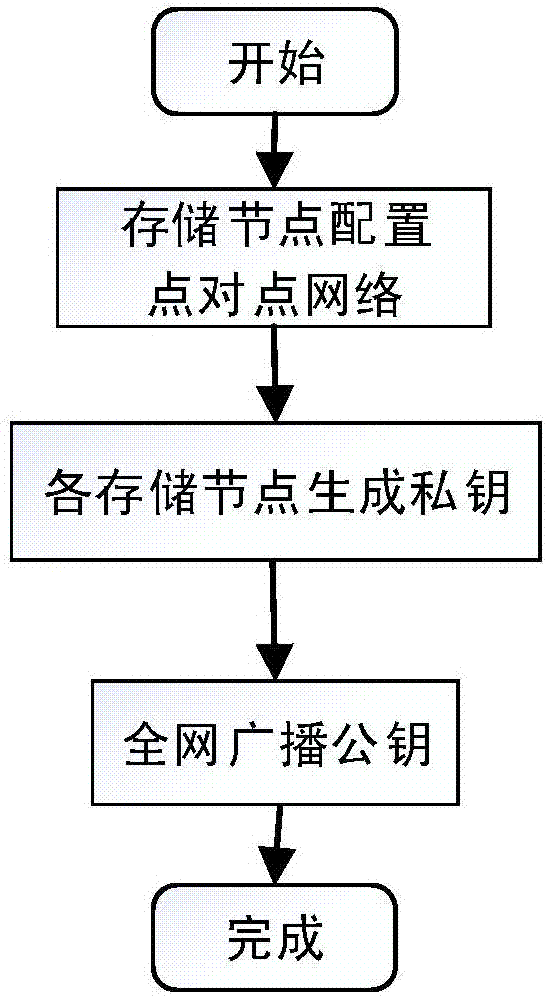
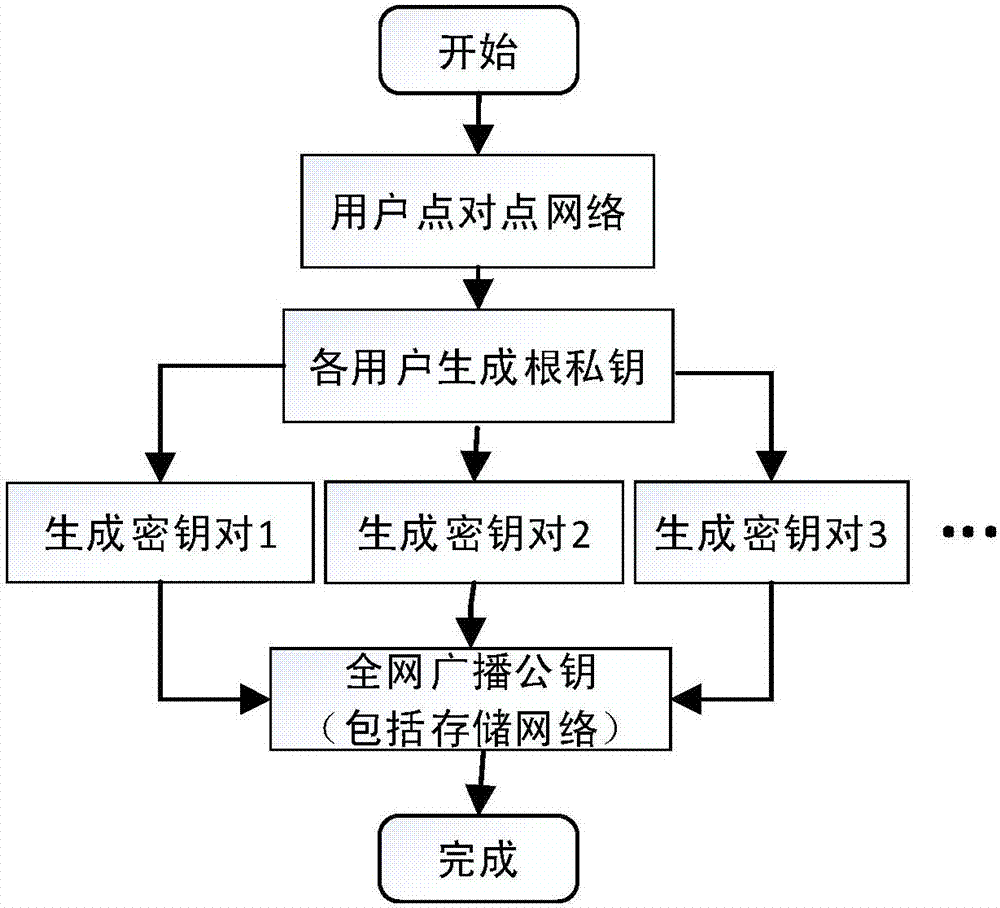
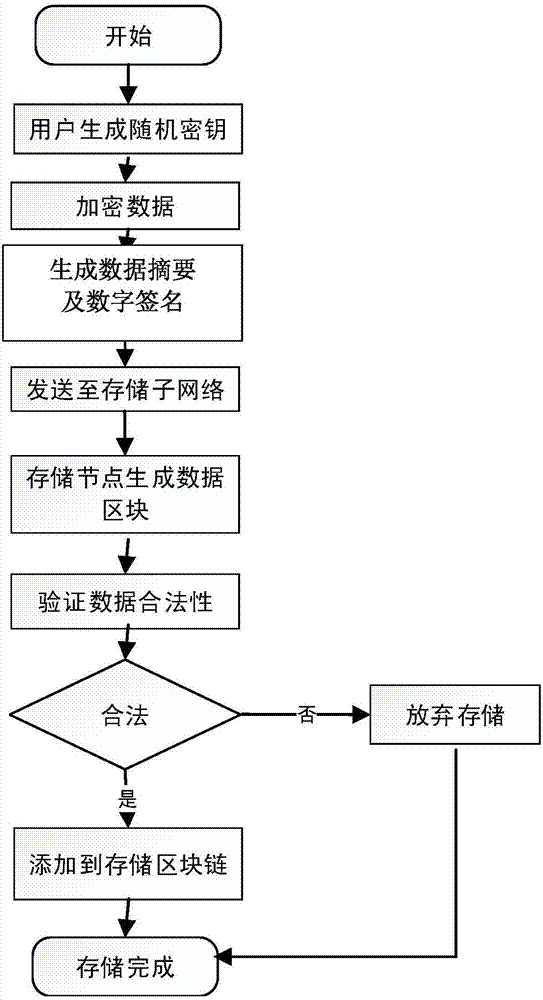
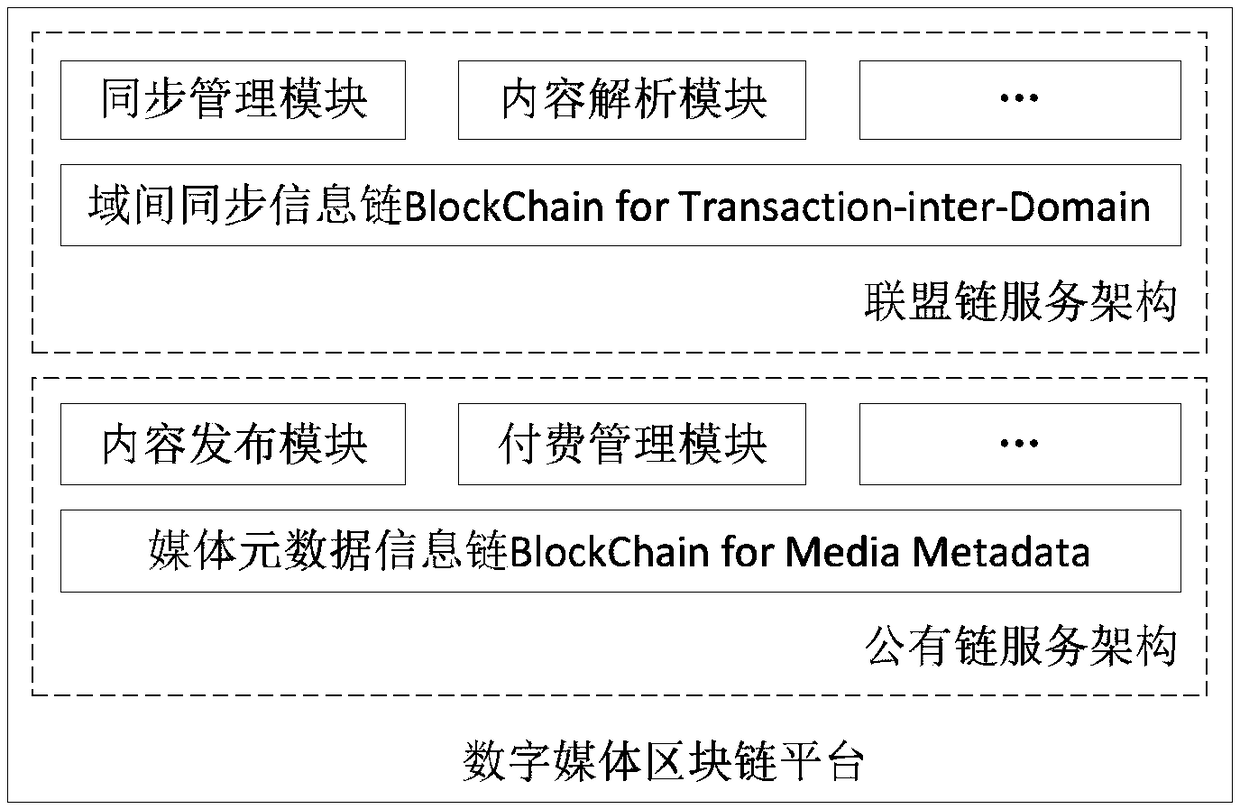
Routing position data secrecy storing and sharing method based on block chain
ActiveCN107181599AGood data protectionSolve workload bottlenecksKey distribution for secure communicationUser identity/authority verificationByzantine fault toleranceOriginal data
Provided is a routing position data secrecy storing and sharing method based on block chains. The routing position data secrecy storing and sharing method includes a data storing method and a data sharing method. The data storing method includes the steps of node configuration, data encryption sending, storage subnetwork verification storing, etc. The data sharing method includes the steps of demand generation, demand response, sharing achievement and the like. The effects of the invention are as follows: through a block chain technology, data sharing is realized through data encryption storage and a decentralized network to solve the problems that data storage parties have no right to use data and users do not have channels to selectively enable personal data to be accessed; local encryption sending is adopted during data storage, service parties store encrypted data, the users themselves save decryption secret keys, and the service parties have no access to original data, so a better data protection effect is achieved; and the block chain technology is adopted during storage, commonly recognized storage is realized through a practical Byzantine fault-tolerant algorithm, workload bottleneck problems of centralized storage are solved, and data is prevented from being tampered.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
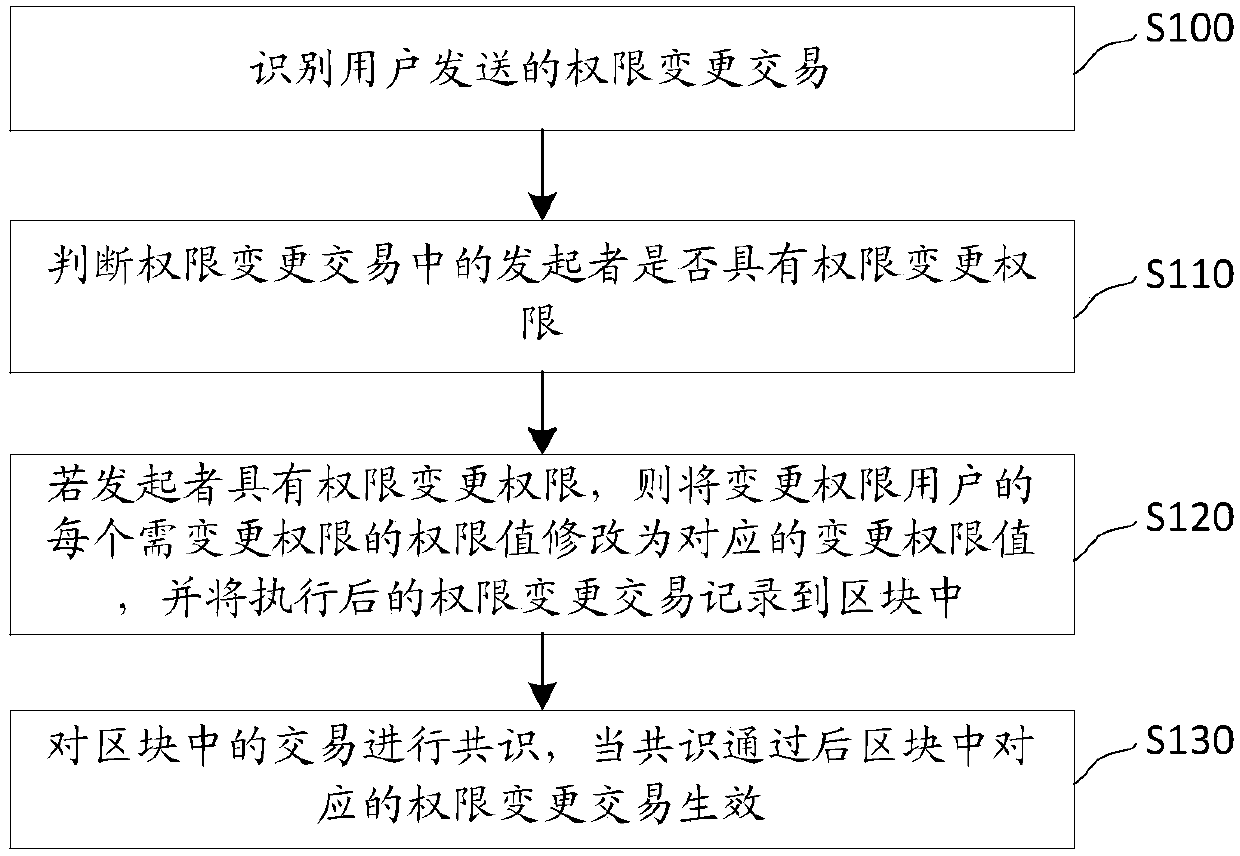
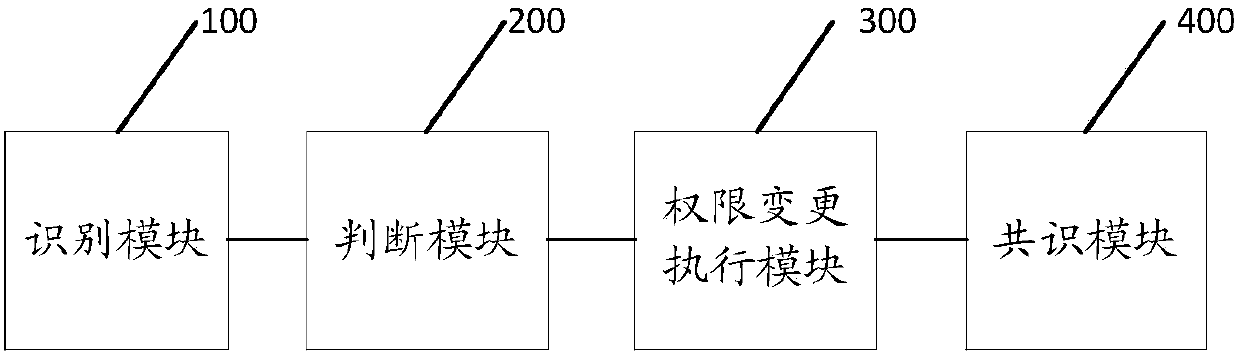
Block chain authority management method and system
ActiveCN107911373AEasy to auditUser identity/authority verificationData switching networksFinancial transactionRights management
The invention discloses a block chain authority management method and system. The method comprises the following steps of identifying an authority change transaction sent by a user, wherein the content of the authority change transaction comprises an initiator, an authority change user, authorities which need to be changed and corresponding change authority values; judging whether the initiator inthe authority change transaction has an authority change authority or not; if the initiator has the authority change authority, modifying an authority value of each authority which needs to be changed of the authority change user into the corresponding authority change value, and recording the executed authority change transaction into a block; and carrying out consensus on the transaction in theblock, and when the consensus passes, making the corresponding authority change transaction in the block take effect. According to the method, the authority management is directly carried out in a block chain without an external facility, and is deeply integrated into the block chain, so that all-directional permission control can be carried out on the block chain, and the authority change needsto pass through the consensus of the whole network and is recorded in the block chain, and thus the change records cannot be tampered and are convenient for auditing.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院
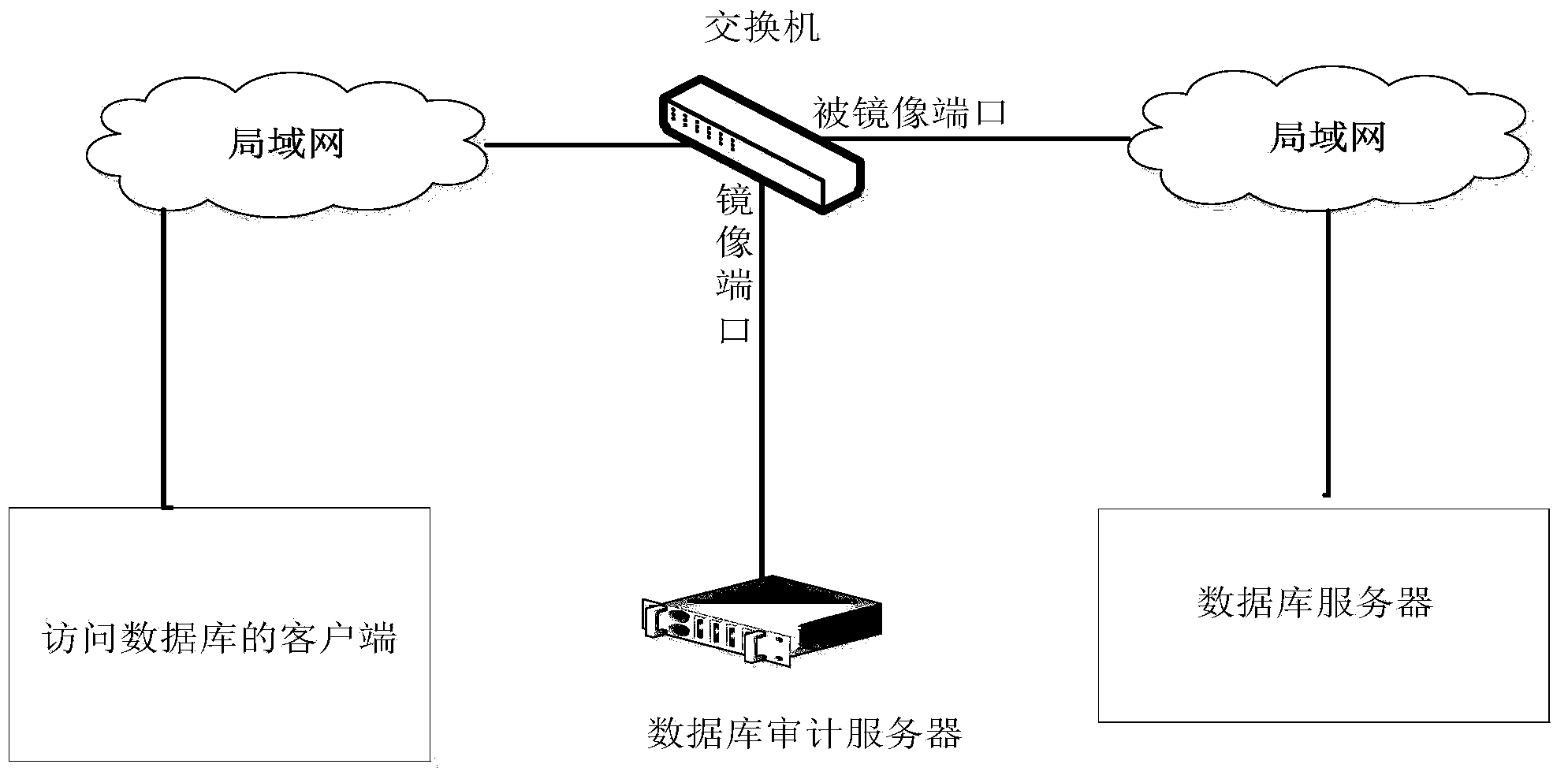
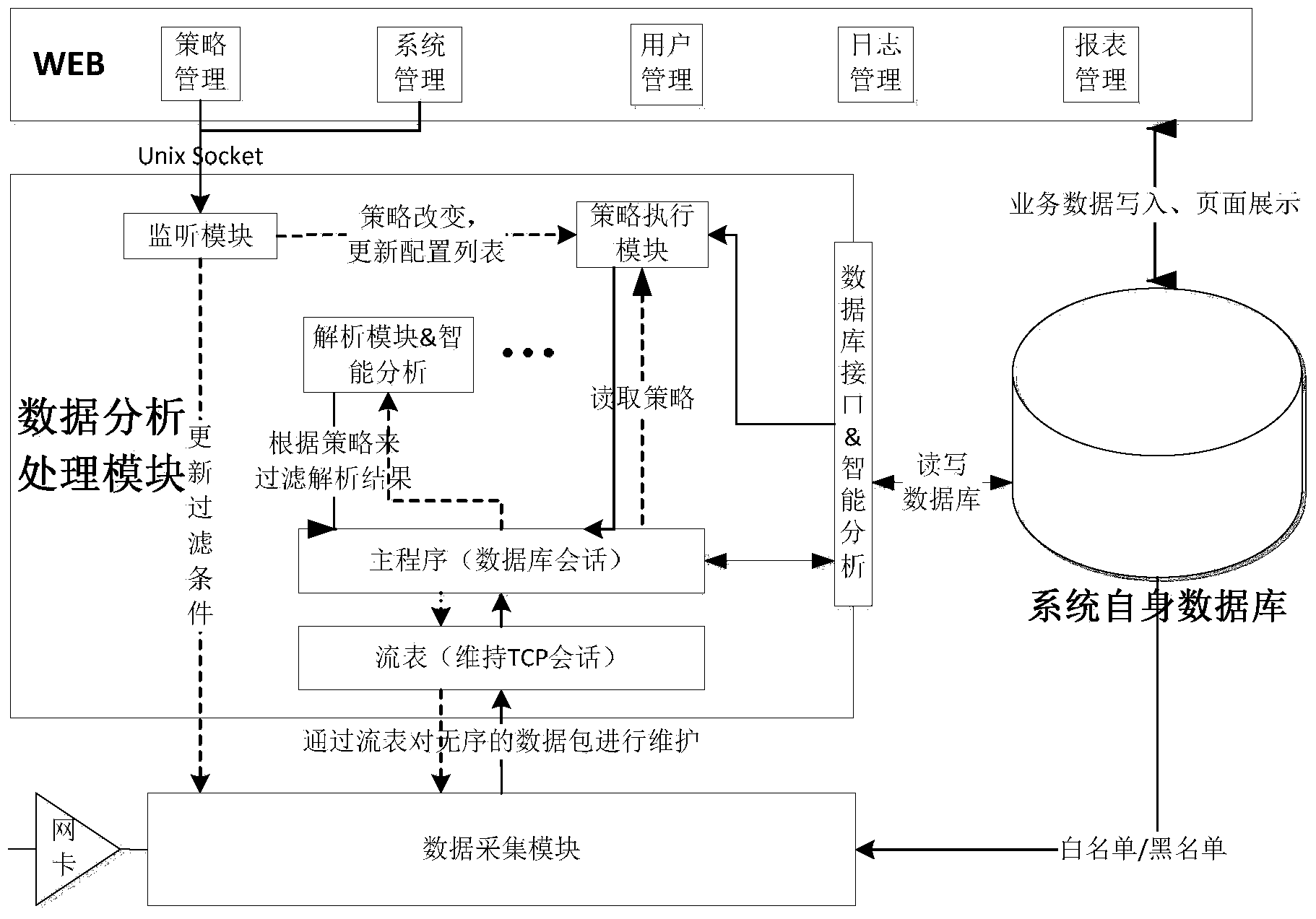
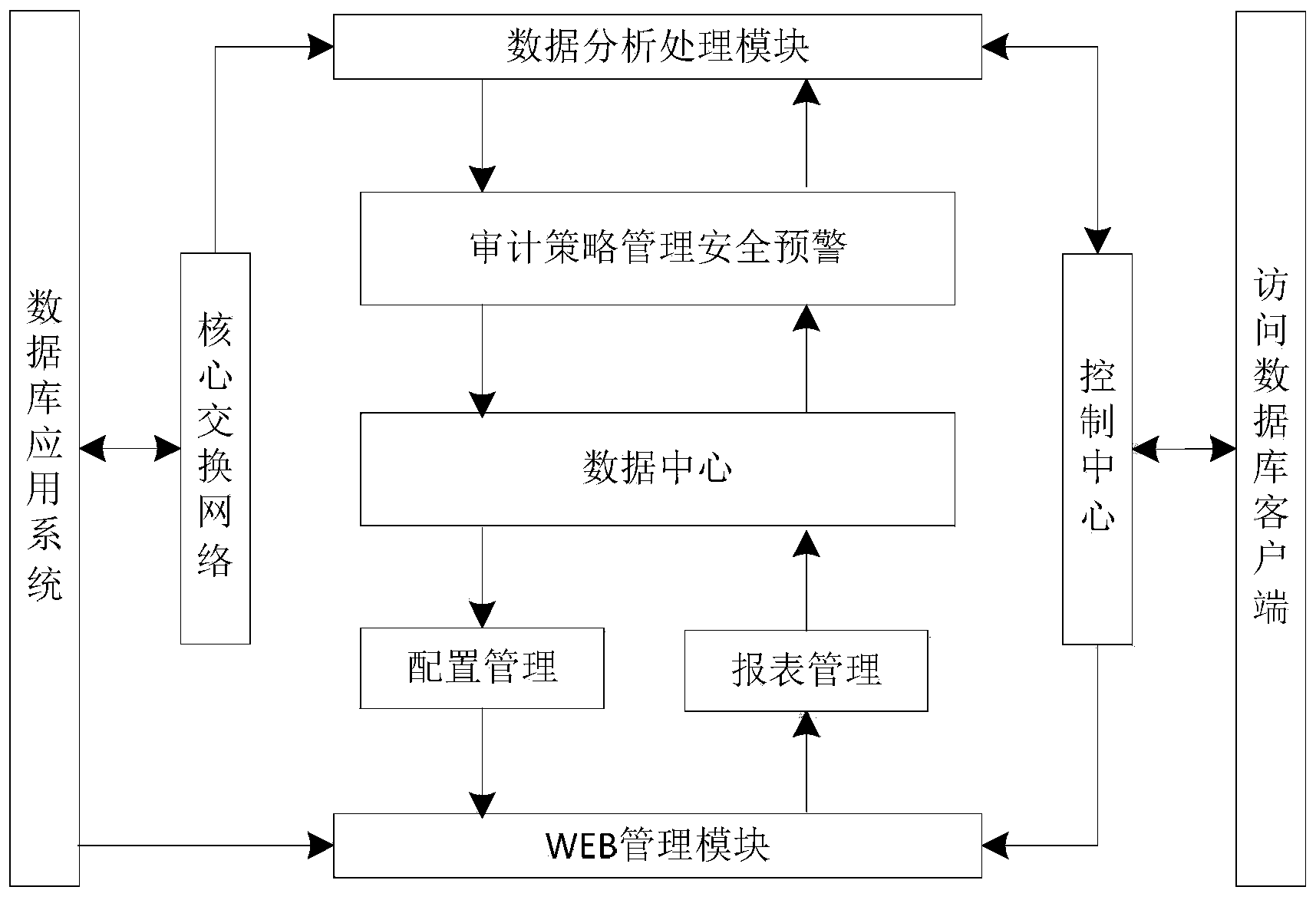
Database auditing monitoring system and database auditing monitoring method
InactiveCN104063473ANo burden on resourcesSimple formatComputer security arrangementsSpecial data processing applicationsDatabase serverMonitoring system
The invention discloses a database auditing monitoring system and a database auditing monitoring method. The database auditing monitoring system comprises a hardware part and a module part, wherein the hardware part comprises a switchboard, a local area network and a database auditing server, the switchboard is respectively connected into the local area network at the two ends through a duplicated port, and is connected with the database auditing server through a mirror port, the local area network at the two ends is respectively communicated with a database accessing client and a database server, and the module part comprises a WEB management module, a local database module, a data collecting module and a data analysis and processing module. The database auditing monitoring system and the database auditing monitoring method have the advantages that various kinds of operation behaviors on the database server are monitored and recorded through a monitoring module arranged in the data analysis and processing module, through the analysis on network data, various kinds of operation and hostile attack event information on the database server can be analyzed intelligently in real time and is recorded into an auditing database so that inquiry and analysis can be realized in future, and the monitoring and the auditing on the operation of a target database system are realized.
Owner:北京华电天益信息科技有限公司
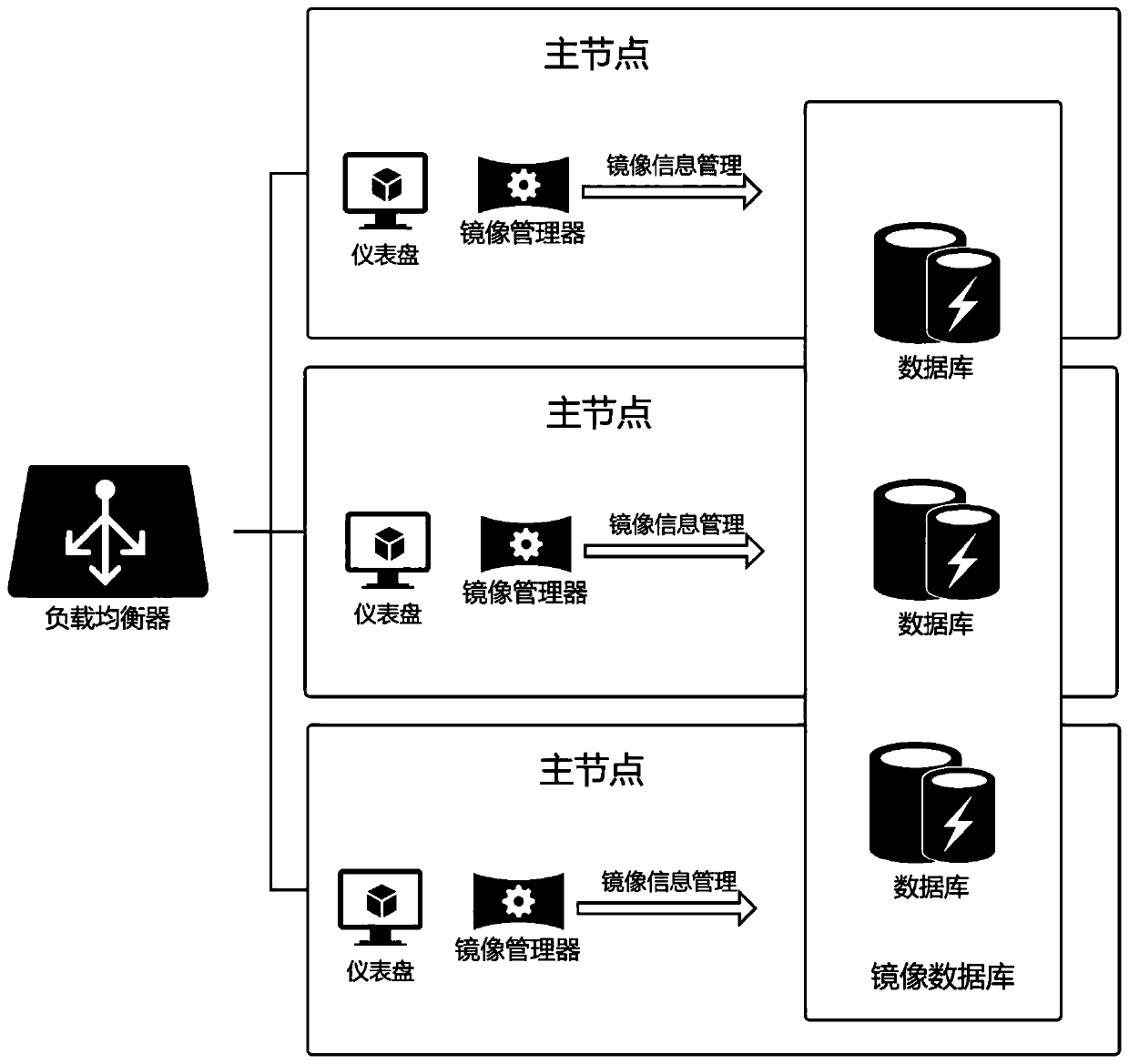
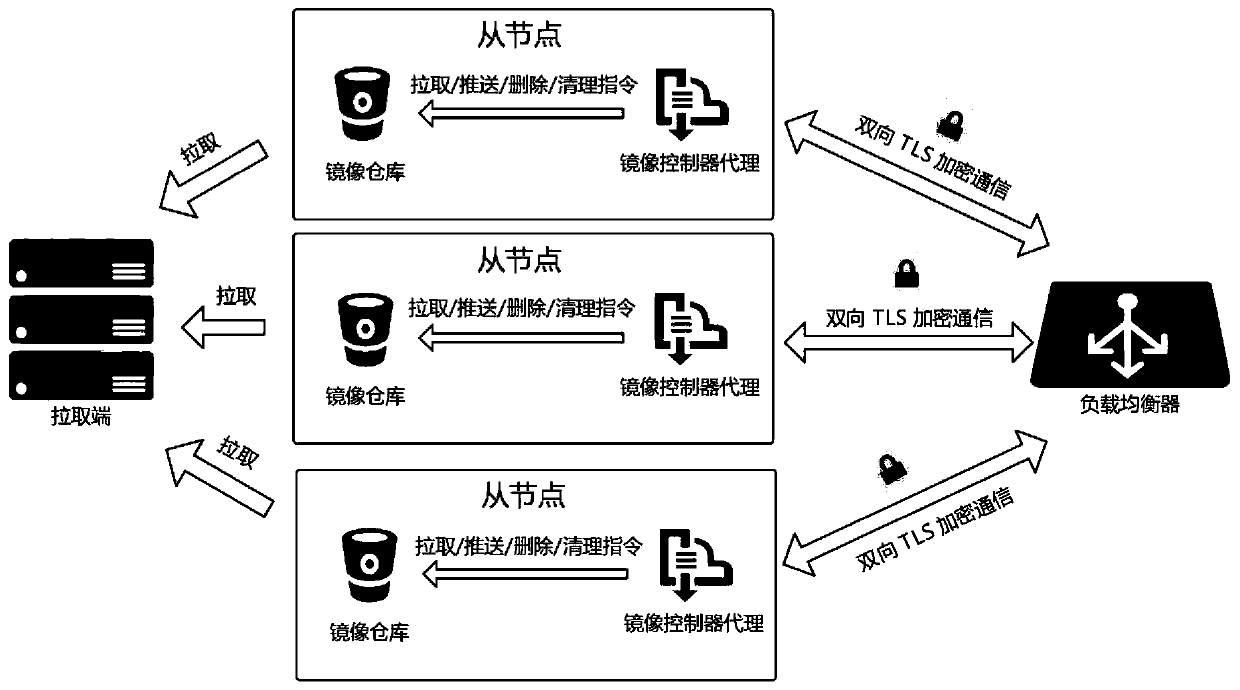
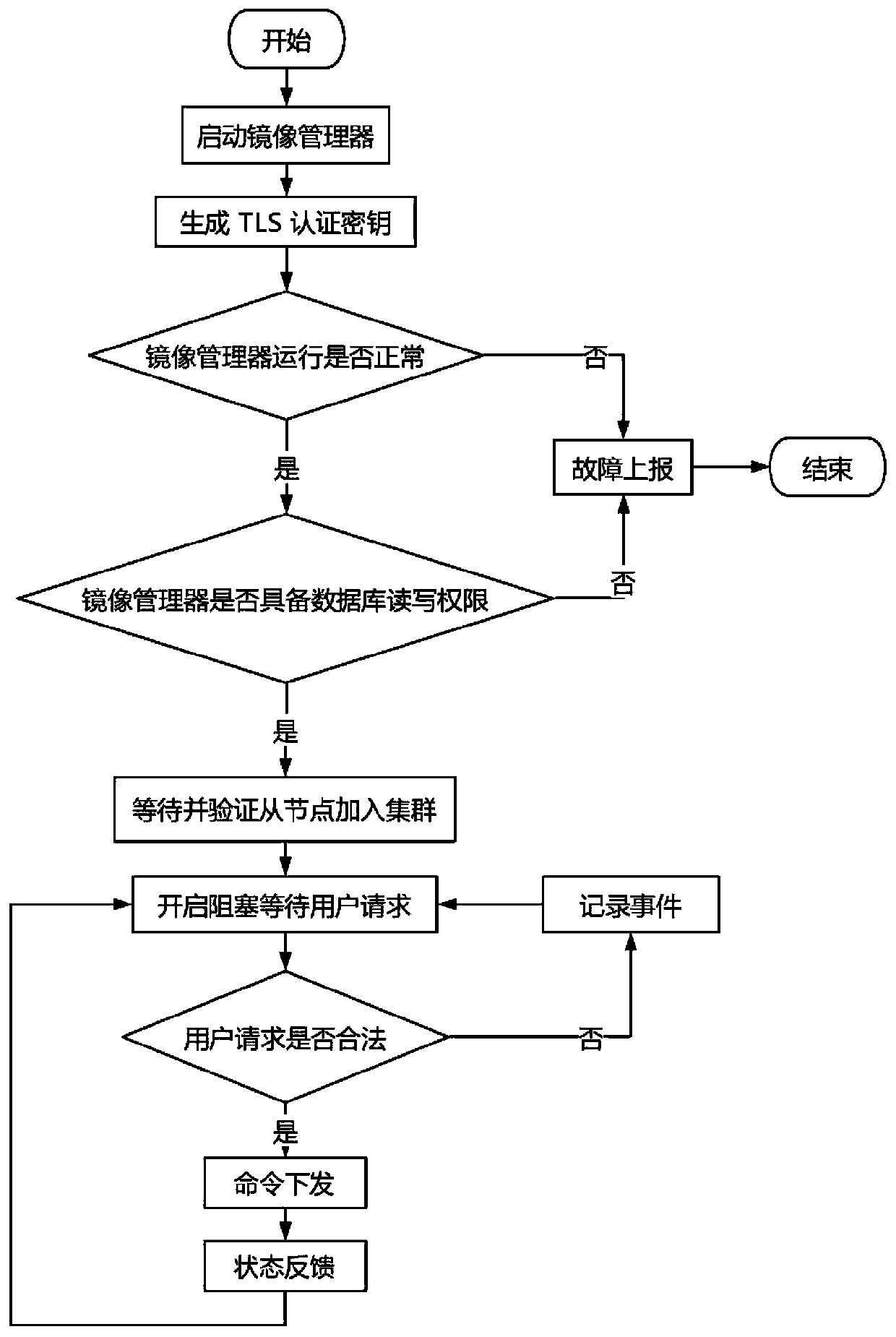
Master node, slave node, system and method for mirror image management of distributed container cluster
ActiveCN110647580AImprove management efficiencyIncrease speedDatabase distribution/replicationOptically investigating flaws/contaminationManagement efficiencyIp address
The invention discloses a distributed container cluster mirror image management master node, slave nodes, a system and a method, wherein the main node comprises a mirror image database which is a distributed database and is used for storing node information of all nodes in the system; the request input module is used for receiving request content including a request target and command execution content; mirror image management module, the verification module is used for communicating the password and verifying whether the request content acquired by the request record input module is legal; ifit is judged that a request target in the request content is a specified single slave node or grouped slave nodes, sending a communication password and command execution content including a pulling operation, an updating operation, a deleting operation and a cleaning operation to IP addresses corresponding to the slave nodes; and receiving the state feedback content sent by the slave node. According to the invention, the flattening management of the container cluster mirror image is realized, the management efficiency of the cluster container mirror image in a distributed system is improved,and the high reliability and safety of the whole cluster are improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
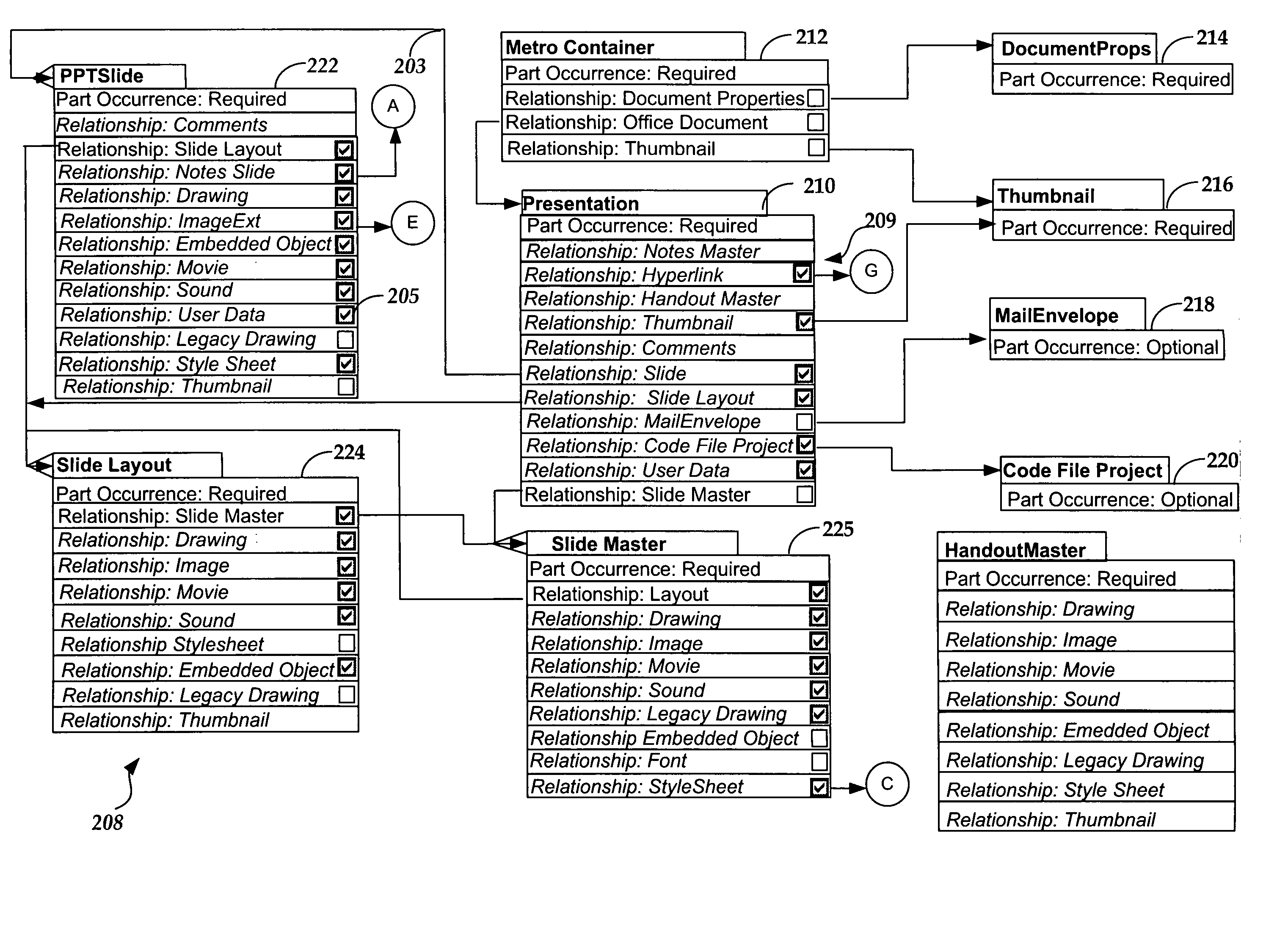
Structuring an electronic document for efficient identification and use of document parts
InactiveUS20060259854A1Easy and open verificationPrecise positioningNatural language data processingSpecial data processing applicationsElectronic documentPaper document
Methods and computer-readable mediums structure an electronic document for identification and use of document parts. A method involves organizing parts of the electronic document as separate parts. The separate parts include resources internal and / or external to where the document is located. The method also involves representing a link between any of the parts as a relationship to be processed listed in a relationship part associated with a source part of the relationship. This relationship part contains a list of relationships for the source part and processing a relationship returns content of a target part of the relationship. Each relationship is also associated with a relationship type. Still further, the method involves representing via the relationship part how one or more parts relate to other separate parts, tracking internal resources, and tracking external resources. Thus, applications can infer the structure of the document by traversing the relationships.
Owner:MICROSOFT TECH LICENSING LLC
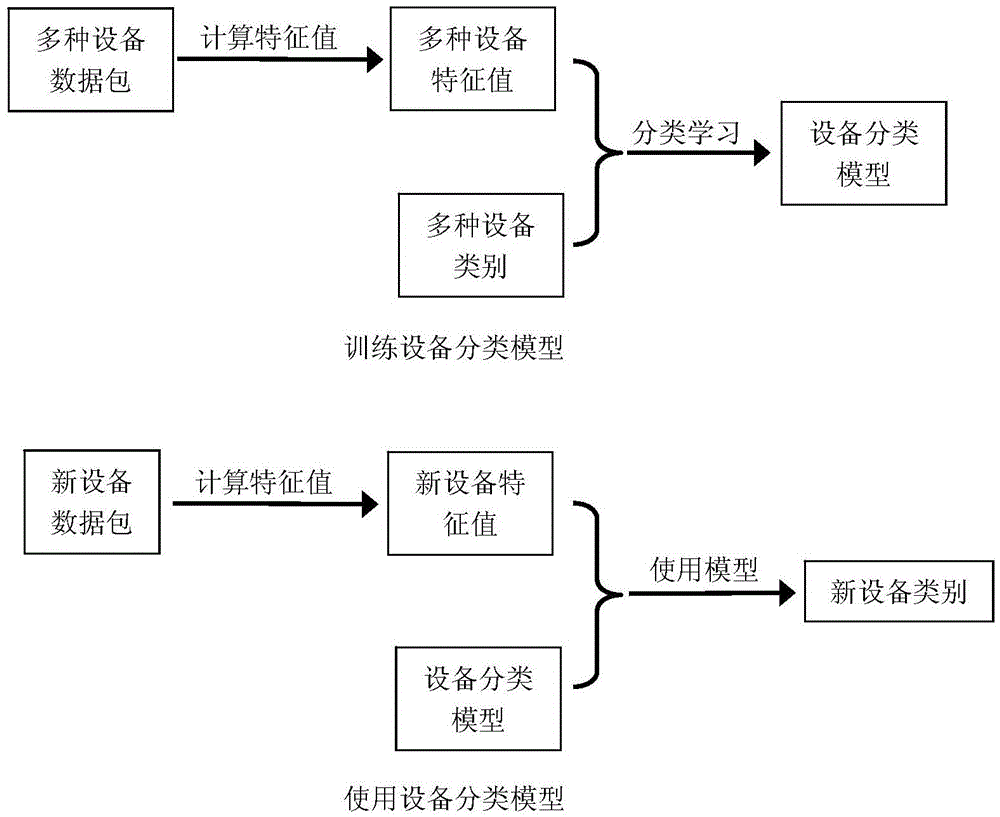
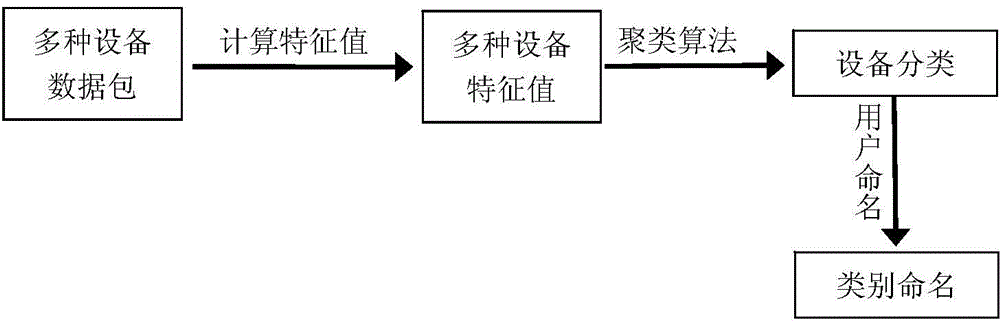
Method for classifying network equipment by utilizing machine learning
InactiveCN104883278AEasy to auditSimple safety rulesData switching networksSecurity specificationNetwork packet
The invention discloses a method for classifying network equipment by utilizing machine learning. The method establishes a classifying model for the network equipment by utilizing a supervised machine learning technology or a non-supervised machine learning technology, so as to classify known or newly added equipment in a network. The method has the technical advantages of analyzing behavior of the equipment through data packets transmitted and received by industrial control network equipment, and further classifying the equipment automatically. The understanding of types of the equipment is conducive to auditing network communication data. Unlike the traditional security specification for individual equipment, the security specification for equipment types is simpler and easy to manage, and the user can define corresponding security specifications for newly added equipment nodes easily.
Owner:BEIJING KUANGEN NETWORK TECH
Operation and maintenance safety auditing method and system
InactiveCN106330919AAvoid substitutionGuarantee authenticityCharacter and pattern recognitionTransmissionCorrelation analysisComputer science
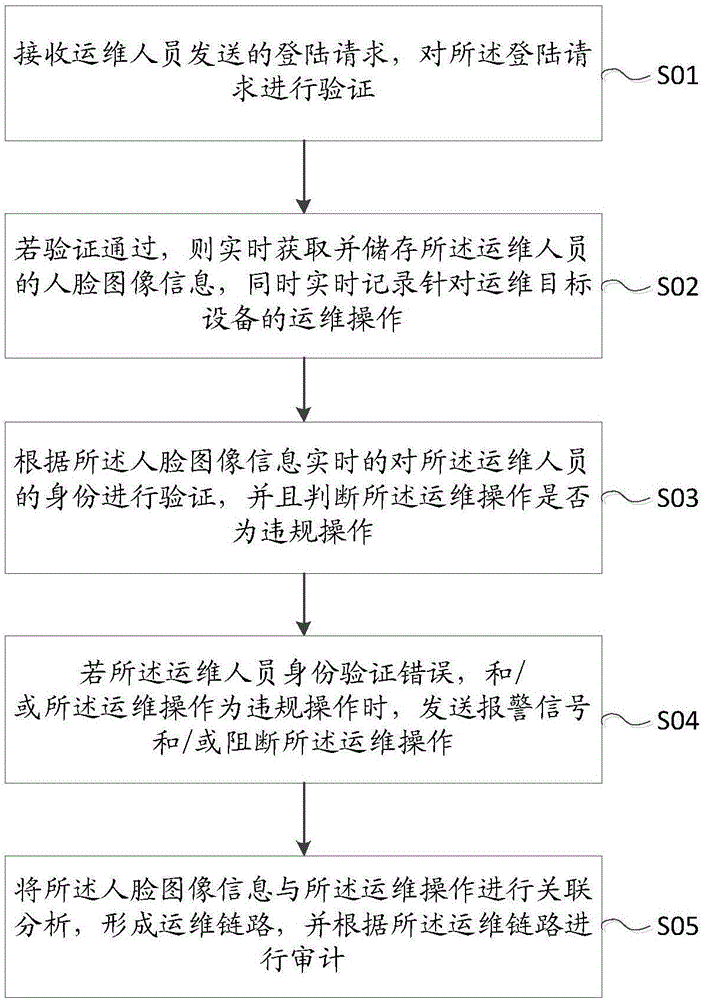
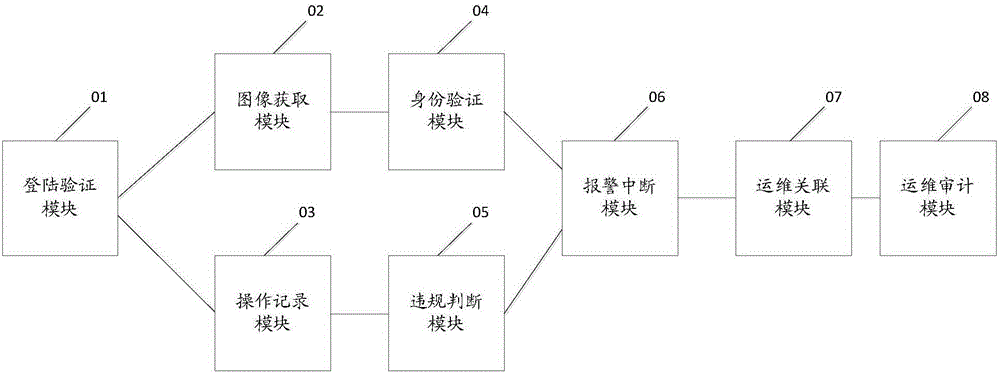
The invention discloses an operation and maintenance safety auditing method. The operation and maintenance safety auditing method comprises the following steps: receiving a login request sent by operation and maintenance personnel, and verifying the login request; if the verification is passed, obtaining and storing face image information of the operation and maintenance personnel in real time, and meanwhile recording an operation and maintenance operation on operation and maintenance target equipment in real time; verifying the identity of the operation and maintenance personnel in real time according to the face image information, and judging whether the operation and maintenance operation is an illegal operation; if the verification of the identity of the operation and maintenance personnel is wrong, and / or the operation and maintenance operation is the illegal operation, sending an alarm signal and / or interrupting the operation and maintenance operation; and carrying out correlation analysis on the face image information and the operation and maintenance operation, forming an operation and maintenance link, and carrying out audit according to the operation and maintenance link. Identity authentication can be carried out on the identity of the IT operation and maintenance personnel in an operation and maintenance personnel process, and the illegal operation and maintenance operation can be found in time. The invention further discloses an operation and maintenance safety auditing system.
Owner:STATE GRID CORP OF CHINA +2
Resource uploading and resource requesting method in blockchain
ActiveCN109246211AAvoid duplicate declarationsAvoid confusionUser identity/authority verificationProgram/content distribution protectionService domainSmart contract
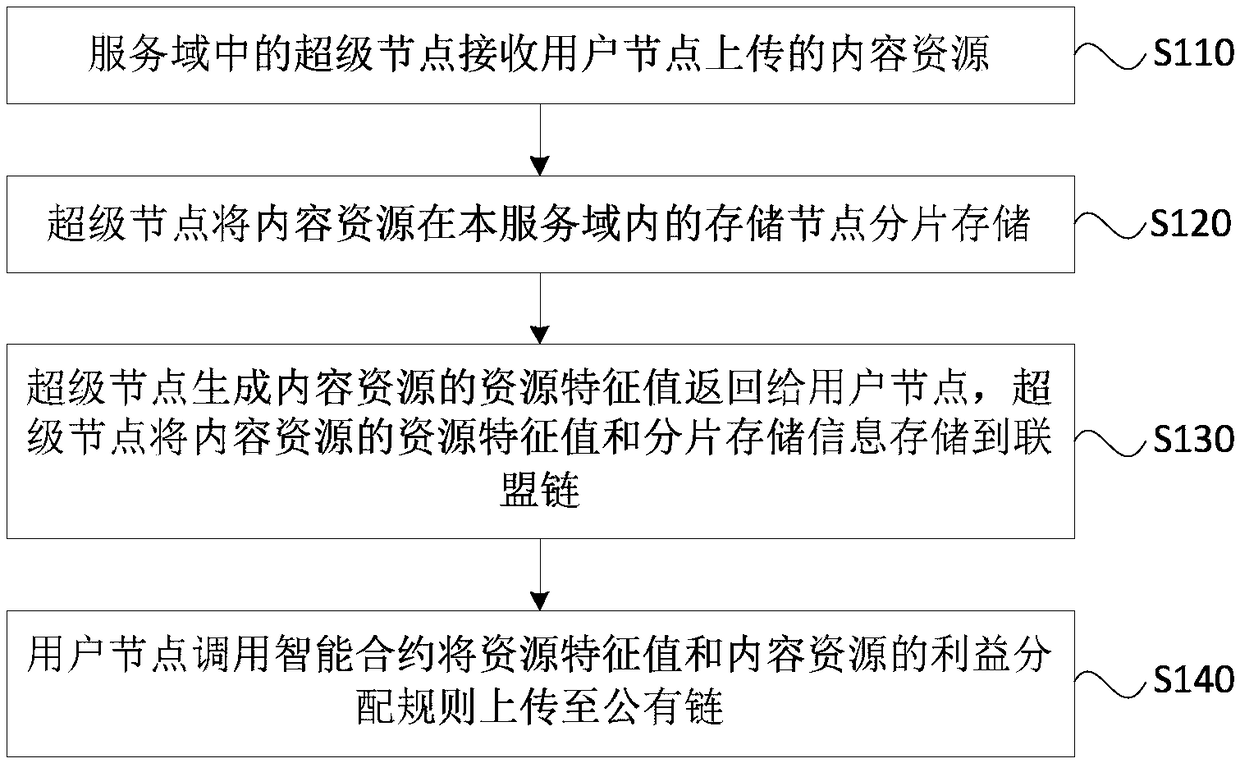
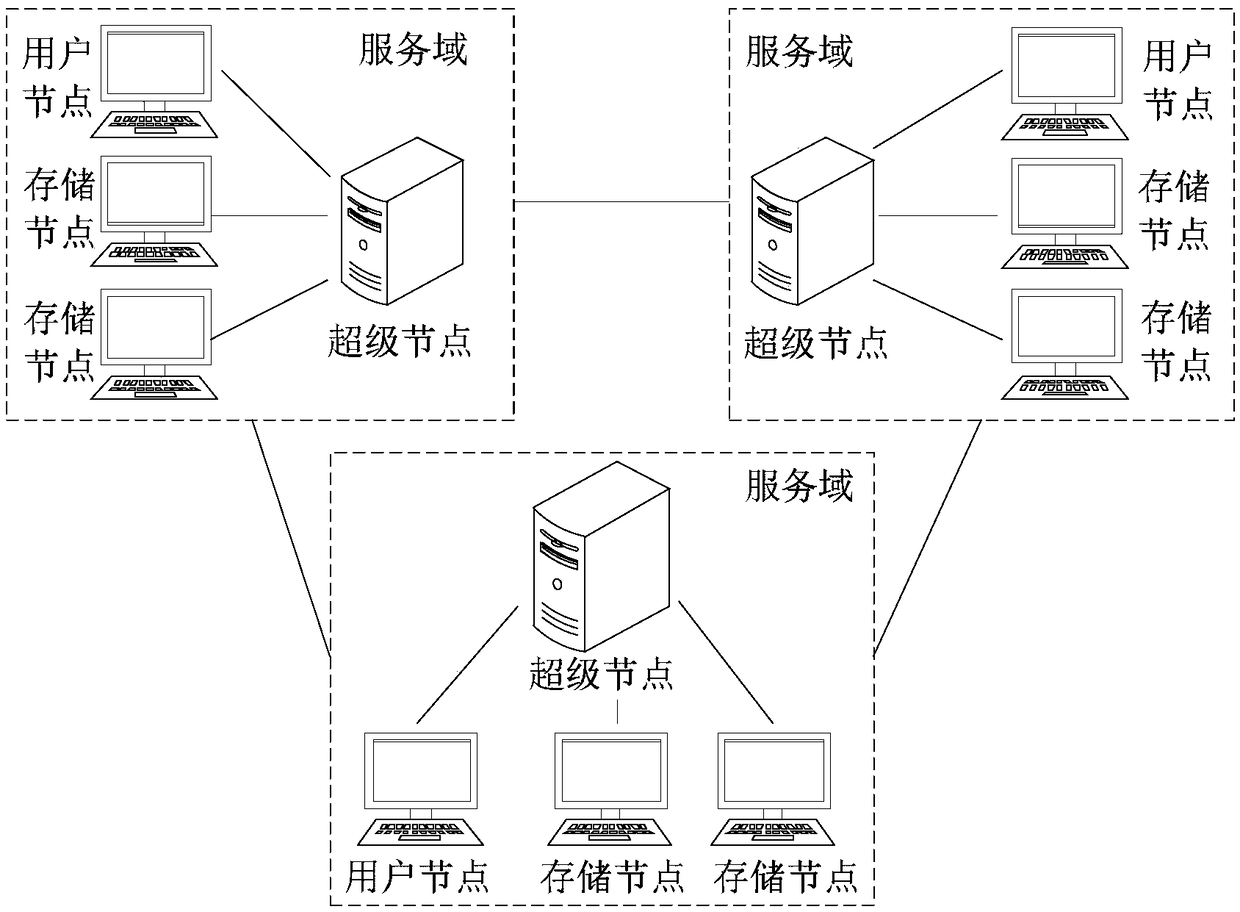
The embodiment of the invention discloses a resource uploading and resource requesting method in a blockchain. The resource request method in the blockchain includes the steps that a super node in a service domain receives a request of a user node, wherein the resource request of the user node includes a resource feature value; the super node searches for segment storage information, correspondingto a content resource, in an alliance chain according to the resource feature value, and returns the segment storage information to the user node; the super node calls an intelligent contract corresponding to the resource feature value in a public chain to declare a current resource service process; the user node downloads the resource data according to the segment storage information; the user node calls the intelligent contact corresponding to the resource feature value in the public chain to pay the benefits of the parties in the current resource service process. According to the technicalsolution provided by the embodiment of the invention, the method makes the copyright information and the benefit distribution rule of a content resource be transparent in the public chain, improves the initiative of resource sharing, and reduces the risk of resource loss in the process of resource access.
Owner:SOUTH UNIVERSITY OF SCIENCE AND TECHNOLOGY OF CHINA
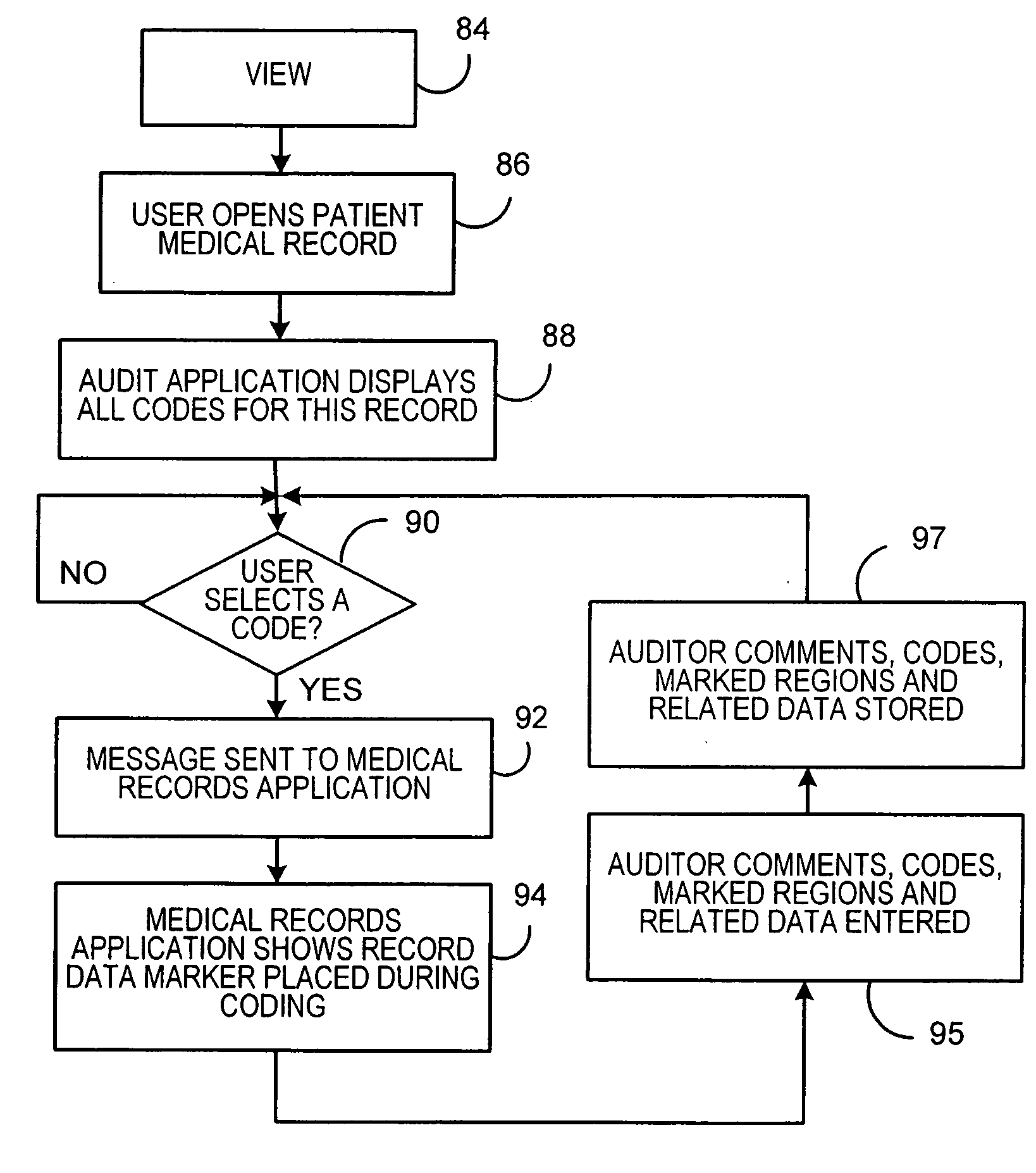
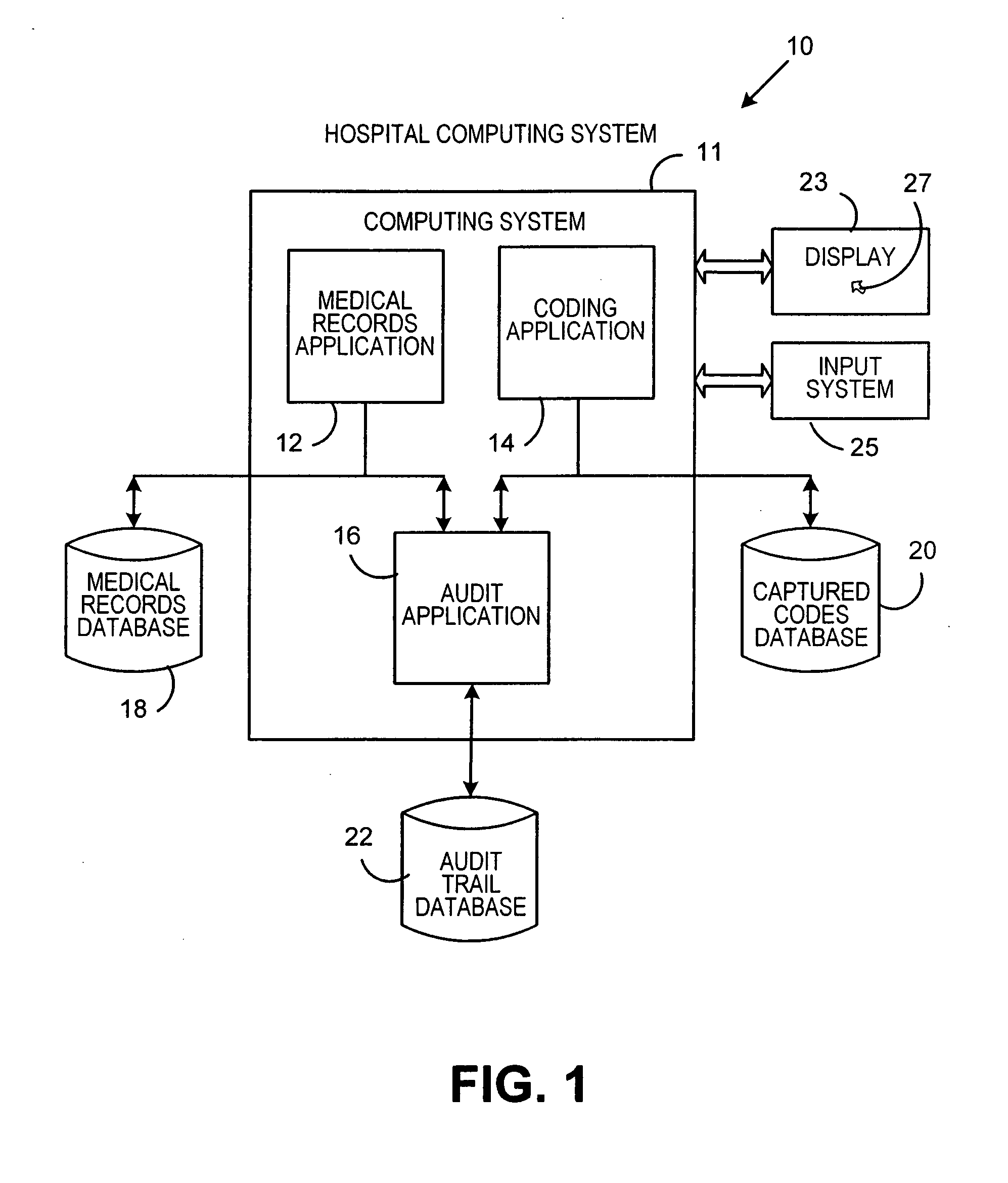
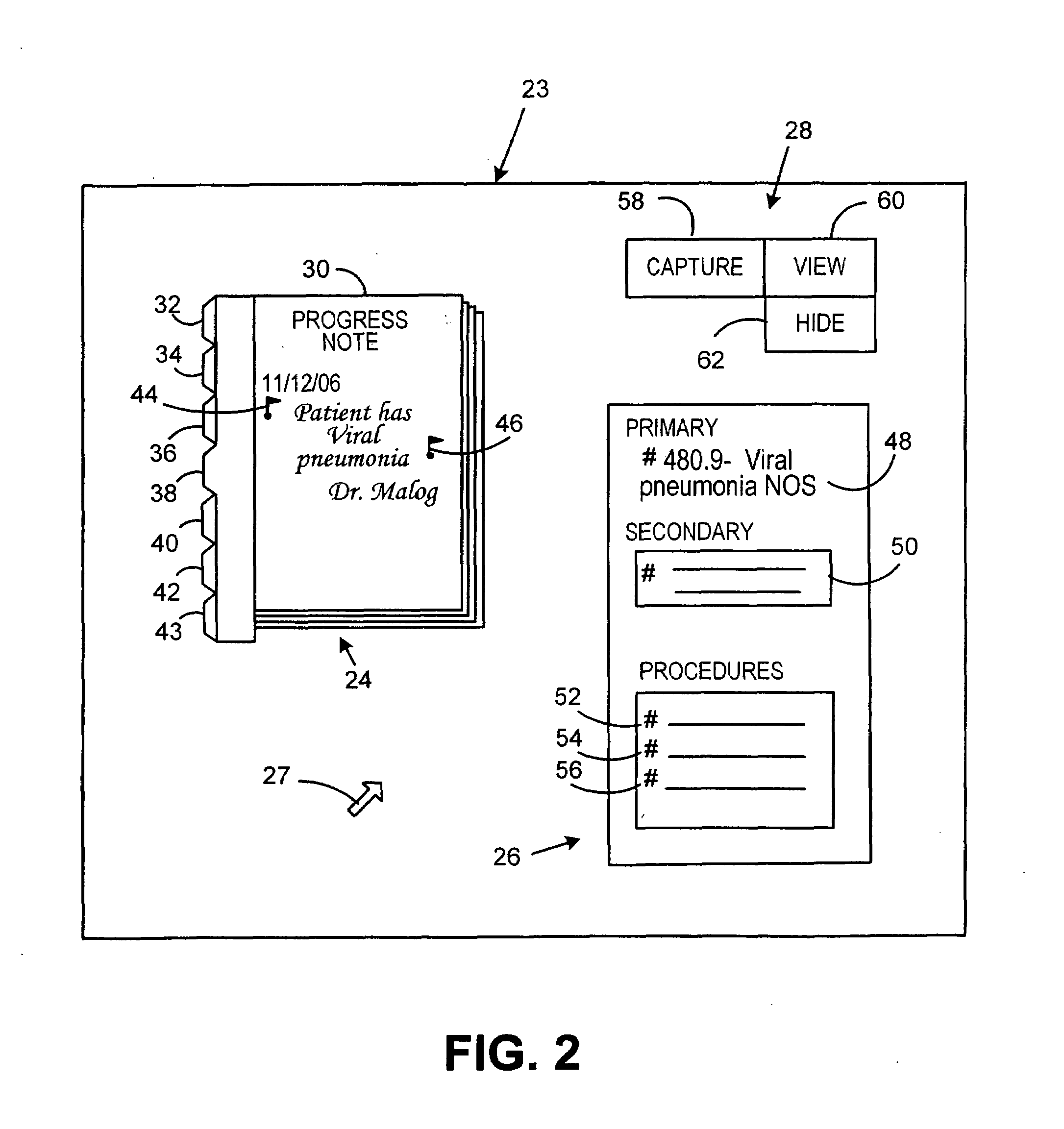
Medical record coding and audit system
InactiveUS20080077443A1Improve accuracyFacilitate communicationData processing applicationsPatient personal data managementMedical recordOperating system
A method and system of processing medical records includes providing an image of a medical record on a screen and inputting a code associated with a portion of the medical record. A region of the medical record is selected that supports the code and the selected region of said medical record is visibly marked and associated with the code. The code and associated selected region of the medical record are stored for subsequent retrieval. The method and system can also enable opening the medical record and displaying at least one code associated with the medical record and displaying the stored selected region of the medical record associated with the code. Plural codes may be selected for a medical record with each code being associated with at least one of a plurality of selected regions of the medical record.
Owner:PITNEY BOWES INC
Three-network convergence oriented digital home network architecture
ActiveCN102064959ARealize interconnectionReduce the burden of useNetwork connectionsSmart applianceNetwork architecture
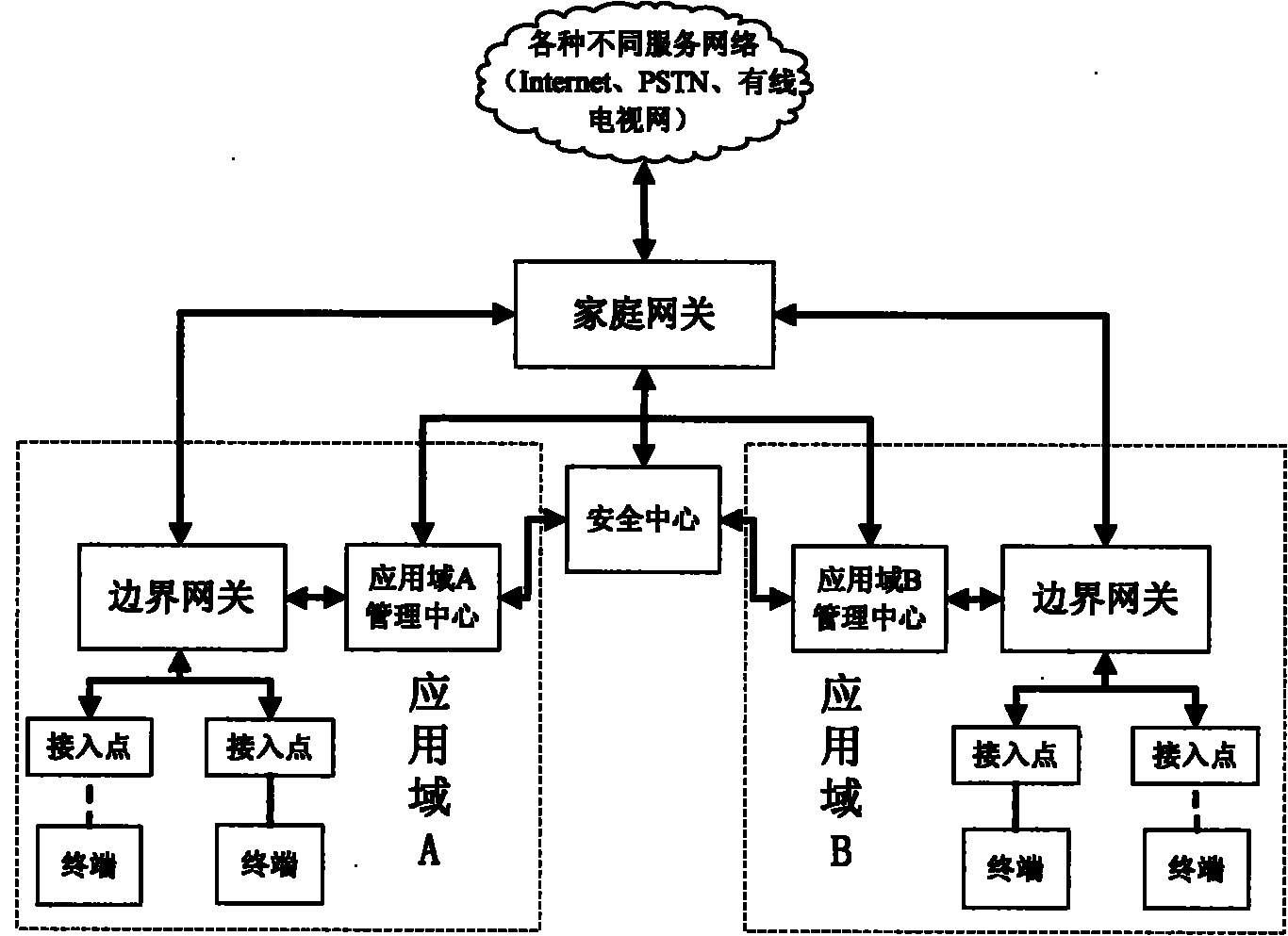
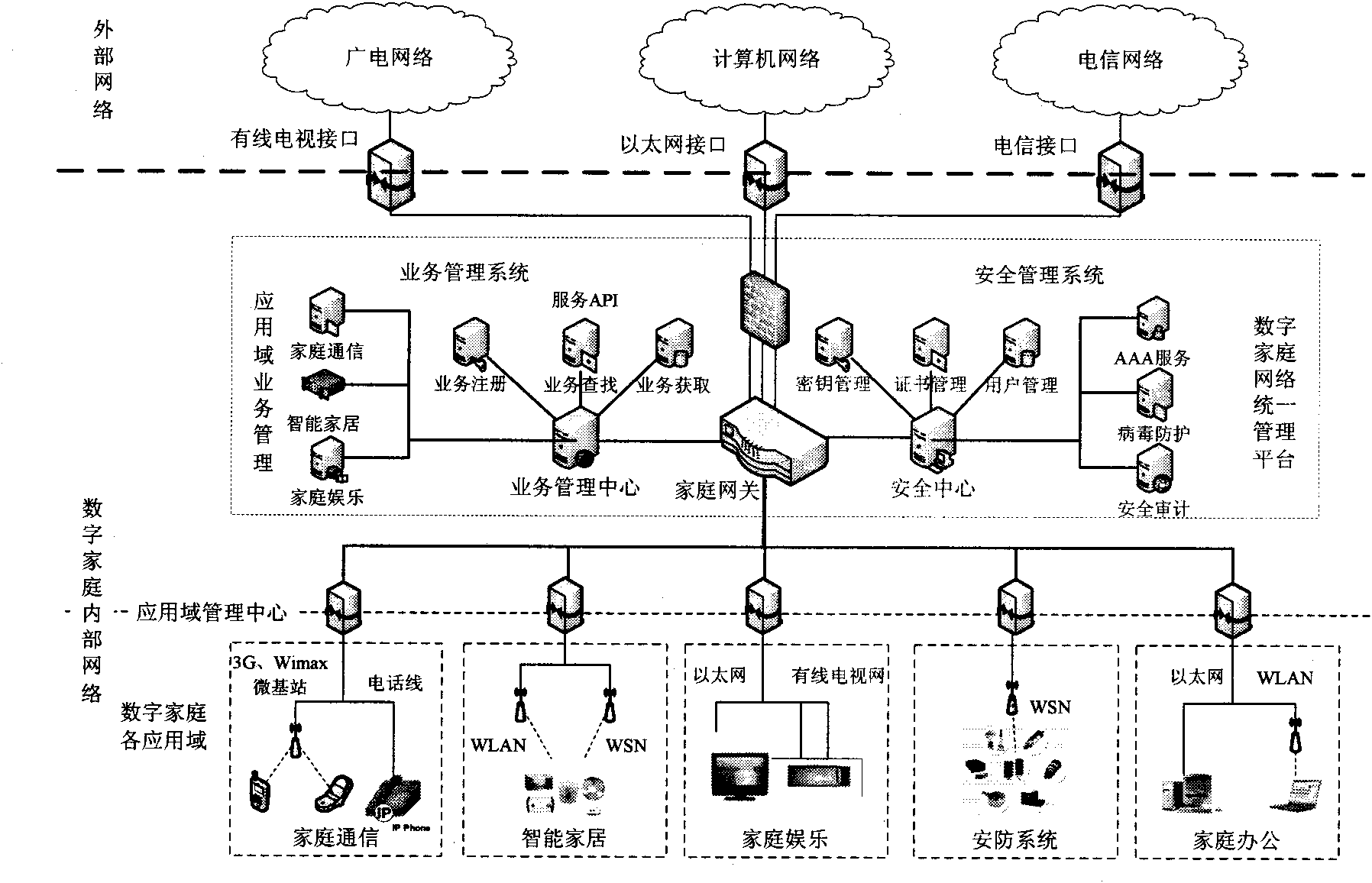
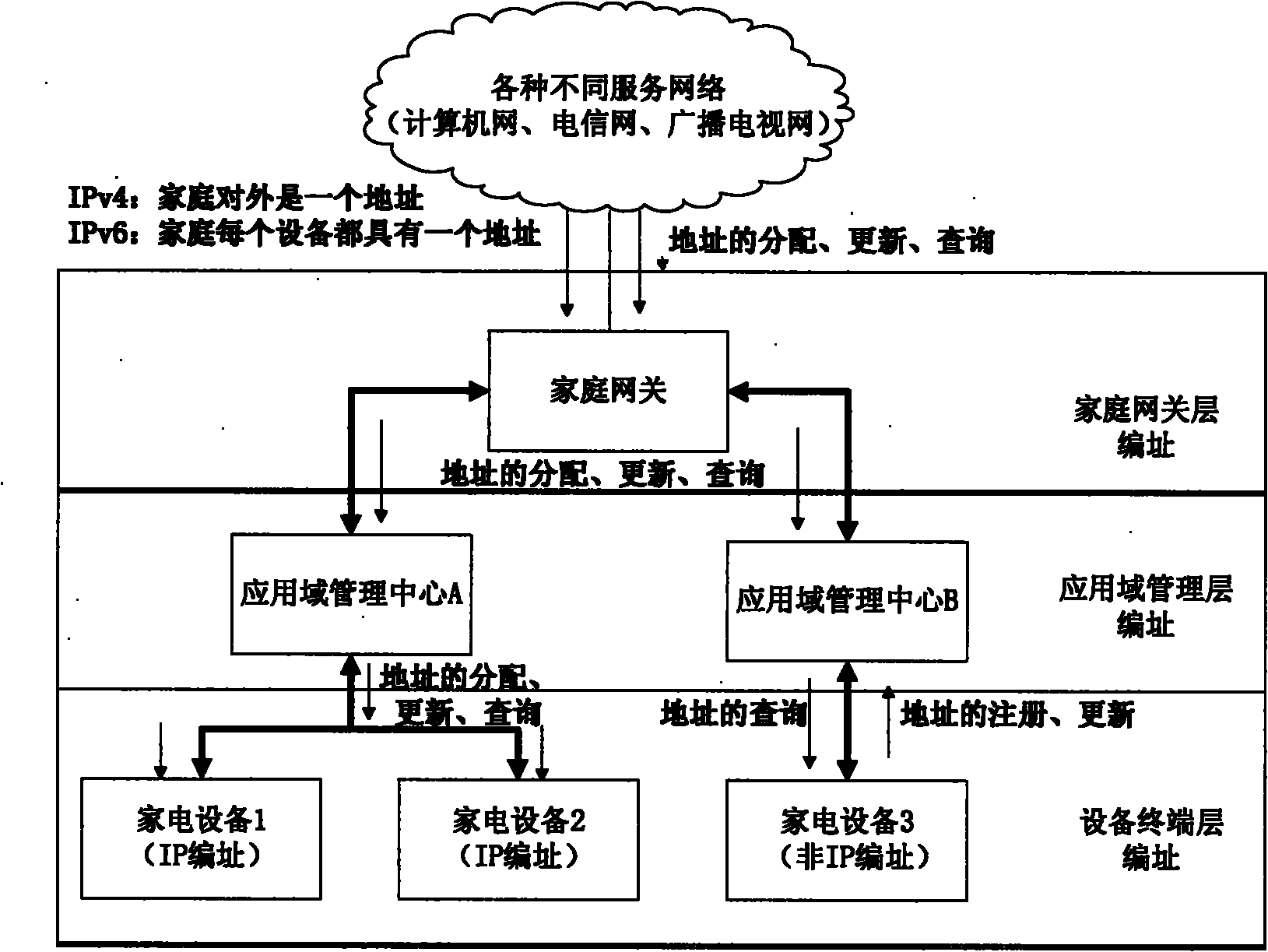
The invention discloses a three-network convergence oriented digital home network architecture. In the architecture, the network is partitioned into different application domains according to the digital home service requirements, information terminal devices with similar home services and similar function requirements are connected in the same application domain, and all terminal devices in the domain and services provided by the all terminal devices are managed by an application domain management center, thereby lightening the burden of a home gateway in managing specific services, and simultaneously being favorable for effective unified management of resources in the application domains. The digital home network architecture is composed of information terminal devices and intelligent home appliances, a network connection device, a digital home application domain management center and a home gateway. Based on the network architecture, the invention provides an addressing scheme and a communication method for a three-network convergence based digital home network architecture layering device, and realizes interconnection and intercommunication among digital home devices.
Owner:XIDIAN UNIV
A block chain member management method and system based on an identification cryptographic algorithm
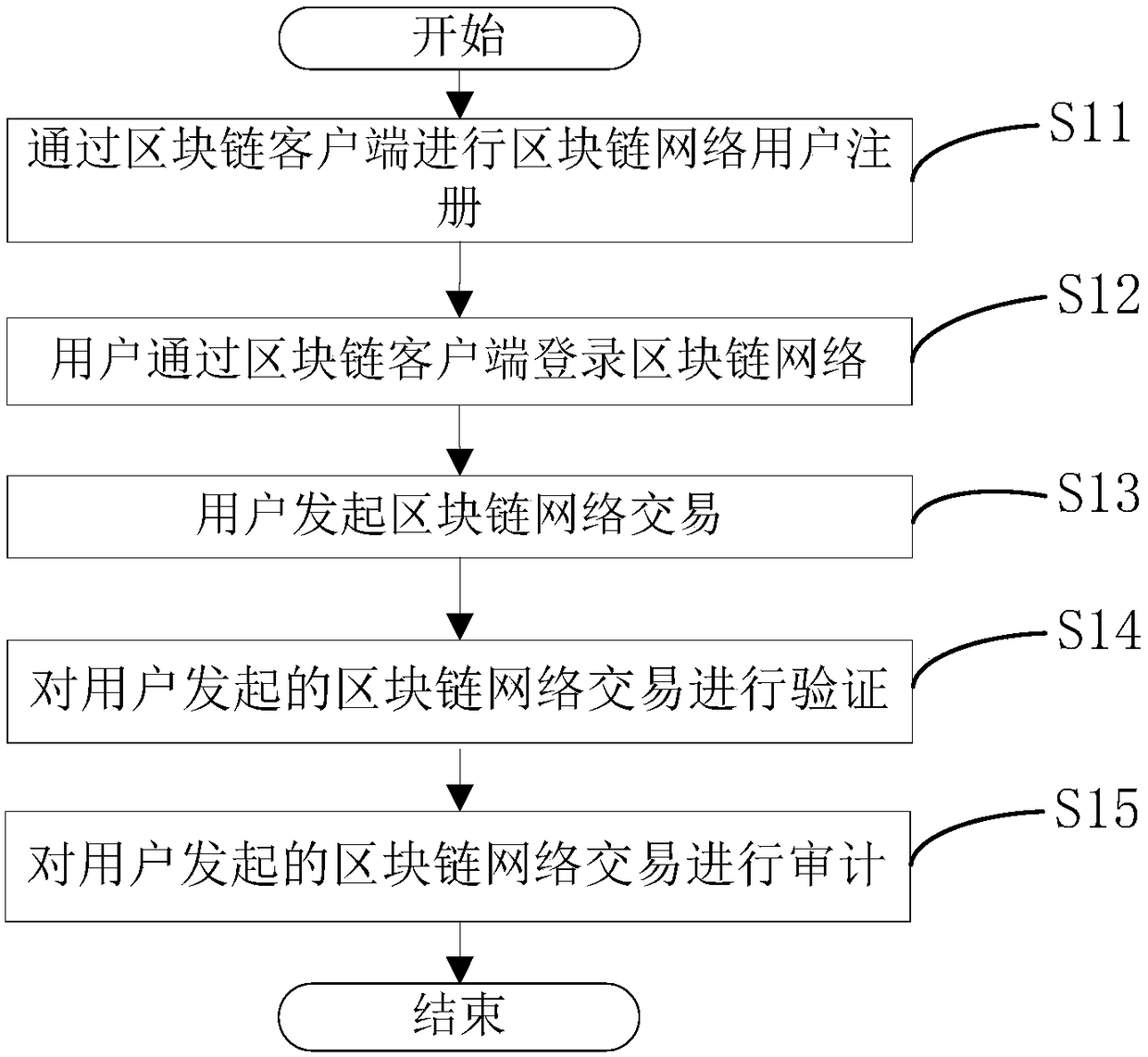
ActiveCN109005036AReduce complexityGuaranteed unforgeabilityKey distribution for secure communicationUser identity/authority verificationChain networkBlockchain
The invention relates to a block chain member management method and system based on an identification cryptographic algorithm. The method of the invention comprises the following steps: (1) registering a user of a block chain network through a block chain client, and generating a signature private key according to the user identity information by using an identification cryptographic algorithm; (2) loging in the block chain network through the block chain client by a user; 3) initiating a block chain network transaction by the user, and using an identification cryptographic algorithm to sign adigital summary of the transaction calculated by the user's block chain client end to generate signature information; (4) verifying the block chain network transaction initiated by the user, and verifying the correctness of the signature of the block chain network transaction by using the identification cryptography algorithm. The method and the system of the invention can reduce the complexityof the management of the members in the block chain network and facilitate the audit of the transaction.
Owner:WATCHDATA SYST
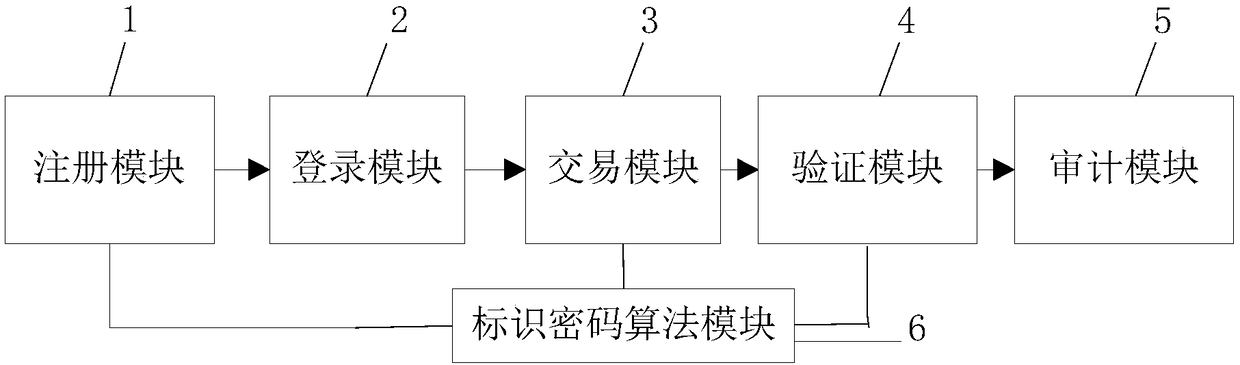
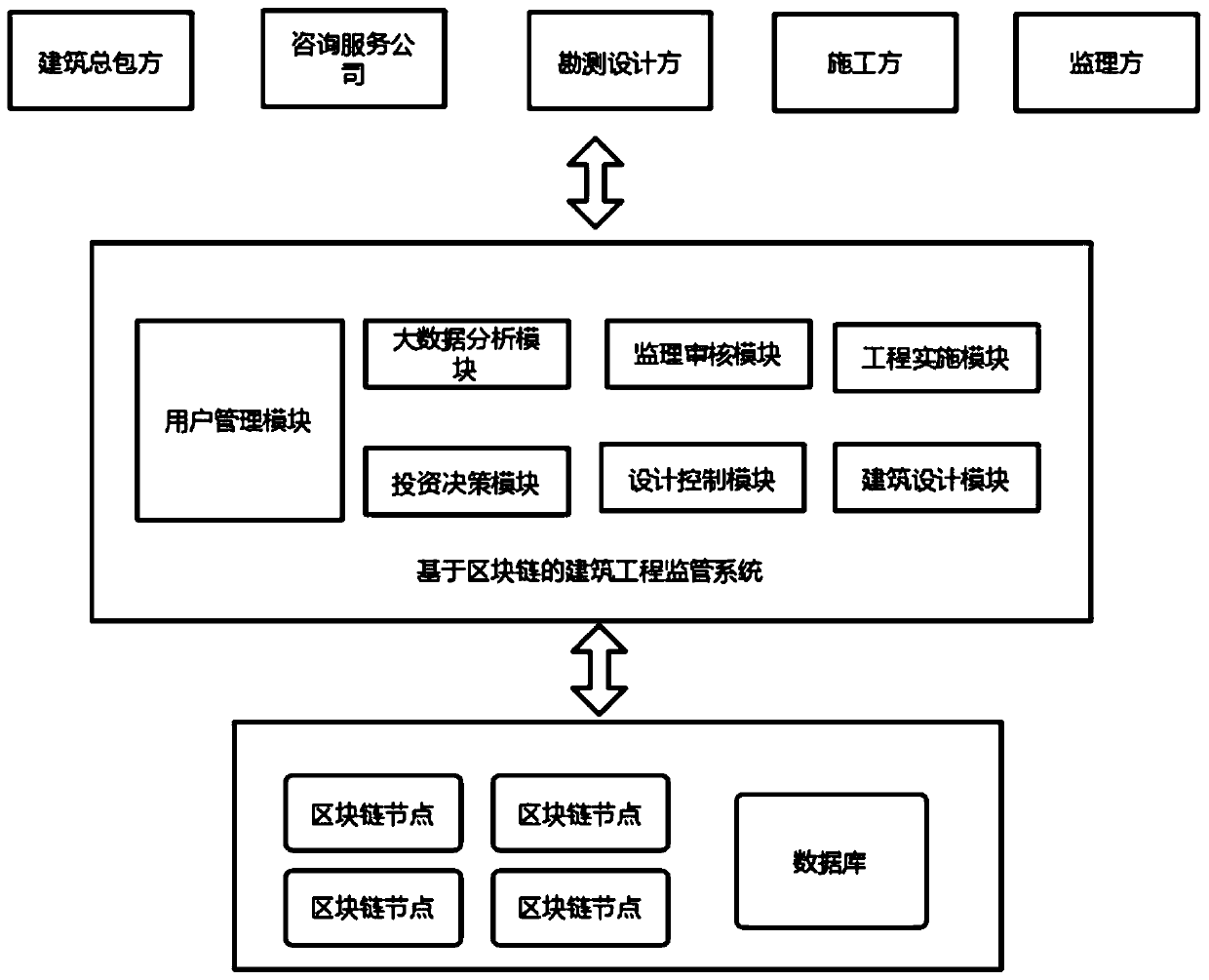
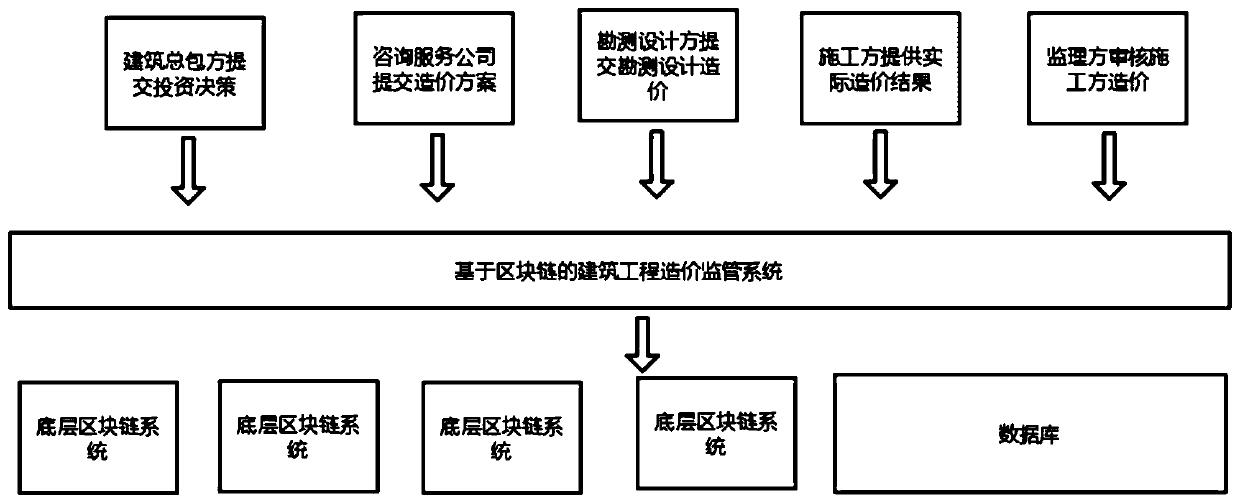
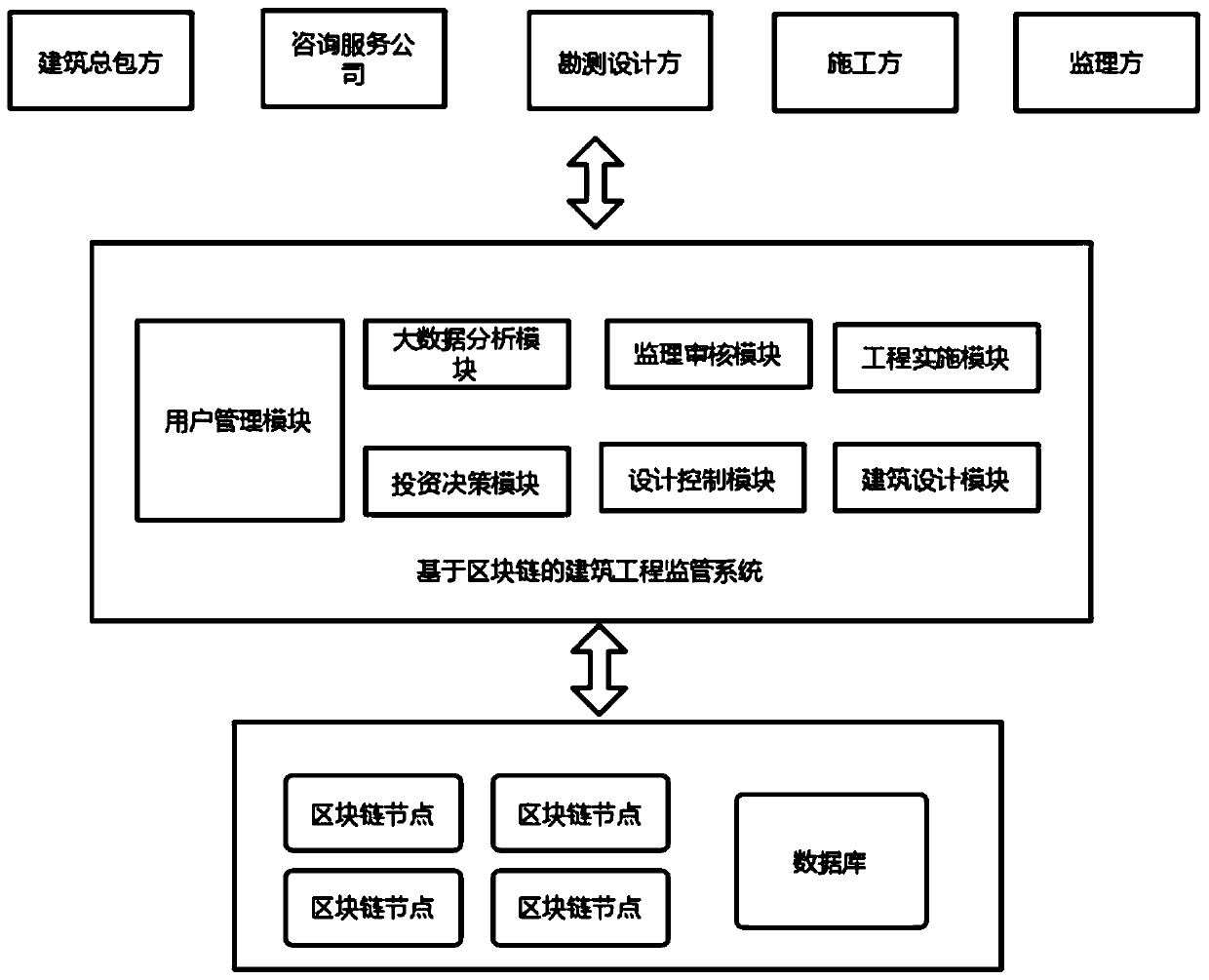
Building engineering cost supervision system and method based on block chain
ActiveCN111159769AHigh transparencyEasy to traceFinanceDigital data protectionDistributed File SystemConstruction engineering
The invention discloses a building engineering cost supervision system and method based on a block chain. The system comprises a user management module, an investment decision module, a design controlmodule, a building design module, an engineering implementation module, a supervision auditing module and a distributed file system. The invention aims to solve the problem that an existing project cost management system is insufficient in transparency. A solution is provided for solving the problems of counterfeiting and easy tampering; the information of each link of the project cost is recorded and tracked through the block chain; a public, transparent, high-credibility and traceable distributed network is constructed by using a block chain technology, so that an auditable constructional engineering cost supervision system which cooperates and mutually supervises from multiple parties including a building general contractor, a consultation service company, a survey designer, a construction party, a supervisor and the like is realized; due to the characteristics of the blockchain system, the data is prevented from being tampered, the information transparency of the system is improved, and illegal operation of illegal users is prevented.
Owner:杭州产链数字科技有限公司
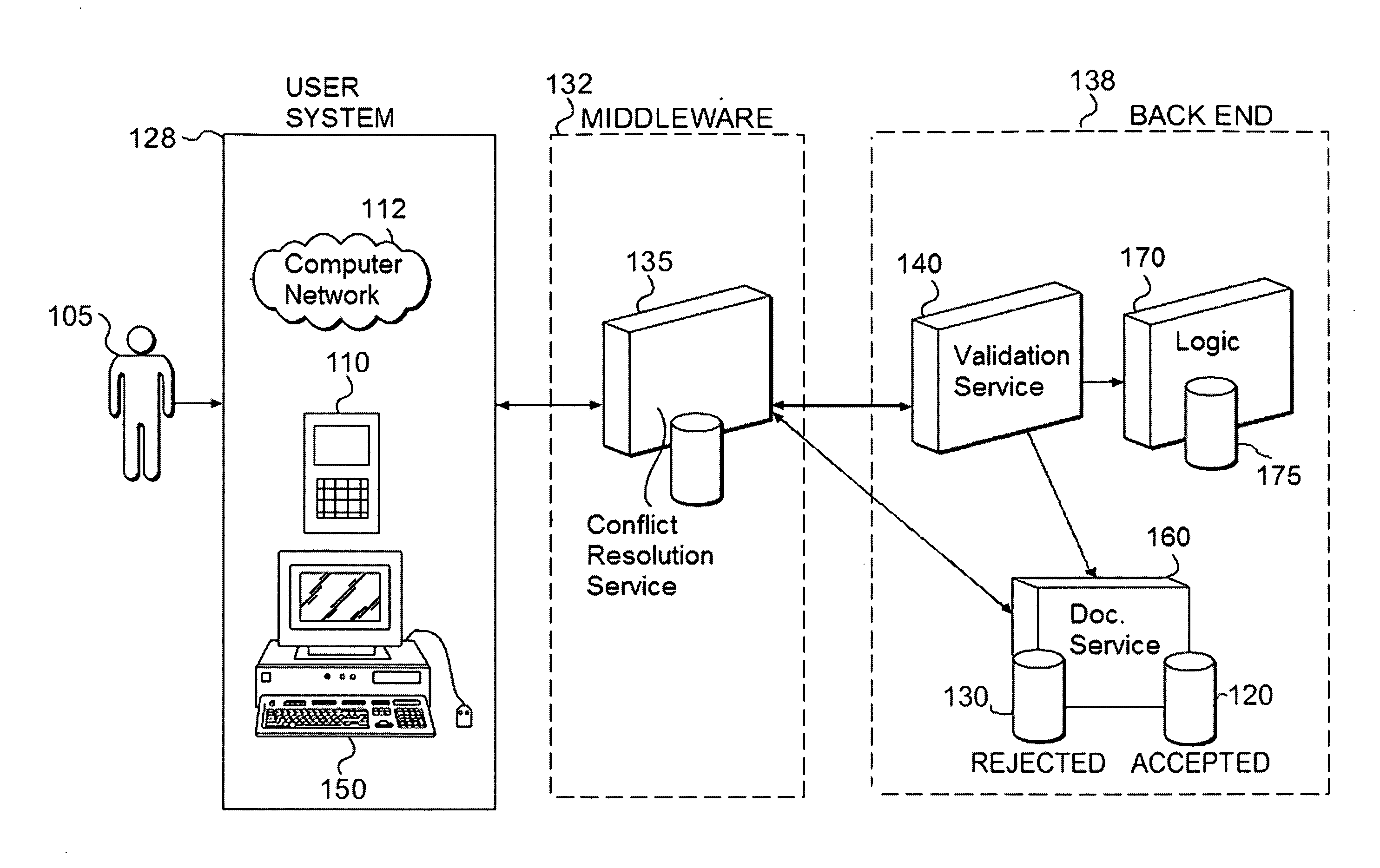
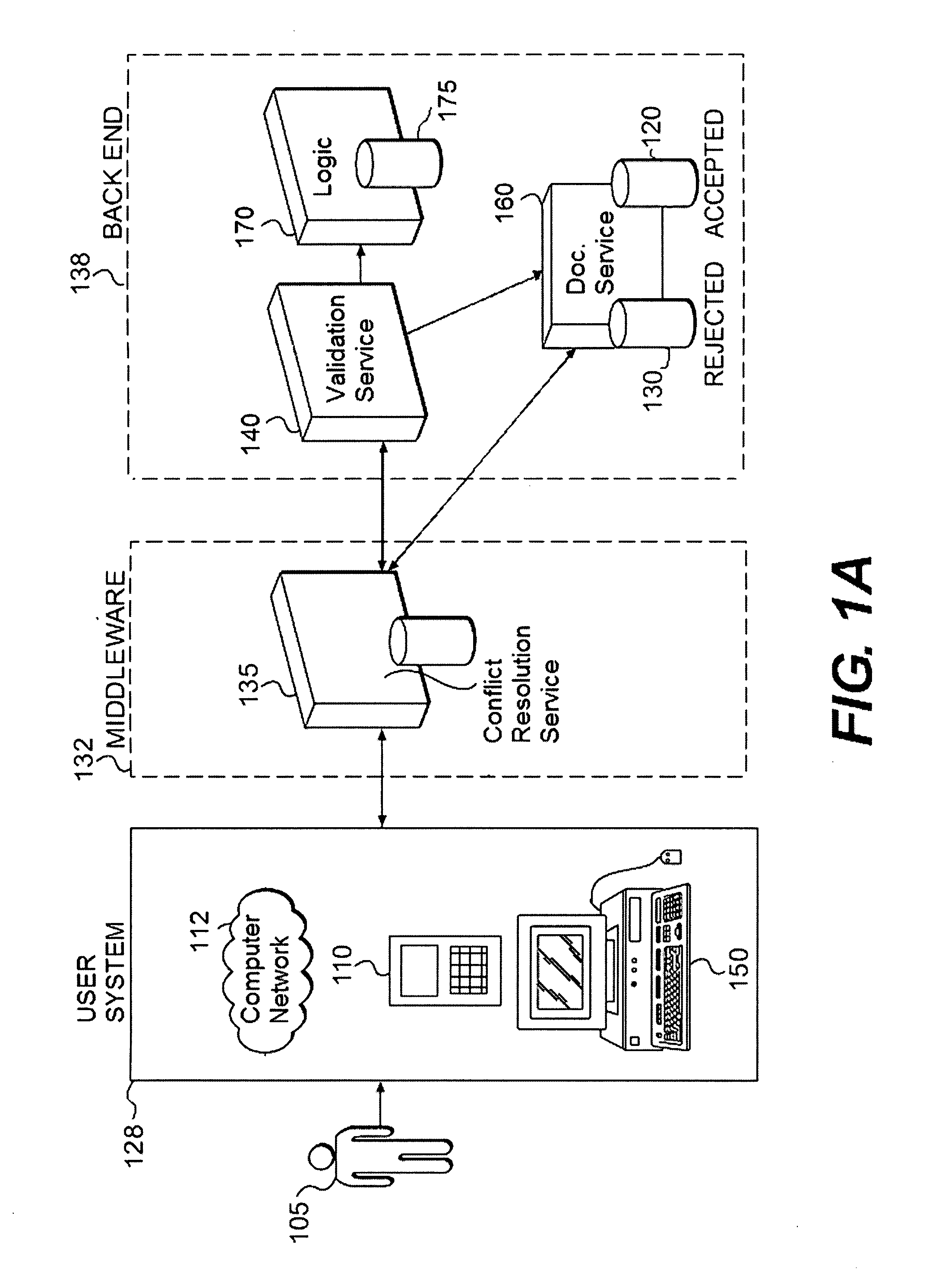
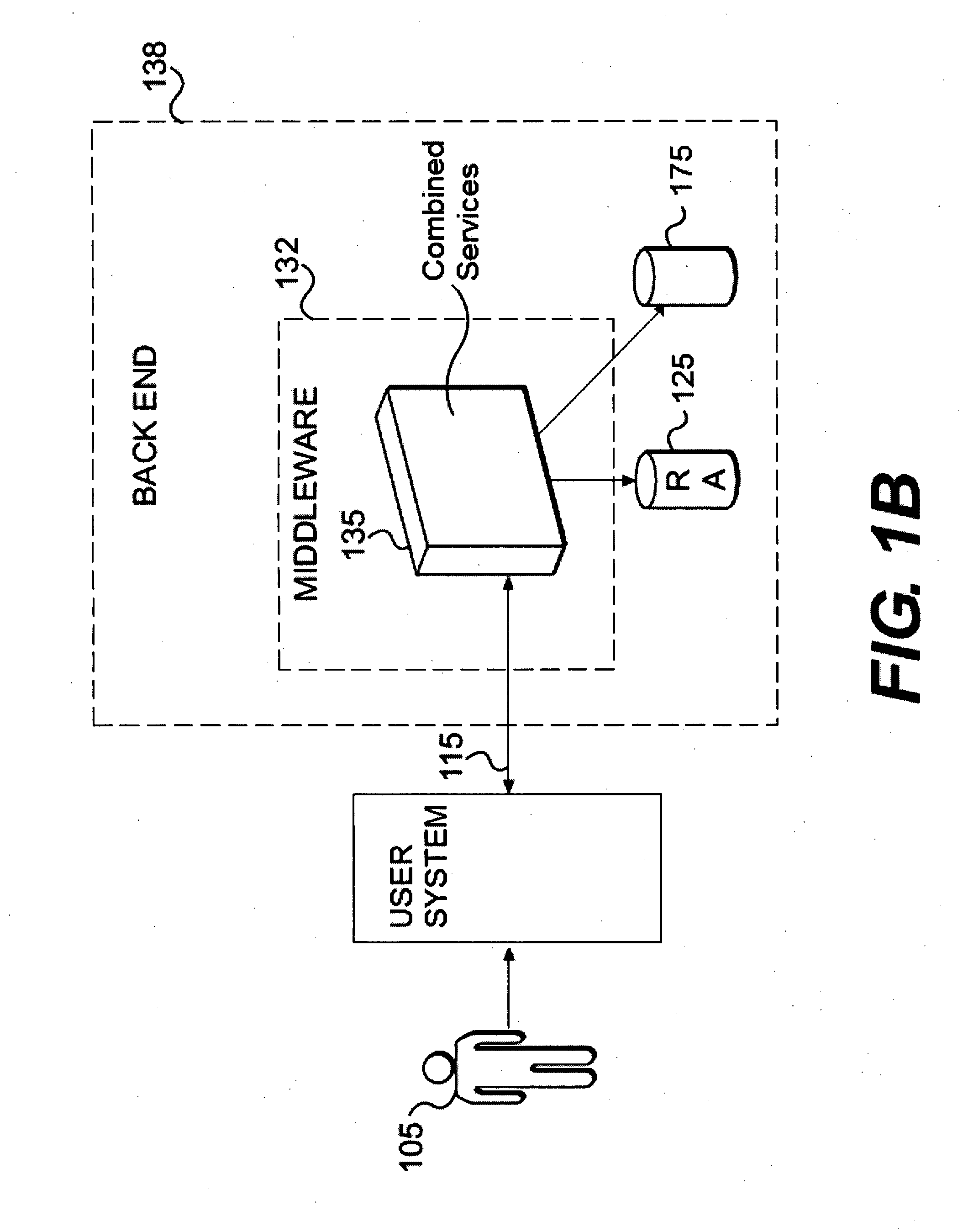
Methods and systems for storing and retrieving rejected data
InactiveUS20090024558A1Easy to auditDigital data information retrievalDigital data processing detailsData valueData objects
Methods, computer-readable media, and systems are provided to facilitate the storage, retrieval, and display of rejected data objects. Even when a data object is accepted on a user system, the data object may be rejected before reaching a backend repository if the user system and backend repository are asynchronously connected. In one implementation, a rejected data object is collected, converted into a storage format, and stored on a storage medium. Information relating the rejected data object in the storage format to a first data model is also stored. At some future time, a request is received and utilized to locate the rejected data object. Then, the rejected data object is translated from a storage format into the first object format by using the relational information. A value from the translated rejected data object can then be displayed contemporaneously with a second data value from an accepted data object. This may allow a user to see transactions and data that might otherwise be lost. Further, this may allow a system analyst to correct system problems when abnormal trends in the rejected data are observed.
Owner:SAP AG
Optical transport concentrator audit system and method
InactiveUS7103149B1Easy to auditConvenient and user friendly formatMultiplex system selection arrangementsSupervisory/monitoring/testing arrangementsReal-time computingUser Friendly
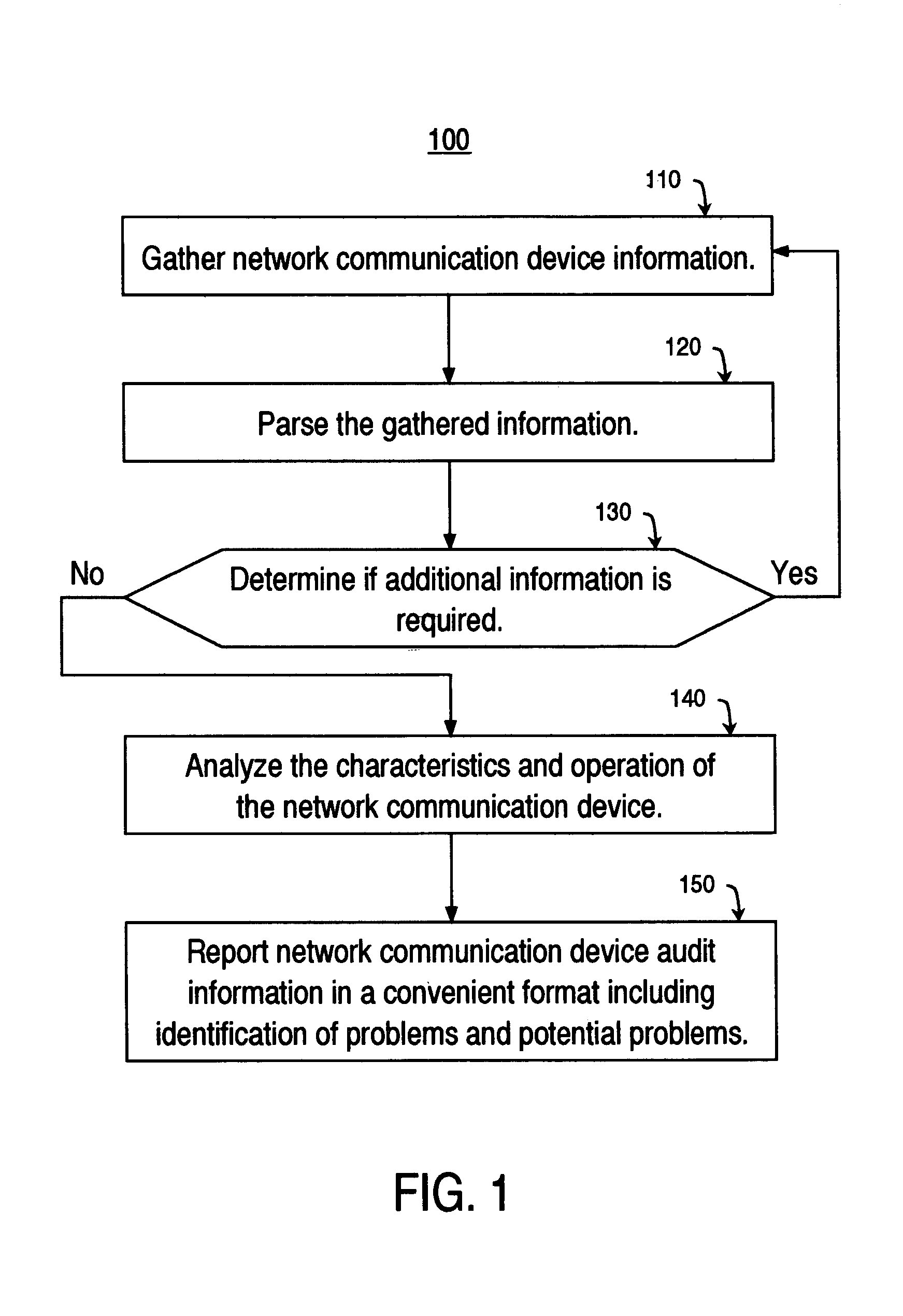
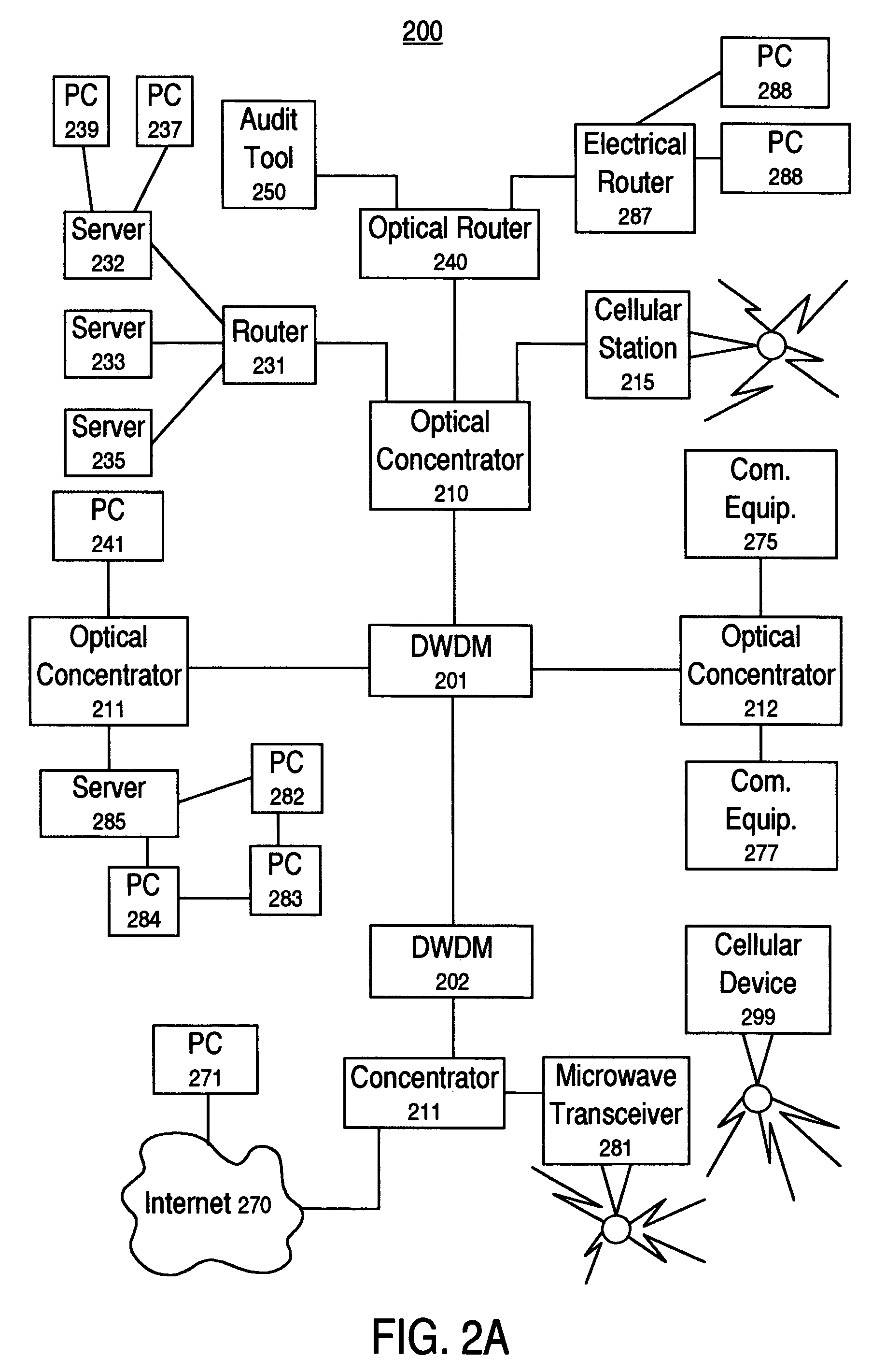
The present invention is a system and method that facilitates audits of network device (e.g., an optical network concentrator) characteristics and operations and presents results in a convenient and user friendly format. The present invention automated network communication device audit tool system and method gathers network communication device information automatically, parses the gathered information automatically, determines if additional information is required, analyzes the characteristic and operations of said network communications device; and reports network communication device information in convenient format including identification of problems and potential problems.
Owner:CISCO TECH INC
Scanning device and scanning method for scanning bar code invoice
InactiveCN103400098ARealize scanningConvenient financial reimbursementSensing by electromagnetic radiationSquare waveformBarcode
The invention discloses a scanning device and a scanning method for a bar code invoice, which are used for scanning a bar code of the bar code invoice. The scanning device comprises a scanning module, a signal shaping module and a decode outputting module, wherein the scanning module is used for optically scanning a bar code sign of the bar code invoice and converting an optical signal of a bar code and bar blank pattern into an electric signal; the signal shaping module is used for amplifying the electric signal generated by the scanning module through a circuit to generate an analog signal and filtering and shaping the analog signal to form a square wave signal corresponding to the analog signal; the decode outputting module is used for interpreting the square wave signal formed by the signal shaping module into a digital signal which can be directly accepted by a computer. According to the scanning device and the scanning method disclosed by the invention, the scanning for bar codes in notes such as various bar code invoices, air tickets, train tickets and bus tickets is realized, the authenticity of the invoices can be detected, financial reimbursement, accounting and auditing of users are facilitated, financial management of the users is enabled to become efficient and accurate and the consumption of labor force and financial resources is reduced.
Owner:SHANGHAI DIANJI UNIV
Duplicating monitoring system
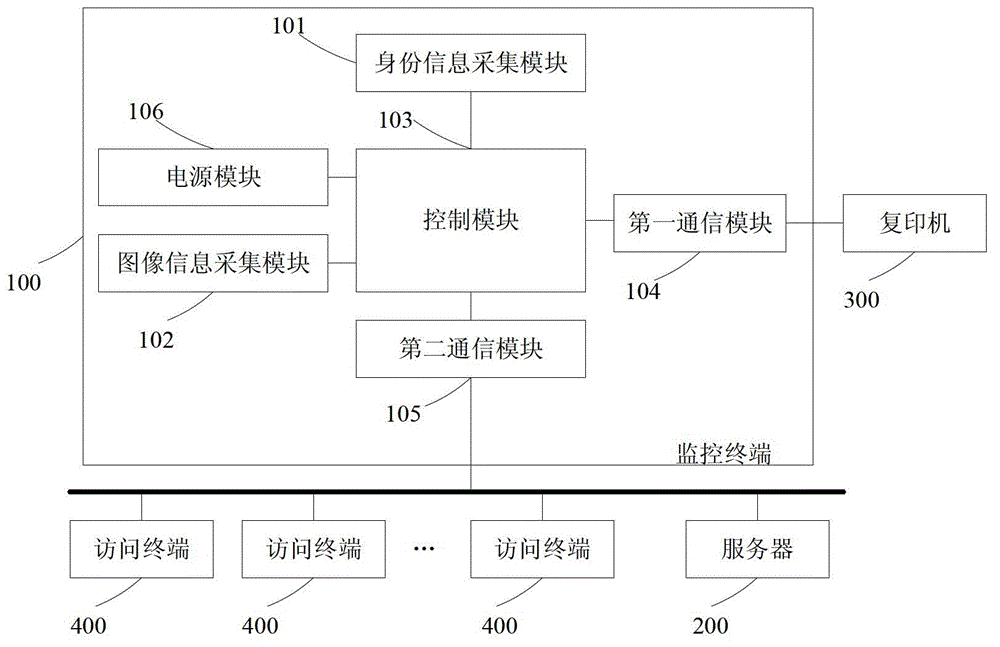
ActiveCN102749874AControl copy permissionsPrevent illegal useProgramme controlComputer controlDuplicate contentMonitoring system
The invention discloses a duplicating monitoring system and relates to the technical field of computer technology and information safety. The system comprises a monitoring terminal and a server, wherein the monitoring terminal is used for locking and unlocking a duplicator to obtain identity information and image information of a duplicator user and duplicating logs and duplicating contents of a legal user, and the identity information, the image information and the duplicating logs and the duplicating contents of the legal user can be uploaded to the server by the monitoring terminal in real time, and the server is used for checking legality of the user, receiving the user's identity information, image information, duplicating logs and duplicating contents sent by the monitoring terminal, generating an audit report which includes the identity information and the image information of the legal user and the corresponding duplicating logs and contents of the legal user, and supplying inquiry of the audit report. The system has the advantages that the duplicator is controlled to be merely used by authorized users, the duplicating logs can be comprehensively, accurately and automatically recorded, simultaneously the audit report of the duplicating logs is supplied, and the system is convenient for administrative stuffs to inquire and audit the duplicating operation.
Owner:BEIJING LANXUM COMP TECH
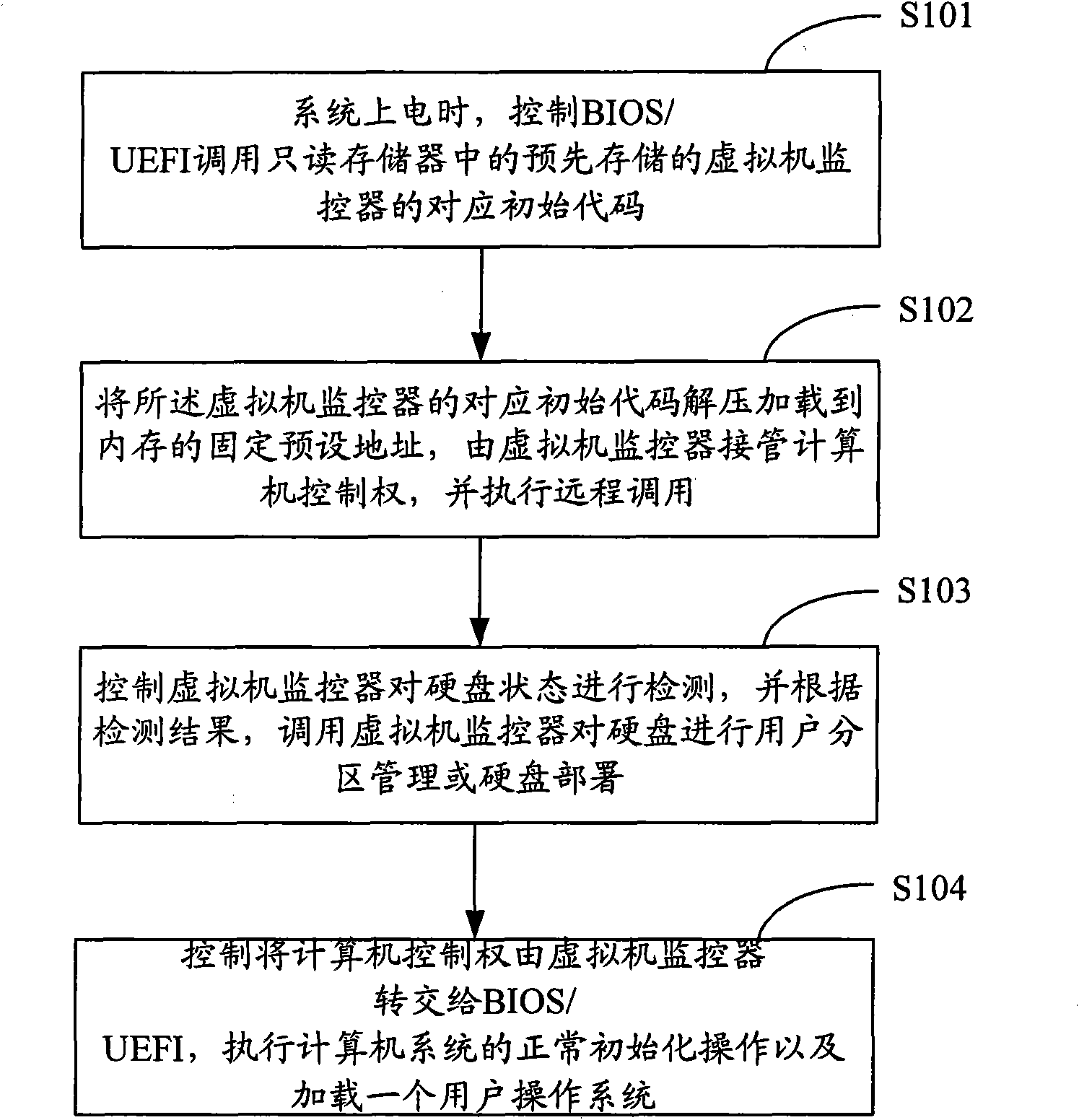
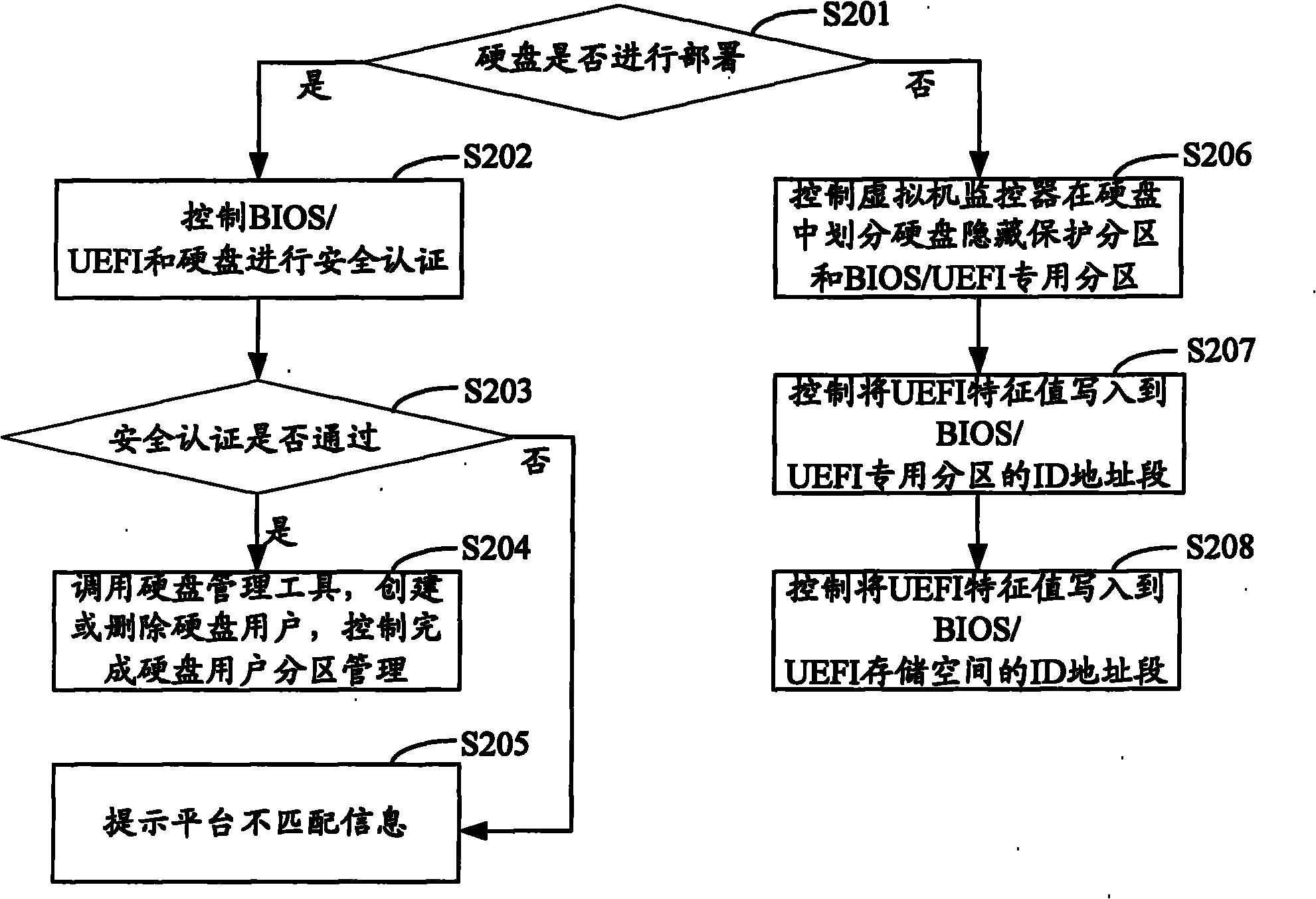
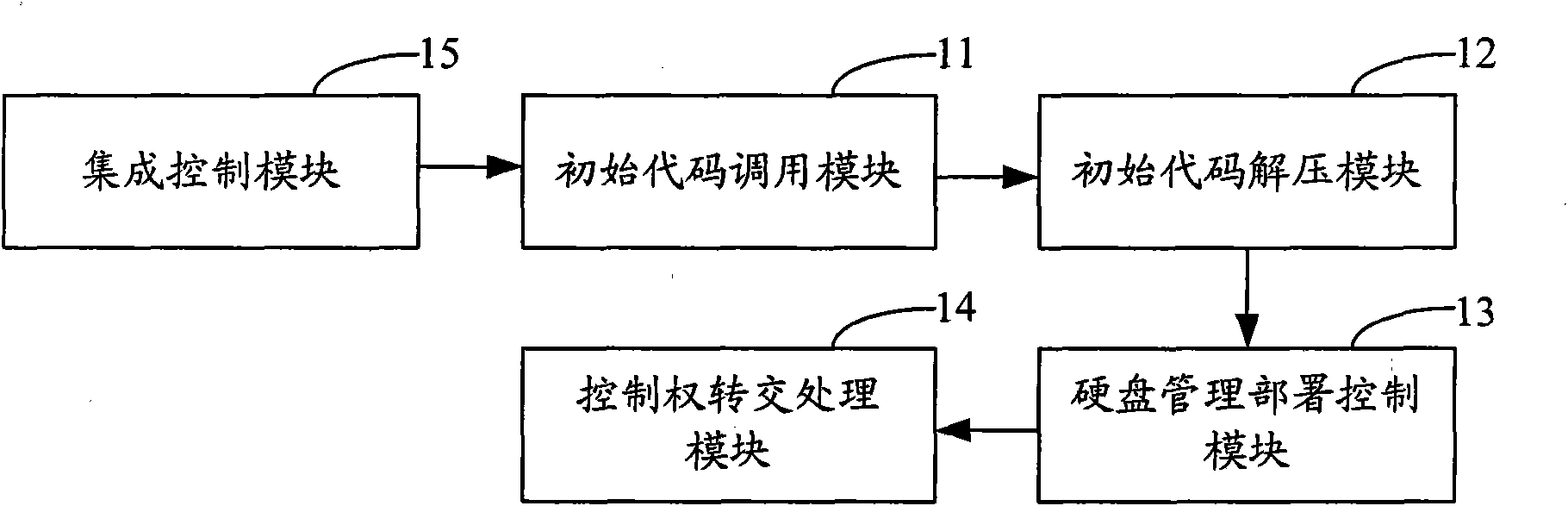
Interaction method and system for BIOS/UEFI and virtual machine monitor
ActiveCN102110007AGuaranteed safe operationSolve the costly flaws of hard encryptionPlatform integrity maintainanceSoftware simulation/interpretation/emulationOperational systemComputerized system
The invention is suitable for the technical field of computers, and provides an interaction method and system for BIOS / UEFI and a virtual machine monitor. The method comprises the steps: controlling BIOS / UEFI to call the corresponding initial code of the virtual machine monitor in a read-only memory when the system is powered on; decompressing and loading the corresponding initial code of the virtual machine monitor to a fixed preset address of a memory to make the virtual machine monitor take over the computer control right, and executing remote call; controlling BIOS / UEFI to detect the state of a hard disc, and calling the virtual machine monitor to carry out user partition management on the hard disc or deploy the hard disc based on the detection result; and controlling to reassign the computer control right from the virtual machine monitor to the BIOS / UEFI, and executing the normal initialization operation of the computer system and loading a user operation system to achieve the operation of the BIOS / UEFI in the virtual machine monitor. Therefore, the method overcomes the disadvantage of expensive hard-encryption of the hard disc, and can monitor any access to the hard disc.
Owner:CHINA GREATWALL TECH GRP CO LTD
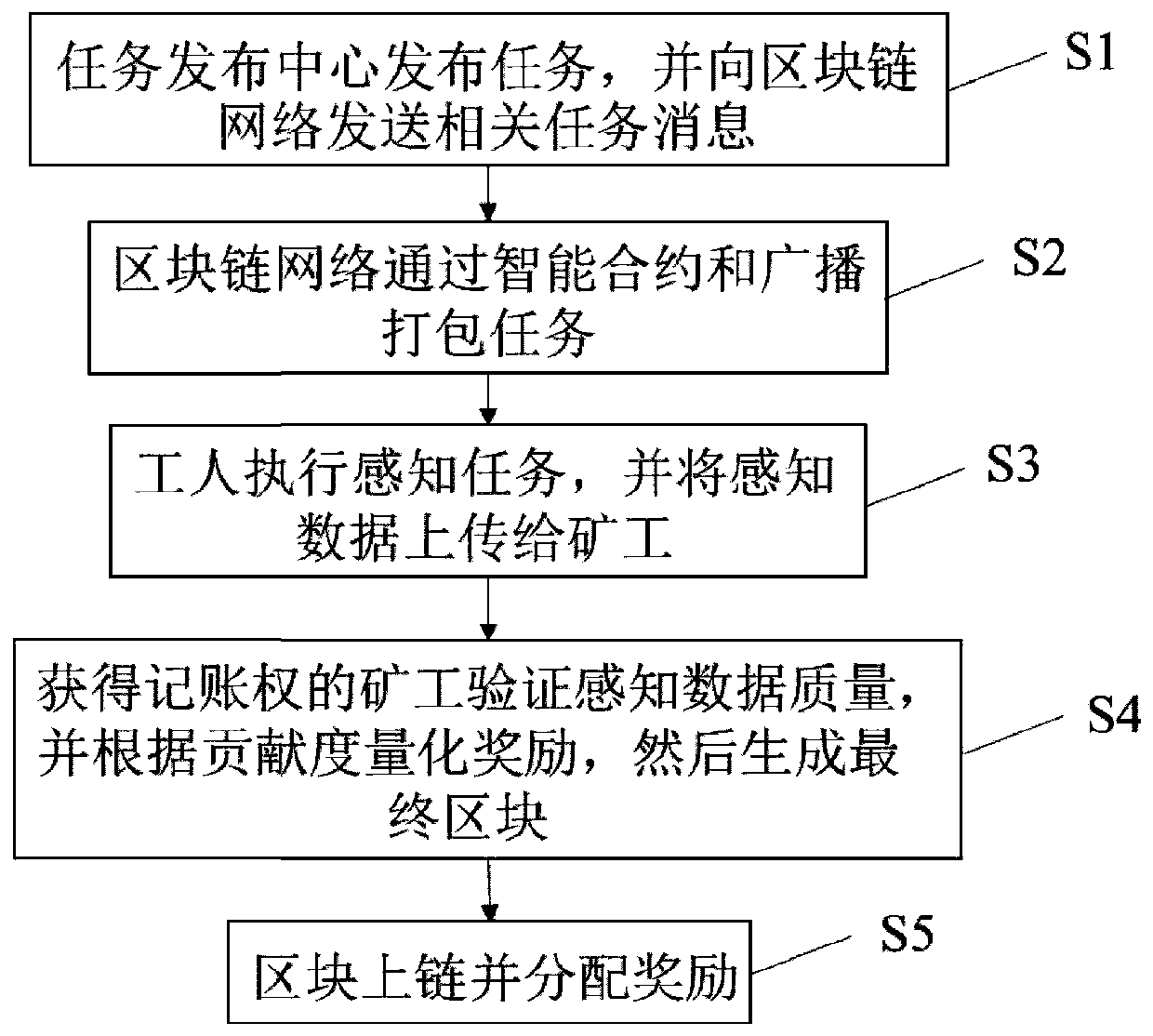
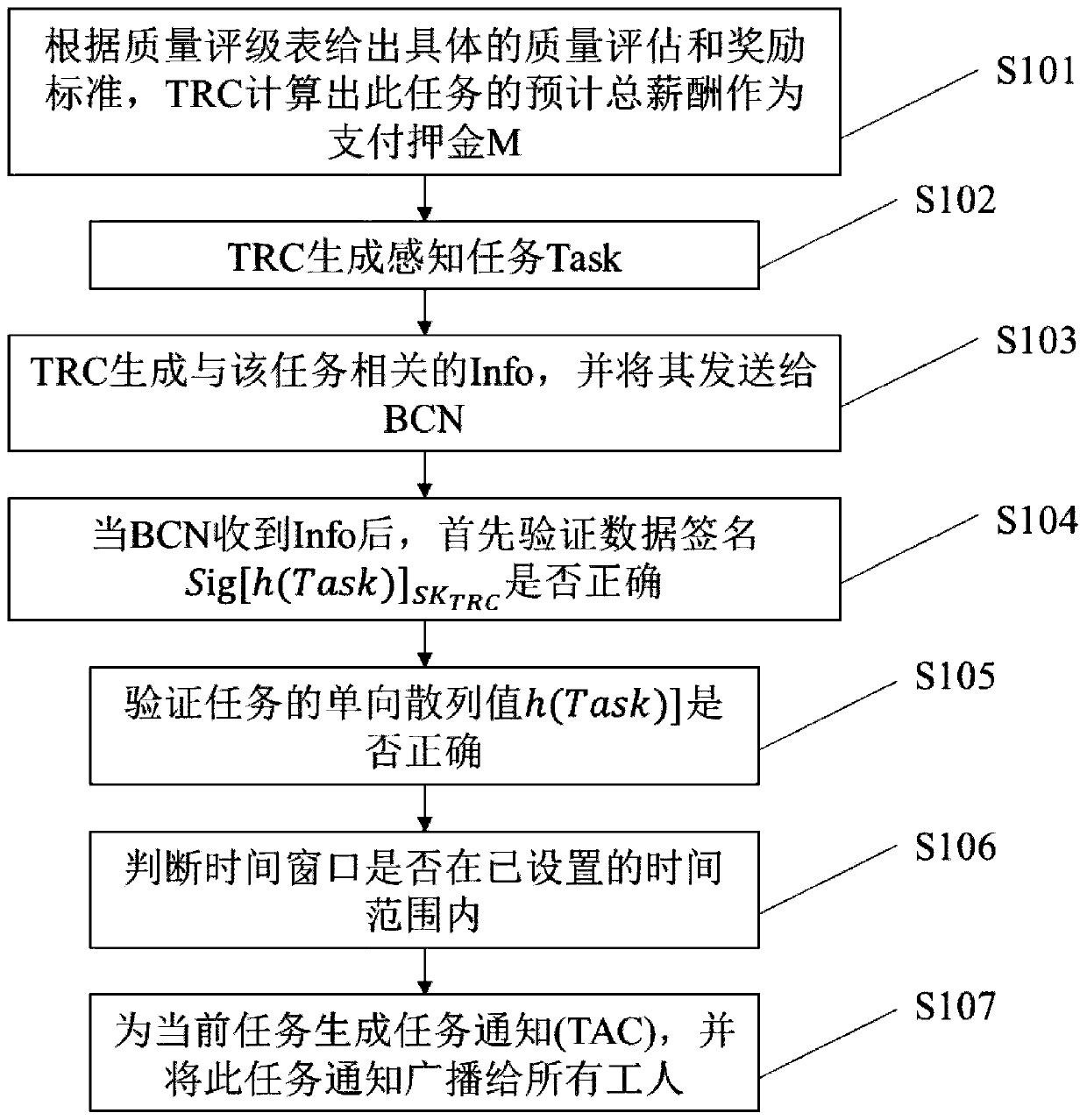
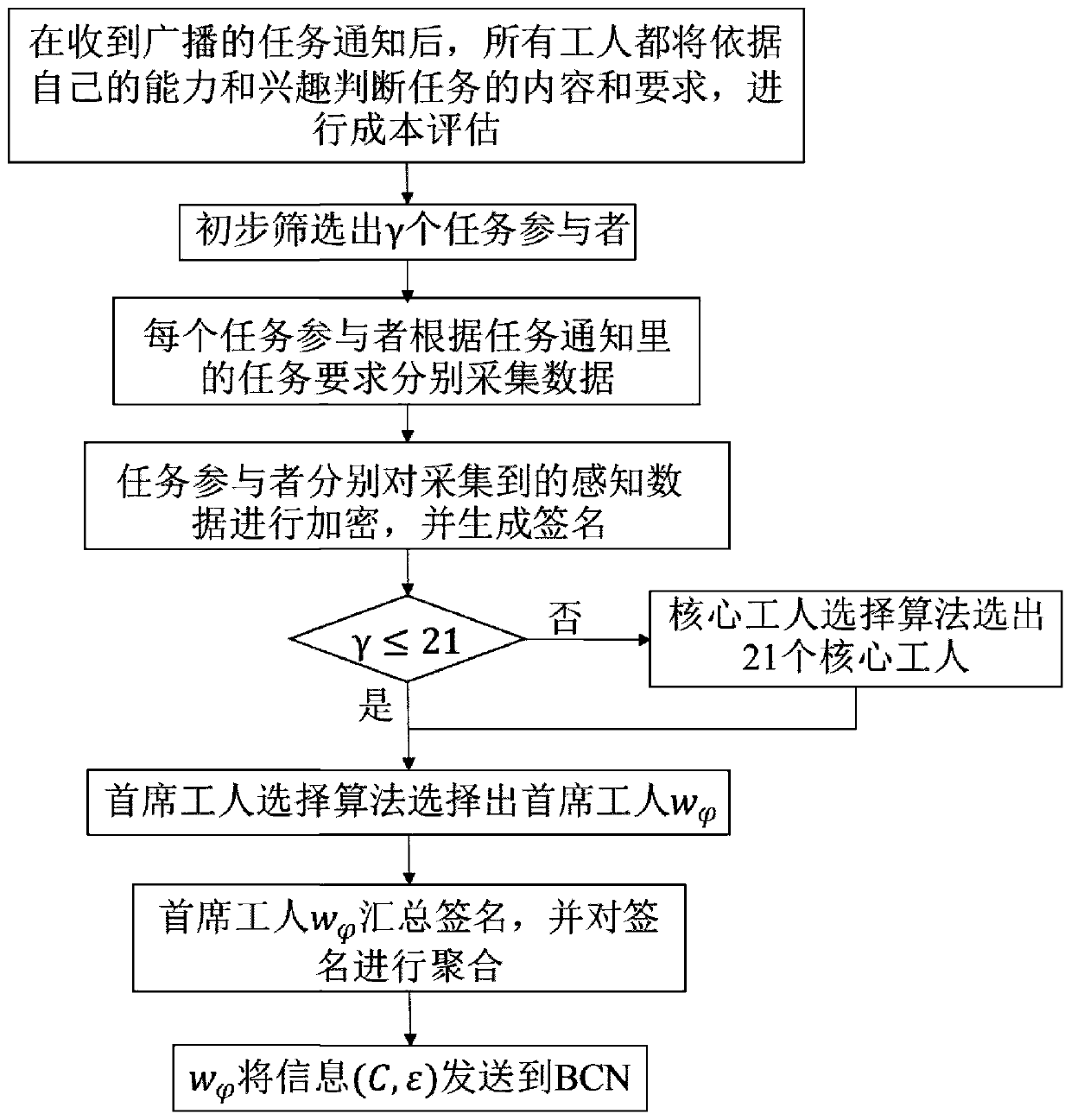
Crowd sensing dual privacy protection method based on block chain
ActiveCN110825810AMeet the needs of scaleSupport joinDatabase distribution/replicationDigital data protectionSensing dataAttack
The invention discloses a crowd sensing dual privacy protection method based on a block chain. The method comprises the steps that a task publishing center publishes a sensing task and sends a messagerelated to the task to a block chain network; the block chain network generates a perception task notification through the smart contract and broadcasts the perception task notification to all workers; the workers execute the sensing task and upload the sensing data to the block chain network; the nodes in the block chain network compete for the accounting right by using a consensus algorithm, the miner obtaining the accounting right verifies the quality of the perception data, quantifies the rewards according to the contribution degree, and then generates a final block; and when the final block is recorded on the block chain, rewards are also allocated to corresponding workers and miners, and the like. The method has the advantages that consensus is achieved through the contribution degree consensus algorithm, the shared block chain is used for storing records, on one hand, transparent records are provided, convenience is brought to auditing, and meanwhile malicious attack behaviorsof lawbreakers on the shared network can be prevented.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
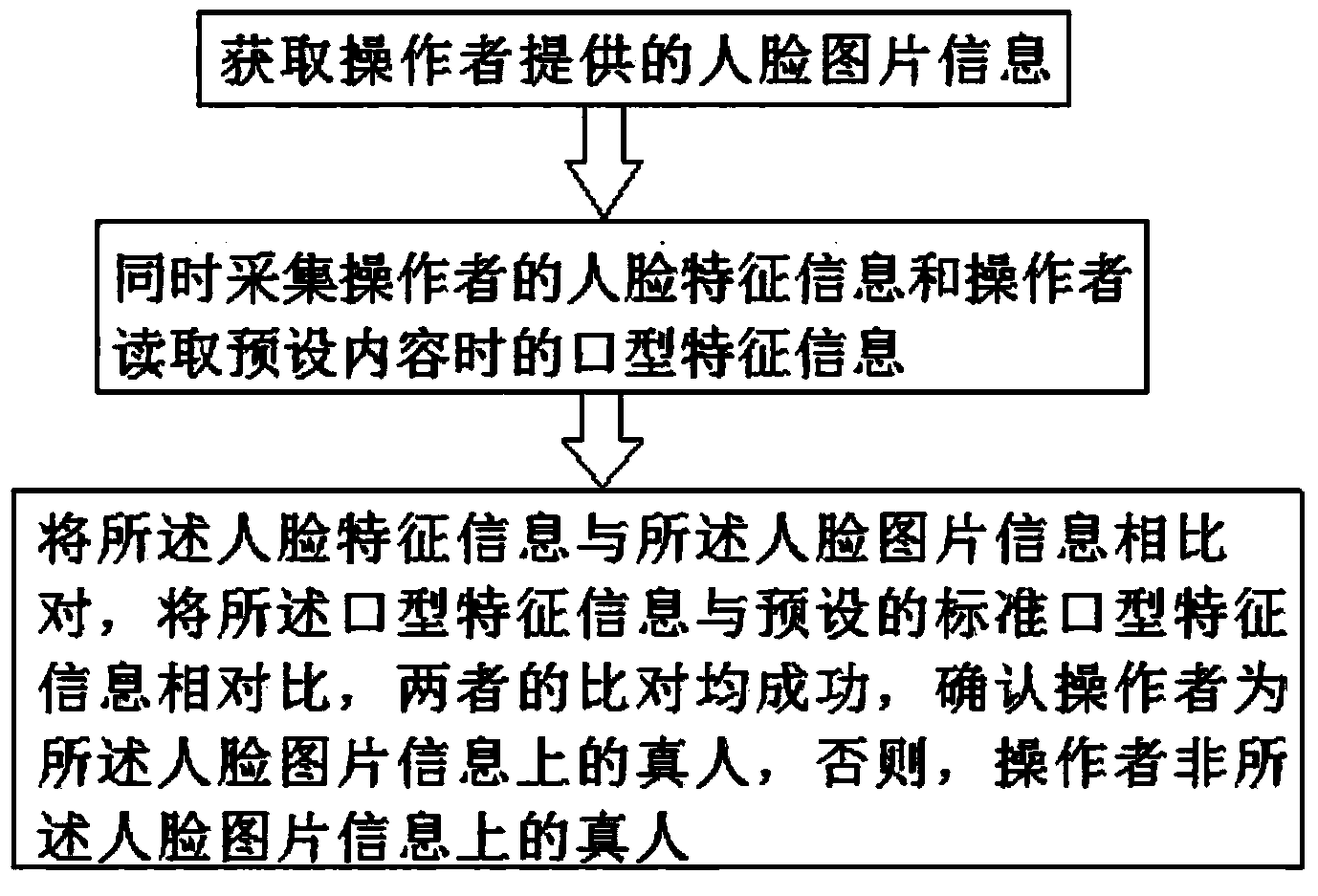
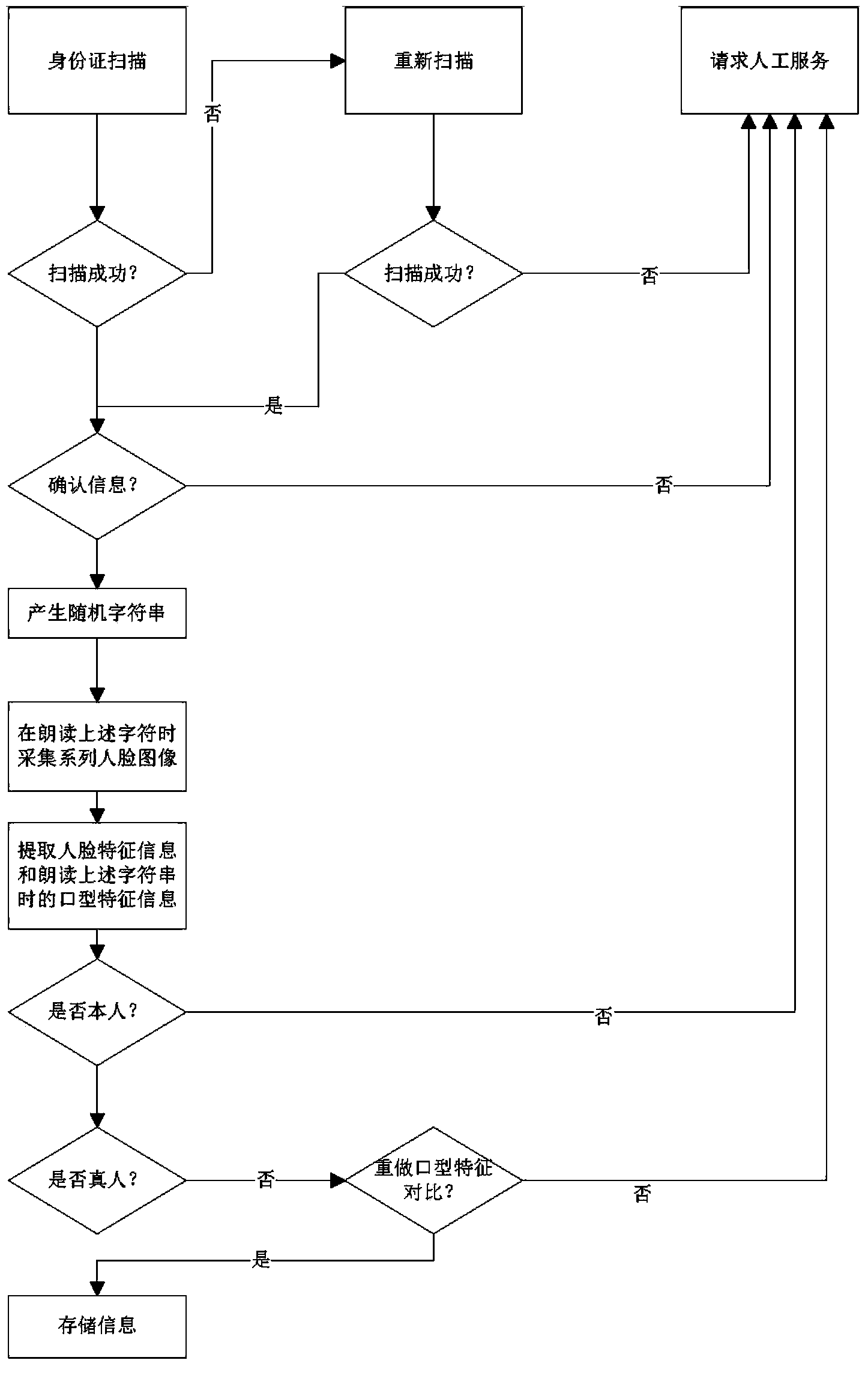
Real person identity verification method
InactiveCN104217212AEasy to useGood for promotionCharacter and pattern recognitionComputer visionPersonal identity verification
The invention discloses a real person identity verification method. The method comprises the following steps: acquiring human face picture information provided by an operator; simultaneously acquiring the human face characteristic information of the operator and the mouth shape characteristic information of the operator during reading of preset content; and comparing the human face characteristic information with the human face picture information, comparing the mouth shape characteristic information with preset standard mouth shape characteristic information, if comparison succeeds, confirming that the operator is a real person on the human face picture information, and otherwise, confirming that the operator is not the real person on the human face picture information. According to the method, the identity of the real person is judged by simultaneously acquiring the human face characteristic information and the mouth shape characteristic information without making contact with the operator, so that the popularization of the method is facilitated; comparison of the human face characteristic information is adopted, so that confirmation and auditing on whether the operator is the real person or not are facilitated, the identification accuracy is high, and the accuracy is increased; and comparison of the mouth shape characteristic information is adopted, so that others can be prevented from cracking a human face identification comparison technology by using non-real-person objects, and the security is enhanced. On-site pictures can be stored, and a monitoring function is realized.
Owner:SUZHOU YOUHUA INTELLIGENT TECH CO LTD
Network security system under mobile Internet environment
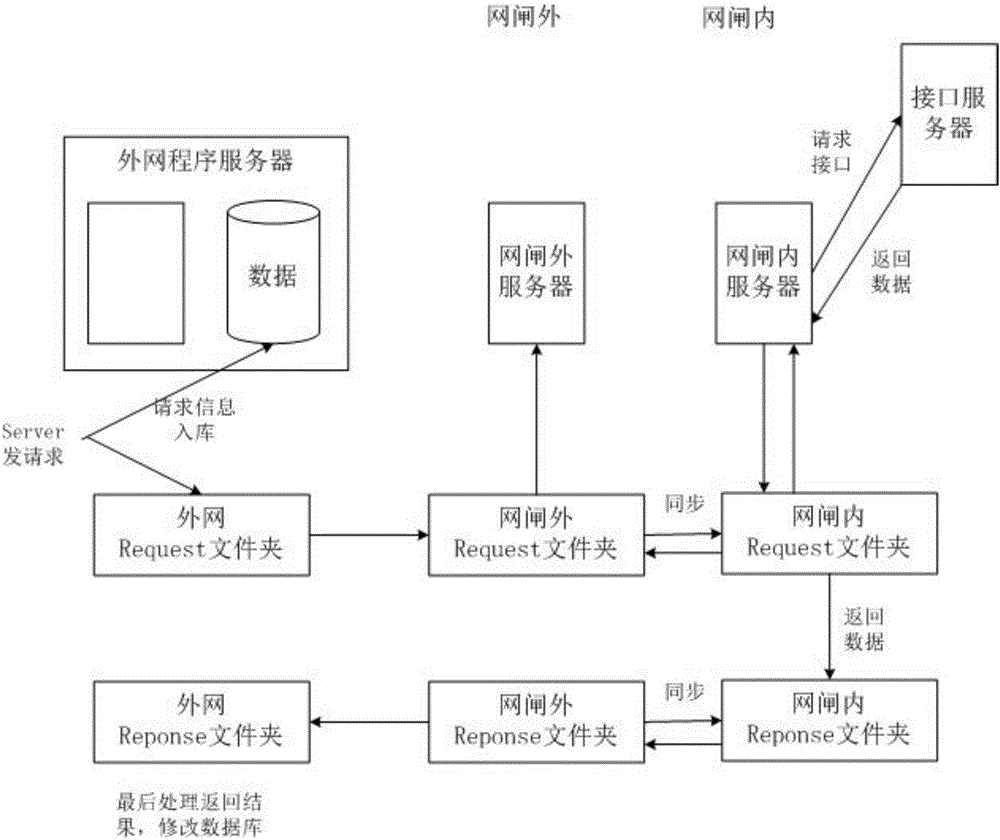
InactiveCN106230795AProtects against internal sabotage and external attacksReduce maintenance costsTransmissionSecurity arrangementService systemApplication server
The invention relates to a network security system under a mobile Internet environment, comprising a security isolation gap, an extranet application server, a gap external server, a gap internal server, and an interface server which is connected with a specific application service system and provides interface service. The extranet application server receives an access request of a user, transmits the access request among the gap external server, the gap internal server and the interface server through an inter-gap asynchronization and synchronization function, and gets returned data through the interface server. The returned data is transmitted among the gap internal server, the gap external server and the extranet application server the inter-gap asynchronization and synchronization function, and is returned to the user. The application service system is deployed through the security isolation gap to establish a perfect access control mechanism, and cross-operation-platform, cross-platform and cross-service-platform security access management strategies can be provided.
Owner:北京近颐科技有限公司
Distributed access control method based on block chain
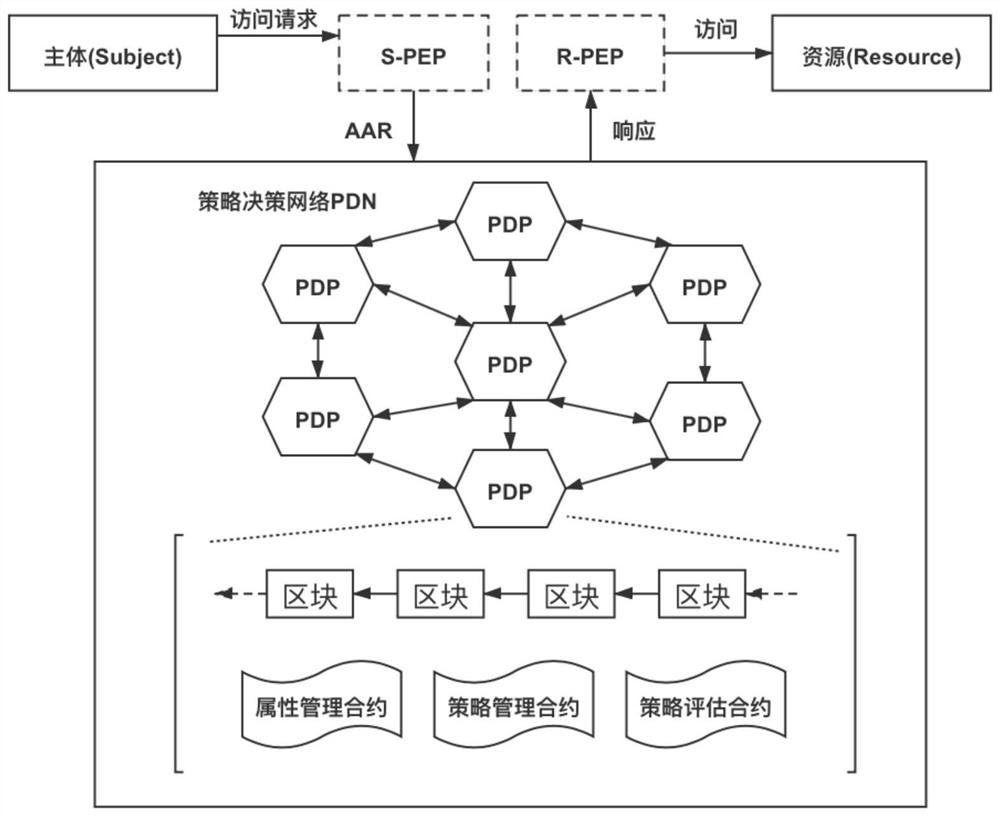
ActiveCN112688927AImprove resistance to attackEliminate single points of failureUser identity/authority verificationDistributed decisionSmart contract
The invention relates to a distributed access control method based on a block chain, and belongs to the field of information security. The method comprises the following steps: designing a distributed access authorization process: designing the distributed access authorization process according to the functions of each component in a distributed access control model B-ABAC based on a block chain; meanwhile, in the authorization process, recording generated authorization access records on the block chain; S2, designing an attribute and strategy intelligent contract: separating functions of attribute authority and strategy authority, and dispersing the functions into an intelligent contract and a block chain account book in the B-ABAC model; and S3, designing consensus algorithm: using the distributed decision network to replace original decision points, and designing and using the improved consensus algorithm to carry out consensus maintenance on the distributed decision network. In an untrusted environment, fine-grained and dynamic access authorization can be provided, meanwhile, the security and auditability of an access model are improved, and human intervention in the authorization process is reduced.
Owner:CHONGQING UNIV +1
Device and method for automatically manufacturing virtual machine mirror image in cloud computing environment
InactiveCN109933408AEasy to auditEasy to trackSoftware simulation/interpretation/emulationSoftware deploymentGraphicsOpen source
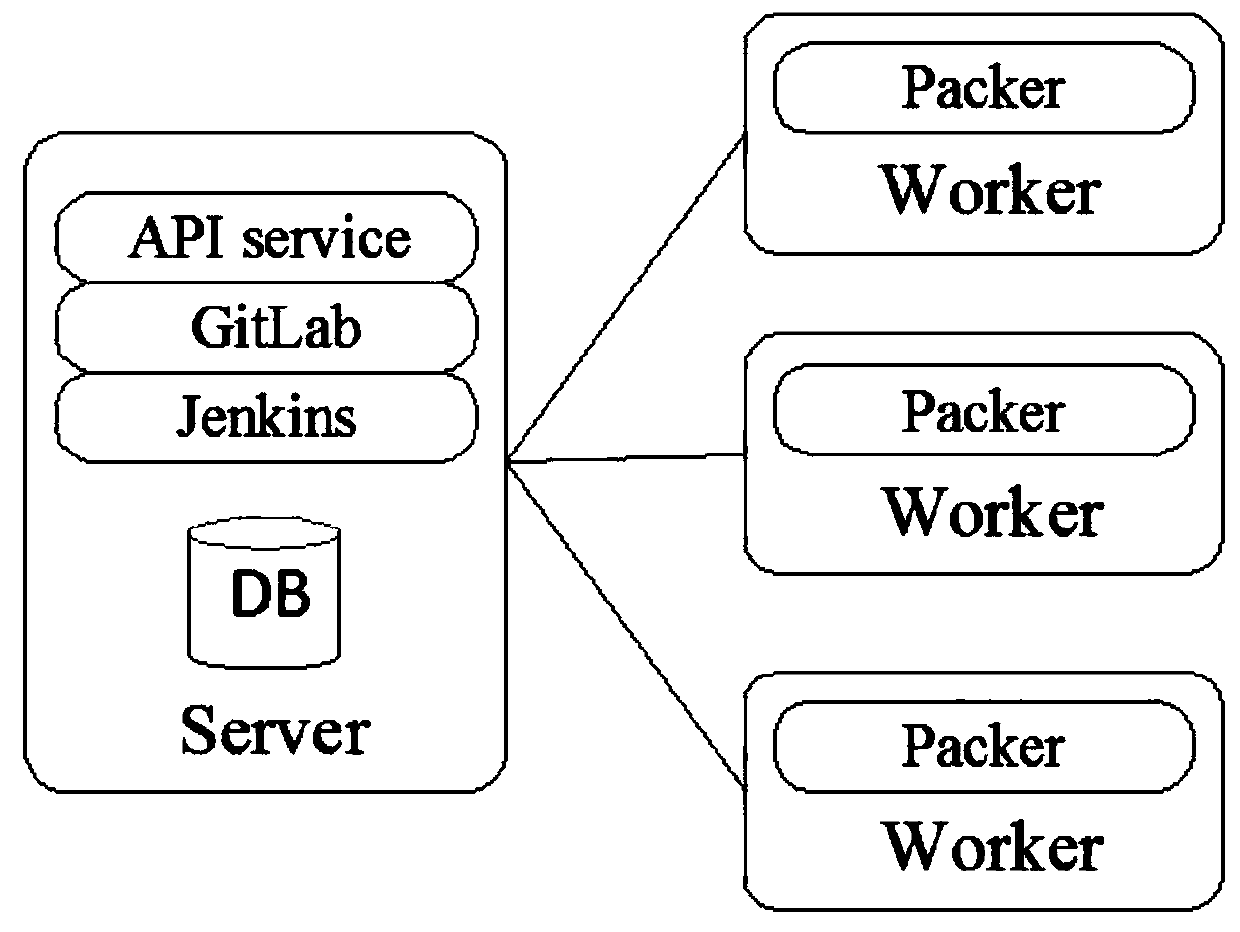
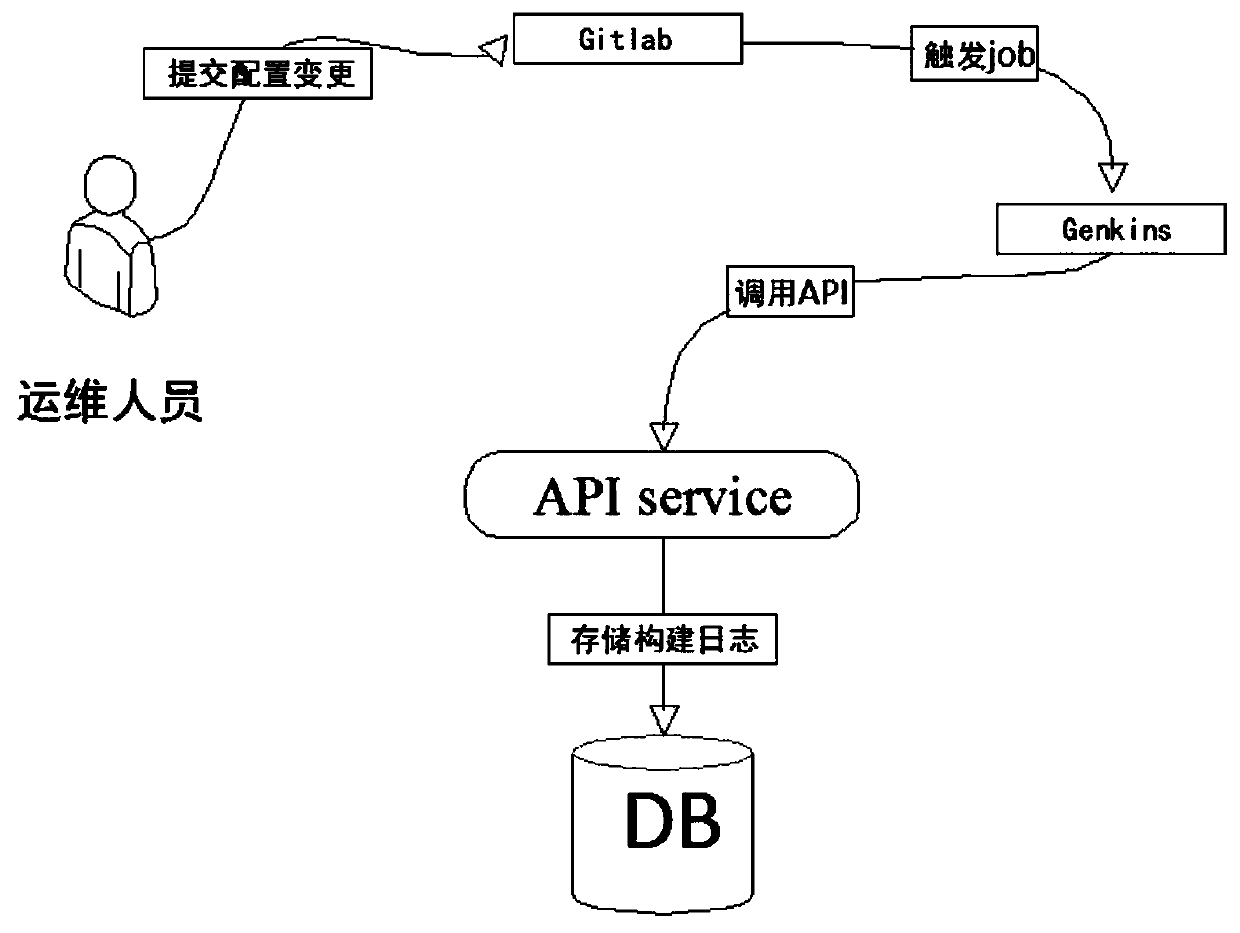
The invention discloses a device and a method for automatically manufacturing a virtual machine mirror image in a cloud computing environment, and belongs to the field of cloud computing. According tothe method, a traditional manual operation mode through a graphical interface mode is changed, unattended template configuration is introduced ingeniously, and then the purpose of automatically manufacturing the virtual machine mirror image is achieved through an open source software tool. Meanwhile, the template configuration can serve as a code to be hosted in a GitLab warehouse. The process ofmirror image making is managed as a job of Jenkins. A project corresponding to the GitLab is linked through webhook and Job of Jenkins, when template configuration changes and is pushed to the GitLab, an instruction can be issued to the Jenkins through the webhook, and automatic manufacturing is triggered. In addition, the built logs including mirror image basic information, change contents and change time are recorded through the database, so that subsequent operation, maintenance and auditing are facilitated.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
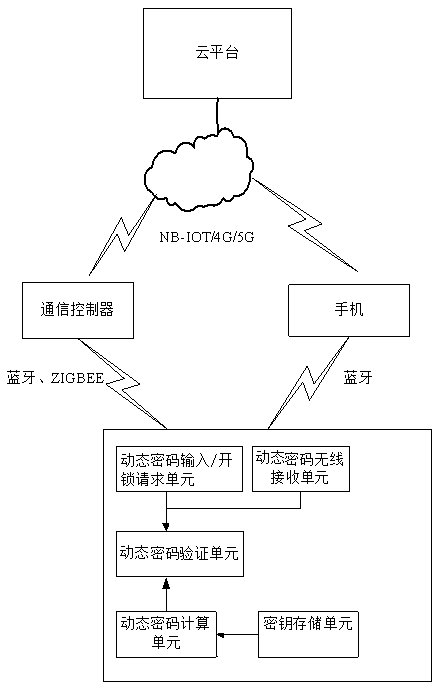
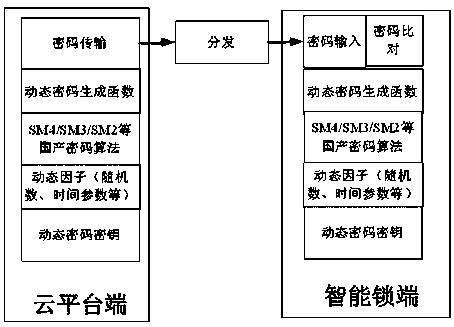
Cabinet access control system and method based on dynamic password
ActiveCN110535968ANo correlationImprove securityIndividual entry/exit registersTransmissionKey pressingControl system
A cabinet access control system based on a dynamic password comprises a cloud platform, a communication controller, an intelligent lock and a mobile device, the communication controller and the mobiledevice are both in wireless connection with the cloud platform, the communication controller is in wired or wireless connection with the intelligent lock, and the mobile device is in wired or wireless connection with the intelligent lock. The invention further discloses a control method of the cabinet access control system based on the dynamic password. According to the invention, the unlocking modes of a contact type or non-contact type IC card and the like of the existing lock are abandoned, and a user does not need to carry the unlocked IC card or user card and the like at any time. Password verification is carried out in the intelligent lock, a secret key is stored in an exclusive area of the intelligent lock, and when an operator inputs a dynamic password through a key or a touch screen of the intelligent lock, the dynamic password is effective once and needs to be input within the effective duration of the password, leakage does not need to be worried about, and safety performance is high.
Owner:长沙北之辰智能技术有限公司
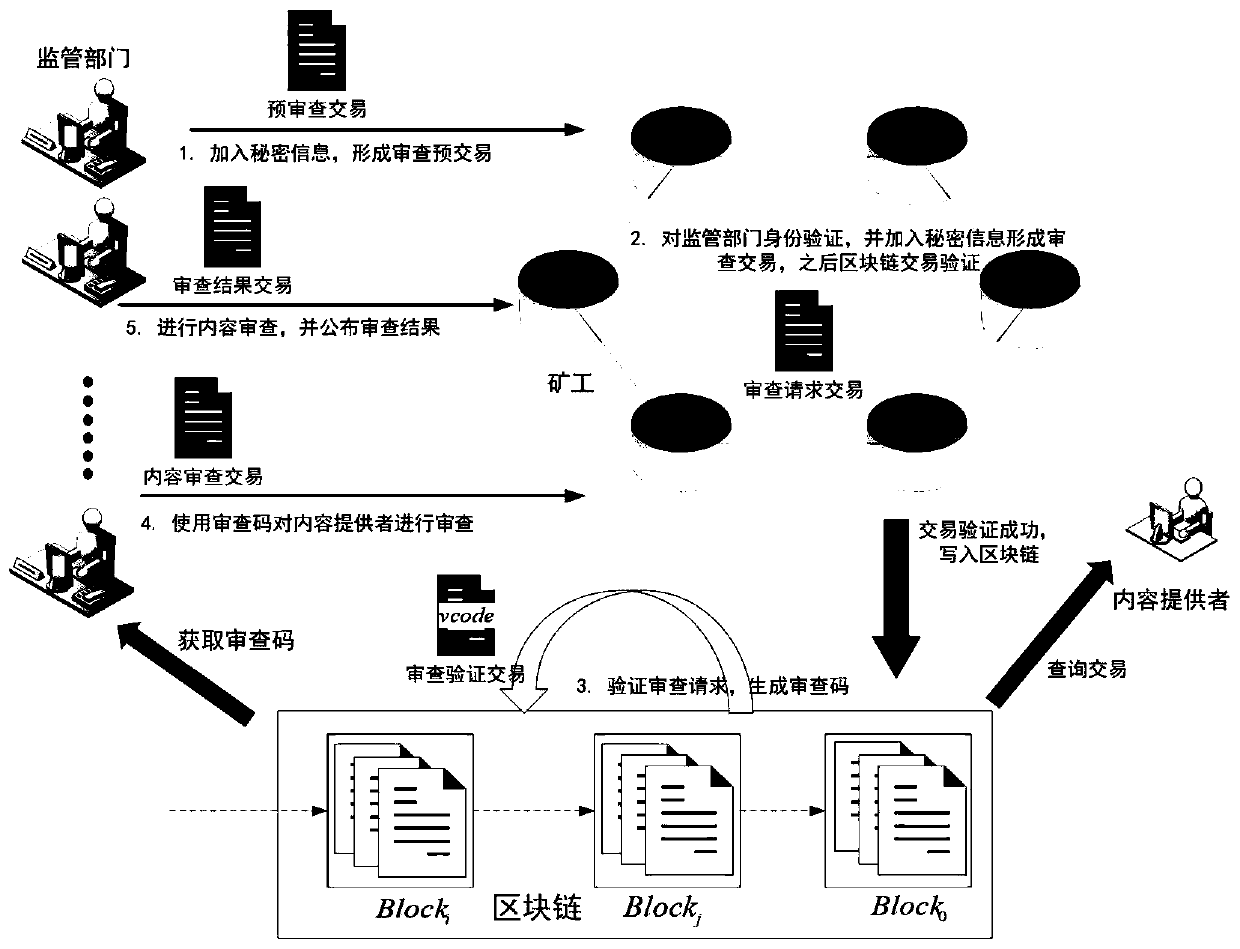
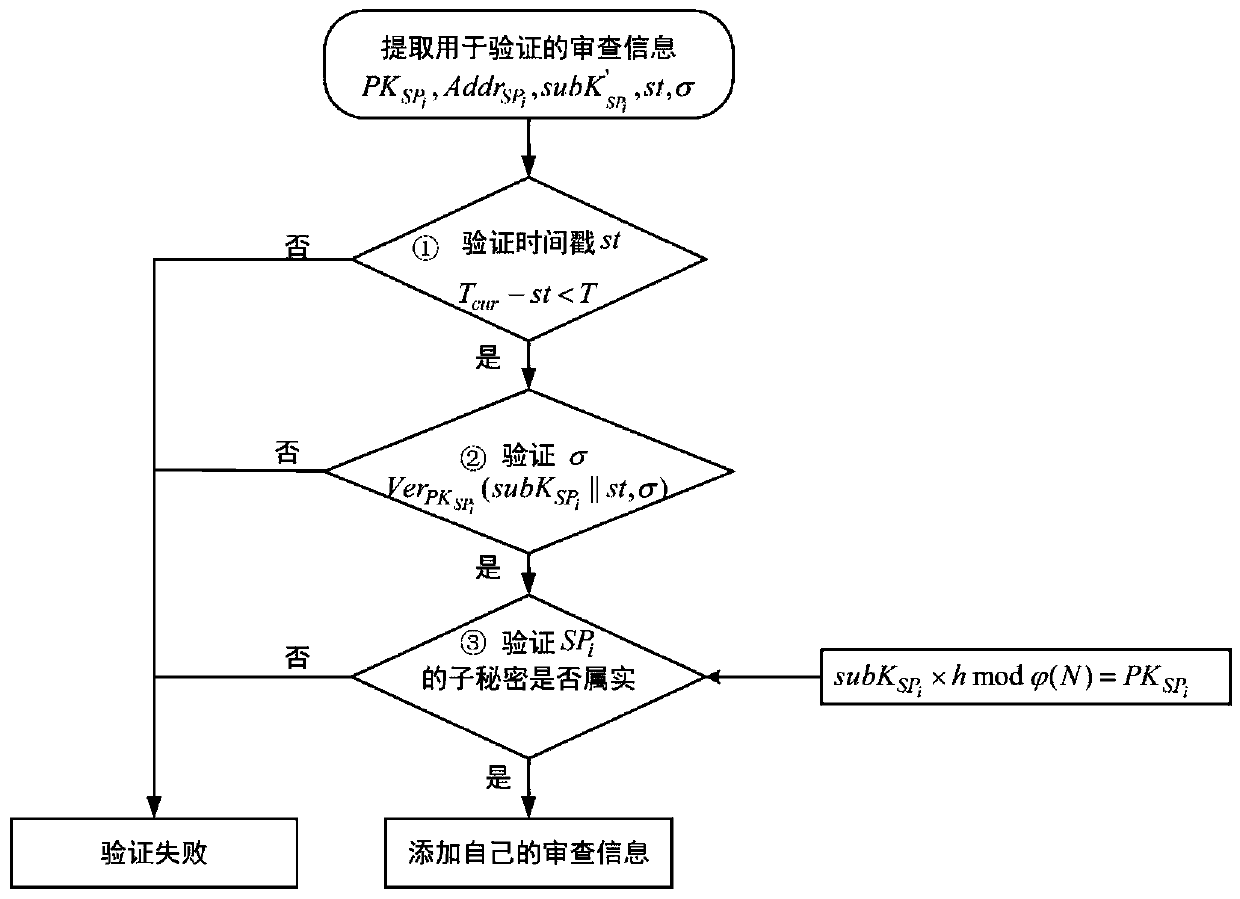
Shared content supervision method based on threshold key sharing and block chain
ActiveCN110289951AAvoid collusionGuaranteed to be openKey distribution for secure communicationKey distributionContent sharing
The invention discloses a shared content supervision method based on threshold key sharing and a block chain. The entity involved in the invention comprises a supervision department, a content provider, a block chain and a miner. The method specifically comprises the following steps: step 1, content permission snapshot; step 2, secret key distribution and recovery based on Shamir (t, n); step 3, content review based on transactions. according to the method and the system, the Shamir (t, n) threshold secret sharing is utilized, so that multiple parties can participate in content review together, the accuracy and fairness of content review executed by a supervision department are ensured, and collusion in the supervision department is effectively prevented. Besides, the whole review process is carried out in a block chain transaction mode, so that the defect of content supervision in a content sharing scheme based on a block chain at present is overcome, absolute disclosure and accuracy of the review records are ensured, and the public can conveniently audit and check the review records.
Owner:HANGZHOU DIANZI UNIV
Apparatus and methods for reducing contaminants in water systems using information distribution
InactiveUS20050015269A1Reducing water runoff pollutionReduce pollutionClimate change adaptationSedimentation separationDemographic dataComputerized system
The present invention relates to apparatus and methods for reducing water runoff pollution. An apparatus for distributing pollution related information, comprises a demographic data store, a television ratings data store, a governmental mandate data store, broadcast media related to the pollution abatement program, wherein the viewing of the broadcast media is used to meet at least a first pollution abatement program mandate and a computer system coupled to the demographic data store, the television ratings data store, governmental mandate data store, wherein the computer system is configured to identify a local government body that is to adhere to a water runoff pollution abatement program and to identify at least a first show as a potential candidate with which the broadcast media related to the pollution abatement program is to be televised in conjunction with.
Owner:ADOPT A WATERWAY
System and method for defending against mobile storage medium virus in island-like Ethernet
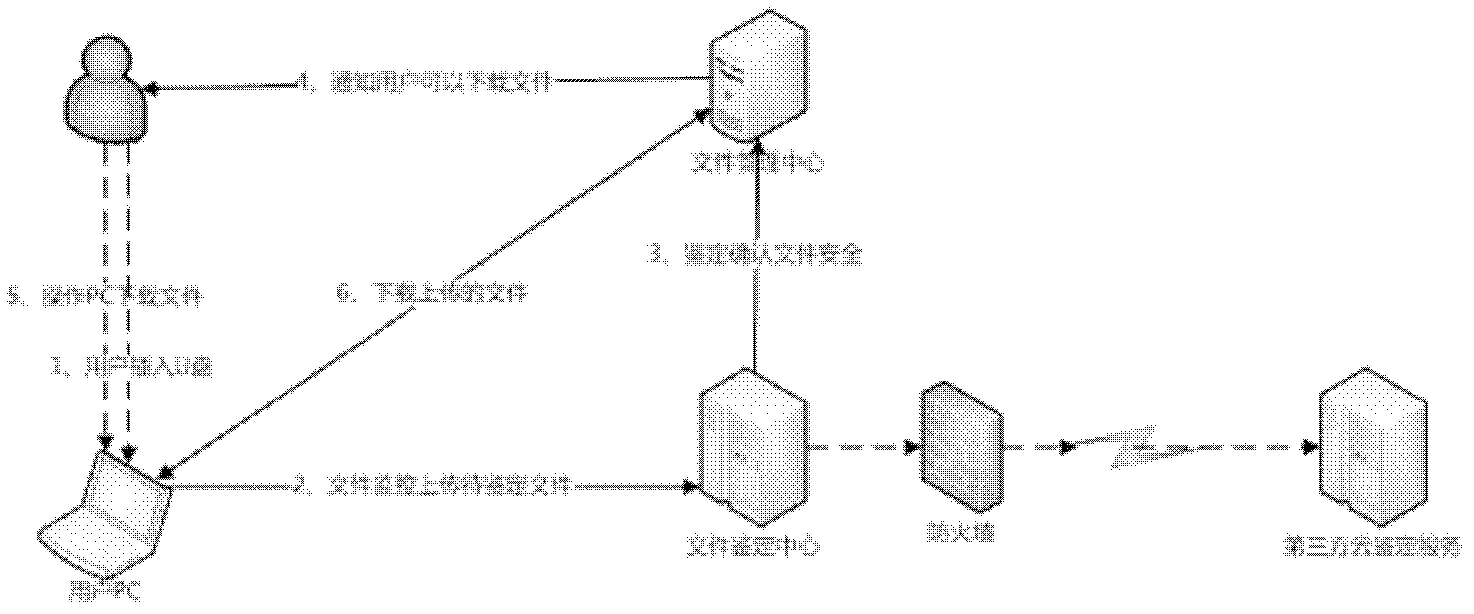
ActiveCN103001937AWithout compromising securityPerformance is not affectedTransmissionRemovable mediaClient-side
The invention provides a system and a method for defending against mobile storage medium virus in island-like Ethernet which comprises a client side and a server. When a user inserts a mobile storage media, the client side monitors read-write operations on the mobile storage media of each process, prevents other processes outside the monitoring processes from reading data, sends prompt messages to prompt users to upload files in the mobile storage media to the server, and prevents the files from being accessed when users refuse to upload the files. The server records information of users uploading files and determines safety of the received files. Files being successfully indentified are sent back to users. The system and the method are capable of improving the effectiveness and practicality of defending mobile storage medium virus with no cost increased.
Owner:ZHUHAI BAOQU TECH CO LTD +1
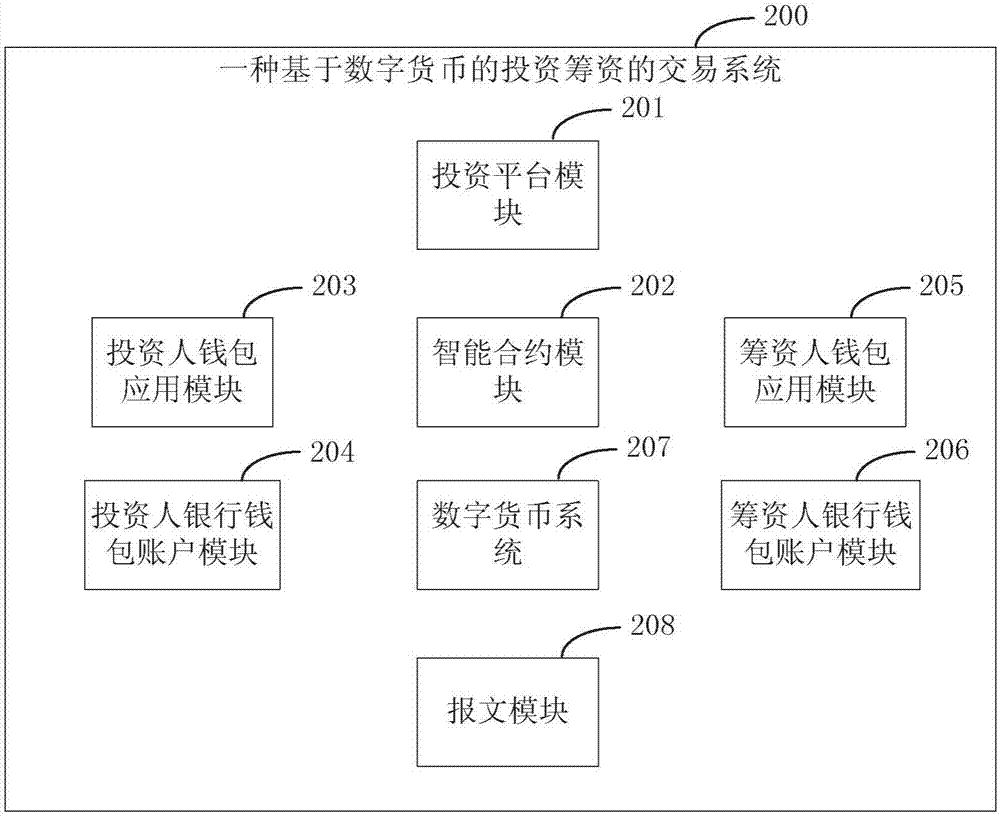
Digital currency-based investment financing transaction method, system and device
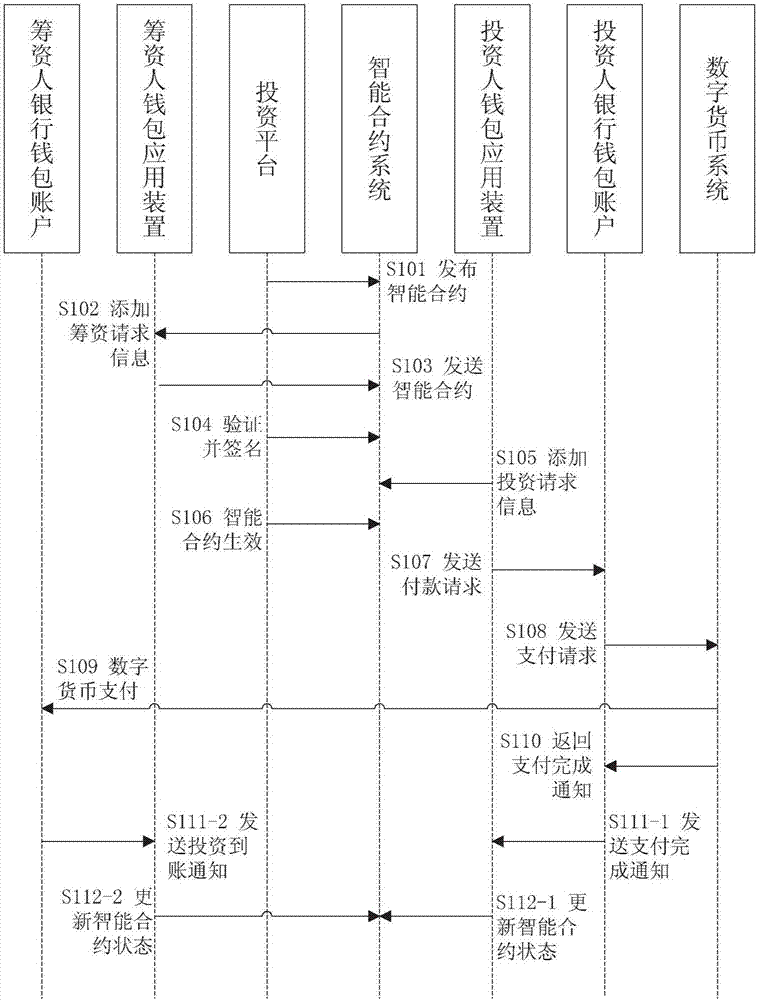
ActiveCN107330789ADirect transferSolve the risk of deposit fundsFinanceDigital currencyDigital signature
The present invention provides a digital currency-based investment financing transaction method, system and device which realizes the situation of utilizing the digital currencies to provide a payment settlement path of investment financing capital allocation for a platform. The method comprises the steps of using an investor wallet application device to receive an intelligent contract; after the investor wallet application device receives a confirmation instruction containing the investment amount provided by an investor, adding the investment confirmation information in the intelligent contract, wherein the information comprises the investment amount, an investor signature and the investor personal information; after an investment platform verifies the investment confirmation information in the intelligent contract, marking that the intelligent contract comes into force; using the investor wallet application device to pay the digital currencies to a fund-raiser bank wallet account according to the executed intelligent contract.
Owner:THE PEOPLES BANK OF CHINA DIGITAL CURRENCY INST
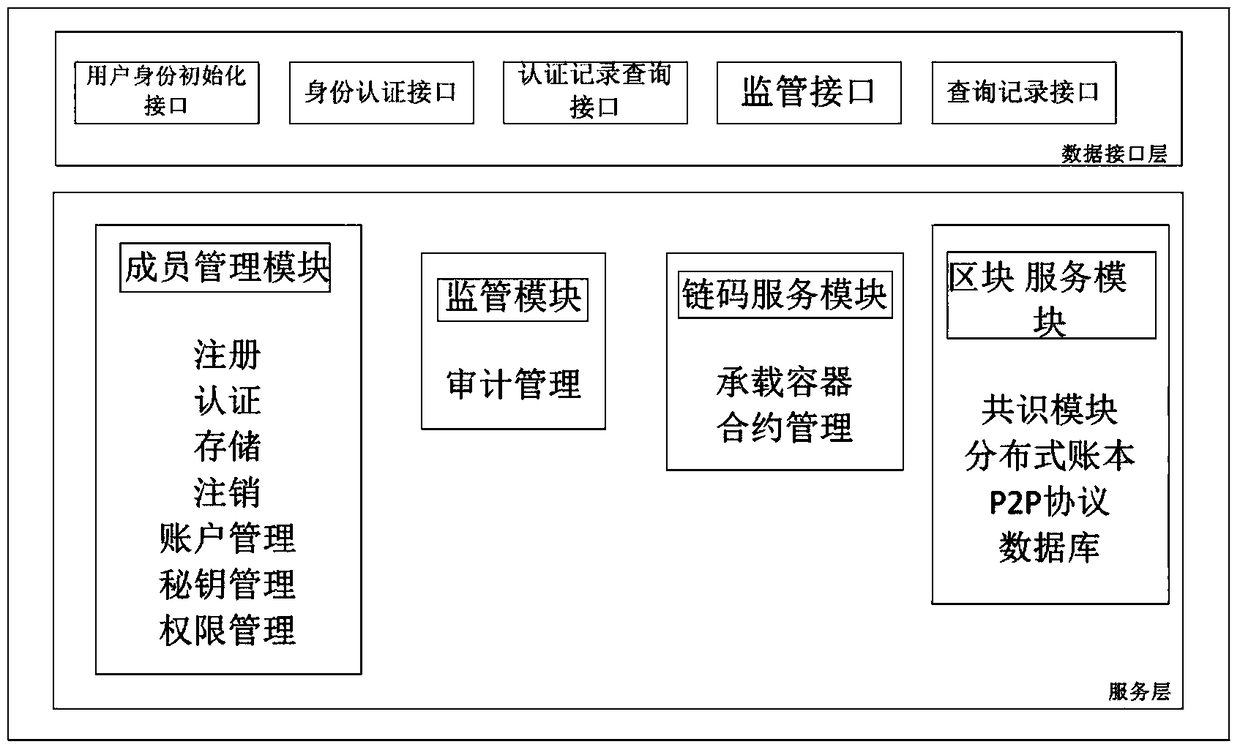
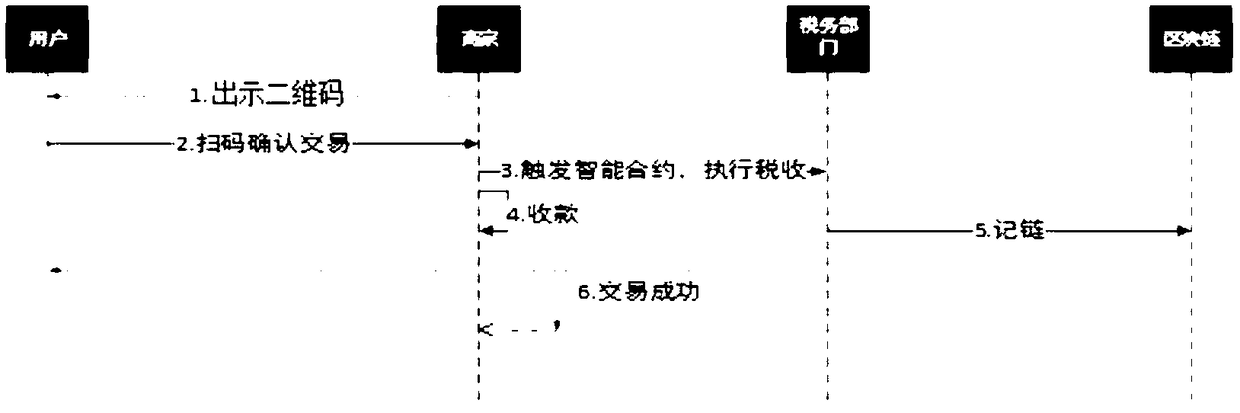
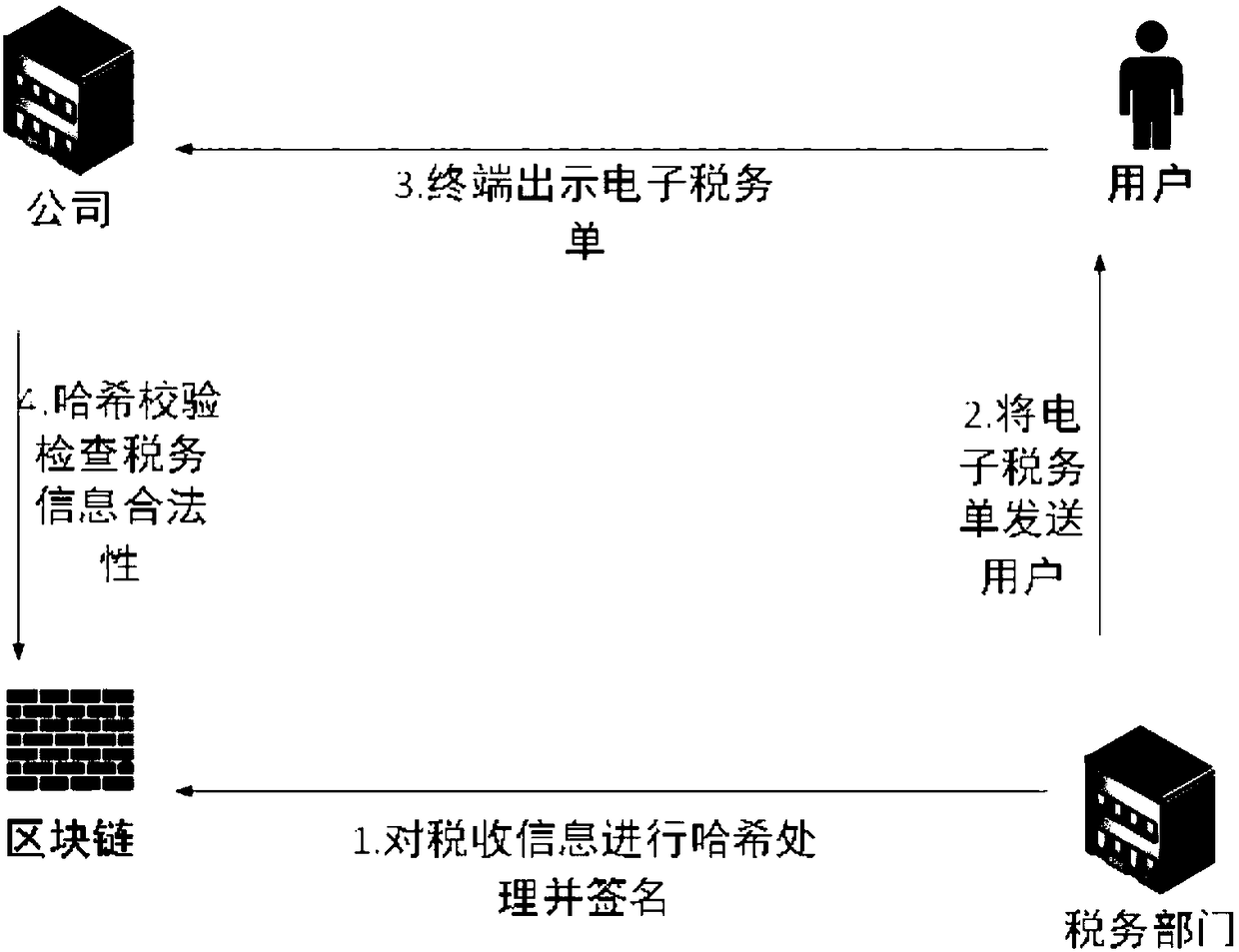
Blockchain-based tax method and architecture
InactiveCN108717659AImprove securityPromote fairness and justiceFinanceDigital data protectionInformation sharingData interface
The invention provides blockchain-based tax architecture. The blockchain-based tax architecture comprises a service layer and a data interface layer; the service layer is connected with the data interface layer; the service layer triggers the interior of the service layer to work cooperatively through an event flow, so that a blockchain service is provided; a block service module and a chain codeservice module are also arranged in the service layer; the block service module is used for storing signed data subjected to hash processing; and a tax rule is stored in the chain code service module.According to the blockchain-based tax method and architecture provided by the invention, trusted information is shared; a database is managed and maintained by multiple parties together through decentralized architecture; any one party cannot completely operate data; a blockchain cannot be tampered by depending on the hash pointer of each block head and the Merkle tree of a block; the data security is reinforced through a consensus mechanism; and thus, justice and equity are promoted.
Owner:CETC BIGDATA RES INST CO LTD
Segmentation method for trust domain of virtual machine monitor
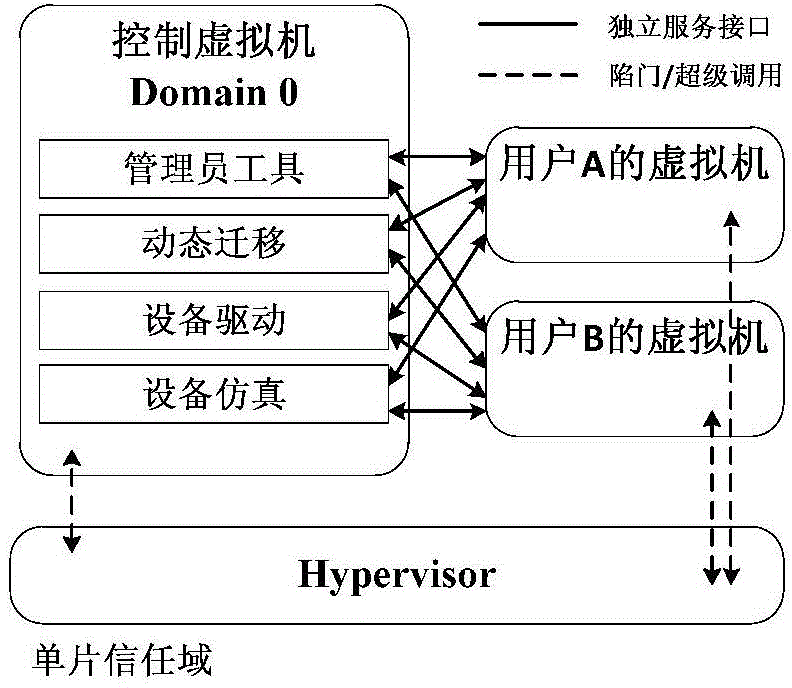
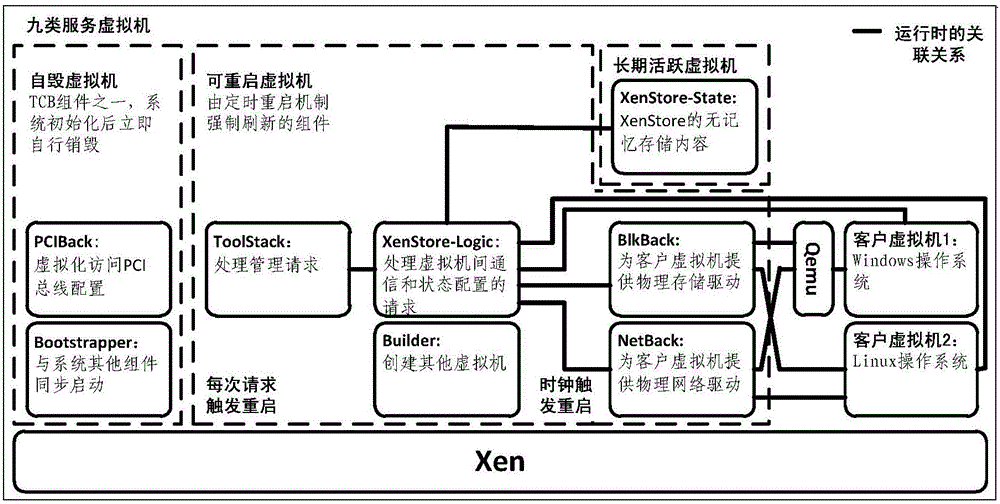
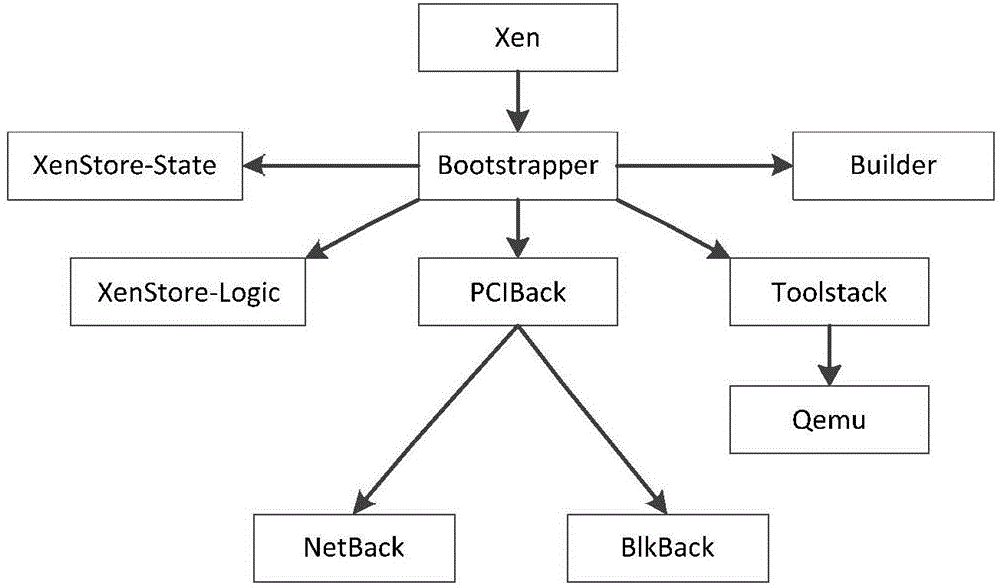
ActiveCN104598842AReduce the Trusted Computing BaseReduce attack surfaceInternal/peripheral component protectionPlatform integrity maintainanceSingle useVirtual machine
The invention discloses a segmentation method for a trust domain of a virtual machine monitor. The original control virtual machine is divided into nine service virtual machines according to different previous functions; each service virtual machine comprises a single-use control logic, and the control logic is deleted from the original control virtual machine. Each service virtual machine only has the authority of finishing the function per se, and each component is limited to access to Hypervisor with the required minimum authority, so the risk is clear. The method has the positive effects that vulnerability location can be effectively performed after attack accidents occur so as to perform remediation, the problem that the control power of the whole system can be obtained by breaking one component originally is solved, and the safety of the virtual machine is improved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
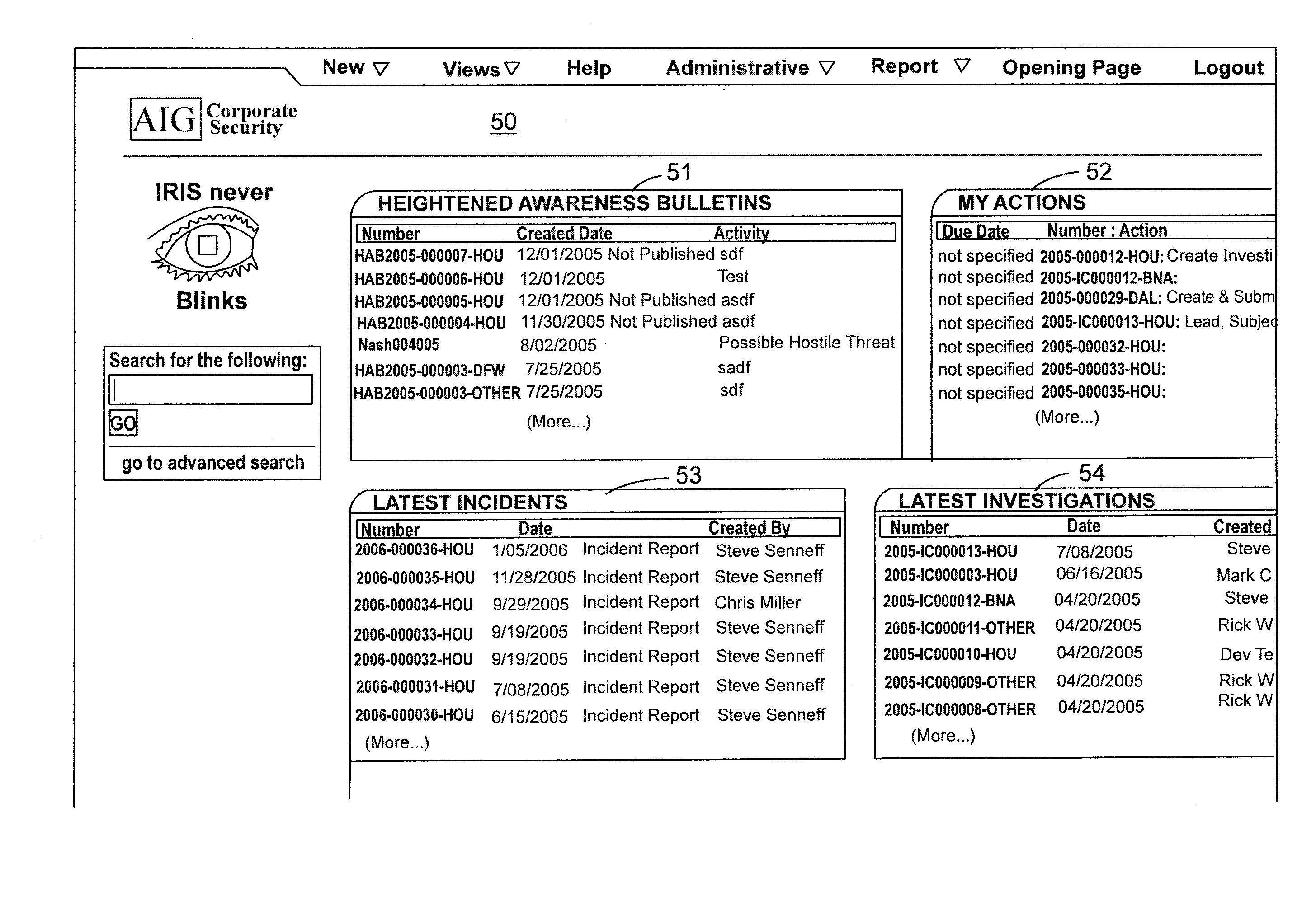
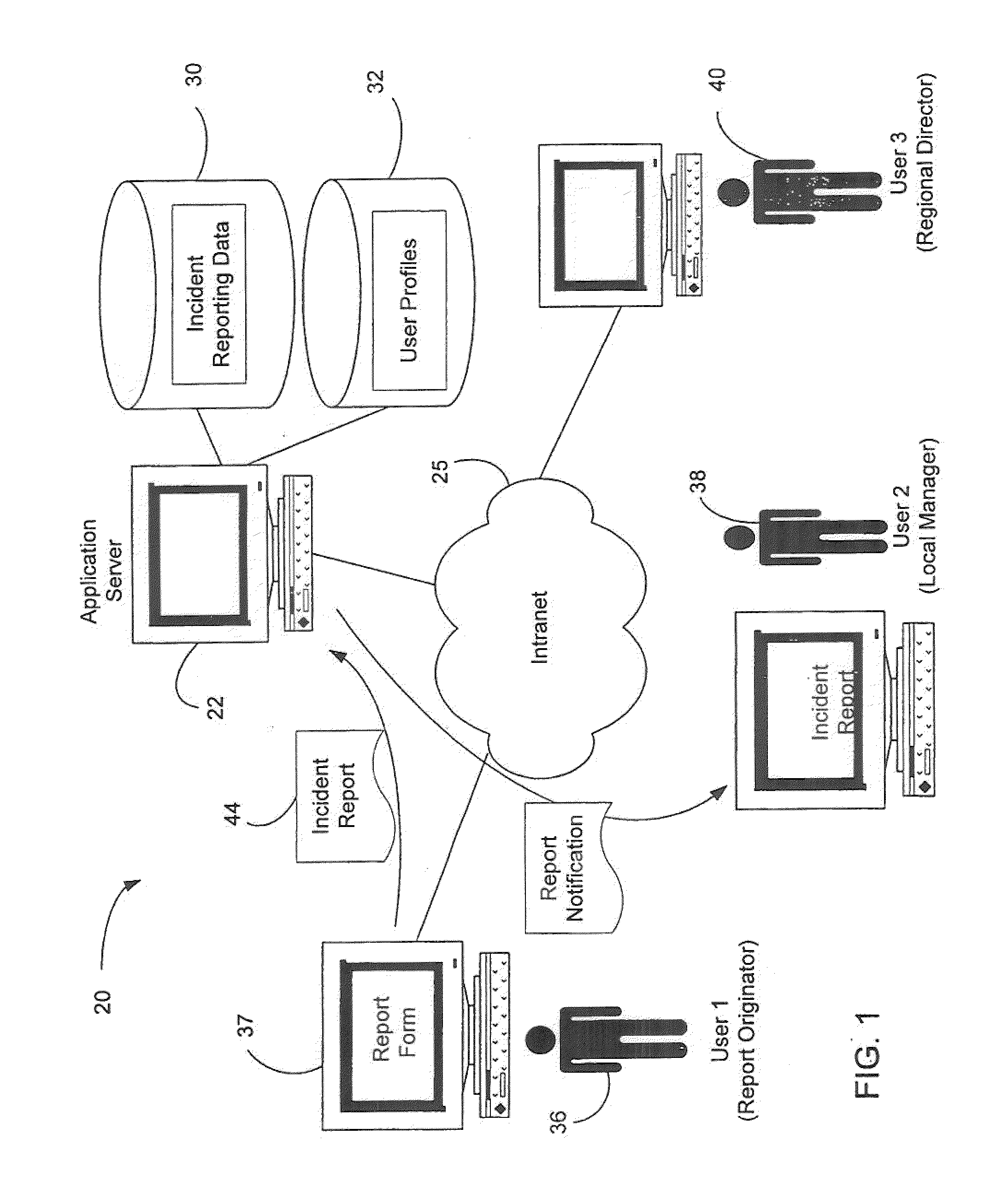
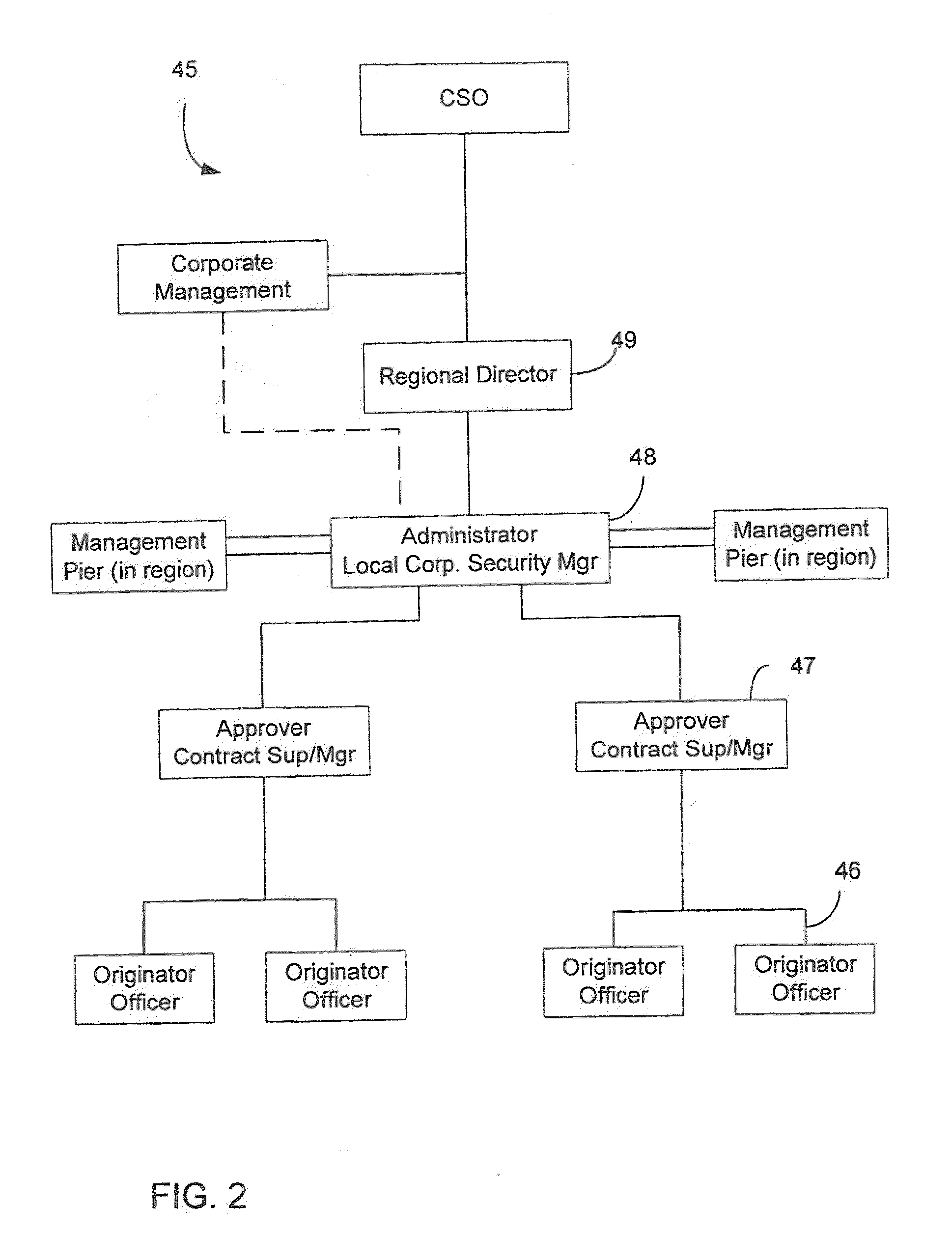
System and method for incident reporting
InactiveUS20110016377A1Easy to manageSecure yet flexible controlDigital computer detailsOffice automationApplication serverIncident report
Owner:AMERICAL INTERNATIONAL GROUP INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com