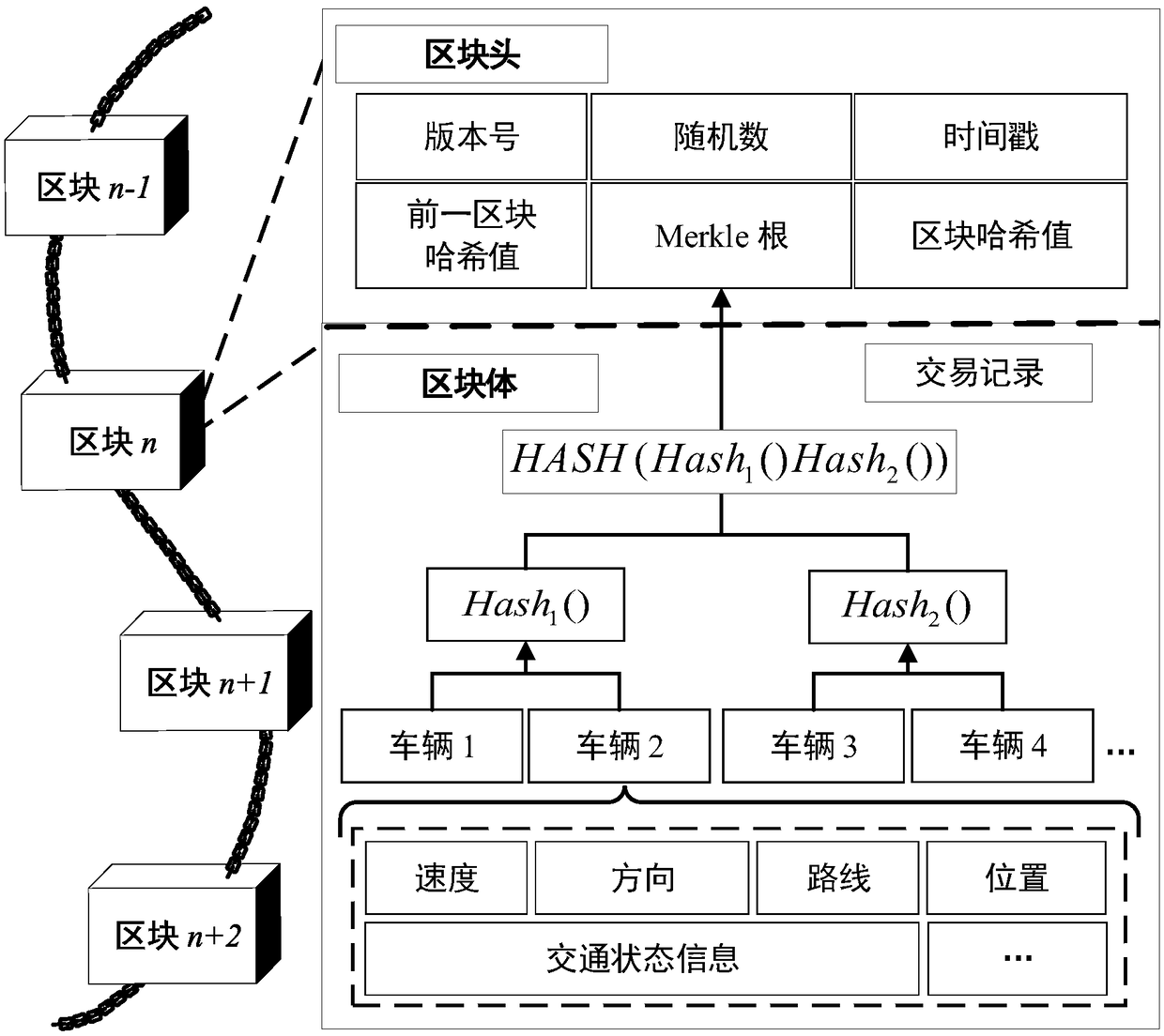
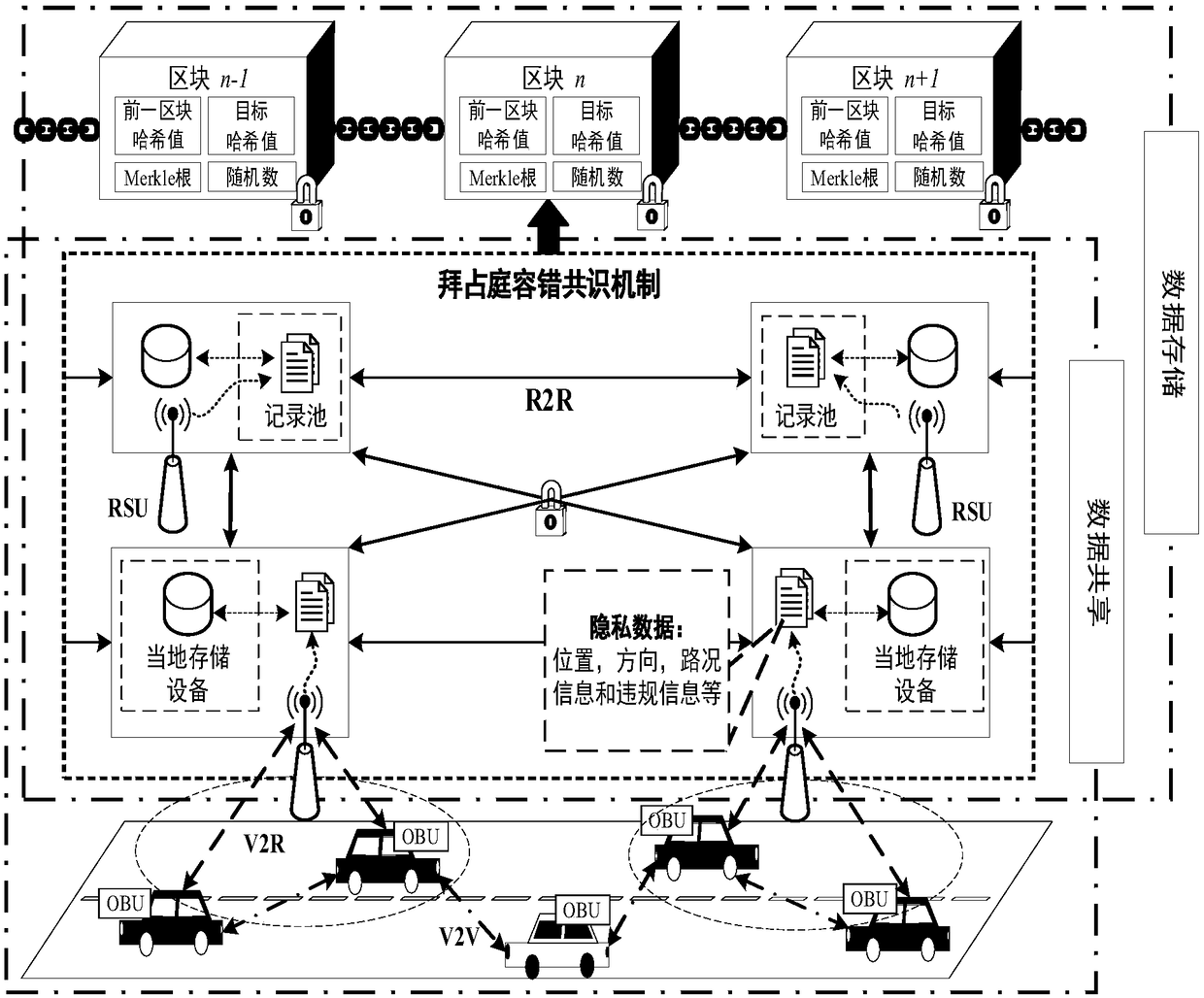
Patents
Literature
71results about How to "Guaranteed tamper resistance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
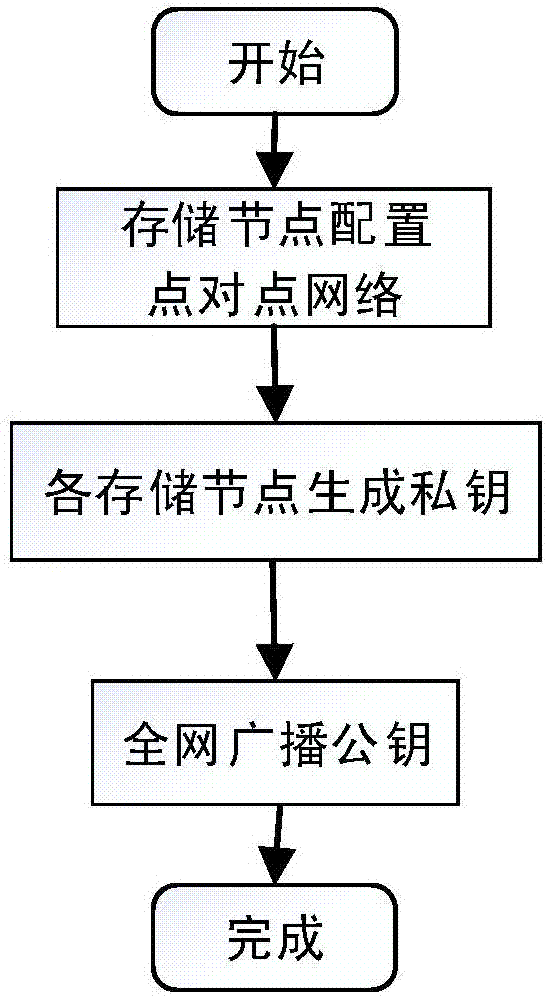
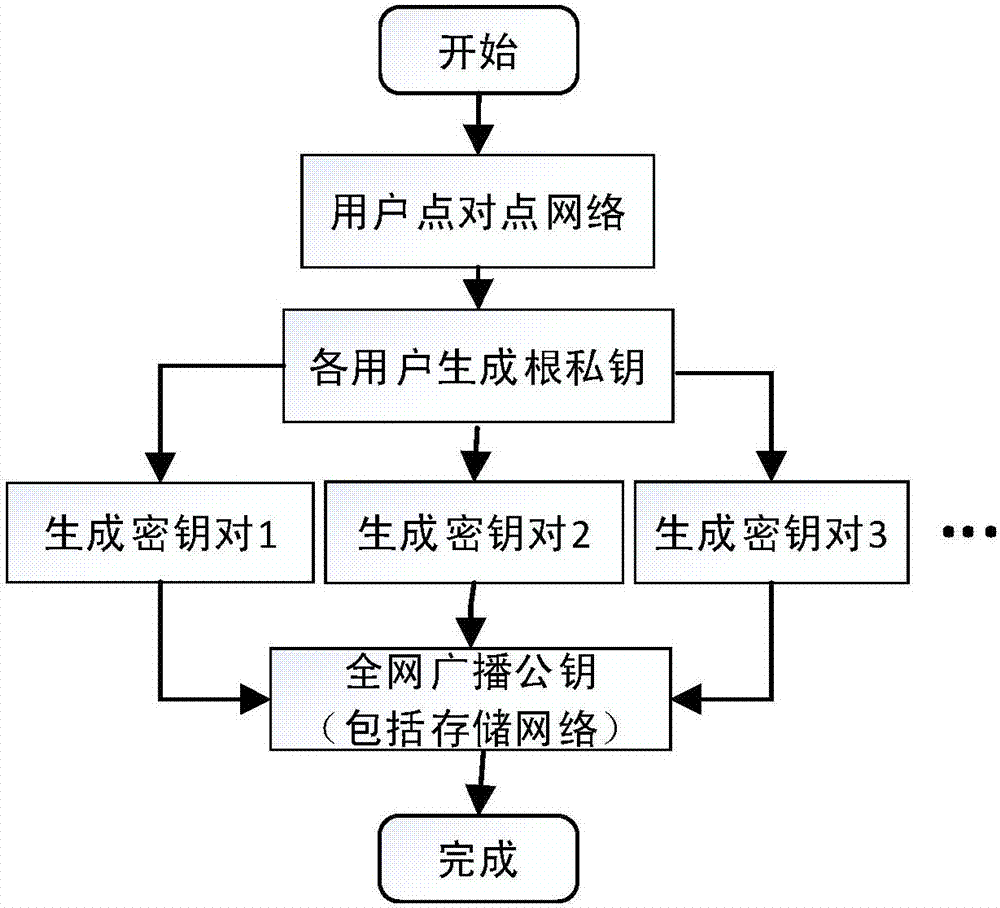
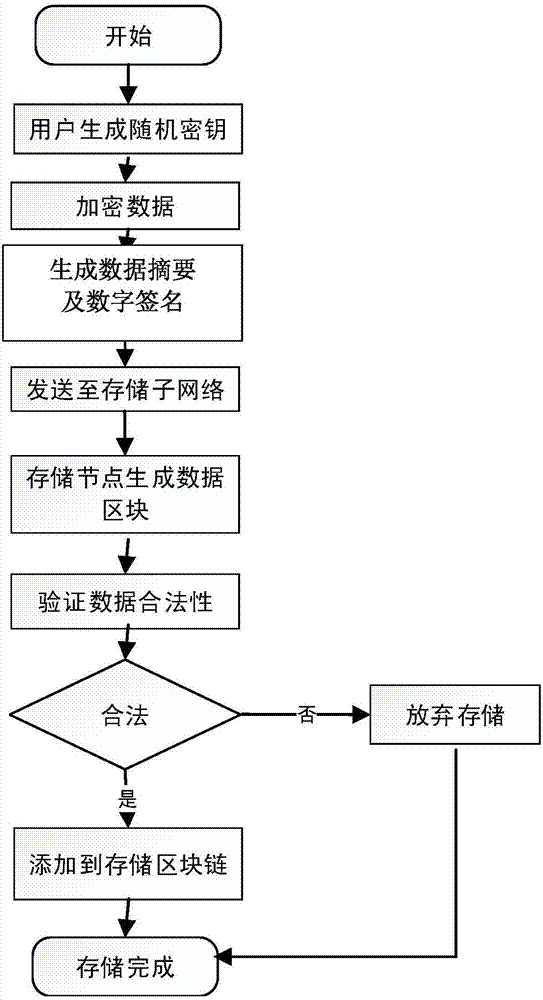
Routing position data secrecy storing and sharing method based on block chain
ActiveCN107181599AGood data protectionSolve workload bottlenecksKey distribution for secure communicationUser identity/authority verificationByzantine fault toleranceOriginal data
Provided is a routing position data secrecy storing and sharing method based on block chains. The routing position data secrecy storing and sharing method includes a data storing method and a data sharing method. The data storing method includes the steps of node configuration, data encryption sending, storage subnetwork verification storing, etc. The data sharing method includes the steps of demand generation, demand response, sharing achievement and the like. The effects of the invention are as follows: through a block chain technology, data sharing is realized through data encryption storage and a decentralized network to solve the problems that data storage parties have no right to use data and users do not have channels to selectively enable personal data to be accessed; local encryption sending is adopted during data storage, service parties store encrypted data, the users themselves save decryption secret keys, and the service parties have no access to original data, so a better data protection effect is achieved; and the block chain technology is adopted during storage, commonly recognized storage is realized through a practical Byzantine fault-tolerant algorithm, workload bottleneck problems of centralized storage are solved, and data is prevented from being tampered.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
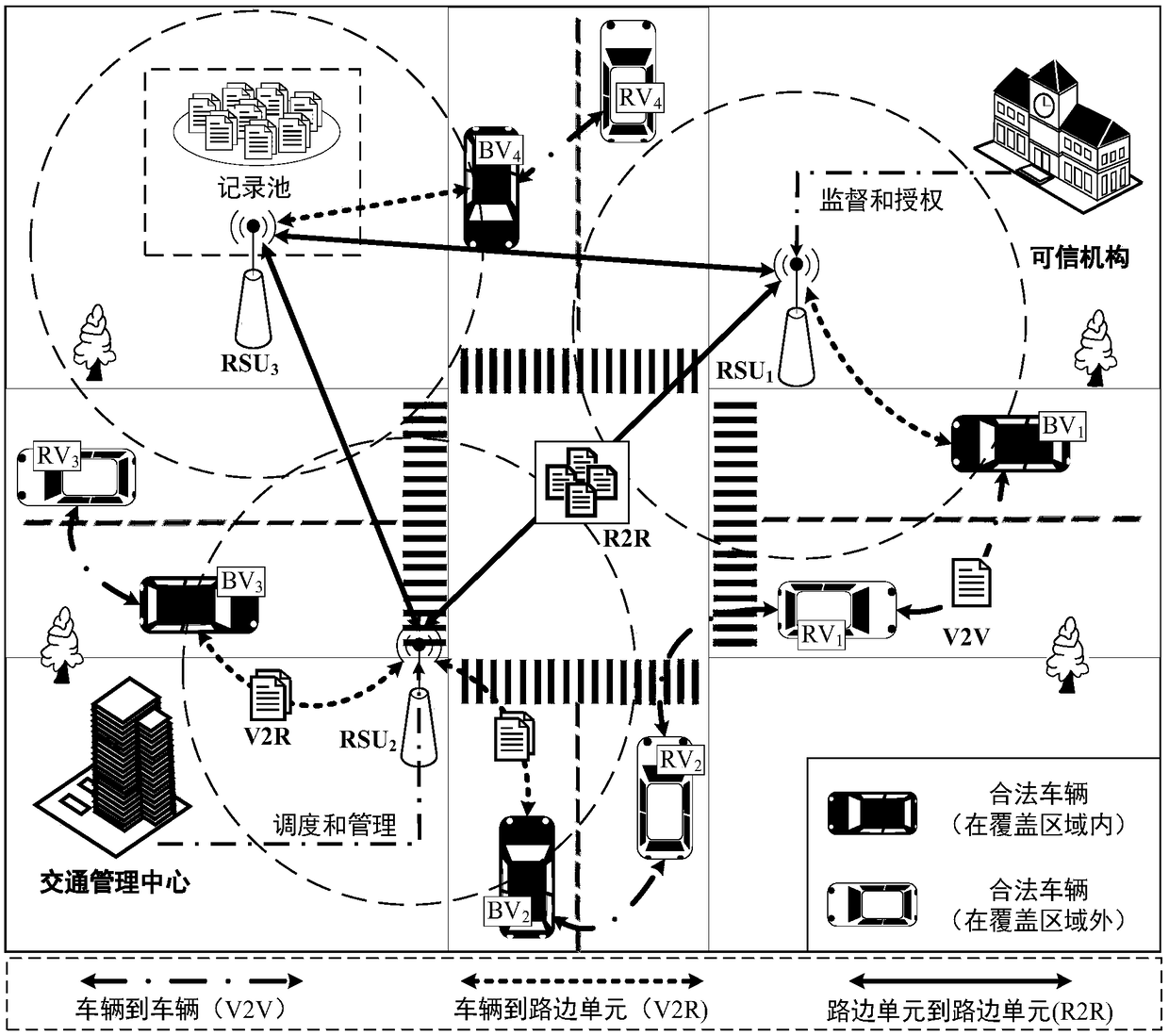
Vehicular ad-hoc network data security sharing and storage system based on blockchain technology
ActiveCN109451467AImprove efficiencyPrevent leakageParticular environment based servicesUser identity/authority verificationByzantine fault toleranceDigital signature
The invention discloses a vehicular ad-hoc network data security sharing and storage system based on a blockchain technology. The vehicular ad-hoc network data security sharing and storage system based on the blockchain technology comprises a vehicle, a roadside unit, and a trusted institution. When data shared by the roadside unit, the vehicle performs digital signature on interactive informationby using a bilinear algorithm based on an elliptic curve to ensure the non-repudiation and integrity of the data; the roadside unit packs the collected data into a block, and uses the Byzantine fault-tolerant consensus mechanism to make the data block reach a coherent protocol across the network, thereby improving the fault tolerance of the system and making system more stable; after reaching theconsensus, the block is sorted by a smart contract in the roadside unit and stored in the blockchain, and other consensus nodes save the data synchronously; and the system rewards a corresponding number of data coins to the roadside unit, and then the data coins are assigned to the vehicle contributing the data by the smart contract, so as to keep the entire system active and stable.
Owner:JIANGXI UNIV OF SCI & TECH
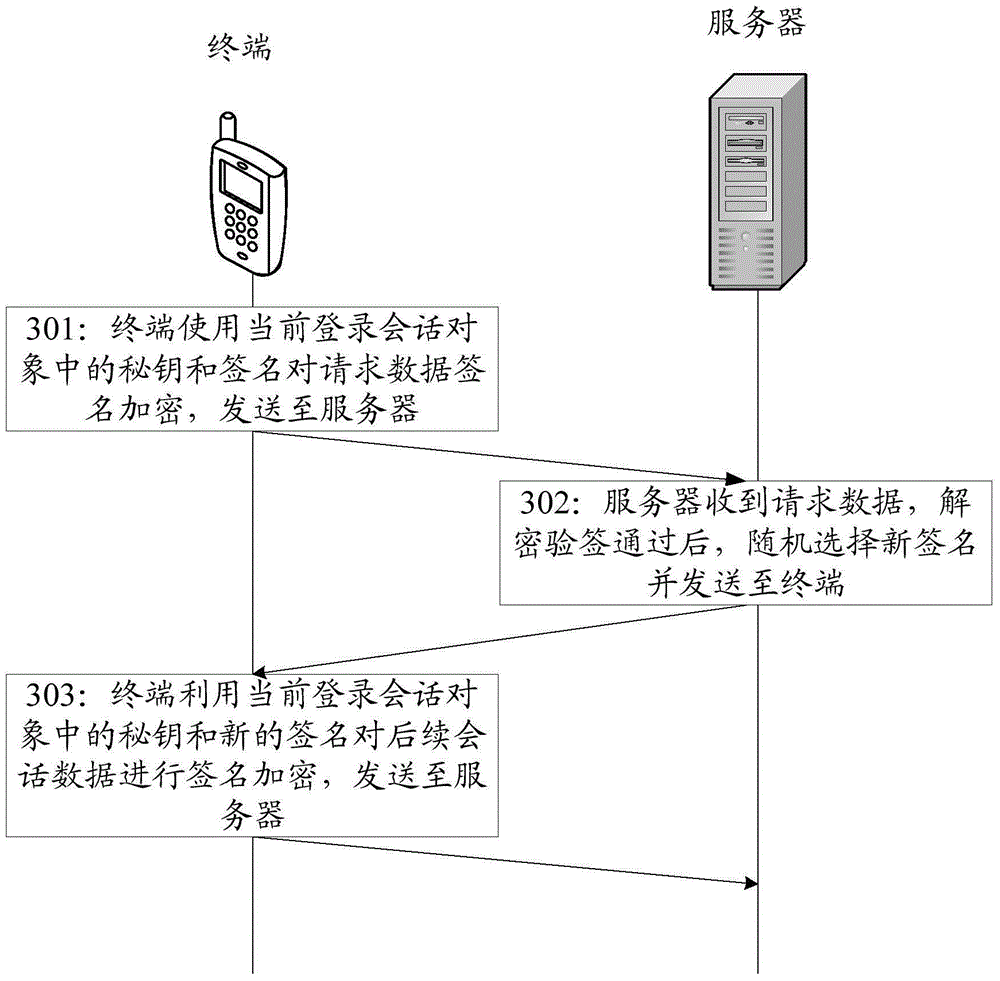
Dynamic encryption method, terminal and server
ActiveCN106559217AImprove securityAvoid the risk of being crackedMultiple keys/algorithms usageUser identity/authority verificationComputer terminalEncryption
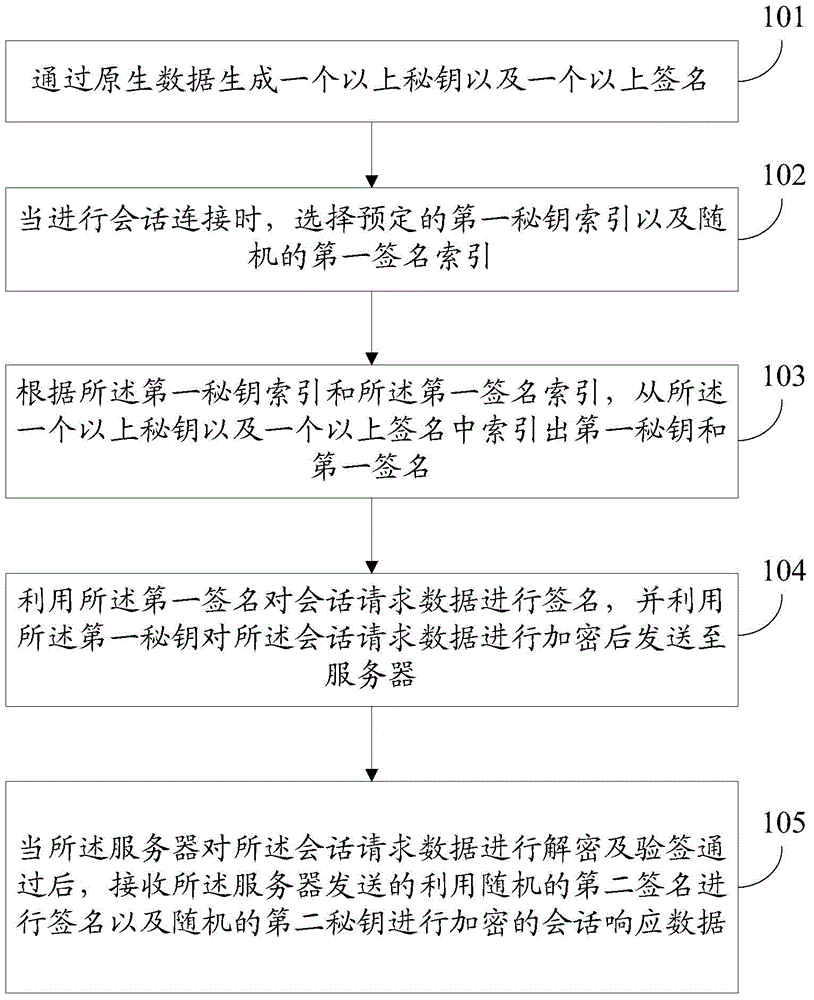
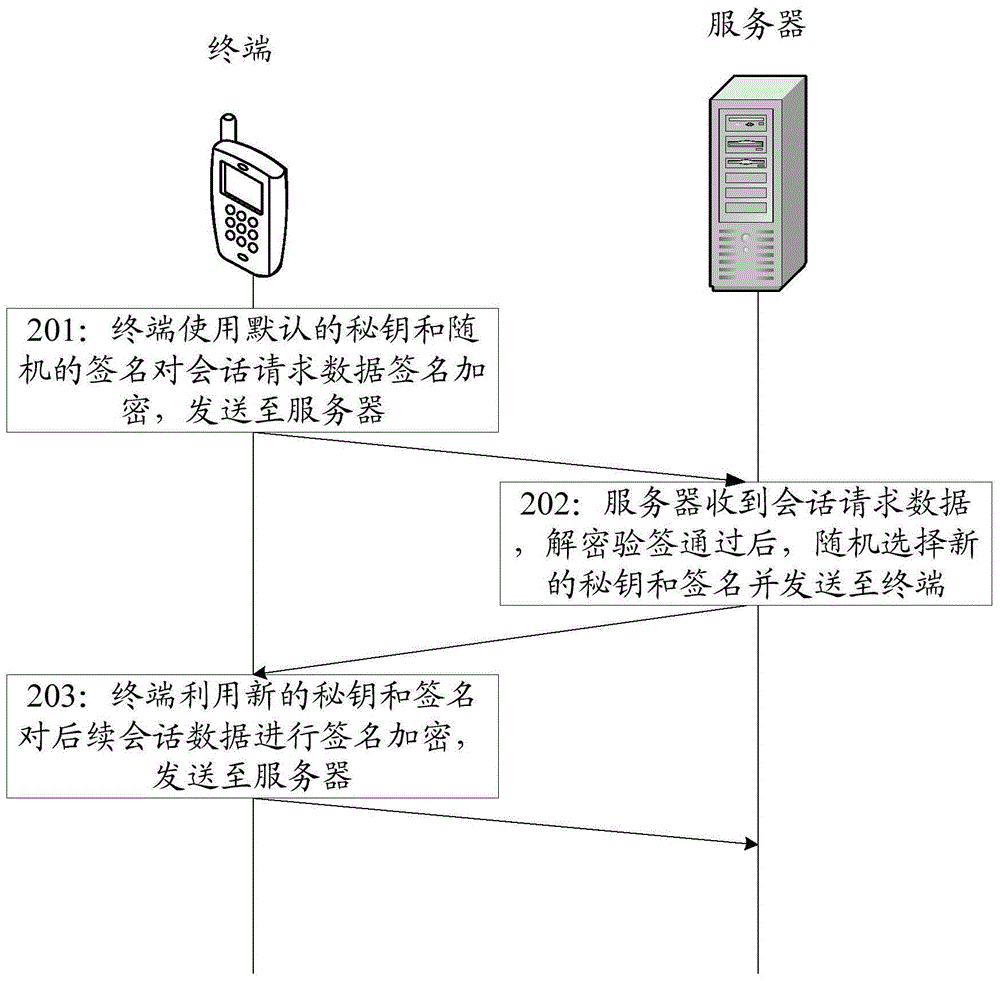
The present invention discloses a dynamic encryption method, a terminal and a server. The method comprises: generating more than one secret keys and more than one signatures through native data; when the session connection is performed, selecting a predetermined first secret key index and random first signature index; according to the first secret key index and random first signature index, indexing a first secret key and a first signature from the more than one secret keys and the more than one signatures; employing the first signature to perform signature of the session request data, and employing the first secret key to perform encryption of the session request data and then send the encrypted session request data to a server; and after the server performs decryption of the session request data and the signature checking passes, receiving the session response data which employs random second signature to perform signature and employs random second secret key to perform encryption.
Owner:TENCENT TECH (SHENZHEN) CO LTD
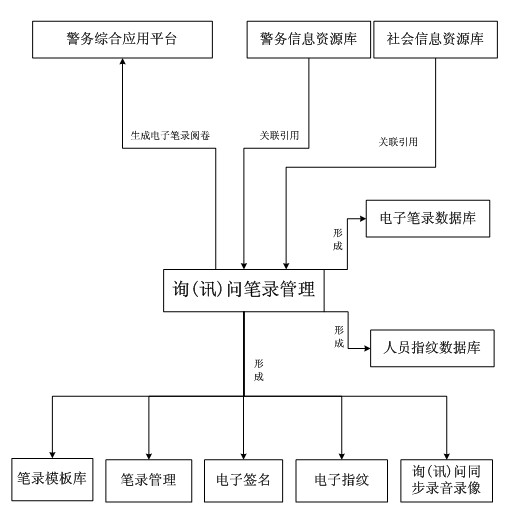
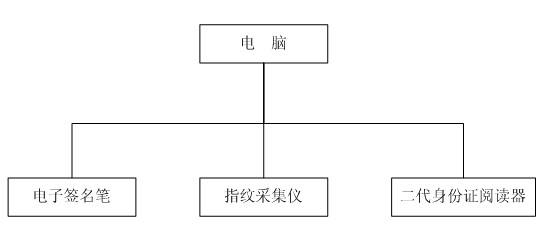
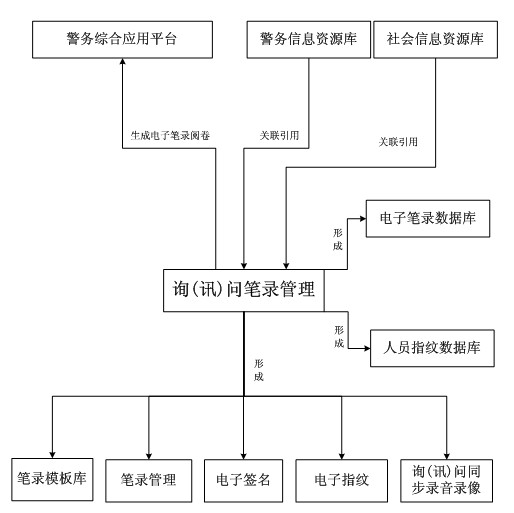
Integrated electronic record, signature and fingerprint system
InactiveCN102208060AEnsure anti-counterfeitingGuaranteed tamper resistanceData processing applicationsInformation resourceExtensible markup
The invention relates to an integrated electronic record, signature and fingerprint system. The system comprises: (1) a police information resource database and a social information resource database for forming a sharable information resource database in a police intranet; (2) a comprehensive application platform based on police information; (3) an electronic fingerprint database constructed according to the requirement of standard fingerprint information collection of the ministry of public security and capable of being applied for special subjects; (4) a full text retrieval system; (5) a hybrid architecture using a C / S structure system, or a B / S structure or the combination of the C / S and B / S structure systems; (6) a unit adopting an MD5 algorithm for digital signature so as to ensure not to modify a generated record file, and a unit adopting Blowfish encryption algorithm for preventing leakage of the record data; and (7) a unit with integrated XML (extensible markup language) and WebService. The electronic record can greatly lower the case handling cost, improves the case handling efficiency, and can expand the information sources.
Owner:昆明市公安局
Data right confirmation method and system based on block chain technology
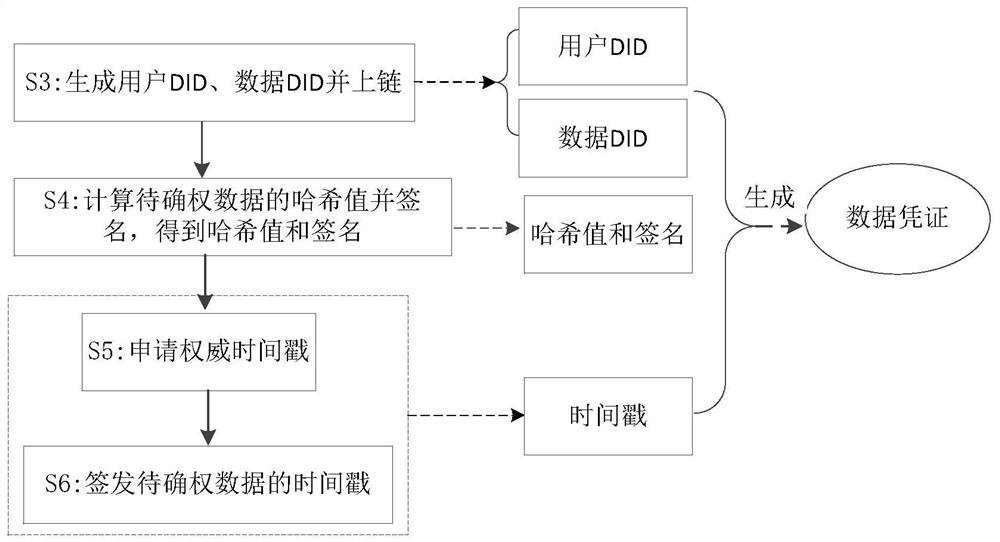
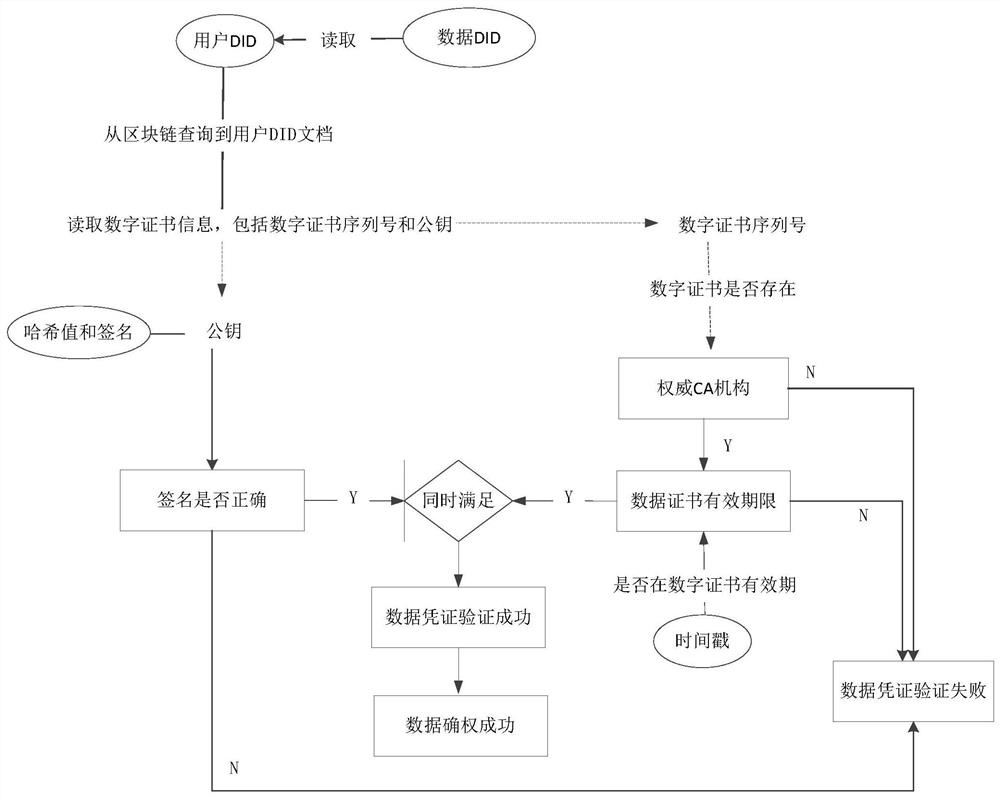
PendingCN112651052AGuarantee authorityGuaranteed credibilityDigital data protectionDigital identityTamper resistance
The invention discloses a data right confirmation method and system based on a block chain technology. The method comprises the following steps: initializing and verifying a digital certificate; generating a user DID and a data DID and uploading the user DID and the data DID; calculating a hash value of the data to be subjected to right confirmation and signing to obtain the hash value and a signature; applying an authoritative timestamp according to the hash value of the to-be-confirmed data; generating a data certificate of the to-be-confirmed data according to the uplink user DID, the data DID, the timestamp, the hash value and the signature, verifying the data certificate, calculating the hash value of the data certificate, and signing the hash value of the data certificate to obtain a signature certificate; and uploading the verified data voucher and signature voucher to obtain right confirmation record uplink hash and returning the right confirmation record uplink hash to the client. According to the invention, the decentralized digital identity DID is adopted, and the data right confirmation information of the to-be-confirmed right data is stored in the block chain in the form of the verifiable certificate, so that the right confirmation function of the to-be-confirmed right data is realized, and the characteristics of verifiability, traceability, tamper resistance and the like of the data right confirmation information are ensured.
Owner:JIANGSU PAYEGIS TECH CO LTD +1
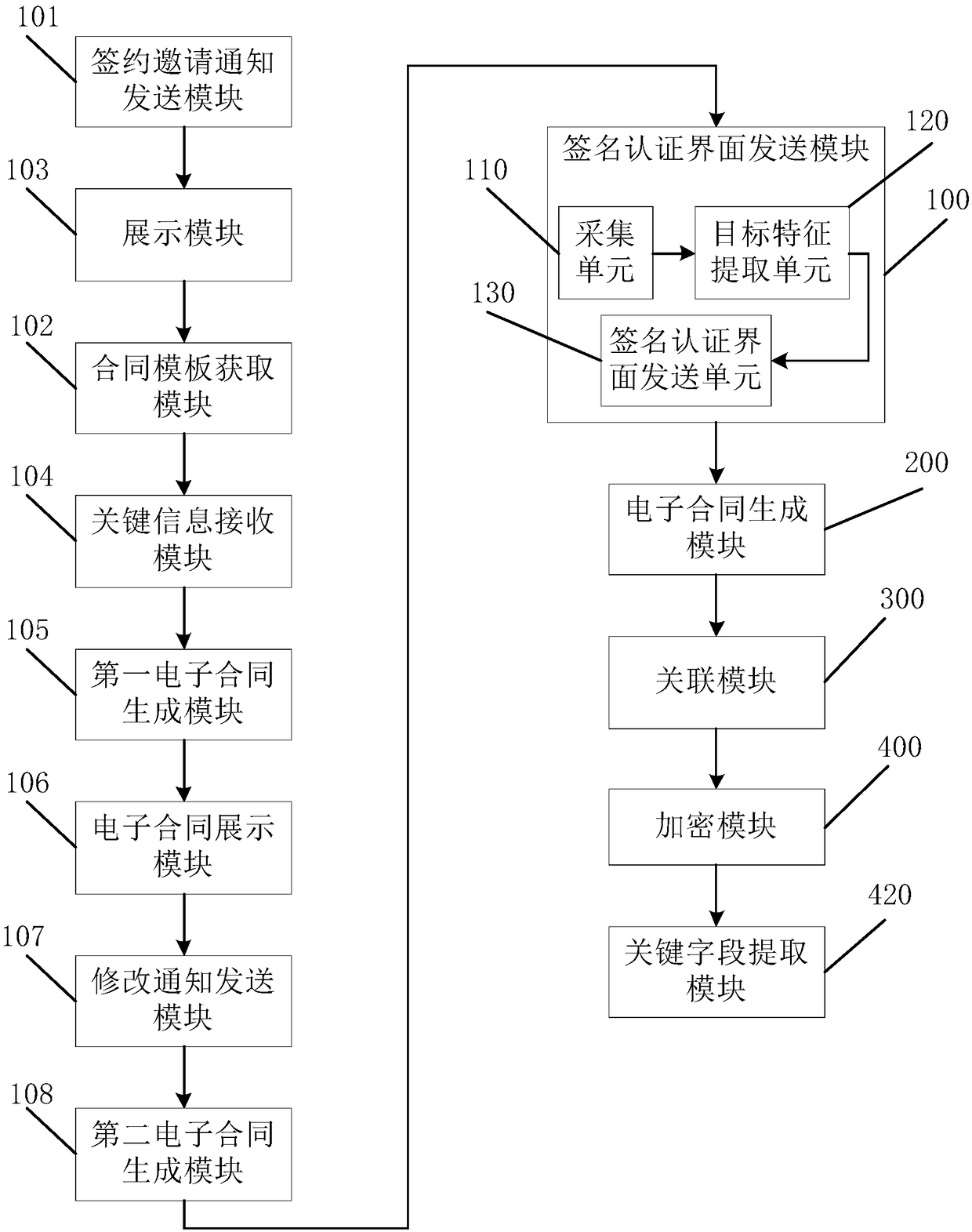
Electronic contract signing method, device and server
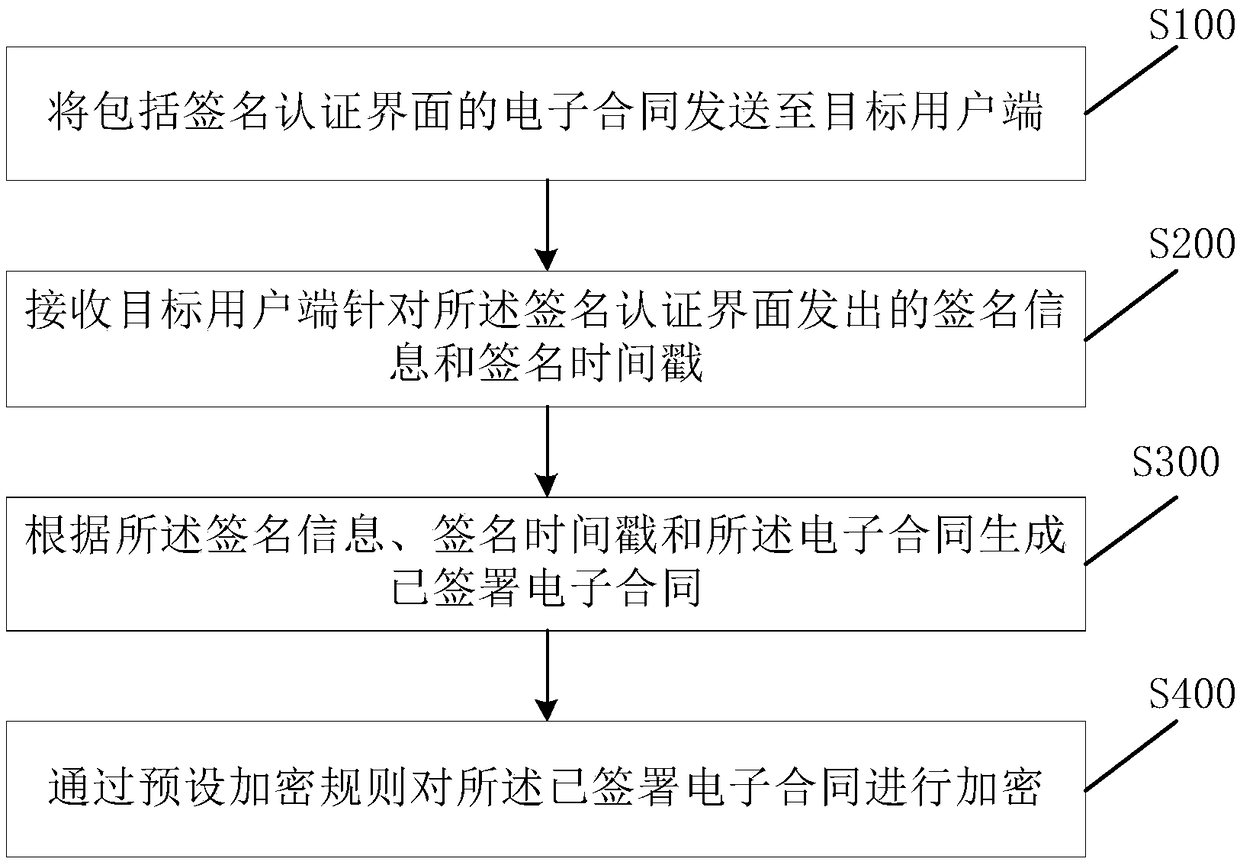
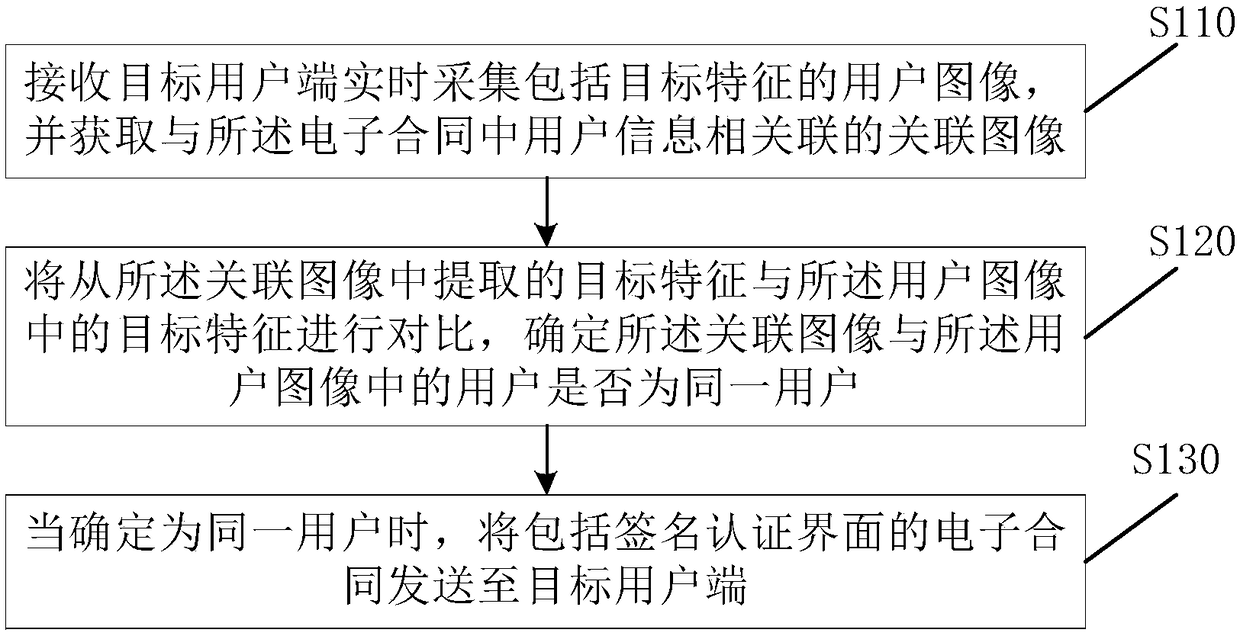
PendingCN109087056AGuaranteed tamper resistanceGuarantee the legal validity of online contractsUser identity/authority verificationOffice automationElectronic contractsEncryption
An electronic contract signing method provided in an embodiment of the present invention includes the steps of: sending the electronic contract including a signature authentication interface to a userin response to a user instruction; receiving a signature of a user on the signature authentication interface, and generating the signature into the electronic contract; acquiring a timestamp associated with the electronic contract and associating the timestamp with the electronic contract; an electronic contract including the signature and associated with the timestamp being encrypted by a presetencryption rule. The invention is applied to the field of house leasing. On the basis of electronically signing the contract, the invention ensures the tamperproof property of the electronic contractand the legal validity of on-line signing the contract through the time stamp and the encryption method.
Owner:PING AN TECH (SHENZHEN) CO LTD
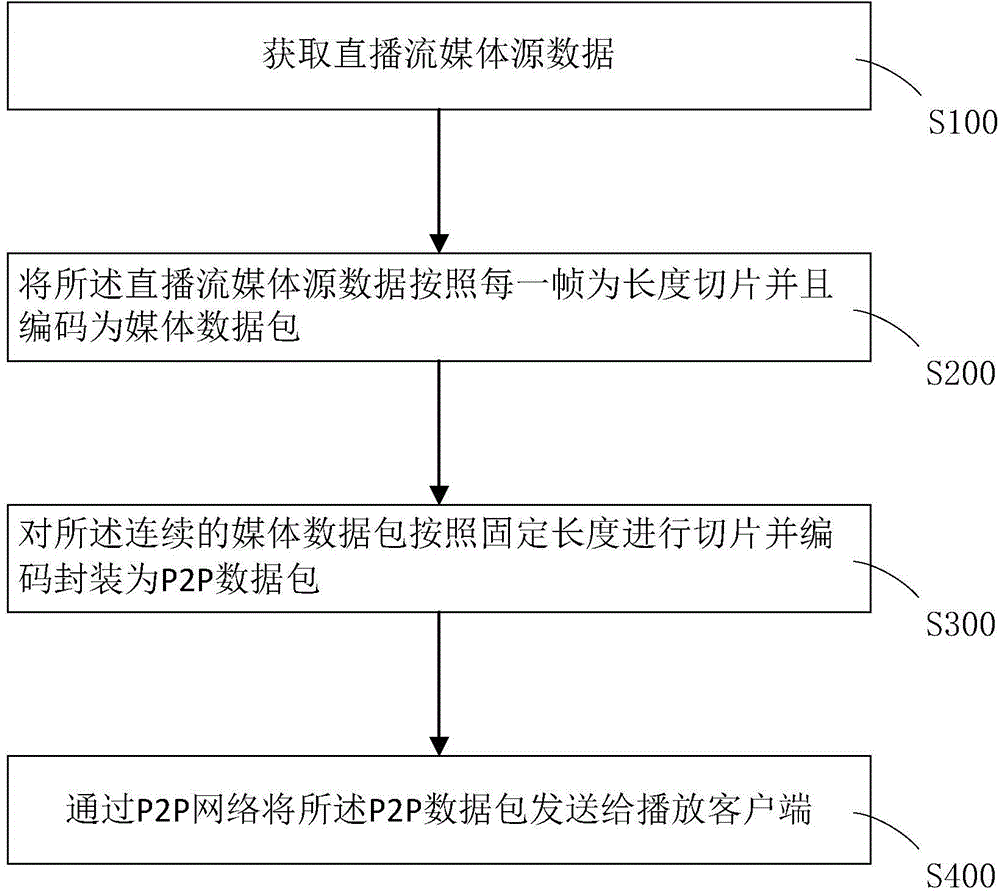
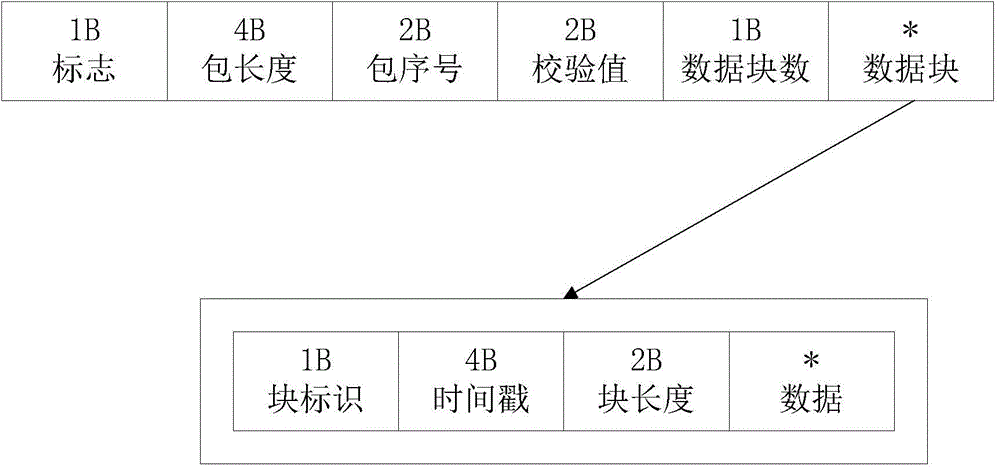
Audio/video live broadcast streaming media data transmission method in P2P system
InactiveCN106034242AGuaranteed tamper resistanceReduce bandwidth requirementsSelective content distributionNetwork packetData transmission
The invention provides an audio / video live broadcast streaming media data transmission method in a P2P system. The method comprises the following steps of acquiring live broadcast streaming media source data; slicing the live broadcast streaming media source data according to a manner that each frame is used as the length unit and coding the live broadcast streaming media source data for obtaining media data packets; slicing the continuous media data packets according to a fixed length and performing code packaging for obtaining P2P data packets; and transmitting the P2P data packets to a playing client through a P2P network. The audio / video live broadcast streaming media data transmission method in the P2P system has advantages of minimizing network transmission expenditure, reducing requirement to bandwidth, and furthermore effectively ensuring no tampering of the live broadcast flow through a verification mechanism.
Owner:HANGZHOU STRONG NETWORK TECH
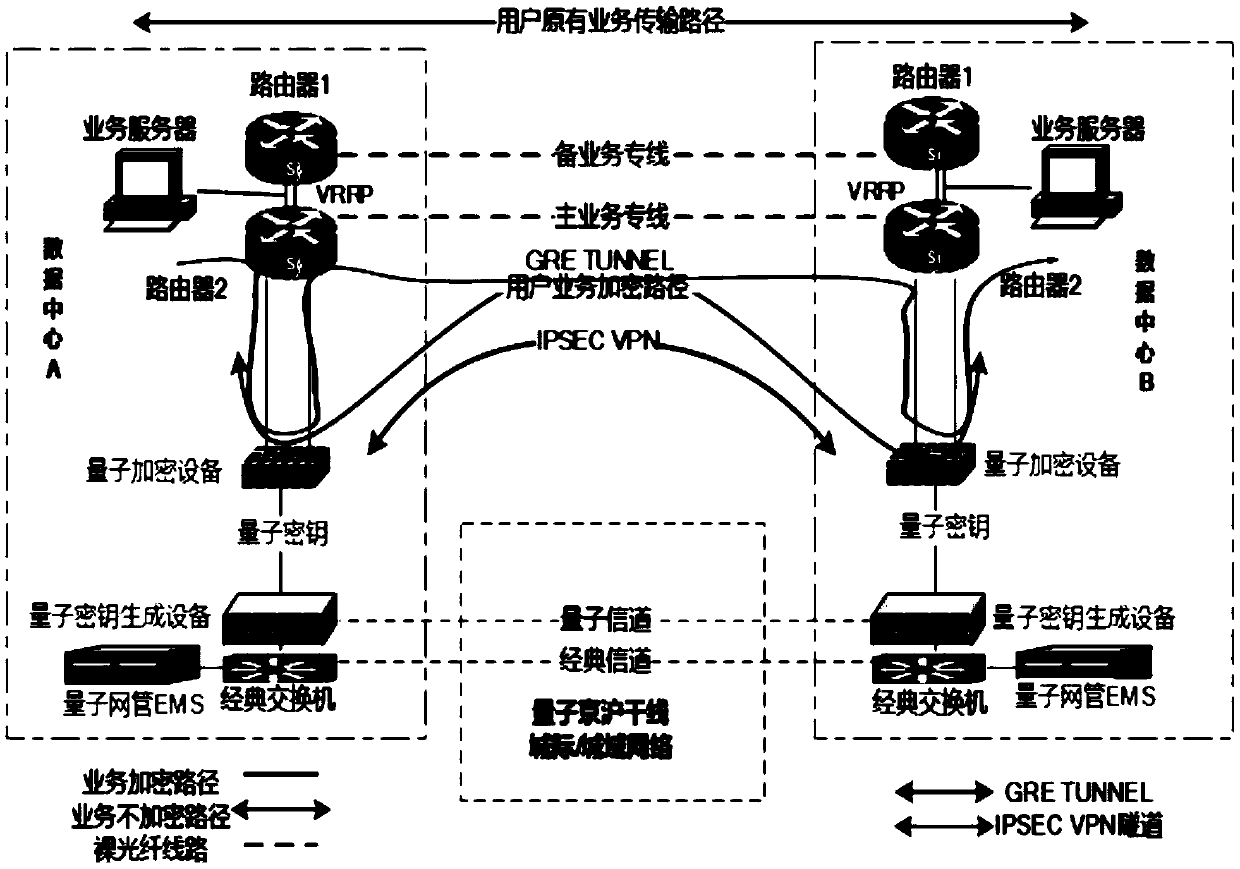
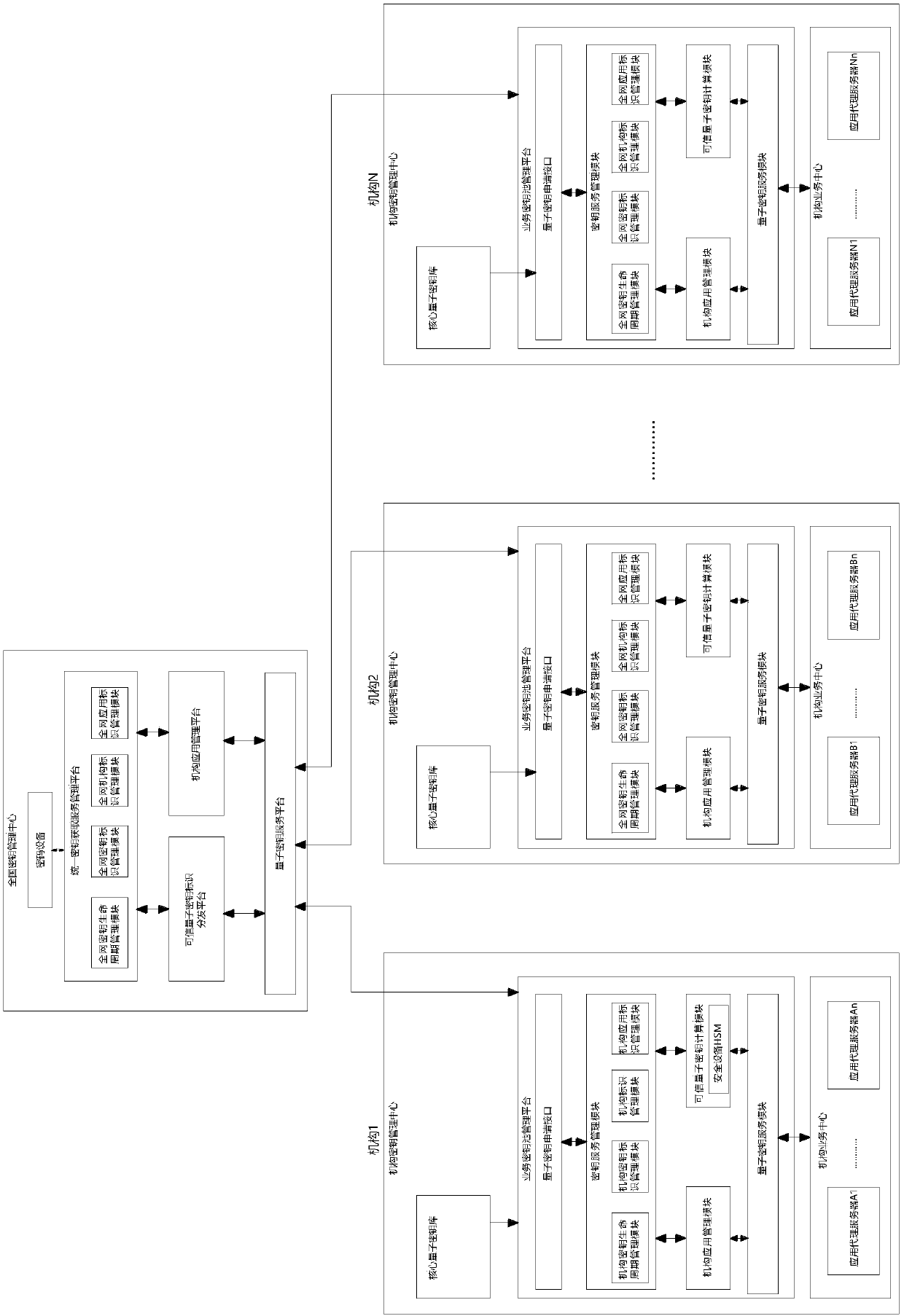
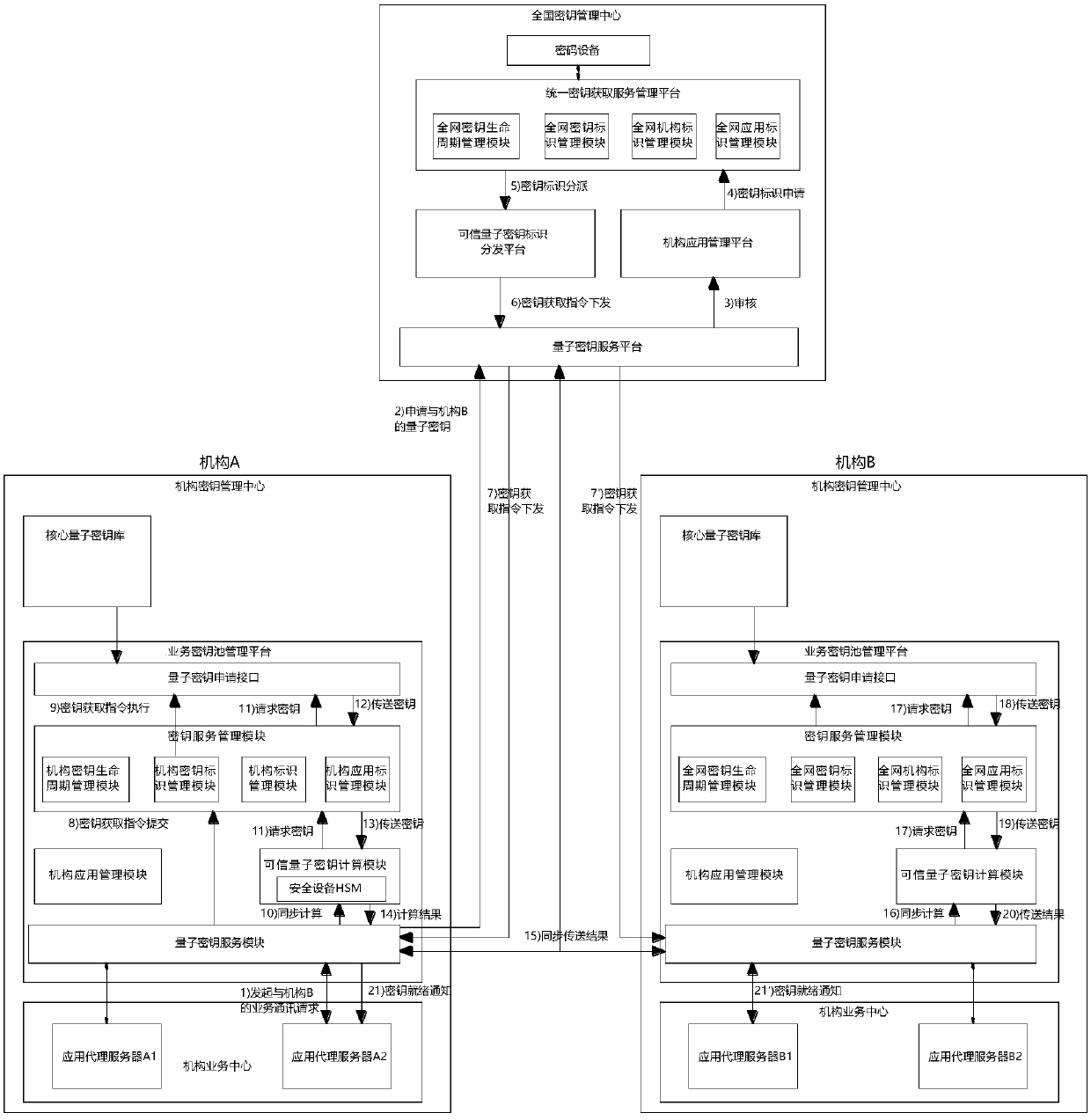
Application system based on quantum keys, and use method of application system
ActiveCN109660340AEasy to work safelyPromote the further development of safety workKey distribution for secure communicationSynchronising transmission/receiving encryption devicesCommunications securityTamper resistance
The invention discloses an application system based on quantum keys. The system comprises institution key management centers arranged at all institutions and used for providing unified quantum key services for application security and communication security, and a national key management center communicating with the institution key management centers of the institutions and responsible for distributing and sending the quantum keys or quantum key IDs for the institutions; and the two institution key management centers need to simultaneously initiate requests of obtaining the same quantum key to the national key management center. A barrier between an entity quantum network and a virtual application network is broken through, so that the high-security characteristics of the quantum keys arefurther extended to the service field, and further development of information security work is promoted; and by utilizing high security of the quantum network, the difficult problem of key distribution synchronization in the service field is solved, and the problems of the authority, credibility and security of key sources are solved, so that the confidentiality and the tamper-proofing performance of service information transmitted in an untrusted network are further guaranteed.
Owner:北京安御道合科技有限公司
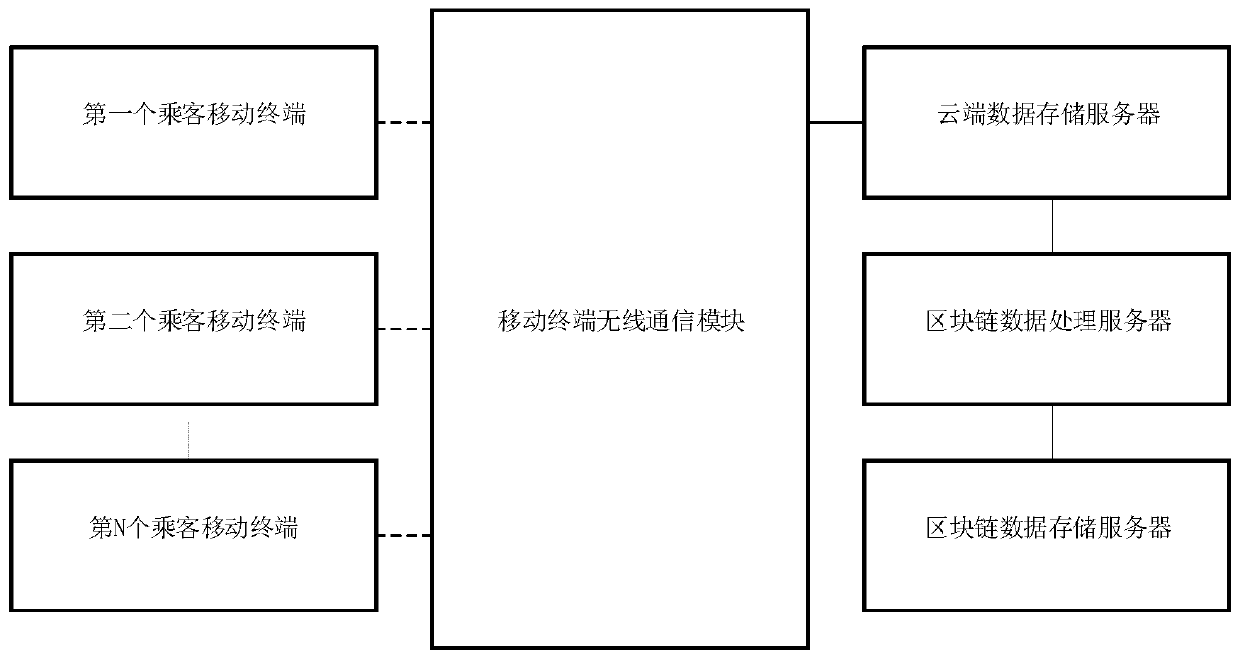
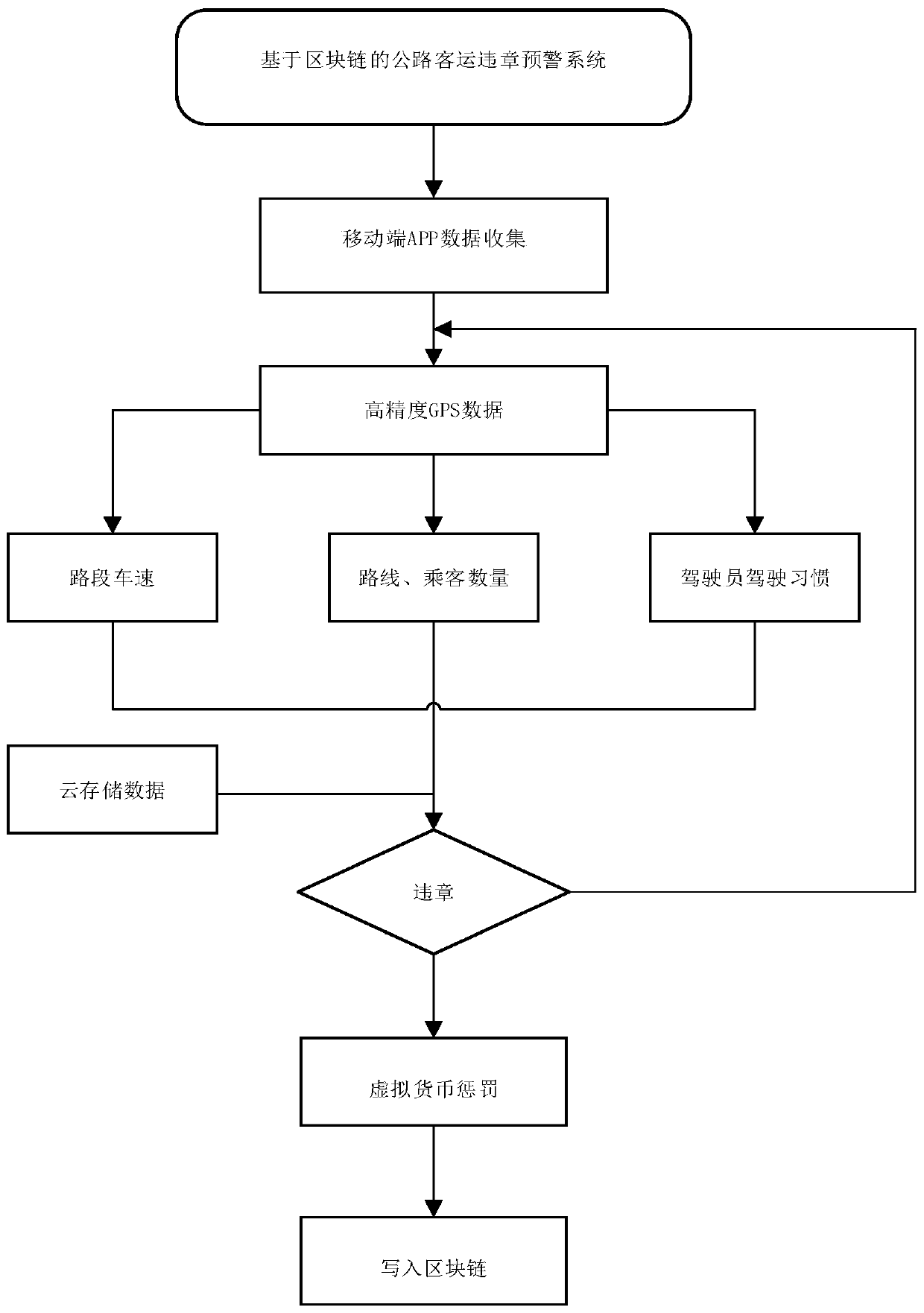
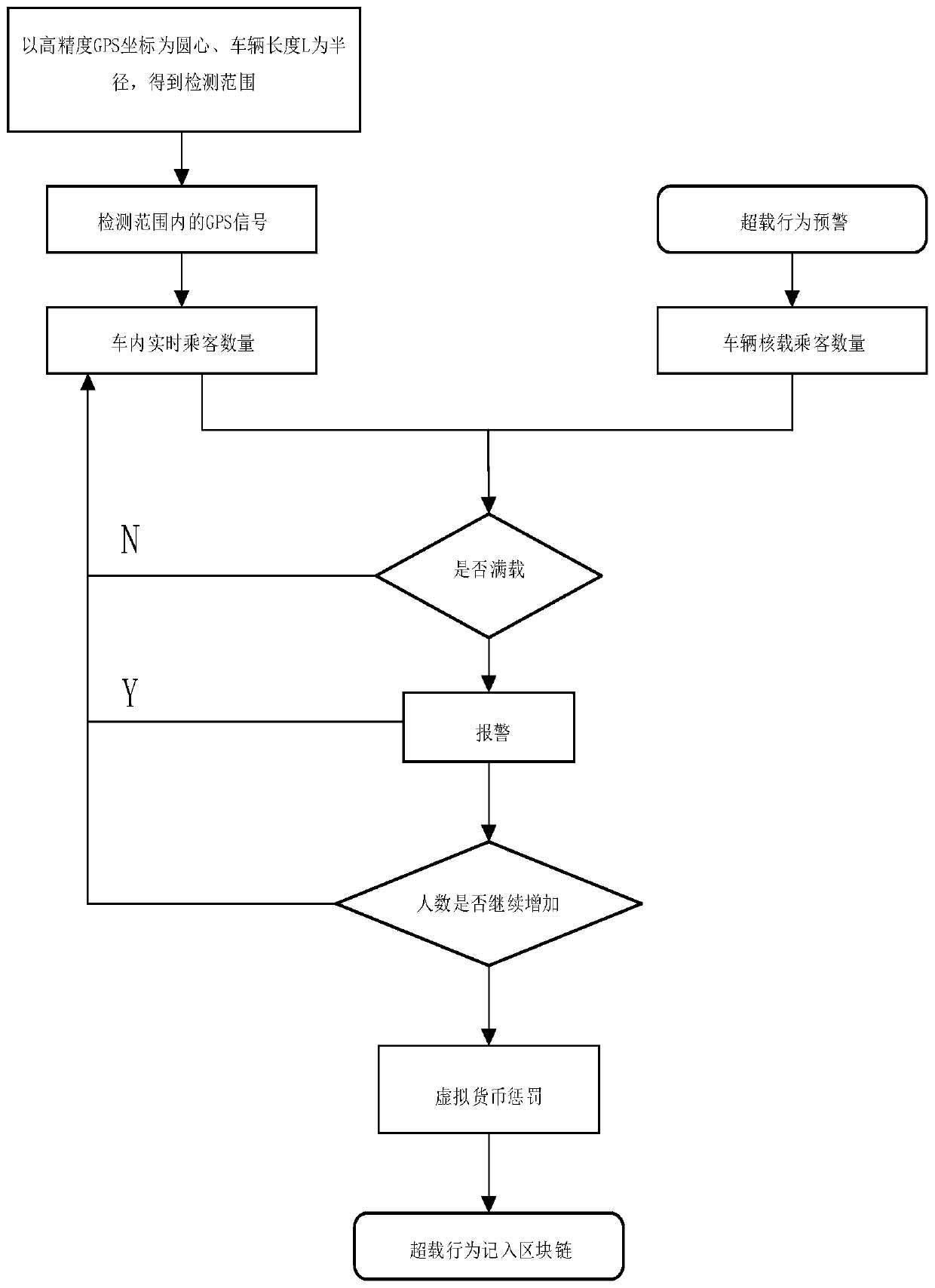
Real-time early warning system and method of highway passenger transportation violation based on block chain
ActiveCN110060484AGuaranteed tamper resistanceGuaranteed traceabilityData processing applicationsRoad vehicles traffic controlEarly warning systemDriver/operator
The invention provides a real-time early warning system and method of the highway passenger transportation violation based on a block chain. The real-time early warning system comprises a plurality ofpassenger mobile terminals, a mobile terminal wireless communication module, a cloud data storage server, a block chain data processing server and a block chain data storage server. According to thereal-time early warning system and method, the basic information of a driver is uploaded to the cloud data storage server through the mobile terminal wireless communication module; passenger GPS dataare collected through the passenger mobile terminals and transmitted to the cloud data storage server through the mobile terminal wireless communication module, and the block chain data processing server calls the passenger GPS data in the cloud data storage server for processing; and the block chain data processing server judges the violation behavior of the driver according to the overspeed early warning, overload early warning, fatigue driving early warning and malicious change of operation route early warning, and sends corresponding warning information to the driver through an intelligentcontract. The real-time early warning system and method have the advantages of timeliness of early warning data and non-tampering of violation information.
Owner:WUHAN UNIV OF TECH
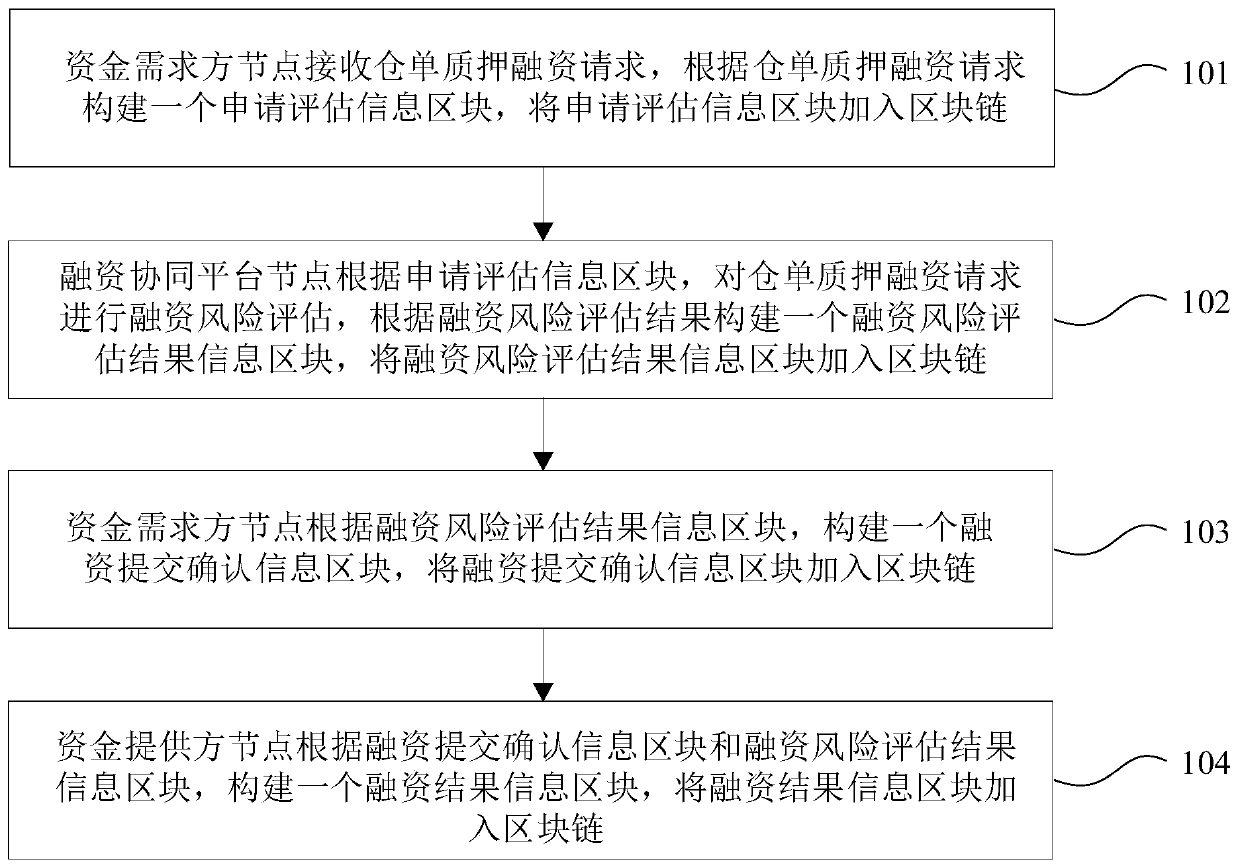
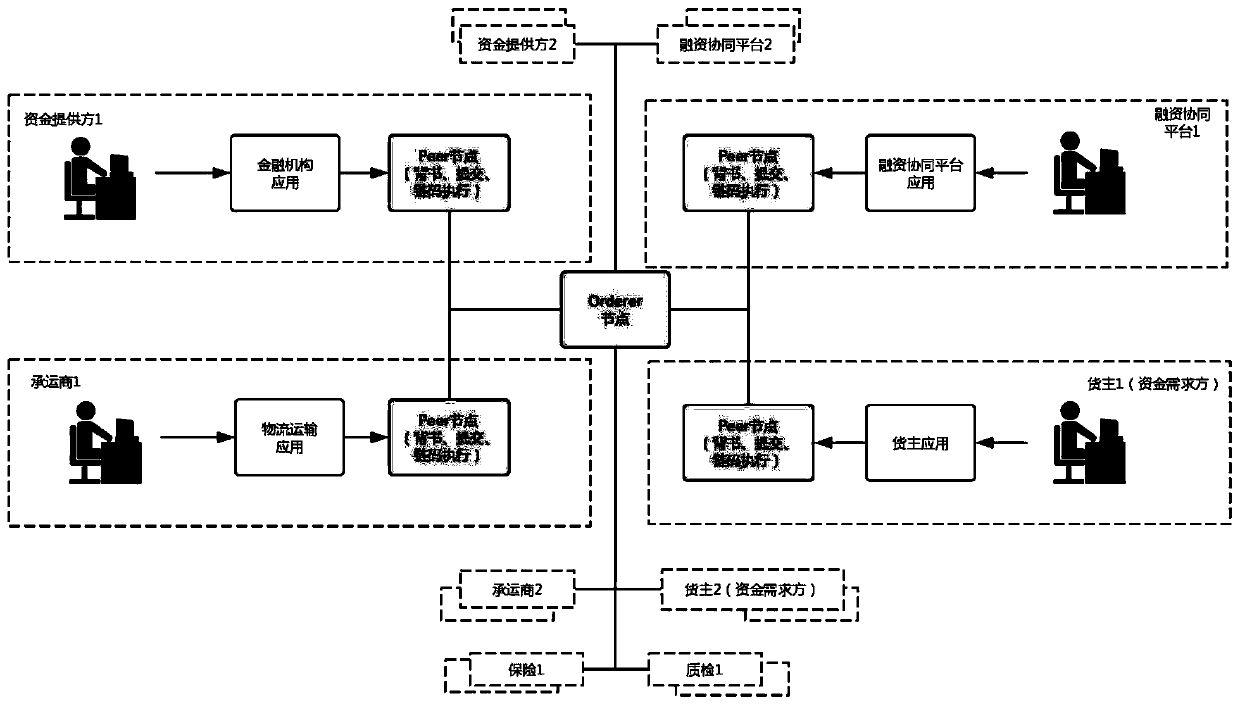
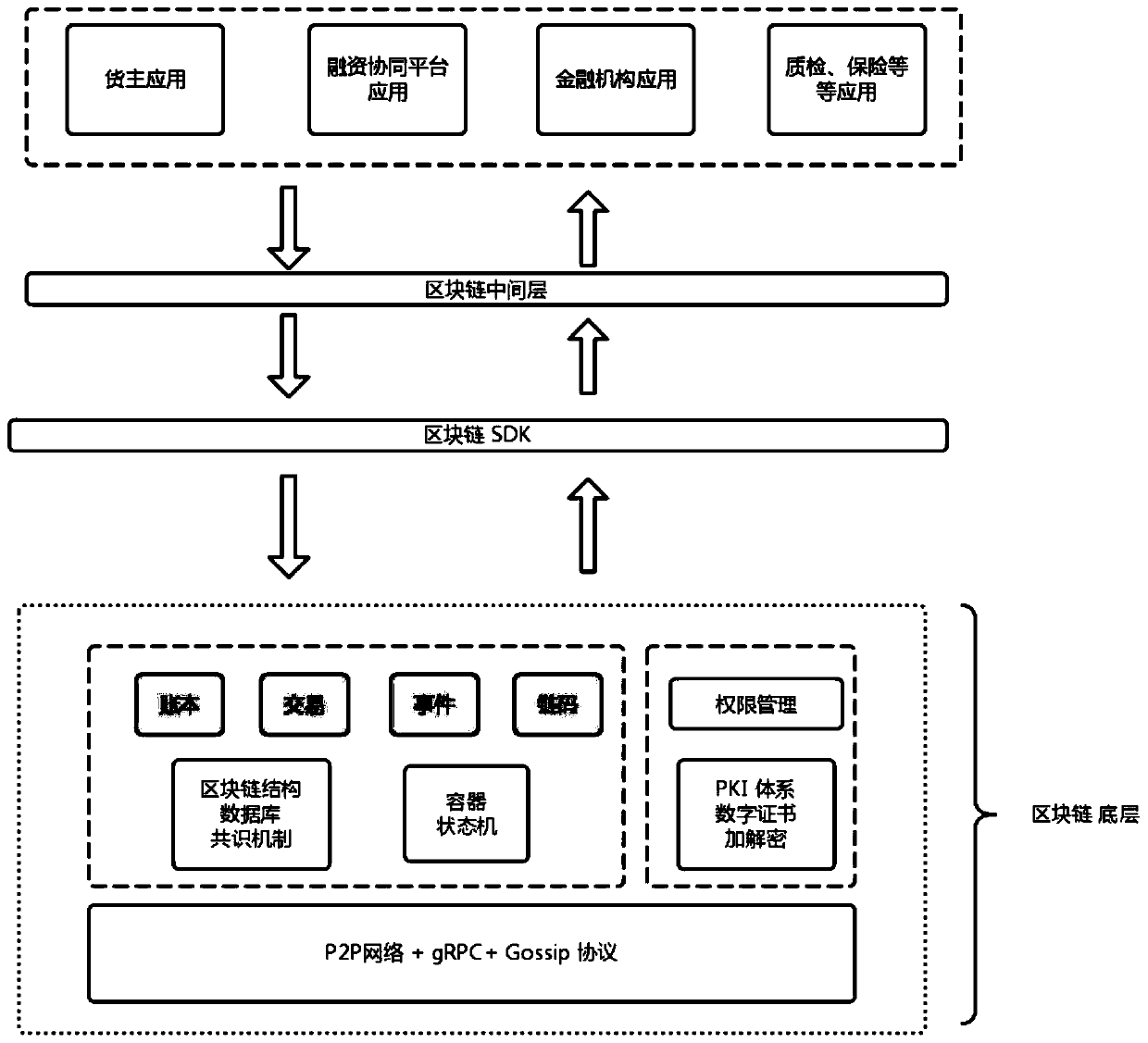
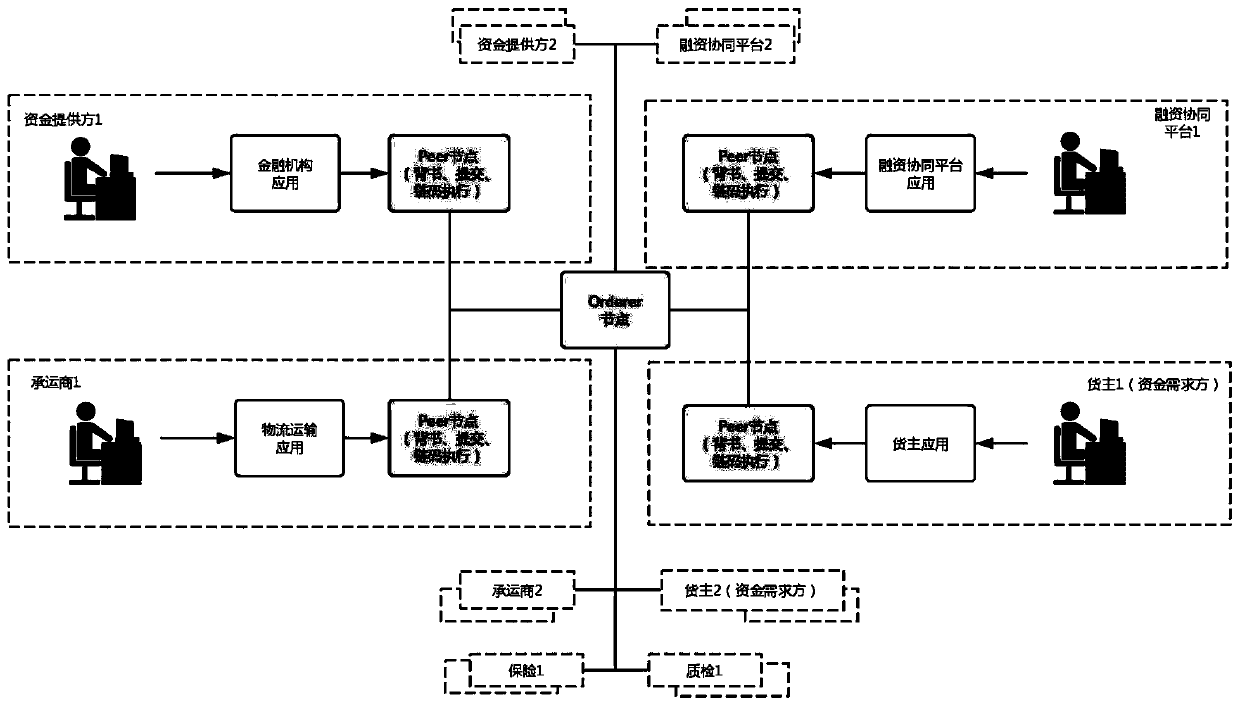
A warehouse receipt pledge financing evaluation method and device based on a block chain architecture
The invention provides a warehouse receipt pledge financing evaluation method and device based on a block chain architecture, and the method comprises the steps that a fund demand side node receives awarehouse receipt pledge financing request, and constructs an application evaluation information block according to the warehouse receipt pledge financing request; the financing cooperation platformnode carries out financing risk assessment on the warehouse receipt pledge financing request according to the application assessment information block, and constructs a financing risk assessment result information block according to a financing risk assessment result; the fund demander node constructs a financing submission confirmation information block according to the financing risk assessmentresult information block; and the fund provider node constructs a financing result information block according to the financing submission confirmation information block and the financing risk assessment result information block, and adds the financing result information block into the blockchain. According to the technical scheme, the safety and efficiency of warehouse receipt pledge financing evaluation are improved, and the development of warehouse receipt pledge financing business is greatly promoted.
Owner:CITIC PHOENIX HARBOR SUPPLY CHAIN MANAGEMENT CO LTD
Electronic seal system and electronic seal method based on time stamp and GPS location
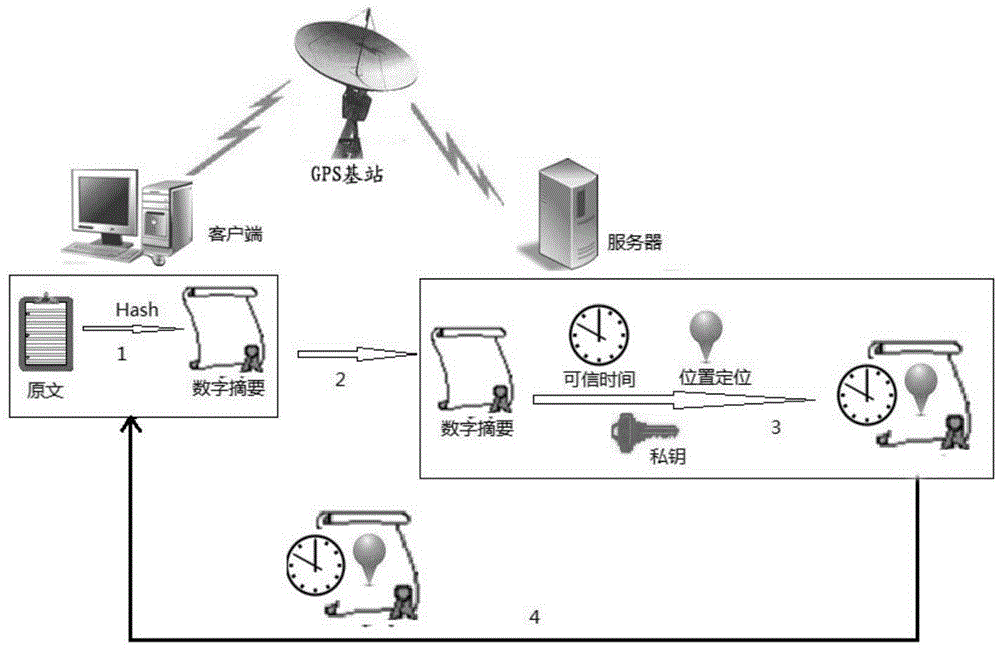
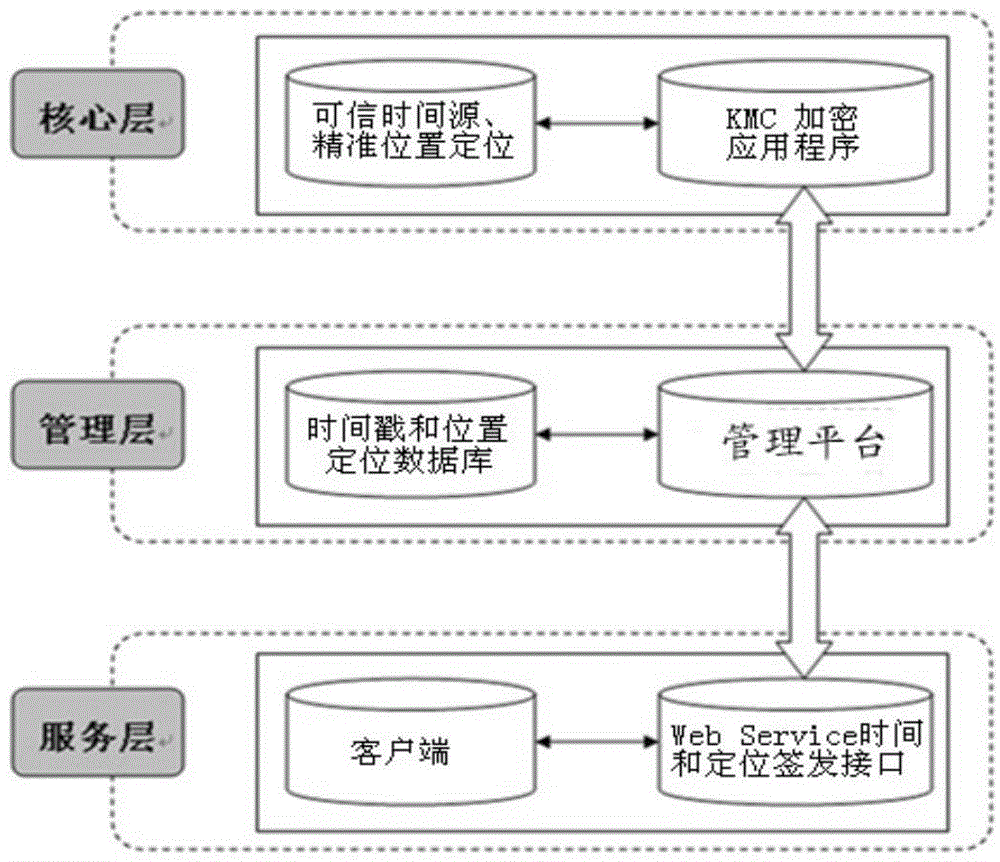
InactiveCN104539434AGuaranteed tamper resistanceGuaranteed non-repudiationUser identity/authority verificationService layerReal-time computing
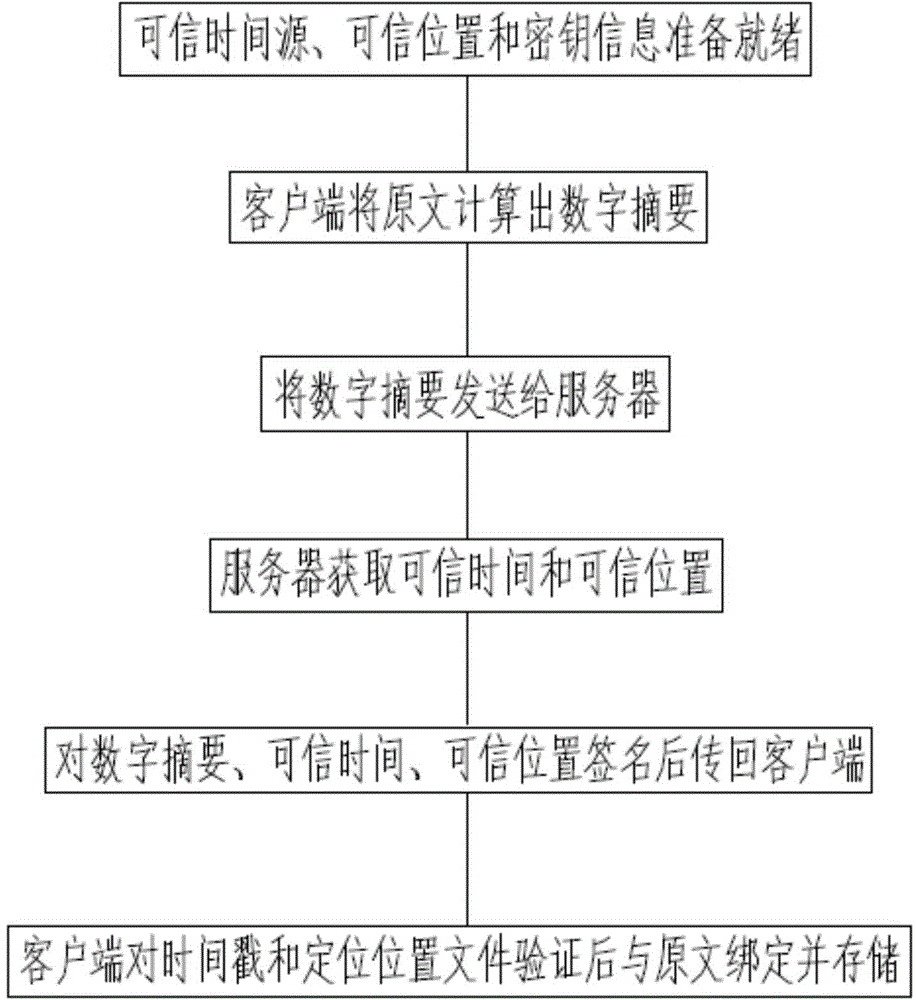
The invention discloses an electronic seal system based on a time stamp and GPS location. The electronic seal system comprises a client, a server and a GPS base station, wherein the client and the server are respectively in communication connection with the GPS base station; the server consists of a core layer, a management layer and a service layer. An electronic seal method based on the electronic seal system comprises the following steps: firstly, preparing a ready credible time source, a credible position and key information, after calculating a digital digest by the client, sending to the server, reading the credible time and a credible position of the client from the GPS base station by using the server, signing the digital digest, the credible time and the credible position by the server, returning a file to the client after the time stamp and a locating position file are generated, verifying the returned file by the client, then binding the file and an original text together, and storing. According to the electronic seal system and the electronic seal method disclosed by the invention, the GPS system is utilized to locate the time and the position of a seal file of the client, the time and the position of carrying out operation in the electronic seal process can be locked, and the tampering and disavowing resistances of the file can be effectively ensured.
Owner:同智伟业软件股份有限公司
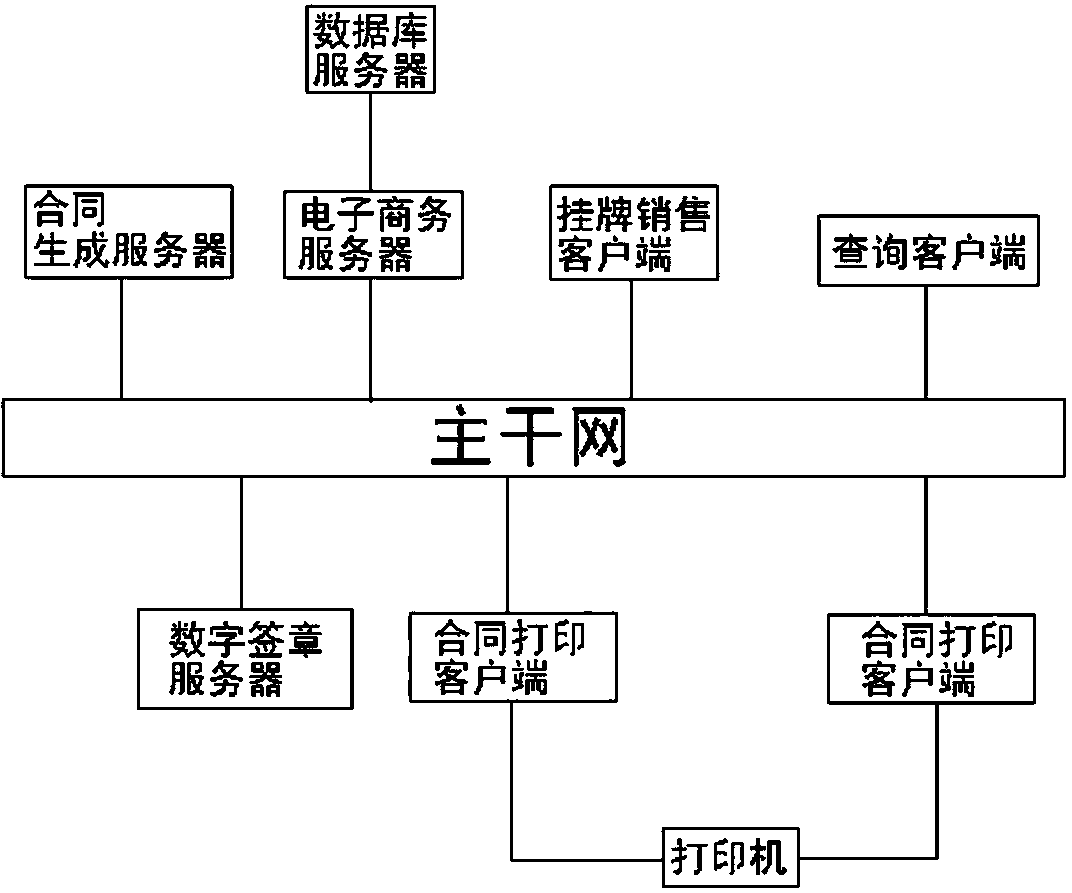
Management system and management method of sales contract
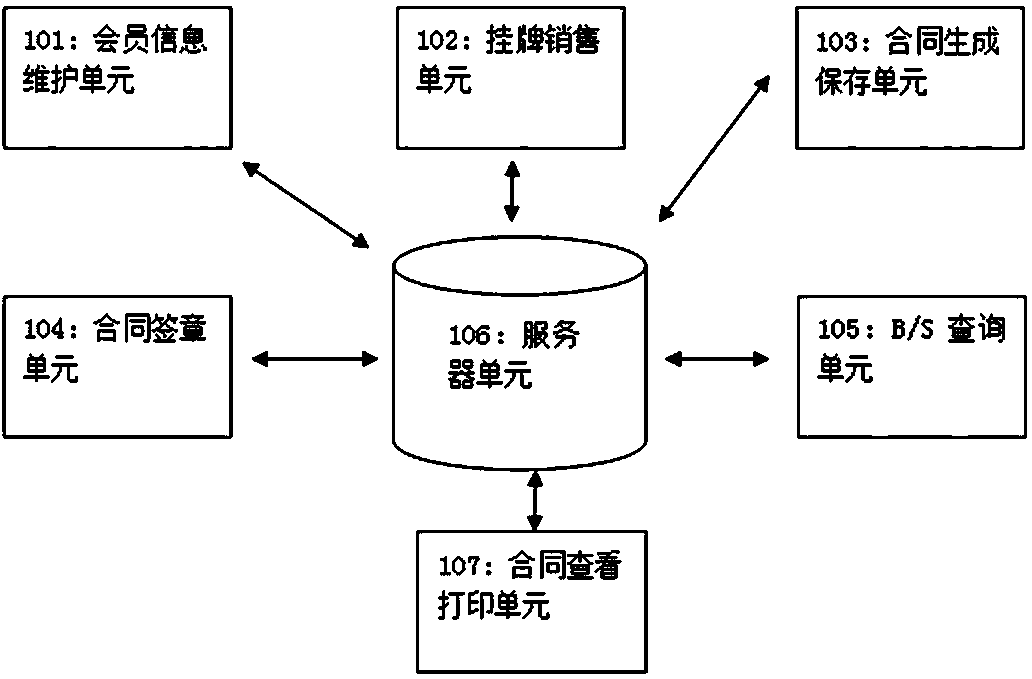
InactiveCN104240100ARealize automatic generationImprove accuracyCommerceRecord carriers used with machinesInformatizationElectronic contracts
The invention discloses a management system and a management method of sales contract. The management system comprises a server unit, an information maintenance unit, a sales unit, a contract generating and saving unit, a contract signing unit, a B / S inquiry unit and a contract checking and printing unit. Techniques of network, computer, communication, mobile equipment, two-dimensional code encryption, digital signature and the like are integrated with the management system and the management method fully. Electronic contract is generated by calling an enterprise information system, is subjected to two-dimensional code encryption and digital signature to avoid being counterfeited, tampered and repudiated, and can be checked and printed and the like. Since iron and steel product contract is generated automatically, signed and printed by customers themselves, accuracy, real-time performance, effectiveness, unlimited location of iron and steel product contract generation are improved, steel product circulation efficiency is improved, and integral informatization level and list sales service level of the iron and steel industry are increased. In addition, security and reliability of the electronic contract are guaranteed by the two-dimensional code encryption and digital signature techniques.
Owner:WUKUN STEEL
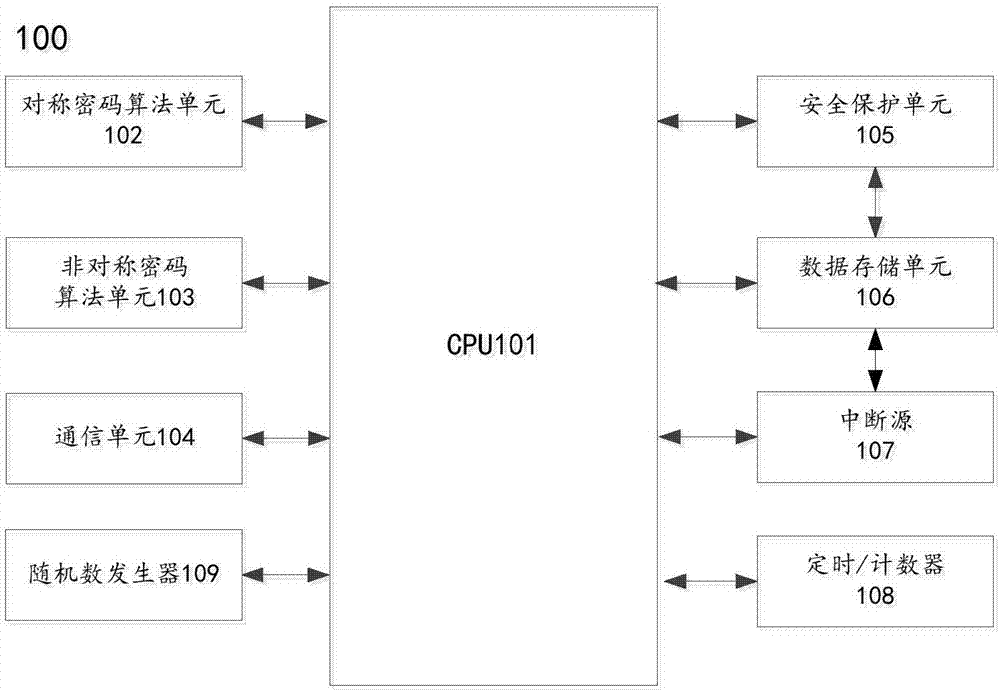
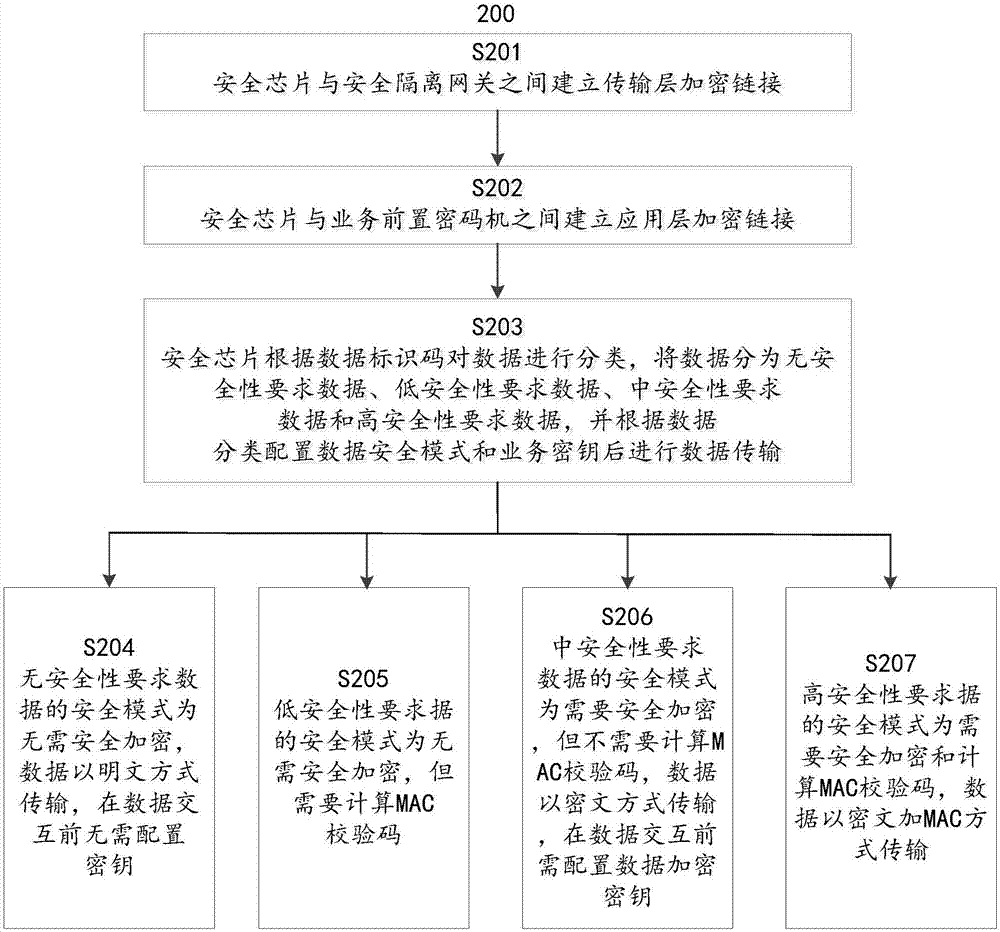
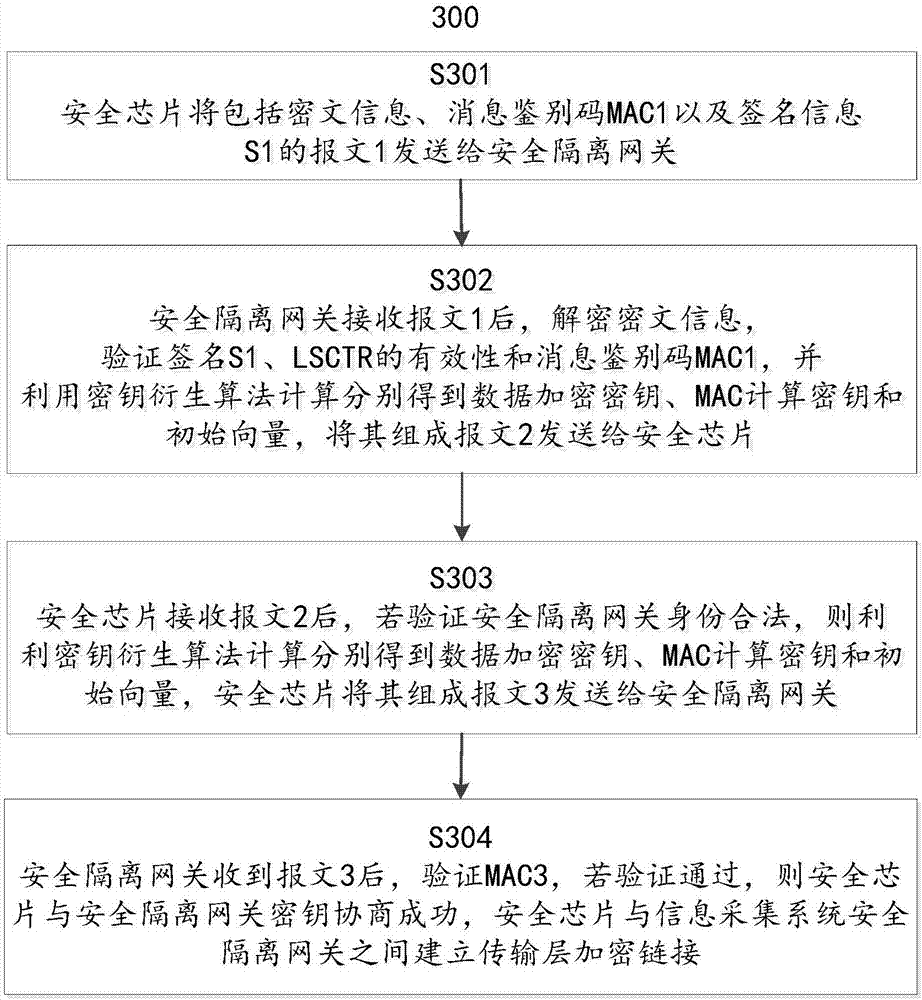
Object-oriented security chip and encryption method thereof
ActiveCN106973056AGuaranteed privacyGuaranteed anti-replayKey distribution for secure communicationUser identity/authority verificationCommunication unitSecure transmission
The invention relates to an object-oriented security chip and an encryption method thereof. The security chip comprises a central processing unit (CPU), a symmetric cryptographic algorithm unit, an asymmetric cryptographic algorithm unit, a communication unit, a security protection unit, a data storage unit, an interruption source and a timer / counter, wherein the CPU is used for coordinating other functional modules in the security chip to ensure the normal operation; the symmetric cryptographic algorithm unit is used for implementing encryption and decryption operations on the data by adopting a national secret symmetric cryptographic algorithm; the asymmetric cryptographic algorithm unit is used for achieving signing and signature verification of digital certificates and calculating message abstracts and key negotiations between two communication parties by adopting a national secret asymmetric cryptographic algorithm; the communication unit is used for performing data communication; the security protection unit is used for guaranteeing the normal operation of the security chip; the data storage unit is used for storing keys; the interruption source is used for initiating an event interruption request to the CPU; and the timer / counter is used for counting and timing during the operation of the security chip. The encryption method of the security chip comprises the following steps: separately establishing a transmission layer security link and an application layer security link, and achieving the secure transmission of the information by adopting a transmission layer and application layer dual-layer protection mechanism.
Owner:CHINA ELECTRIC POWER RES INST +1
Factoring and financing method and device based on block chain architecture
InactiveCN110738575ACertificate of authenticityEnsure transparencyFinanceLogistics managementComputer science
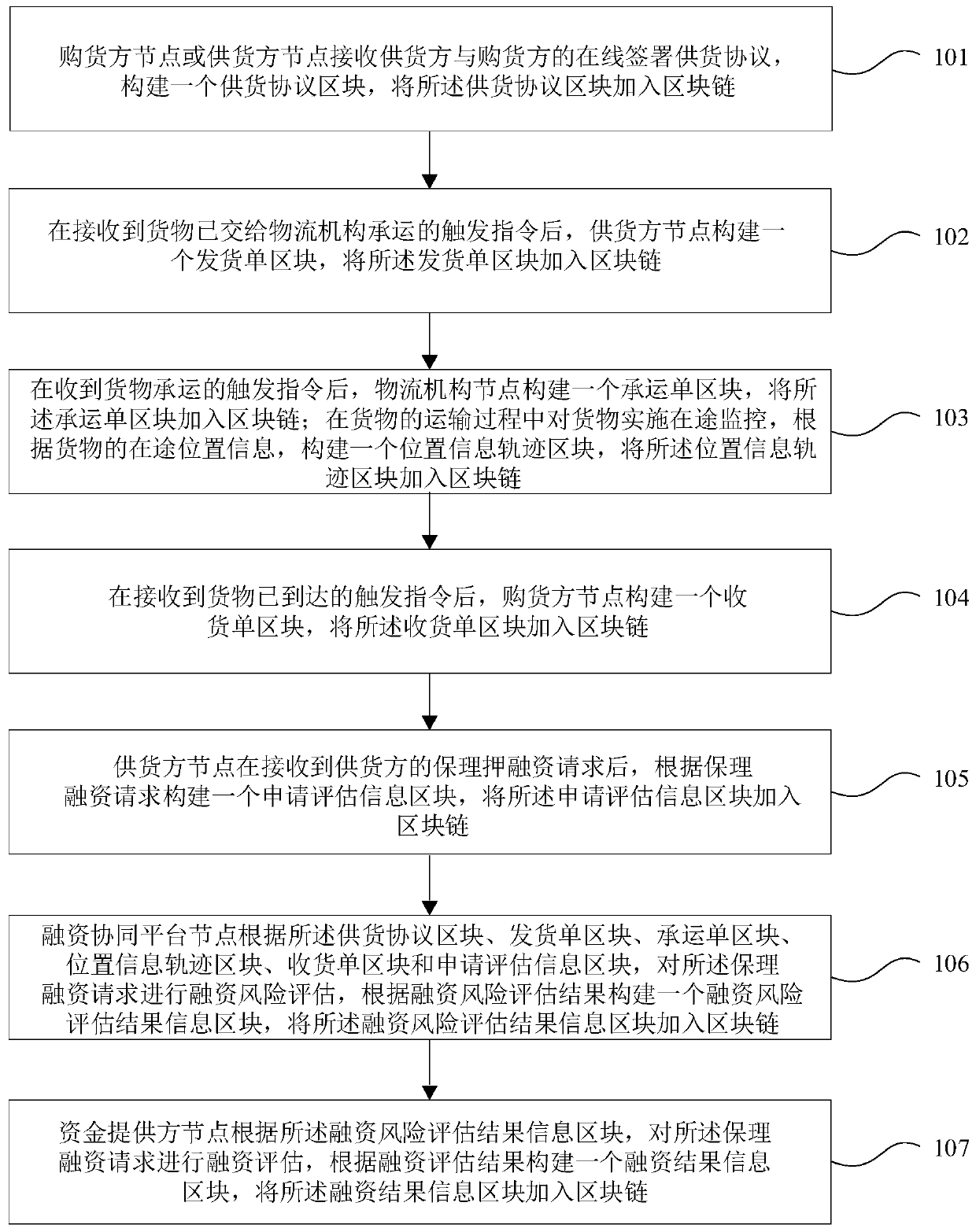
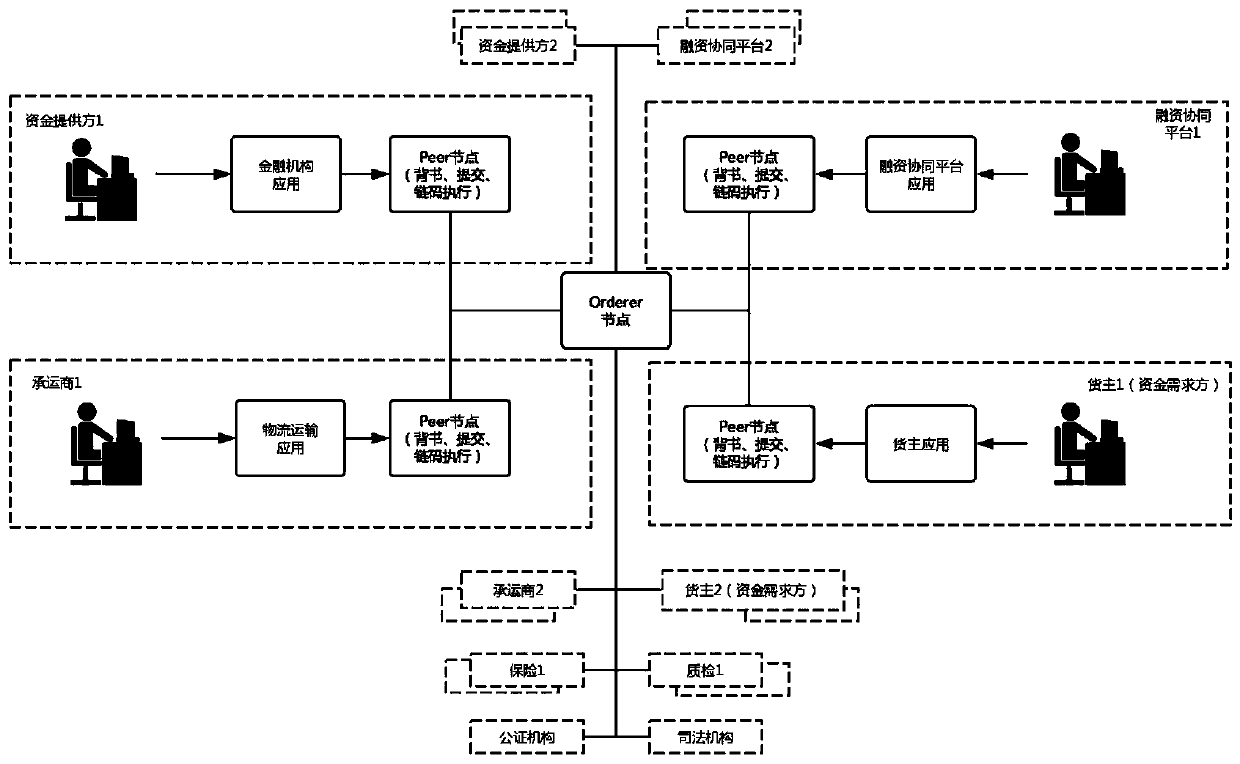
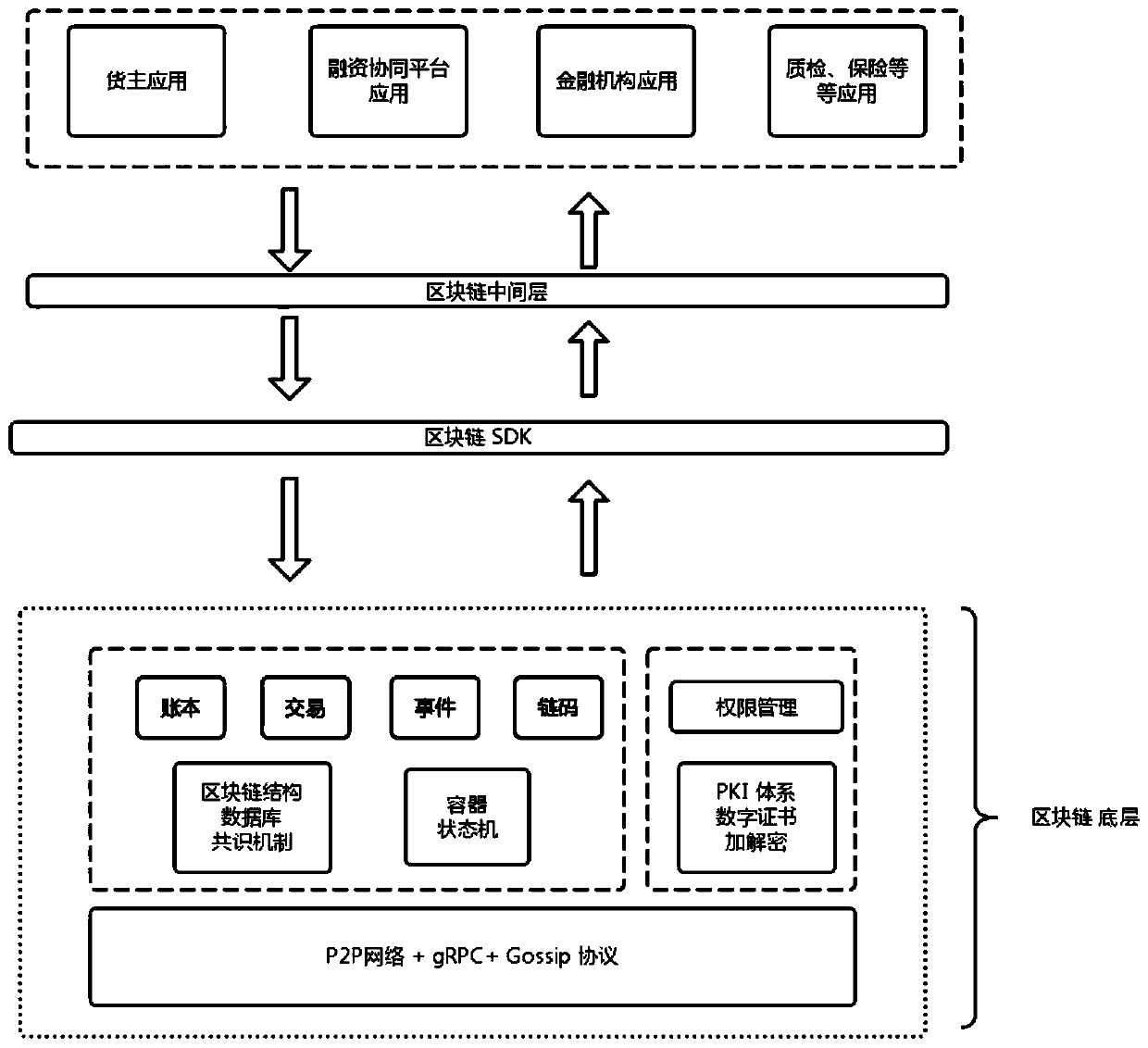
The invention provides a factoring and financing method and device based on a block chain architecture, and the method comprises the steps that a purchaser node or a supplier node adds a constructed supply agreement block into a block chain; the supplier node adds the constructed dispatch list block into a block chain; the logistics institution node adds the constructed carrier list block into a block chain, and adds the constructed position information track block into the block chain; the purchaser node adds the constructed receipt block into a block chain; the supplier node adds the constructed application evaluation information block into a block chain; the financing collaboration platform node performs financing risk assessment on the factoring financing request, and adds a constructed financing risk assessment result information block into a block chain; and the fund provider node performs financing assessment according to the financing risk assessment result information block, and adds the constructed financing result information block into the block chain. According to the technical scheme, the security and efficiency of factoring and financing are improved, and the development of factoring and financing services is greatly promoted.
Owner:CITIC PHOENIX HARBOR SUPPLY CHAIN MANAGEMENT CO LTD
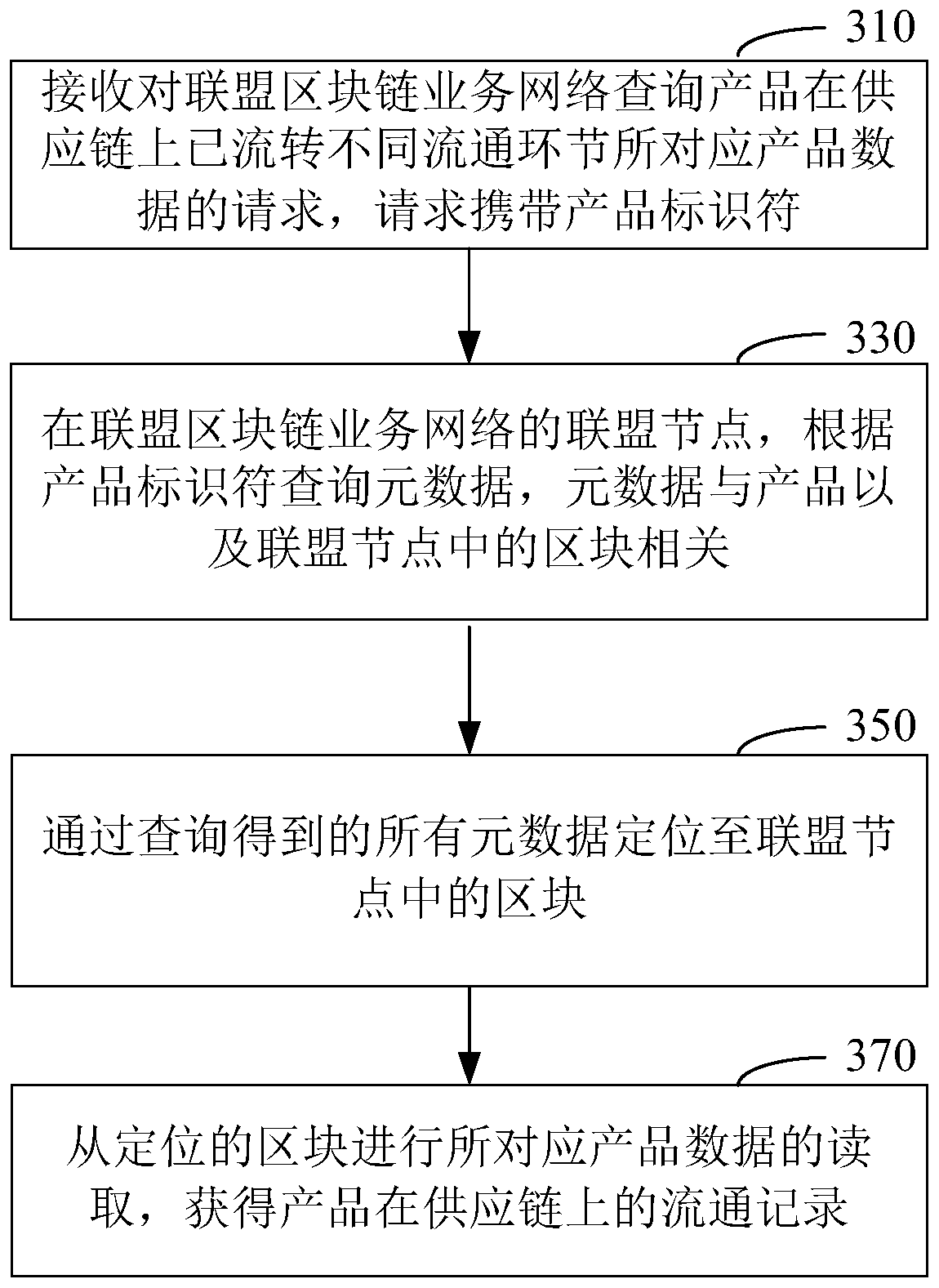
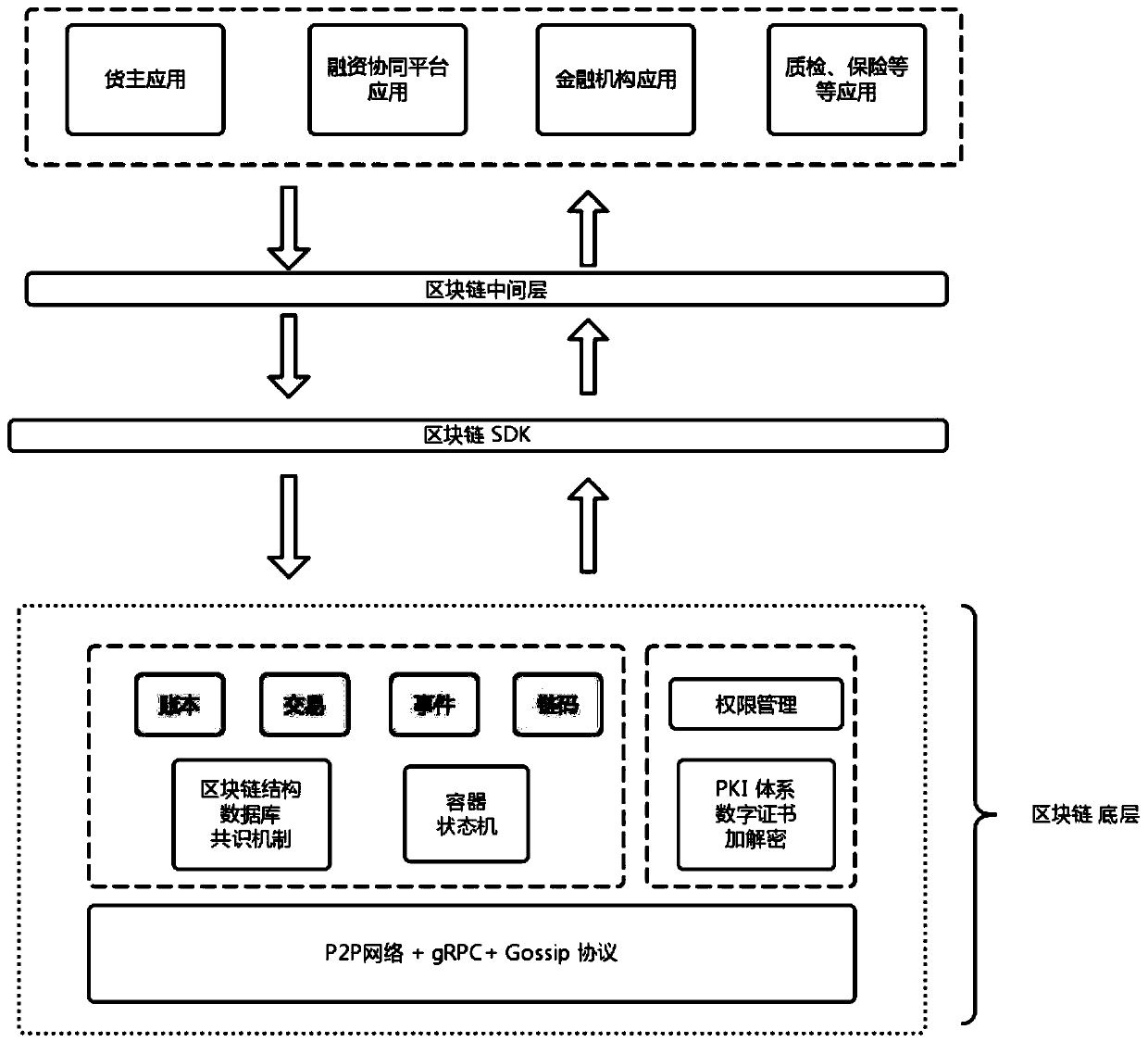
Alliance block chain service network and alliance node and product data storage method thereof
ActiveCN110472116AImprove safety and reliabilityImprove reliabilityCommerceSpecial data processing applicationsMessage queueDigital signature
The invention discloses an alliance block chain service network, an alliance node thereof and a product data storage method. The alliance node comprises a message queue module configured to uniformlydistribute communication messages with other alliance nodes; a data acquisition module configured to acquire product data of a product, use a unique identifier for the product, process the product data by using encryption and digital signature technologies, and then send the processed product data to other alliance nodes through network messages; and an alliance chain module configured to regularly perform workload certification on the collected product data to compete for a main alliance node, integrate the product data into a new data block, and write the newly generated block into an alliance block chain service network with other alliance nodes through a consensus mechanism. According to the embodiments of the invention, the data of each node is ensured to be public and transparent toother nodes. The trust among alliance nodes of a product supply chain system is enhanced.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Session security processing system, equipment, device, and method
The invention discloses a session security processing system, equipment, device, and method. The session security processing system comprises a client and a server; the client respectively encrypts user authentication information and a generated random key according to a set algorithm and a locally stored public key certificate at the session authentication stage, generates ciphertext information that contains the user authentication information and the random key, sends the ciphertext information to the server, receives encrypted session information transmitted by the server containing a session identifier and a session key, and decrypts the session information to acquire the session identifier and the session key; and the client encrypts transmitted data according to the session key in the received session information at the session communication stage, and generates a ciphertext data packet containing the session identifier and the transmitted data and transmits the ciphertext data packet to the server. The scheme provided by the invention can improve the session security.
Owner:ALIBABA (CHINA) CO LTD
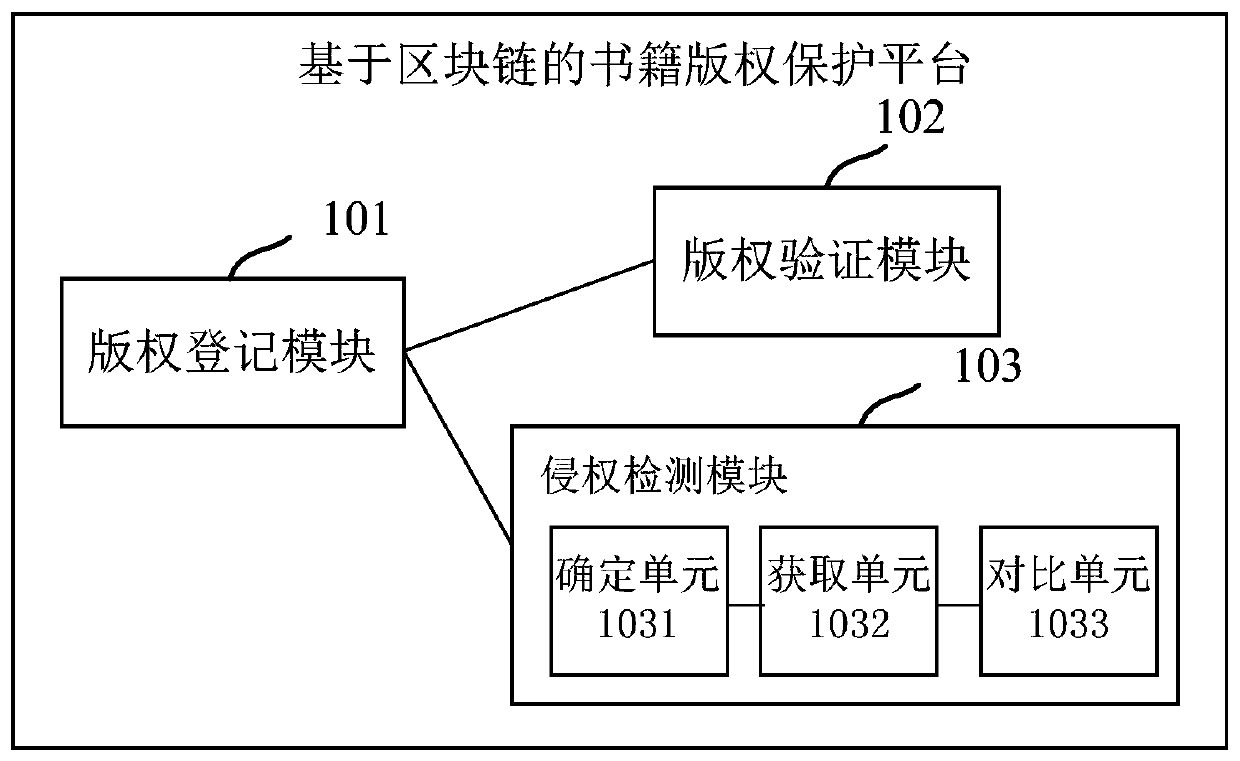
Book copyright protection platform and device based on block chain and medium
PendingCN111046346AGuaranteed tamper resistanceGuaranteed legalityDigital data protectionProgram/content distribution protectionBlockchainTimestamp
The invention discloses a book copyright protection platform and device based on a block chain and a medium. The platform comprises: a copyright registration module which is used for signing book information based on a digital certificate issued by an authorization center and writing the signed book information and timestamp information into a block chain; a copyright verification module which isused for verifying the signature of the book information written into the blockchain; and an infringement detection module which is used for detecting published information of a preset website according to the book information so as to determine whether the published information infringement exists or not. Through the platform, the identity of the book author can be effectively verified, the bookcopyright of the author is ensured, and meanwhile, the book copyright information in the blockchain is maintained not to be tampered.
Owner:山东浪潮质量链科技有限公司
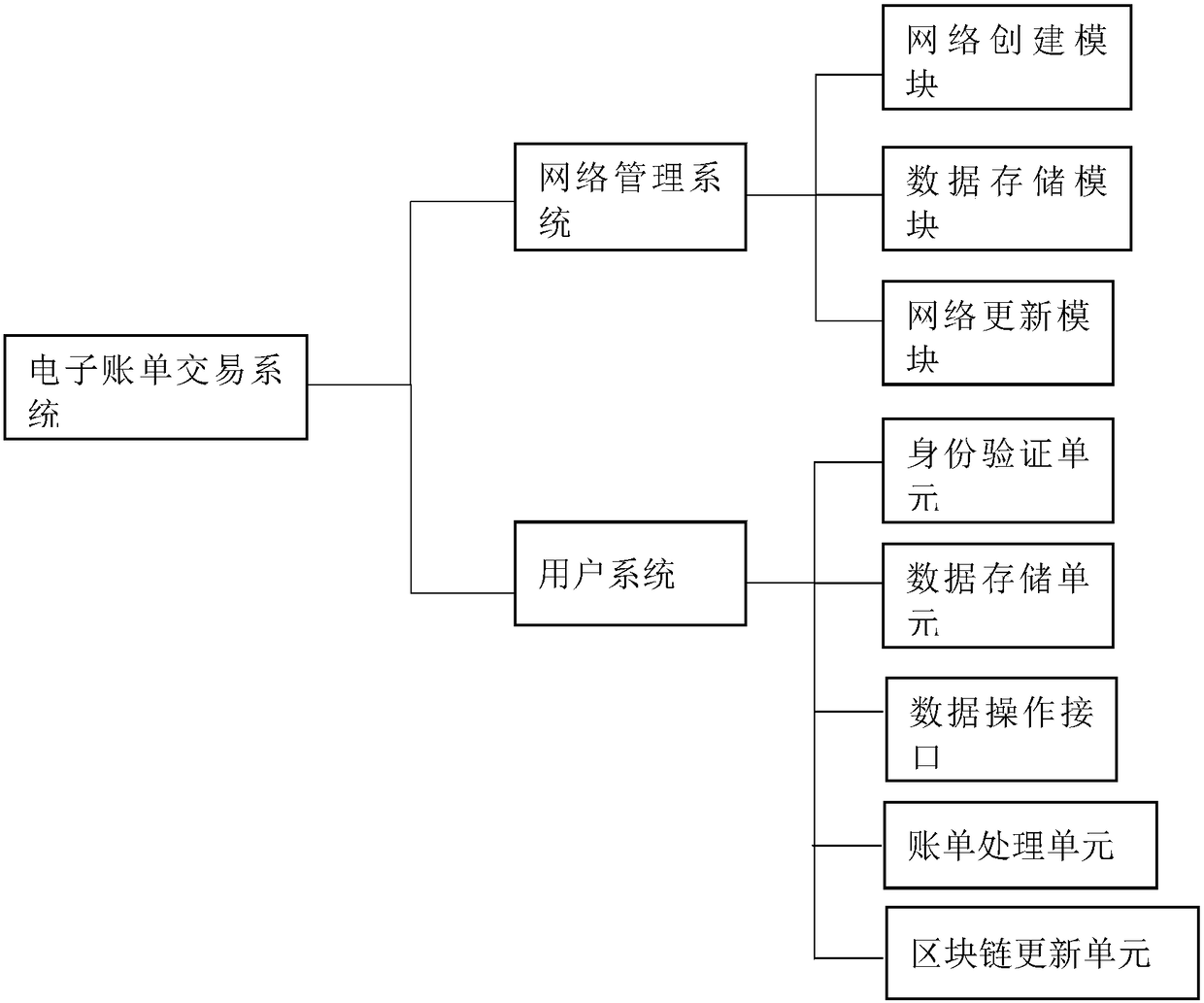
Electronic billing transaction system based on private block chain
ActiveCN108712409AImprove transaction efficiencyEnsure safetyFinanceTransmissionTamper resistanceTransaction data
The invention discloses an electronic billing transaction system based on a private block chain. The system comprises a network management system and a user system; the management system comprises a network creating module, a statistical storage module and a network updating module; the network creating module comprises multiple routes and multiple user nodes; each route sets a routing interface through route mapping, the user node is connected to another user node through the routing interface set by the route; the network updating module is used for initializing the user node, newly adding the user node and deleting the user node; the user system is installed at the user node; the user system is used for realizing the transaction between a transaction sender and a transaction receiver, and adding a block formed by packing the transaction data in the longest block chain in the node network through intelligent contract. The security of the account information in the transaction is guaranteed in the invention, and the security and the tamper resistance of the transaction information are guaranteed.
Owner:广西创轩科技有限公司
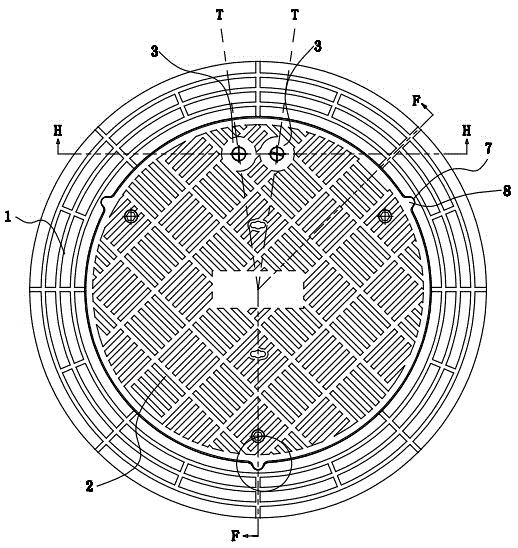
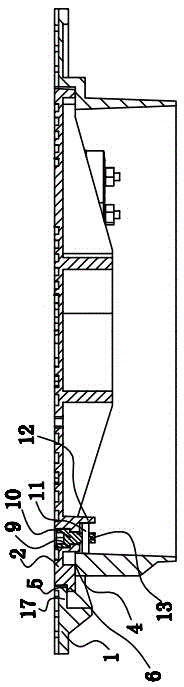
Pit well cover with mechanical password locks and cam locking locating
ActiveCN104088303AGuaranteed tamper resistanceImprove securityArtificial islandsUnderwater structuresCamMechanical engineering
The invention relates to a pit well cover, in particular to a pit well cover with mechanical password locks and cam locking locating. The pit well cover comprises a well cover base, a well cover matched with the inner diameter of the well cover base and a mechanical password lock arranged on the well cover. A mounting sinking table is arranged on the inner wall of the well cover base. The well cover is arranged on the mounting sinking table. An inner boss which protrudes inwards is arranged on the inner wall of the well cover. A mounting locating groove is formed in the inner boss. A mounting locating protruding block which protrudes outwards is arranged on the outer edge wall of the well cover. The mounting locating protruding block is matched with the mounting locating groove. At least two sets of mechanical password locks are placed on the well cover on the opposite face of the mounting locating protruding block. A locking device is arranged on the well cover. The locking device locates the well cover and the well cover base in a locking mode through the cam. Through the structure, manufacturing cost is lowered, safety is improved, stability is enhanced, and the prying resistance and the anti-vibration performance are improved.
Owner:欧健
SCR emission-reduction detection control system and method for diesel engine
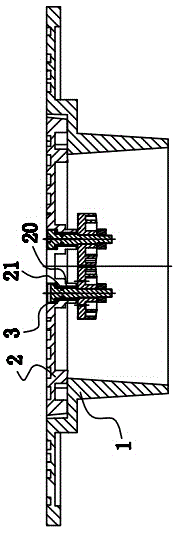
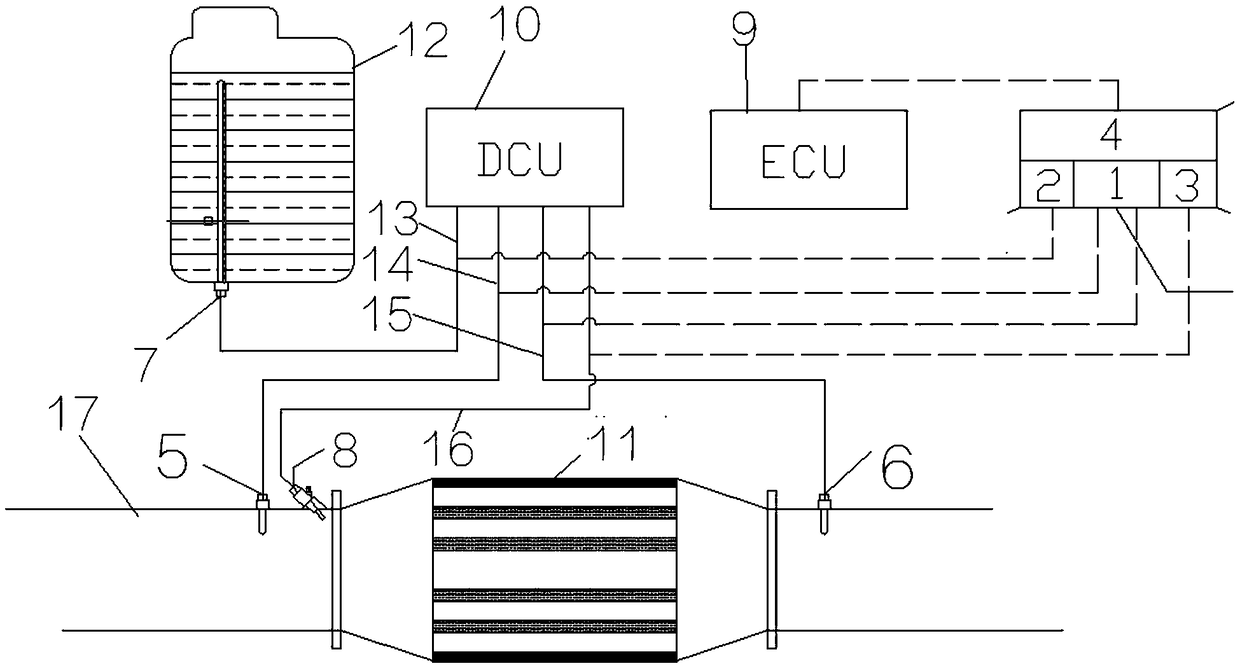
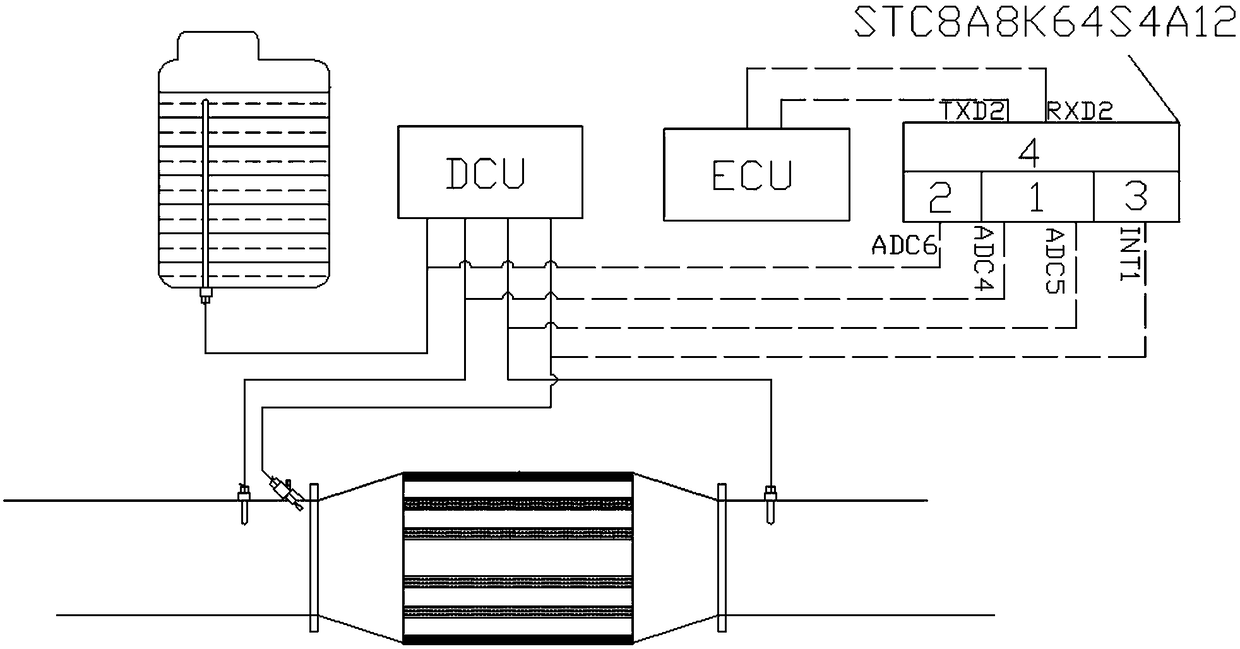
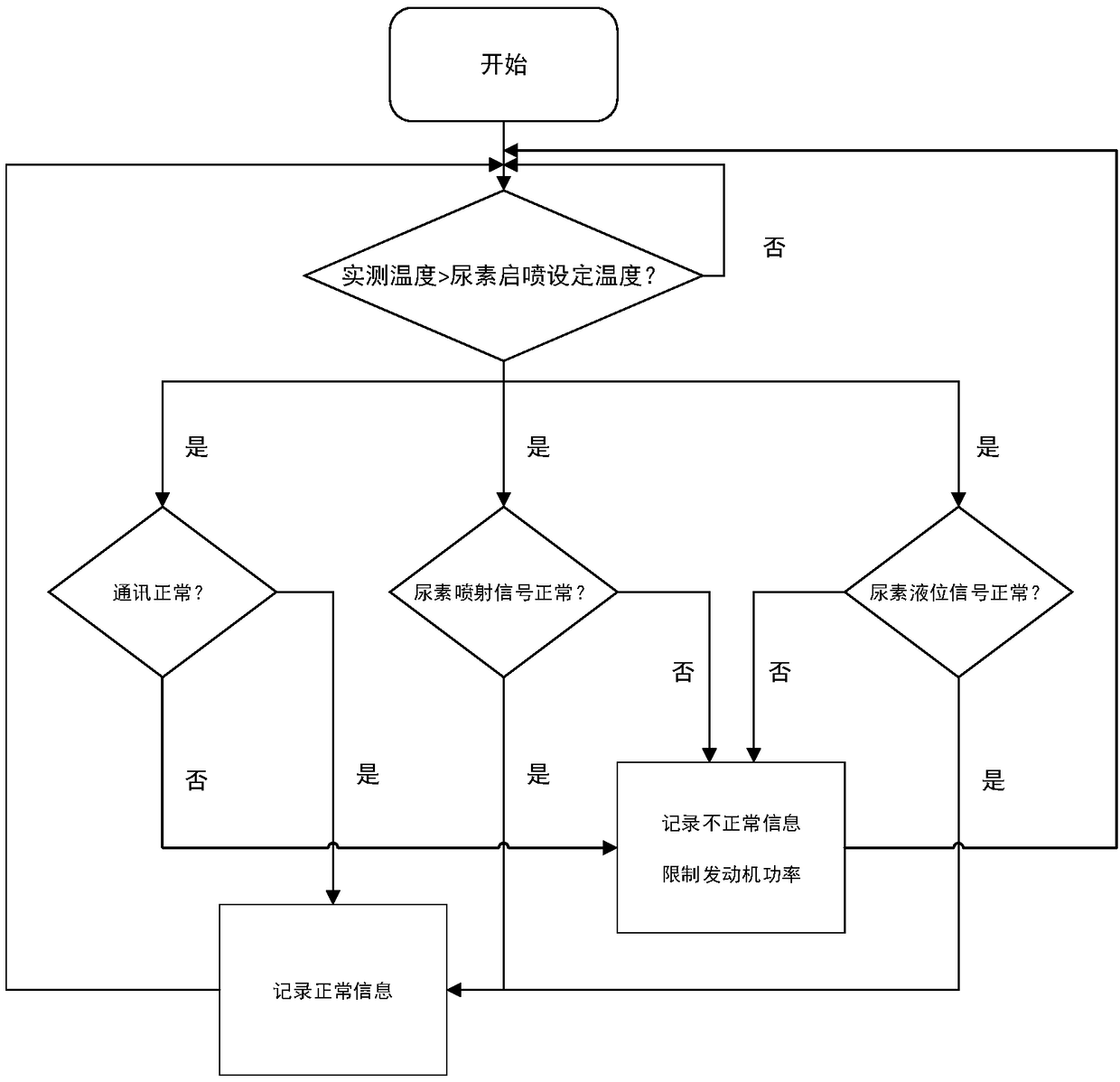
PendingCN109372616AGuaranteed uptimePower limitElectrical controlInternal combustion piston enginesControl systemOn board
The invention discloses an SCR emission-reduction detection control system and method for a diesel engine. According to the control system, whether the liquid level in a urea tank is lowered or not and whether or not a urea sprayer works normally or not can be detected through a detection control device, and then whether or not a whole SCR emission-reduction system works normally or not is judged;and when it is found that the SCR emission-reduction system is abnormal, a signal is sent back to an ECU system of a whole vehicle in time, and the power of the engine is limited through an ECU of the whole vehicle. By adoption of the SCR emission-reduction detection control system for the diesel engine, the working condition of the SCR system can be detected and recoded on board after the dieselengine is started; the system can be matched with an original on-board diagnosis system to form a dual-detection system, so that the detection reliability is ensured; after the diesel engine is started, the system detects and records the working condition of the SCR system on board to control the power of the whole vehicle, and the power of the engine is limited, so that pollution is prevented from further aggravated; and the system can be additionally arranged easily and rapidly based on an existing on-board detection system, an anti-tamper can be achieved to prevent a driver to refitting the system without permission, and thus, reliable operation of the SCR system is ensured.
Owner:CHANGAN UNIV
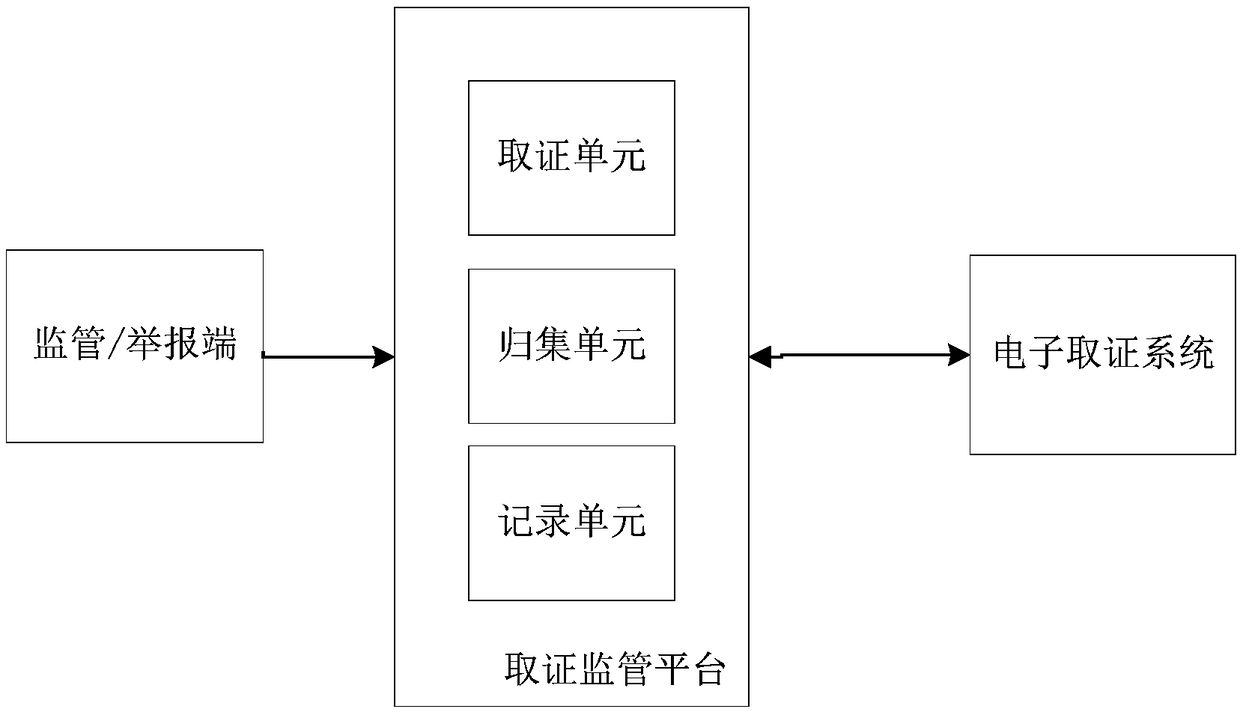
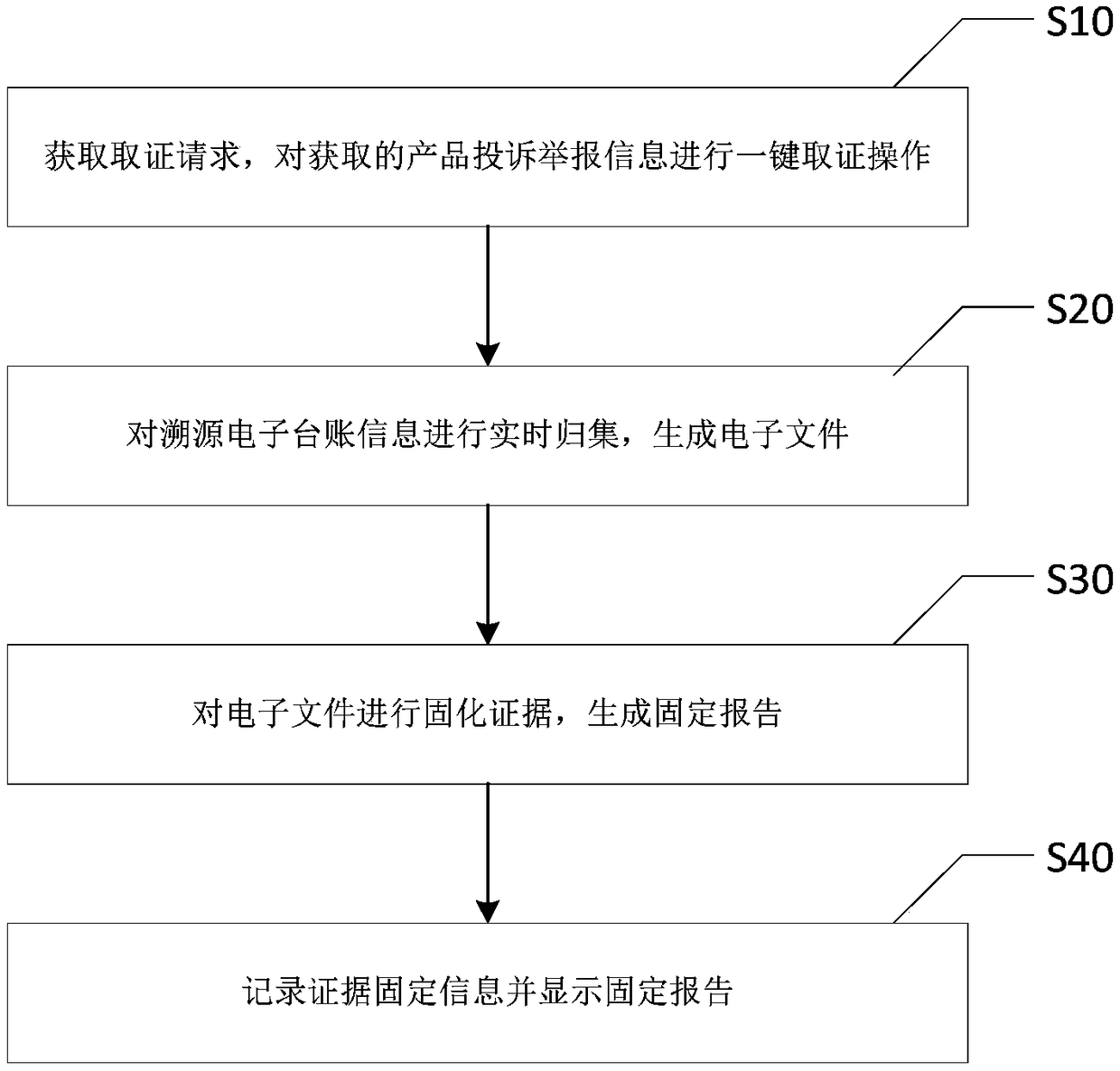
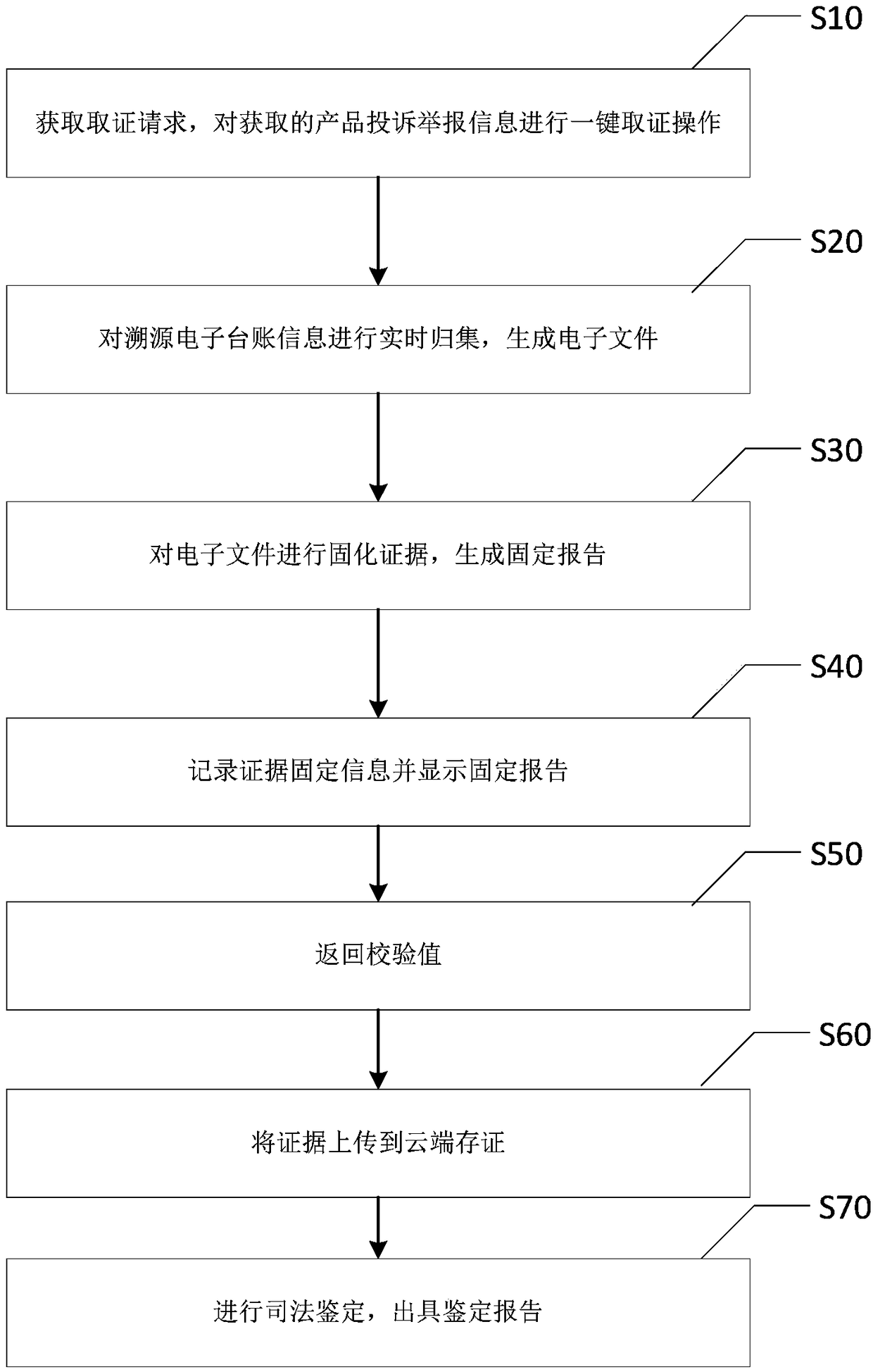
One-click forensics supervision system and method for commodity traceability information
PendingCN108694593AImprove timelinessIncrease authenticityCommerceSensing by electromagnetic radiationThird partyNon destructive
The invention discloses a one-click forensics supervision system and method for commodity traceability information, and relates to the technical field of internet platforms. The system comprises an electronic forensics system for solidifying evidence of received electronic files and generating a fixation report, and also comprises a forensics supervision platform integrated with the electronic forensics system. The forensics supervision platform is used for obtaining a forensics request, performing one-click forensics operations on the obtained product complaint report information, collectingthe traceability electronic account information in real time, generating electronic files and submitting the files to the electronic forensics system, and is also used for recording evidence fixationinformation and displaying fixation reports. Through the application of the system and method, the timeliness of electronic forensics, the authenticity of electronic data, the tamper resistance and the effectiveness of electronic evidence can be improved in the inspection work; non-destructive forensics of electronic forensics is realized, in order to ensure the authenticity of the data; the "original copy" is fixed, to ensure the integrity of the data, to solve the problem that third parties do not cooperate with forensics.
Owner:广州中科易德科技有限公司
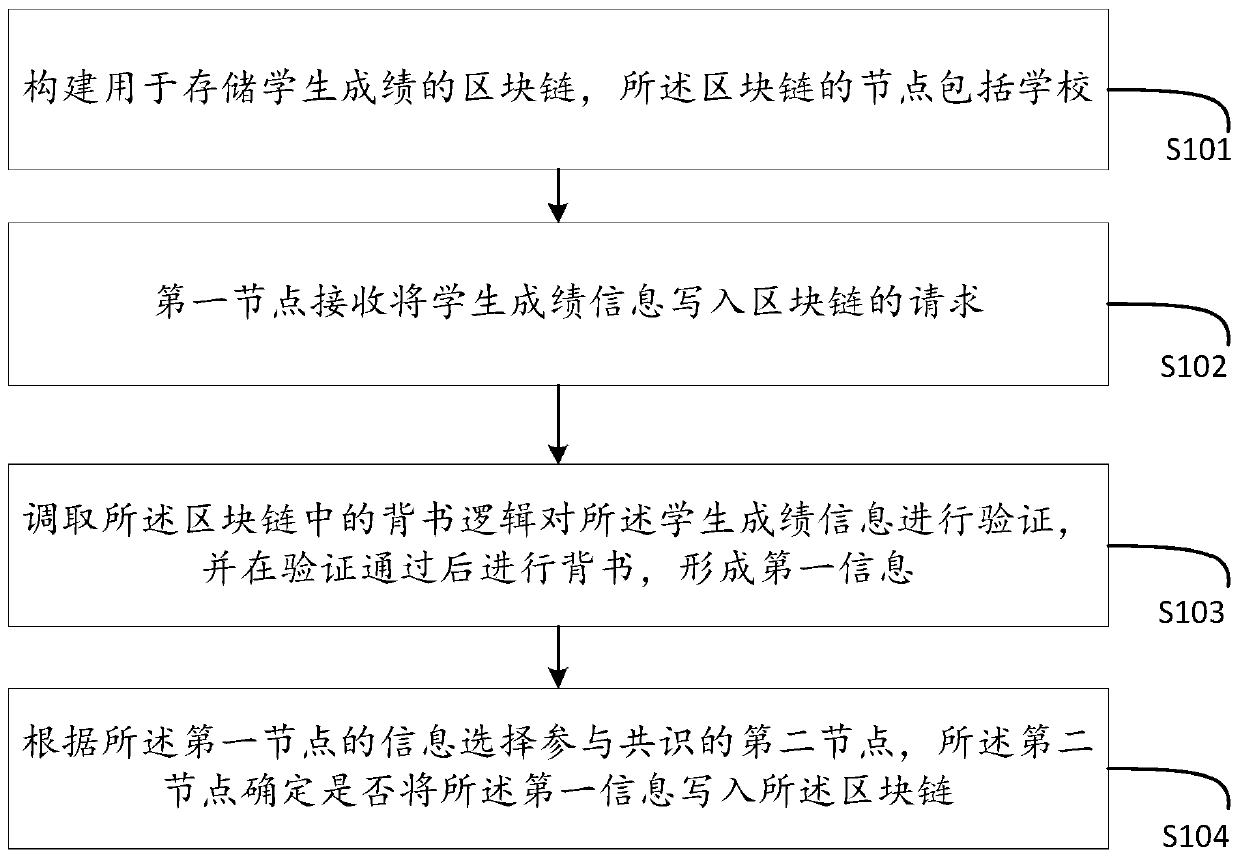
Block chain-based score management method and device and medium
PendingCN111008397AGuarantee authenticityGuaranteed tamper resistanceData processing applicationsDatabase distribution/replicationTamper resistanceData mining
The invention discloses a method and device for managing scores based on a block chain and a medium. The method comprises the steps of enabling a first node to receive a request for writing student score information into the block chain; invoking endorsement logic in the block chain to verify the student score information, and endorsing after the student score information passes the verification to form first information; and selecting a second node participating in consensus according to the information of the first node, wherein the second node determines whether to write the first information into the block chain. According to the method, the characteristic of decentralization of the block chain is utilized; each school reserves one piece of score data; authenticity and tamper resistance of scores are guaranteed; tamper difficulty is increased due to multi-node distributed storage; and the scores of one person in each stage are public and transparent.
Owner:浪潮云洲工业互联网有限公司
Method for fast on-line electronic bid opening
InactiveCN109064297AEnsure safetyGuaranteed tamper resistanceTransmissionCommerceUser authenticationClient-side
The invention discloses a fast on-line electronic bid opening method in the electronic bidding transaction process. The method comprises utilizing digital certificate + Web technology to realize usersign-in on bid opening timeline, online decryption of tender documents, Online bid evaluation process, and the use of digital identity authentication to achieve security, the system uses Web 2.0 three-tier architecture, can support a large number of bidders simultaneously bid opening, bid singing, improve the efficiency of bid opening evaluation more than 20 times, and bidders do not need to go tothe trading center to achieve electronic remote bid opening, greatly reducing the bidder bidding costs. The invention realizes the authentication of the user identity by using the public key algorithm built in the digital certificate through the cooperation of the client end and the server end. As the private key is stored in the digital certificate, it can not be read in any way in theory, so itensures the security of user authentication, and ensures the user sign-in anti-tampering and anti-repudiation.
Owner:宁夏神州好易信息发展股份有限公司
Traceable tamper-proof chip research and development transaction data storage method and system
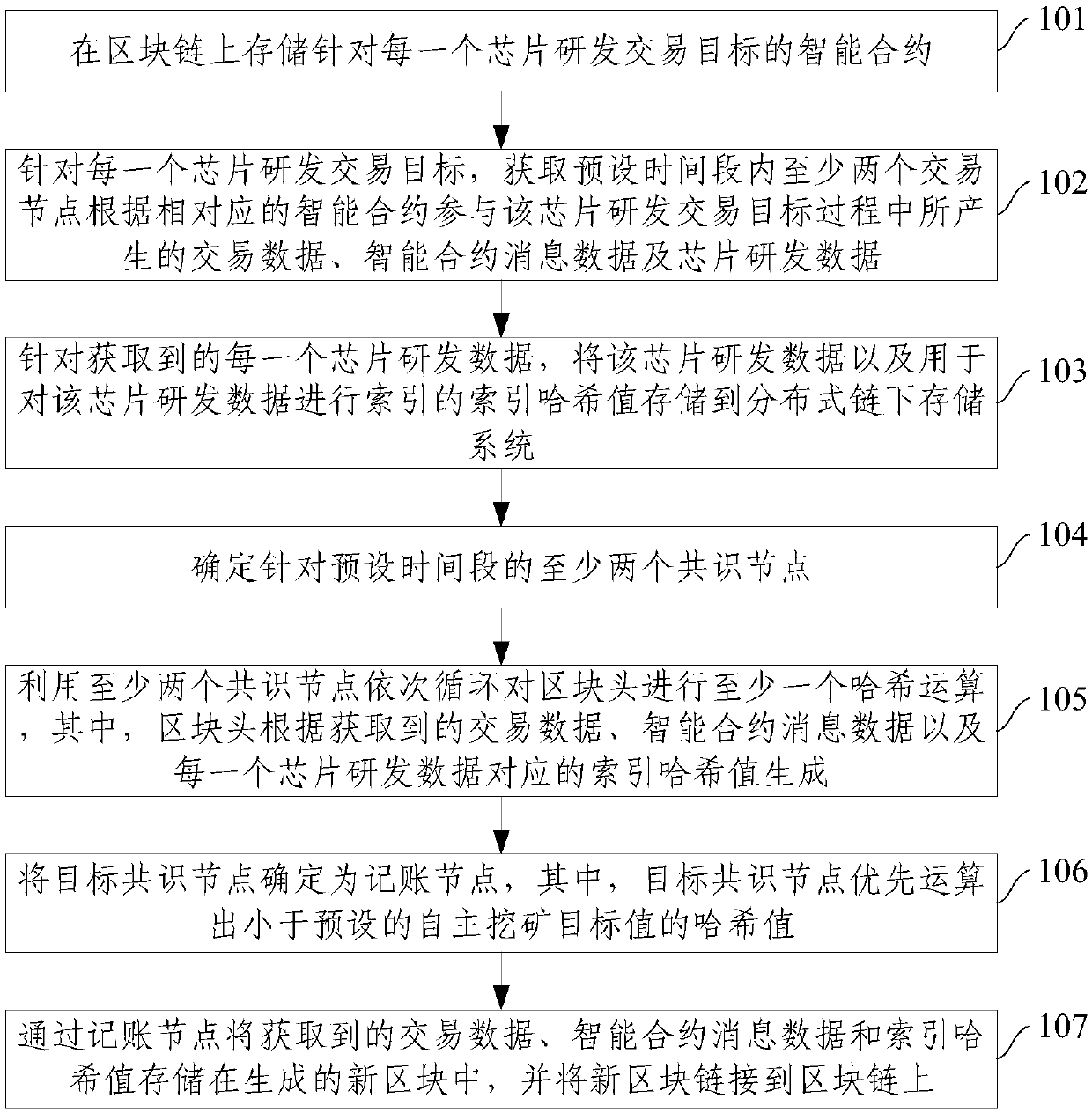
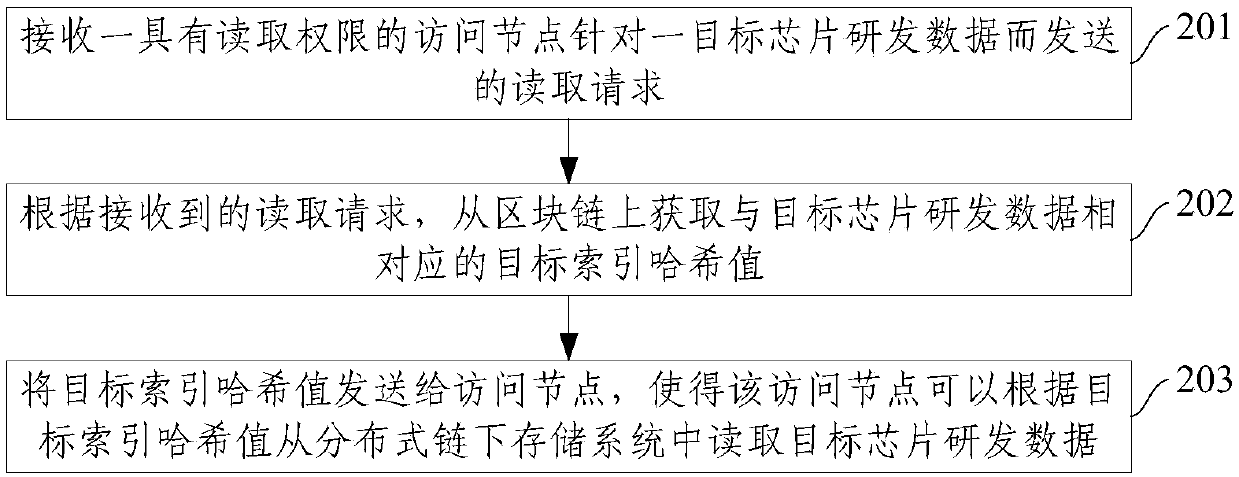
ActiveCN109657501AGuaranteed traceabilityGuaranteed tamper resistanceDigital data protectionTamper resistanceTransaction data
The invention relates to the technical field of data storage. The invention provides a chip research and development transaction data storage method and system. The method comprises the steps of obtaining transaction data, intelligent contract message data and chip research and development data generated by at least two transaction nodes participating in a chip research and development transactiontarget process according to corresponding intelligent contracts in a preset time period; Storing the obtained research and development data of each chip and the index hash value for indexing into a distributed chain storage system; Determining an accounting node from at least two consensus nodes corresponding to a preset time period by using a rapid consensus algorithm; And storing the obtained transaction data, the intelligent contract message data and the index hash value in the generated new block through the accounting node, and linking the new block to the block chain. The scheme can enable chip research and development transaction data to be traceable and tamper-proof.
Owner:HANGZHOU KILBYBLOCK CHAIN TECH LTD
Cross-network dynamic service flow verification method and system, storage medium and computing device
ActiveCN112487465APrevent tamperingGuaranteed validityError prevention/detection by using return channelEncryption apparatus with shift registers/memoriesSelf-signed certificateCommon key
The invention discloses a cross-network dynamic service flow verification method and system, a storage medium and computing equipment. The method comprises the steps of uploading node address information and a public key to a blockchain through a PBFT consensus mechanism, and achieving the network access application of a node and the distributed secret key storage for a self-signature certificate.Aiming at the service request behavior of the node, based on a consensus mechanism of a block chain, the distributed verification node carries out verification, service serial number generation, service abstract uplink storage and service flow permission return on the node identity to realize cross-network service request uplink recording. Aiming at a service completion requirement required by across-network service flow in sequence, real-time service and processing node information are uploaded to a block chain by introducing a service completion identification mechanism, so as to realize effective verification of service continuity. Aiming at the situation that the cross-network service is tampered in the transmission process, a historical routing path tracking technology is utilized to mine malicious network segments possibly existing in cross-network service flow transmission, and the possibility of tampering the service flow again by the malicious network segments is reduced byidentifying bad routing nodes in the retransmission process.
Owner:XI AN JIAOTONG UNIV
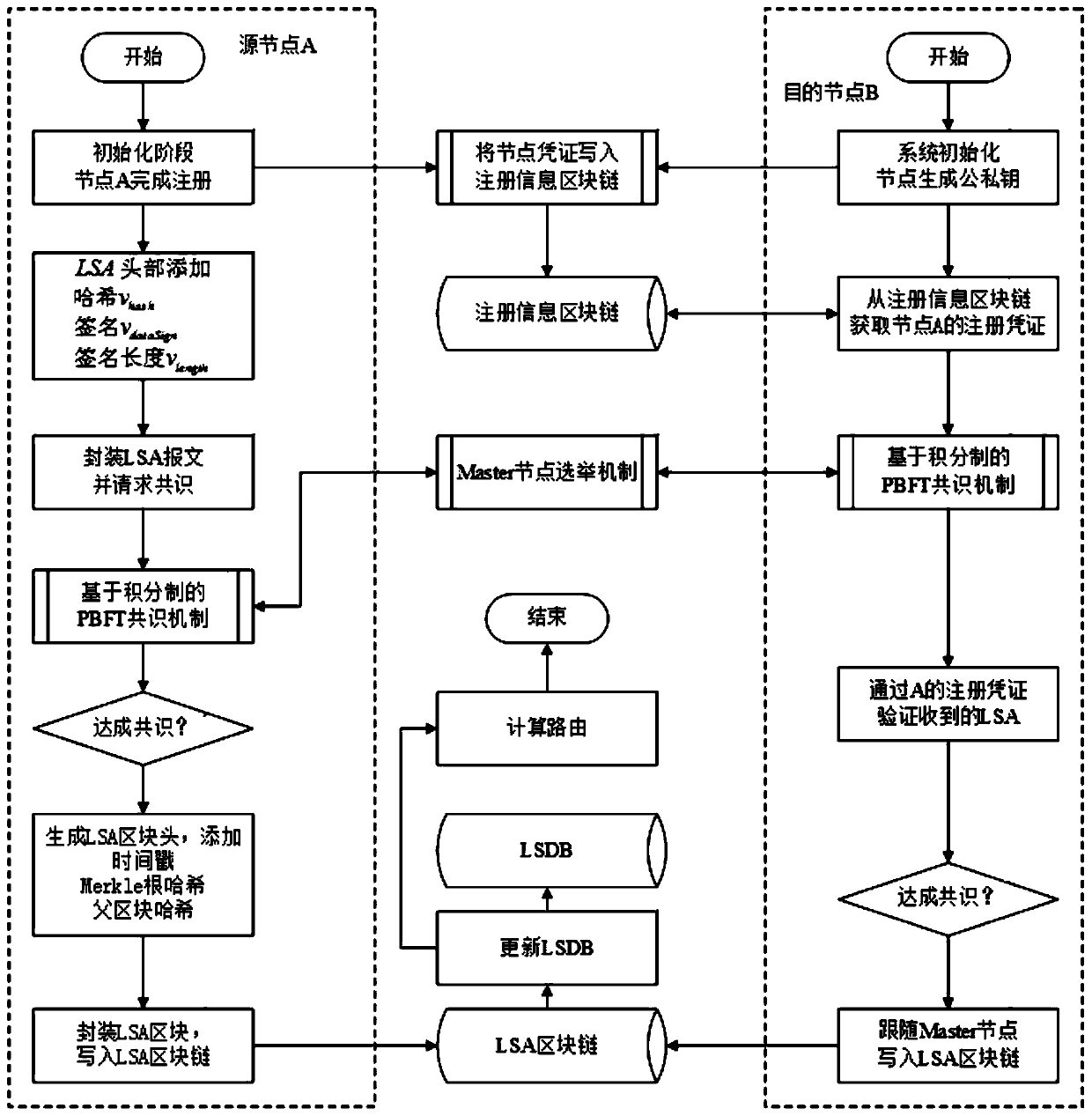
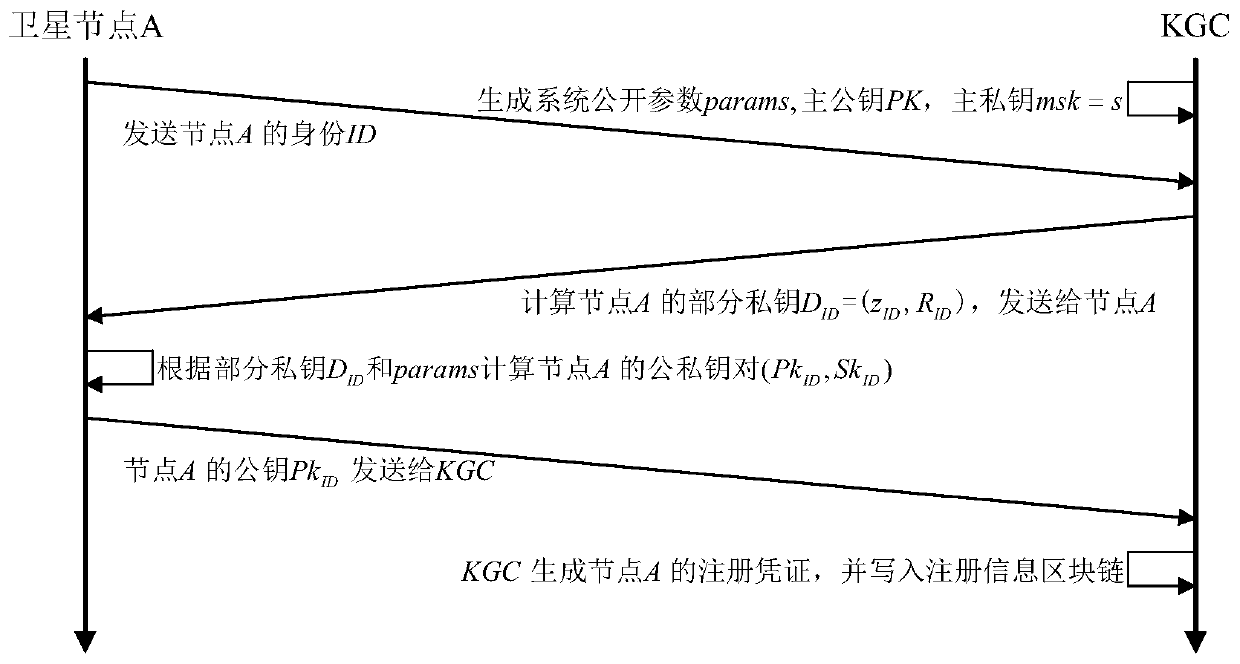
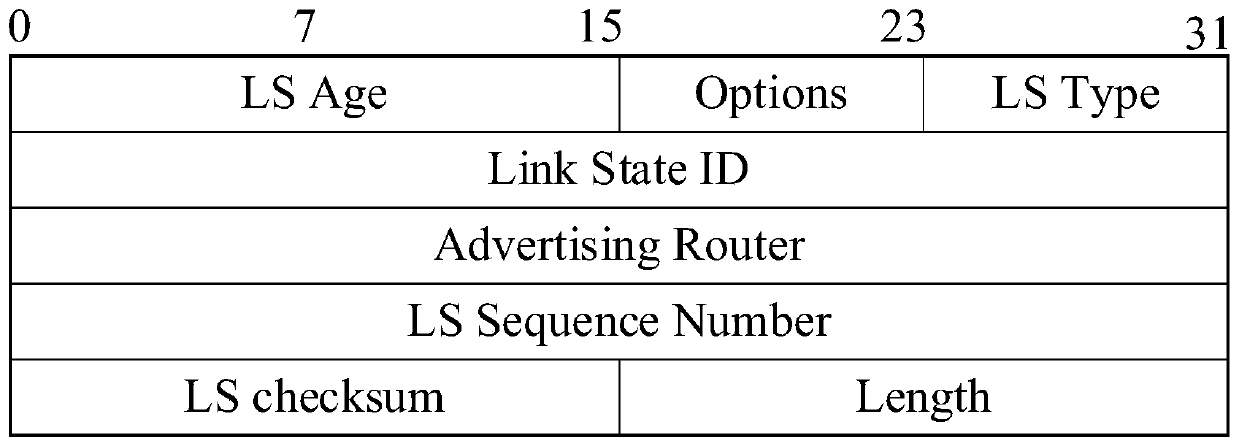
Satellite network security routing method based on blockchain
ActiveCN111314391AAuthenticity and Integrity GuaranteedResists maximum age attack and maximum sequence number attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTelecommunicationsBlockchain
The invention discloses a satellite network security routing method based on blockchain, and belongs to the technical field of communication and is based on the blockchain technology, and the method comprises the following steps: an initialization stage: registering all legal satellite nodes, packaging registration information into a registration information block, and writing the registration information block into a registration blockchain; in the system operation stage, a source node generates an LSA describing the node, signs the LSA, encapsulates the LSA into an LSA block and writes the LSA block into an LSA blockchain; when the destination node writes in a new LSA block, triggering LSDB update (including adding, replacing or deleting LSA) of the destination node, and then calculatinga route by using an SPF algorithm; and when the system detects that unpredictable interruption occurs in a certain link, the KGC sends a request for updating the credentials to the nodes involved inthe link. In this way, the authenticity and integrity of the LSDB can be guaranteed through the LSA blockchain, and then safe and reliable routing is calculated through the LSDB.
Owner:四川九强通信科技有限公司
Electronic commercial acceptance bill financing method and device based on block chain architecture
PendingCN111539724AEnsure transparencyGuaranteed traceabilityFinancePayment protocolsBlockchainSystems engineering
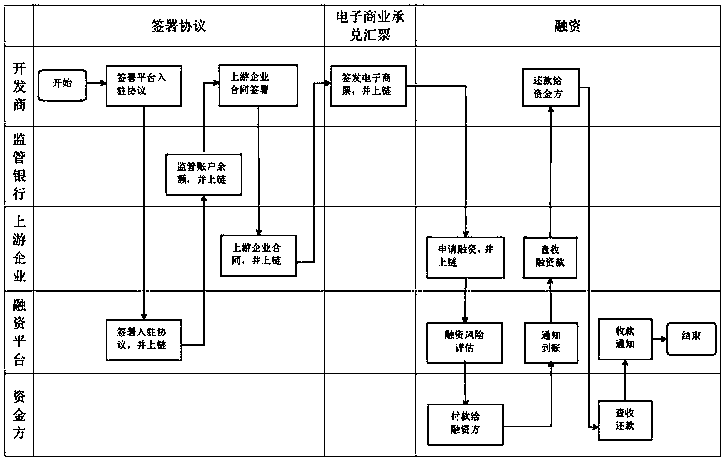
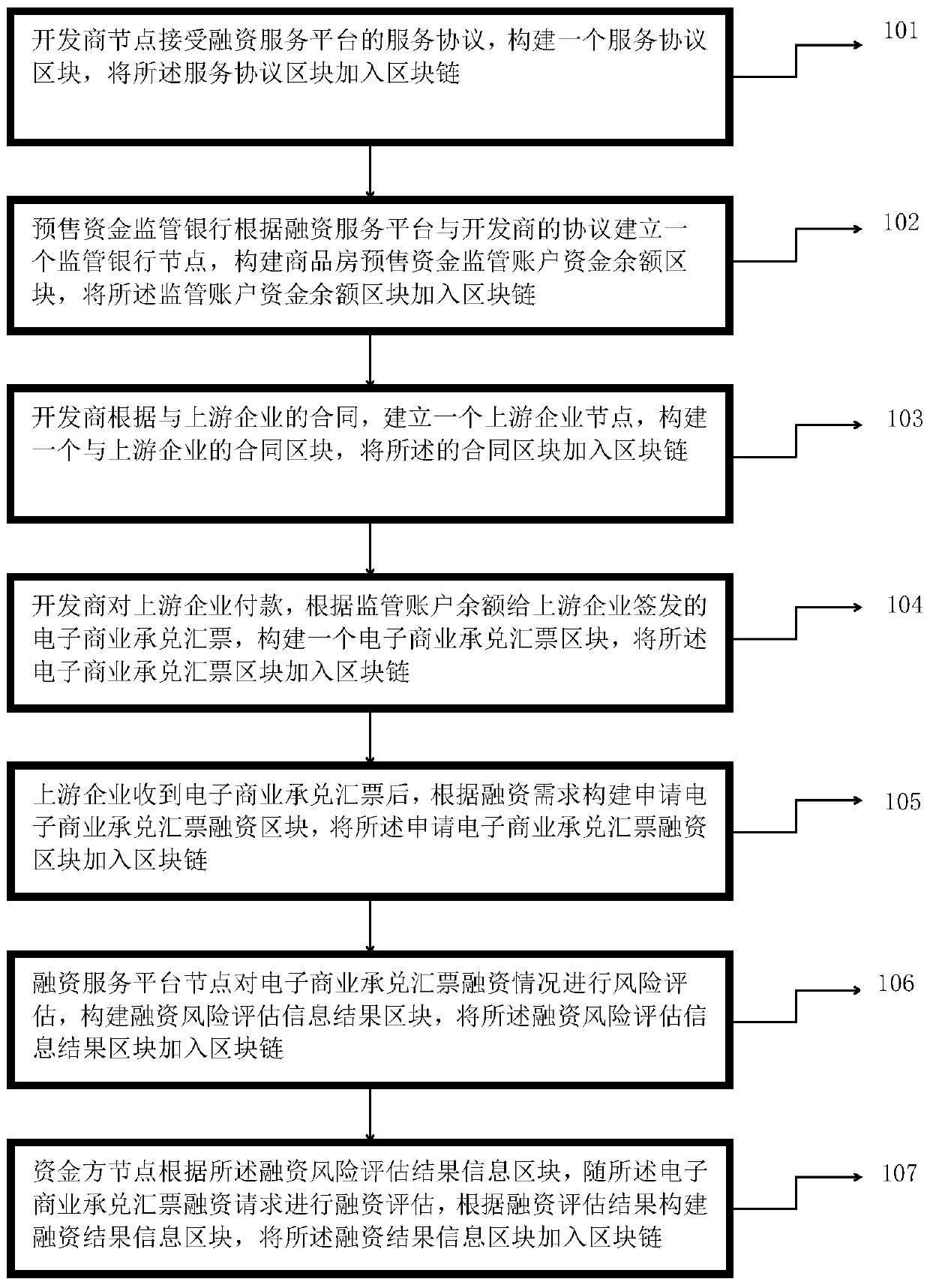
The invention provides an electronic commercial acceptance bill financing method and device based on a block chain architecture. The method comprises the steps that: a developer node adds a constructed service agreement block of a financing service platform to a block chain, and a presale fund supervision bank node adds a constructed developer supervision account fund balance block to the block chain; the developer node adds a constructed contract block with an upstream enterprise into the block chain; the developer node adds a constructed electronic commercial acceptance bill block issued according to the supervision account balance into the block chain; an upstream enterprise node constructs an application electronic commercial acceptance bill financing block according to financing requirements, and adds the application electronic commercial acceptance bill financing block into the block chain; a financing service platform node performs risk assessment on an electronic commercial acceptance bill financing request, and adds a constructed financing risk assessment result information block into the block chain; and a fund party node performs financing assessment according to the financing risk assessment result information block, and adds the constructed financing result information block into the block chain. The above technical scheme improves the security and efficiency of electronic commercial acceptance bill financing, is beneficial to commercial credit billing, and greatly promotes the development of bill market business.
Owner:大宇(深圳)新动能产业投资有限公司
Hierarchical marked distortion-preventing system
InactiveCN1349331AGuaranteed tamper resistanceGuaranteed functionData switching by path configurationSecuring communicationComputer hardwareDigital signature
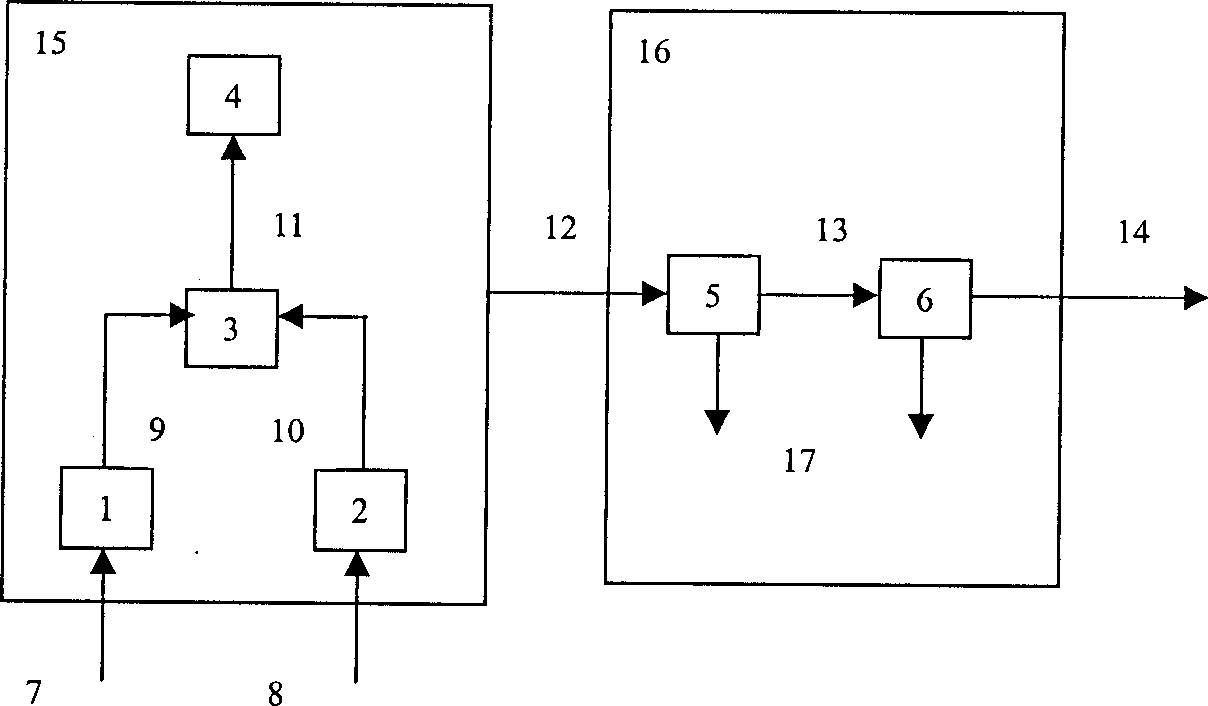
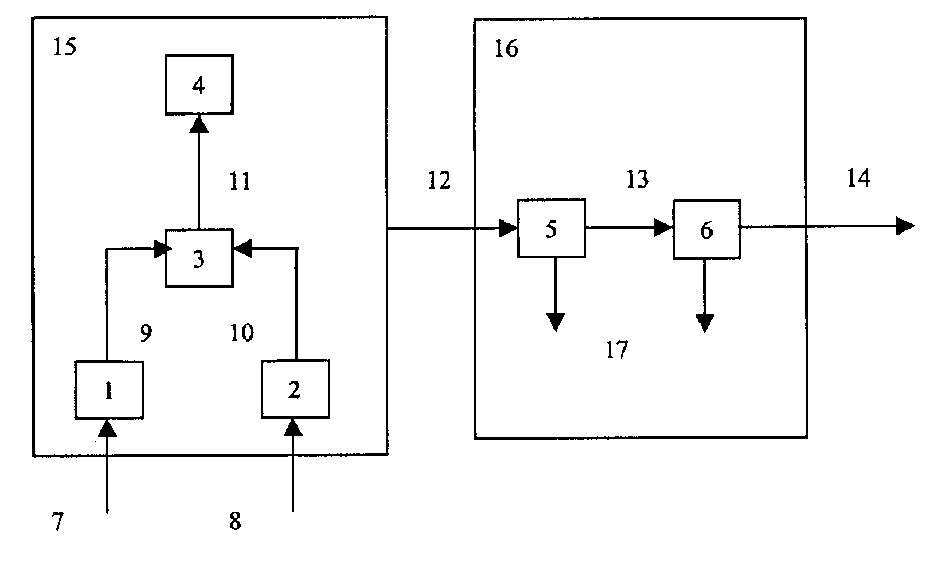
The system comprises information transmitting and receiving ends. The transmitting end consists of a global greation module receiving primary page content and a Harsy algorithm module receiving primary page content which greate global data and harsy data, a character string superimposis receiving global data and Harsy data generates character string and a digital sign module receiving the adding character string generates digital sign data. A stop signal is sent out when the digital sign data is different from Harsy data, otherwise a exact informatino content global is sent out. The global transmitting is sotpped as soon as the stop signal is catched bysystem. The system can find any distortion for graded global and page content to ensure facticity and reliability of graded global.
Owner:SHANGHAI JIAO TONG UNIV
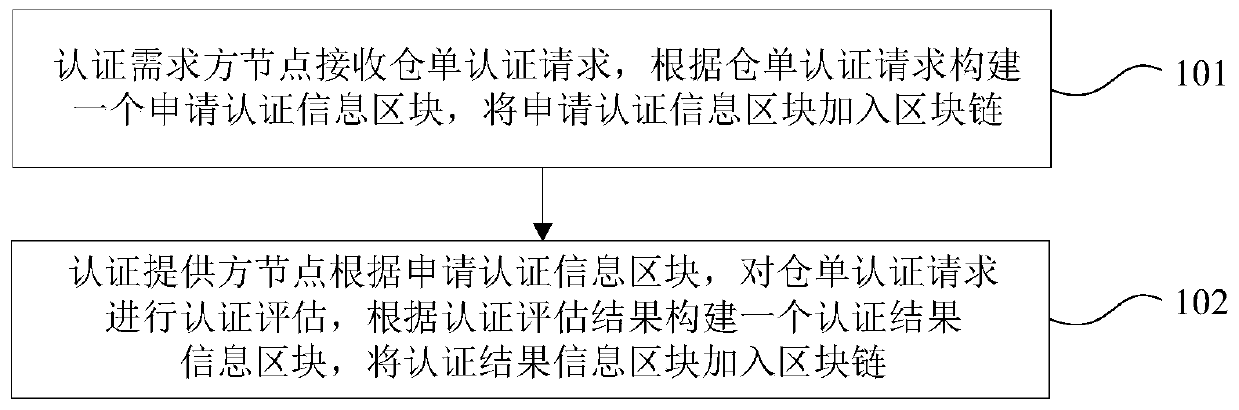
Warehouse receipt authentication method and device based on block chain architecture
PendingCN109784924AImprove securityImprove efficiencyFinancePayment protocolsDemand sideAuthentication information
The invention provides a warehouse receipt authentication method and device based on block chain architecture, warehouse receipt authentication participant nodes form block chain nodes, and the blockchain nodes comprise authentication demander nodes and authentication provider nodes; The warehouse receipt authentication method based on the block chain architecture comprises the steps that an authentication demander node receives a warehouse receipt authentication request, constructs an application authentication information block according to the warehouse receipt authentication request, andadds the application authentication information block into a block chain; And the authentication provider node performs authentication evaluation on the warehouse receipt authentication request according to the application authentication information block, constructs an authentication result information block according to an authentication evaluation result, and adds the authentication result information block into the blockchain. According to the technical scheme, the safety and efficiency of warehouse receipt authentication are improved, and the development of warehouse receipt pledge financing business is greatly promoted.
Owner:CITIC PHOENIX HARBOR SUPPLY CHAIN MANAGEMENT CO LTD
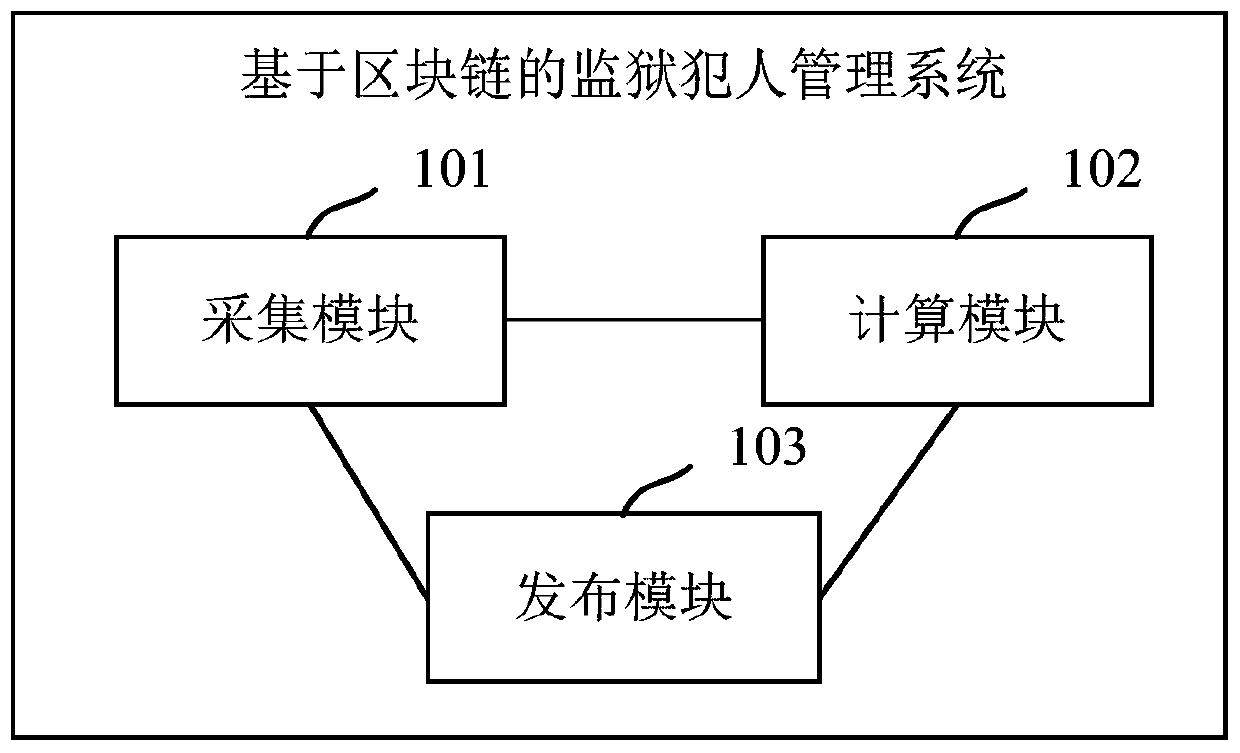
Prisoner management system and device based on block chain, and medium
PendingCN111091485ASentence is normal and smoothEfficient managementDigital data protectionResourcesJail inmateChain network
The invention discloses a prisoner management system and device based on a block chain and a medium. The system comprises an acquisition module used for acquiring criminal penalty information of a prisoner and prize and penalty conditions of the prisoner in a prisoning period; a calculation module which is used for calculating points of the prisoner based on a preset intelligent contract accordingto the criminal penalty information and the prize and penalty conditions of the prisoner; and a publishing module which is used for writing the criminal penalty information, the prize and penalty conditions and the points of the prisoner into a block chain network. Through an integration method, the prisoner can be prompted to obey supervision and compliance management carefully, prisoner relateddata is stored through the blockchain network, it is ensured that the data is not maliciously tampered, the authenticity of the data is ensured, and good management of the prisoner is facilitated.
Owner:浪潮云洲工业互联网有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com