Vehicular ad-hoc network data security sharing and storage system based on blockchain technology
A vehicle-mounted self-organization and network data technology, applied in digital transmission systems, services based on specific environments, security devices, etc., can solve problems such as low efficiency, network congestion, and vulnerability to security attacks, so as to improve efficiency and prevent leakage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0057] Example 1. Digital signature technology.
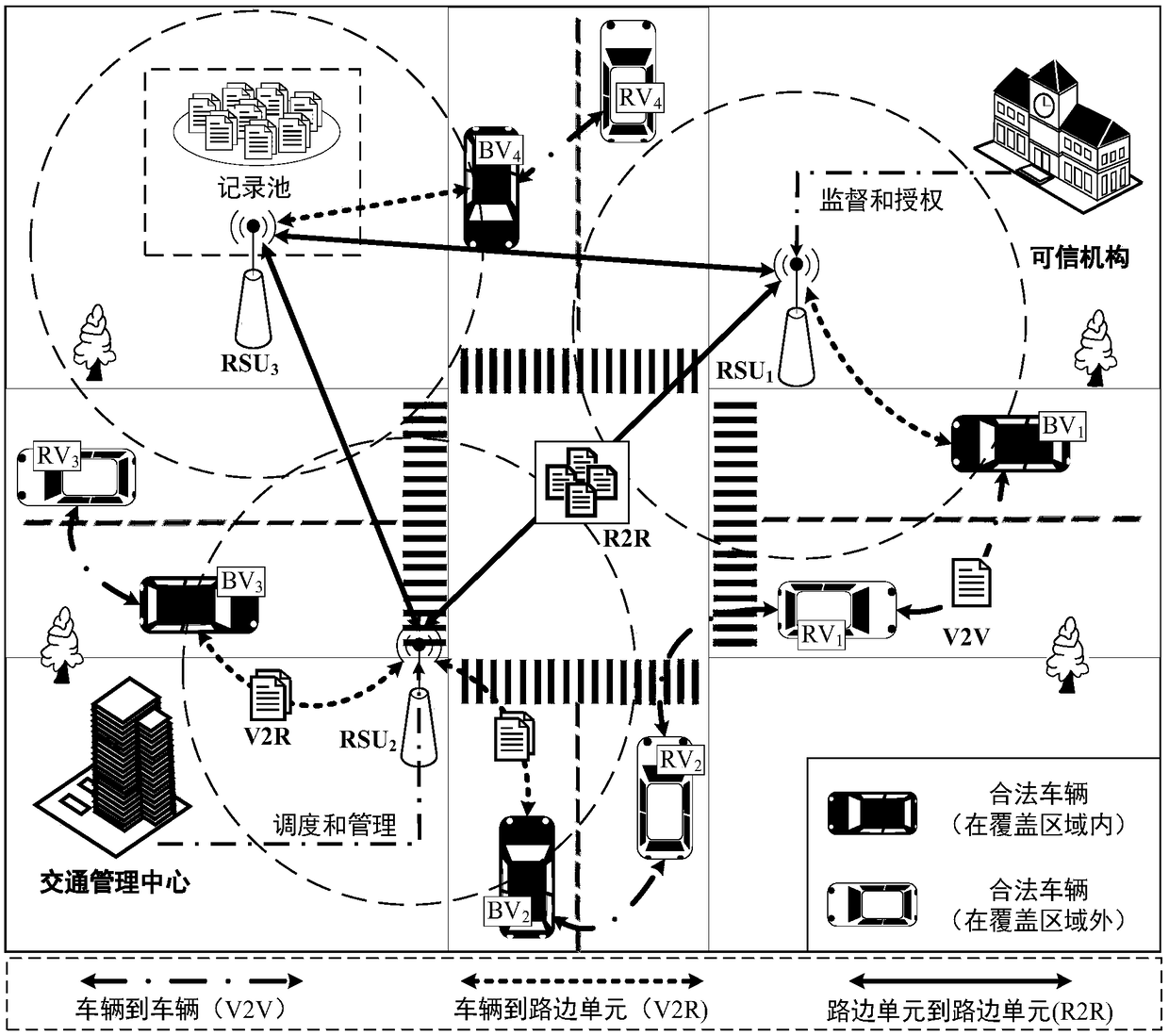
[0058] The invention involves a large number of vehicles for data sharing, which can easily be monitored and forged in the process of information interaction. The system needs a safe privacy protection method to ensure the accuracy of information and tamper-proof. The basic information from the vehicle node must be authenticated and integrity checked before it can be authorized. Otherwise, the attacker can replace the data or even fake other vehicles to broadcast the wrong information. Therefore, the digital signature technology based on elliptic curve bilinear pairing properties is used in the alliance chain to perform batch anonymous authentication on the message transmission in the vehicle ad hoc network. Corresponding (S02) and Figure 4 , The specific steps of digital signature will be described in detail below.
[0059] (1) Pre-distribution stage
[0060] Vehicle nodes and roadside unit nodes need to be registered with trus...
Embodiment 2
[0104] Example 2. The establishment of blockchain data blocks.
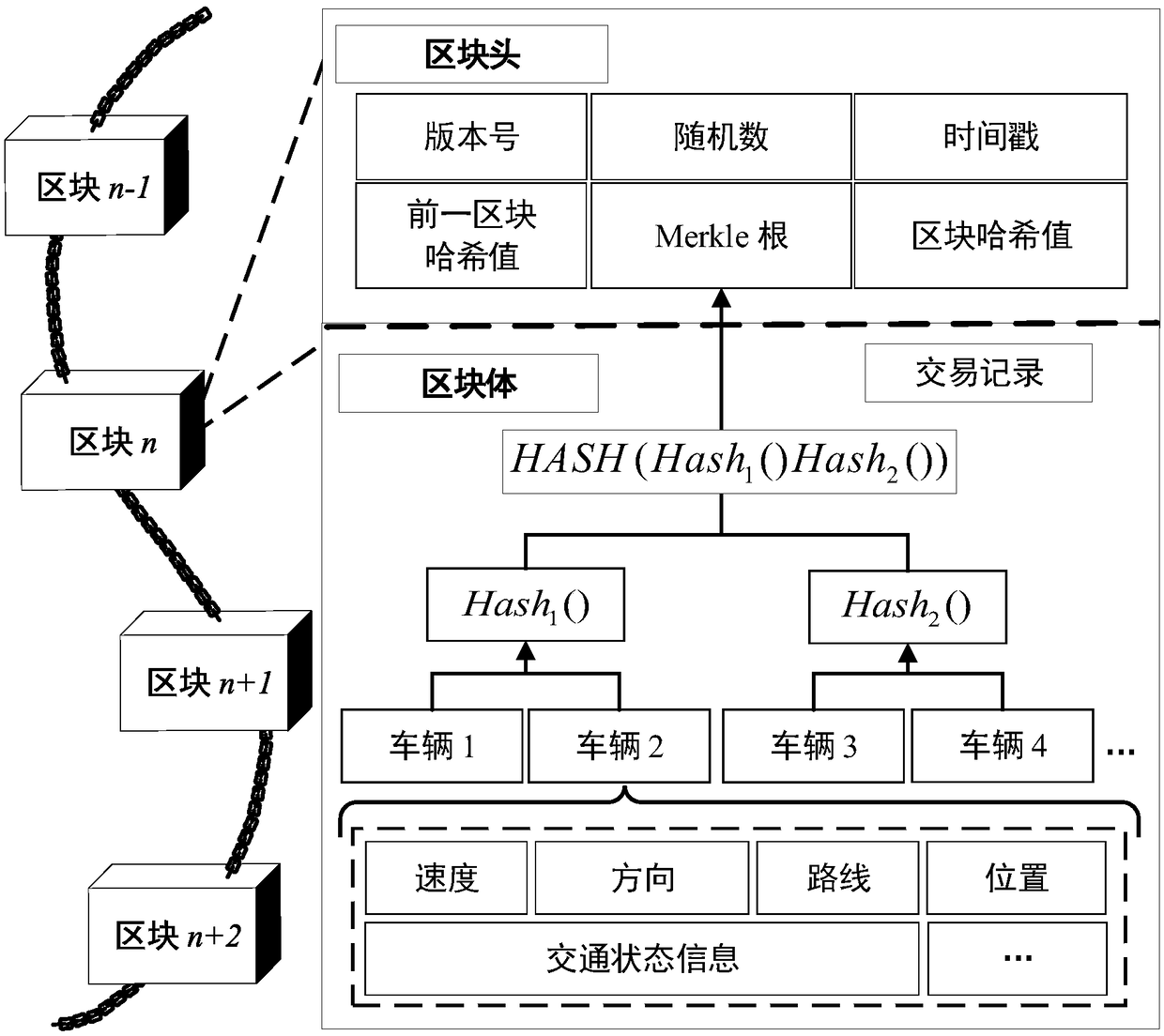
[0105] The billing node of the roadside unit of the alliance blockchain of the present invention is responsible for collecting the interactive information uploaded by the vehicle within a certain period of time into the local storage device. Encrypt and digitally sign these records, and then organize them into blocks, such as (S04). figure 2 It is the block chain structure of the present invention. In order to make the data traceable and tamper-proof, each block contains the encrypted hash value of the previous block. Similar to the Bitcoin system, the accounting node needs to find a hash value that meets a certain difficulty to provide effective proof of work.
[0106] The data block is generally composed of a block header and a block body. The block header contains information such as the current version number, the solution random number of the current block consensus process, the value of the timestamp and the ...
Embodiment 3
[0109] Example 3. The realization of the consensus process.
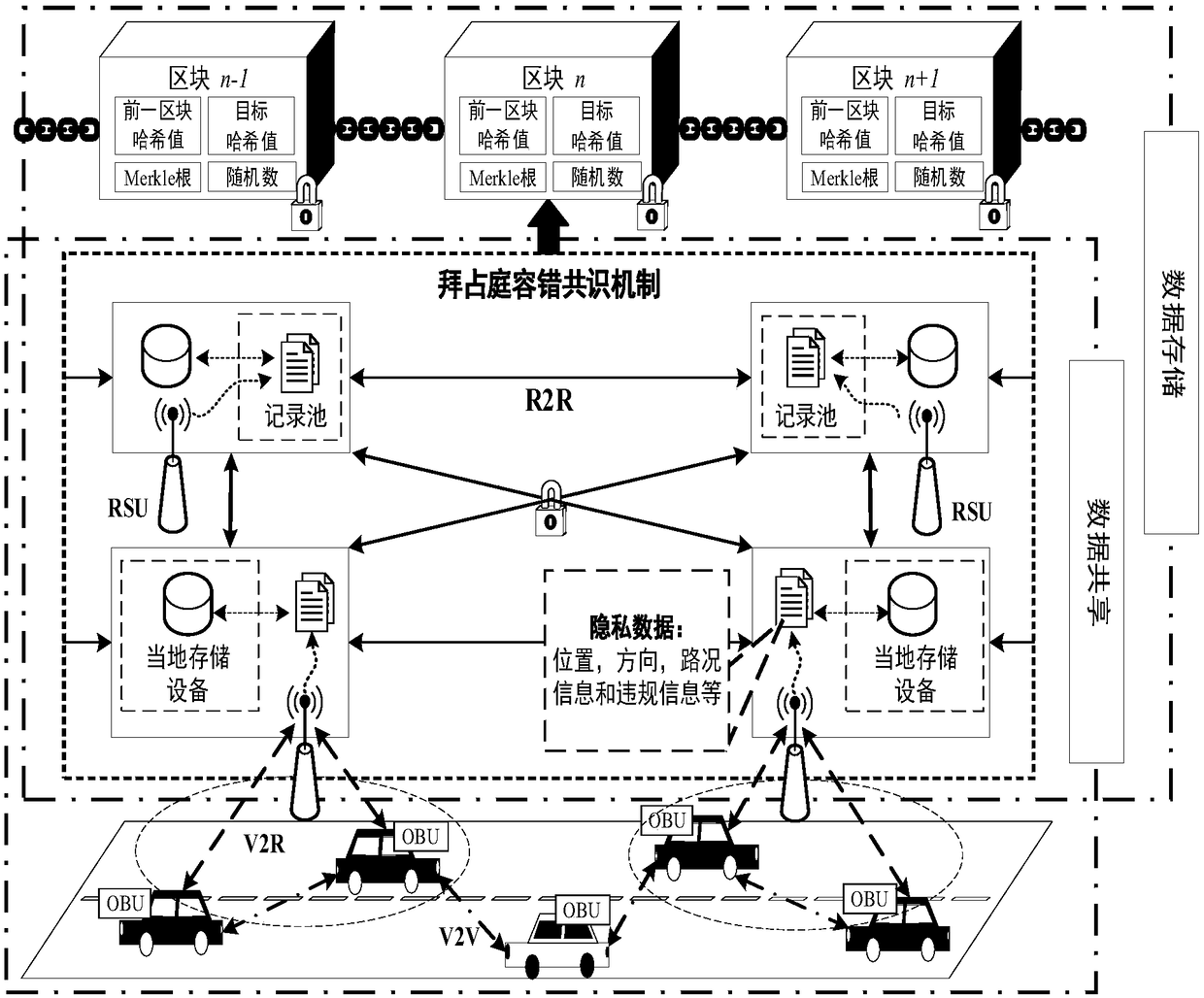
[0110] The Practical Byzantine Fault Tolerance (PBFT) consensus mechanism is adopted in the alliance blockchain in the present invention. The consensus process is jointly completed by ordinary roadside unit nodes and leader (denoted as Leader) roadside unit nodes. Leader is the master node in the consensus process, and other common roadside unit nodes are slave nodes, such as (S05). Figure 5 It is a flowchart of the consensus process of the present invention. The leader broadcasts the collected data blocks to the slave nodes for verification and review. Among the abnormal slave nodes, there are generally malicious nodes and faulty nodes, and their behavior is that they do not respond to requests from other nodes. Suppose the total number of nodes in the network is n, and the number of abnormal nodes is f. The system uses the PBFT consensus algorithm to allow a maximum of abnormal nodes with f=(n-1) / 3 to exist, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com