Patents
Literature
161results about How to "Guarantee authority" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
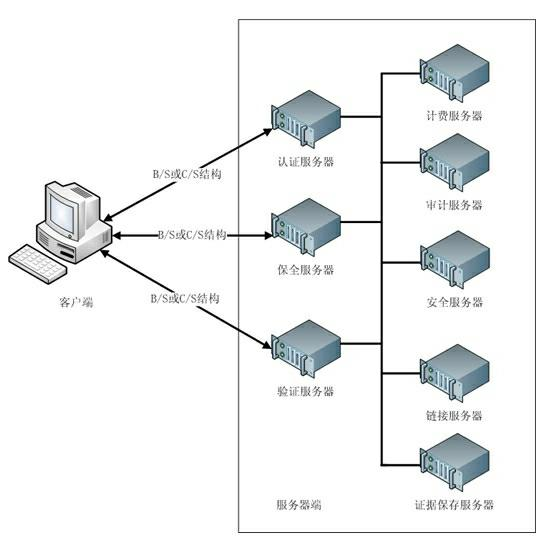
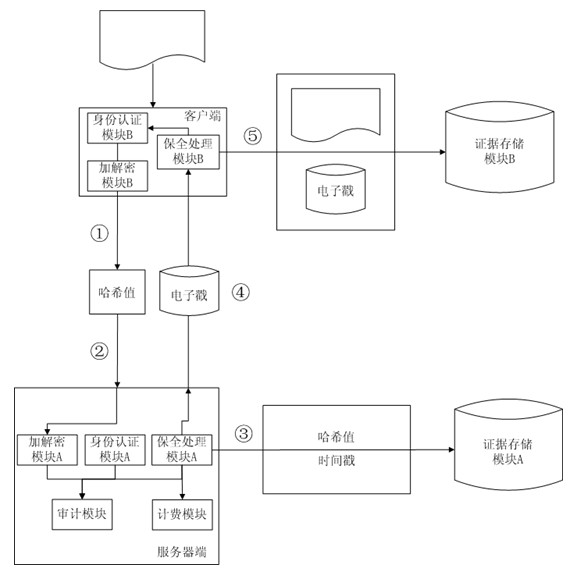
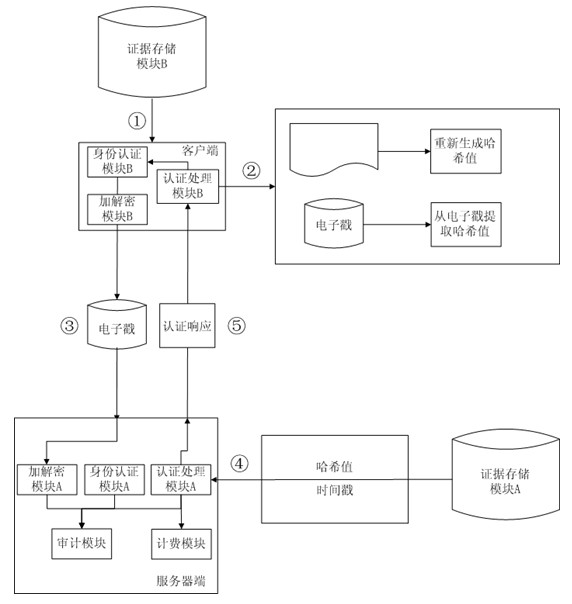
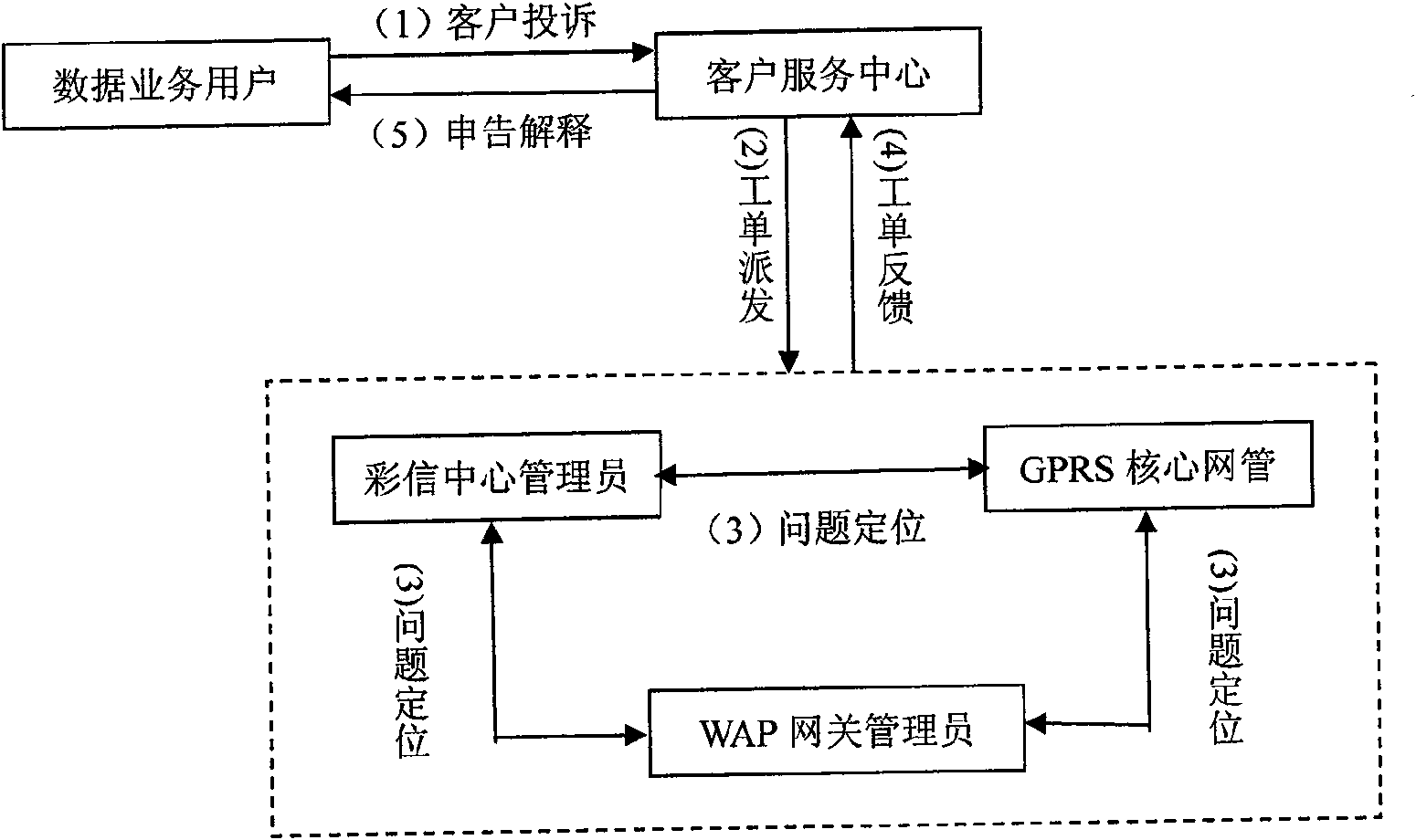
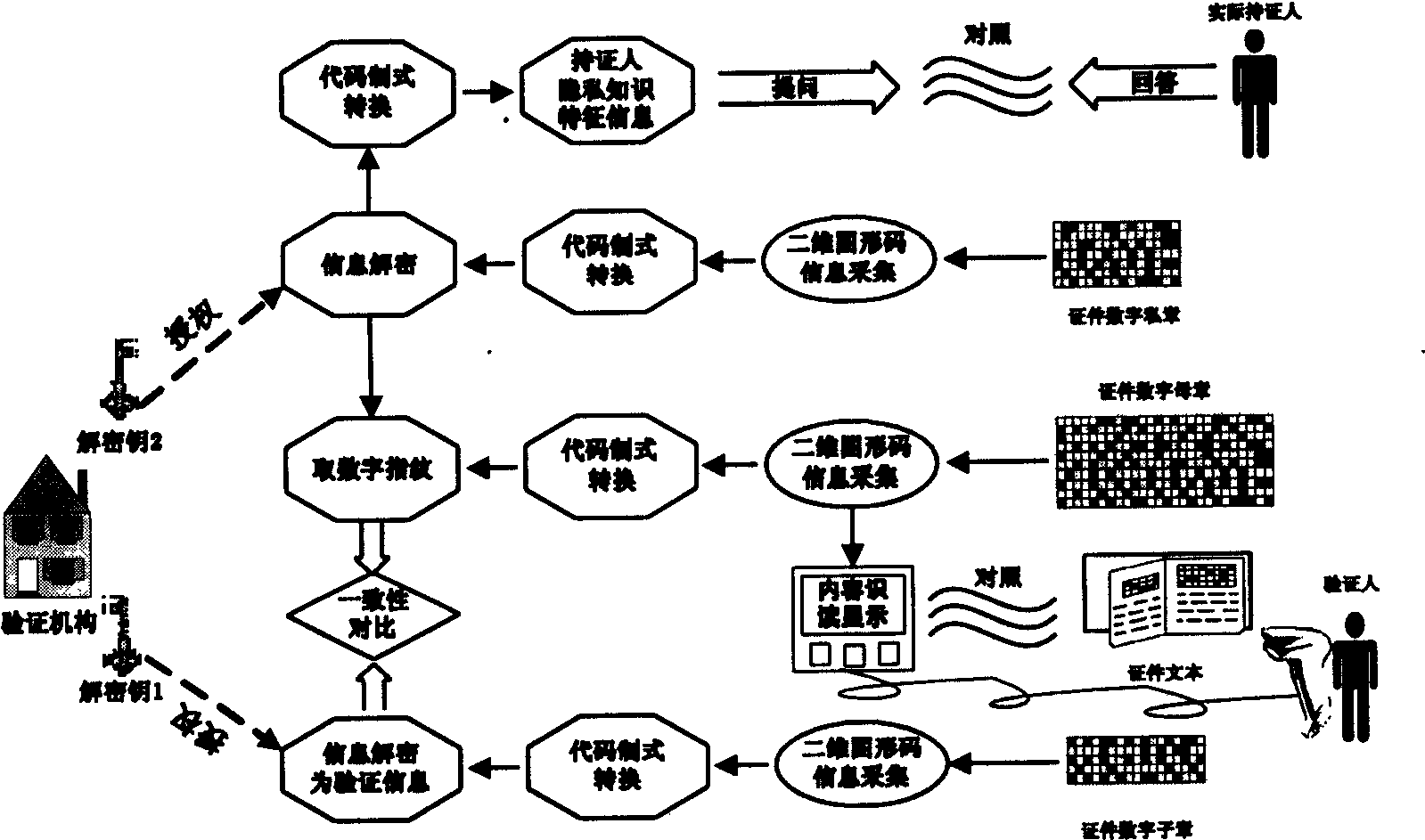
Third-party authentication security protection system and third-party authentication security protection method based on online security protection of electronic evidence
InactiveCN102223374AGuaranteed to be objective and trueGuaranteed reasonablenessUser identity/authority verificationThird partyInformation processing
The invention discloses a third-party authentication security protection system and a third-party authentication security protection method based on the online security protection of an electronic evidence and relates to an information processing technology of a computer. The method comprises the following steps that: after sending a security protection request to a server side, a client side generates a Hash value associated with electronic data which is subjected to security protection and transmits the Hash value to the server side for storage; the client side sends an authentication security protection request, and the server side compares a client side Hash value which is stored in the system with the Hash value which is transmitted by the client side to judge whether the security protection behaviors of the client side are objective and real; communication between the client side and the server side is encrypted by using a secure cryptographic algorithm; the server side carries out association processing on all Hash values in the system to ensure that the Hash value which is stored in the server side and associated with the electronic data cannot be falsified; and when the used cryptographic algorithm is decoded, the client side applies for updating of security protection, and carries out security protection processing on data to be required for security protection and result data generated by the last security protection application again so as to ensure the continuous security of the system.
Owner:重庆兴际云大数据科技有限公司
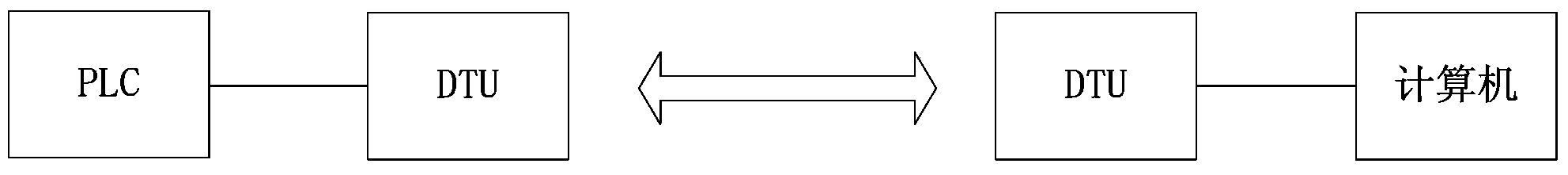
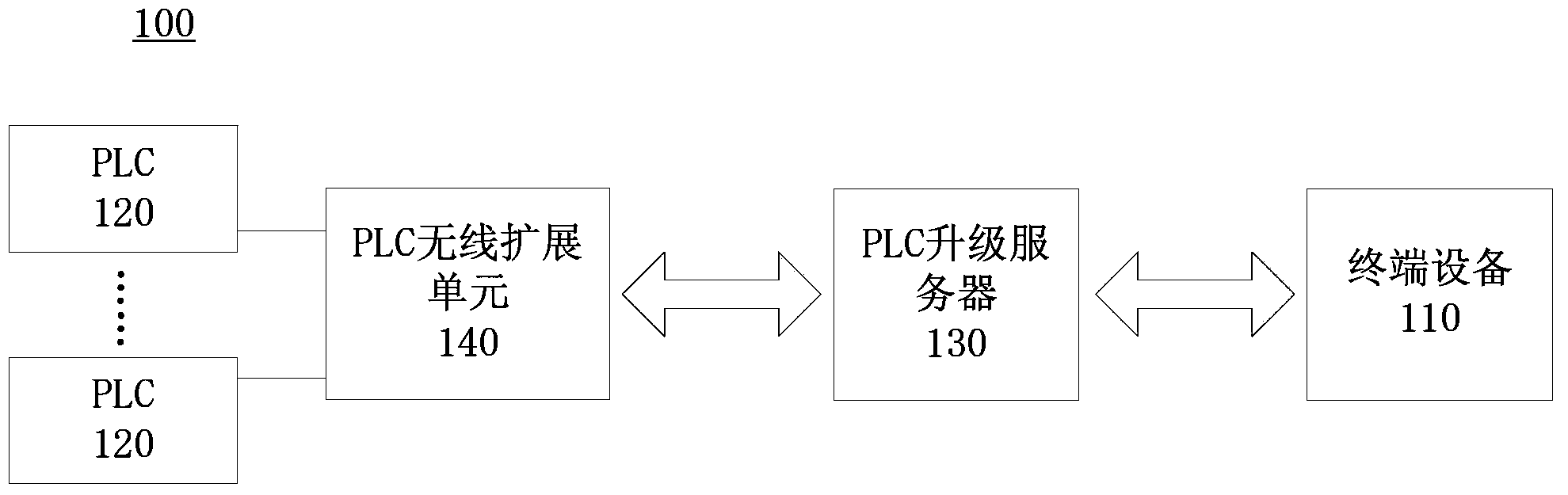
Method and system for remote upgrade of PLC (Programmable Logic Controller)
ActiveCN103414741AAchieve upgradeFast data transferProgram loading/initiatingData switching networksProgrammable logic controllerTerminal equipment
A method and a system for a remote upgrade of a PLC (Programmable Logic Controller) are provided by the invention. The system includes a terminal device, one or more PLCs, a PLC update server and a PLC wireless extension unit. The method comprises the steps: S1, the terminal device transmits an upgrade instruction to the PLC wireless extension unit through the PLC update server; S2, the PLC wireless extension unit downloads an upgrade file instructed by the upgrade instruction from the PLC update server; and S3, the PLC wireless extension unit uses the downloaded upgrade file to upgrade a target PLC instructed by the upgrade instruction. In the system, the data transmission speed is fast; and the use of safe, reliable protocol is allowed in the system to complete the remote upgrade of the PLC.
Owner:SUZHOU INOVANCE TECH CO LTD
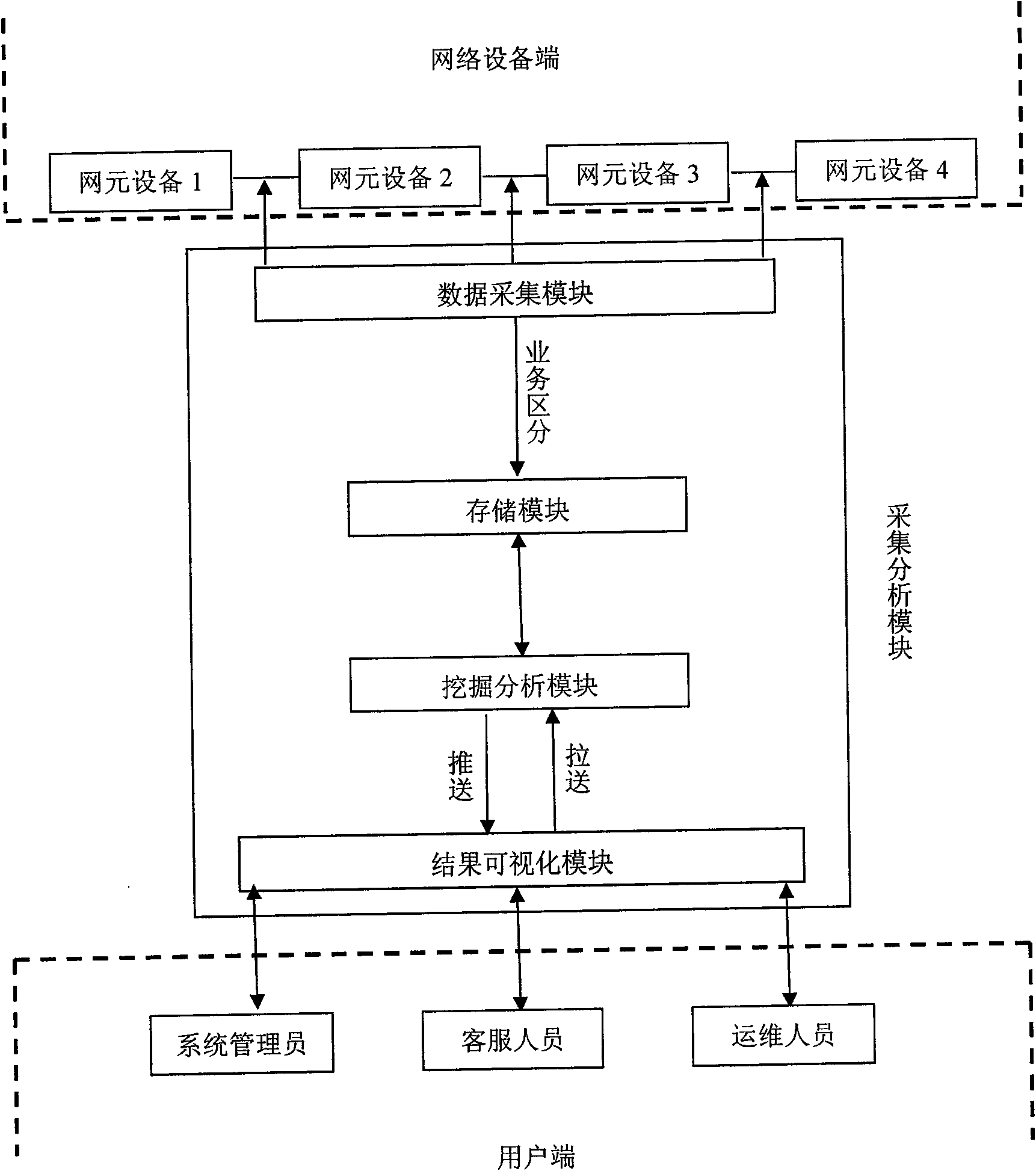
Mobile data service monitoring analysis system and implementation method thereof
InactiveCN101616428AGuarantee authorityData switching networksSpecial data processing applicationsService modelReal time services
The invention discloses a mobile data service monitoring analysis system and an implementation method thereof. The invention carries out service differentiation through packet-based real-time mining analysis, which can not only meet the operation and maintenance requirements of the routine network maintenance personnel but also automatically and timely carry out system performance evaluation, service fault discovery and elimination, equipment and terminal fault exploration, service model and user behavior statistics, etc. The system comprises a network device terminal, an acquisition and analysis model and a client; wherein, the acquisition and analysis model is the core model of the system and mainly completes acquisition, processing, analysis and exploration, visualization and the like of the real-time service data. The system and implementation method thereof of the invention reduce the operation and maintenance cost and greatly improve the service maintainability.
Owner:BEIJING XIECHENGZHIYUAN NETWORK TECH
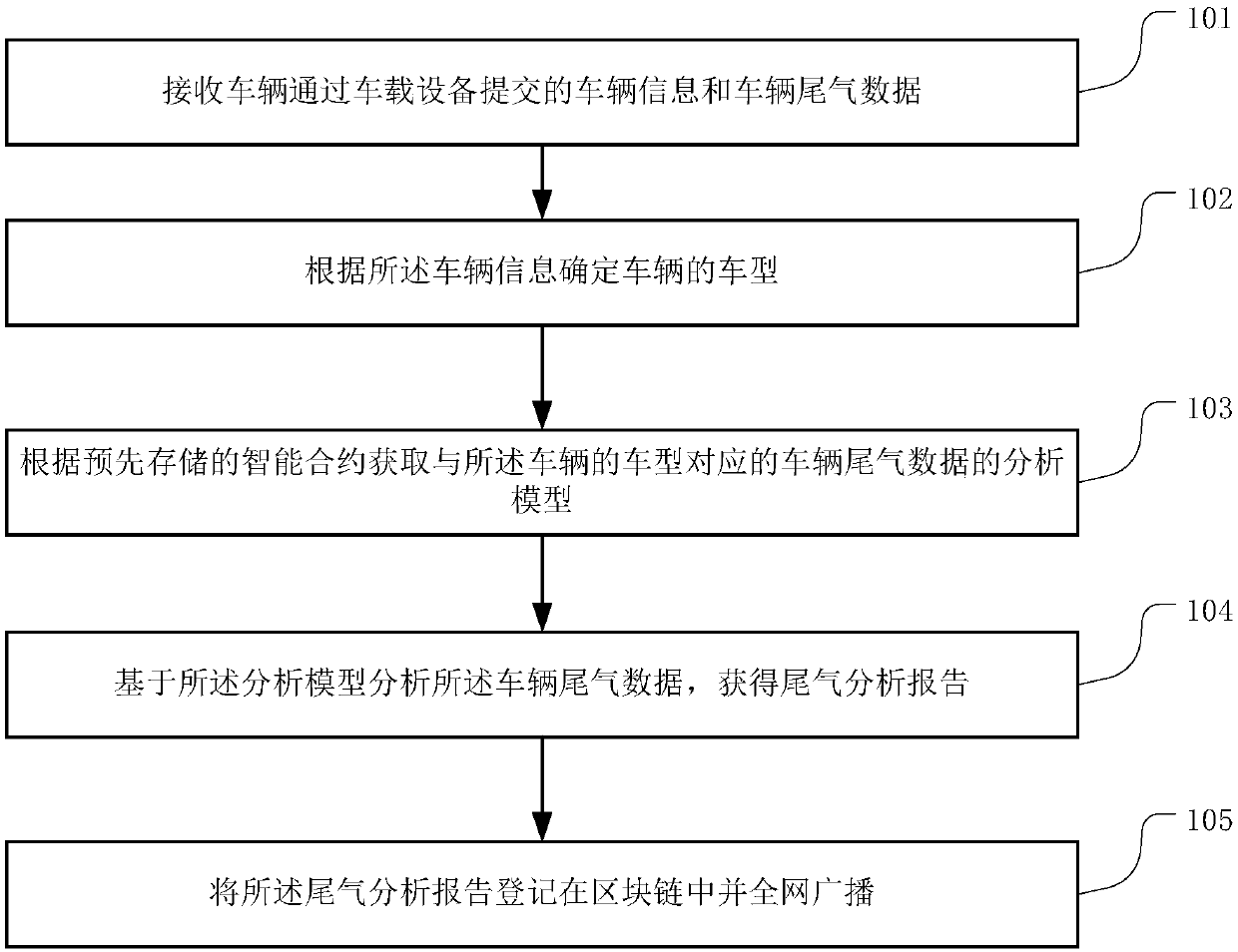
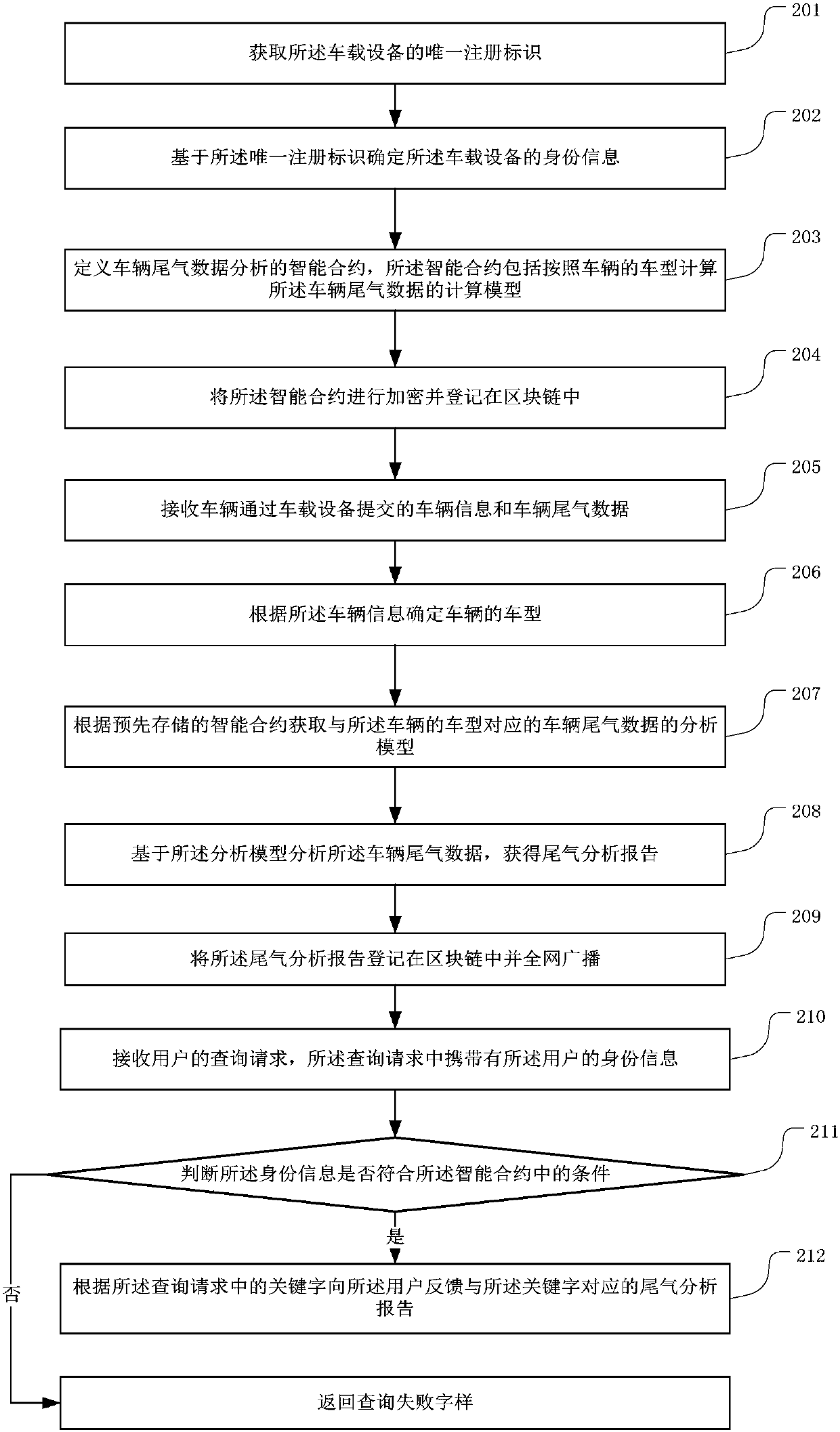
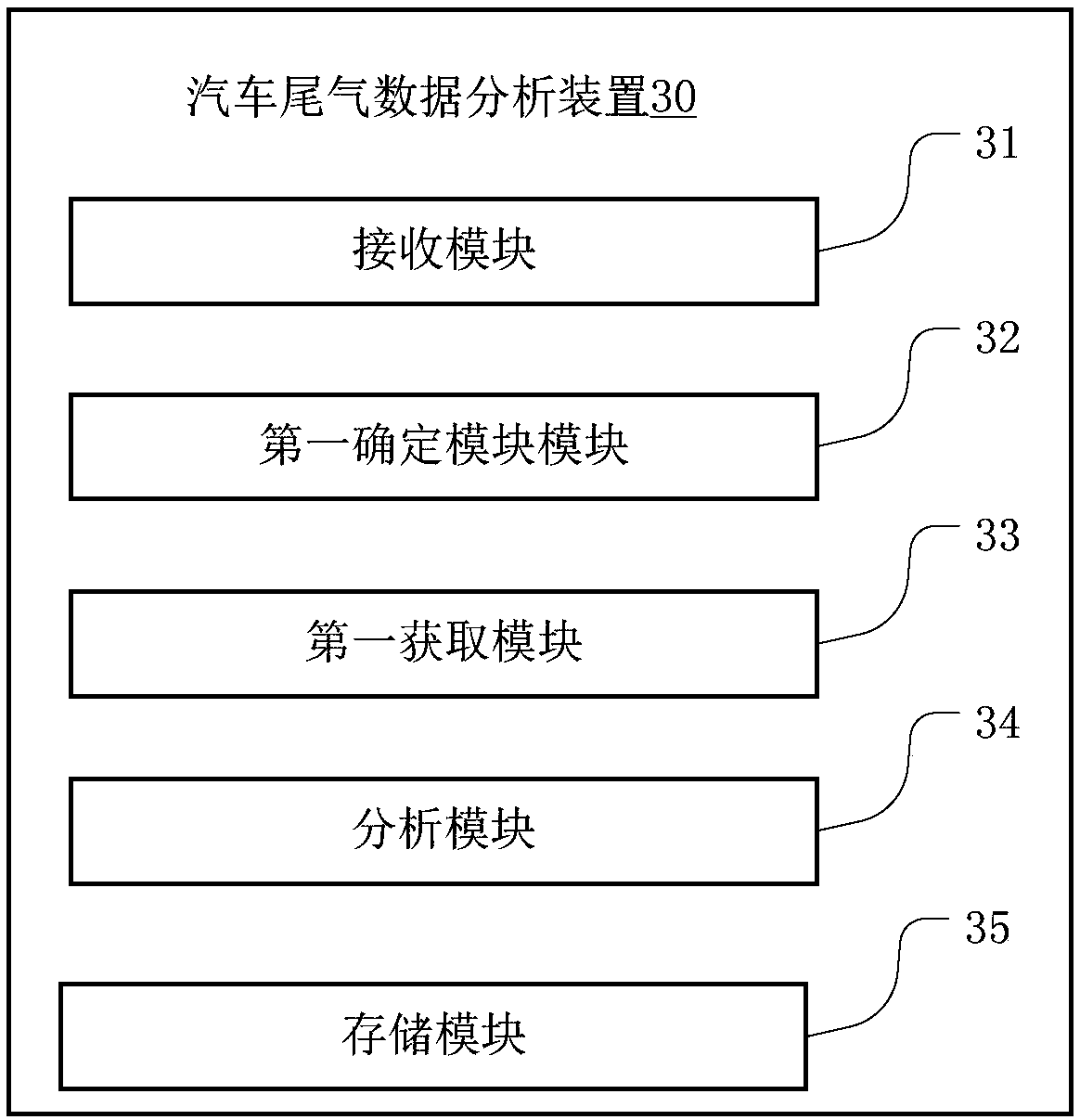
Block-chain-based vehicle exhaust gas data analysis method and device, and server
InactiveCN107945090AGuarantee authenticityGuarantee authorityData processing applicationsSmart contractBroadcasting
The invention relates to the technical field of block chains and provides a block-chain-based vehicle exhaust gas data analysis method and device, and a server. The method comprises: receiving vehicleinformation and vehicle exhaust data submitted by a vehicle through a vehicle-mounted device; determining a vehicle model of the vehicle according to the vehicle information; acquiring an analysis model of vehicle exhaust data corresponding to the vehicle model of the vehicle according to a pre-stored smart contract; and analyzing the vehicle exhaust data based on the analysis model and obtainingan exhaust gas analysis report; and registering the exhaust gas analysis report in a block chain and carrying gout full-network broadcasting. According to the invention, the analysis model of the exhaust gas data corresponding to the vehicle model is obtained from the smart contract, the exhaust gas data uploaded by the vehicle-mounted device are analyzed, and the exhaust gas analysis report is obtained; and the reported is registered in the block chain and is broadcasted in the full network. Because of the exhaust gas data provided by the vehicle-mounted device, the authenticity of the exhaust gas data is ensured; and the exhaust gas analysis report is stored in block chain mode and can not be tampered, so that the authority of the exhaust gas analysis result is ensured.
Owner:GOLO IOV DATA TECH CO LTD
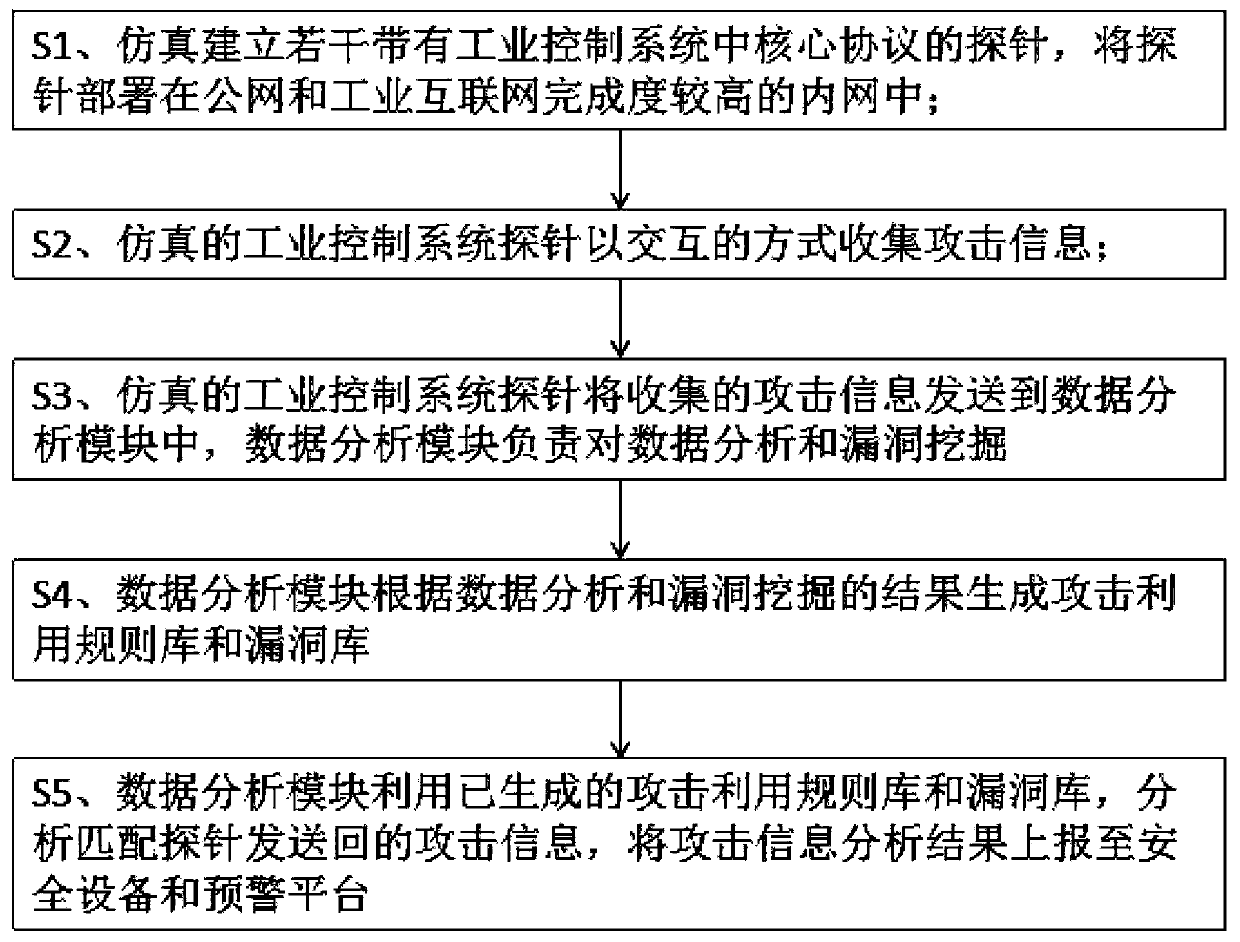
Industrial control system vulnerability trend analysis and early warning method and system
ActiveCN109818985AFix hidden vulnerabilities in a timely mannerAvoid production accidentsData switching networksInformation analysisPublic network
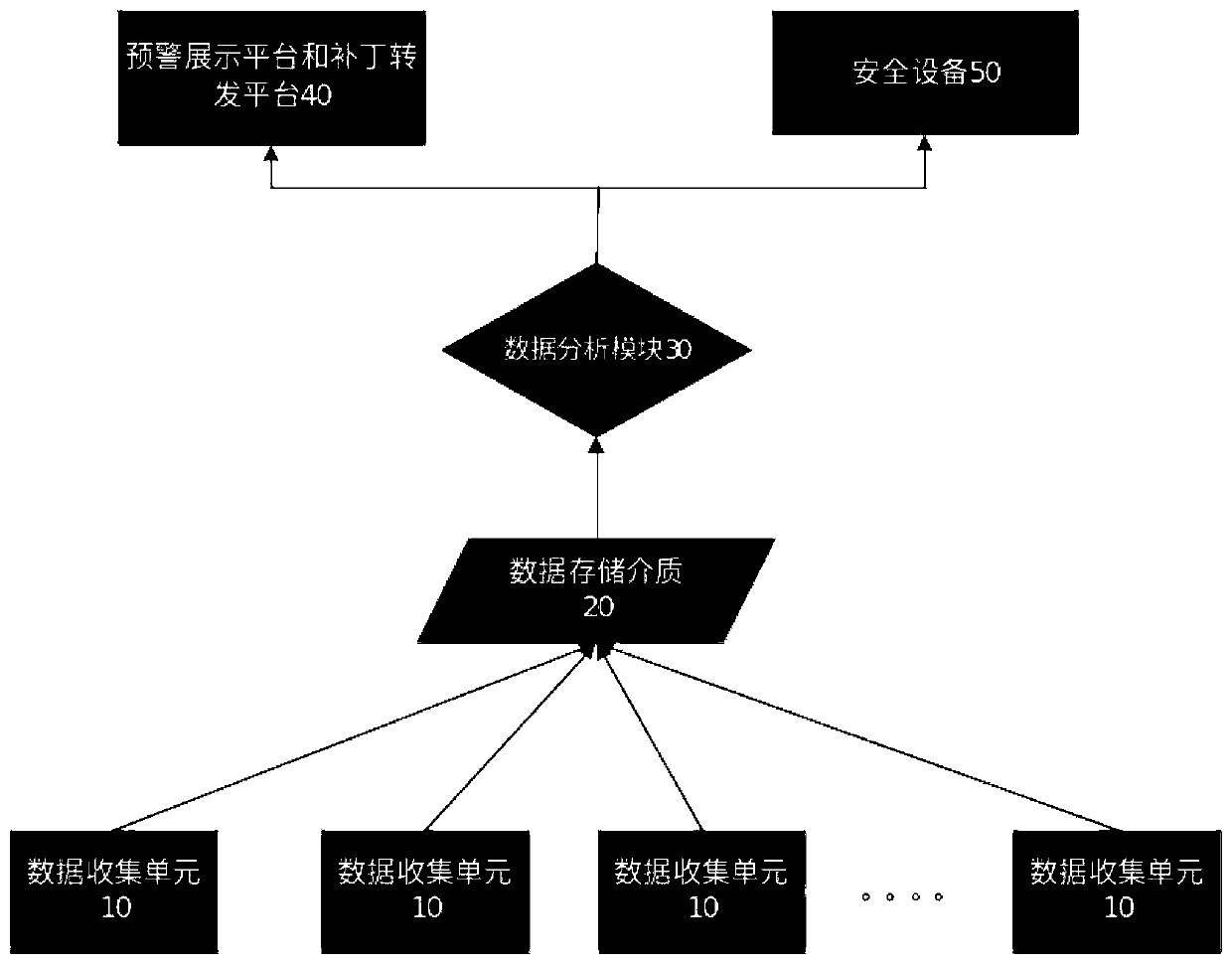
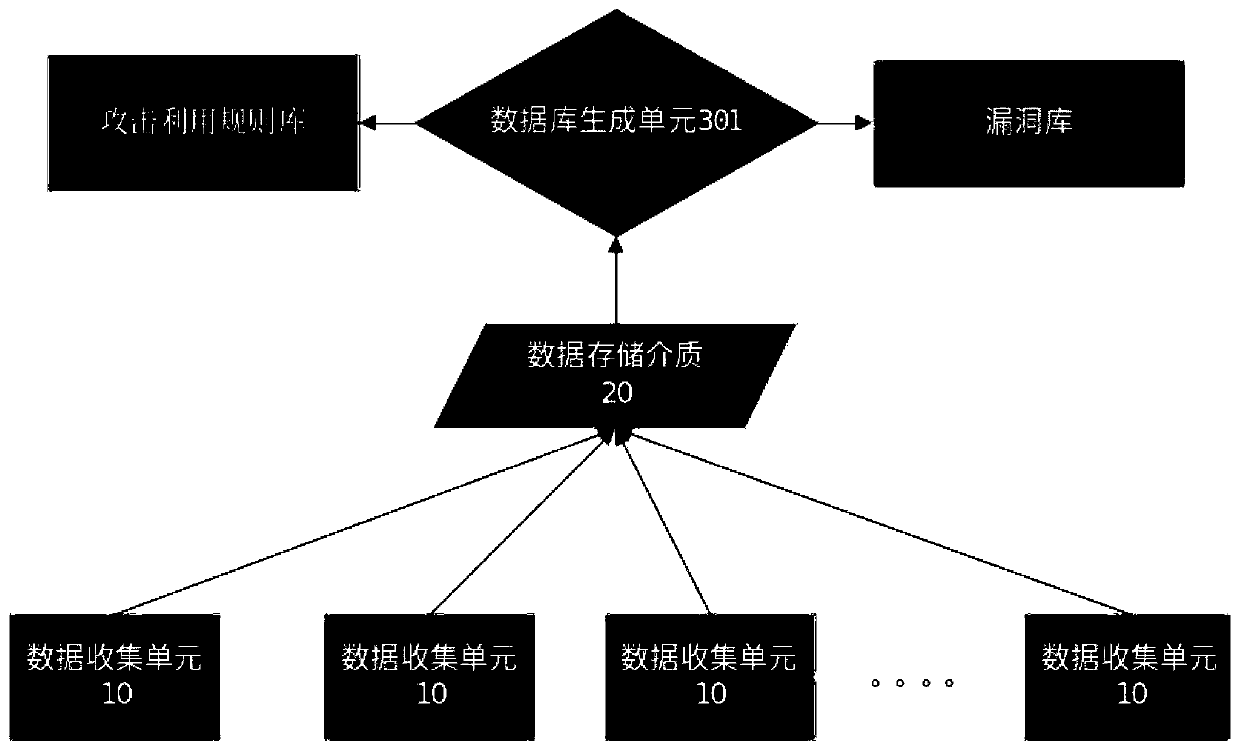
The invention discloses an industrial control system vulnerability trend analysis and early warning method and system, and the method comprises the steps: the simulation establishment of a plurality of probes is carried out with a core protocol in an industrial control system, and enabling the probes to be deployed in a public network and an intranet; The probe collects attack information in an interactive mode; The simulated industrial control system probe sends the collected attack information to a data analysis module, and the data analysis module is responsible for data analysis and vulnerability mining; The data analysis module generates an attack utilization rule base and a vulnerability base according to data analysis and vulnerability mining results; And the data analysis module analyzes the attack information sent back by the matching probe by using the generated attack utilization rule base and the vulnerability base, and reports the analysis result of the attack informationto the security equipment and the early warning display platform. According to the simulation industrial control system, the simulation industrial control system is induced to send an attack to the simulation industrial control system, an attack means is collected, vulnerabilities are analyzed, and serious vulnerability information existing in a production environment or to be utilized is early warned to a user.
Owner:江苏亨通工控安全研究院有限公司
GPS positioning vehicle safe driving recorder
InactiveCN101165723ARealize whole-process monitoring and storageImprove securityRegistering/indicating working of vehiclesBeacon systems using radio wavesDriver/operatorTachograph
The invention comprises: an in-car GPS signal receiver, an electronic map, an in-car video camera, an image data processing system, a vehicle part motion signal generator, a vehicle running state data recorder, a central processor and a memory. The in-car video camera is connected to the central processor through the vehicle running state data recorder; the GPS signal receiver is connected to the central processor; the central processor is connected to the memory.
Owner:王仁坤
A method and a device for providing and acquiring security identity information
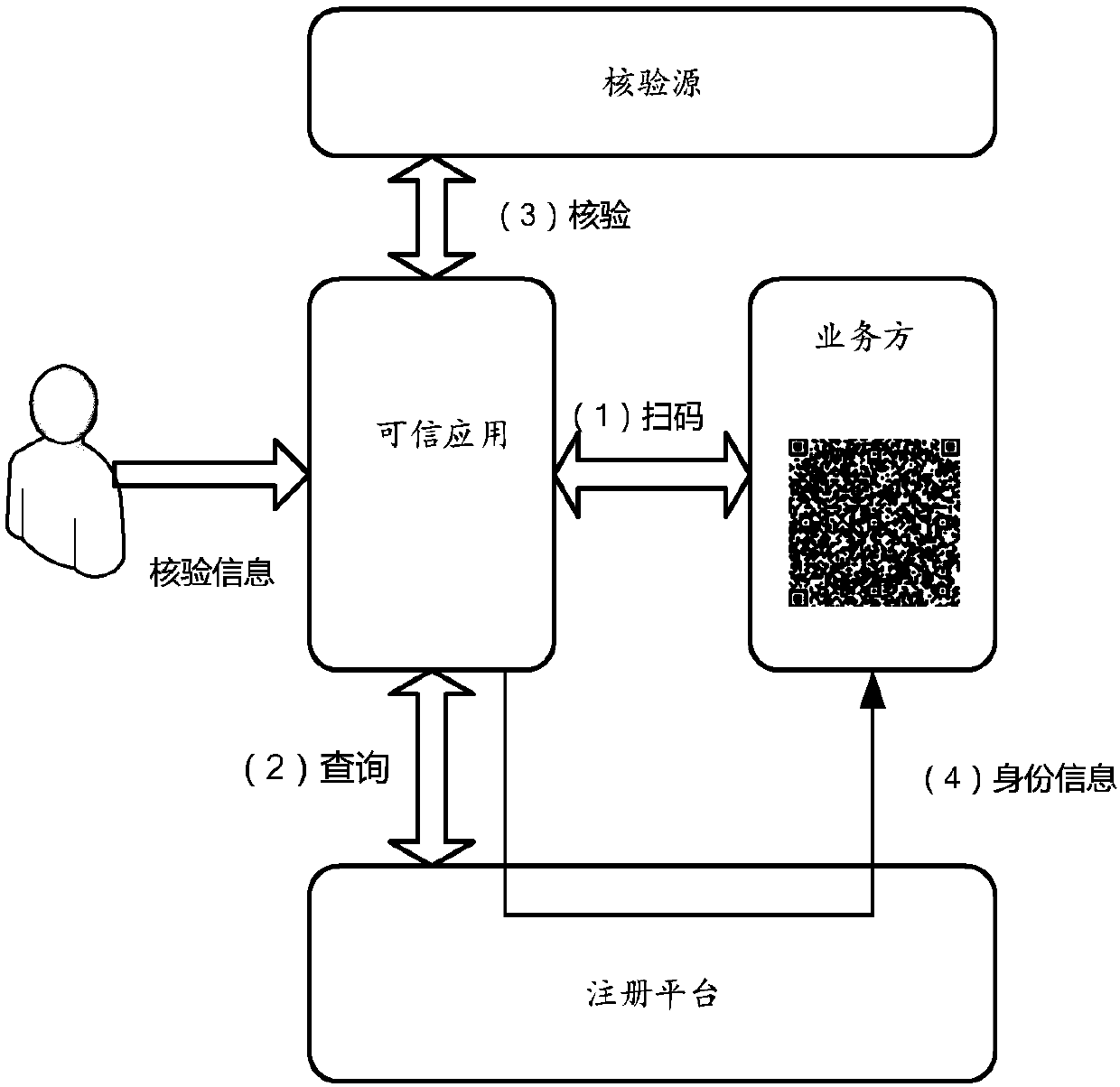
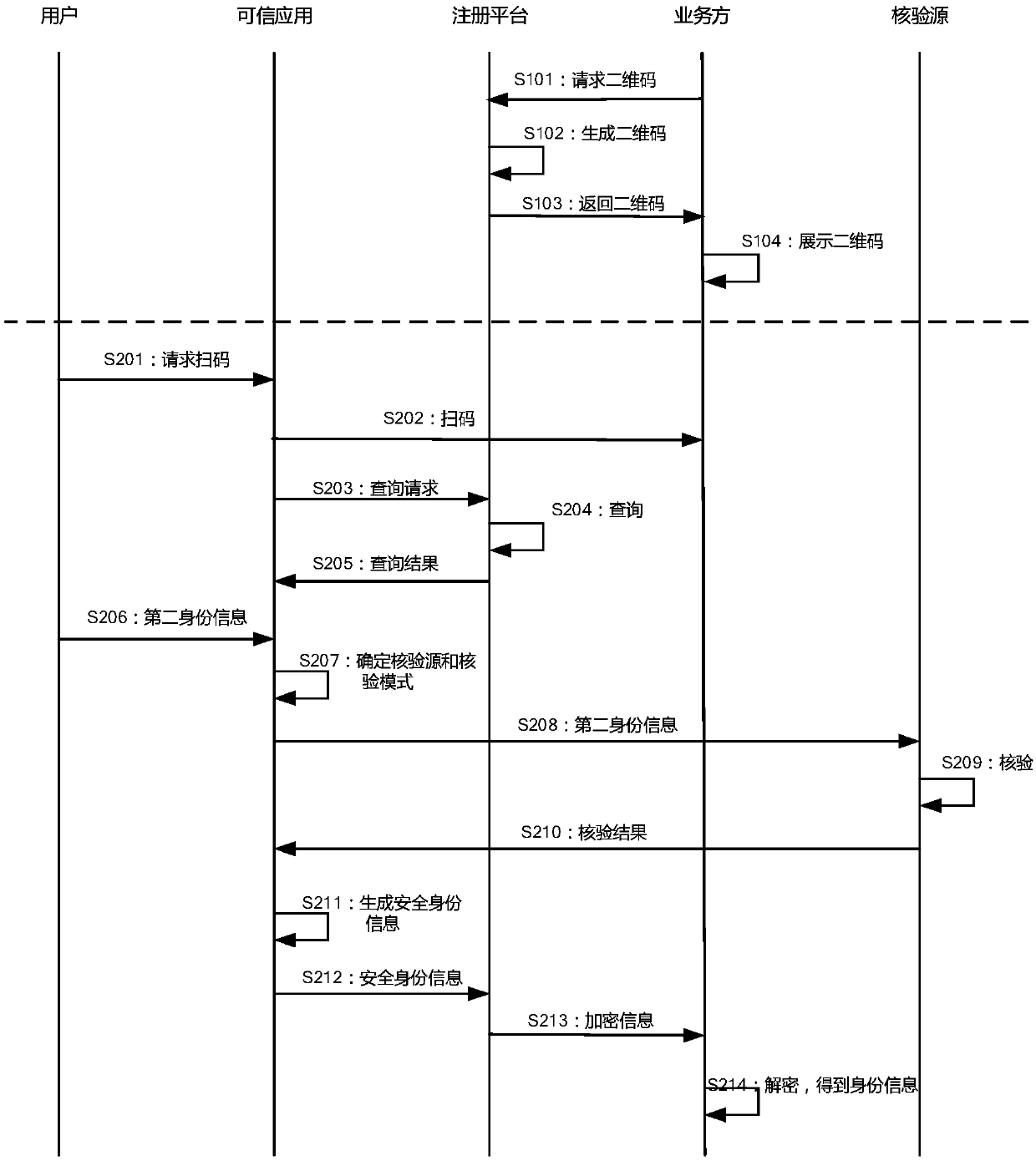
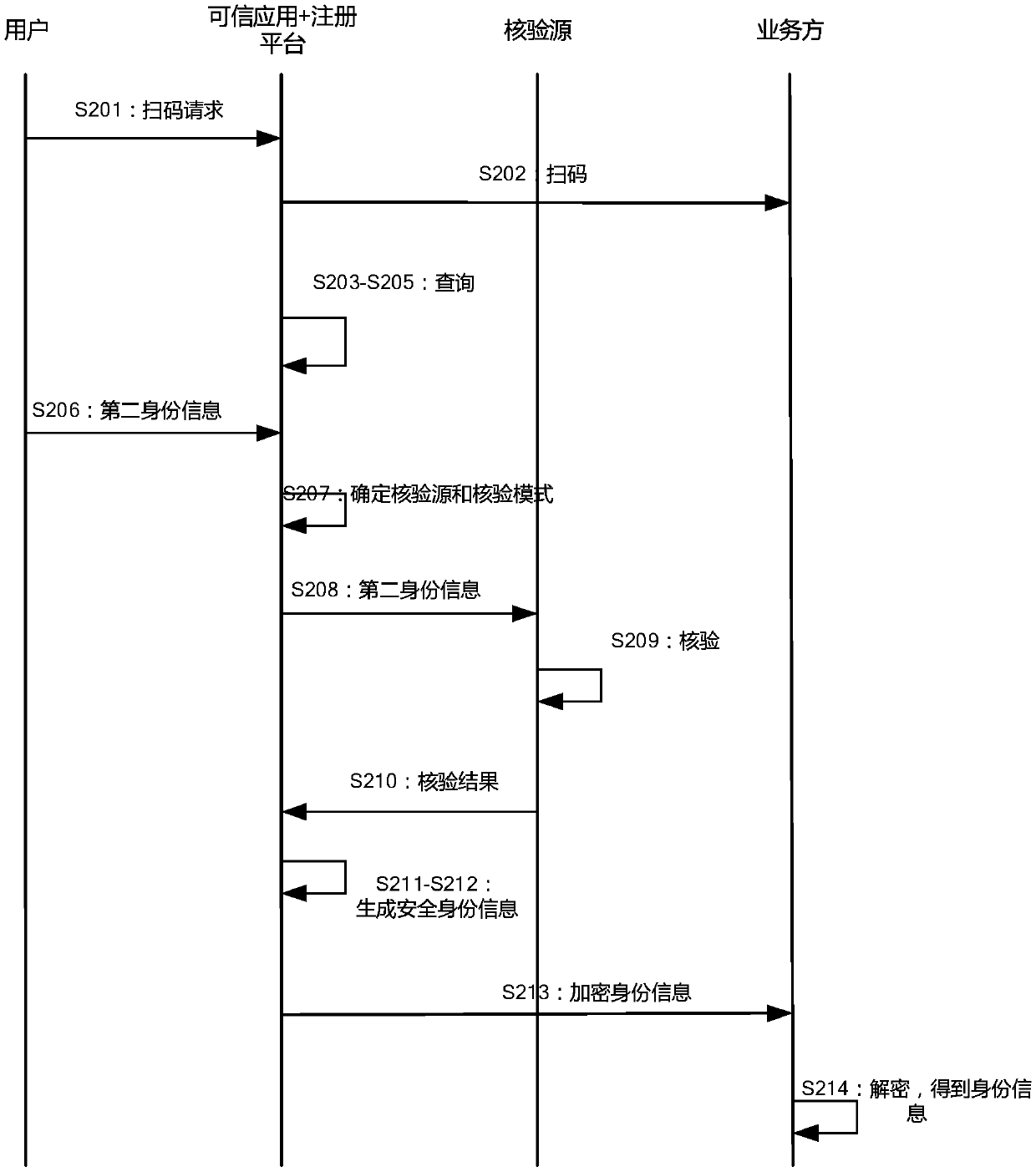
ActiveCN109598663AGuaranteed accuracyGuarantee authorityData processing applicationsSensing by electromagnetic radiationThird partyUser needs
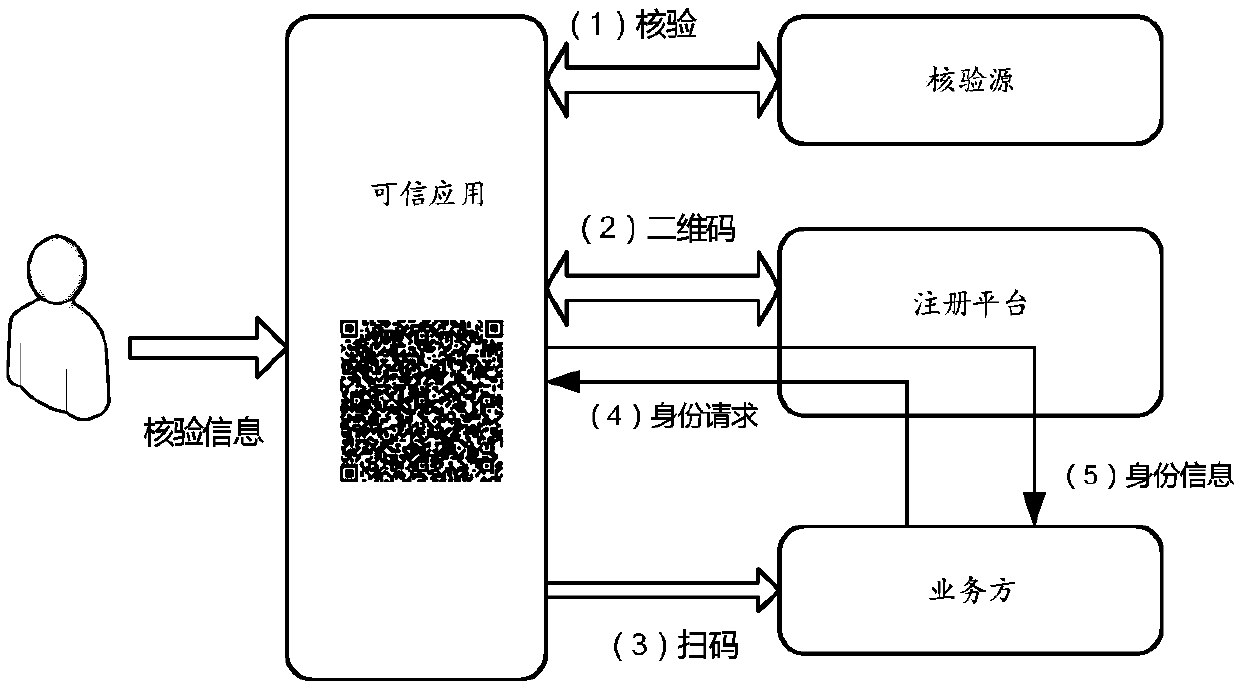
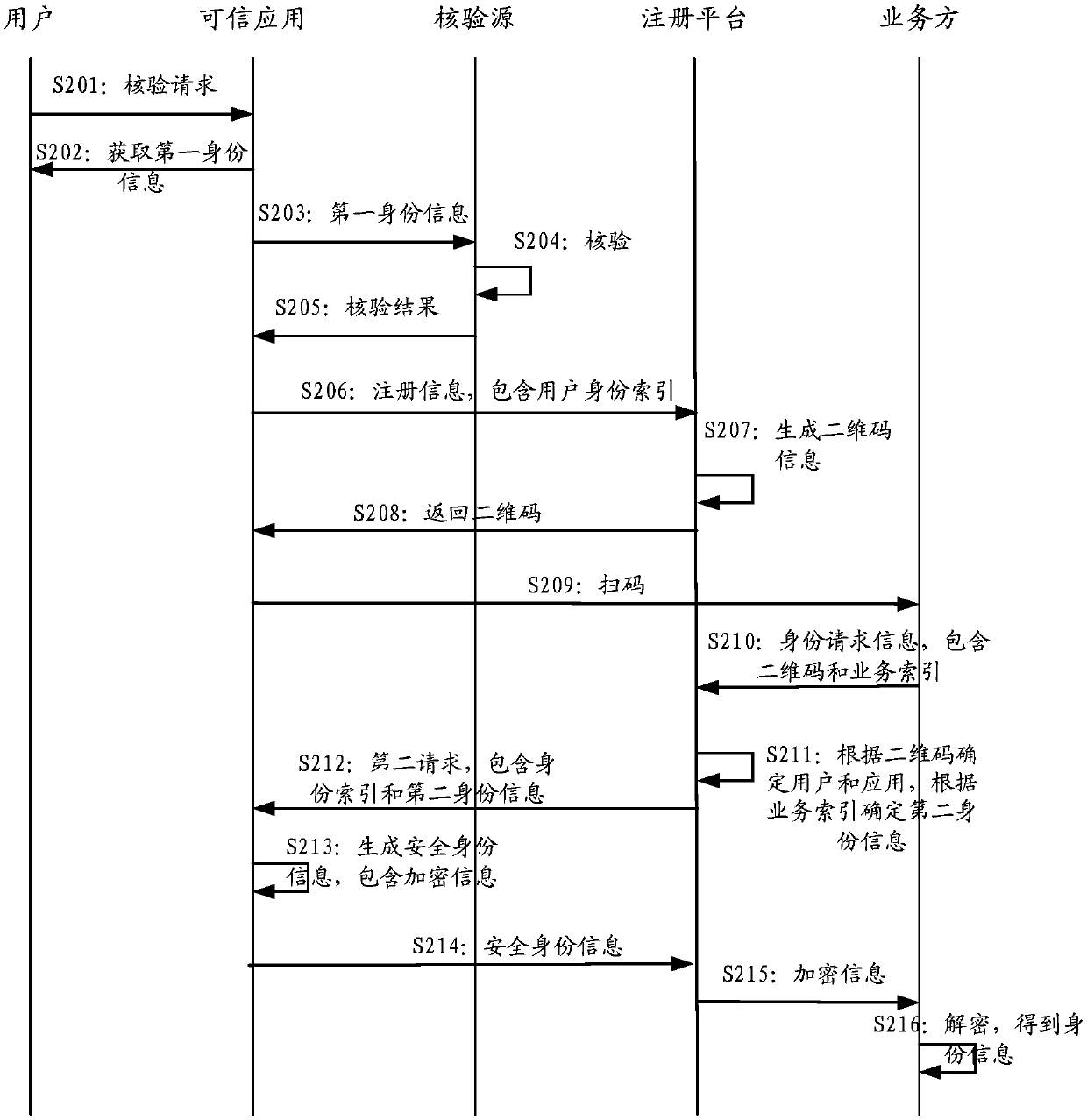
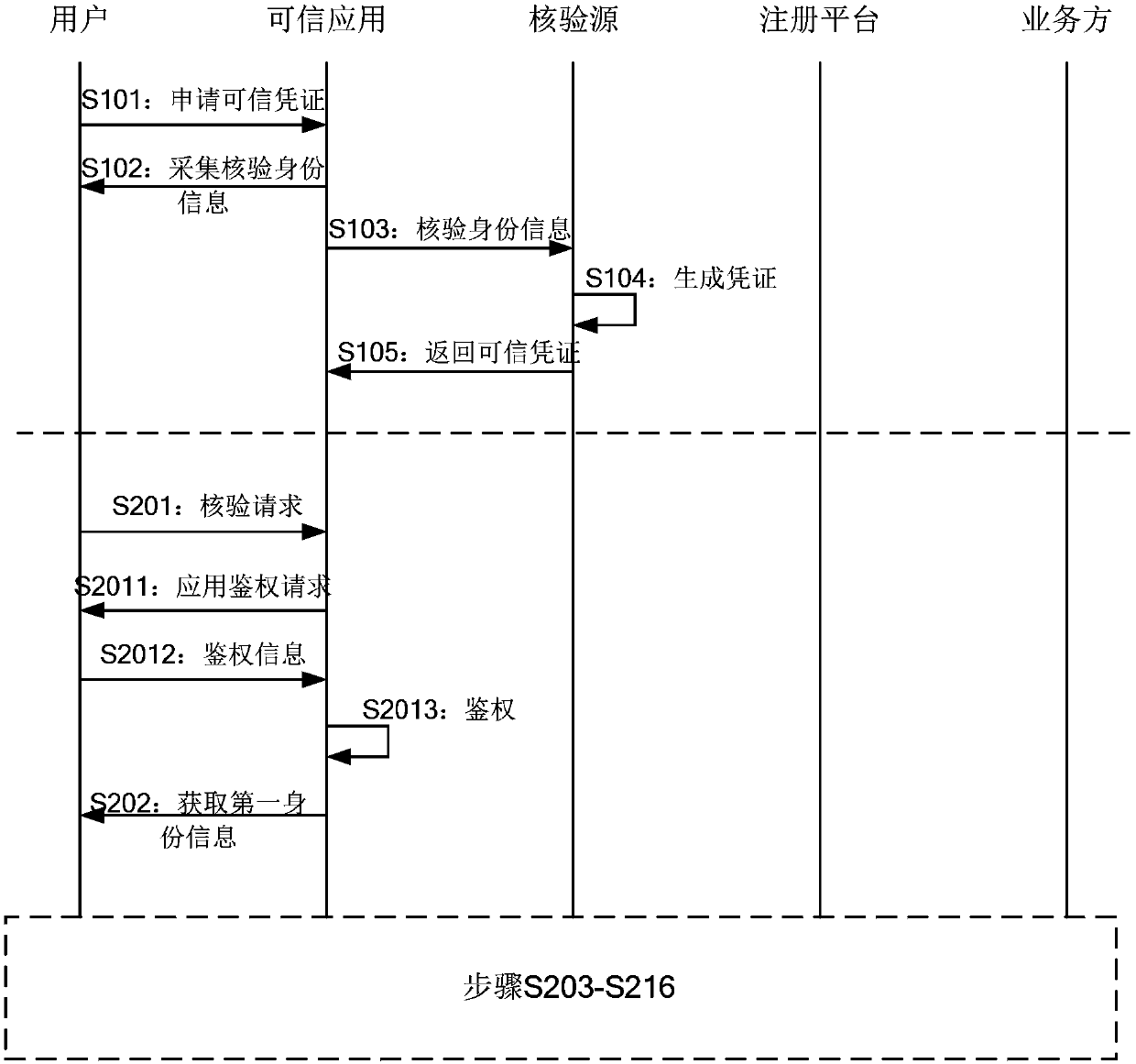
The embodiment of the invention provides a method and a device for providing and acquiring security identity information. And under the condition that the user needs to carry out identity verificationor provide safety identity information, the credible application acquires the identity information of the user and sends the identity information to a third-party verification source for verification. And after the verification is passed, the trusted application registers with the registration platform based on the verified information, thereby obtaining the two-dimensional code for the user. Theuser can then display the two-dimensional code through the trusted application. A service party needing security identity information scans the two-dimensional code, and based on the two-dimensionalcode, an identity request for the user is sent to the trusted application through the registration platform to request for obtaining the needed identity information; And then, the trusted applicationreturns required identity information to the service party through the registration platform.
Owner:ADVANCED NEW TECH CO LTD
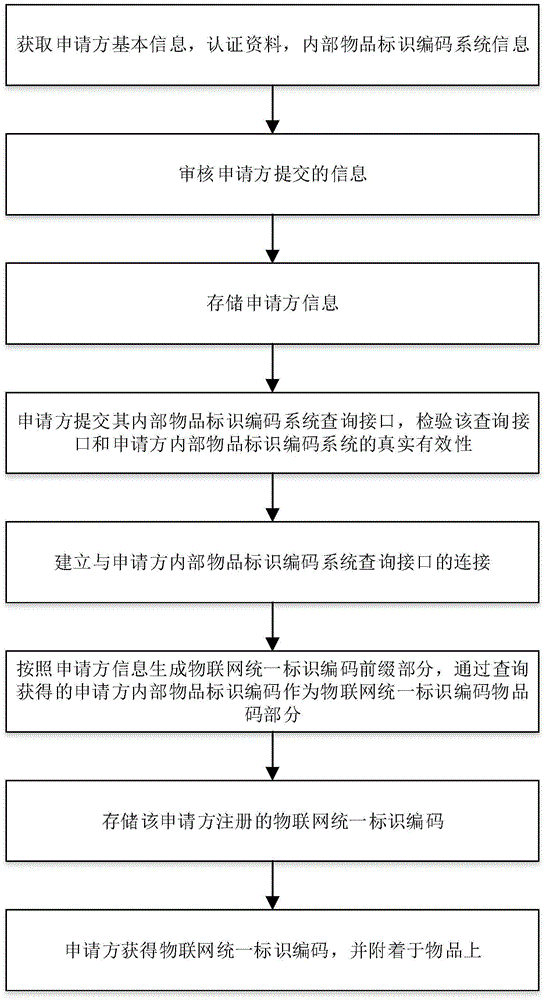
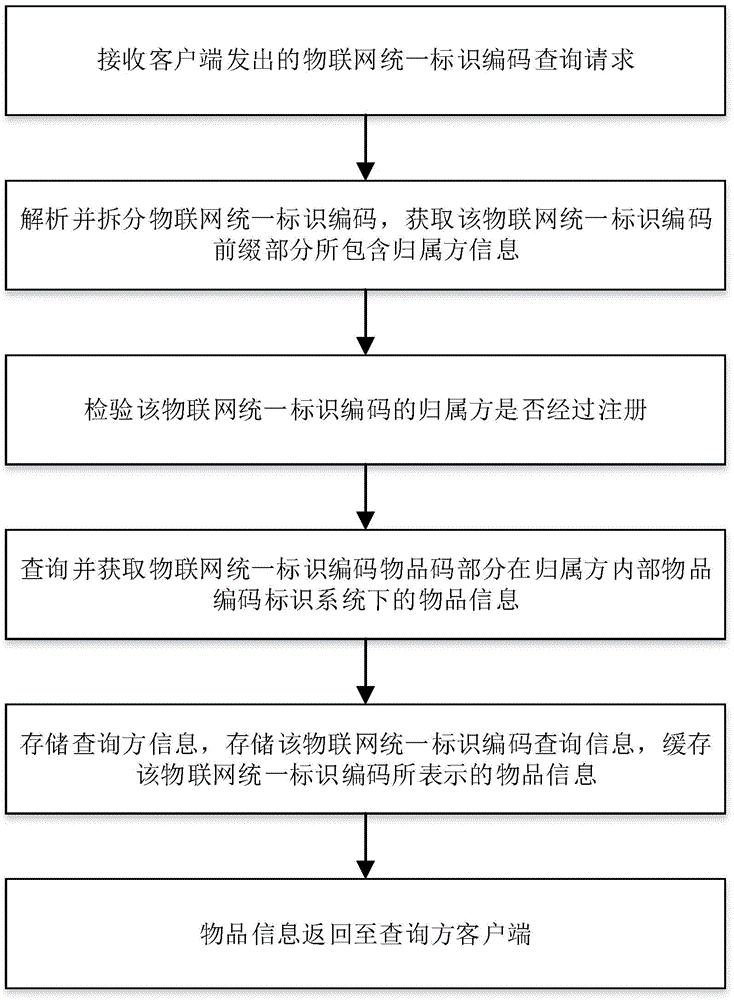
Internet of Things unified identification code registration system and method, and analysis system and method
ActiveCN105139144AGuaranteed accuracyIntegrity guaranteedResourcesTransmissionThe InternetRule system
The invention discloses an Internet of Things unified identification code registration system and method, and an analysis system and method. The registration system obtains basic data of an applicant and carries out audit on the basic data; storage is carried out after the audit is passed; an article code of the applicant is obtained through a query interface of an article identification code system, and the query interface and the validity of the article identification code system in the applicant are verified; the connection with the article identification code system in the applicant is established; a prefix part of the Internet of Things unified identification code and an article code part of the Internet of Things unified identification code are generated, the ownership information of the queried article and the information of the article are obtained, and the ownership information of the queried article and the information of the article are sent to a query side. The registration system is compatible with a plurality of kinds of code rule systems in the prior art, and an enterprise can register an Internet of Things unified identification code for each article does without changing an existing article identification code system.
Owner:刘治
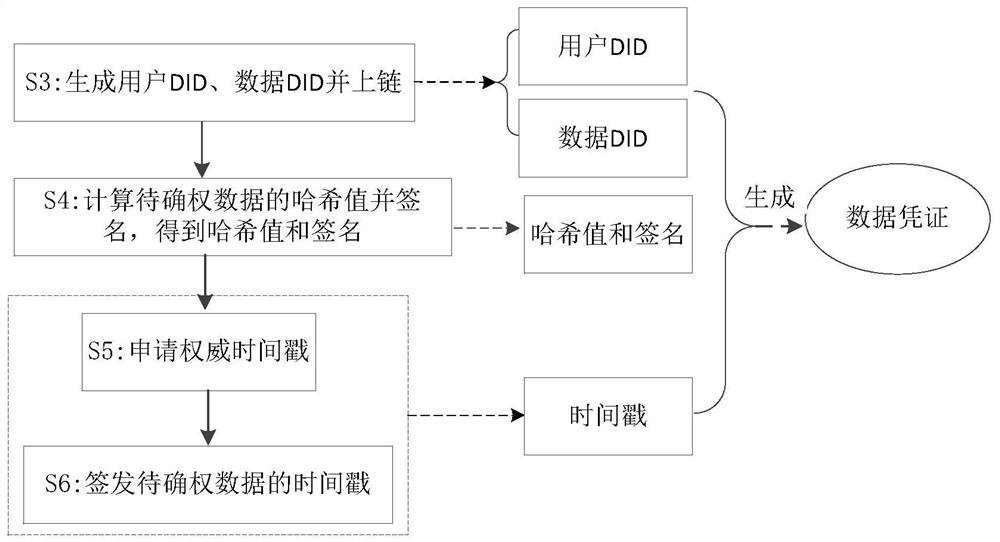
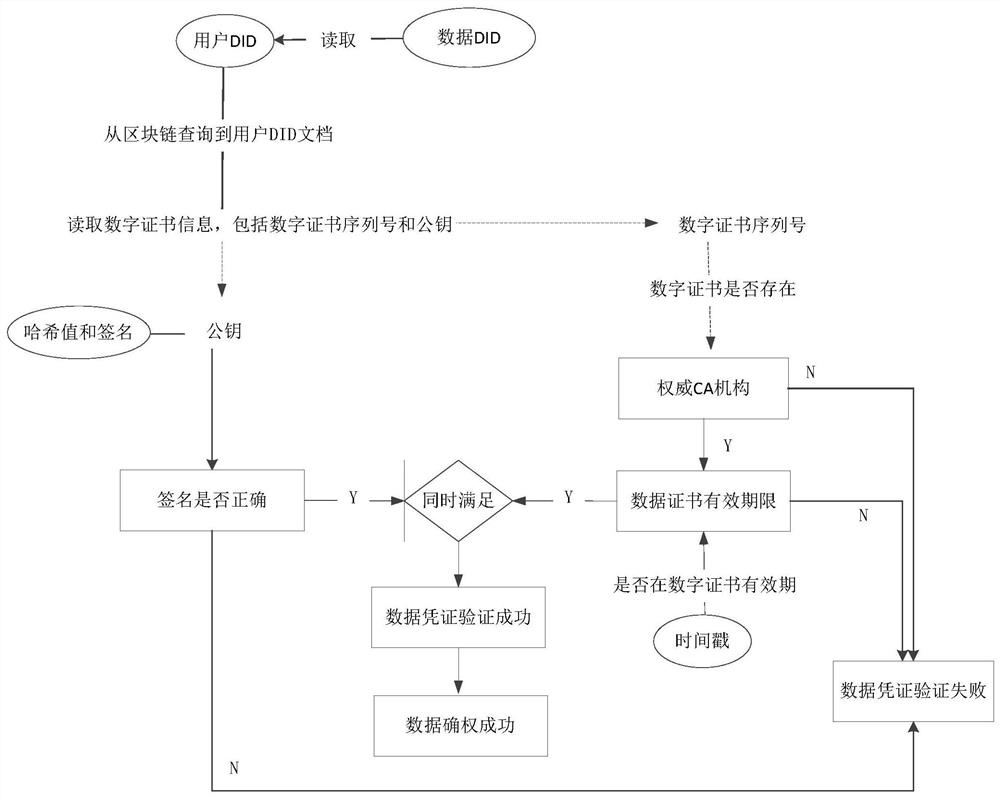
Data right confirmation method and system based on block chain technology
PendingCN112651052AGuarantee authorityGuaranteed credibilityDigital data protectionDigital identityTamper resistance
The invention discloses a data right confirmation method and system based on a block chain technology. The method comprises the following steps: initializing and verifying a digital certificate; generating a user DID and a data DID and uploading the user DID and the data DID; calculating a hash value of the data to be subjected to right confirmation and signing to obtain the hash value and a signature; applying an authoritative timestamp according to the hash value of the to-be-confirmed data; generating a data certificate of the to-be-confirmed data according to the uplink user DID, the data DID, the timestamp, the hash value and the signature, verifying the data certificate, calculating the hash value of the data certificate, and signing the hash value of the data certificate to obtain a signature certificate; and uploading the verified data voucher and signature voucher to obtain right confirmation record uplink hash and returning the right confirmation record uplink hash to the client. According to the invention, the decentralized digital identity DID is adopted, and the data right confirmation information of the to-be-confirmed right data is stored in the block chain in the form of the verifiable certificate, so that the right confirmation function of the to-be-confirmed right data is realized, and the characteristics of verifiability, traceability, tamper resistance and the like of the data right confirmation information are ensured.
Owner:JIANGSU PAYEGIS TECH CO LTD +1
Commodity anti-counterfeiting traceability system, method, device and storage medium
InactiveCN109360000AGuarantee authenticity and reliabilityPremium shopping experienceCo-operative working arrangementsCommerceBlockchainInternet of Things
Owner:SF TECH
Human sperm DNA fragment detection method and detection kit
InactiveCN102051413ASCSA test results are stableTest results are stableMicrobiological testing/measurementStainingFluorescence
The invention provides a human sperm DNA fragment detection method comprising the following steps: (1) diluting liquefied sperm with a buffer solution of 4 DEG C; (2) adding the diluted sperm into a sample tube of a flow cytometry; (3) adding an acid treatment buffer solution; (4) after 30 seconds, adding an AO staining solution; (5) setting a calibration and flow chamber of the flow cytometry, equilibrating a sample line by an AO equilibration buffer solution; (6) continuously determining each sample at least twice, recording at least 5000 cells and carrying out statistical analysis; and (7) after determining, respectively thoroughly cleaning the cell fragments and fluorescent dye remaining in the sample line of the flow cytometry by bleacher, sample tube detergent and degerming double distilled water. A human sperm DNA fragment detection kit comprises 50mL of staining buffer solution, 300mu L of AO stock solution, 20mL of acid treatment solution, 100mL of buffer solution, 100mL of sheath fluid, 100mL of AO remover, 100mL of sample tube detergent and 100mL of double distilled water (ddH2O). The invention realizes the purpose of clinically detecting the sperm DNA fragments simply, conveniently, quickly and accurately.
Owner:ZHEJIANG CELLPRO BIOTECH
A multi-party fair contract evidence storage method and system based on a block chain technology
ActiveCN109840767ASolve the problem of credit dependenceGuaranteed non-repudiationProtocol authorisationChain networkBlockchain
The invention relates to a multi-party fair contract evidence storage method based on a block chain technology. Activated management mode of digital data storage technology is realized by utilizing ablock chain technology and a CA digital certificate system, and management processes such as initialization addition, updating and freezing of storage data are mapped into a transaction list form of ablock chain network; the evidence storage data is confirmed by signatures of multiple evidence storage parties and is written into the transaction bill; the storage process is written into the blockchain global account book data after the storage multi-party confirmation and the whole network consensus verification of the block chain network; A management mode of the stored data which cannot betampered, cannot be denied and does not have a single-point fault is formed, and the problems that in the current centralized storage technology, a credit single-point dependence problem exists generally, and the stored original data cannot be recovered after the single-point fault are solved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
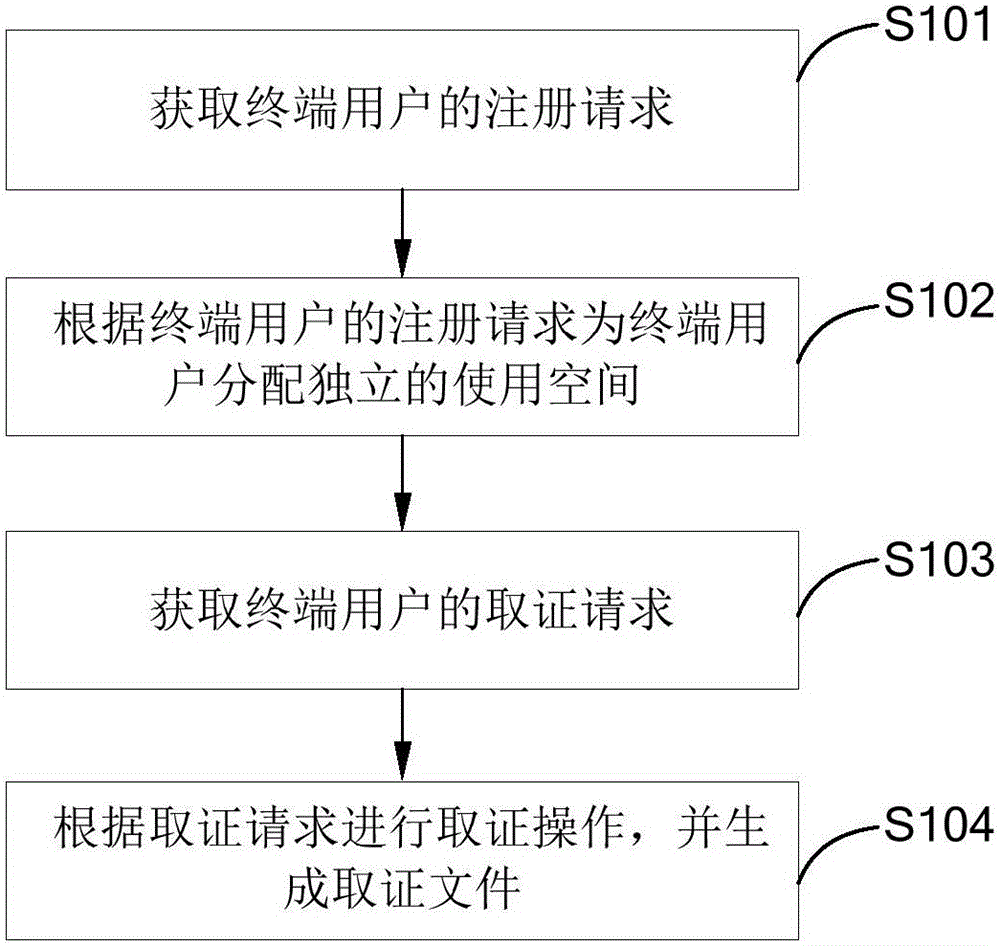
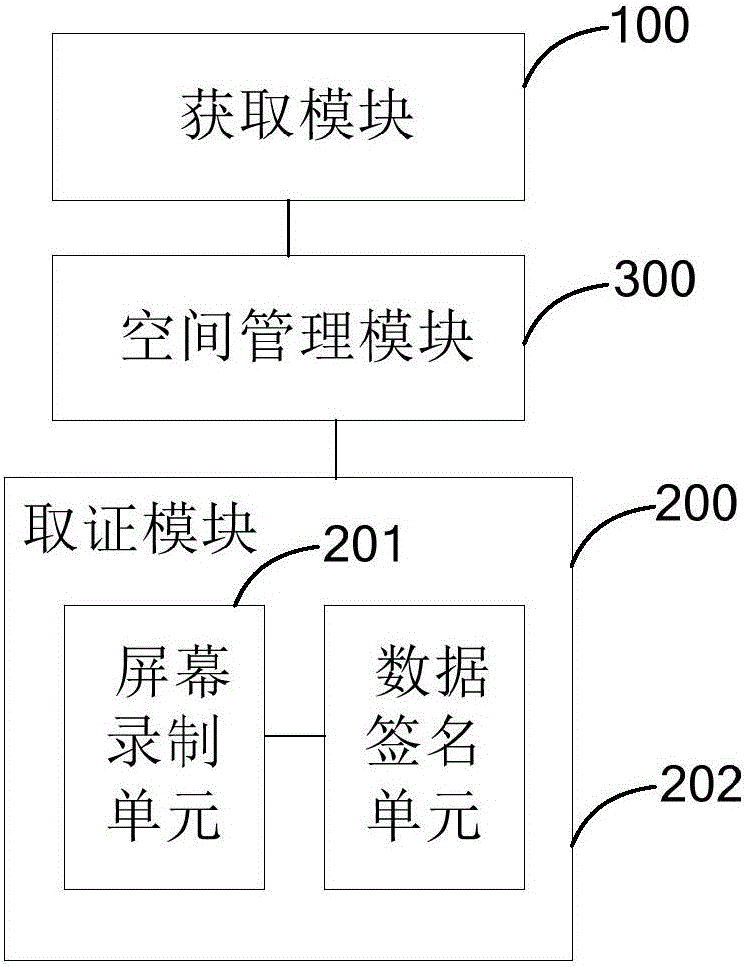
Autonomous electronic evidence obtaining method and system
InactiveCN106059772AGuaranteed to be reliableGuarantee authorityUser identity/authority verificationVirtual spaceDigital signature
The invention provides an autonomous electronic evidence obtaining method and system. The method includes the following steps: based on an evidence obtaining request, carrying out evidence obtaining operation and generating an evidence obtaining file. The system includes an acquiring module and an evidence obtaining module. According to the invention, a virtual space mode is used to establish a controllable evidence obtaining environment, such that a user can carry out evidence obtaining through the virtual space on a cloud rather than on individual terminal, which guarantees reliability of the environment. At the same time, the recording of whole process of the evidence obtaining guarantees controllability and audit of the evidence obtaining. Finally, the use of digital signature and time stamp guarantees authority and impossibility of tampering of electronic evidence, so that the contradiction between the evidence obtaining request and traditional evidence obtaining procedure is overcome.
Owner:SHANGHAI PINGAN NETWORK TECH CO LTD
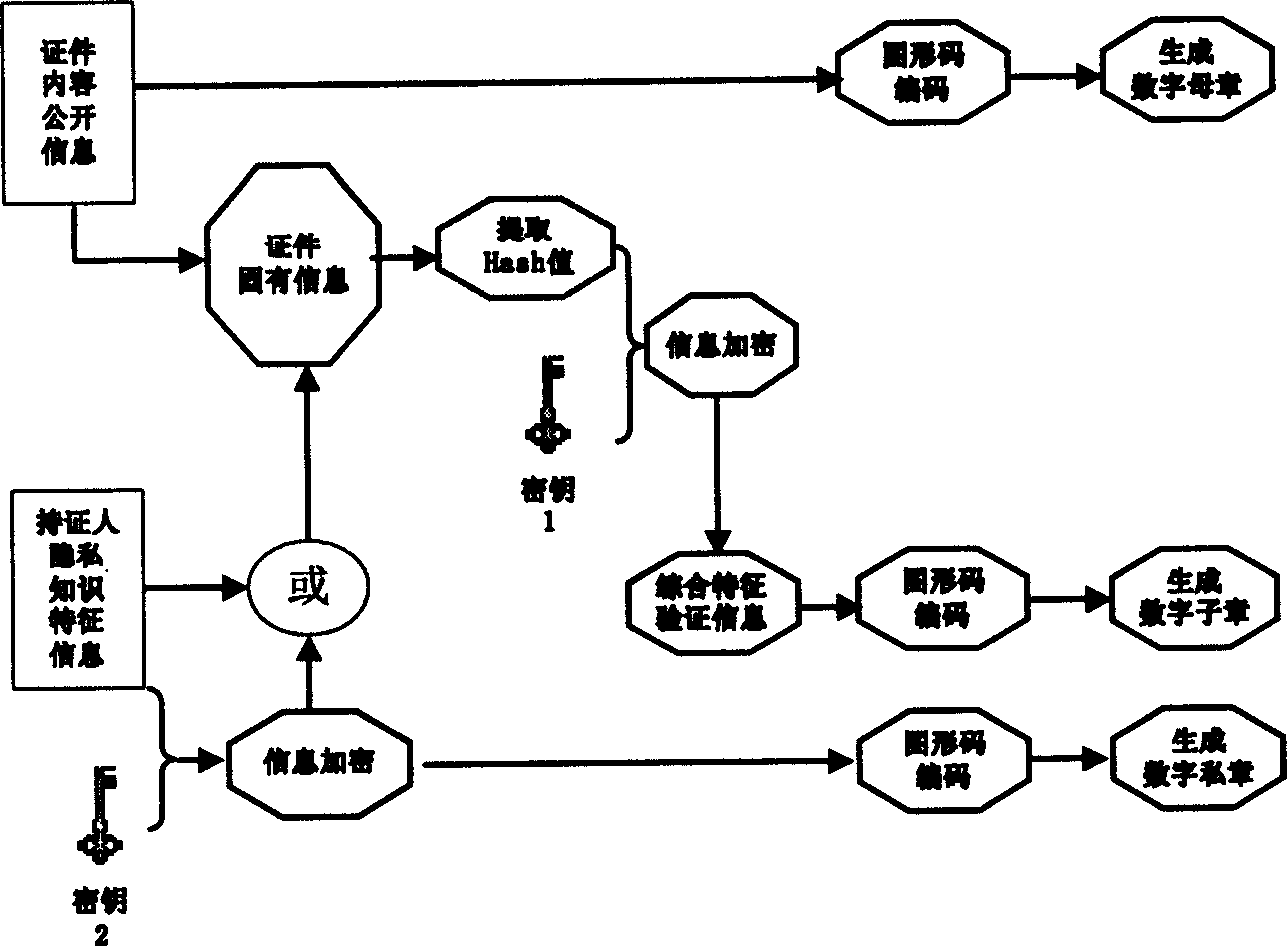
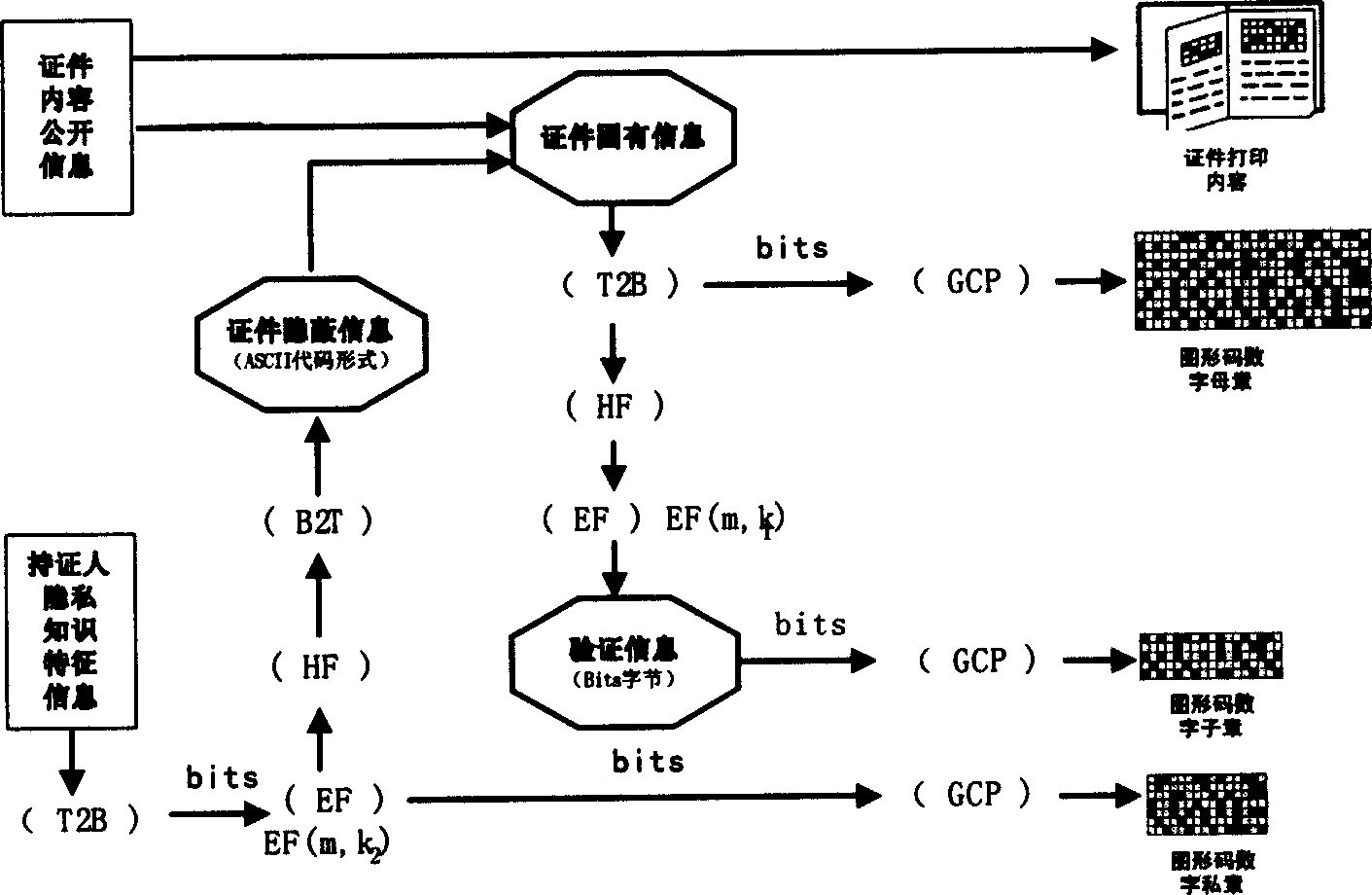
Soft certification anti-false method based on graphic code primary and secondary signet series information association mechanism
InactiveCN1570962AGood choiceEasy to implementUser identity/authority verificationCo-operative working arrangementsGraphicsHuman sense
Owner:中国科学院成都计算机应用研究所
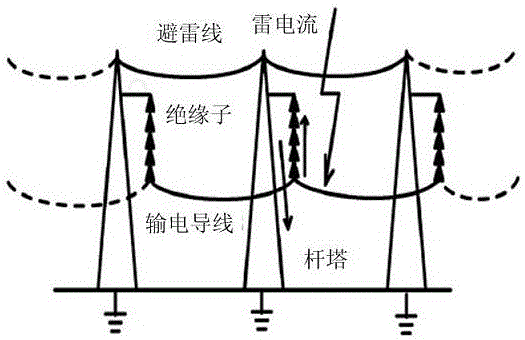
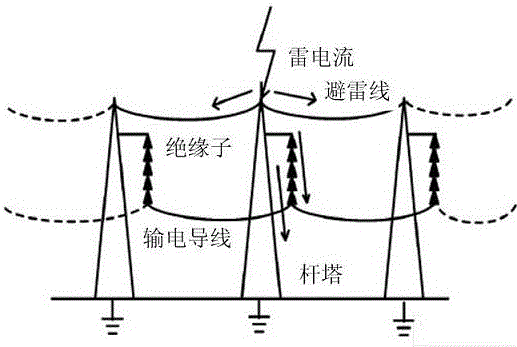
Method for calculating direct lightning tripping-out rate of distribution line up to 35kV
ActiveCN105160049AGuaranteed accuracyGuarantee authoritySpecial data processing applicationsEngineeringThree-phase
The invention relates to a method for calculating the direct lightning tripping-out rate of a distribution line up to 35kV. In the method, firstly, the lightning damage condition of the region where the distribution line is arranged, and the line parameters and the tower parameters are obtained, and the probability of the event that the lightning current hits the towers and the probability of the event that the lightning current hits the wires are obtained. Secondly, in view of the special neutral point grounding manner of the distribution line, when the lightning current directly hits wires, and two phase flashover and three phase flashover of insulators occur, and the amplitude of the lightning current is calculated through a brand new formula. the simulation model that the lightning current hits towers and lightning conductors under the condition of a specific tower shape and a specific loop is established by means of electromagnetic transient simulating calculation software, the amplitude of the lightning current which causes two phase flashover and three phase flashover of the insulators is obtained, furthermore, the straight hit tripping-out rate is calculated through a new formula, the back flashover tripping-out rate is calculated through a new formula, and by adding the straight hit tripping-out rate to the back flashover tripping-out rate, the total straight hit tripping-out rate can be obtained. The method for calculating the direct lightning tripping-out rate of the distribution line up to 35kV is suitable for calculating the tripping-out rate of the distribution line under the condition of different tower shapes and loops, and can provide basis to lightning damage assessment and line reconstruction.
Owner:STATE GRID JIANGXI ELECTRIC POWER CO LTD RES INST +2
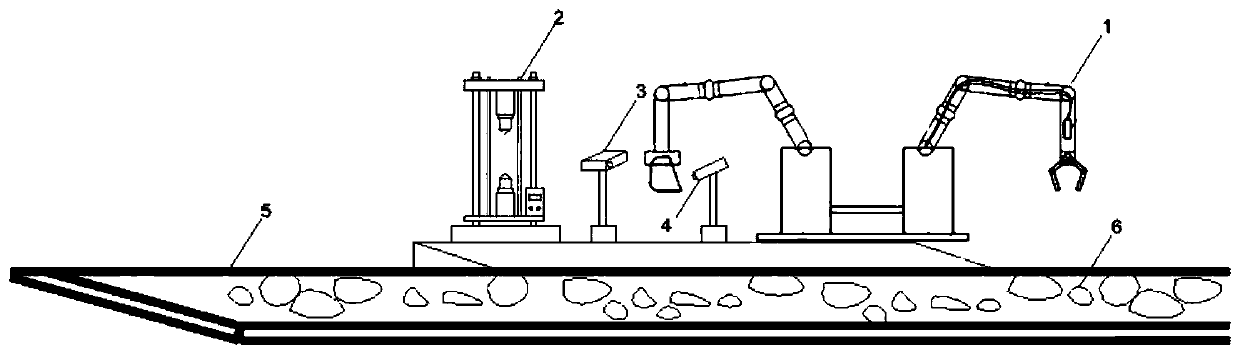
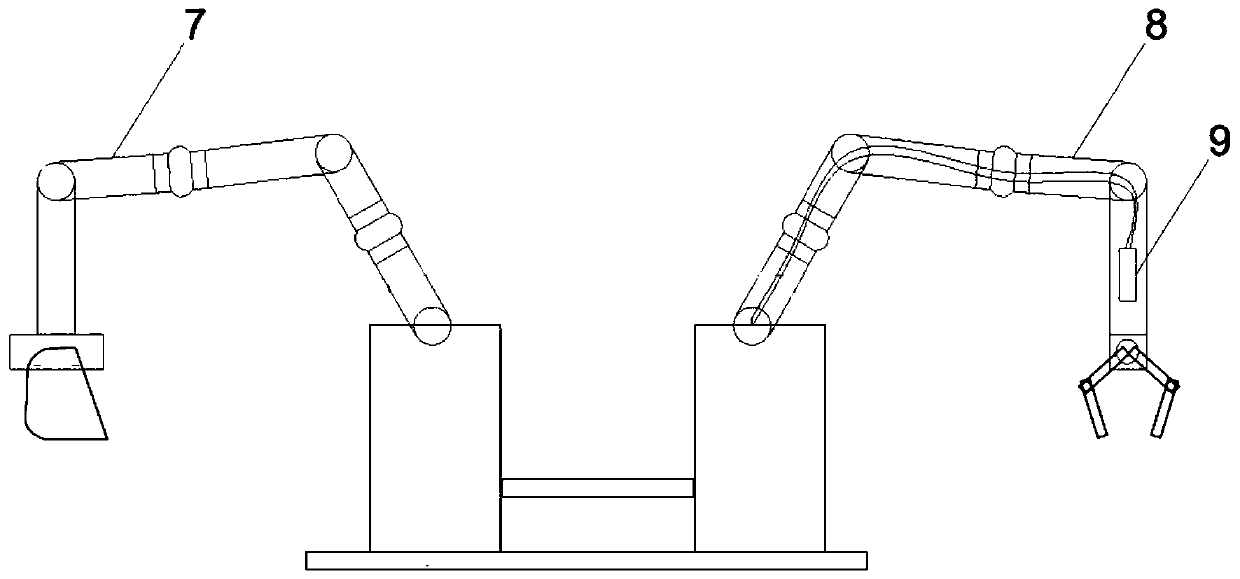
Surrounding rock mechanical parameter automatic testing system and method suitable for TBM
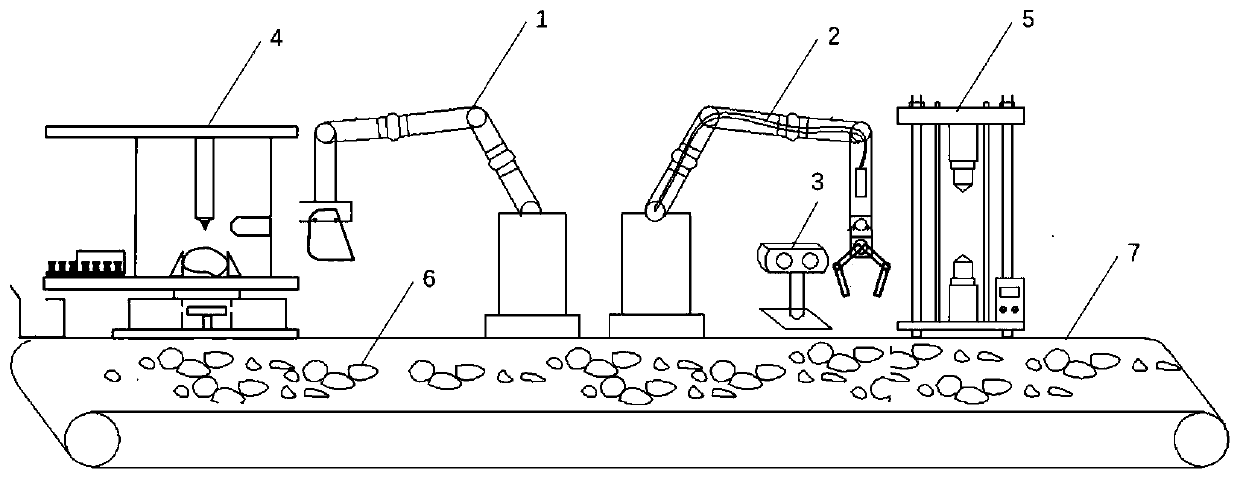
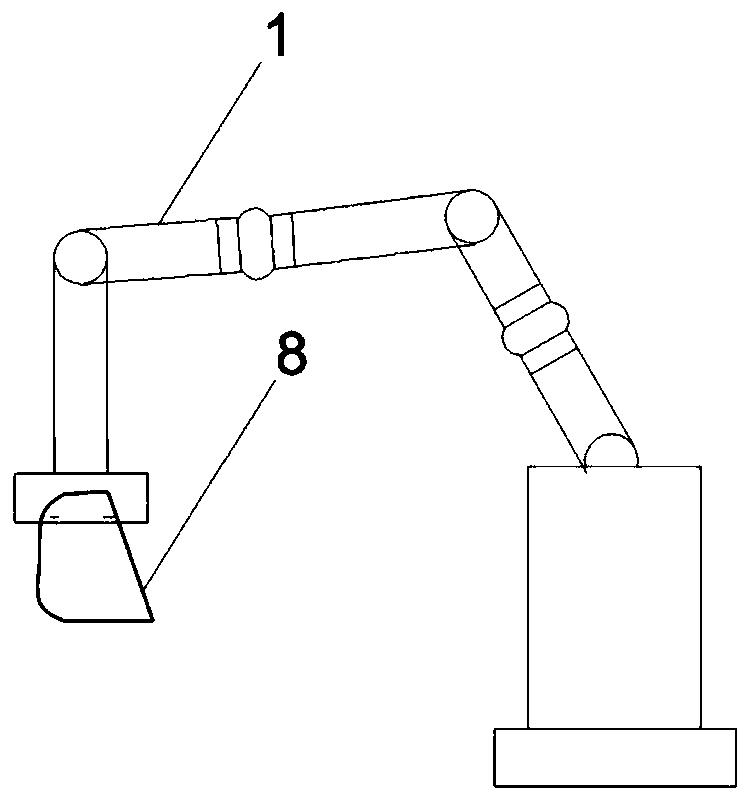
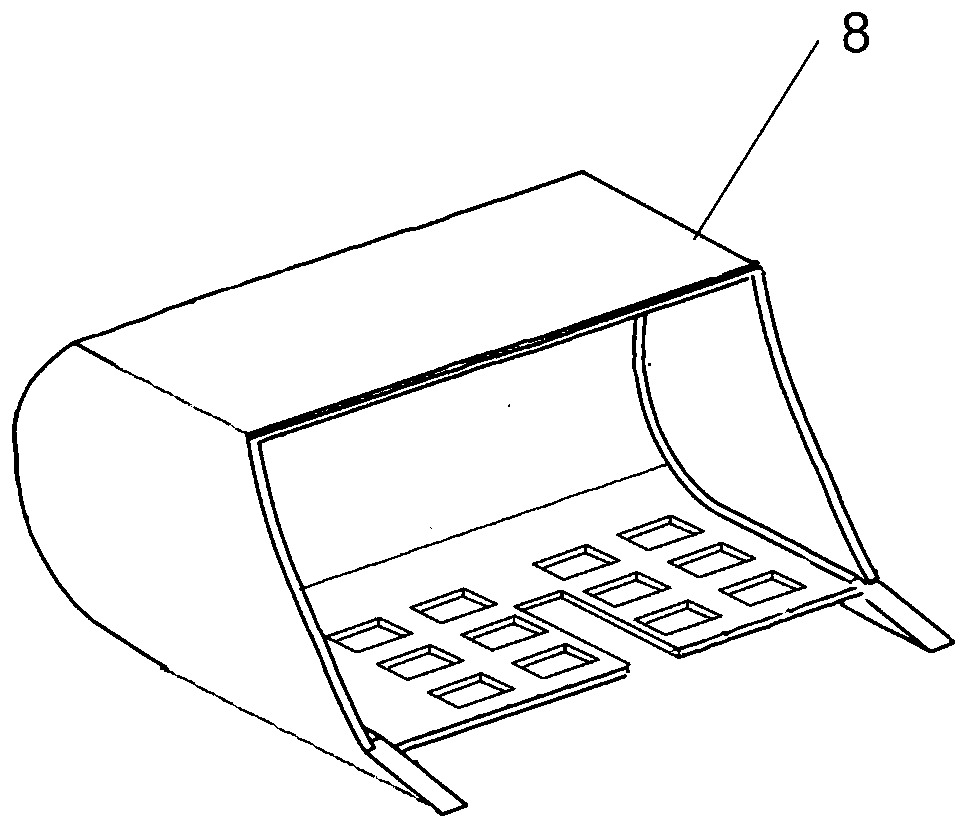
ActiveCN110823737AStrong timelinessHigh degree of automationProgramme-controlled manipulatorMaterial strength using tensile/compressive forcesVision processingClassical mechanics
The invention discloses a surrounding rock mechanical parameter automatic testing system and a surrounding rock mechanical parameter automatic testing method suitable for a TBM. The surrounding rock mechanical parameter automatic testing system comprises a material collecting part, a grabbing part, a visual processing device and a rock abrasiveness testing device, wherein the material collecting part which can collect rock slag in a tunneling process of the TBM in real time; the grabbing part can grab arbitrary rock slag from the obtained rock slag; the visual processing device can perform three-dimensional imaging on the tested rock slag in an infrared distance measurement mode, calculates positions of loading points of an abrasiveness testing experiment, determines whether the tested rock slag meets requirements or not according to the distance between the loading points, if so, determines actual positions of the loading points, and determines that a region, meeting a set condition,on the surface of the rock slag serves as an action region of the abrasiveness testing experiment; and the rock abrasiveness testing device can automatically carry out abrasiveness testing on tested rock slag meeting the requirements. The surrounding rock mechanical parameter automatic testing system and the method have the advantages of being high in timeliness, high in automation degree, safe, economical and the like, effectively solve the problem that surrounding rock strength information of current TBM construction is difficult to obtain in real time, and provide real-time surrounding rockcondition information and a control parameter decision basis for TBM tunneling.
Owner:山东百廿慧通工程科技有限公司
Electronic signature method and device
ActiveCN109756341APrevent tamperingImprove reliabilityUser identity/authority verificationOffice automationSignature fileComputer terminal
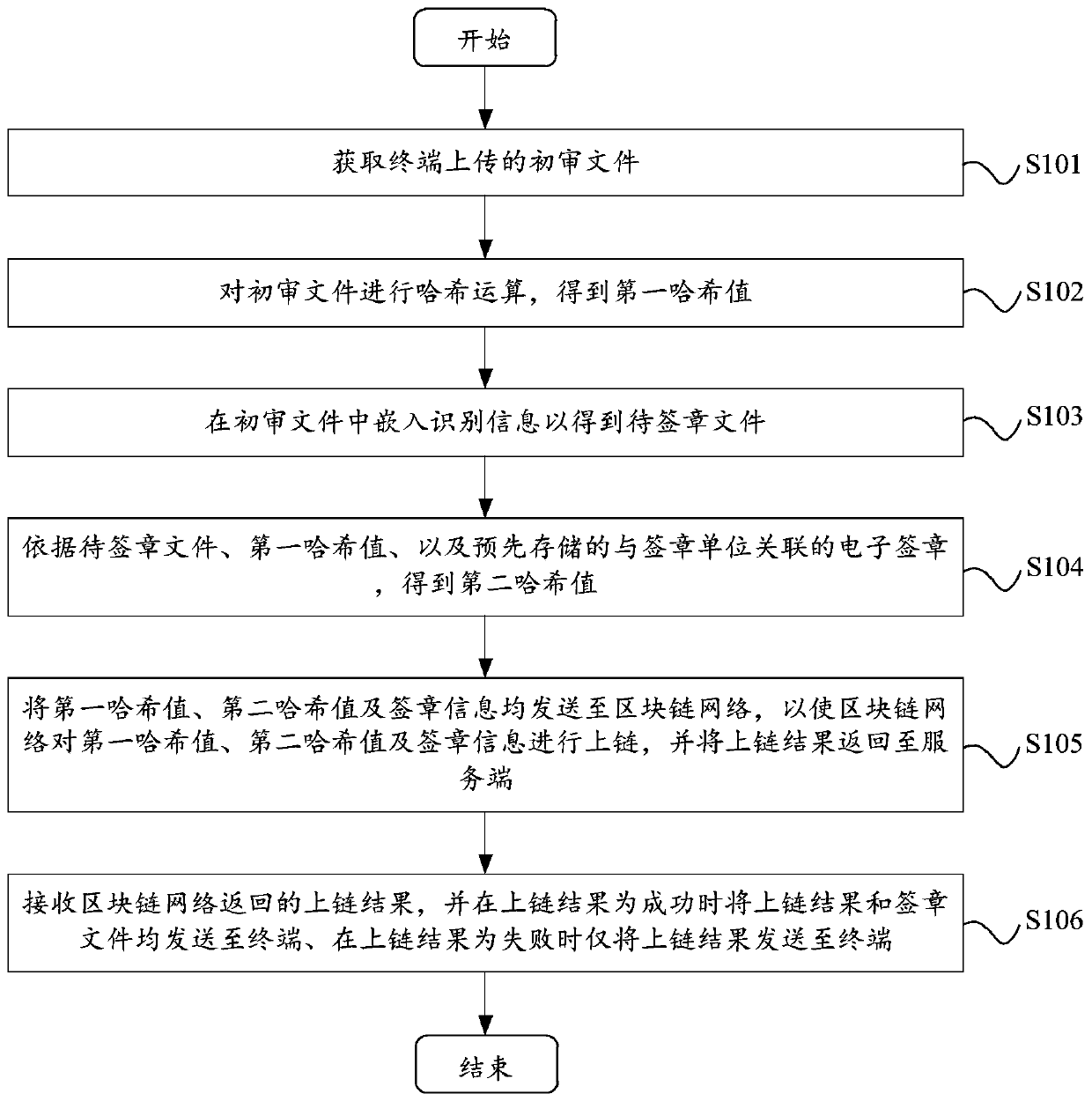
The embodiment of the invention relates to the technical field of block chains, and provides an electronic signature method and device, and the method comprises the steps: obtaining a primary review file uploaded by a terminal; performing Hash operation on the primary review file to obtain a first Hash value; embedding identification information into the primary review file to obtain a to-be-signed file; obtaining a second hash value according to the to-be-signed file, the first hash value and a pre-stored electronic signature associated with the signature unit; and sending the first hash value, the second hash value and the signature information to a block chain network, so that the block chain network links the first hash value, the second hash value and the signature information, and returns a link result to the server. Compared with the prior art, the block chain network is introduced into the electronic signature technology, the signature file can be effectively prevented from being tampered by utilizing the technical characteristic that information in the block chain network cannot be tampered, and the reliability is high.
Owner:NEW H3C TECH CO LTD
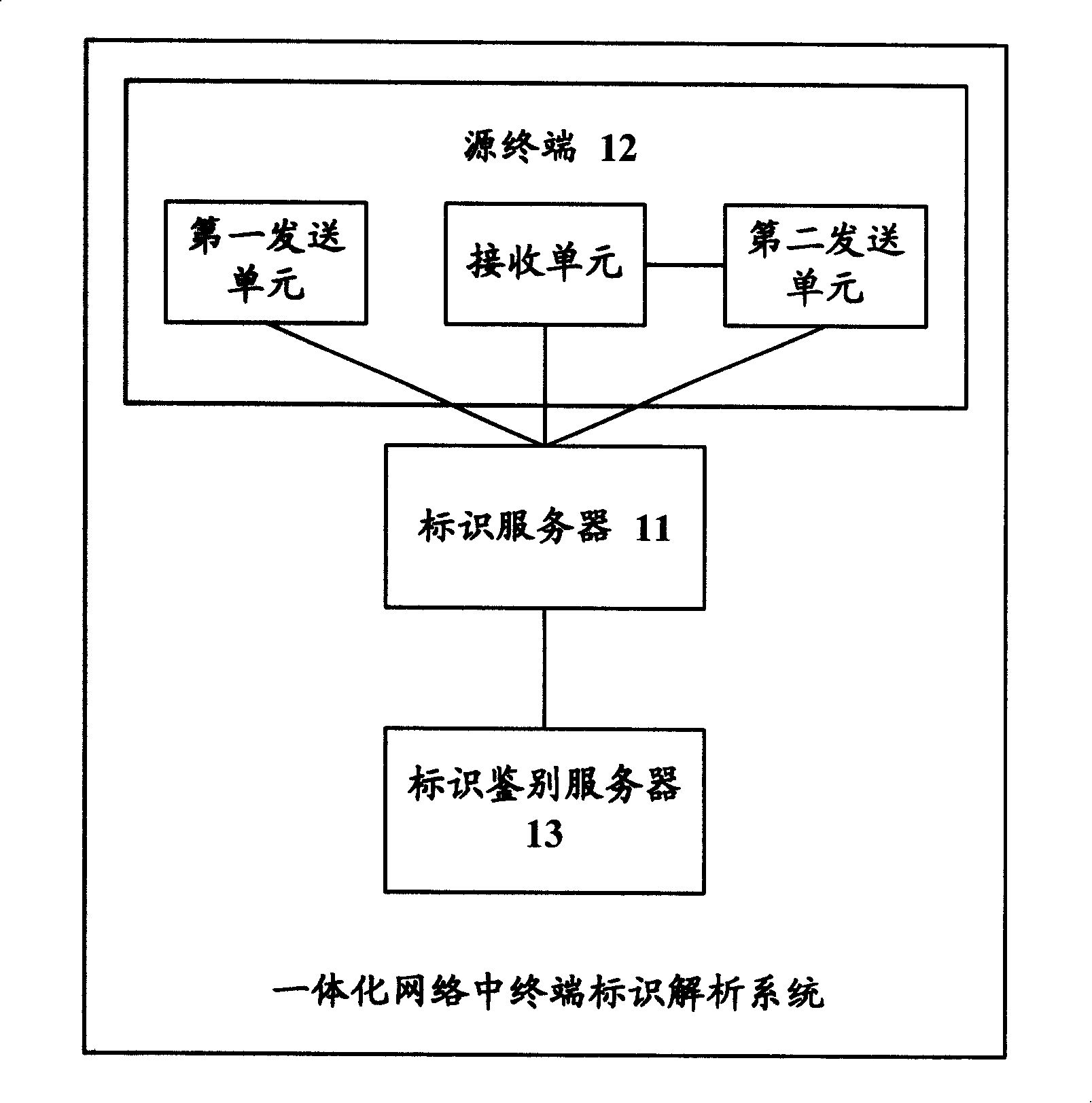
Terminal identifier parsing and service transmission method, system and device in integrated network
InactiveCN101237442AGuaranteed legalityGuarantee authoritySpecial service provision for substationNetwork dataData transmission
The invention discloses a terminal identification analyzing method in an integrated network, comprising the following steps that; A. a demand message sent to a source terminal is received and comprises a service identifier demanded by the source terminal; B. a destination terminal identifier corresponding to the service identifier demanded by the source terminal is found out in the correspondenceof the terminal identifier stored in advance and the service identifier supported by the terminal; C. a reply report is sent back to the source terminal and comprises the destination terminal identifier. The terminal identification analyzing method realizes the process of analyzing the terminal identifier and provides the good support for gaining access to the integrated network for the source terminal of an external network; in addition, the method realizes the effective authentication of the identifier and guarantees the validity and the authority of the identifier as well as guarantees thesecurity of the network data transmission. The invention also discloses a terminal identification analyzing system in the integrated network and a device as well as a method for transmitting the service in the integrated network and a system and a device.
Owner:HUAWEI TECH CO LTD +1
Authority authentication method, device and system
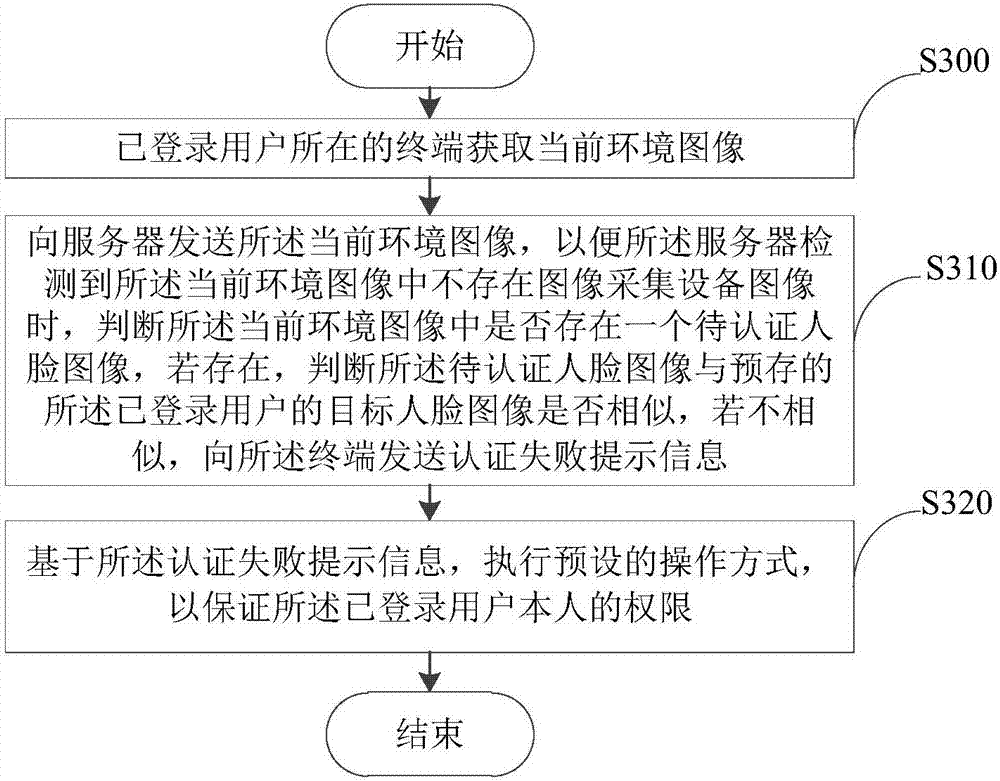
InactiveCN107403086AImplement real identity authenticationGuarantee authorityCharacter and pattern recognitionDigital data authenticationFace detectionThe Internet
The embodiment of the invention provides an authority authentication method, device and system and relates to the technical field of internet. The method comprises the following steps: acquiring a current environmental image by a terminal at which a logged user is positioned; transmitting the current environmental image to a server, so that whether a to-be-authenticated facial image exists in the current environmental image or not is judged when the server detects that an image of image acquisition equipment does not exist in the current environmental image; if yes, judging whether the to-be-authenticated facial image is similar to a prestored target facial image of the logged user; if no, transmitting authentication failure prompt information to the terminal; and executing a preset operating mode based on the authentication failure prompt information, thereby ensuring the authority of the logged user. According to the method, real identity authentication of the user is realized by performing face detection on the acquired environmental image, the authority of the logged user is ensured, and the security of the system is improved.
Owner:SHANGHAI ZHONGXIN INFORMATION DEV
Method and device for providing and acquiring security identity information
ActiveCN109636411AGuaranteed accuracyGuarantee authorityDigital data authenticationCommerceTrusted application
Embodiments of the invention provide a method and a device for providing and acquiring security identity information. Under the scene that identity verification needs to be carried out offline or identity information is provided offline, a user can scan a two-dimensional code displayed by a service party through a trusted application, and the two-dimensional code is generated by registering the service party with a registration platform in advance. After the credible application scans the code, the credible application obtains which identity information the service party needs by inquiring inthe registration platform, and then the identity information of the user is collected and obtained. And then, the trusted application sends the acquired identity information to a verification source for verification, encrypts the verified identity information, and forwards the encrypted identity information to a service party through the registration platform.
Owner:ADVANCED NEW TECH CO LTD
Lexicon construction method and computing device
PendingCN110704391AGuarantee authorityGuaranteed professionalismNatural language data processingStructured data retrievalProgramming languageEngineering
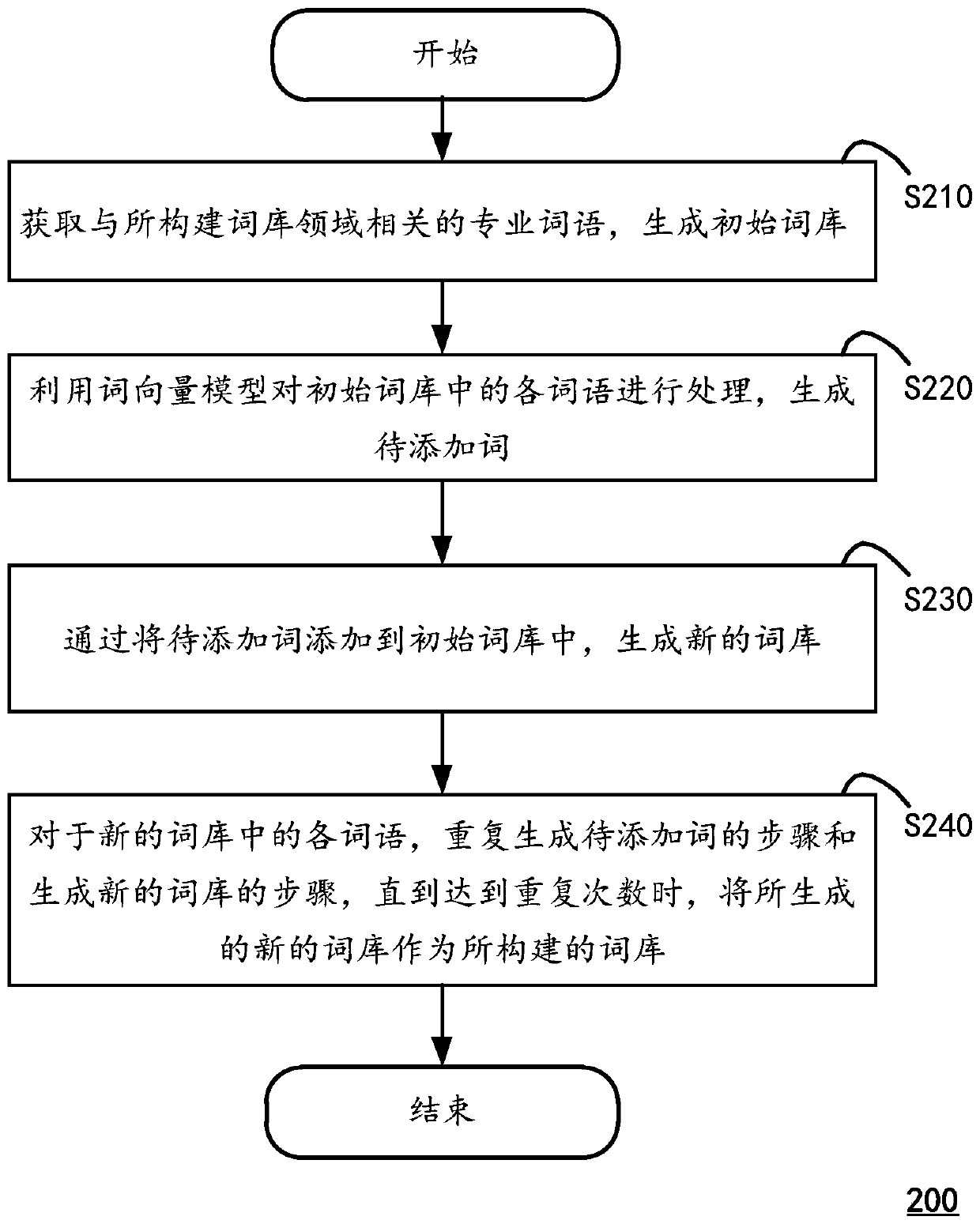
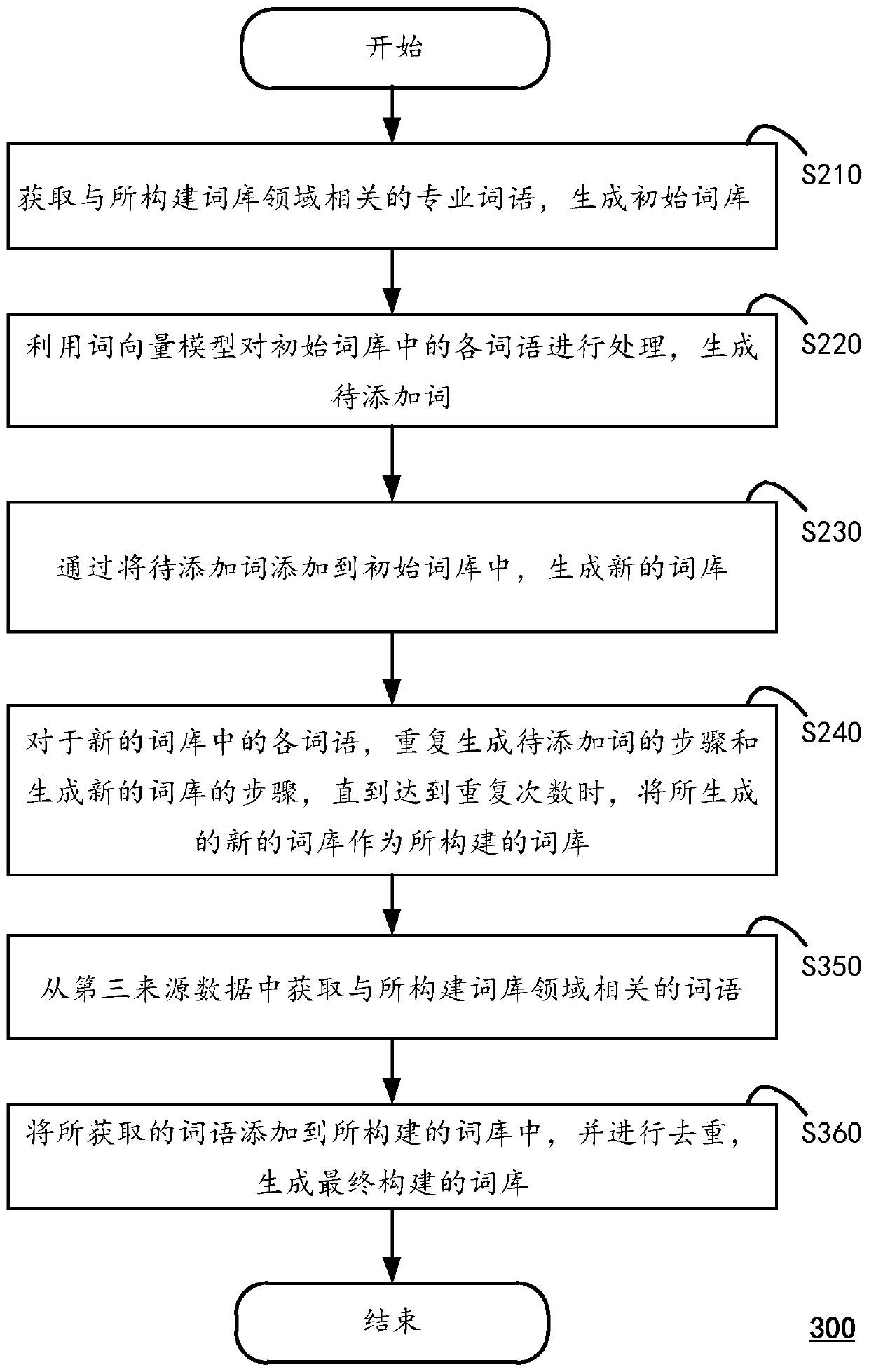
The invention discloses a lexicon construction method which comprises the following steps: acquiring professional words related to the field of constructed lexicons, and generating an initial lexicon;utilizing the word vector model to process each word in the initial word bank to generate a word to be added, the word to be added being a word similar to each word in the initial word bank; adding words to be added into an initial word bank to generate a new word bank; and for each word in the new word bank, repeating the step of generating the word to be added and the step of generating the newword bank until the number of repetitions is reached, and taking the generated new word bank as the constructed word bank. The invention also discloses a corresponding computing device.
Owner:CHEZHI HULIAN BEIJING SCI & TECH CO LTD
Detector and detecting method for three parameters of escalator
InactiveCN103411787AGuarantee authorityGuaranteed to be scientificStructural/machines measurementEscalatorsLaser rangingEngineering
Disclosed are a detector and detecting method for three parameters of an escalator. The detector for the three parameters of the escalator comprises a main test device, a secondary test device, a laser range finder and an electric box, the secondary test device comprises a fixing base, suckers, a fixed disc, a movable disc and emitting and receiving heads, three end portions of the fixing base are respectively provided with one sucker, the fixed disc is perpendicularly fixed in the middle of the fixing base, the included angle between the center line of the fixed disc and the center line of an upper transverse pipe of the fixing base ranges from 32 degrees to 42 degrees, one side of the fixed disc is connected with the movable disc, the top of the movable disc is provided with a probe frame, and the emitting and receiving heads are fixed at the two ends of the probe frame; the main test device and the secondary test device are identical, and the laser range finder and the electric box are further fixed on the probe frame of the main test device; a steel wire rope is connected between the main test device and the secondary test device. The three parameters of the escalator can be automatically detected, and authority, scientificity, seriousness and authenticity of an examining report are guaranteed.
Owner:SHANDONG SPECIAL EQUIP INSPECTION LIAOCHENG BRANCH
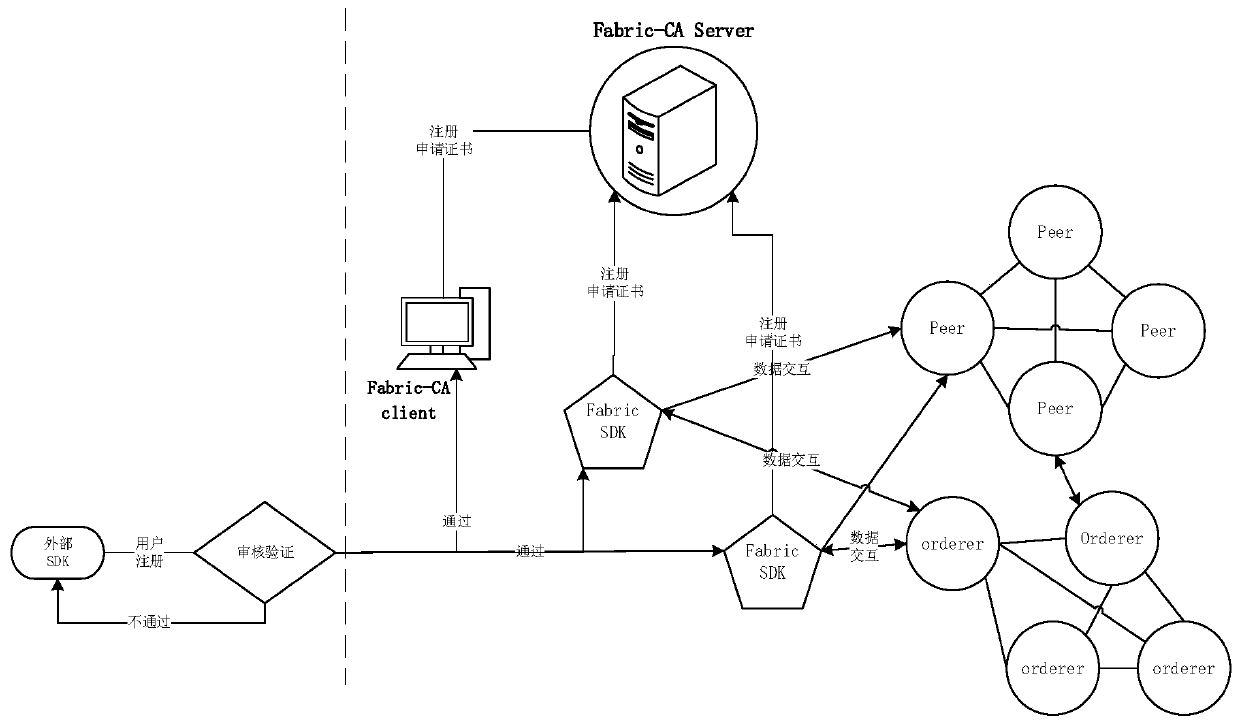
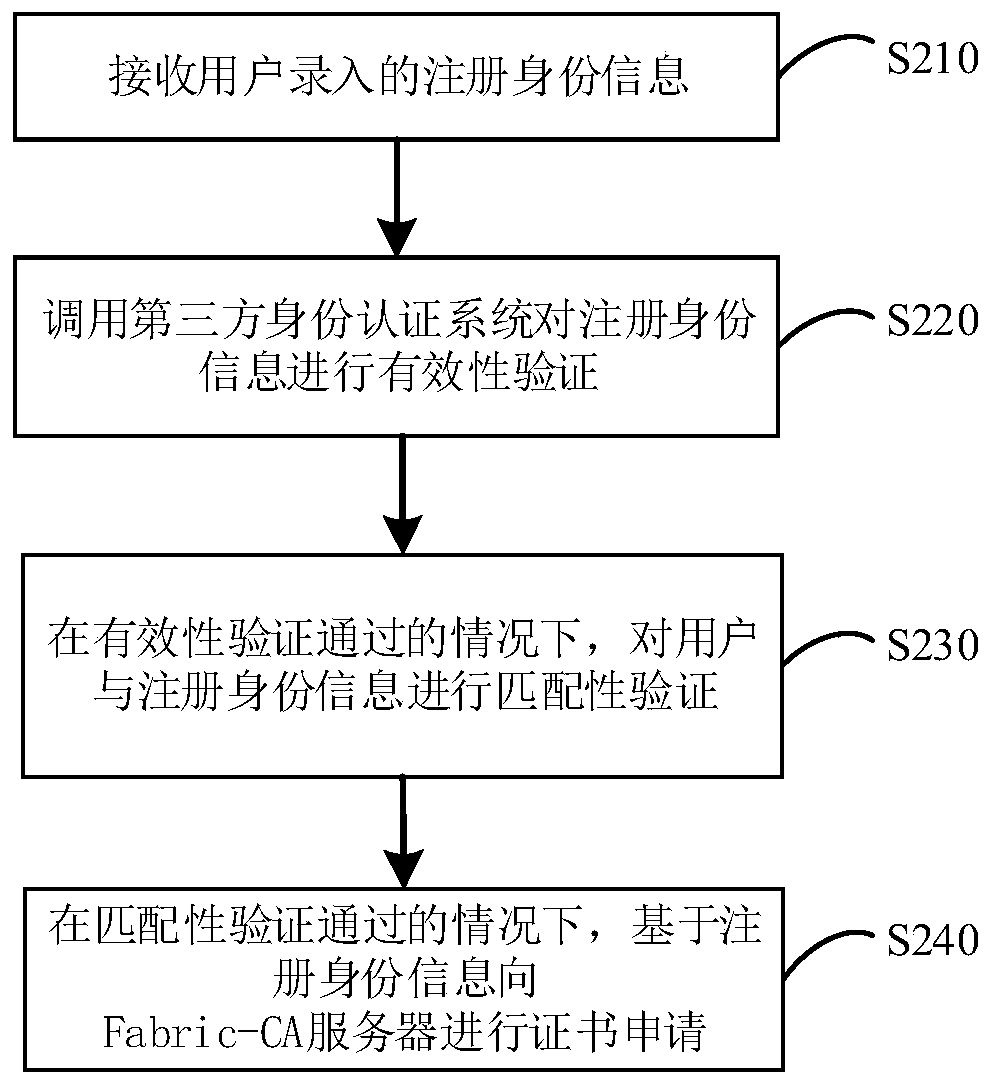
Acquisition method and acquisition device for block chain network Fabric-CA digital certificate
InactiveCN110135992ASafety and Efficiency GuaranteeSolve the problem of weak regulationFinanceProtocol authorisationChain networkAuthentication system
The invention discloses an acquisition method and acquisition device for a block chain network Fabric-CA digital certificate. The method comprises the steps that registration identity information input by a user is received; calling a third-party identity authentication system to carry out validity verification on the registered identity information; carrying out matching verification on the userand the registration identity information under the condition that the validity verification is passed; under the condition that the matching verification is passed, based on the registration identityinformation, certificate application is carried out by the Fabric-CA server to obtain Fabric-CA digital certificate. According to the invention, the registration identity information of the user is audited and verified in advance, and application and acquisition of the Fabric-CA digital certificate are carried out on the registration identity information passing the verification; the problem of weak supervision of the block chain is solved.
Owner:北京智签科技有限公司 +1
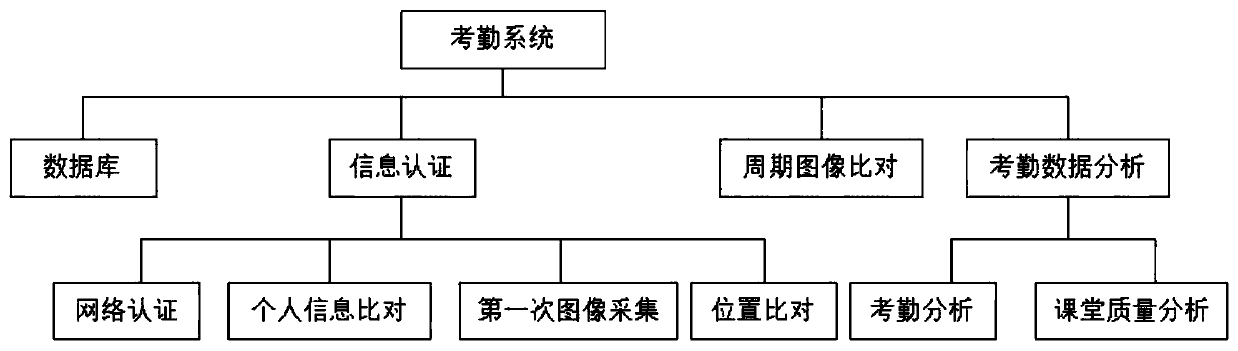
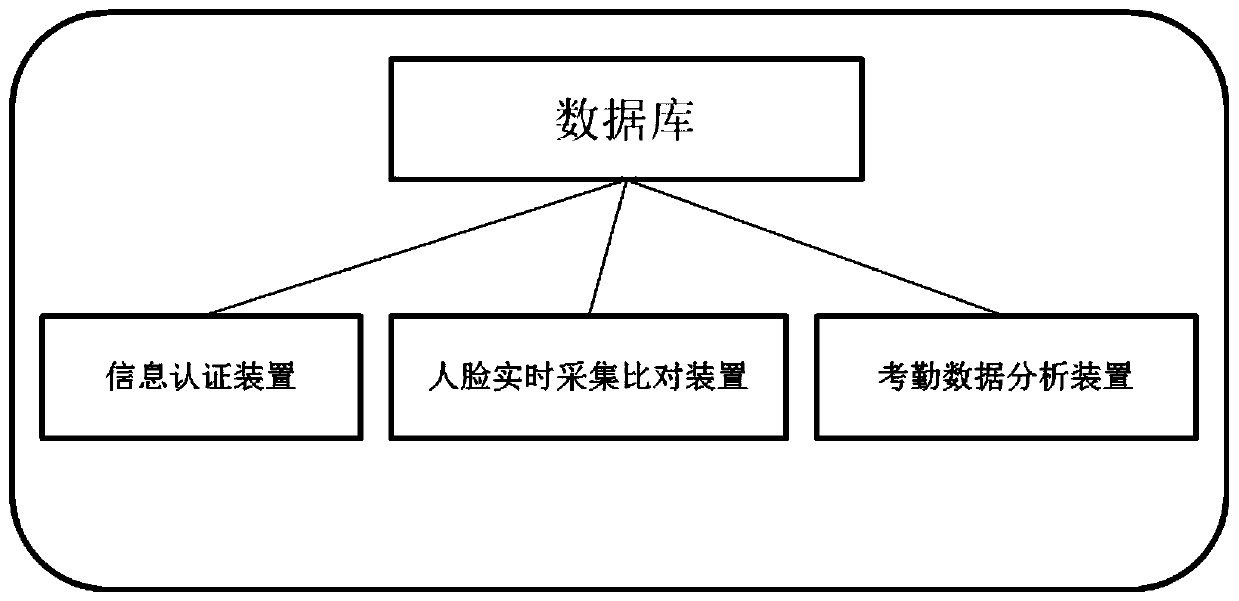
College student attendance system based on face recognition and online real-time data
ActiveCN110533788AGuaranteed growthGuarantee authorityRegistering/indicating time of eventsData processing applicationsReal-time dataImaging data
The invention provides a college student attendance system based on face recognition and online real-time data. Curriculum and teacher information consistent with identity verification information such as student face image data, fingerprint information or the like is stored in the attendance system in advance; before a curriculum is carried out, students log in the system to complete identity verification and curriculum confirmation; and in class, the attendance conditions of the students and the quality condition of the current class are analyzed based on student face image and position information collection in a certain period. A wireless network technology, a face recognition technology and a face comparison technology are fused, so that the accuracy and specialty of student attendance are achieved, and the incompleteness of manual attendance or single-mode attendance is avoided.
Owner:合肥智圣新创信息技术有限公司
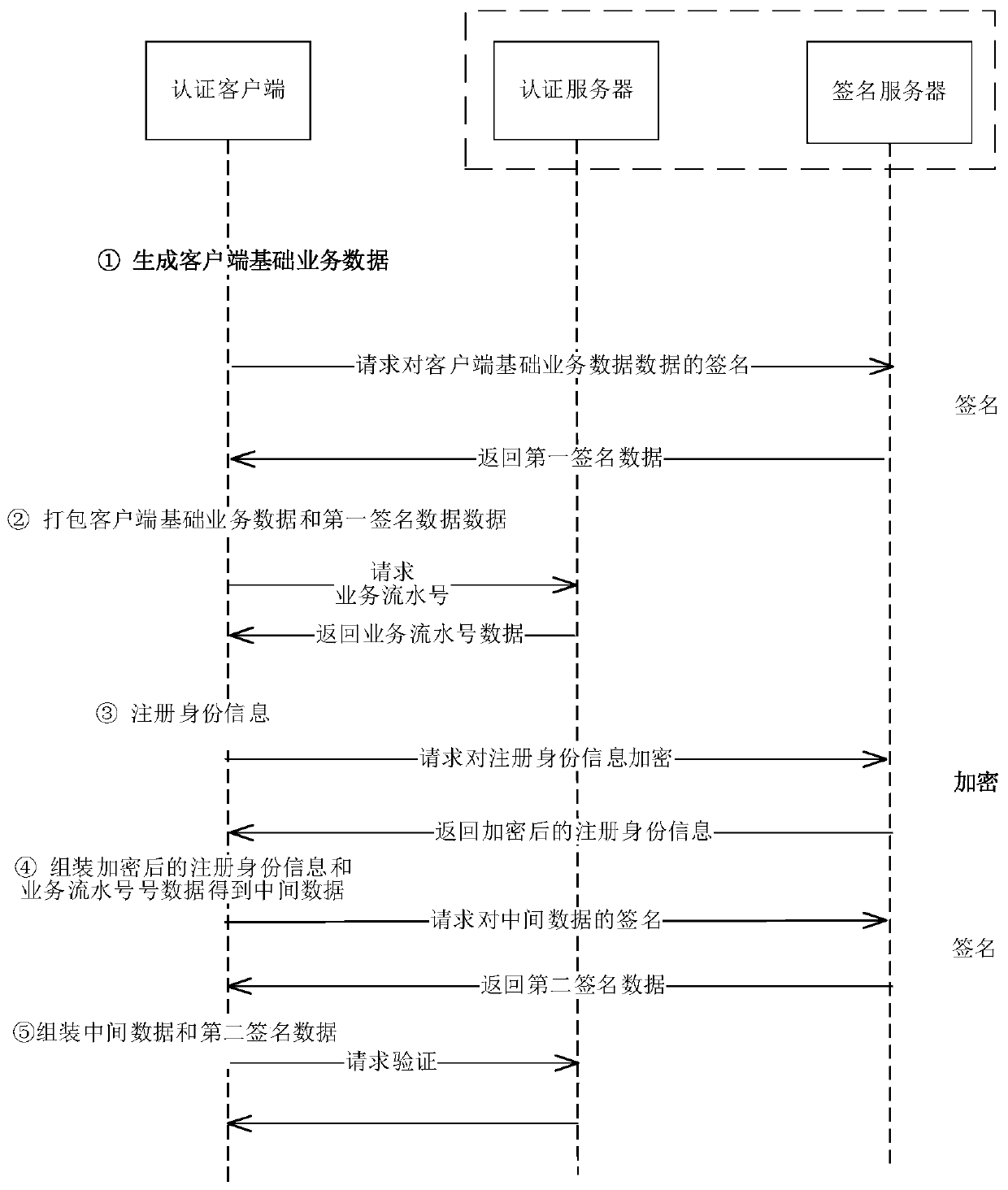
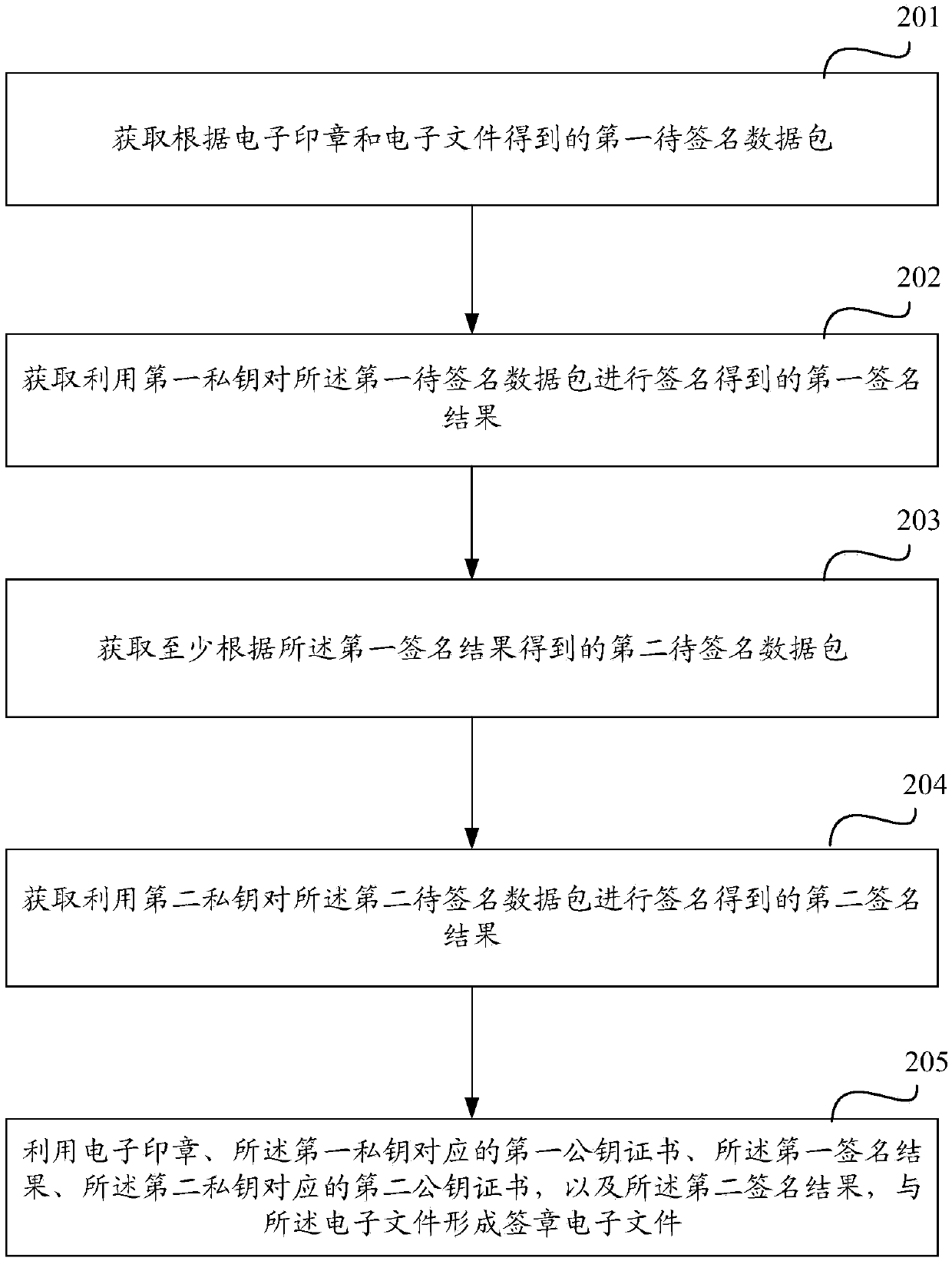
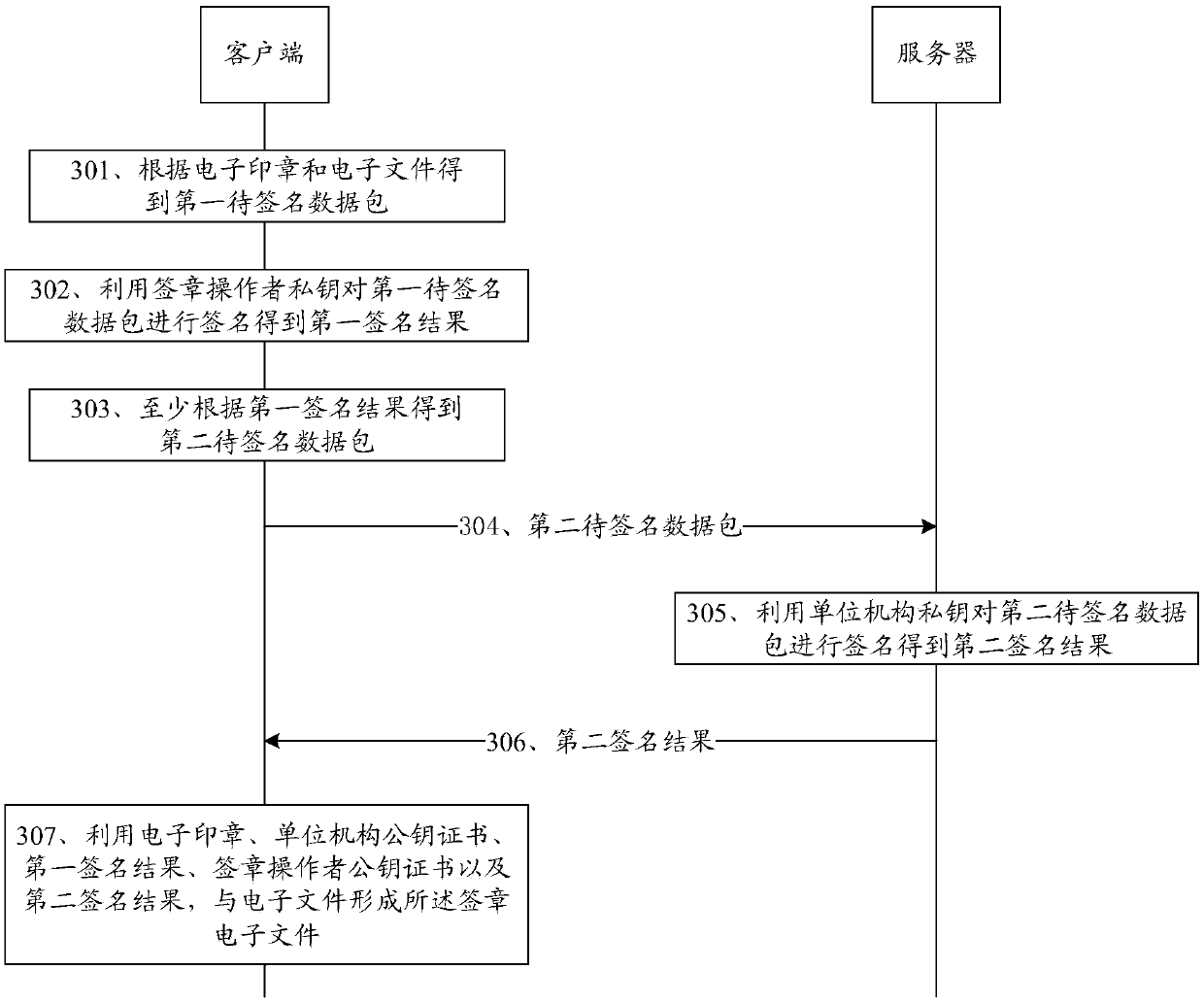
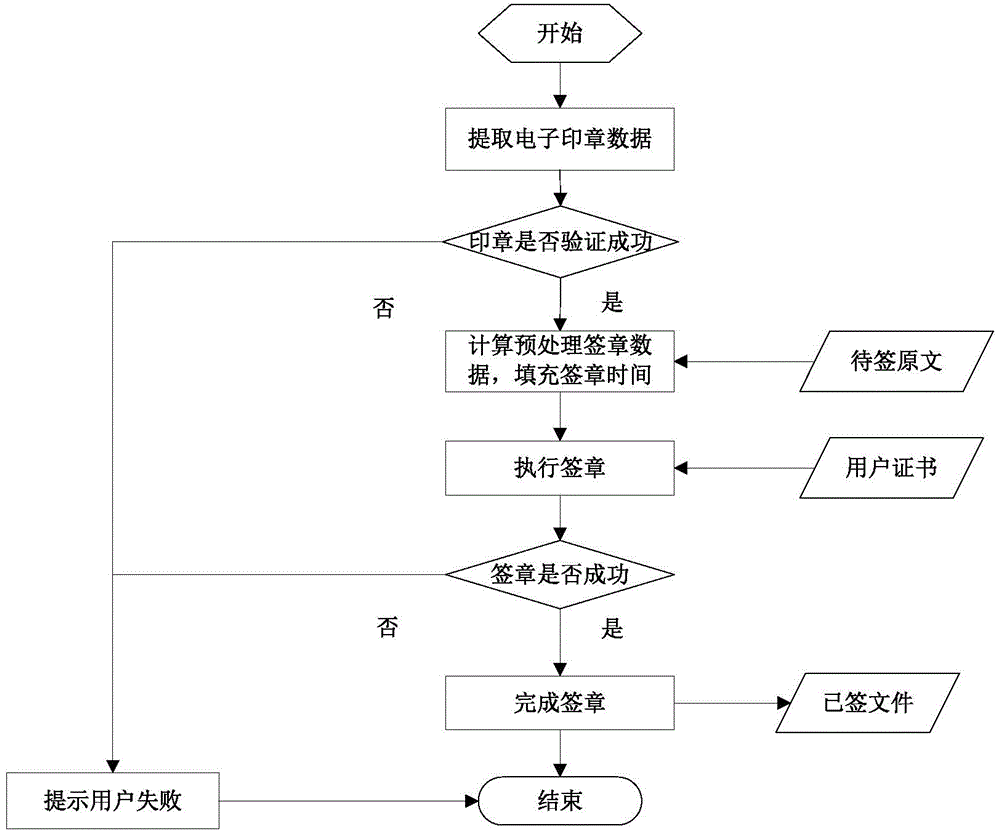
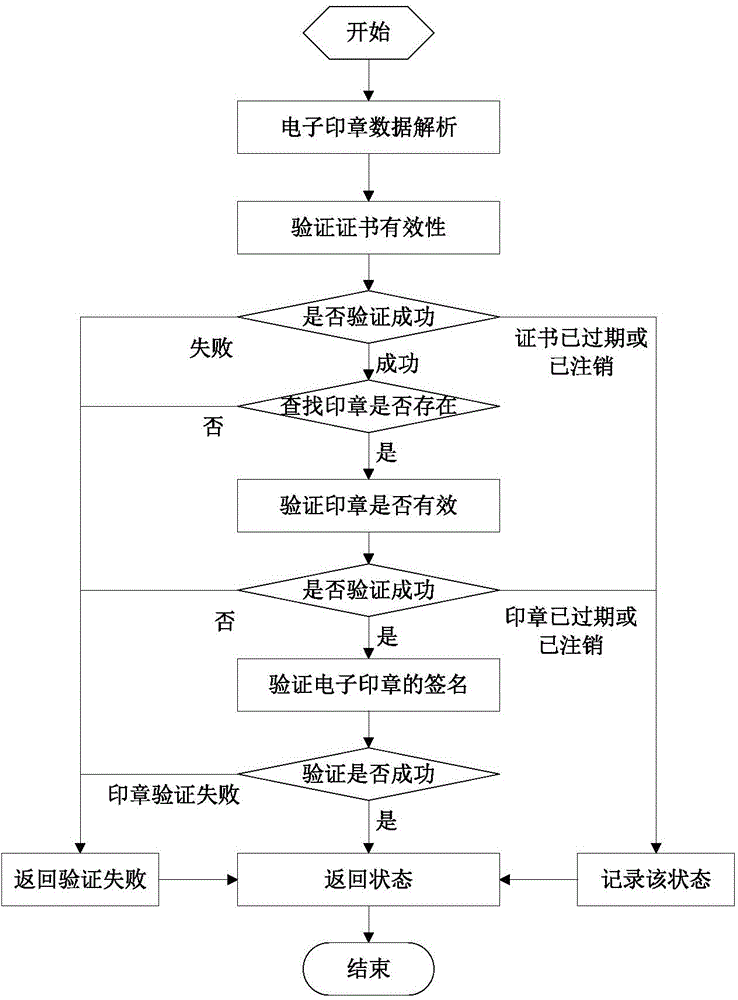
Electronic signature and seal verification method and device
PendingCN111092729AGuarantee authorityImprove efficiency of retroactive stamping operatorsUser identity/authority verificationDigital data protectionData securityEngineering
The embodiment of the invention relates to the technical field of data security, in particular to an electronic signature and verification method and device, which are used for improving the efficiency of tracing a signature operation executor while maintaining the authority of an electronic seal. The method comprises the steps of obtaining a first to-be-signed data packet obtained according to anelectronic seal and an electronic file; acquiring a first signature result obtained by signing the first to-be-signed data packet by using a first private key; obtaining a second to-be-signed data packet obtained at least according to the first signature result; obtaining a second signature result obtained by signing the second to-be-signed data packet by using a second private key; and forming asignature electronic file with the electronic file by utilizing the electronic seal, a first public key certificate corresponding to the first private key, the first signature result, a second publickey certificate corresponding to the second private key and the second signature result.
Owner:方正国际软件(北京)有限公司
TBM-carried rock slag online compressive strength testing system and method
ActiveCN110823704AMeet the requirements of real-time online analysis and testingSatisfy faster requirementsMaterial strength using tensile/compressive forcesUsing optical meansVision processingGrating
The invention discloses a TBM-carried rock slag online compressive strength testing system and a TBM-carried rock slag online compressive strength testing method. The TBM-carried rock slag online compressive strength testing system comprises a robot, a grating projection device, a visual processing device and a compressive strength testing device, wherein the robot is used for acquiring rock slagin the TBM tunneling process; the grating projection device can project structured light to the tested rock slag to form a two-dimensional light bar image in the surface shape of the rock slag; the visual processing device can calculate to obtain a rock slag three-dimensional shape model according to the two-dimensional light bar image shot and projected onto the rock slag surface to form distortion; a loading point position is calculated by means of a rock slag three-dimensional shape model, and whether the tested rock slag meets the requirements or not through the distance between the loading points is judged; and the compressive strength testing device is used for automatically testing the compressive strength of the tested rock slag meeting the requirements. The TBM-carried rock slag online compressive strength testing system and the TBM-carried rock slag online compressive strength testing method have the beneficial effects of being high in timeliness, high in automation degree, safe, economical and the like, effectively solves the problem that surrounding rock strength information of current TBM construction is difficult to obtain in real time, and real-time surrounding rockcondition information and a control parameter decision basis are provided for TBM tunneling.
Owner:山东百廿慧通工程科技有限公司
Electronic signature realization method and system for electronic invoice
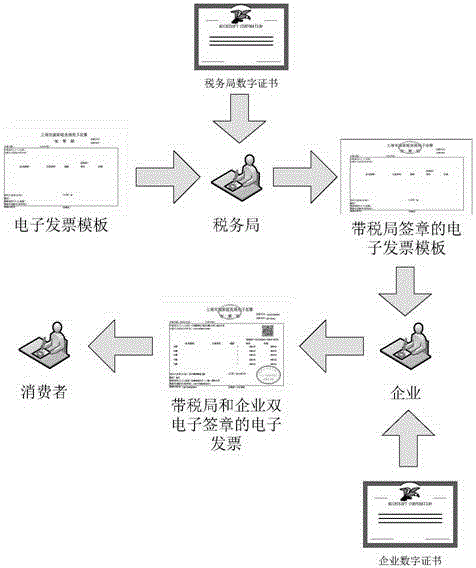
InactiveCN105809009AGuarantee authenticity and authorityGuaranteed non-repudiationFinanceDigital data protectionInvoiceElectronic signature
The invention discloses an electronic signature realization method and system for an electronic invoice. In one embodiment, the method comprises a tax bureau signature step of generating an electronic tax bureau signature of a tax bureau on a template of an electronic invoice, an enterprise signature step of generating the electronic invoice according to the template of the electronic invoice and transaction data and generating an electronic enterprise signature of a bill provider in the electronic invoice, a tax bureau signature verification step of verifying whether the template used by the electronic invoice is modified or not according to the electronic tax bureau signature, and an enterprise signature verification step of verifying whether the electronic invoice is provided by the bill provider or not according to the electronic enterprise signature. According to the method and system, the authority and authenticity of an invoice source are ensured and the completeness and undeniability of the electronic invoice content are ensured.
Owner:AEROSPACE INFORMATION
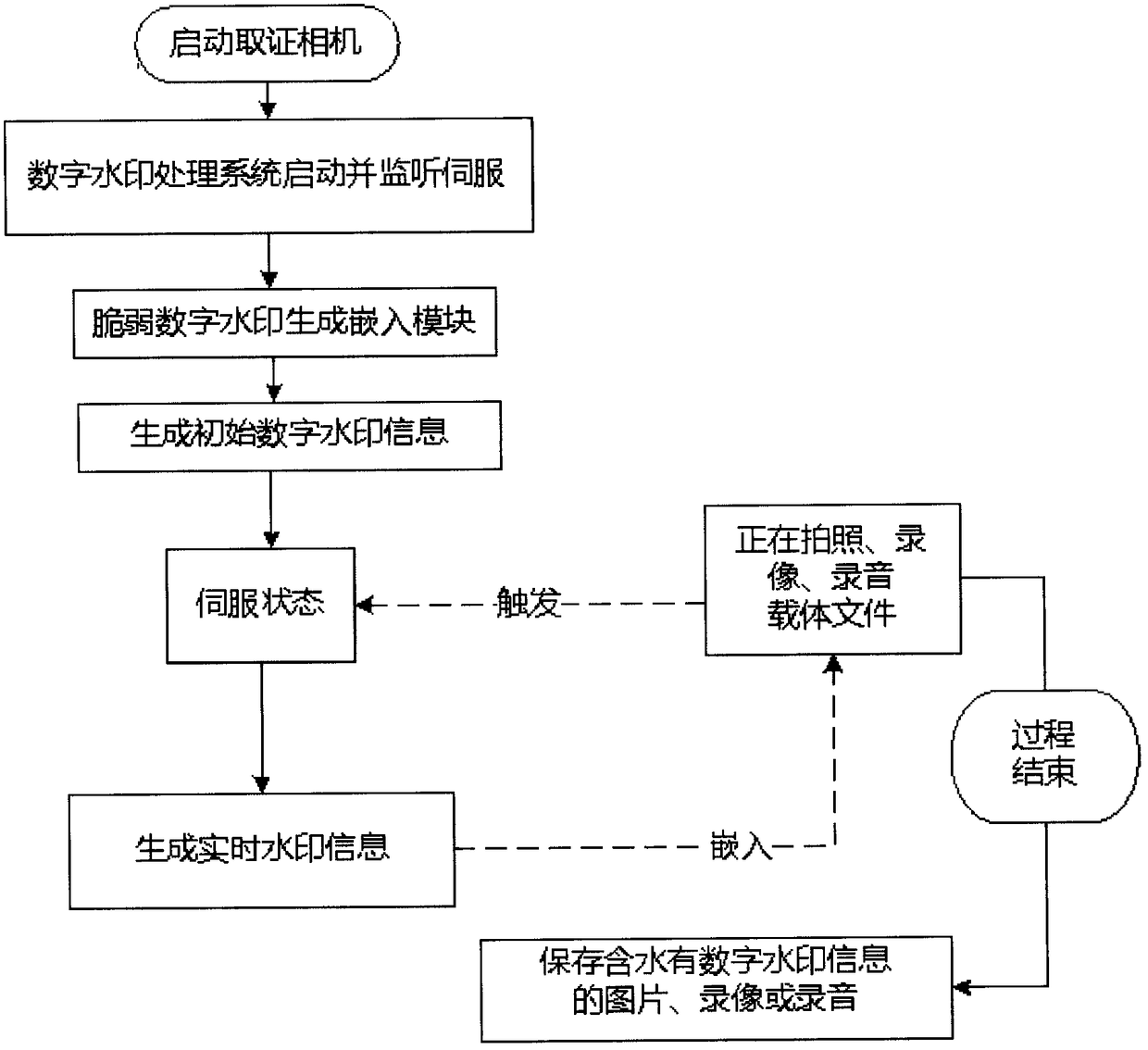
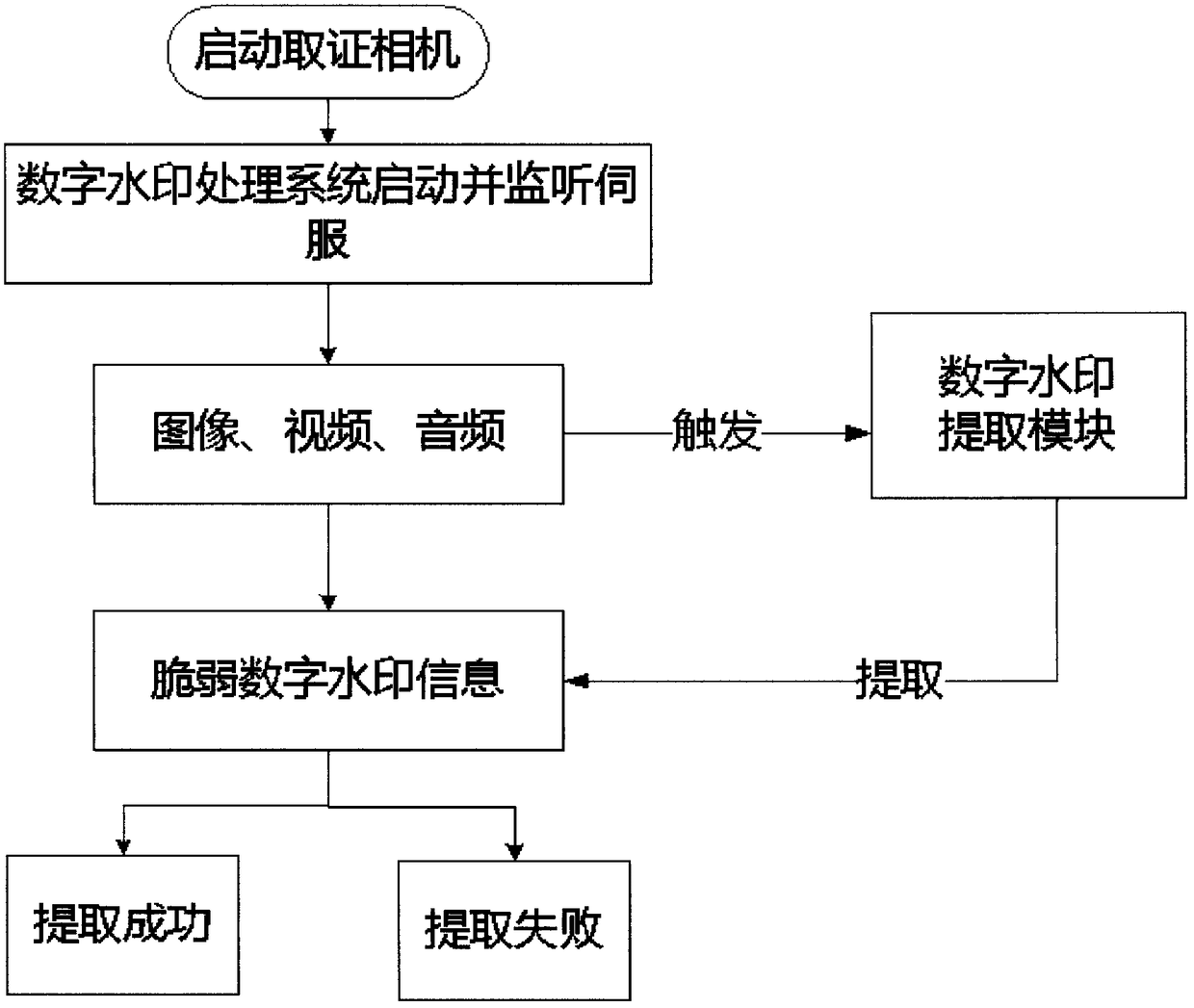
Multimedia digital watermark evidence taking mobile phone
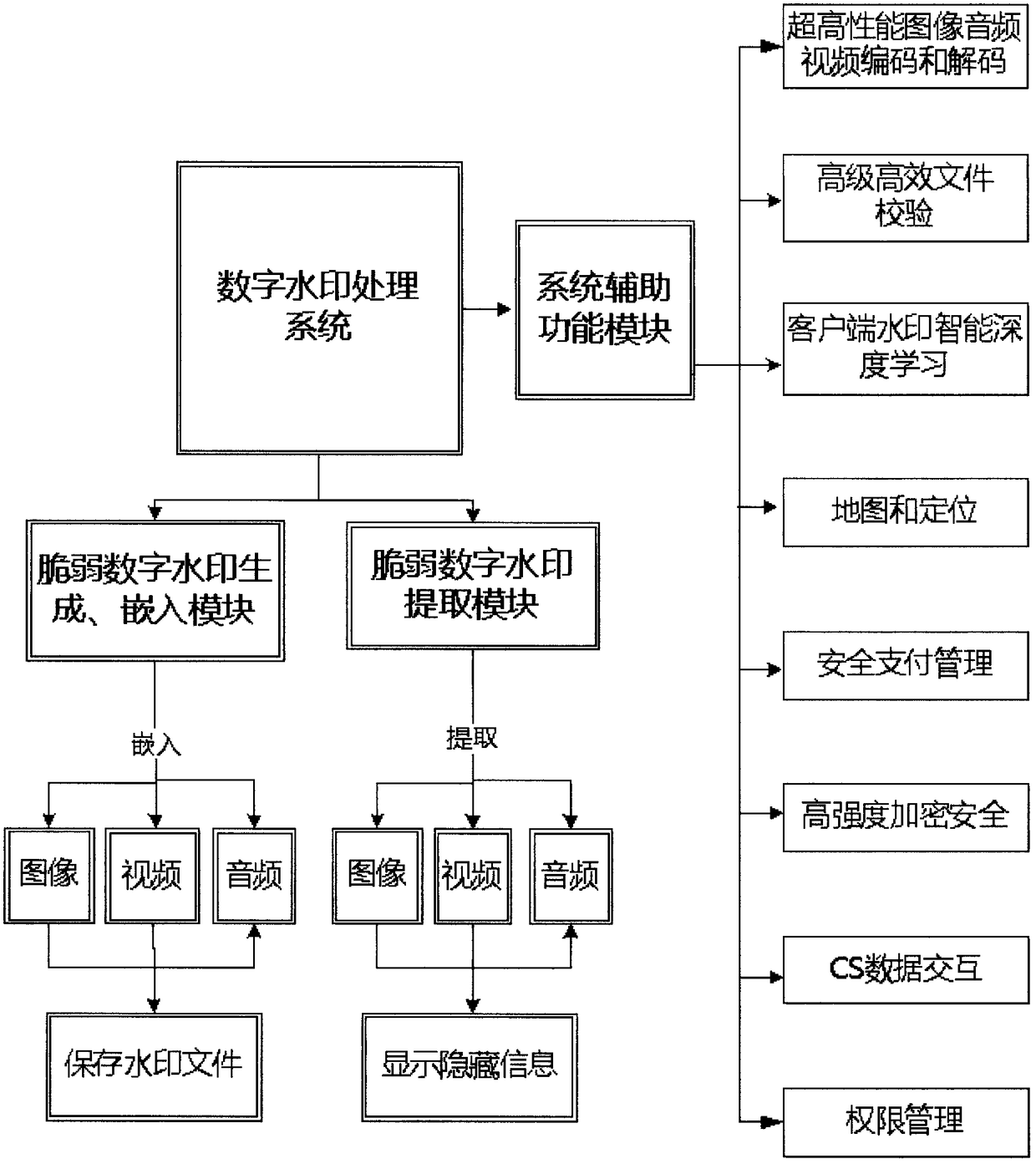
ActiveCN109151157AGain credibilityHave completeSubstation equipmentDigital video signal modificationFragilityDigital evidence
The invention discloses a multimedia digital watermark evidence taking mobile phone. The multimedia digital watermark evidence taking mobile phone is an intelligent evidence taking mobile phone whichuses the unique stability, concealment, security and fragility of a fragile digital watermark to ensure the integrity, the authenticity, the stability, the reliability and the authority of photographed and recorded multimedia data based on an image, audio and video fragile digital watermark embedding and extraction technology. When a user uses the mobile phone, imperceptible and unmodifiable fragile digital watermark information with unique identity confirmation is embedded in real time in a photographed image, audio and video. The image or the audio or the video with the fragile watermark canbe normally used and distributed but can not be modified manually. The authenticity of a file can be identified according to whether the photographed digital file contains the digital watermark information. The evidence taking process is quick, efficient, accurate, safe and convenient. The evidence taking content has the uniqueness of a digital evidence and the legal authority of evidence use, and the multimedia digital watermark evidence taking mobile phone disclosed in the invention can be used for evidence taking and recording in fields such as judicature, law enforcement and claim.
Owner:CHENGDU YUFEI INFORMATION ENG
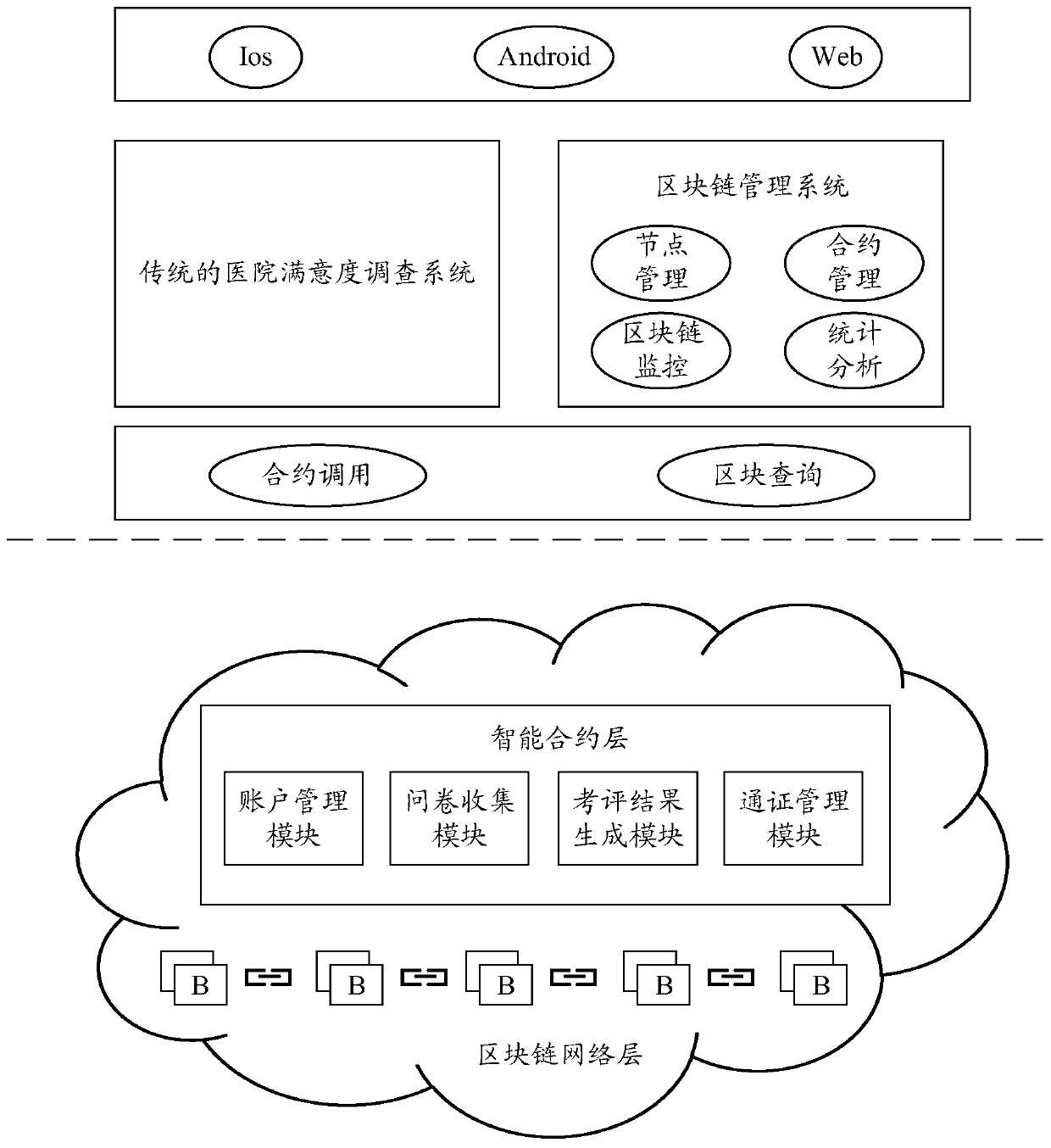
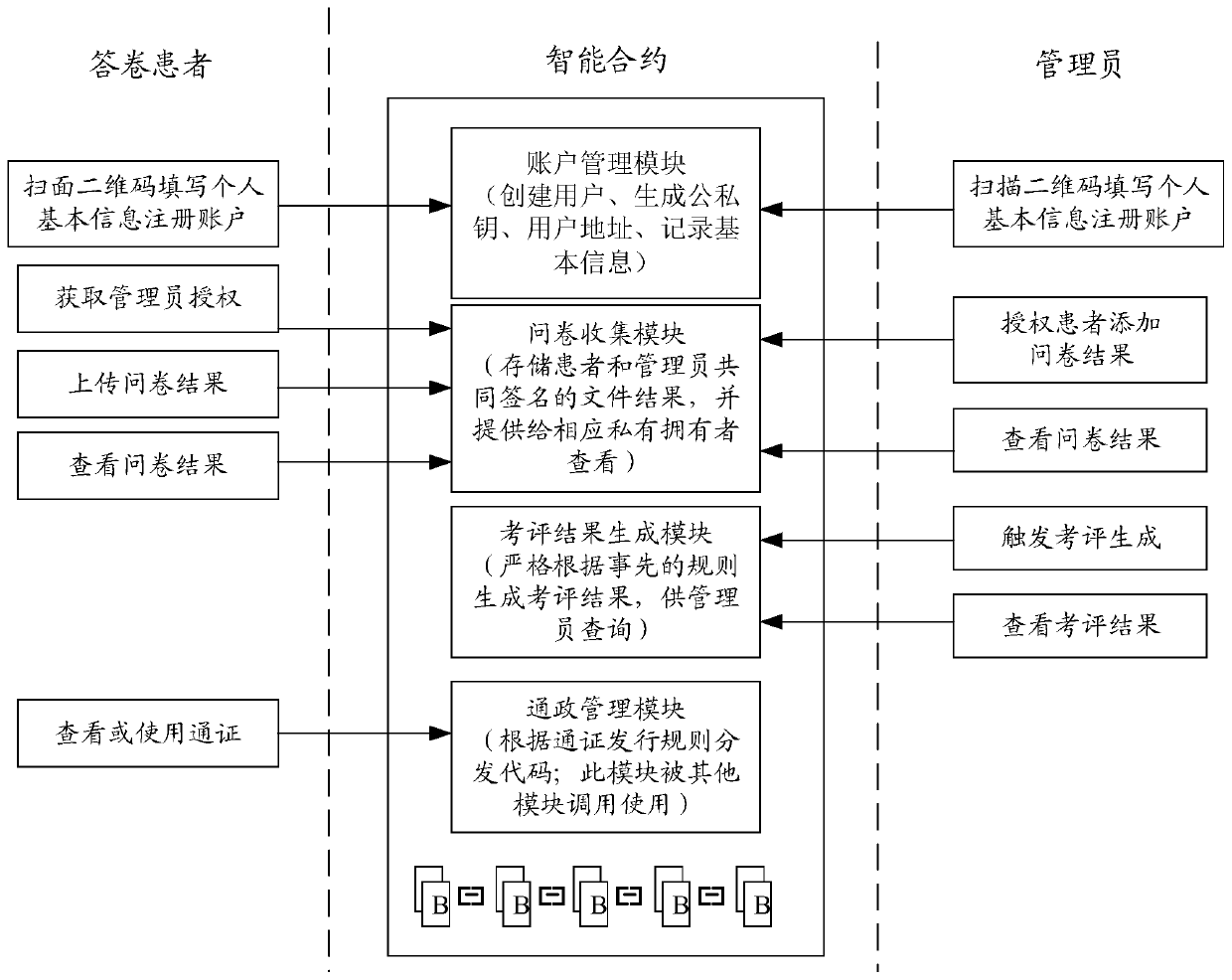
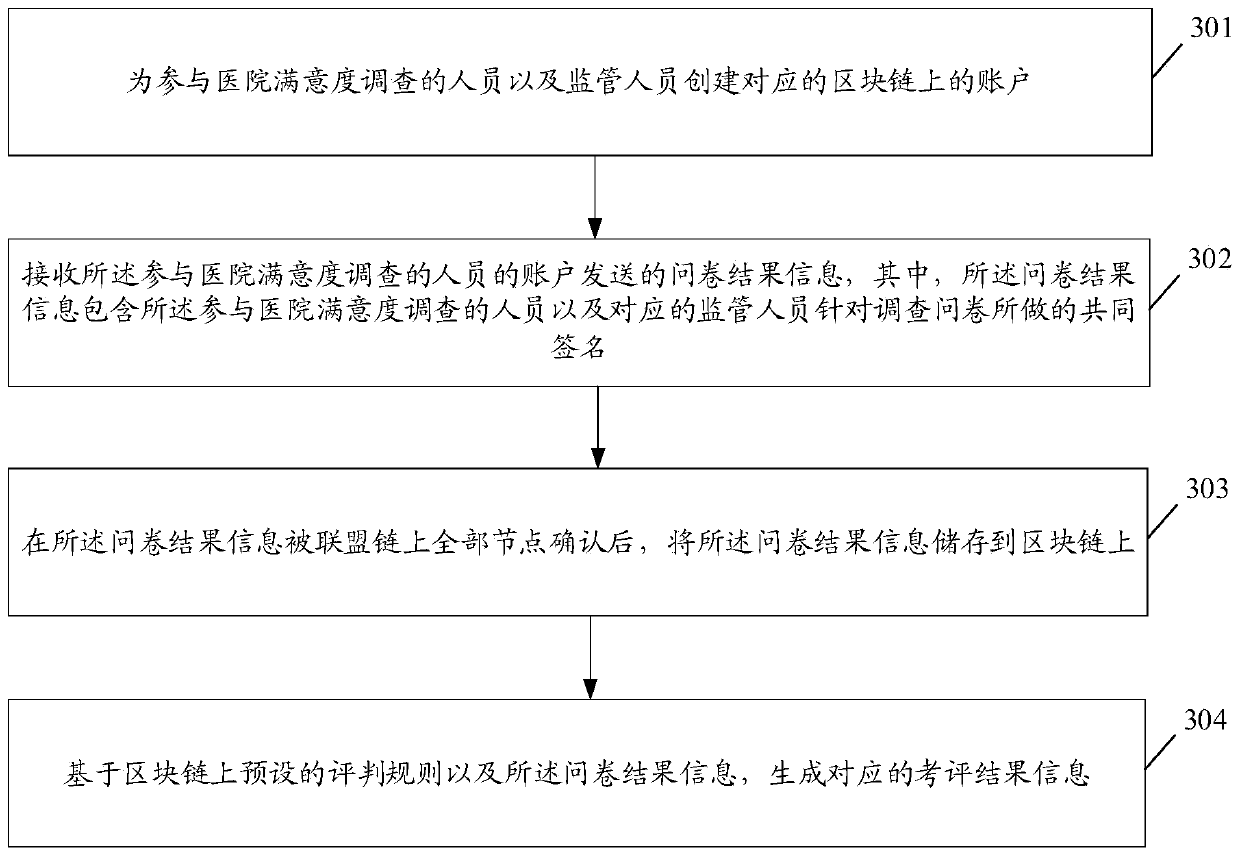
Hospital satisfaction survey method and system based on block chain and computer readable storage medium
PendingCN111403009AGuarantee authorityGuaranteed security cannot be tampered withDigital data protectionHealthcare resources and facilitiesEvaluation resultSurvey methodology
The invention discloses a hospital satisfaction survey method and system based on a block chain and a computer readable storage medium. The method comprises the steps that accounts on corresponding block chains are created for personnel participating in a hospital satisfaction survey and for supervisors; questionnaire result information sent by the accounts of the personnel participating in the hospital satisfaction survey is received, wherein the questionnaire result information comprises common signatures made by the personnel participating in the hospital satisfaction survey and corresponding supervisors for questionnaires; after the questionnaire result information is confirmed by all nodes on an alliance chain, the questionnaire result information is stored in a block chain; and corresponding evaluation result information is generated based on a preset evaluation rule on the blockchain and the questionnaire result information.
Owner:CHINA MOBILE COMM LTD RES INST +1
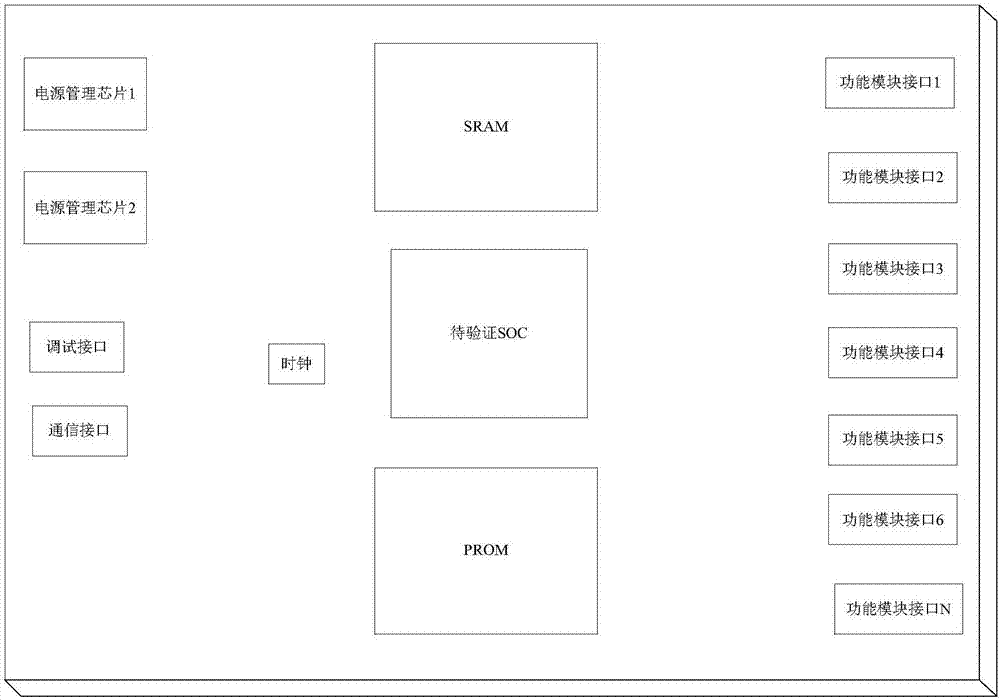
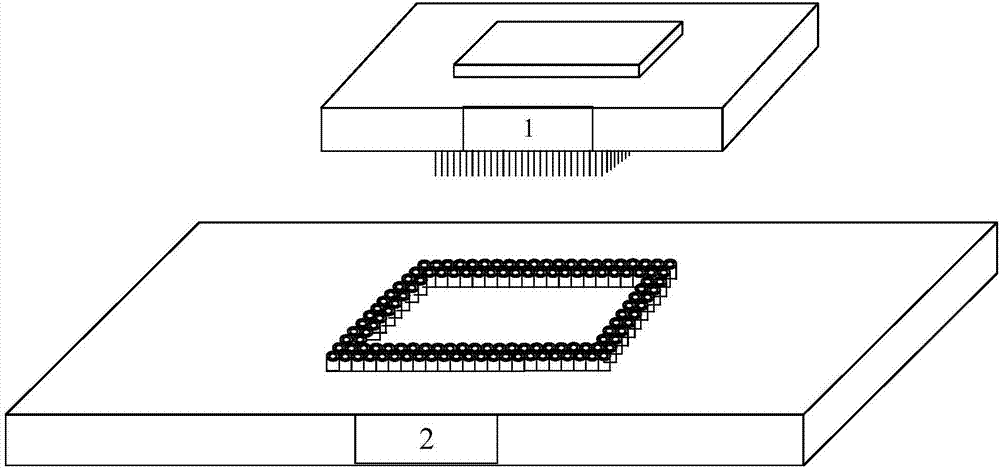
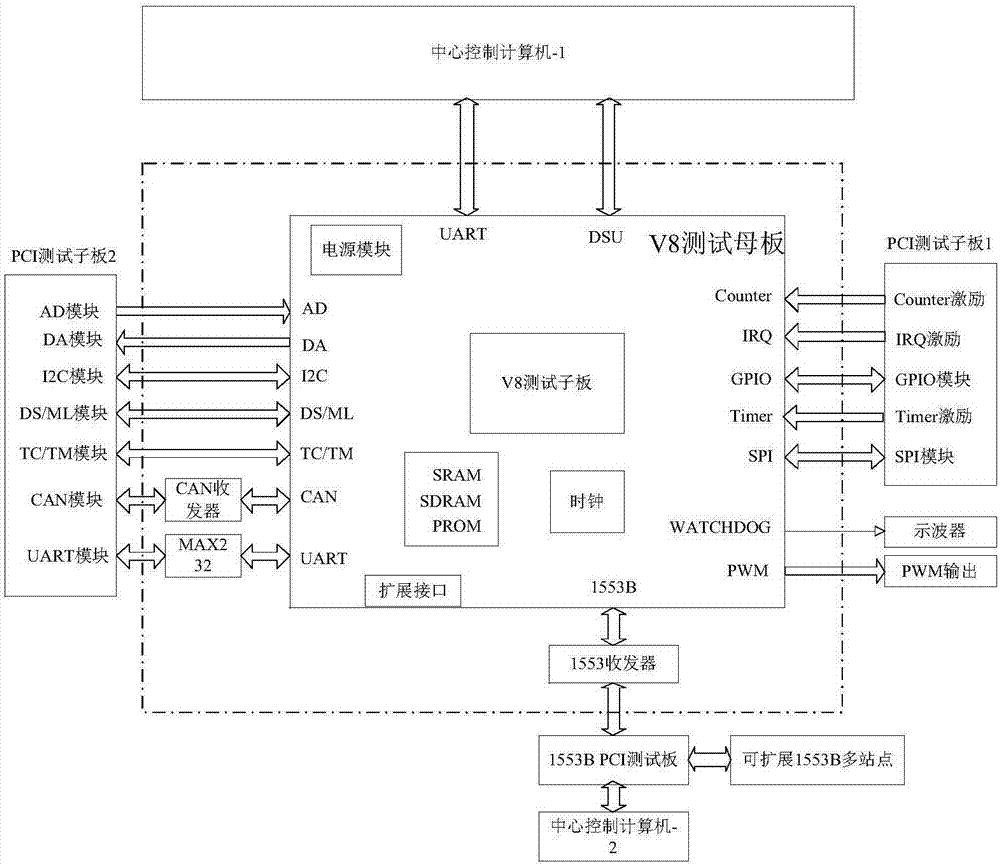
Single machine application verification system compatible with sparc V8 framework SOC
ActiveCN107368636AEasy to useGuaranteed maintenanceSpecial data processing applicationsSystem integrationComputer architecture
The invention relates to a single machine application verification system compatible with a sparc V8 framework SOC. The system comprises a single machine application verification board, an excitation source and a central control computer. For the single machine application verification board, application verification of multiple chips and system integration for a single chip are finished only by replacing chip daughter boards on the premise of maximized design of an application verification mother board; the excitation source required in an application verification process is subjected to standardized and maximized development, so that repeated use and maintenance of the single machine application verification system can be ensured, the development cost and cycle of the application verification system are greatly reduced and shortened, and system integration design and system simulation based on a to-be-verified chip can be realized; and application verification examples of mature modules are integrated in the central control computer, and the whole verification process is controlled, so that the efficiency and comprehensiveness of chip application verification are ensured, a universal platform for development by users is formed, and the performance of the verification system is exerted to the maximum extent.
Owner:XIAN MICROELECTRONICS TECH INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com