Method and device for providing and acquiring security identity information
An identity information and security technology, which is applied in the direction of secure communication devices, security devices, computer security devices, etc., can solve the problems of face verification breaches (attacks against real-name and real-person verification, etc., to achieve flexible and convenient verification and ensure accuracy. and authoritative effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
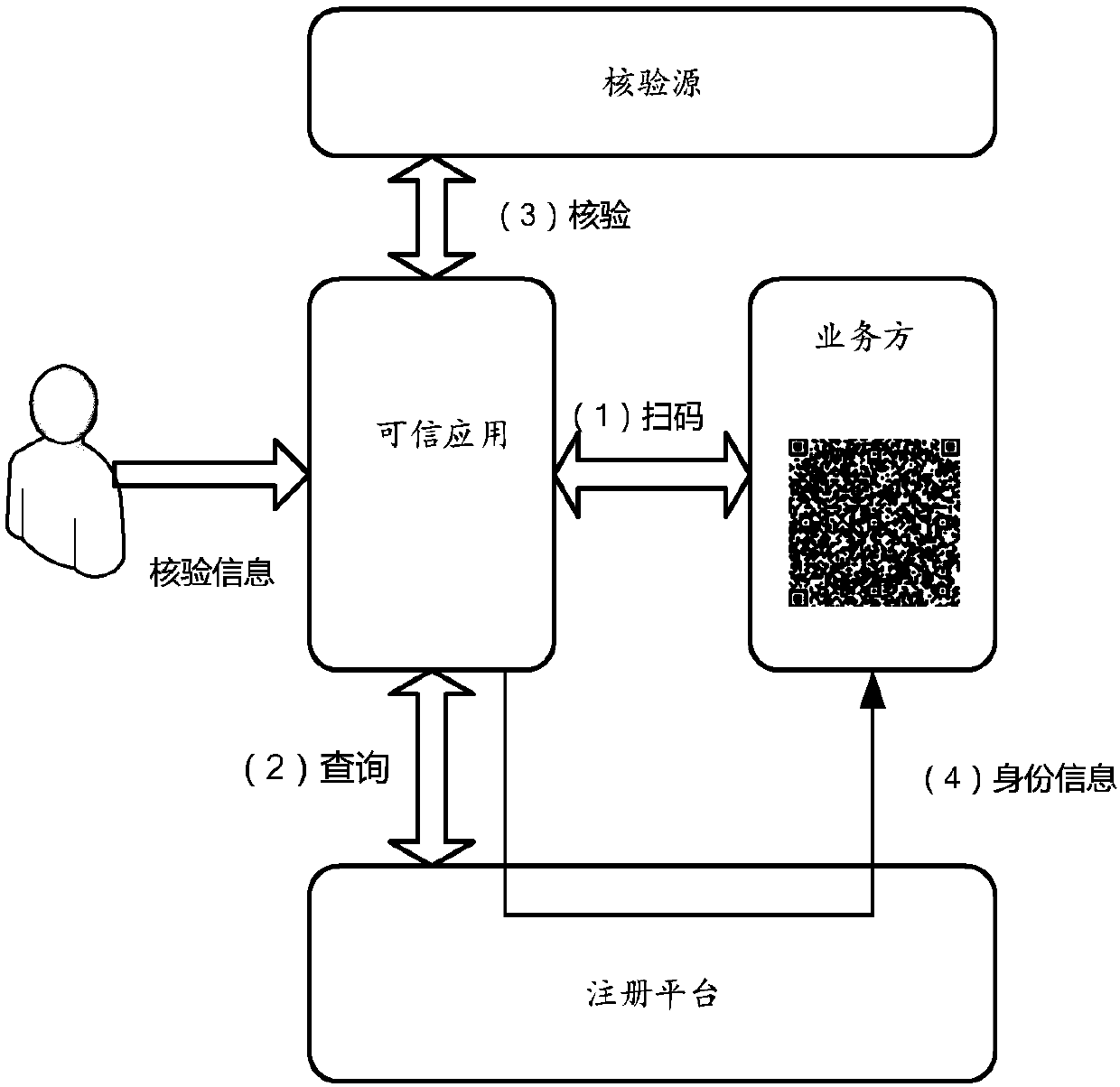
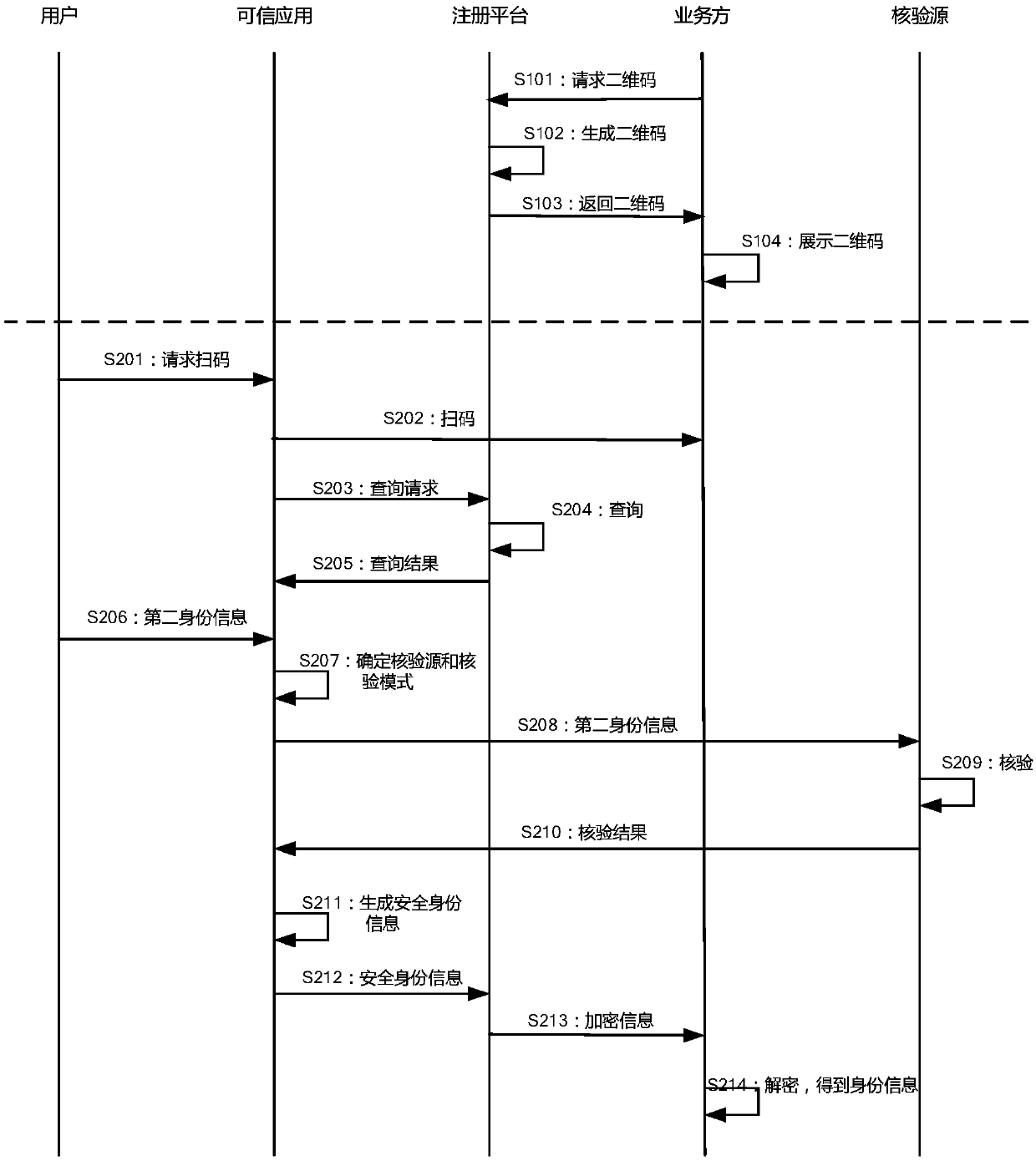
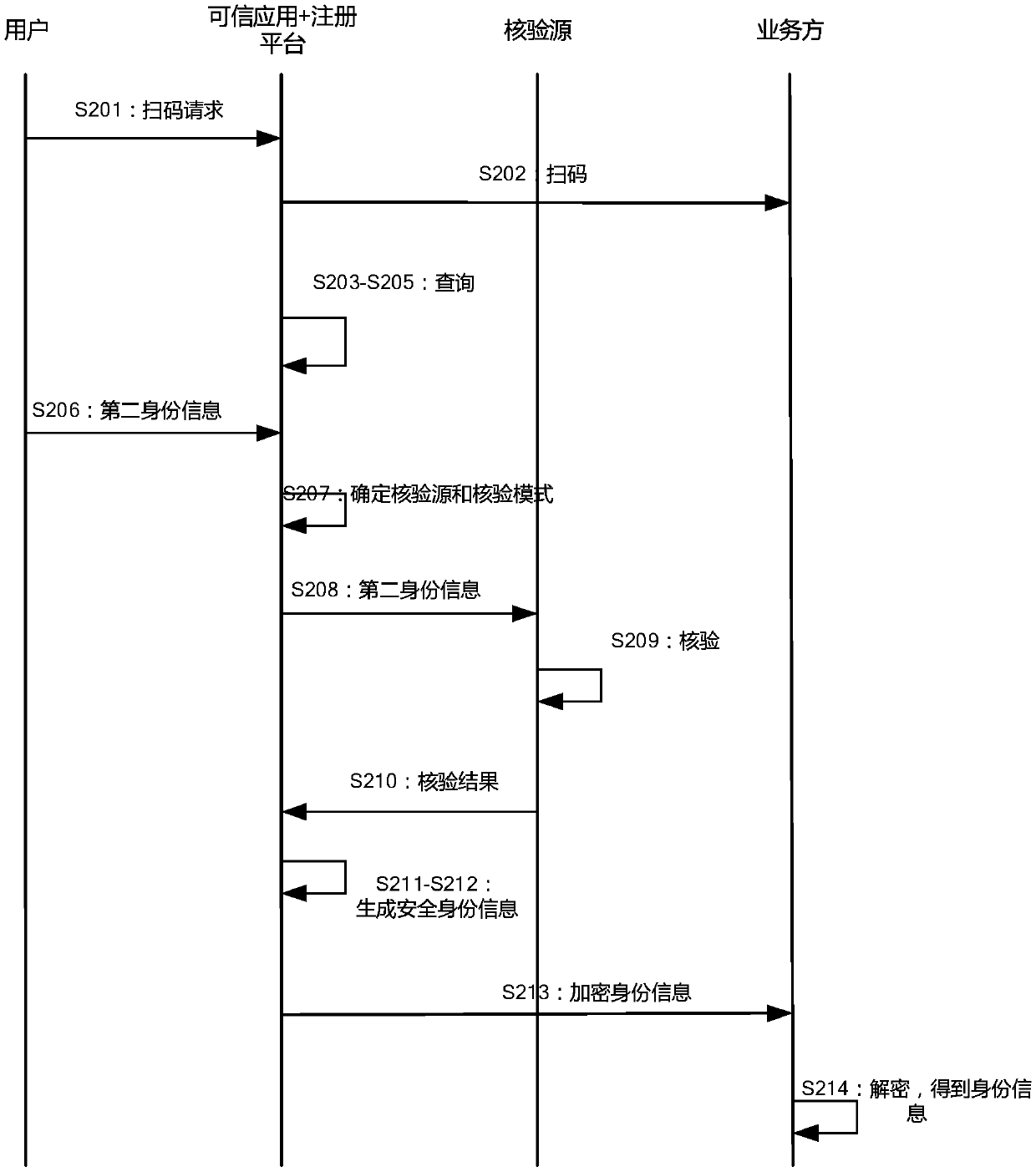
[0075] figure 1 It is a schematic diagram of an implementation scenario of an embodiment disclosed in this specification. according to figure 1 In the embodiment, each business party that needs security identity information (that is, the aforementioned scene merchant) registers with the registration platform in advance, and the registration platform generates its own two-dimensional code for each business party. In the scenario where identity verification or identity information needs to be provided offline, the user does not need to directly provide the identity information to the staff of the business party, but scans the QR code displayed by the business party through a trusted application, and then the acquired user Identity information is submitted to an authoritative third-party verification source for identity verification. After passing the ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com