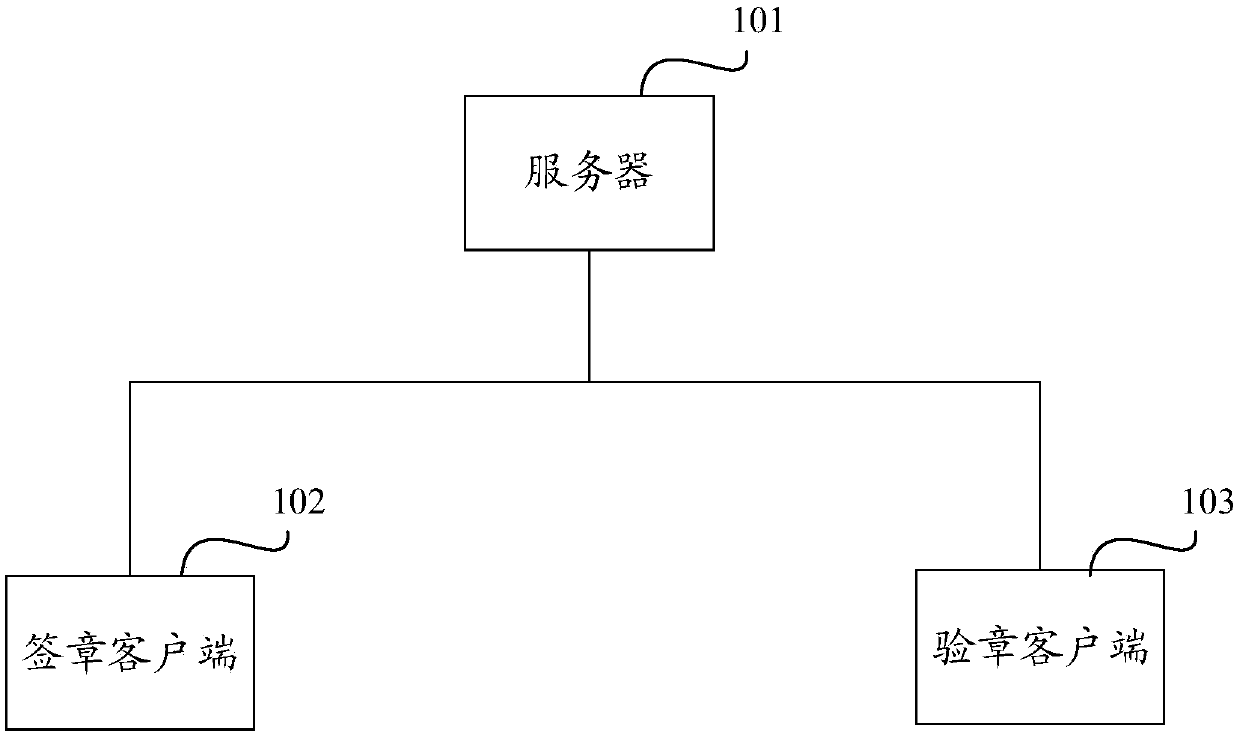
Electronic signature and seal verification method and device
An electronic signature and electronic seal technology, applied in the field of data security, can solve the problems of electronic signature credibility discount, unfavorable network office promotion, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
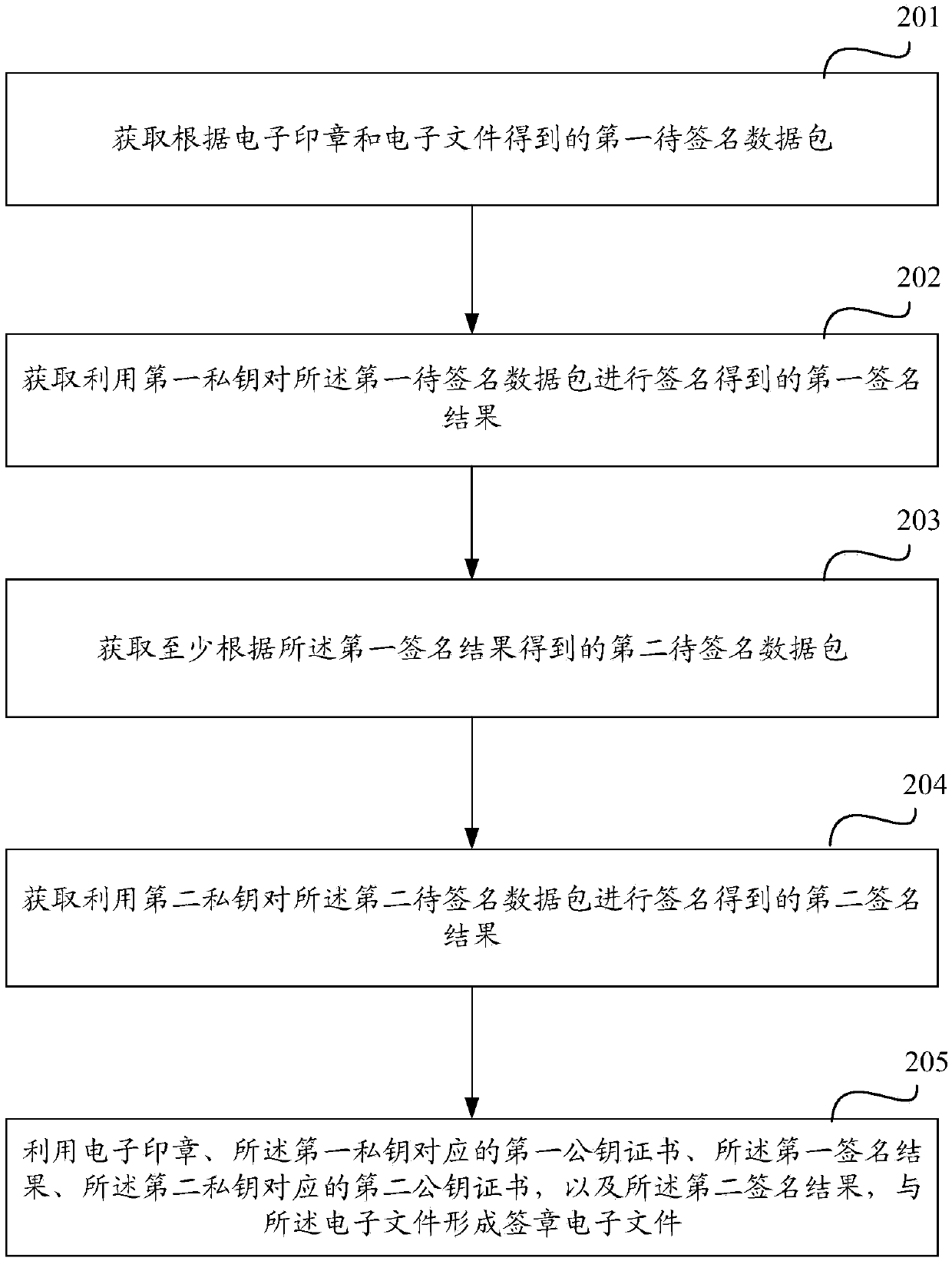
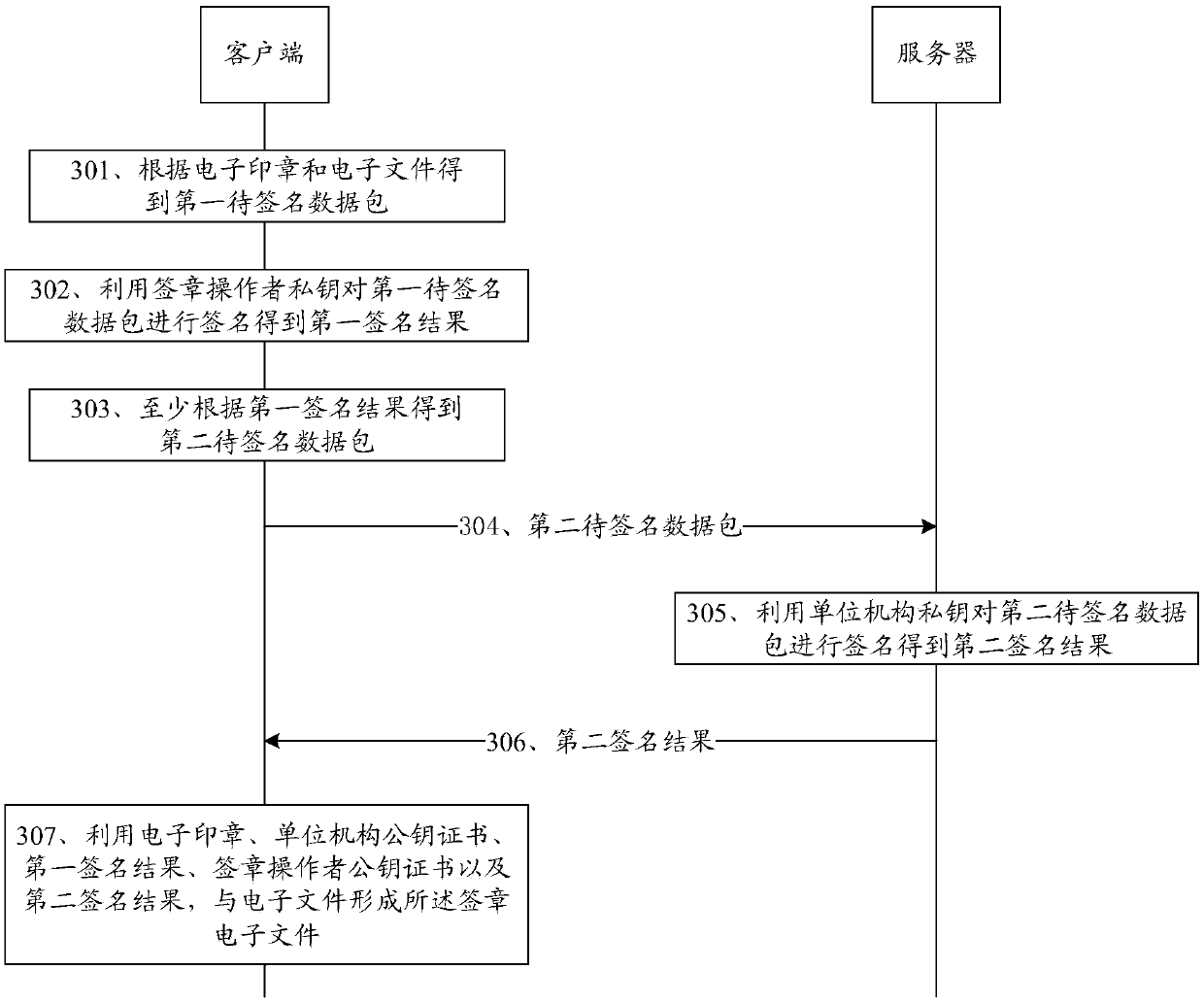
[0088] Embodiment 1: Use the private key of the signature operator to sign the first data package to be signed, and use the private key of the organization to sign the second data package to be signed, as shown in image 3 shown, including:
[0089] Step 301, the client obtains the first data package to be signed according to the electronic seal and the electronic file.
[0090] Step 302, the client uses the private key of the signature operator to sign the first data package to be signed to obtain a first signature result.
[0091] Step 303, the client obtains the second data packet to be signed at least according to the first signature result.
[0092] Step 304, the client sends the second data packet to be signed to the server.
[0093] Step 305 , the server signs the second data package to be signed by using the organization's private key to obtain a second signature result.
[0094] Step 306, the server sends the second signature result to the client.
[0095] Step 30...
Embodiment 2
[0096] Embodiment 2, use the private key of the organization to sign the first data package to be signed, and use the private key of the signature operator to sign the second data package to be signed, as shown in Figure 4 shown, including:
[0097] Step 401, the client obtains the first data package to be signed according to the electronic seal and the electronic file.
[0098] Step 402, the client sends the first data packet to be signed to the server.
[0099] Step 403, the server signs the first data package to be signed by using the organization's private key to obtain a first signature result.
[0100] Step 404, the server sends the first signature result to the client.
[0101] Step 405, the client obtains the second data packet to be signed at least according to the first signature result.
[0102] Step 406, the client uses the private key of the signature operator to sign the second data packet to be signed to obtain a second signature result.
[0103] Step 407 ,...
Embodiment 3
[0126] The specific steps of embodiment three include:
[0127] Step 501, the signature component module invokes the client storage module after successfully verifying the PIN code.
[0128] Step 502, the signature component module reads and analyzes the electronic seal, extracts the unique identification code of the seal, the image data of the seal, the name of the seal, the effective time of the seal, the public key certificate of the signature operator, the public key certificate of the seal maker, and the number of the seal maker Signature value, and the public key certificate of the institution to which the electronic seal belongs.
[0129] Step 503, the signature component module verifies the authenticity of the electronic seal itself, specifically using the seal maker's public key certificate to verify the digital signature value of the seal maker, if true, execute step 504, otherwise terminate the signature process.
[0130] Step 504, the signature component module pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com