Patents
Literature
970results about "Structured data retrieval" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
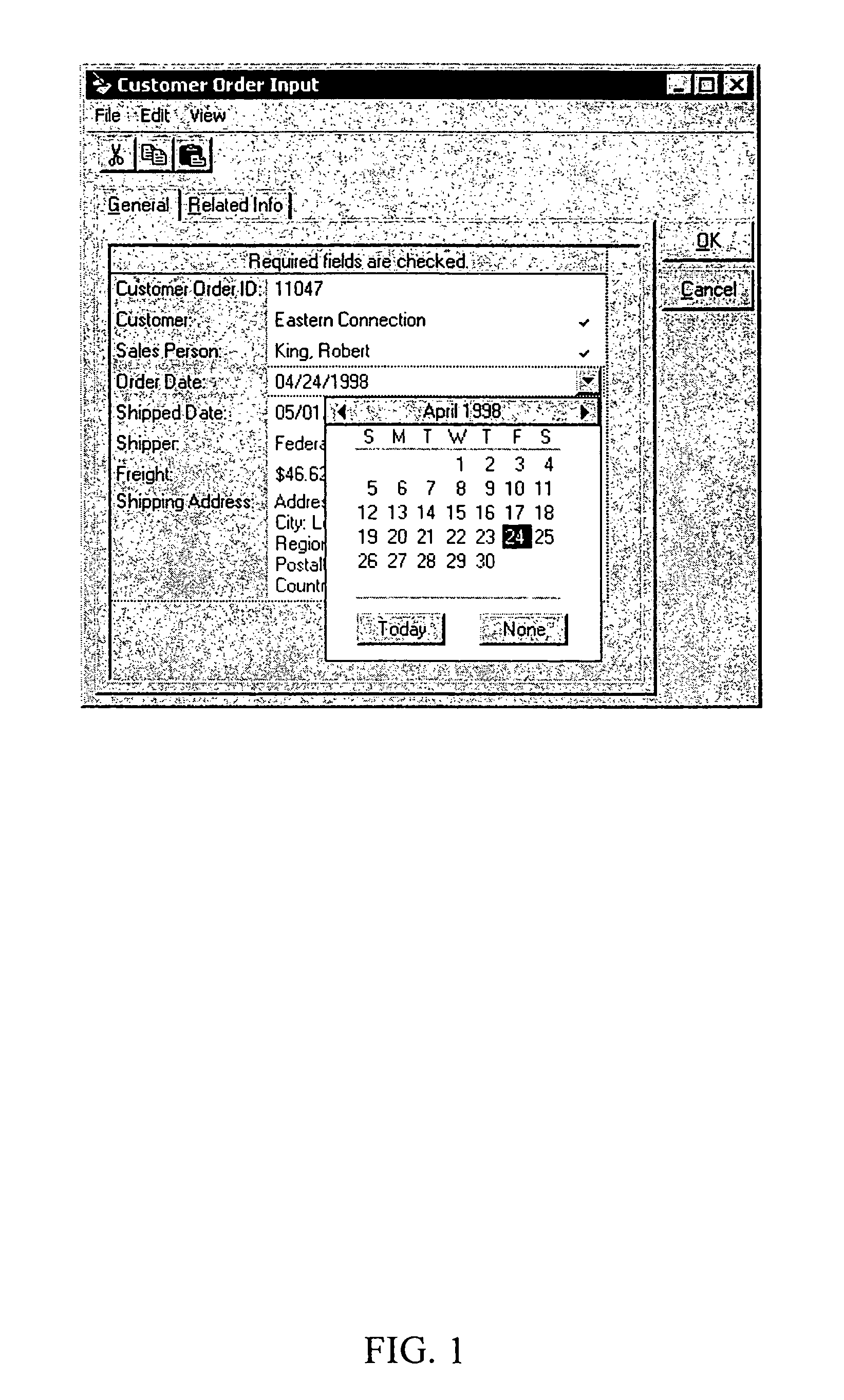
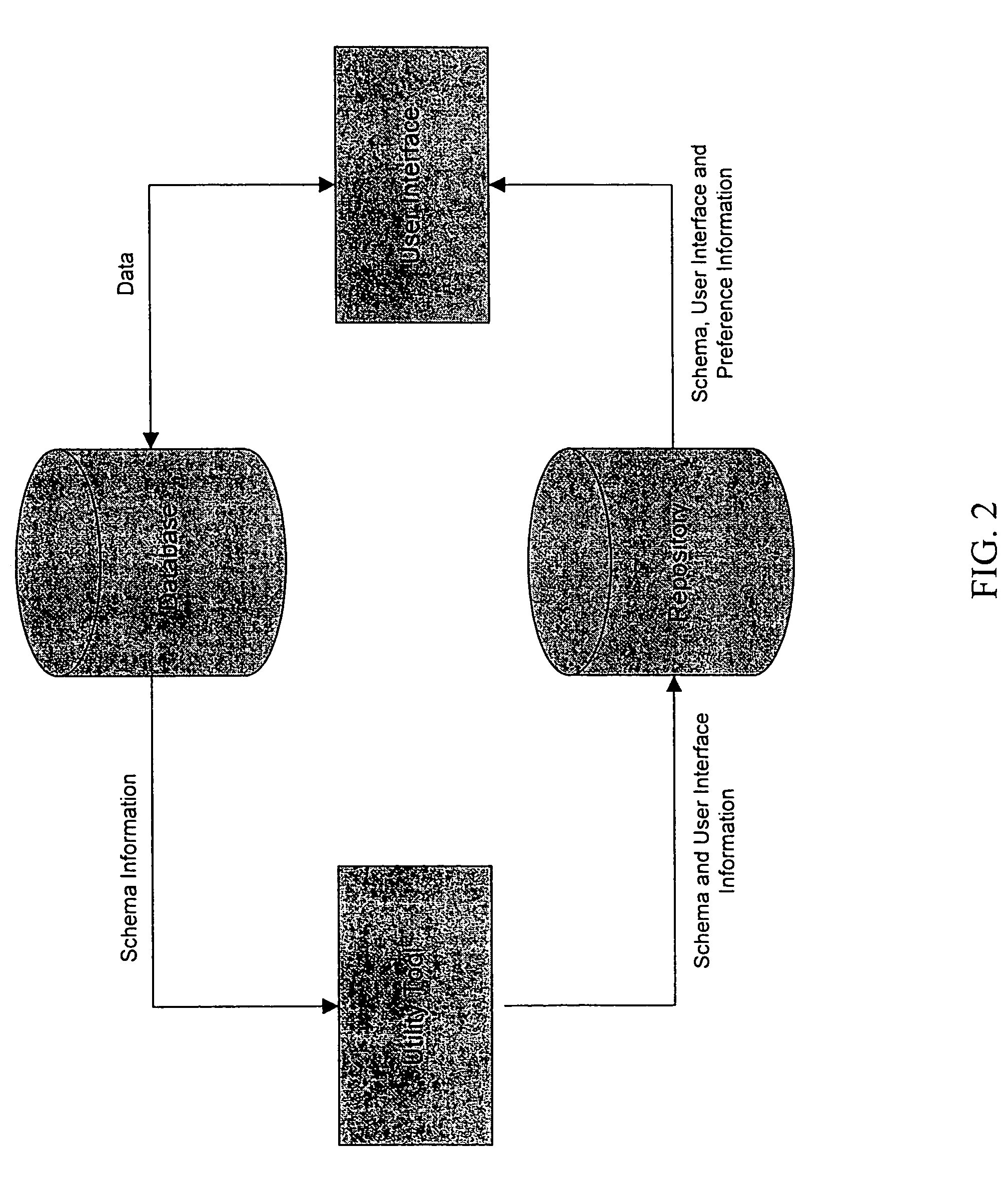
Automated generation of dynamic data entry user interface for relational database management systems
InactiveUS7062502B1Easy to navigateData processing applicationsMultiple digital computer combinationsRelational database management systemComputer software
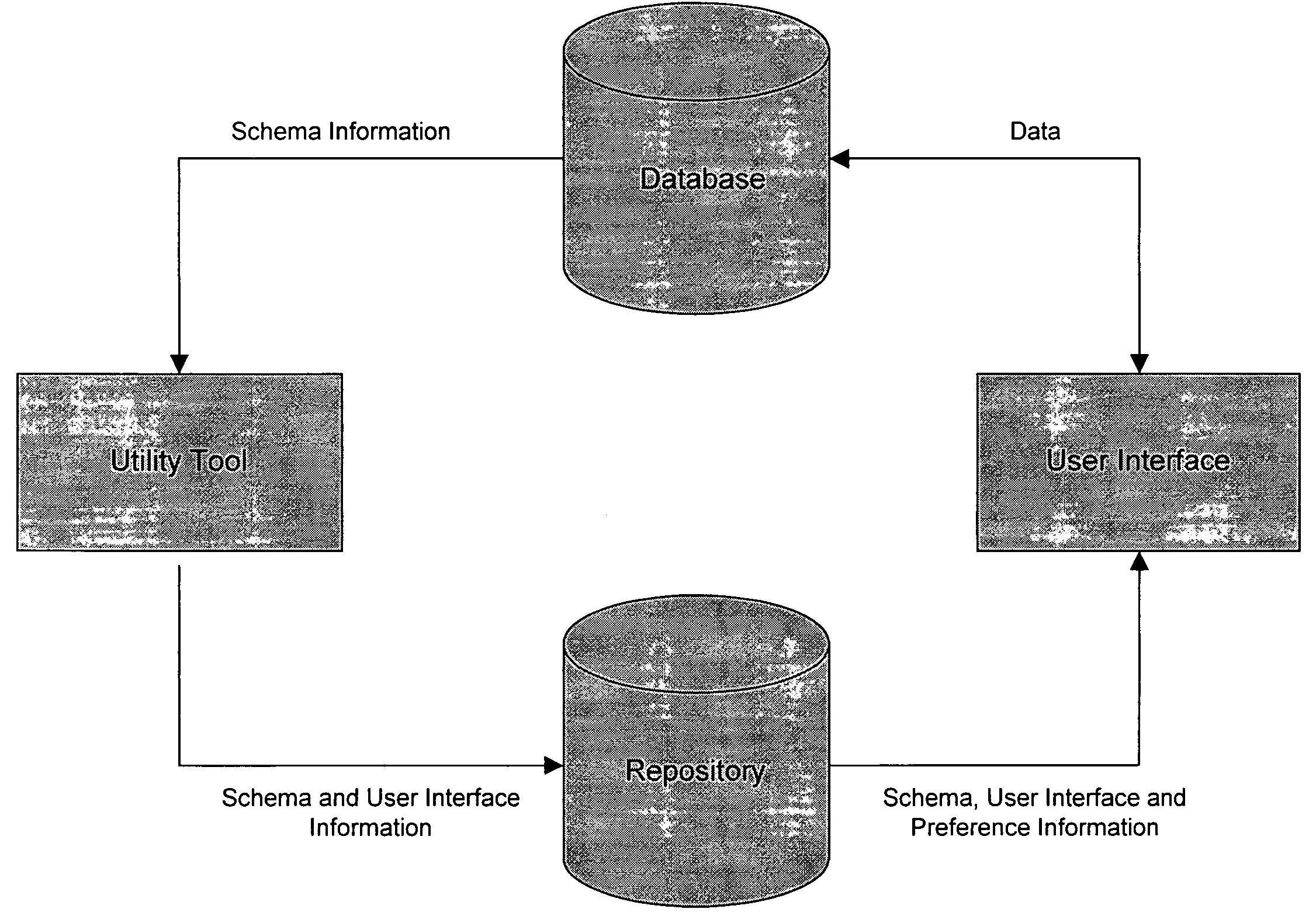
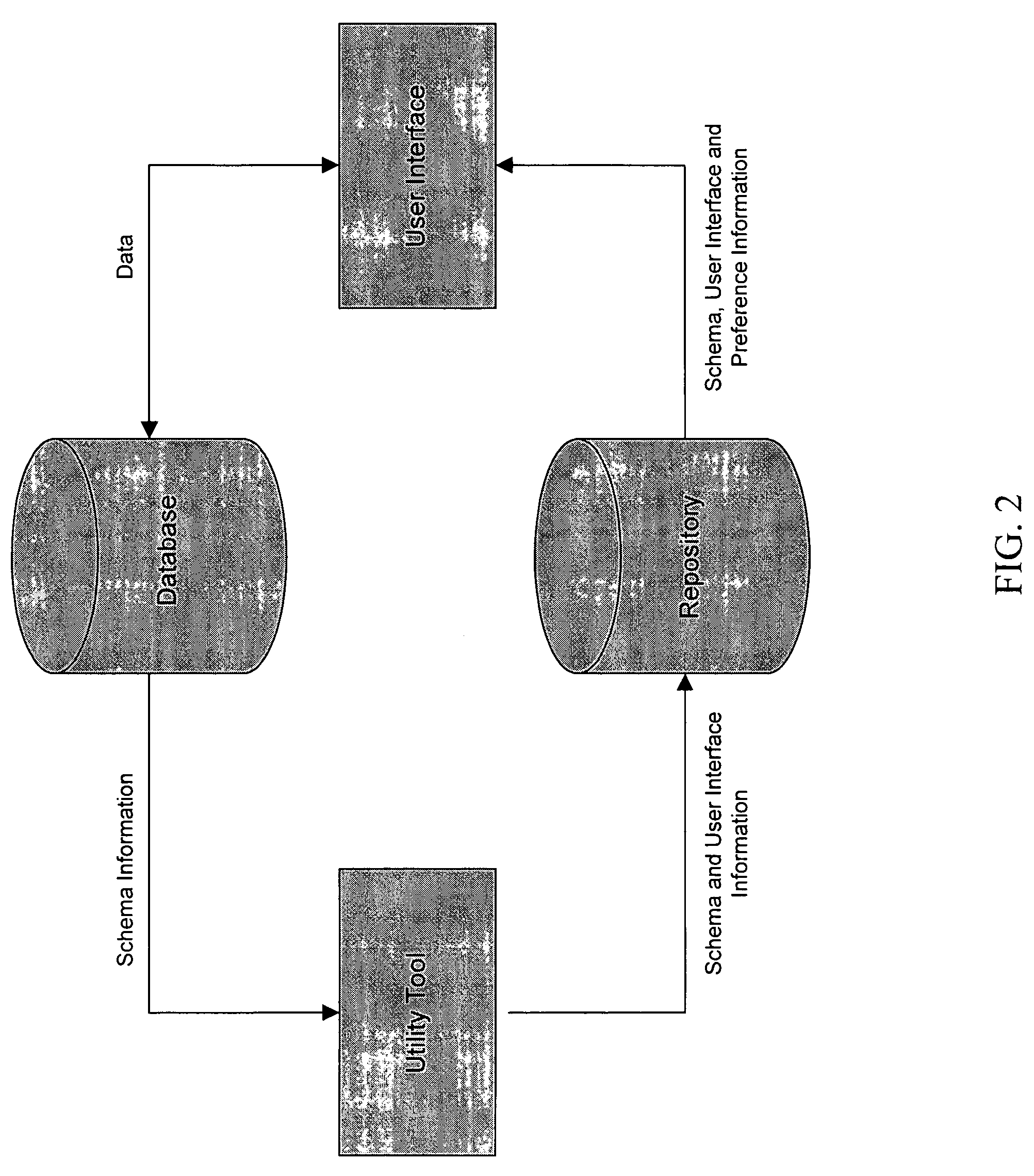
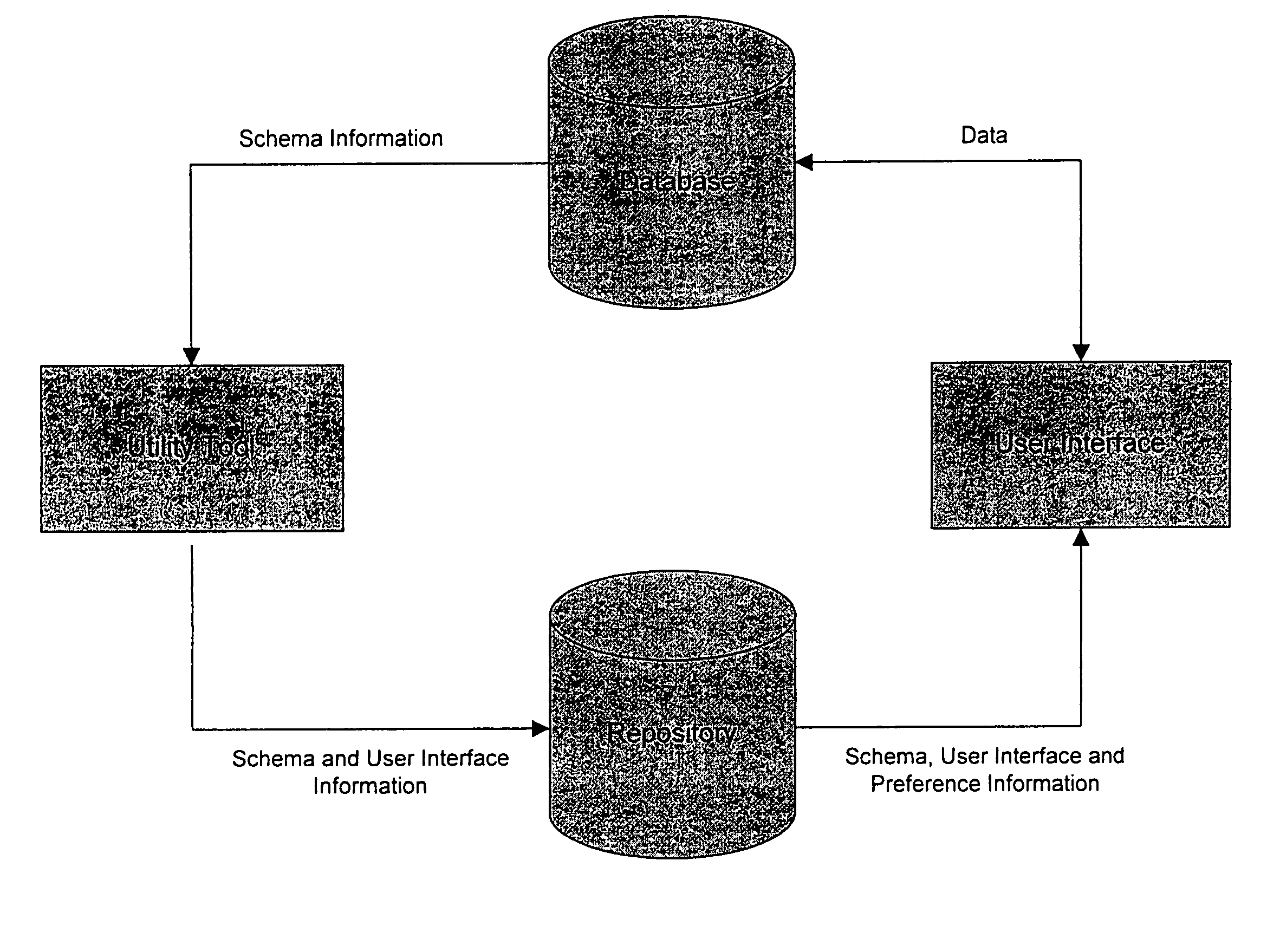
Computer software for, computer apparatus for, and a method of automatically generating a user interface for a relational database comprising extracting schema information from the relational database and automatically generating corresponding schema and user interface metadata, storing the metadata in a repository, and automatically developing from the metadata a user interface appropriate to the relational database.
Owner:ADVANCED DYNAMIC INTERFACES
Automated generation of dynamic data entry user interface for relational database management systems
InactiveUS7401094B1Easy to navigateData processing applicationsDigital data processing detailsRelational database management systemComputer software
Owner:ADVANCED DYNAMIC INTERFACES
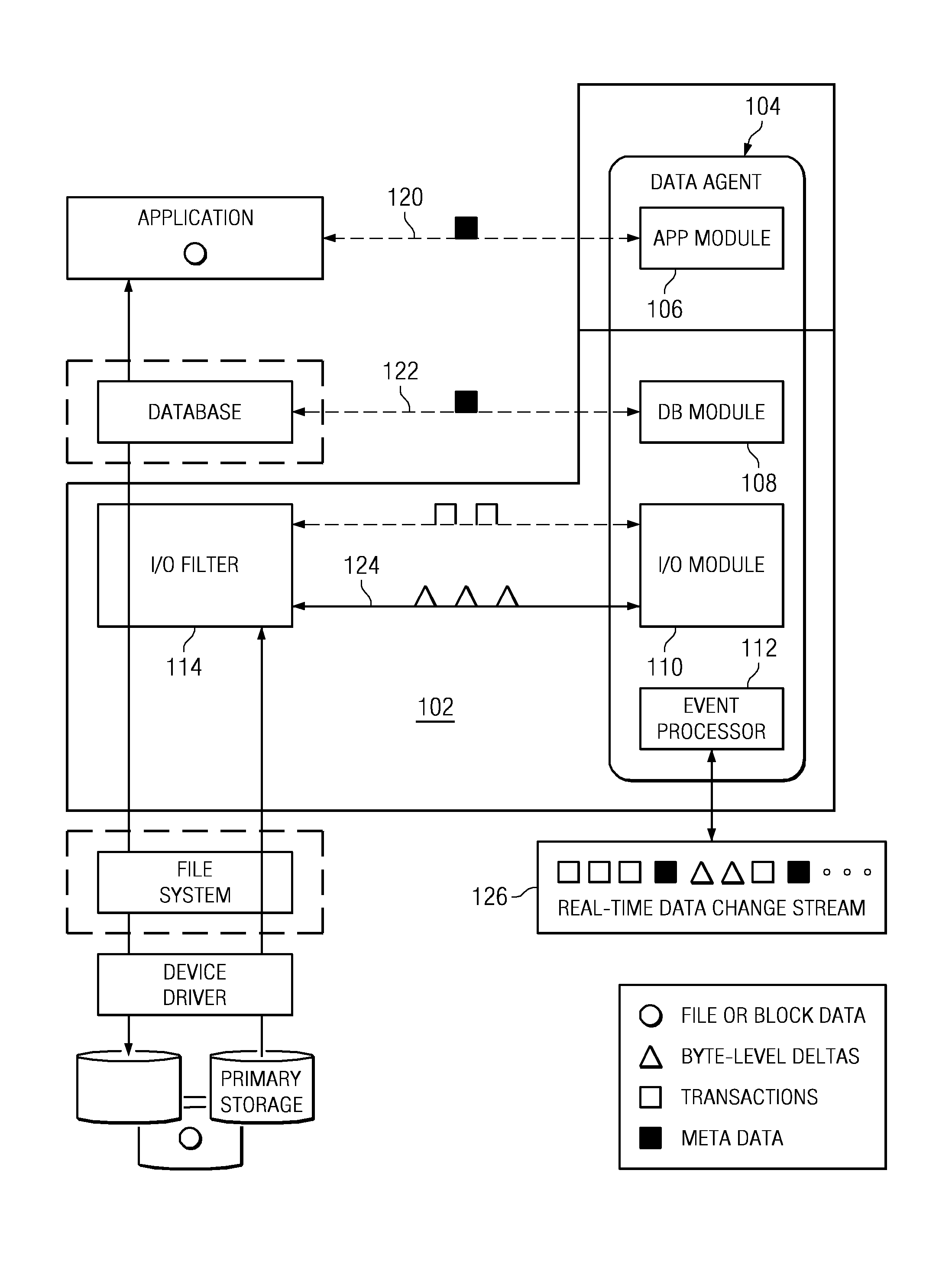
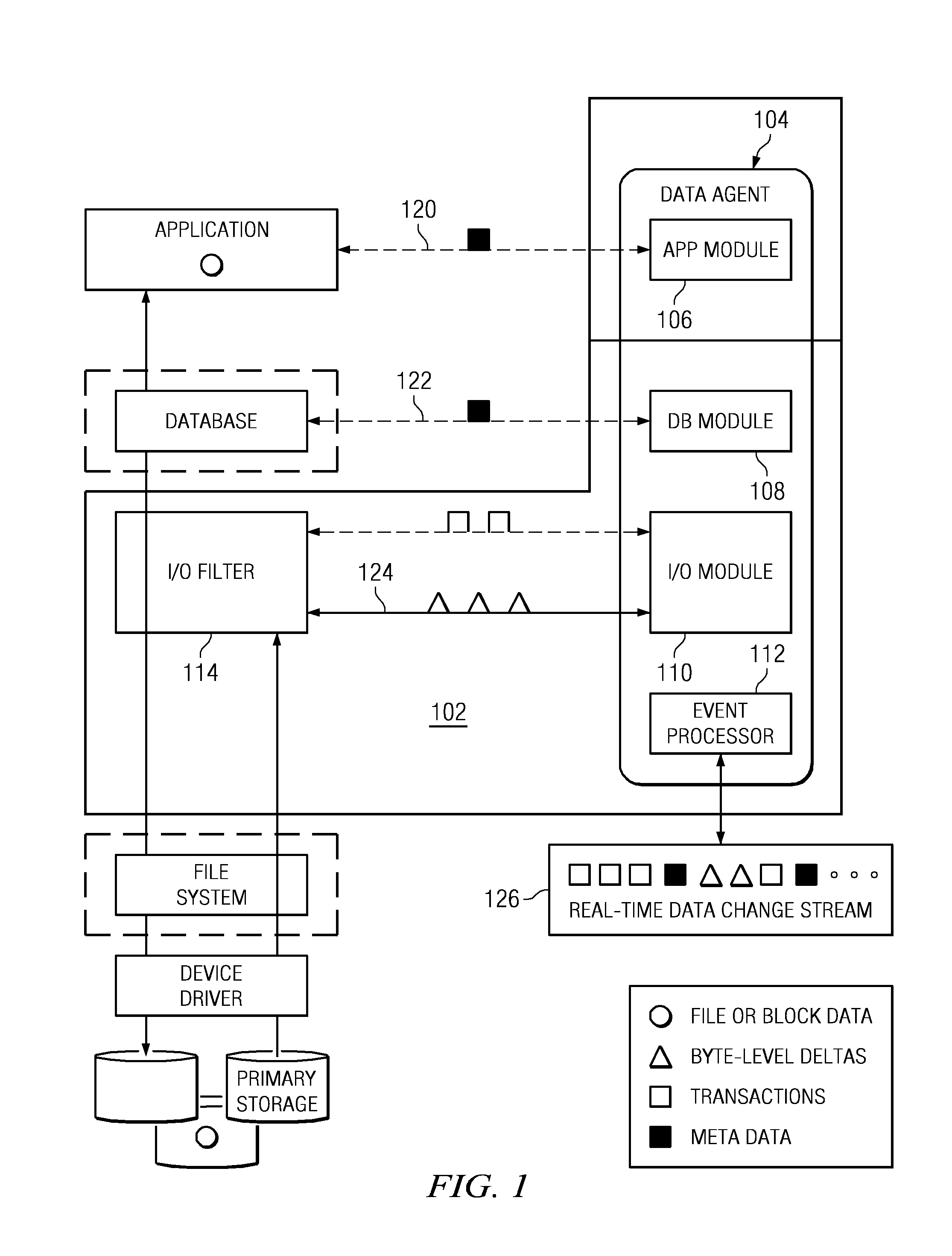
Recovering a database to any point-in-time in the past with guaranteed data consistency
ActiveUS8364648B1Digital data processing detailsStructured data retrievalTransaction dataData management
A data management method wherein a real-time history of a database system is stored as a logical representation and the logical representation is then used for any point-in-time recovery of the database system. More specifically, a method for capturing transaction data, binary data changes, metadata, and events, and for tracking a real-time history of a database system according to the events. The method enables tracking and storing of consistent checkpoint images of the database system, and also enables tracking of transaction activities between checkpoints. The database system may be recovered to any consistent checkpoint or to any point between two checkpoints.
Owner:QUEST SOFTWARE INC
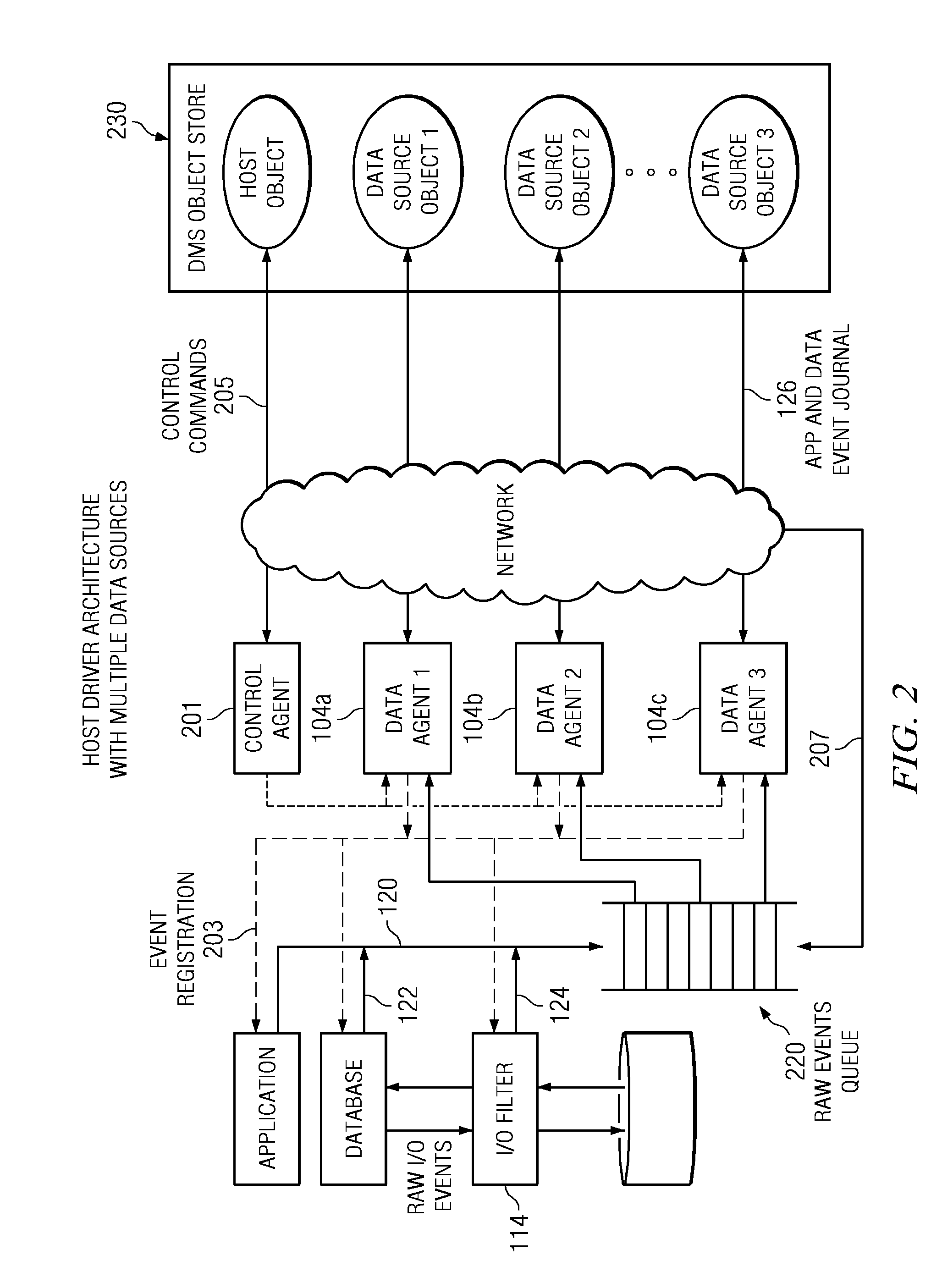
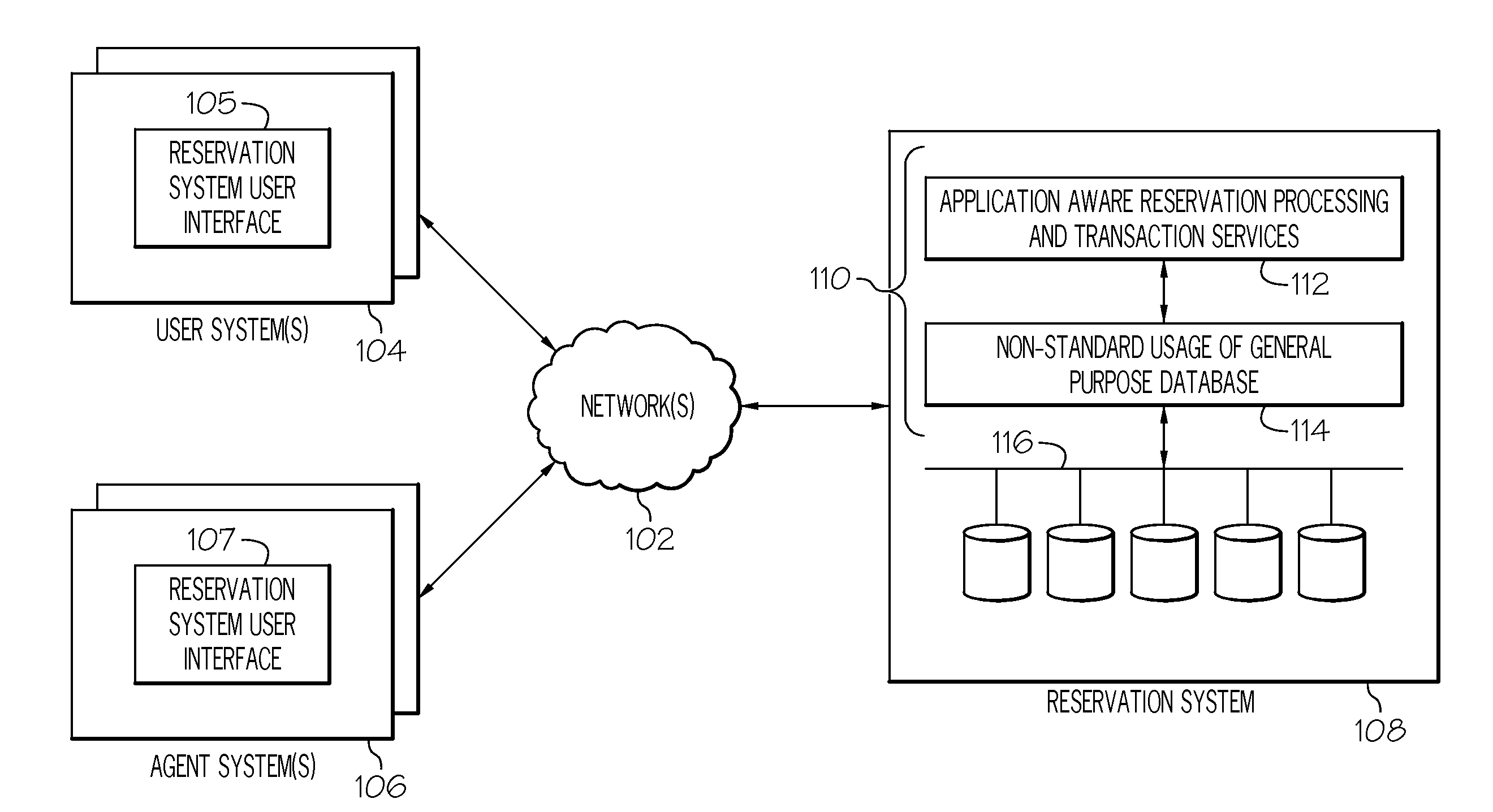
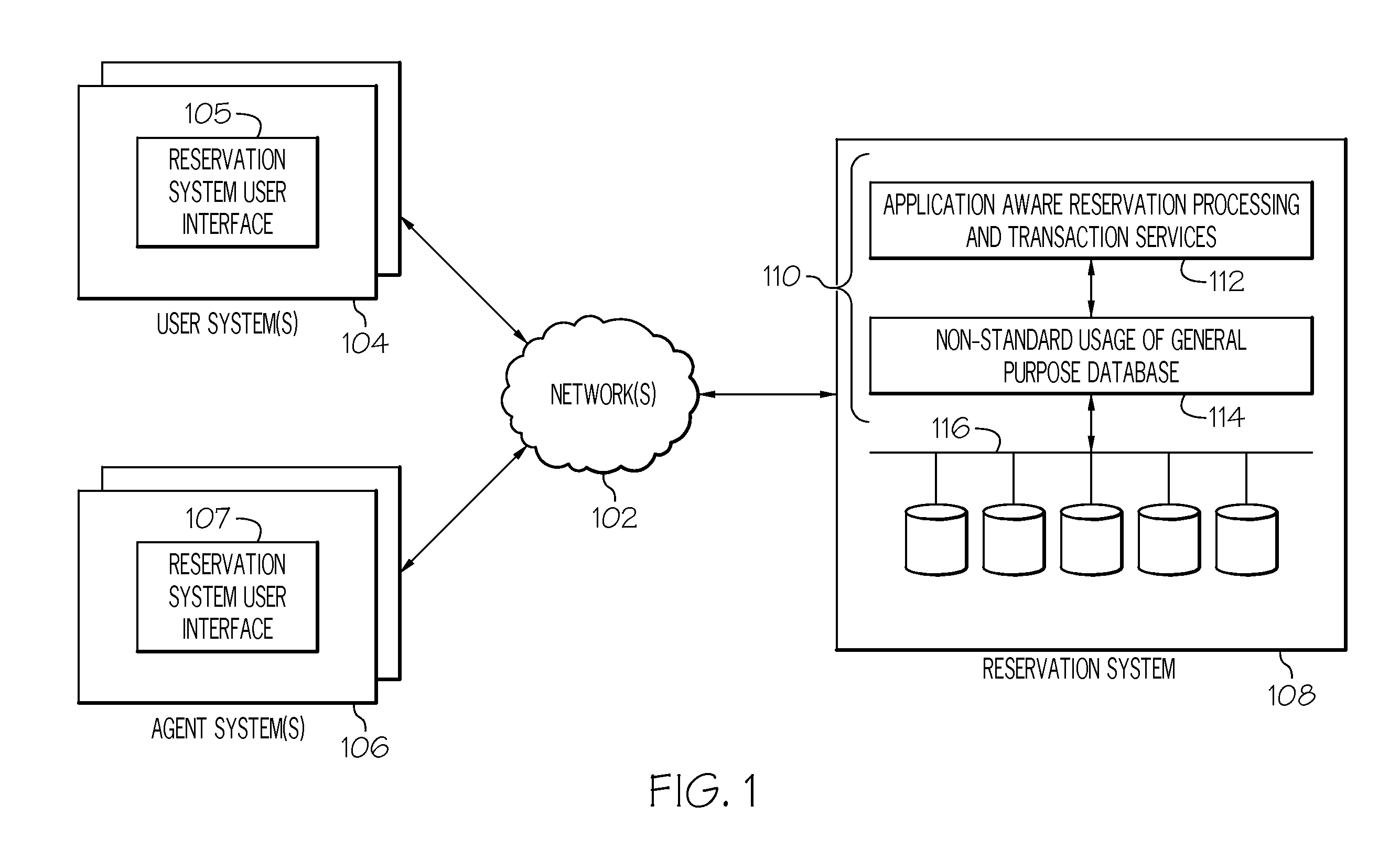
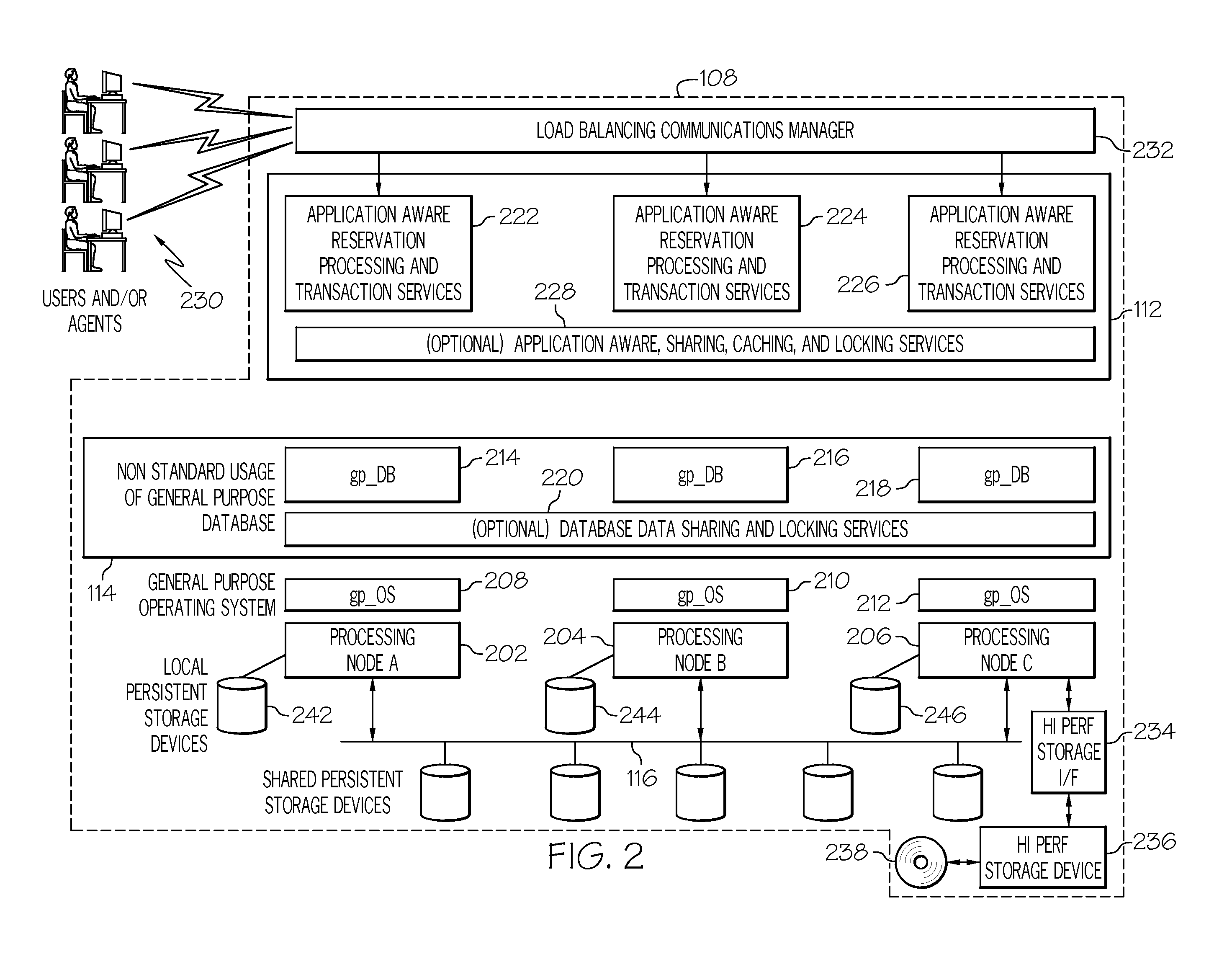
Two-layer data architecture for reservation management systems
A reservation management system includes at least one processing node that includes a memory and a processor. The at least one processing node further includes a set of reservation processing and transaction modules that manage and process reservation requests and inquiries. At least one general purpose database is communicatively coupled to the at least one processing node. The at least one general purpose database includes a set of pre-allocated tables of fixed length records. At least one persistent storage device is communicatively coupled to the at least one processing node. The general purpose database persistently stores the set of pre-allocated tables of fixed length records on the at least one persistent storage device.
Owner:IBM CORP
Business intelligence system and method utilizing multidimensional analysis of a plurality of transformed and scaled data streams
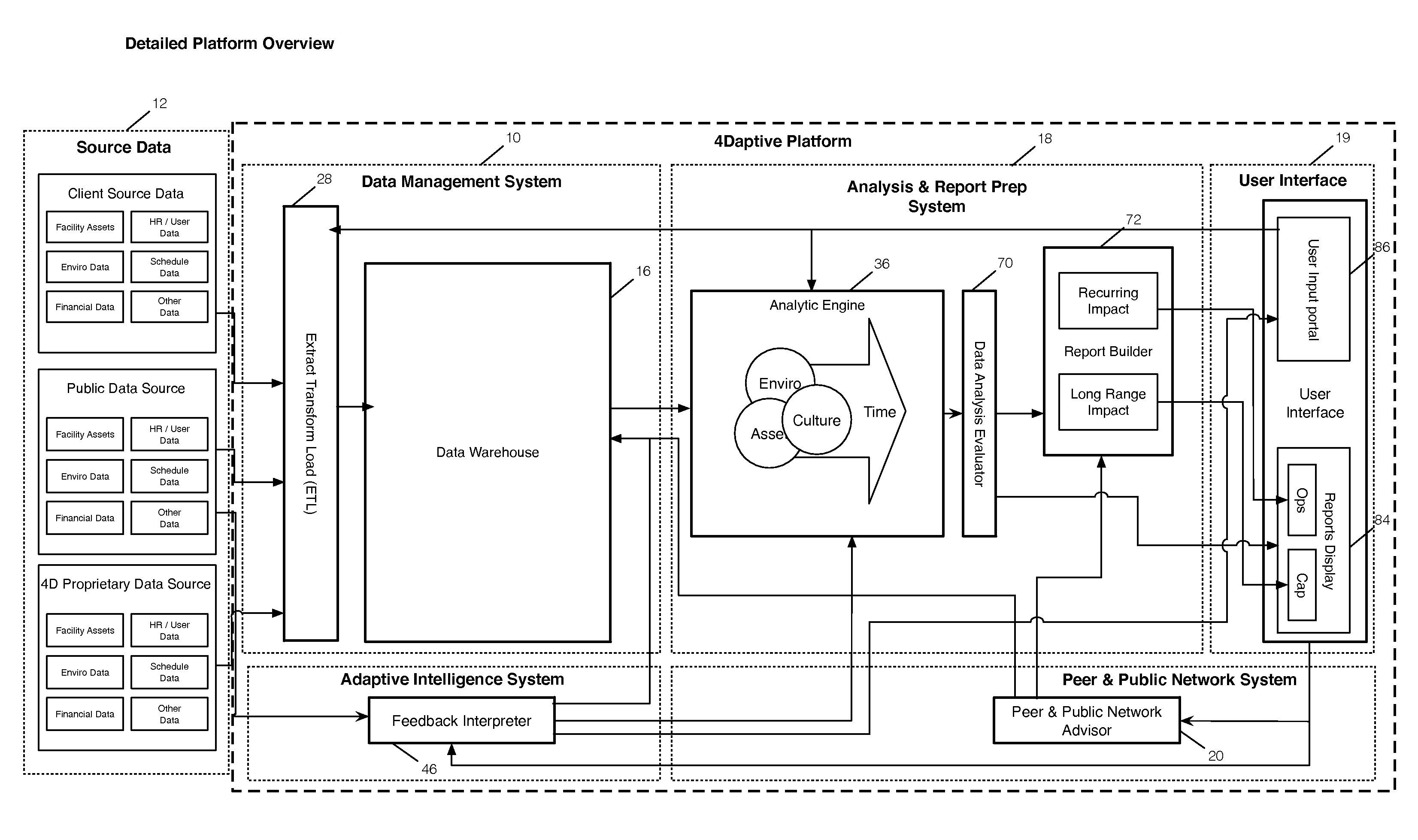
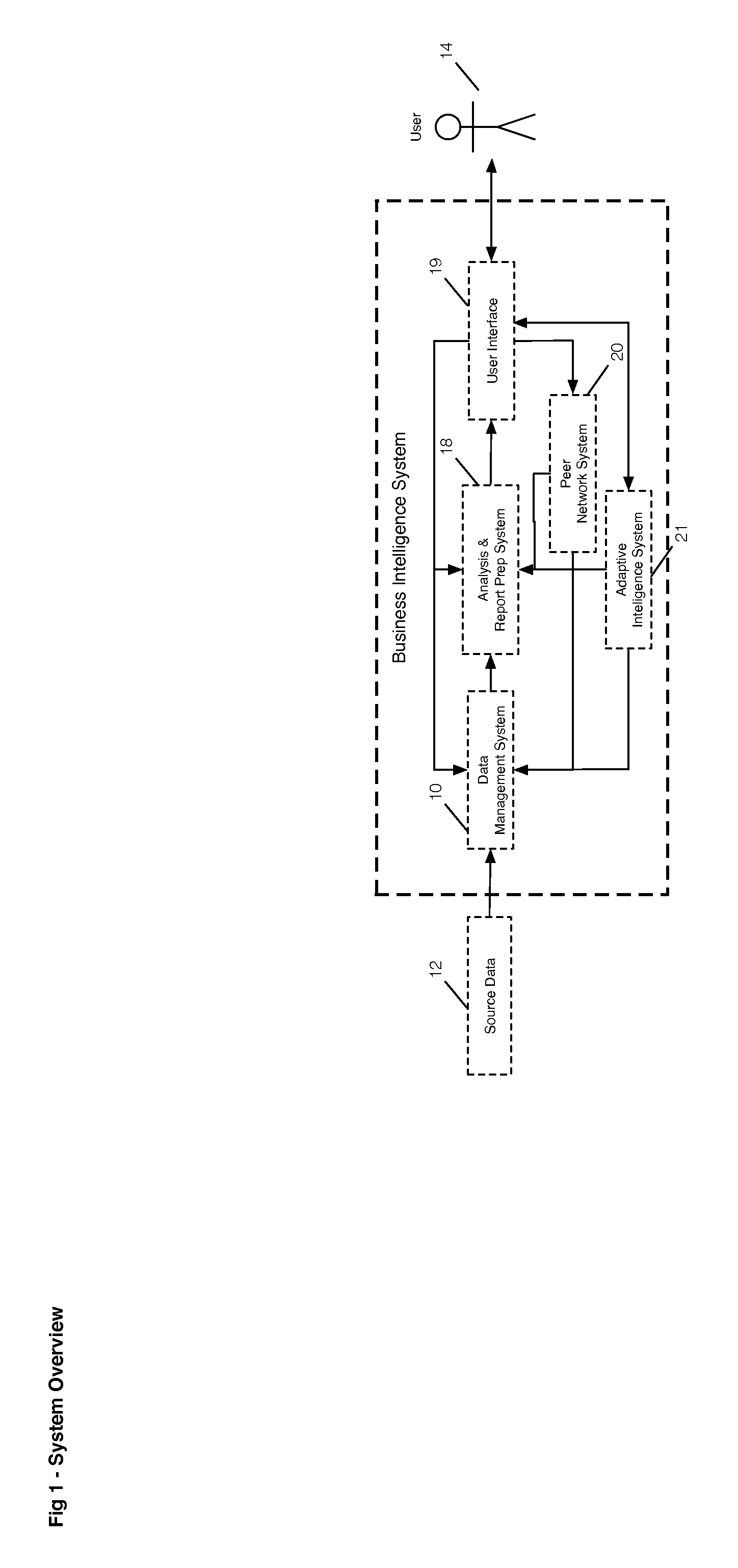
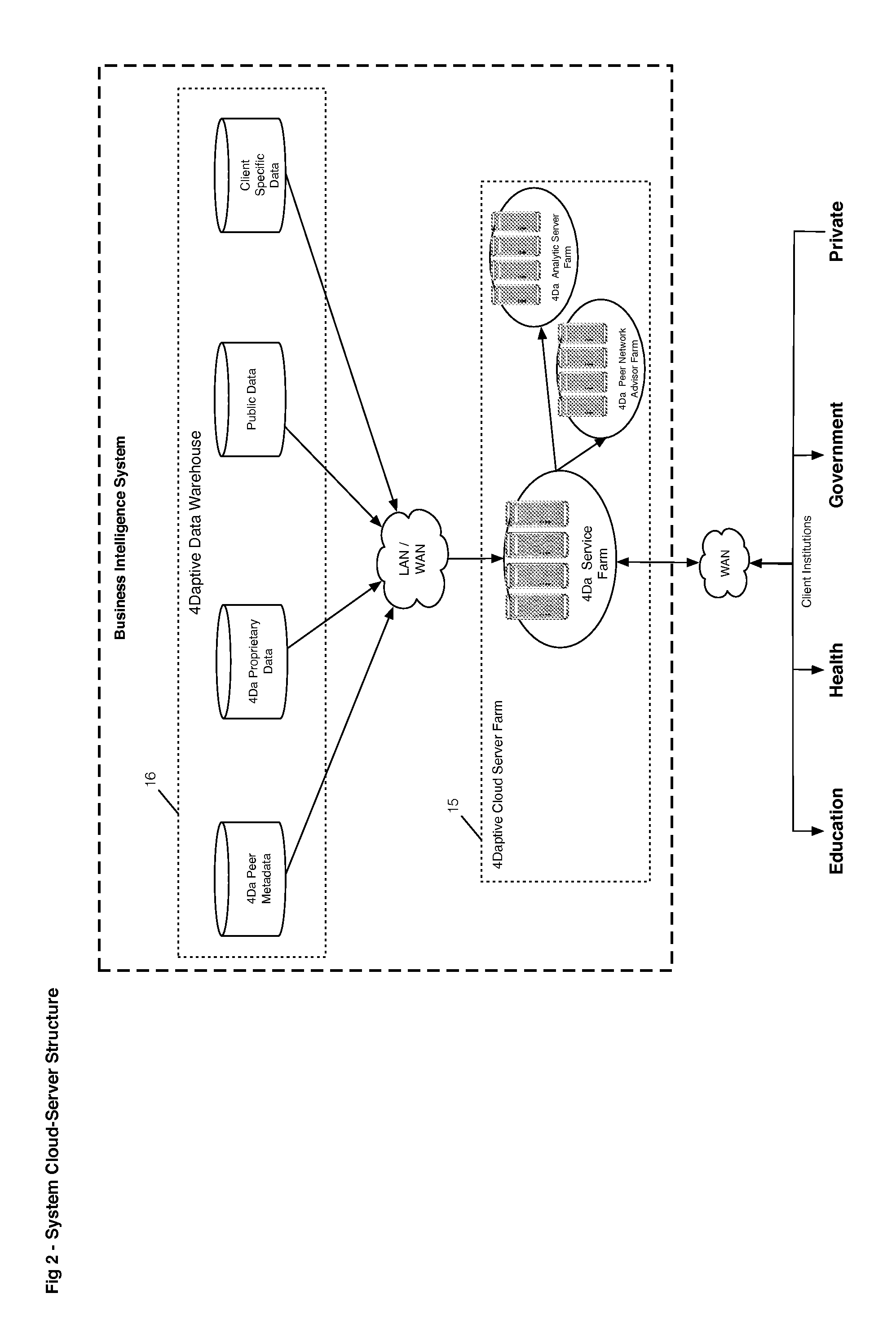
A method is provided for qualifying and analyzing business intelligence. At a first part of a data management system receives first, second and third streams of data. The first stream is client provided source data, the second is public source data and the third is data management system internal data previously collected and managed source data in the data management system. The three streams of data are organized into items and their attributes at the data management system. The source data is transformed at a data warehouse where it becomes normalized. Logic is applied to provide multi-dimensional analysis of transformed source data relative to a scale for at least one business intelligence. The data warehouse includes updated data from the multi-dimensional analysis. A user interface communicates with the data management system to create statistical information that illustrates impact over time and value.
Owner:ROUNDHOUSE ONE
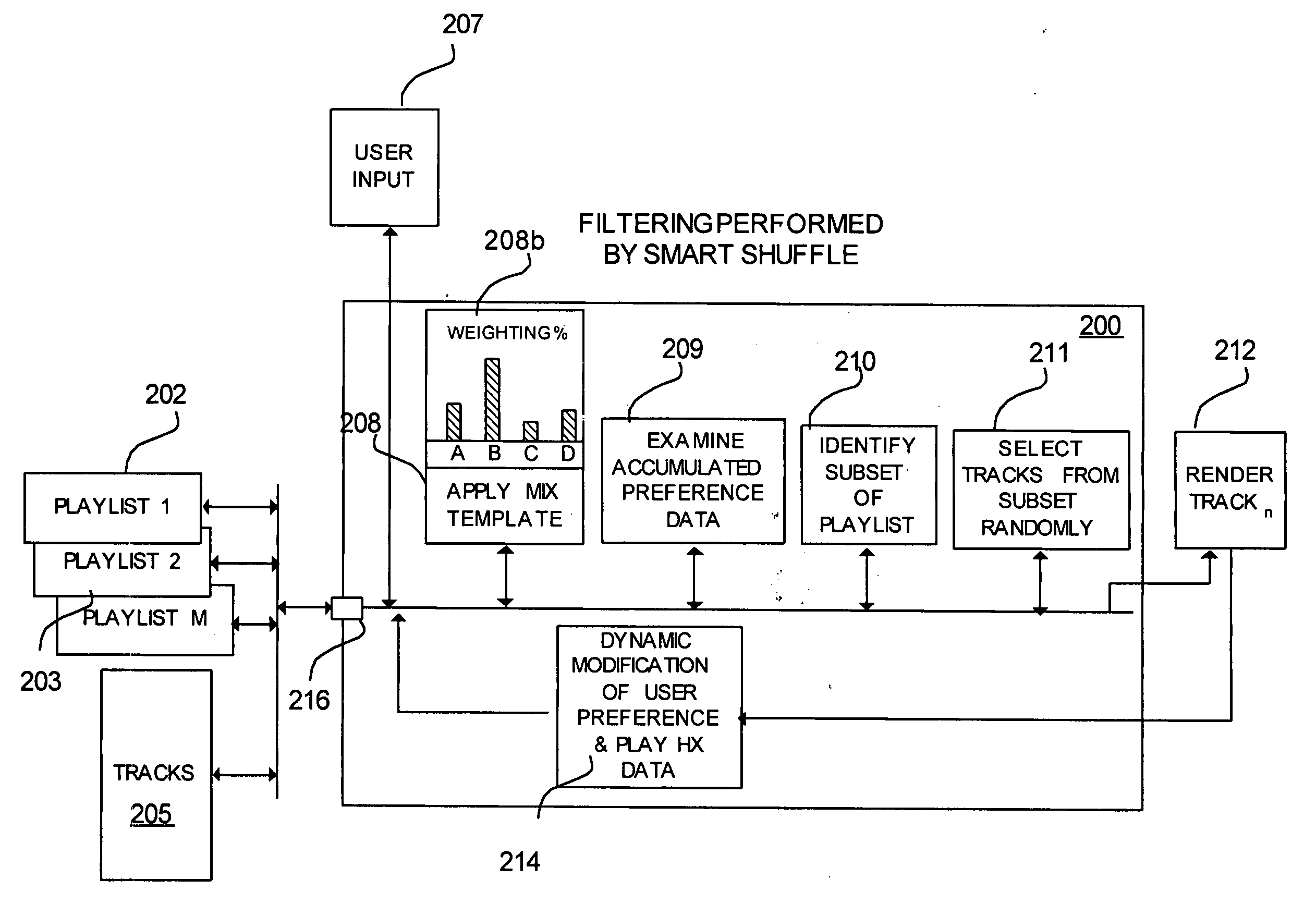
System and method for modifying media content playback based on an intelligent random selection
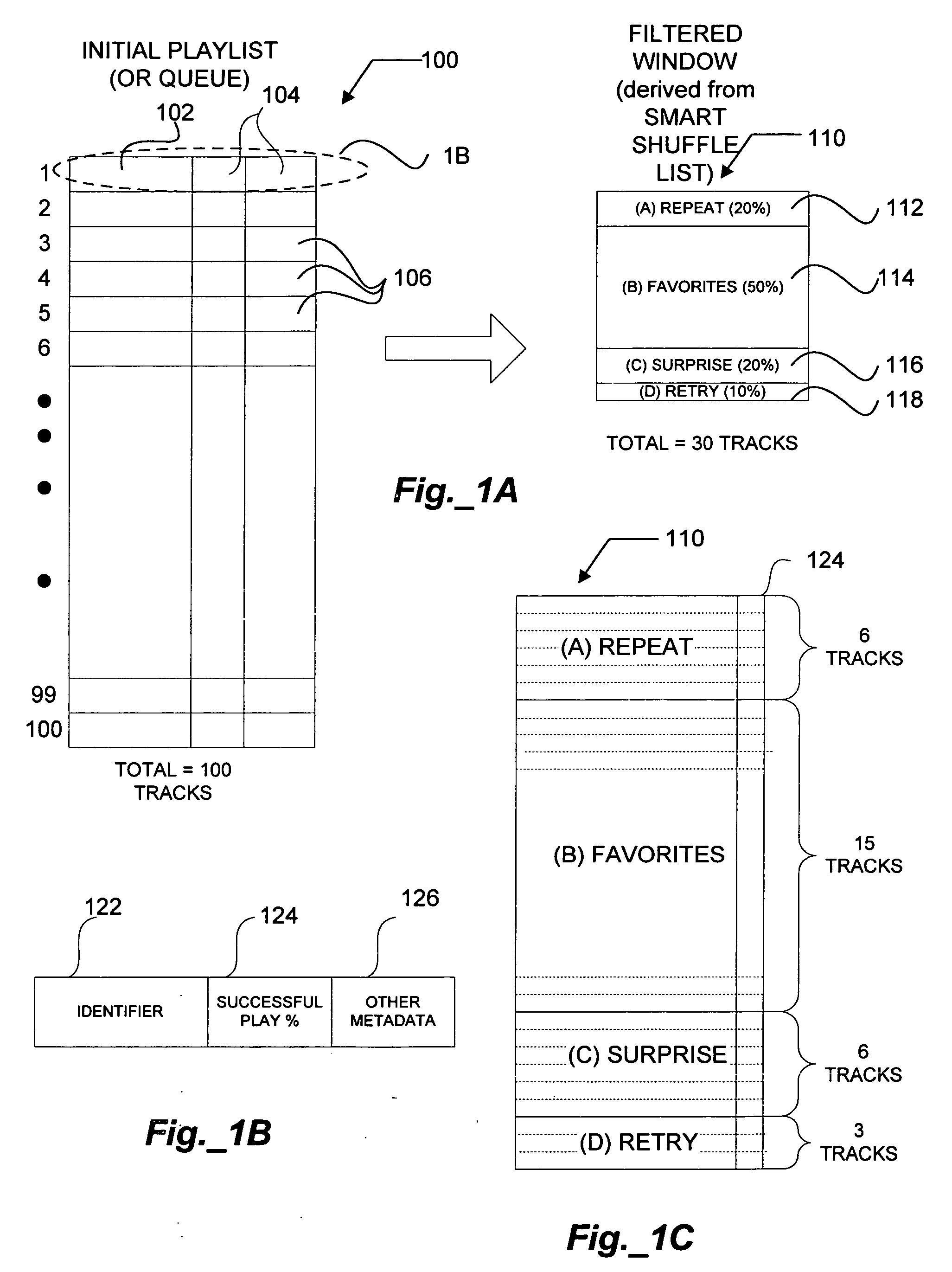
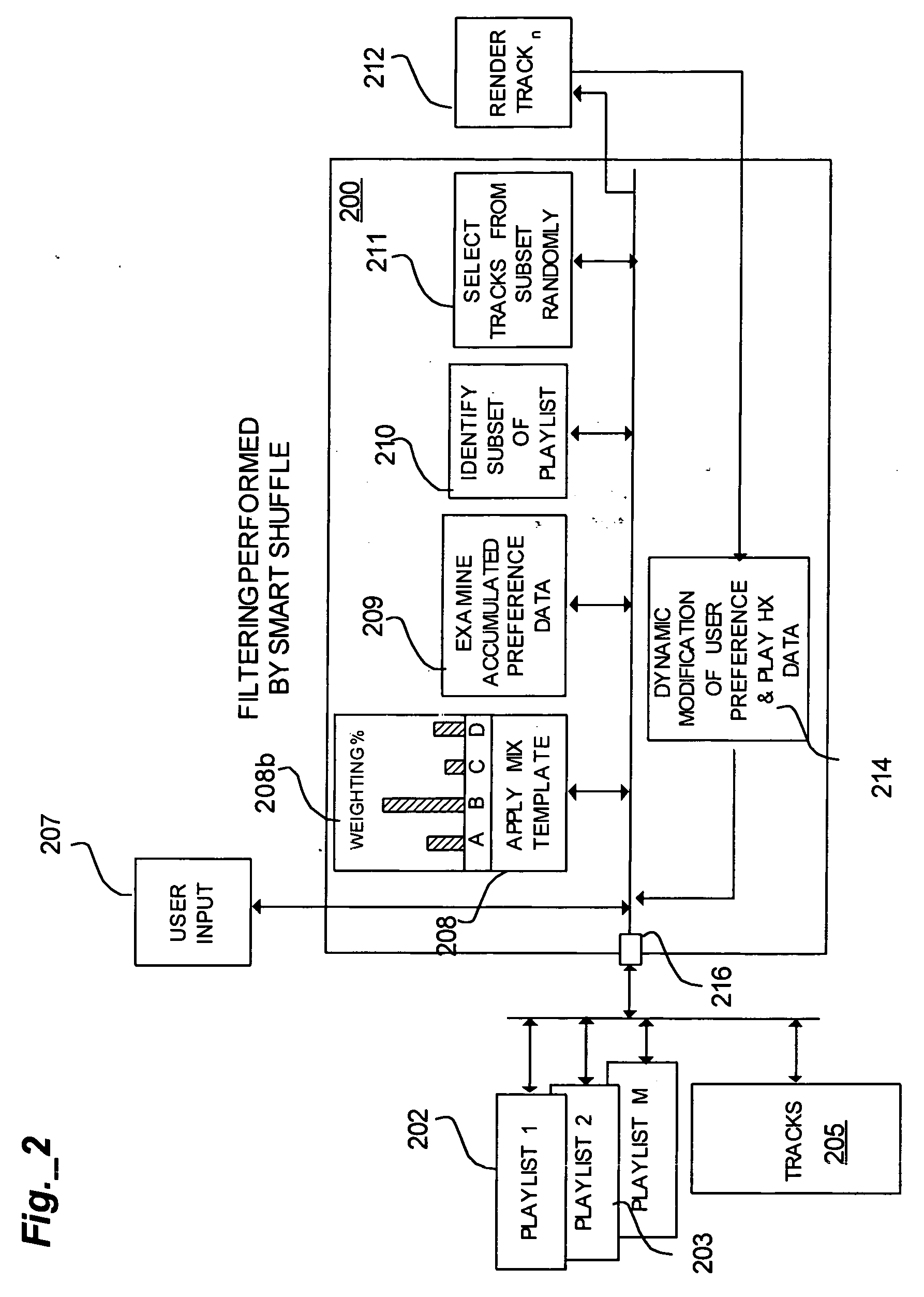
ActiveUS20070025194A1Web data indexingElectronic editing digitised analogue information signalsComputer sciencePreference data
A playlist containing a plurality of tracks is filtered to generate a customized subset or window of tracks for playback. The method includes automatically determining user preference data for each of the plurality of tracks based on the user's conduct when each of the plurality is accessed for playback. The tracks in the playlist are reordered after each track is accessed based on the user preference data. A subset of the playlist is selected for playback based on the reordered track arrangement.
Owner:CREATIVE TECH CORP
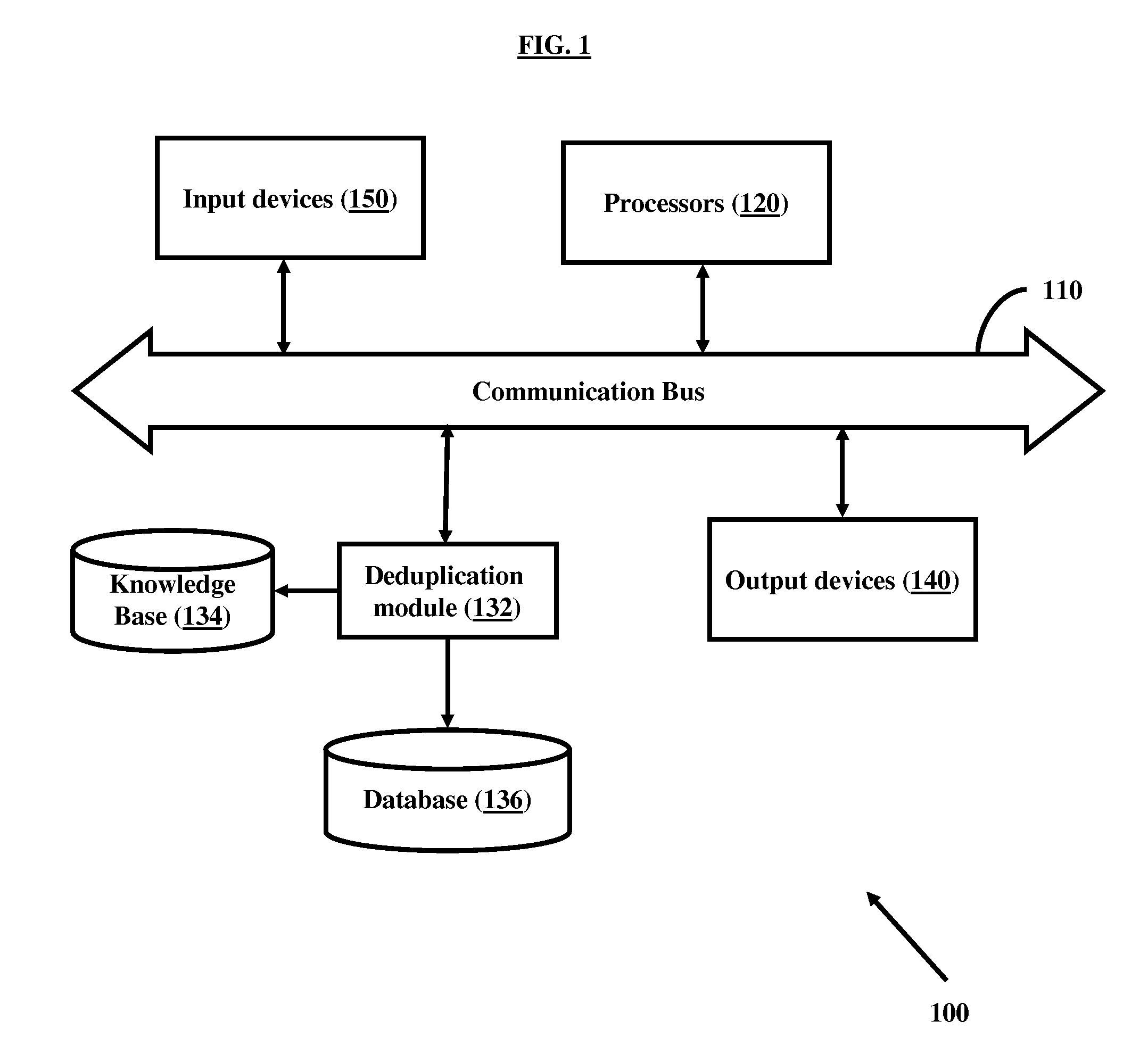
Method and system for determining presence of probable error or fraud in a data set by linking common data values or elements
ActiveUS7373669B2Easy to operateEfficient and methodicalFinanceDigital data processing detailsFistData set
Owner:THE 41ST PARAMETER
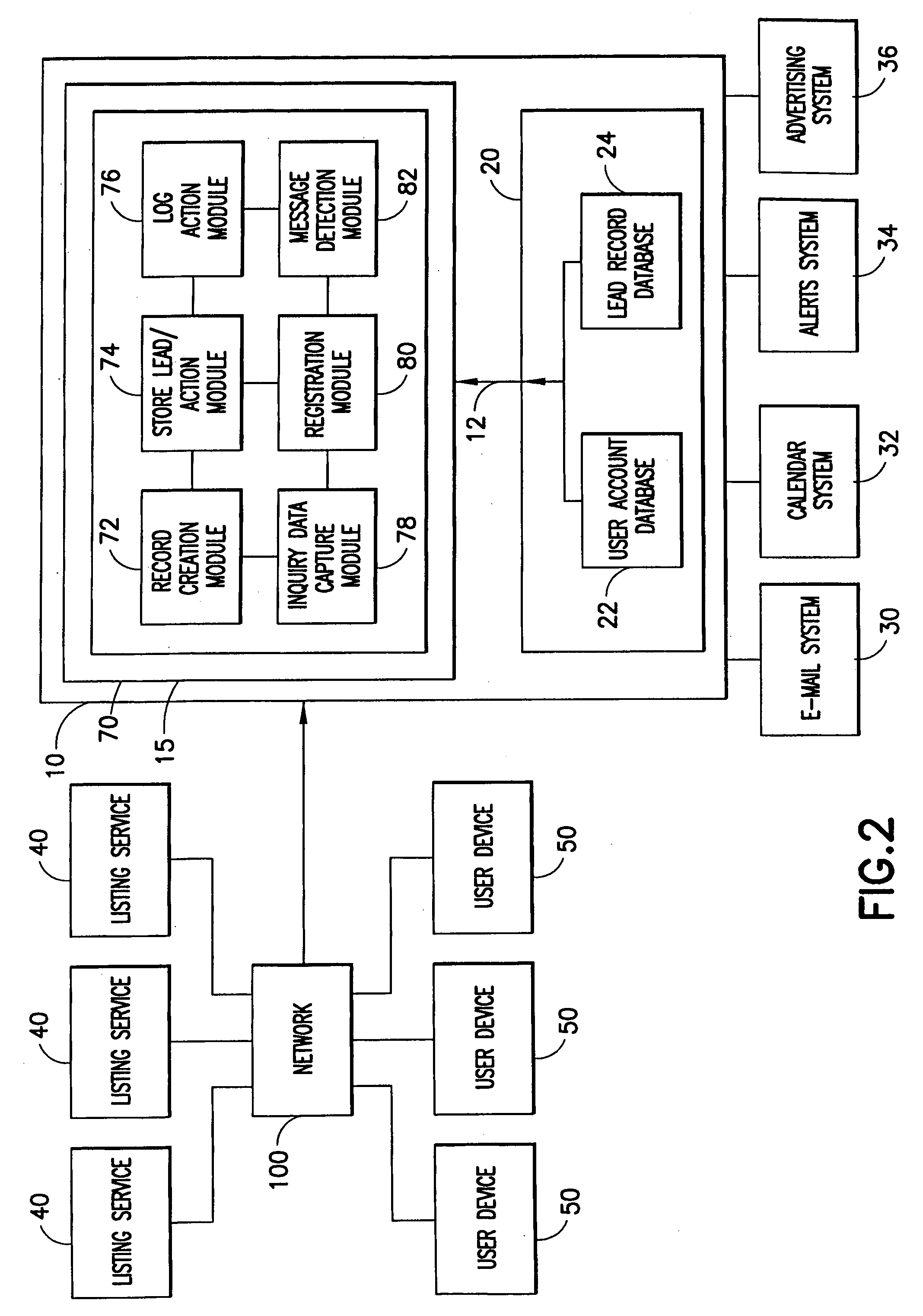
Listing service tracking system and method for tracking a user's interaction with a listing service
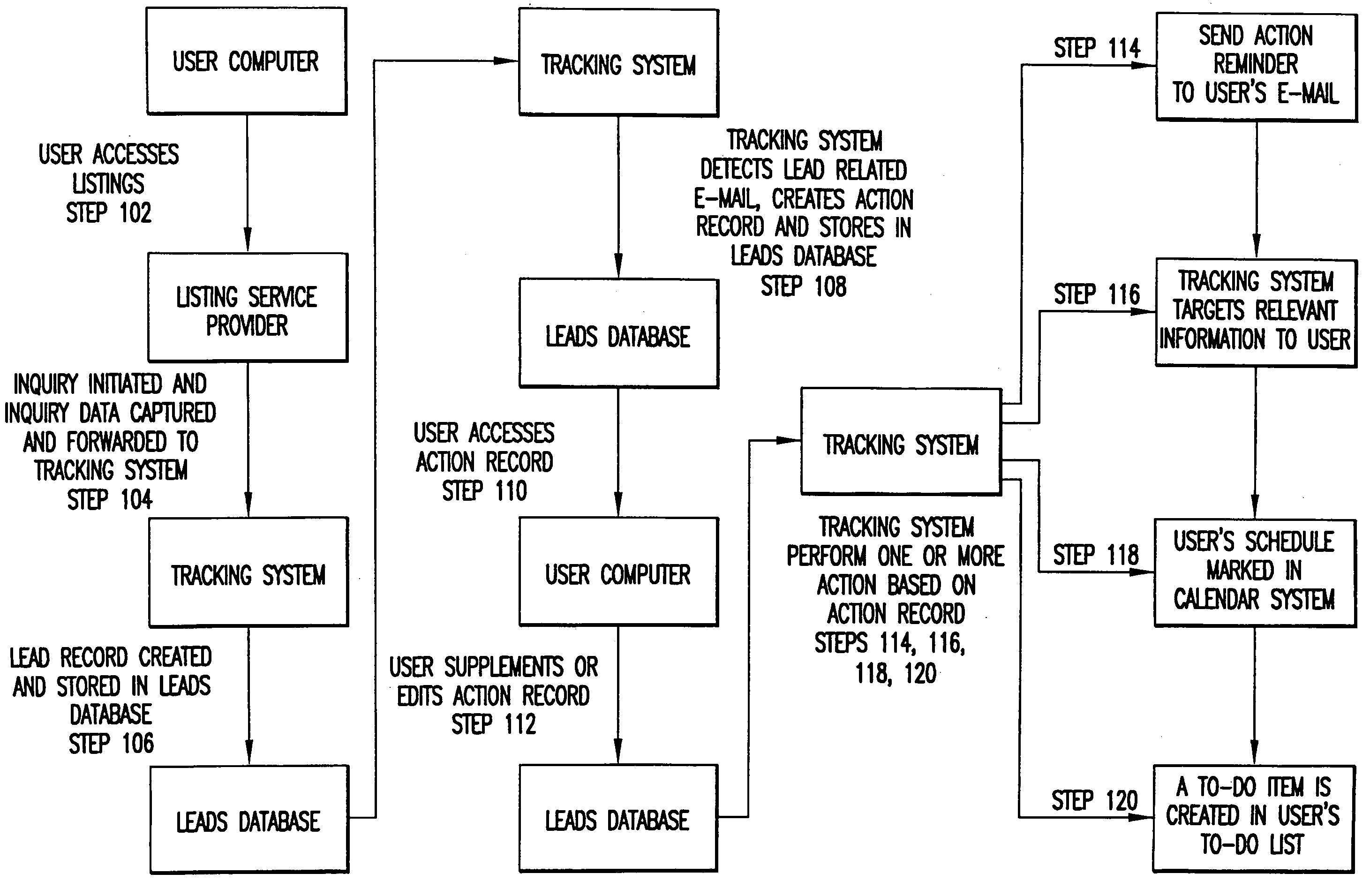
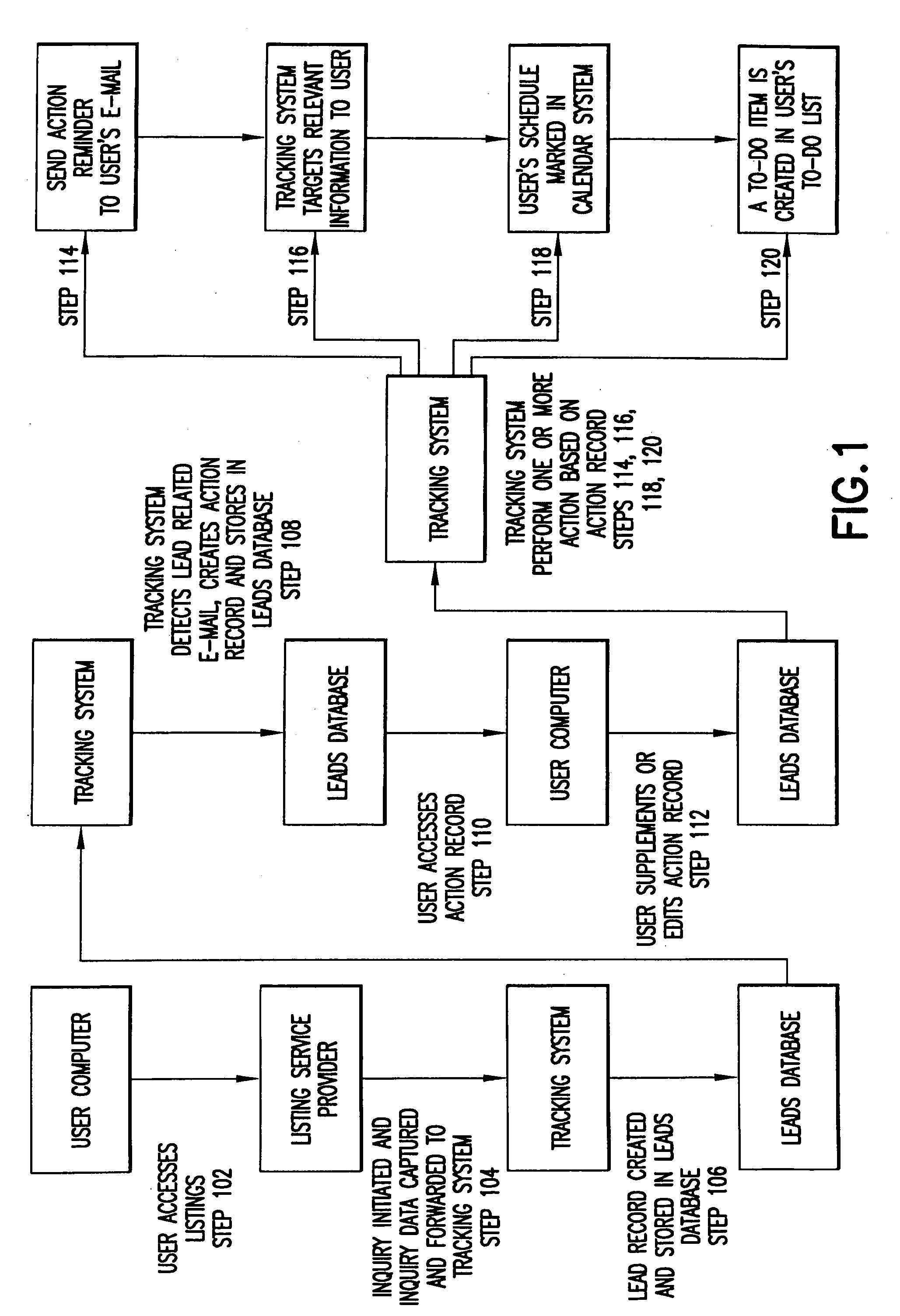
InactiveUS20050125408A1Improve portabilityReceive quicklyDigital data processing detailsMultiple digital computer combinationsAncillary serviceWorld Wide Web
A listing service tracking system and method for tracking a user's interaction with a listing service operates on a core tracking platform that utilizes a “lead” based concept to allow a user to efficiently and concurrently manage a large number of different leads initiated on one or more listing services. In an exemplary embodiment, the core listing service tracking platform is a software application that can be adapted to track a user's interaction with various types of listing services and to communicate with and integrate various types of ancillary services, such as e-mail, calendar systems, alerts systems, and the like.
Owner:OATH INC
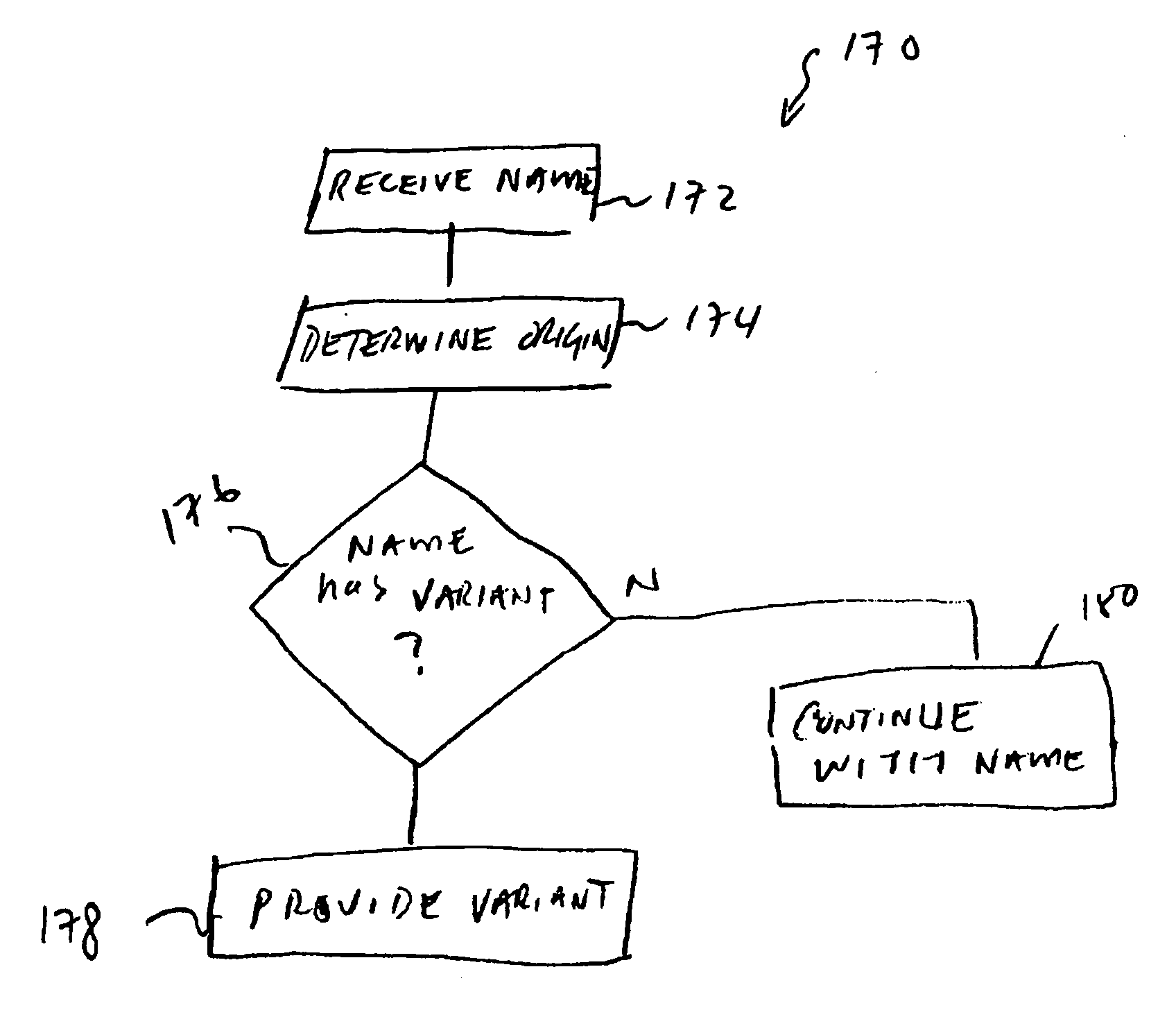
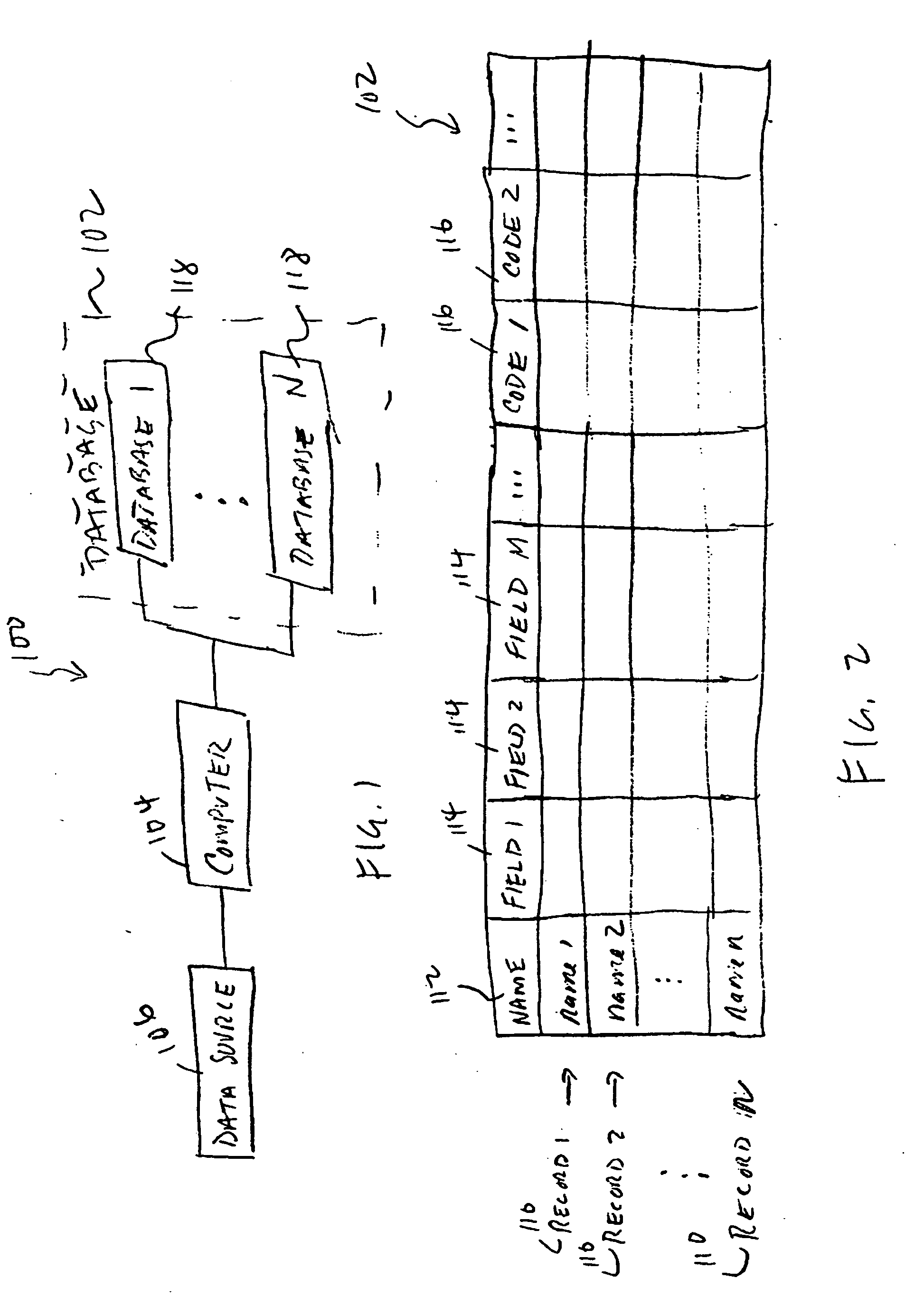
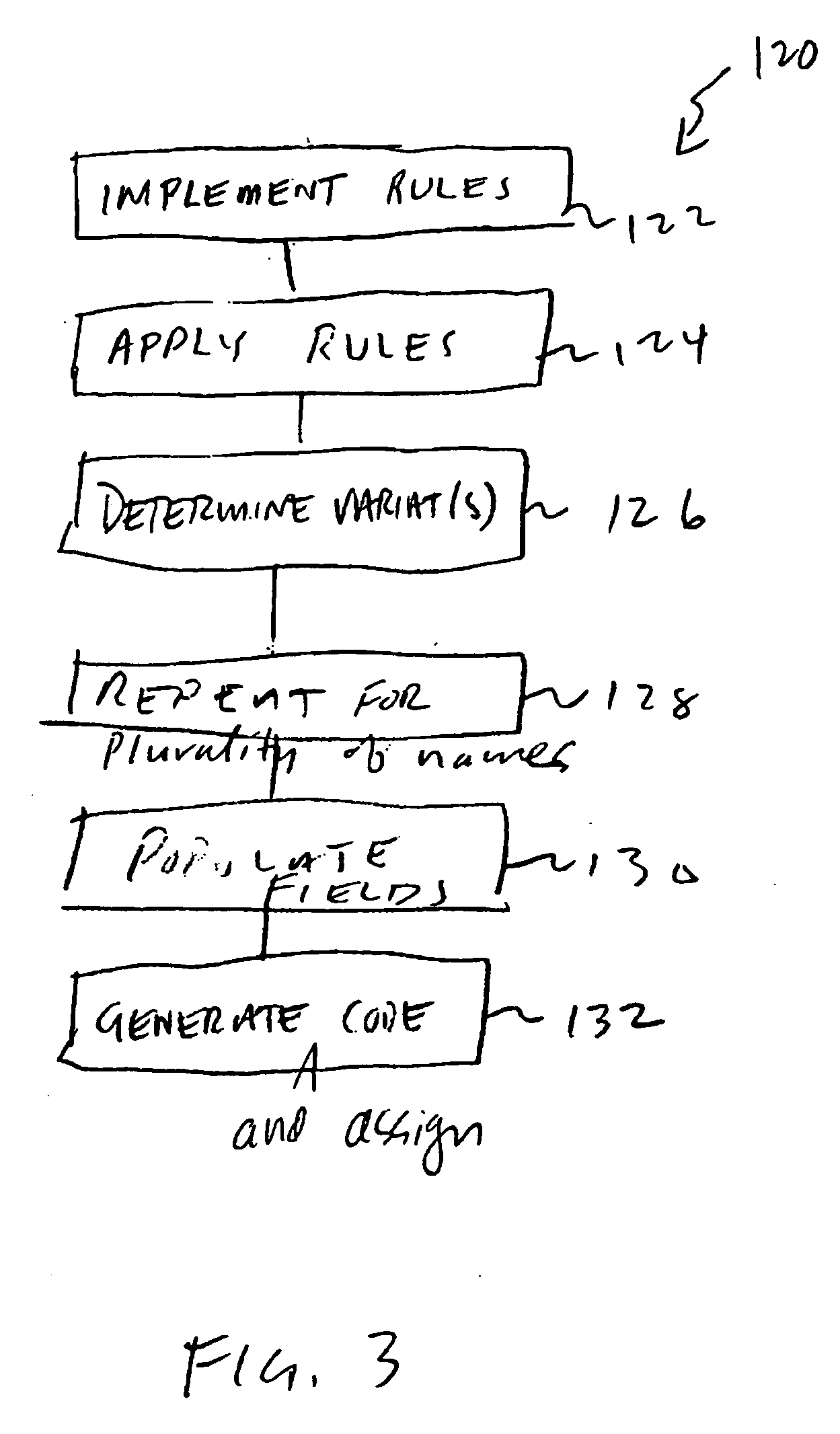
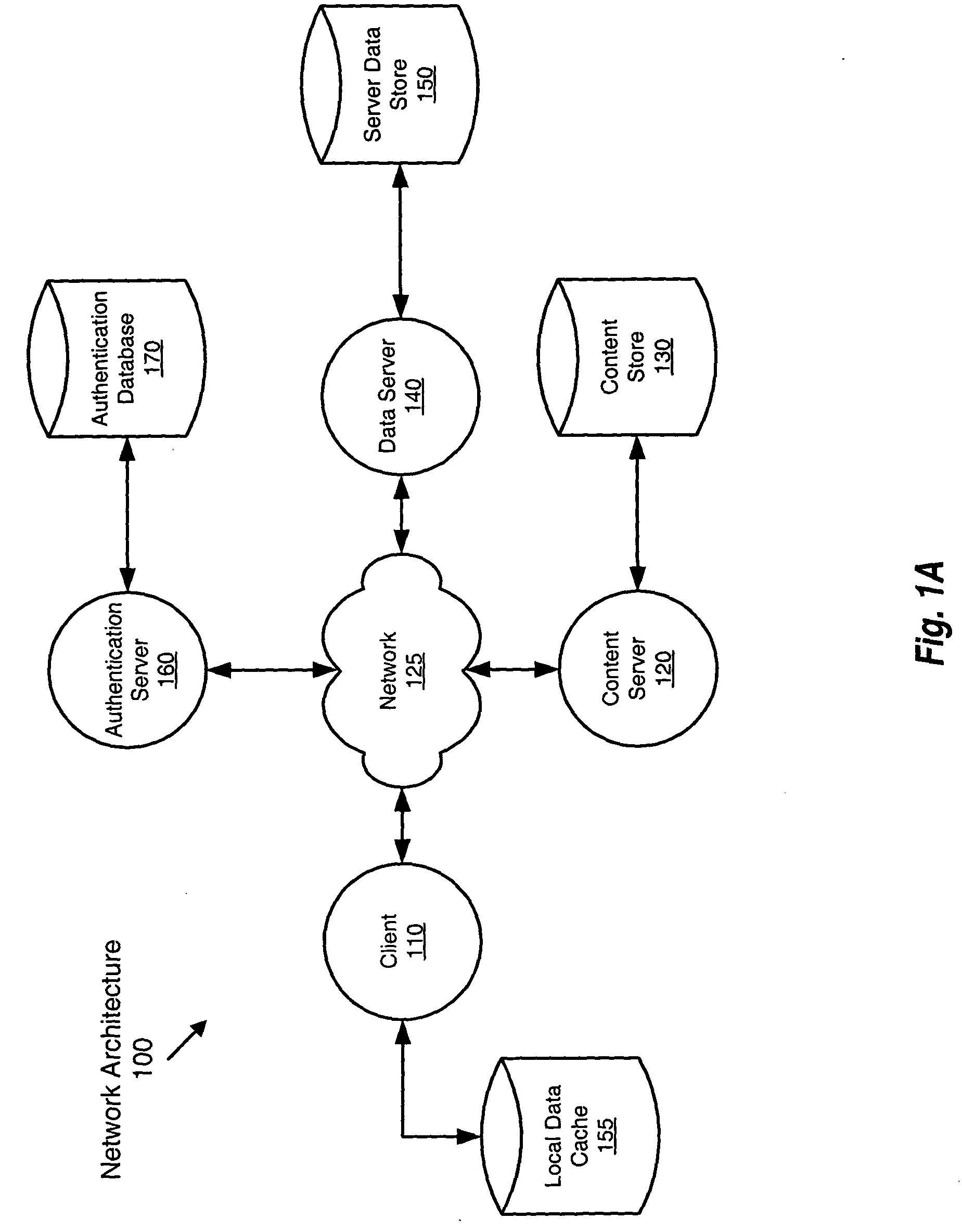
Methods and apparatus for authenticating names
InactiveUS20060031239A1Improve accuracyDigital data processing detailsStructured data retrievalComputer scienceDatabase
Systems and methods for developing, managing and utilizing a name database including a plurality of records each associated with a name with one or more variants and / or equivalents. The name database is driven by geographic, cultural, and linguistic considerations. The name database provides searchers across multiple disciplines, industries, and governments the ability to determine quickly and accurately all possible variants of a name from a query of the database.
Owner:KOENIG DANIEL WILLIAM
Asynchronous peer-to-peer data replication
InactiveUS20050193024A1Low costDigital data processing detailsStructured data retrievalDatabaseAsynchronous data
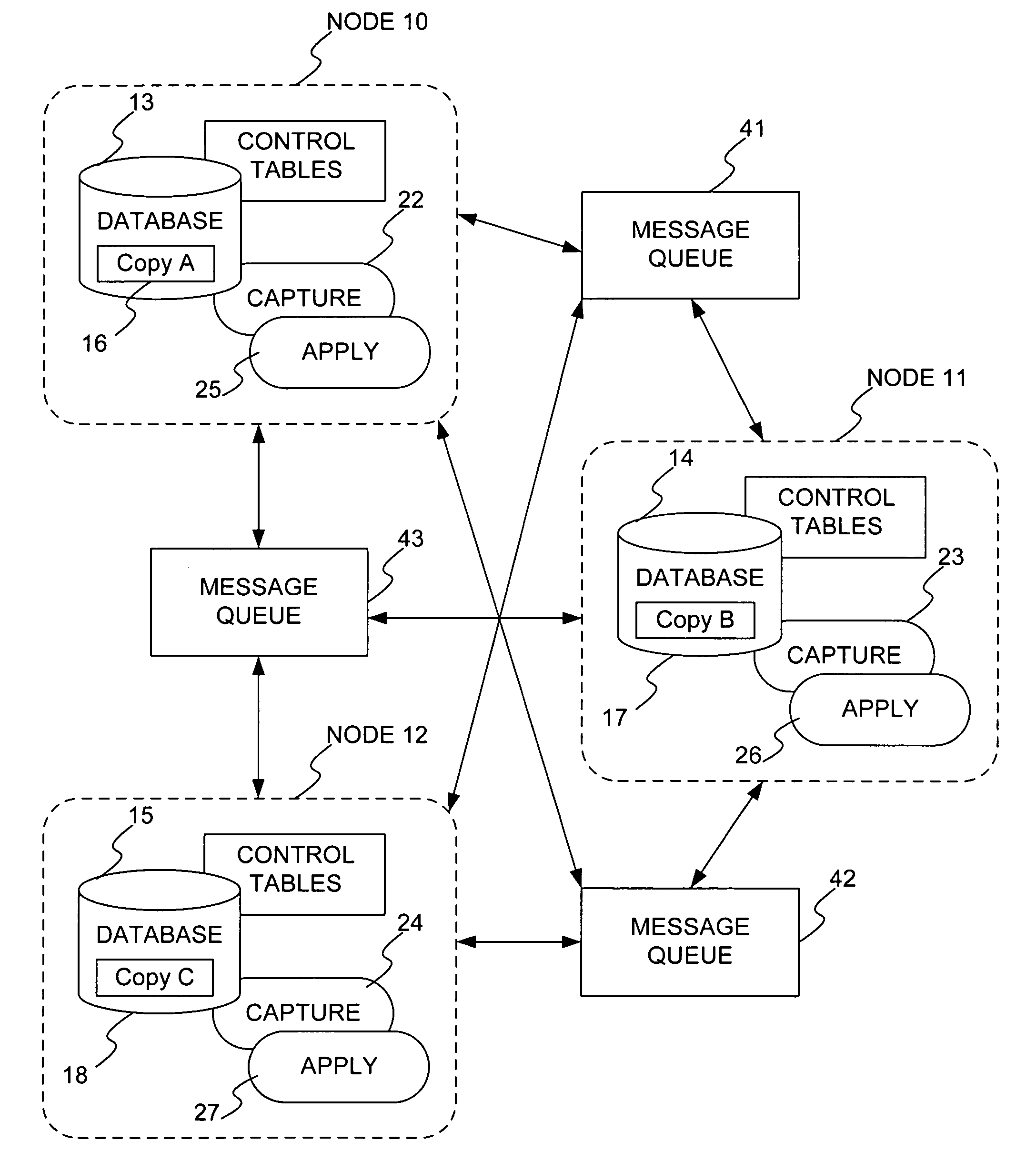
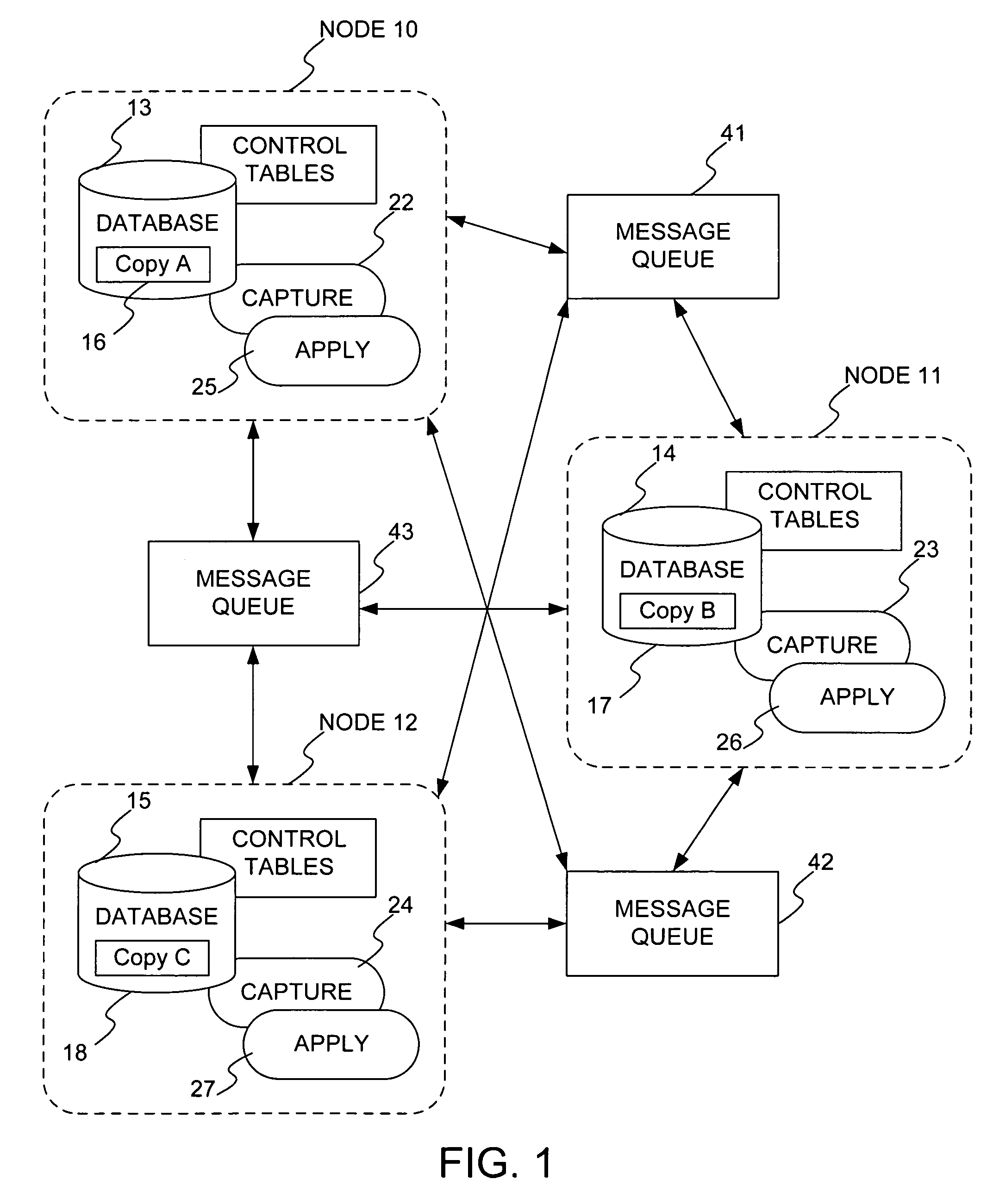
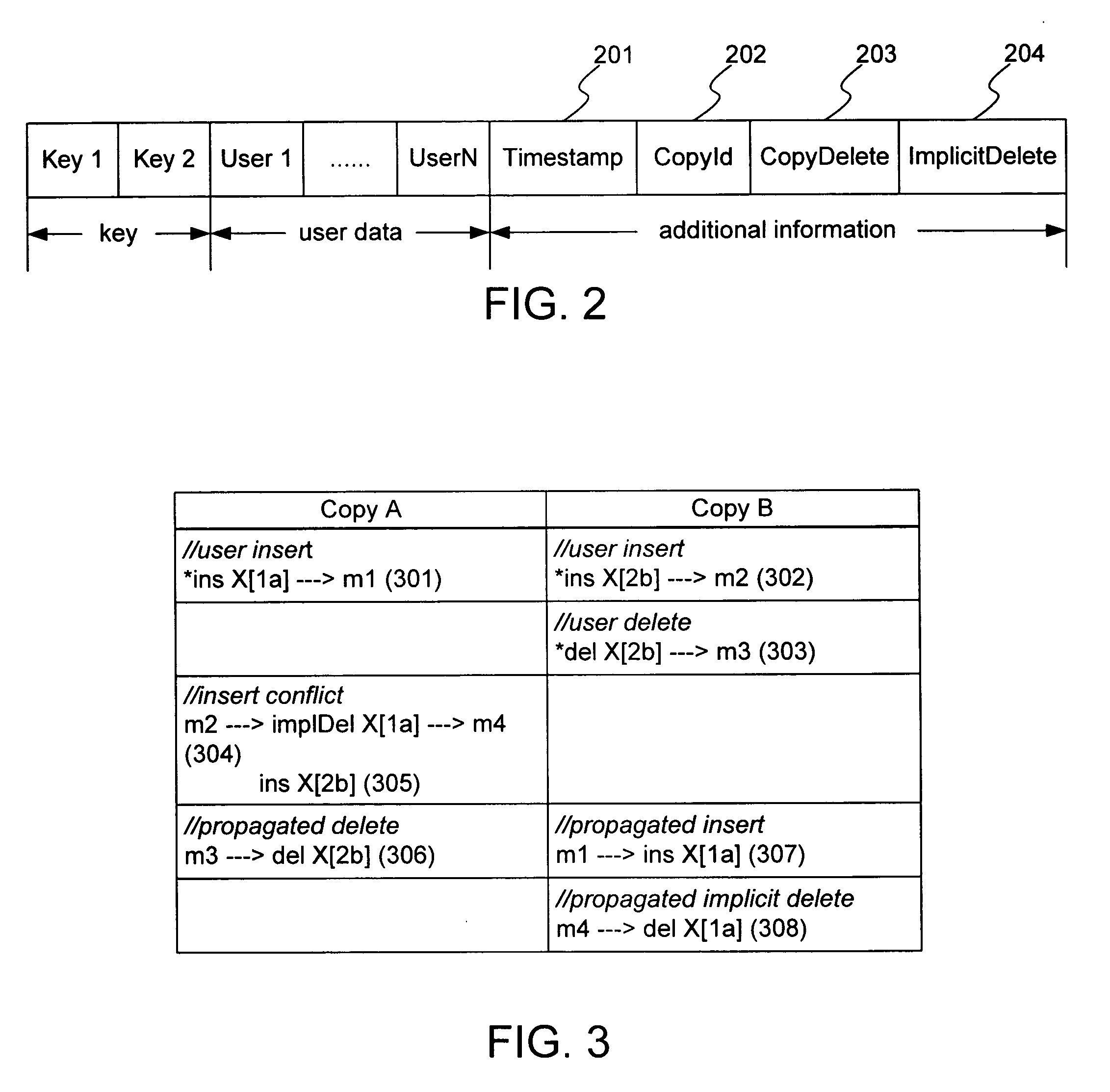
A method and system for providing convergence of data copies in asynchronous data replication in a database system, includes: labeling rows of a plurality of table copies with a monotonic number, a copy identification, and propagation controls; asynchronously capturing at least one labeled change to any row of any of the plurality of table copies from a database recovery log; determining that the captured change is to be communicated to others of the plurality of table copies; communicating the captured change to the others of the plurality of table copies; and applying the communicated change to the others of the plurality of table copies, where the plurality of table copies converge to a same state. In applying the communicated changes, conflicting changes are identified and resolved. In this manner, convergence of data copies in asynchronous data replication is provided, and processing and storage costs are significantly reduced.
Owner:IBM CORP
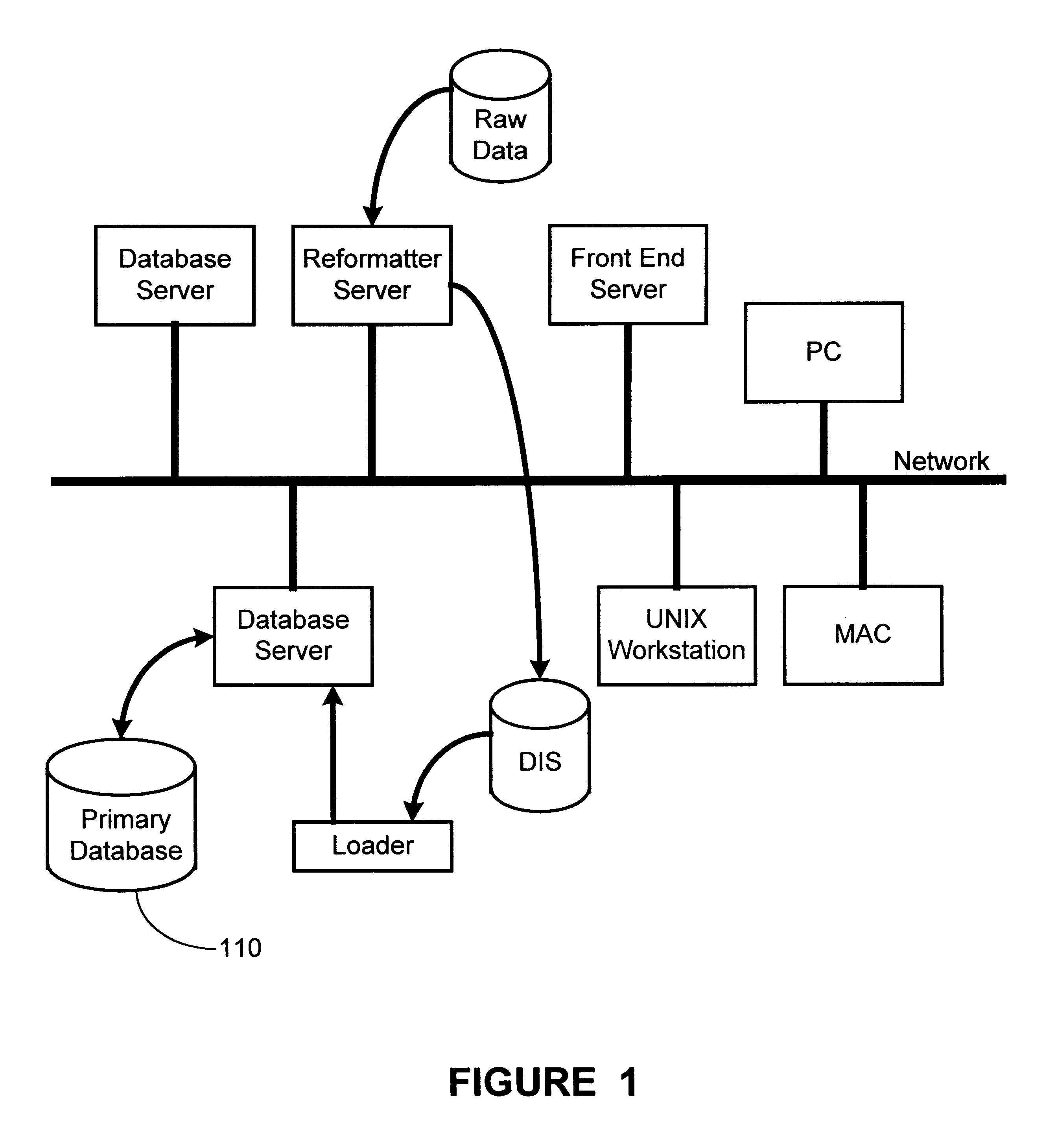
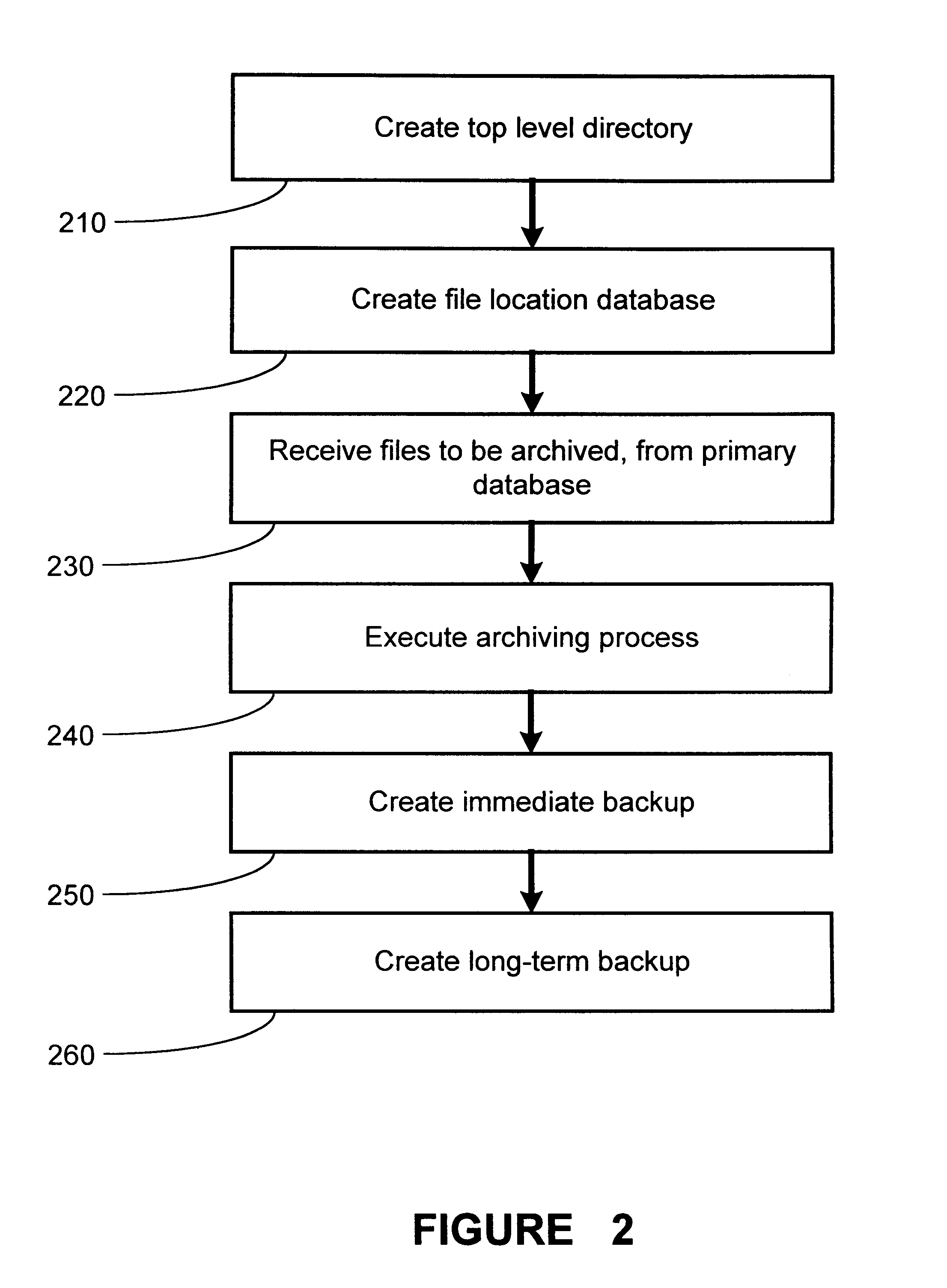
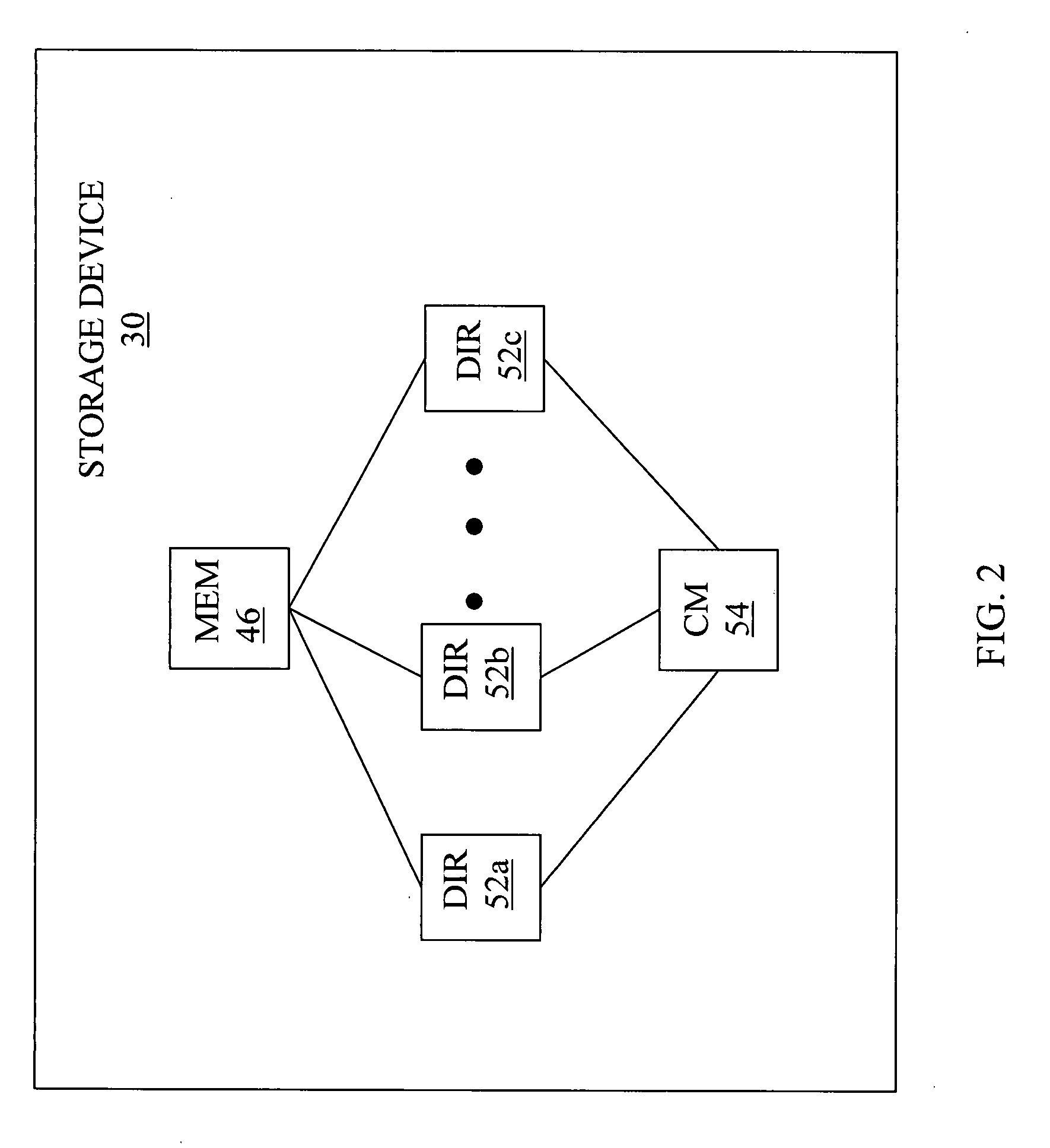
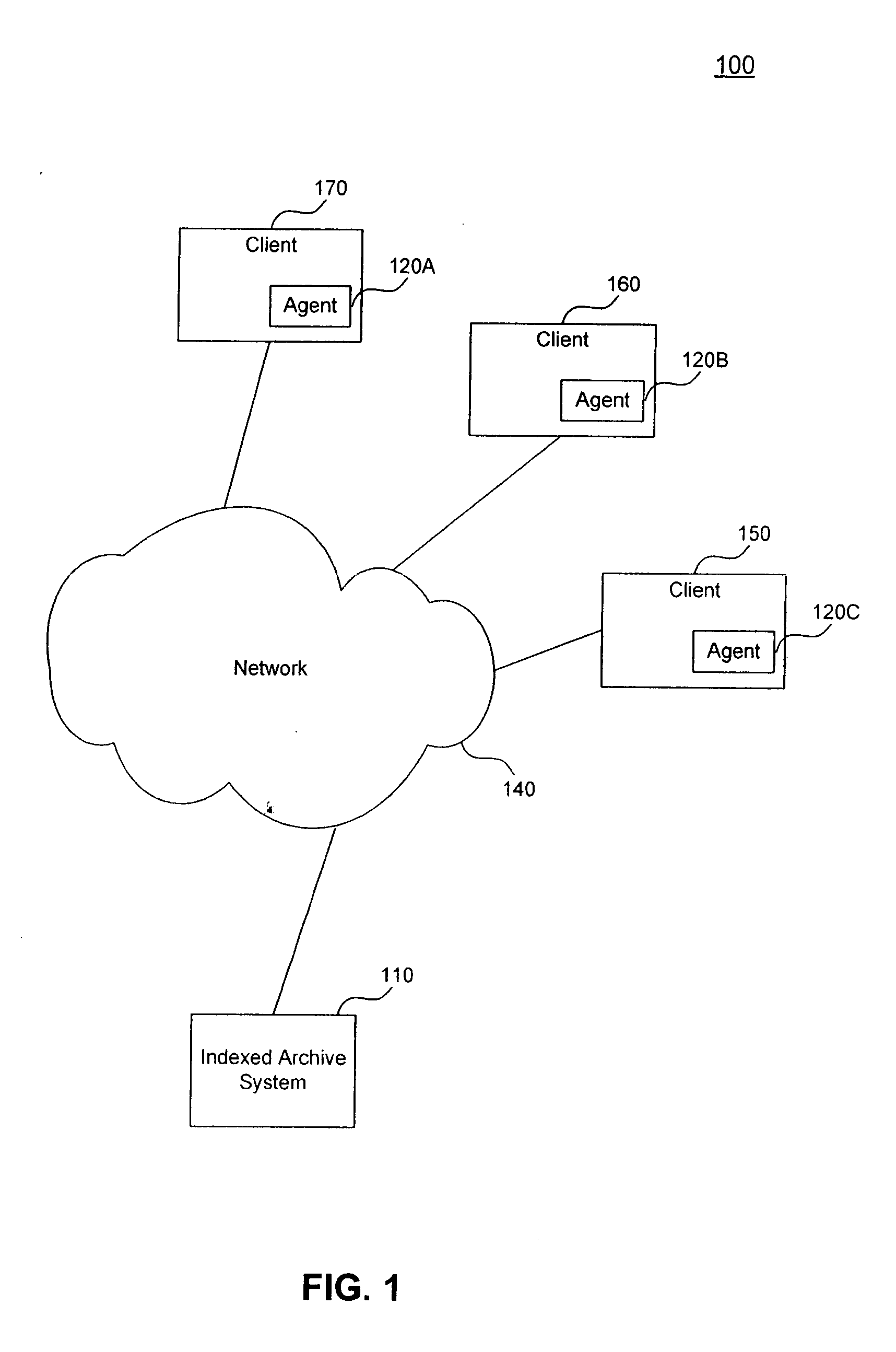
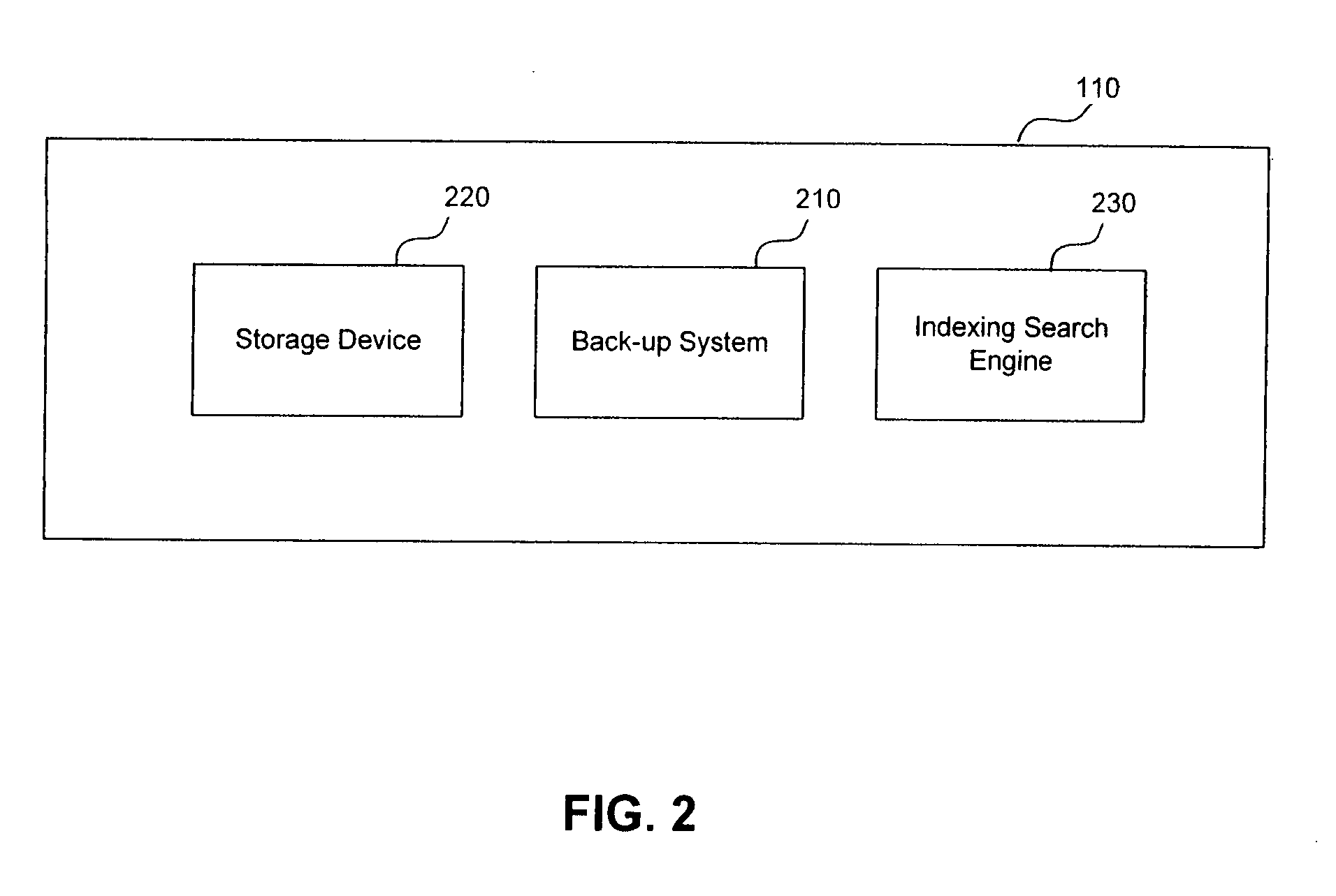
Method and apparatus for hierarchical storage of data for efficient archiving and retrieval of data
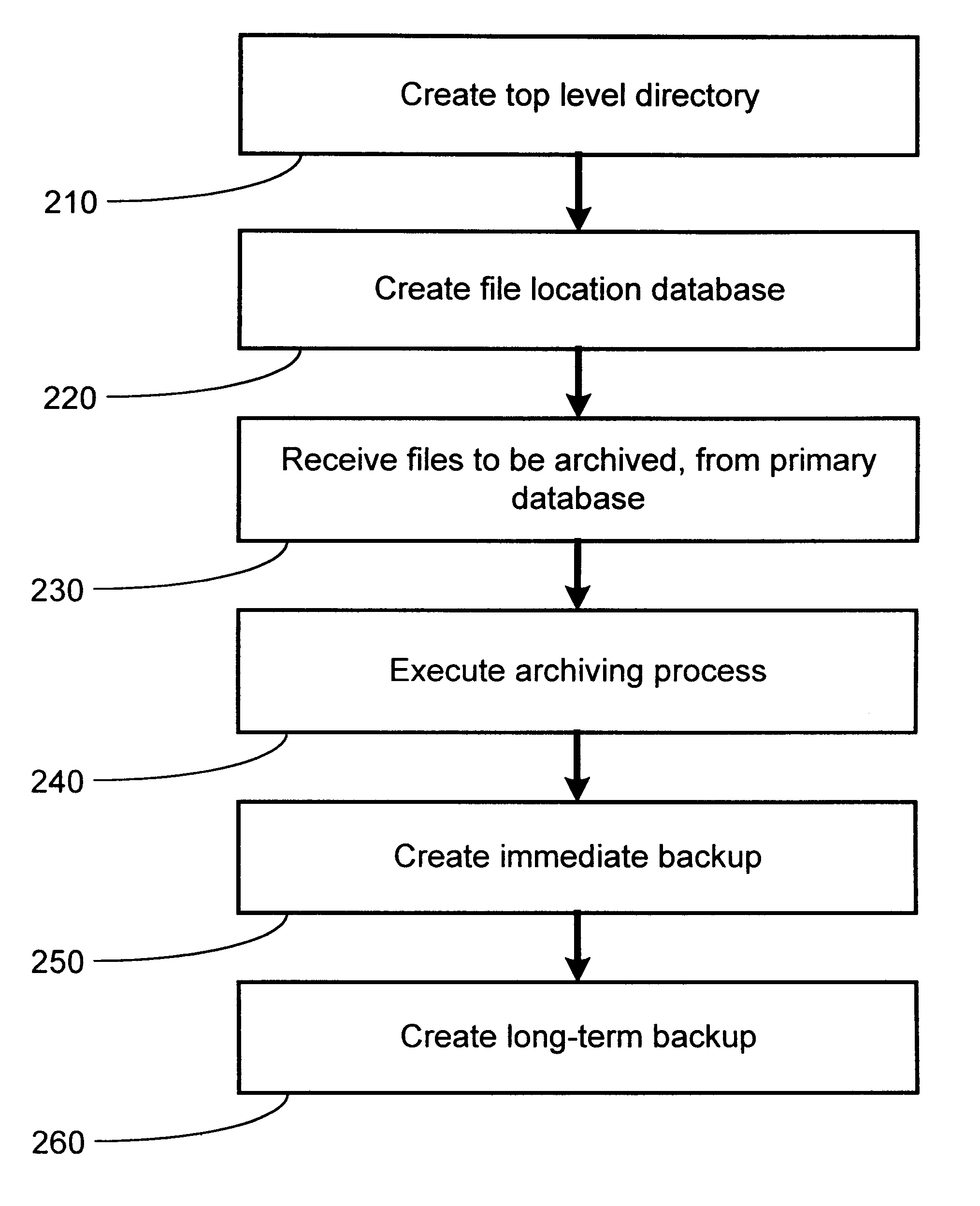
The present invention provides for a method and an apparatus for archiving and retrieving data. At least one top-level directory is created to store files. A file-location database is created to track stored files in the top level directory. Files from a primary database are received. Files received from the database are archived into the top level directory, in response to receiving files from a primary database. An immediate backup of the archived files is created. A long-term backup of the archived files is created.
Owner:GLOBALFOUNDRIES INC
Automated information life-cycle management with thin provisioning
ActiveUS20090070541A1Memory adressing/allocation/relocationStructured data retrievalThin provisioningComputer science
A system for managing data includes providing at least one logical device having a table of information that maps sections of the logical device to sections of at least two storage areas. Characteristics of data associated with at least one section of the logical device may be evaluated. The at least one section of the data may moved between the at least two storage areas according to a policy and based on the characteristics of the data. The table of information is updated according to the movement of data between the at least two storage areas.
Owner:EMC IP HLDG CO LLC
Synchronization of database data
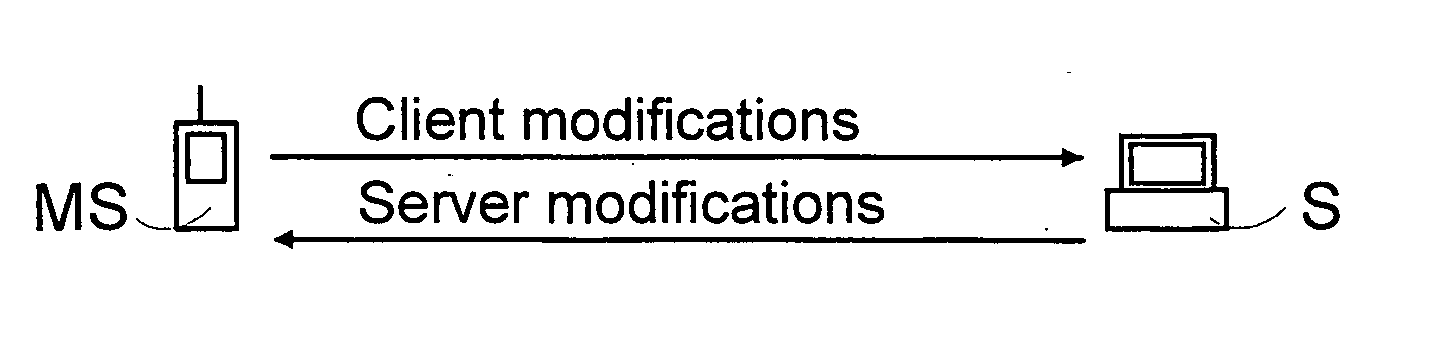
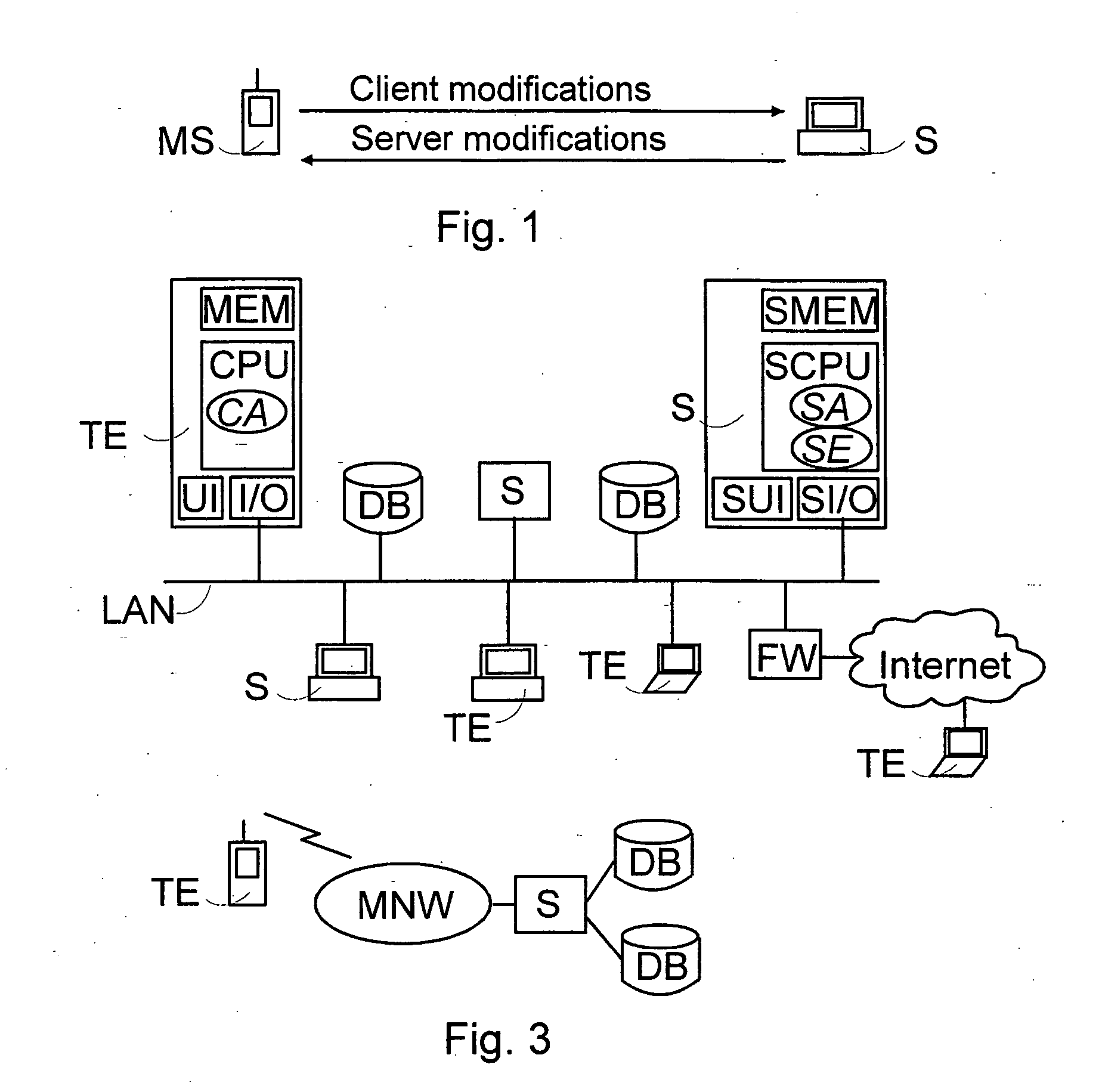
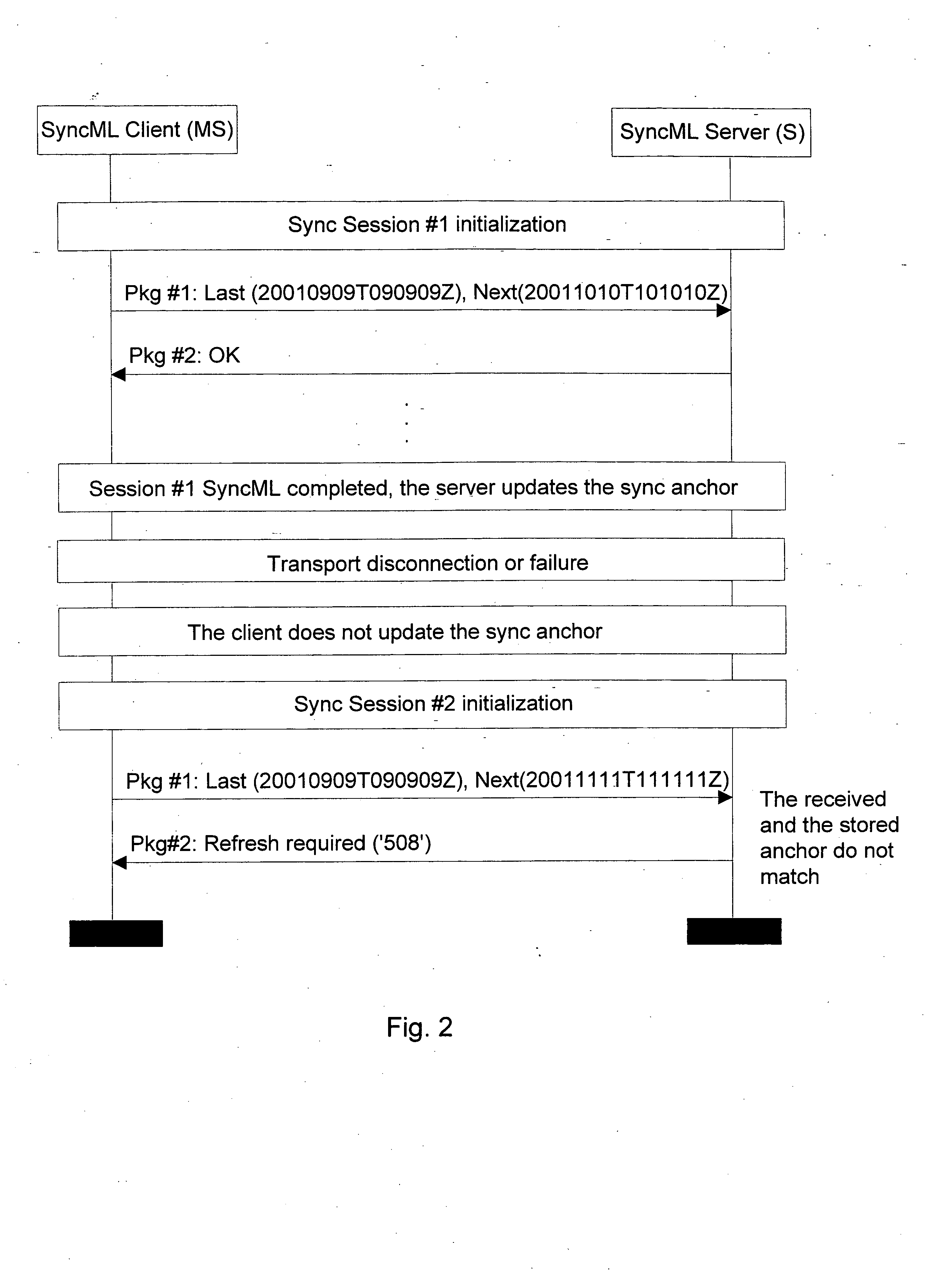
InactiveUS20050125459A1Good synchronizationData processing applicationsNetwork traffic/resource managementTransport layerDistributed computing
A method of arranging synchronization of databases, the method comprising the steps of establishing a transport layer connection for synchronization between a first and a second device which synchronize databases. During initialization of synchronization a first update identifier, which is stored at least in the first device and describes the latest synchronization event the devices have performed in the databases, and a second update identifier, which is defined by the first device and describes the present synchronization, are transmitted from the first device to the second device. The second update identifier is stored in the first and the second device. The contents of the first update identifiers stored in the devices are updated in the first and the second device if synchronization has been performed and after this said transport layer connection has been ended substantially properly.
Owner:NOKIA TECH OY
Method, system, and program for archiving files
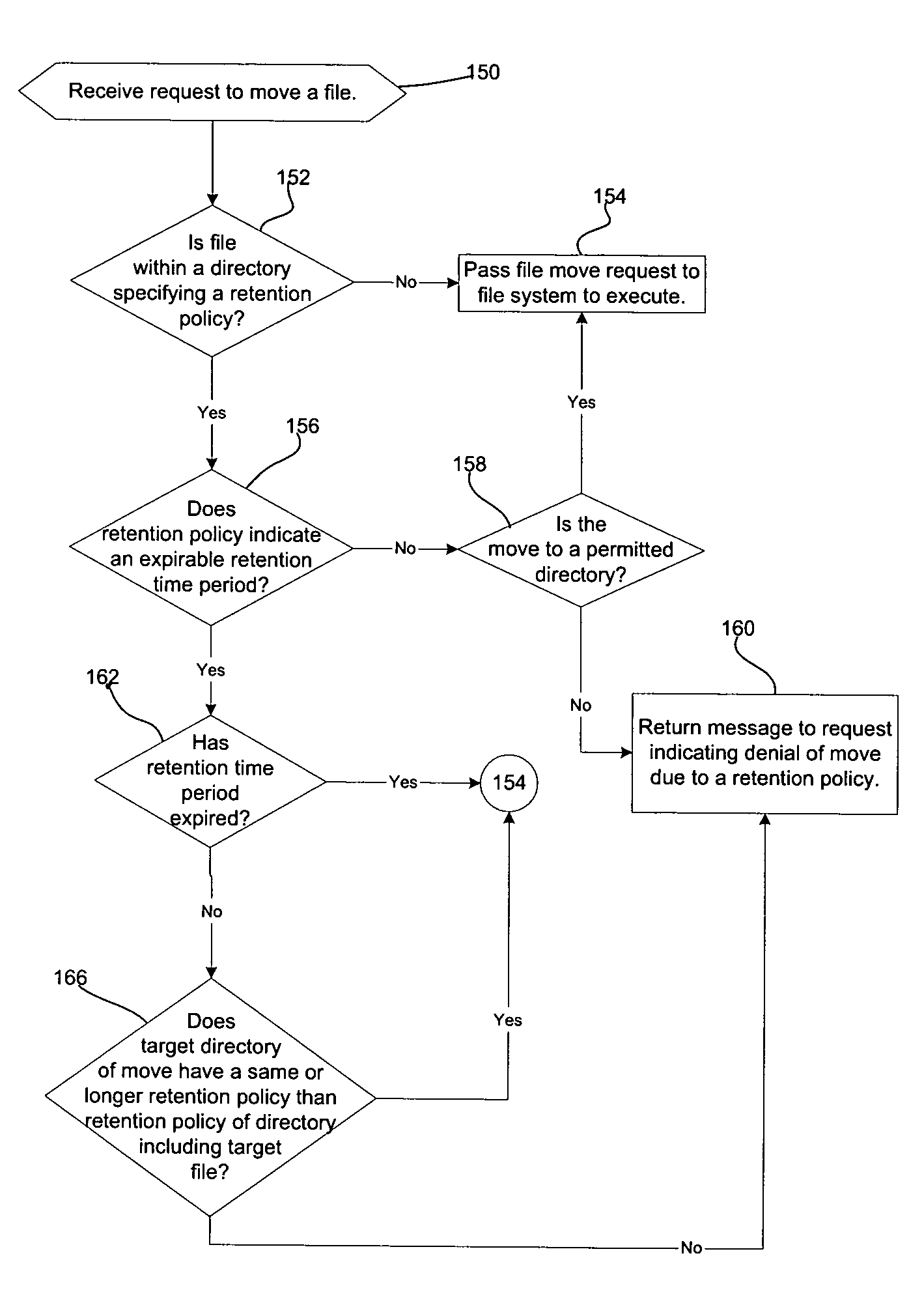
Provided are a method, system, and program for archiving files. A hierarchical file system having directories is provided. An archival retention policy is associated with at least one of the directories in the hierarchical file system, wherein the retention policy applies to files included in the associated directory, and wherein the retention policy specifies a retention time indicating a time period during which a file is subject to the retention policy.
Owner:GOOGLE LLC
System and method for the automated notification of compatibility between real-time network participants
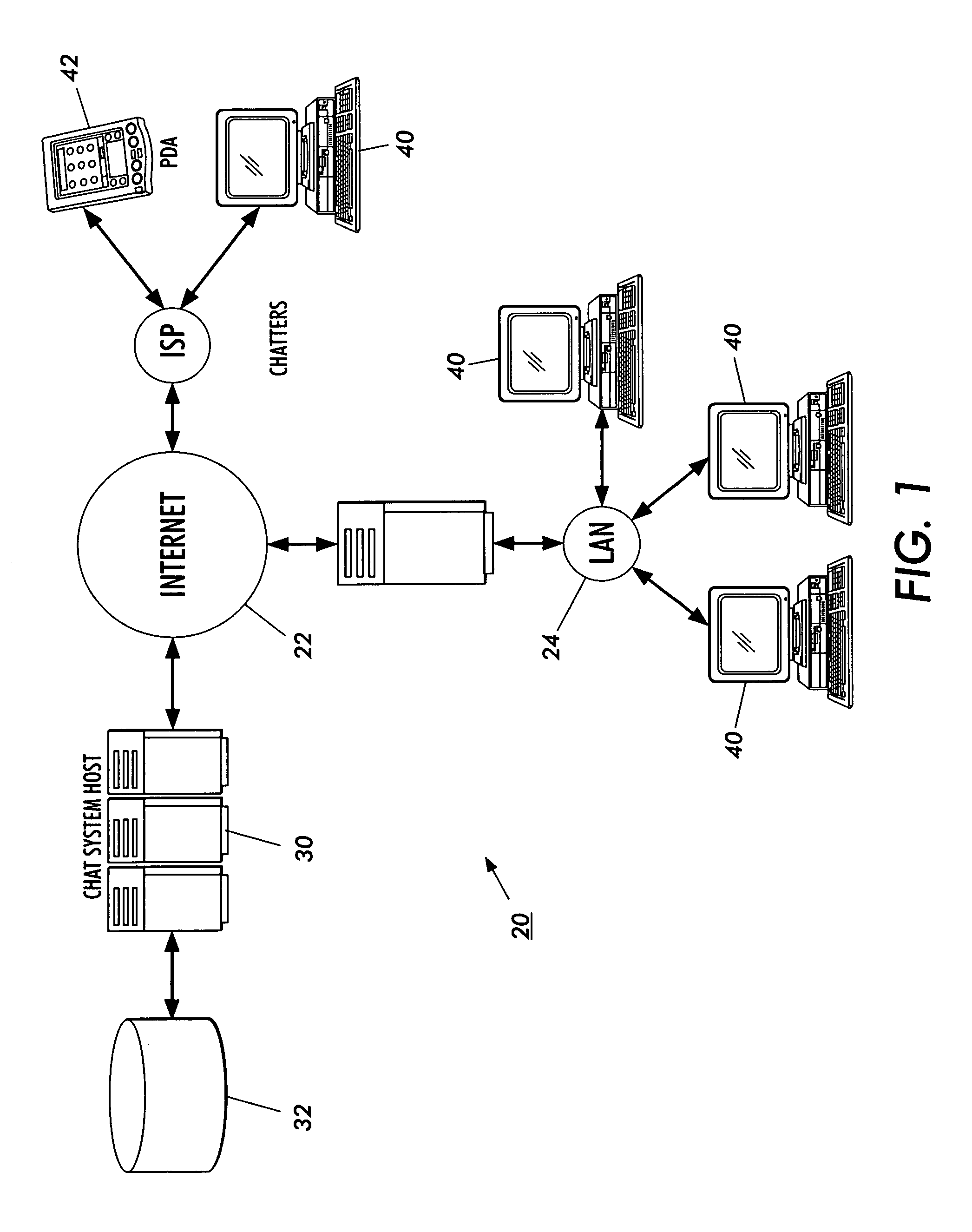
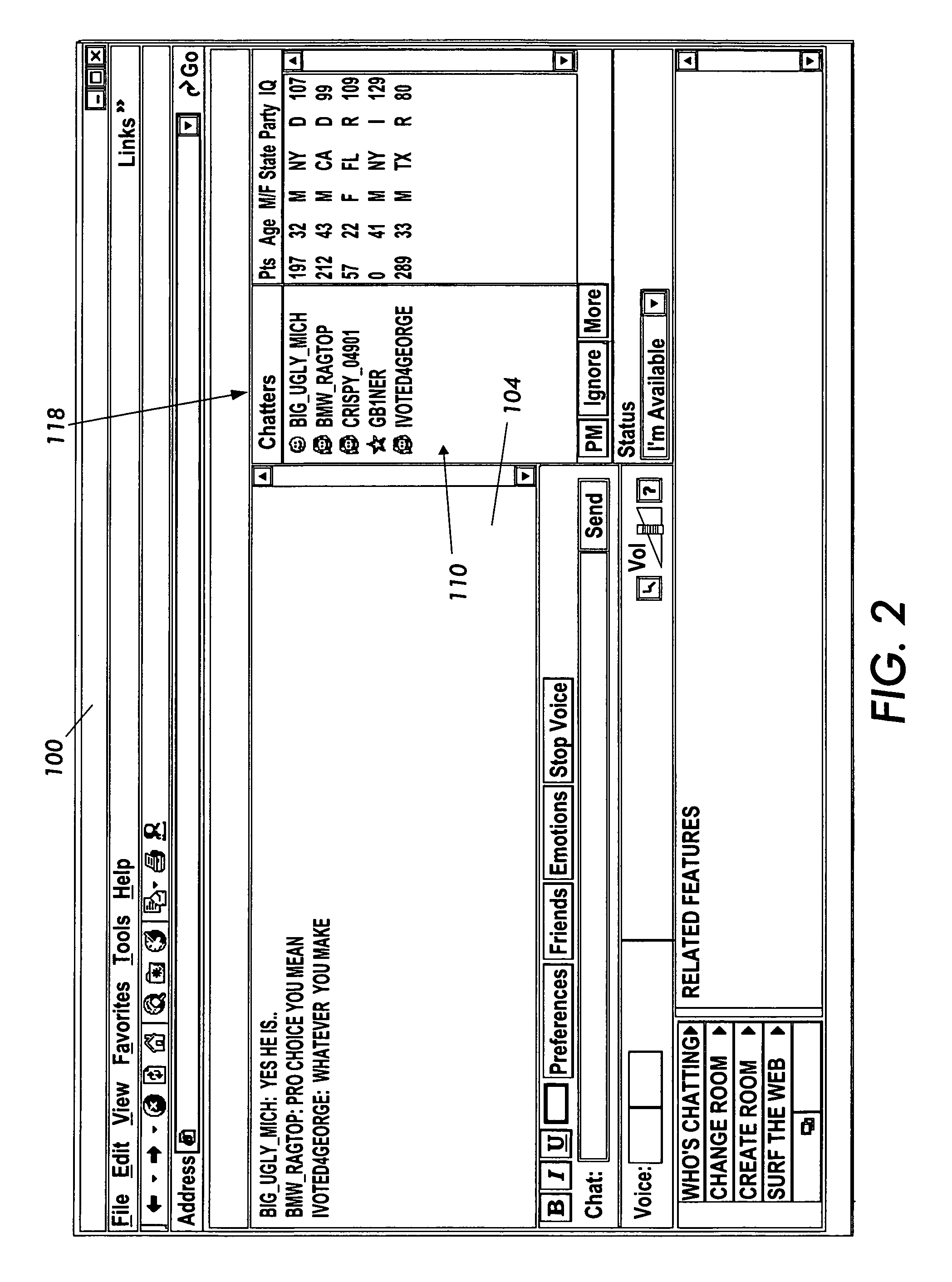
InactiveUS7401098B2Shorten the timeSolve the real problemSpecial service provision for substationInformation formatReal-time webChat room
The present invention is a method and system for using predetermined preferences / characteristics to ascertain personal compatibility between network or chat room participants based upon profile information. When the system determines that these preferences are favorable for interpersonal compatibility, the system will automatically notify or page the participants so as to facilitate their introduction. Further functionality, aside from the compatibility based upon profile information, includes e-mail and other electronic notification of personal compatibility as well as geographic compatibility.
Owner:JEDI TECH
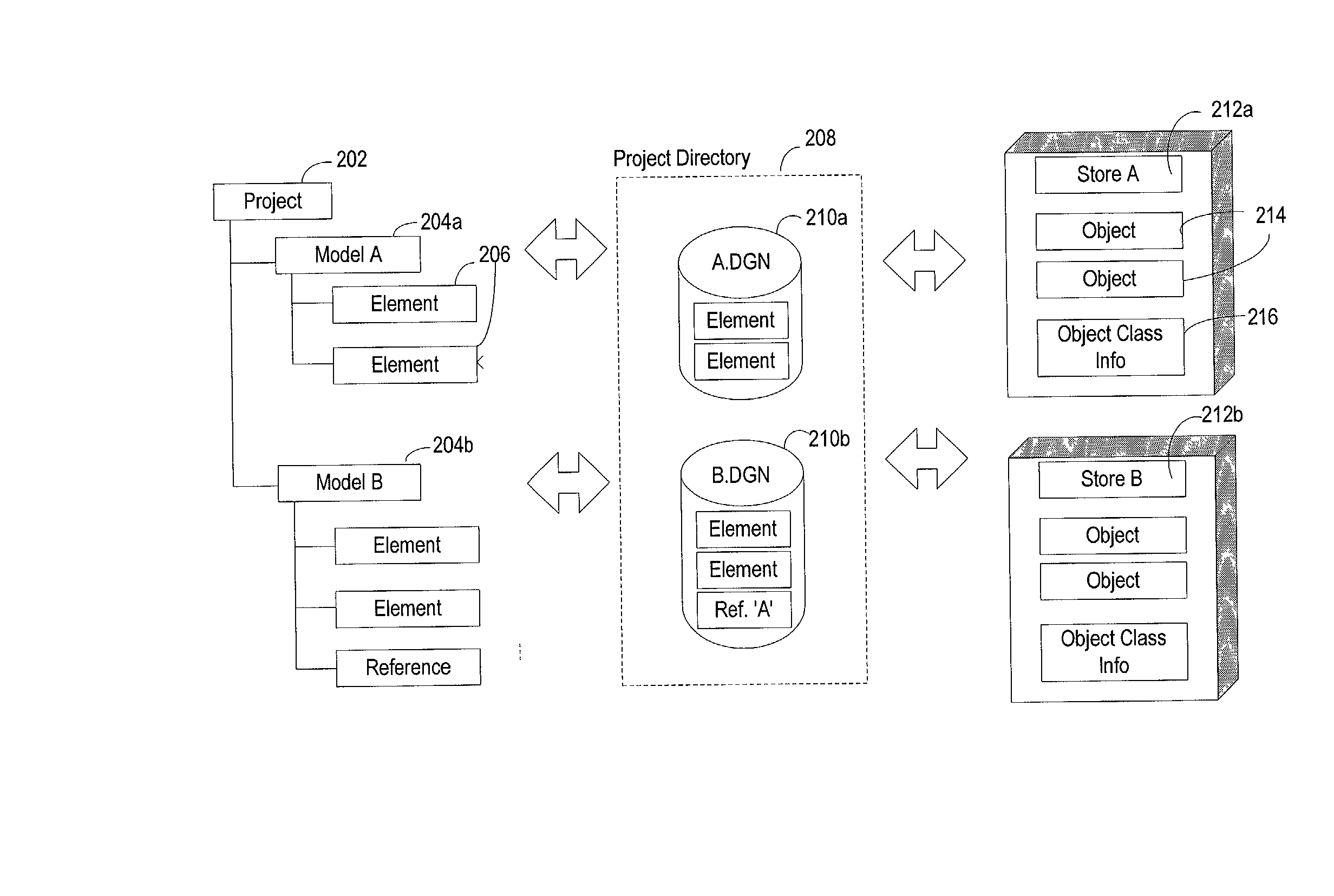
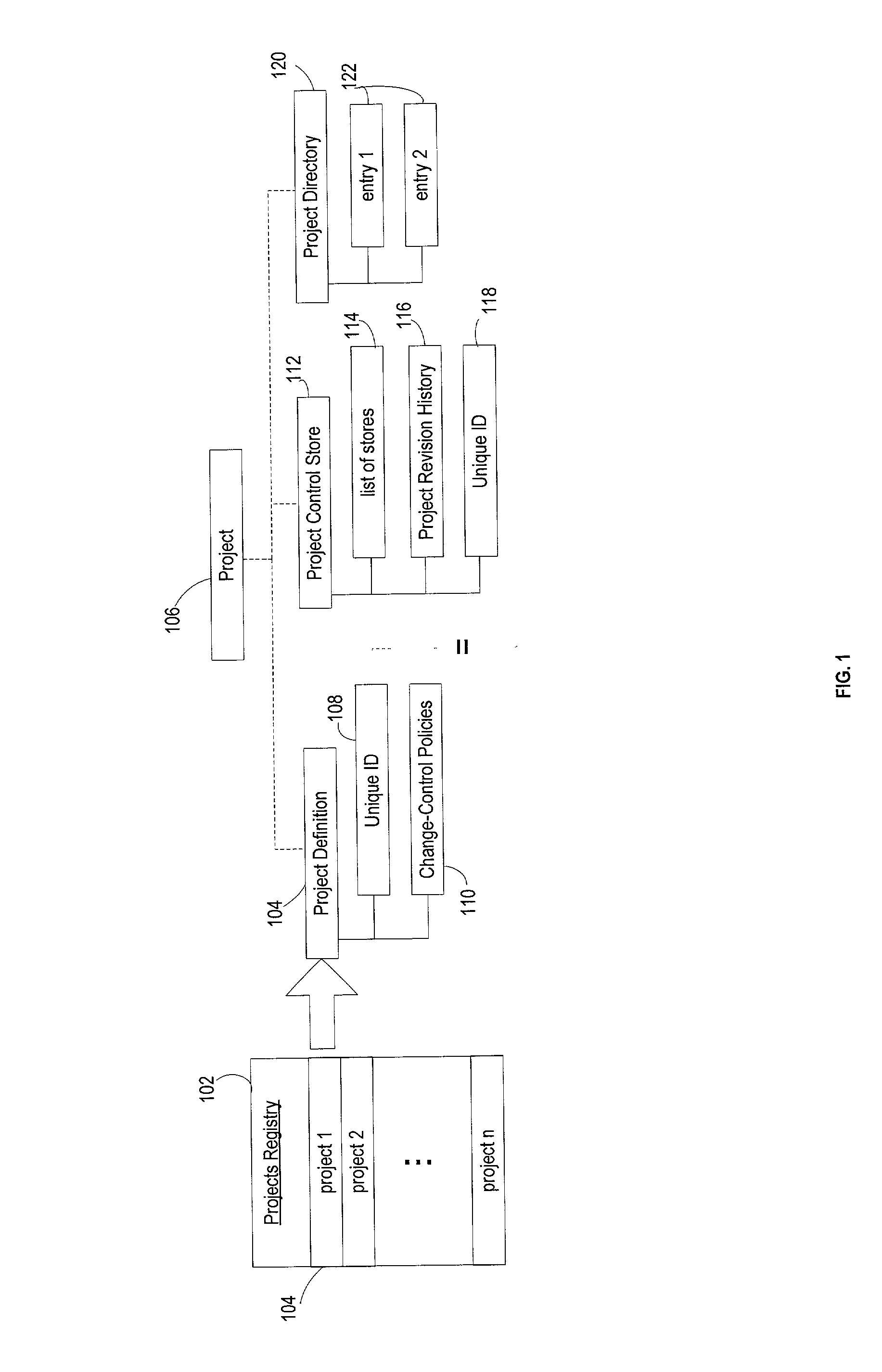
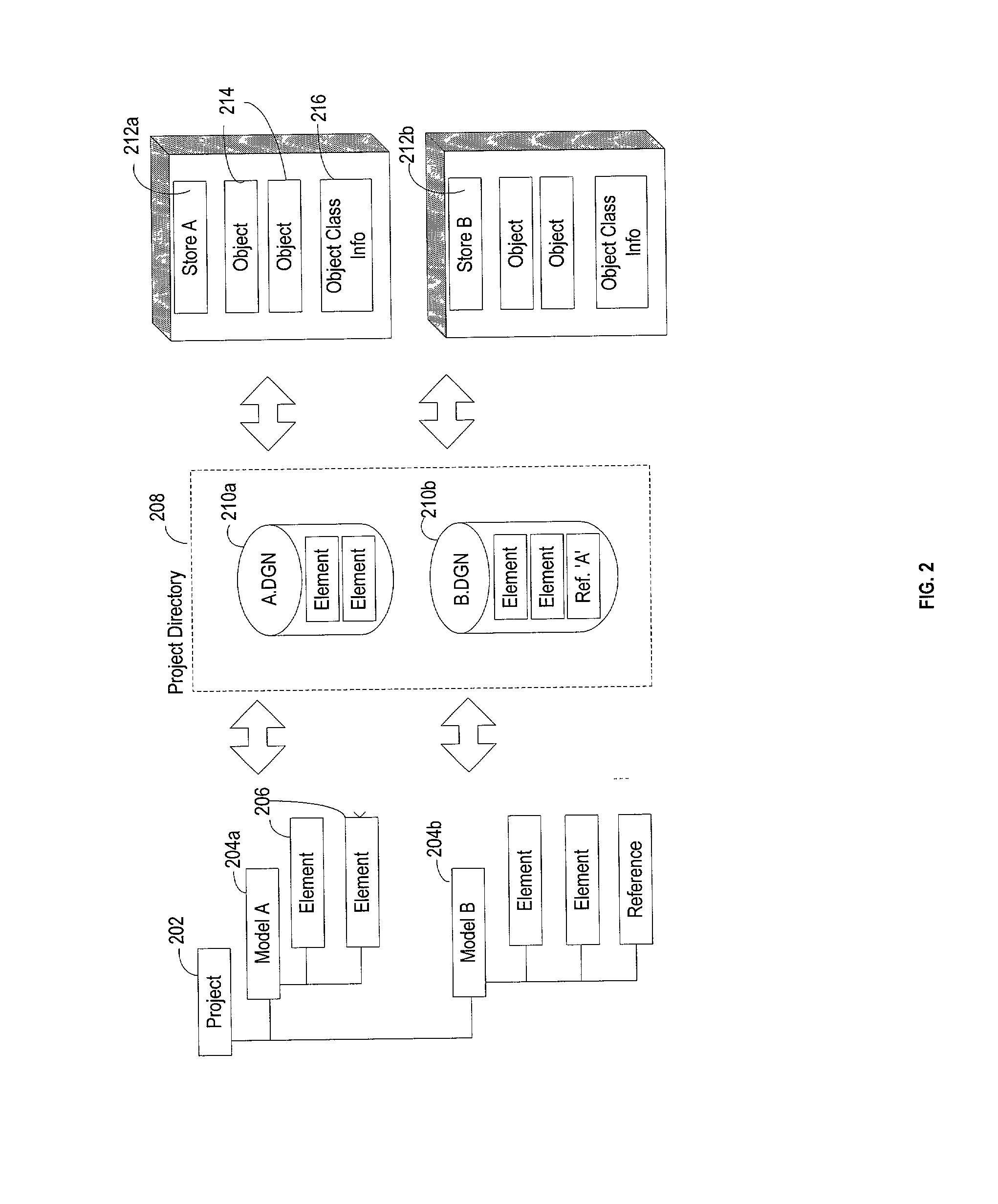
System, method and computer program product for collaborative engineering using component and file oriented tools
InactiveUS20020029218A1Data processing applicationsDigital data processing detailsSoftware engineeringClient-side
Conventional file-based engineering design data for an engineering model are represented by a plurality of components. The plurality of components are kept in stores, which reside on servers. Each store contains the components that correspond to the elements of one design file. The stores also maintain a history of changes made to the components. A plurality of client computers are bidirectionally connected to the servers. Each client computer may obtain the current version of the components and may send locally edited versions of the components back to the servers to replace the current versions in the stores. At the client computer, the user interacts with the components using conventional file-based software. Before the locally edited versions of the components are committed to the servers to replace the current versions, a synchronization and merging process occurs whereby the latest version of the components are downloaded to the client computer and are compared to the locally edited version of the components to detect resolvable (compatible) and unresolvable (incompatible) conflicts. The commit process is performed only if no unresolvable conflicts exist between the two versions of the components. To facilitate translation between file-based data and components, a schema is written to "wrap" each of the engineering file formats. Each schema is a set of classes that capture all of the information in the file-based data.
Owner:BENTLEY SYST INC
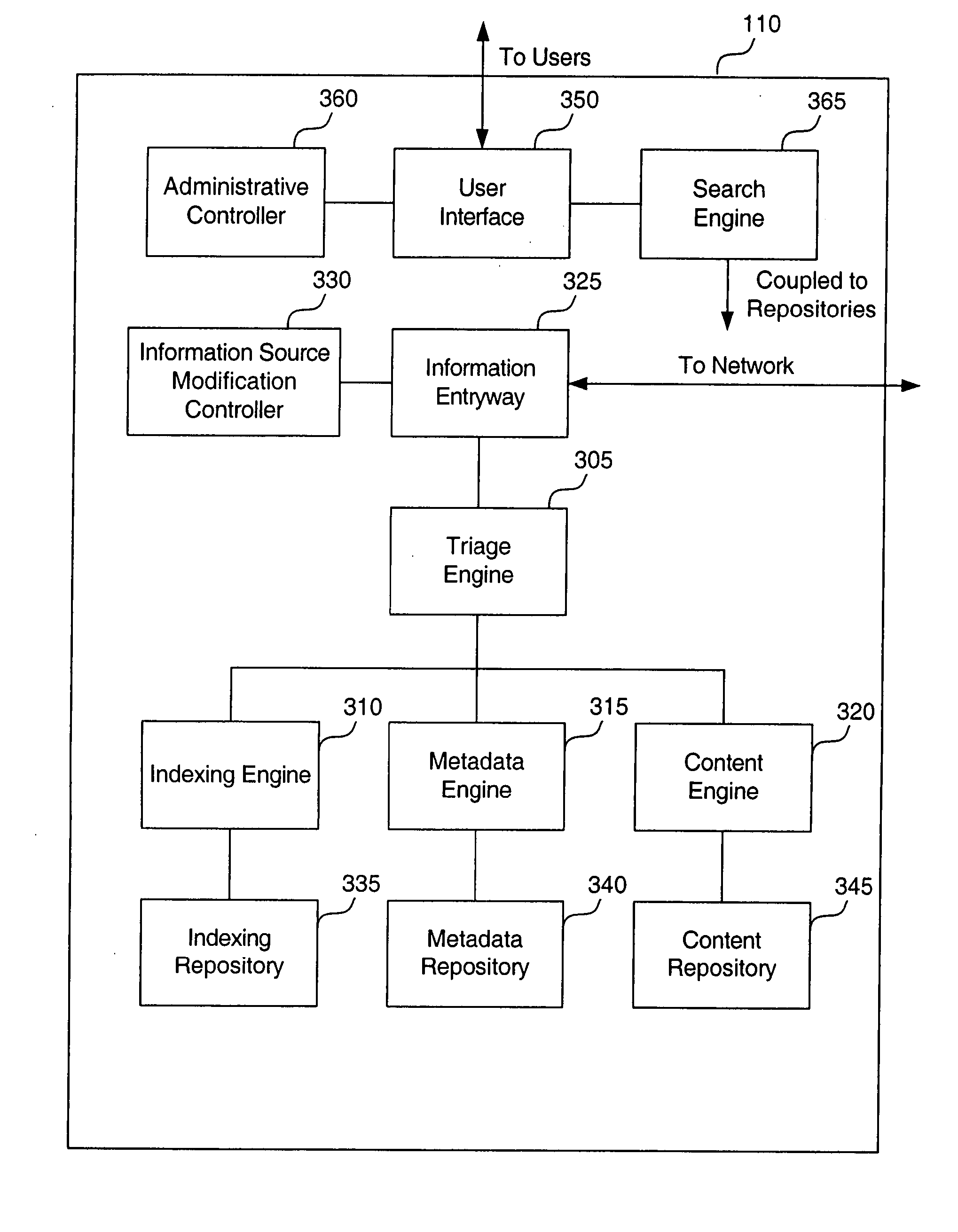
Data management systems and methods for distributed data storage and management using content signatures
InactiveUS20070276823A1Error detection/correctionComputer security arrangementsDistributed data storeData management
Data management systems and methods for distributed content storage and management using content signatures that use file identicality properties are provided. A data management system is provided that includes a content engine for managing the storage of file content, a content signature generator that generates a unique content signature for a file processed by the content engine, a content signature comparator that compares content signatures and a content signature repository that stores content signatures. Methods are provided for the efficient management of files using content signatures that take advantage of file identicality properties. Content signature application modules and registries exist within information source clients and centralized servers to support the content signature methods.
Owner:CARMENSO DATA LIABILITY
System and method for data management
InactiveUS20050203864A1Small sizeEliminate duplicationStructured data retrievalSpecial data processing applicationsData sliceClassification treatment
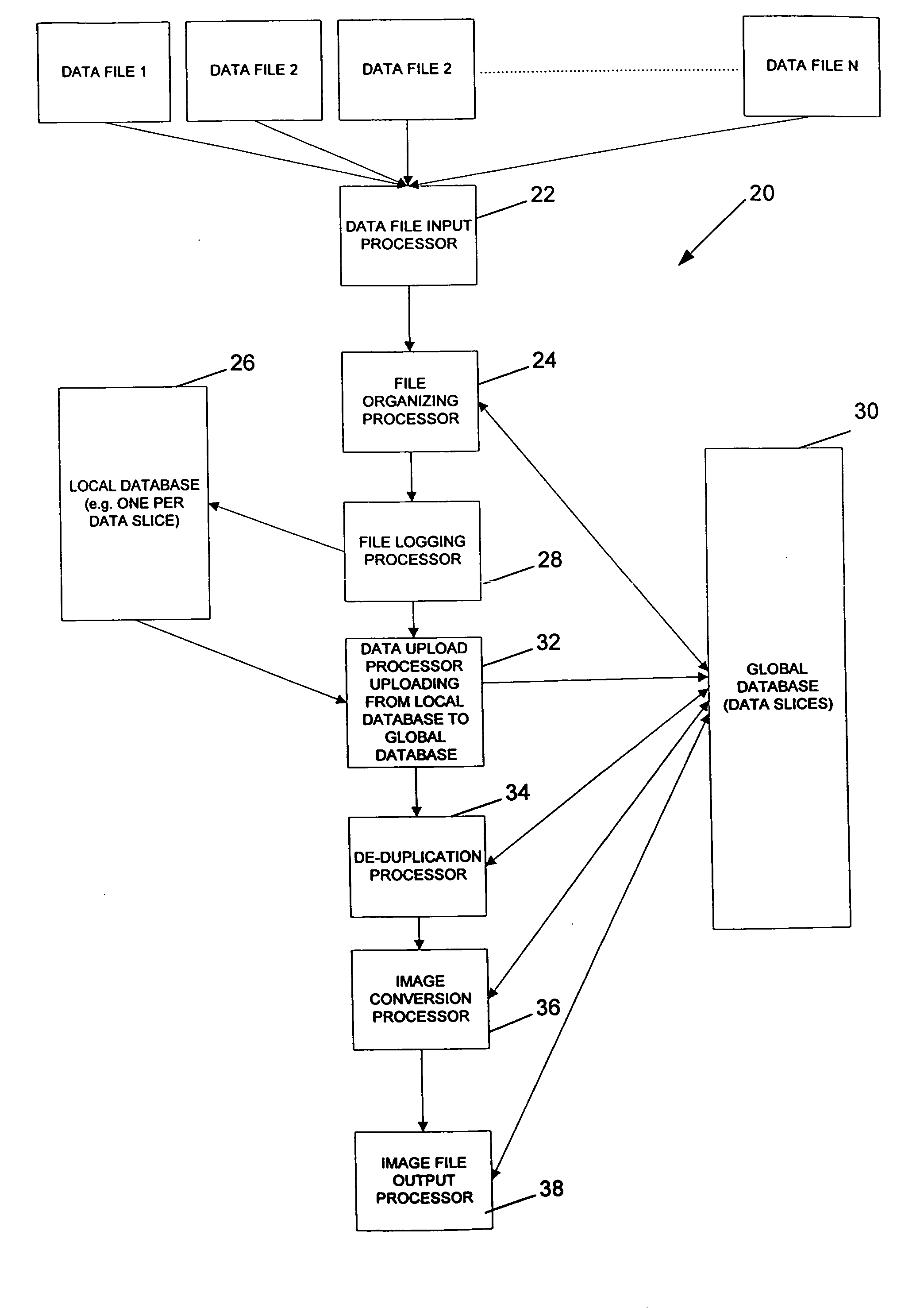
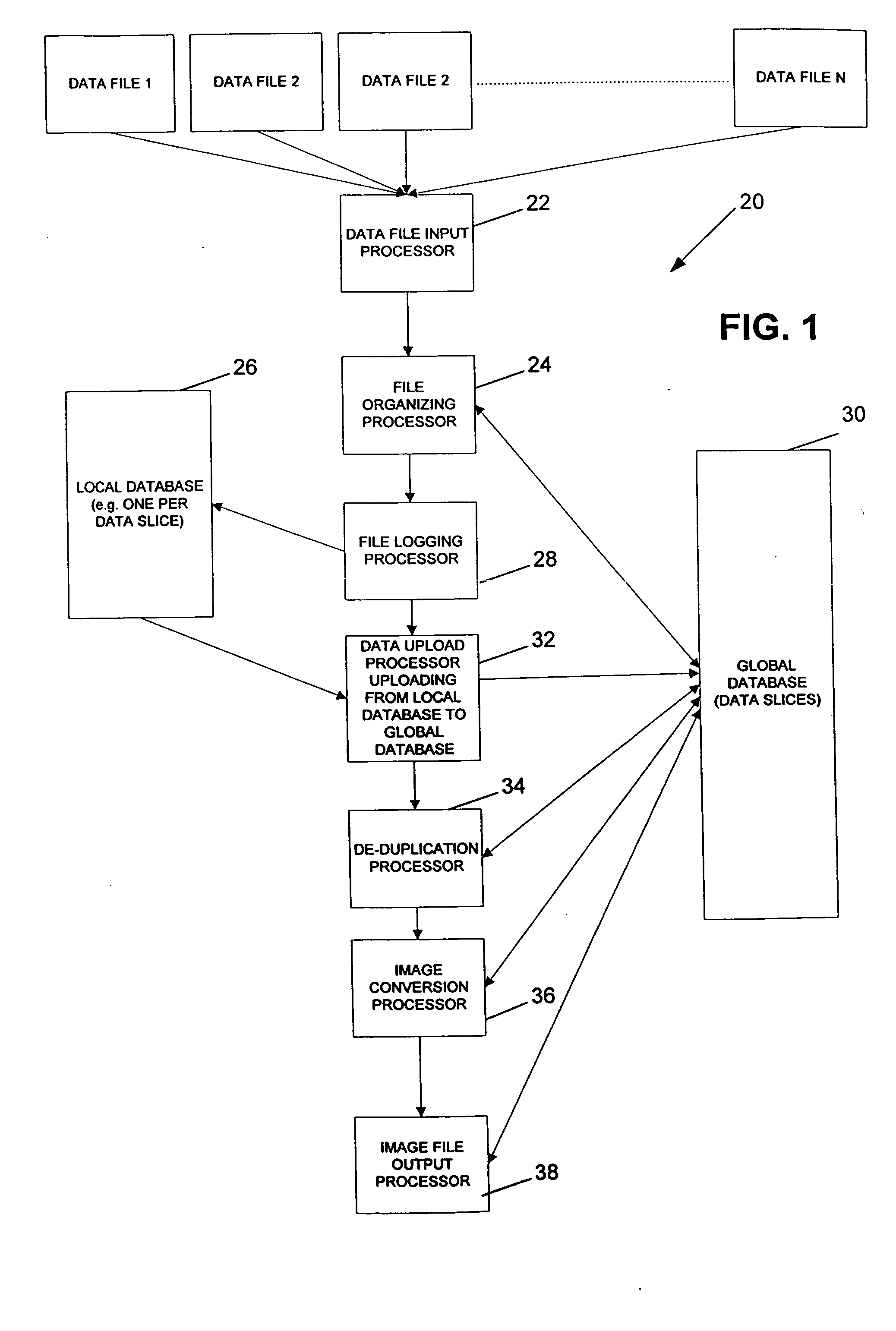
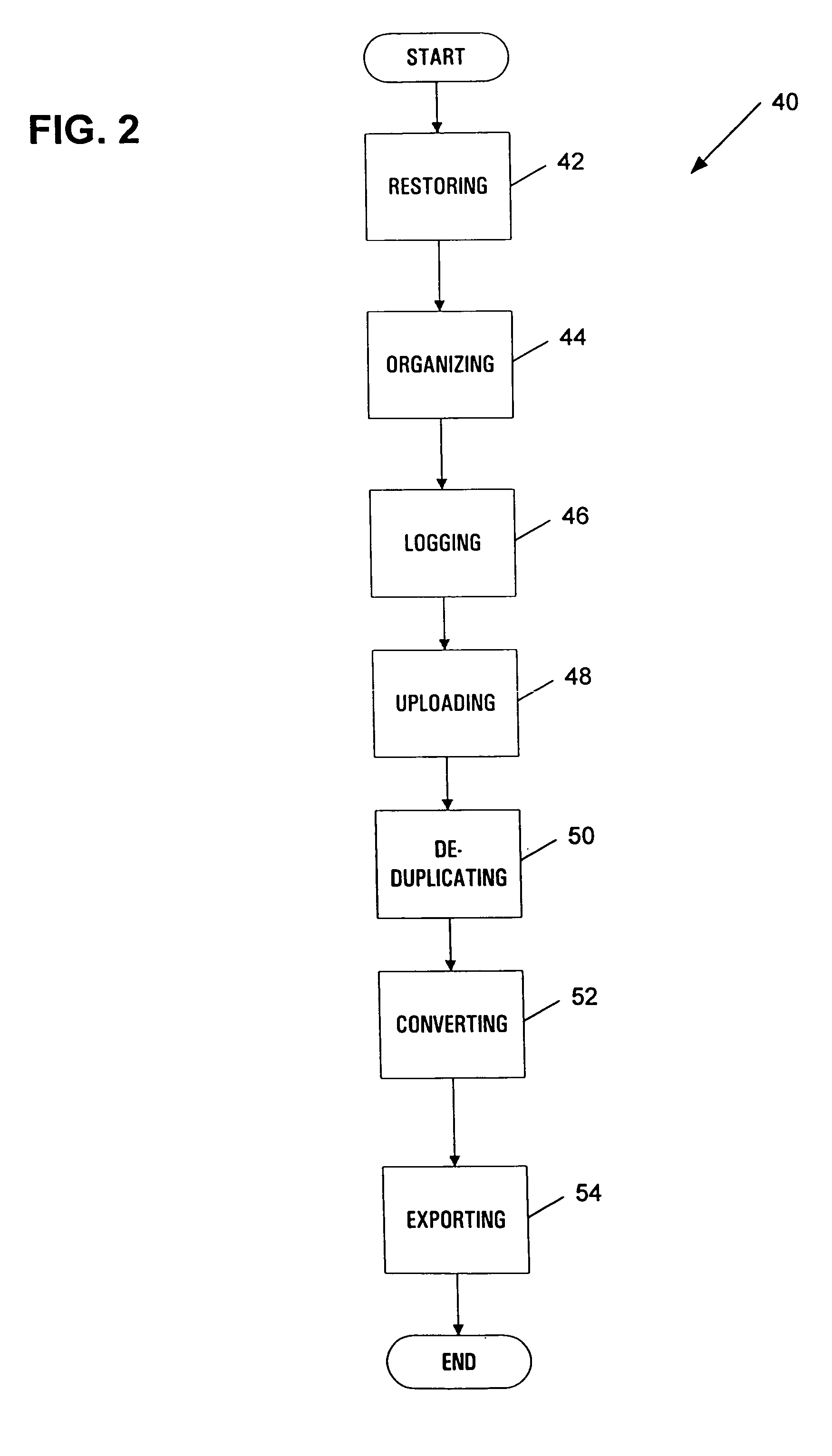
An automated data management system and method for logging, processing, and reporting a large volume of data having different file types, using different versions, stored on different media, and / or run by different operating systems, includes a first processor for restoring a plurality of received data files, the data files being capable of being different file types; a file organizing / categorizing processor for organizing the received data files into data slices, each data slice including an identification number and a descriptor that describes characteristics of the received data file; a file logging processor for logging the received data files into a first database based on the data slices; a data uploading processor for uploading the first database to a second database; a de-duplicate processor for calculating a SHA value of the received data files to determine whether the received data files have duplicates and flagging duplicated data files in the second database; an image conversion processor for converting at least a portion of the received data files into image files; and a second processor for exporting the image files.
Owner:KROLL ONTRACK INC
Information source agent systems and methods for distributed data storage and management using content signatures
Information source agent systems and methods for distributed content storage and management using content signatures that use file identicality properties are provided. A data management system is provided that includes a content engine for managing the storage of file content, a content signature generator that generates a unique content signature for a file processed by the content engine, a content signature comparator that compares content signatures and a content signature repository that stores content signatures. Information source agents are provided that include content signature generators and content signature comparators. Methods are provided for the efficient management of files using content signatures that take advantage of file identicality properties. Content signature application modules and registries exist within information source clients and centralized servers to support the content signature methods.
Owner:CALLAHAN CELLULAR L L C
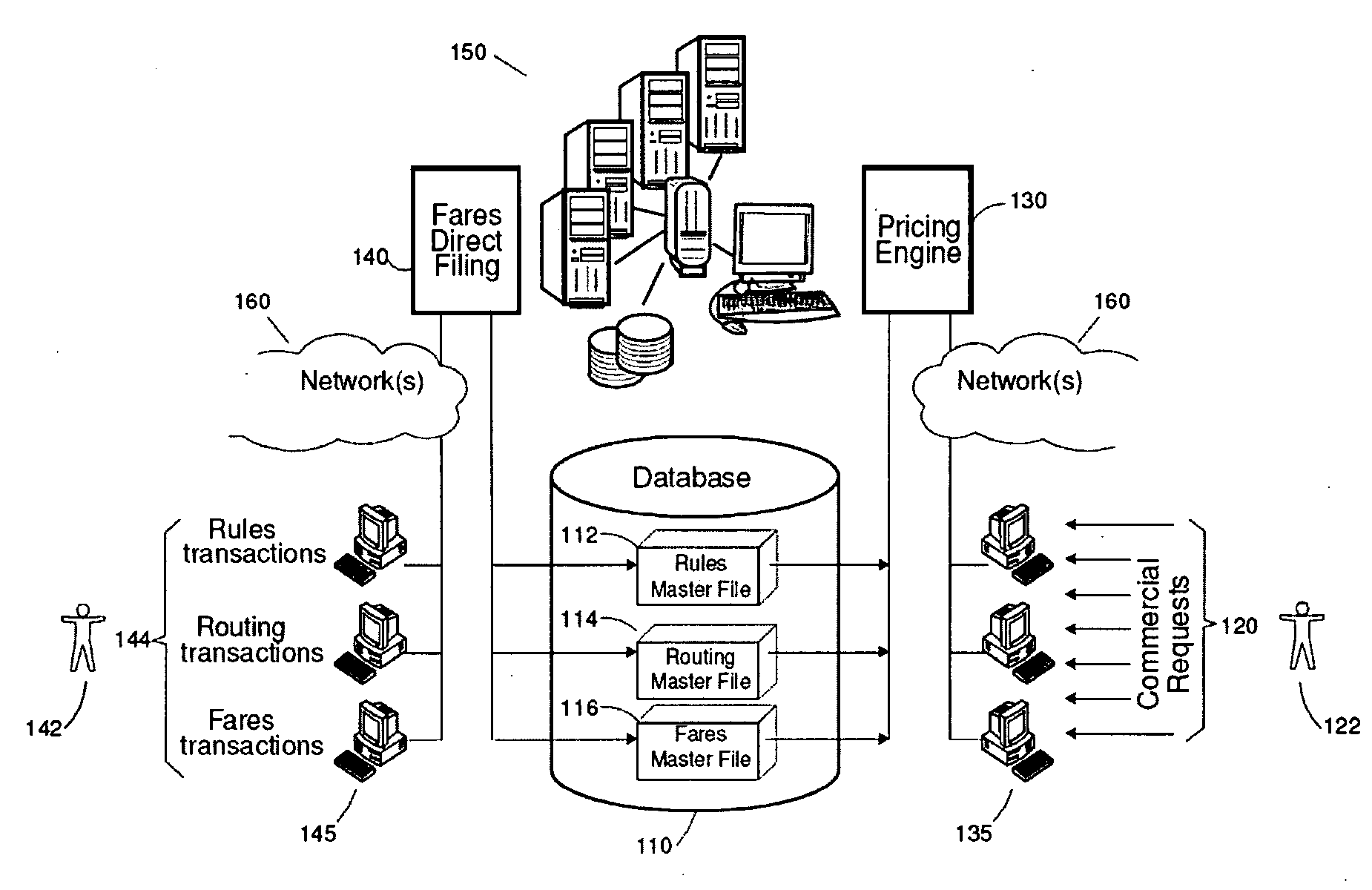
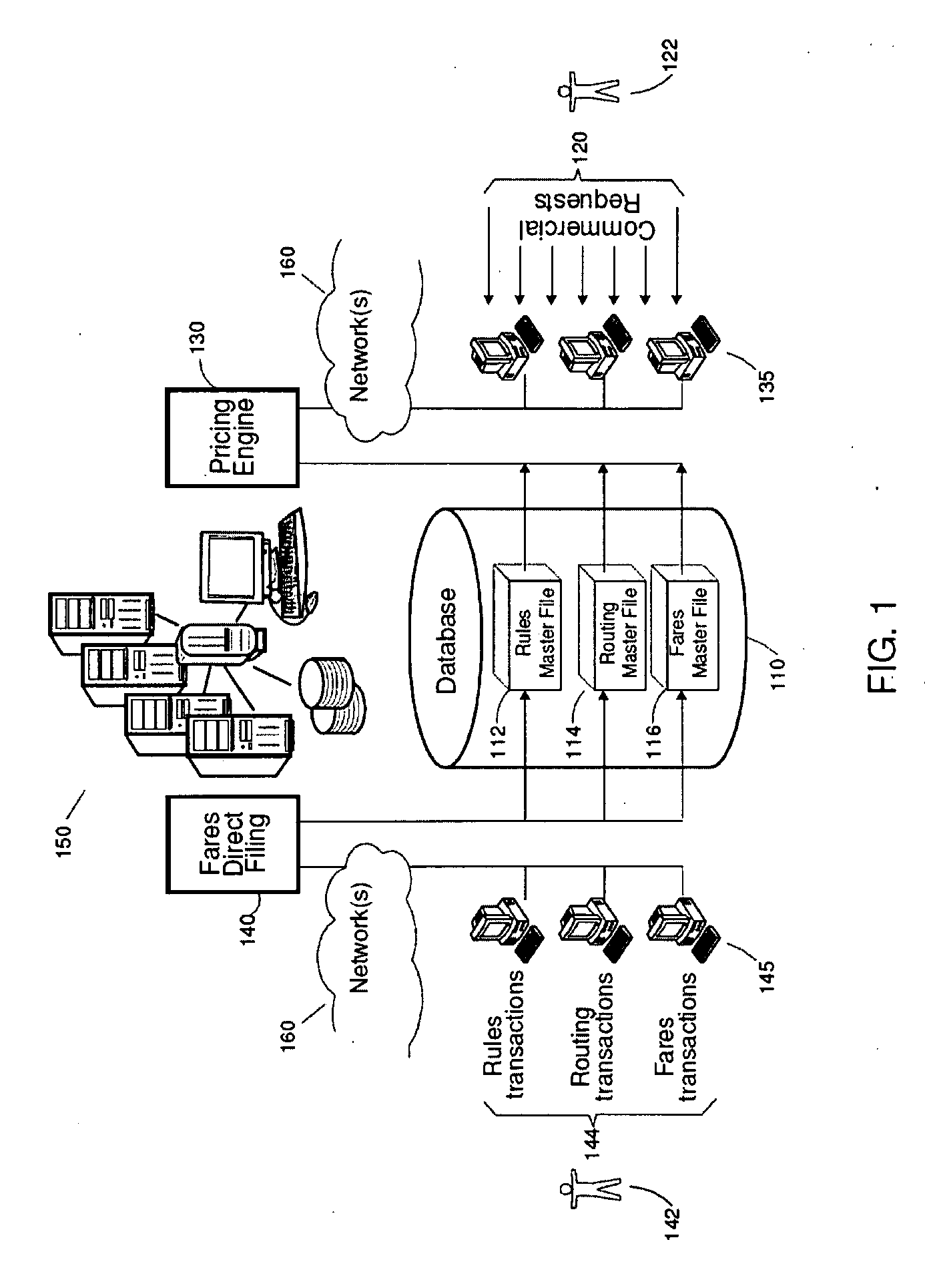
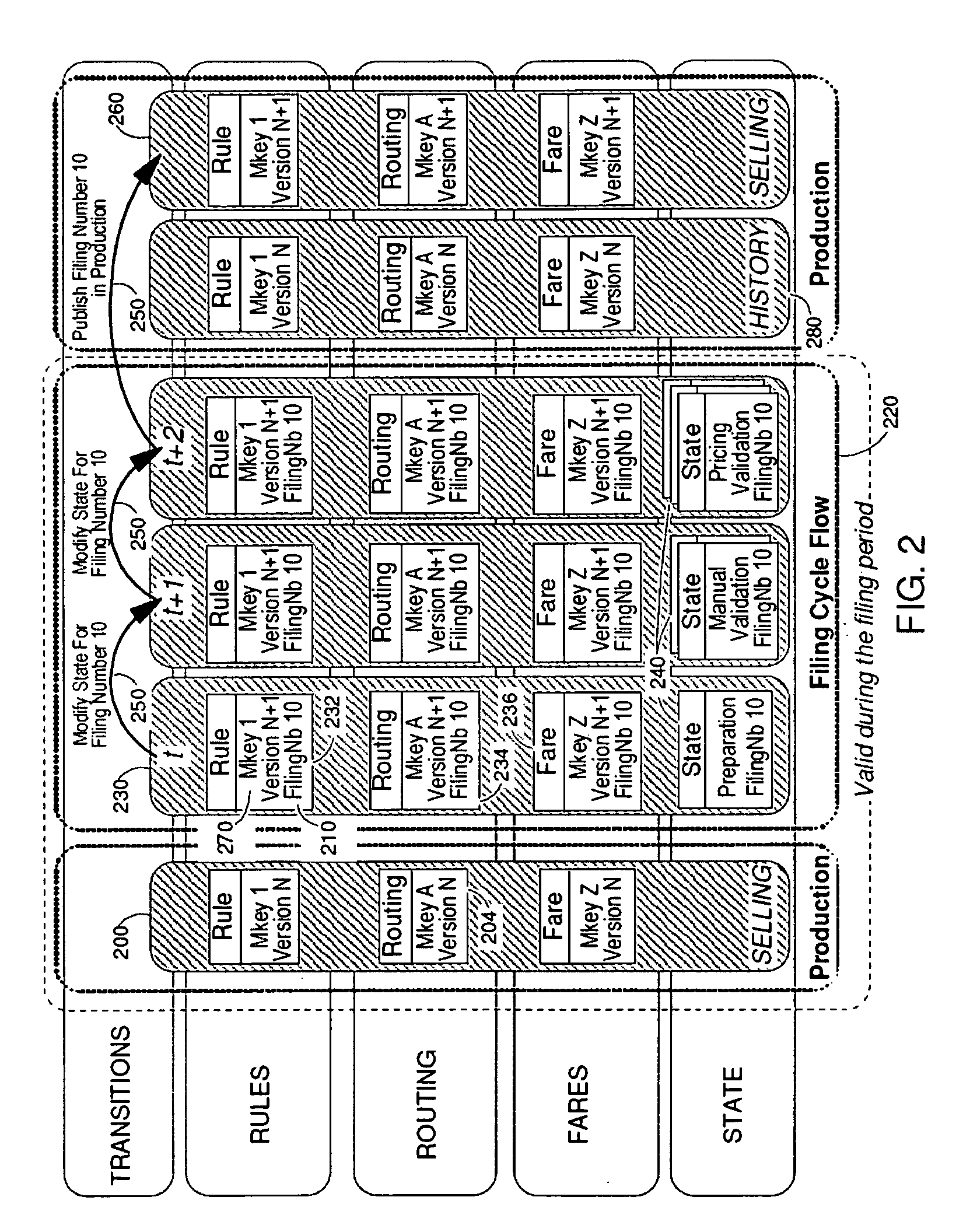
Method allowing validation in a production database of new entered data prior to their release
A method of insuring the integrity of a plurality of updates brought in real-time to a production database concurrently used by one or more software applications is described. The production database includes a plurality of products participating to the definition of objects. The method first includes requesting the issuance of a unique filing number associated to a draft state version of the plurality of updates while keeping them invisible to the end-users of the production database. Then, a set of product items identified as a whole by the unique filing number are created or copied from the production database and gathered under the form of a meta-product on which the plurality of updates is applied. After updating, the meta-product is successively set into a customizable flow of one or more validation states in order to perform a cross-validation of the plurality of updates. After validation, the meta-product is set into a production state where the uniquely identified meta-product becomes immediately visible and useable by the end-users.
Owner:AMADEUS S
Query integrity assurance in database outsourcing
InactiveUS20080183656A1Digital data processing detailsUnauthorized memory use protectionData setData memory
A method, system and computer program product for confirming the validity of data returned from a data store. A data store contains a primary data set encrypted using a first encryption and a secondary data set using a second encryption. The secondary data set is a subset of the primary data set. A client issues a substantive query against the data store to retrieve a primary data result belonging to the primary data set. A query interface issues at least one validating query against the data store. Each validating query returns a secondary data result belonging to the secondary data set. The query interface receives the secondary data result and provides a data invalid notification if data satisfying the substantive query included in an unencrypted form of the secondary data result is not contained in an unencrypted form of the primary data result.
Owner:LINKEDIN
Configuring systems for generating business transaction reports using processing relationships among entities of an organization
Business data (including transactional data) may be gathered, stored, sorted, and / or collated into financial service organization (FSO) reports used by various entities of a FSO. A processing relationship configuration program may be used to create a processing relationship structure between various entities of the FSO. Processing relationship structure information may be stored on a database of an FSO. Nodes may be created and uniquely defined to represent FSO physical entities and / or FSO functions. A nodes structure may correspond to the processing relationship structure within an FSO. In some embodiments, an FSO application program, such as a report program, may be generated based on a defined processing relationship structure. The report records may be arranged in a particular sequence by one or more of the break key fields. Changes to the processing relationship structure may be automatically reflected in the reports generated by the report program.
Owner:COMP SCI A OF NV
Genealogical investigation and documentation systems and methods
InactiveUS20050147947A1Structured data retrievalSpecial data processing applicationsDocumentation procedureData mining
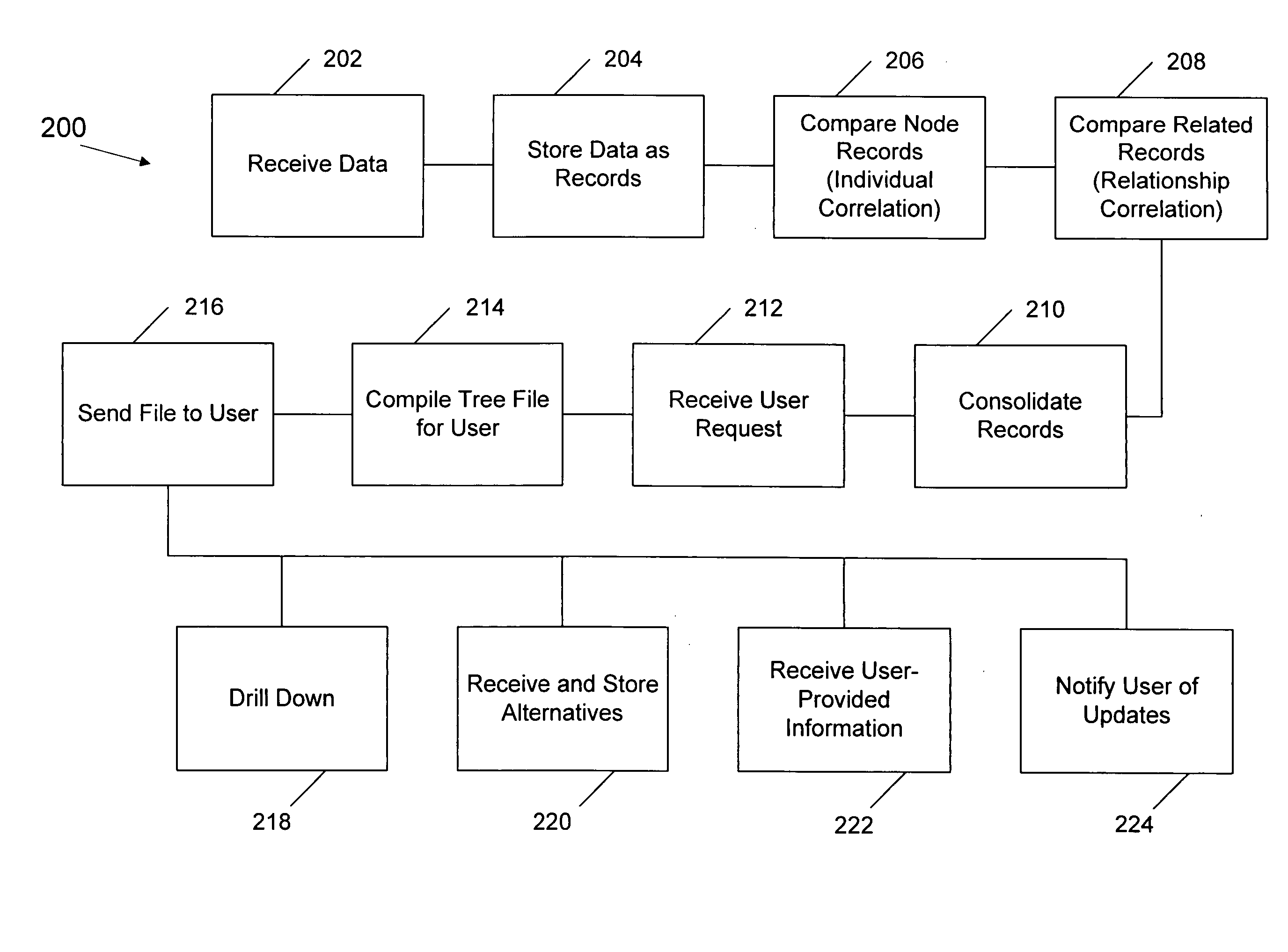
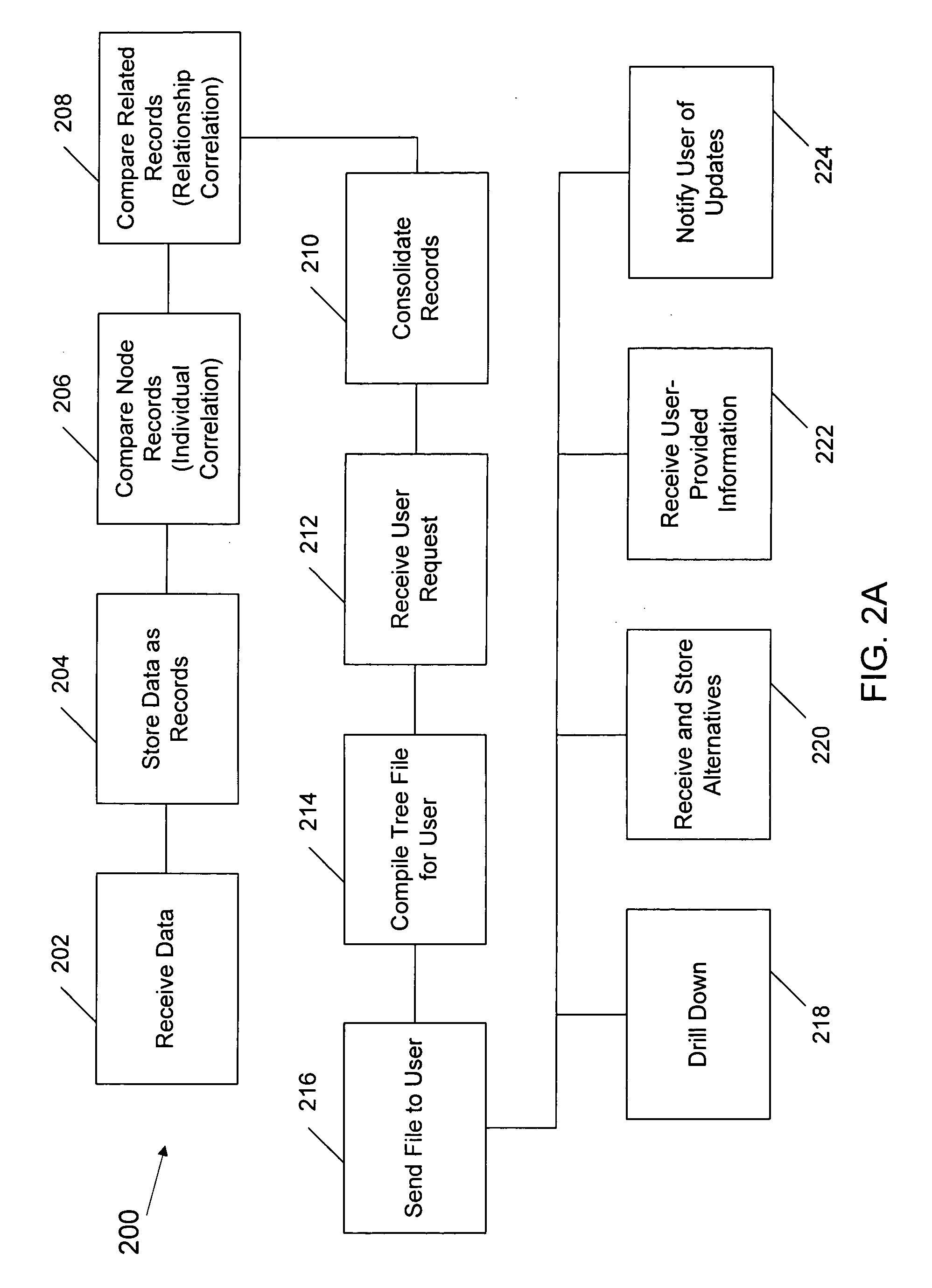
A method of creating a family tree includes receiving genealogy data at a host computing system from at least one primary source and creating one or more node records and one or more link records using the genealogy data. The individual node records include at least name data and each individual link record includes relationship data that represents a relationship between individual node records. The method also includes comparing individual node records and identifying pairs of records having similar data. For each identified pair of individual node records, the method includes comparing related individual node records and deciding based on predetermined criteria whether the identified pair of individual node records represent the same person. The method also includes consolidating the information from a plurality of records determined to represent the same person into a single person record. The method also includes receiving a request at the host computing system from a user computer to display a family tree and using the individual link records, the individual node records, and the single person records to create a data representation comprising the requested family tree. The method also includes sending the data representation to the user computer.
Owner:ANCESTRY COM OPERATIONS
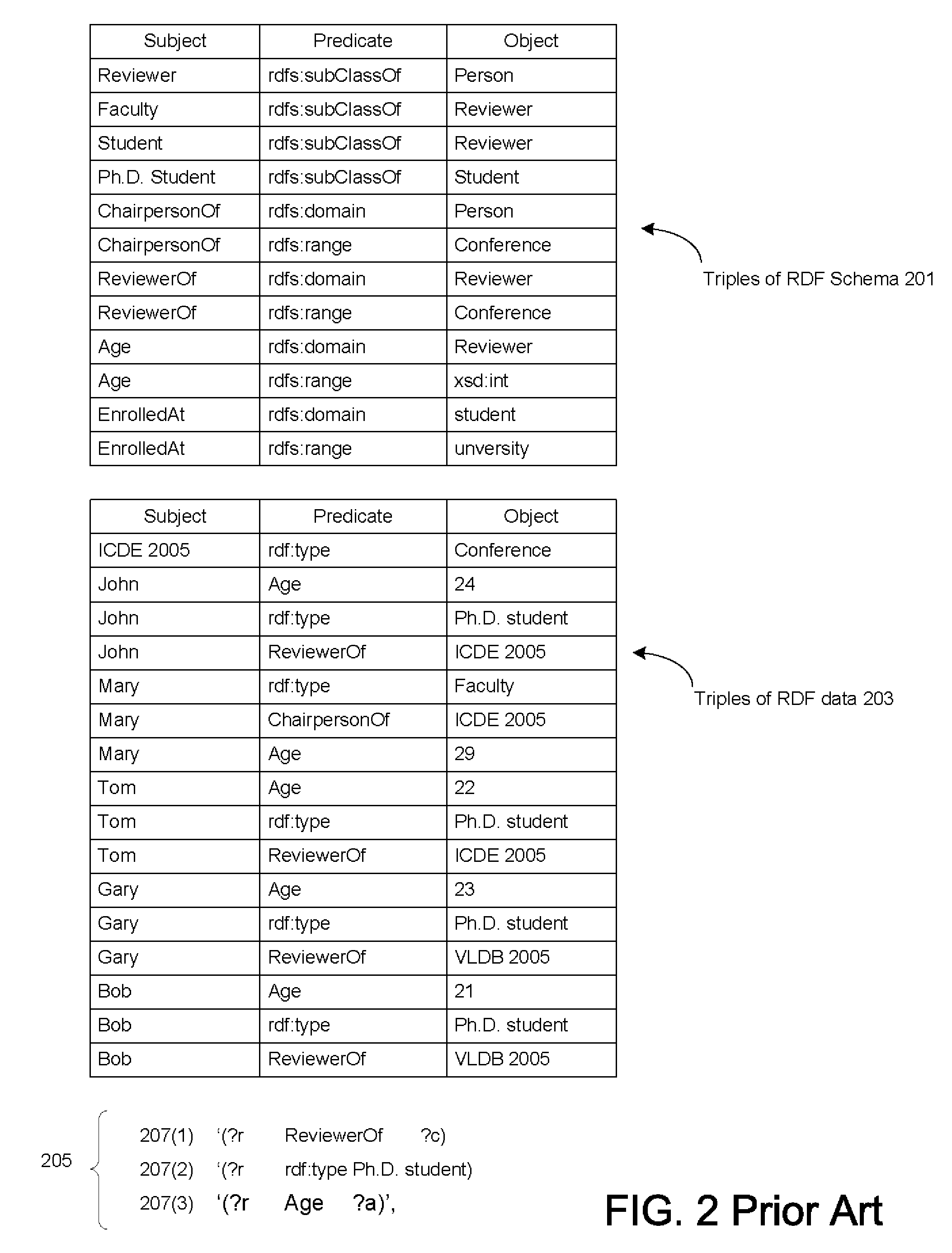
Database-based inference engine for RDFS/OWL constructs
ActiveUS20100036788A1Improve efficiencyAvoid overheadDigital data processing detailsKnowledge representationIncremental maintenanceRelational database
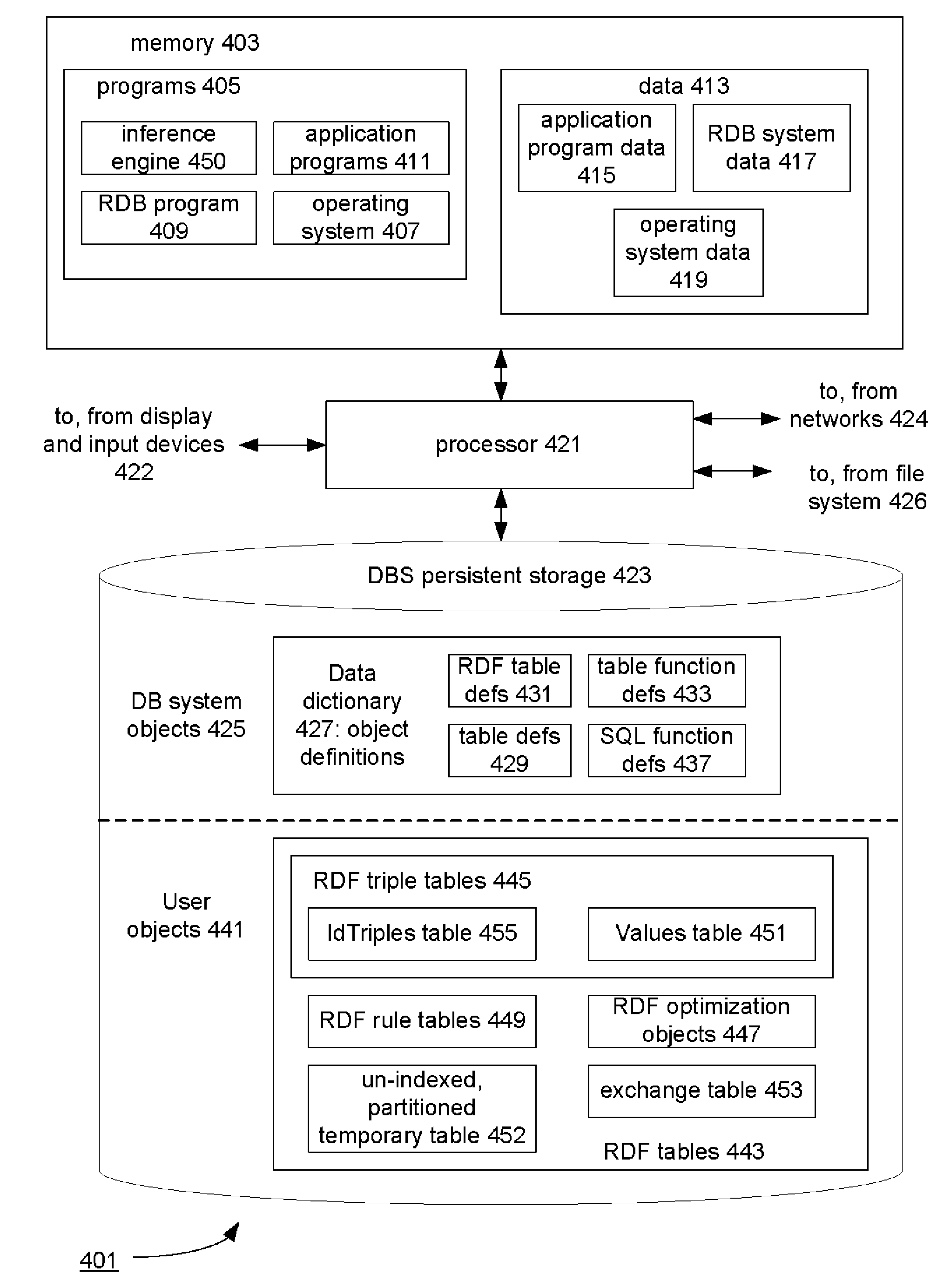
An un-indexed, partitioned temporary table and an exchange table are used in the inferencing of semantic data in a relational database system. The exchange table has the same structure as a semantic data table storing the semantic data. In the inferencing process, a new partition is created in the semantic data table. Inference rules are executed on the semantic data table, and any newly inferred semantic data generated is added to the temporary table. Once no new data is generated, the inferred semantic data is copied from the temporary table into the exchange table. Indexes that are the same as indexes for the semantic data table are built for the exchange table. The indexed data in the exchange table is then exchanged into the new partition in the semantic data table. By use of the un-indexed, partitioned temporary table, incremental maintenance of indexes is avoided, thus allowing for greater efficiency.
Owner:ORACLE INT CORP
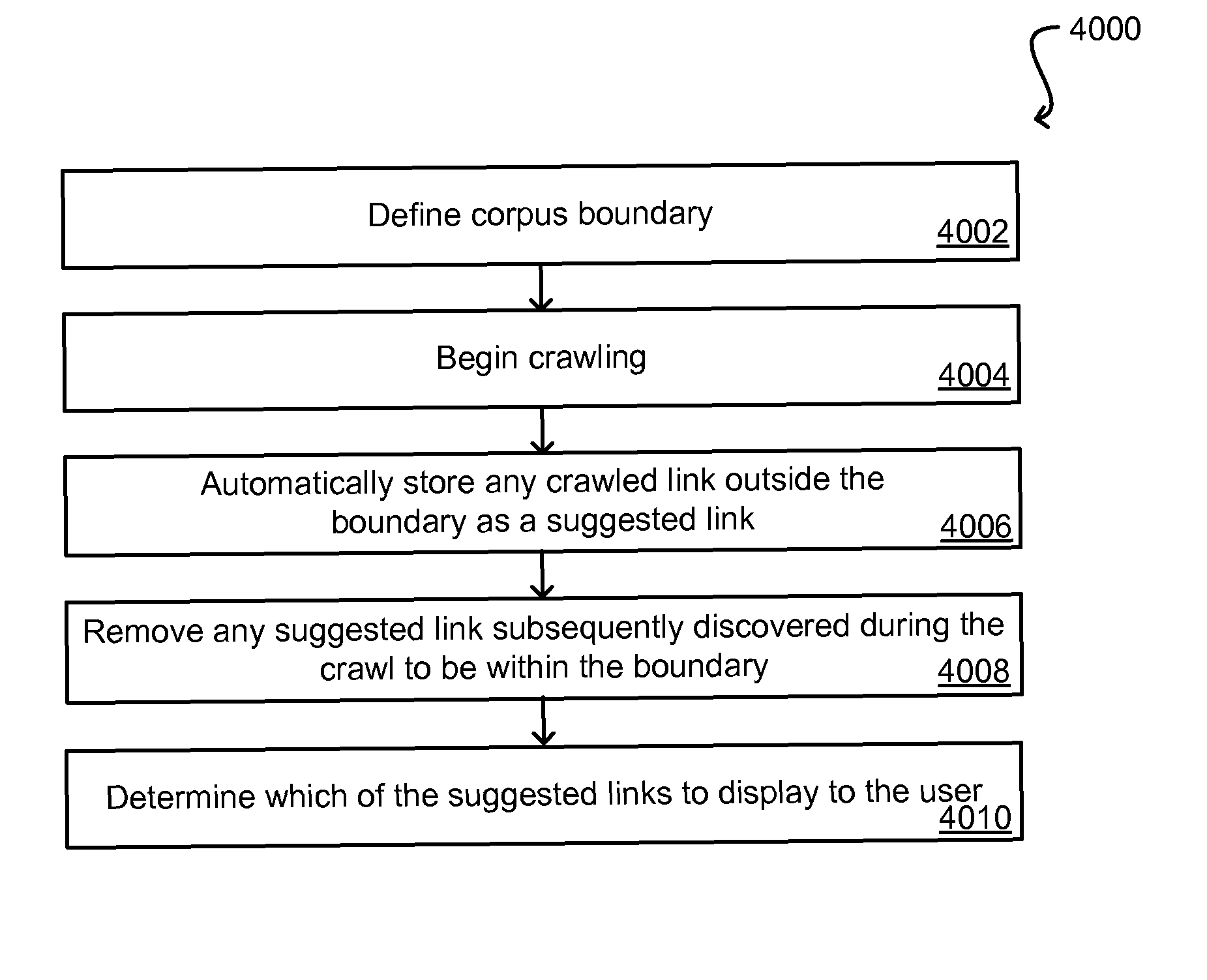
Auto generation of suggested links in a search system
ActiveUS8005816B2Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Dynamic chunking for media streaming
ActiveUS20120005312A1Increase flexibilityMultimedia data indexingMultiple digital computer combinationsComputer networkComputer science
Owner:BRIGHTCOVE
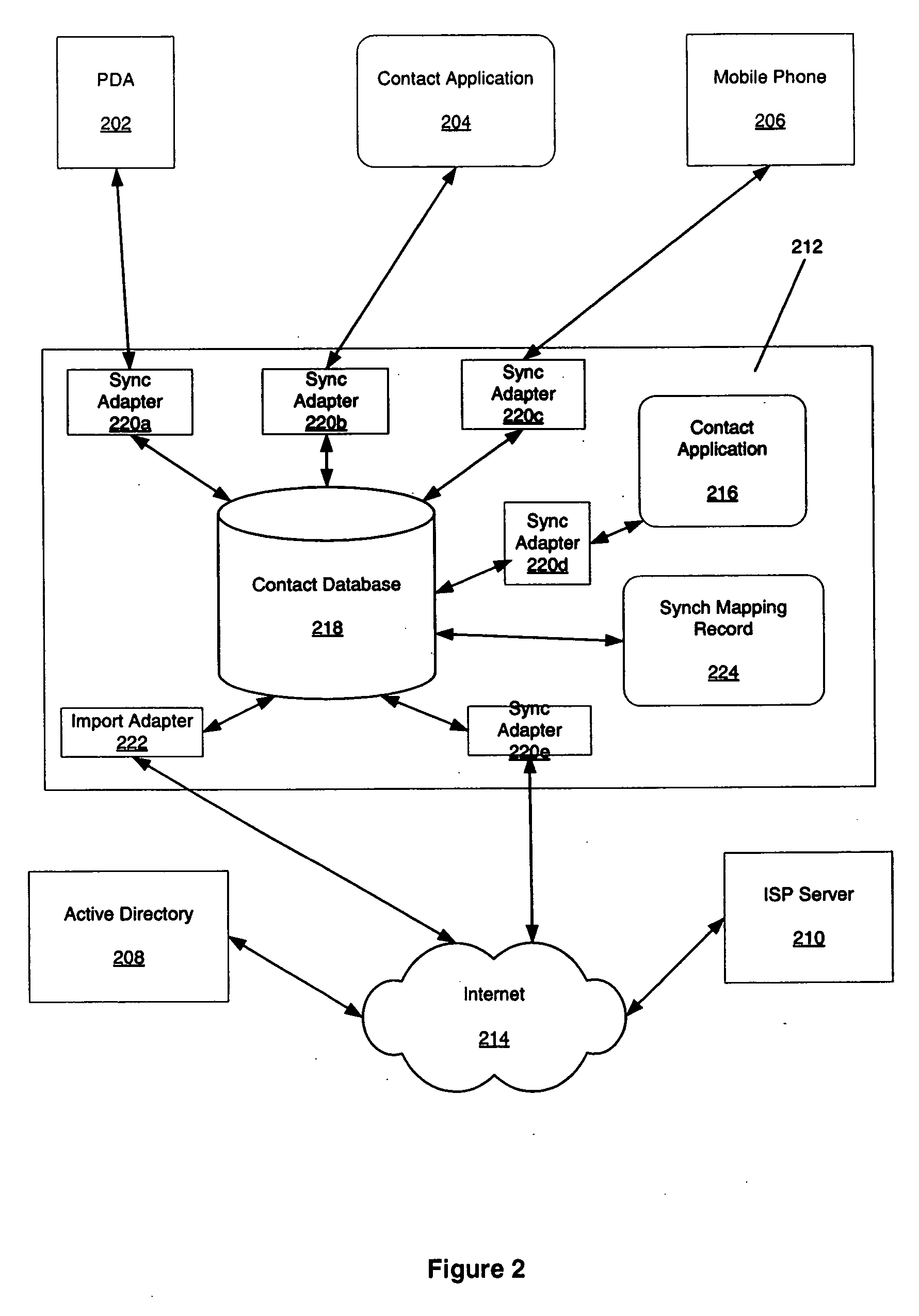
Method and apparatus for providing desktop application functionality in a client/server architecture
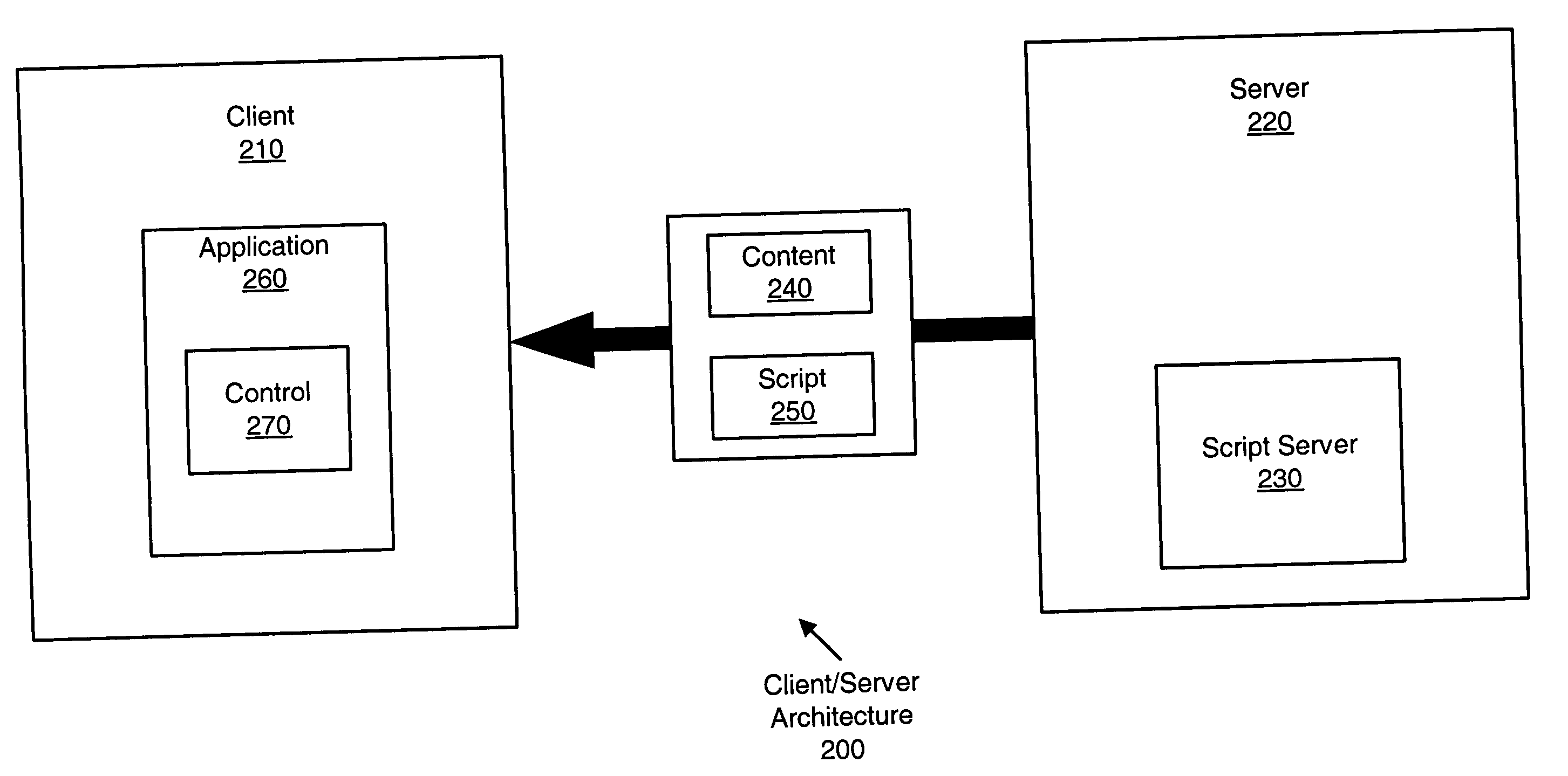
InactiveUS20050050547A1Quick and efficient and extensible accessAdversely impacting network resourceMultiprogramming arrangementsStructured data retrievalApplication softwareClient-side
A method and apparatus for synchronizing a client-side information store with a server-side database in a client / server architecture are disclosed. The method includes receiving data and receiving a script. The script defines a function of a control, and the function allows the control to perform an operation using the data.
Owner:R2 SOLUTIONS
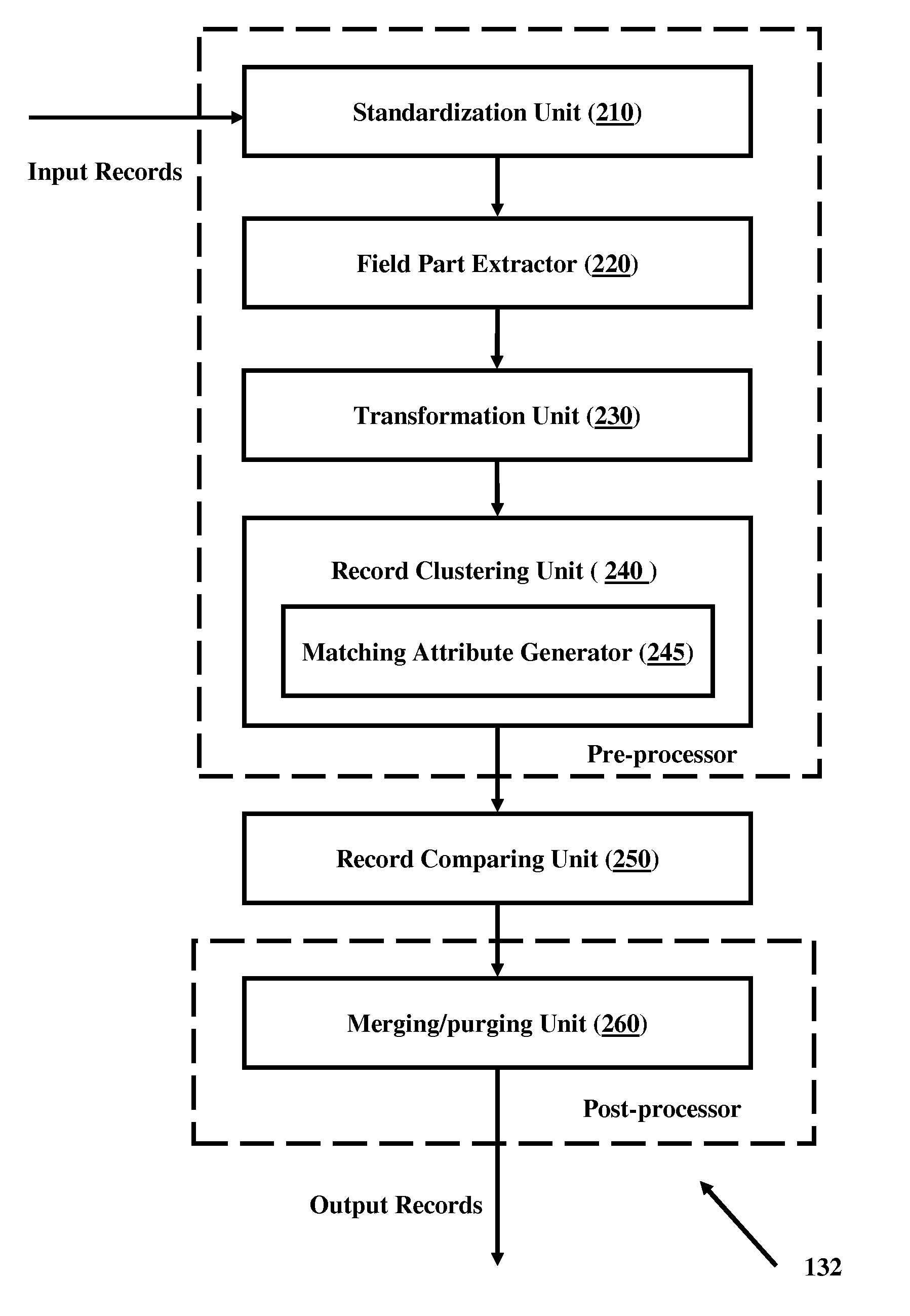
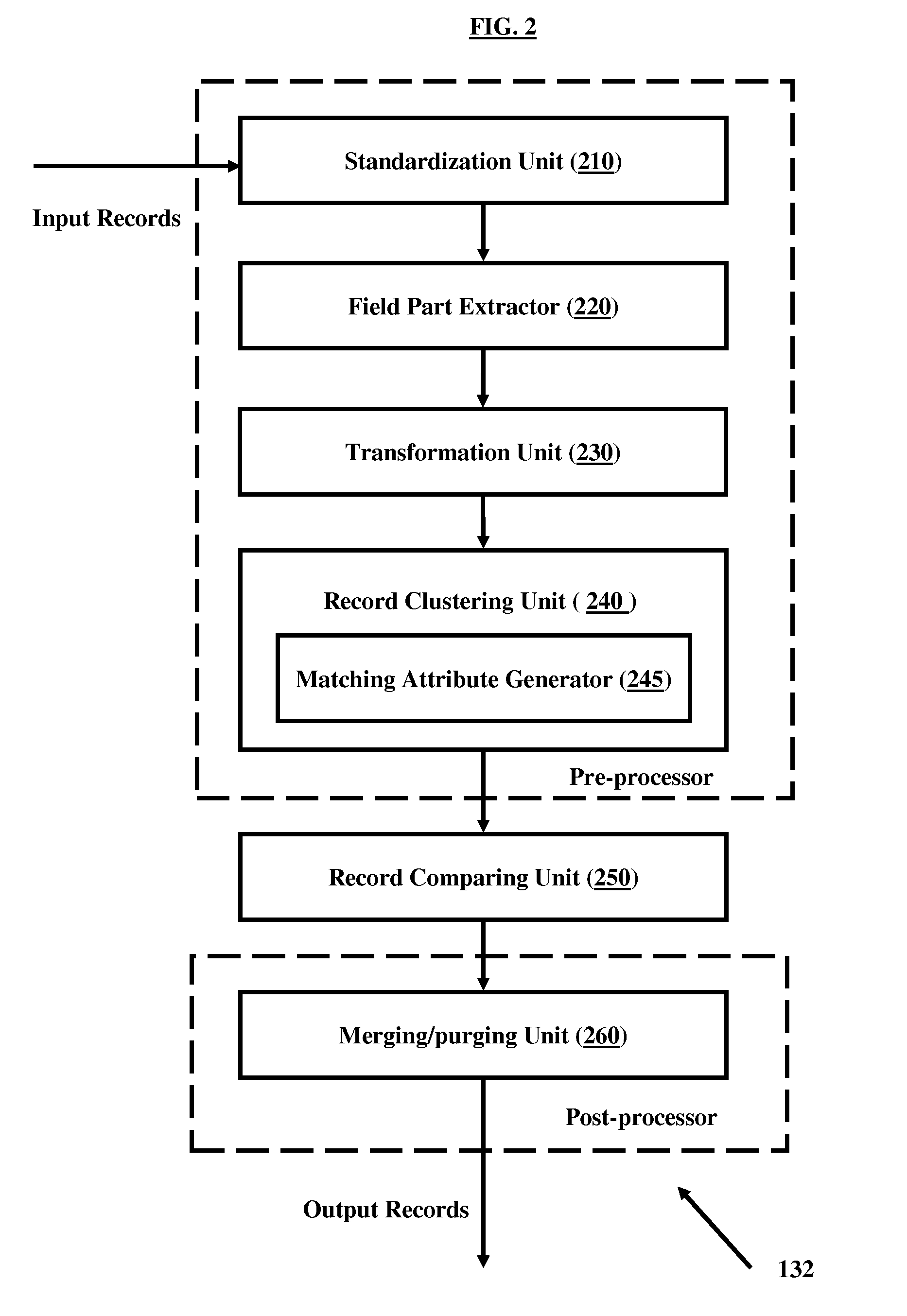
Detecting duplicate records
ActiveUS20100005048A1Digital data processing detailsKnowledge representationData miningComputer science
A method for finding duplicates by matching group of fields in records is disclosed. The method comprises standardizing data using field specific knowledge base; extracting at least part of one or more related fields of records; applying a matching attribute function to generate keys on the “comparable” field part extracted data; generating record level keys using generated field level keys; clustering the records based on generated record level keys; identifying reference record for each cluster identified; and calculating matching percentage for each record in a cluster with respect to reference record of the cluster. Devices and systems are disclosed that enable the method for finding duplicates.
Owner:EGRABBER
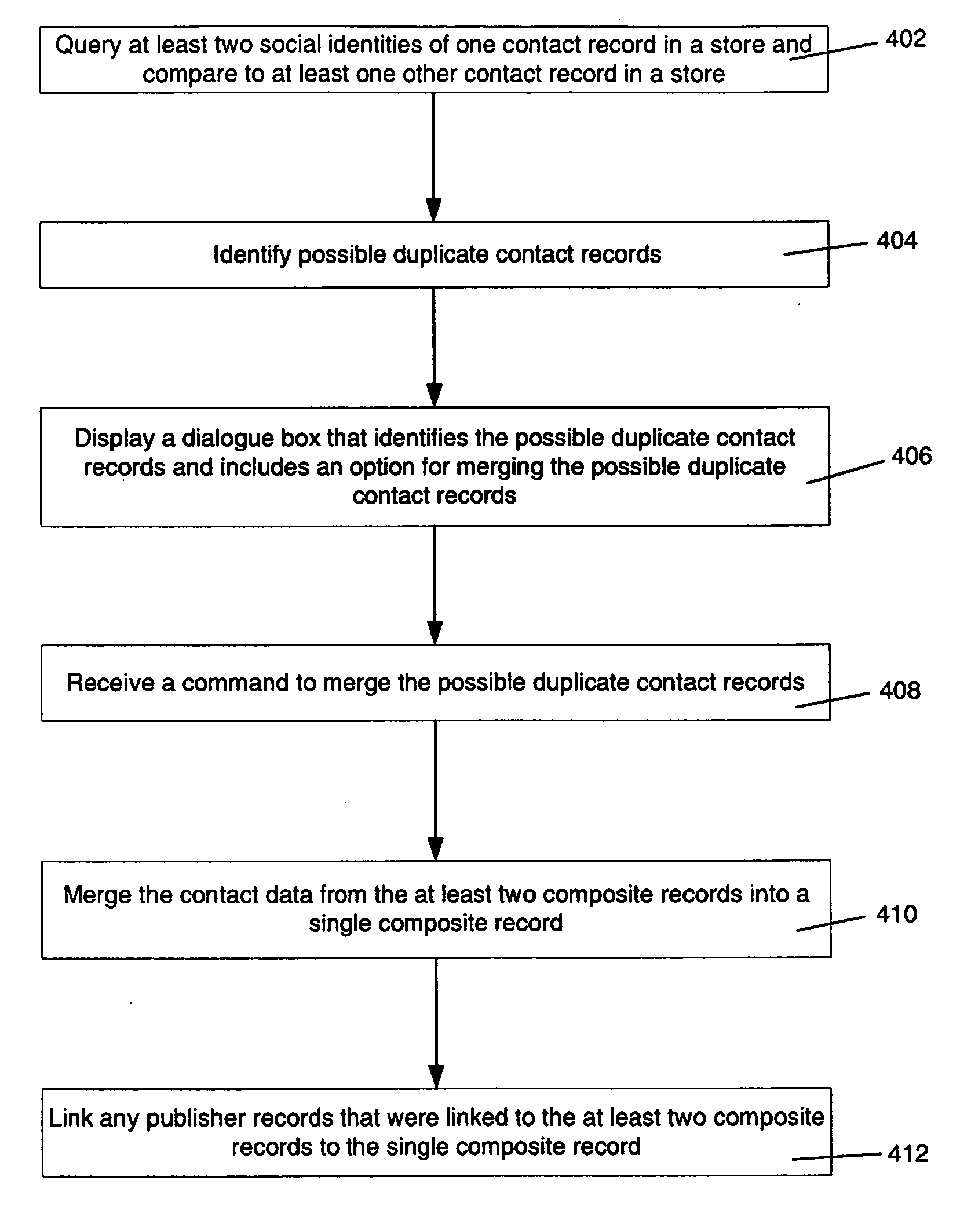
Contact merge auto-suggest
InactiveUS20060184584A1Structured data retrievalSpecial data processing applicationsDigital identityData science
Aspects of the present invention identify duplicate entries across multiple sources of information, such as databases. Further aspects of the invention relate to auto-suggesting entries as duplicates. Embodiments of the invention relate to an algorithm constructed to match or discard duplicates based upon information relating to at least two social identities in one store. Further embodiments of the invention relate to an algorithm constructed to match or discard duplicate entries based upon a legal and / or digital identity. This can be in conjunction with information relating to social identity.
Owner:MICROSOFT TECH LICENSING LLC
Efficient algorithm and protocol for remote differential compression on a local device
InactiveUS20050262167A1Structured data retrievalSpecial data processing applicationsHorizonTheoretical computer science
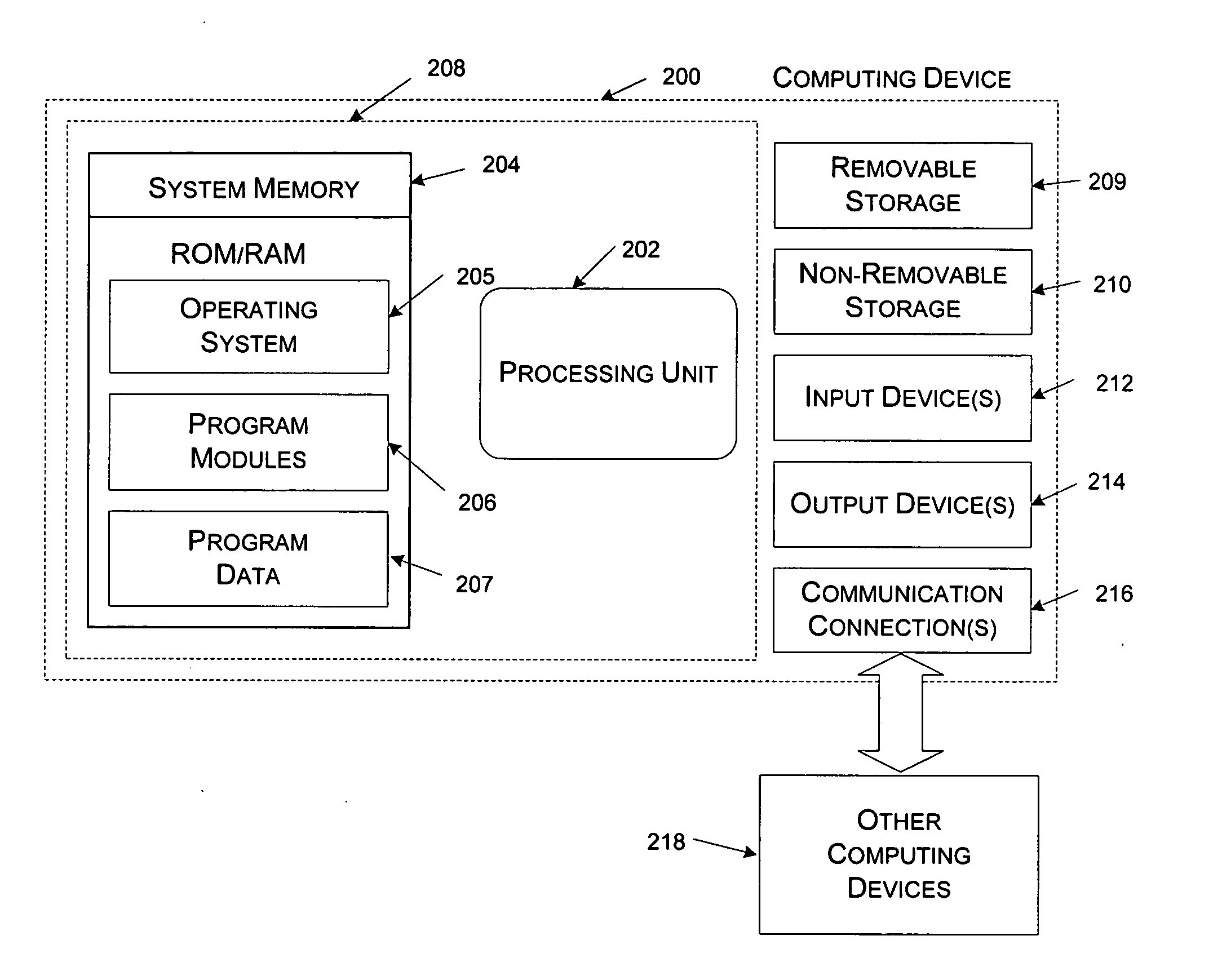
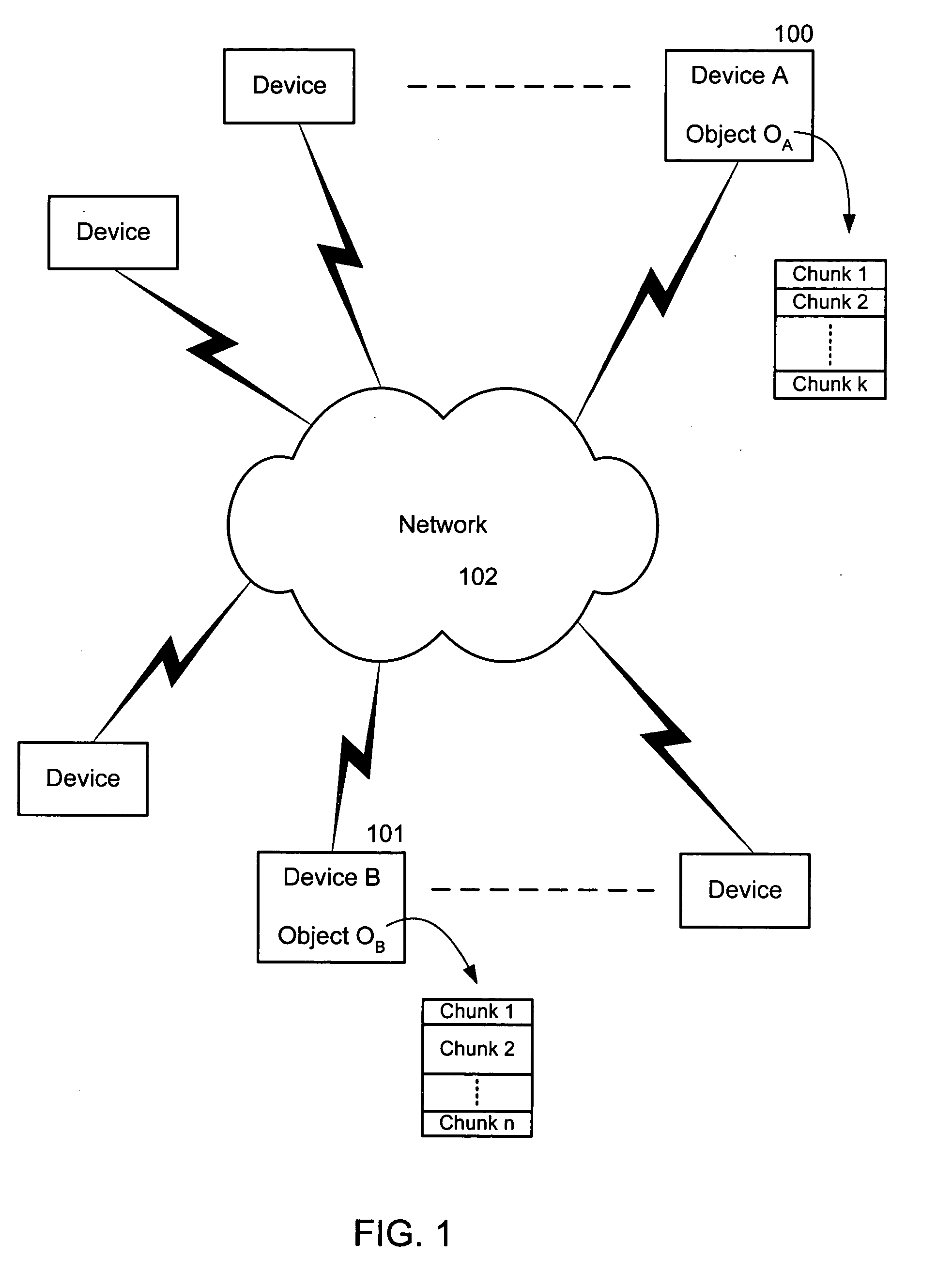
The present invention is used to update objects over limited bandwidth networks. Objects are updated between two or more computing devices using remote differential compression (RDC) techniques such that required data transfers are minimized. In one aspect, efficient large object transfers are achieved by recursively applying the RDC algorithm to its own metadata; a single or multiple recursion step(s) may be used in this case to reduce the amount of metadata sent over the network by the RDC algorithm. Objects and / or signature and chunk length lists can be chunked by locating boundaries at dynamically determined locations. A mathematical function evaluates hash values associated within a horizon window relative to potential chunk boundary.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
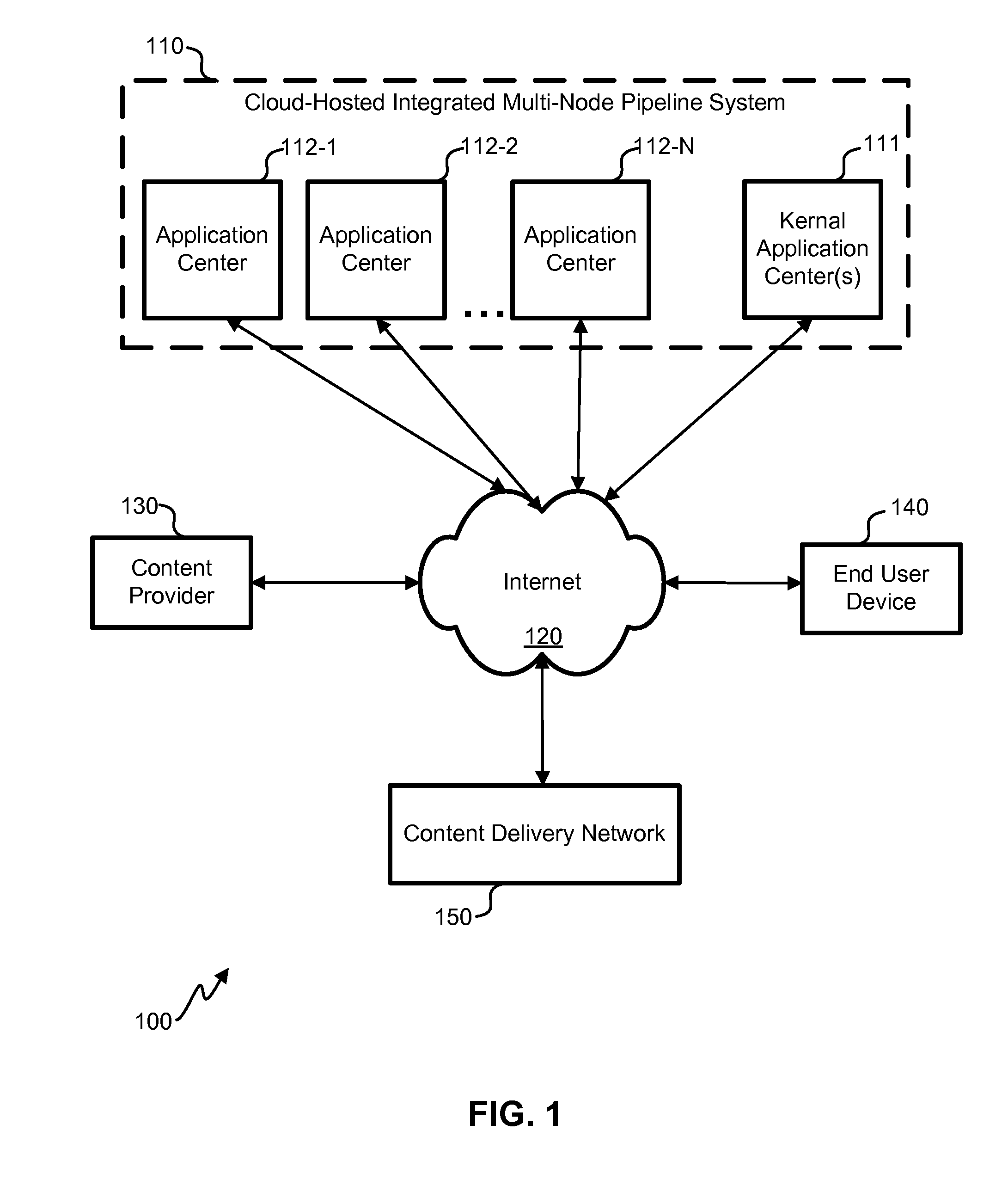
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com