Soft certification anti-false method based on graphic code primary and secondary signet series information association mechanism
An information association and graphic code technology, applied in the field of electronic information, can solve problems such as threats to the credit system and integrity and security, inconvenience in implementation and verification, and large dependence on the timeliness of multi-party collaborative work. The effect of choosing a device provider
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
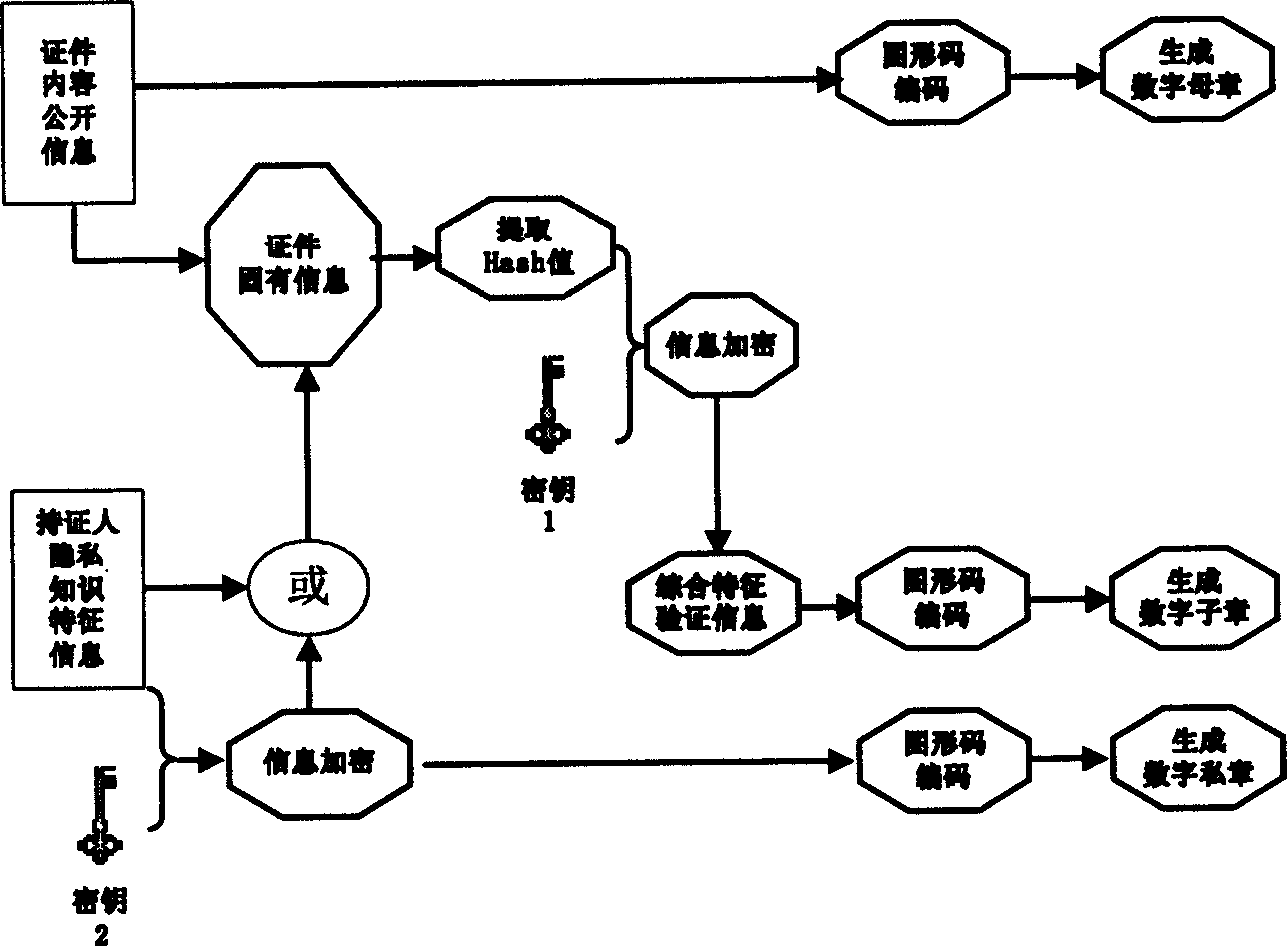
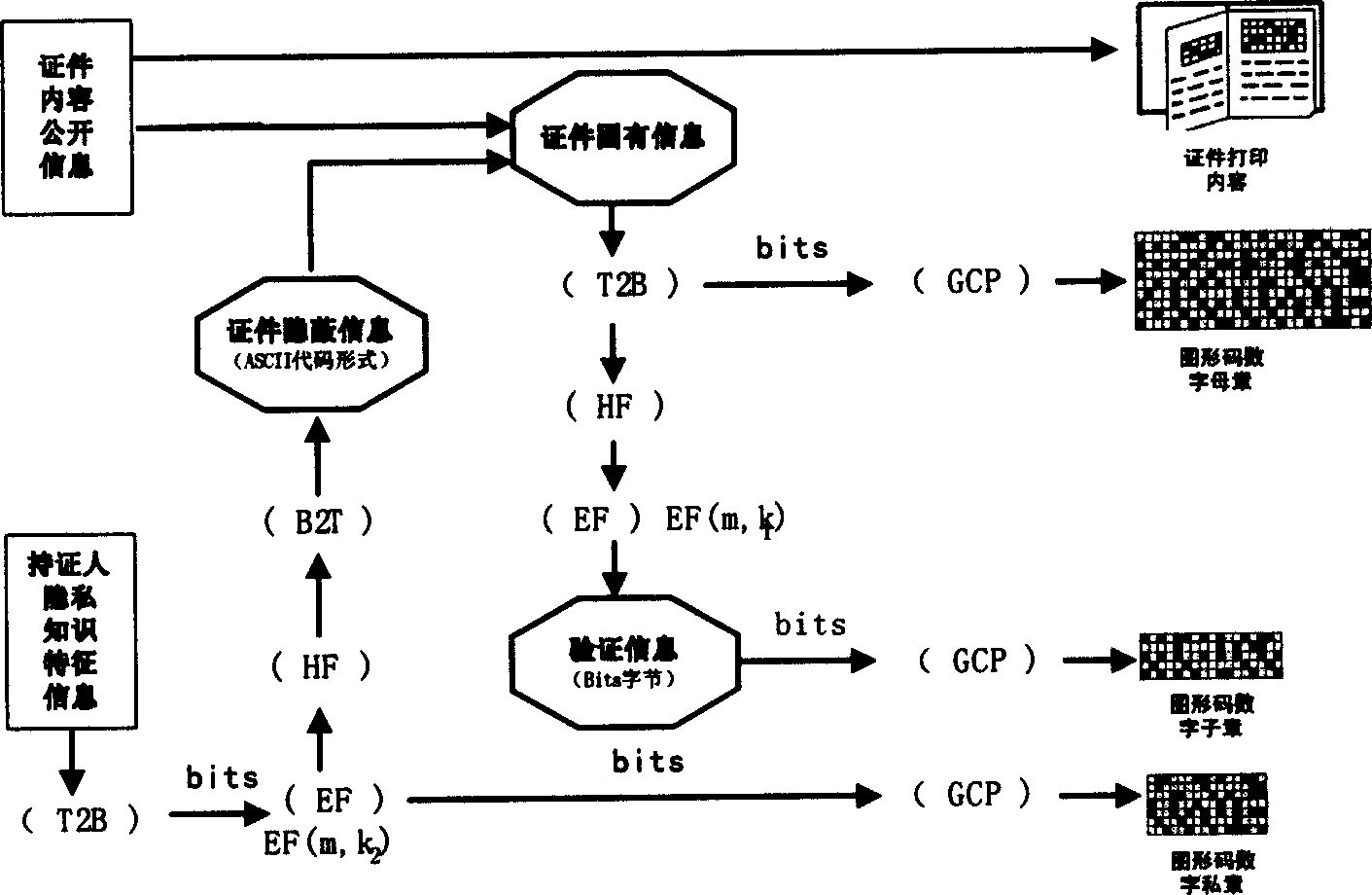
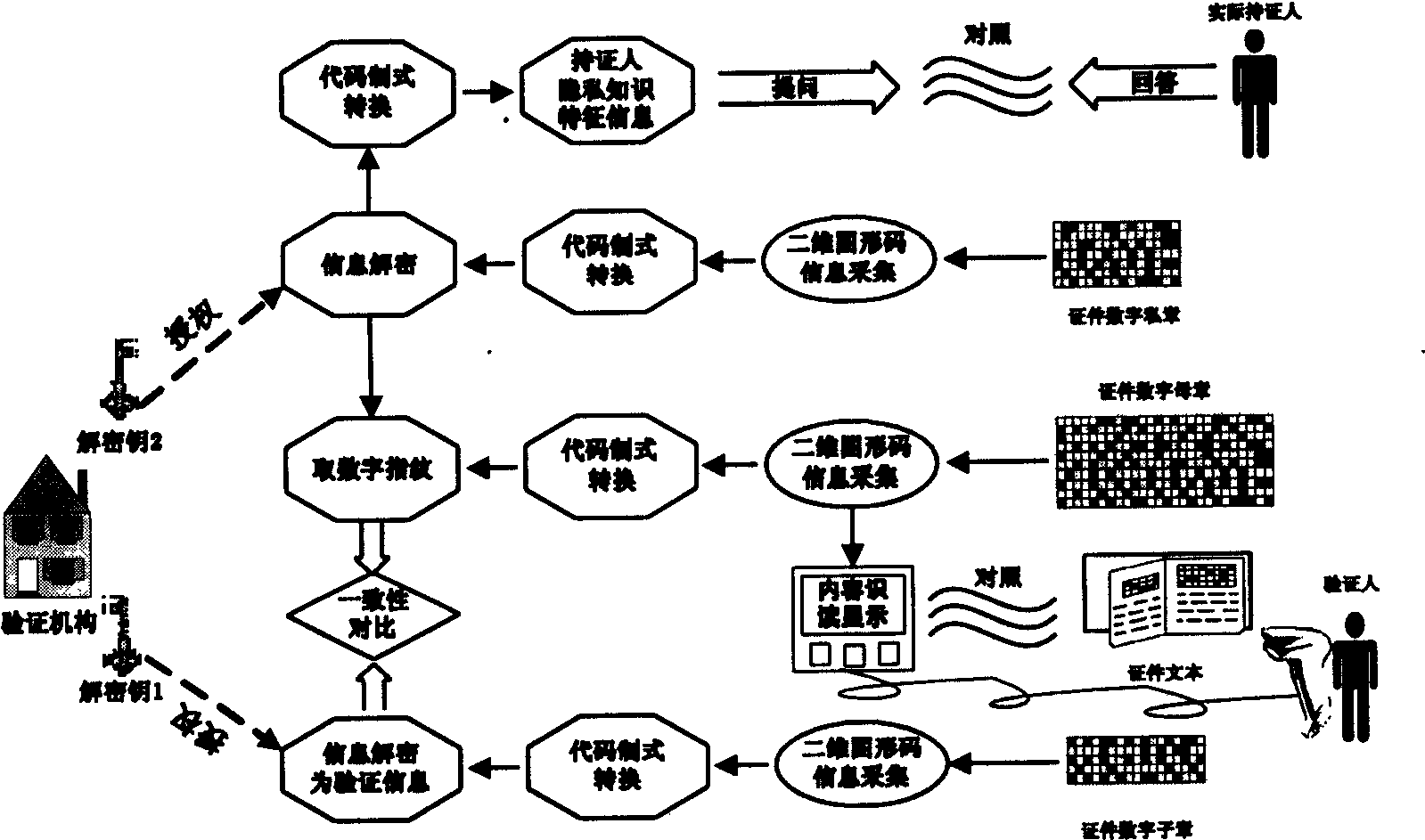
[0117] In this anti-counterfeiting system, the technical equipment and method standards for certification and verification are disclosed (for engineering implementation and popularization and application), and the equipment used can also be publicly purchased from merchants (helping to reduce costs and improve cost performance). The owner authorizes the certificate maker to secretly use the encryption key set, so the encryption key is also called the certificate production key. At the same time, the owner authorizes the verifier to use the decryption key set, so the decryption key is also called the verification key. In principle, neither the certificate maker nor the verifier can master the two keys of certificate making and verification at the same time, so as to prevent the technical approach of "self-stealing". There are two implementations for granting a verifier a decryption key: Main scheme: The owner sends the decryption key K of the digital subchapter v1 , the decr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com