Patents
Literature
457 results about "Data dependent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data Dependent Acquisition (DDA) is the standard method for running LC-MS/MS experiments. Here, we present a quick overview of the DDA method, as well as of the less common Data Independent methods (DIA). In LC-MS/MS, purified peptides are separated on an online chromatography gradient (usually low pH Reverse Phase)...
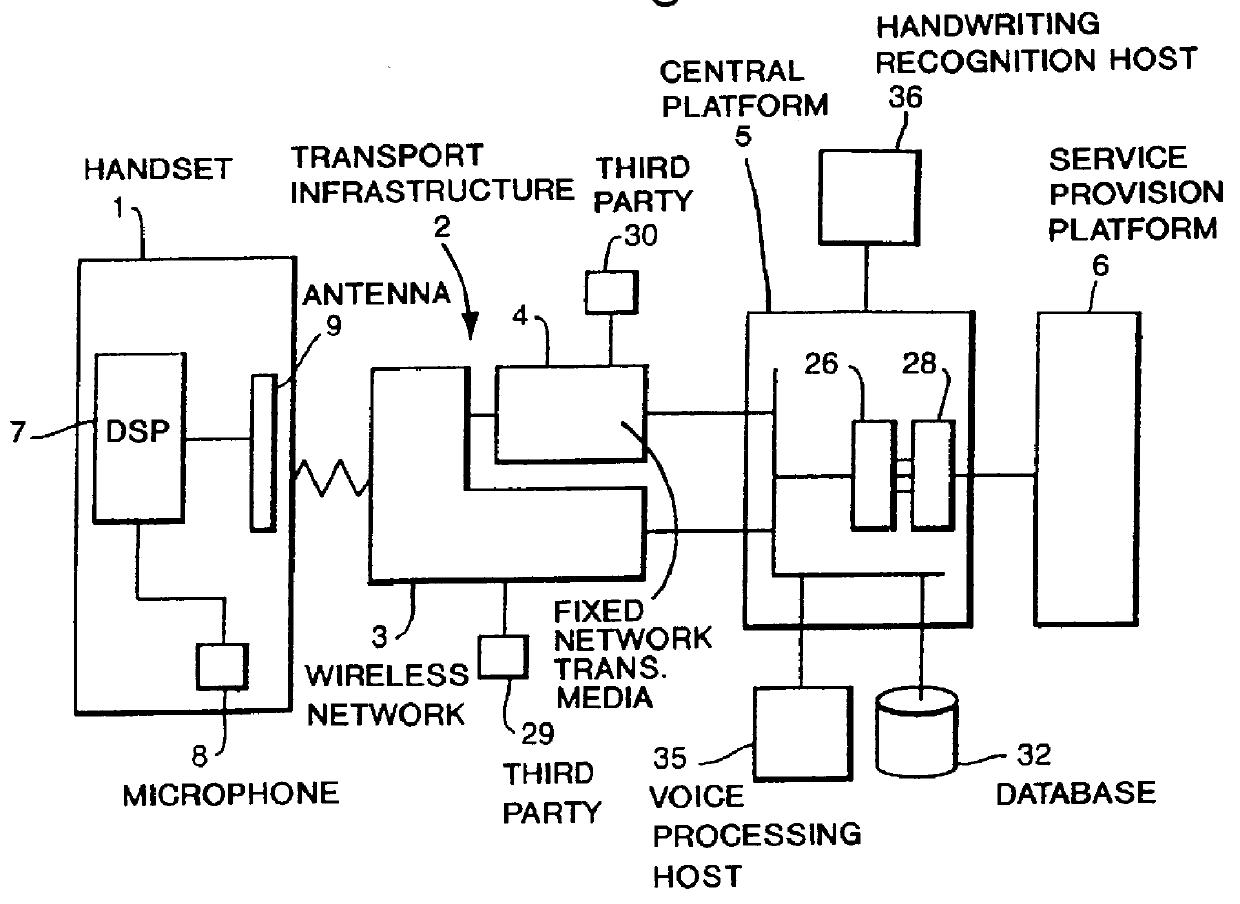
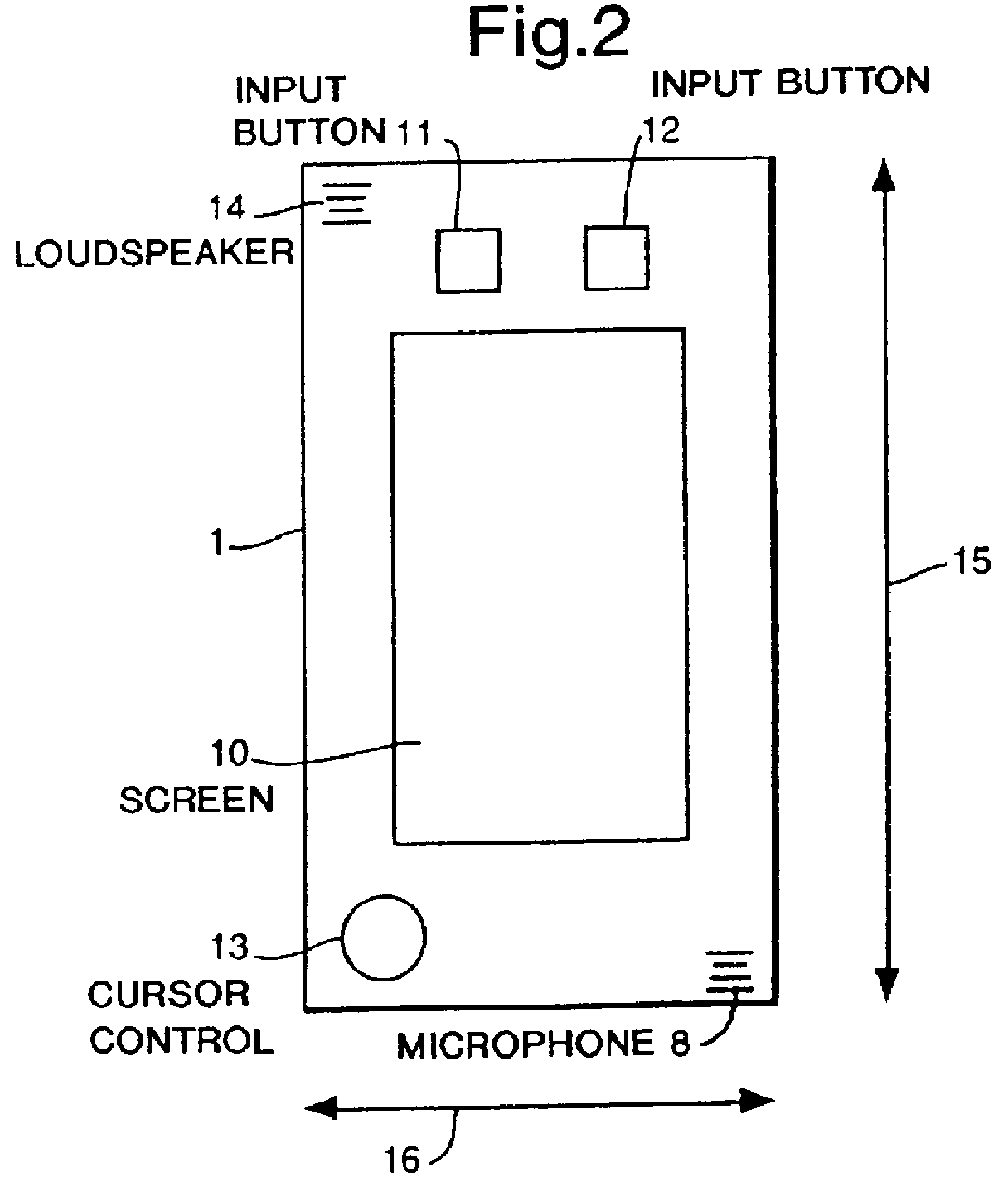
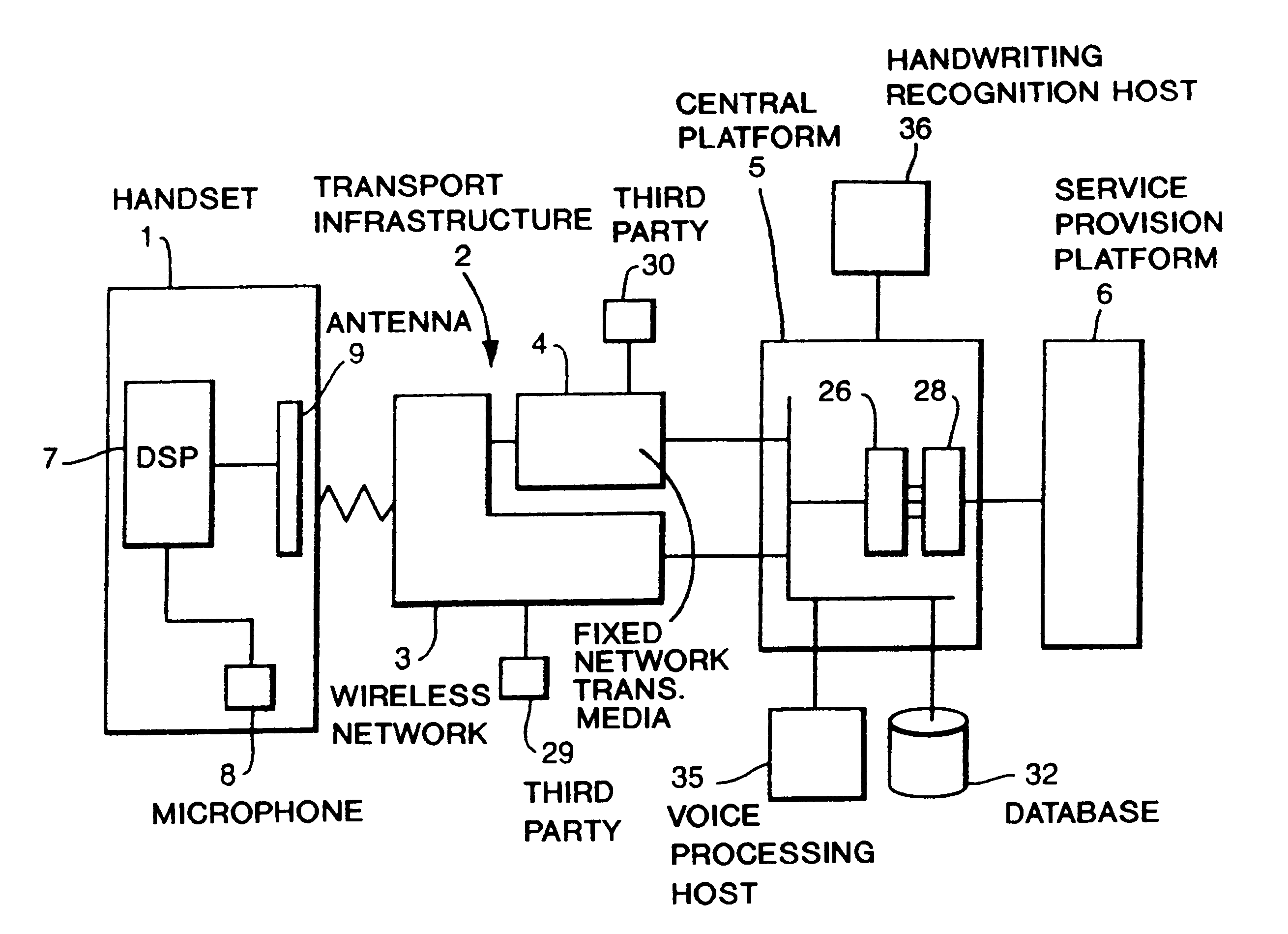
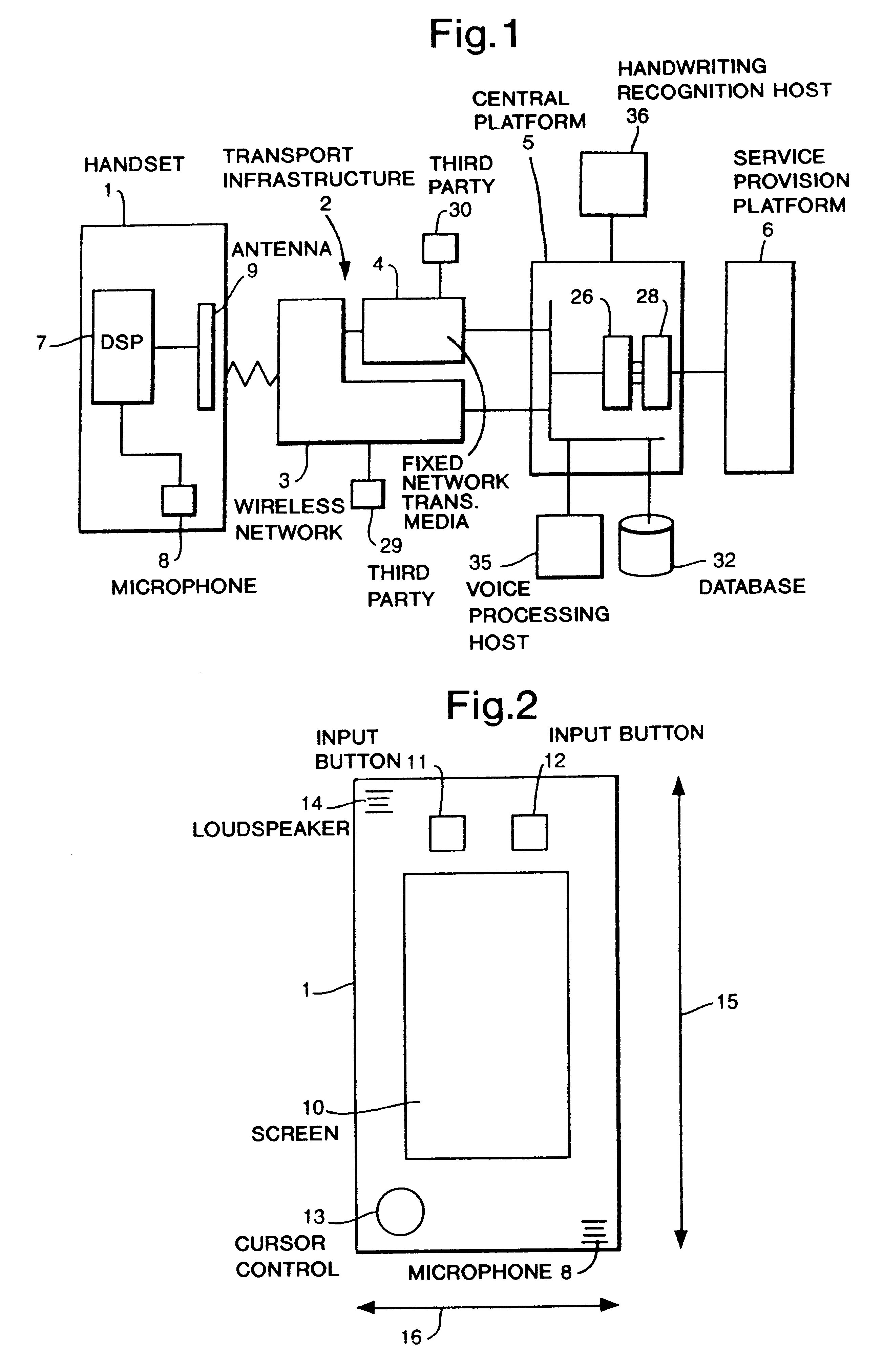
Communication system with handset for distributed processing
InactiveUS6125284ACordless telephonesSpecial service for subscribersThird partyCommunications system
A communication system comprising at least one mobile handheld telephone handset adapted to communicate via a wireless telephony medium with a telephone network handling system. The handset comprises input devices to receive input from a user and produce signals dependent thereupon, an onboard processor to adapt speech input to produce a voice transmission signal as part of a telephone conversation with a third party; and an antenna to transmit the voice transmission signal via the wireless telephony medium. The telephone network handling system comprises a receiver to receive the voice transmission signal, and means to forward the voice signal to a third party. The handset further comprises a first processor to carry out a first processing step on selected input signals and produce data dependent thereupon which preserves predetermined information necessary to carry out a remote second processing step, an onboard processor to adapt the data according to a conventional wireless telephony protocol to produce a transmission signal, and an antenna to transmit the transmission signal via the wireless telephony medium to the telephone network handling system. The system further comprises a remote processor adapted to receive and adapt the transmission signal from the telephone network handling system to regenerate the data, and to carry out a second processing step on the data and produce an output dependent thereupon.
Owner:CABLE & WIRELESS PLC
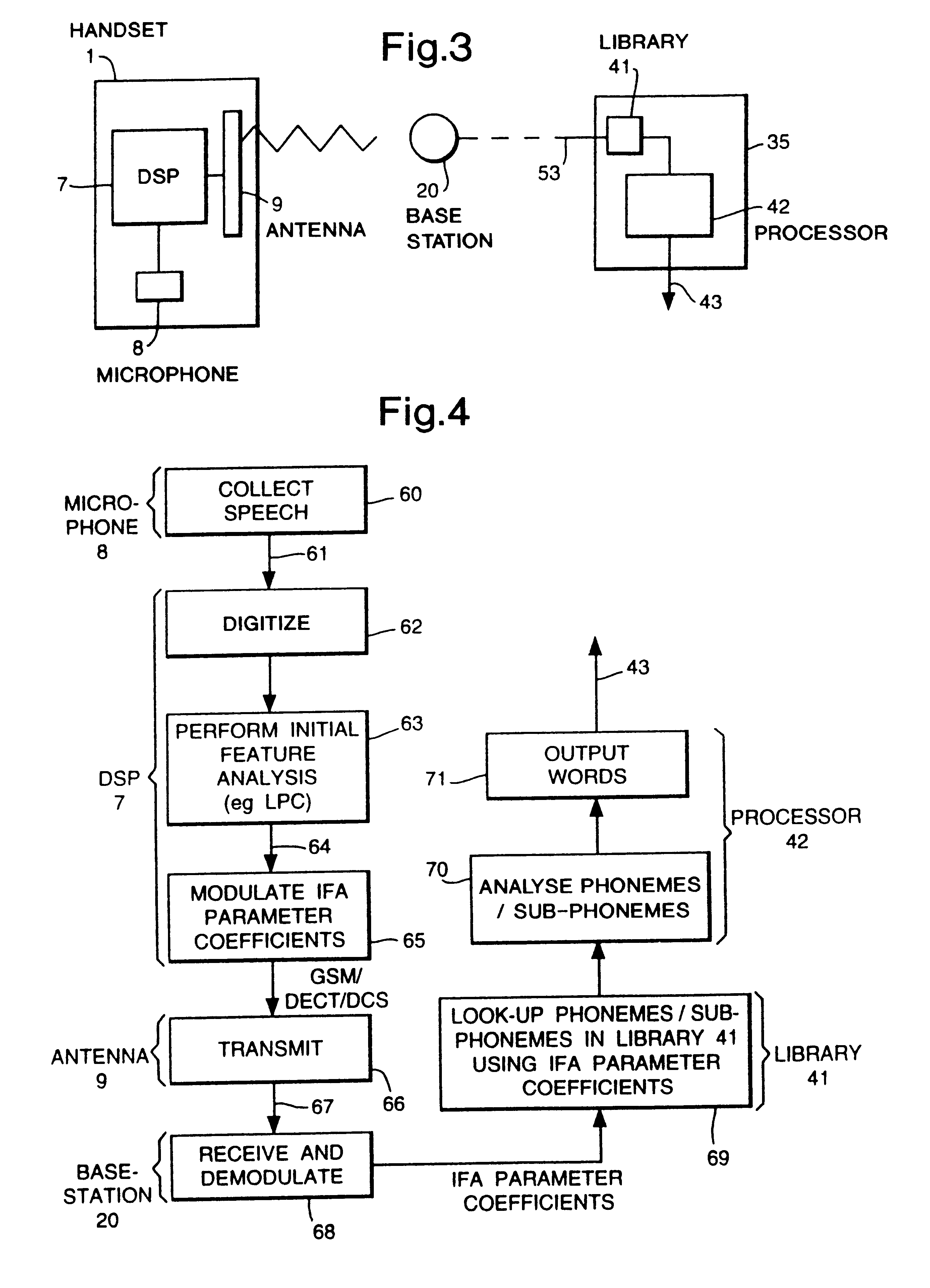
Communication system with handset for distributed processing
InactiveUS6216013B1Cordless telephonesSpecial service for subscribersCommunications systemTelephone network
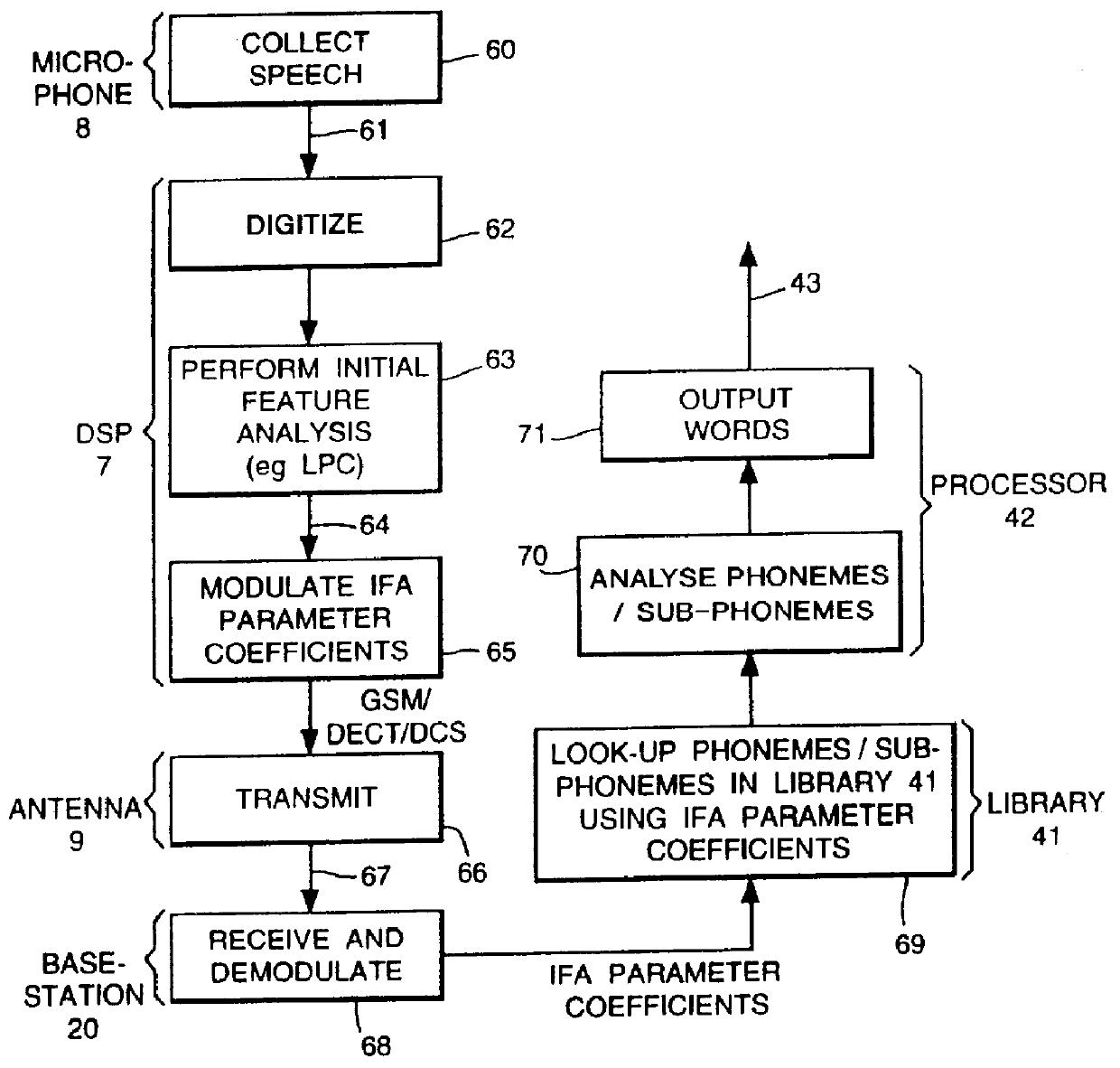
A communication system, comprising at least one mobile handheld telephone handset adapted to communicate with a telephone network handling system. The handset comprises means to produce first signals dependent thereupon, means to produce a voice transmission signal and means to transmit the voice transmission signal. The handset also comprises first processing means to carry out a speech recognition process to produce initial feature analysis parameter coefficients data dependent thereupon. The first processing step preserves predetermined information. The handset further comprises means to produce a data transmission. The telephone network handling system comprises means to receive the voice signal, means to forward the voice signal, and means to receive and process the data transmission signal. The telephone handling system also comprises means to carry out the remote second processing step in a speech recognition process on the regenerated data.
Owner:CABLE & WIRELESS PLC
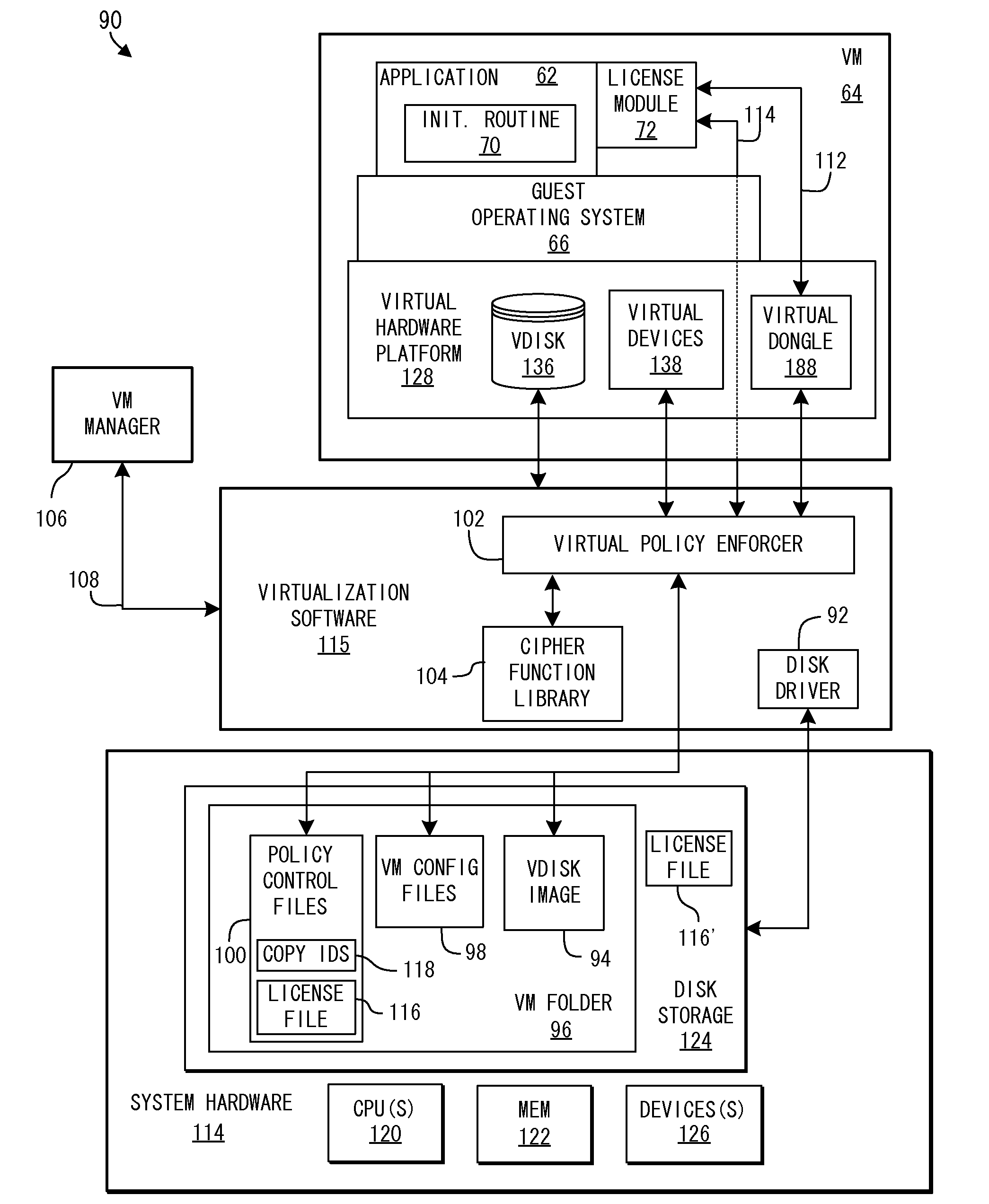
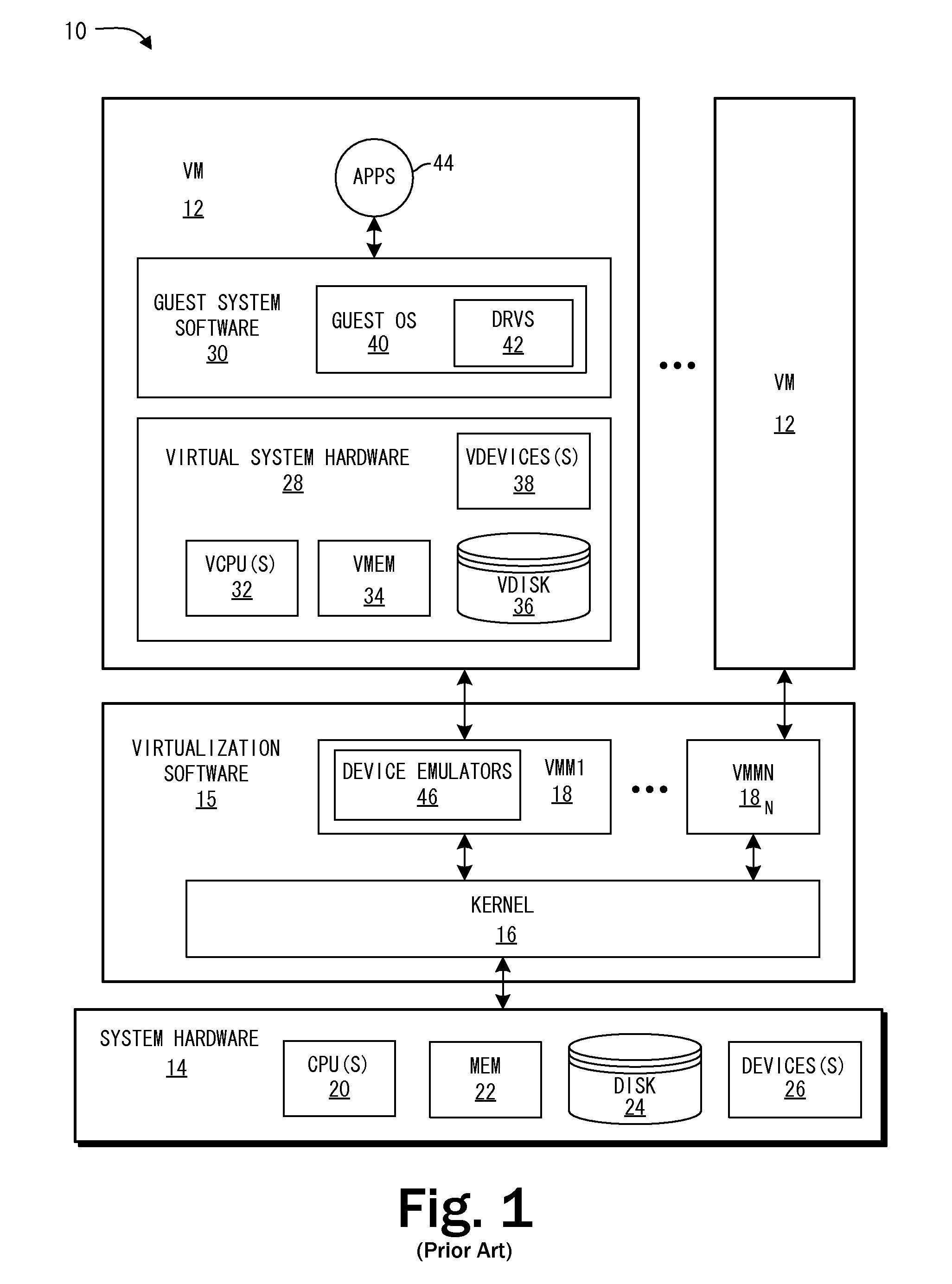
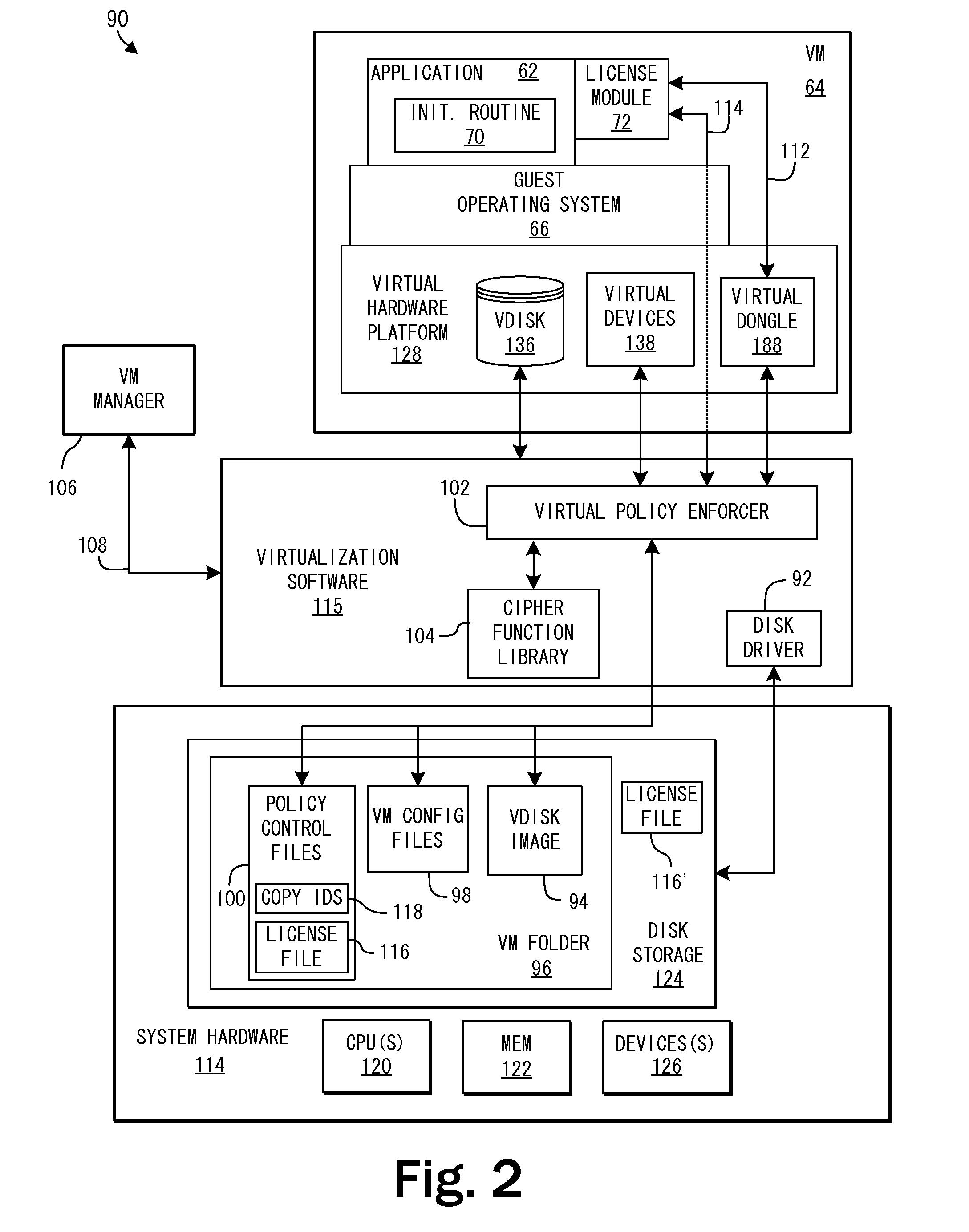
System and Methods for Enforcing Software License Compliance with Virtual Machines
ActiveUS20090328225A1Digital data processing detailsAnalogue secracy/subscription systemsVirtualizationOperational system
A virtualization system supports secure, controlled execution of application programs within virtual machines. The virtual machine encapsulates a virtual hardware platform and guest operating system executable with respect to the virtual hardware platform to provide a program execution space within the virtual machine. An application program, requiring license control data to enable execution of the application program, is provided within the program execution space for execution within the virtual machine. A data store providing storage of encrypted policy control information and the license control data is provided external to the virtual machine. The data store is accessed through a virtualization system including a policy controller that is selectively responsive to a request received from the virtual machine to retrieve the license control data dependent on an evaluation of the encrypted policy control information.
Owner:VMWARE INC
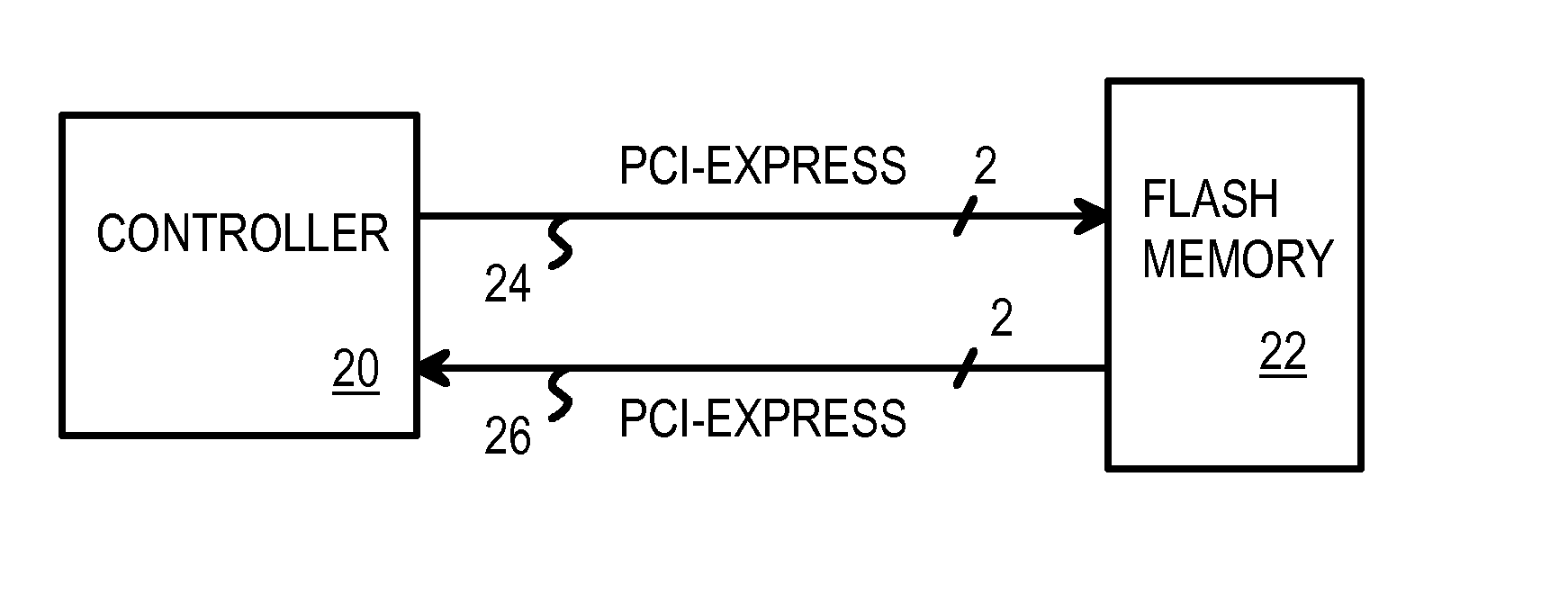
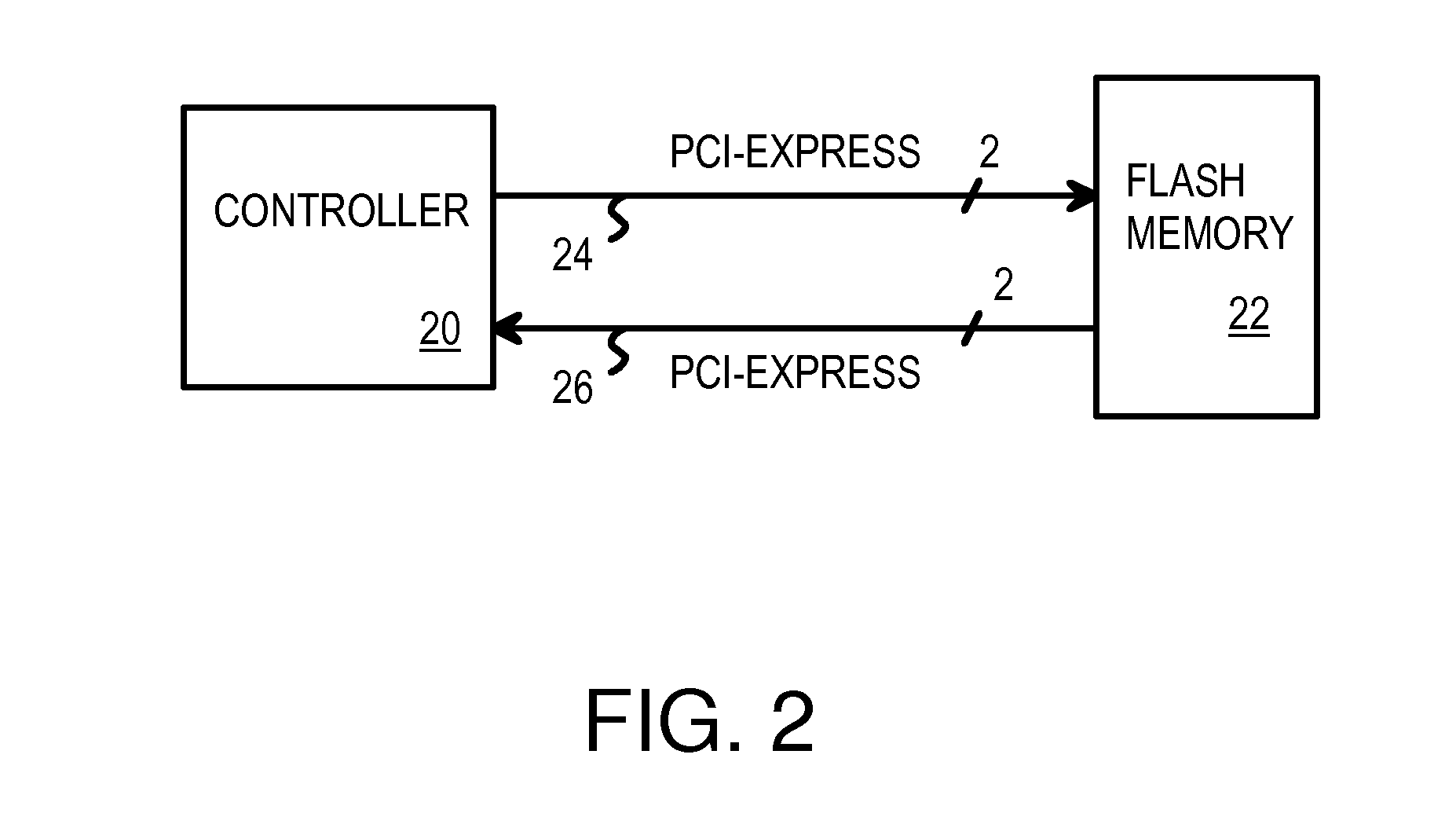
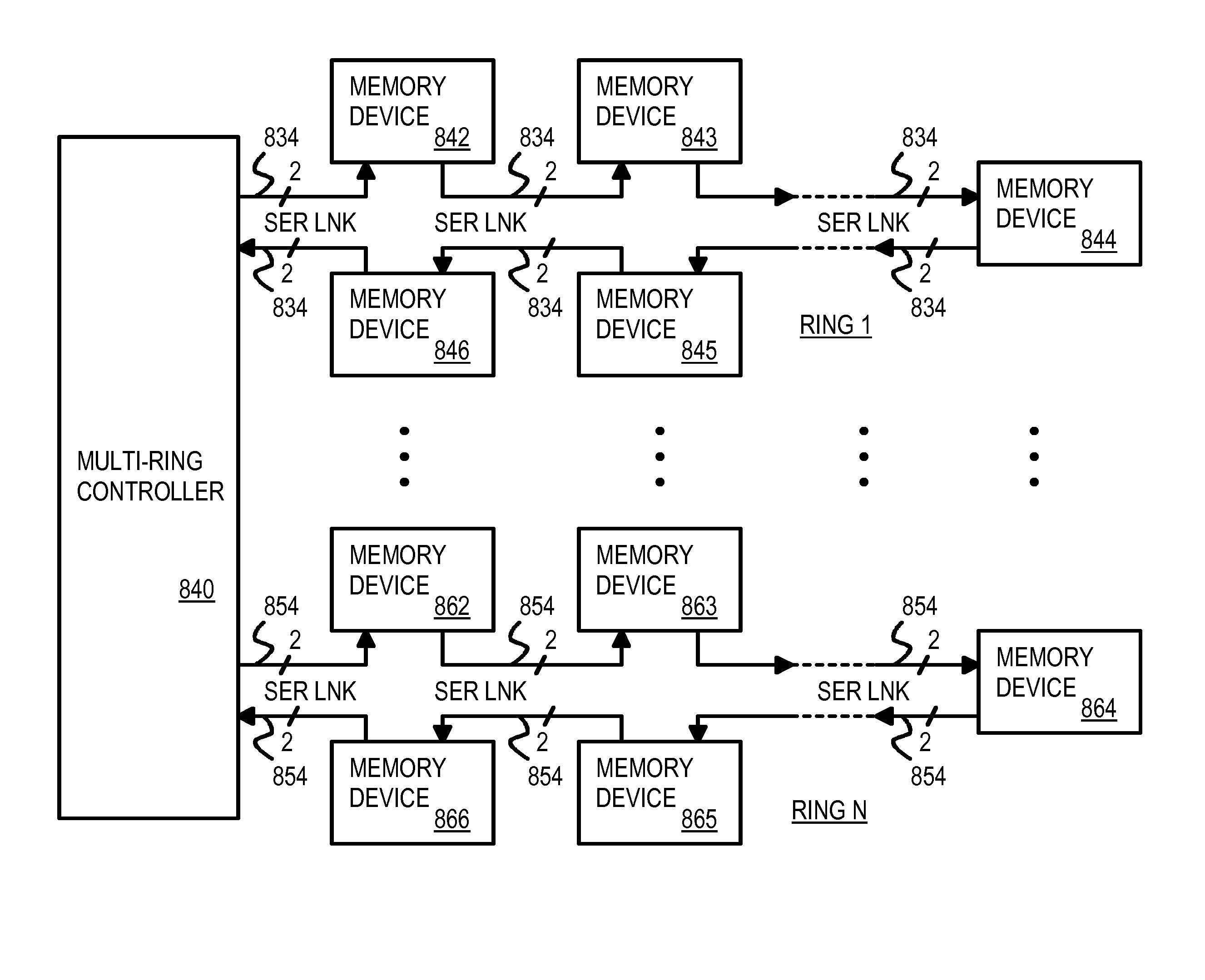
Flash / Phase-Change Memory in Multi-Ring Topology Using Serial-Link Packet Interface
A multi-ring memory controller sends request packets to multiple rings of serial flash-memory chips. Each of the multiple rings has serial flash-memory chips with serial links in a uni-directional ring. Each serial flash-memory chip has a bypassing transceiver with a device ID checker that bypasses serial packets to a clock re-synchronizer and bypass logic for retransmission to the next device in the ring, or extracts the serial packet to the local device when an ID match occurs. Serial packets pass through all devices in the ring during one round-trip transaction from the controller. The average latency of one round is constant for all devices on the ring, reducing data-dependent performance, since the same packet latency occurs regardless of the data location on the ring. The serial links can be a Peripheral Component Interconnect (PCI) Express bus. Packets have modified-PCI-Express headers that define the packet type and data-payload length.
Owner:SUPER TALENT ELECTRONICS
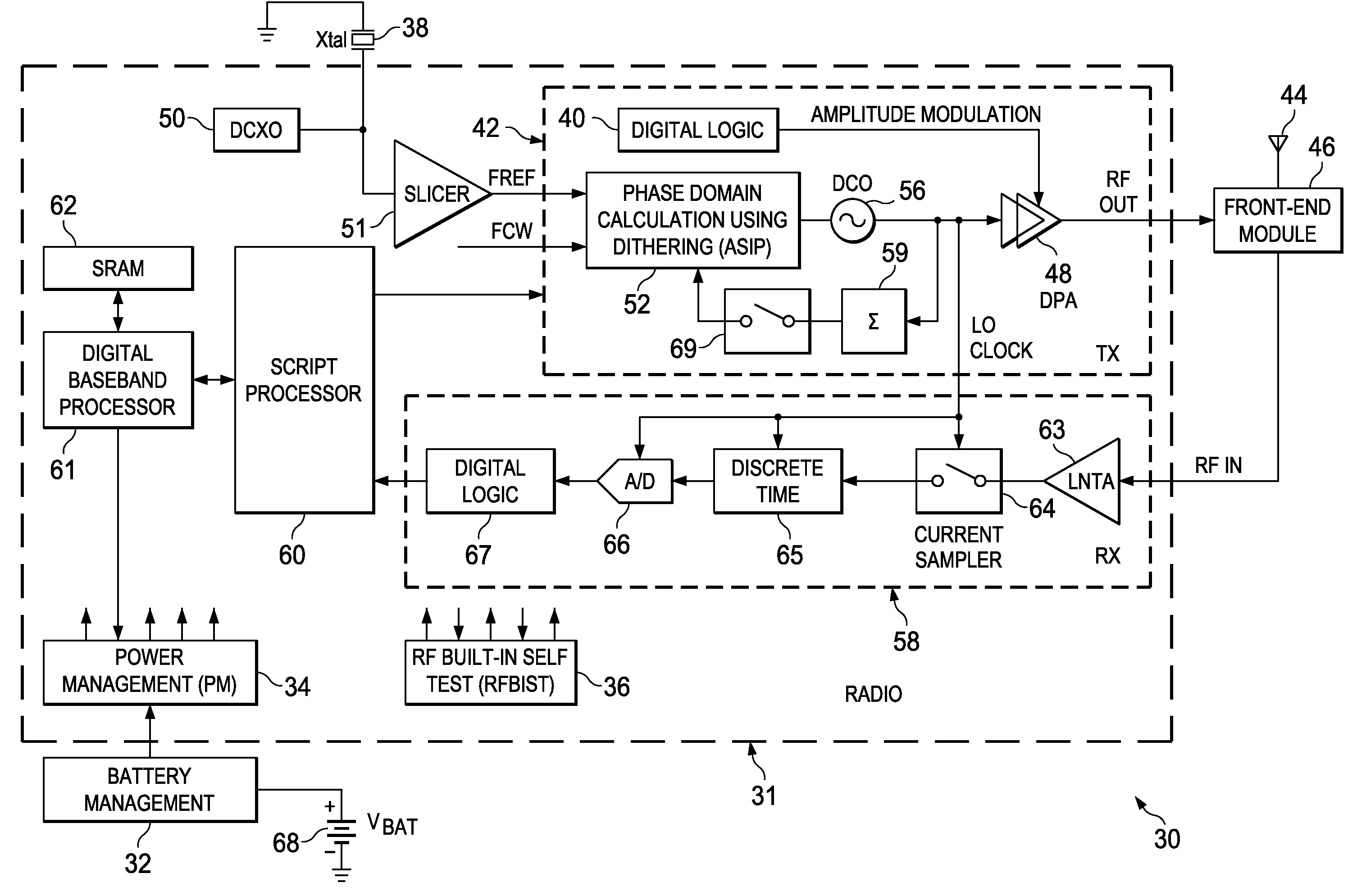
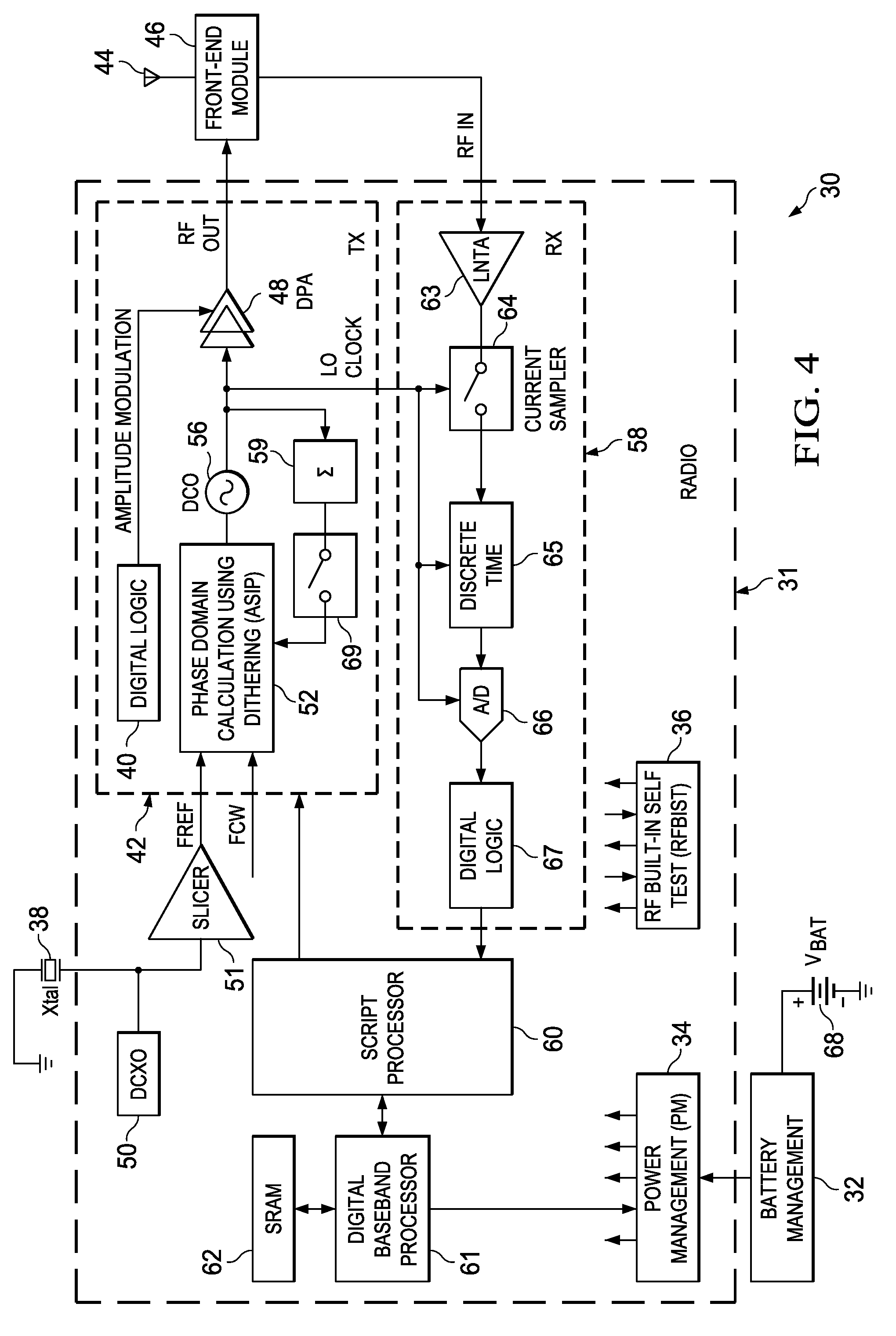
Computation spreading utilizing dithering for spur reduction in a digital phase lock loop
ActiveUS20090262877A1Easy to reconfigureReduce generationPulse automatic controlGenerator stabilizationFrequency spectrumClock rate
A novel and useful apparatus for and method of spur reduction using computation spreading with dithering in a digital phase locked loop (DPLL) architecture. A software based PLL incorporates a reconfigurable calculation unit (RCU) that is optimized and programmed to sequentially perform all the atomic operations of a PLL or any other desired task in a time sharing manner. An application specific instruction-set processor (ASIP) incorporating the RCU is adapted to spread the computation of the atomic operations out over a PLL reference clock period wherein each computation is performed at a much higher processor clock frequency than the PLL reference clock rate. This significantly reduces the per cycle current transient generated by the computations. The frequency content of the current transients is at the higher processor clock frequency which results in a significant reduction in spurs within sensitive portions of the output spectrum. Further reduction in spurs is achieved by dithering the duration of the software loop of atomic operations and / or by randomly shuffling one or more non-data dependent instructions within each iteration of the software loop.
Owner:TEXAS INSTR INC
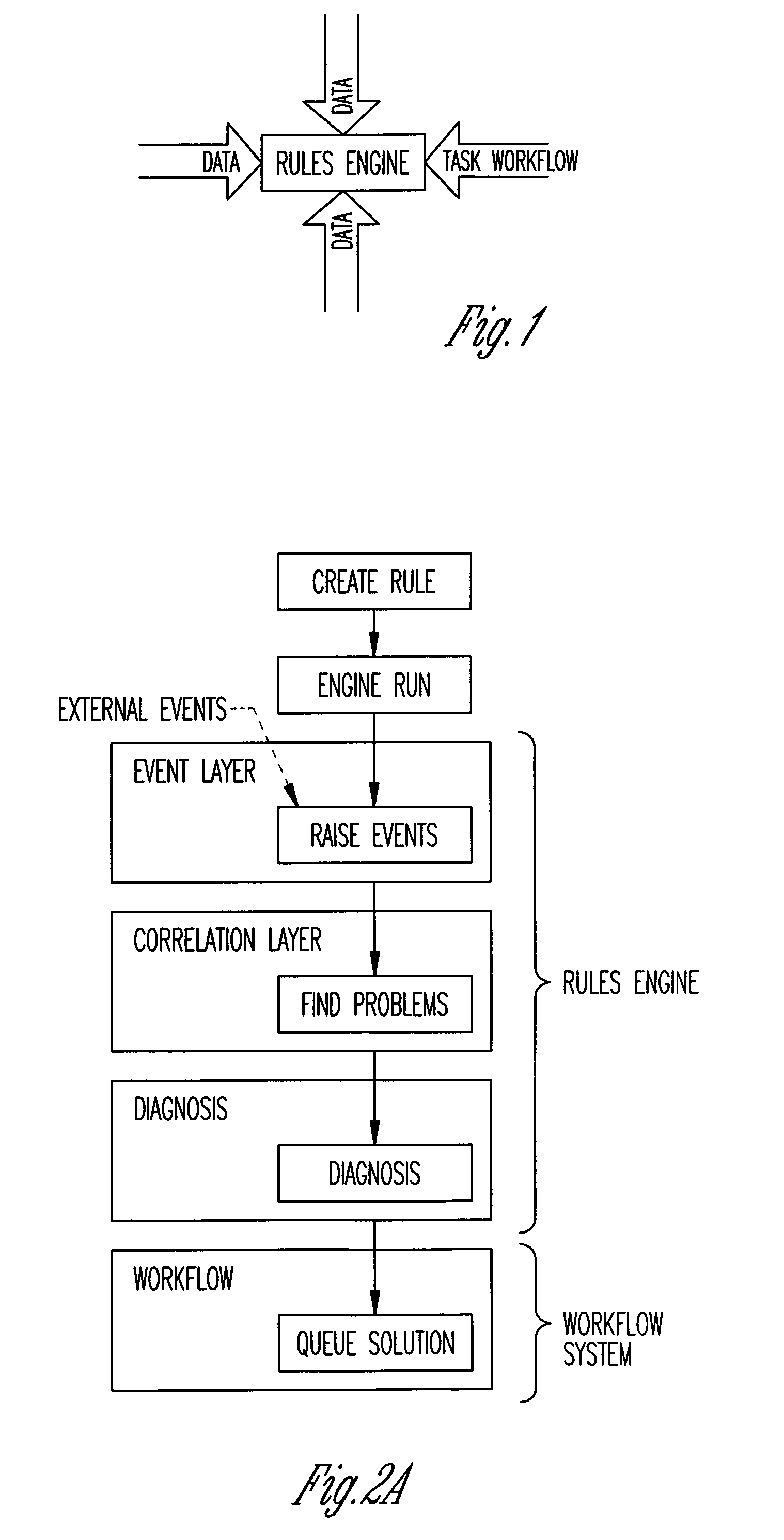
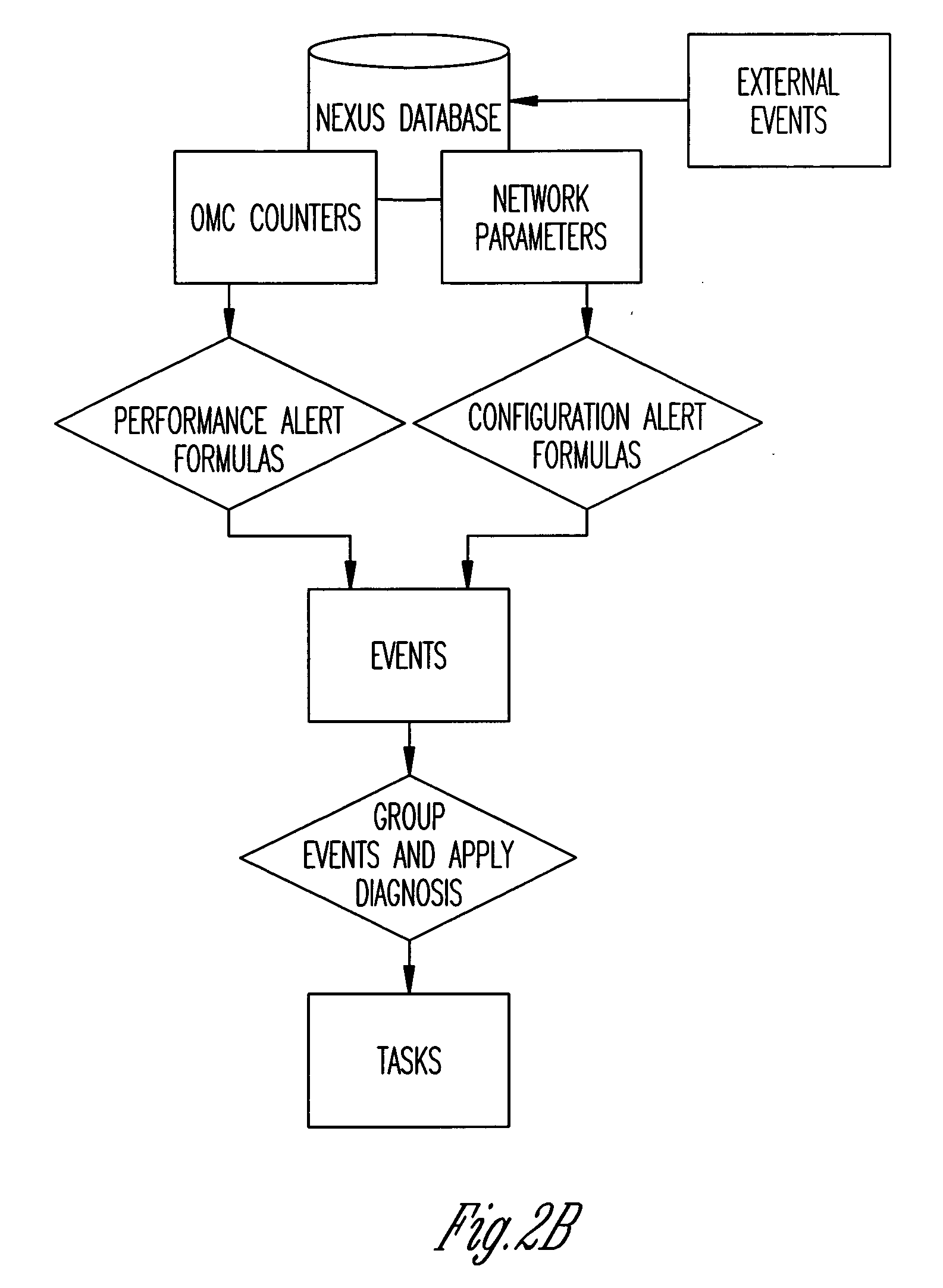
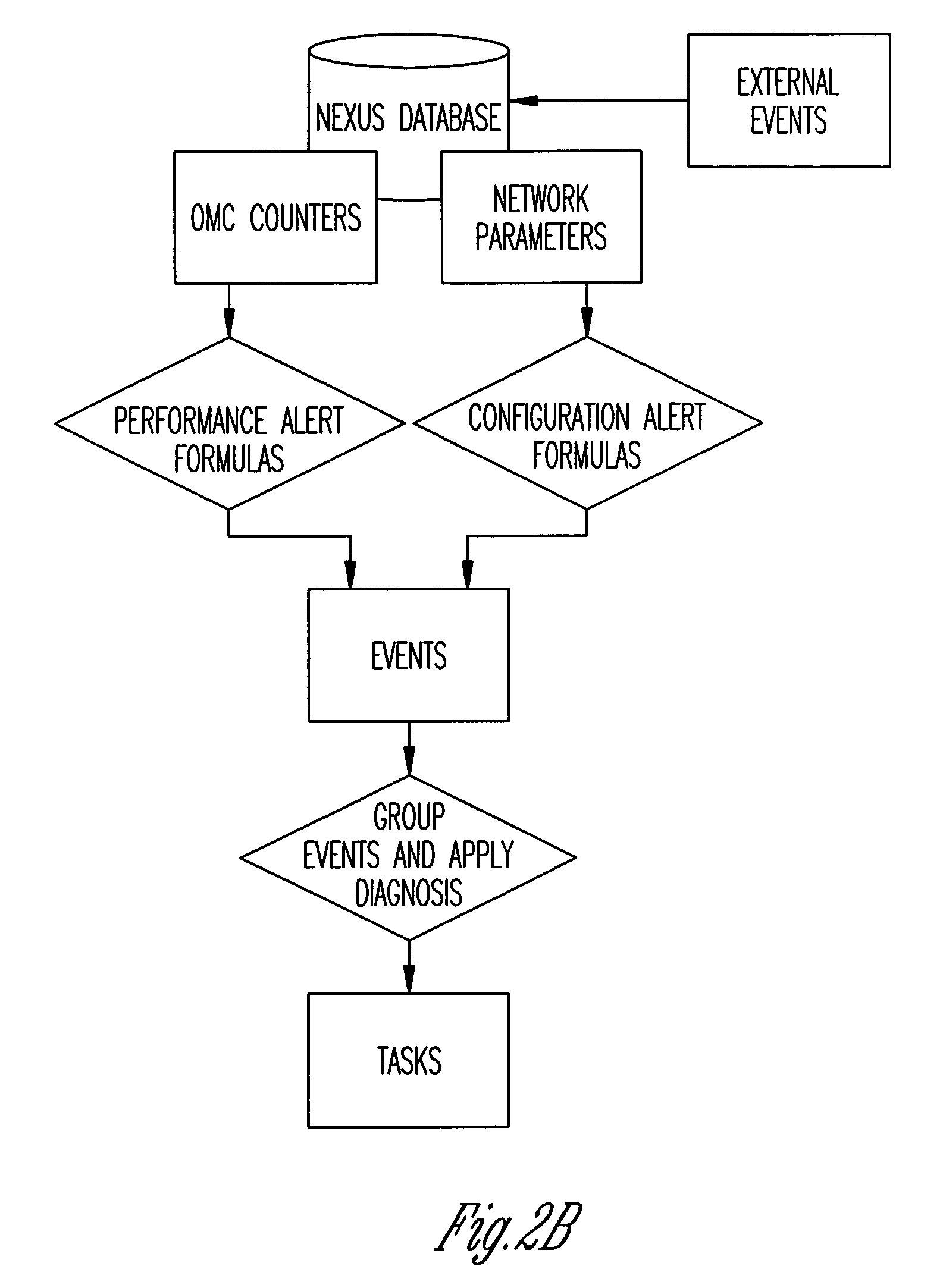
Mobile phone network optimisation systems
InactiveUS20090075648A1Improve performanceReduce said mismatchTransmissionWireless communicationAnalysis dataData analysis system
We describe a system to optimize performance of a mobile phone network towards a performance goal. The system receives performance data comprising aggregated data for a plurality of calls and commissions measurement data comprising data logged for a plurality of mobile phones, and outputs data for changing a configuration of said network. The system includes a performance monitoring system; a measurement data request system, wherein measurement data is selectively commissioned in response said performance mismatch; a measurement data analysis system to analyze the commissioned measurement data to determine a probable cause of said mismatch, and to provide analysis data identifying the probable cause; and an action determination system to receive said analysis data and to output action data dependent on the analysis data, the action data identifying one or more configuration changes to be made to the mobile phone network to reduce the mismatch.
Owner:ACTIX
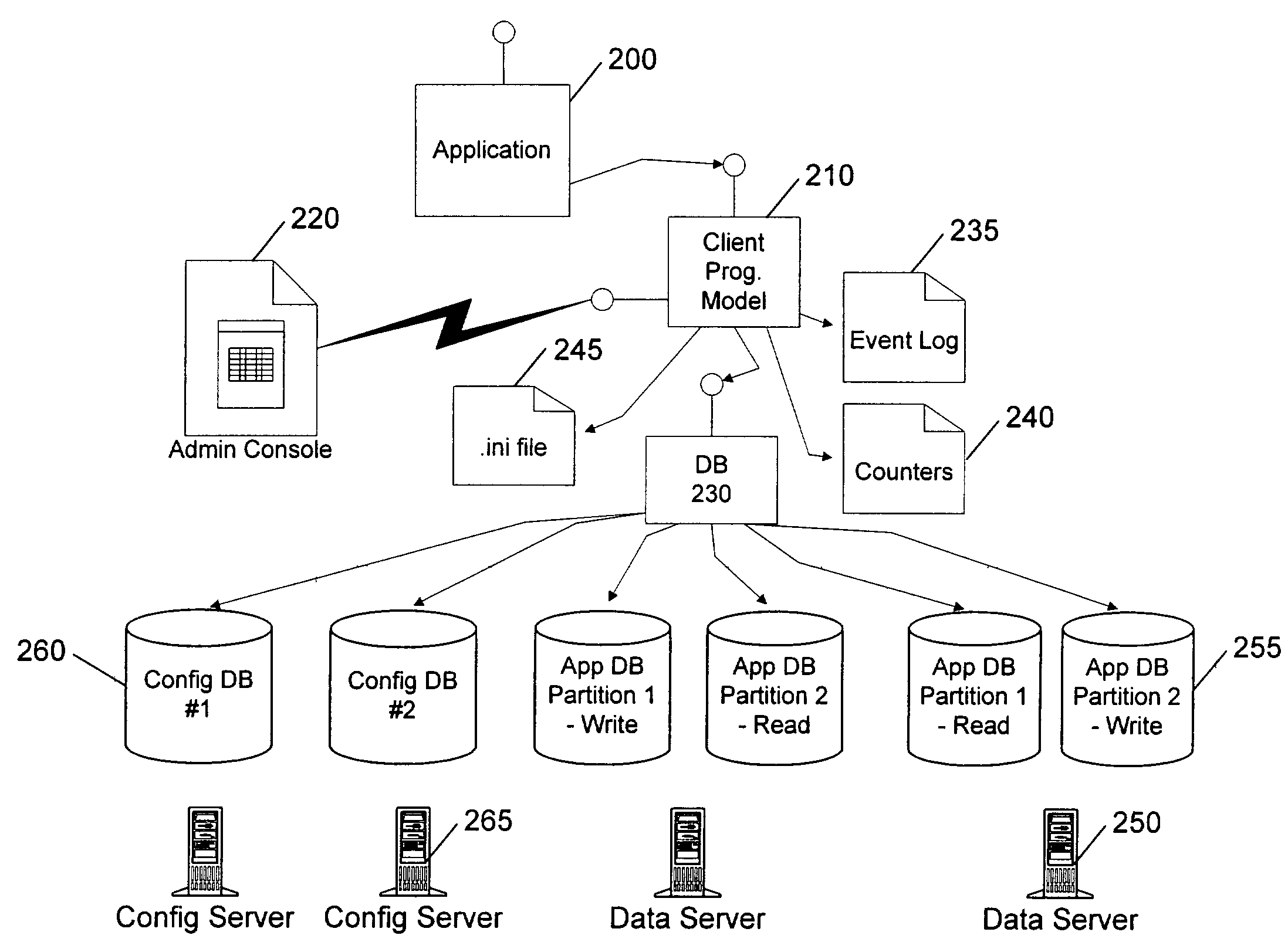
Client programming model with abstraction
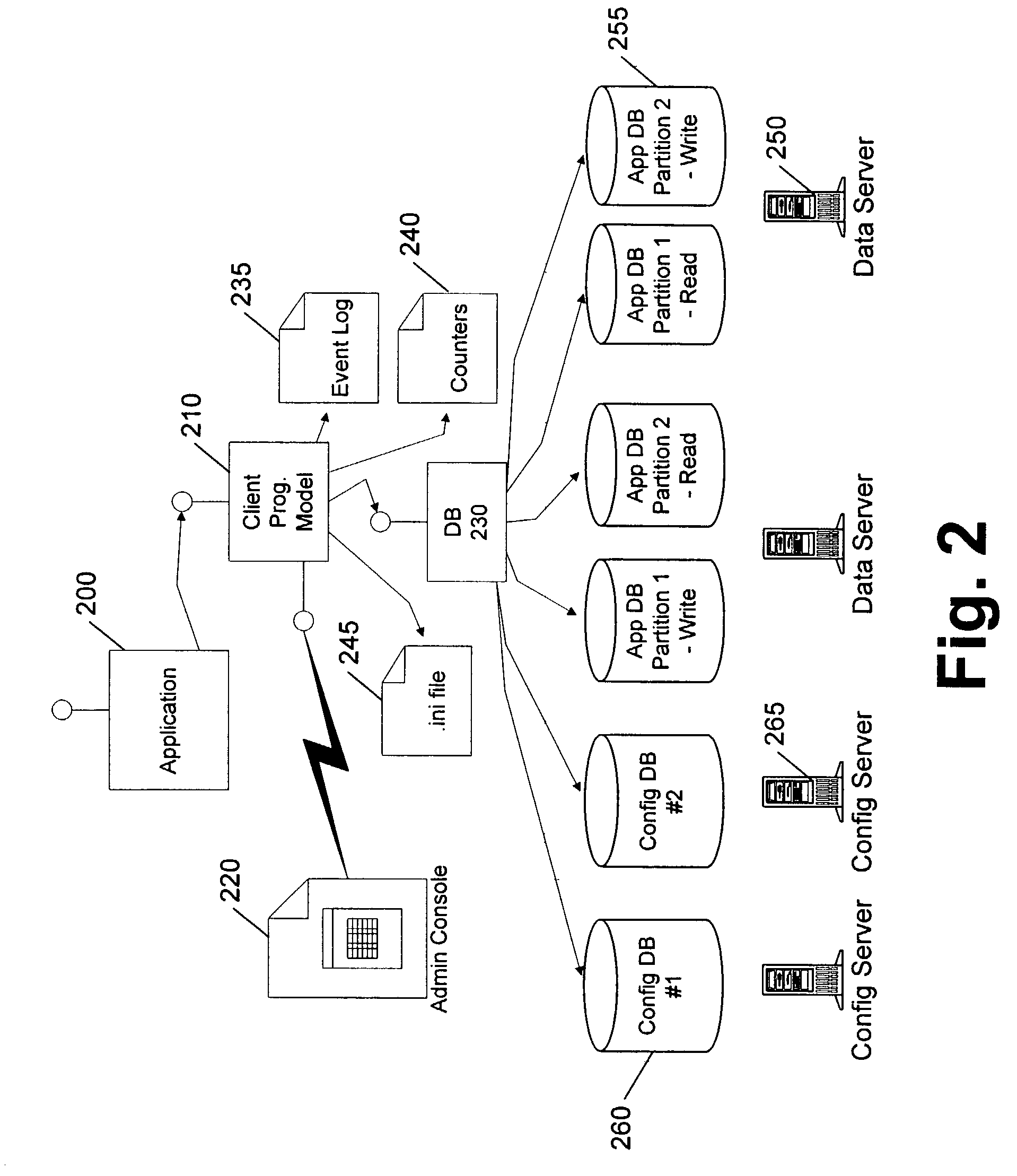
InactiveUS7058958B1Digital data information retrievalData processing applicationsFailoverParallel programming model
A client programming model with abstraction hides from an underlying client application or application program interface (API) the details of where each element of data is located, and which copy of the data is resident on an available server and associated databases. The model wraps a database, such as a virtual database, and provides data-dependent and application-dependent routing, failover, and operational administration.
Owner:MICROSOFT TECH LICENSING LLC
Image encoding using reordering and blocking of wavelet coefficients combined with adaptive encoding
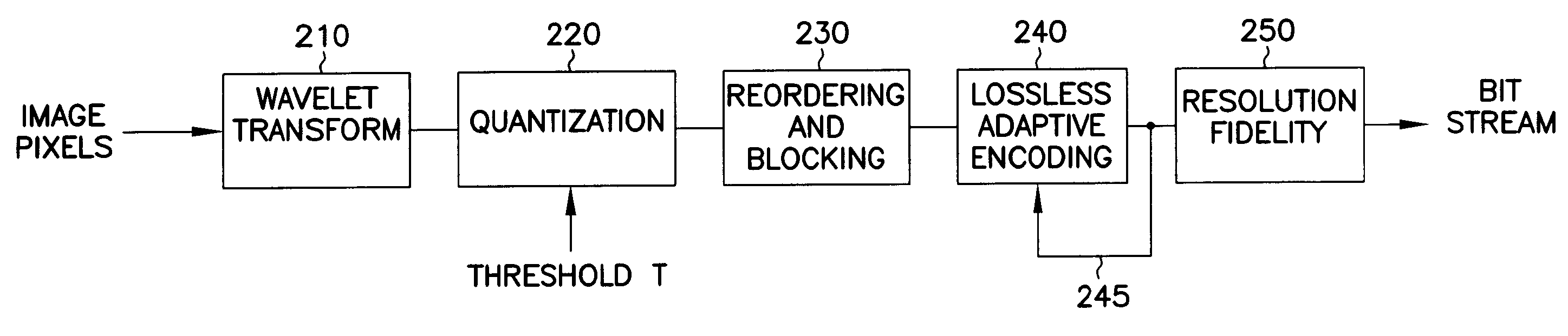
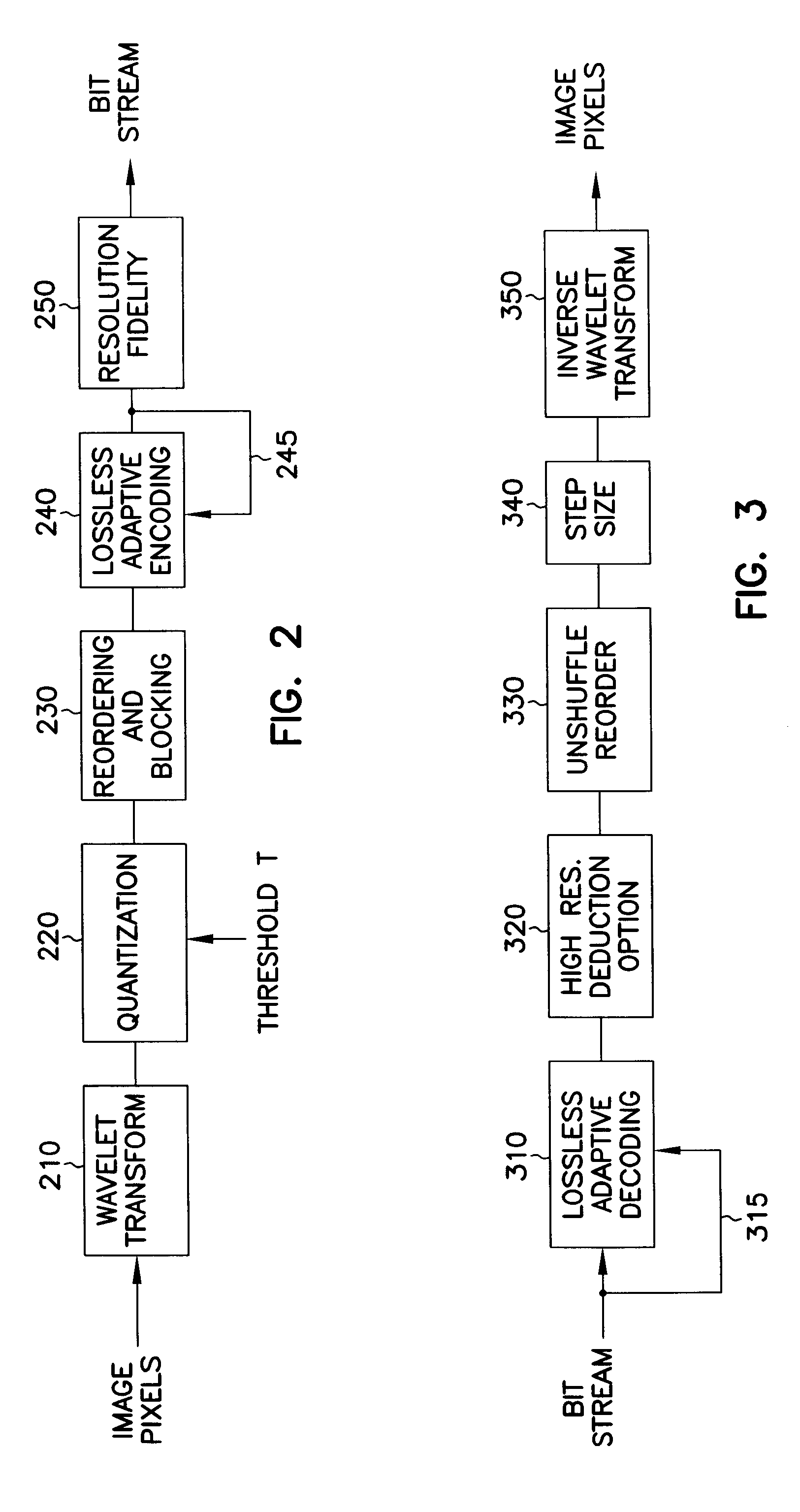
InactiveUS6850649B1Increase the compression ratioEasy to buildCode conversionImage codingReverse orderAdaptive encoding
An encoder reorders quantized wavelet coefficients to cluster large and small wavelet coefficients into separate groups without requiring the use of data-dependent data structures. The coefficients are then adaptively encoded based on a run-length code which continuously modifies a parameter that controls the codewords uses to represent strings of quantized coefficients, seeking to minimize the number of bits spent in the codewords. A matrix of indices contains the coarsest coefficients in the upper left corner, and filling in low high and high low sub bands in larger and larger blocks in an alternating manner, such that low high sub bands comprise the top of the matrix and the high low sub bands comprise the left side of the matrix. The shortest codewords are assigned to represent a run of the most likely character having length of 2k, where k is a parameter. k is adjusted based on successive characters being encountered. k is increased when the character is the same, and decreased when the character is different. A decoder applies the above in reverse order. Decoding of the encoded coefficients is first performed, followed by an unshuffling of the coefficients. The unshuffled coefficients are then subjected to an inverse wavelet transform to recover the transformed and compressed data, such as image pixels.
Owner:DYNADEX DATA LLC
Intelligent personal information management system
The invention comprises a personal data sharing system comprising an aggregator for aggregating data from a plurality of disparate sources and for categorising said aggregated data into discrete groups of data, a platform configured to enable the assignment of an access permission level for each one of said discrete groups of data by allowing the user to configure said access permission level or by automatically assigning said access permission level from a number of pre-determined access permission levels; said platform being further configured to permit access to a discrete group of data dependent upon said access permission level. The invention also comprises a method of sharing personal data comprising the steps of aggregating data from a plurality of disparate sources and categorising said aggregated data into discrete groups of data, assigning an access permission level for each one of said discrete groups of data by allowing the user to configure said access permission level or by automatically assigning said access permission level from a number of pre-determined access permission levels; and permitting access to a discrete group of data dependent upon said access permission level.
Owner:ATANDA DELE
Detecting non-redundant component dependencies in web service invocations
ActiveUS20100281488A1Efficient identificationError detection/correctionMultiprogramming arrangementsApplication softwareMutual dependence
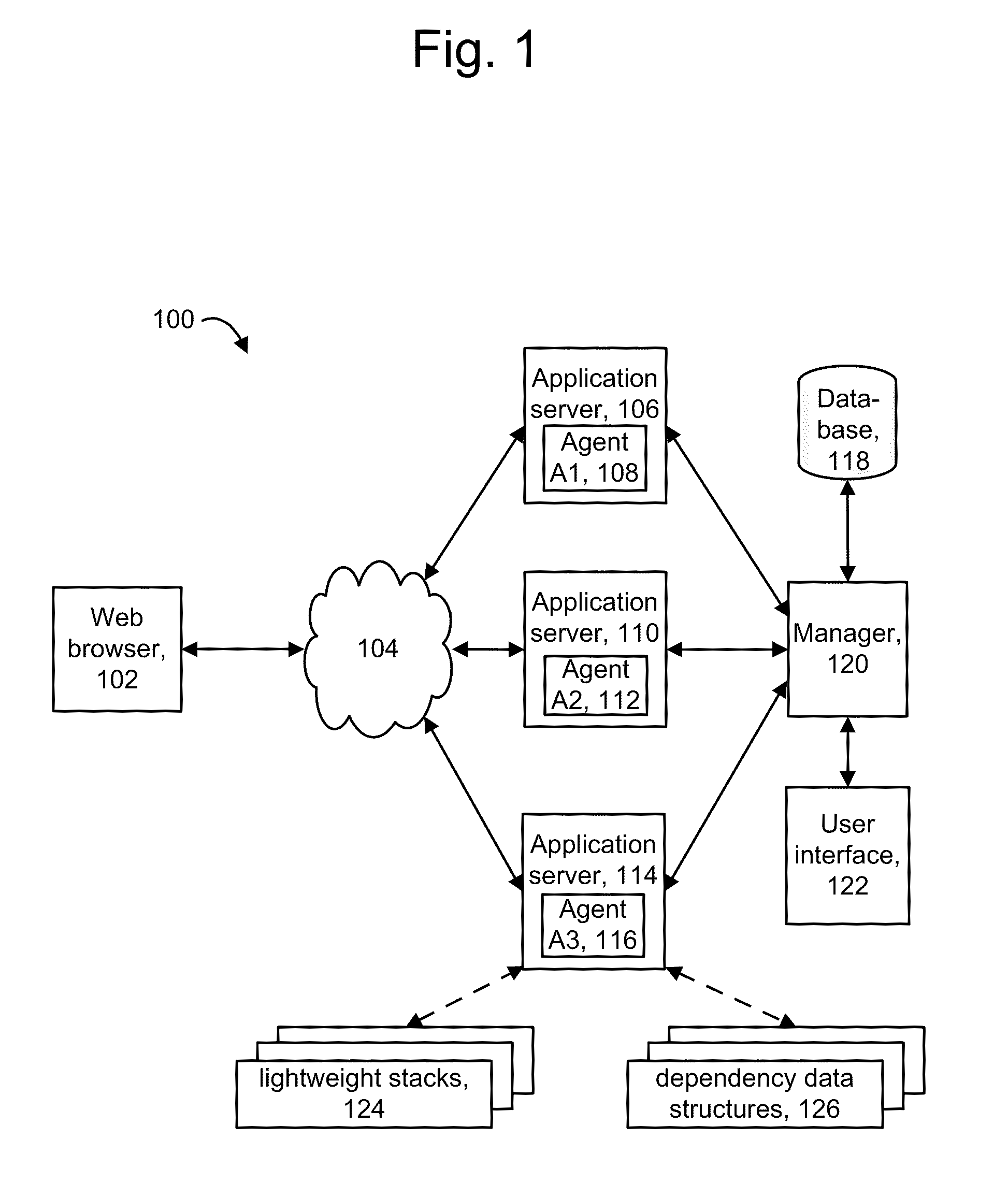
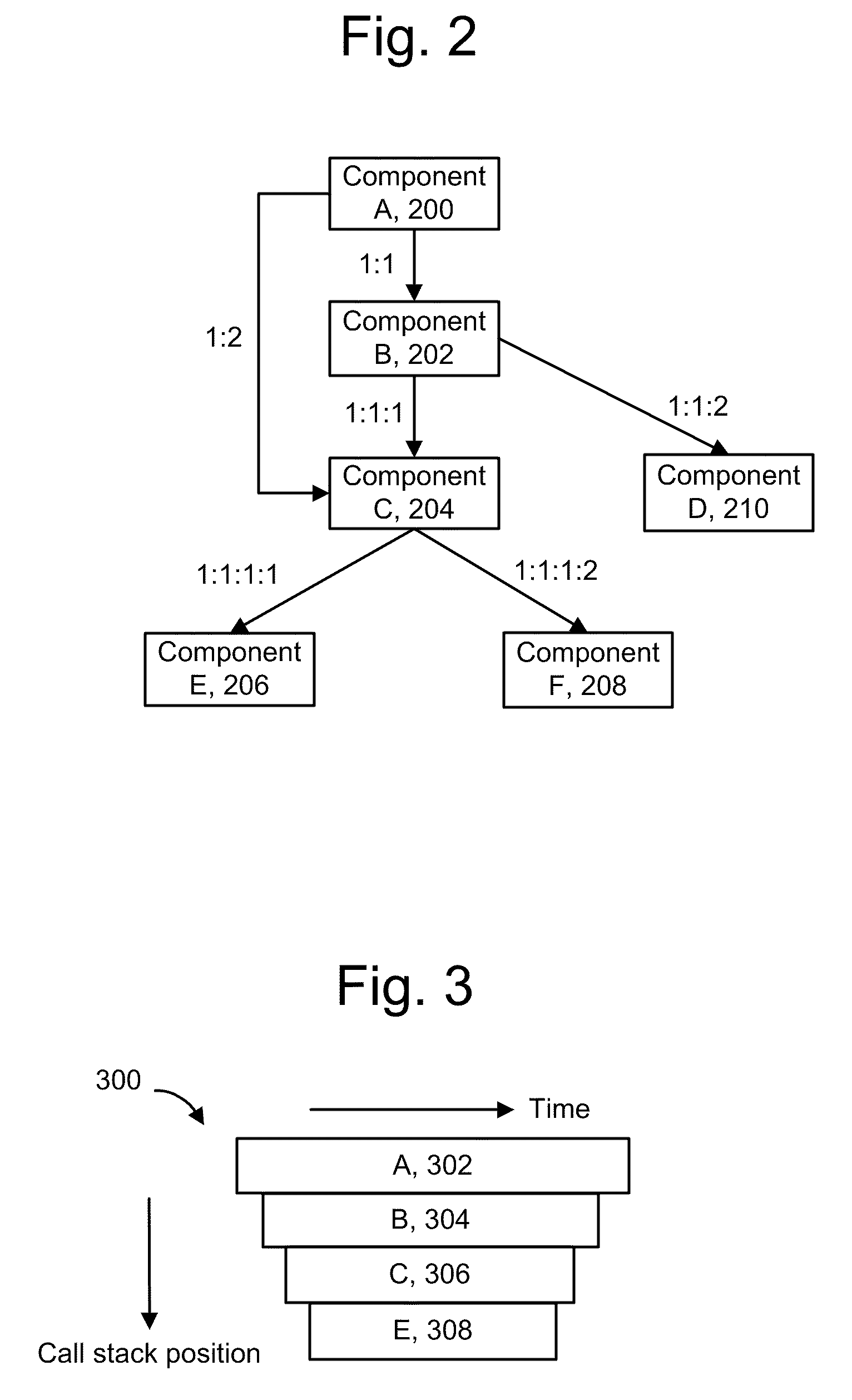
Relationships between components in an application and the services they provide are identified, including redundant caller-callee sequences. Specific components of interest are instrumented to obtain data when they execute. Data structures are created which identify the components and their dependencies on one other. To avoid excessive overhead costs, redundant dependencies are identified. A dependency data structure can be provided for each unique dependency. When repeated instances of a dependency are detected, the associated dependency data structure can be augmented with correlation data of the repeated instances, such as transaction identifiers and sequence identifiers. Sequence identifiers identify an order in which a component is called. A flag can be used to force the creation of a new dependency data structure, and a calling component's name can be used instead of a sequence identifier. Agents report the dependency data structures to a manager to provide graph data in a user interface.
Owner:CA TECH INC
Data Cache Invalidate with Data Dependent Expiration Using a Step Value
InactiveUS20090019228A1Energy efficient ICTMemory adressing/allocation/relocationParallel computingData storing
According to embodiments of the invention, a step value and a step-interval cache coherency protocol may be used to update and invalidate data stored within cache memory. A step value may be an integer value and may be stored within a cache directory entry associated with data in the memory cache. Upon reception of a cache read request, along with the normal address comparison to determine if the data is located within the cache a current step value may be compared with the stored step value to determine if the data is current. If the step values match, the data may be current and a cache hit may occur. However, if the step values do not match, the requested data may be provided from another source. Furthermore, an application may update the current step value to invalidate old data stored within the cache and associated with a different step value.
Owner:IBM CORP
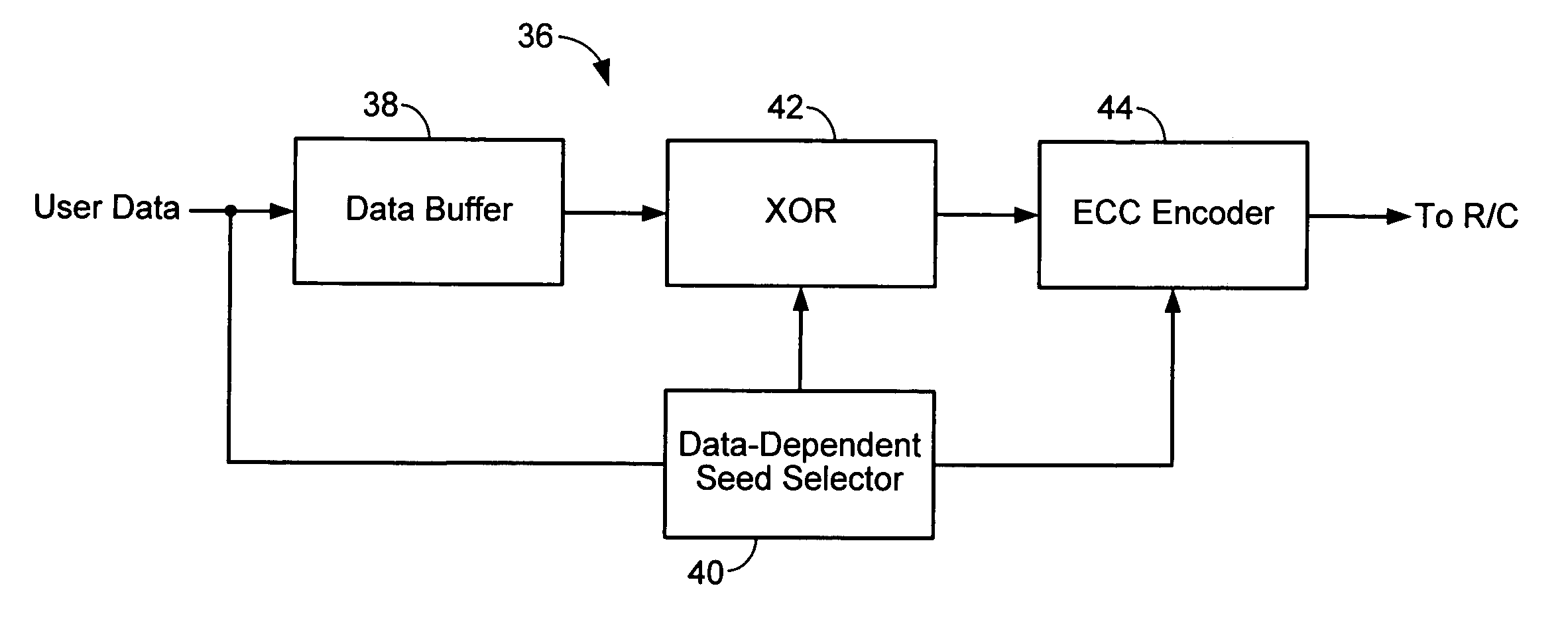
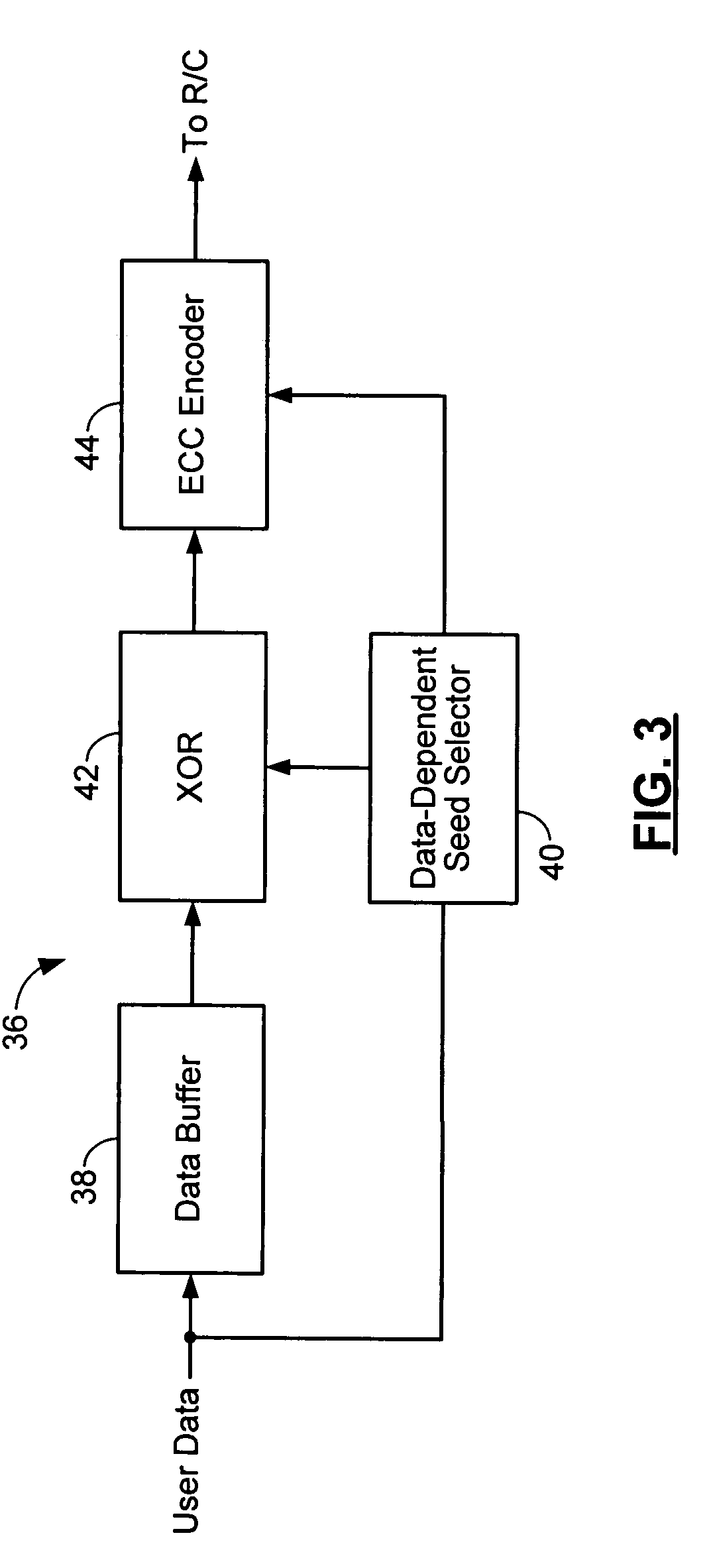
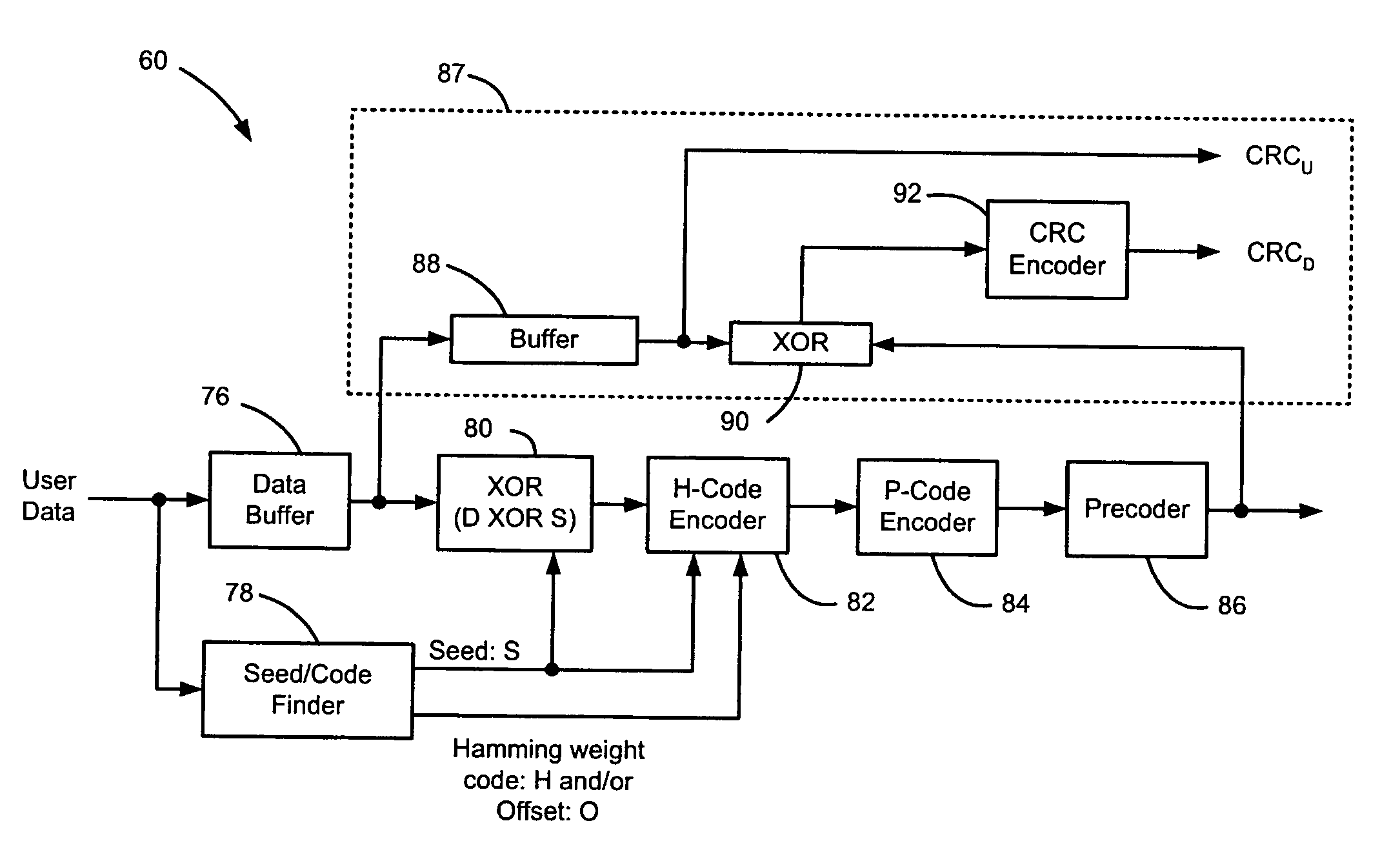
Method and apparatus for generating a seed set in a data dependent seed selector
InactiveUS7158058B1Modification of read/write signalsRecord information storageComputer networkHamming distance
A communications channel includes a buffer that receives user data symbols including a plurality of M-bit symbols. A seed selector receives the plurality of M-bit symbols, selectively removes symbols from a seed set based on Hamming distances between at least two of the M-bit symbols, and selects a scrambling seed from remaining symbols in the seed set. A scrambling device that communicates with the seed selector and the data buffer generates scrambled user data based on the user data symbols and the scrambling seed. The communications channel is implemented in a data storage system. The seed selector ensures a minimum Hamming weight of 15 percent in the scrambled user data. The seed selector compares first and second user data symbols in the plurality of M-bit symbols.
Owner:MARVELL ASIA PTE LTD
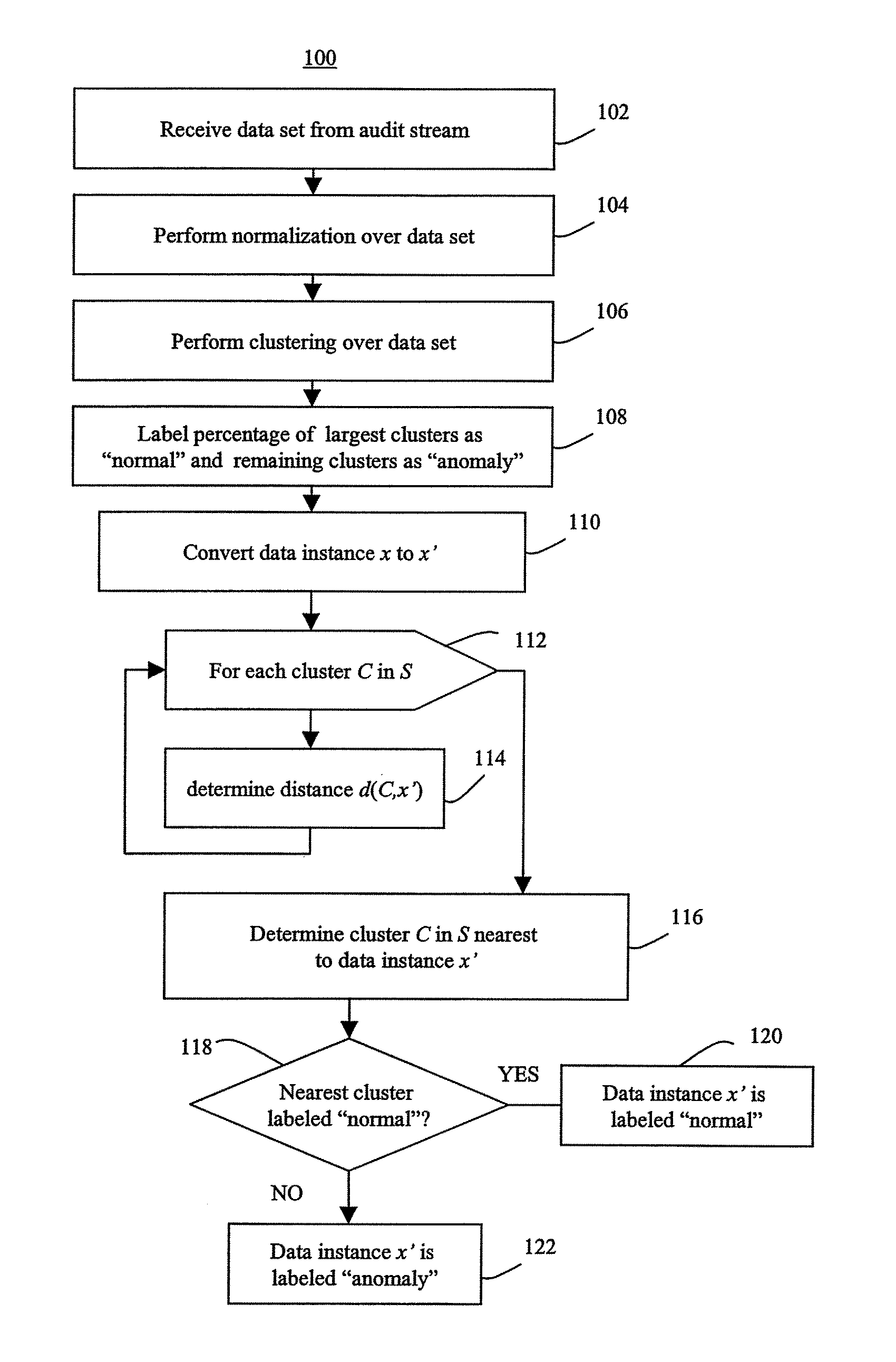
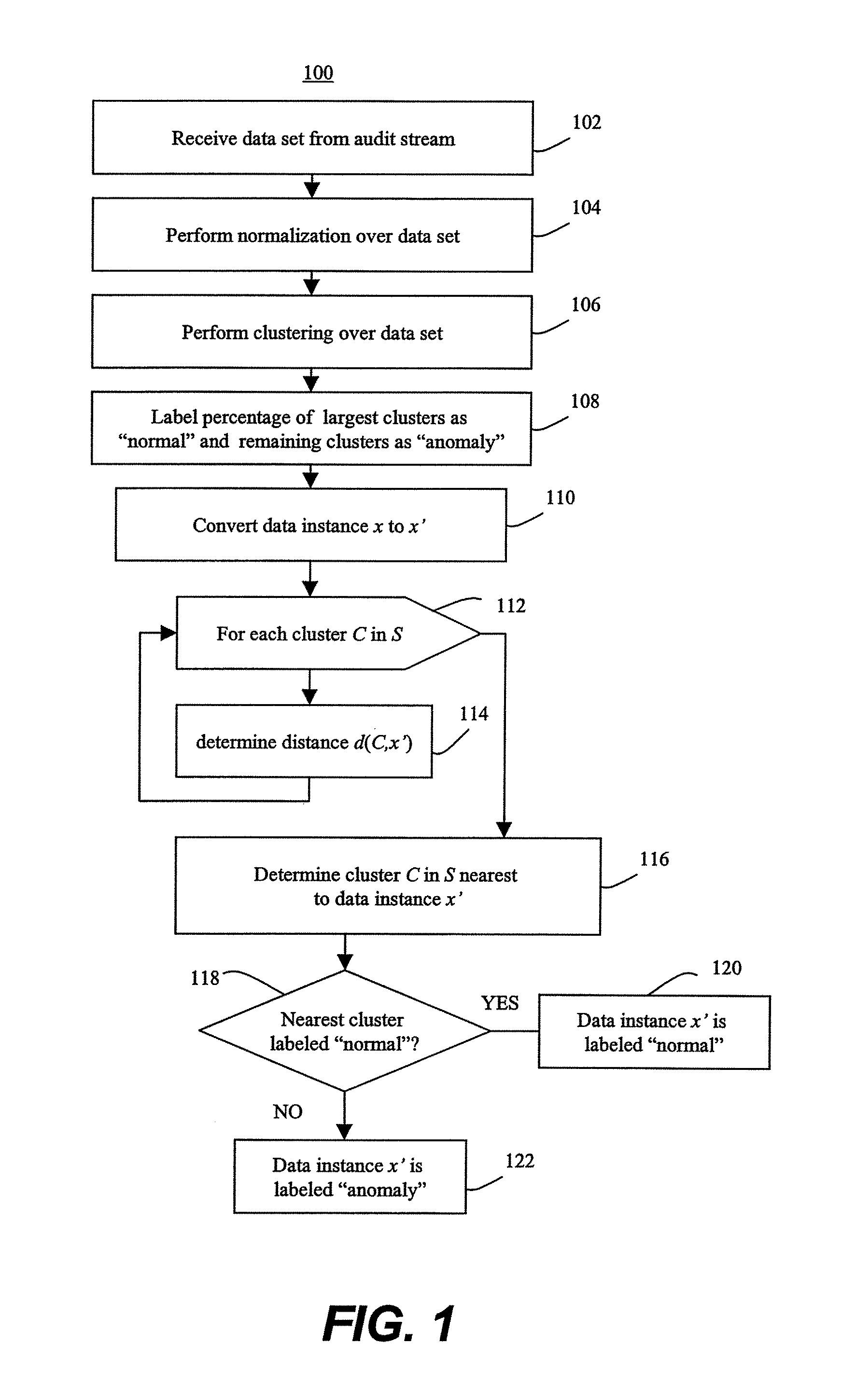
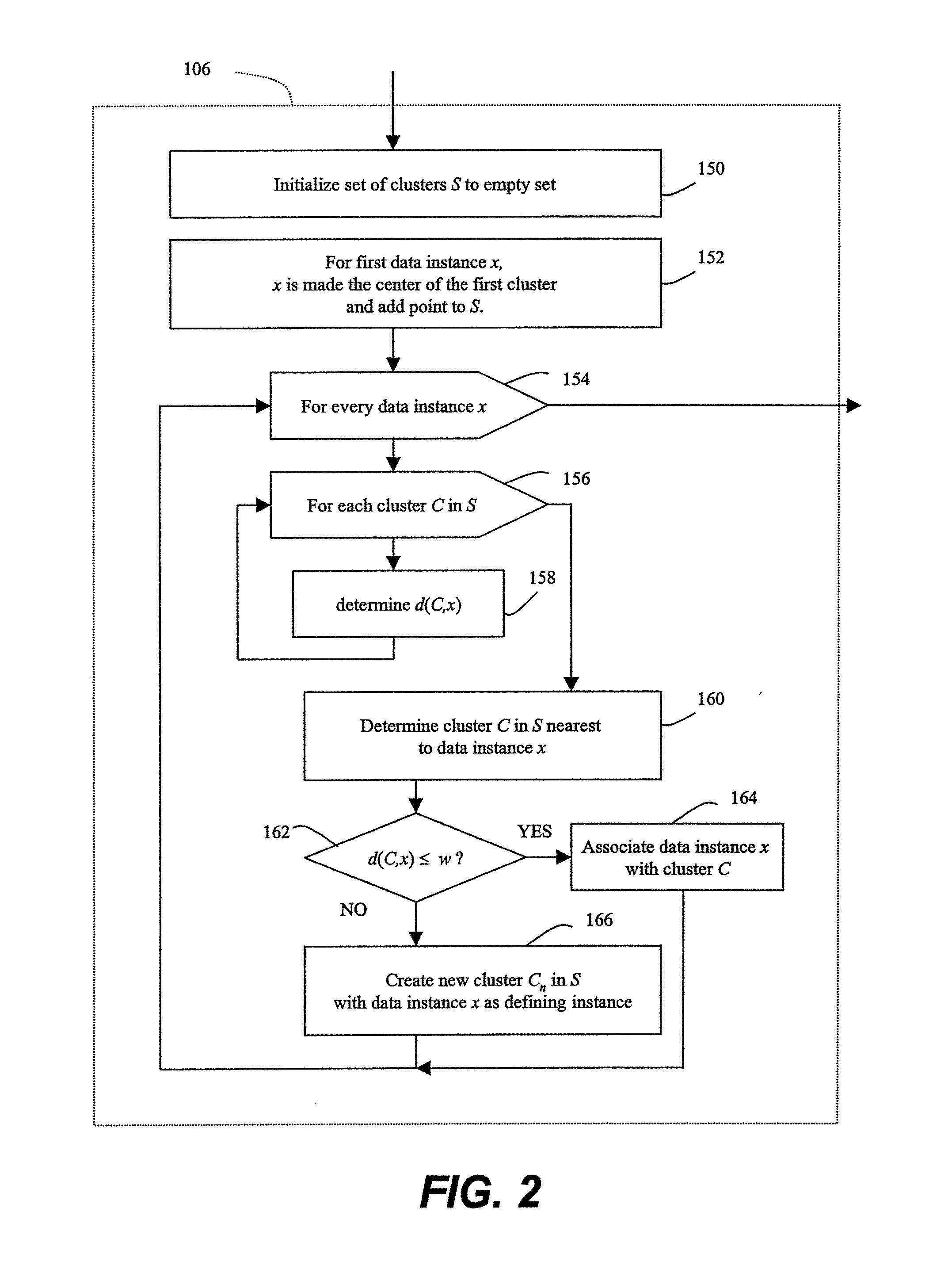
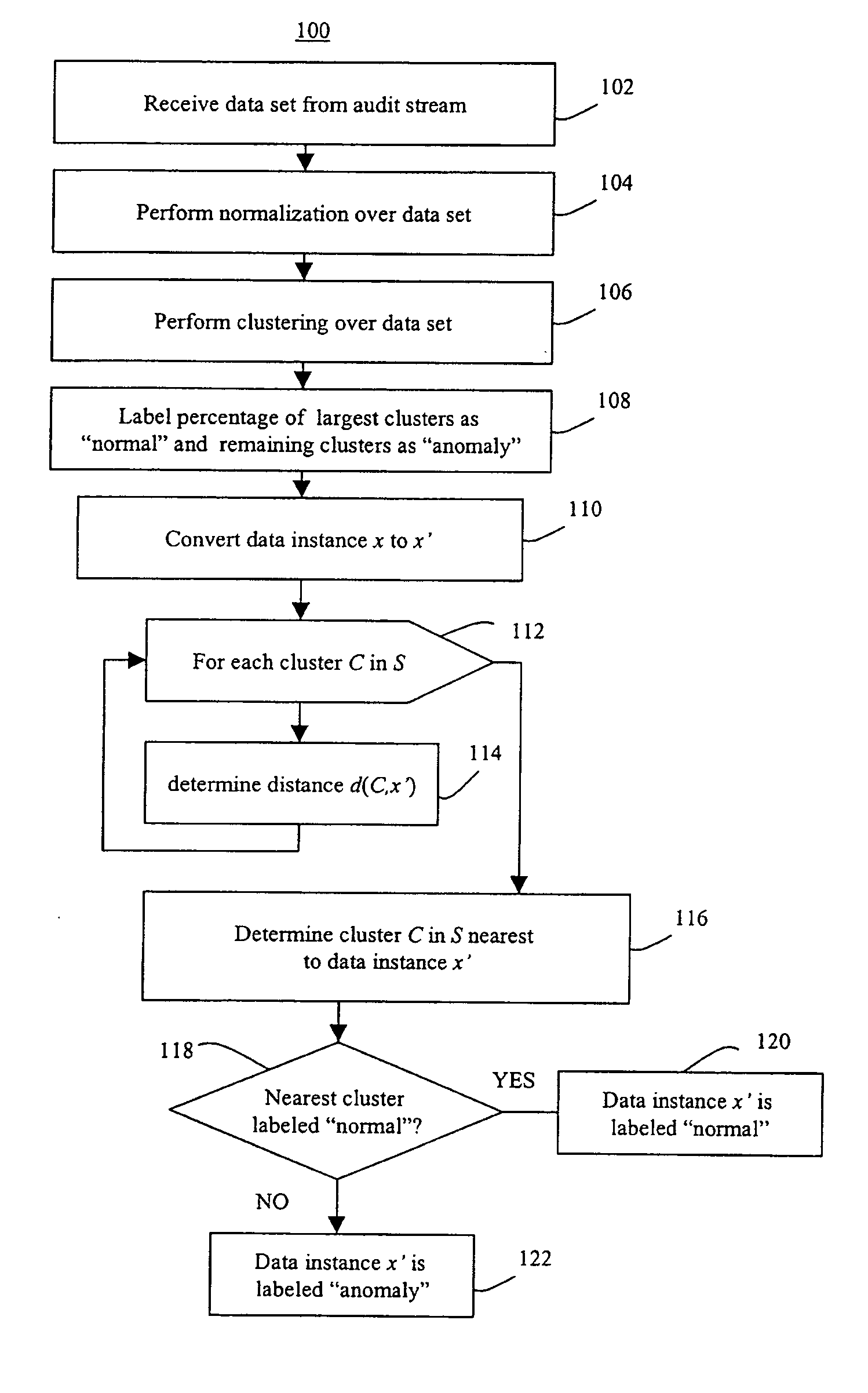
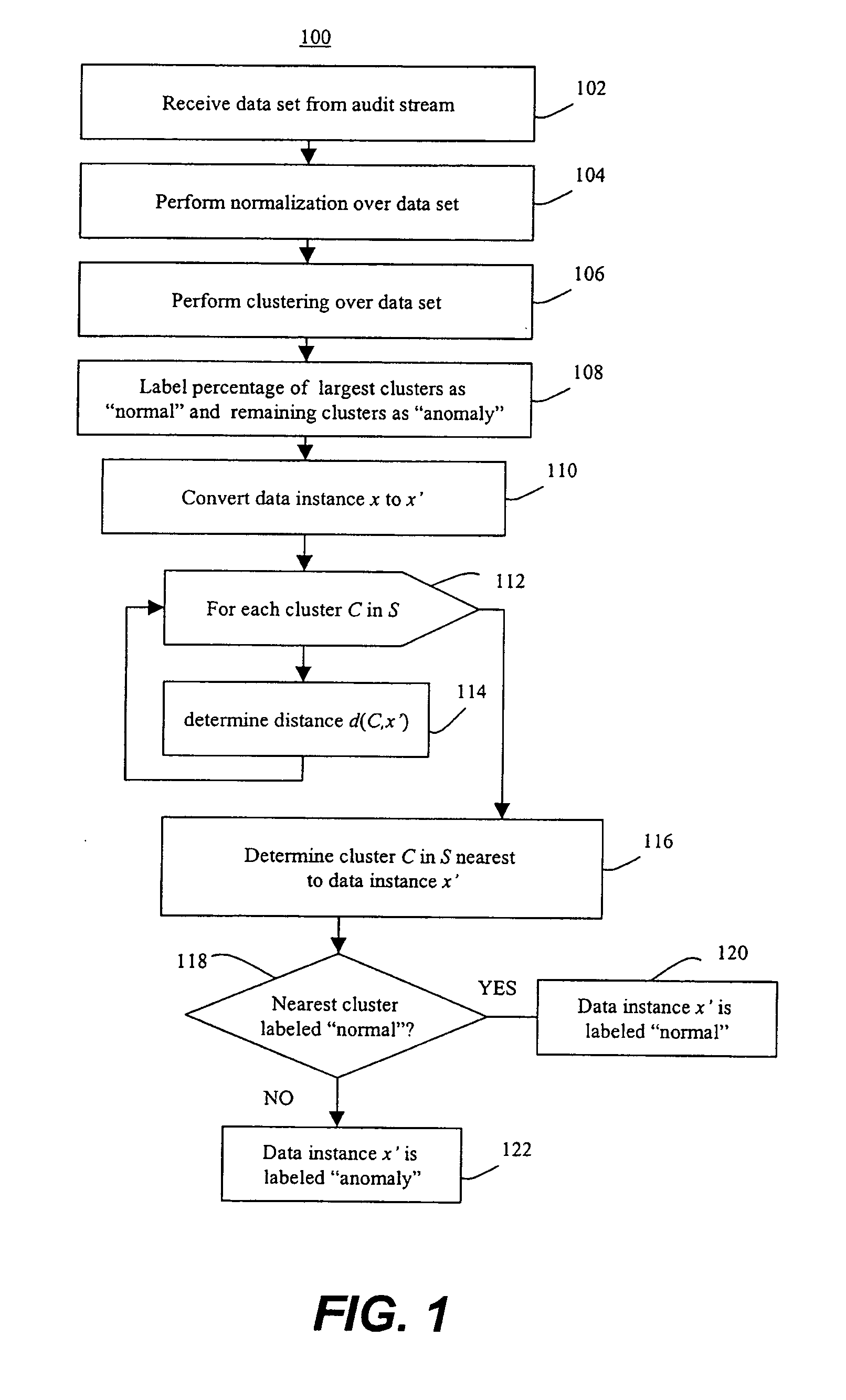
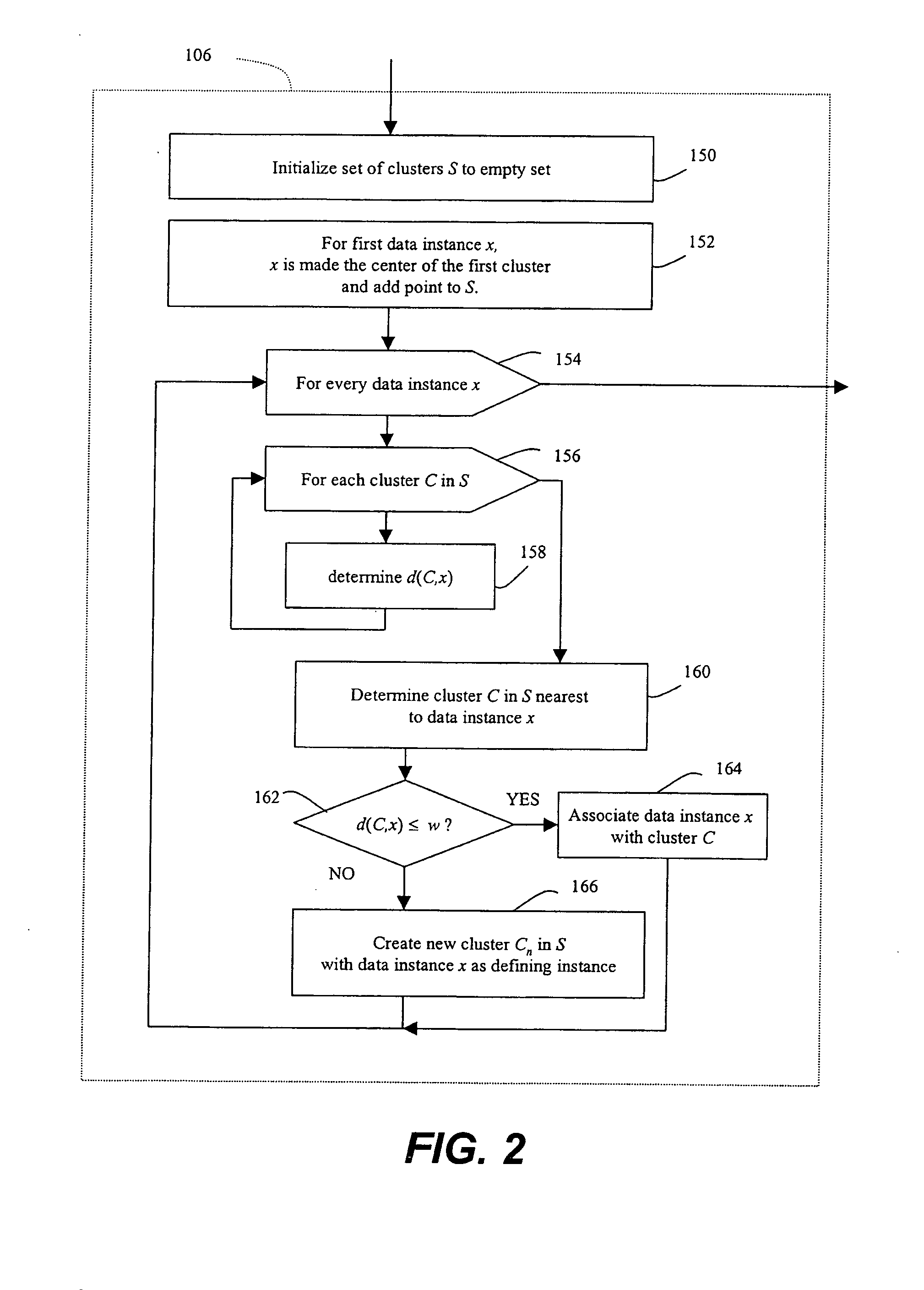
Methods of unsupervised anomaly detection using a geometric framework
ActiveUS8544087B1New typeEasy to operateMemory loss protectionError detection/correctionFrequency spectrumAlgorithm
A method for unsupervised anomaly detection, which are algorithms that are designed to process unlabeled data. Data elements are mapped to a feature space which is typically a vector space . Anomalies are detected by determining which points lies in sparse regions of the feature space. Two feature maps are used for mapping data elements to a feature apace. A first map is a data-dependent normalization feature map which we apply to network connections. A second feature map is a spectrum kernel which we apply to system call traces.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
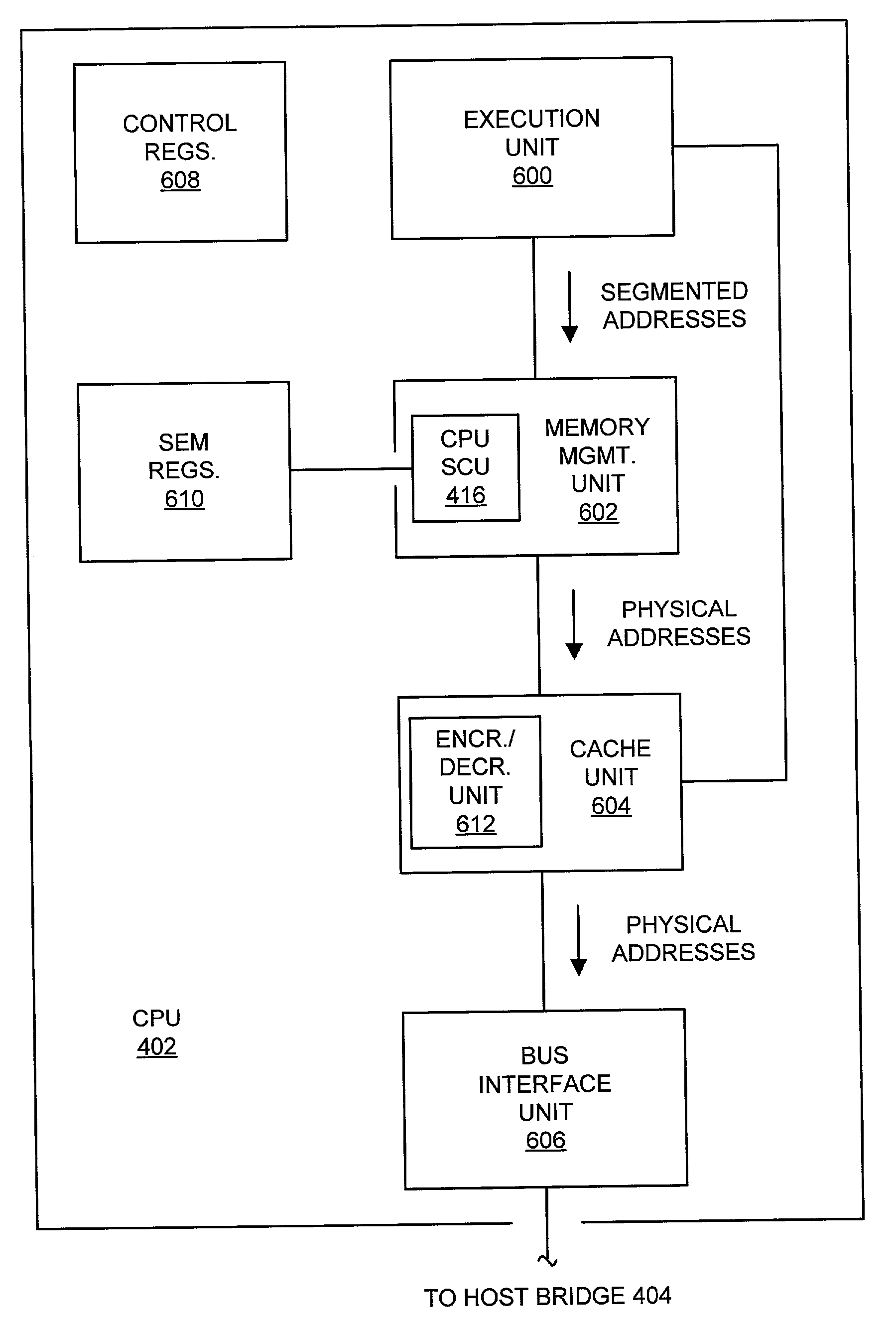
System and method providing region-granular, hardware-controlled memory encryption
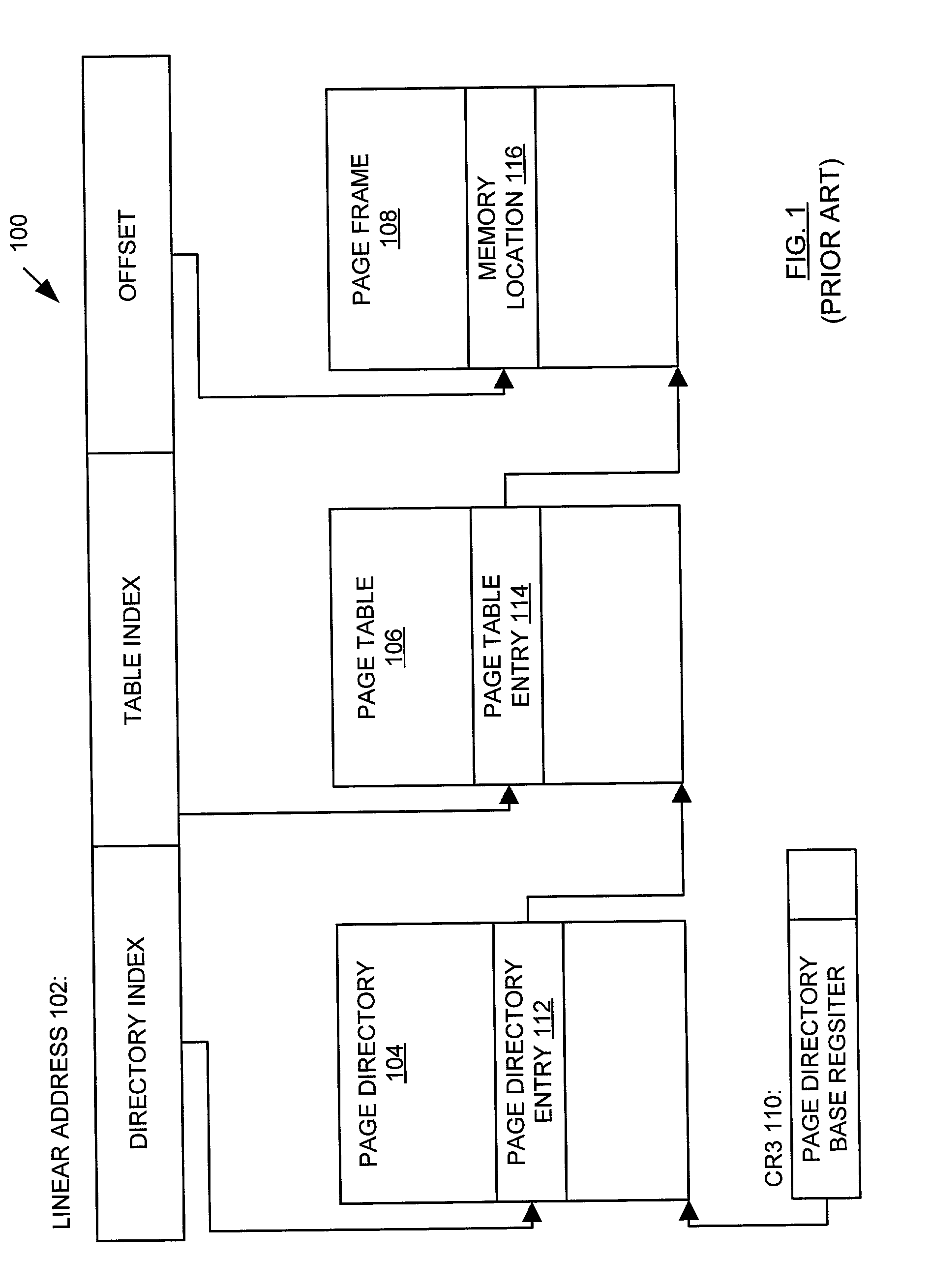
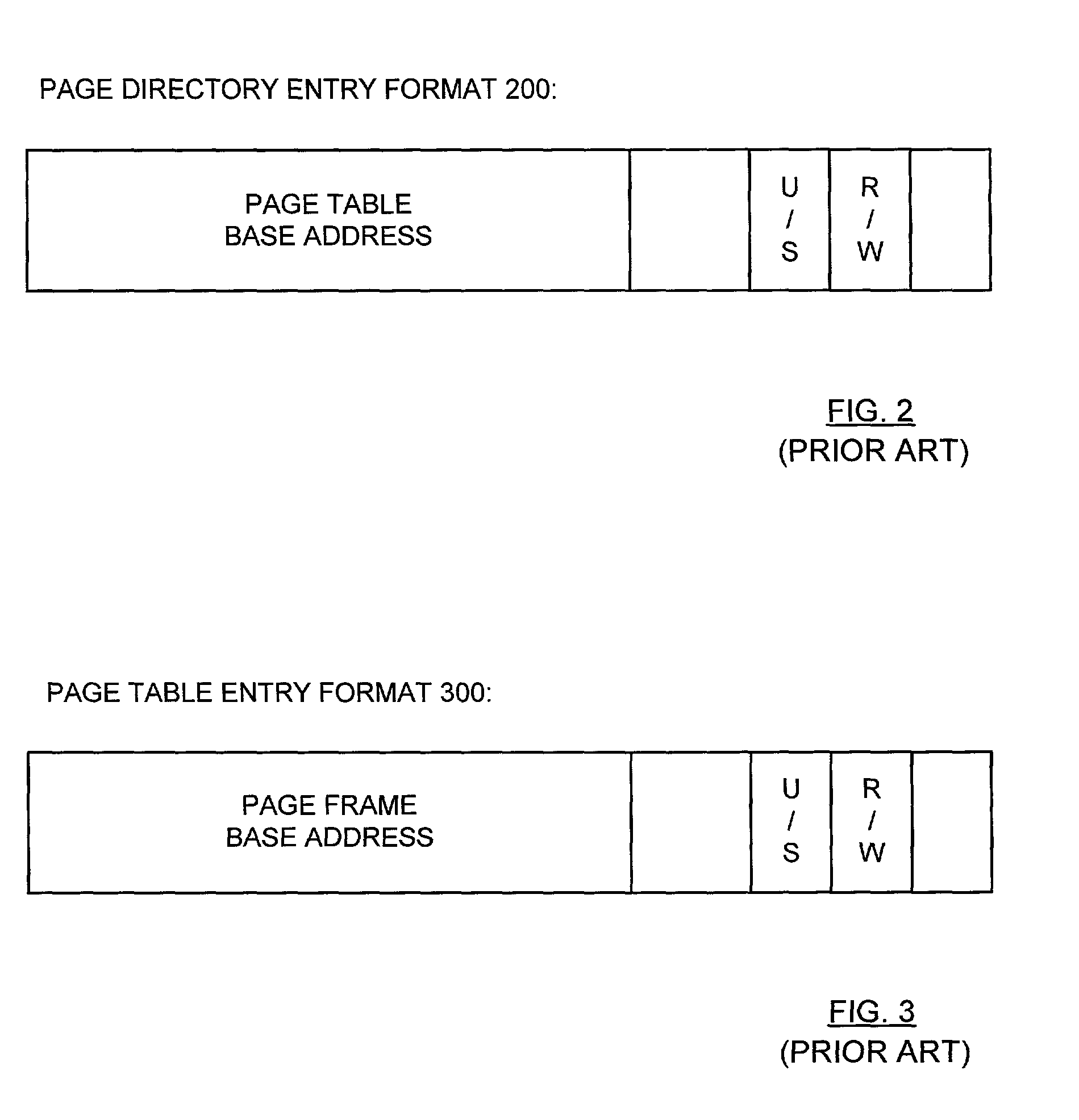
ActiveUS20030188178A1User identity/authority verificationMemory adressing/allocation/relocationControl memoryData dependent
A memory, system, and method for providing security for data stored within a memory and arranged within a plurality of memory regions. The method includes receiving an address within a selected memory region and using the address to access an encryption indicator. The encryption indicator indicates whether data stored in the selected memory page are encrypted. The method also includes receiving a block of data from the selected memory region and the encryption indicator and decrypting the block of data dependent upon the encryption indicator.
Owner:MEDIATEK INC
Using transactional memory with early release to implement non-blocking dynamic-sized data structure
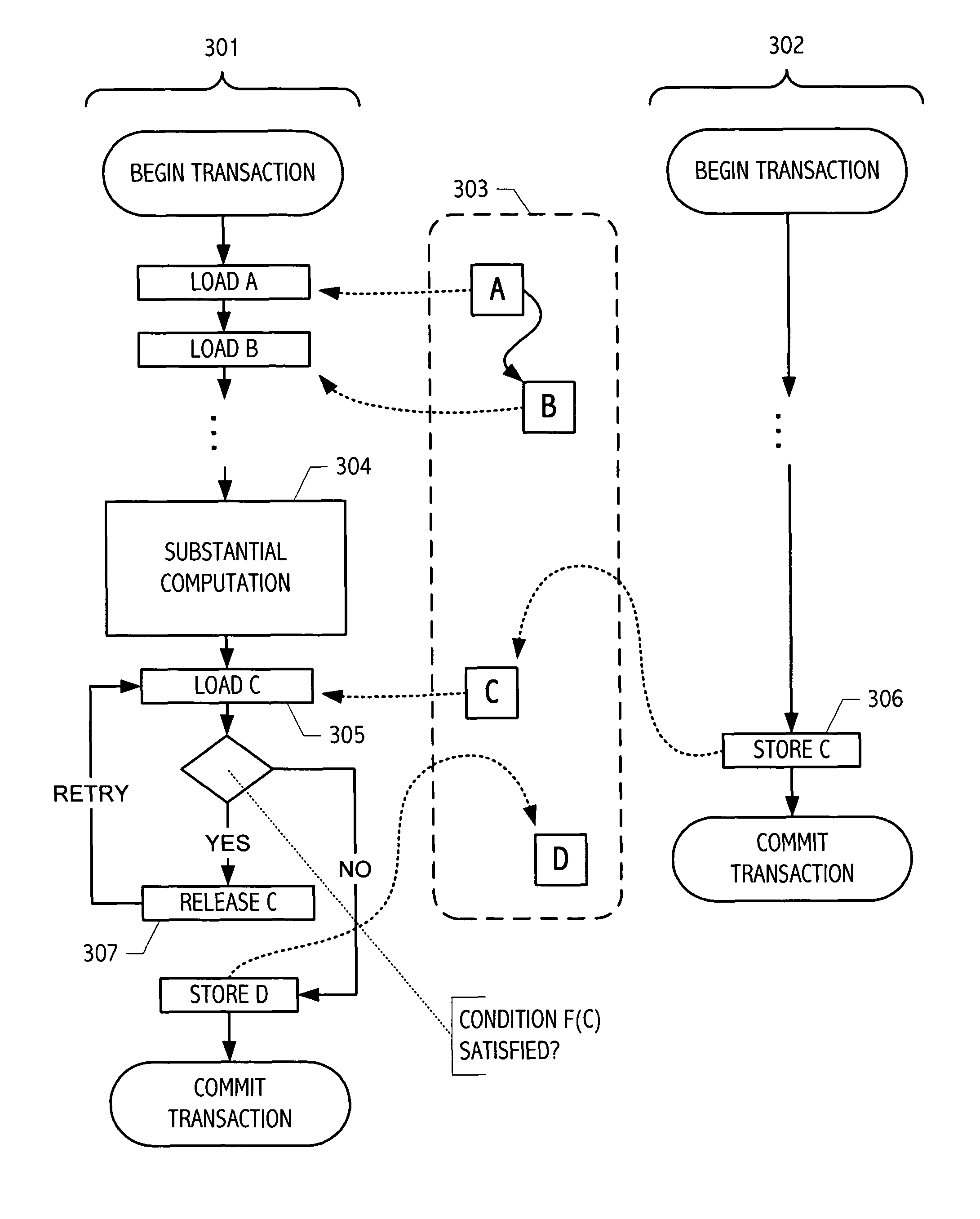
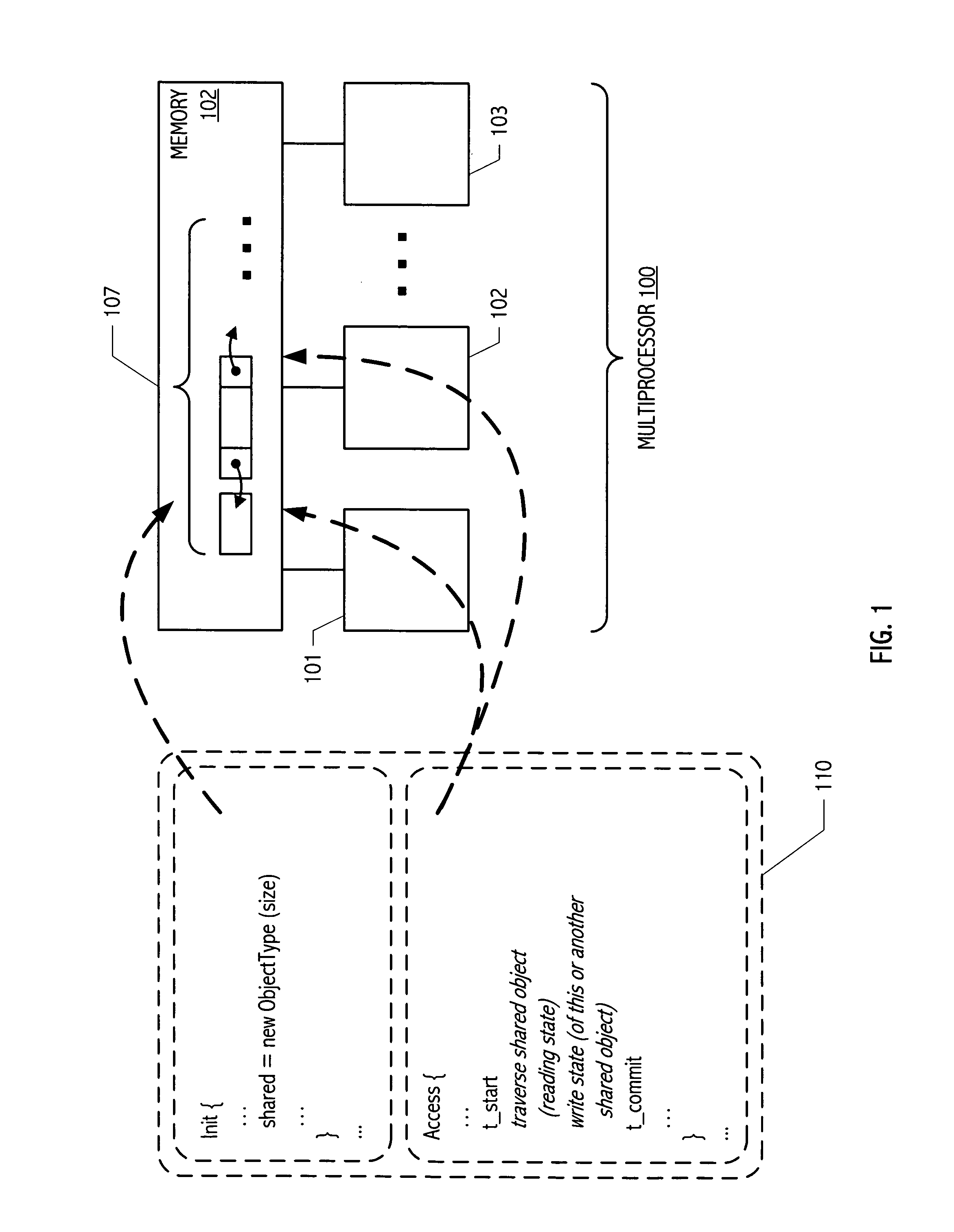
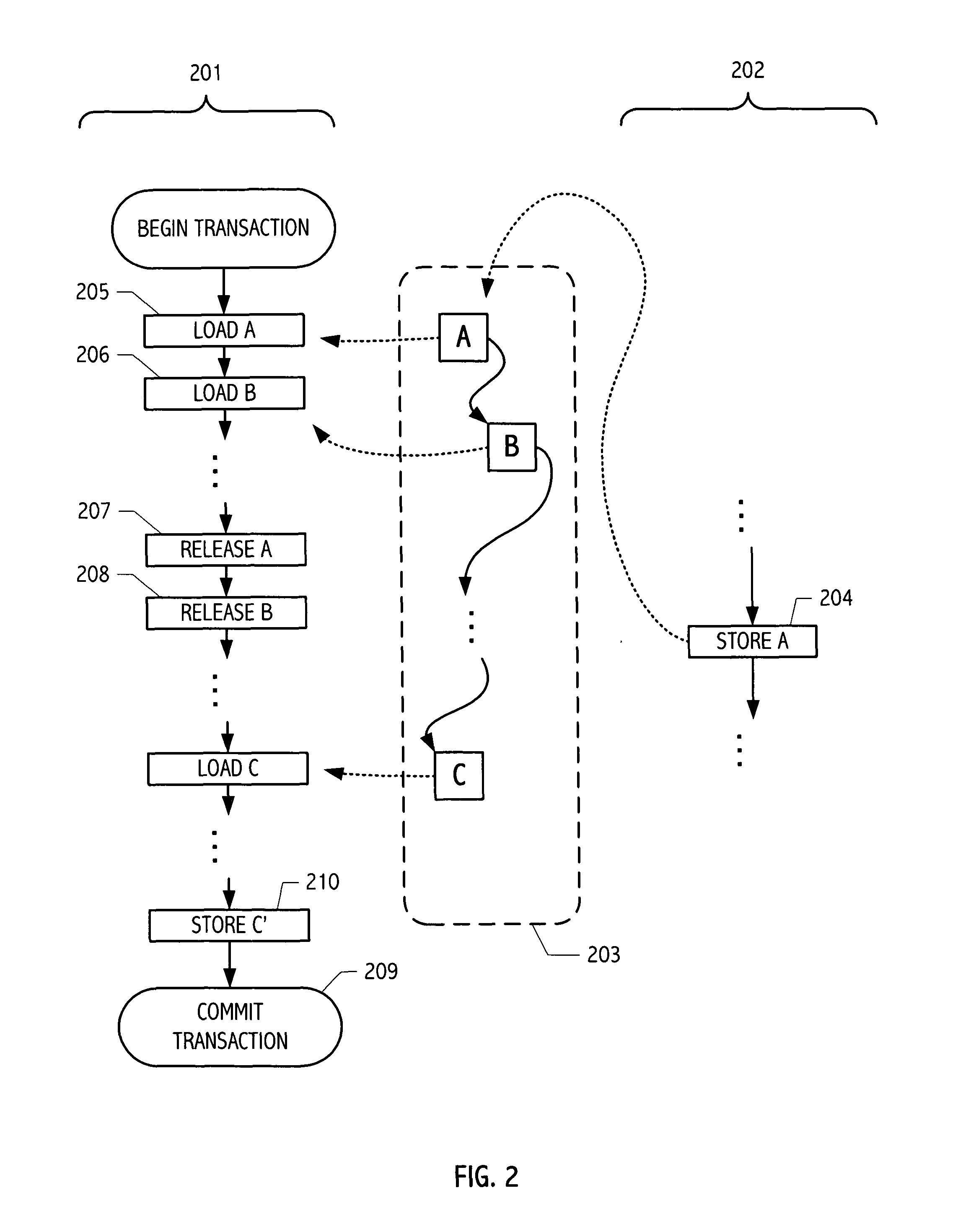
ActiveUS8074030B1Easy to optimizeSimple and convenient coordination facilityMemory systemsTransaction processingEarly releaseData dependent
Owner:ORACLE INT CORP
Method and apparatus for computerized extracting of scheduling information from a natural language e-mail
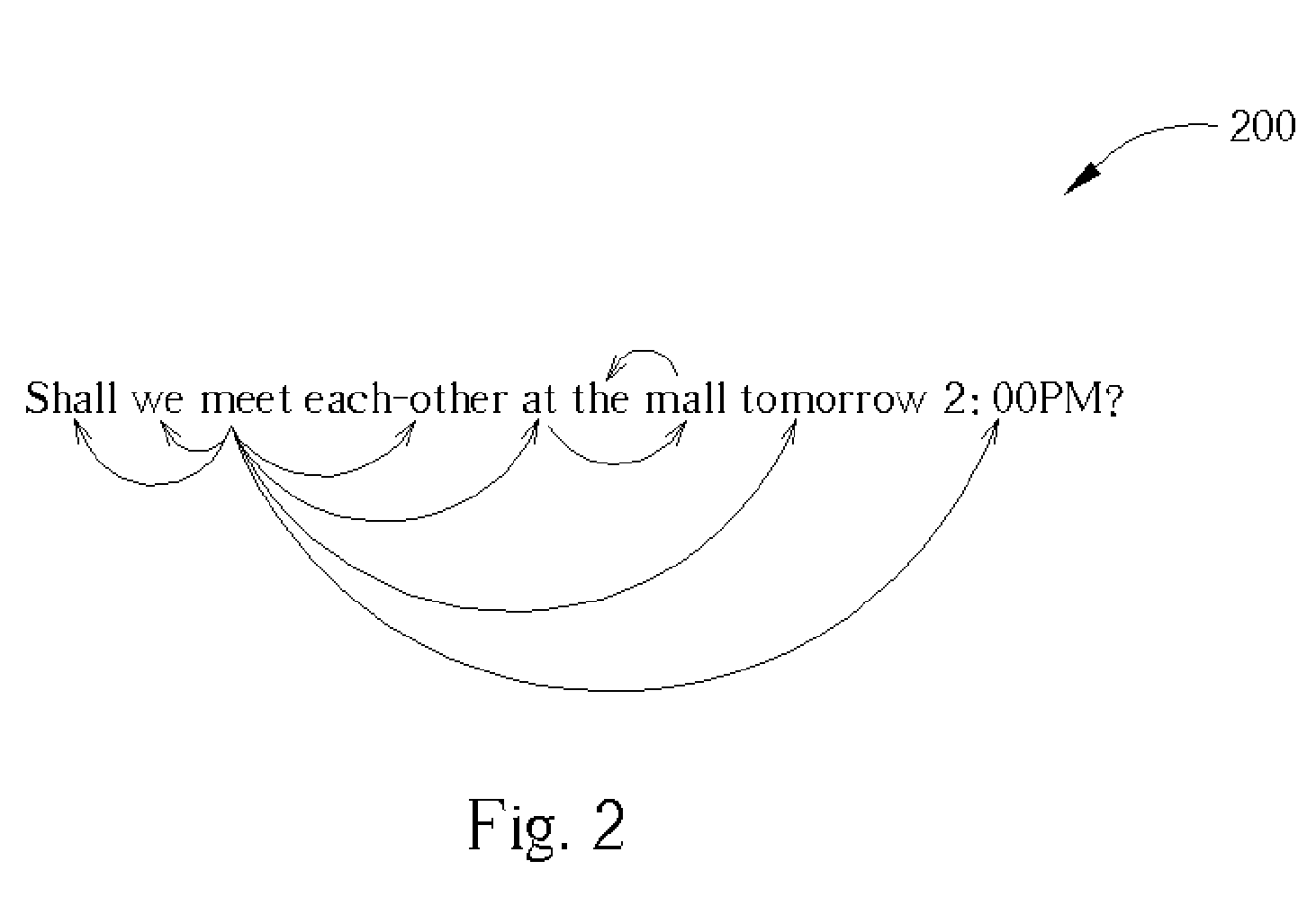
ActiveUS20050076037A1Data processing applicationsNatural language data processingTheoretical computer scienceData dependent
A processor is connected to a storage device storing an incoming e-mail, a dependency database, and code for a calendar application. The dependency database can be built from an e-mail corpus containing a plurality of natural language e-mails containing scheduling information. The incoming e-mail is parsed by the processor to build a dependency tree containing word pairs from the e-mail that are found in the dependency tree. The word pairs are stored as dependency pairs in a tree structure in the dependency tree. A probability sum for the dependency tree is calculated to determine if the e-mail contains scheduling information. If the probability sum exceeds a predetermined value, the e-mail is assumed to contain scheduling information and the scheduling information is extracted from the dependency tree and exported to the calendar application.
Owner:ACER INC
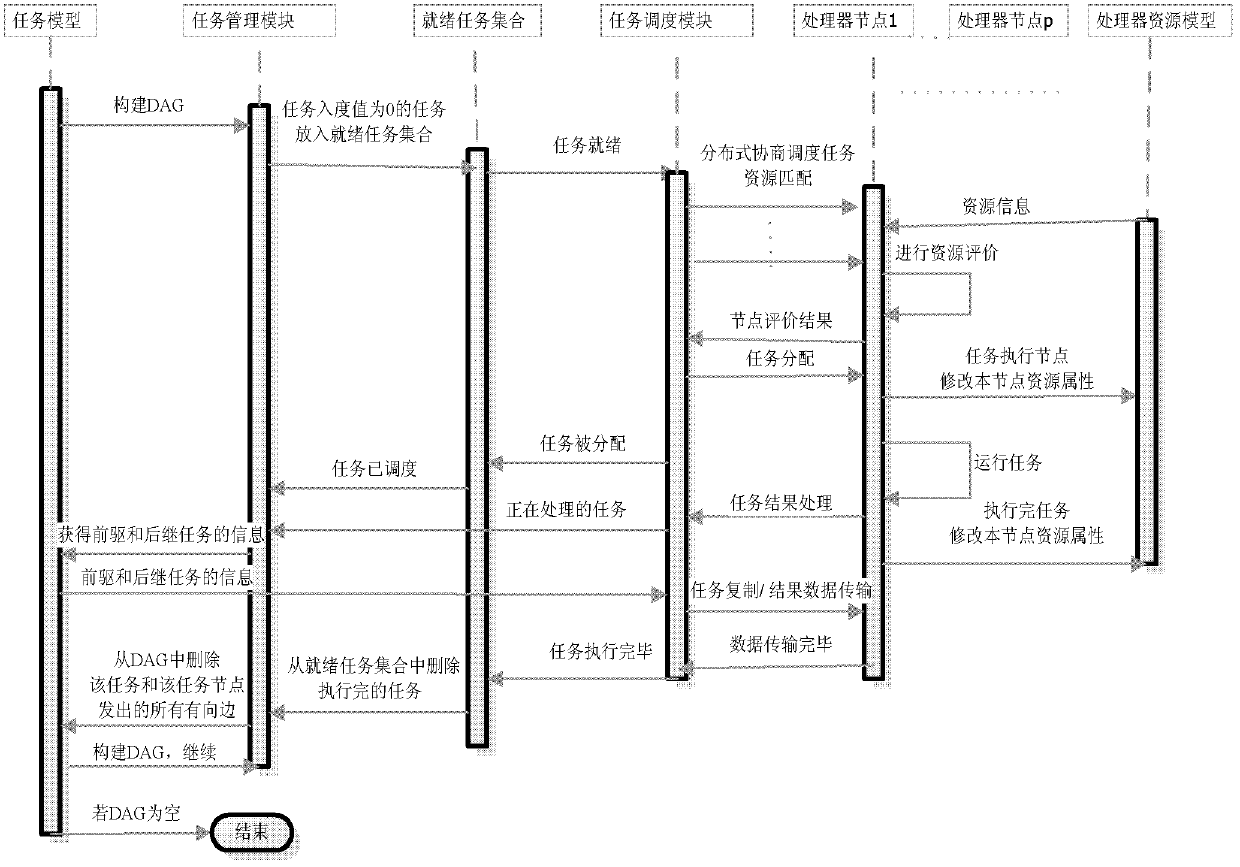
Decoupling parallel scheduling method for rely tasks in cloud computing
InactiveCN102591712AStrong parallelismLoad balancingMultiprogramming arrangementsTransmissionParallel computingPerformance index
The invention belongs to the field of cloud computing application, and relates to method for task rely relation description, decoupling, parallel scheduling and the like in cloud service. Rely task relations are provided, and a decoupling parallel scheduling method of rely tasks are constructed. The method comprises first decoupling the task rely relations with incoming degree being zero to construct a set of ready tasks and dynamically describing tasks capable of being scheduled parallelly at a moment; then scheduling the set of the ready tasks in distribution type and multi-target mode according to real time resource access so as to effectively improve schedule parallelism; and during the distribution of the tasks, further considering task execution and expenditure of communication (E / C) between the tasks to determine whether task copy is used to replace rely data transmission so as to reduce the expenditure of communication. The whole scheduling method can schedule a plurality of tasks in the set of the ready tasks in dynamic parallel mode, well considers performance indexes including real time performance, parallelism, expenditure of communication, loading balance performance and the like, and effectively improves integral performance of the system through the dynamic scheduling strategy.
Owner:DALIAN UNIV OF TECH
Mobile phone network optimisation systems
InactiveUS7941136B2Reduce said mismatchImprove stabilityTransmissionWireless communicationAnalysis dataTelephone network
Owner:ACTIX
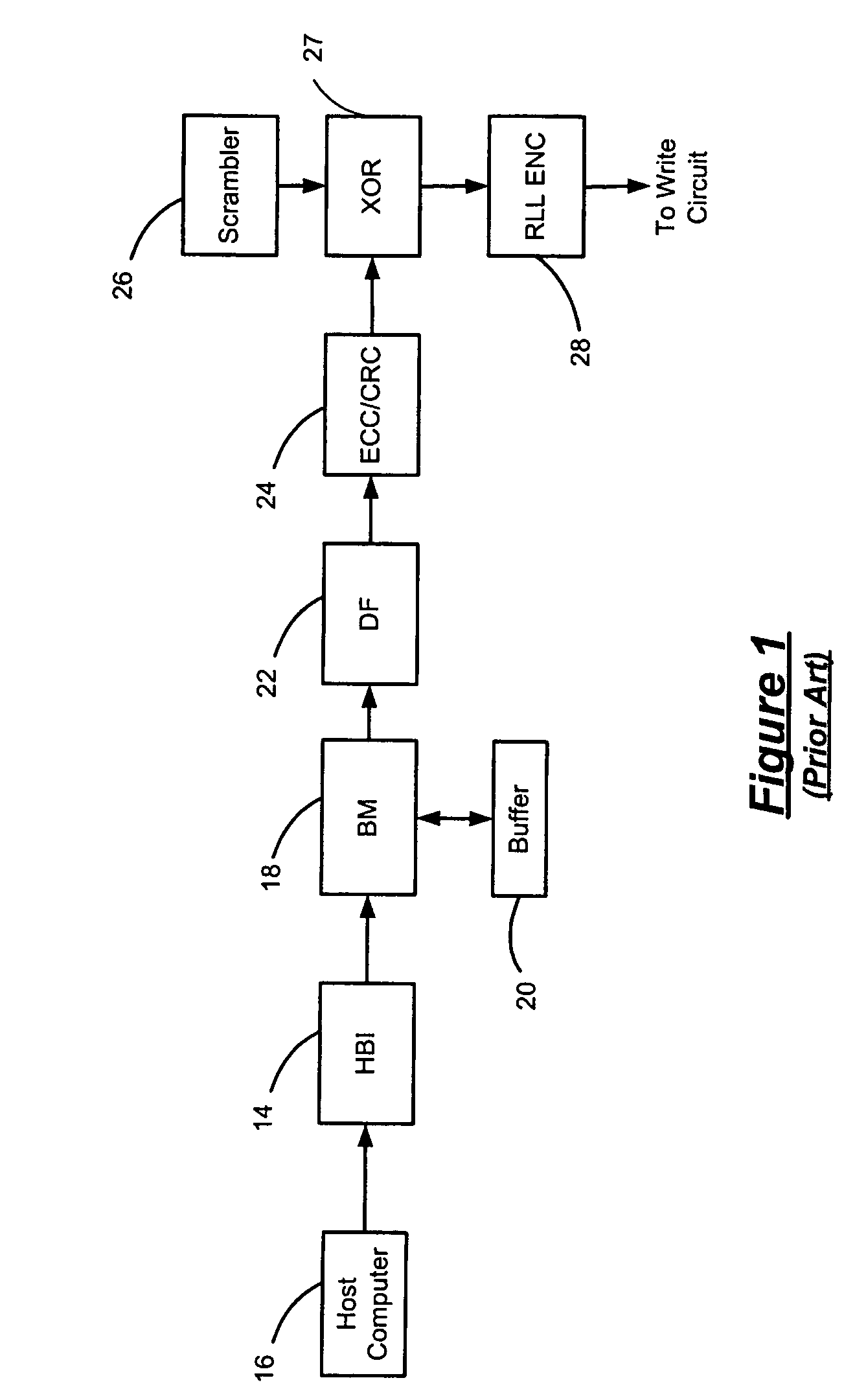
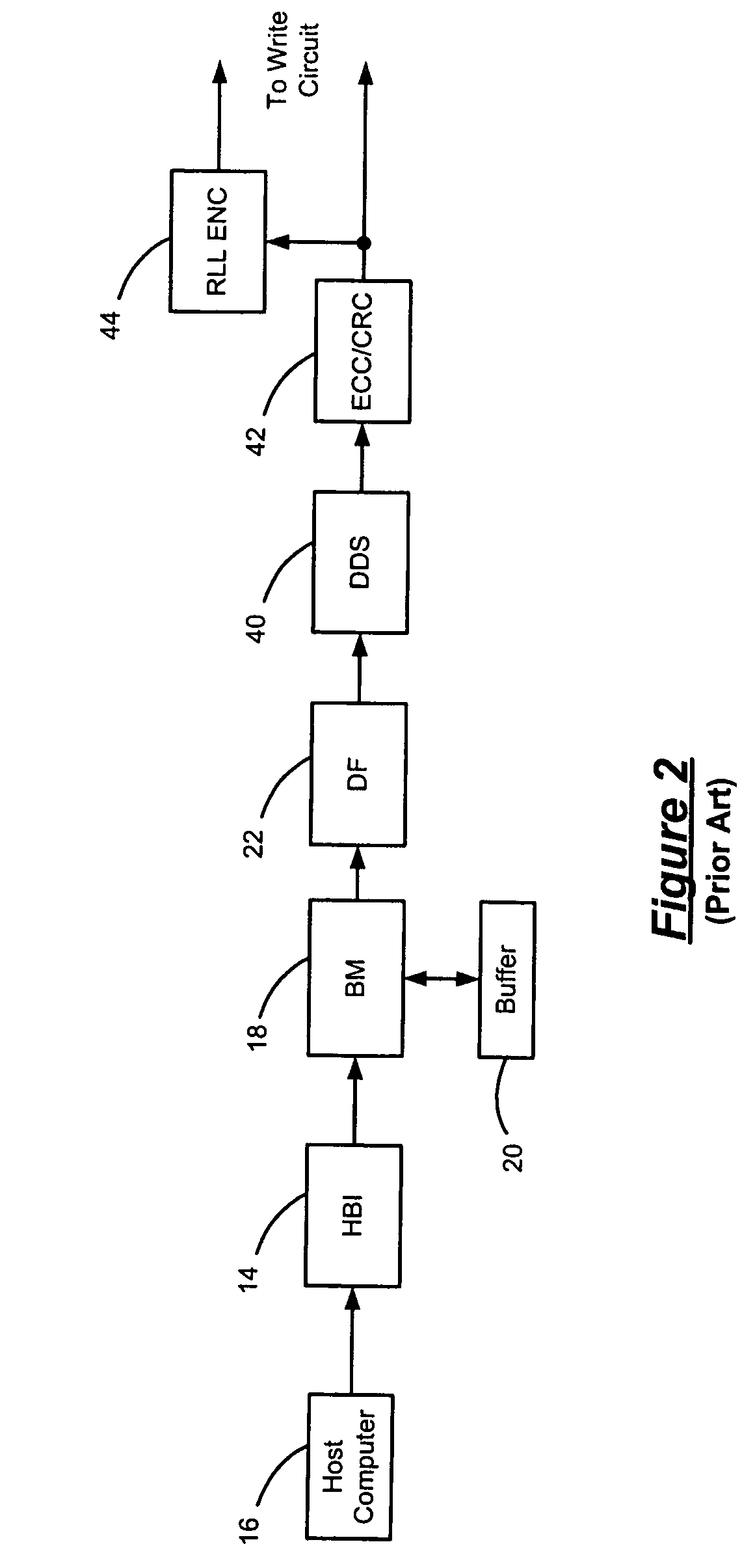
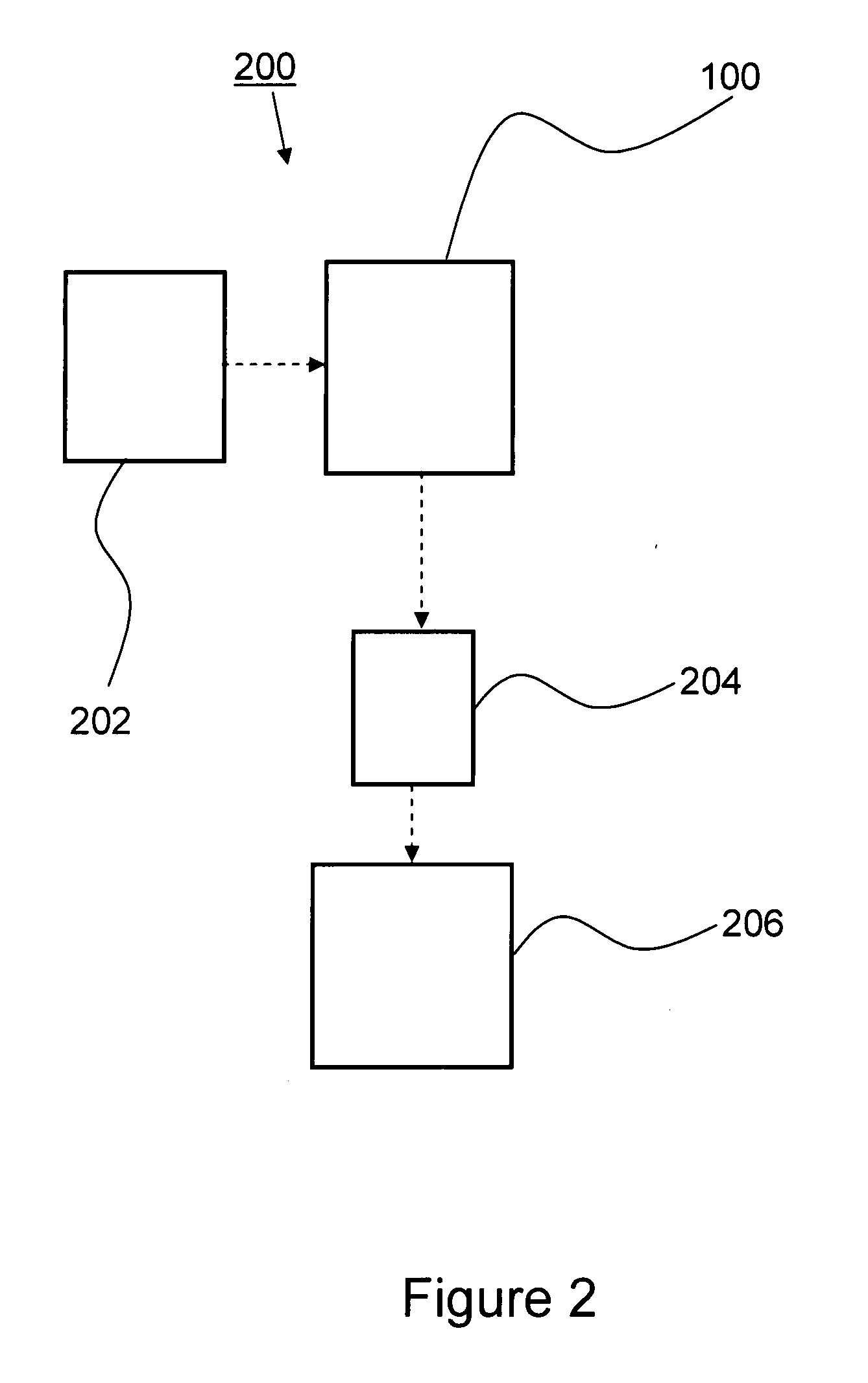
Data dependent scrambler with reduced overhead
ActiveUS7469049B1Data augmentationReduce in quantityTelevision system detailsUser identity/authority verificationData dependentComputer science
A data dependent scrambler for a communications channel that receives a user data sequence including X bits that are organized as N M-bit symbols includes a seed finder that generates a scrambling seed that is dependent upon the symbols in the user data sequence. A first scrambler receives the user data sequence from the data buffer and the scrambling seed from the seed finder and generates the scrambled user data sequence. An H-code finder generates at least one of an H-code token that is dependent upon the symbols in the user data sequence and an offset of the H-code token from the scrambling seed. An H-code encoder receives the scrambled user data sequence and at least one of the H-code token and the offset. The H-code encoder increases a Hamming weight of the scrambled user data sequence using the at least one of the H-code token and the offset.
Owner:MARVELL ASIA PTE LTD
Methods of unsupervised anomaly detection using a geometric framework
InactiveUS20150058982A1Easy to operateMemory loss protectionError detection/correctionFir systemFrequency spectrum
A method for unsupervised anomaly detection, which are algorithms that are designed to process unlabeled data. Data elements are mapped to a feature space which is typically a vector space d. Anomalies are detected by determining which points lies in sparse regions of the feature space. Two feature maps are used for mapping data elements to a feature apace. A first map is a data-dependent normalization feature map which we apply to network connections. A second feature map is a spectrum kernel which we apply to system call traces.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Flash / phase-change memory in multi-ring topology using serial-link packet interface
A multi-ring memory controller sends request packets to multiple rings of serial flash-memory chips. Each of the multiple rings has serial flash-memory chips with serial links in a uni-directional ring. Each serial flash-memory chip has a bypassing transceiver with a device ID checker that bypasses serial packets to a clock re-synchronizer and bypass logic for retransmission to the next device in the ring, or extracts the serial packet to the local device when an ID match occurs. Serial packets pass through all devices in the ring during one round-trip transaction from the controller. The average latency of one round is constant for all devices on the ring, reducing data-dependent performance, since the same packet latency occurs regardless of the data location on the ring. The serial links can be a Peripheral Component Interconnect (PCI) Express bus. Packets have modified-PCI-Express headers that define the packet type and data-payload length.
Owner:SUPER TALENT ELECTRONICS
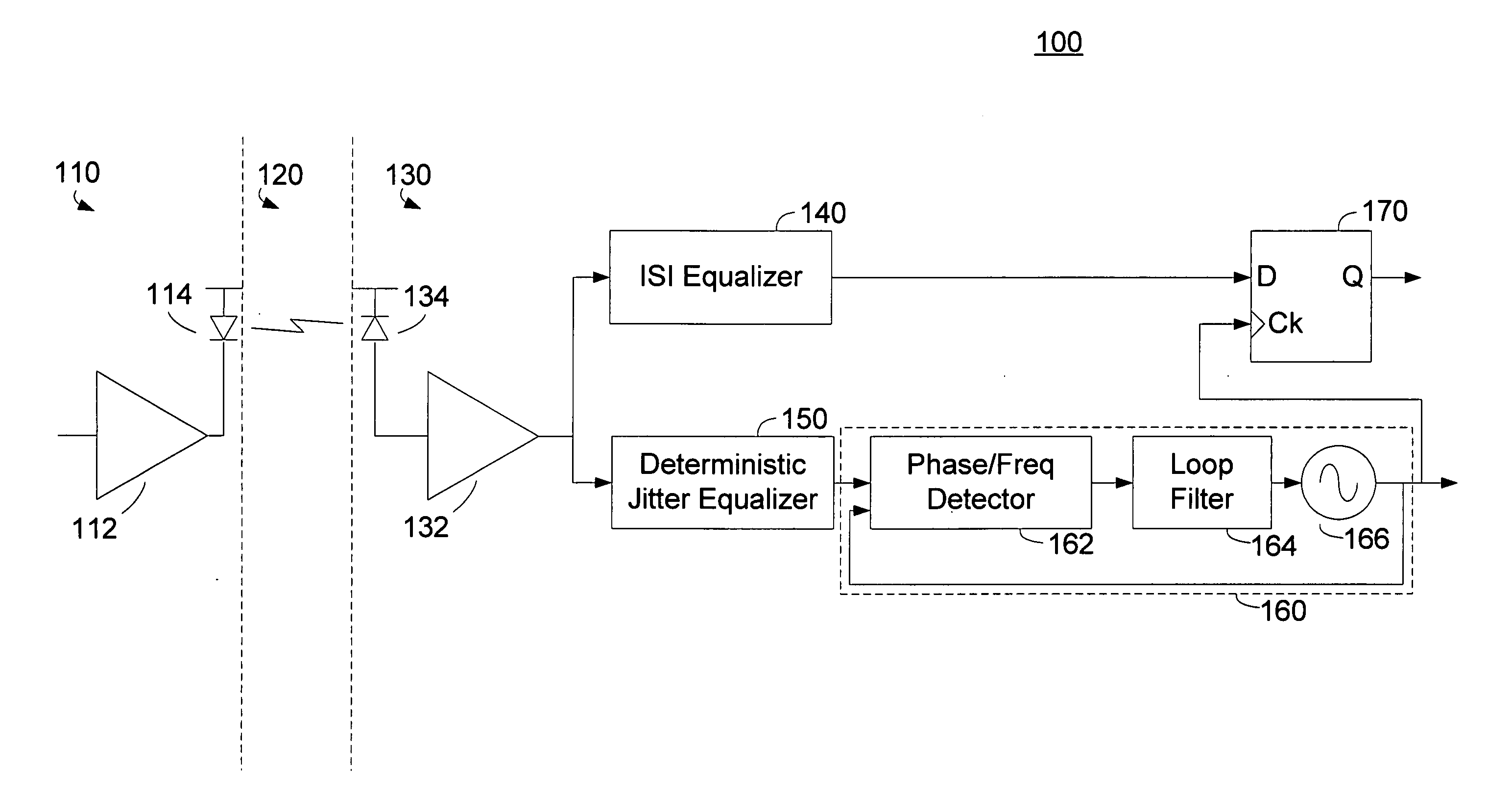
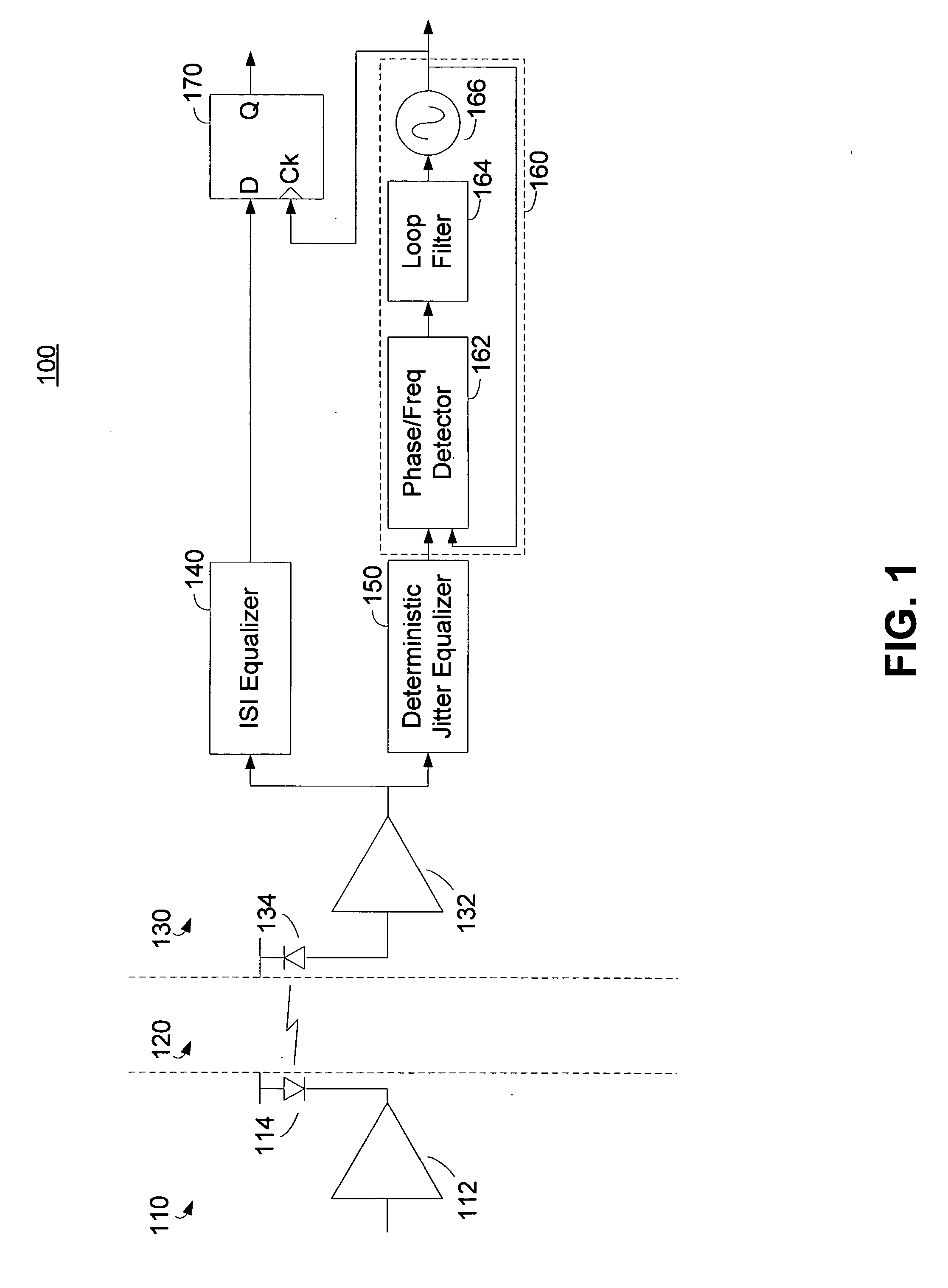
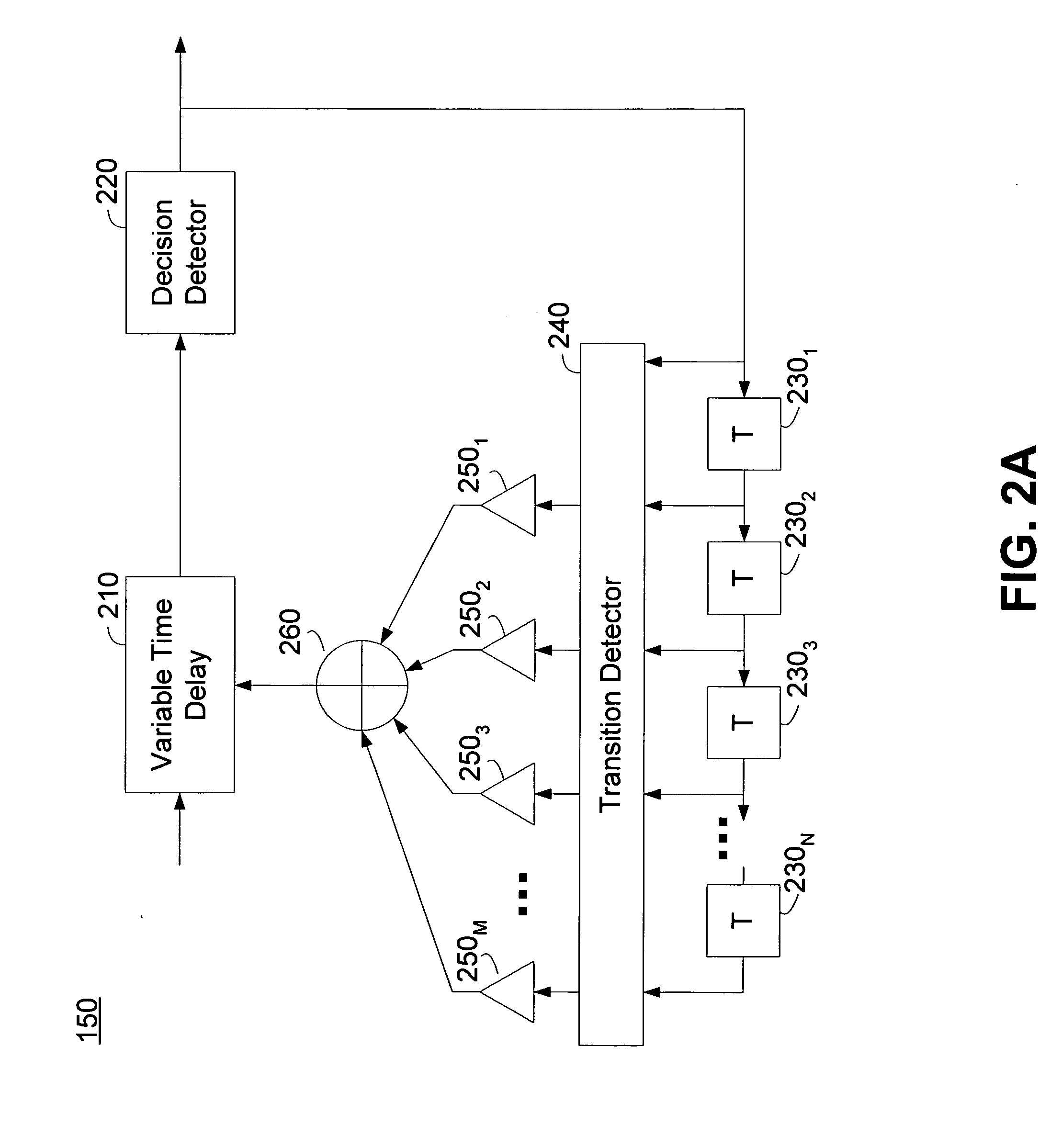
Deterministic jitter equalizer
ActiveUS20050152488A1Easy to implementImprove phase noiseMultiple-port networksError detection/prevention using signal quality detectorData streamDuty cycle distortion
An equalizer for serial data communications can be configured to compensate for the effects of deterministic jitter. The equalizer can be configured to compensate a received serial data stream for the effects of data-dependent jitter as well as duty cycle distortion jitter. The equalizer can be configured to determine the value of one or more previously received symbols and compare them to a recovered symbol. The equalizer can adjust a variable delay positioned in the serial data path to introduce a delay into the data path that is based in part on the received data stream. The equalizer can be configured to vary the delay when any of the one or more previously received symbols is different from the recovered symbol, and can be configured to maintain a constant delay if the one or more previously received symbols is the same as the recovered symbol.
Owner:CALIFORNIA INST OF TECH
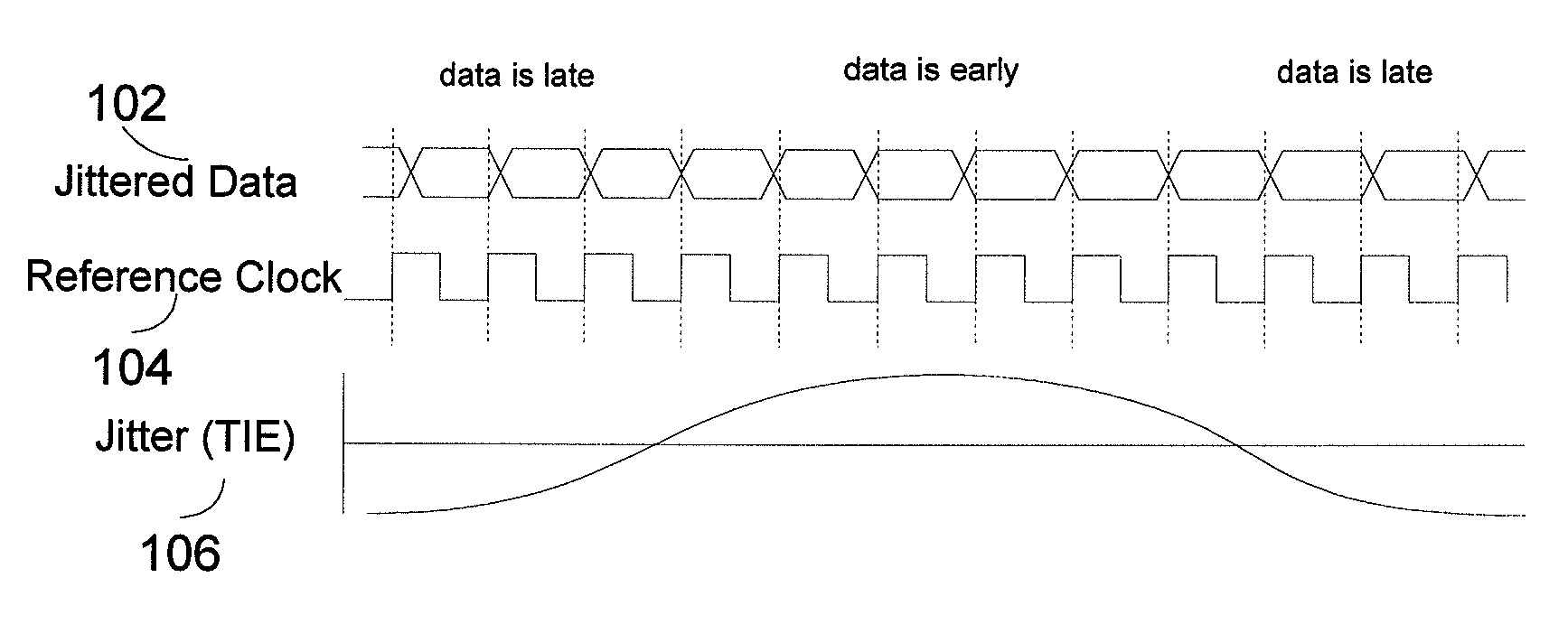
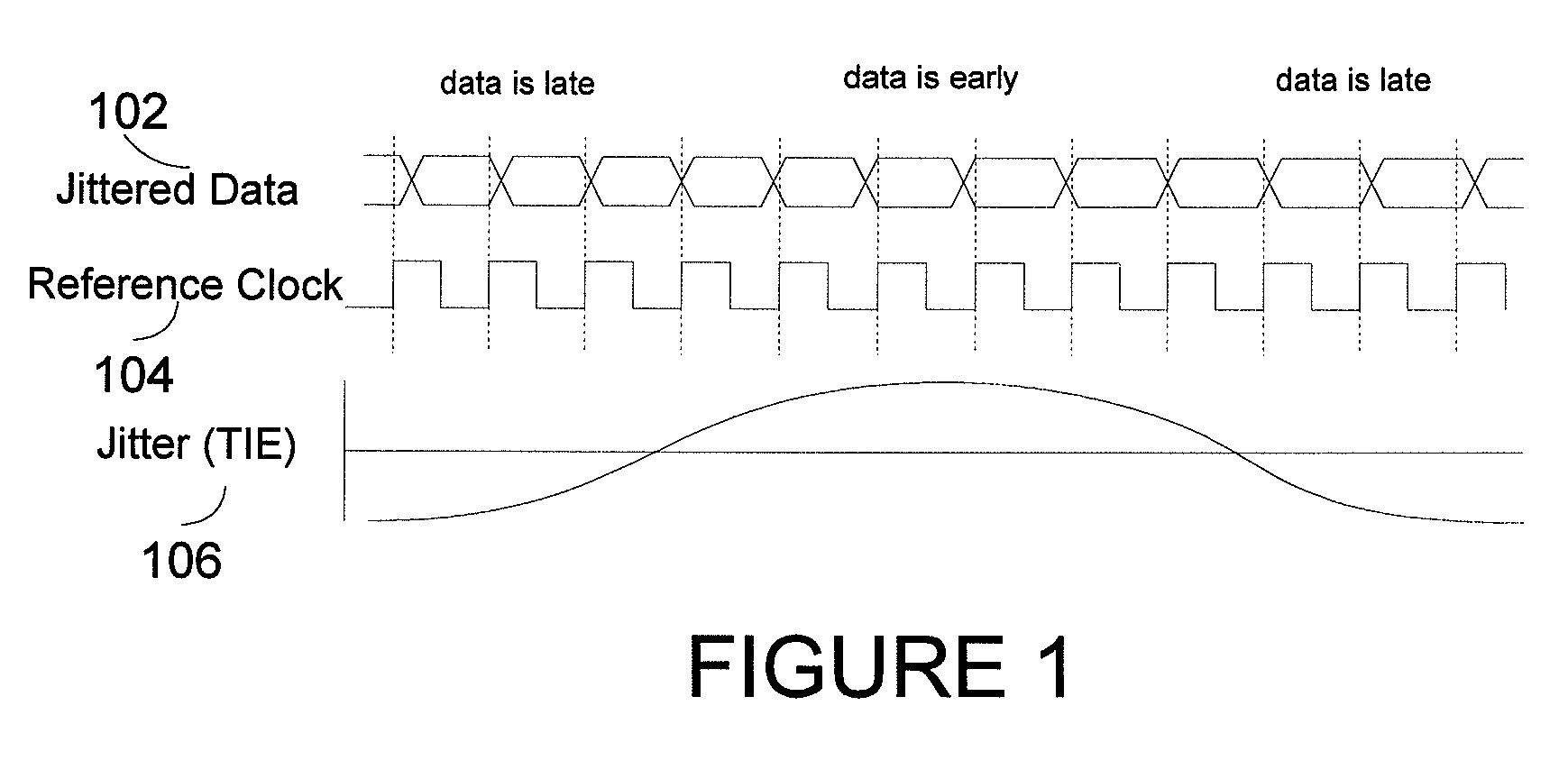
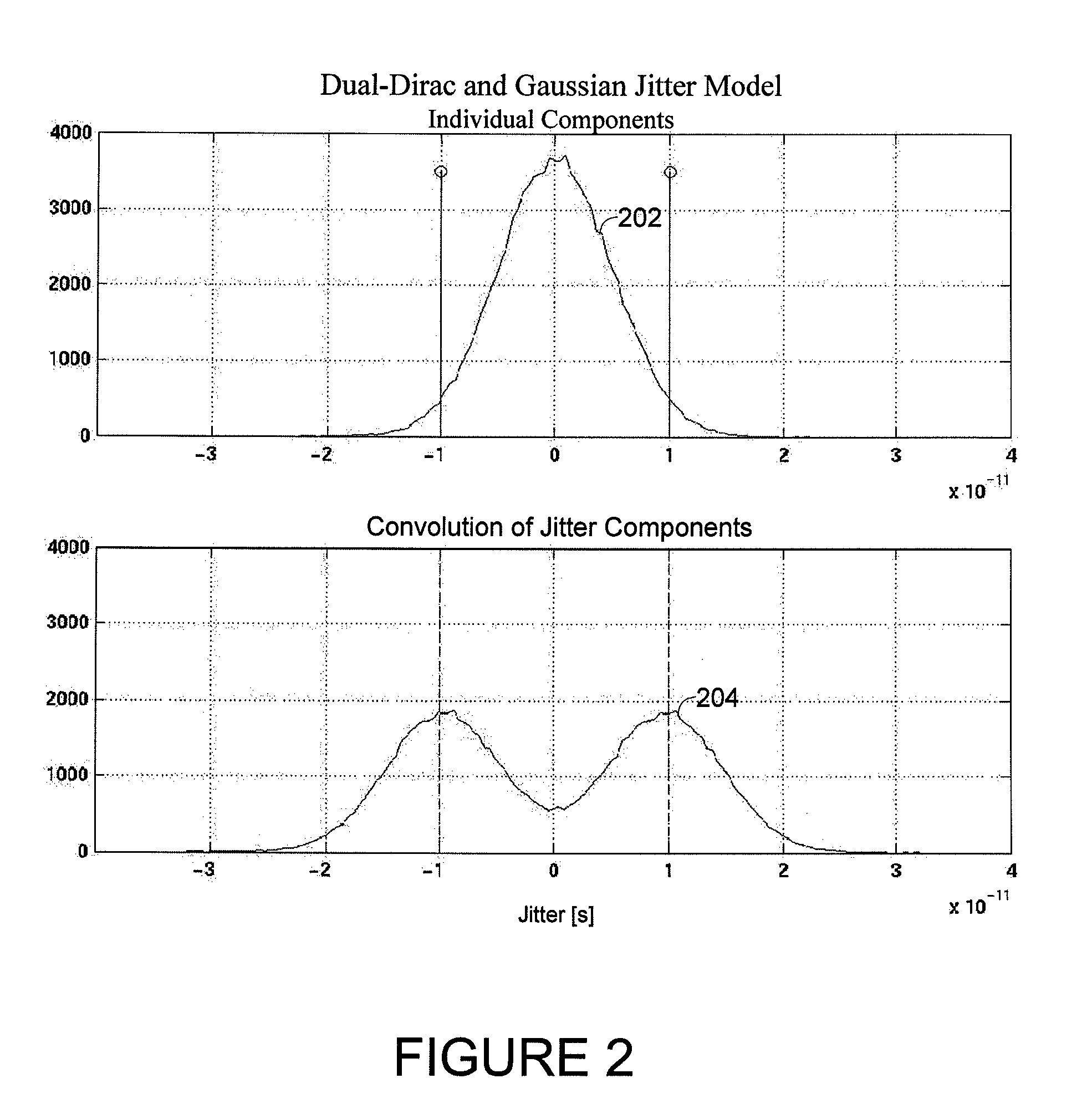
Systems and methods for jitter analysis of digital signals
InactiveUS7388937B1Accurate identificationFacilitates decomposition and quantificationError preventionLine-faulsts/interference reductionState dependentData dependent
Systems and methods for analyzing the jitter content of an oversampled digital communication signal are disclosed. Advantageously, the communication signal can correspond to an arbitrary data sequence, rather than only to a repeating test sequence. For example, the systems and methods can be embodied in test equipment and in simulation equipment as design tools and / or validation tools. The systems and methods disclosed advantageously facilitate the decomposition and quantification of the main jitter components (random and deterministic), as well as its various subcomponents (periodic jitter, data-dependent jitter, inter-symbol interference, device-state-dependent jitter, other bounded uncorrelated jitter, and data-dependent-random jitter).
Owner:MICROSEMI STORAGE SOLUTIONS
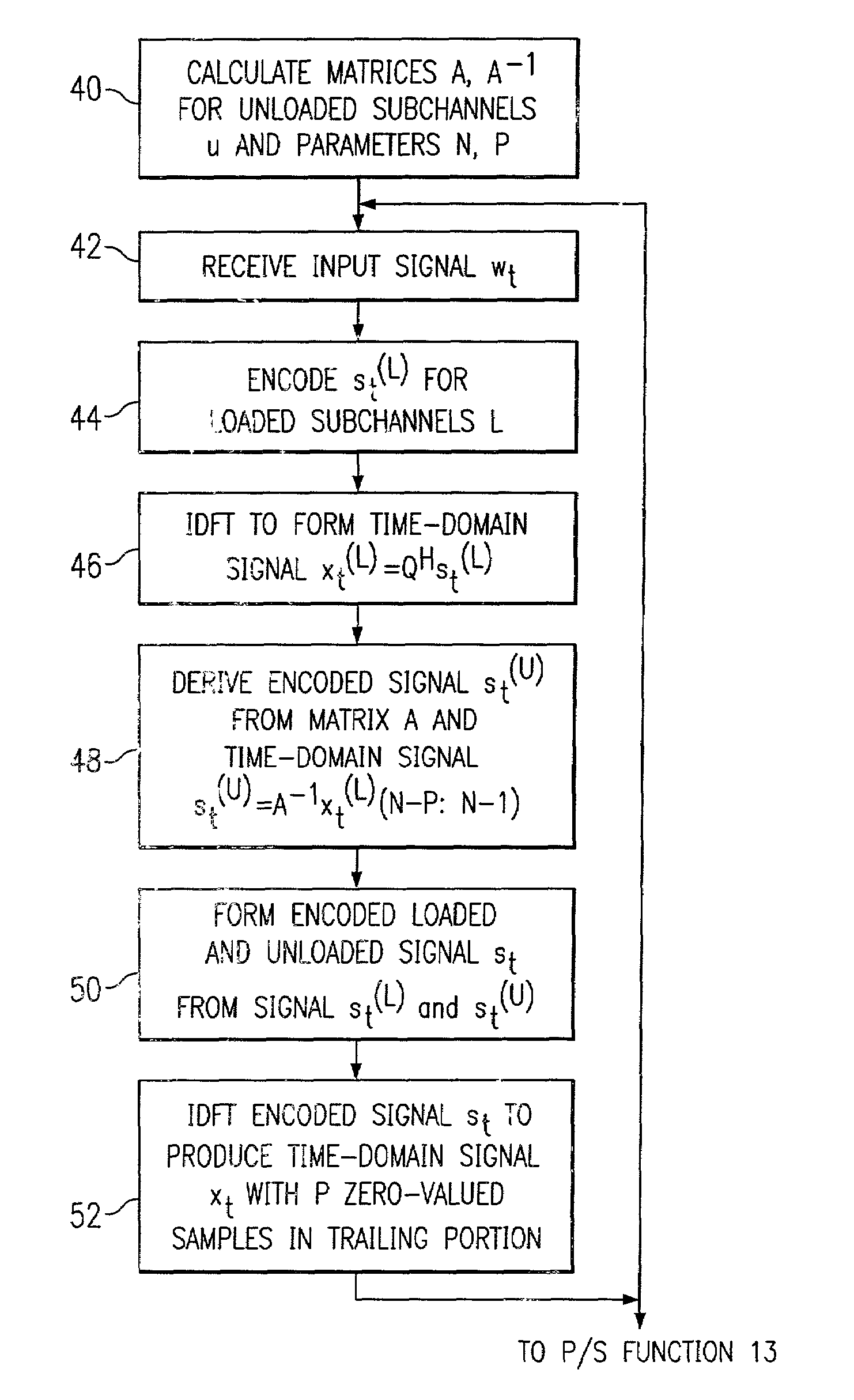
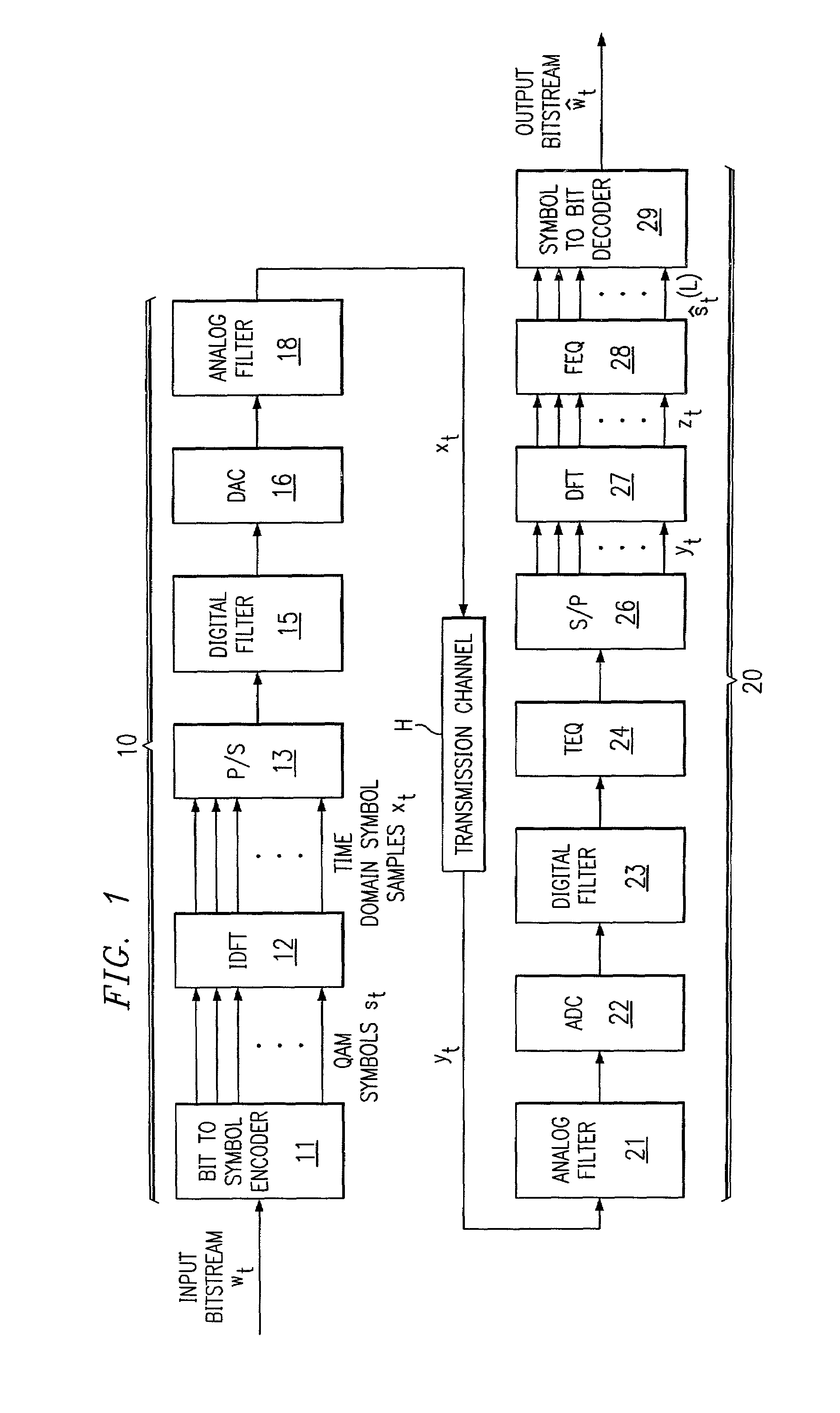
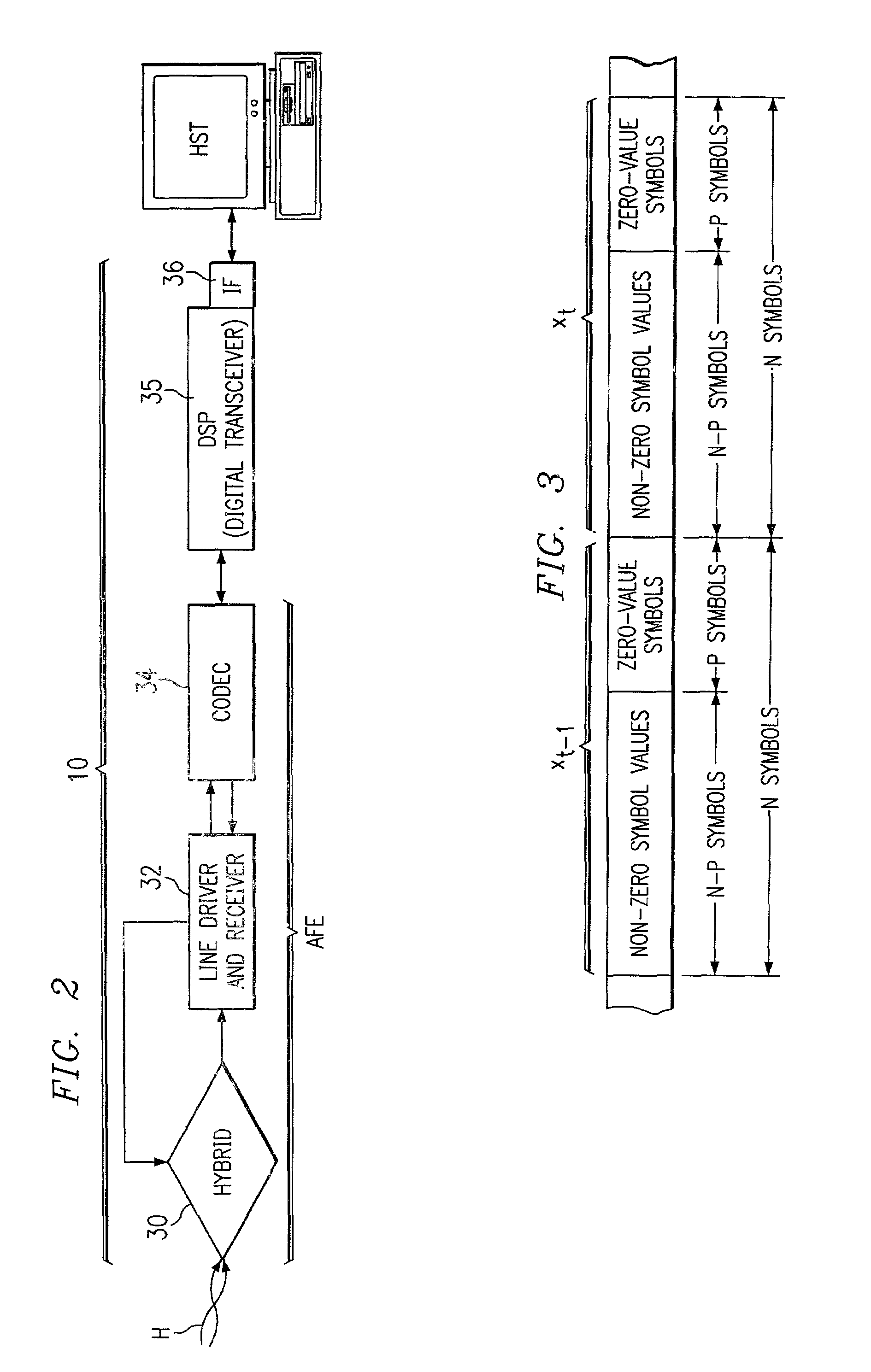
Multicarrier modulation with data dependent frequency-domain redundancy
ActiveUS7075999B2Eliminate distractionsIncreasing data rate lossSecret communicationMulti-frequency code systemsData streamModem device
A modem (10) for transmitting a discrete multitone modulated (DMT) signal over a communications channel (H) is disclosed. In the encoding of an input bitstream, unloaded subchannels in the DMT spectrum are assigned signal values so that a trailing portion of each block or frame of the resulting datastream are forced to a known value, for example zero. The known-valued trailing portion of each block provides the effect of a cyclic prefix, without necessitating the prepending of an actual cyclic prefix and incurring the corresponding data rate loss; alternatively, the effect of a cyclic prefix can be augmented by the forcing of the trailing portion of the blocks to known values.
Owner:TEXAS INSTR INC
In-flow packet prioritization and data-dependent flexible QOS policy
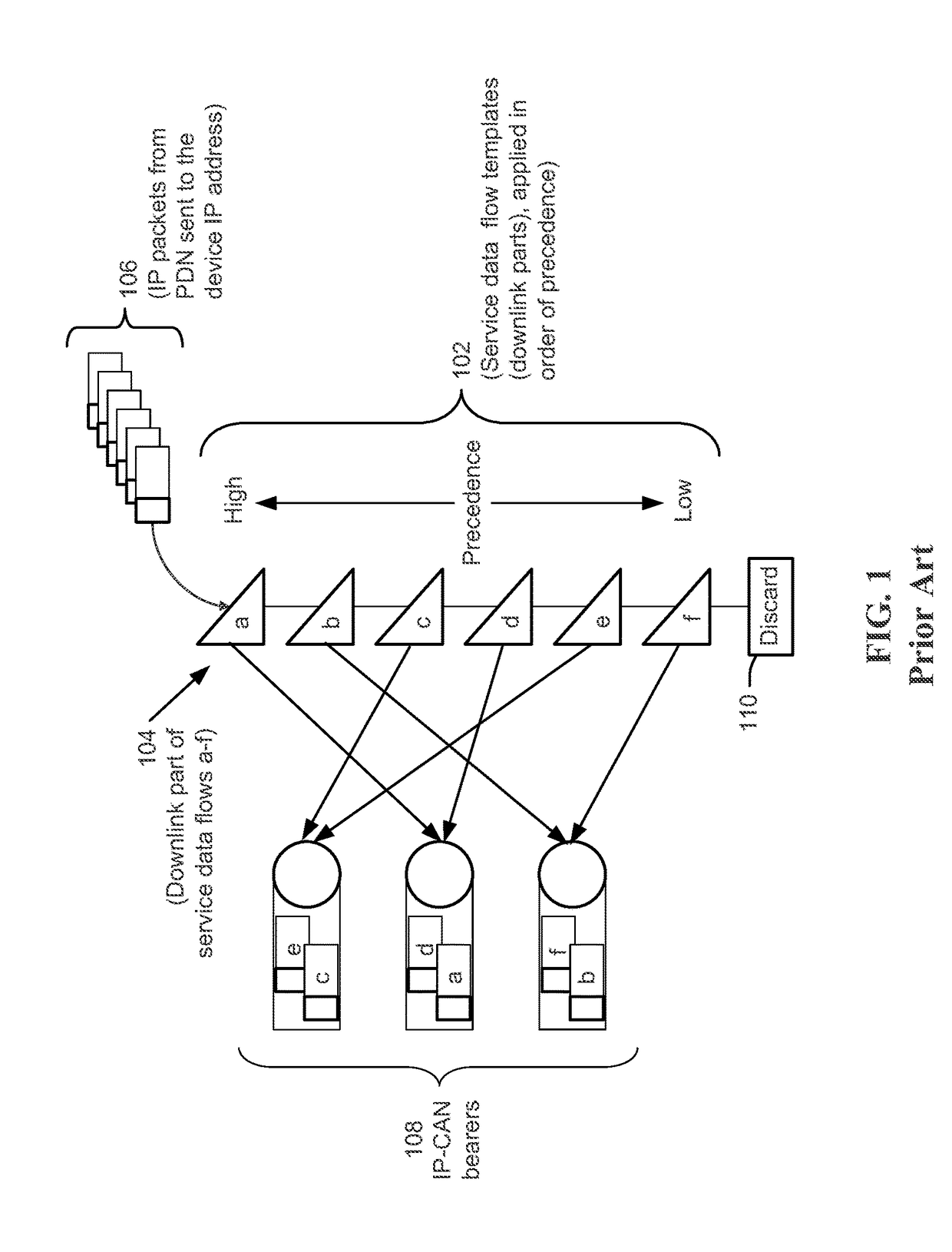
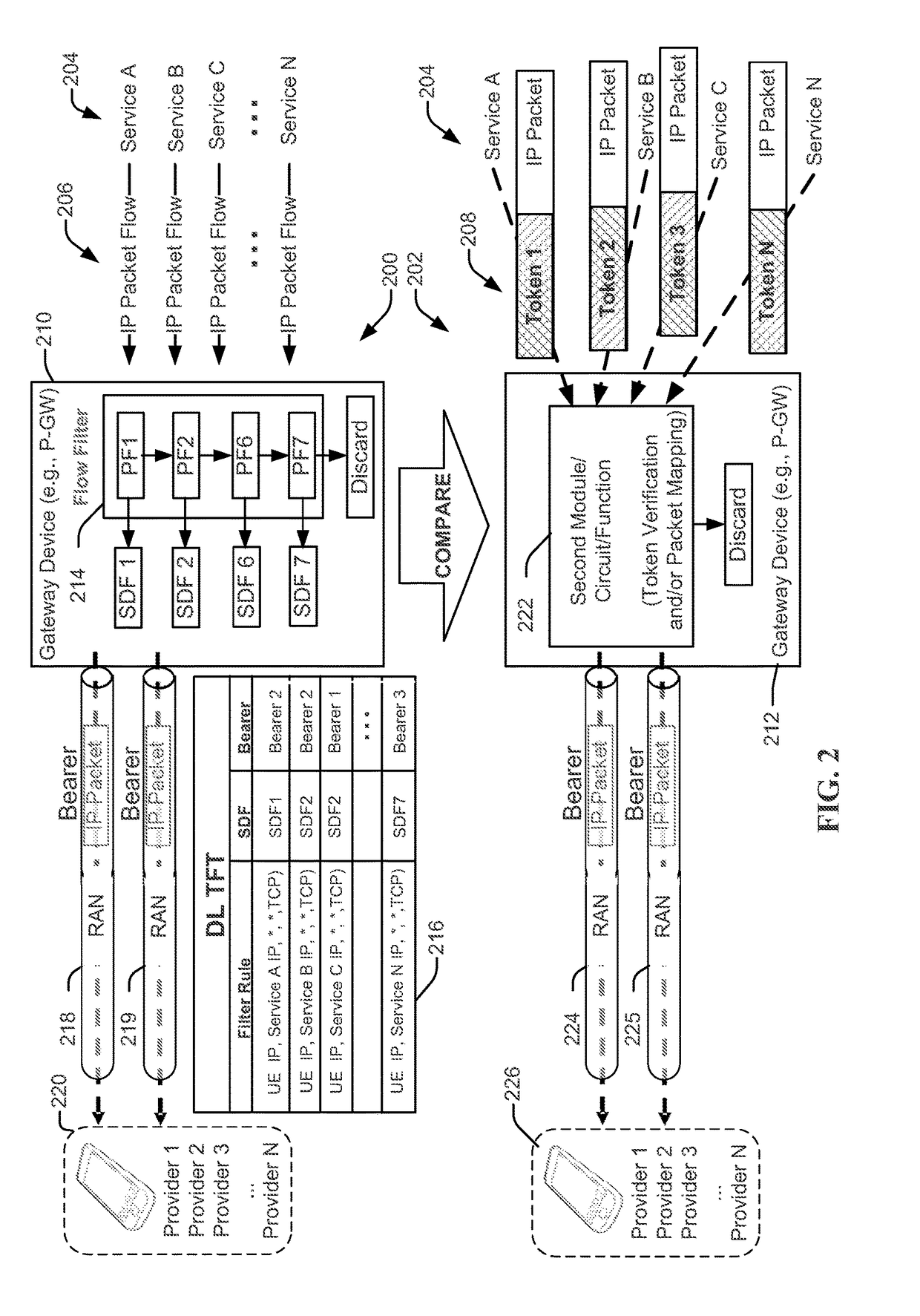
ActiveUS20170324652A1Well formedNetwork traffic/resource managementNetwork topologiesData dependentReal-time computing
A method, operational at a device, includes receiving at least one packet belonging to a first set of packets of a packet flow marked with an identification value, determining that the at least one packet is marked with the identification value, determining to change a quality of service (QoS) treatment of packets belonging to the first set of packets marked with the identification value that are yet to be received, and sending a request to change the QoS treatment of packets belonging to the first set of packets marked with the identification value that are yet to be received to trigger a different QoS treatment of packets within the packet flow, responsive to determining to change the QoS treatment. Other aspects, embodiments, and features are also claimed and described.
Owner:QUALCOMM INC
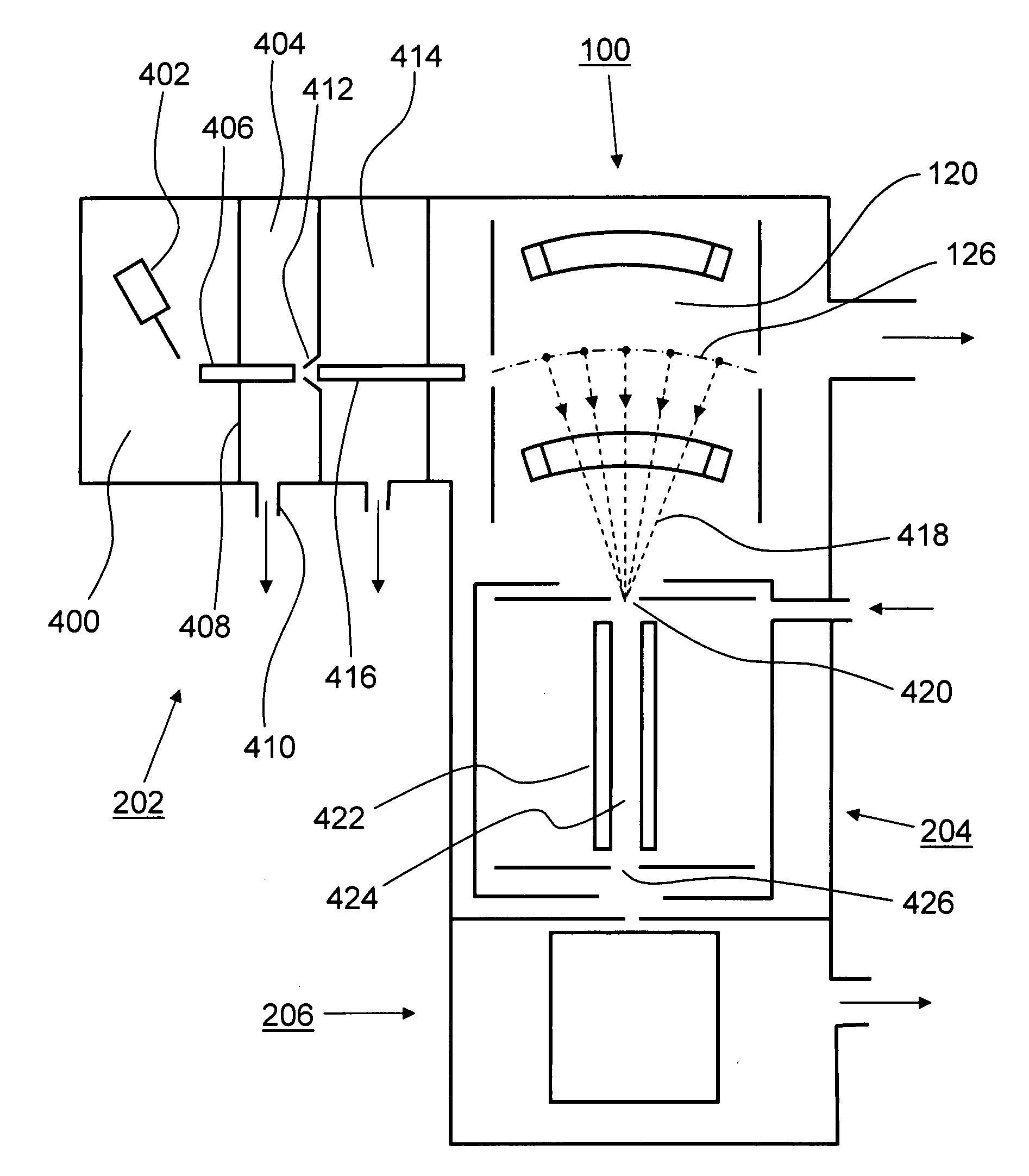
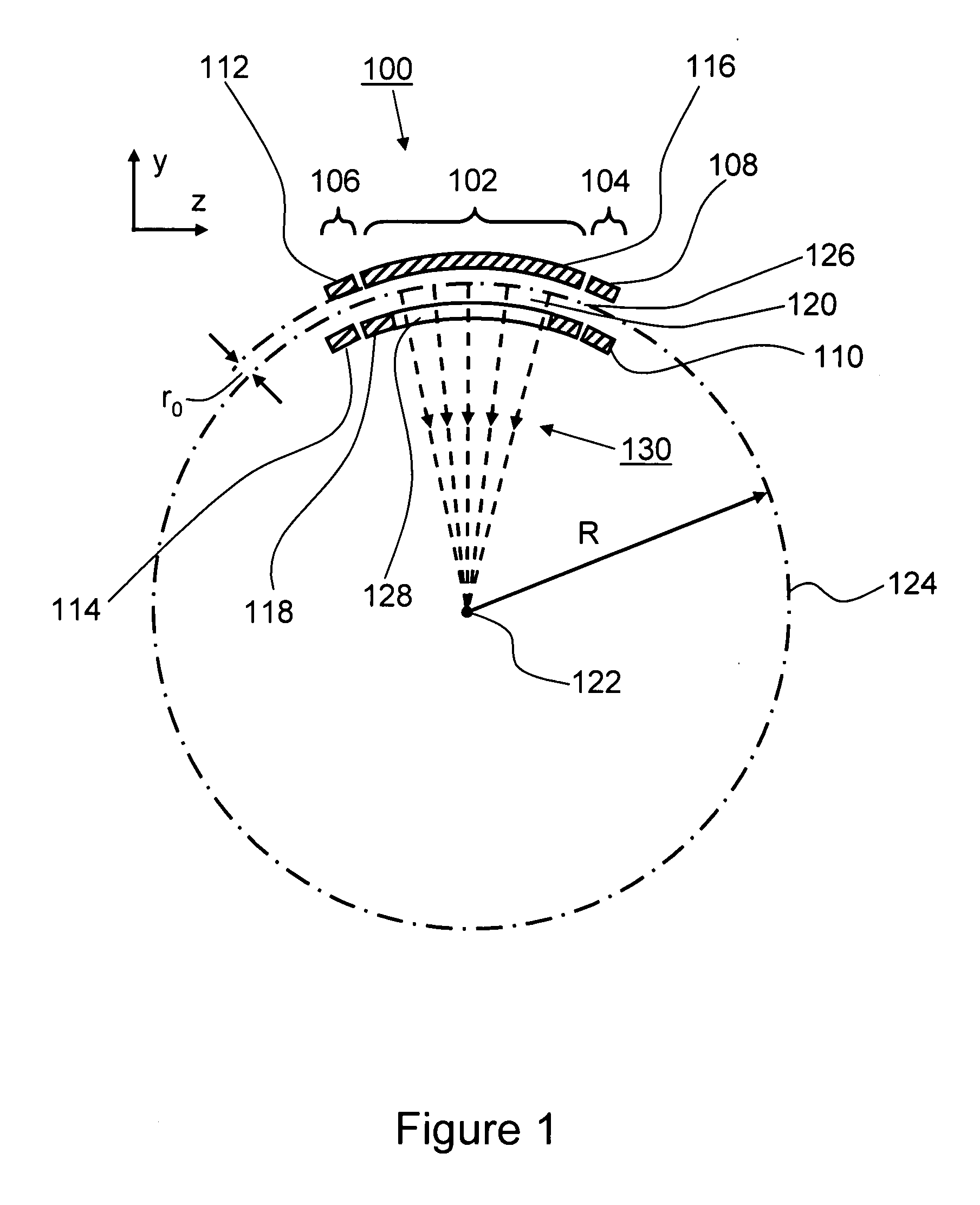
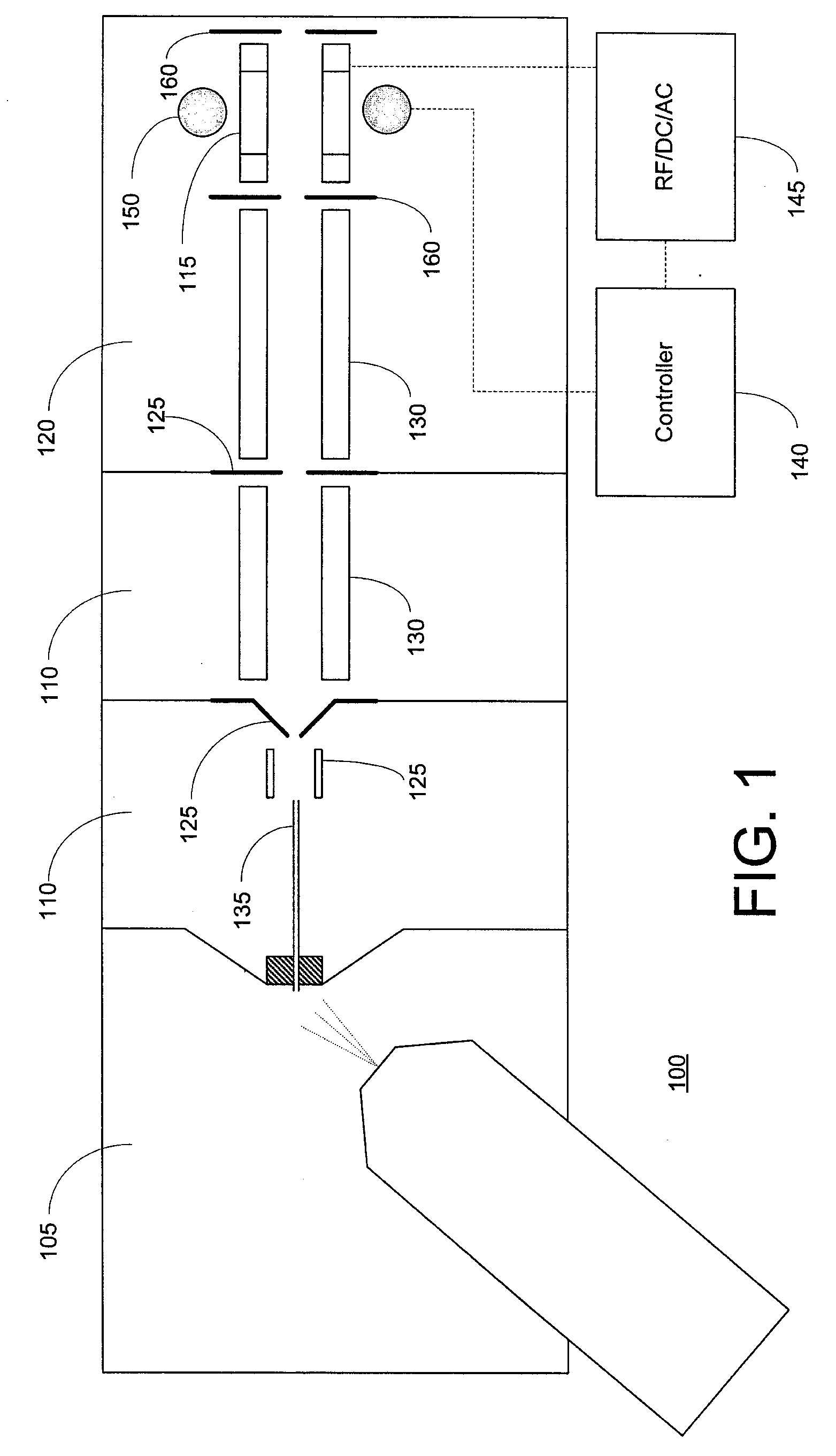
Tandem mass spectrometer
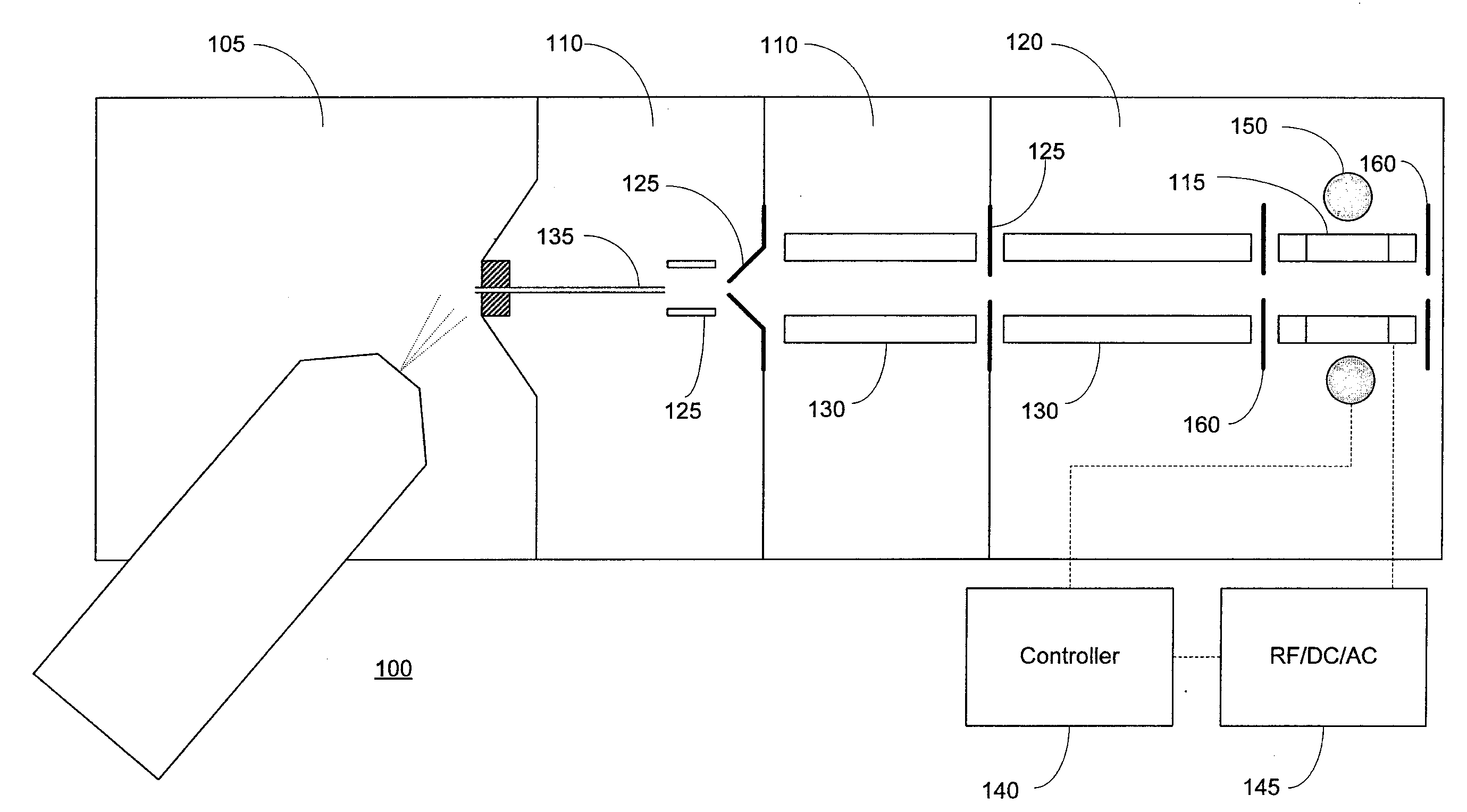
A tandem mass spectrometer includes a two-dimensional ion trap that has an elongated ion-trapping region extending along a continuously curving path between first and second opposite ends thereof. The elongated trapping region has a central axis that is defined substantially parallel to the curved path and that extends between the first and second opposite ends. The two-dimensional ion trap is configured for receiving ions through the first end and for mass selectively ejecting the ions along a direction that is orthogonal to the central axis, such that the ejected ions are directed generally toward a common point. The tandem mass spectrometer also includes a collision cell having an ion inlet that is disposed about the common point for receiving the ions that are ejected therefrom and for causing at least a portion of the ions to undergo collisions and form product ions by fragmentation. A mass analyzer in communication with the collision cell receives the product ions from the collision cell and obtains product ion mass spectra with a rapid scan rate. In this way, a plurality of product ion spectra may be obtained for a large number of precursor ions in a sample without the need for data-dependent operation.
Owner:THERMO FINNIGAN
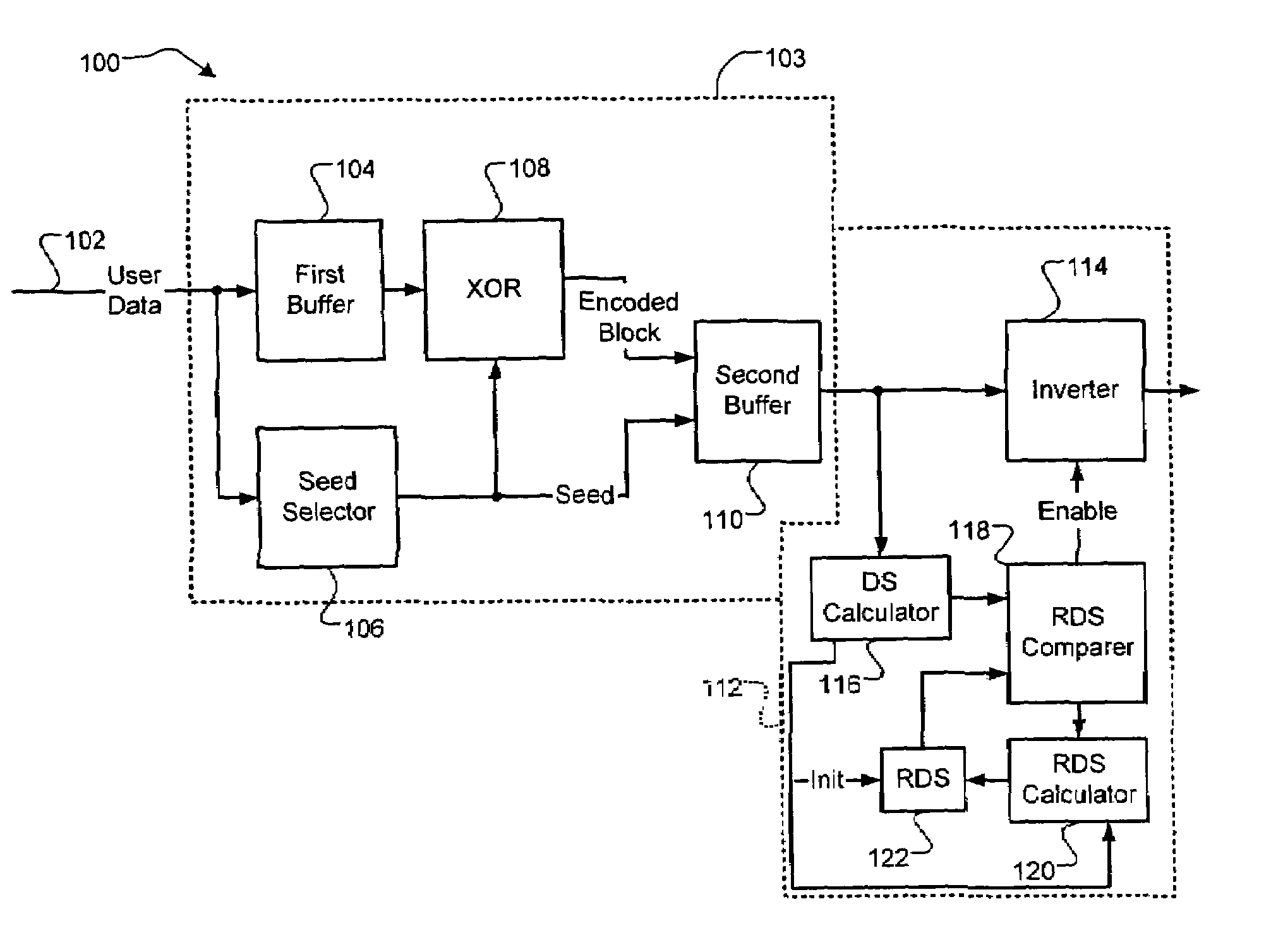
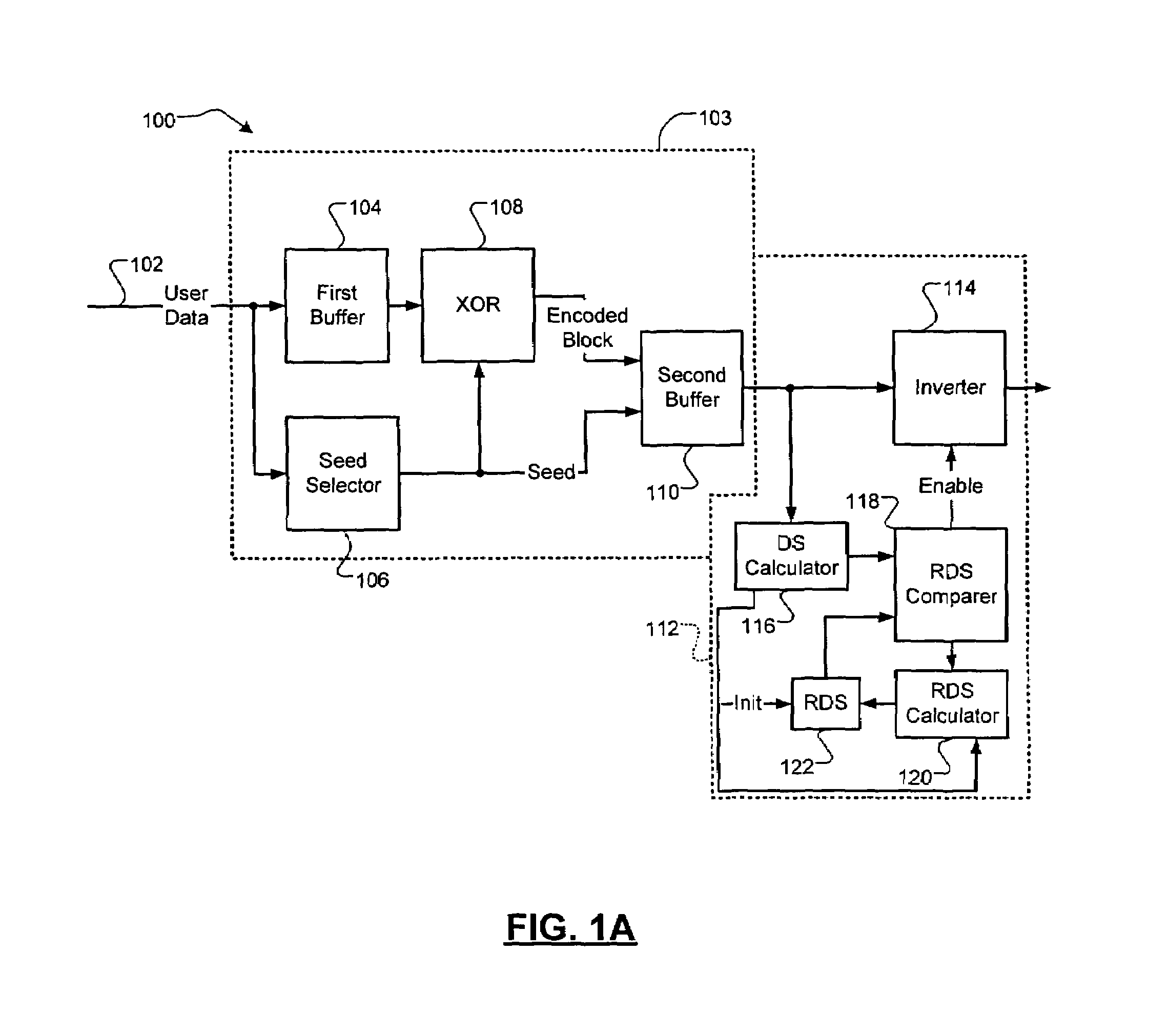
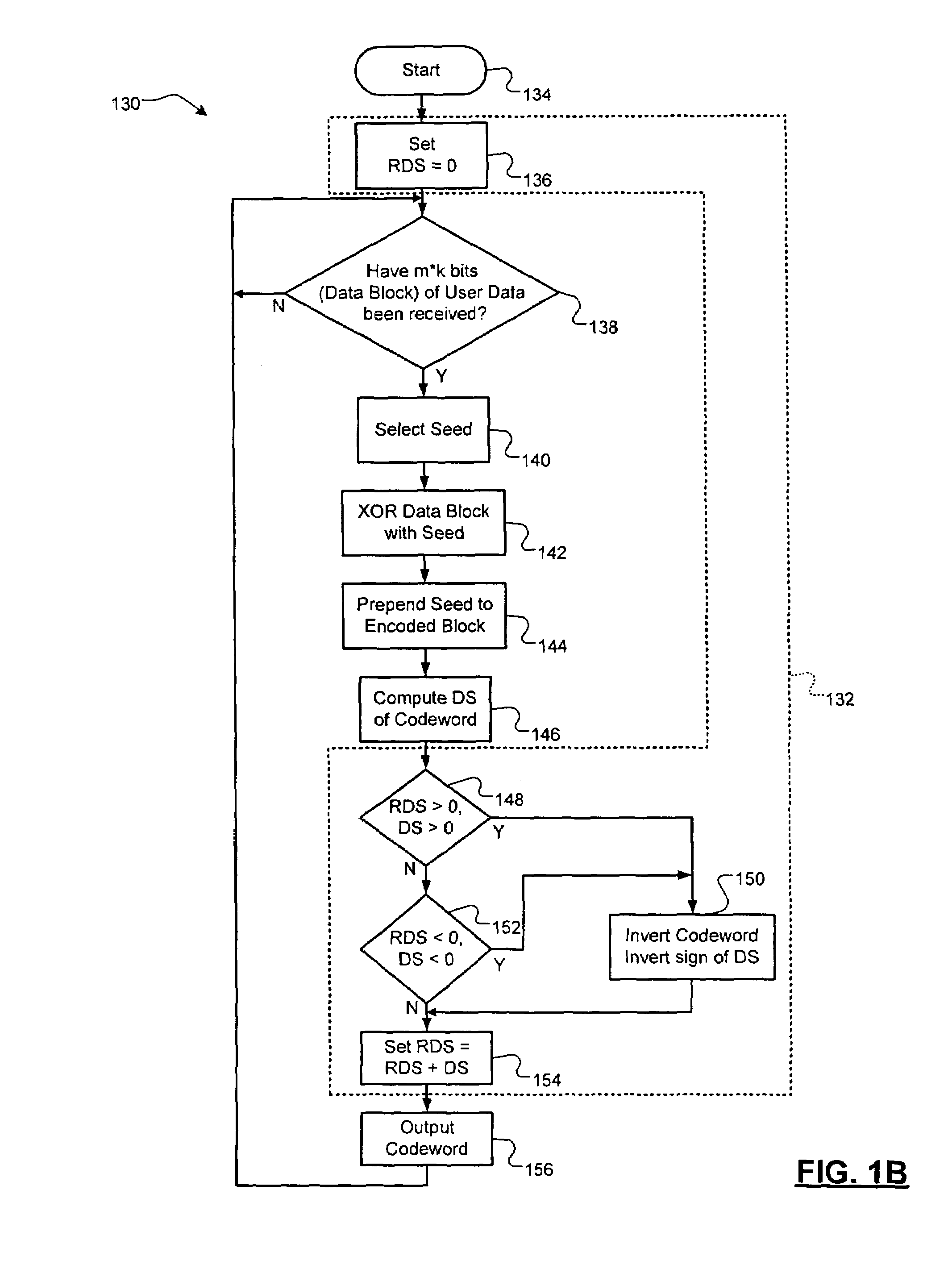
DC-free line codes
A data encoding system for a data stream comprises a data dependent scrambler that receives the data stream including K m-bit symbols, that selects a seed based on the K m-bit symbols, that scrambles the K m-bit symbols using the seed and that outputs a codeword including the scrambled K m-bit symbols and the seed. A DC control module receives a plurality of the codewords from the data dependent scrambler, selectively inverts selected ones of the plurality of codewords to reduce a difference between a total number of zeroes and total number of ones in the plurality of codewords and outputs an encoded data stream.
Owner:MARVELL INT LTD
System and method for providing service management in a distributed database system
InactiveUS7984073B1Eliminate and substantially reduce shortcomingDigital data processing detailsSpecial data processing applicationsDatabase serverService product management
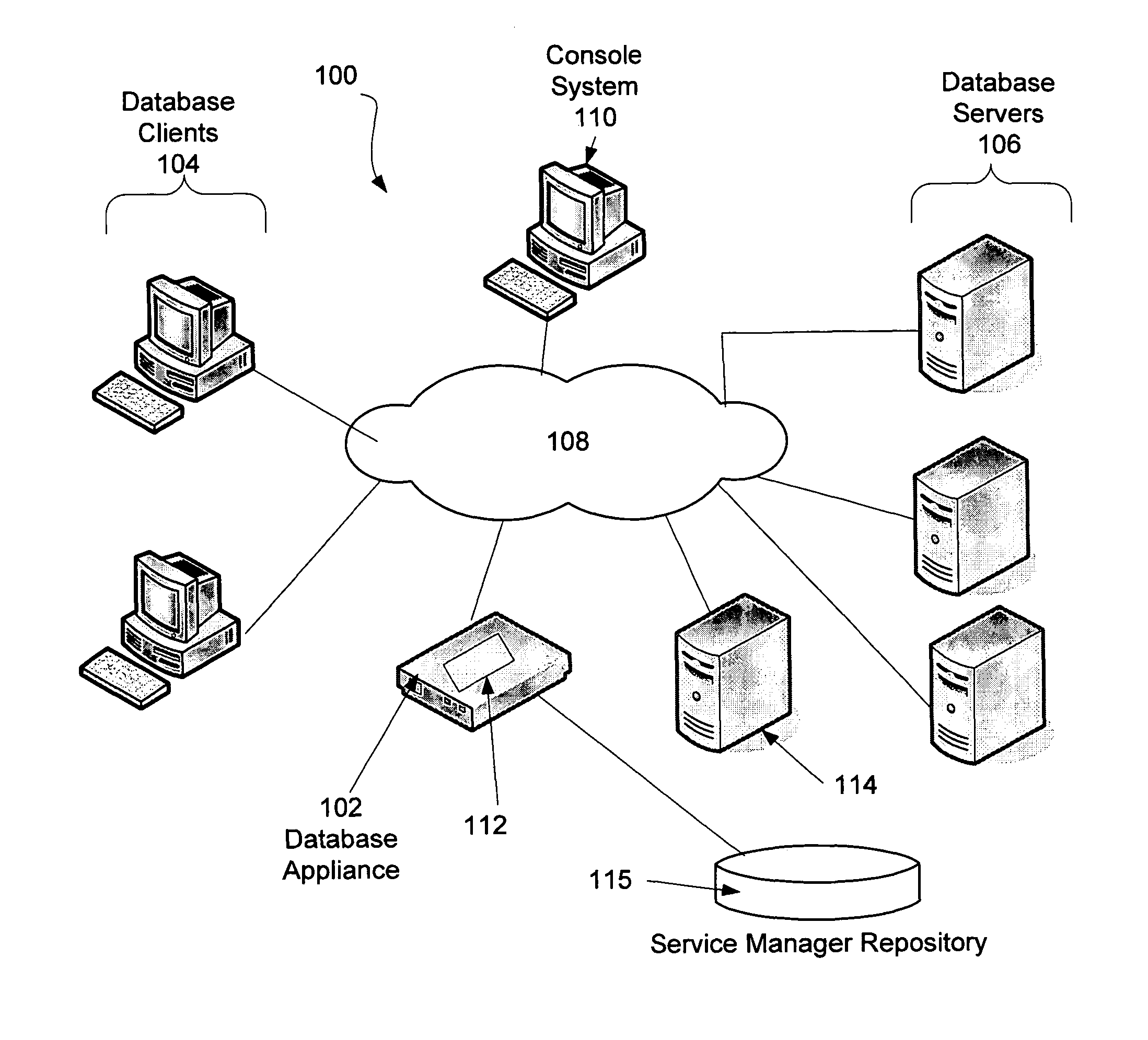
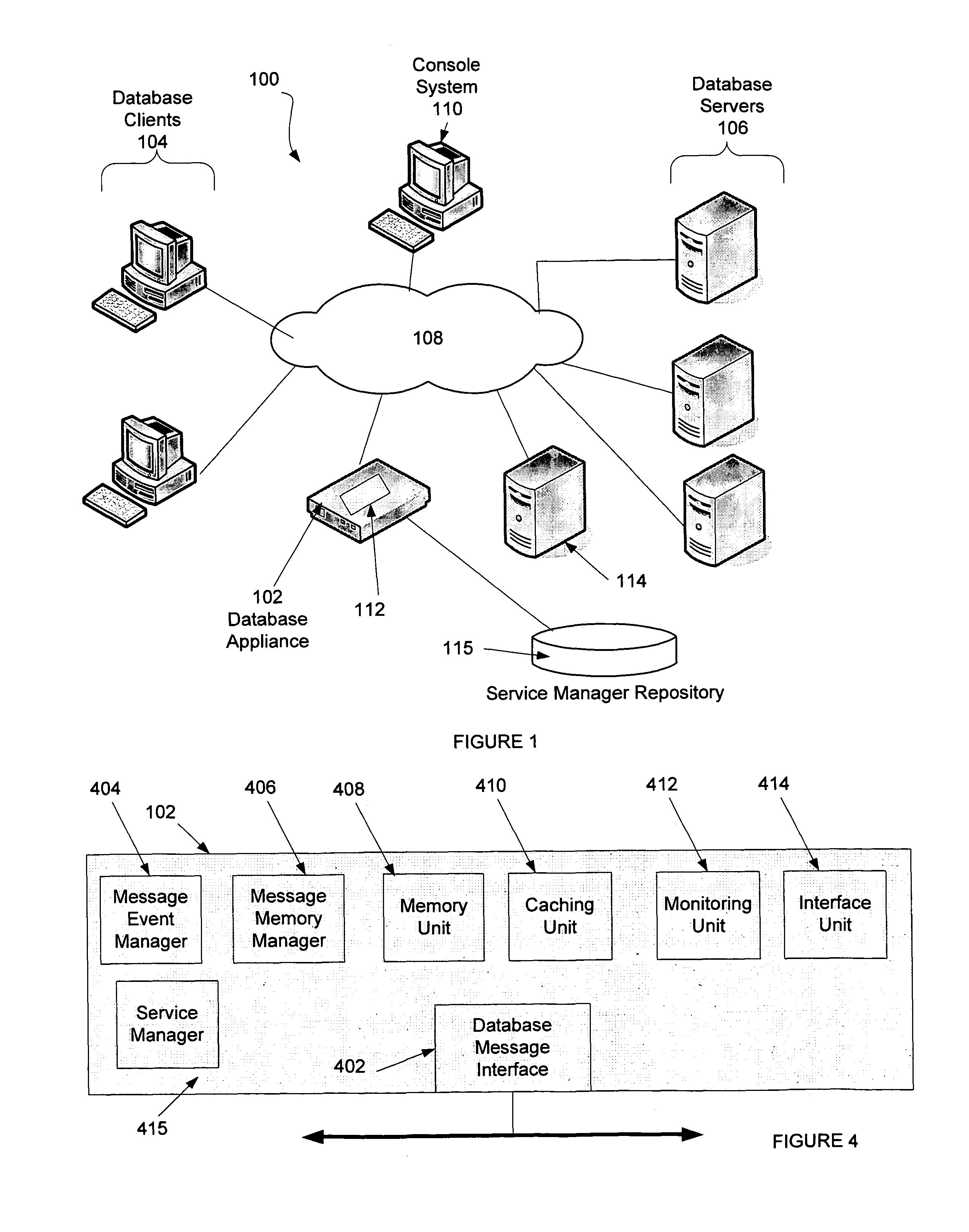
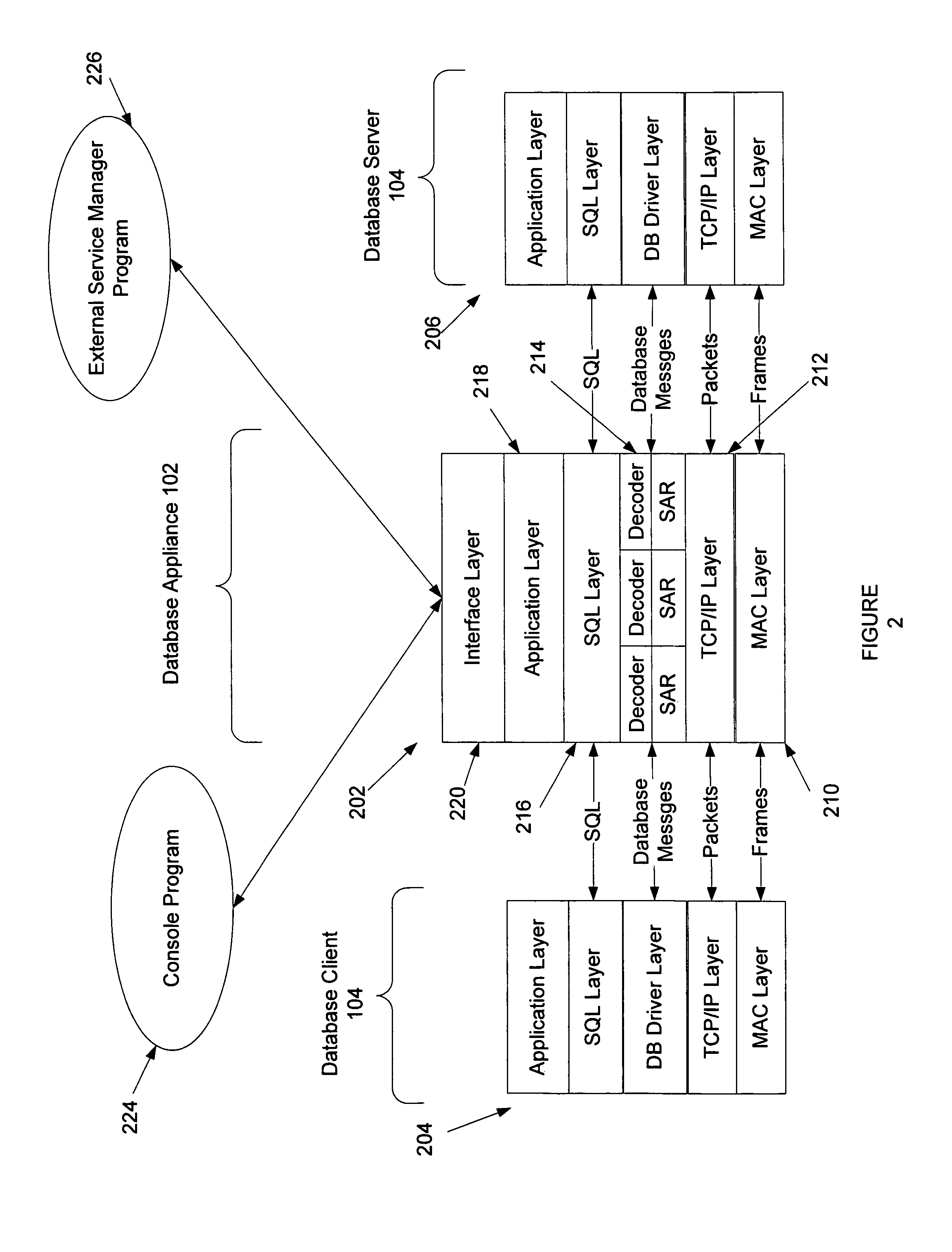
Embodiments of the present invention provide a system and method for service management in a distributed database environment. In general, embodiments of the present invention provide a service manager that connects to or is part of a database appliance that collects database performance data in the distributed database system. The database appliance accesses traffic between database clients and database servers and collects a variety of database performance statistics without having to rely on agents at the database clients or database servers. The service manager can access the performance data from the database appliance (locally or over communications link) and archive the performance data. Additionally, the service manager can compare items of the performance data (e.g., specific performance statistics) to user defined thresholds. If a threshold is met, the service manager can notify a user by, for example, sending an email.
Owner:KIP CR P1 +1
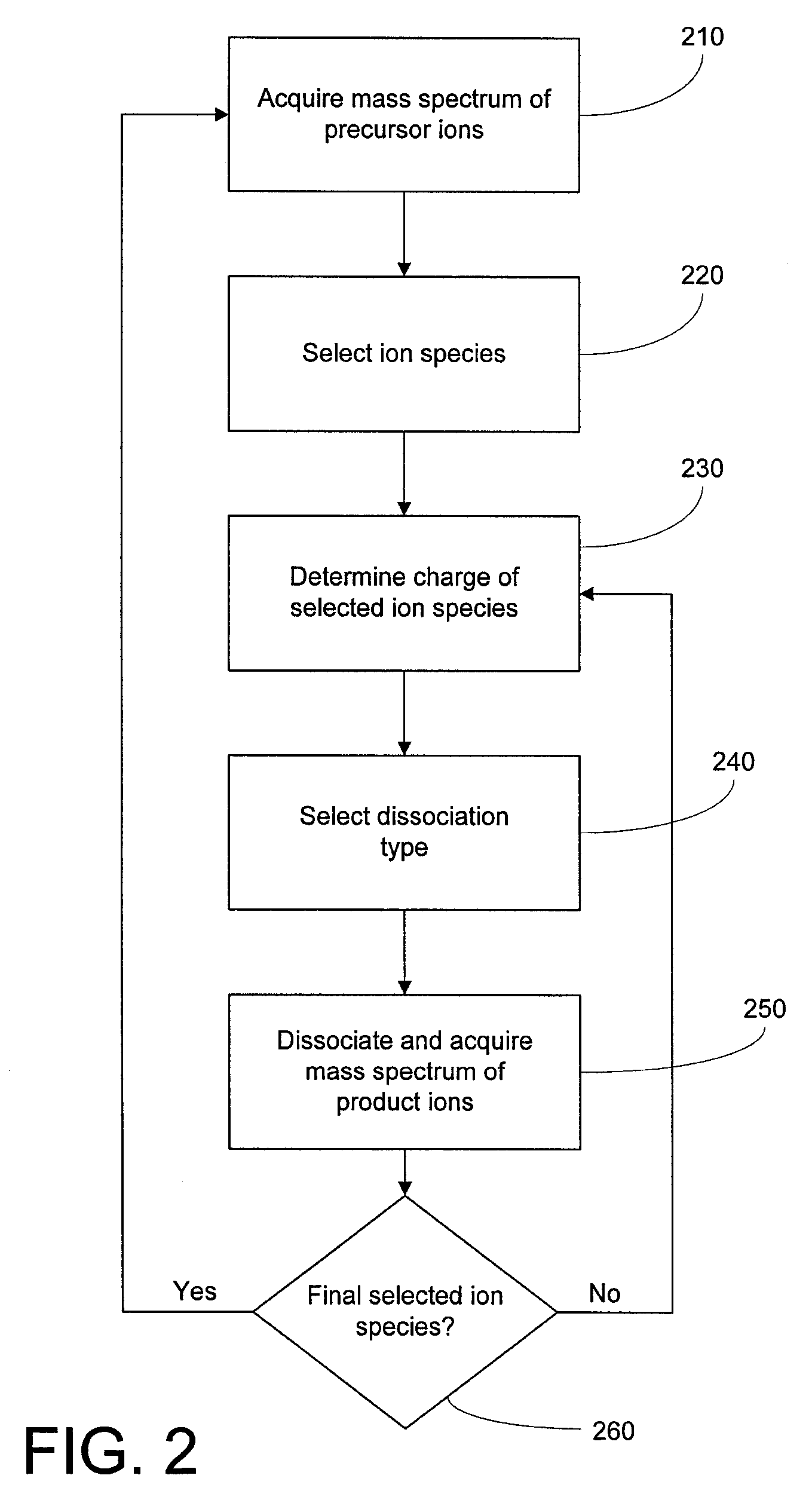
Data-dependent selection of dissociation type in a mass spectrometer
ActiveUS20080048109A1Easy to produceStrong dependenceIsotope separationMass spectrometersBiological activationData dependent
Methods and apparatus for data-dependent mass spectrometric MS / MS or MSn analysis are disclosed. The methods may include determination of the charge state of an ion species of interest, followed by automated selection of a dissociation type (e.g., CAD, ETD, or ETD followed by a non-dissociative charge reduction or collisional activation) based at least partially on the determined charge state. The ion species of interest is then dissociated in accordance with the selected dissociation type, and an MS / MS or MSn spectrum of the resultant product ions may be acquired.
Owner:THERMO FINNIGAN
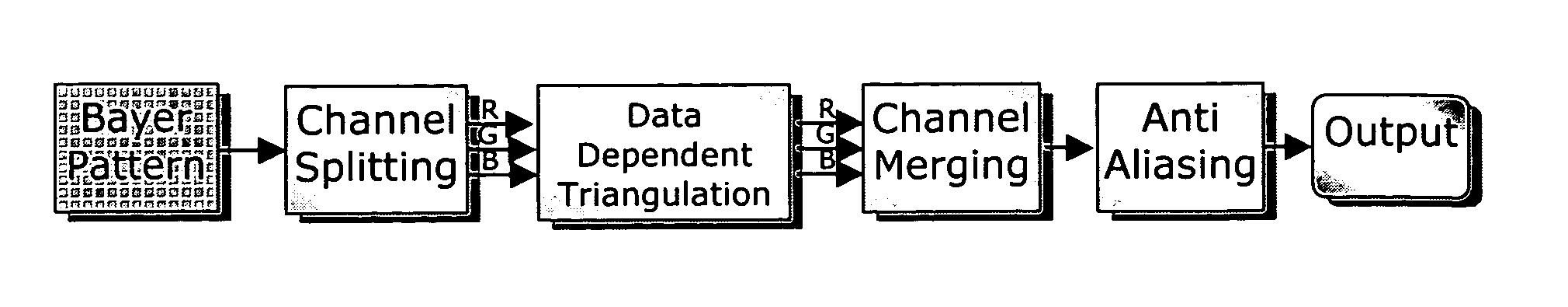
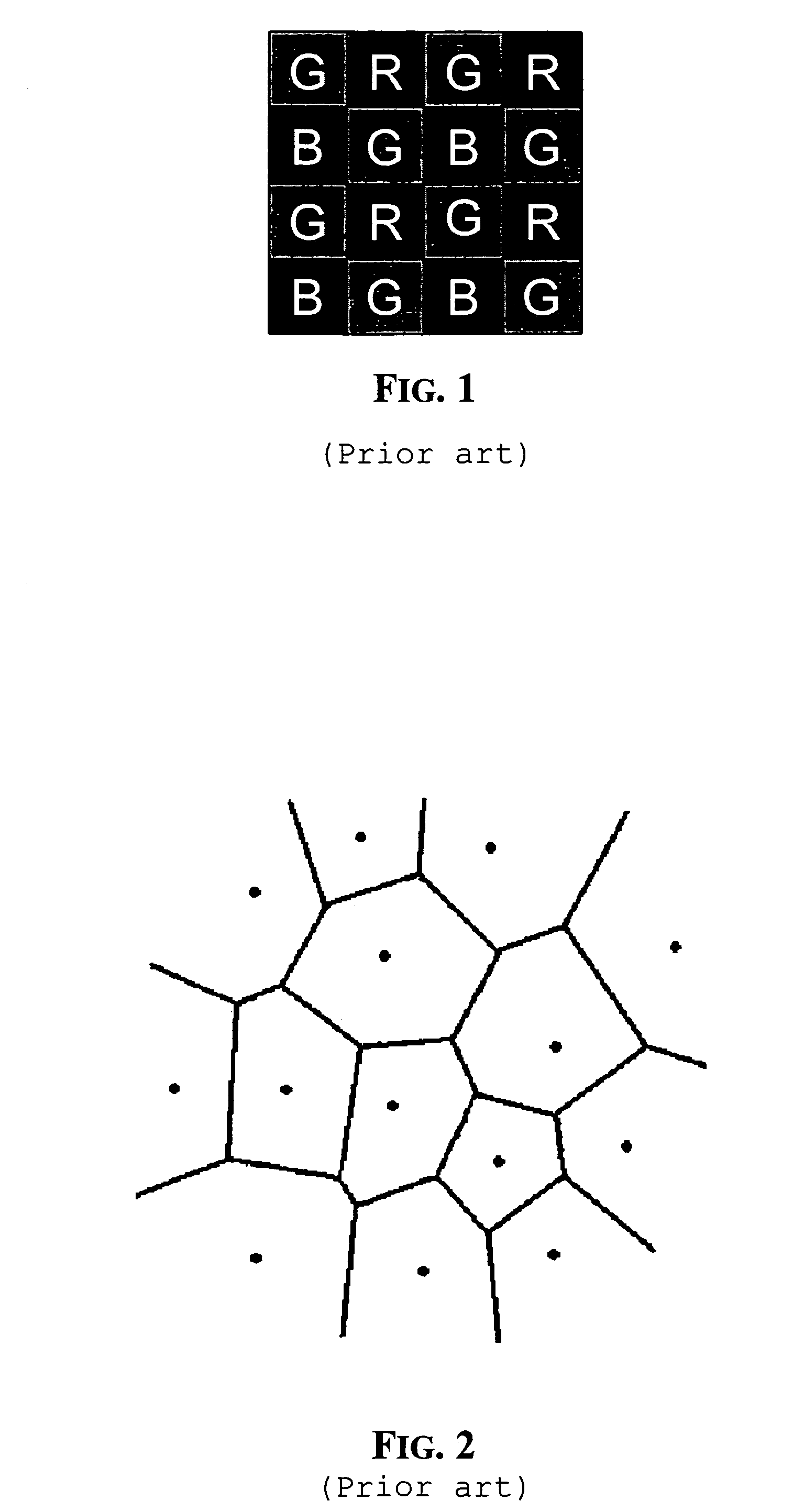
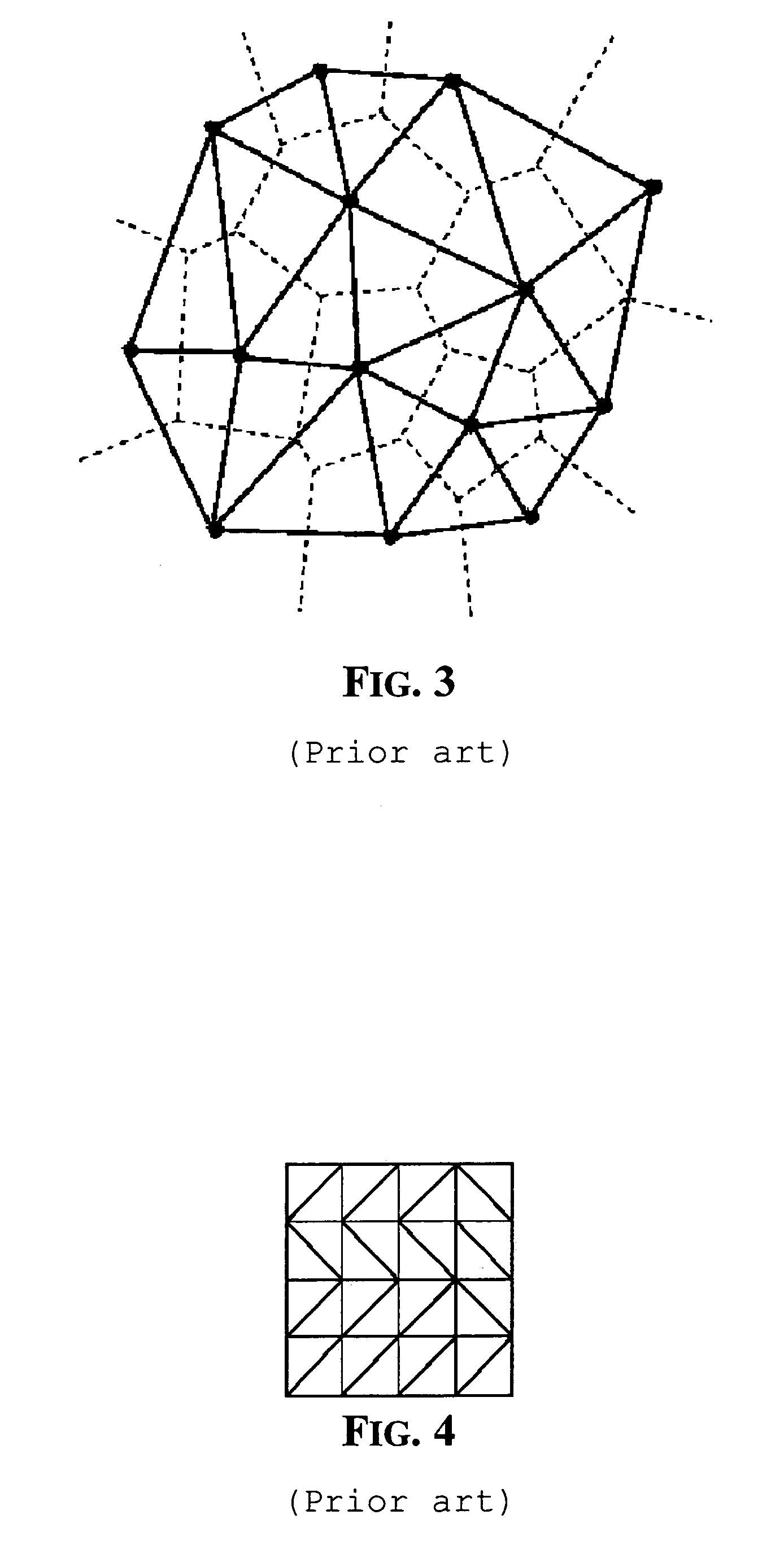
Color interpolation using data dependent triangulation
ActiveUS7305148B2Quality improvementFunction increaseGeometric image transformationCharacter and pattern recognitionAnti-aliasingTriangulation
A fast method of color interpolation of pixels of an image acquired by a color filtered digital sensor uses a very simple cost function that nevertheless produce interpolated images of good quality. The cost function is computationally simpler because it does not require the calculation of powers and square roots. The triangulation algorithm may be executed in far less time, while practically ensuring the same performance. The triangulation algorithm on average may use only two iteration steps. The interpolation process may be followed by an anti-aliasing processing that effectively removes color artifacts.
Owner:STMICROELECTRONICS SRL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com