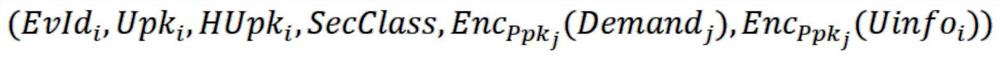Patents
Literature
934results about How to "Guaranteed credibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
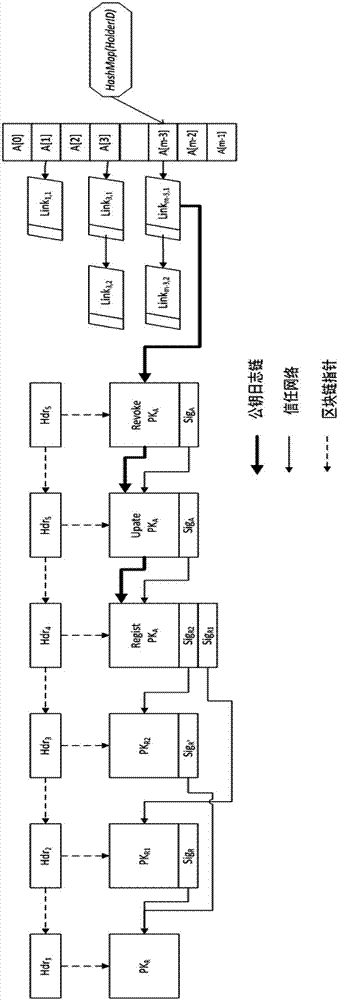
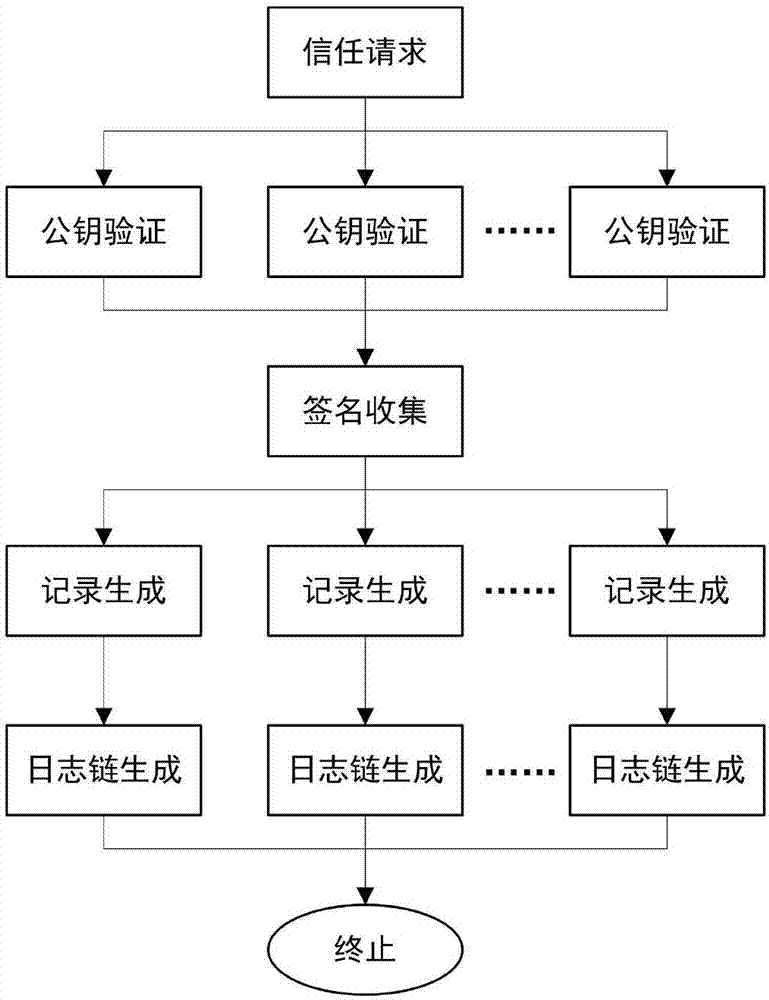
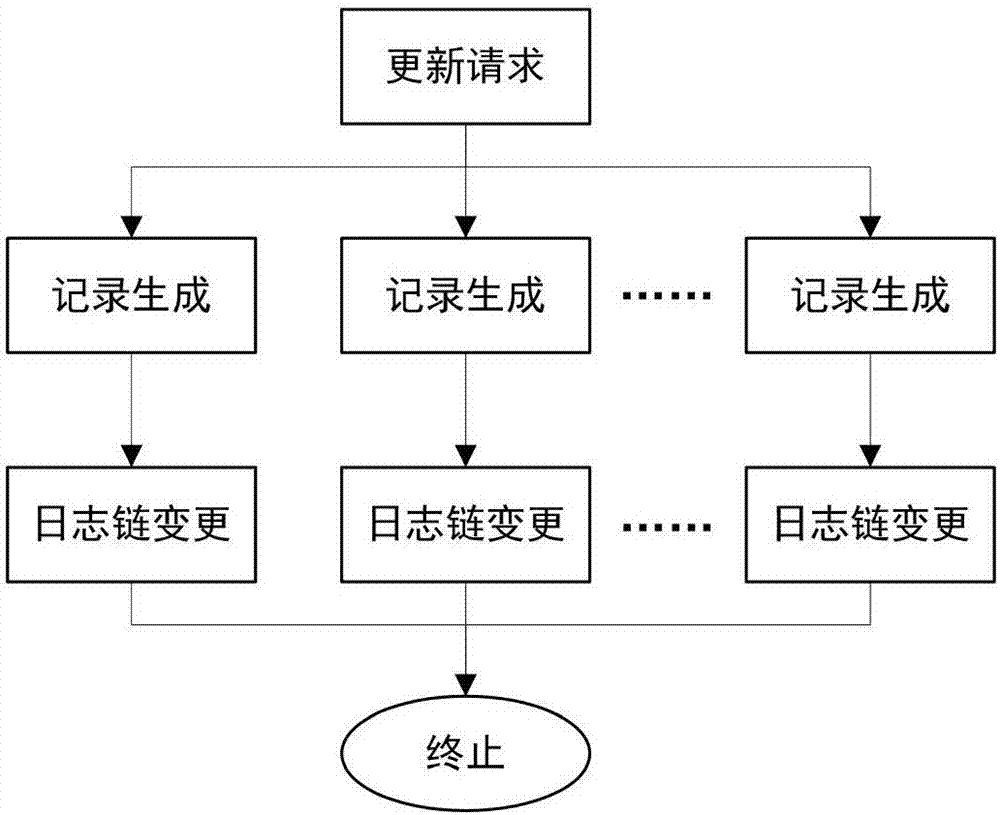
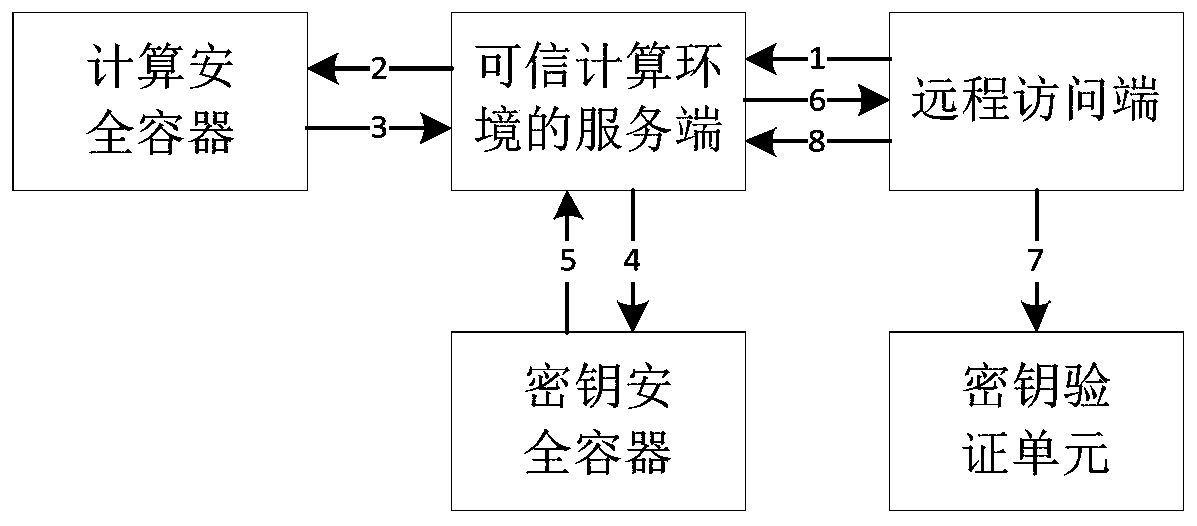
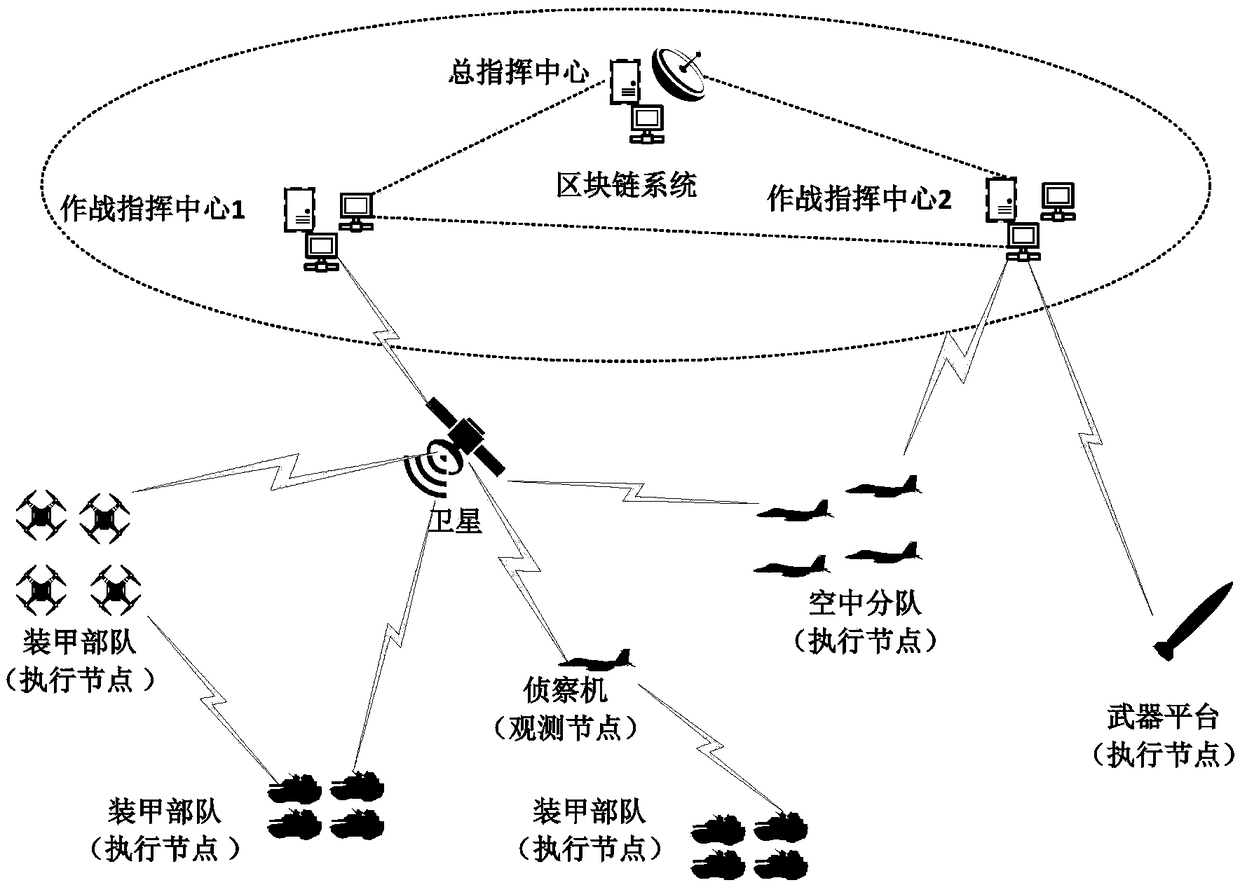
Decentralized public key management method and system based on trusted network
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
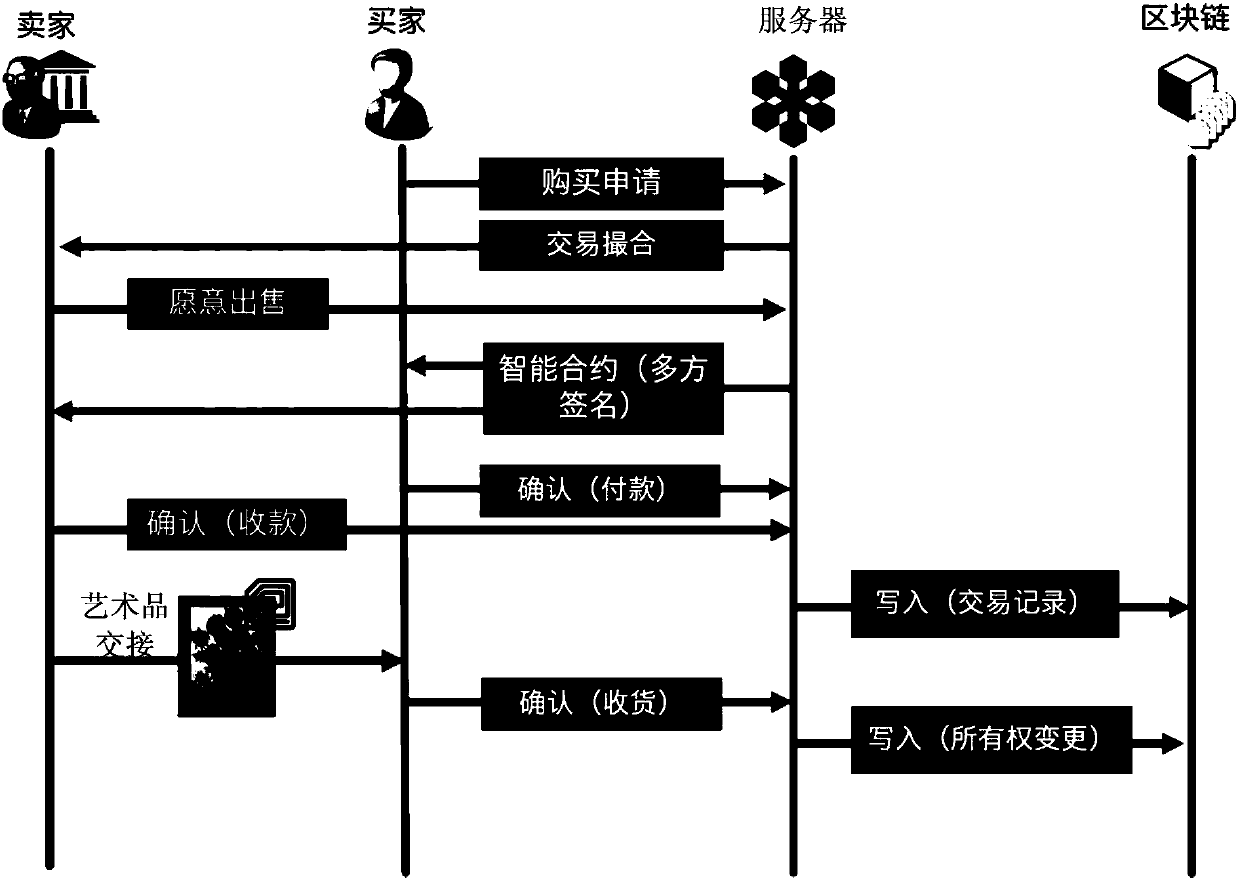
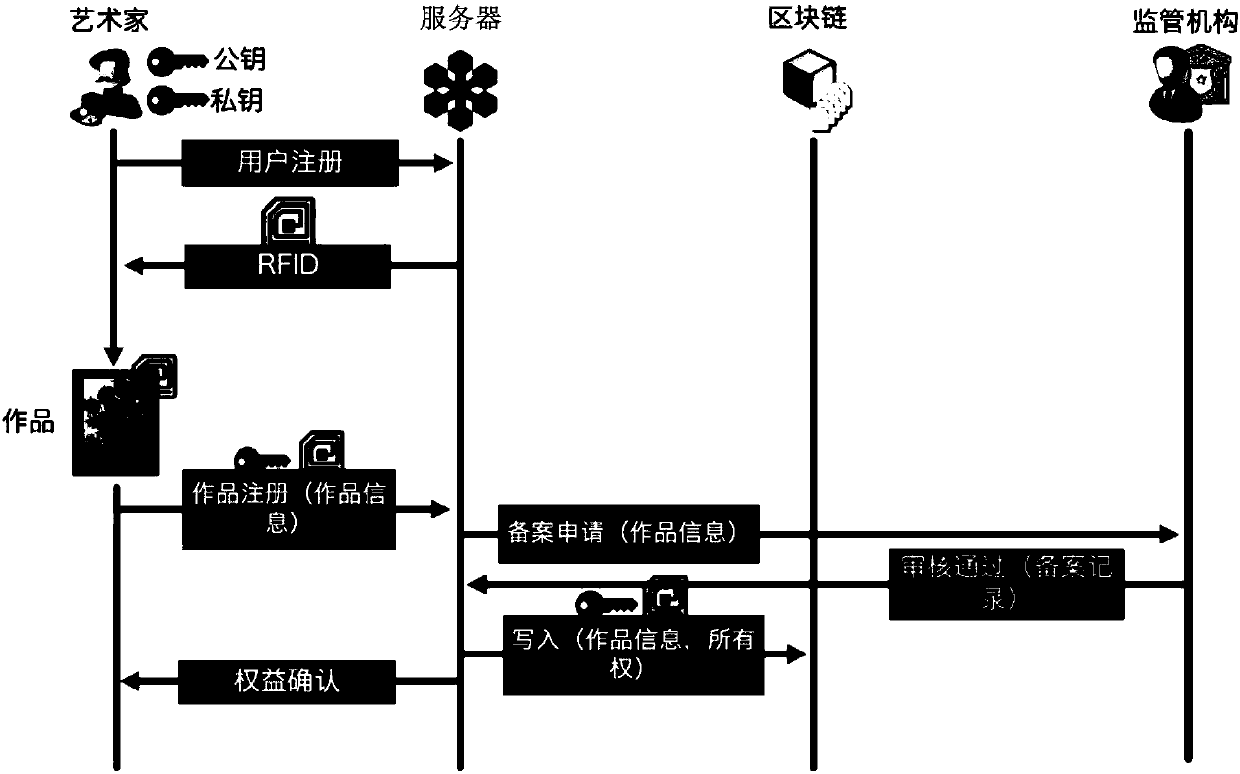
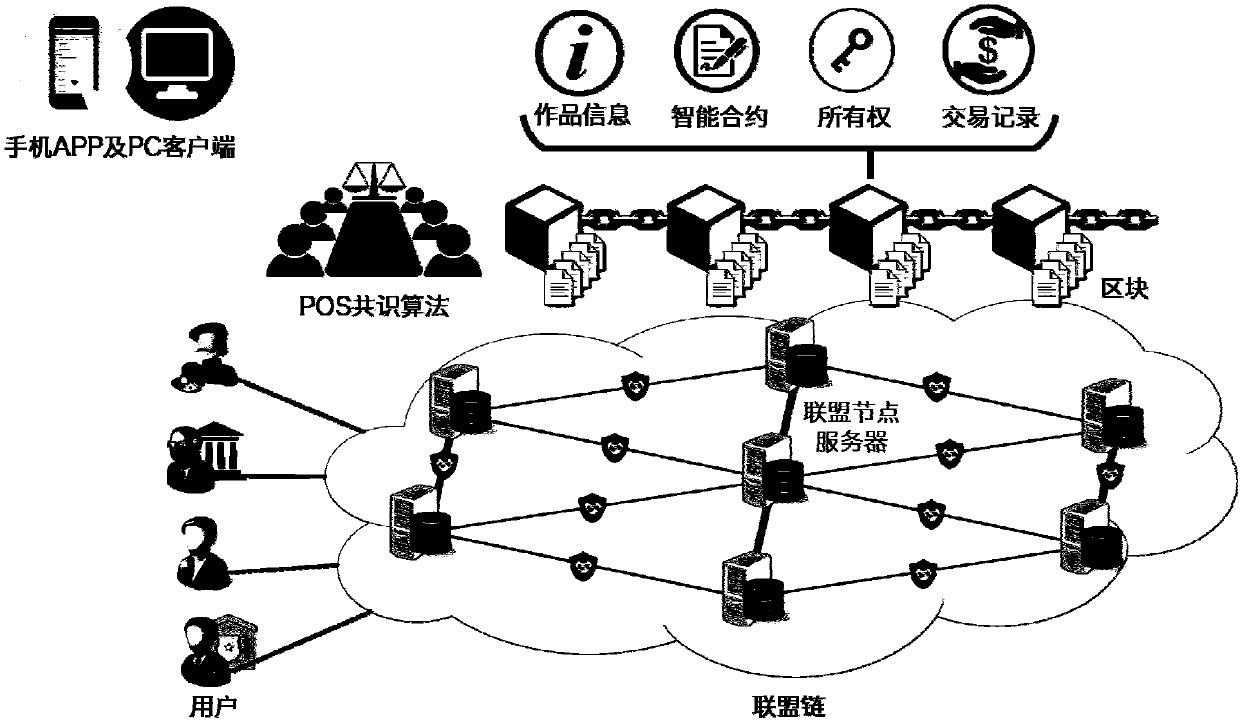
Block chain-based artwork trading method, server, server end and system
InactiveCN107730384AGuaranteed credibilityEnsure effective smooth progress and safetyFinancePayment protocolsComplex networkWeb technology
The invention provides a block chain-based artwork trading method. The method is suitable for use in the field of network technology, and includes: receiving a buying application request, determiningseller information according to a target artwork, and sending a trading request to the seller; sending a smart contract to the seller and a buyer if selling willing information is received; judging whether the smart contract becomes valid, and if yes, generating trading records, and sending the same to a block chain for saving; and judging whether an ownership change condition of the target artwork is met, and if yes, generating ownership change records, and sending the same to the block chain for saving. According to the embodiment of the invention, all servers of a node network in the blockchain are used to participate in management and maintenance thereof through a decentralized structure of the block chain, thus credibility of databases in the block chain are guaranteed, and the servers are built on the peer-to-peer network at the same time, an effect that property rights and trading records stored in the block chain can be all accessed under any complex network environment is guaranteed, and effective and smooth performing and security of trading are guaranteed.
Owner:SHENZHEN UNIV
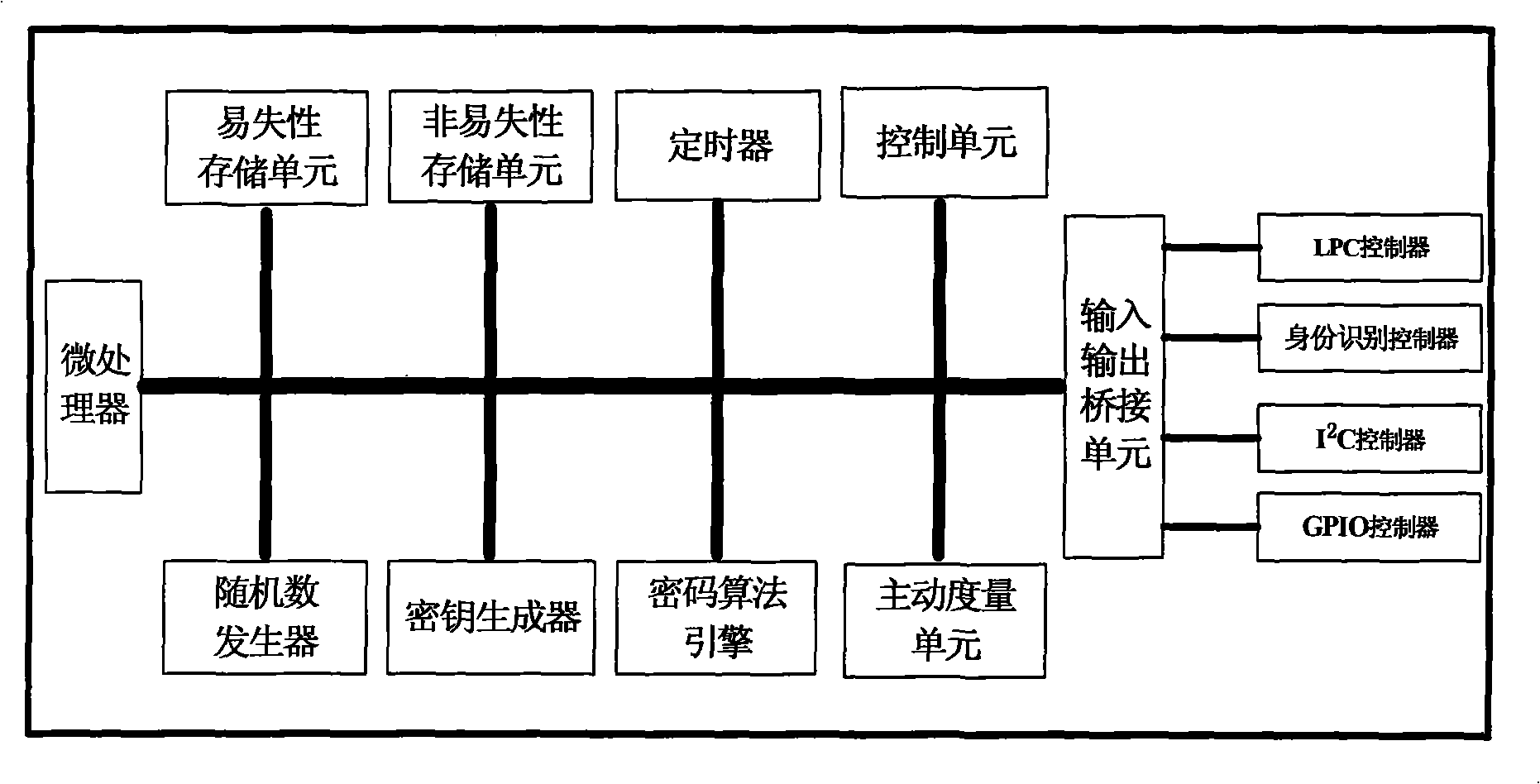
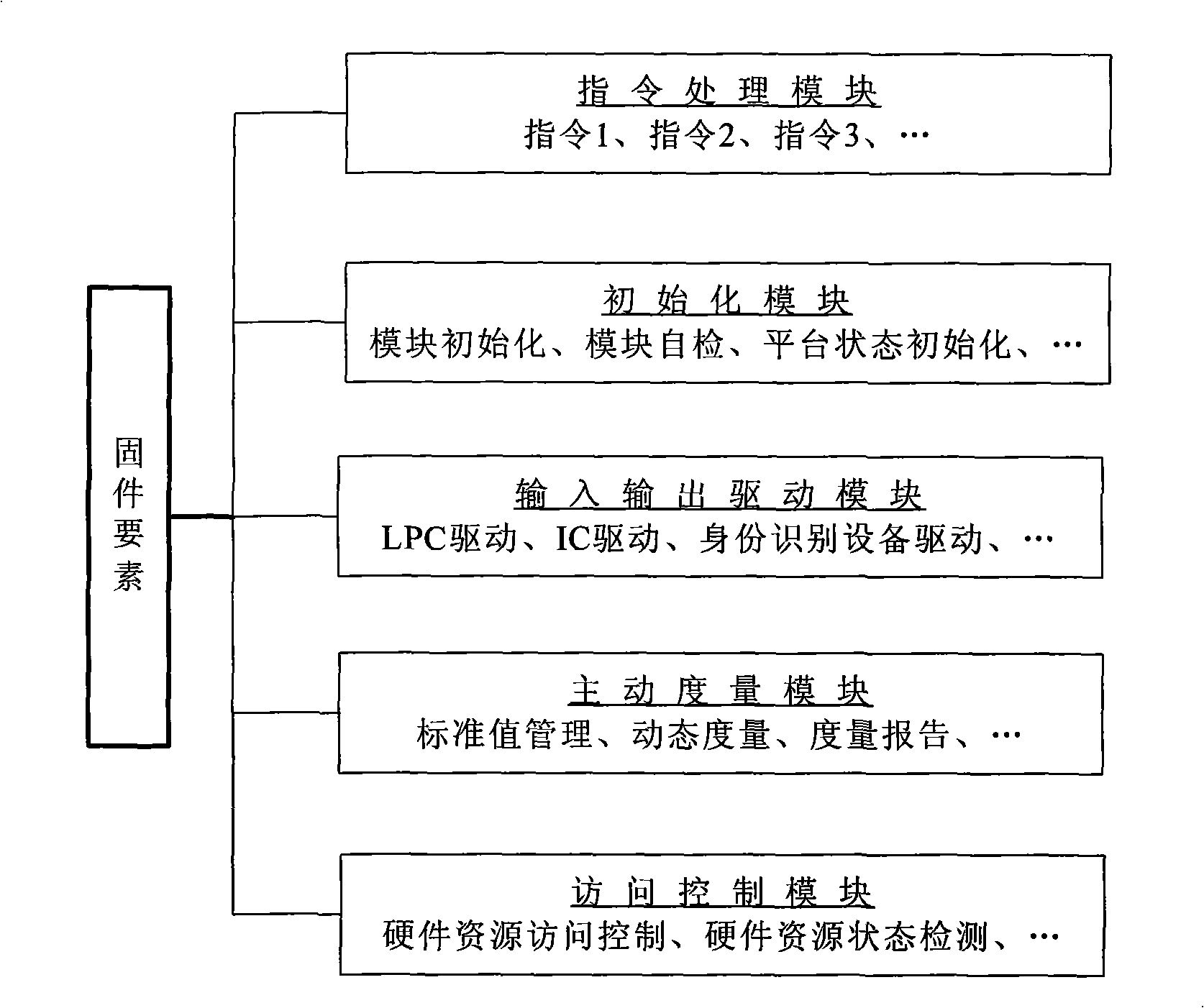
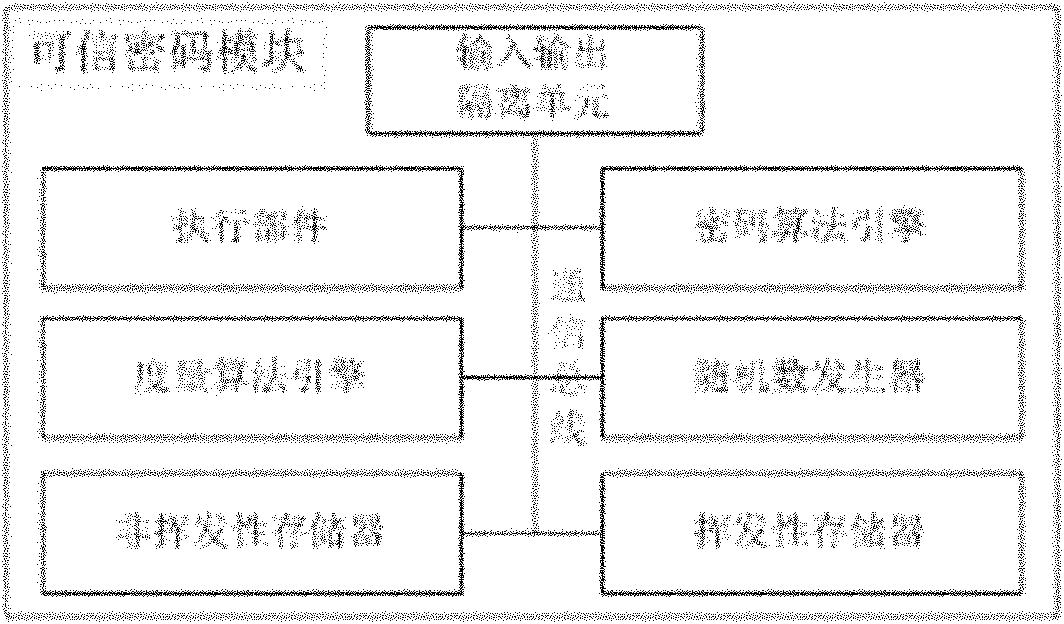
Credible platform module and active measurement method thereof
InactiveCN101295340ARealize functionPrevent tamperingInternal/peripheral component protectionTrusted Platform ModuleTrusted Computing
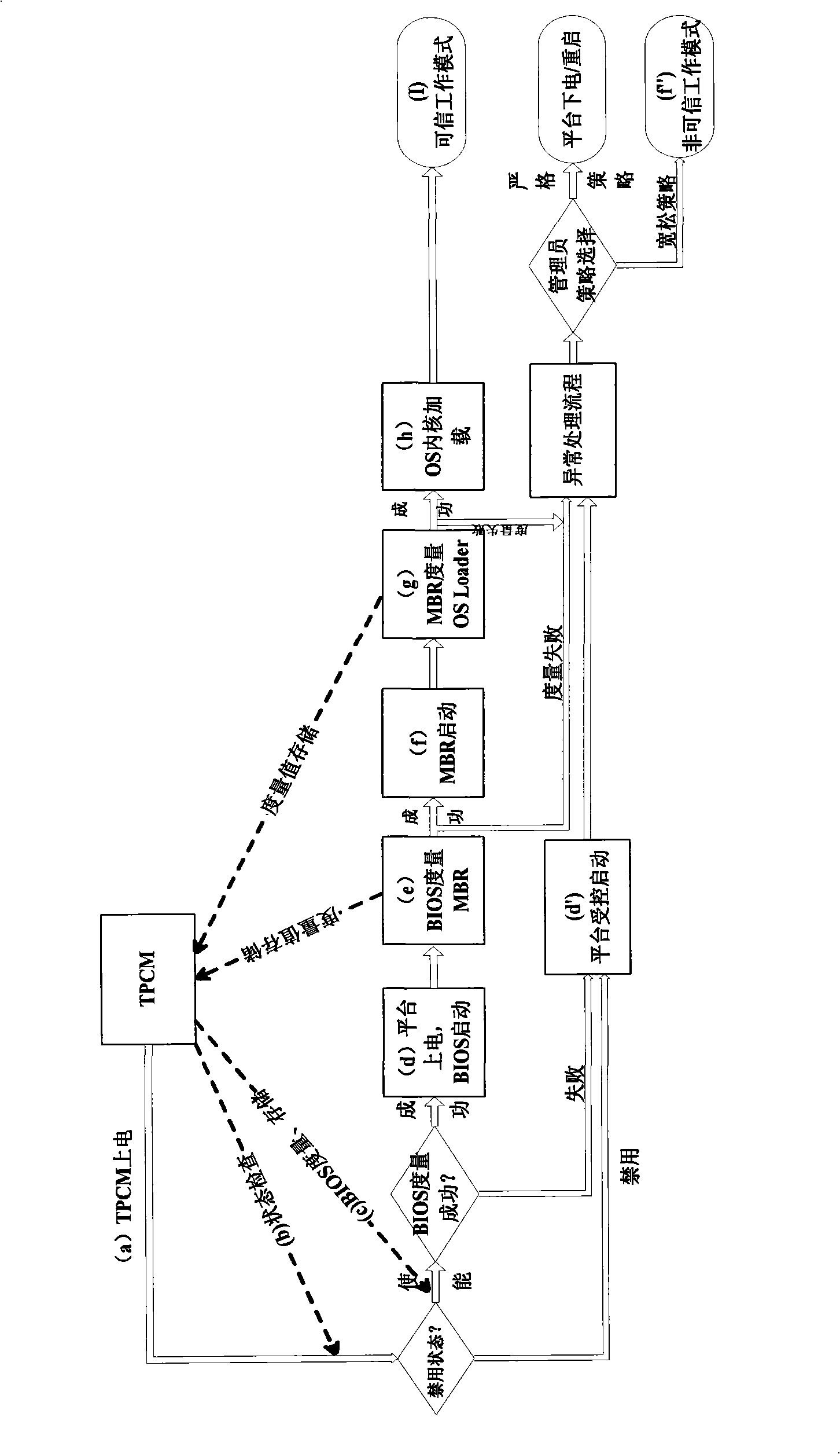
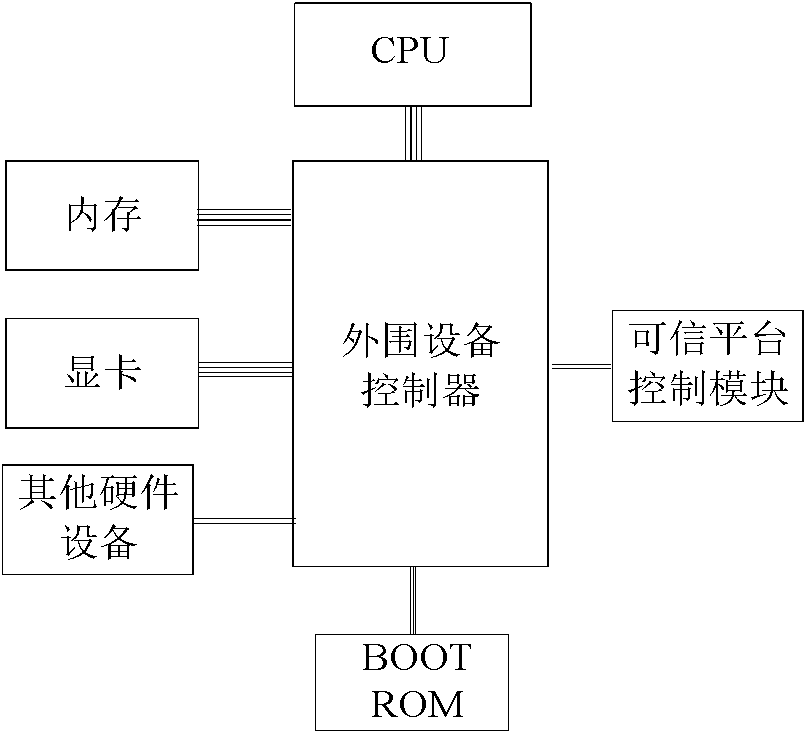
The invention discloses a trusted platform module and an active measurement method thereof, which relate to the field of information safety. The trusted platform module TPM is a root of trust of a trusted computing platform and a core module of trusted computing; the invention points out CRTM constitution of a root core of measurement in a TPM chip and a problem of establishing an information chain, proposes a new design proposal of the trusted platform module and the measurement method with an active mode based on the trusted platform module, designs the root of trust for measurement of the platform in the trusted platform module, solves the safety threat on the root of trust caused by tampering the BIOS and utilizes the module as the root of trust to establish a trust chain with the active mode. The invention names the module as a Trusted Platform Control Module TPCM and reflects the control function of the root of trust in the whole platform.
Owner:BEIJING UNIV OF TECH
Distributed data storage system and method based on blockchain
ActiveCN107193490AReduce storageAvoid inefficiencyInput/output to record carriersData contentData store
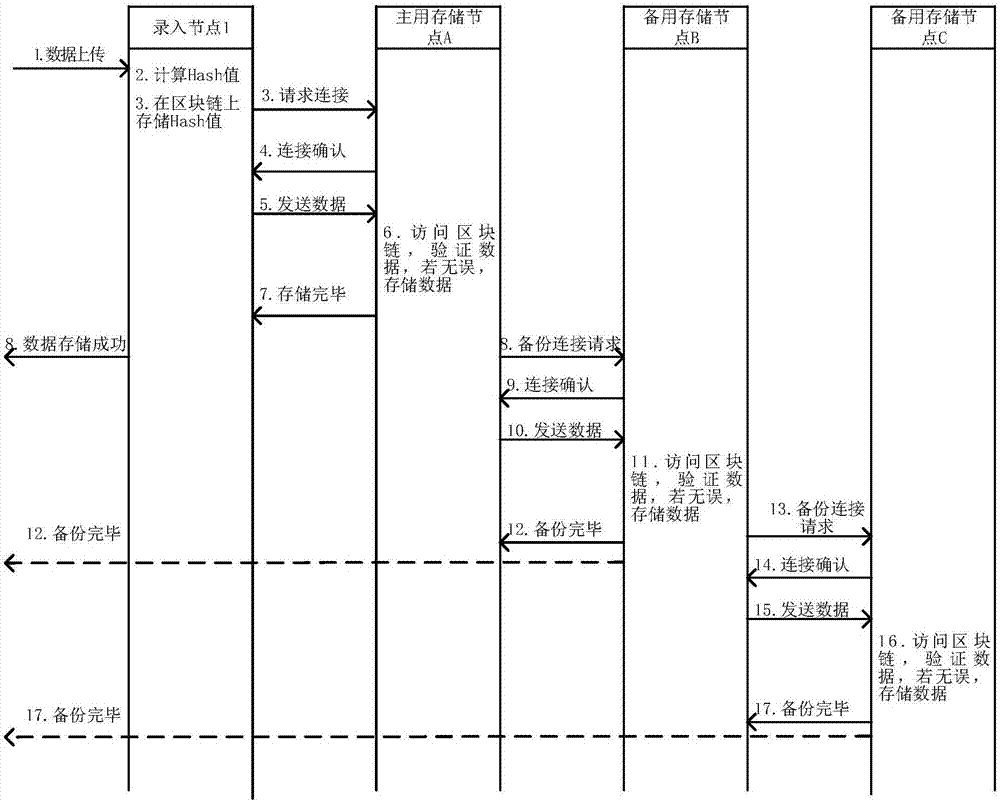
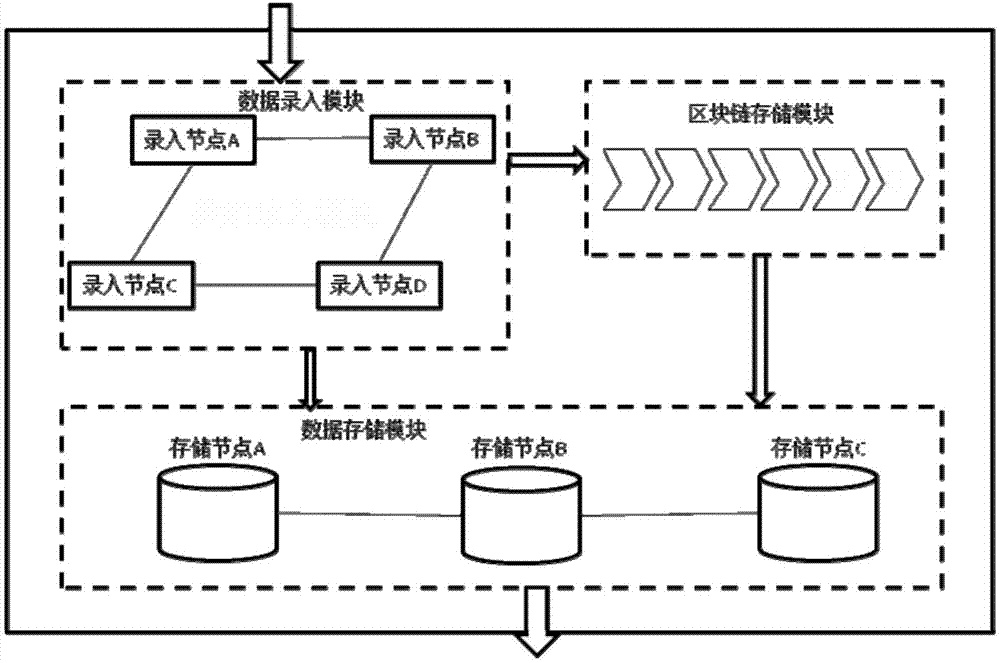
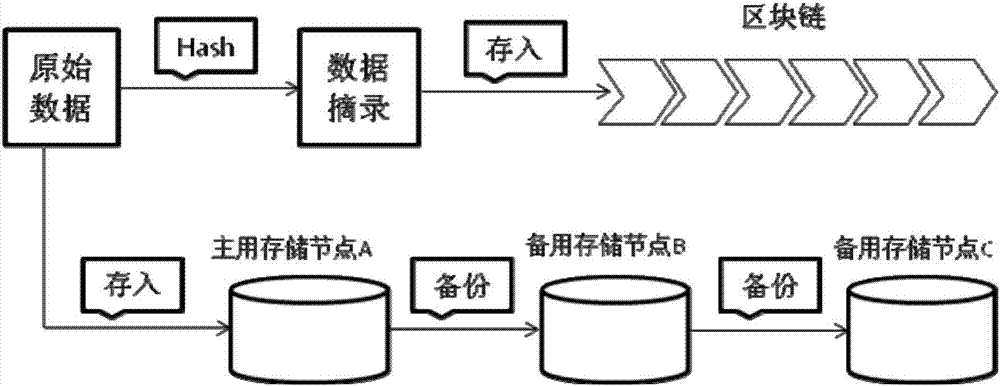
The invention discloses a distributed data storage system and method based on a blockchain. The method comprises: inputting a data content into a data storage module by a data inputting module, and using a hash algorithm to calculate an extract of the data content to store on the blockchain; receiving the data content by the data storage module, retrieving the extract corresponding to the data content, and storing the data content that is consistent with the extract; and when data querying is carried out, finding a stored queried data content by the data storage module, retrieving an extract corresponding to the data content, and returning the queried data content that is consistent with the corresponding extract to a querying node. According to the system and method, the blockchain is used in the information storage system, a Root-privilege administrator does not exist, no one can arbitrarily modify an information content without being detected, and reliable management and secure sharing of information are realized; and the blockchain is not directly used to store the data content, only the extract obtained by calculating by using the hash algorithm is stored, the amount of storage on the blockchain is reduced, low efficiency of the blockchain is avoided, and the practicality is improved.
Owner:北京中科锐链科技有限公司
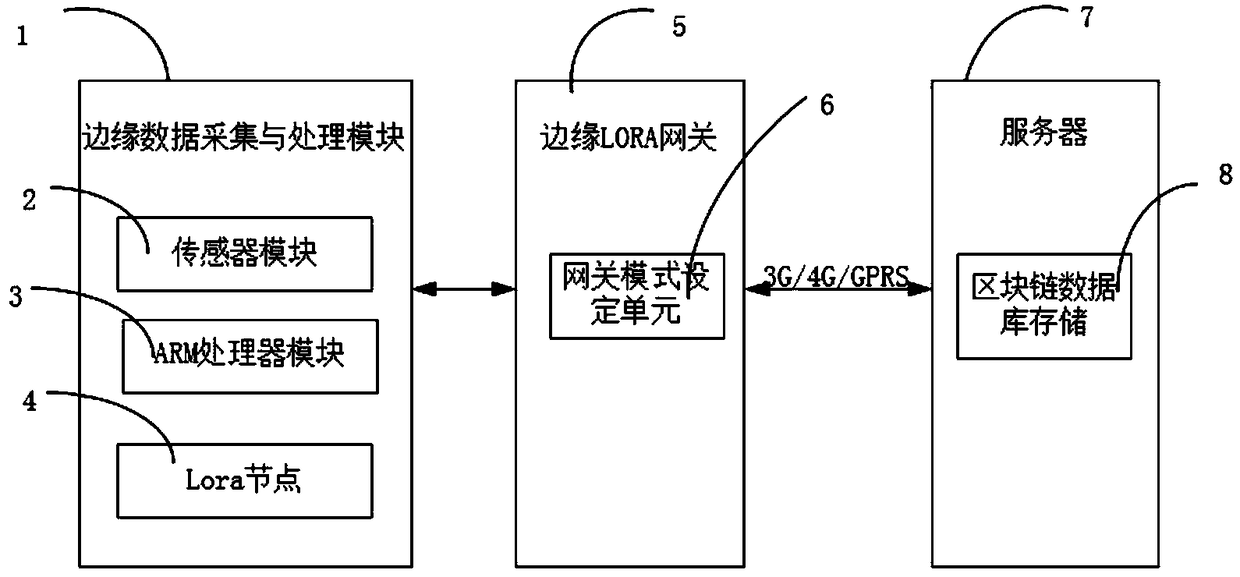
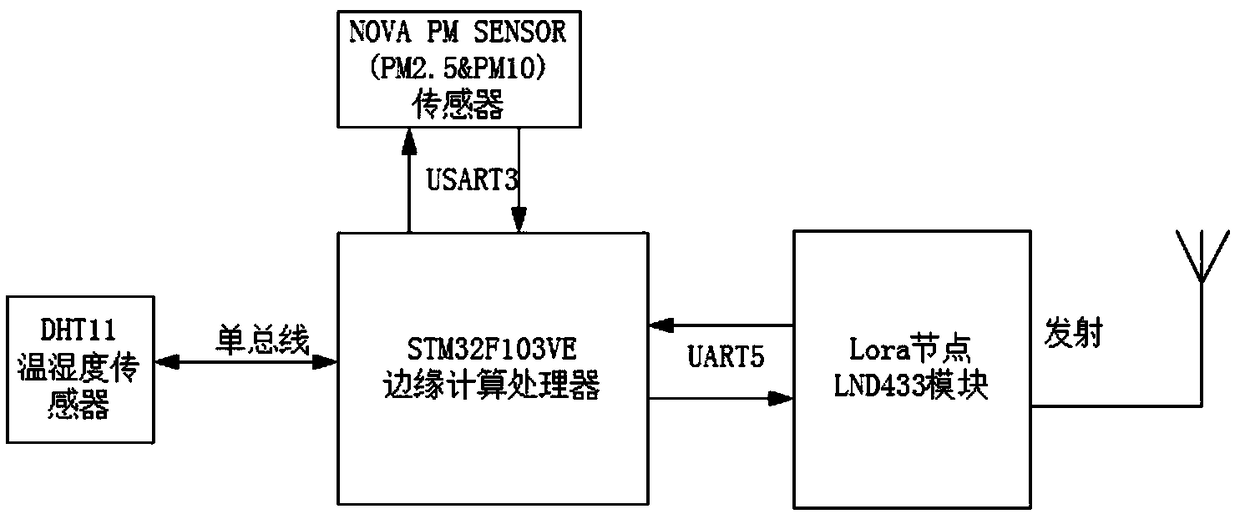
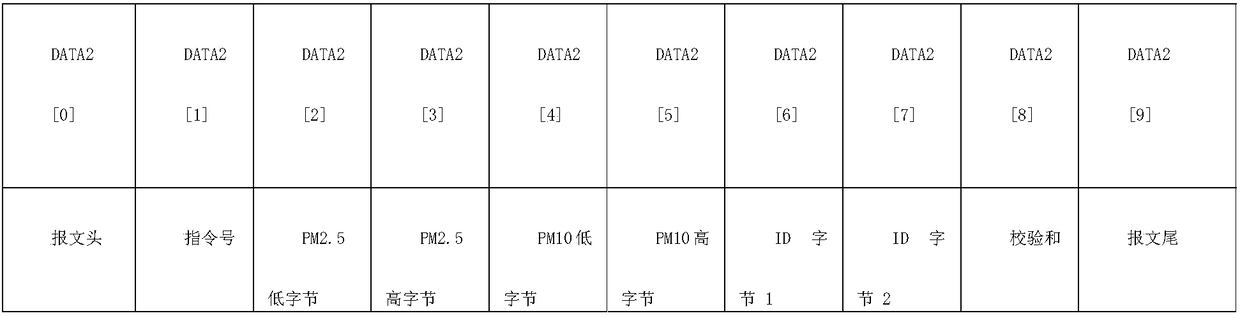
LORA Internet-of-Things environmental data collection and cochain implementation method based on edge computing and blockchain
ActiveCN109194761AMeet access needsReduce transmission loadParticular environment based servicesTransmissionEdge computingMobile edge computing
The present invention provides a LORA Internet-of-Things environmental data collection and cochain implementation method based on edge computing and a blockchain, belonging to the related field of Internet-of-Things data collection and storage. The mechanism provides a feasibility method capable of overcoming the problem or at least partially solving the problem. The implementation system architecture of the method comprises the following steps of: achieving blockchain data and at least one LORA edge gateway communication by a server; allowing the LORA networking technology to meet the accessdemand of a lot of edge devices in an Internet-of-Things environment with low cost; employing an embedded microprocessor to achieve edge computing, performing preprocessing of the obtained environmentdata to reduce the calculated amount of the data processing and analysis, improve the calculation efficiency, reduce the network transmission load, reduce the network transmission delay and save theenergy consumption; and employing the blockchain storage technology to ensure the credibility and the safety of data storage.
Owner:BEIJING UNIV OF TECH
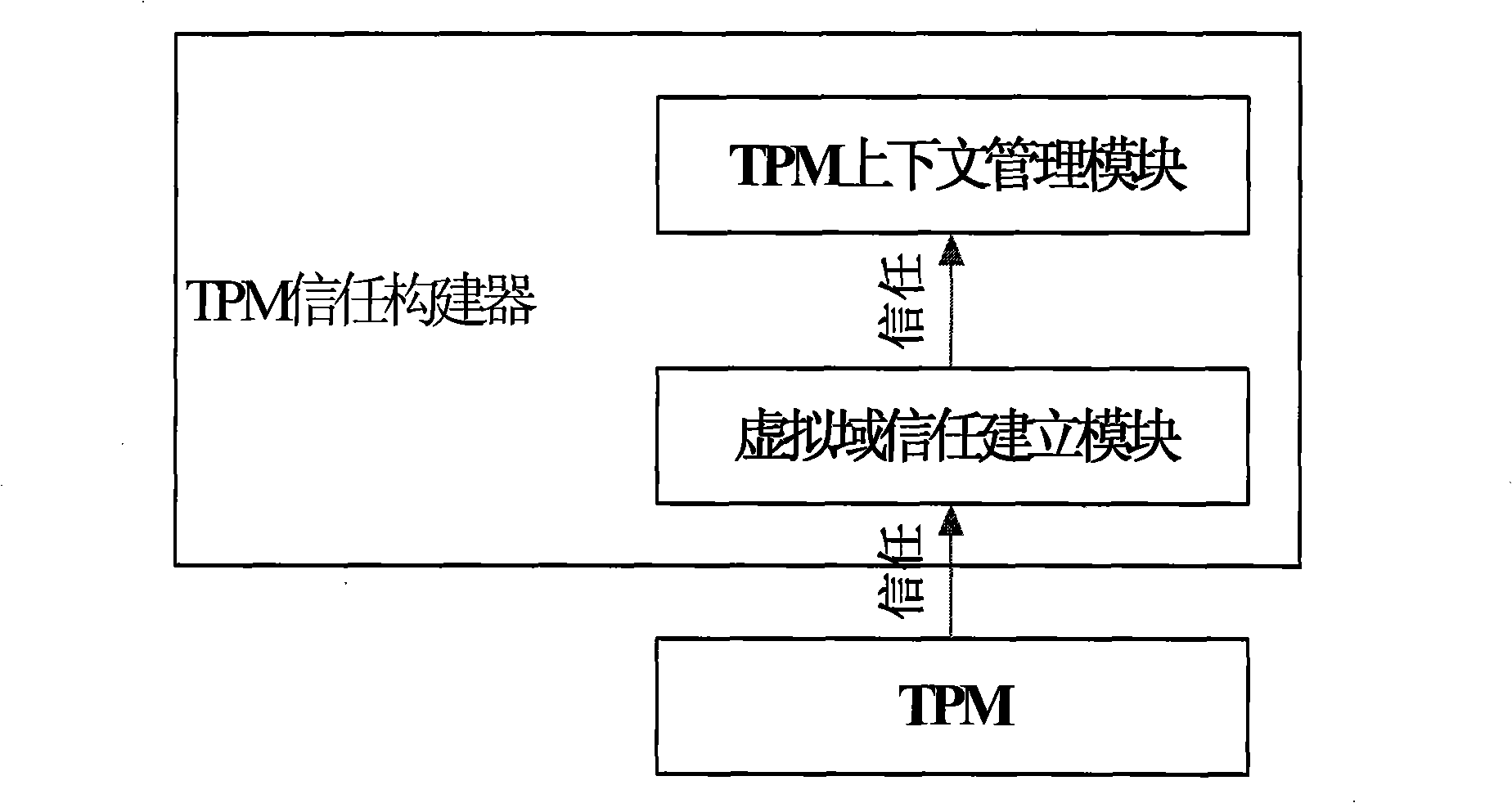
Method for constructing virtual environment trust
ActiveCN101350044ASecure Distributed ApplicationGuaranteed credibilityPlatform integrity maintainanceTrusted applicationIsolating mechanisms
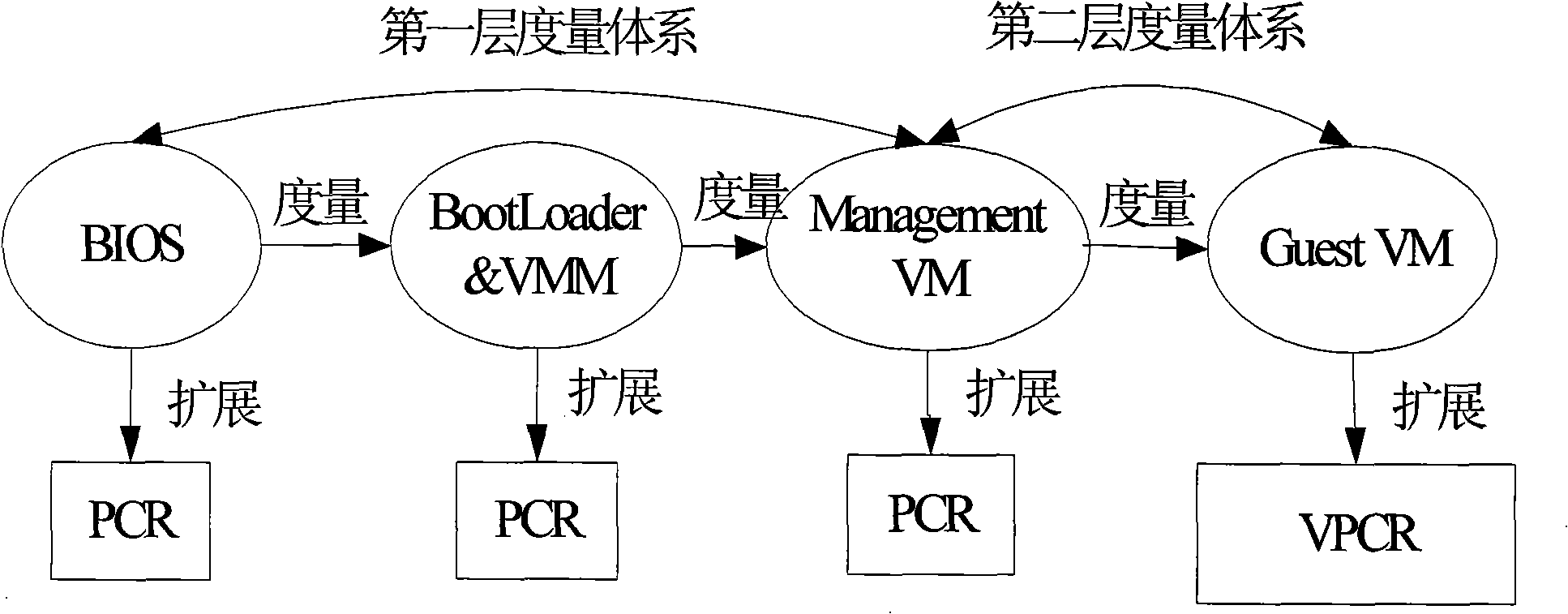
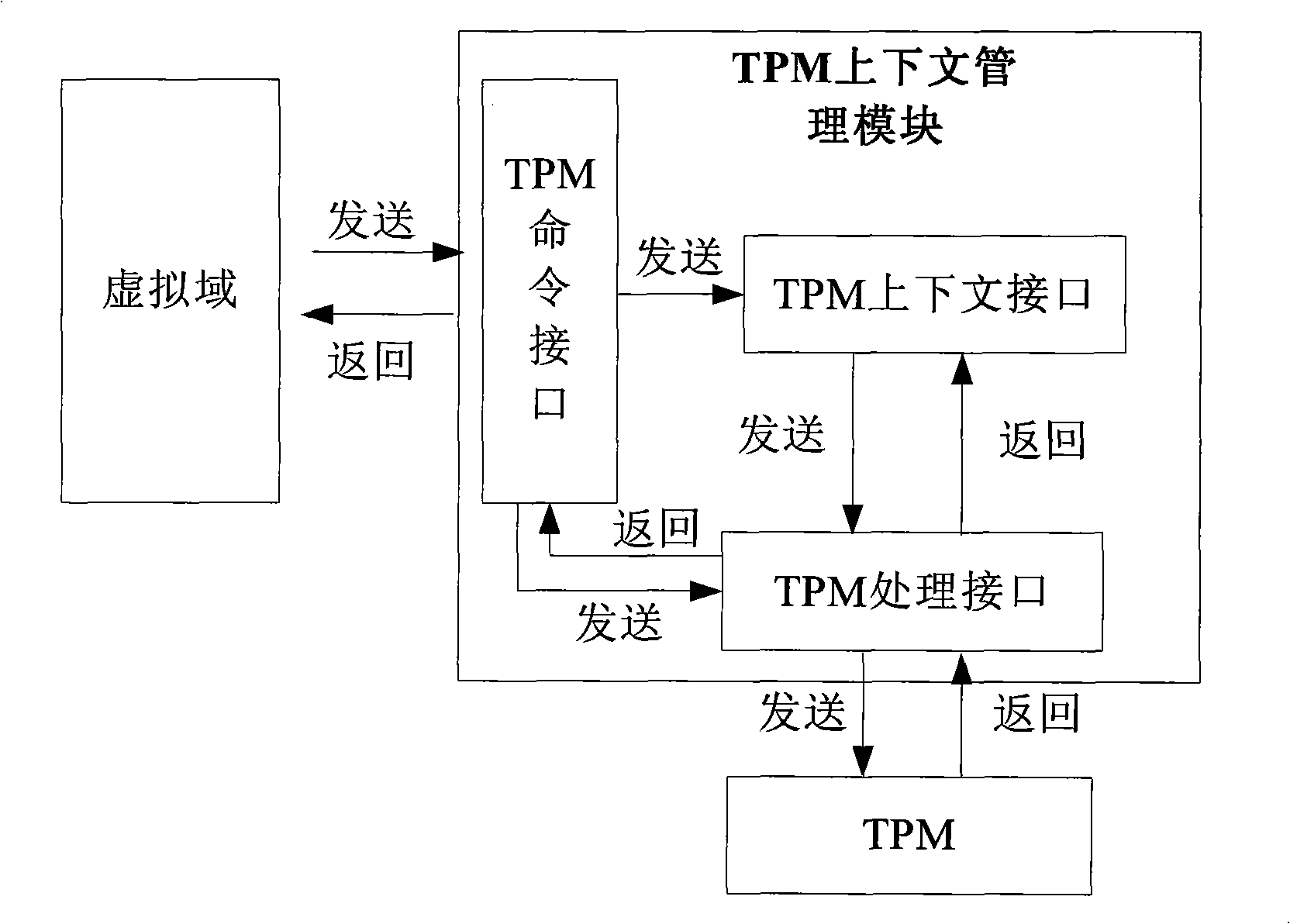
The invention discloses a virtual environment trust building method, which belongs to the trusted computing field in information security. The invention uses a single TPM to realize the trust of one or a plurality of virtual domains and comprises the following steps: firstly, measuring hardware, a virtual layer, a management virtual domain and one or a plurality of application virtual domains in turn by the TPM, realizing the trust of the application virtual domains, secondly, receiving and processing TPM command requests from each virtual domain, and establishing and maintaining TPM context for each virtual domain. The invention has the advantages that firstly, the platform safety and credibility are intensified through a complete trusted isolating mechanism, the trusted application service is better supported, and secondly, the safe sharing of each virtual domain to a trusted hardware root TPM is realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Rockburst grade predicting method based on information vector machine
ActiveCN104732070AOvercoming the lack of low forecasting accuracyGuaranteed credibilityCharacter and pattern recognitionSpecial data processing applicationsFeature vectorRock engineering
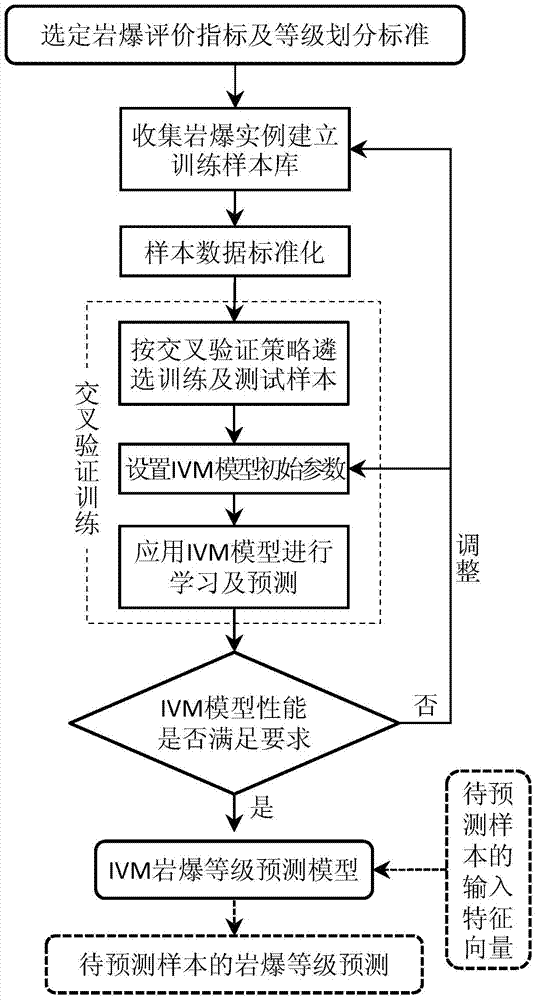
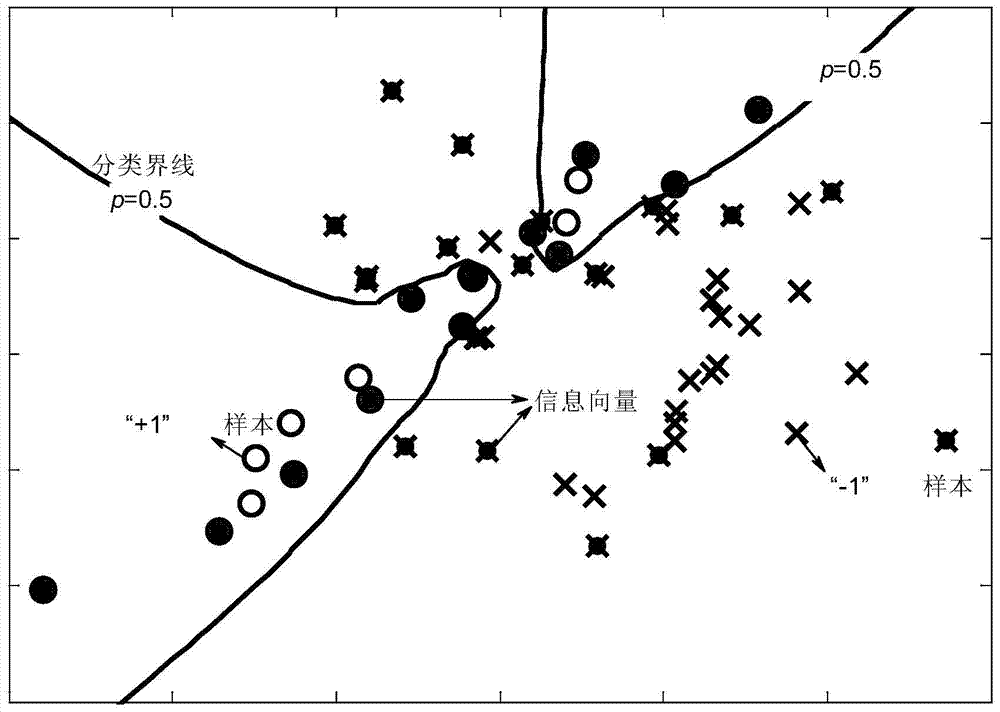
The invention discloses a rockburst grade predicting method based on an information vector machine to mainly solve the problem that in the current underground engineering construction process, the rockburst geological disaster prediction effect is not good. A rockburst evaluation index and a grading standard are selected, and domestic and overseas great deep rock engineering rockburst instances are widely collected to establish an abundant training sample library. A cross validation strategy is utilized for training an IVM model with the superior statistics mode recognition performance, accordingly, a nonlinear mapping relation between the rockburst evaluation index and the rockburst grade is established, model initial parameter setting and the training sample library are adjusted according to the training result, and the IVM model predicting the rockburst grade is finally established. By means of the method to predict the rockburst grade, the complex mechanical analysis or calculation is not needed, only the input feature vector of a sample to be predicted needs to be input in the prediction model, and then the prediction value of the rockburst grade can be obtained. The method is economical, efficient and high in prediction precision and has good engineering application prospects.
Owner:GUANGXI UNIV
Fingerprint identification method
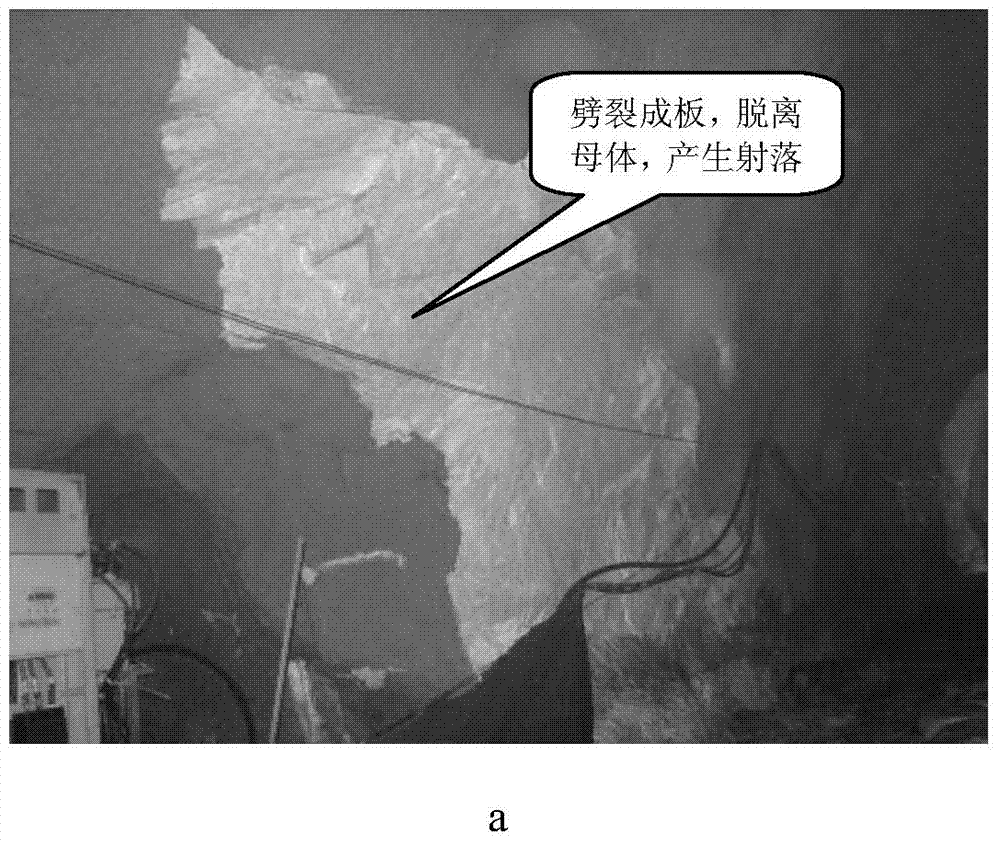
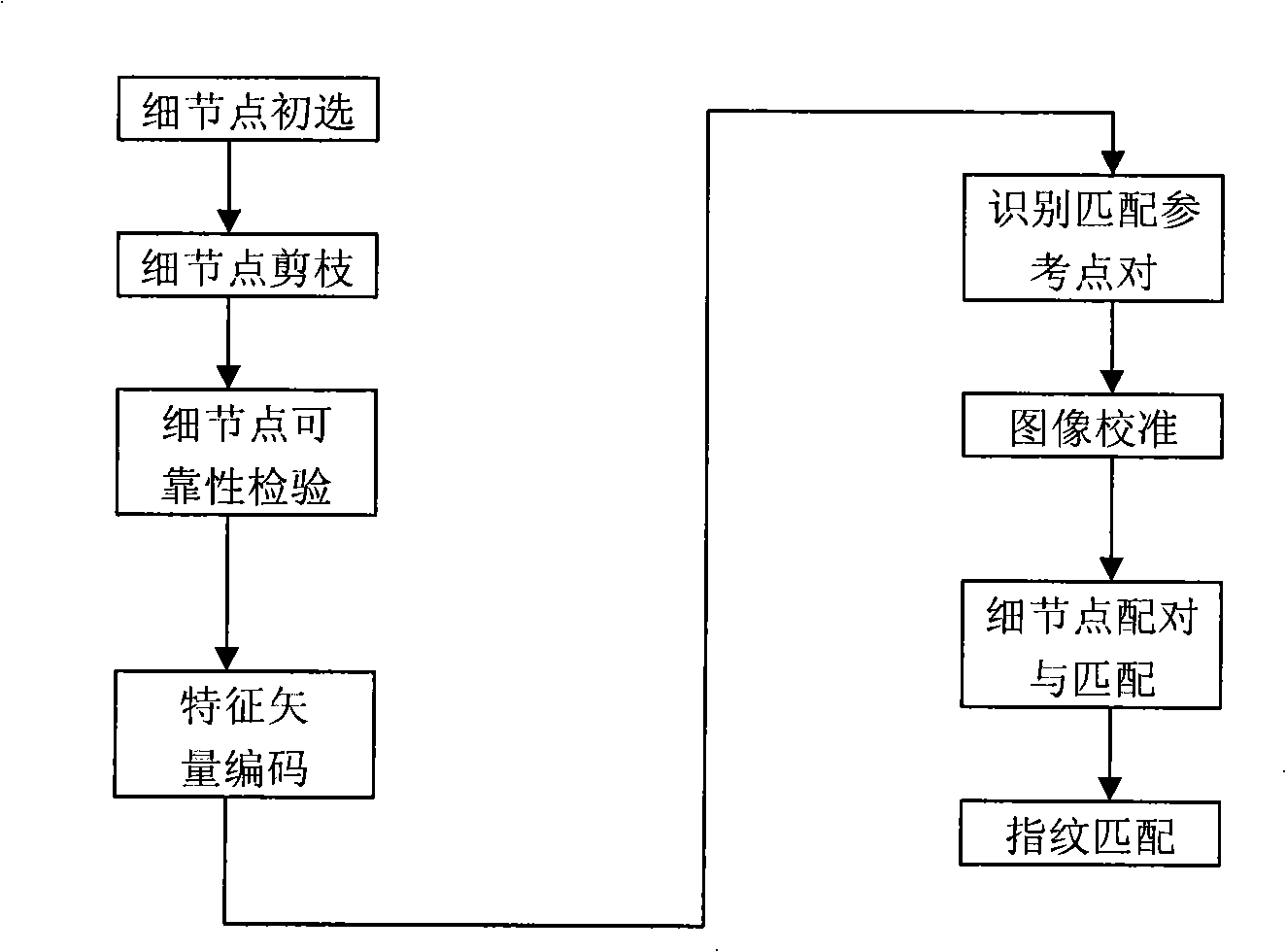
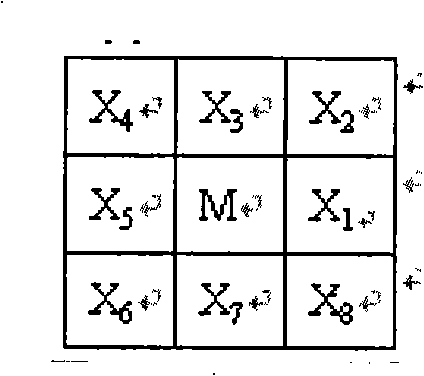
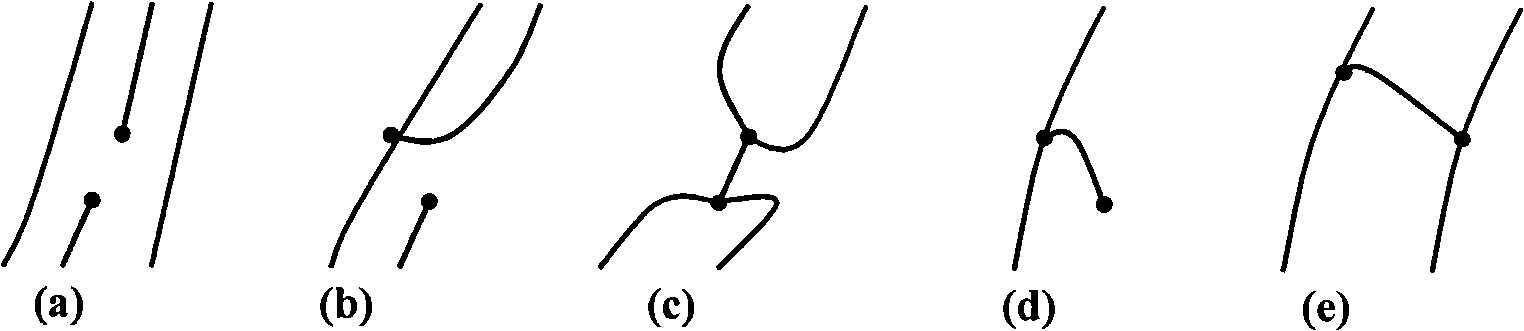
InactiveCN101276411AGuaranteed credibilityImprove robustnessCharacter and pattern recognitionFeature extractionTwo step
The invention relates to a fingerprint identification method, which is composed by two steps of extracting fingerprint characteristics and matching the characteristics: extracting characteristics comprises extracting characteristics of minutia points aiming at the pre-processed fingerprint image, pruning the primarily-selected minutia points, verifying reliability of the characteristics of the minutia points after pruning, and performing characteristic vector coding; characteristics matching at first utilizes the curvature characteristics of ridgeline to calibrate the images for the reduction of complexity of calibration, then uses the adjacent domain relation characteristics of the fingerprint to carry out the computation of matching score and statistic of matching double points, and in accordance with the number of matching double points and the matching score, makes use of multilevel judgement system to judge the similarity of two fingerprints. The invention has the advantages of high identification rate, fast identification speed and strong reliability.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
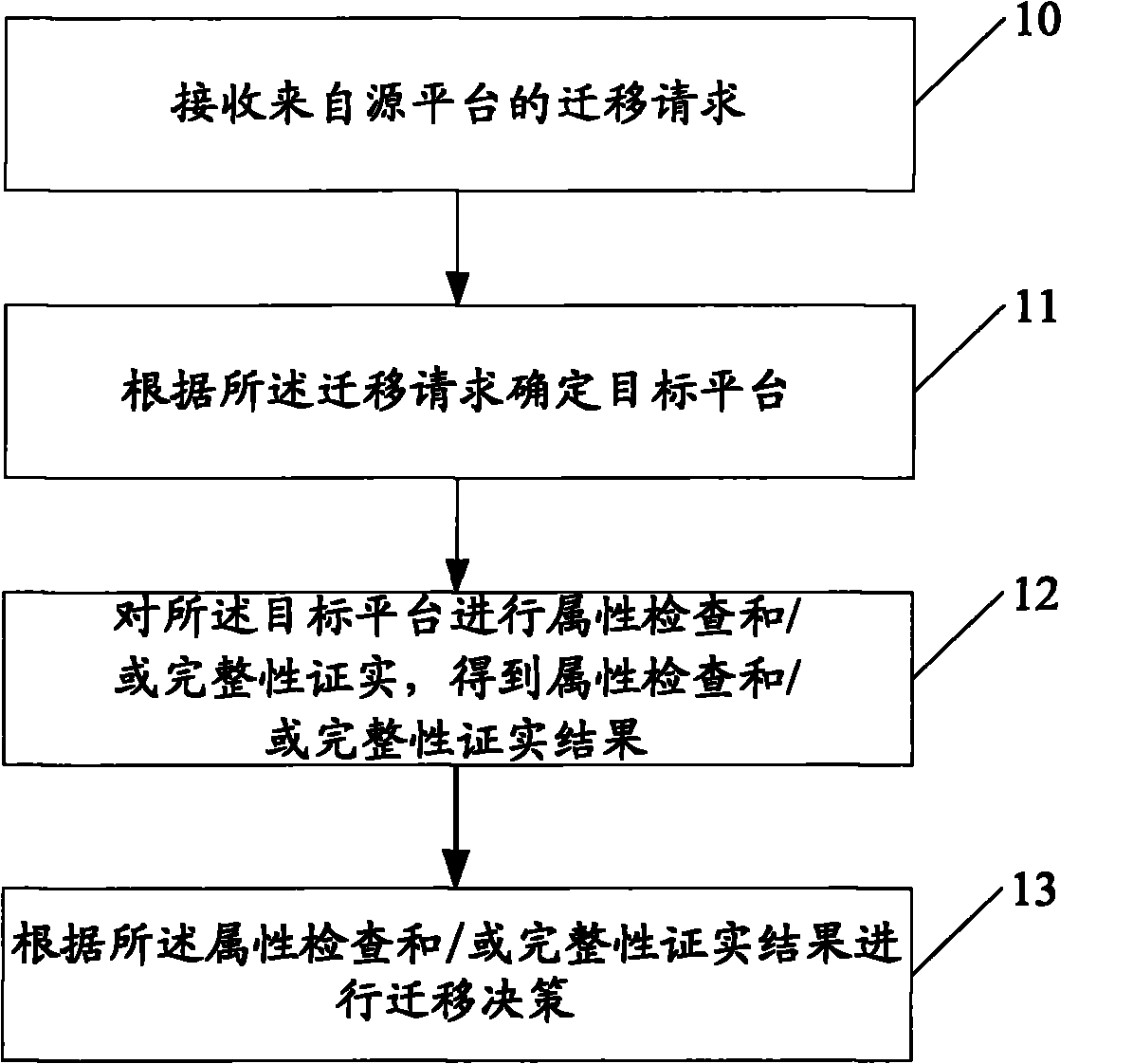
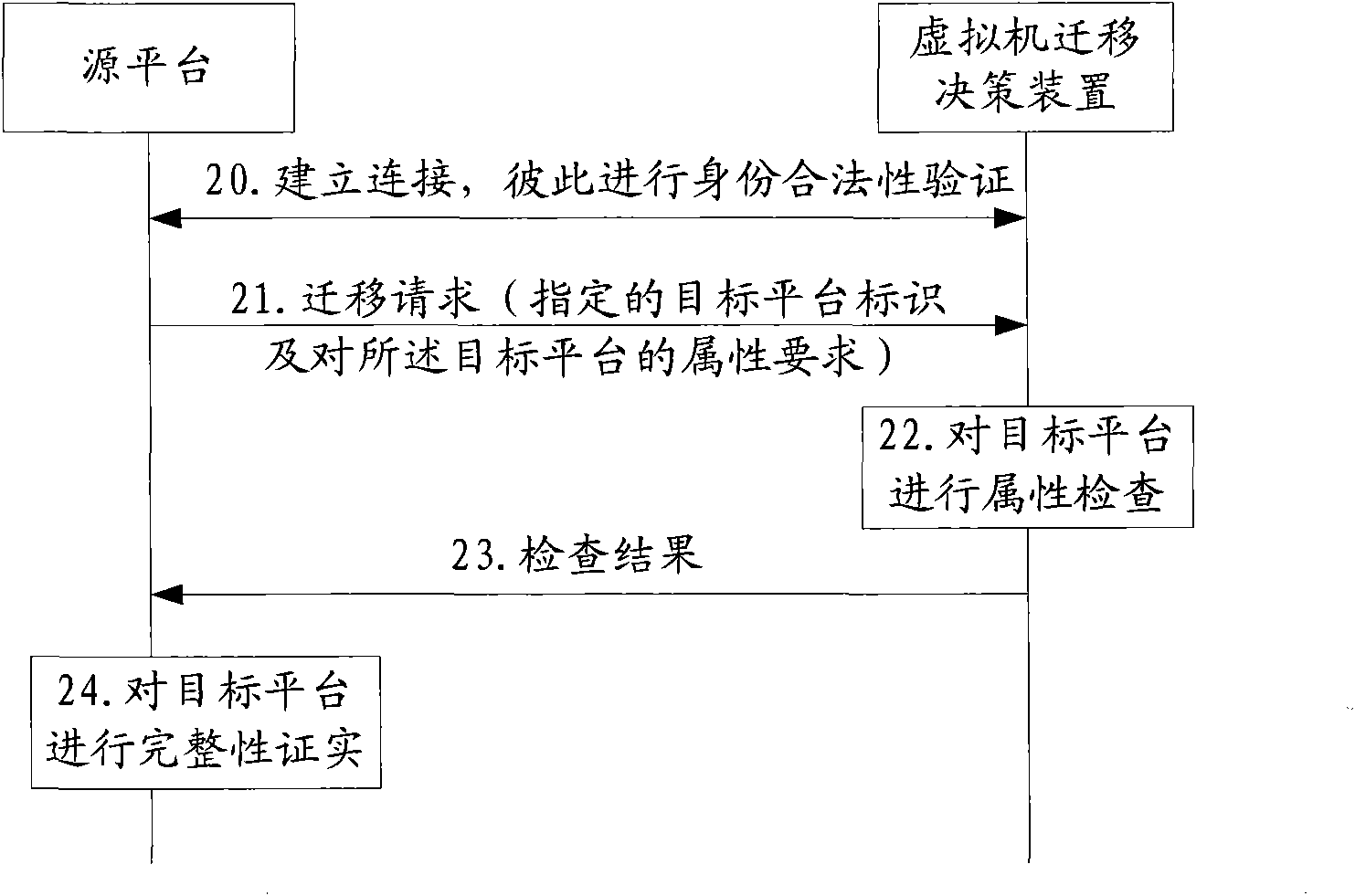
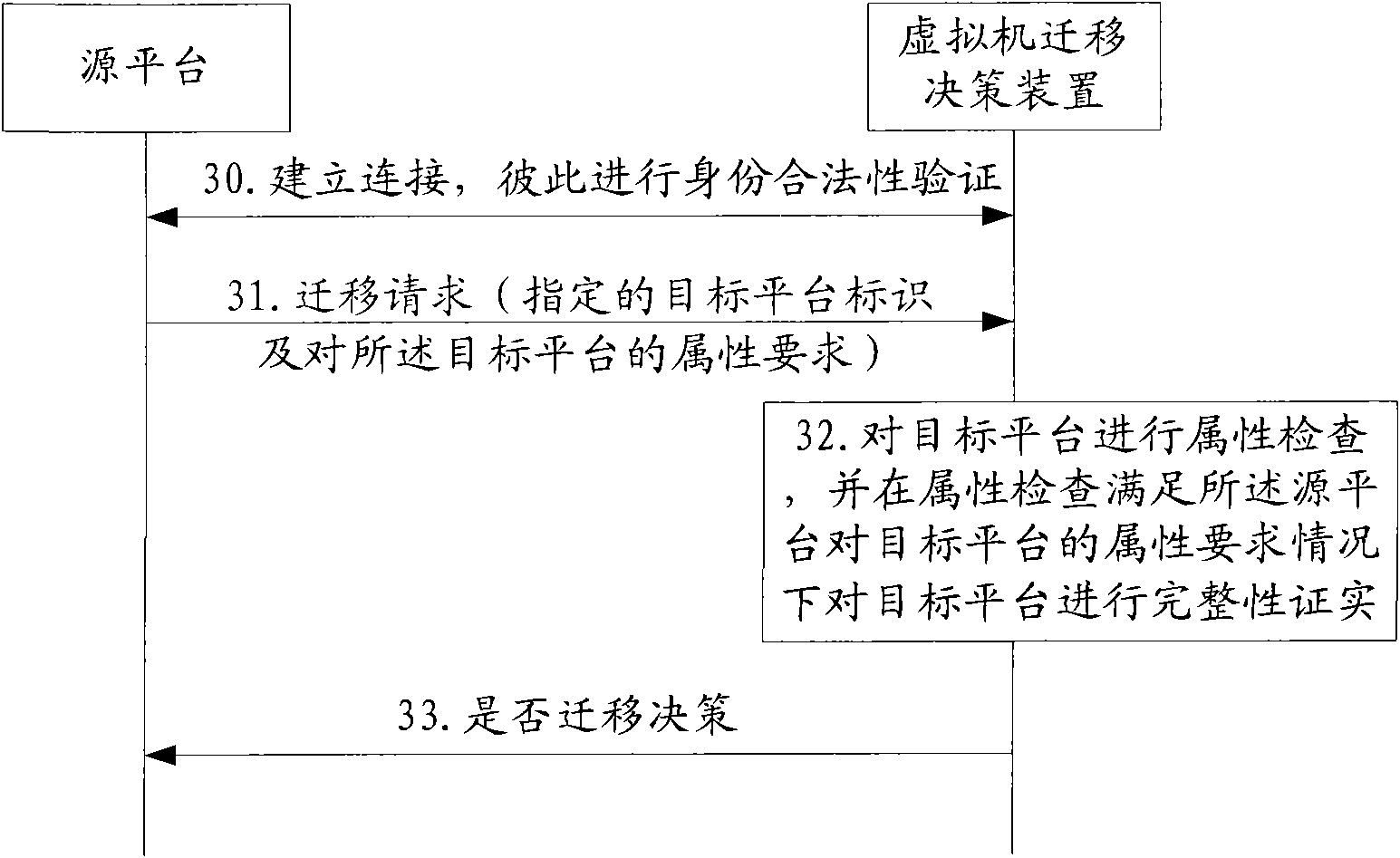
Method, device and system for migration decision-making of virtual machine
InactiveCN101876921AEnsure safetyGuaranteed credibilityMultiprogramming arrangementsTransmissionDecision methodsVirtual machine
The embodiment of the invention discloses a method for migration decision-making of a virtual machine, which comprises the following steps of: receiving a migration request from a source platform; determining a target platform according to the migration request; performing attribute inspection or integrity confirmation on the target platform so as to obtain a result of the attribute inspection or the integrity confirmation; and performing the migration decision-making according to the result of the attribute inspection or the integrity confirmation. The embodiment of the invention also provides a device and a system for the migration decision-making of the virtual machine. In the embodiment of the invention, the attribute inspection or the integrity confirmation of the target platform is performed before the migration of the virtual machine, so the safety and the reliability of the migration of the virtual machine are effectively ensured.
Owner:HUAWEI TECH CO LTD +1
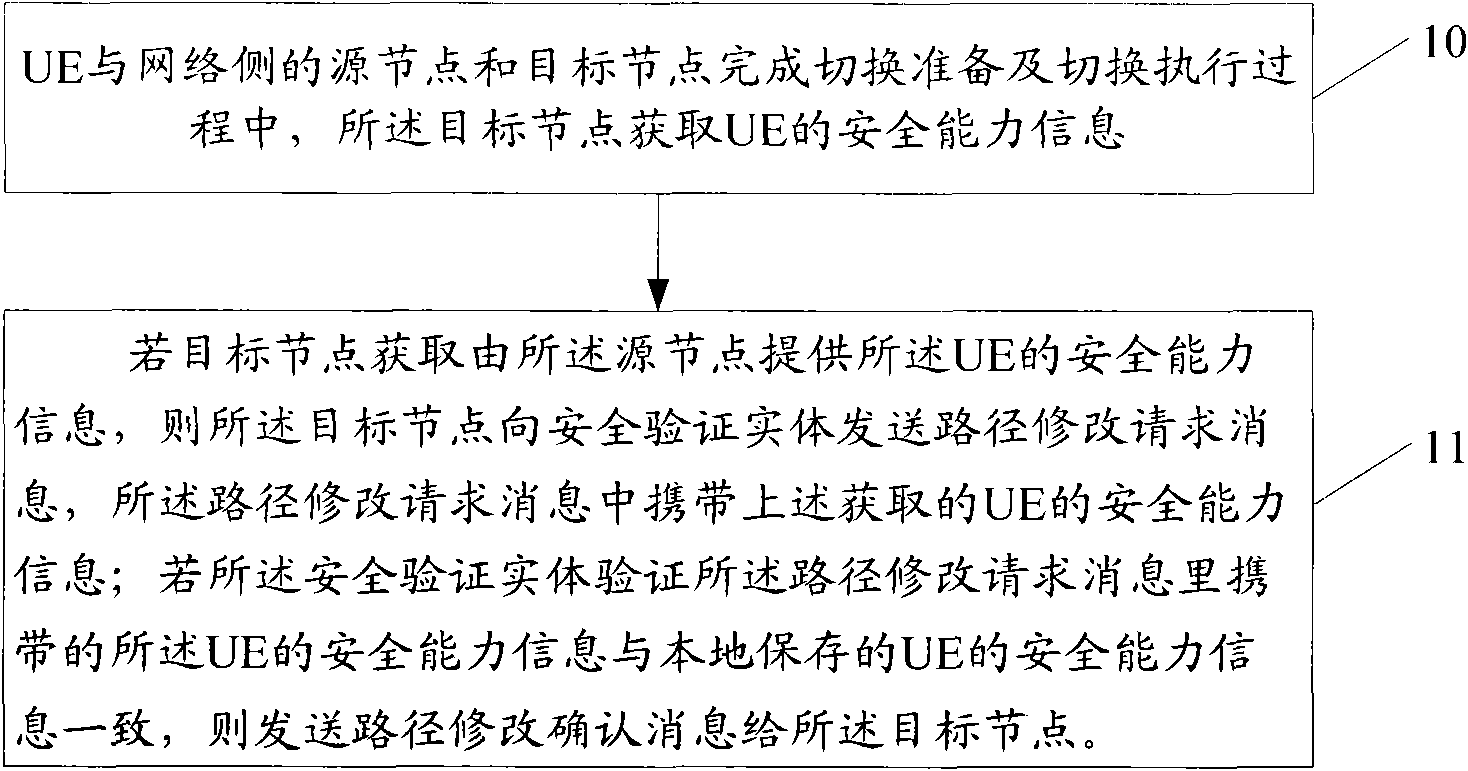
Security processing method, device and system in conversion process
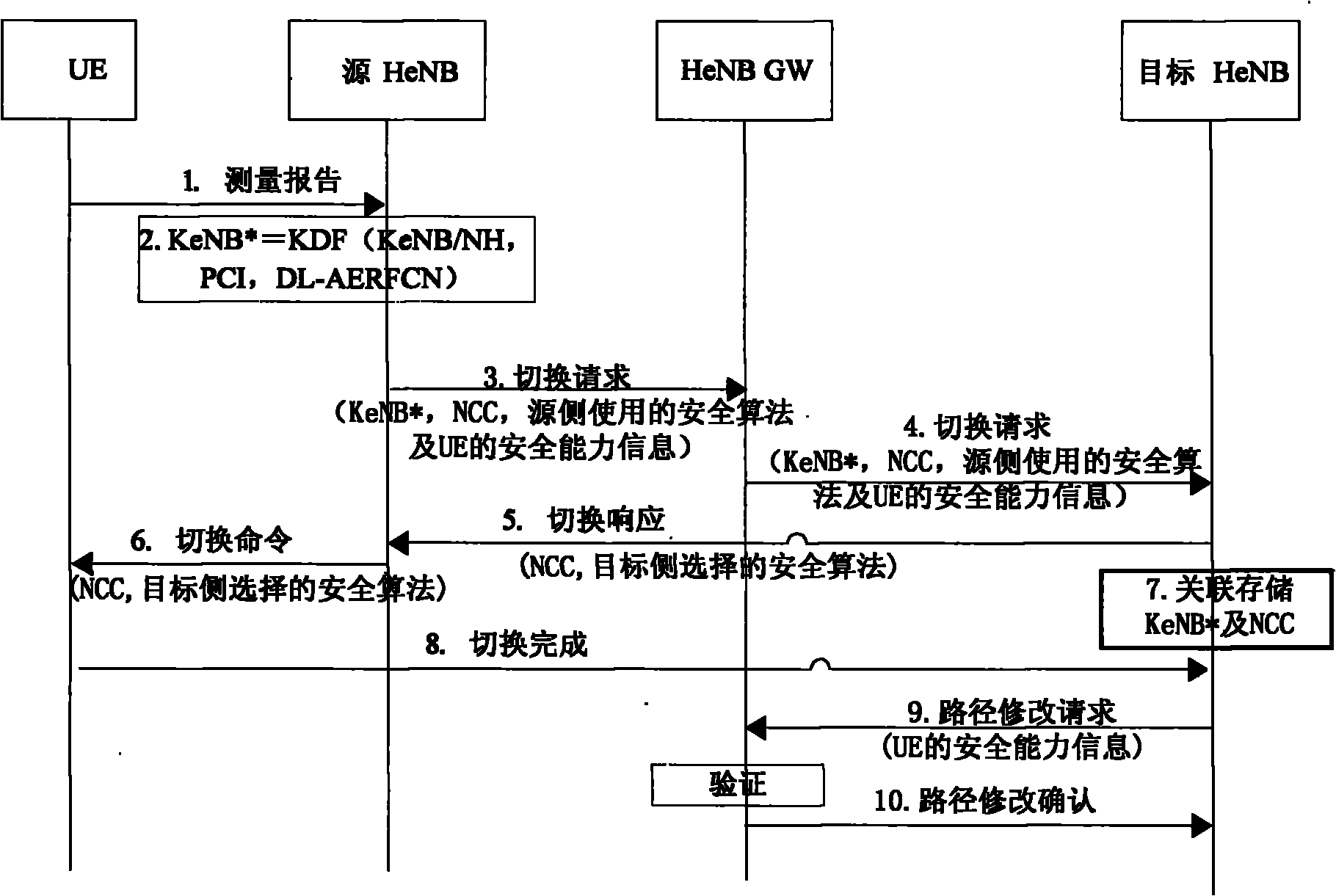
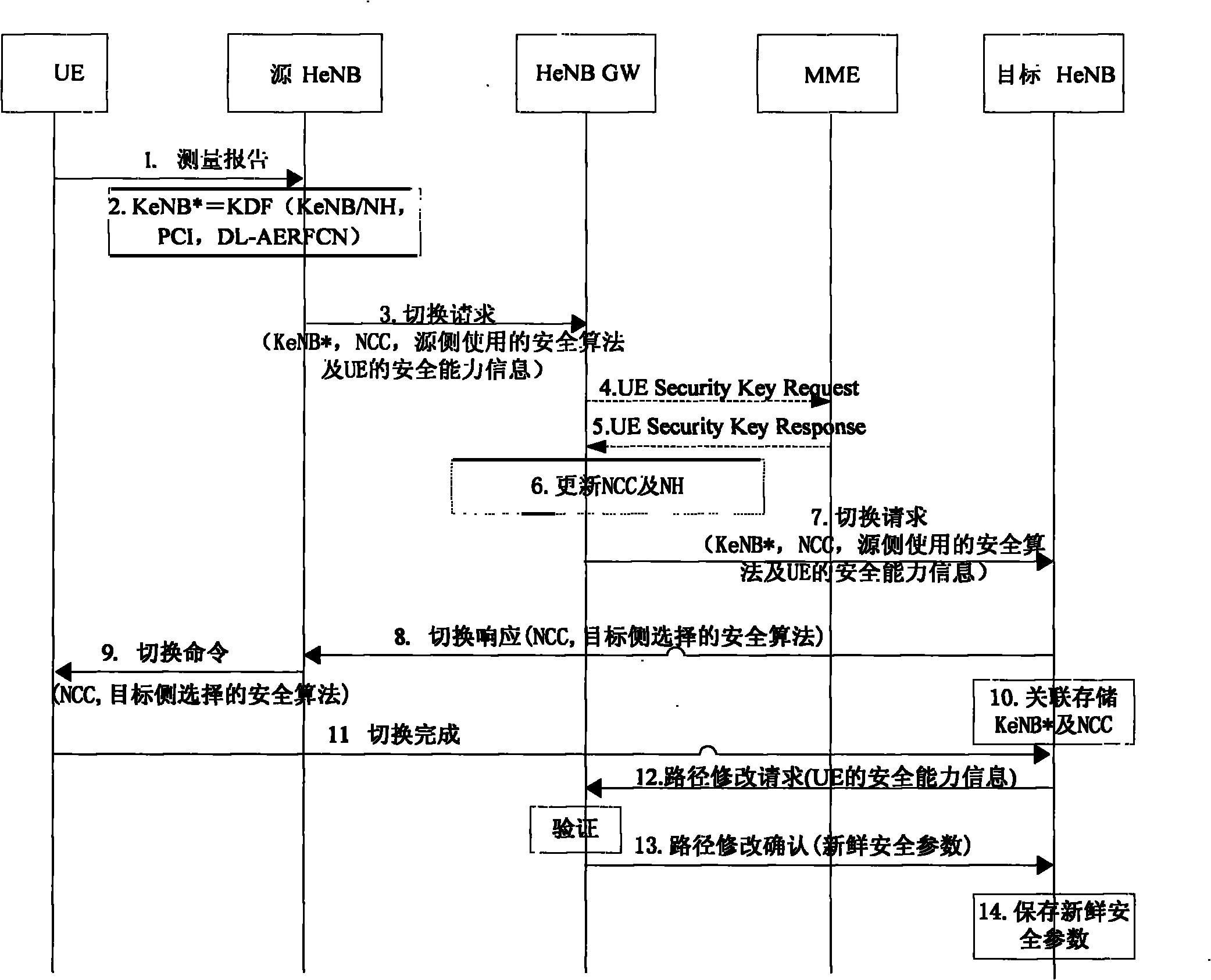
InactiveCN102340772AImprove securityGuaranteed credibilityAssess restrictionNetwork topologiesSecurity validationAnchor point
The invention provides a security processing method, device and system in a conversion process, which belong to the technical field of communication. UE (User Equipment), and a source node and a target node at the side of a network finish conversion preparation, and in a conversion execution process, the target node acquires the security capability information of the UE, provided by the source node or a security verification entity. The security verification entity comprises a gateway in an UE conversion scene under a base station or an anchor point base station in the UE conversion scene under a relay node. If the source node provides the security capability information of the UE, the method also comprises the following step of: sending routine correction confirm information to the target node if the security verification entity verifies that the security capability information of the UE in routine correction request information is consistent with the security capability information of the UE, which is locally saved. The embodiment of the invention ensures that the target node can select proper secure algorithm, so that the security of the optimized conversion process is further improved.
Owner:HUAWEI TECH CO LTD
Evidence storage method, evidence verification method and device, equipment and medium
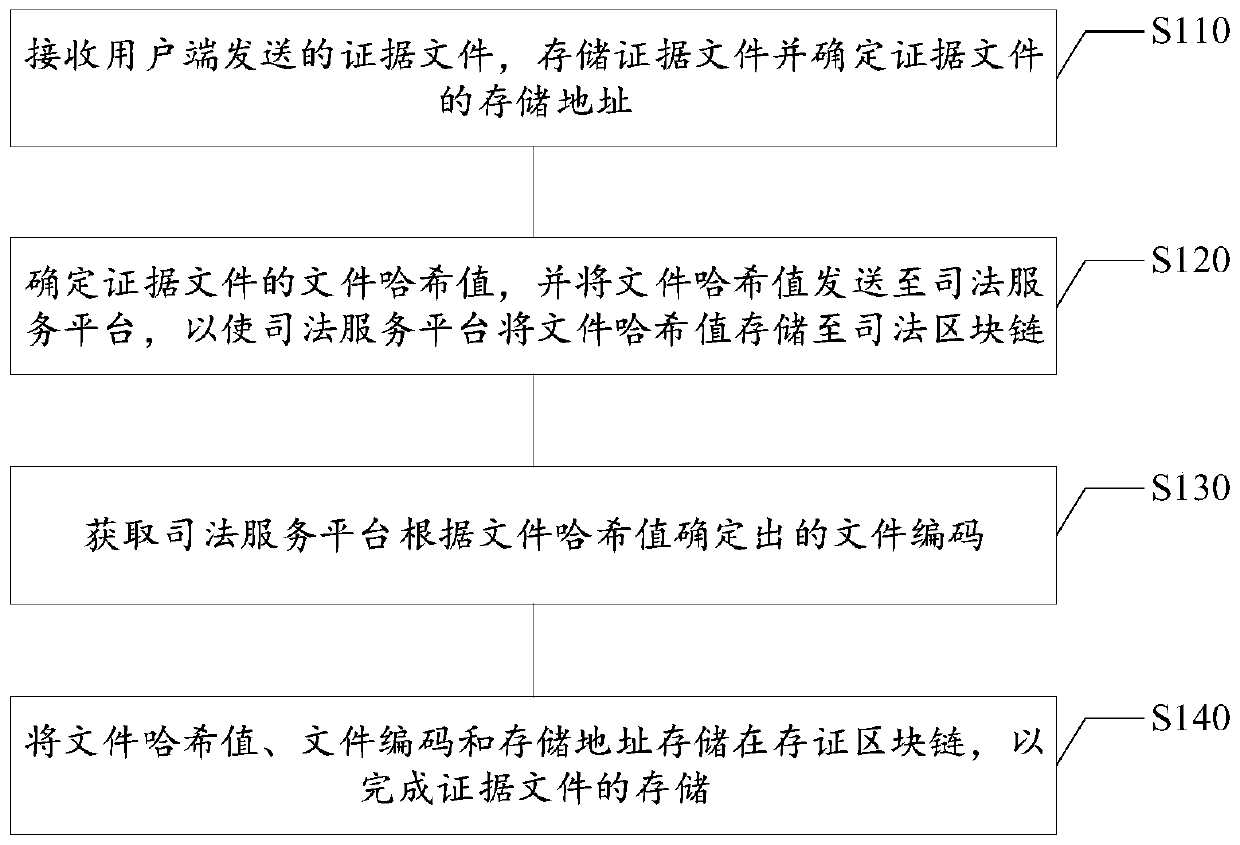
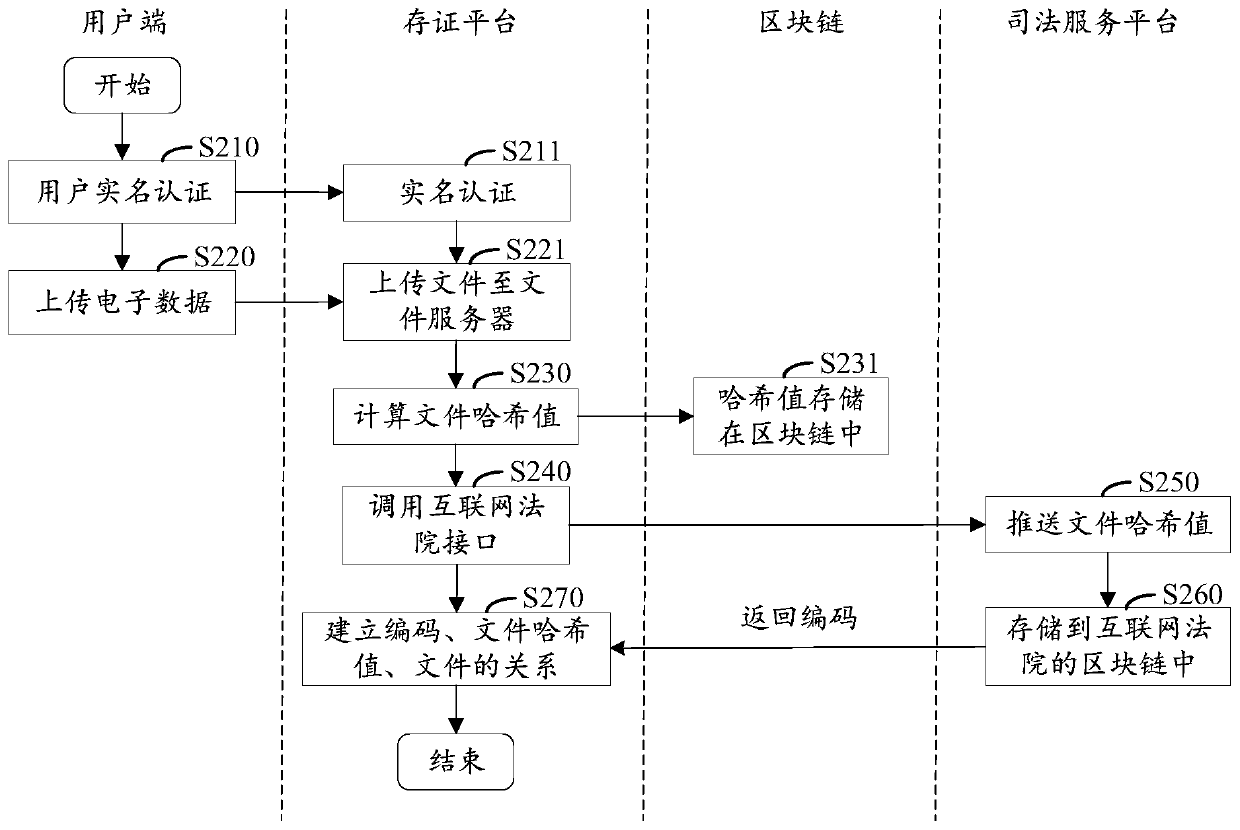
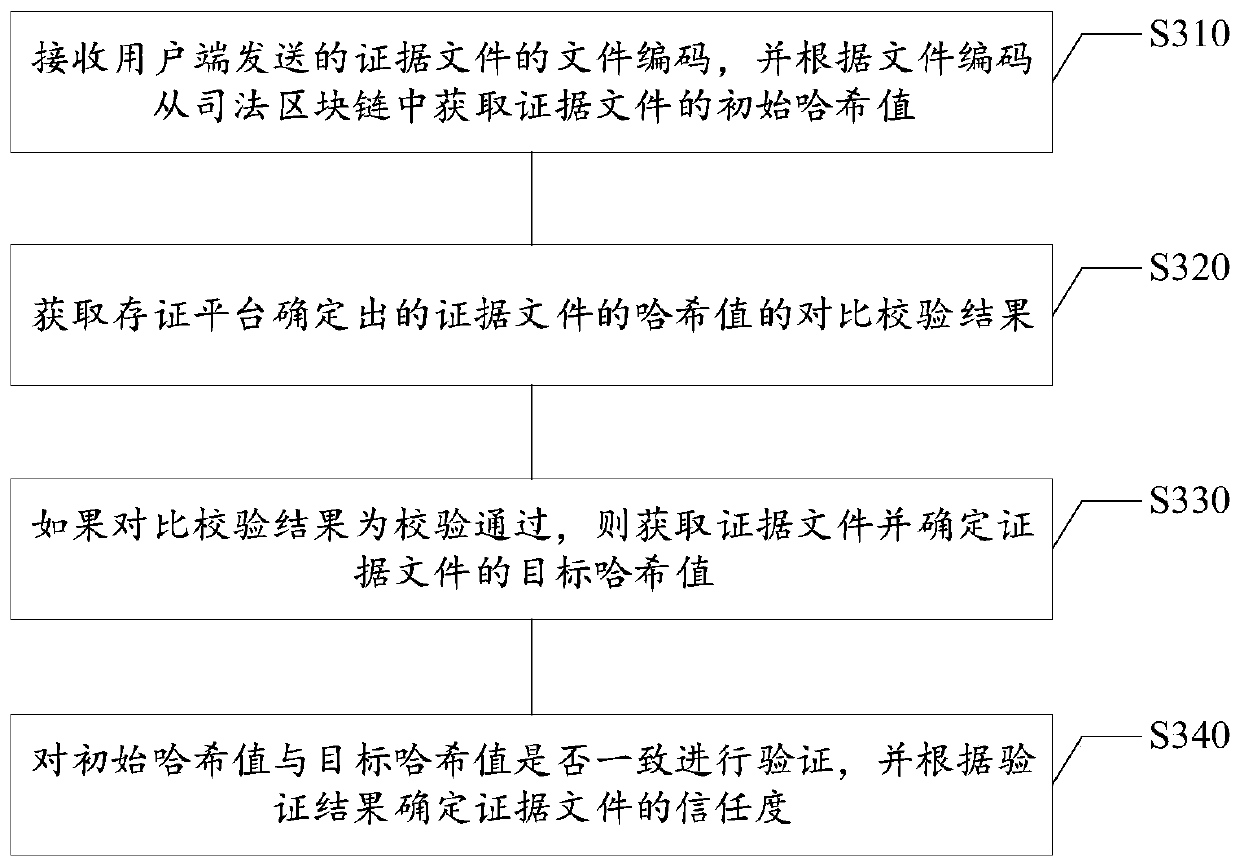
PendingCN110879903AGuarantee authenticityGuaranteed credibilityDigital data protectionInternal/peripheral component protectionEngineeringDatabase
The invention relates to an evidence storage method, an evidence verification method and a device based on a blockchain, electronic equipment and a storage medium, relates to the technical field of blockchain application, and can be applied to a scene of storing and verifying electronic evidences in judicial procedures. The evidence storage method based on the blockchain comprises the steps of receiving an evidence file sent by a user side, storing the evidence file and determining a storage address of the evidence file; determining a file hash value of the evidence file, and sending the filehash value to a judicial service platform, so that the judicial service platform stores the file hash value to a judicial blockchain; obtaining a file code determined by the judicial service platformaccording to the file hash value; and storing the file hash value, the file code and the storage address in an evidence storage blockchain to finish the storage of the evidence file. According to themethod, the blockchain technology can be introduced into the data evidence storage platform, so that the electronic evidence can be stored and verified based on the blockchain technology.
Owner:JD DIGITS HAIYI INFORMATION TECHNOLOGY CO LTD
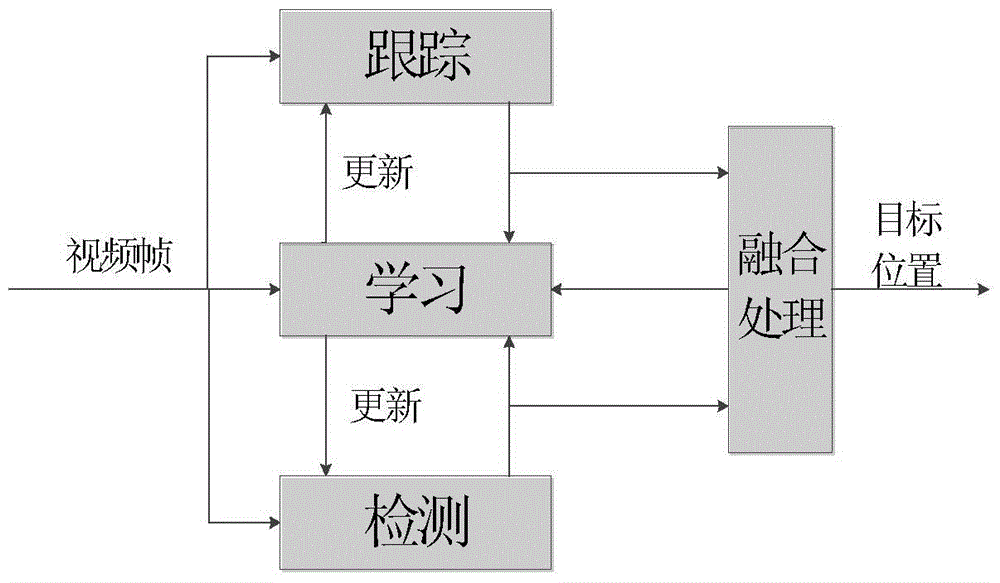
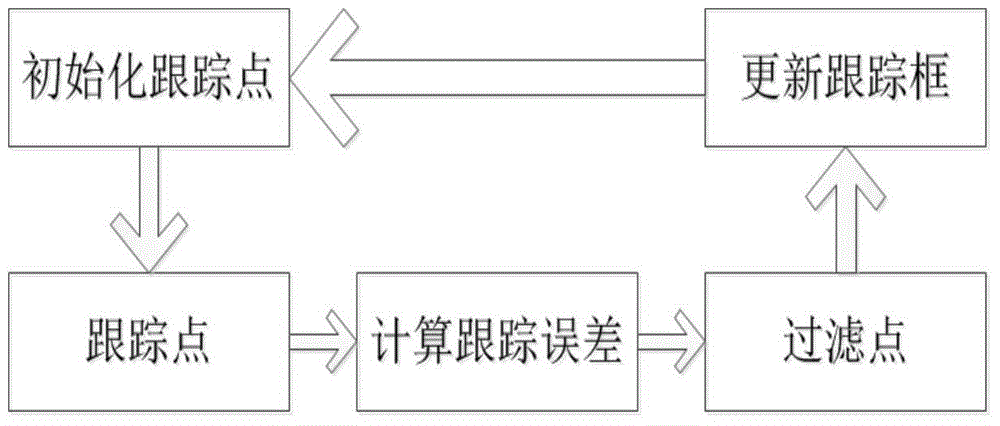
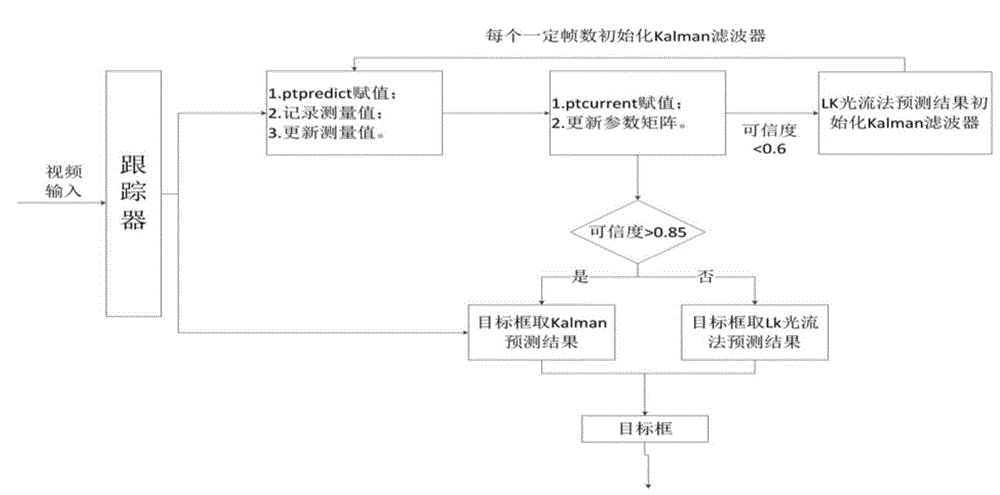
Kalman filtering and TLD (tracking-learning-detection) algorithm integrated target tracking method
InactiveCN104574439AGuaranteed credibilityIncrease sampling rateImage enhancementImage analysisKaiman filterAlgorithm
The invention discloses a Kalman filtering and TLD (tracking-learning-detection) algorithm integrated target tracking method. The method comprises steps as follows: firstly, the principle of a Kalman filter is analyzed, and the Kalman filter is improved; then a TLD algorithm is enhanced by the aid of the improved Kalman filter, and the reliability of a system is improved; finally, a detection module is improved by the aid of a prediction result obtained through the improved Kalman filter, the detection area of the TLD algorithm is reduced, and the tracking instantaneity is further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Modular computer forensic system and method based on hardware virtualization
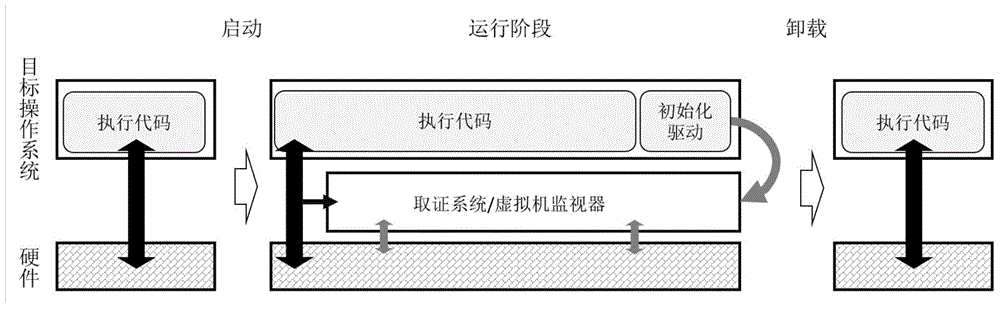
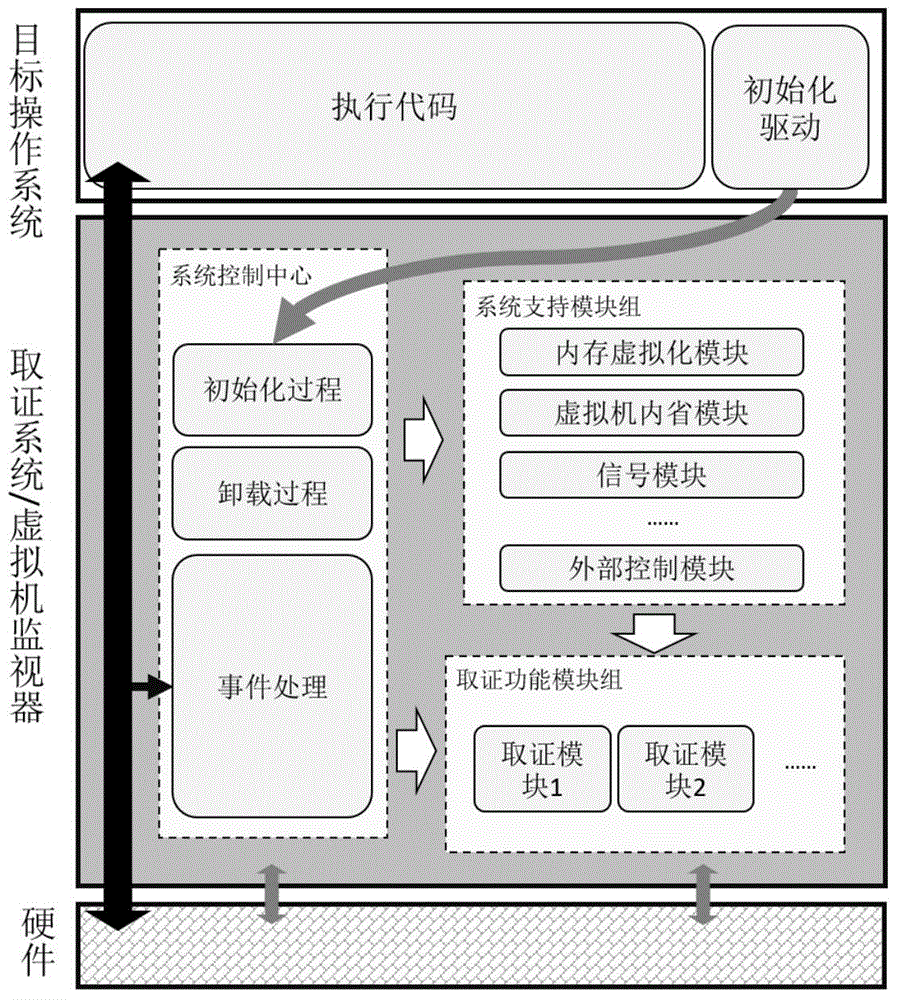
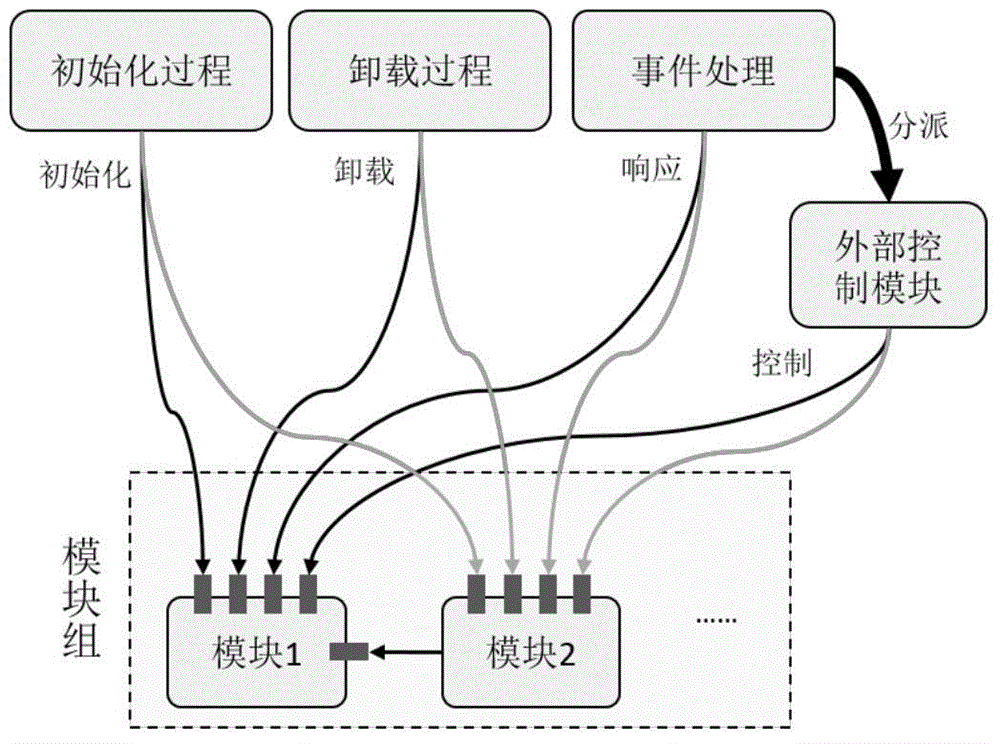
InactiveCN104021063AAvoid lossPrevent tamperingHardware monitoringSoftware simulation/interpretation/emulationModularityData virtualization
The invention discloses a modular computer forensic system and method based on hardware virtualization. The modular computer forensic system comprises an initialization drive, a system control center, a system support module set and a forensic function module set. The method is based on the hardware virtualization technology, a light virtual machine is set up through the initialization drive when an operation system operates, the system control center supports a hardware virtual platform and manages all sub modules, and the system support module set supports all basic functions of the forensic module set. According to the method, interfaces of the forensic function module set are standardized, multiplexing and extension of the modules are supported, and forensic tools can focus on the core function, and a large amount of repetitive work is reduced; no codes of the target operation system need to be modified, performance losses are low, memory usage is less, a safe and credible real-time forensic foundation platform is set up, and convenience is brought to acquisition of the various forensic tools based on virtualization.
Owner:NANJING UNIV
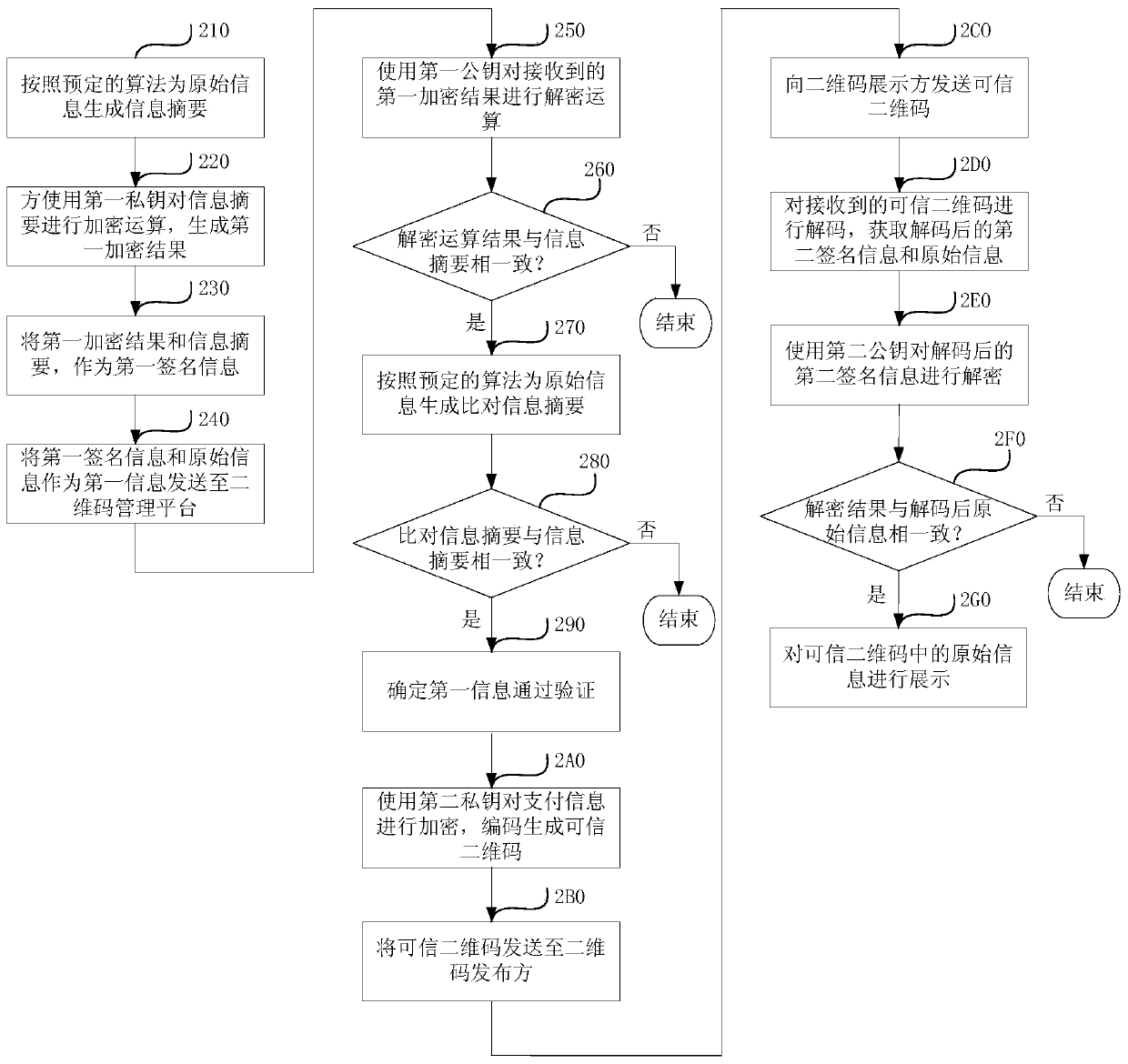
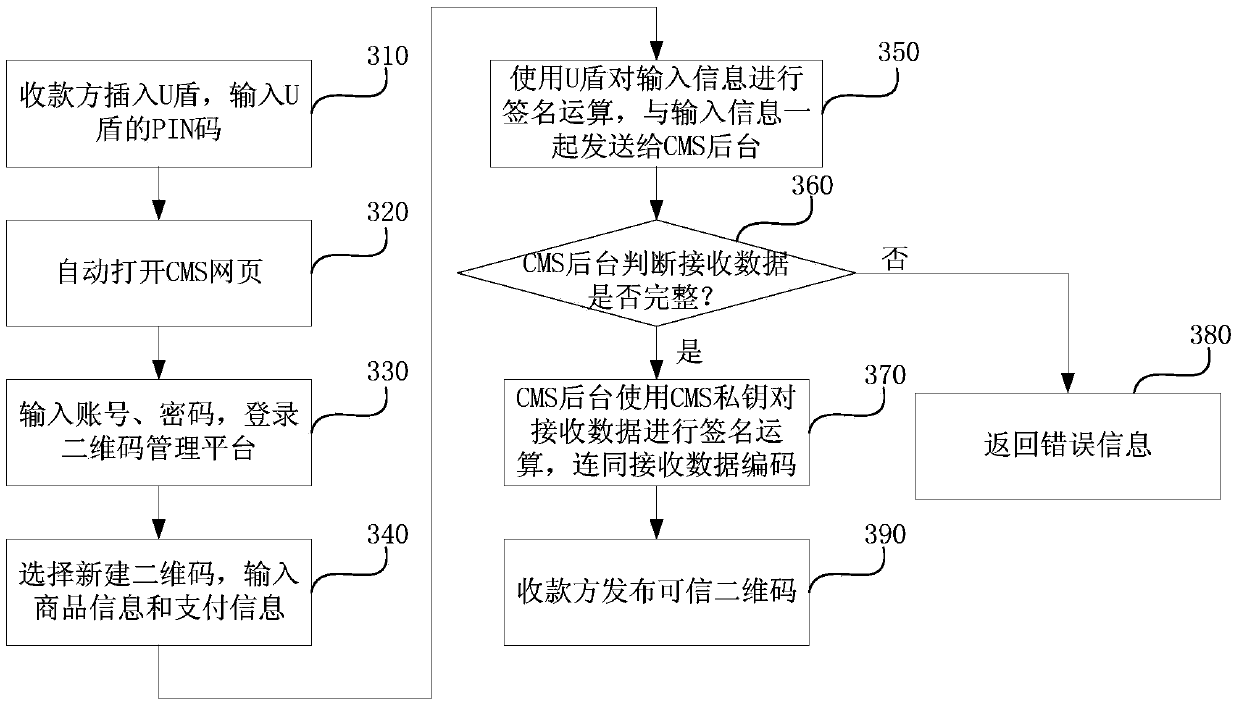
Safety payment method and device based on credible two-dimension code
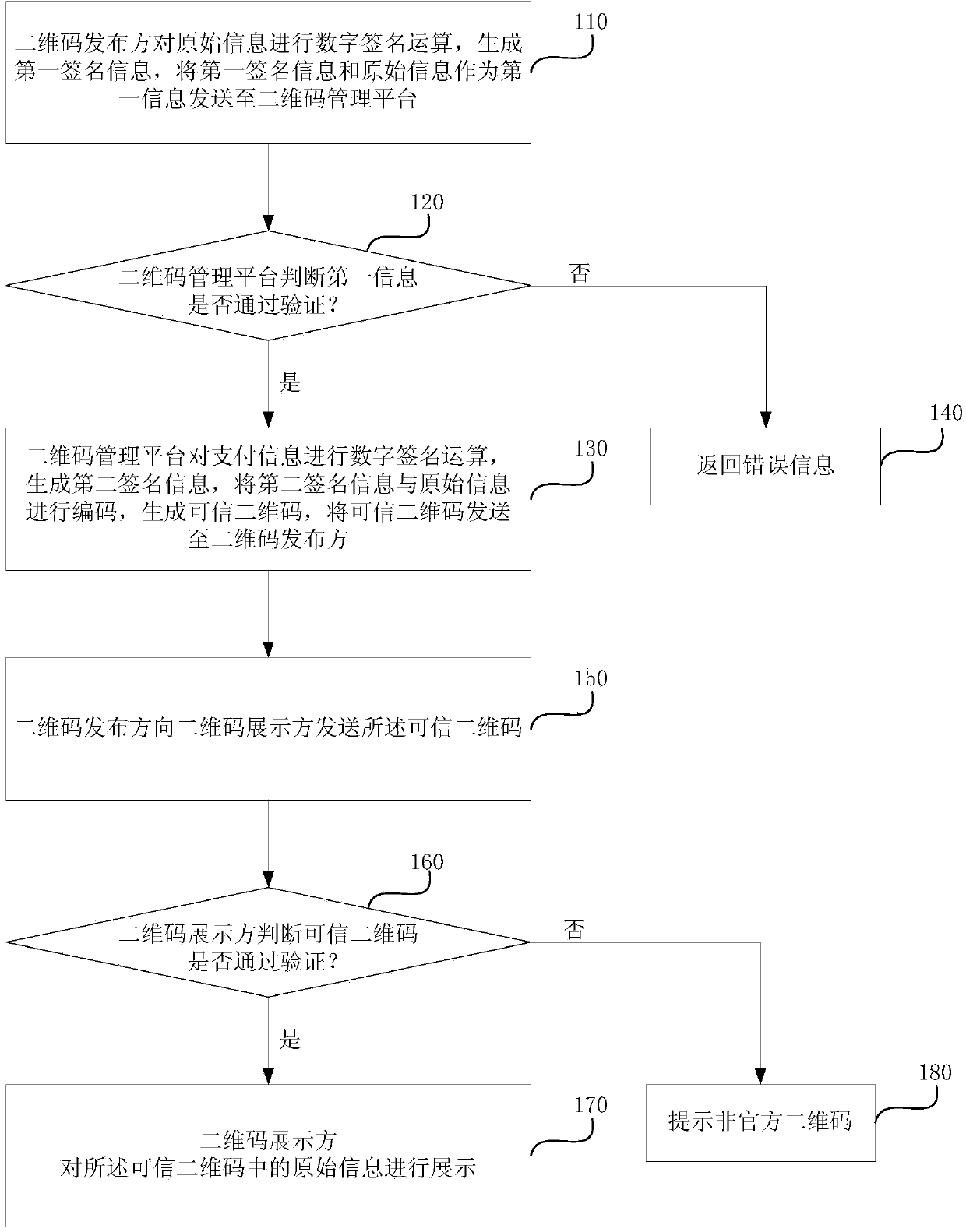
ActiveCN103617531AGuaranteed credibilityReduce riskRecord carriers used with machinesProtocol authorisationDigital signatureTheoretical computer science
The invention discloses a safety payment method and system based on a credible two-dimension code. The safety payment method comprises the steps that a two-dimension code publisher performs digital signature computation on original information to generate first signature information and sends the first signature information and the original information, as first information, to a two-dimension code management platform; the two-dimension code management platform verifies the first information, performs digital signature computation on payment information to generate second signature information when the first information passes the verification, encodes the second signature information and the original information to generate the credible two-dimension code, and sends the credible two-dimension code to the two-dimension code publisher; the two-dimension code publisher sends the credible two-dimension code to a two-dimension code displayer; the two-dimension code displayer verifies the credible two-dimension code, and displays the original information in the credible two-dimension code when the credible two-dimension code passes the verification. According to the method and the device, the risk of a user in the two-dimension code using process is reduced, the safety of the two-dimension code is ensured, and the reliability of the two-dimension code payment system is further improved.
Owner:SUNYARD SYST ENG CO LTD
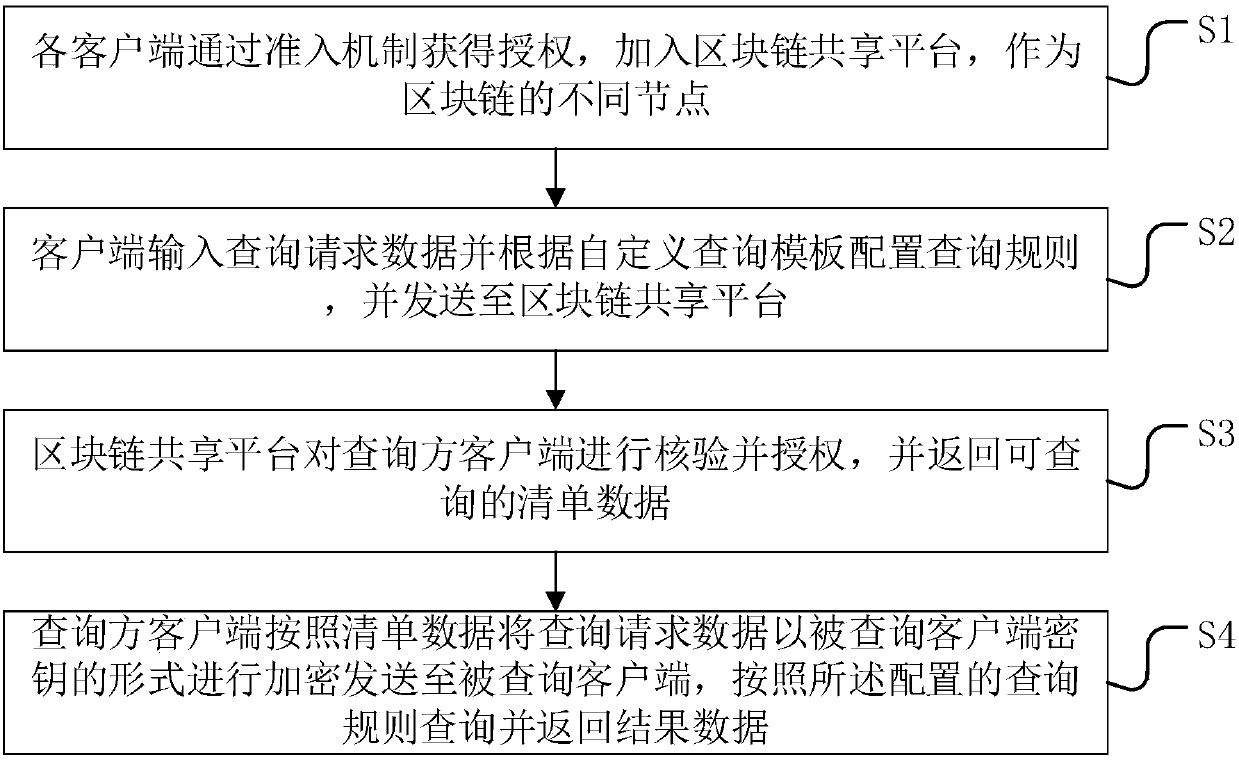
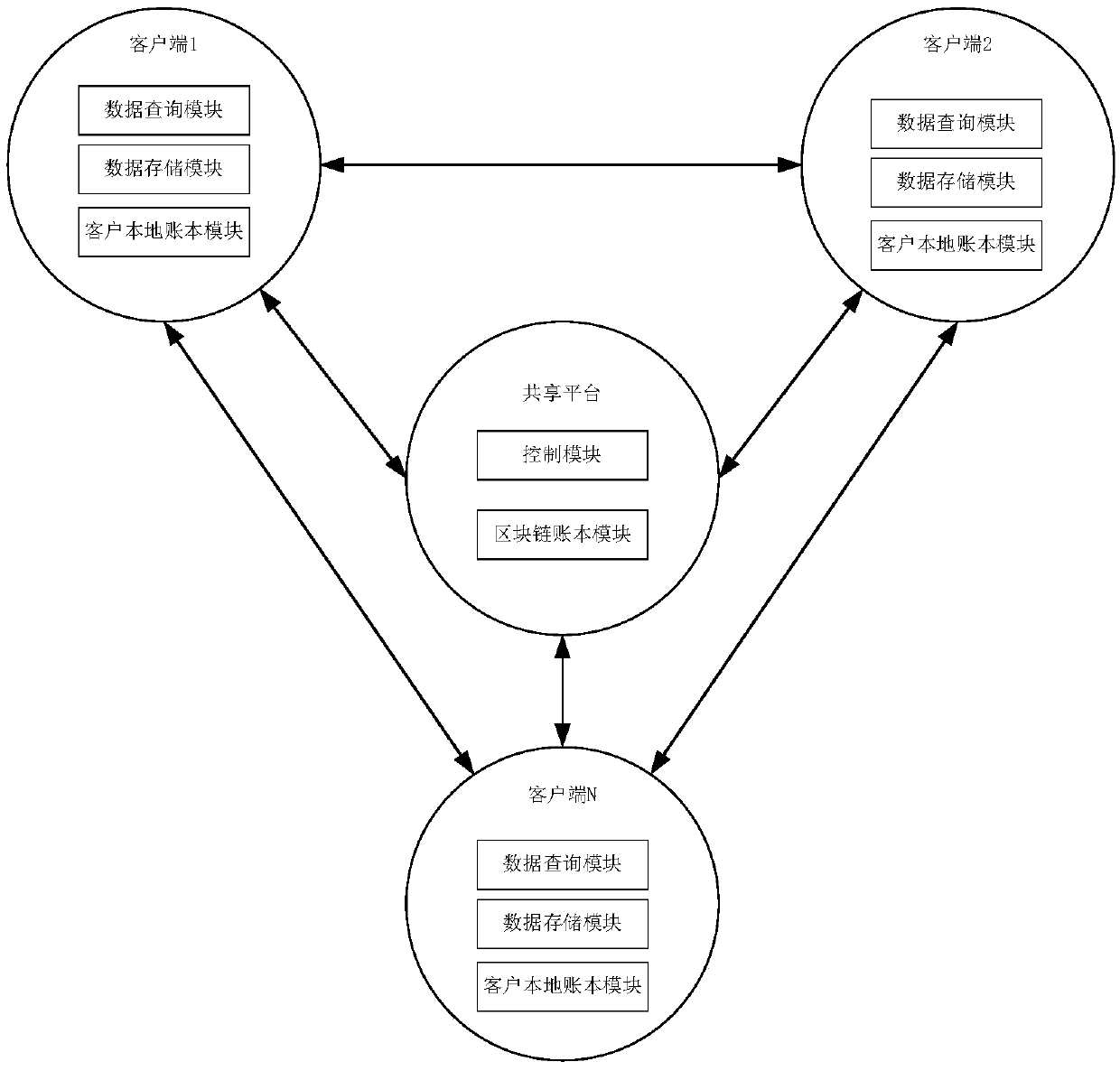
Financial institution user data sharing method and system based on a block chain technology
The invention provides a financial institution user data sharing method and system based on a block chain technology, and the method comprises the steps: S1, enabling each client to obtain authorization through an admission mechanism, and adding the authorization into a block chain sharing platform to serve as different nodes of a block chain; S2, enabling the client to input query request data and configures a query rule according to a user-defined query template; S3, enabling the block chain sharing platform to verify and authorize the query party client, and return inquirable list data; AndS4, enabling the query party client to encrypt the query request data in the form of a queried client key according to the list data, and querie and return result data according to the configured query rule. According to the method, financial platform user data sharing is achieved, desensitization, encryption and other technologies are adopted for multiple protection, original data cannot be checked, and the safety and integrity of the data cannot be affected; Based on the blockchain technology, a distributed transaction account book is co-built, and query information is accurately recorded and cannot be tampered.
Owner:青岛中瑞云数科技有限公司
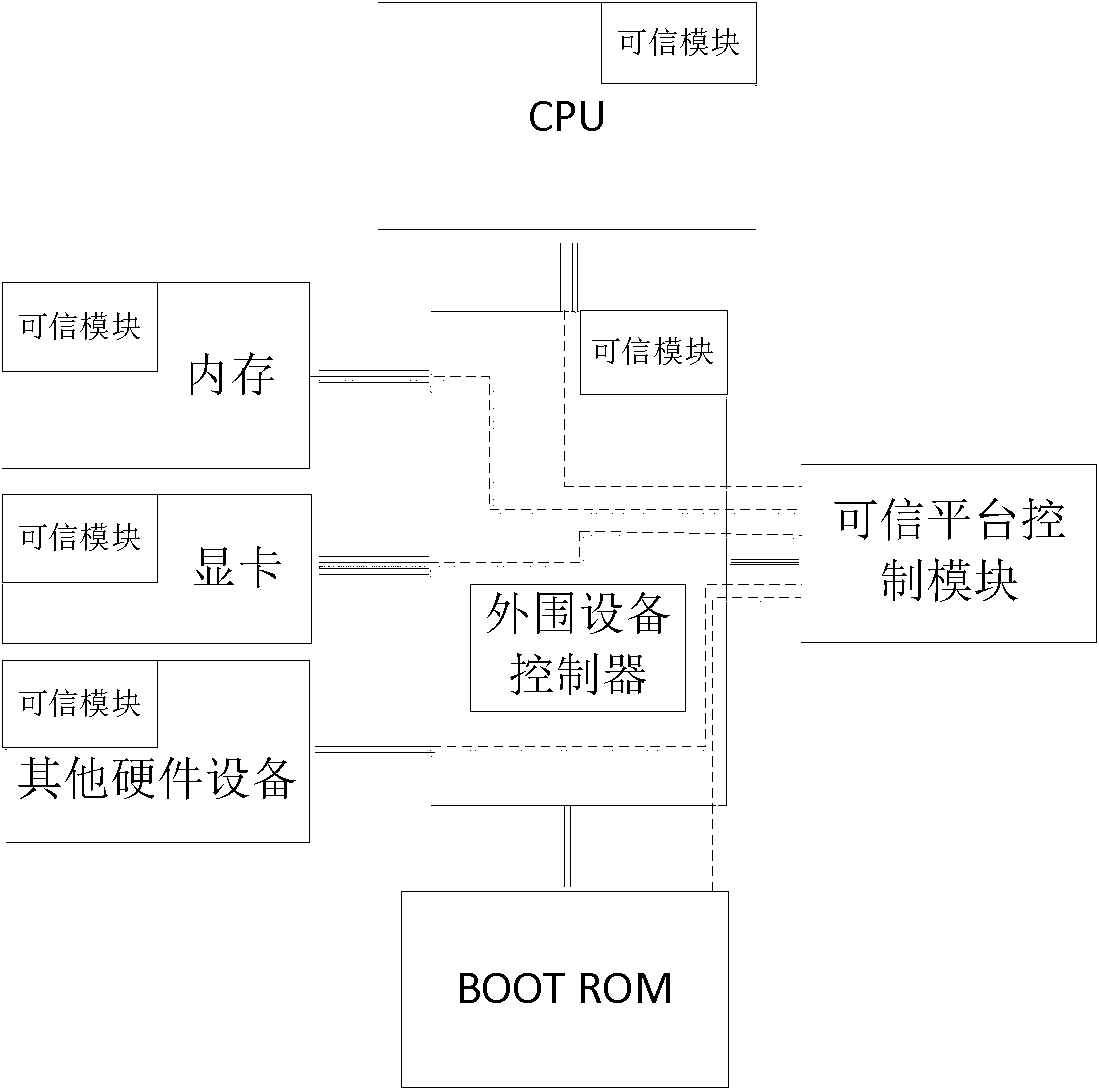
Safe computing platform
InactiveCN101980235AGuaranteed credibilitySafe and smooth startInternal/peripheral component protectionElectricityComputer module
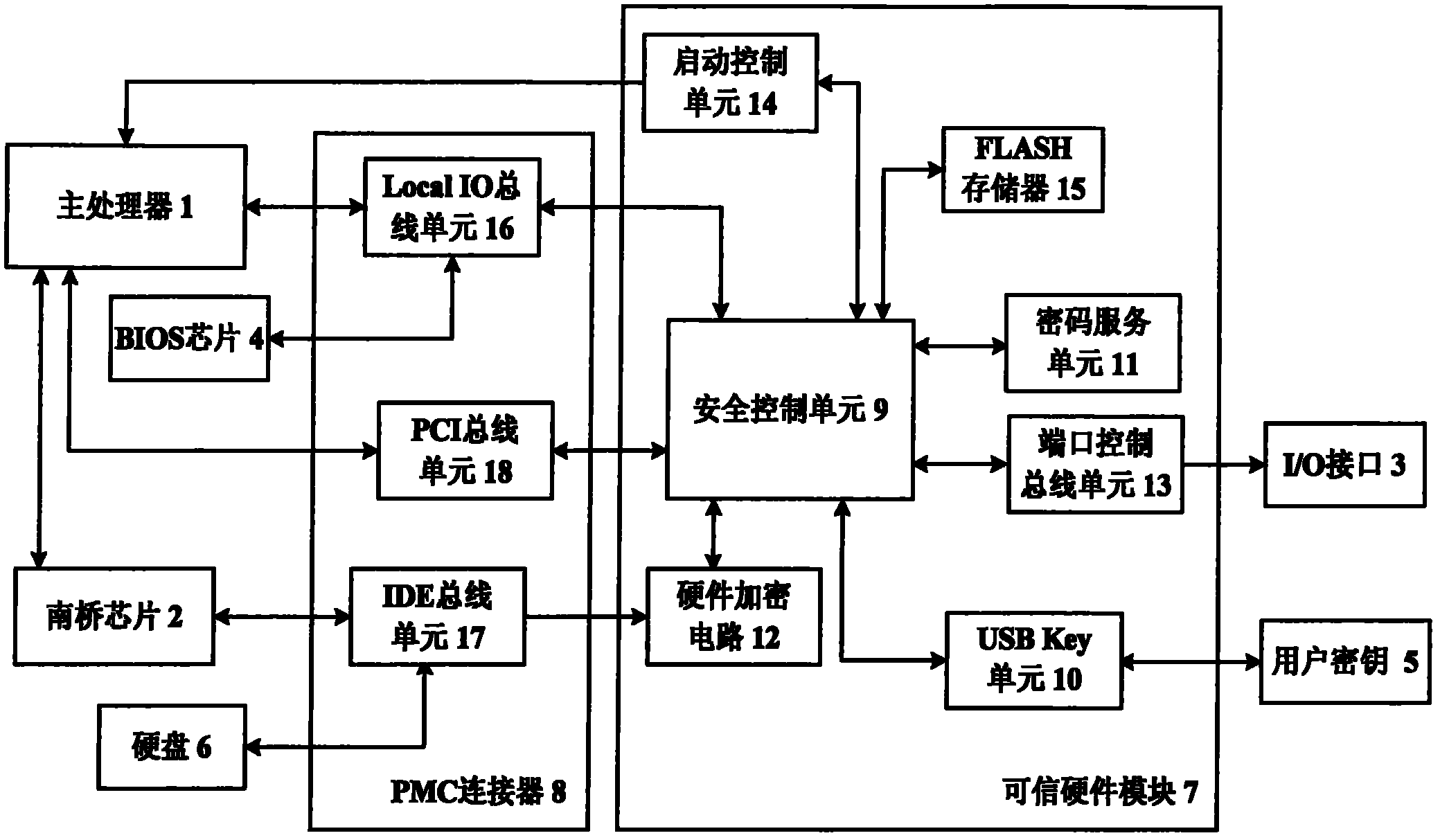
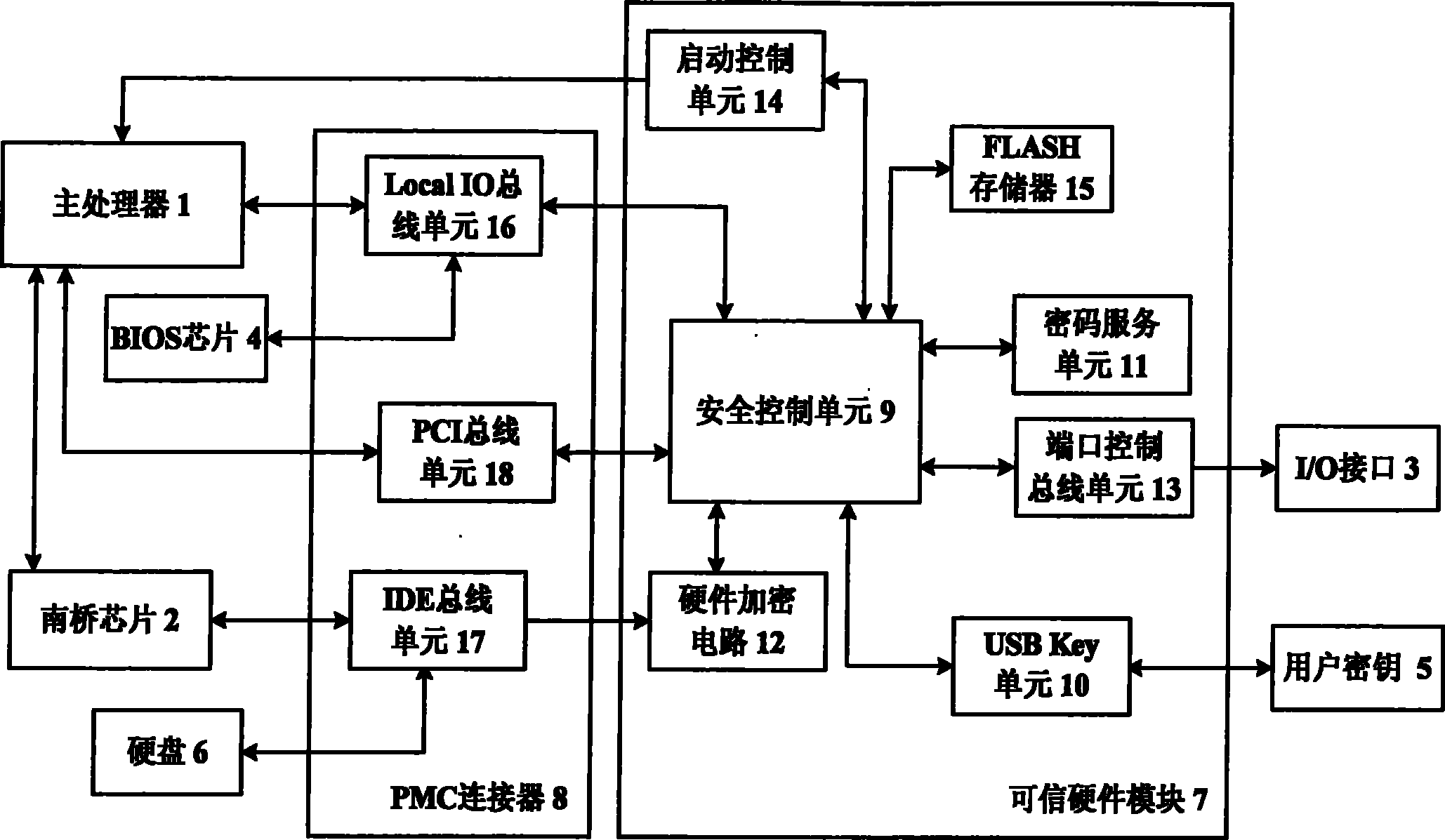
The invention discloses a safe computing platform. The safe computing platform comprises a main processor (1), a South Bridge chip (2), an I / O interface (3), a BIOS chip (4), a user key (5), a hard disk (6), a credible hardware module (7) and a PMC connector (8), wherein the main processor (1) is in bidirectional connection with the South Bridge chip (2); and the safe computing platform is electrified to be started. The credible hardware module (7) is electrified for self-detect initialization first and then restore the main processor (1); at the same time, a safe control unit (9) in the credible hardware module (7) compares BIOS data; if the BIOS data passes the comparison, the main processor (1) is normally started and directly accesses the BIOS chip (4); and the platform finishes hardware-level identity authentication, I / O port control and data real-time encryption / decryption based on the safe hardware module (7). A new mainboard structure is adopted to implement various hardware-level safe control measures, so that the safety of the whole computing platform is effectively ensured.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Calculation processing method and device based on block chain, equipment and medium
ActiveCN111143890AAvoid disclosureGuaranteed privacyDatabase distribution/replicationDigital data protectionComputer networkTrusted Computing
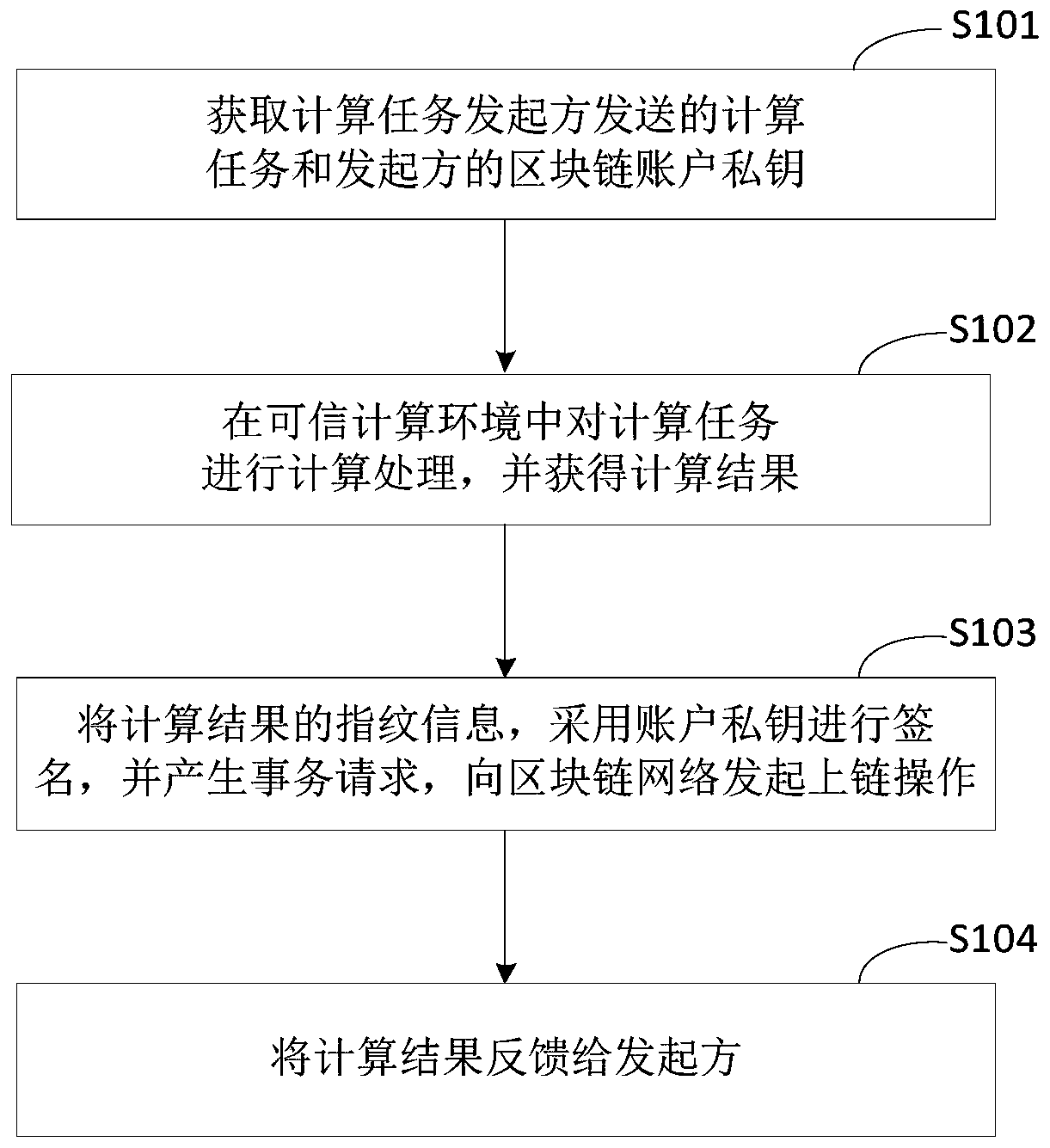
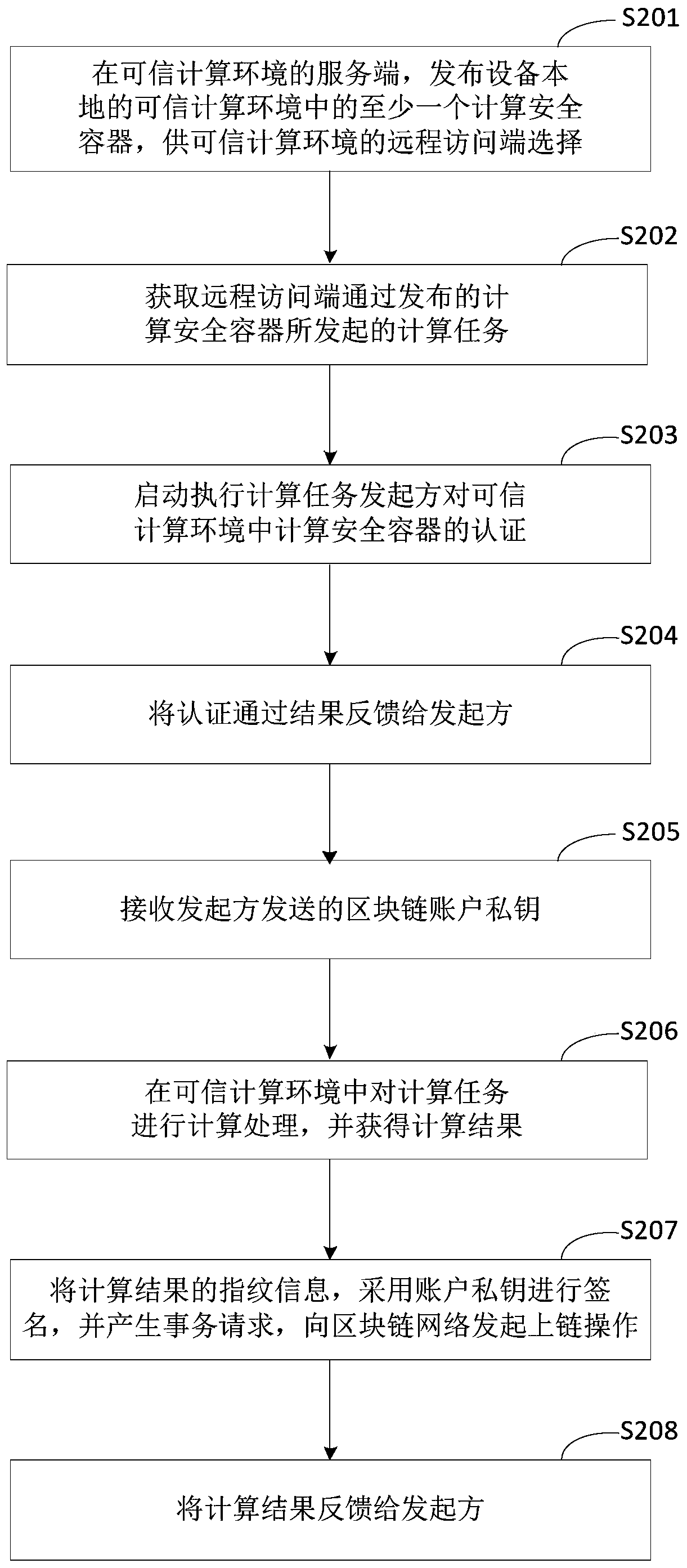
The invention discloses a computing processing method and device based on a block chain, equipment and a medium, and relates to the technical field of block chains. When the method is executed by trusted computing equipment configured with a trusted computing environment, the specific implementation scheme is as follows: obtaining a computing task sent by a computing task initiator and a blockchain account private key of the initiator; performing calculation processing on the calculation task in a trusted computing environment, and obtaining a calculation result; signing the fingerprint information of the calculation result by adopting the account private key, generating a transaction request, and initiating an uplink operation to a blockchain network; and feeding back the calculation result to the initiator. The problem of computational verifiability of private data is solved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
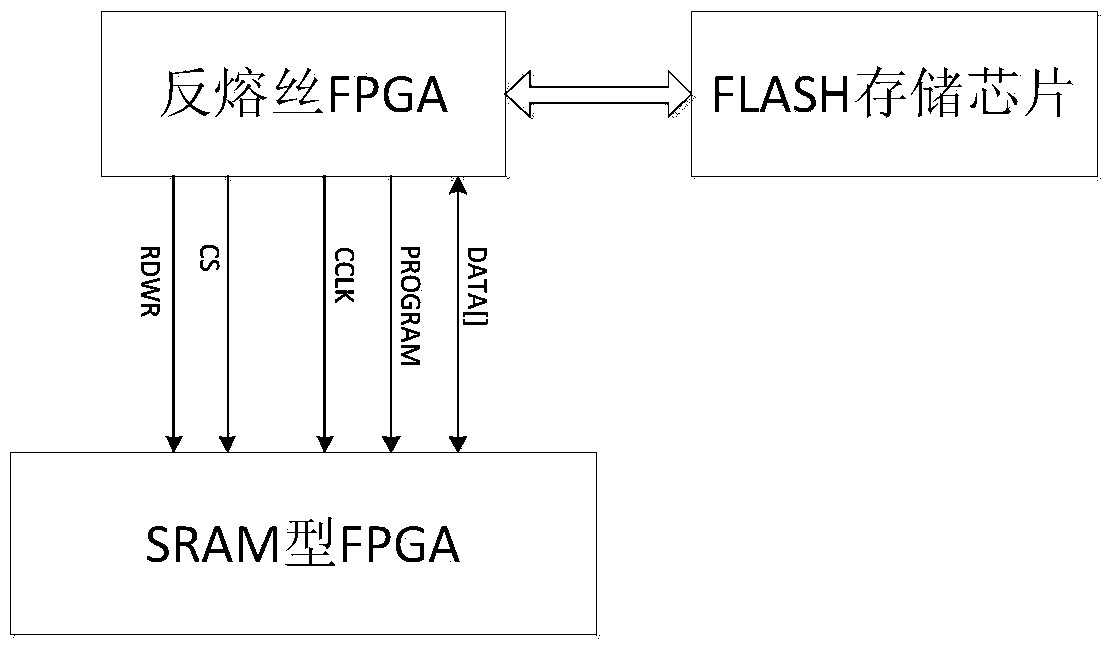
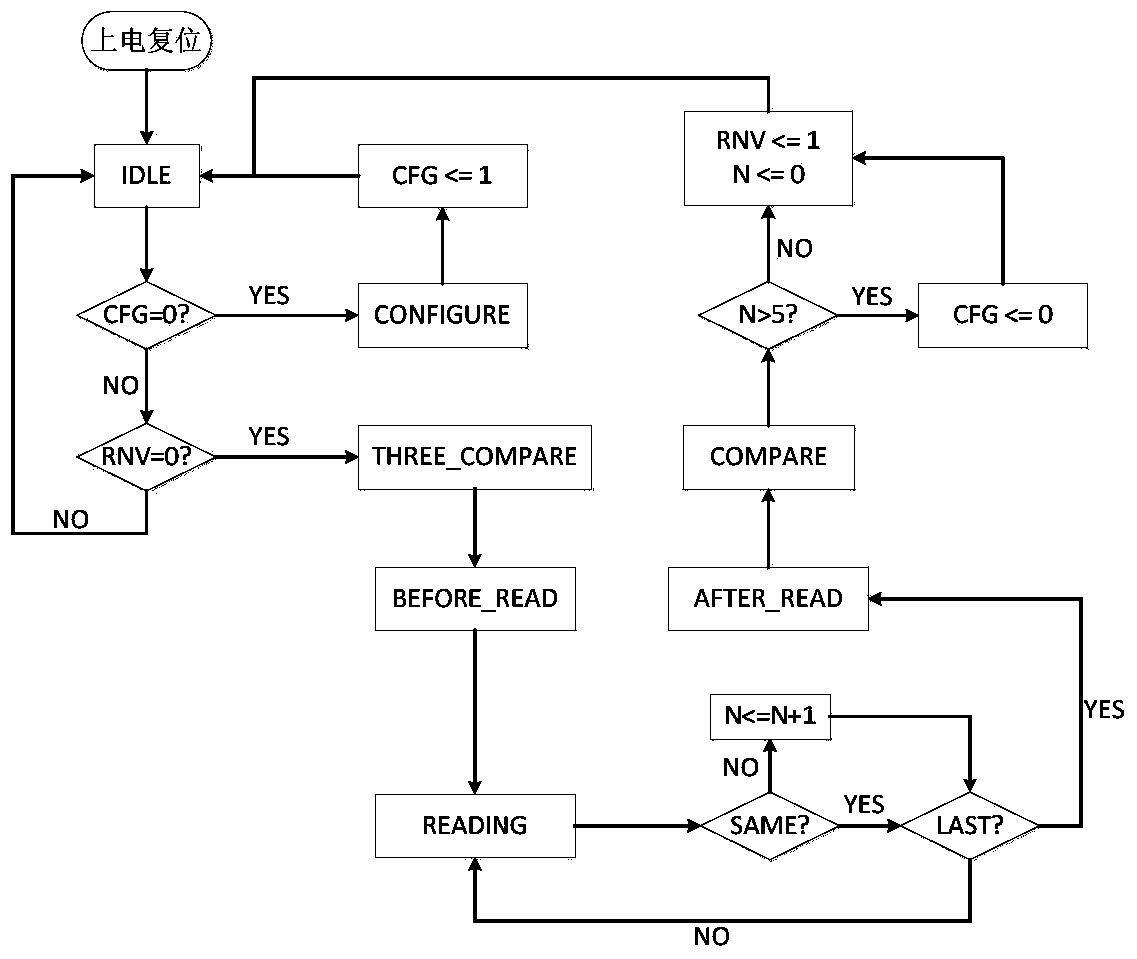
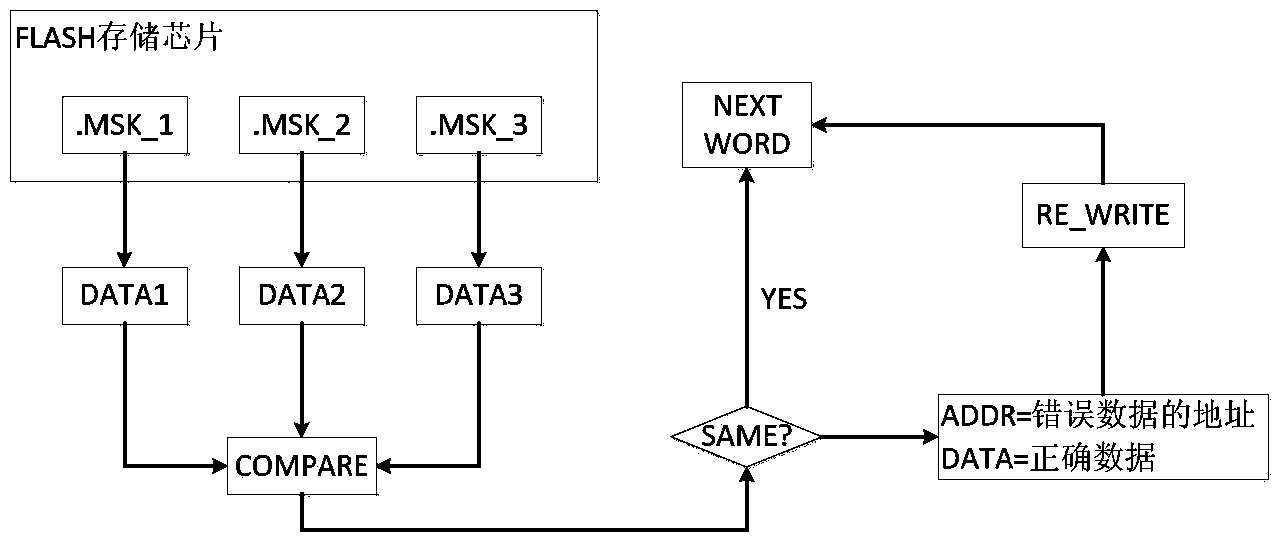
Method and system for monitoring single event upset effect of FPGA (field programmable gate array) and correcting reloading
InactiveCN103971732AReduce areaImproved ability to resist single event effectsDigital storageFpga field programmable gate arrayProgrammable read-only memory
The invention discloses a method for monitoring a single event upset effect of an FPGA (field programmable gate array) and correcting reloading. The method comprises the steps: an antifuse FPGA reads back a configuration word through a configuration word readback function of an SRAM (static random access memory) type FPGA, compares the configuration word with a correct configuration word pre-stored in an FLASH storage chip, checks whether the SRAM type FPGA generates single event upset or not, and performs reloading through a loading program pre-stored in the FLASH storage chip if the SRAM type FPGA generates the single event upset. The invention also discloses a system for monitoring the single event upset effect of the FPGA and correcting the reloading. The system comprises the FLASH storage chip, the antifuse FPGA and the SRAM type FPGA which are connected in sequence. The method and the system which are disclosed by the invention simulate a time sequence of a PROM (programmable read-only memory) to load the SRAM type FPGA through a loading file pre-stored in the FLASH storage chip; compared with the system adopting a preliminary writing PROM, the system disclosed by the invention has the advantages that the distribution area of a PCB (printed circuit board) is reduced, and equipment minimization is facilitated.
Owner:ZHEJIANG UNIV
On-chain and off-chain data sharing scheme based on distributed oracle machine and homomorphic encryption
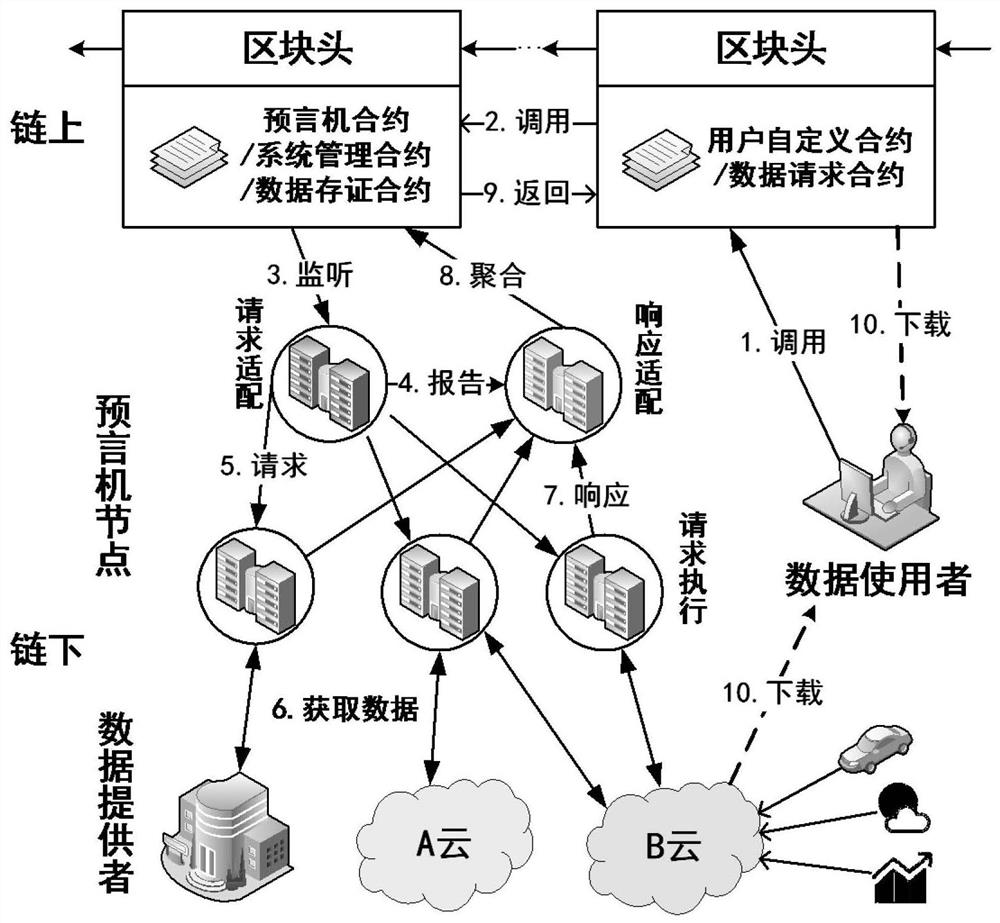
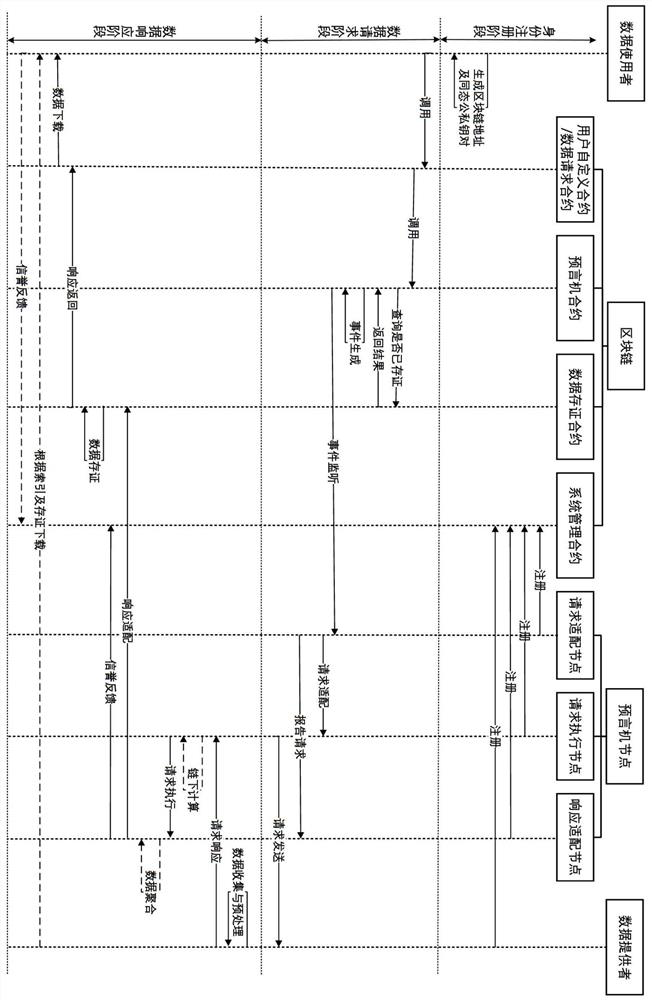
ActiveCN112016105ATake the initiative to obtainImprove timelinessDigital data protectionCommunication with homomorphic encryptionData integrityData provider
The invention belongs to the technical field of block chains. The scheme comprises four kinds of entities including a data user, a block chain, an oracle machine node and a data provider, and the block chain deploys a system management contract, an oracle machine contract, a data storage contract, a data request contract and a user-defined contract; wherein the oracle machine node comprises a request adaptation node, a response adaptation node and a request execution node; according to the scheme, cooperative sharing of the on-chain data and the off-chain data is realized by using the distributed oracle machine, the network bandwidth and the on-chain storage space demand are reduced, and the data integrity can be verified through the on-chain evidence storage; according to the scheme, homomorphic encryption is used for protecting data privacy in the processing process of the oracle machine and realizing basic under-chain computing capacity, better universality and verifiable safety areachieved. Meanwhile, data aggregation operation is set under a chain, and the processing performance is improved compared with on-chain aggregation.
Owner:东北大学秦皇岛分校
Credible device with active control function and authentication method thereof
ActiveCN102063593AEnsure safetyAchieve authenticationPlatform integrity maintainanceApplication softwareActive measurement
The invention discloses a credible device with an active control function and an authentication method thereof, relating to the field of information security. A credible platform control module with the active control function and a hardware device are connected to a credible platform of the credible device with the active control function, wherein the hardware device are separated into a credible hardware device and an incredible hardware device by the credible platform control module through the active control function, and the credible platform control module is internally provided with hardware units such as an active measurement engine, a control judgment engine, a work mode customizing engine, a credible control policy configuration engine and the like to realize active check on theworking condition configuration information of the hardware device, control policy configuration information, a firmware code and the working condition of a circuit. Mutual binding between the credible platform and the credible hardware is realized through combing the credible platform control module and a credible pipeline technology, the binding process of the credible platform control module and the credible hardware is completely transparent to an operating system and an application program, and the operating system cannot bypass or intervene the process of binding the credible hardware by the credible platform.
Owner:BEIJING UNIV OF TECH
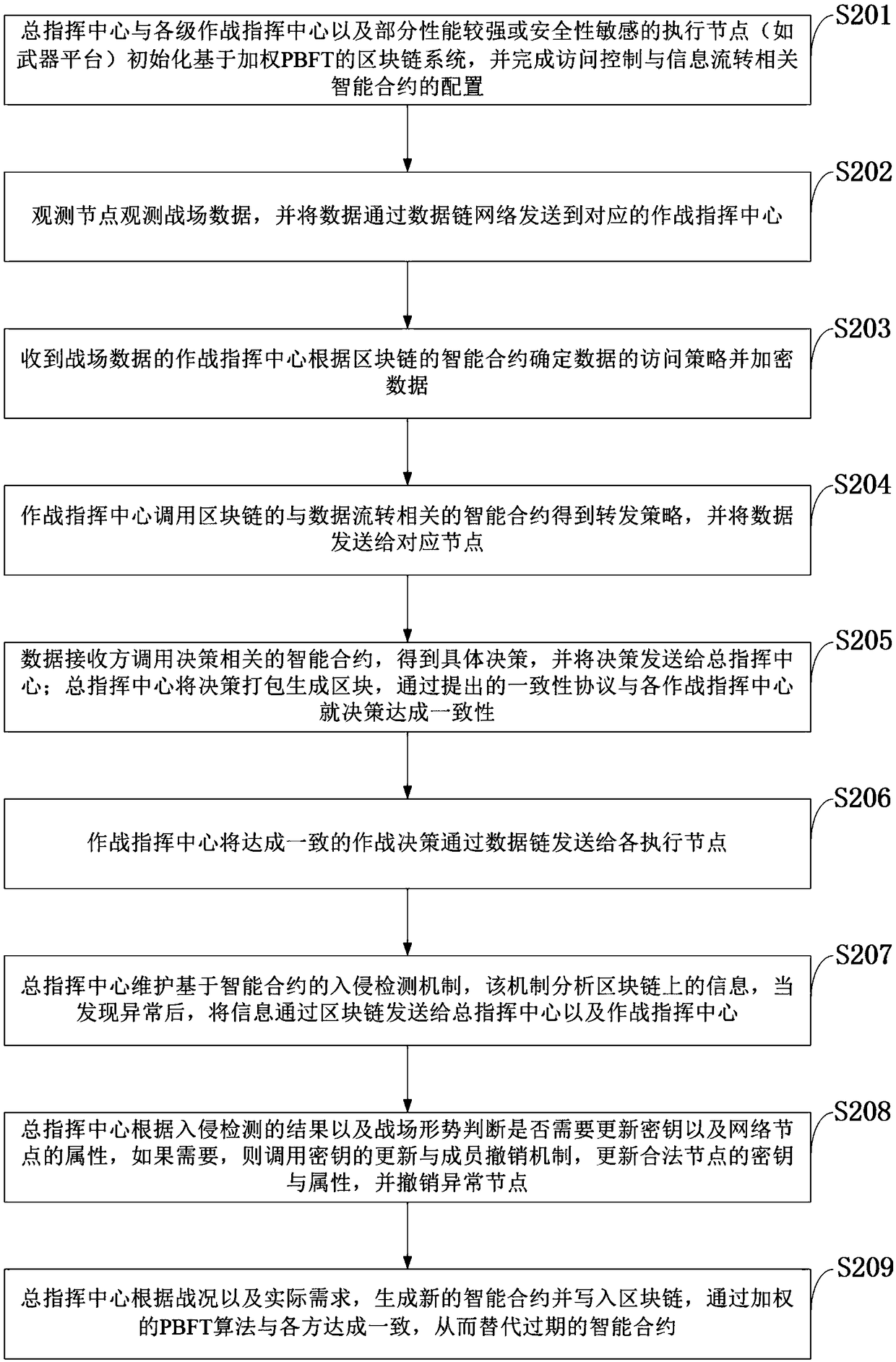
Data chain information circulation control system based on block chain as well as method
ActiveCN109450856AGuaranteed credibilityIncrease flexibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTamper resistanceControl system
The invention belongs to the technical field of transmission control procedures such as a data chain stage control procedure and discloses a data chain information circulation control system based ona block chain as well as a method. The system disclosed by the invention is based on a weighted PBFT algorithm, can distribute weights specific to different entity characters of a data chain, fully considers significance of different characters of the data chain as well as influence of the different characters on consistency and has high flexibility; based on an access control scheme of the blockchain, consistency and tampering resistance of the block chain guarantee credibility of a contract self, a smart contract can be automatically executed, characteristics of the block chain are combined, and credibility of an access strategy output by the contract is guaranteed, so that data security is effectively guaranteed; and attribute encryption is combined with symmetrical encryption, data isencrypted by using a symmetrical encryption scheme, and a symmetric key is encrypted by using an attribute encryption algorithm, so that efficient encryption is guaranteed, and flexible access control is supported.
Owner:XIDIAN UNIV
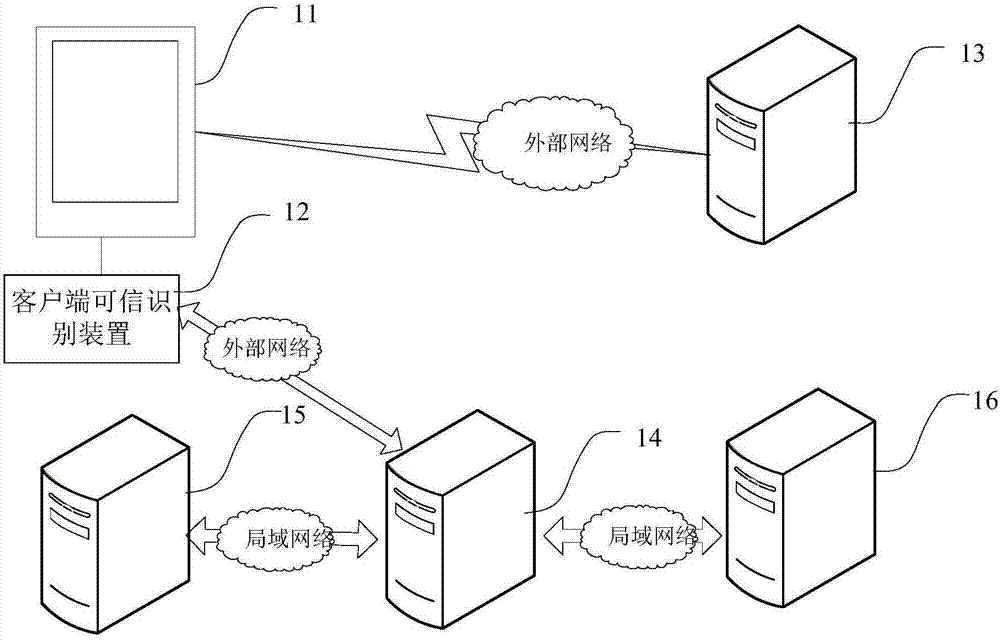
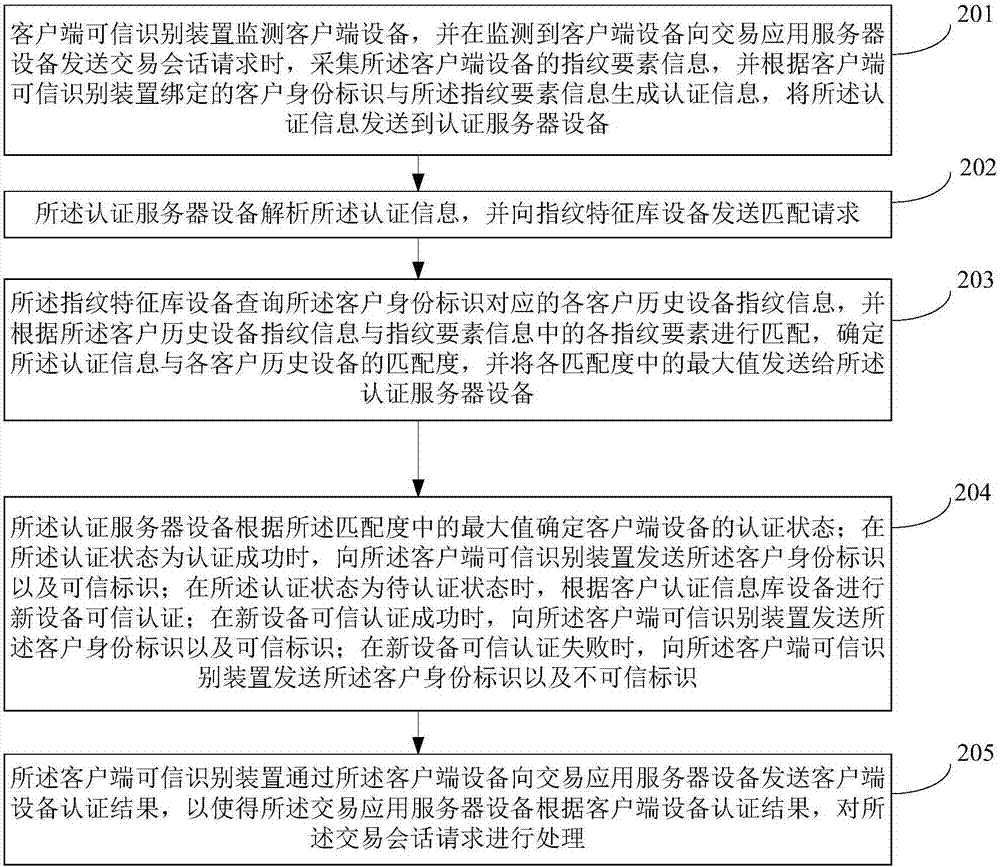
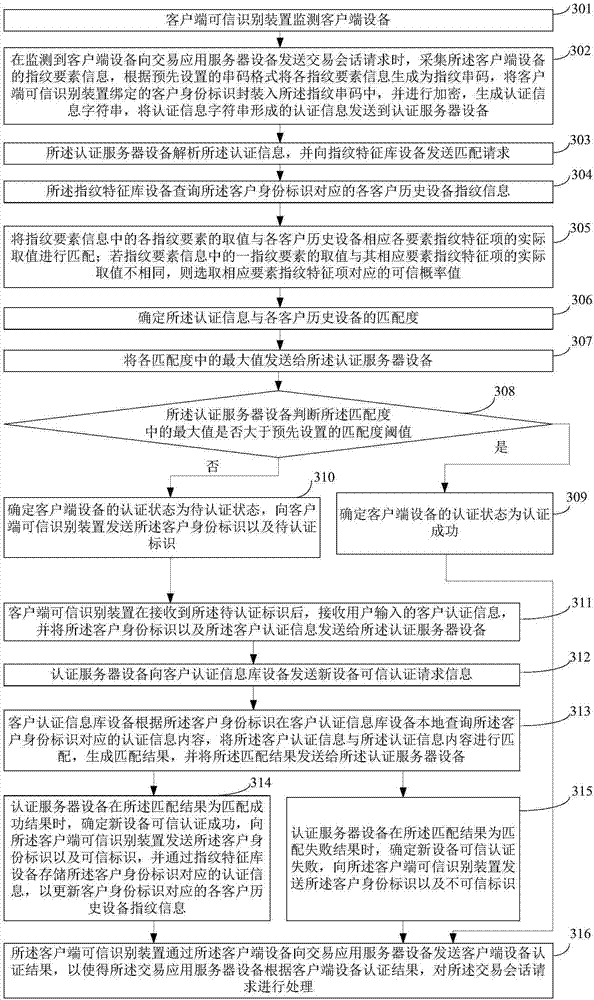
Client side equipment security authentication system and method and client side trusted identification device
InactiveCN106952096AGuaranteed credibilityImprove operating experienceTransmissionProtocol authorisationClient-sideApplication server
The invention provides a client side equipment security authentication system and method and a client side trusted identification device, and relates to the technical field of client side security authentication. The method comprises the steps that the client side trusted identification device acquires fingerprint element information of client side equipment so as to generate authentication information; authentication server equipment analyzes the authentication information and transmits a matching request to fingerprint feature library equipment; the fingerprint feature library equipment inquires fingerprint information of each set of client historical equipment corresponding to a client identifier and determines the matching degree of the authentication information and each set of client historical equipment; the authentication server equipment determines the authentication state of the client side equipment according to the maximum value of the matching degree; when the authentication state indicates successful authentication, the client identifier and a trusted identifier are transmitted to the client side trusted identification device; when the authentication state is the under authentication state, new equipment trusted authentication is performed according to client authentication information library equipment; and transaction application server equipment is enabled to process a transaction session request according to the client side equipment authentication result.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
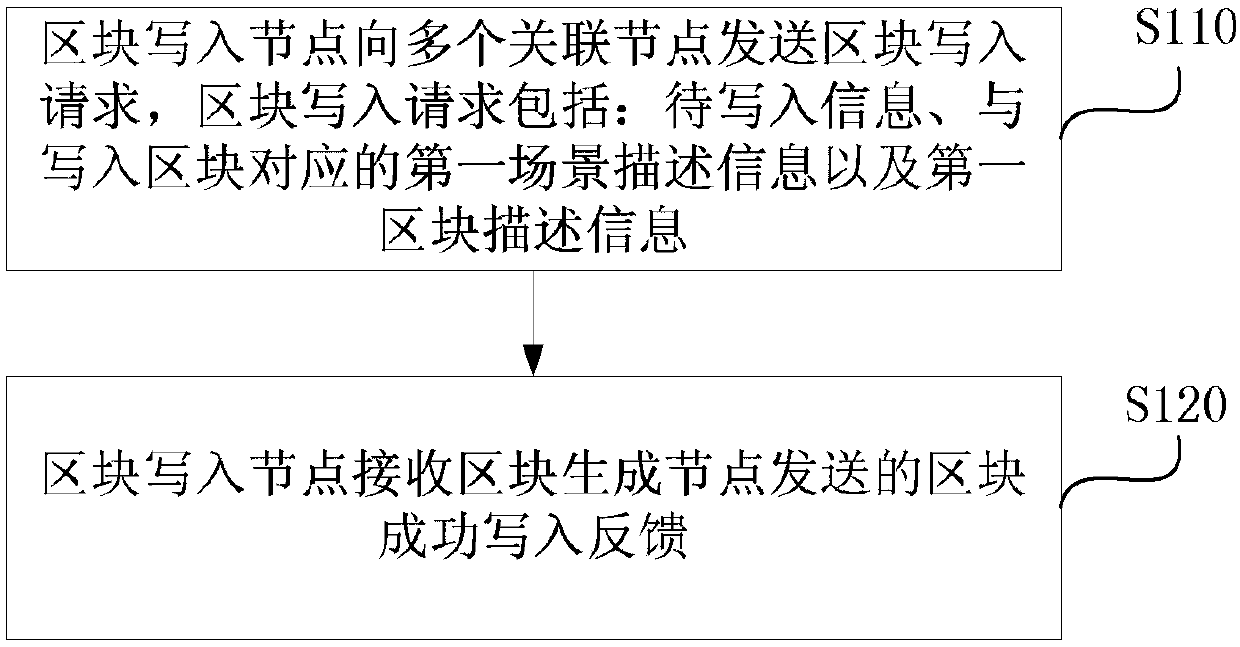
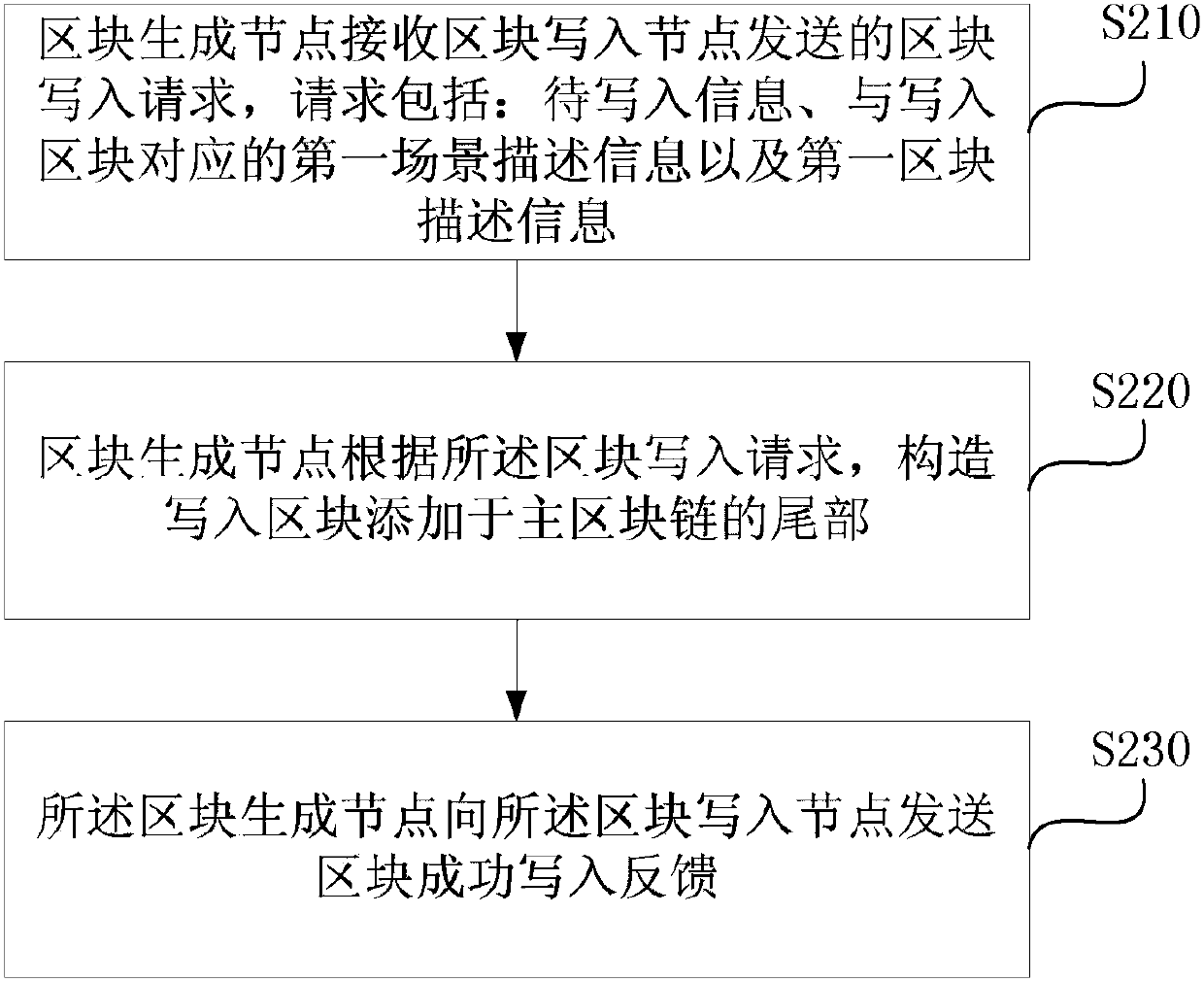
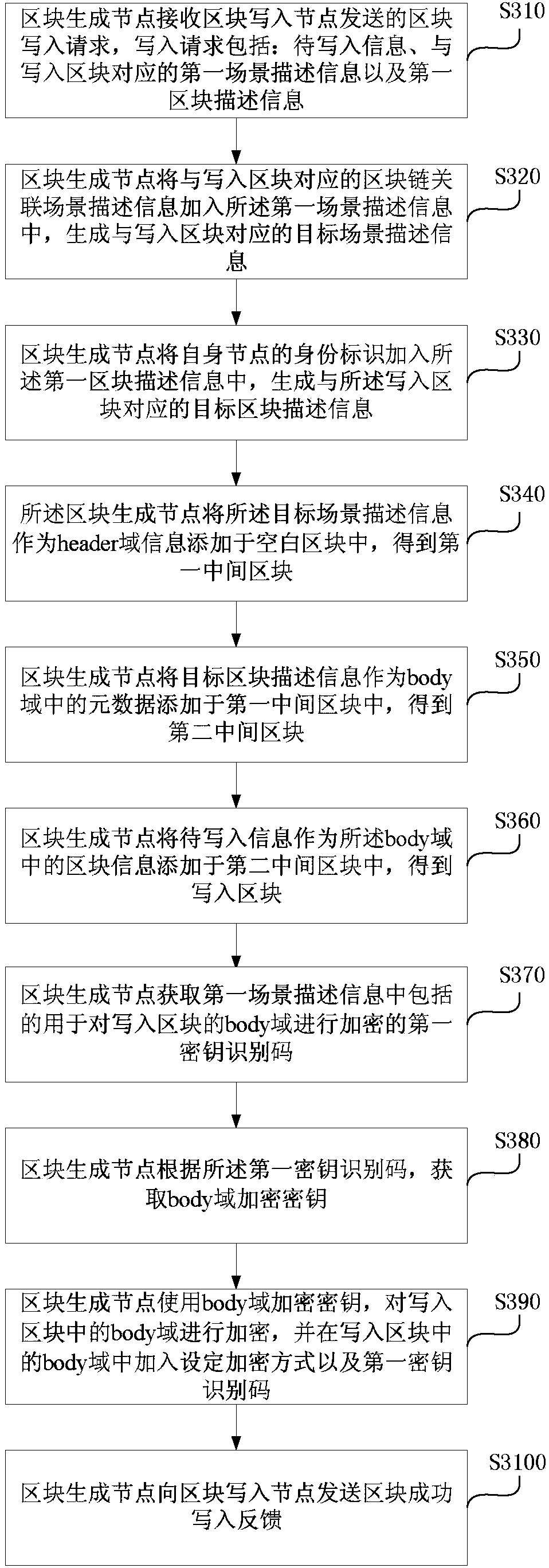
Data storage and recovery method, device and equipment based on block chain and medium
ActiveCN110019235AEffective recoveryGuaranteed credibilityDigital data protectionRedundant operation error correctionBlockchainTamper resistance
The embodiment of the invention discloses a data storage and recovery method, device and equipment based on block chain and a medium. The data storage method comprises the following steps of using a block write-in node to send a block write-in request to a plurality of associated nodes, wherein the block write-in request comprises the to-be-written-in information, the first scene description information corresponding to the write-in block and the first block description information; and using the block write-in node to receive the block successful write-in feedback sent by the block generationnode. According to the technical scheme provided by the embodiment of the invention, the effective restoration of the block chain can be realized when the block chain is damaged or lost during transmission, the problem that the data storage and sharing completely depends on a single center is effectively solved, and the data tamper resistance and credibility and the data security are ensured. Compared with an existing data storage mode, the sense of security of the participating users is increased, and the data is more difficult to lose and is safer.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Implementation method and device of application-type honeypot
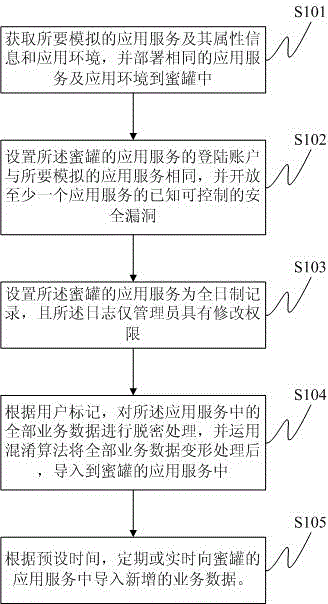
InactiveCN104978519ADetect behavioral intentionDiscovery Analysis ForensicsPlatform integrity maintainanceSoftware engineeringBusiness data
The invention provides an implementation method and device of an application-type honeypot. The implementation method comprises the following steps: obtaining application service to be simulated and the attribute information and the application environment of the application service to be simulated, and deploying the same application service and application environment into the honeypot; setting the corresponding attributes of the honeypot, for example, a login account of the application service of the honeypot is set to be the same with the application service to be simulated, and the known controllable security holes of at least one application service is opened; according to a user flag, carrying out decryption processing on all pieces of business data in the application service, applying a confounding algorithm to carry out deformation processing on all pieces of business data, and then, importing the business data into the application service of the honeypot; and importing newly-added business data into the application service of the honeypot in fixed time or real time. The invention also provides corresponding equipment. The application-type honeypot can be combined with the real business data of the user to confuse an attacker to a maximum degree, and the attacker is enabled to think that the honeypot is the real application service data of the user.
Owner:HARBIN ANTIY TECH
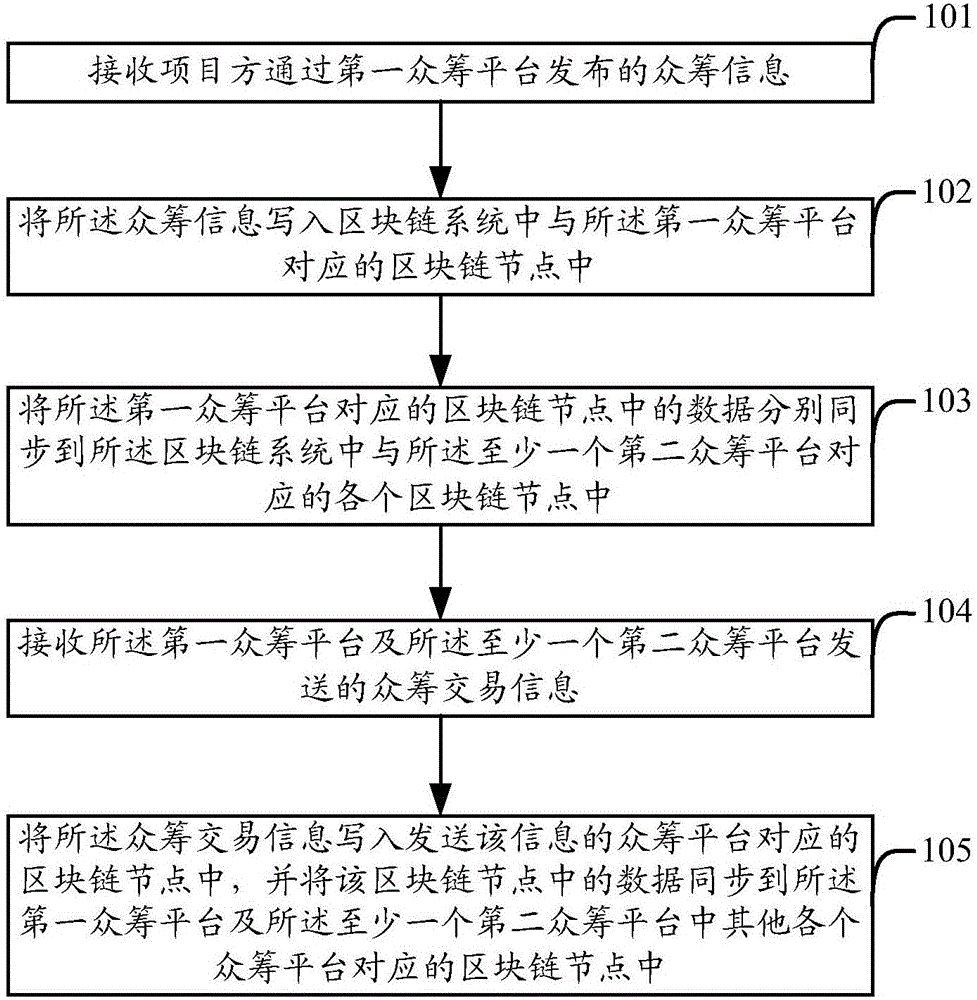
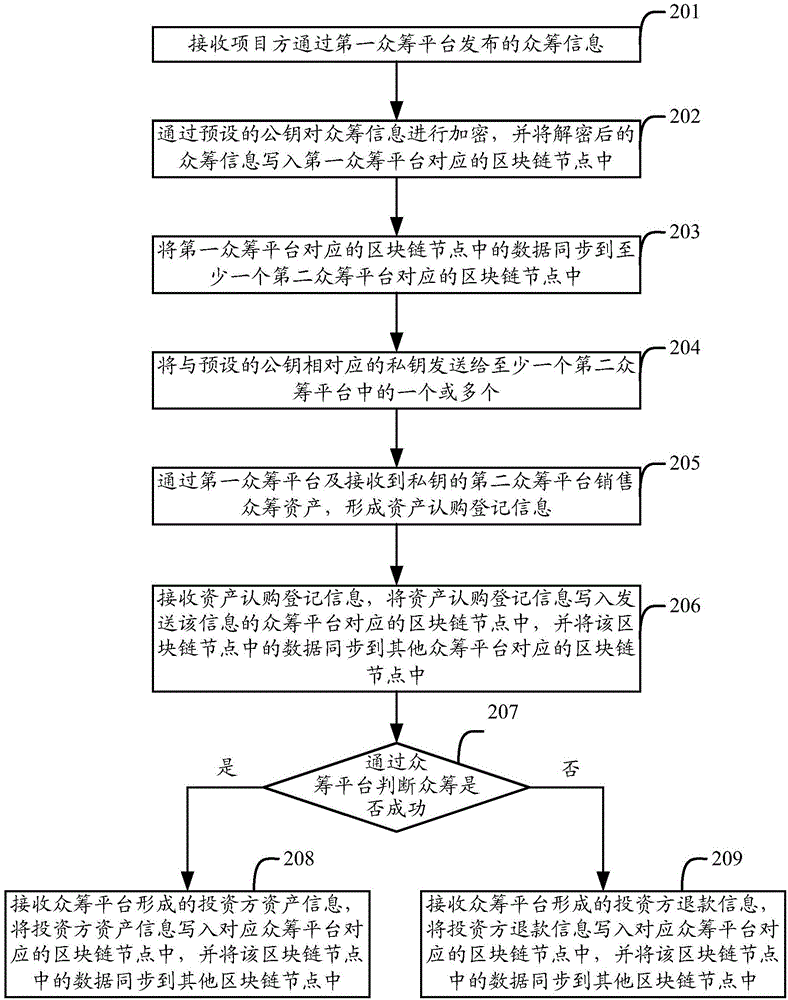
Block chain-based crowd funding method, device and system
The invention provides a block chain-based crowd funding method, a device and a system. The method comprises steps: crowd funding information released by a project manager through a first crowd funding platform is received; the crowd funding information is written to a block chain node corresponding to the first crowd funding platform in the block chain system; data in the block chain node corresponding to the first crowd funding platform are synchronized to each block chain node corresponding to at least one second crowd funding platform in the block chain system respectively; crowd funding transaction information sent by the first crowd funding platform and the at least one second crowd funding platform is received; and the crowd funding transaction information is written to the block chain node corresponding to the crowd funding platform releasing the information, and the data in the block chain node are synchronized to block chain nodes corresponding to other crowd funding platforms except the first crowd funding platform and the at least one second crowd funding platform. The device comprises a receiving unit, a storage unit and a synchronizing unit. Crowd funding cross crowd funding platforms can be realized.
Owner:北京金股链科技有限公司
Imaging simulation method and system for decimeter-scale satellite-borne TDI CCD stereoscopic mapping camera
ActiveCN105528500ARealize the combinationAvoid low fidelity issuesMeasurement devicesDesign optimisation/simulationAngle of viewRadiation response
The invention discloses an imaging simulation method and system for a decimeter-scale satellite-borne TDI CCD stereoscopic mapping camera. Stereoscopic images of a commercial satellite Worldview-3 which has the highest resolution at present as a data source, and a data form of image+ground point is formed through stereoscopic matching processing. To acquire the instant imaging face irradiance of a TDI CCD is regarded as a core step, an orbit, attitude parameters, camera installation parameters, TDI CCD geometric parameters, camera MTF and the like are organically linked up. The multistage dynamic integral simulation of the TDI CCD is achieved through time domain integral and TDI CCD multistage charge accumulation, and then, the strict simulation of radiation response and linear array image imaging of the camera are achieved. According to the method and the system, the disadvantage in the traditional imaging simulation that the difference of geometric and radiation information corresponding to different vision angles in high-resolution satellite stereoscopic imaging is hard to simulate due to the adopting of a single data source can be avoided, and the accuracy of simulating stereoscopic mapping satellite images is improved.
Owner:自然资源部国土卫星遥感应用中心
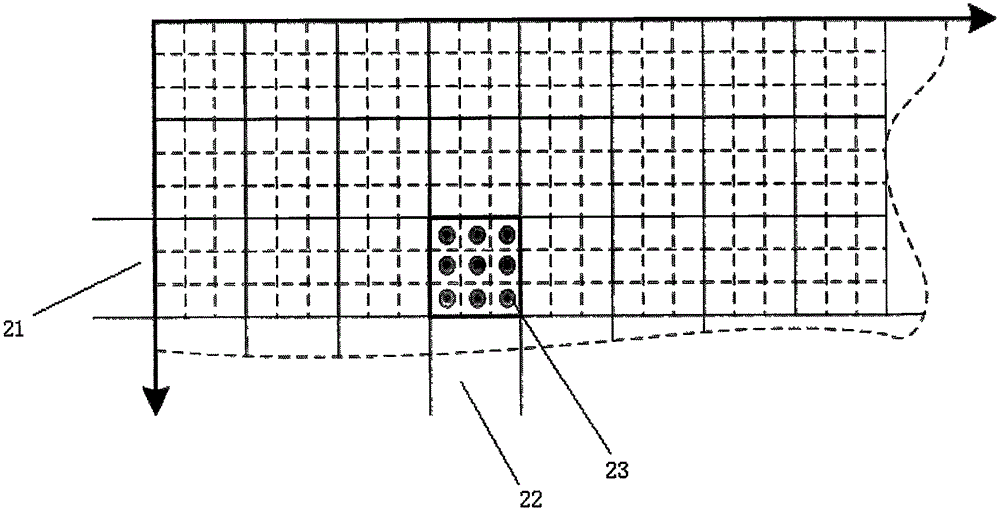
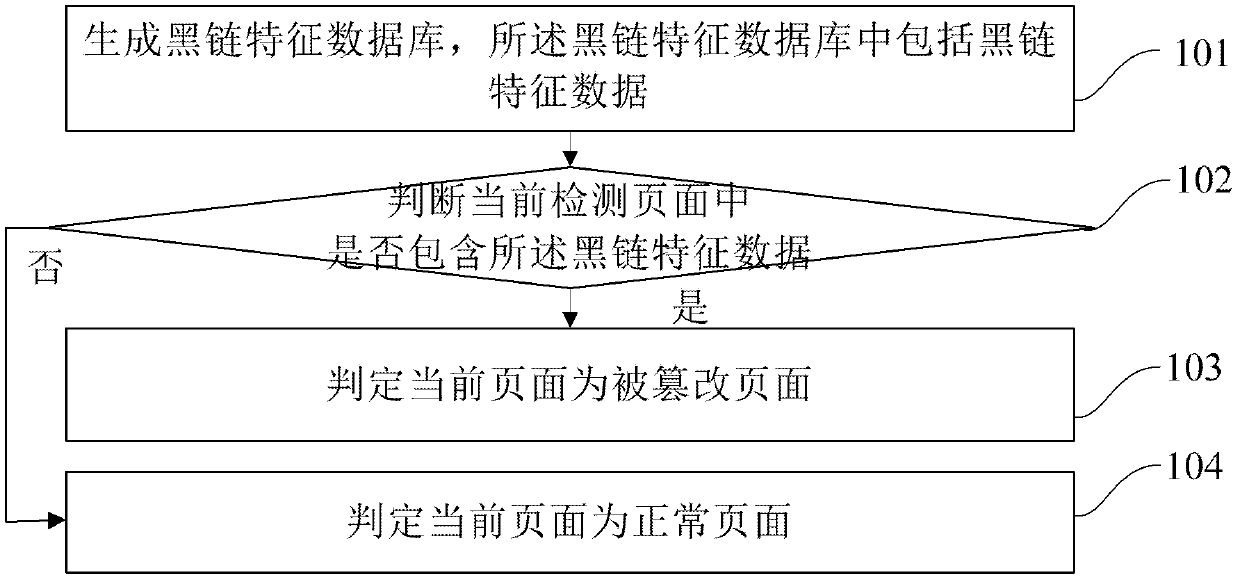
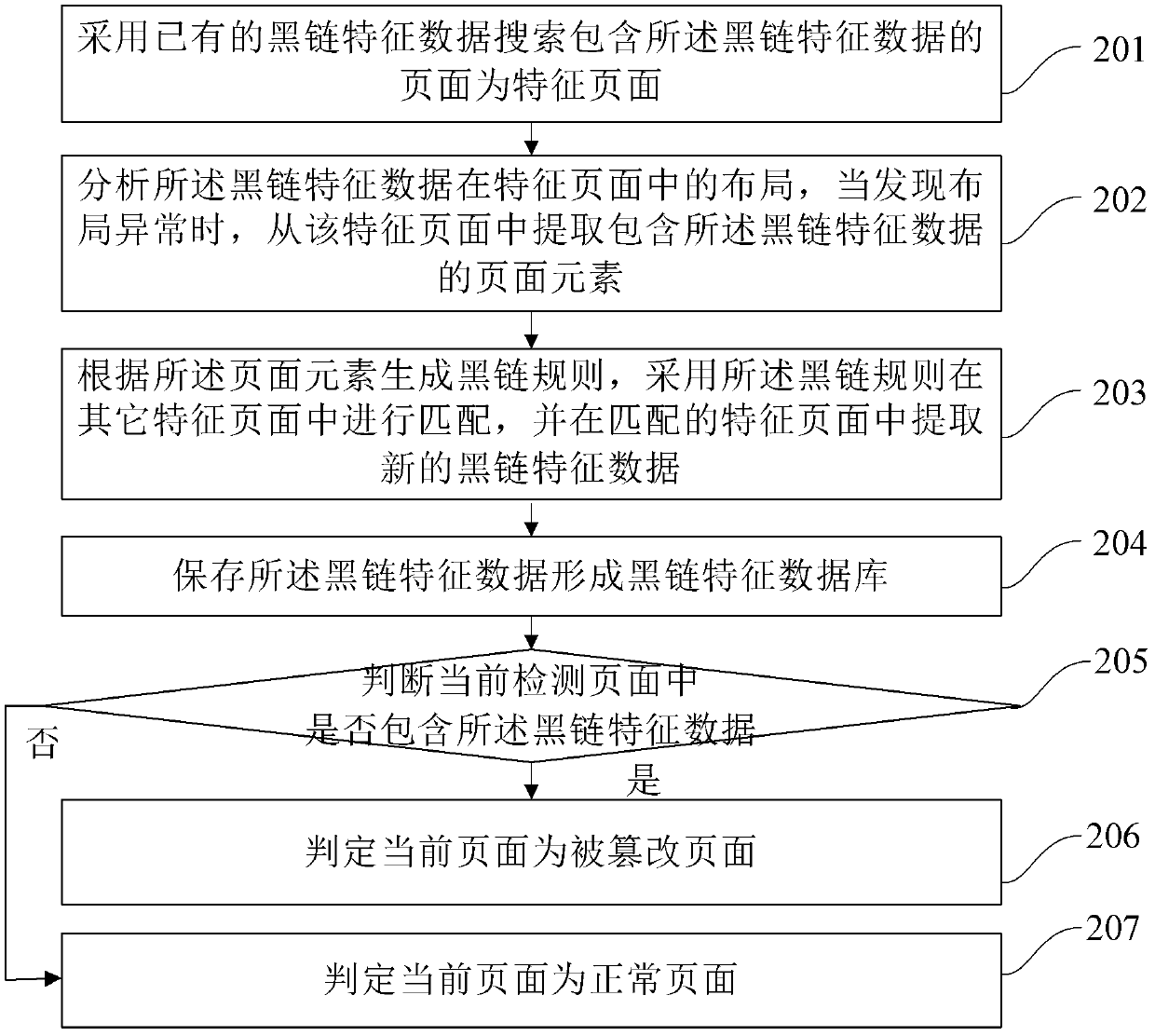
Method and device for detecting page tampering
ActiveCN102436563AImprove the efficiency of tamperingEnsure safetyPlatform integrity maintainanceSpecial data processing applicationsData miningDatabase
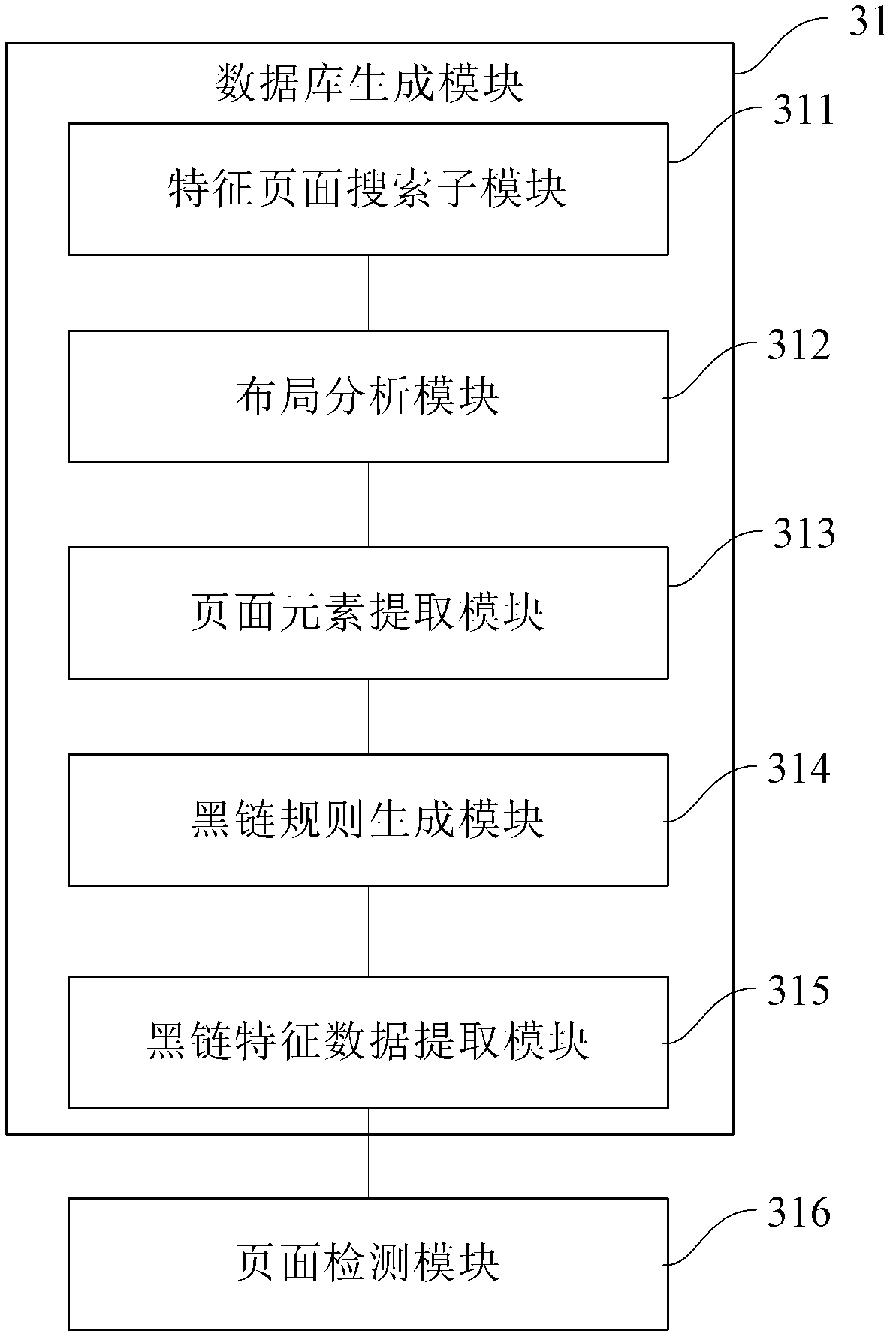
The invention provides a method and device for detecting page tampering. The method comprises the following steps of: generating a black chain characteristic database, wherein the black chain characteristic database comprises black chain characteristic data; judging whether a current detected page includes the black chain characteristic data; and if the current detected page includes the black chain characteristic data, judging that the current page is a tampered page. Through the method and the device, the efficiency and the accuracy for tampering the detected page can be improved on the premise of reducing manual intervention as much as possible.
Owner:三六零数字安全科技集团有限公司
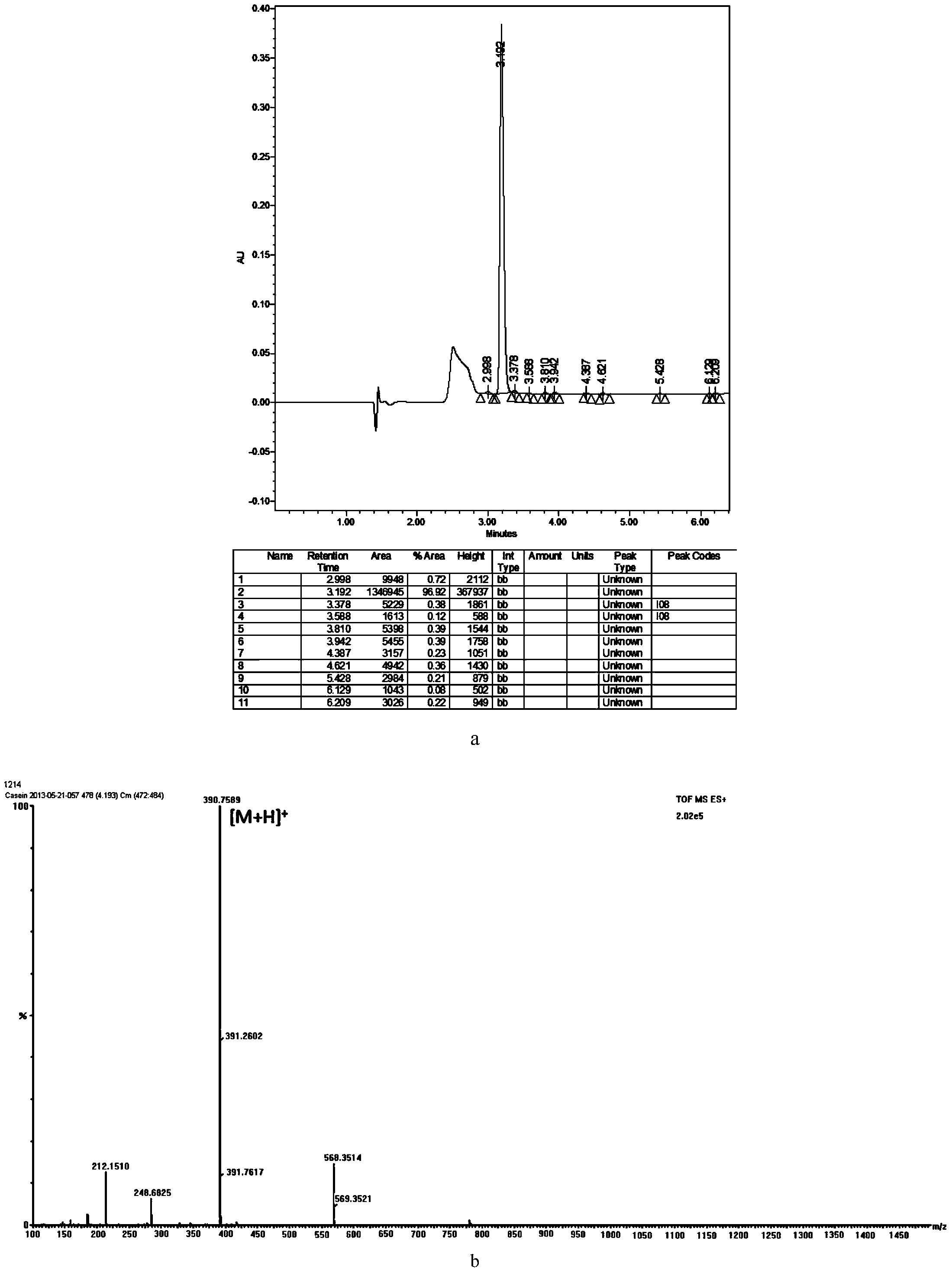
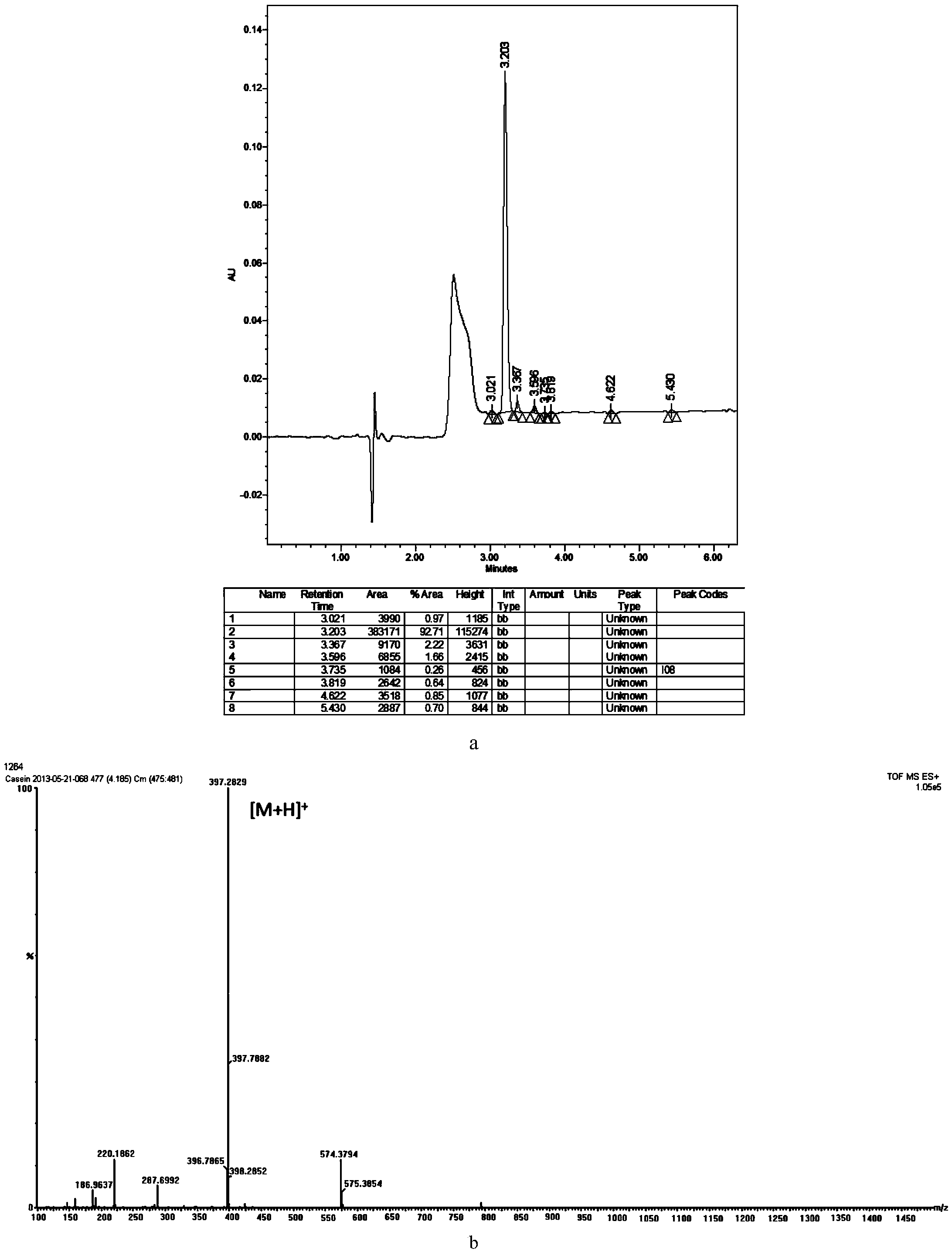
Bovine beta-casein quantitative determination kit and application thereof
ActiveCN103529138AAccurate quantitative detectionComplete range of configurationsComponent separationQuantitative determinationInternal standard
The invention provides a bovine beta-casein quantitative determination kit. The kit mainly comprises a bovine beta-casein specific peptide of which the amino acid sequence is VLPVPQK, an isotope labeled bovine beta-casein specific peptide (VL*PV*PQK) and an isotope labeled bovine beta-casein internal standard substance of which the amino acid sequence is QSVLSLSQSKVL*PV*PQKAVPYPQRD). According to the kit, the ration is limited to be 1mg / 100g, the reproducibility RSD less than 9.50 percent (n is equal to 11), the recovery in a food substrate is 73.41-93.88 percent (n is equal to 6), and the recovery in a powdered milk substrate is 91.62-107.28 percent (n is equal to 6); a sample is pre-treated simply and quickly, and is low in cost. The bovine beta-casein quantitative determination kit is applicable to multiple food substrates, and can be used for accurately quantitating macro and trace bovine beta-casein.
Owner:ZHEJIANG CENT FOR DISEASE CONTROL & PREVENTION
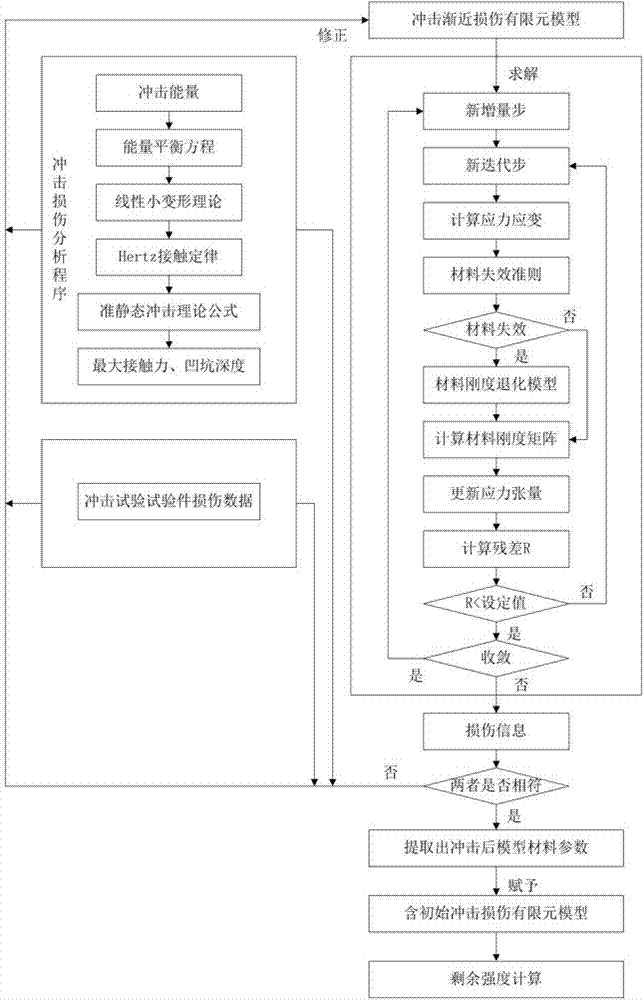
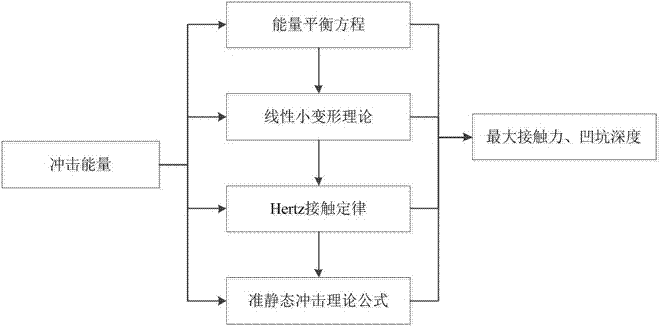
Method for assessing residual intensities of composite material structures with low-speed impact damage
InactiveCN107092721AGuaranteed accuracyHigh precisionDesign optimisation/simulationSpecial data processing applicationsResidual strengthElement model
The invention discloses a method for assessing residual intensities of composite material structures with low-speed impact damage. The method comprises six steps of: 1, obtaining a curve relationship between impact energy and damage characteristic parameters through low-speed impact test results; 2, obtaining a maximum contact force and a maximum pit depth under corresponding impact energy by adoption of an impact damage theory; 3, establishing a low-speed impact progressive damage finite element model; 4, correcting the low-speed impact progressive damage finite element model; 5, establishing a residual intensity finite element model with impact damage; and 6, solving the residual intensity finite element model with the impact damage to obtain a residual intensity value. According to the method disclosed by the invention, finite element simulation is applied to impact damage models, and the impact test results and the impact damage theory are combined, so that the accurate simulation for damage states, the accurate building of finite element models with initial impact damage and the continuity of assessment processes are realized, and a relatively high practical value is provided.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
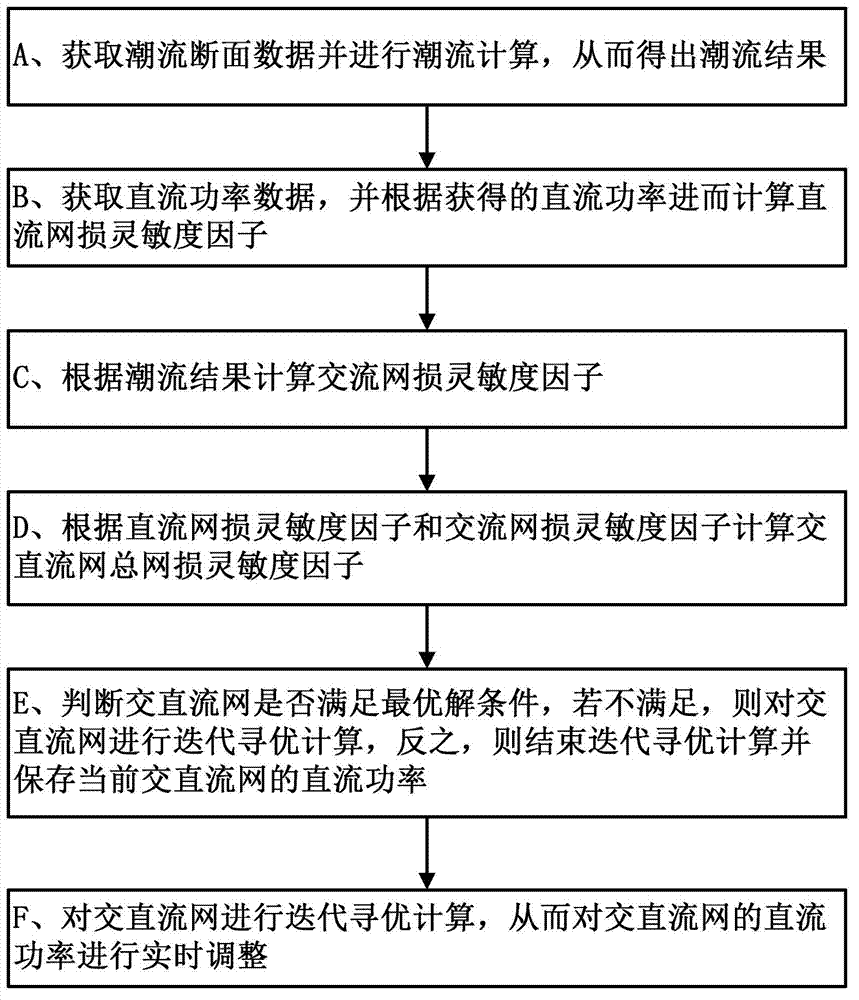
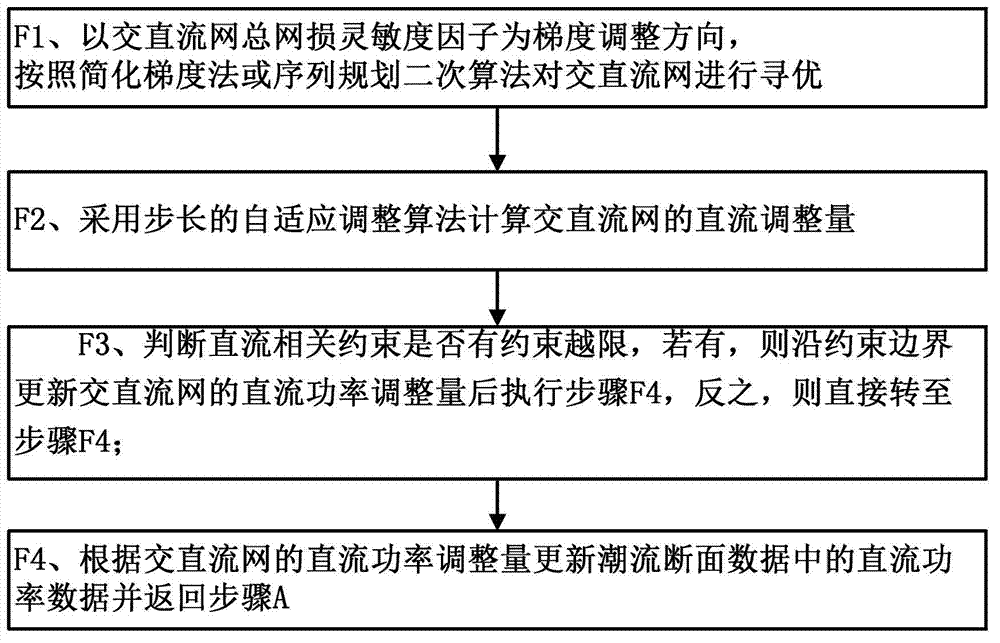
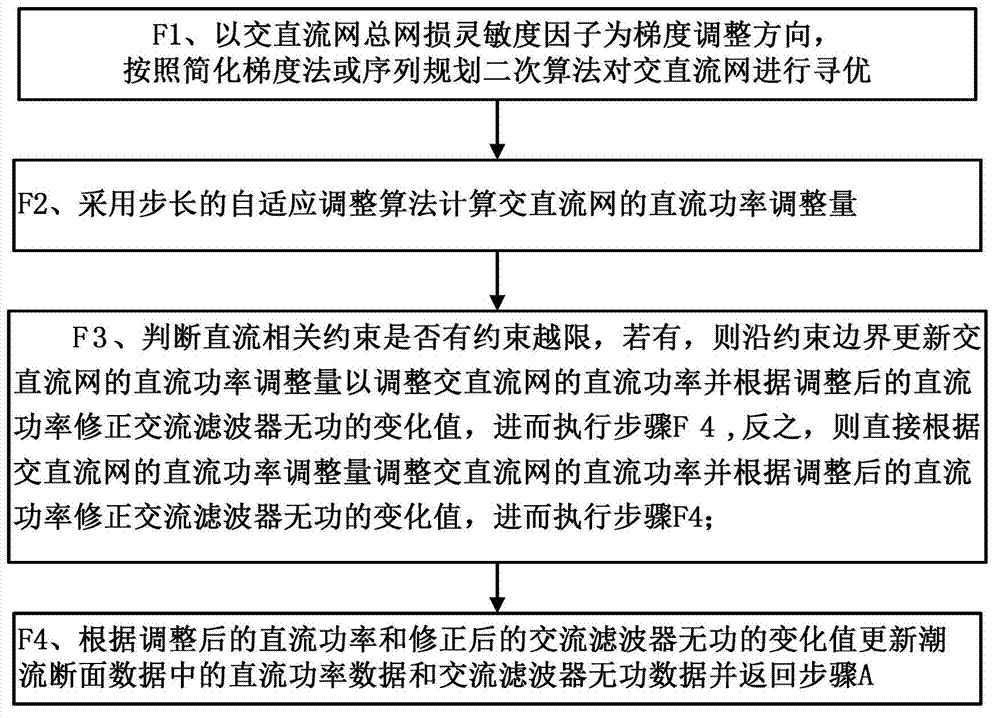
Novel transmission loss reducing method by alternating current or direct current (AC / DC) synergy used in interconnected network and novel transmission loss reducing system by AC / DC synergy used in interconnected network
ActiveCN103036245AReduce total network lossGuaranteed credibilityElectric power transfer ac networkTransmission lossAlternating current
The invention discloses a novel transmission loss reducing method by alternating current or direct current (AC / DC) synergy used in an interconnected network and a novel transmission loss reducing system by the AC / DC synergy used in the interconnected network. The method comprises the steps of acquiring load flow interface data and carrying out load flow calculation to acquire a load flow result, acquiring DC power data and calculating a DC transmission loss sensitivity factor according to the acquired DC power value; calculating an AC transmission loss sensitivity factor according to the load flow result, calculating a general transmission loss sensitivity factor of an AC / DC network according to the DC transmission loss sensitivity factor and the AC transmission loss sensitivity factor, judging whether the AC / DC network meets requirements of an optimal solution, carrying out iteration optimizing calculation to the AC / DC network if the AC / DC network does not meet the requirements of the optimal solution; finishing the iteration optimizing calculation and saving the current DC power value of the AC / DC network if the AC / DC network meets the requirements of the optimal solution, and carrying out the iteration optimizing calculation to the AC / DC network to adjustment the DC power of the AC / DC network in real time. The method supports on-line calculation, and calculation is accurate, fast and strong in robustness. The novel transmission loss reducing method by the AC / DC synergy used in the interconnected network and the novel transmission loss reducing system by the AC / DC synergy used in the interconnected network can be widely used in transmission loss optimizing of big AC / DC interconnected networks.
Owner:CHINA SOUTHERN POWER GRID COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com