Credible device with active control function and authentication method thereof
An active control and trusted technology, applied in the field of information security, can solve problems such as increased design complexity, trusted chip hardware scale and internal firmware scale, and undefined hardware device credibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
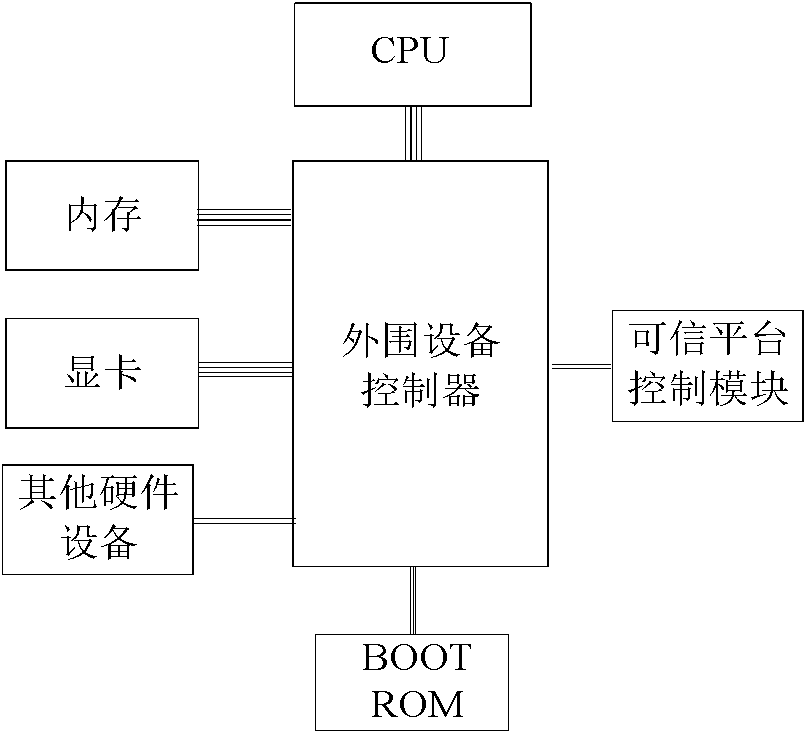
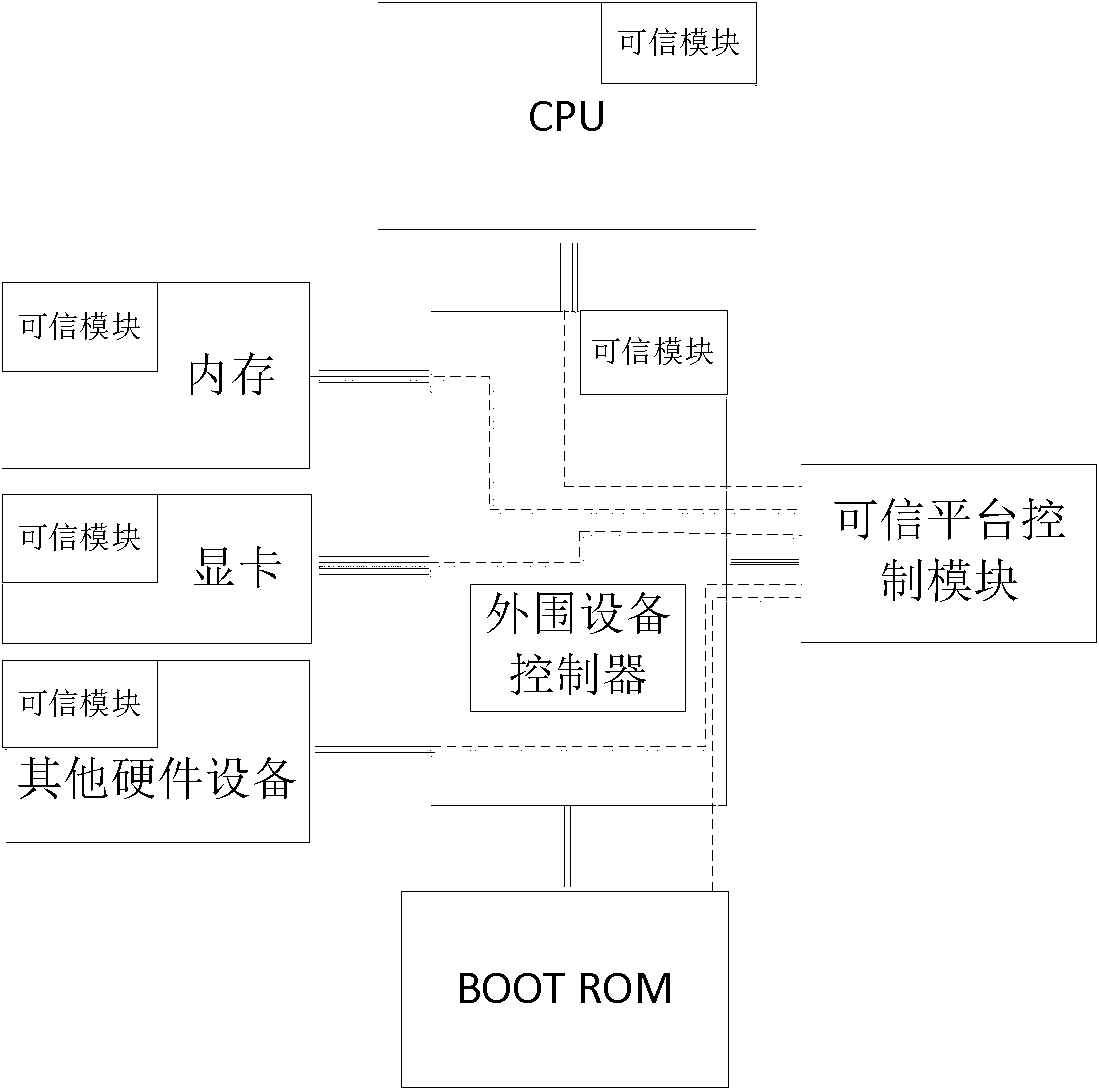
[0058] The trusted module and the trusted platform control module selected in the present invention all adopt the programmable development board of the trusted platform control module provided by domestic Ruida Information Security Industry Co., Ltd.
[0059] Based on the trusted platform control module programmable development board, a trusted platform control module and a trusted module are developed. The trusted platform control module is connected with the peripheral device controller through a signal line. The trusted module is connected with the trusted hardware device through the signal line.
[0060] Ritar is a large-scale domestic supplier specializing in R&D and production of information security products and an information security solution provider. The devices it provides can be considered authentic.
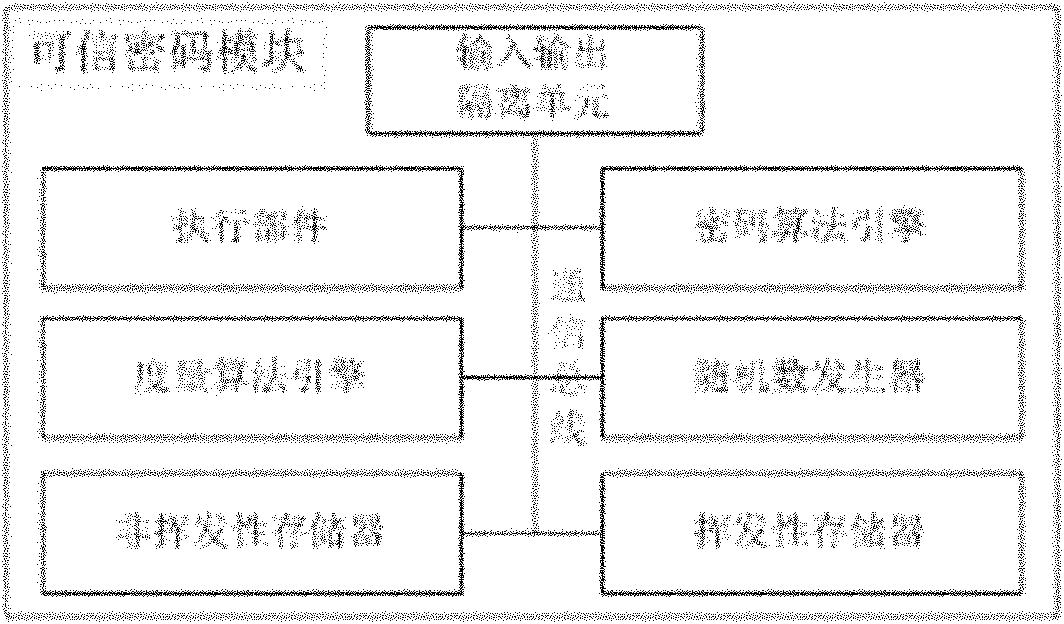
[0061] The authentication methods of the trusted platform and the trusted platform control module include: a trusted platform initialization method, a trusted pla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com