Safety payment method and device based on credible two-dimension code
A secure payment and two-dimensional code technology, which is applied in the field of computer technology and information security, can solve problems such as potential safety hazards, and achieve the effects of improving reliability, ensuring credibility, and reducing risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
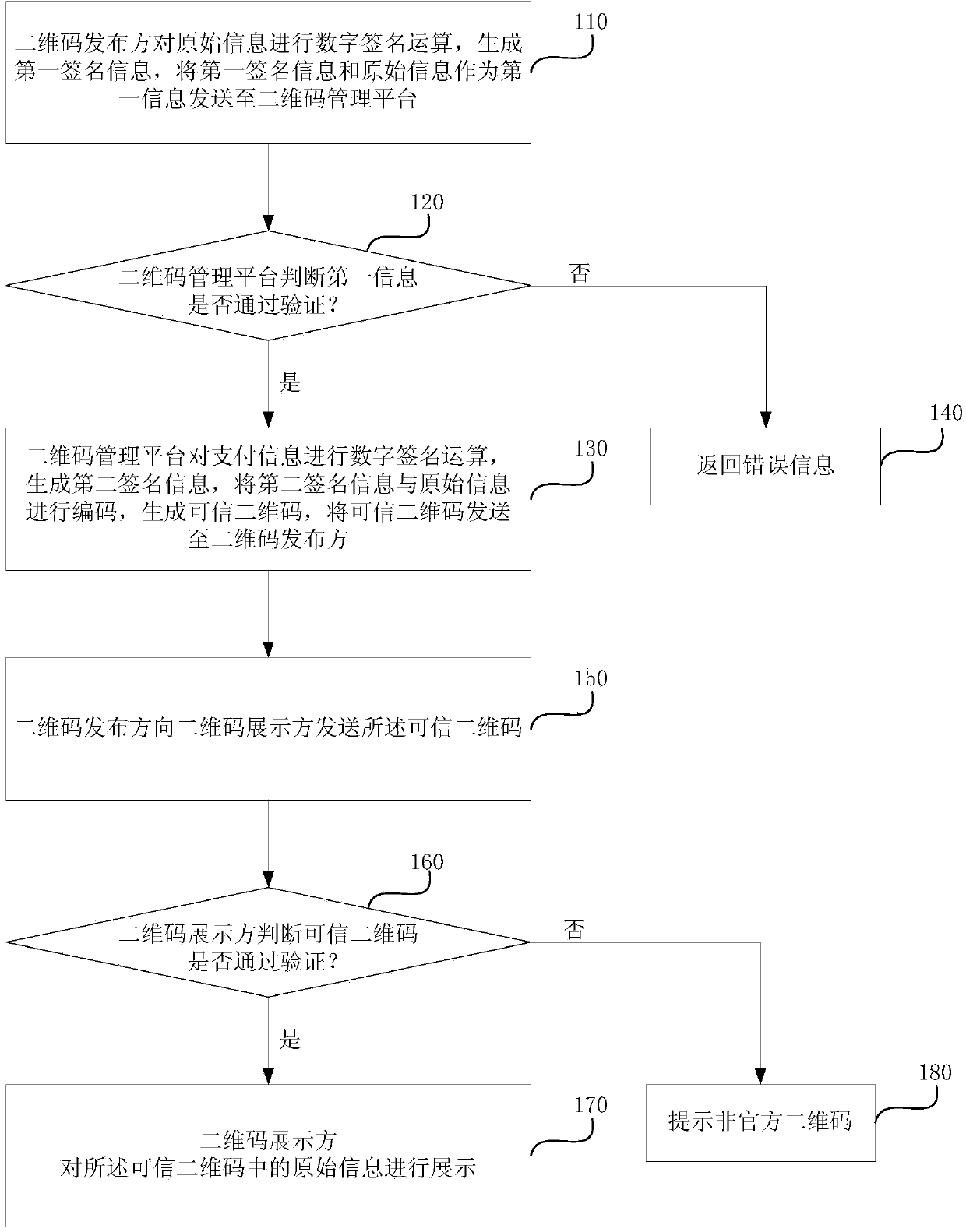
[0034] figure 1 It is a flowchart of a secure payment method based on a trusted two-dimensional code provided in the first embodiment of the present invention. The method in this embodiment can be executed by a secure payment system based on a trusted two-dimensional code. The system includes a two-dimensional Code issuer, QR code management platform and QR code display party. The method of this embodiment specifically includes the following steps:
[0035] Step 110, the two-dimensional code issuer performs digital signature calculation on the original information, generates first signature information, and sends the first signature information and original information as first information to the two-dimensional code management platform. Wherein, the original information includes item information and payment information.
[0036] In this embodiment, the two-dimensional code issuer does not directly generate the two-dimensional code, but sends the original information for gen...
no. 2 example
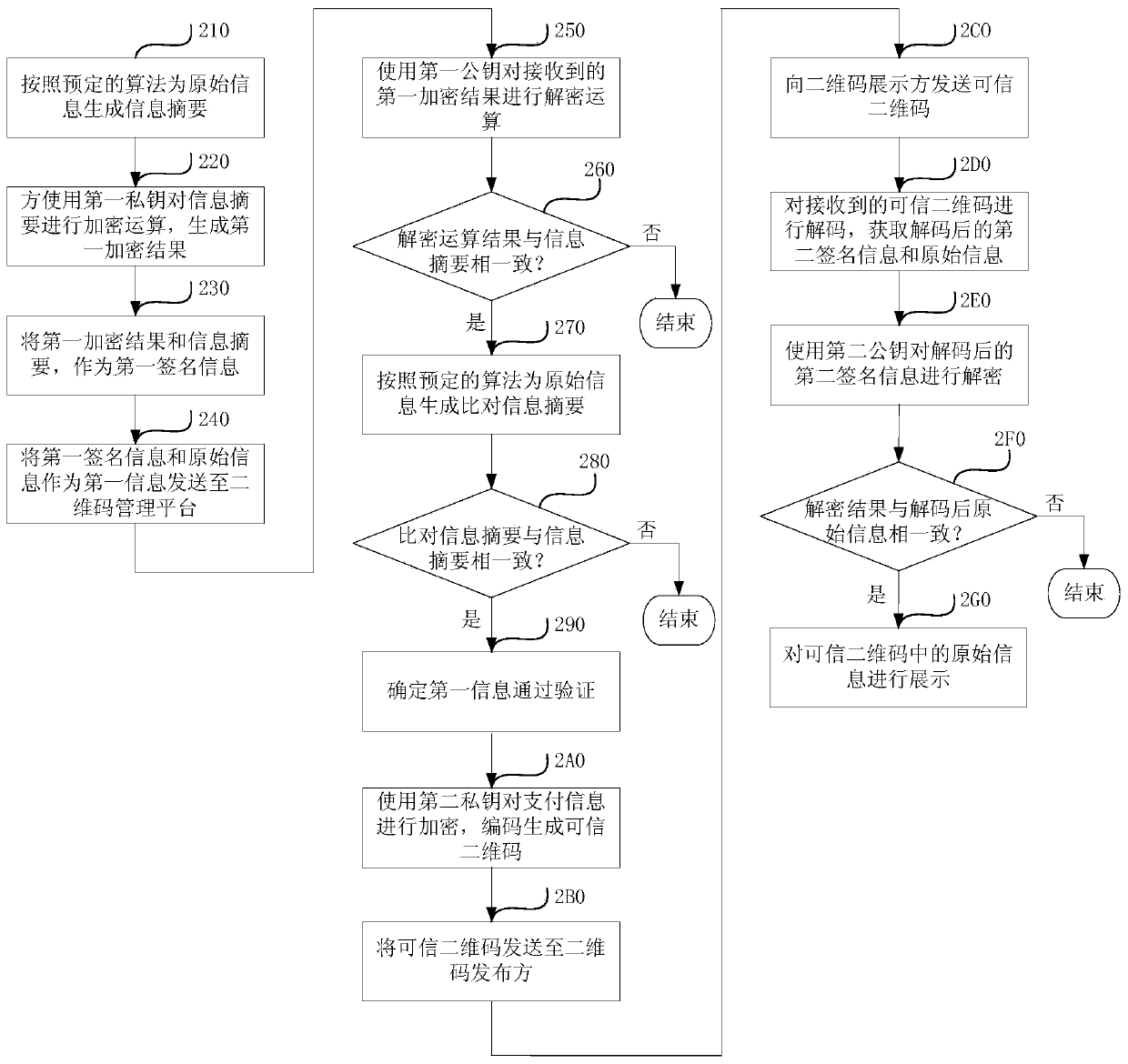
[0062] figure 2 It is a flow chart of a secure payment method based on a trusted two-dimensional code provided in the second embodiment of the present invention. On the basis of the above-mentioned embodiments, this embodiment uses a public key pair to perform digital signatures. Wherein, the two-dimensional code issuer stores the first public key-private key pair, including the first public key and the first private key, and stores the first public key in the two-dimensional code management platform at the same time; the two-dimensional code management platform stores the first public key The second public key-private key pair includes a second public key and a second private key, and simultaneously stores the second public key on the two-dimensional code display party. The method of this embodiment specifically includes the following steps:
[0063] Step 210, the two-dimensional code issuer generates an information summary for the original information according to a predet...
no. 3 example
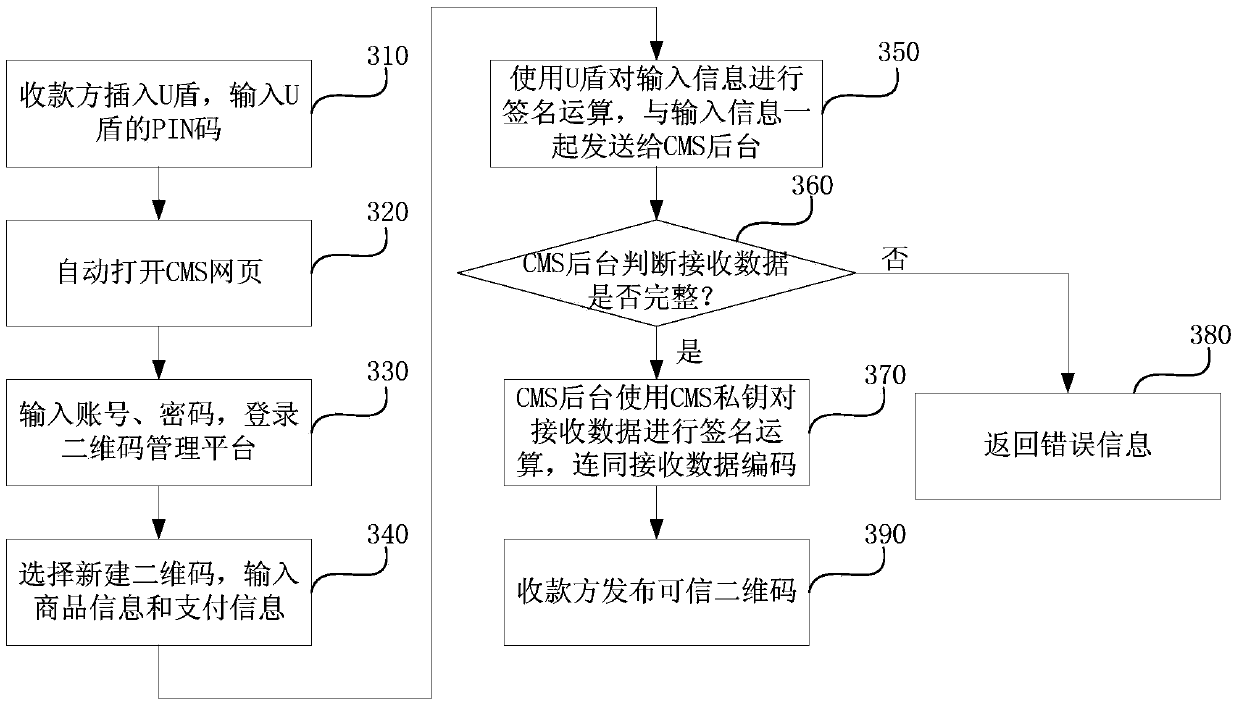
[0083] image 3 and Figure 4 It is a flow chart of creating and scanning an authentic two-dimensional code according to the third embodiment of the present invention. In this embodiment, the two-dimensional code issuer is the payee in the payment activity. The two-dimensional code management platform is established through CMS and opened to the payee through web page login. The two-dimensional code issuer first needs to enter the Register on the CMS webpage. After the registration is successful, the QR code management platform will assign a USB shield to the QR code issuer to verify the identity of the payee; the QR code display party is the payer in the payment activity, and the QR code The code management platform provides a specific scanning client for the payer to realize the credible verification of the received QR code by the payer.
[0084] like image 3 Shown is a flow chart of a method for creating a trusted two-dimensional code according to the third embodiment o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com