Patents
Literature
261 results about "Data virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data virtualization is any approach to data management that allows an application to retrieve and manipulate data without requiring technical details about the data, such as how it is formatted at source, or where it is physically located, and can provide a single customer view (or single view of any other entity) of the overall data.
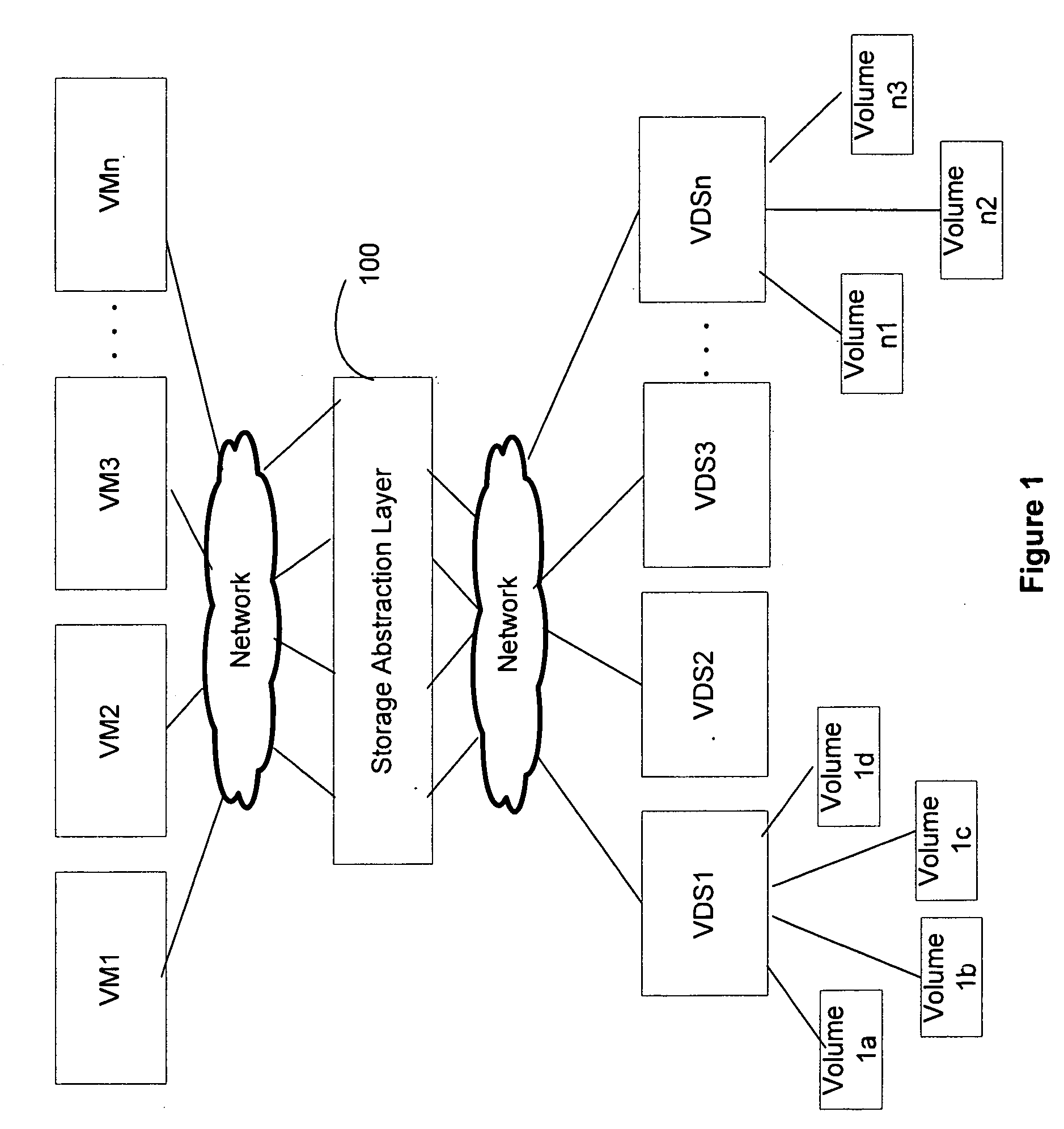
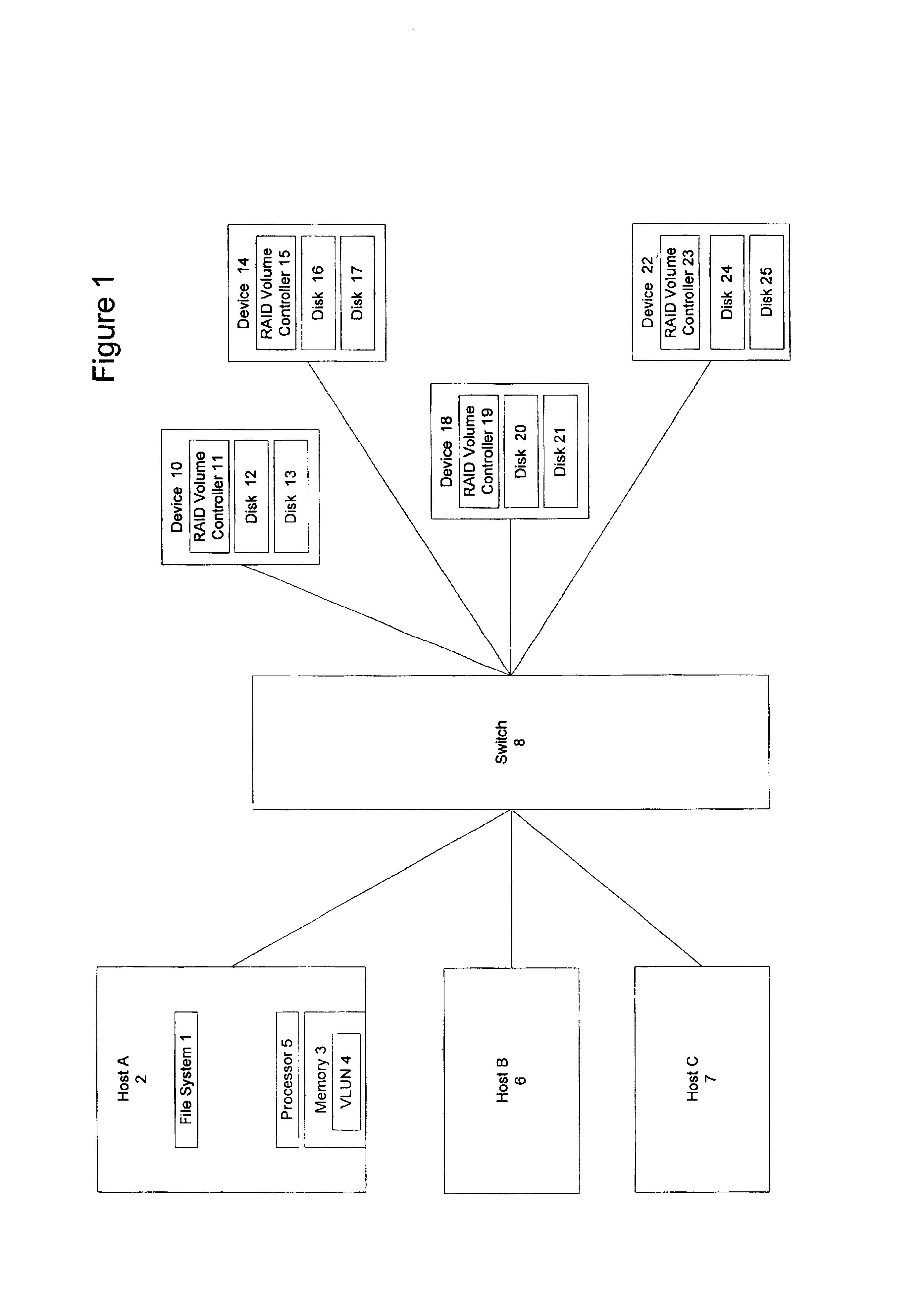
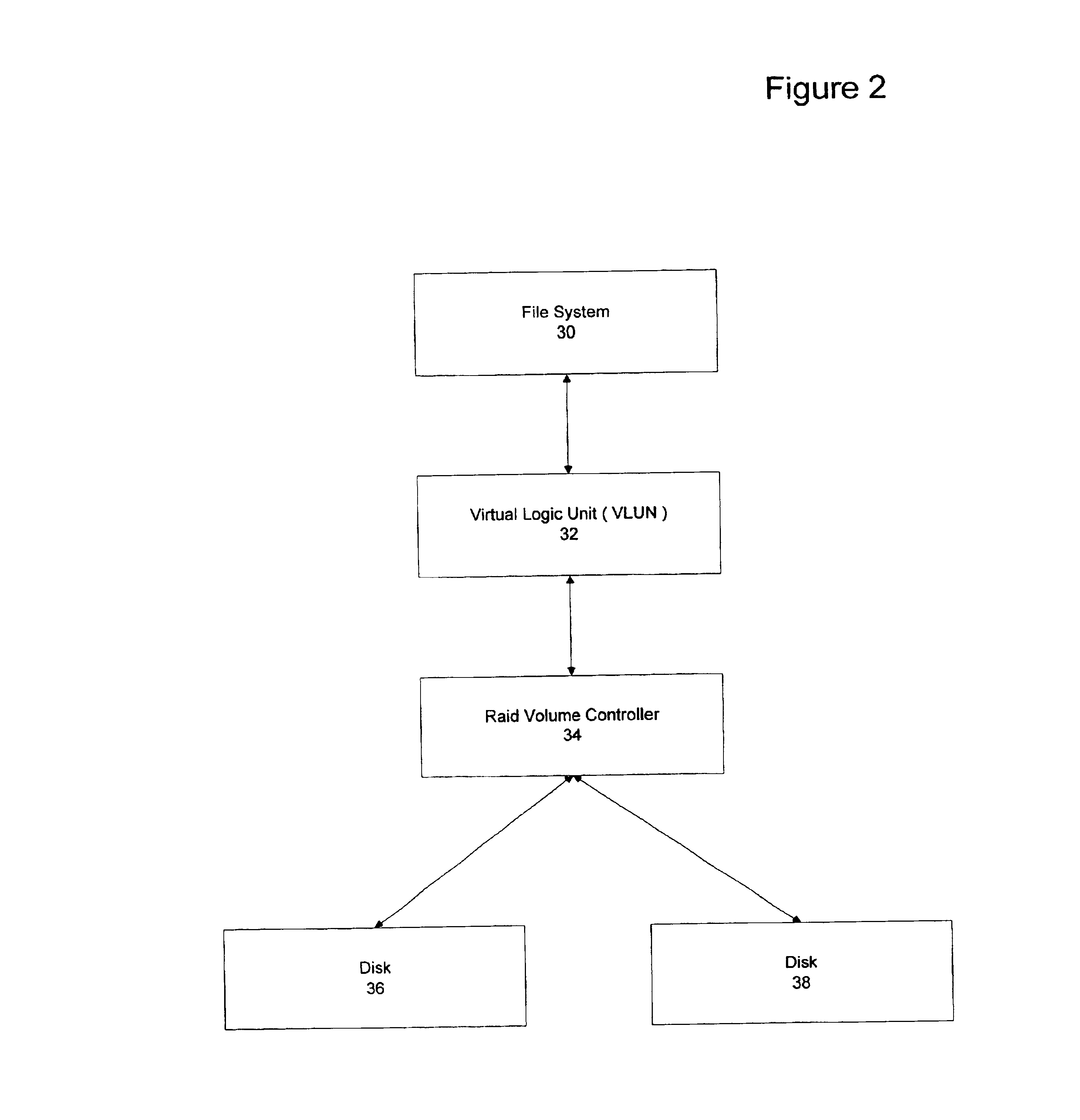
Storage virtualization by layering virtual disk objects on a file system
InactiveUS7107385B2Input/output to record carriersData processing applicationsOperational systemFile system
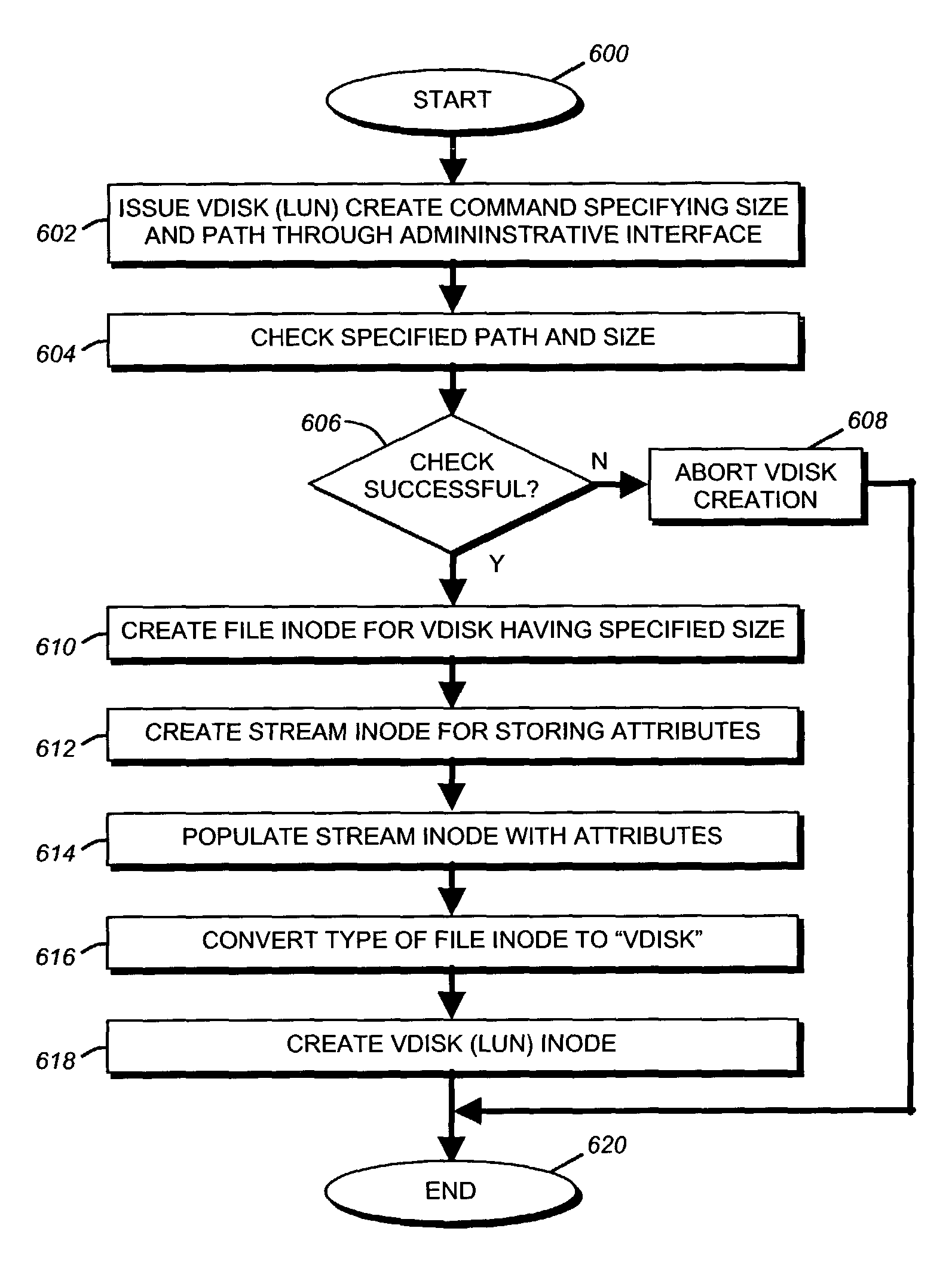
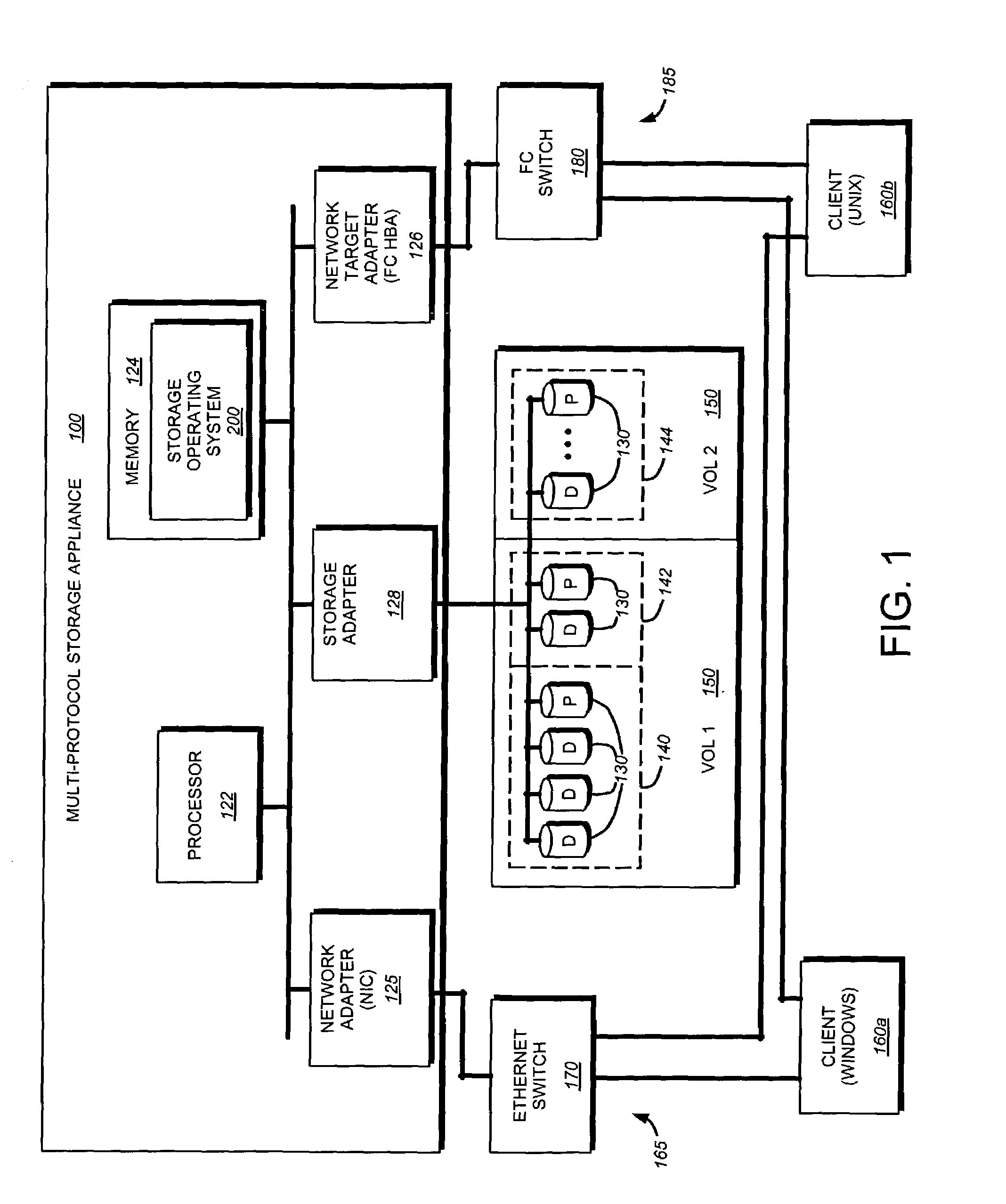
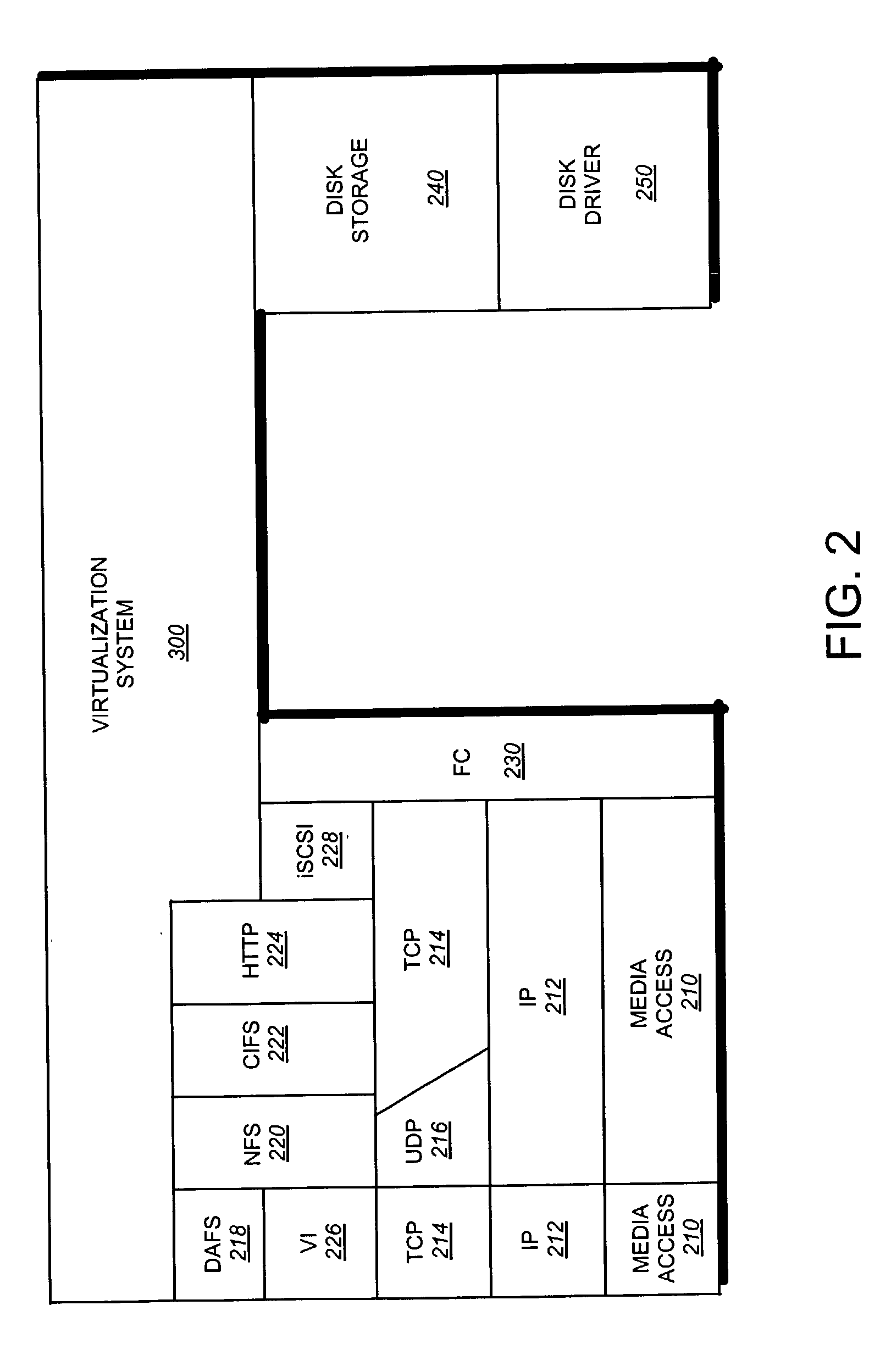
A storage virtualization selection technique “automates” a virtualization selection process to create virtual disk (vdisk) storage objects over a volume of a file system implemented by a storage operating system of a multi-protocol storage appliance. The file system provides a virtualization system that aggregates physical storage of a set of disks or portions (e.g., extents) of disks into a pool of blocks that can be dynamically allocated to form a vdisk. The file system also provides reliability guarantees for the vdisks in accordance with its underlying architecture. That is, the file system organizes its storage within volumes created among the managed disks. The vdisk is thereafter created as a storage object within a volume and, thus, inherits the underlying reliability configuration associated with that volume. The portions are aggregated and allocated as a vdisk with reliability guarantees in response to a request to create the vdisk from a user of the storage appliance and without further user involvement.
Owner:NETWORK APPLIANCE INC
End-to-end virtualization
InactiveUS20120099602A1Facilitates end-to-end virtualizationData switching by path configurationData virtualizationNetwork virtualization
One embodiment of the present invention provides a system that facilitates end-to-end virtualization. During operation, a network interface residing on an end host sets up a tunnel. The network interface then encapsulates a packet destined to a virtual machine based on a tunneling protocol. By establishing a tunnel that allows a source host to address a remote virtual machine, embodiments of the present invention facilitate end-to-end virtualization.
Owner:AVAGO TECH INT SALES PTE LTD
Data virtualization across heterogeneous formats
ActiveUS20160055184A1Digital data information retrievalDigital data processing detailsData sourceData virtualization
Various embodiments virtualize data across heterogeneous formats. In one embodiment, a plurality of heterogeneous data sources is received as input. A local schema graph including a set of attribute nodes and a set of type nodes is generated for each of the plurality of heterogeneous data sources. A global schema graph is generated based on each local schema graph that has been generated. The global schema graph comprises each of the local schema graphs and at least one edge between at least one of two or more attributes nodes and two or more type nodes from different local schema graphs. The edge indicates a relationship between the data sources represented by the different local schema graphs comprising the two or more attributes nodes based on a computed similarity between at least one value associated with each of the two or more attributes nodes.
Owner:IBM CORP
Storage virtualization system and methods
InactiveUS6857059B2Reduce consumptionWithout impactInput/output to record carriersMemory adressing/allocation/relocationStorage area networkNetwork virtualization
Storage virtualization systems and methods that allow customers to manage storage as a utility rather than as islands of storage which are independent of each other. A demand mapped virtual disk image of up to an arbitrarily large size is presented to a host system. The virtualization system allocates physical storage from a storage pool dynamically in response to host I / O requests, e.g., SCSI I / O requests, allowing for the amortization of storage resources through a disk subsystem while maintaining coherency amongst I / O RAID traffic. In one embodiment, the virtualization functionality is implemented in a controller device, such as a controller card residing in a switch device or other network device, coupled to a storage system on a storage area network (SAN). The resulting virtual disk image that is observed by the host computer is larger than the amount of physical storage actually consumed.
Owner:EMC IP HLDG CO LLC
Apparatus and method for data virtualization in a storage processing device
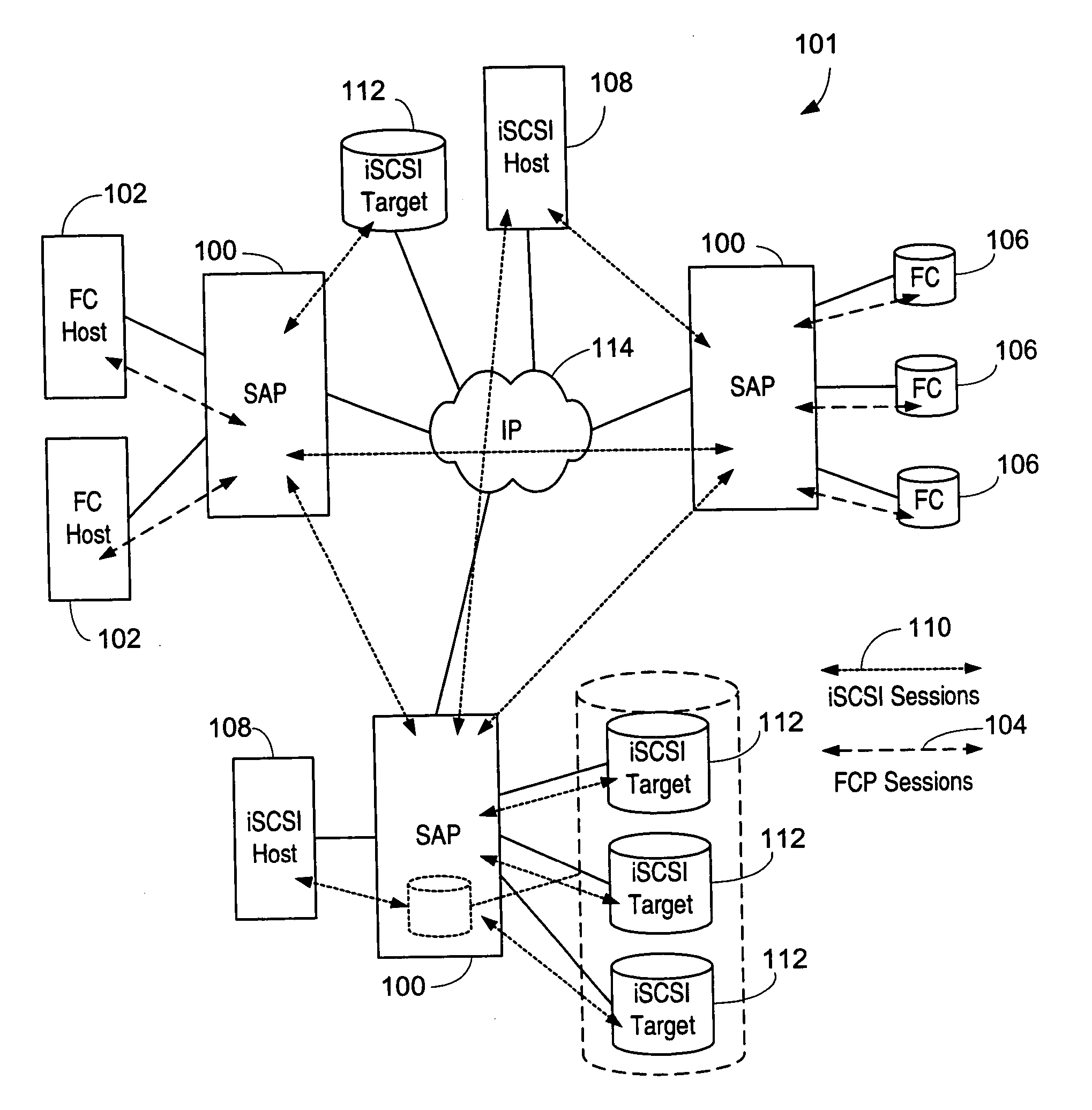
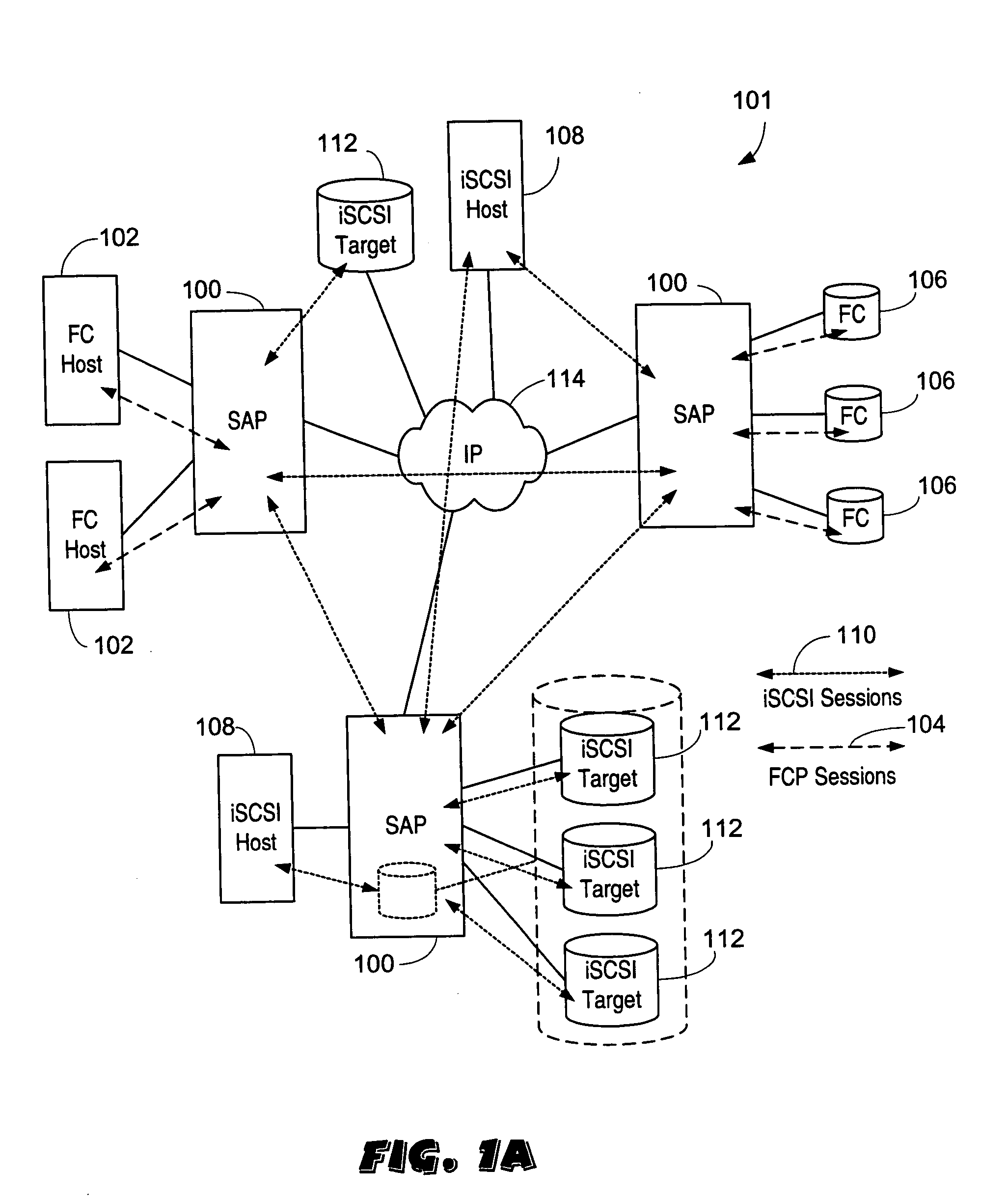
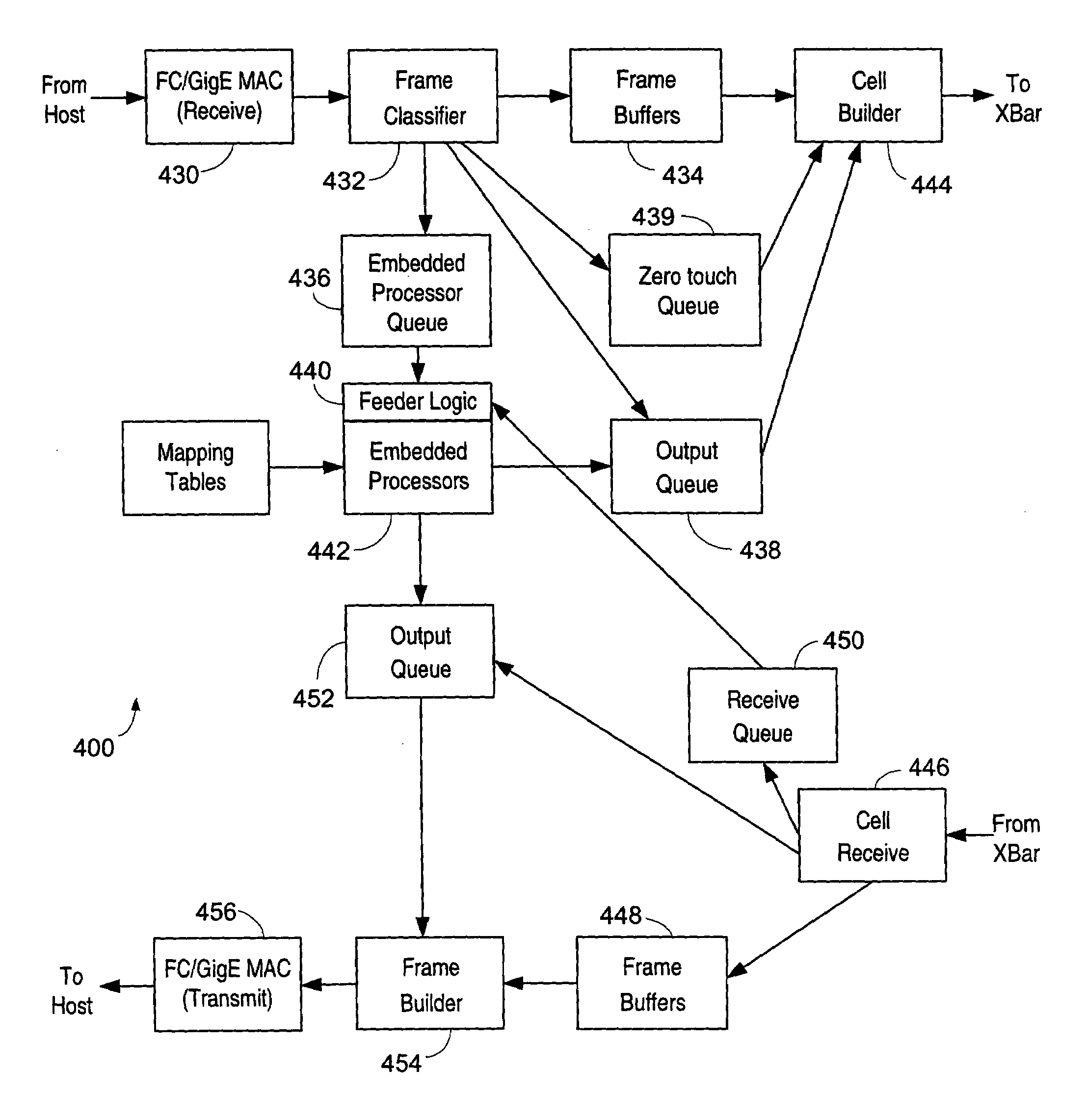
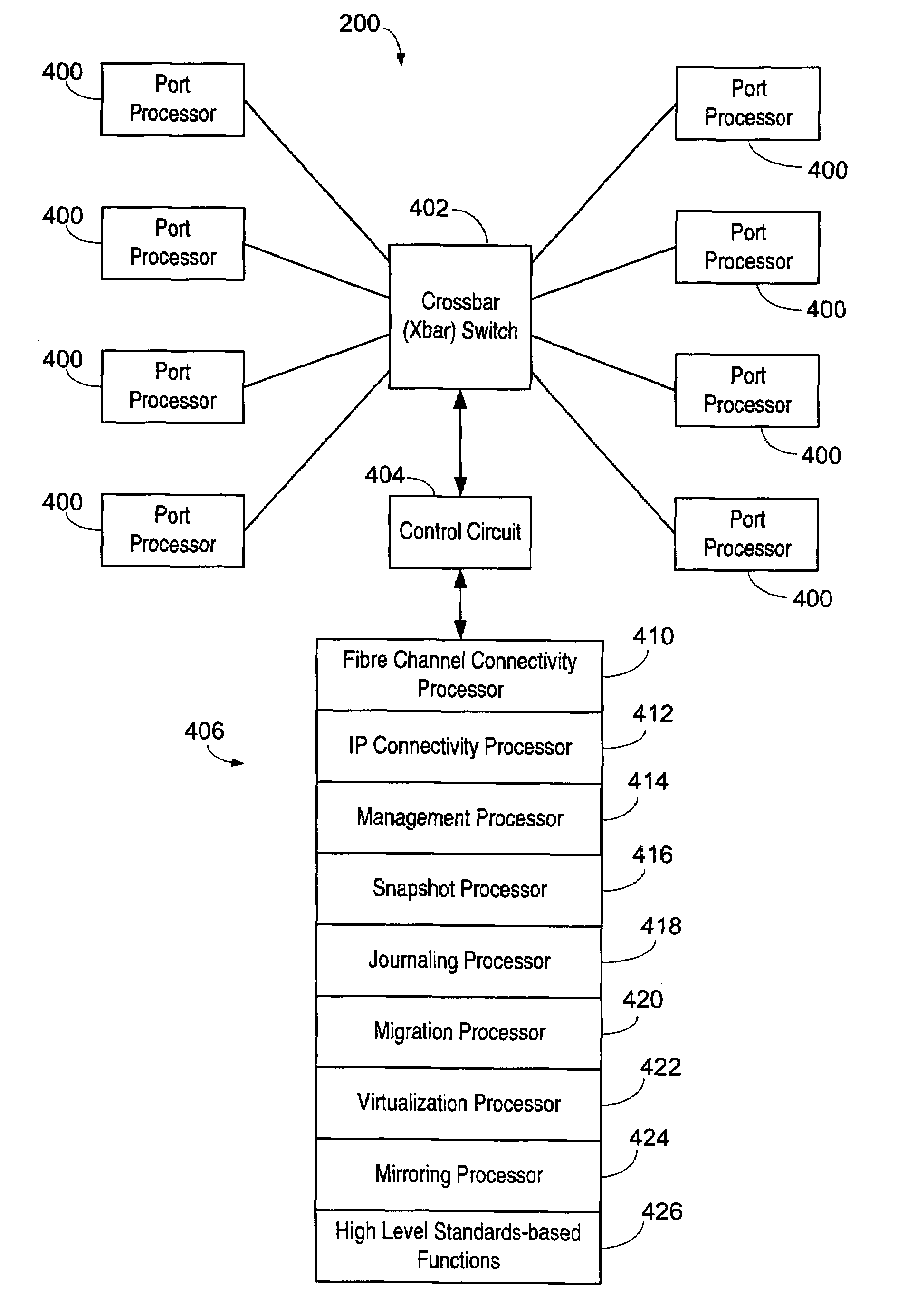
ActiveUS20050033878A1Achieve scaleProvide flexibilityMultiplex system selection arrangementsInput/output to record carriersInternet trafficMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
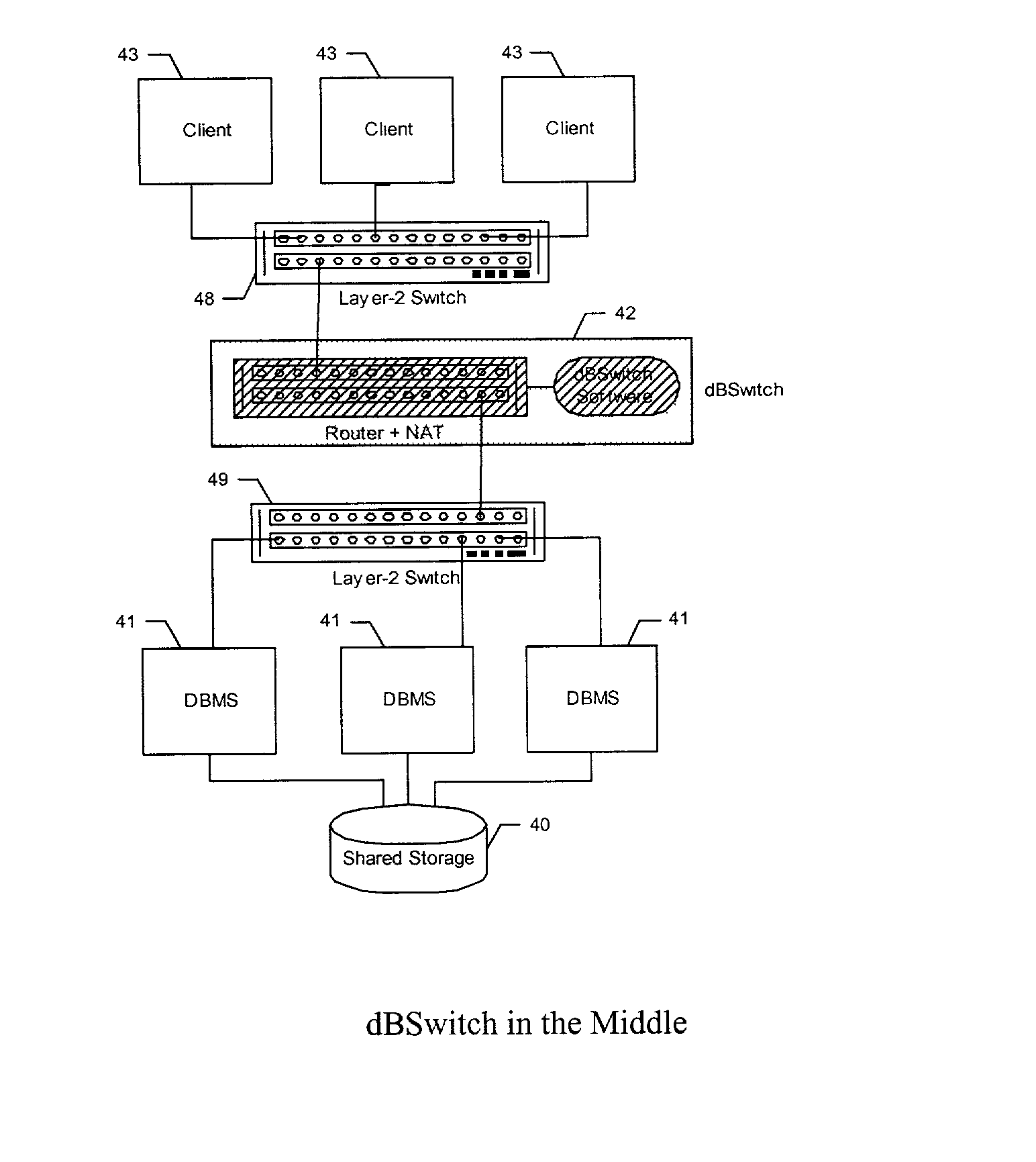
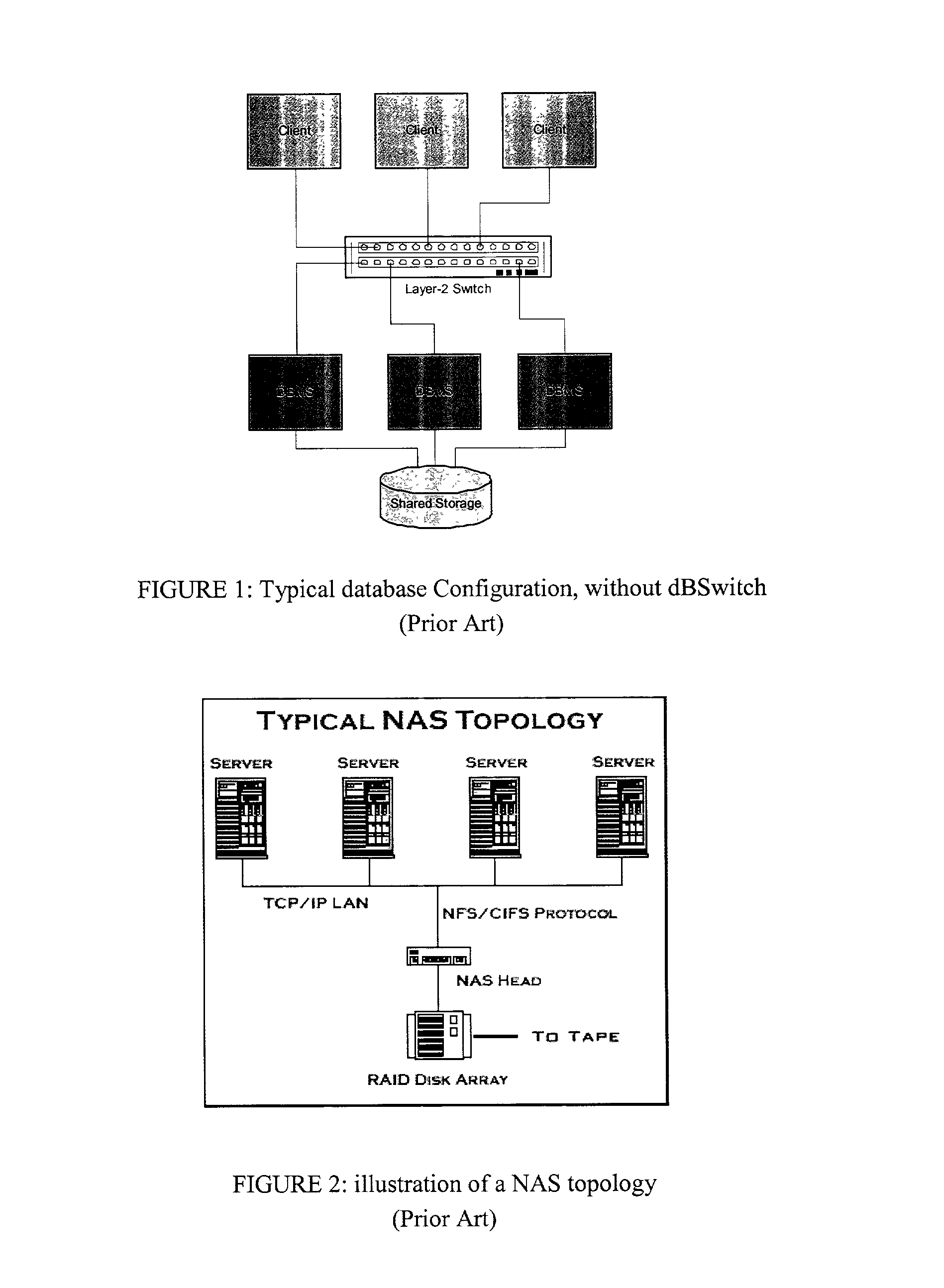
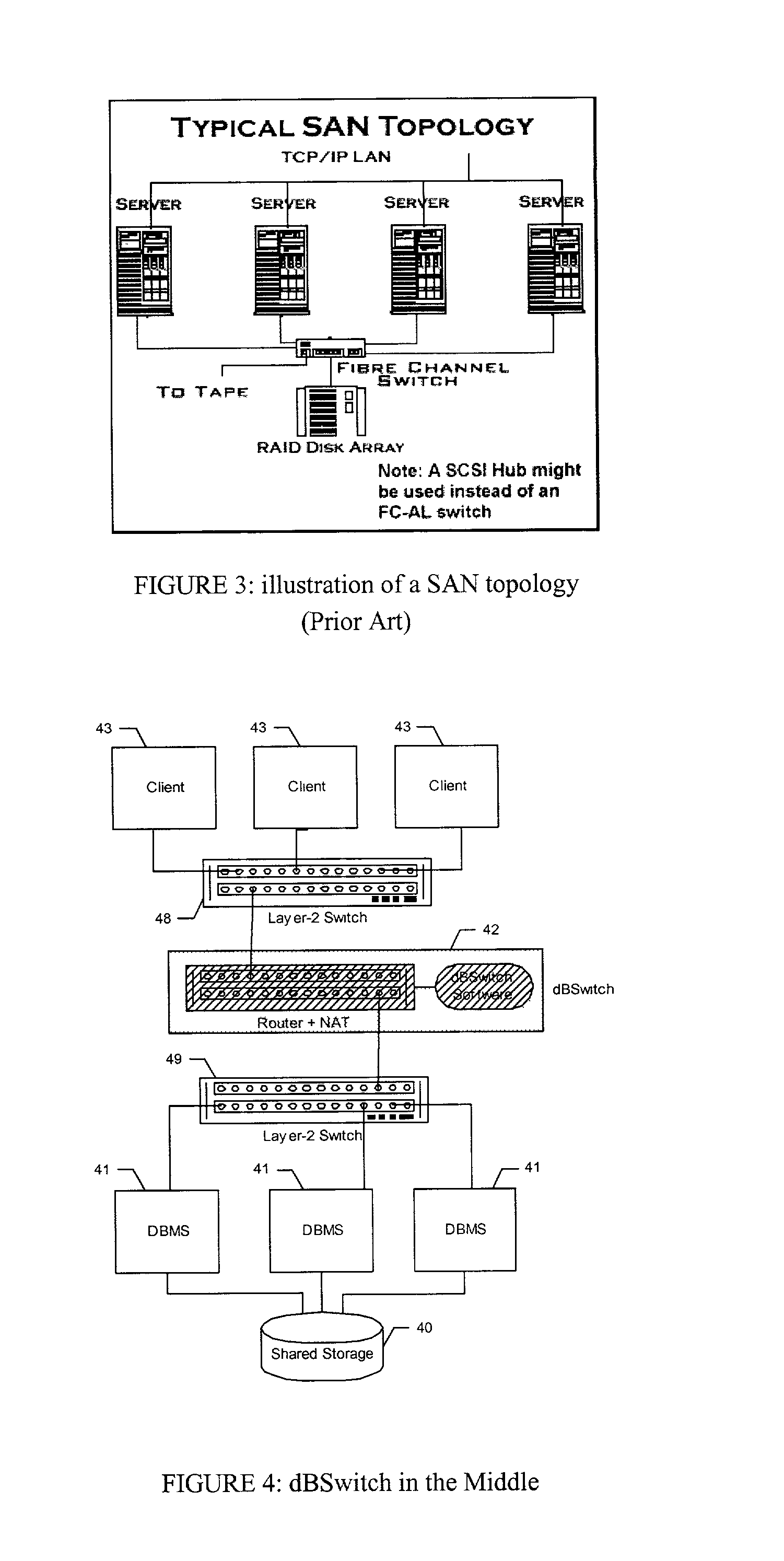
Database Switch enabling a database area network
InactiveUS20030154236A1Multiple digital computer combinationsTransmissionArea networkApplication software
A method and system for improving utilization of the typical DBMS client-server configuration is provided. Specifically, the present invention can include a Database Switch (dBSwitch) situated between the applications and database servers in a network, capable of dynamically and transparently connecting applications to databases using standard database servers and standard protocols. The Database Switch appliance performs this database routing in real time, with high bandwidth and negligible latency. The Database Switch enables the formation of a Database Area Network (DAN) architecture, which promotes database virtualization by integrating the database servers, the shared storage, and the interconnecting network, making them appear to be one large, scalable database server. This DAN architecture yields high utilization, high availability, scalability on demand, simplified management and security, in a shared and heterogeneous application environment.
Owner:DAR SHAUL +3
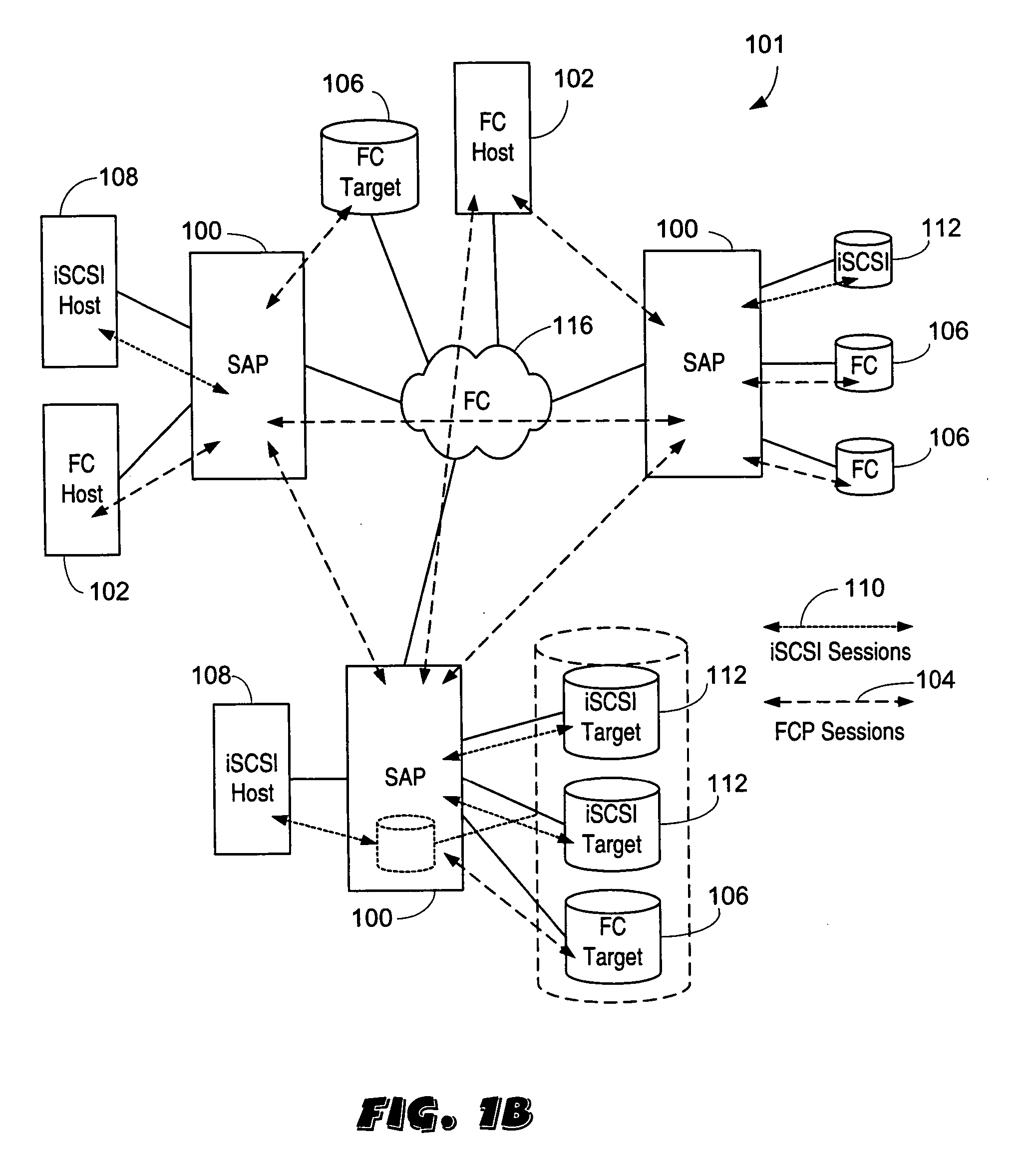
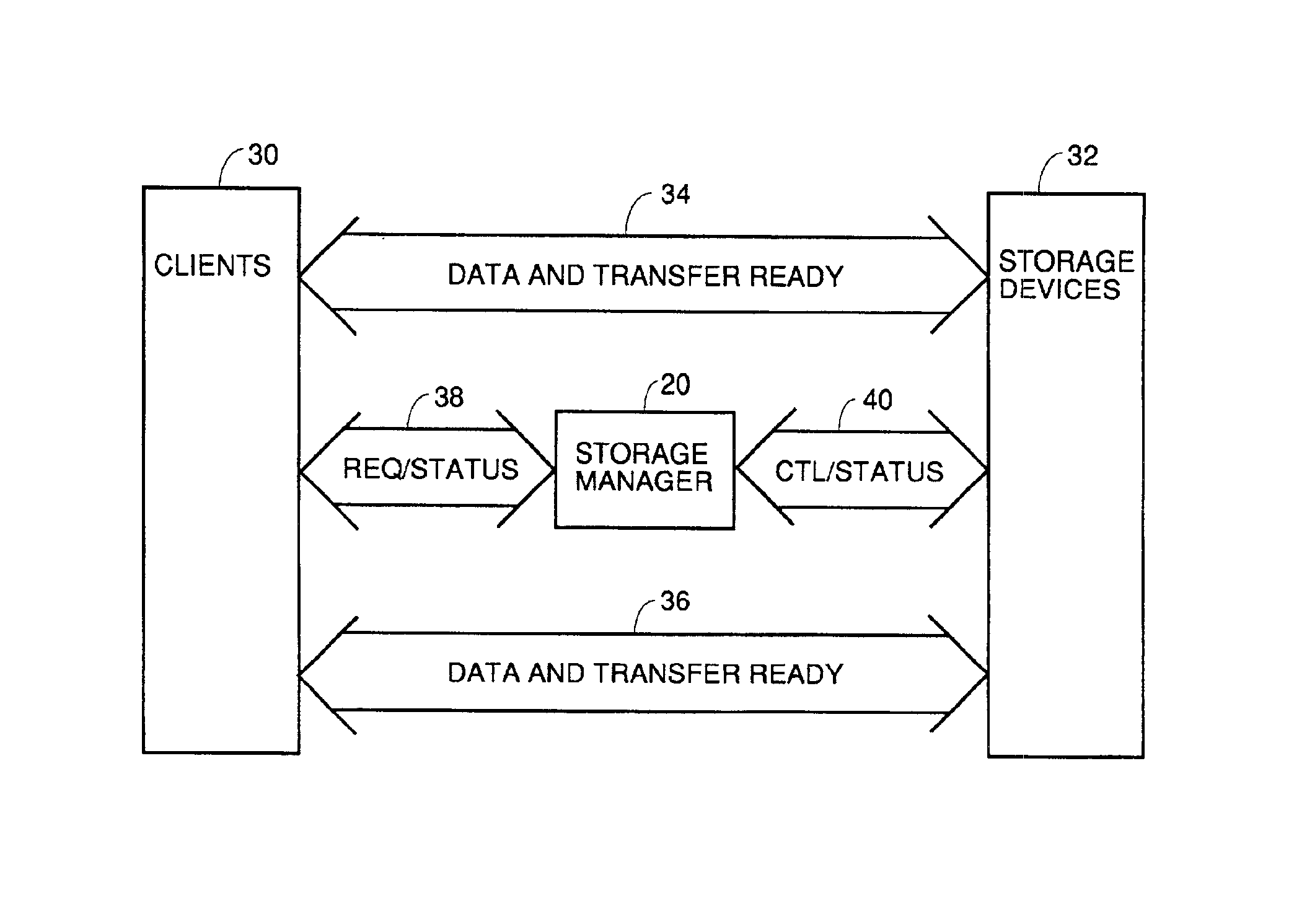
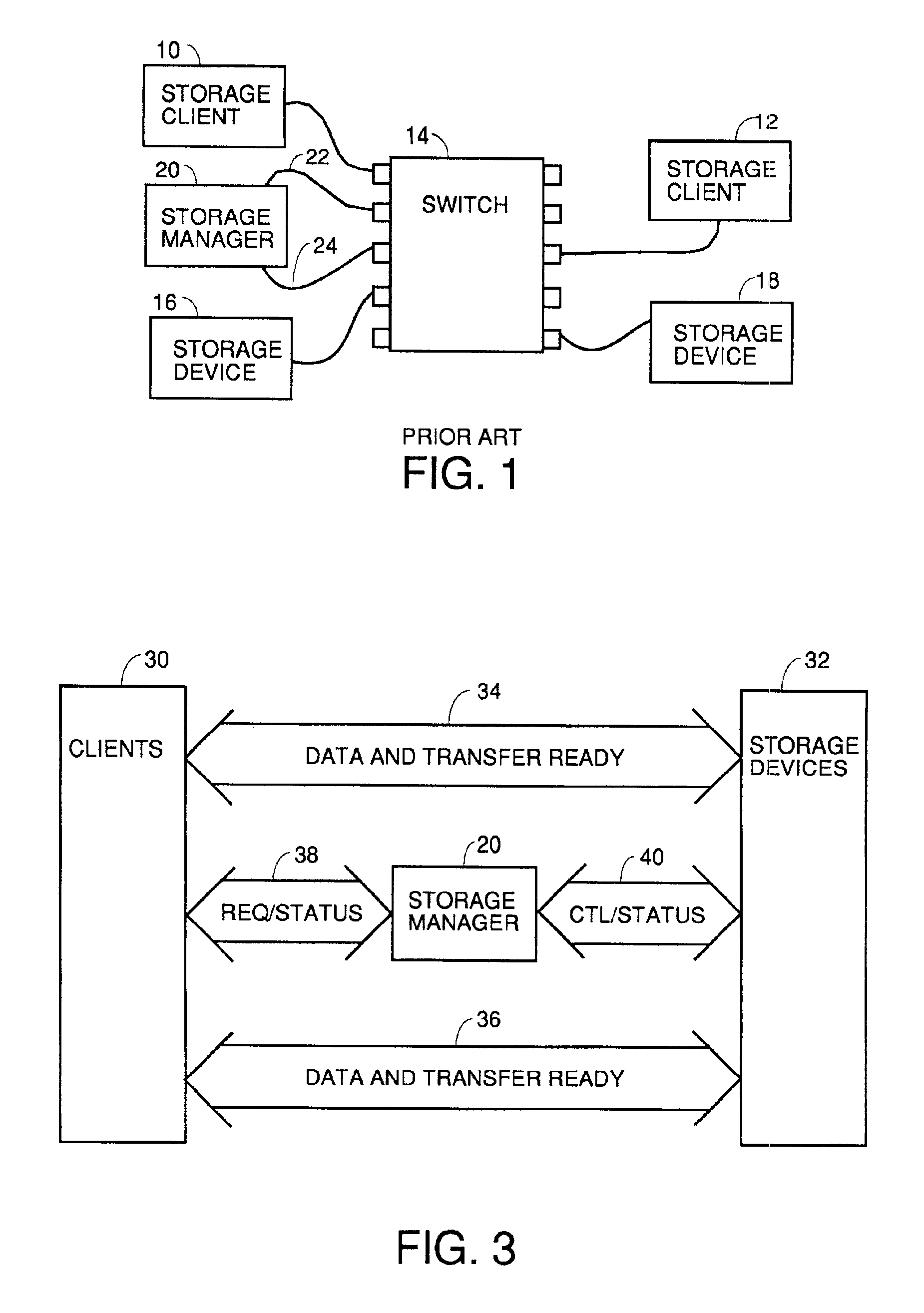
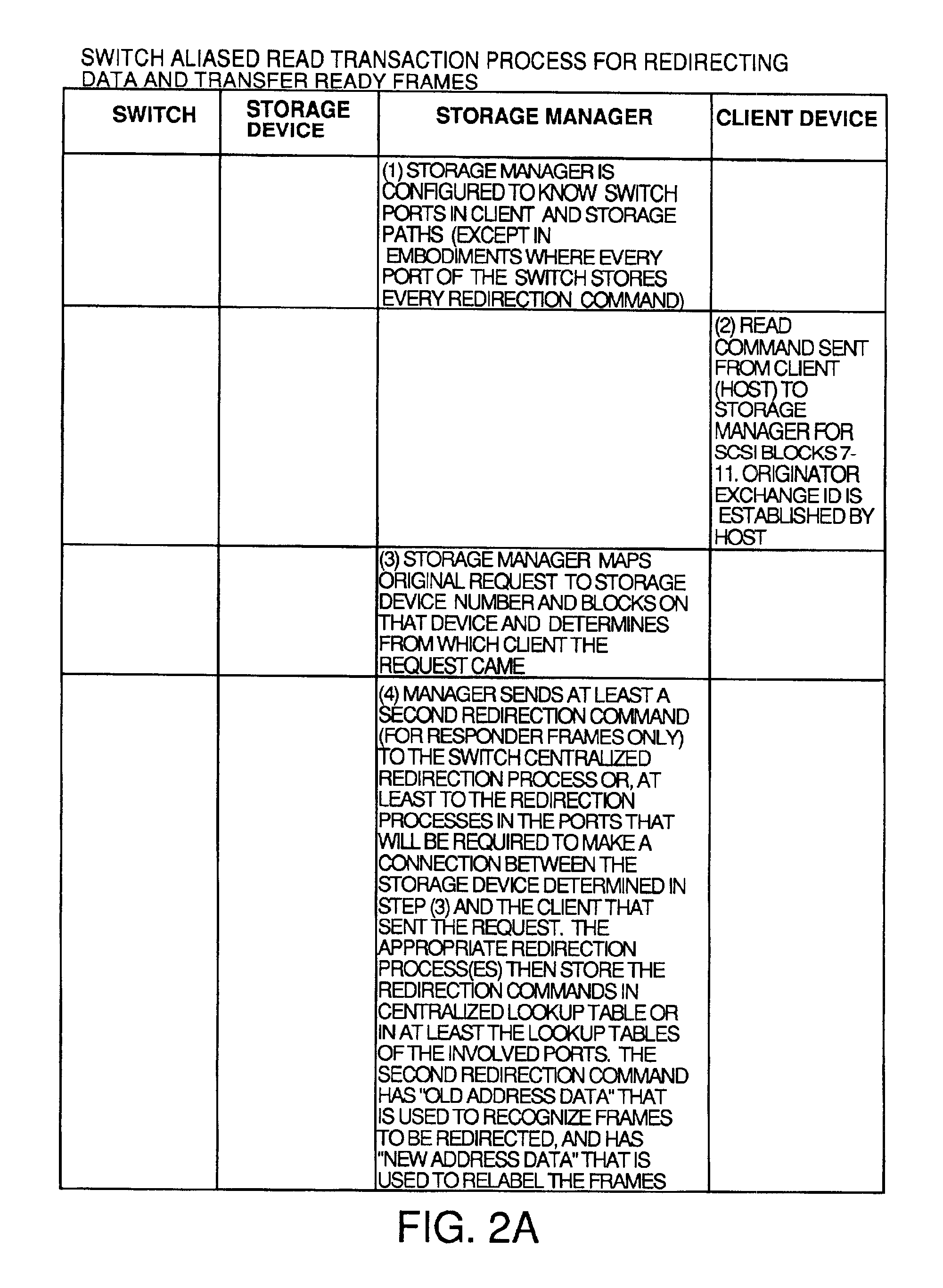
Switch assisted frame aliasing for storage virtualization
InactiveUS6876656B2Reduce the burden onError preventionTransmission systemsTransaction dataData virtualization
An apparatus and process for relabelling and redirecting at least some of the read transaction data frames and the write transaction write data and transfer ready frames in a network so as to bypass a storage manager and pass directly between the client and a storage device via a switch. This eliminates the storage manager as a bottleneck. Some embodiments redirect every read and write transaction, and others redirect only large transactions, or only ones not stored in cache or when latency gets too high. Redirection is accomplished by transmission from the storage manager to a switch redirection commands that contain old and new address data. When a frame to be redirected comes in, its address is compared to the old address data. If there is a match, the new address data is substituted and the frame is passed to a conventional routing process to be routed so as to bypass the storage manager.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
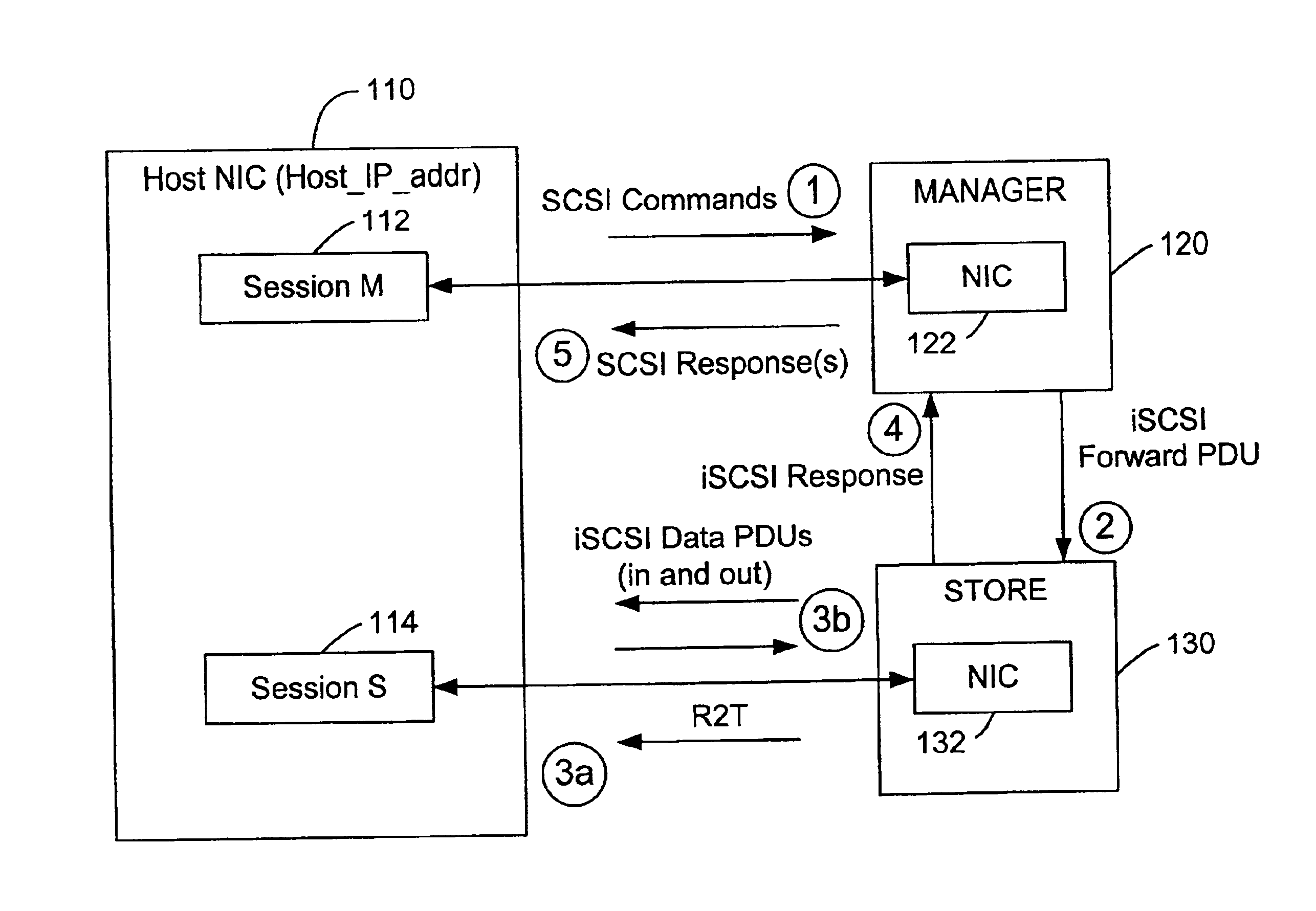
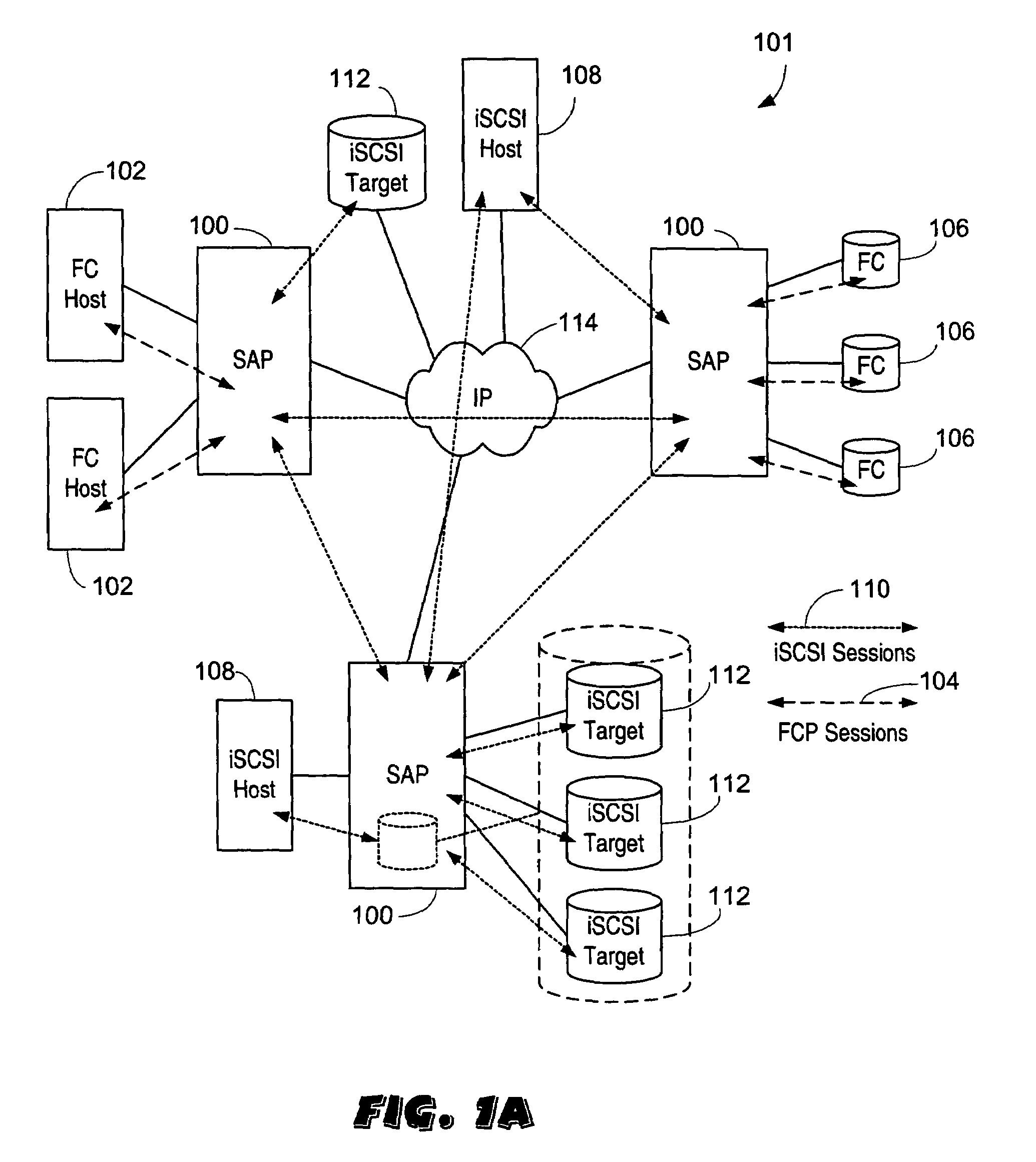
System and method for storage virtualization
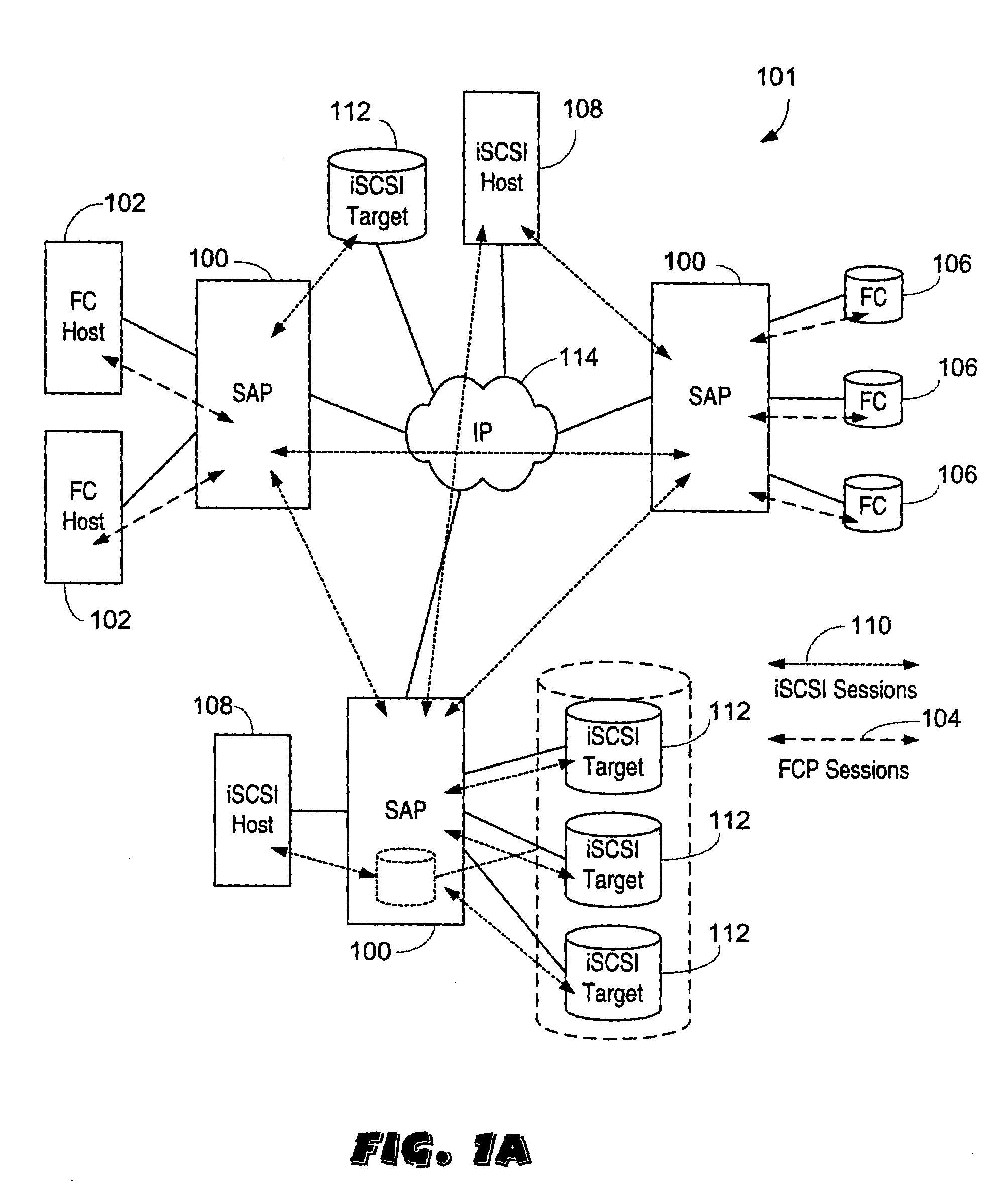
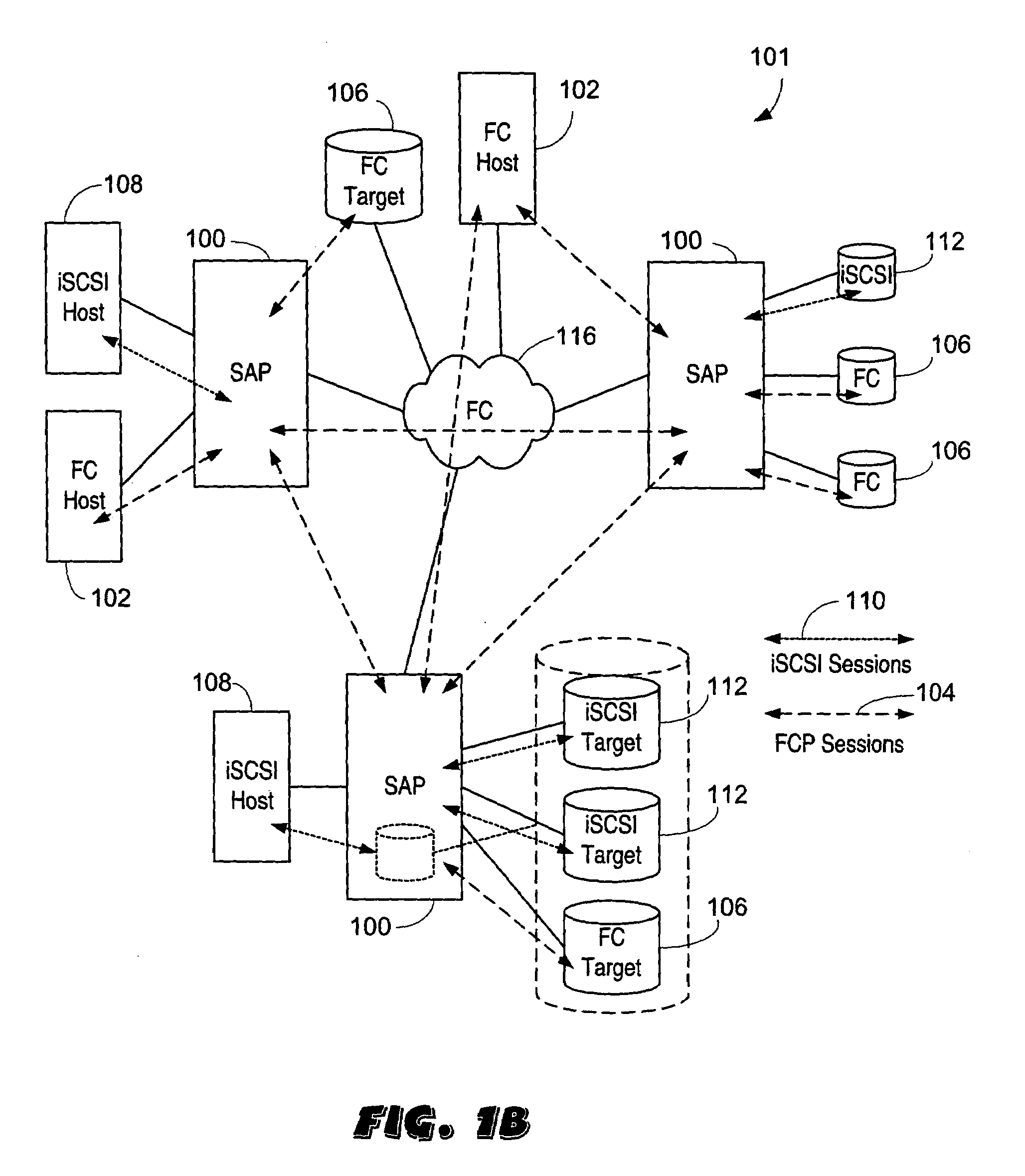
The present invention is generally directed to a system and method for virtualizing storage in a networked system. In accordance with one aspect of the invention, in a system having an initiator and at least one storage device, an inventive method determines, based upon a SCSI command received by a manager from the initiator, which of the data storage devices are implicated by the SCSI command. The method then forms an iSCSI command that is sent from the manager to each of the implicated storage devices, and receives at the manager an iSCSI response from each of implicated storage devices, after each of the storage devices has completed its implicated data transactions with the initiator. Finally, the method forms a SCSI response that is sent by the manager to the initiator. A corresponding system is also provided.
Owner:QUALCOMM INC
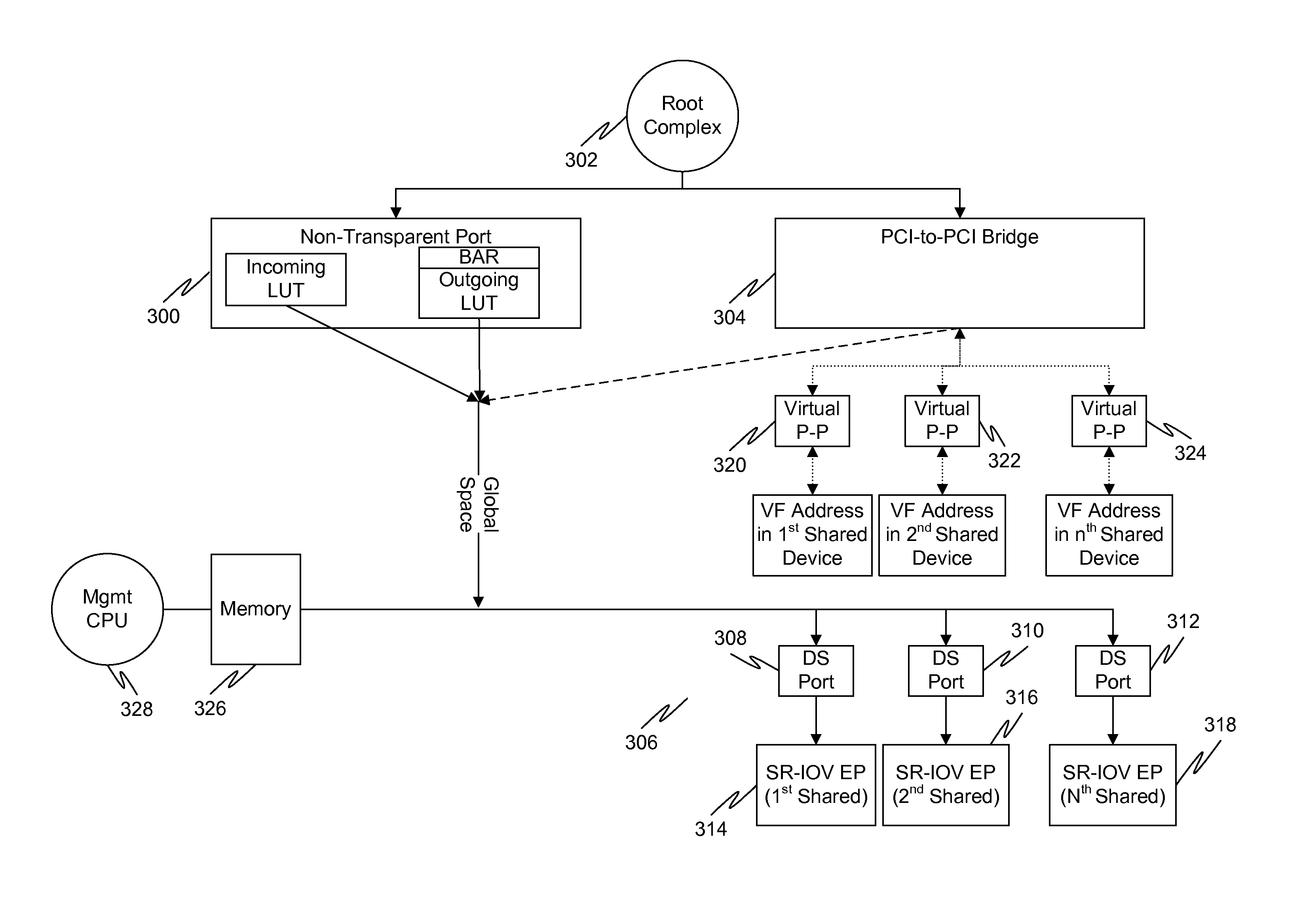
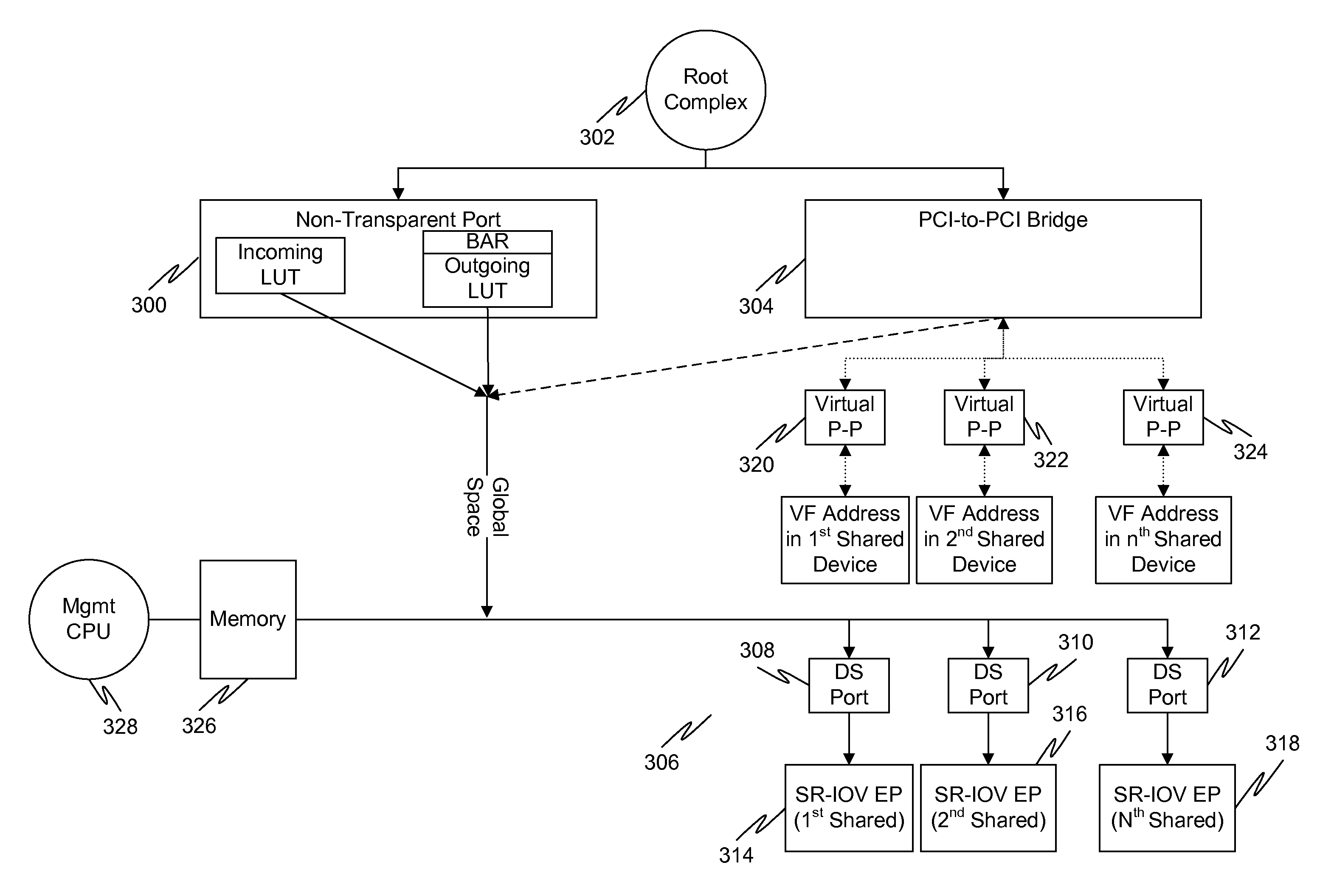
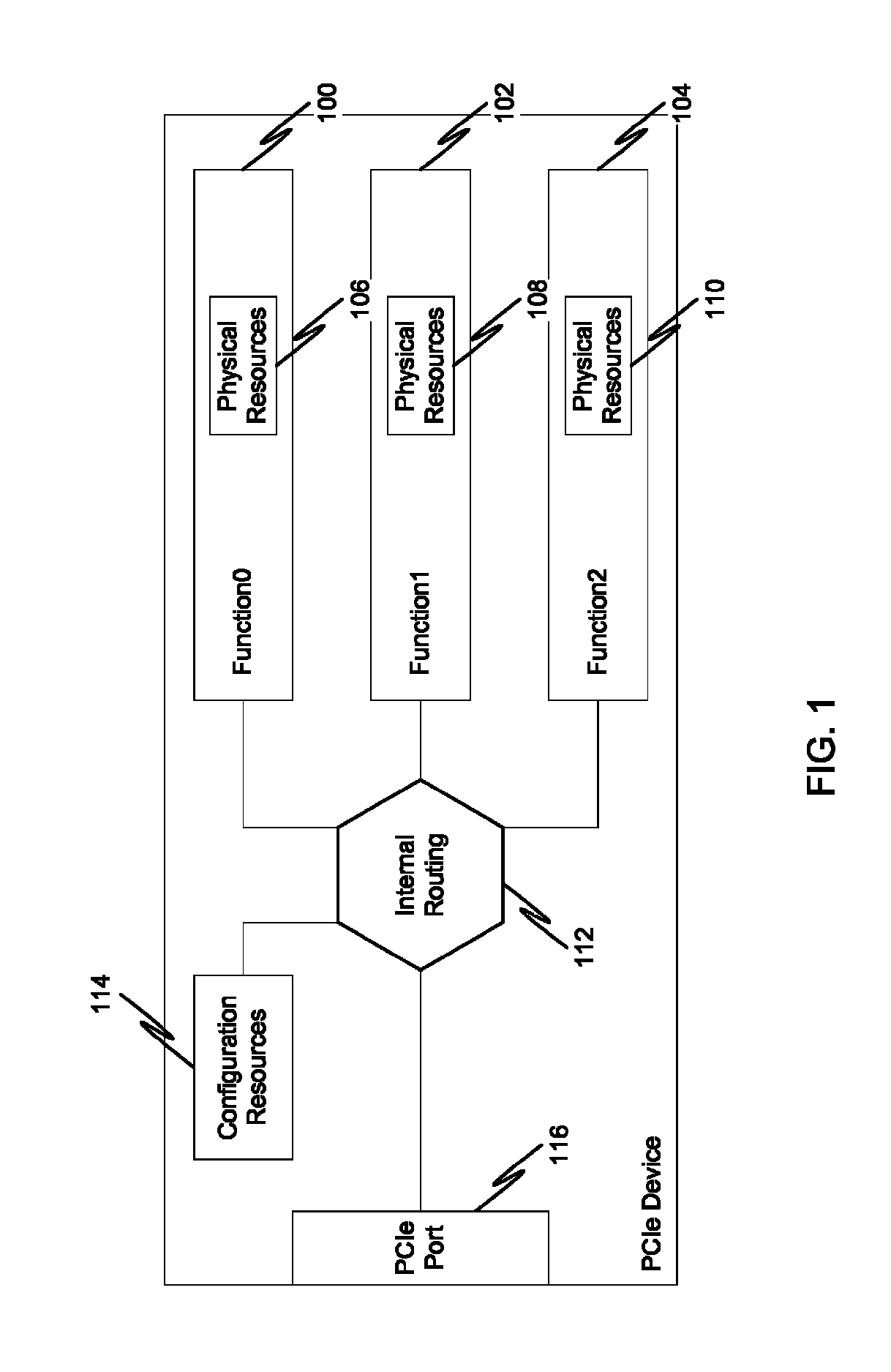
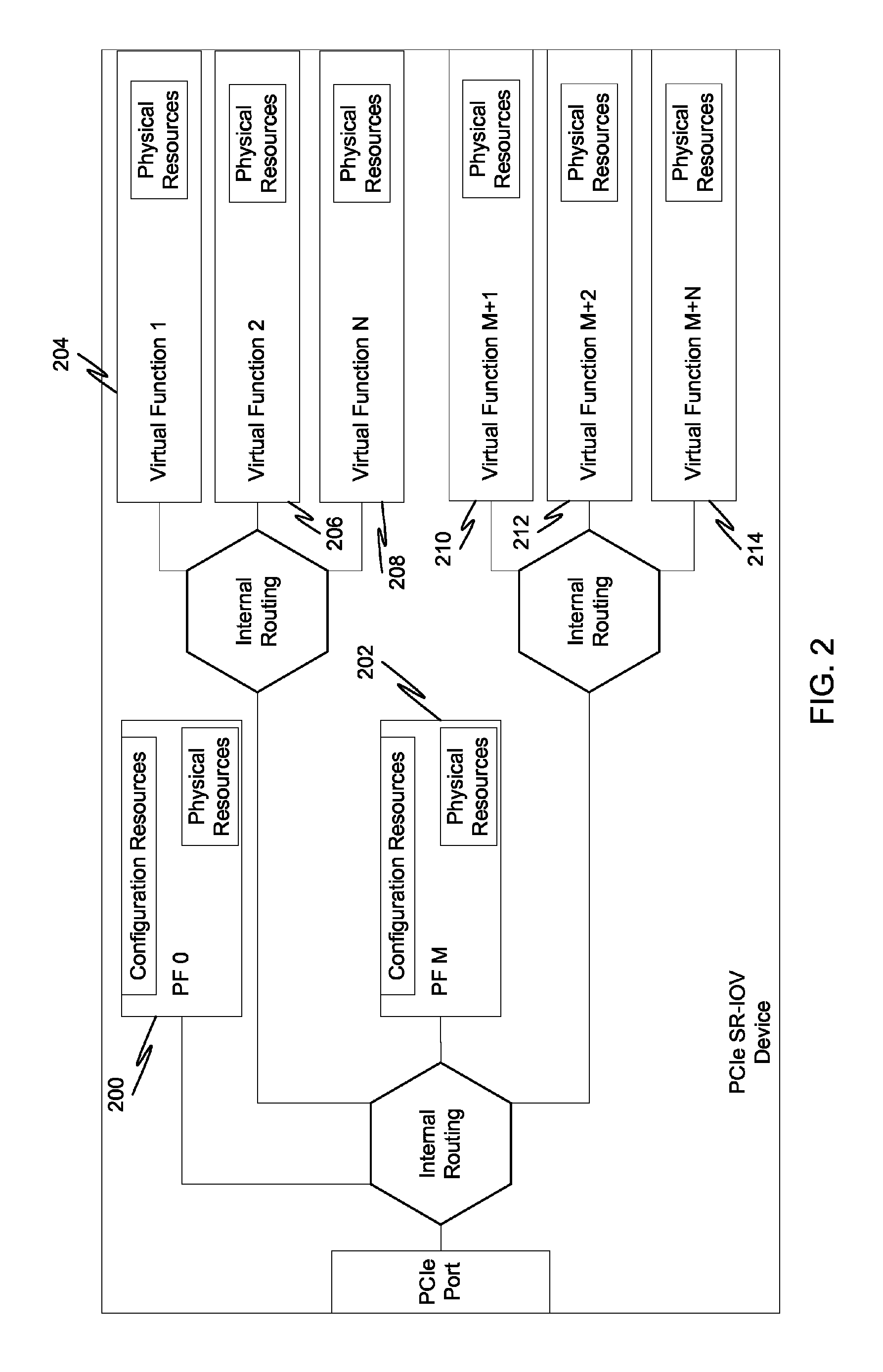
Multi-root sharing of single-root input/output virtualization
In a first embodiment of the present invention, a method for multi-root sharing of a plurality of single root input / output virtualization (SR-IOV) endpoints is provided, the method comprising: CSR redirection to a management processor which either acts as a proxy to execute the CSR request on behalf of the host or filters it and performs an alternate action, downstream routing of memory mapped I / O request packets through the switch in the host's address space and address translation with VF BAR granularity, upstream routing of requests originated by I / O devices by table lookup indexed by Requester ID, and requester ID translation using a fixed local-global RID offset.
Owner:AVAGO TECH INT SALES PTE LTD
Offloading packet processing for networking device virtualization
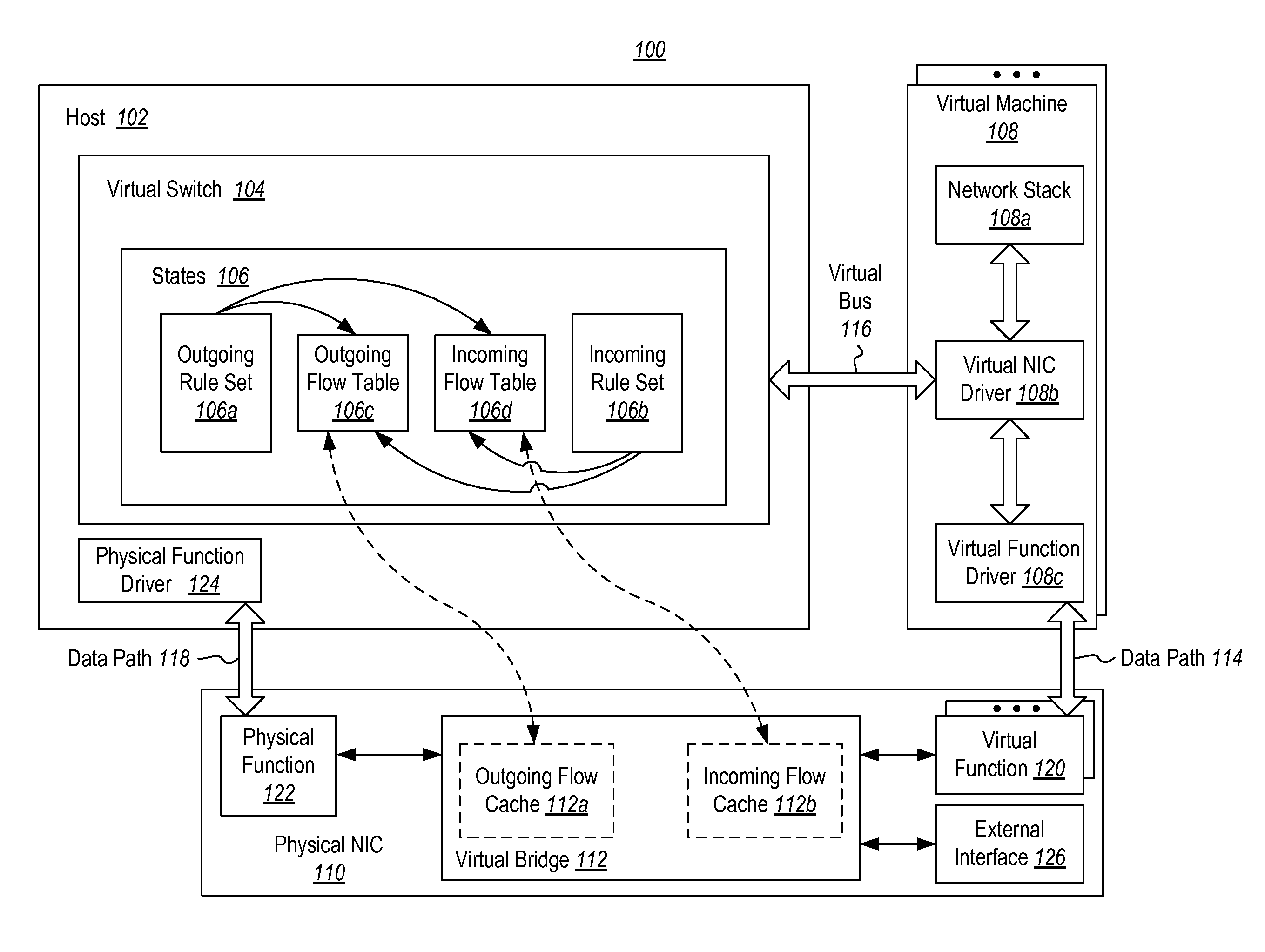
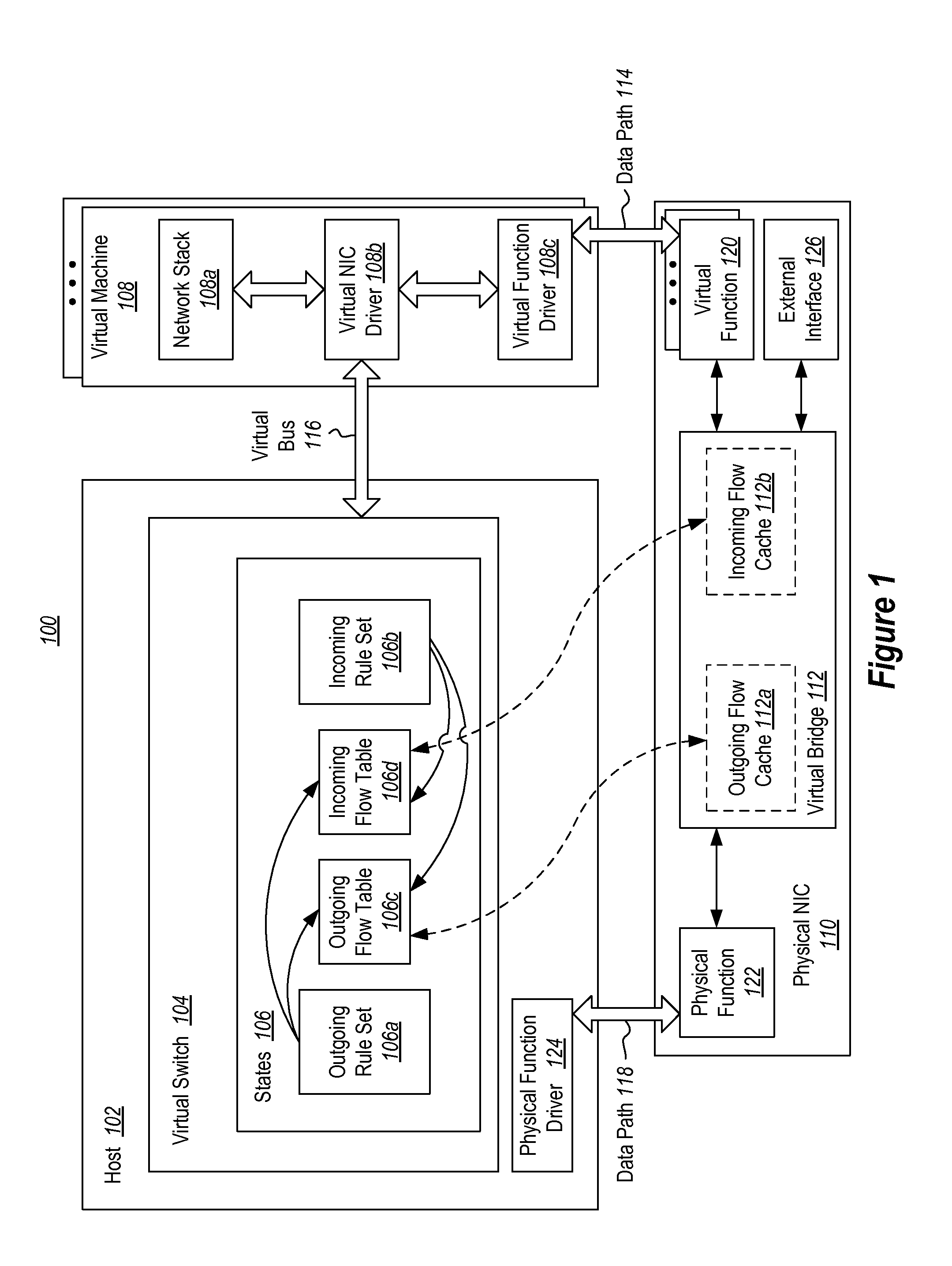
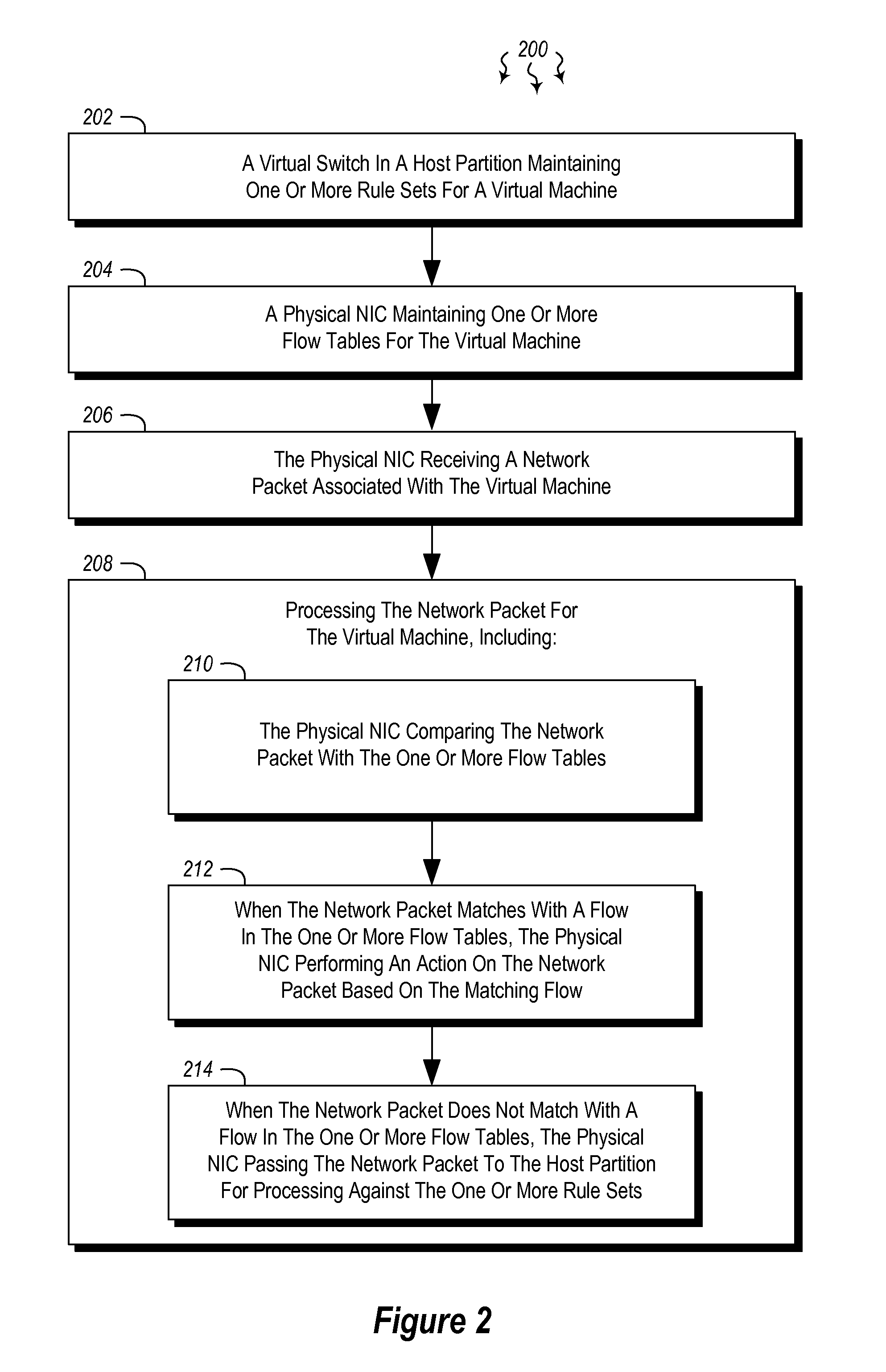
ActiveUS20130254766A1Improve network performanceTransmissionSoftware simulation/interpretation/emulationComputer hardwareData virtualization
The present invention extends to methods, systems, and computer program products for offloading packet processing for networking device virtualization. A host maintains rule set(s) for a virtual machine, and a physical network interface card (NIC) maintains flow table(s) for the virtual machine. The physical NIC receives and processes a network packet associated with the virtual machine. Processing the network packet includes the physical NIC comparing the network packet with the flow table(s) at the physical NIC. When the network packet matches with a flow in the flow table(s) at the physical NIC, the physical NIC performs an action on the network packet based on the matching flow. Alternatively, when the network packet does not match with a flow in the flow table(s) at the physical NIC, the physical NIC passes the network packet to the host partition for processing against the rule set(s).
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for the virtualization of resources using a virtualization broker and context information
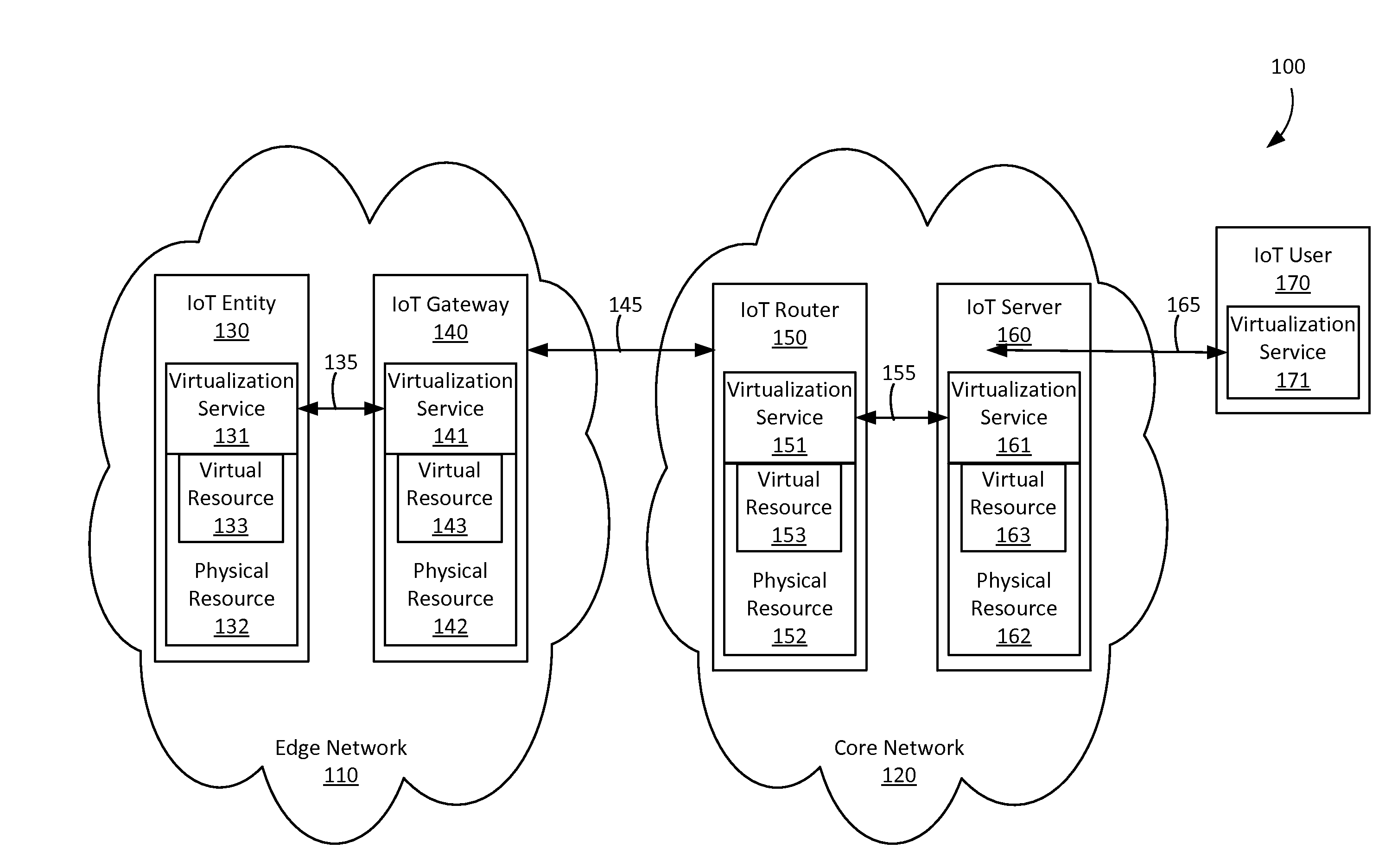
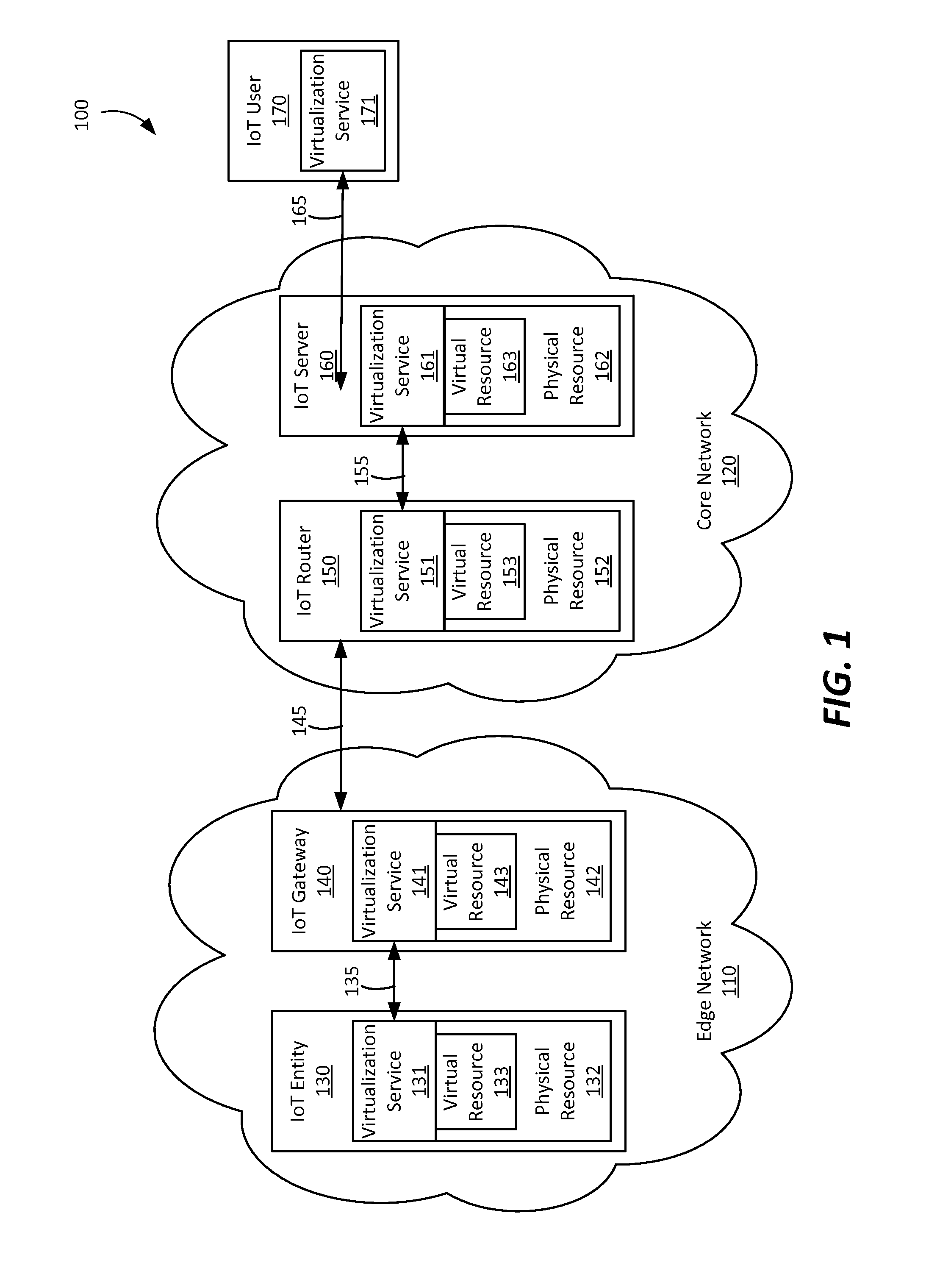
InactiveUS20160085594A1Well formedResource allocationDigital computer detailsThe InternetData virtualization
A method and entities for virtualizing resources by receiving a first virtualization request from a first entity at a virtualization broker in a network of connected entities, wherein the first virtualization request comprises context information associated with the first entity, transmitting a request from the virtualization broker to a virtualization manager for a virtualization server identifier, and receiving a virtualization server identifier from the virtualization manager. A second virtualization request may be transmitted to a virtualization server associated with the virtualization server identifier, and a first response may be received from the virtualization server comprising an indication that a resource has been virtualized. A second response comprising the indication from the virtualization broker may be transmitted to the first entity. The method is applied in the context of the Internet of Things (IoT).
Owner:CONVIDA WIRELESS LLC
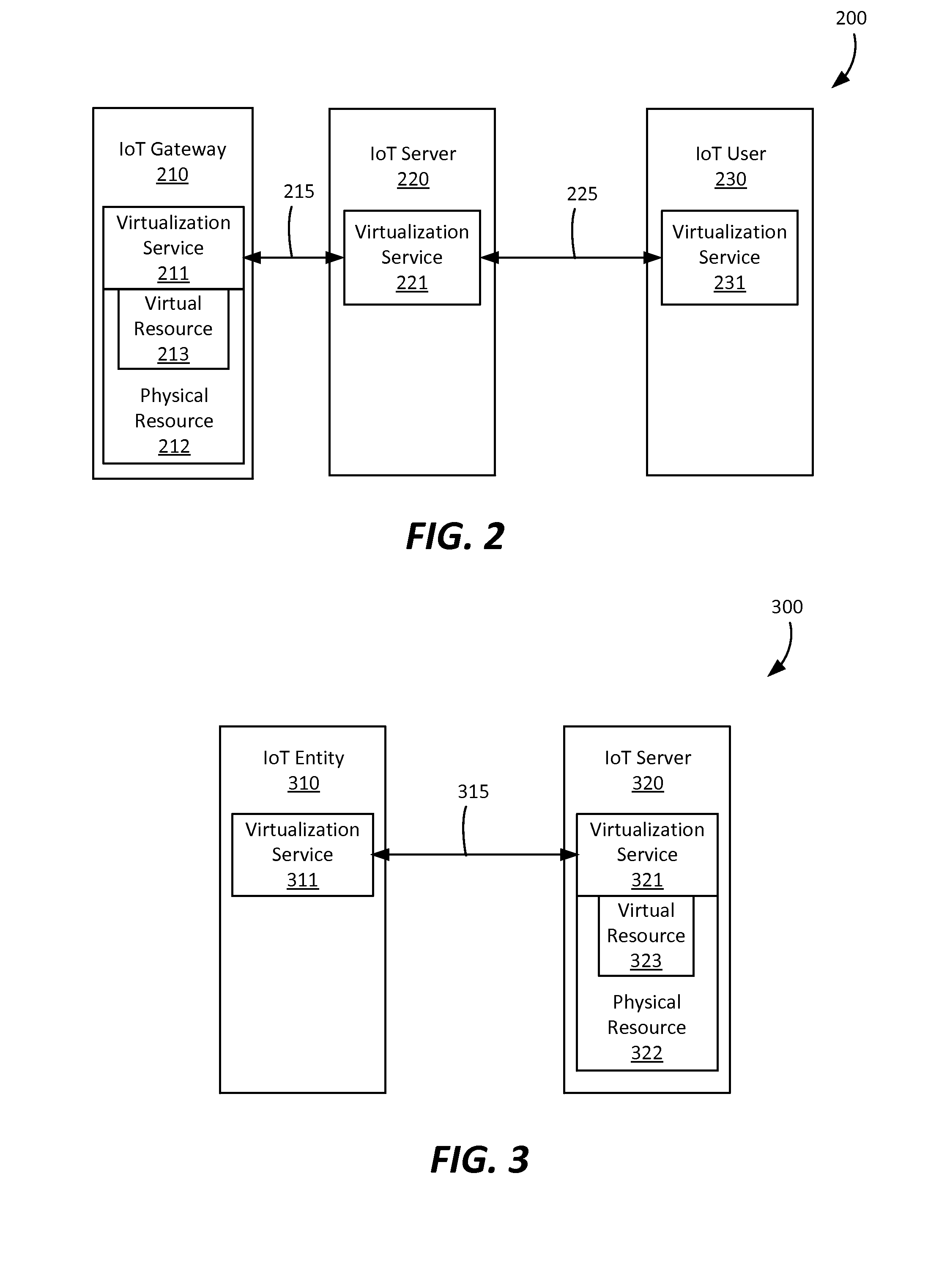
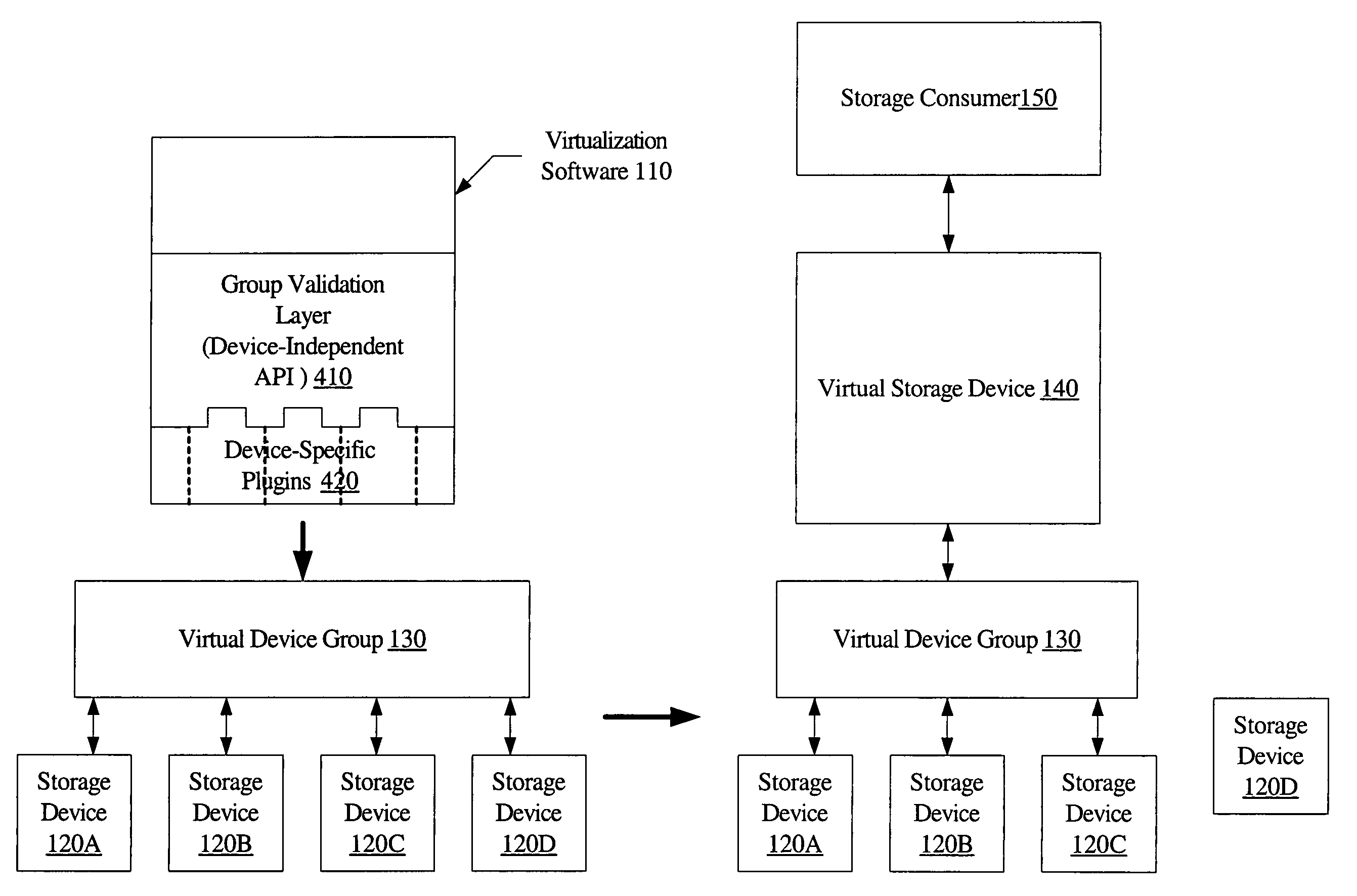
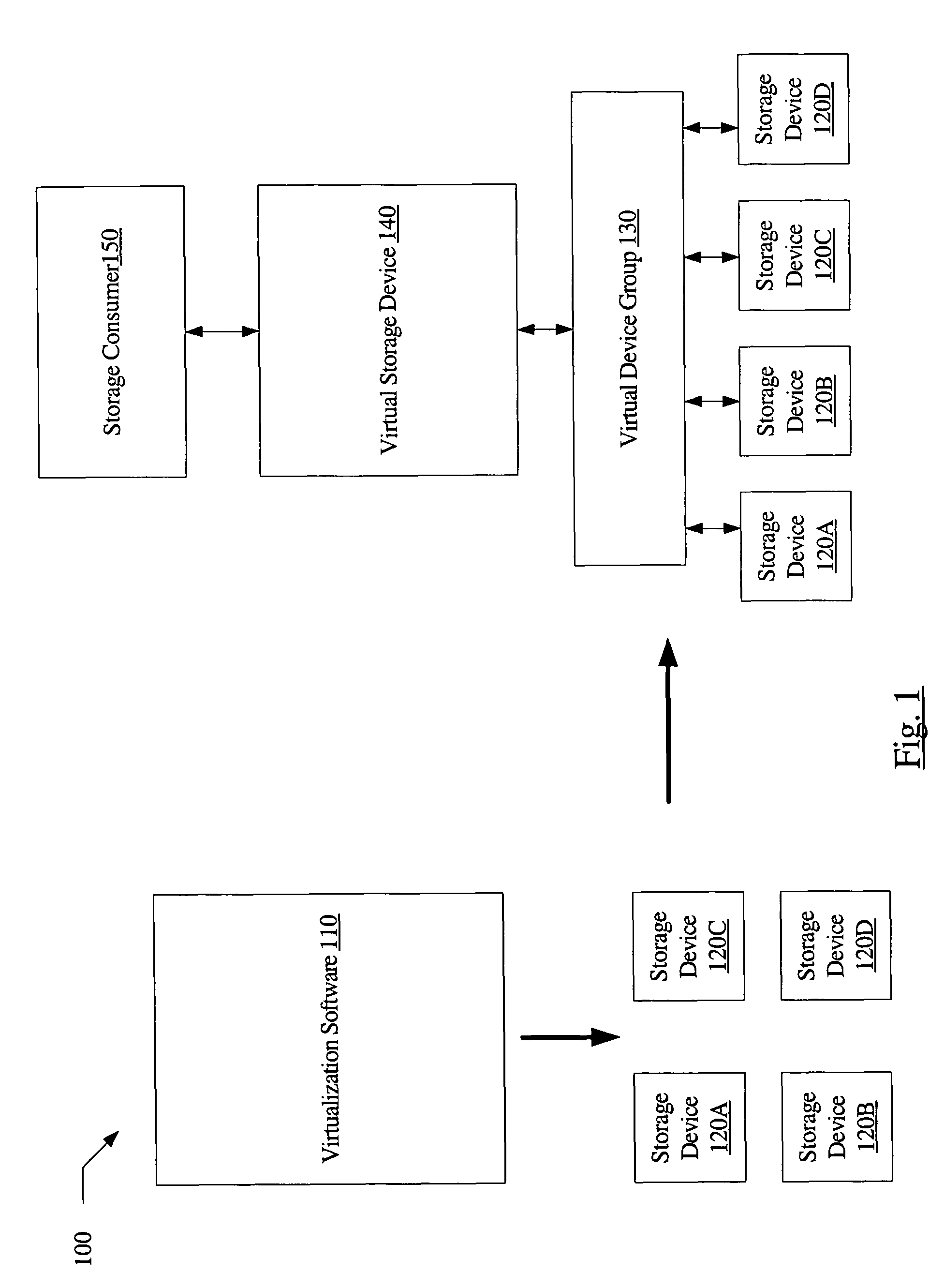
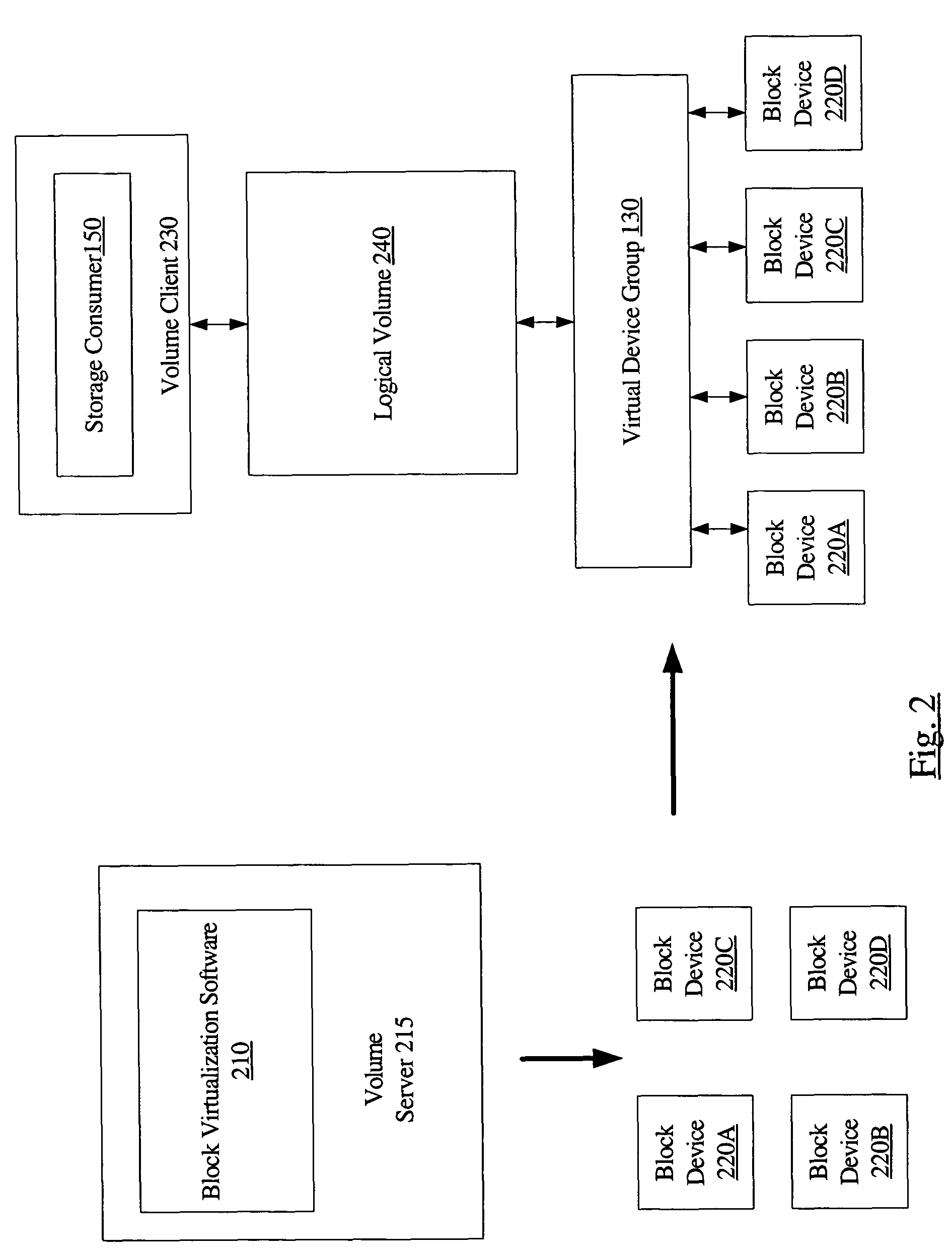
System and method for enforcing device grouping rules for storage virtualization
A system includes one or more storage devices and virtualization software configured to aggregate storage in the one or more storage devices into a virtual storage device accessible to a storage consumer. The virtualization software may include a group validation layer comprising a device-independent interface configured to validate a proposed group configuration operation on the one or more storage devices. The device-independent interface may be used to verify that the proposed configuration operation would, if completed, result in a configuration capable of supporting a desired virtualization functionality. The device-independent interface may allow an application to manage the one or more devices as a unit known as a virtual device group.
Owner:SYMANTEC OPERATING CORP
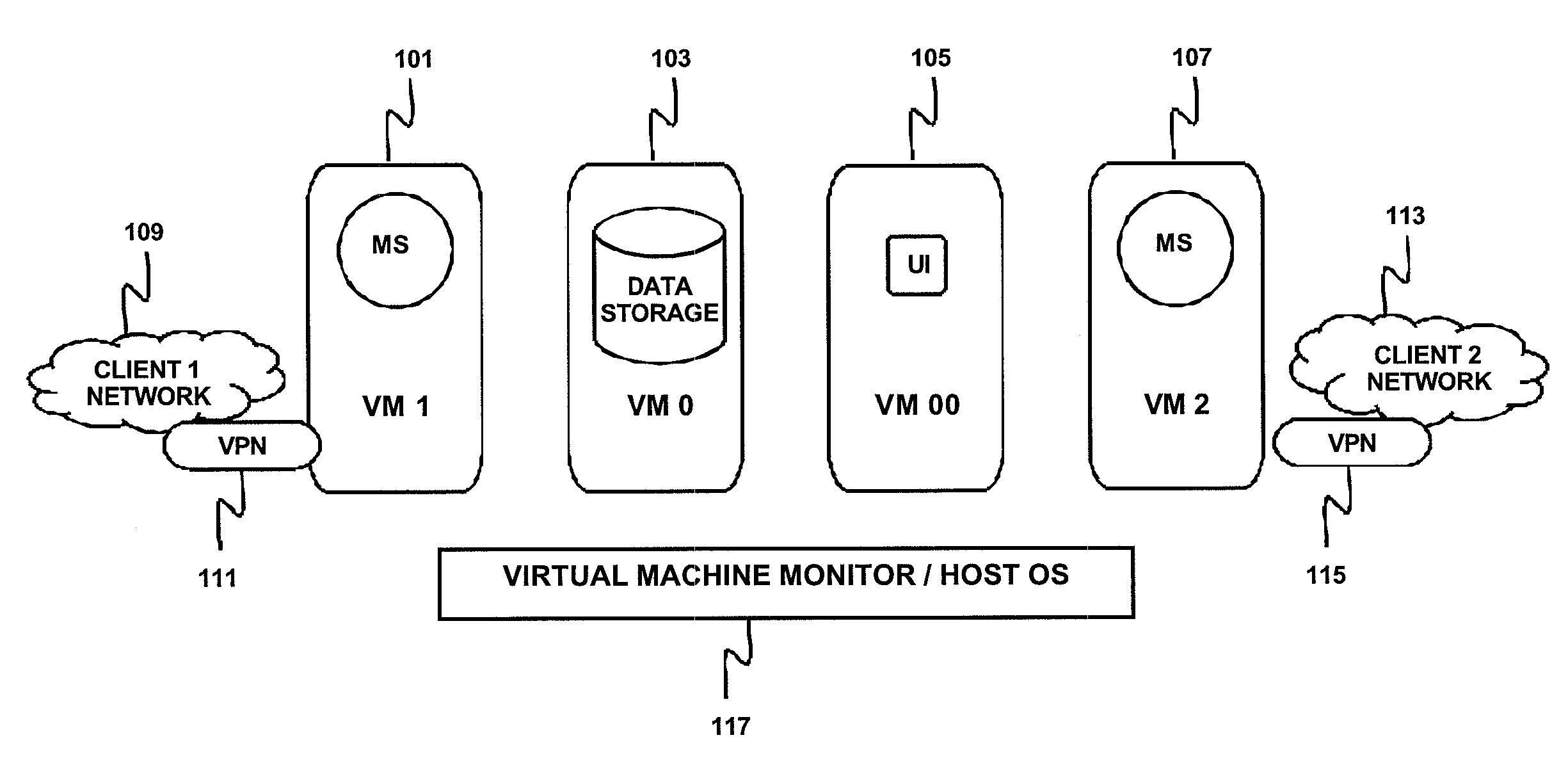
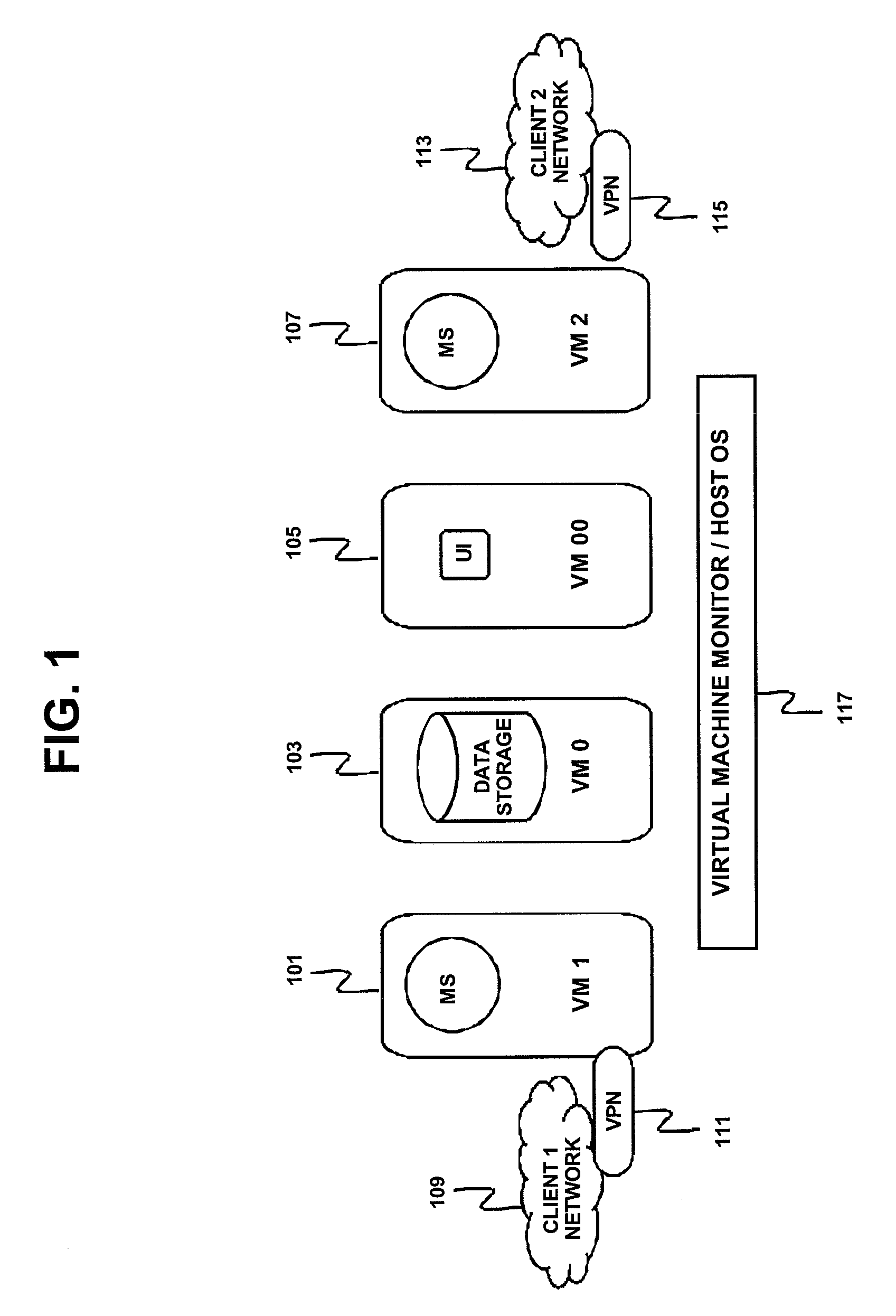
Method, Apparatus And Computer Program Product Implementing Multi-Tenancy For Network Monitoring Tools Using Virtualization Technology
InactiveUS20090113031A1Digital data processing detailsDigital computer detailsOperational systemManagement tool
Method, apparatus and computer program product manage a plurality of networks with a single tenant network management tool using virtualization and implement control plane virtualization of the single tenant management tool; data storage virtualization of a data storage apparatus and network address virtualization of an available address range. A virtual machine may be implemented for each network of the plurality of networks to contain an instance of the single tenant management tool. In one implementation, a proxy is used to implement data storage virtualization. In another implementation, separate data storage is maintained for each network and data storage virtualization is achieved by managing the network protocol stack virtualization. The network address virtualization may be implemented using machine-level virtualization or operating-system-level virtualization.
Owner:IBM CORP
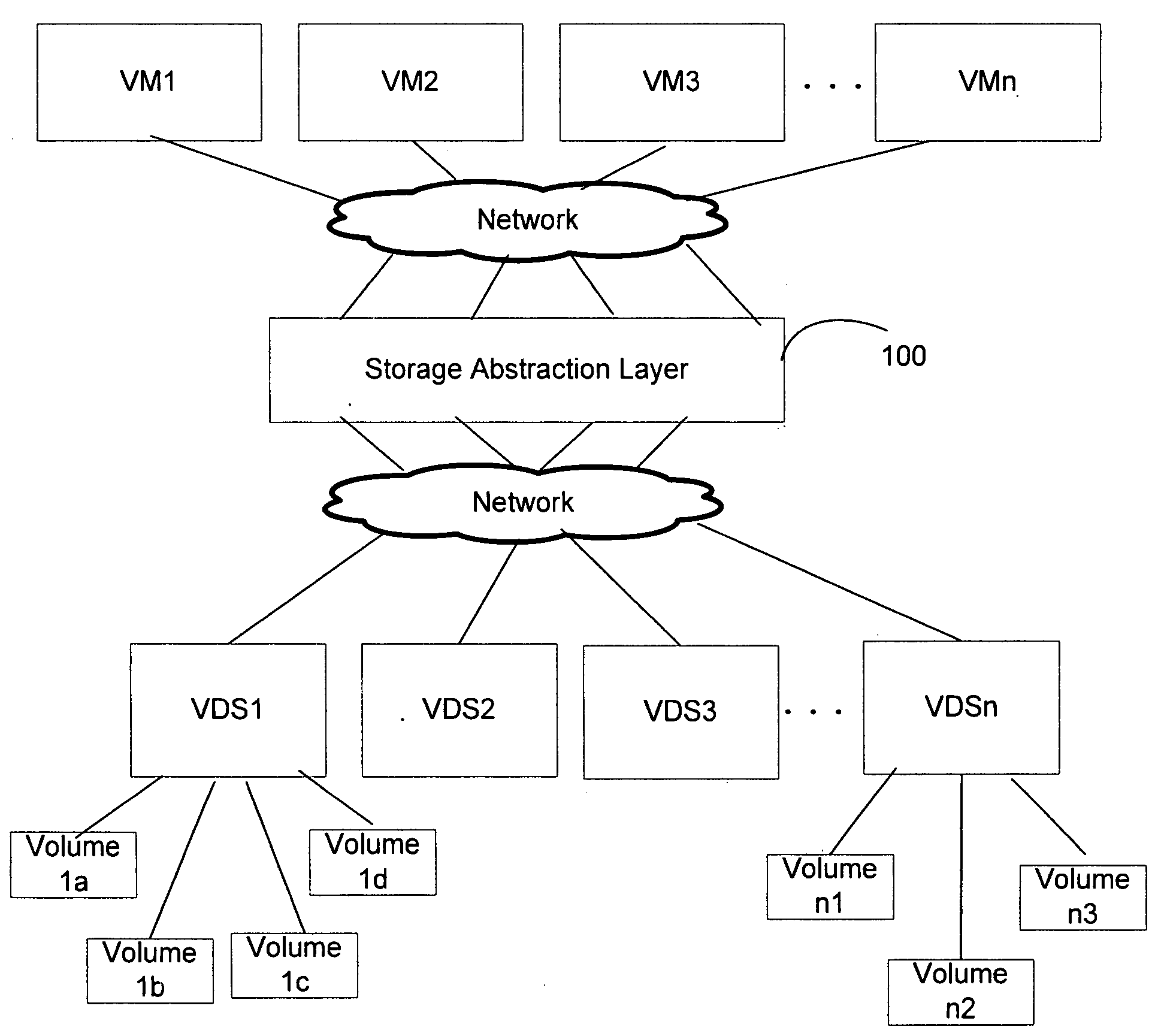
Storage Virtualization With Virtual Datastores
ActiveUS20100235832A1Digital computer detailsMultiprogramming arrangementsUnique identifierData virtualization
Computer implemented methods and systems for providing storage virtualization of physical storage include receiving a request for storage from a virtual machine during provisioning of the virtual machine. The request includes a capability and quota requirement for storage as required by the virtual machine. A virtual datastore that satisfies the capability and quota requirements of the request is identified. If not found, one or more volumes, that satisfy the storage requirements, are discovered or created. A virtual datastore is created and maps to one or more volumes which have unique volume identifiers. A unique virtual datastore identifier is generated for the virtual datastore. The virtual datastore identifier is distinct from the volume identifiers of the underlying volumes. The volumes are mapped to the virtual datastore while retaining the virtual datastore identifier for the virtual datastore. The virtual datastore identifier for the virtual datastore is not changed when modifications are made to the physical storage entities mapped to the virtual datastore.
Owner:VMWARE INC
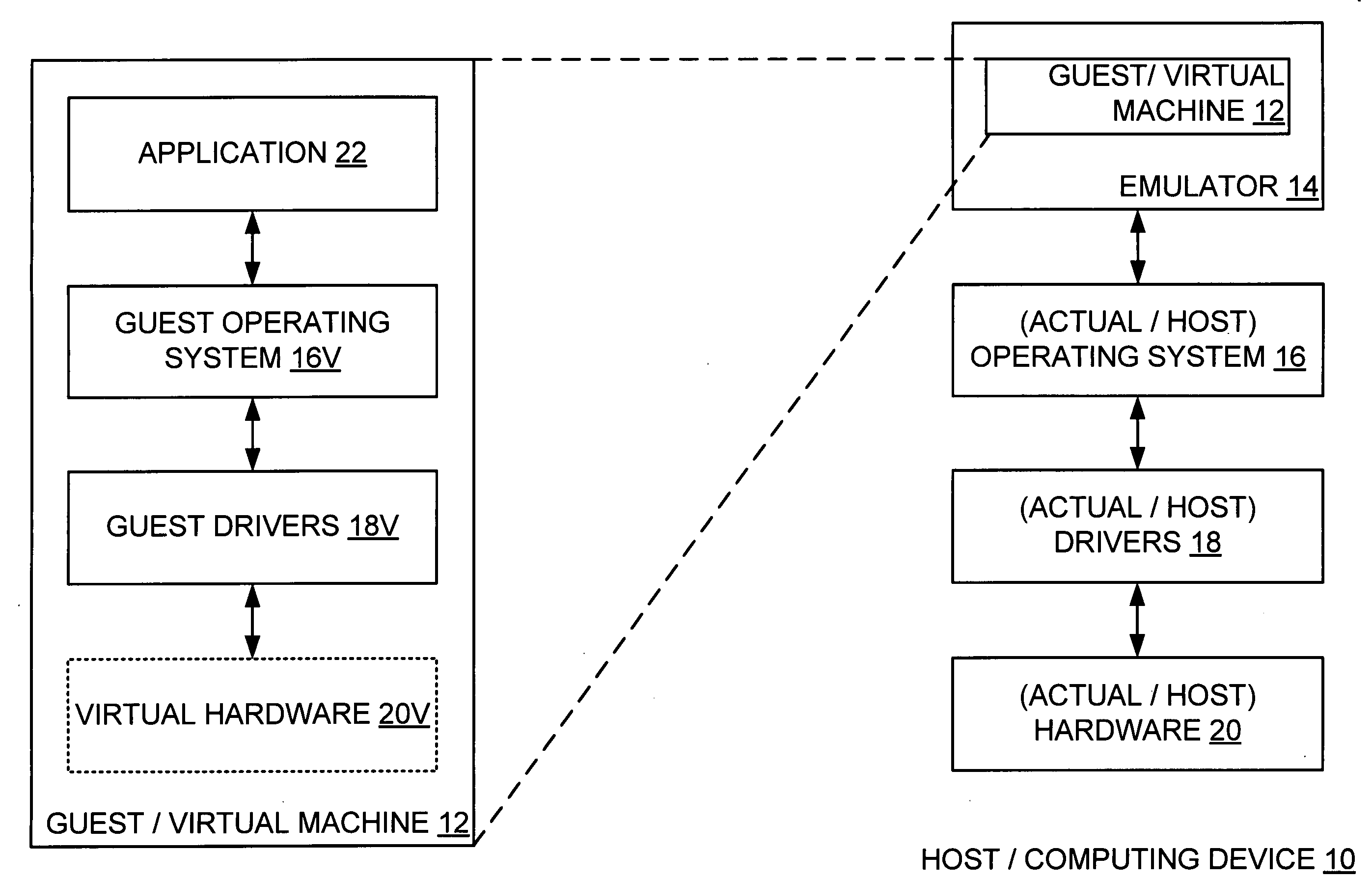
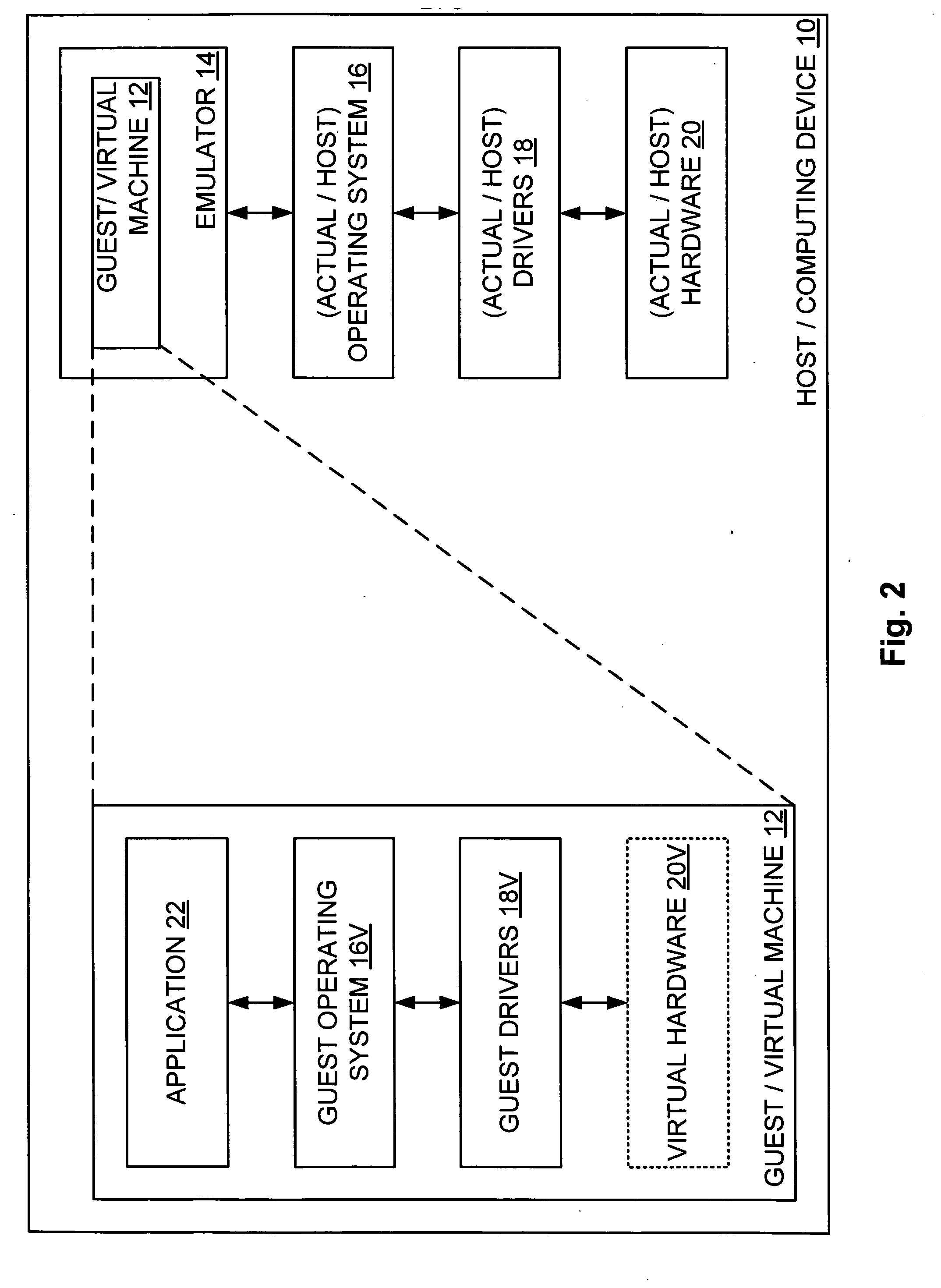
Partial virtualization on computing device
ActiveUS20070288228A1Satisfies needSoftware simulation/interpretation/emulationMemory systemsComputer hardwareOperational system
A computing device hosts a virtual machine executing a guest that issues guest hardware requests by way of any of a plurality of paths. Such paths include a path to non-existent virtual hardware, where an emulator intercepts and processes such guest hardware request with a corresponding actual hardware command; a path to an instantiated operating system, where the instantiated operating system processes each such guest hardware request with a corresponding actual hardware request; and a path to device hardware, where the device hardware directly processes each such guest hardware request.
Owner:MICROSOFT TECH LICENSING LLC
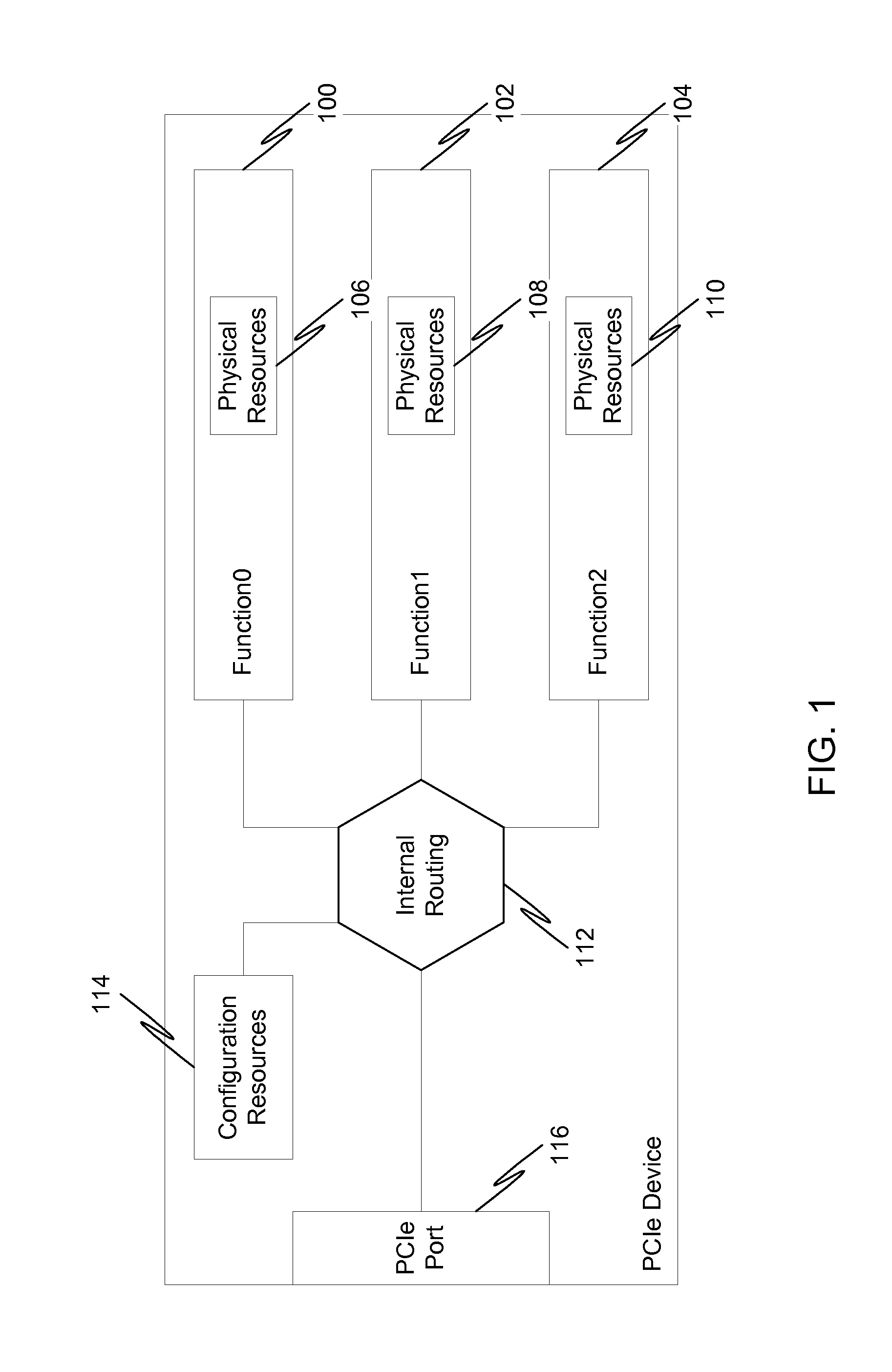
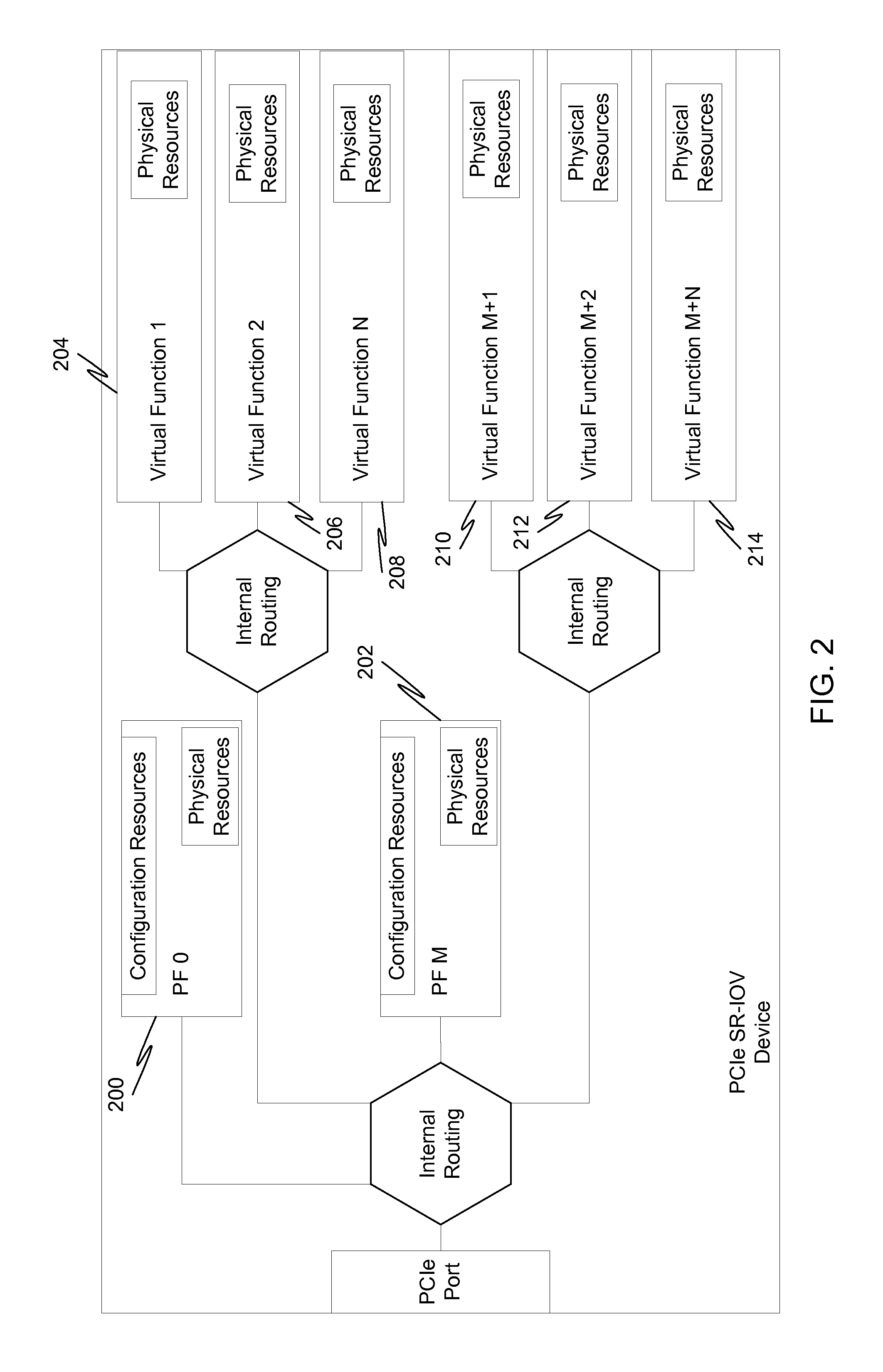
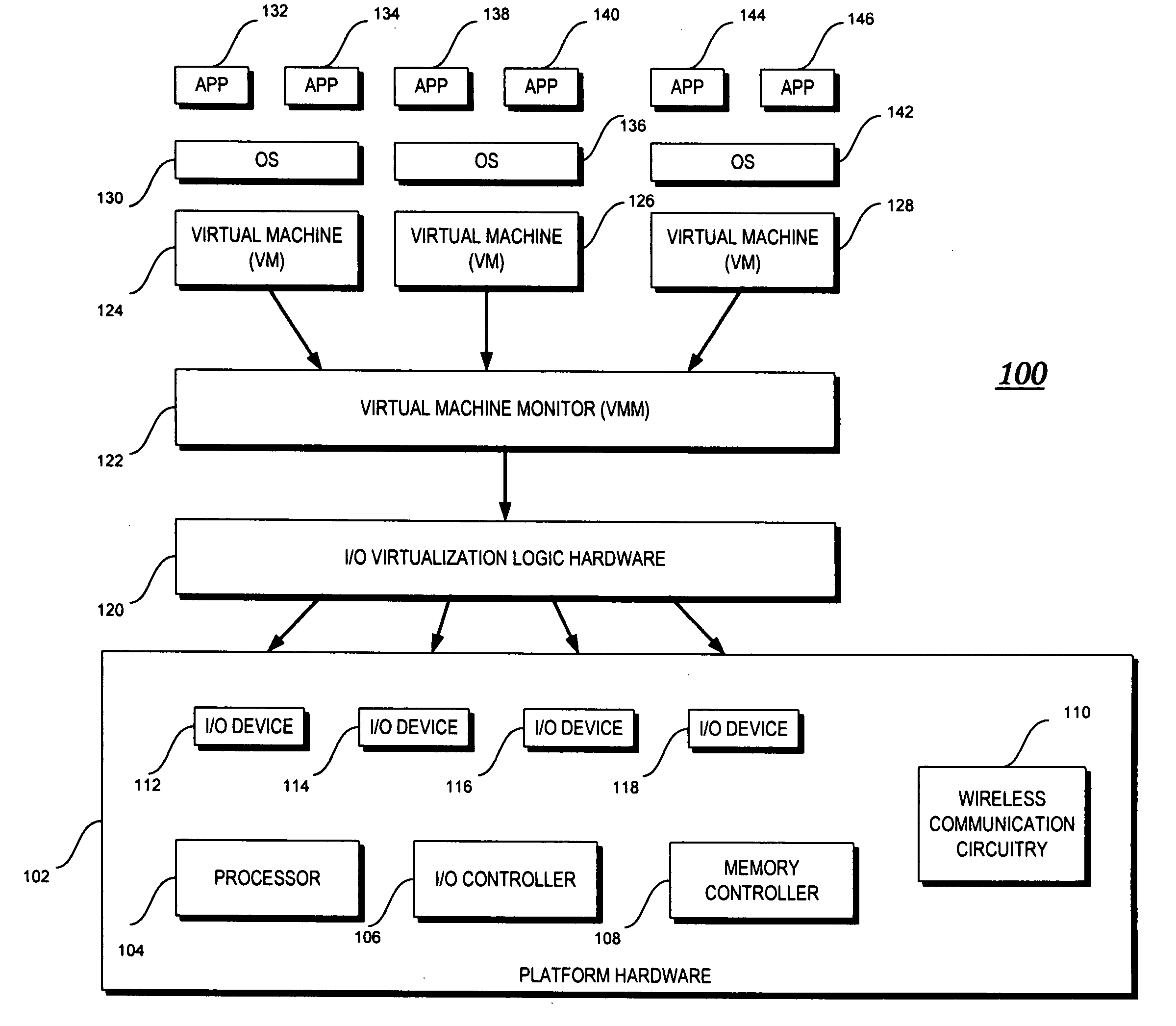
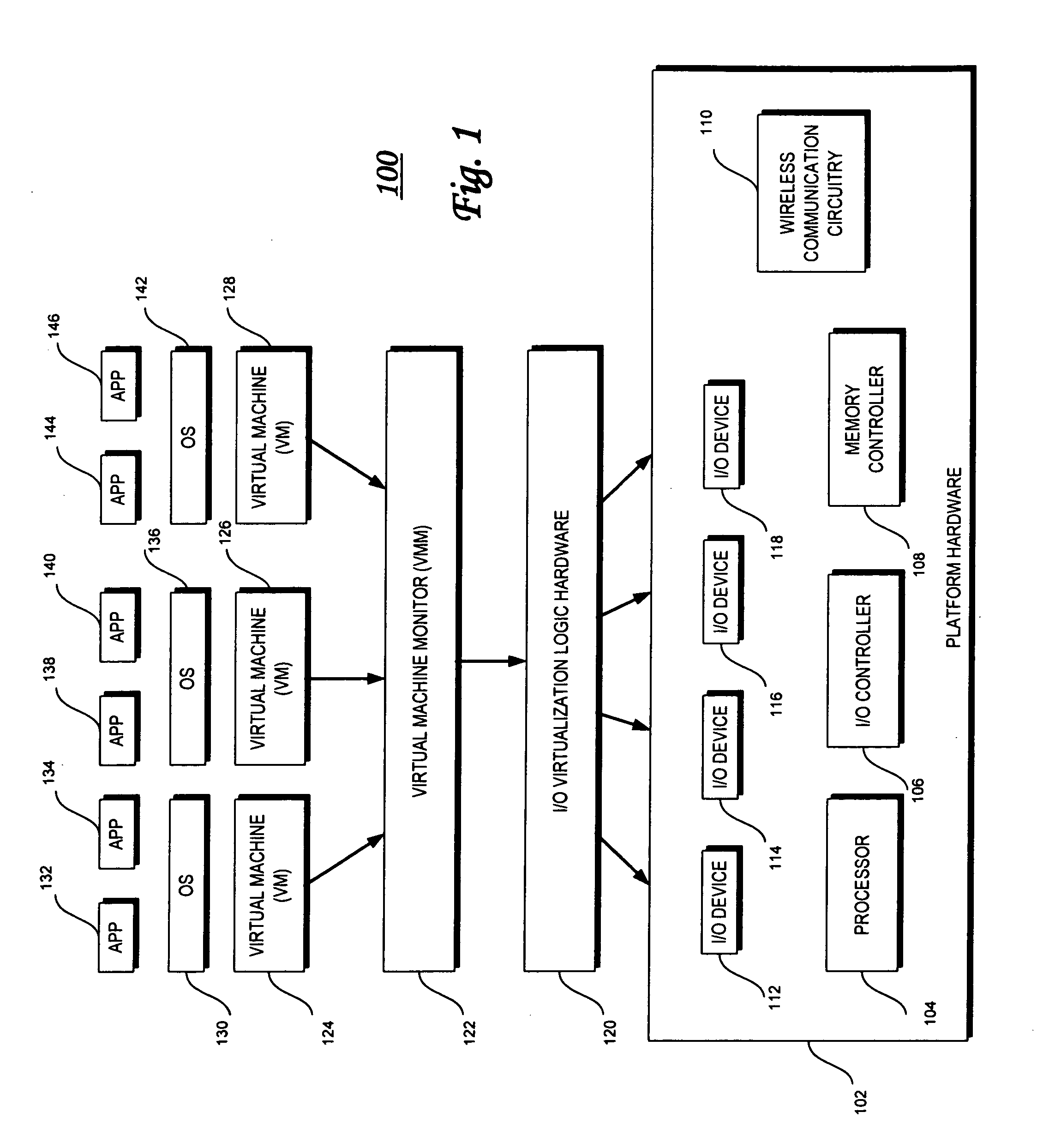
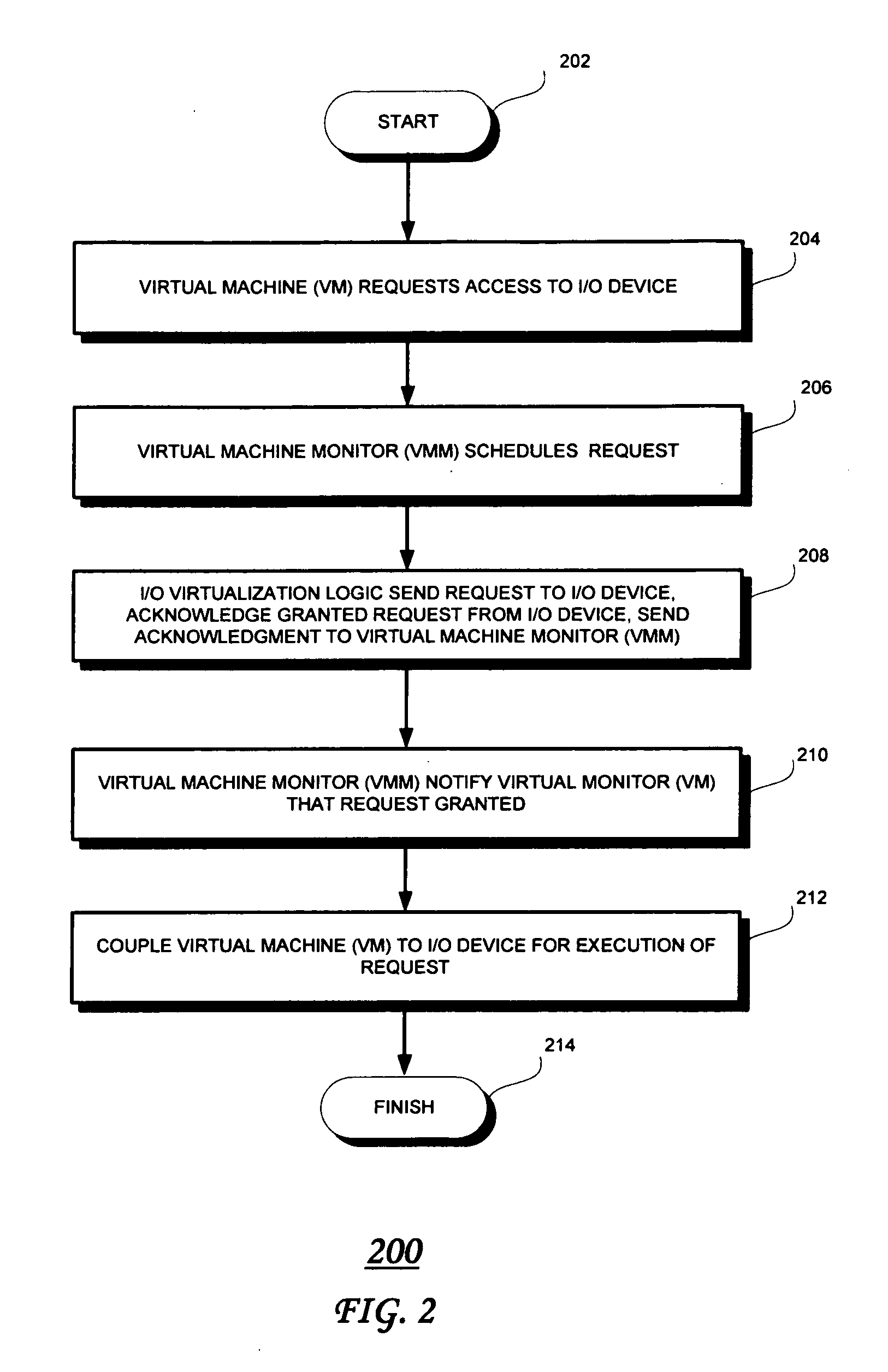
Input/output (I/O) device virtualization using hardware
InactiveUS20080126614A1Program controlInput/output processes for data processingOperational systemComputerized system
According to embodiments of the present invention a computer system that is capable of sharing physical devices among several virtual machines (VM) includes hardware assisted logic to allow requests from guest operating systems (guest OS) to circumvent a virtual machine monitor ((VMM) and be processed by the hardware assisted logic.
Owner:INTEL CORP
Apparatus and method for storage processing through scalable port processors
InactiveUS7237045B2Achieve scaleProvide flexibilityMultiplex system selection arrangementsInput/output to record carriersWire speedMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
Methods and apparatus for storage virtualization
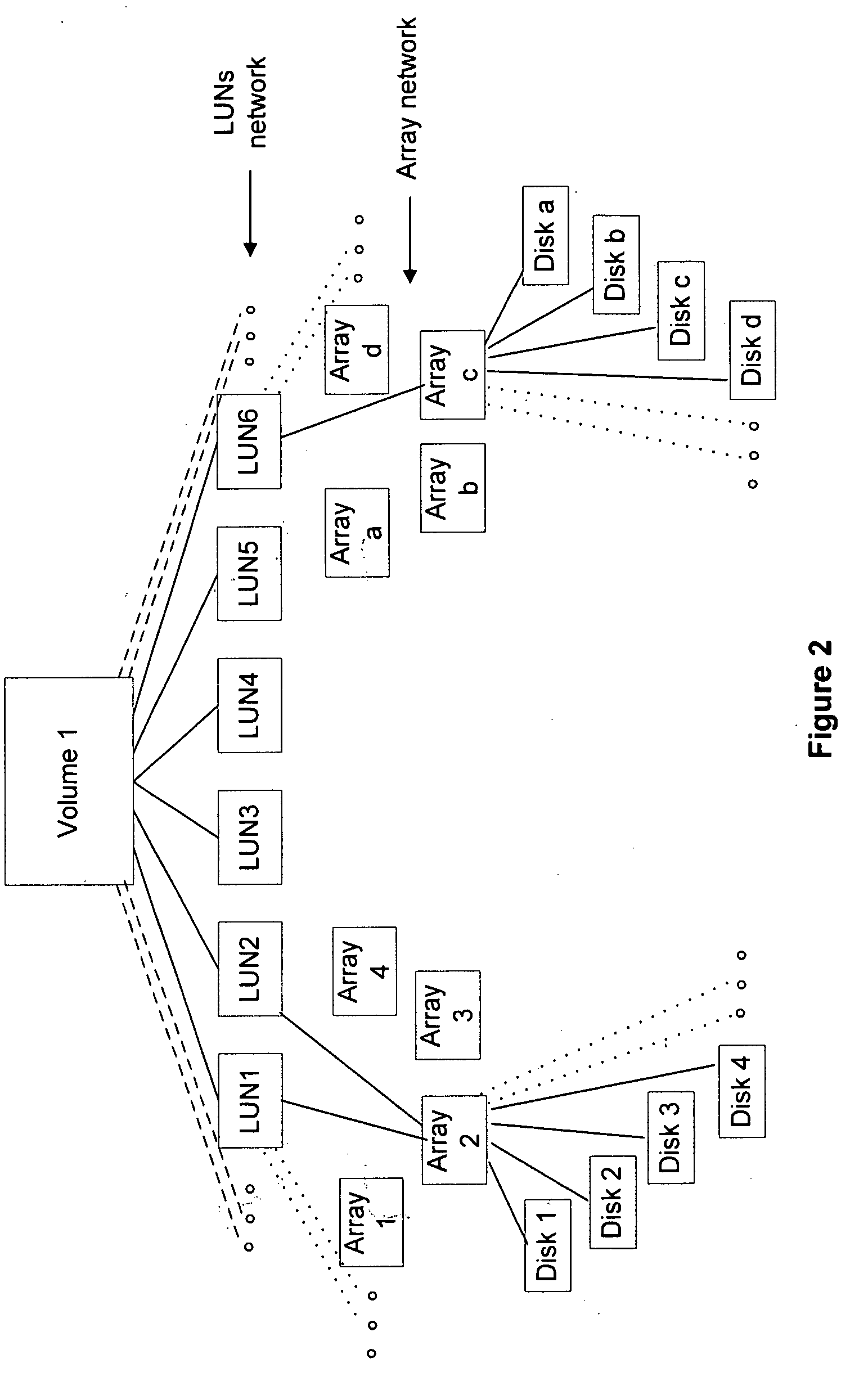
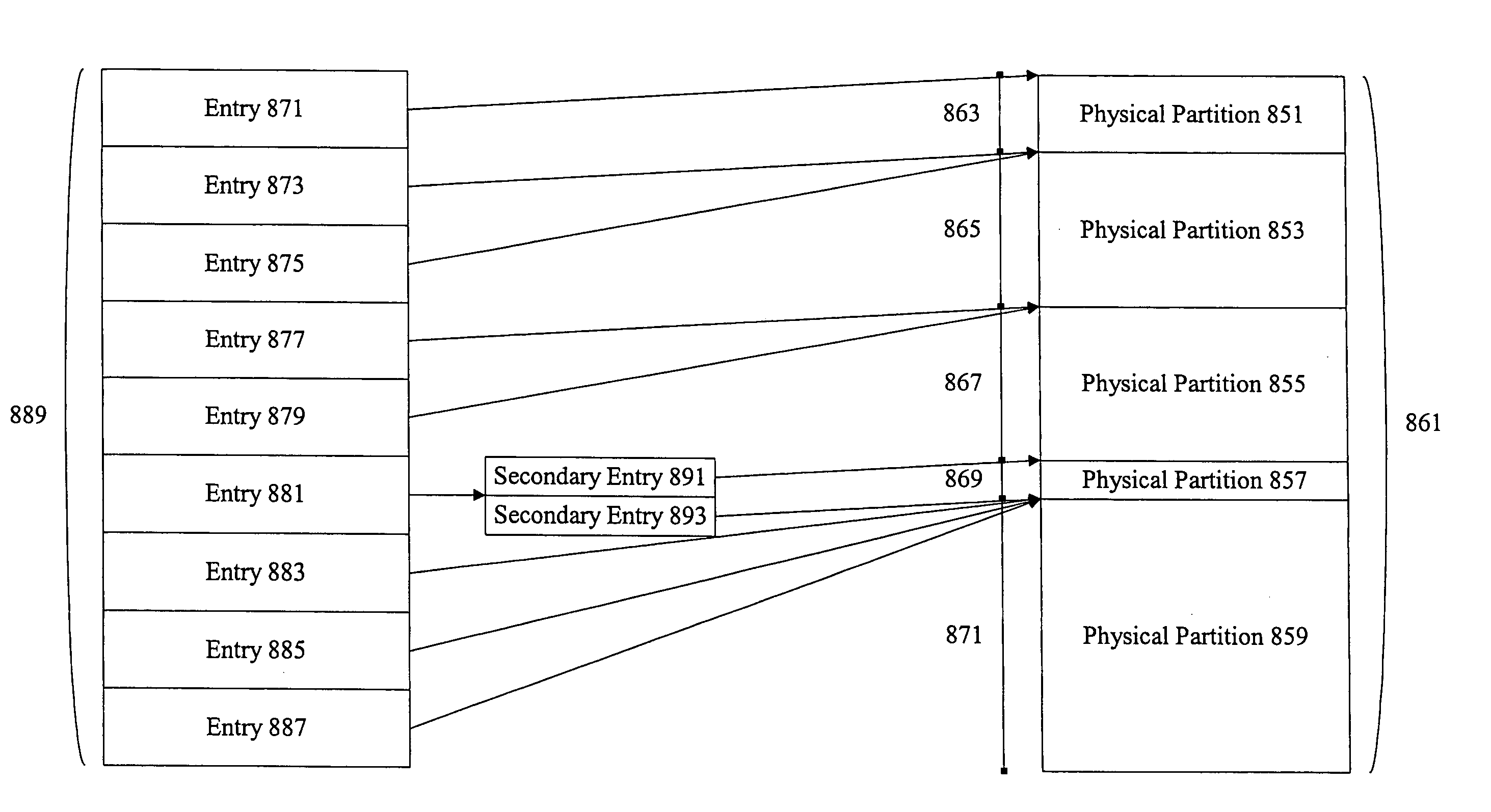
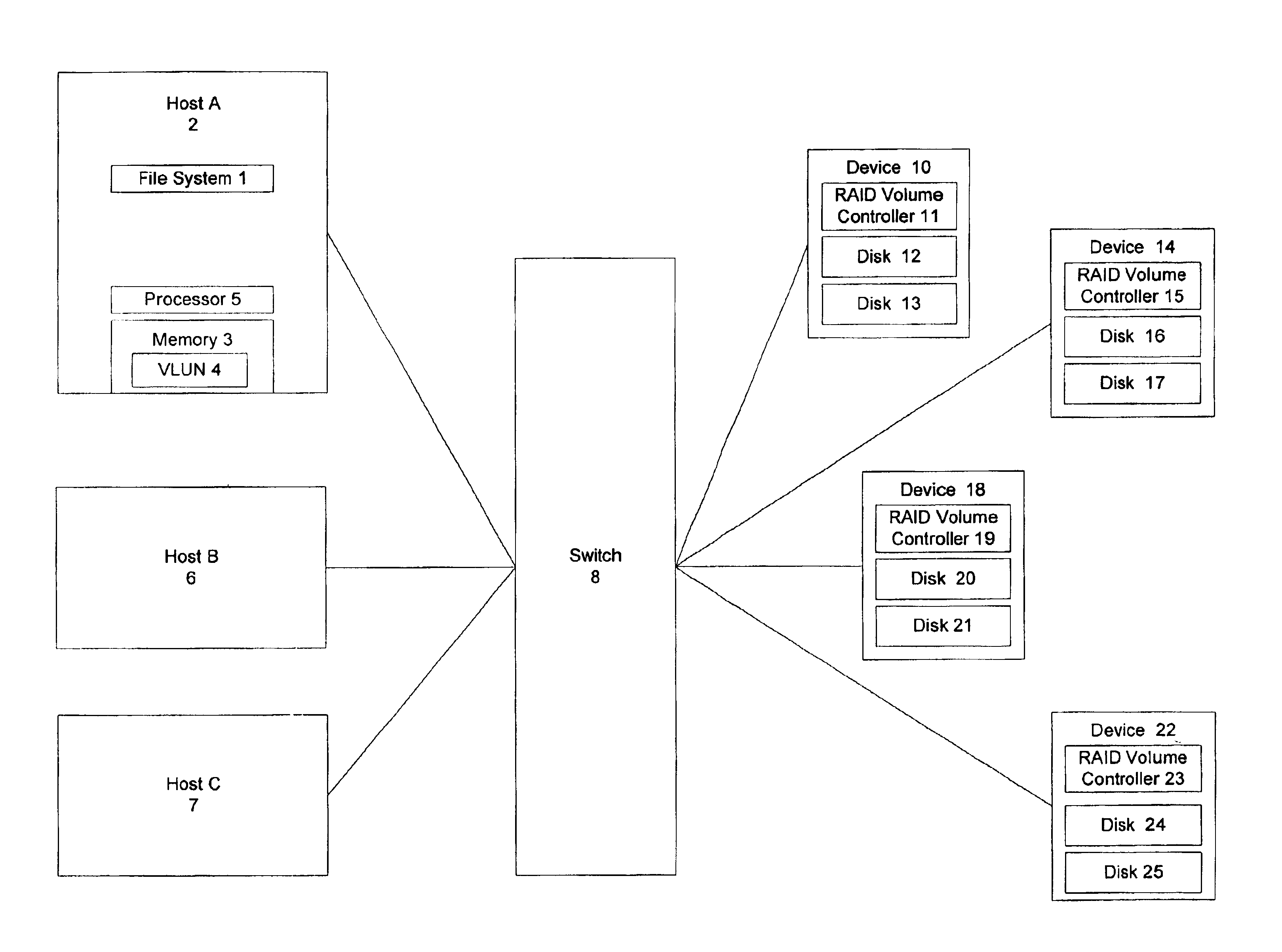
InactiveUS6948044B1Improve data access efficiencyEfficient mappingInput/output to record carriersError preventionStorage area networkData access
Methods and apparatus are provided improving data access efficiency in a storage area network. Mechanisms are provided to allow a virtual disk address to be efficiently mapped to a particular physical partition in a virtual disk while recognizing the mirroring, striping, and concatenation characteristics associated with the virtual disk. A variety of indices are used to allow direct access of a physical partition upon identification of a virtual disk address.
Owner:CISCO TECH INC
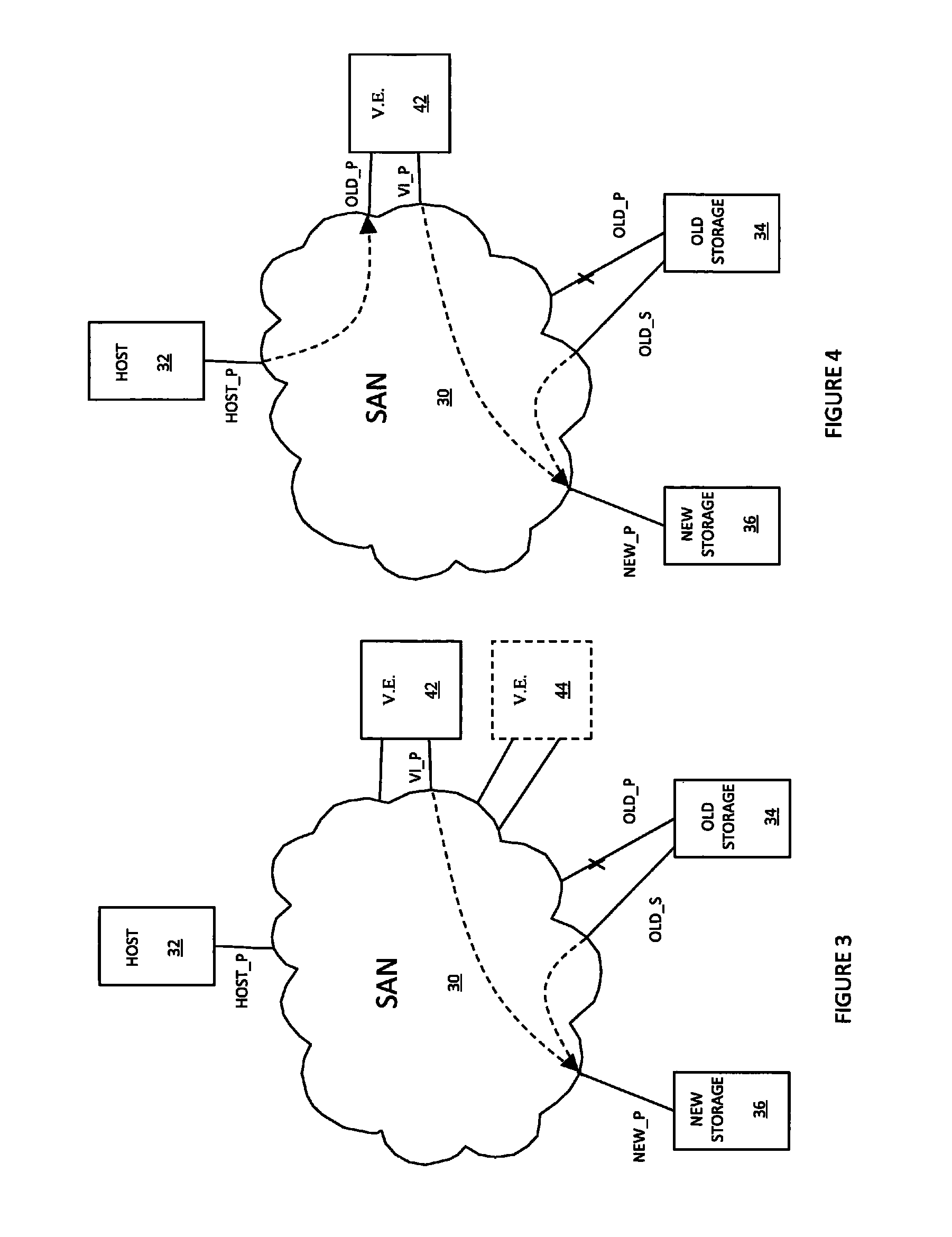
Non-disruptive data mobility using virtual storage area networks with split-path virtualization
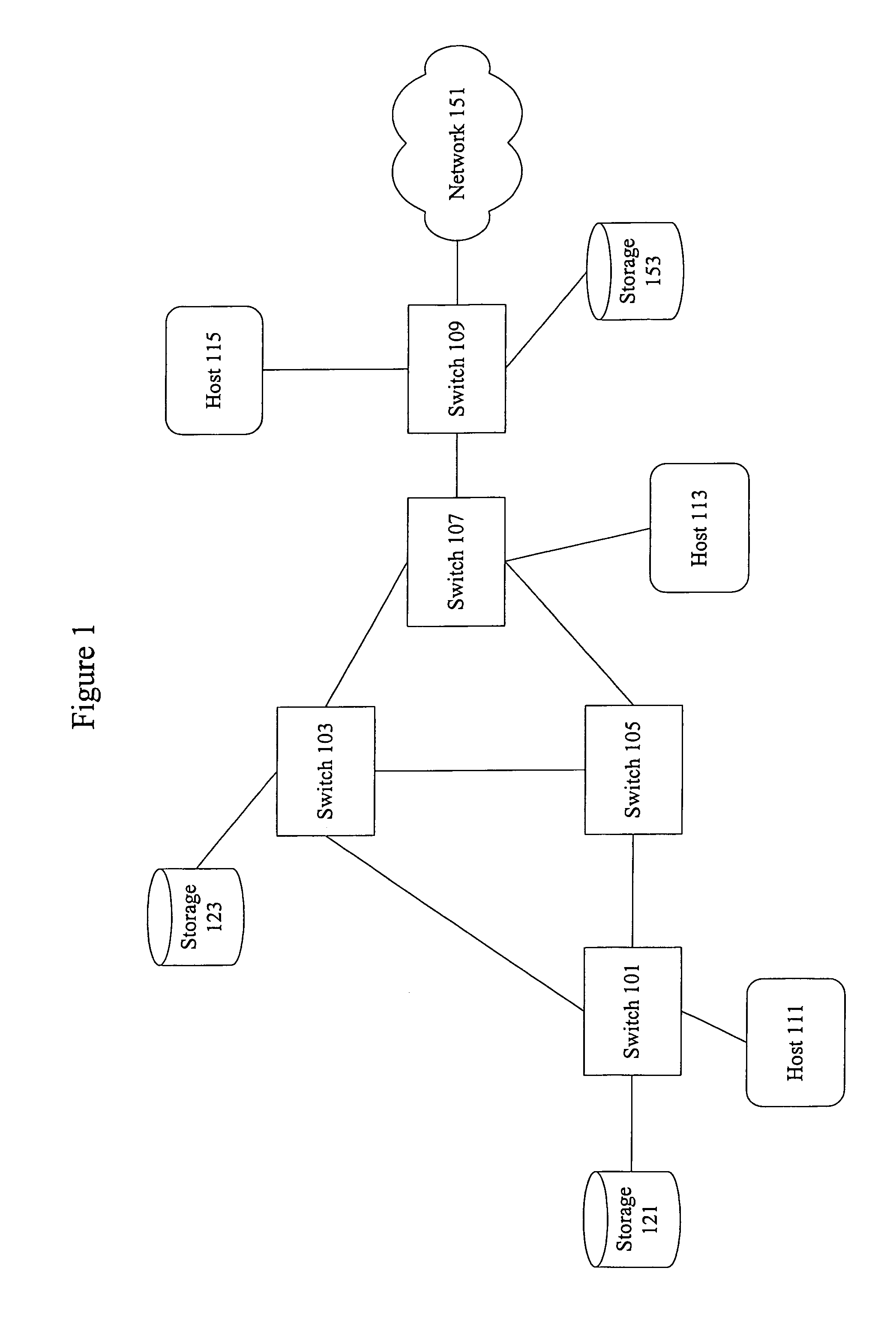
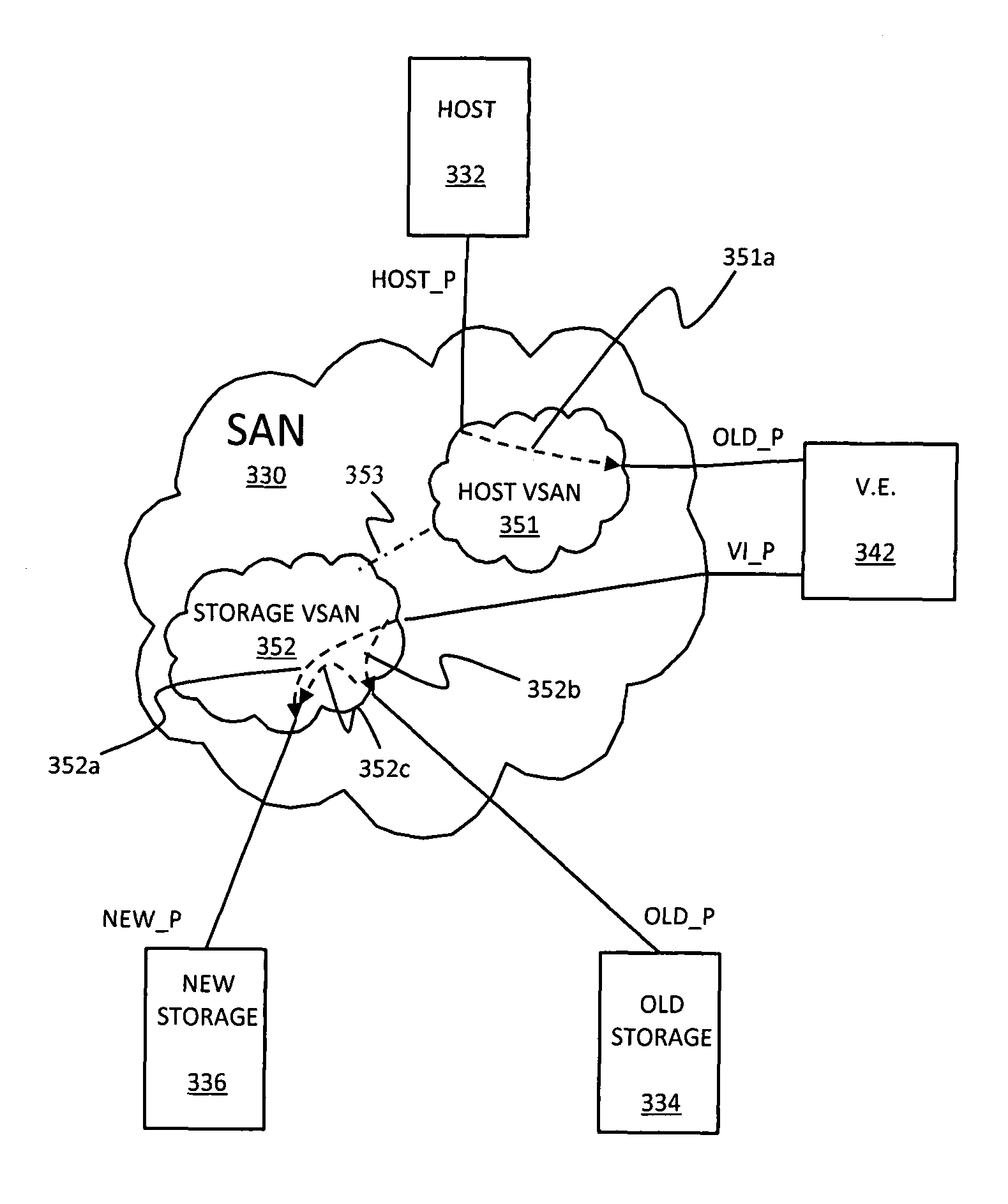
ActiveUS8028062B1Computer security arrangementsMultiple digital computer combinationsArea networkName server
A system creates a storage area network (SAN) centric storage virtualization layer in front of storage devices. The system allows data mobility and migration without disruption to the one or more host servers attached to the SAN. Specifically, the host servers are not disrupted when switching I / Os between physical and virtual storage, for example, by taking advantage of WWPN spoofing and Fibre Channel VSAN technology. The use of VSANs effectively allow multiple virtual directors and / or switches to be created within a physical director and / or switches, each with their own separate name server, thereby providing complete isolation from one another. The host-storage pathing information is unchanged as the original physical storage port's WWPNs are spoofed by the virtual storage port. The result is two identical WWPNs within the SAN which is normally disallowed; however, by separating the physical port WWPN into one VSAN and the virtual port WWPN into another, the restriction may be circumvented.
Owner:EMC IP HLDG CO LLC
Apparatus and method for internet protocol data processing in a storage processing device
InactiveUS20060013222A1Achieve scaleProvide flexibilityError detection/correctionData switching by path configurationInternet trafficMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:BROCADE COMMUNICATIONS SYSTEMS
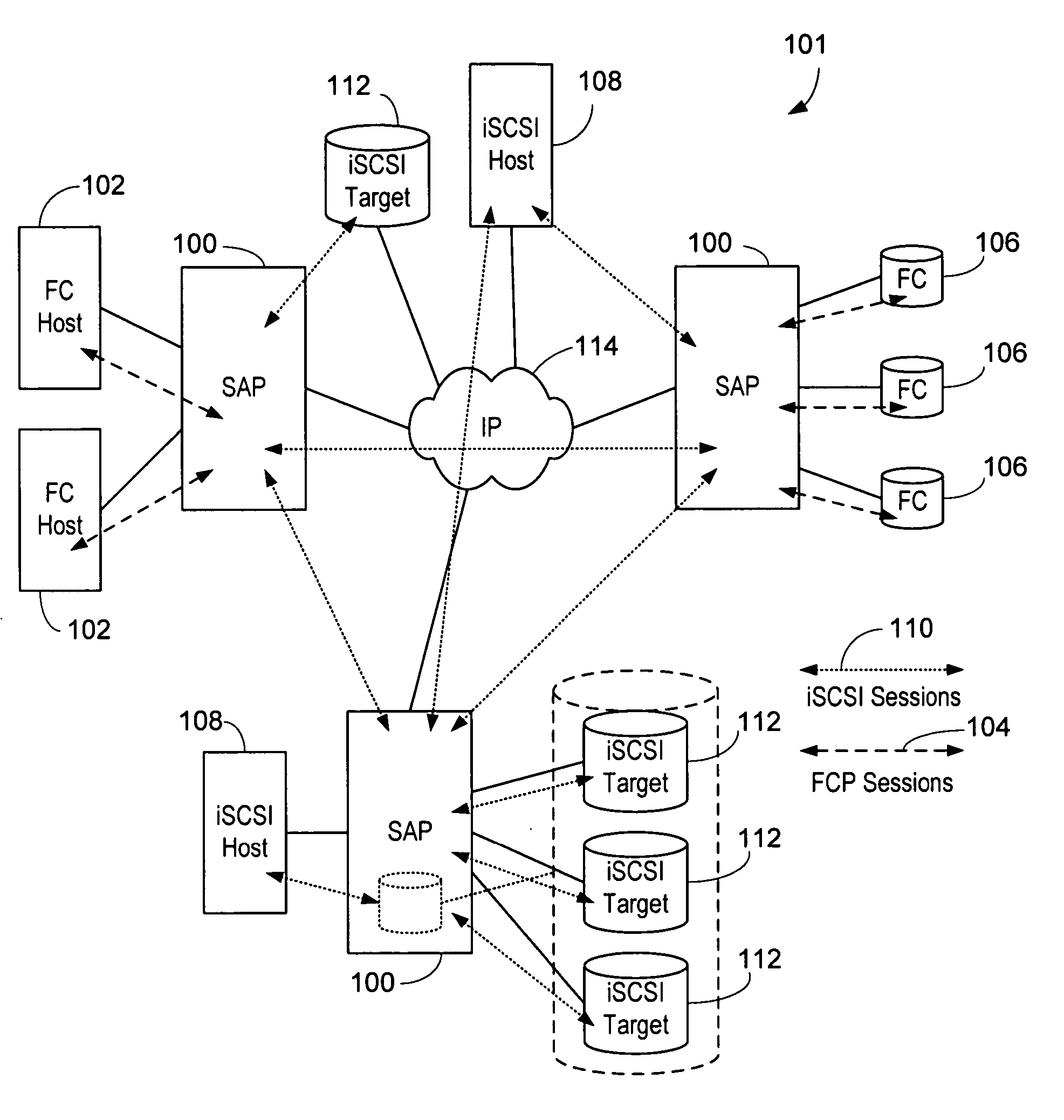
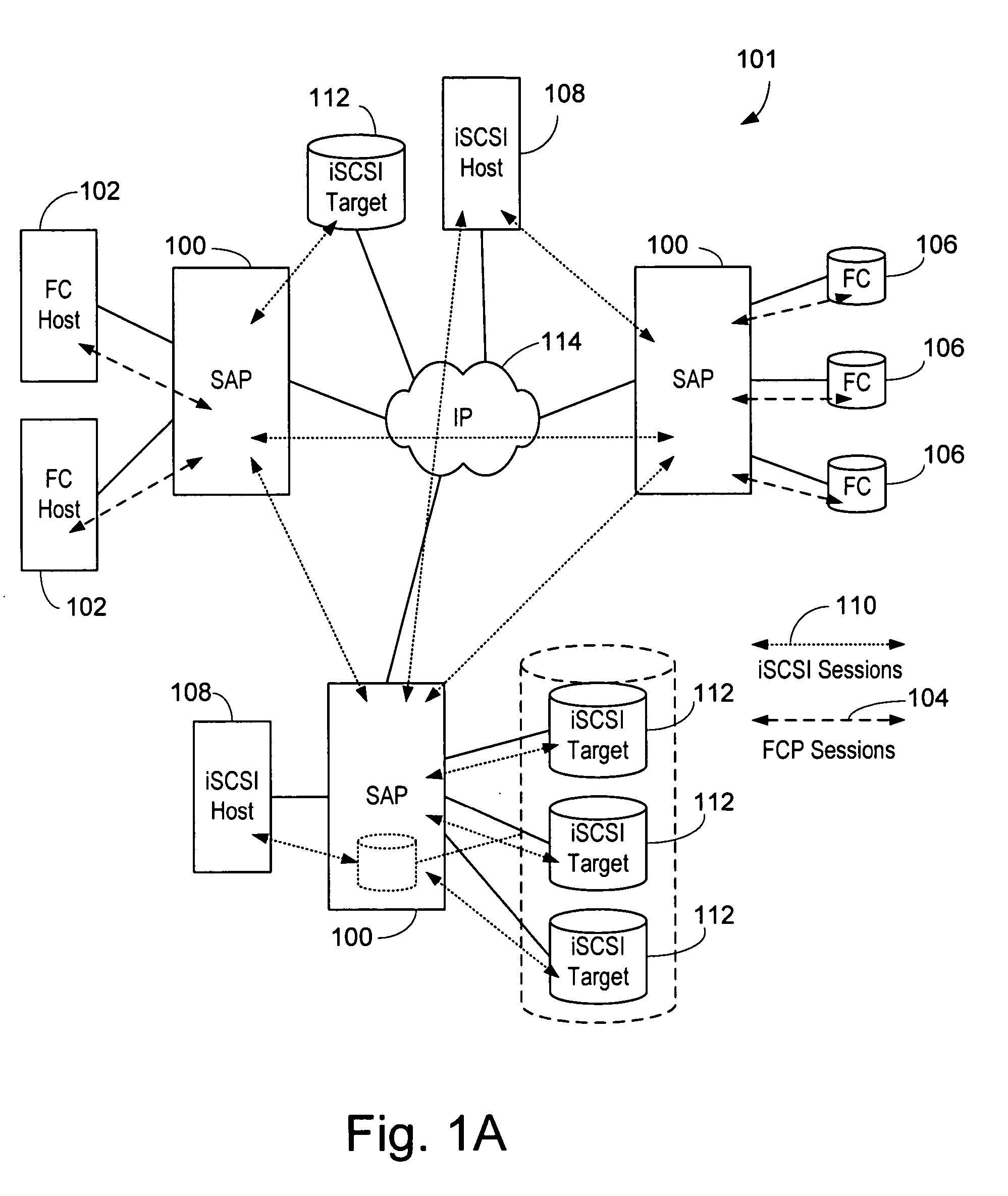
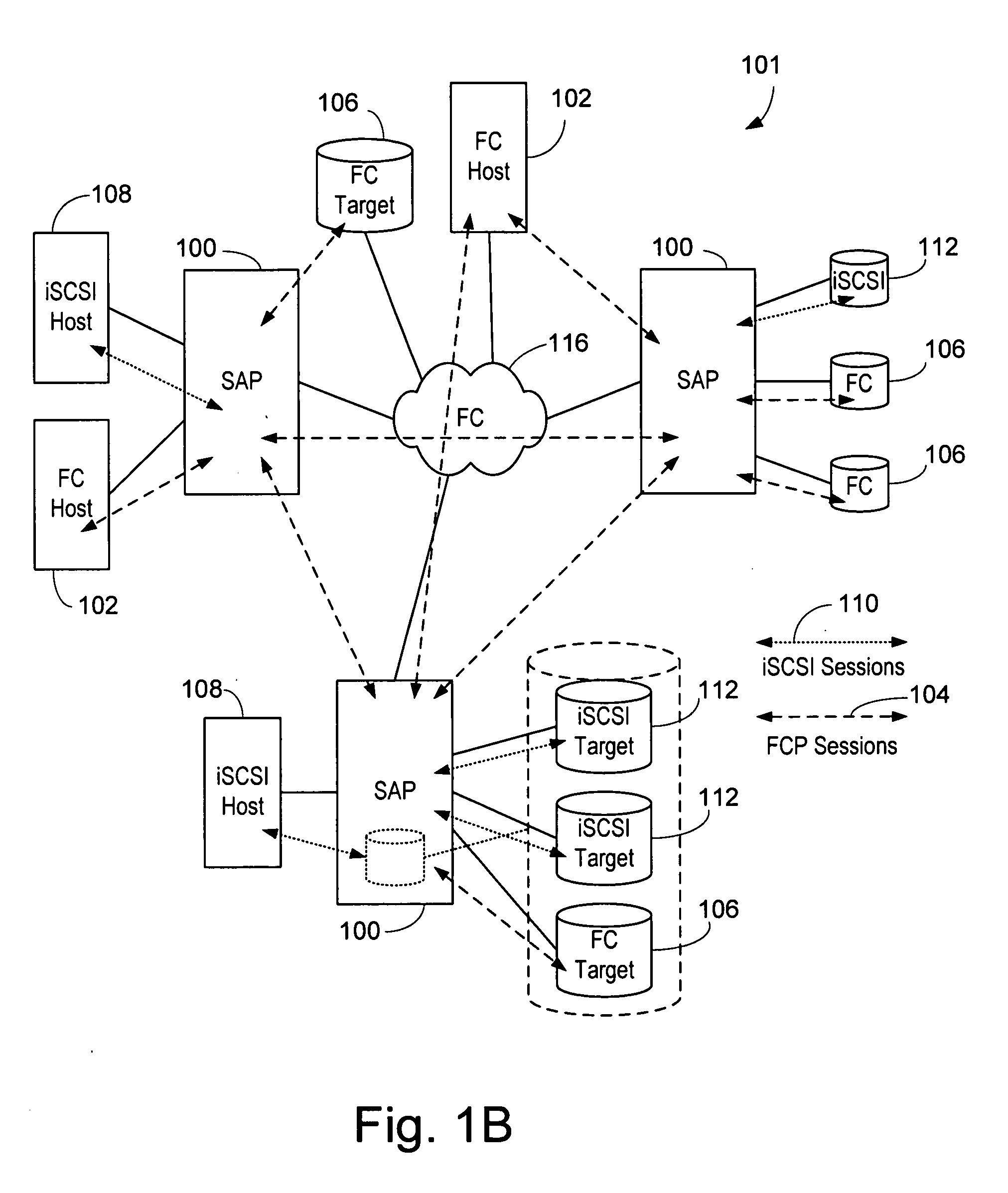
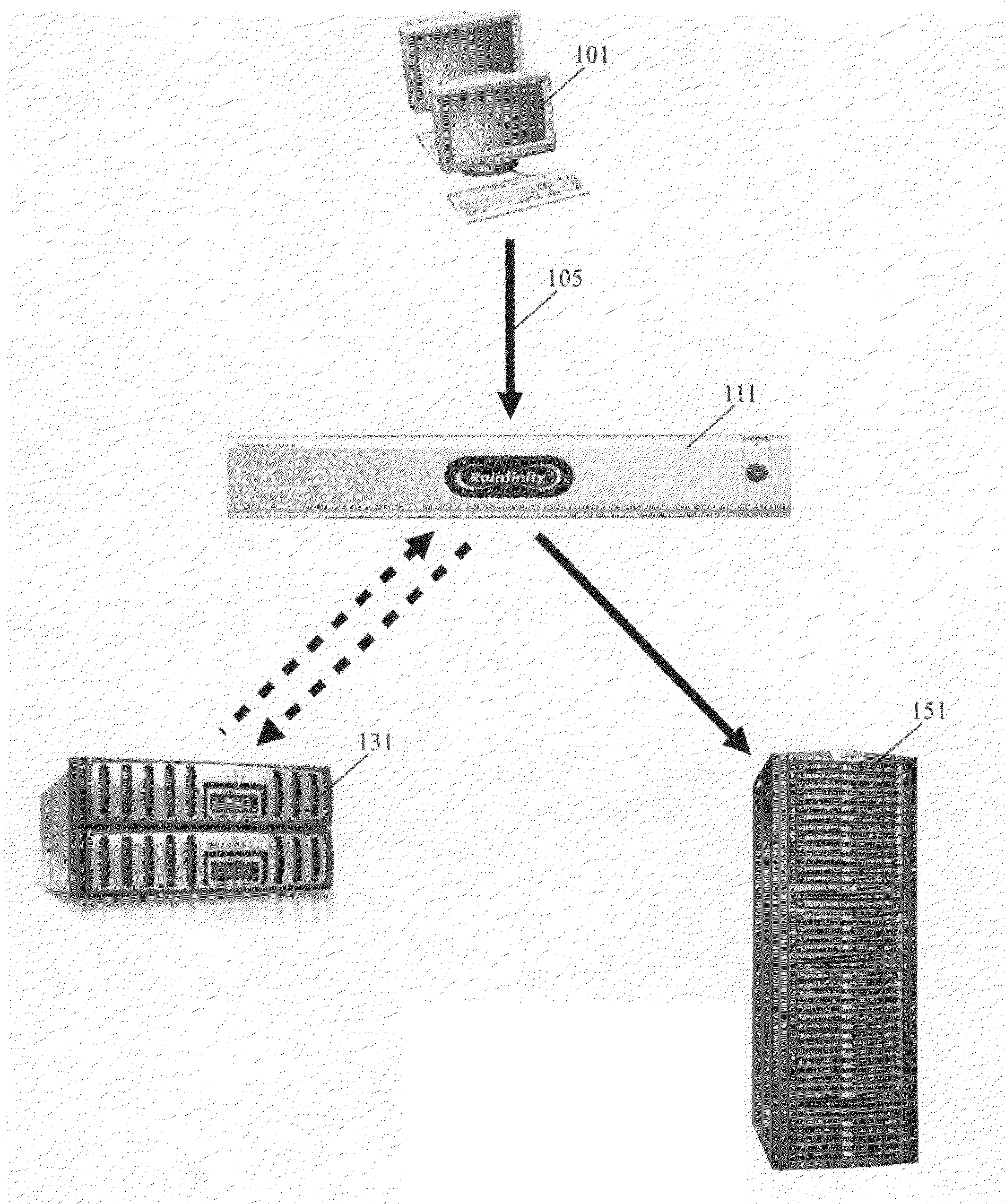
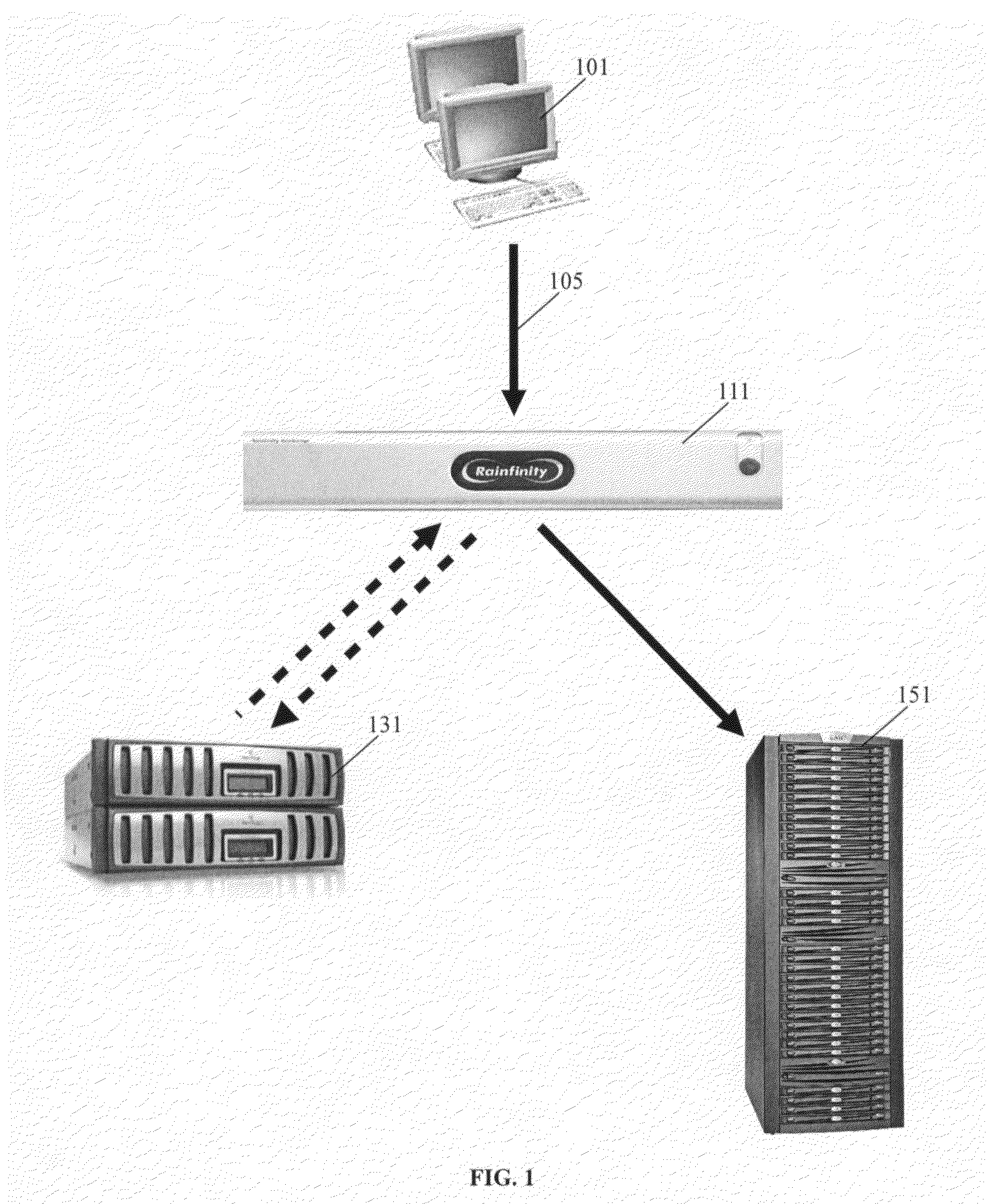
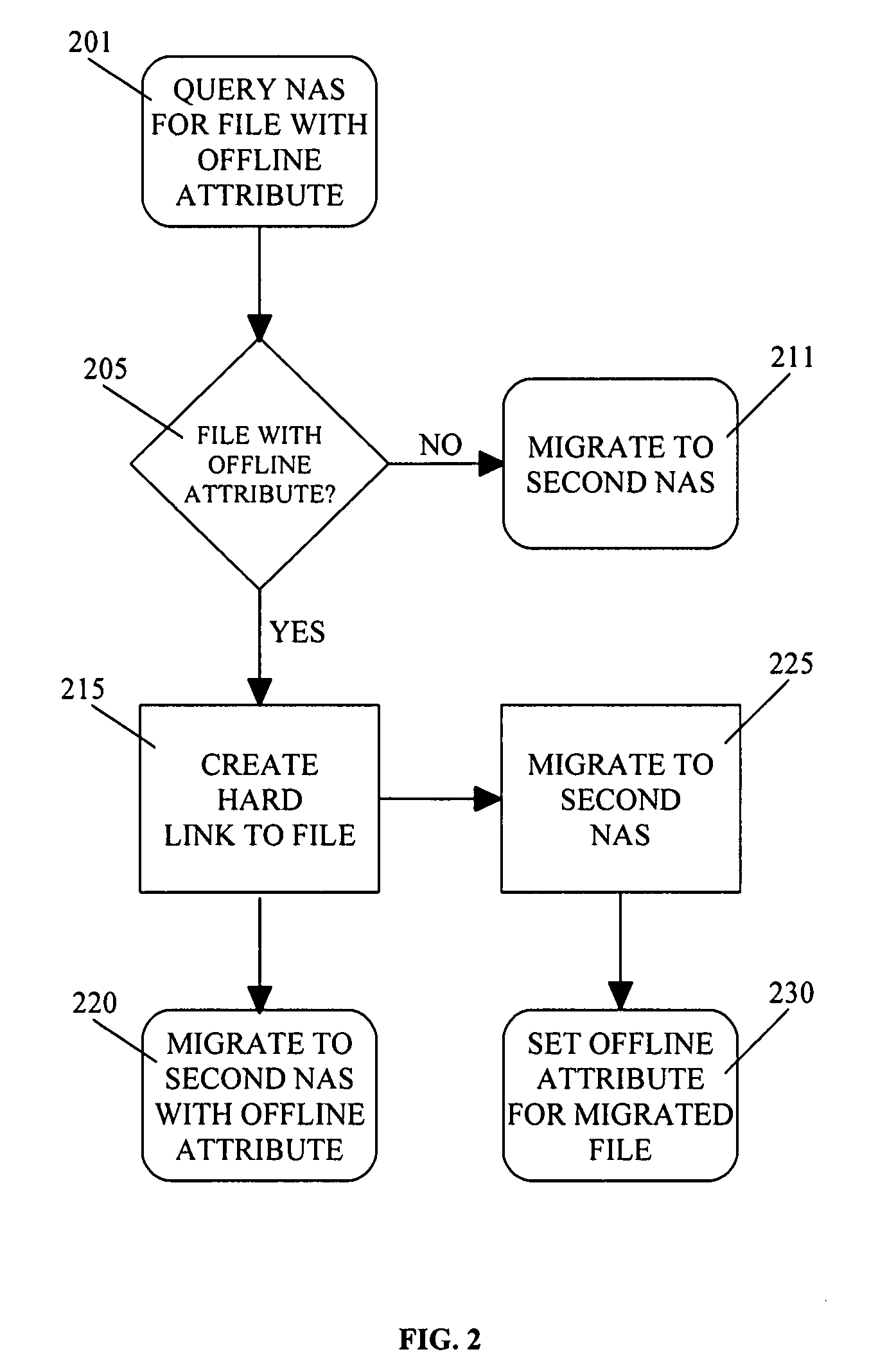
Network accessed storage files system query/set proxy service for a storage virtualization system
ActiveUS20090089344A1Digital data information retrievalMemory adressing/allocation/relocationFile systemMulti protocol
A system and method provides for querying and setting file attributes between Network File System and Common Internet File System network attached storage systems. Aspects of the present invention may be performed by a storage virtualization system that acts as an intermediary between one or more network attached storage systems. By querying and setting file attributes, files may be migrated between network attached storage systems while keeping the file attributes and primary location of the file contents intact. In addition, the present invention provides an additional aspect of ensuring that file names of multi-protocol files are compatible across every protocol.
Owner:EMC IP HLDG CO LLC
System and method for host based storage virtualization
InactiveUS6877011B2Minimal disruptionReconfiguration and repair of the storage systemInput/output to record carriersData processing applicationsComputer hardwareData virtualization
The illustrative embodiment of the present invention provides a method of inserting a software created virtual interface between the user of a host electronic device and a network storage medium. Data read and write requests are written to the virtual interface. The virtual interface is located on the host electronic device and allocates data to available storage mediums. Recovery and reconfiguration operations on the storage mediums holding stored data are hidden from the user by the virtual interface and may be performed contemporaneously with the user accessing the stored data.
Owner:ORACLE INT CORP
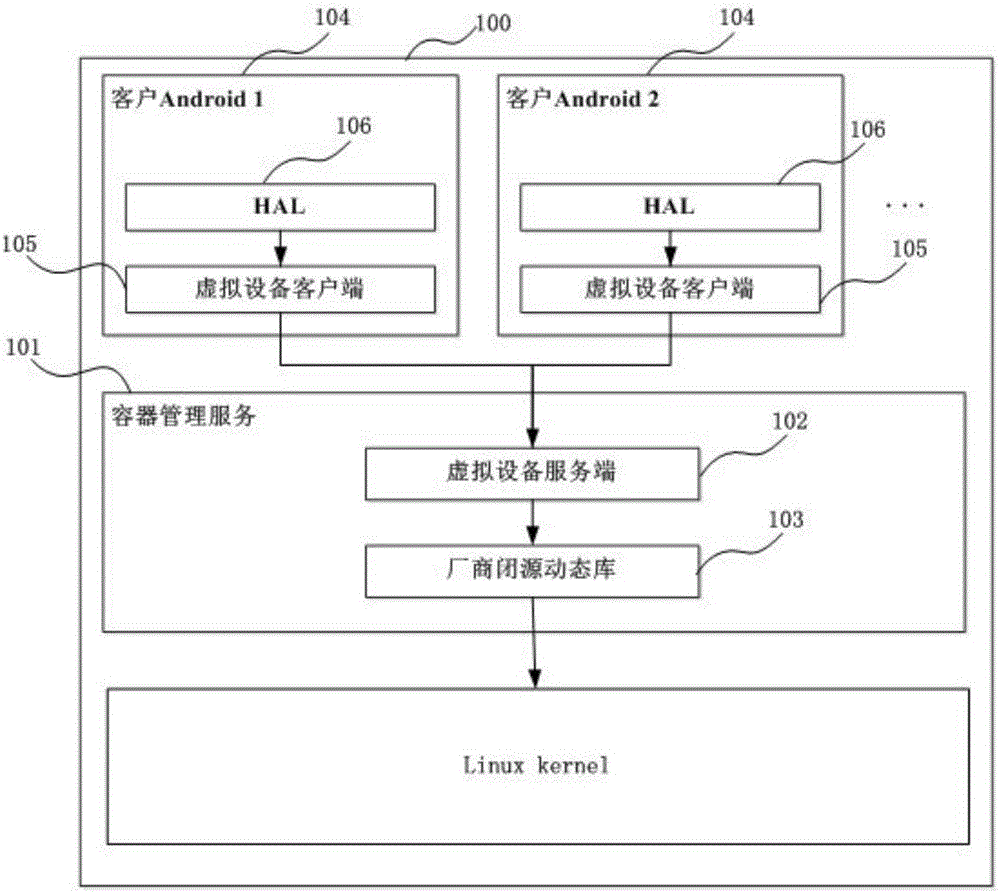
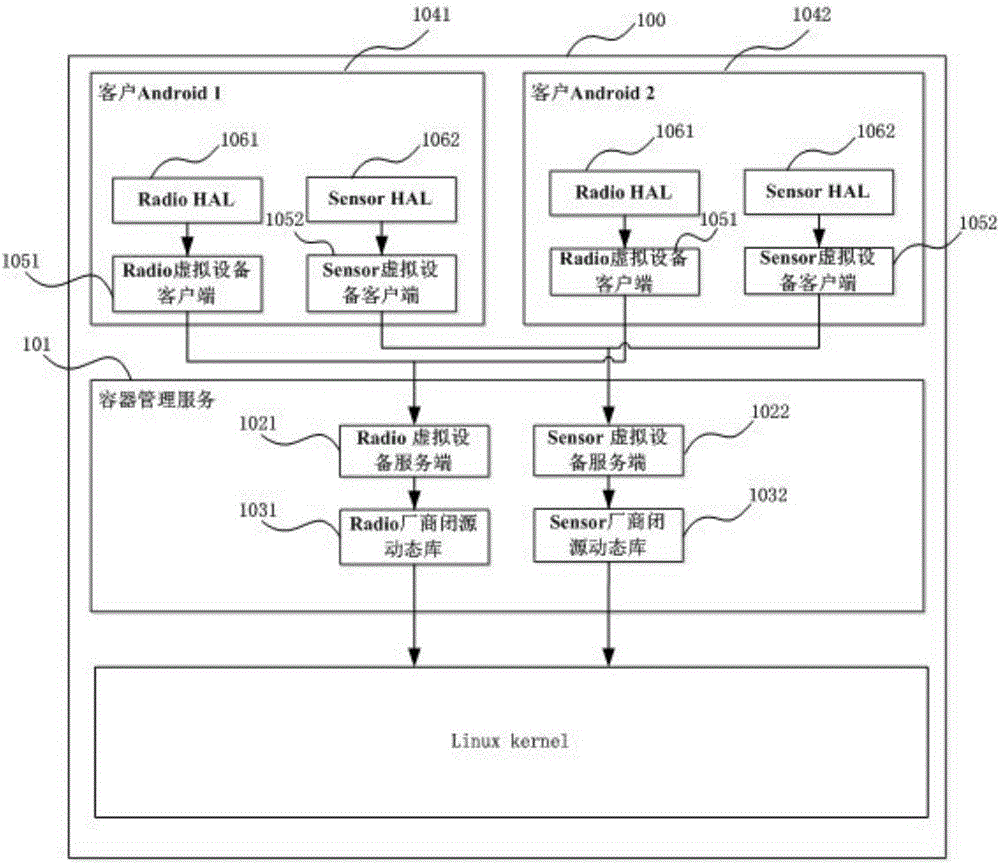
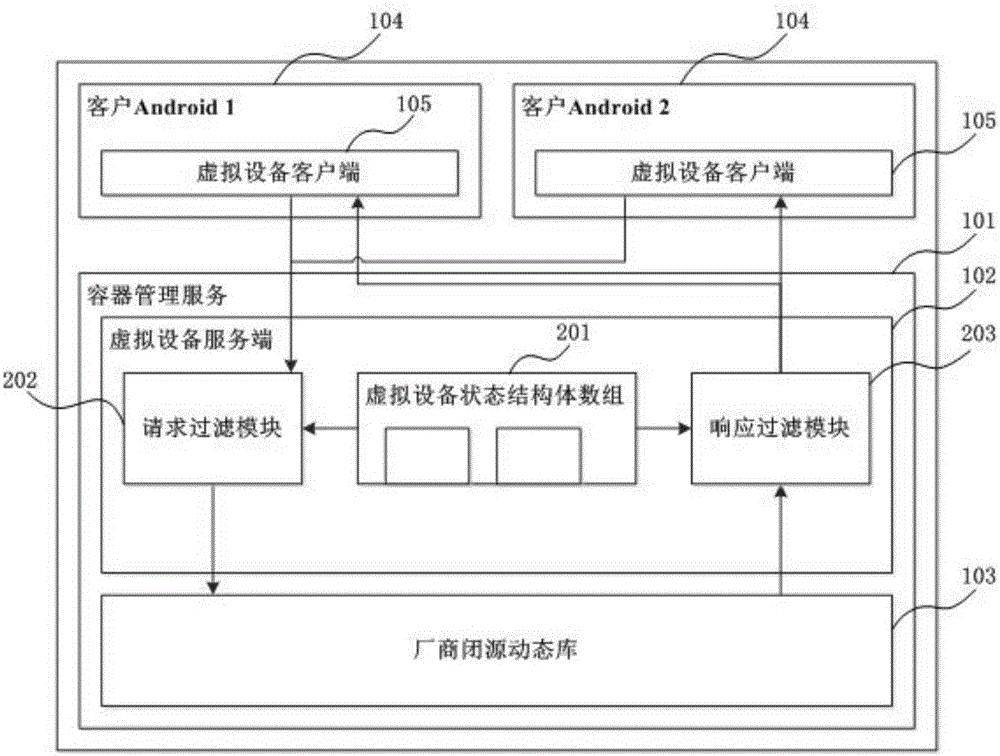
Device virtualization system and method based on Linux containers
ActiveCN105808320ARealize multiplexingAvoid cumbersomeSoftware simulation/interpretation/emulationGNU/LinuxOpen source
The invention provides a device virtualization system and method based on Linux containers. Virtual device clients and a virtual device server are loaded between Android system HALs and a device subsystem; device operation requests are sent to the virtual device server through the virtual device clients; and then the virtual device server finishes function call in a manufacturer dynamic library, thus realizing agency for the device operations, or constructs device operation results, thus realizing reuse of the device subsystem. According to the device virtualization system and method provided by the invention, through loading the virtual device clients and the virtual device server in multiple Android systems and container management service in a Linux kernel, the agency for the device operations and the reuse of the device subsystem are finished, thus realizing virtualization of the device; a new method different from a traditional device virtualization method is provided; and the reuse of special devices (especially devices without open source code) such as Radios is realized in the multi-Android platform based on a Linux container technique.
Owner:杨霞
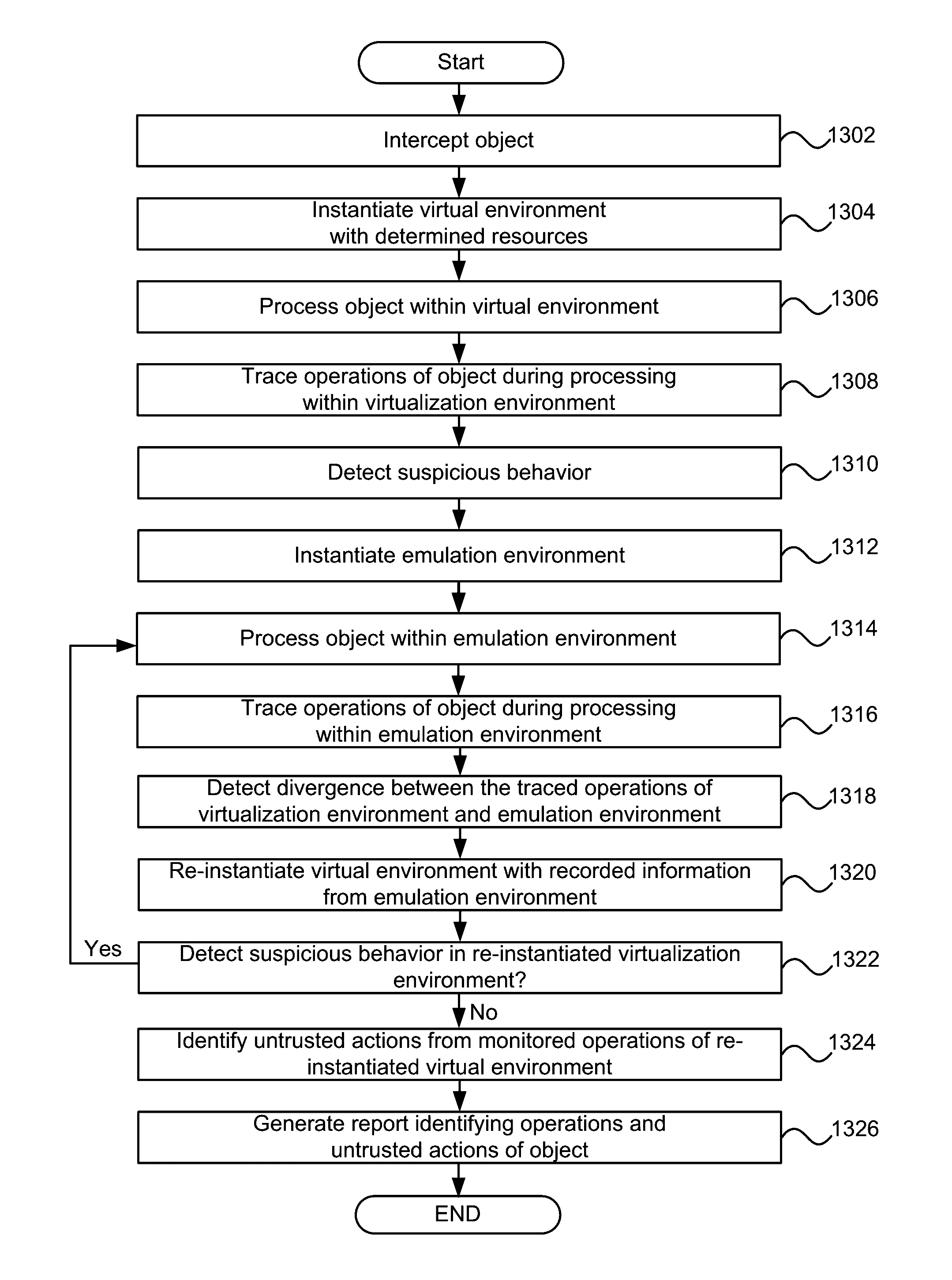
Systems and methods for virtualization and emulation assisted malware detection
Systems and methods for virtualization and emulation assisted malware detection are described. In some embodiments, a method comprises intercepting an object; instantiating and processing the object in a virtualization environment; tracing operations of the object while processing within the virtualization environment; detecting suspicious behavior associated with the object; instantiating an emulation environment in response to the detected suspicious behavior; processing, recording responses to, and tracing operations of the object within the emulation environment; detecting a divergence between the traced operations of the object within the virtualization environment to the traced operations of the object within the emulation environment; re-instantiating the virtualization environment; providing the recorded response from the emulation environment to the object in the virtualization environment; monitoring the operations of the object within the re-instantiation of the virtualization environment; identifying untrusted actions from the monitored operations; and generating a report regarding the identified untrusted actions of the object.
Owner:CYPHORT
Cross domain delegation by a storage virtualization system
ActiveUS20090089862A1Digital data processing detailsMultiple digital computer combinationsDomain nameData virtualization
The present is a system and method for preserving user account security privileges during a migration or re-direction of data from one network attached storage (“NAS”) system to another. Certain NAS systems authenticate user accounts using Kerberos Delegation Technology. In addition, some NAS systems feature the ability to constrain delegation to certain services. While effective in limiting access and promoting network security, this constrained delegation restricts the ability of a storage virtualization system to migrate or re-direct data to other NAS systems, especially if the other NAS system resides or is identified by a different domain name. The present invention is a system and method for storing user account credentials that work with the former NAS system, and providing a way to translate these credentials to a new NAS system with a new domain, permitting seamless data migration and re-direction across domains.
Owner:EMC IP HLDG CO LLC
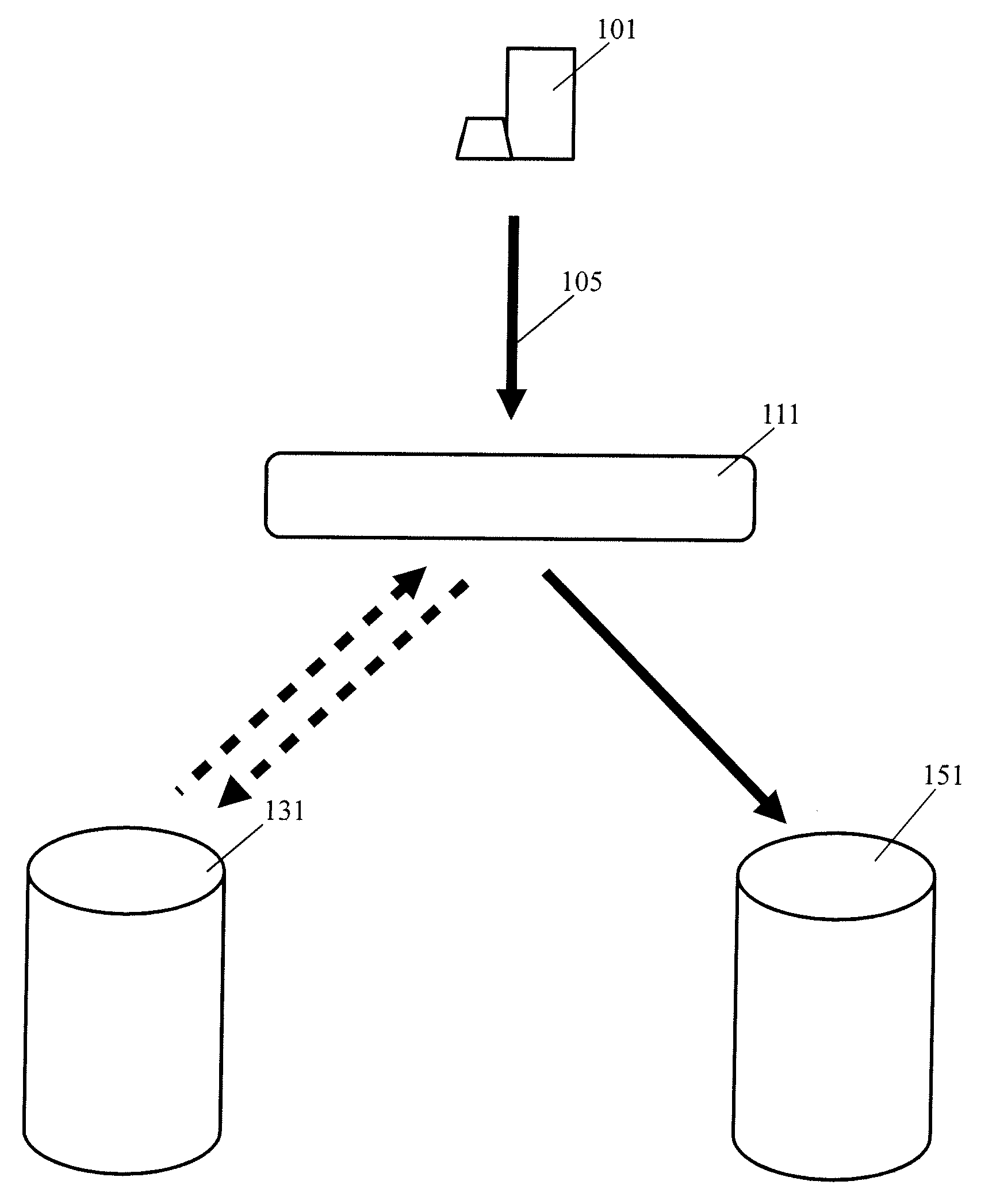
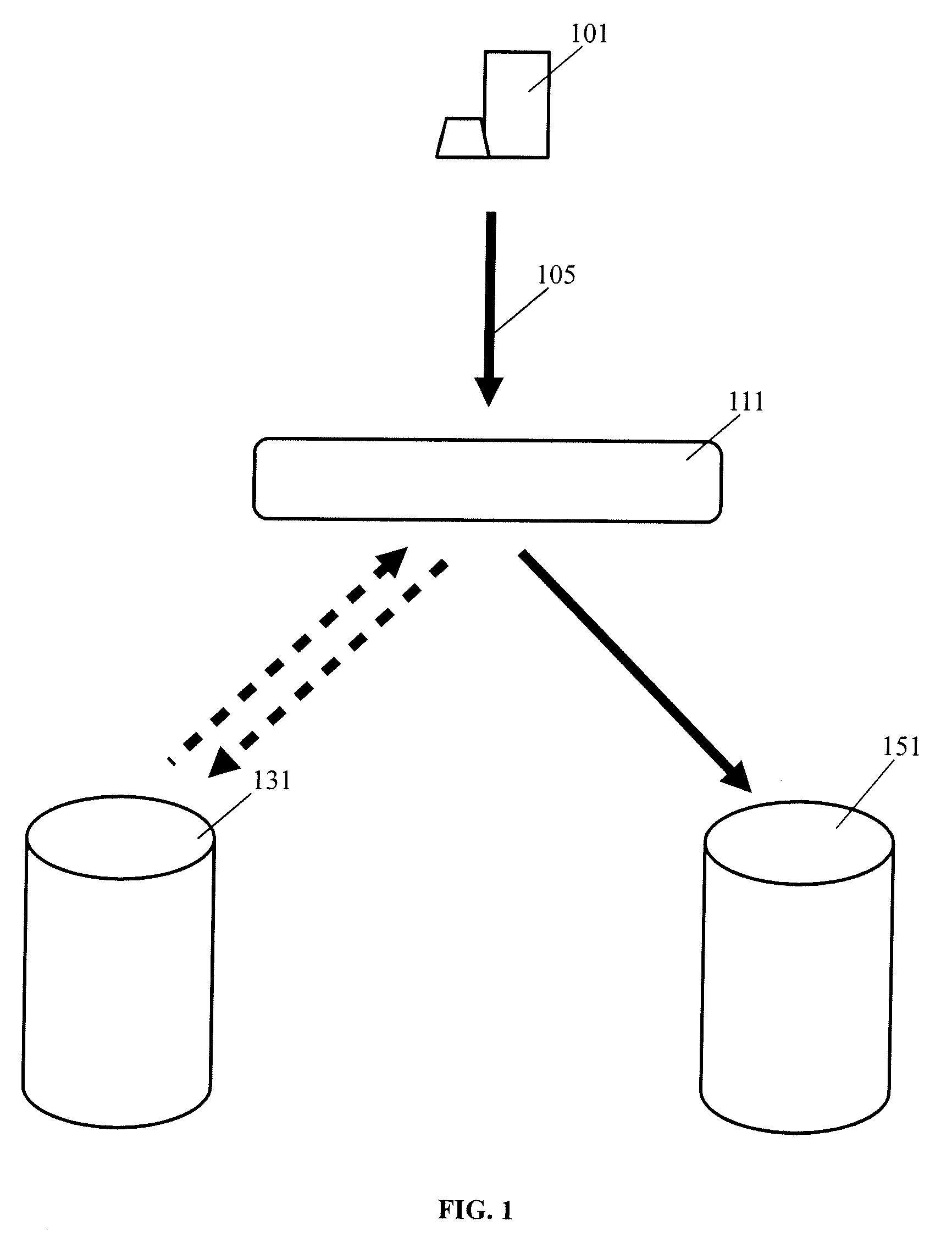
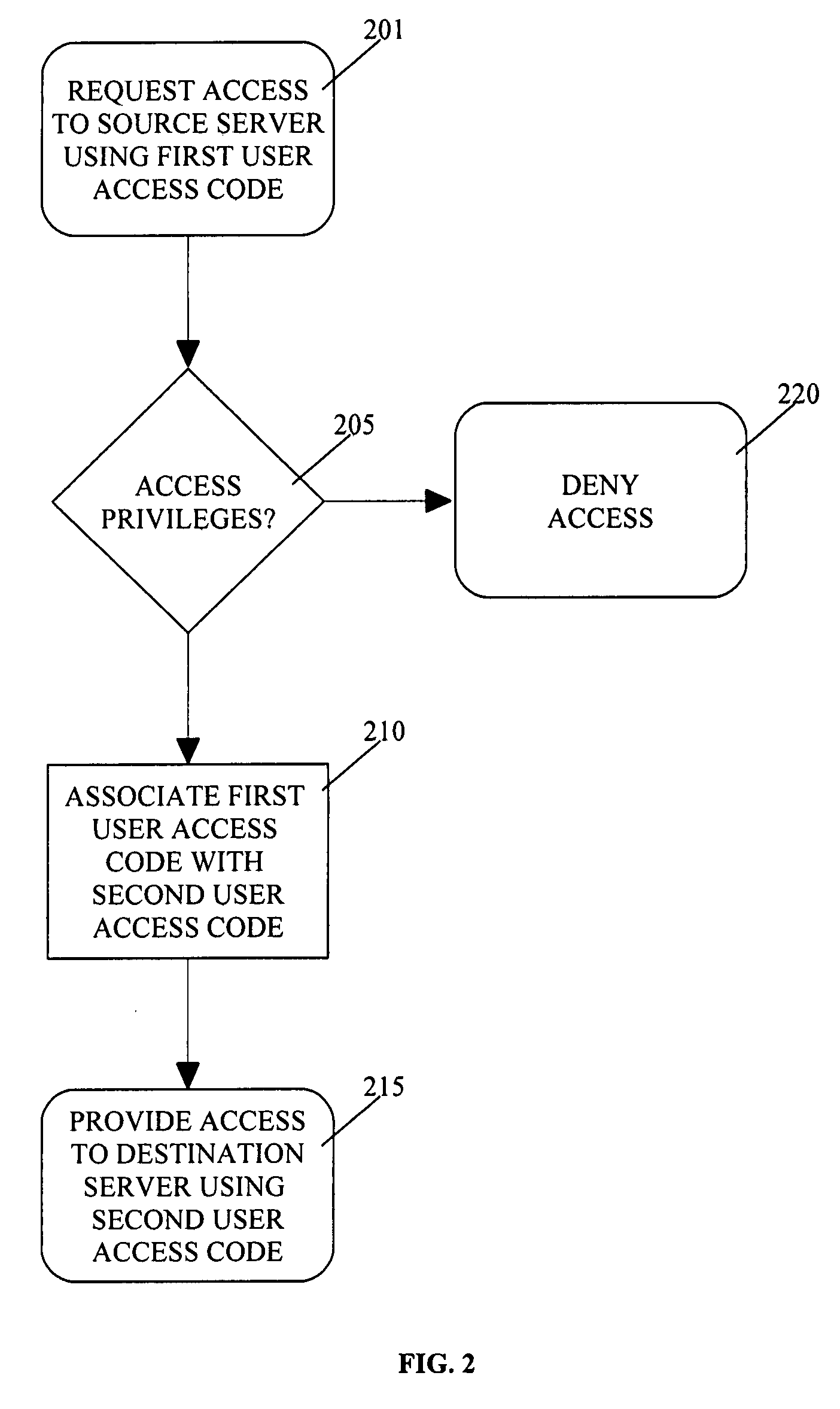
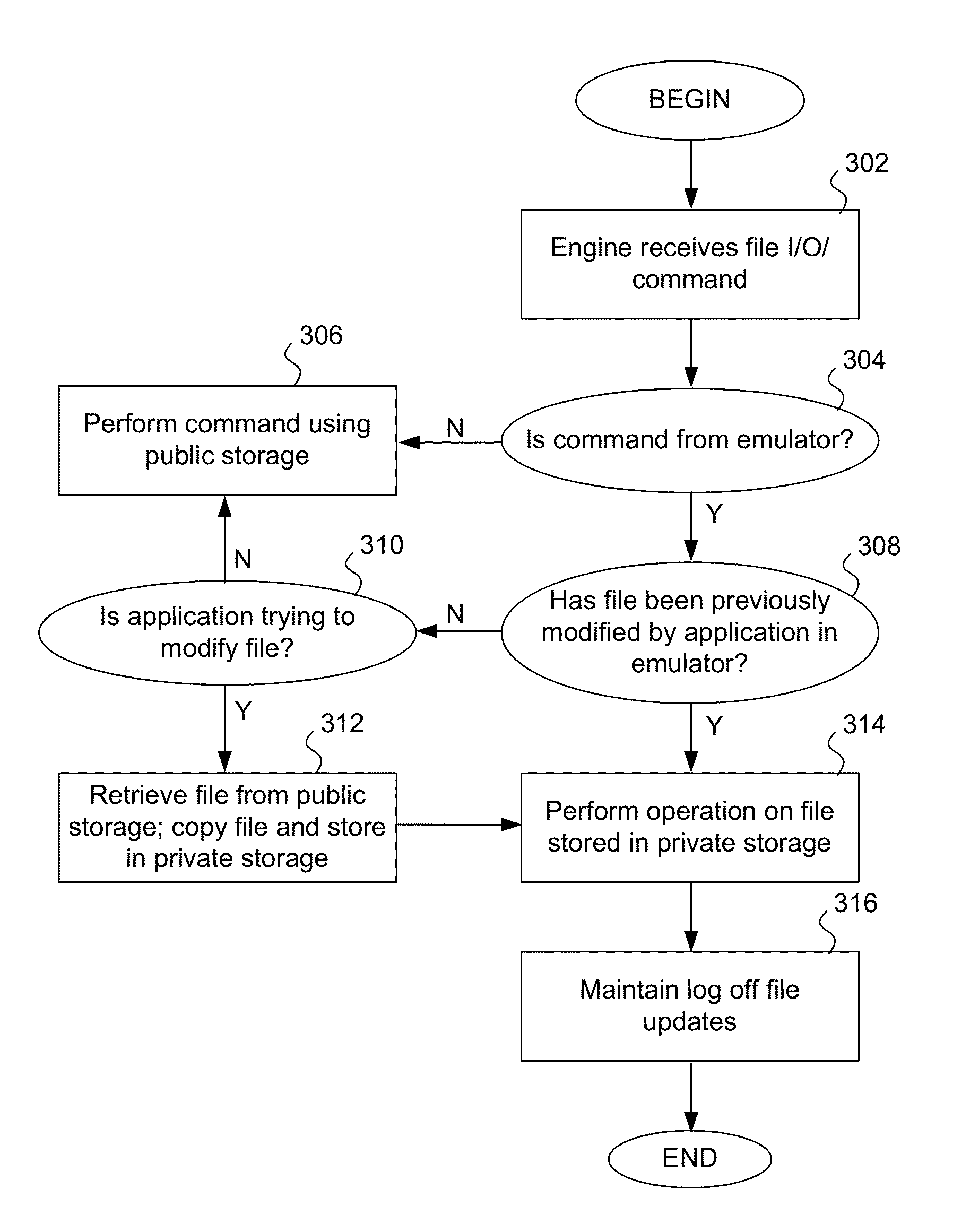
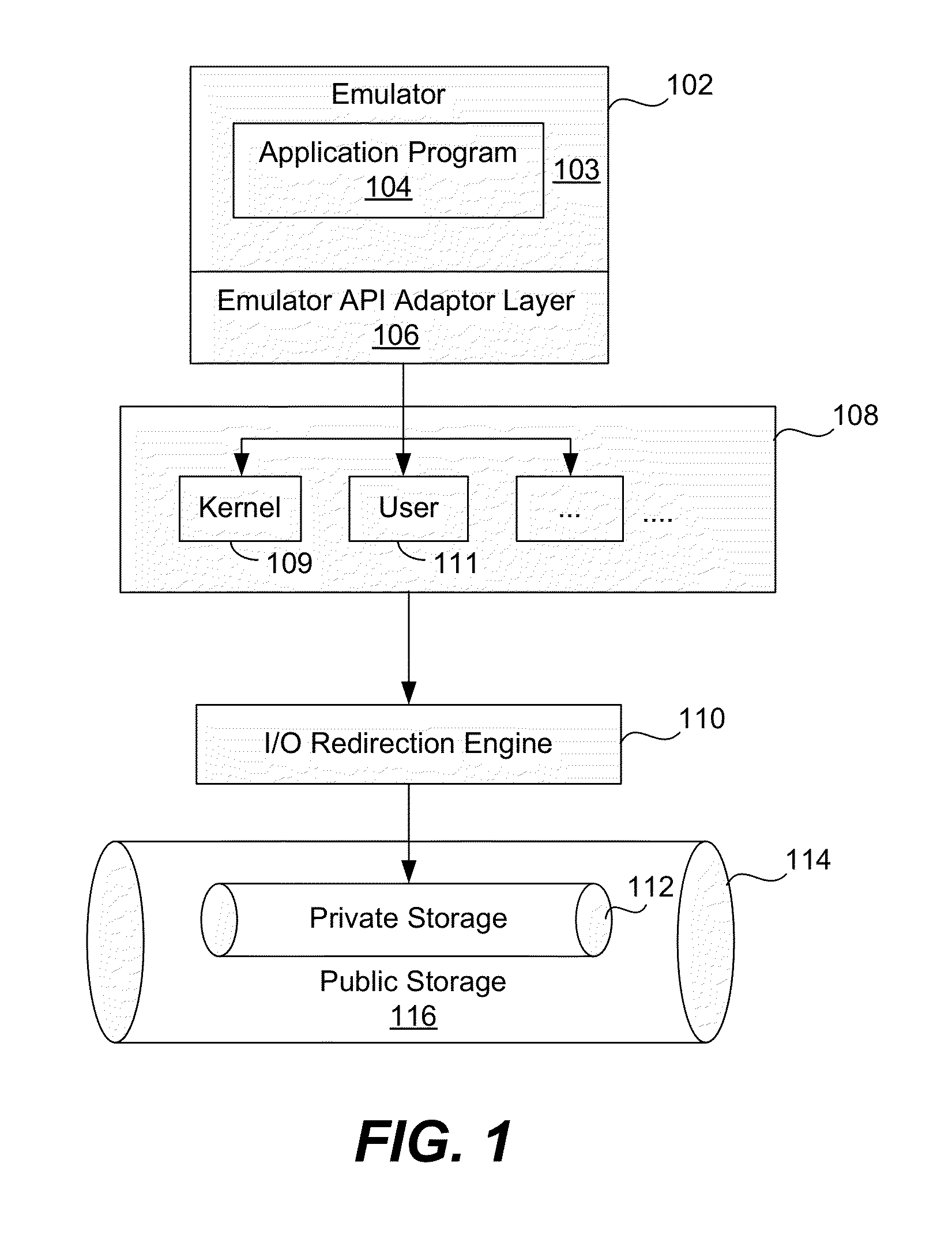
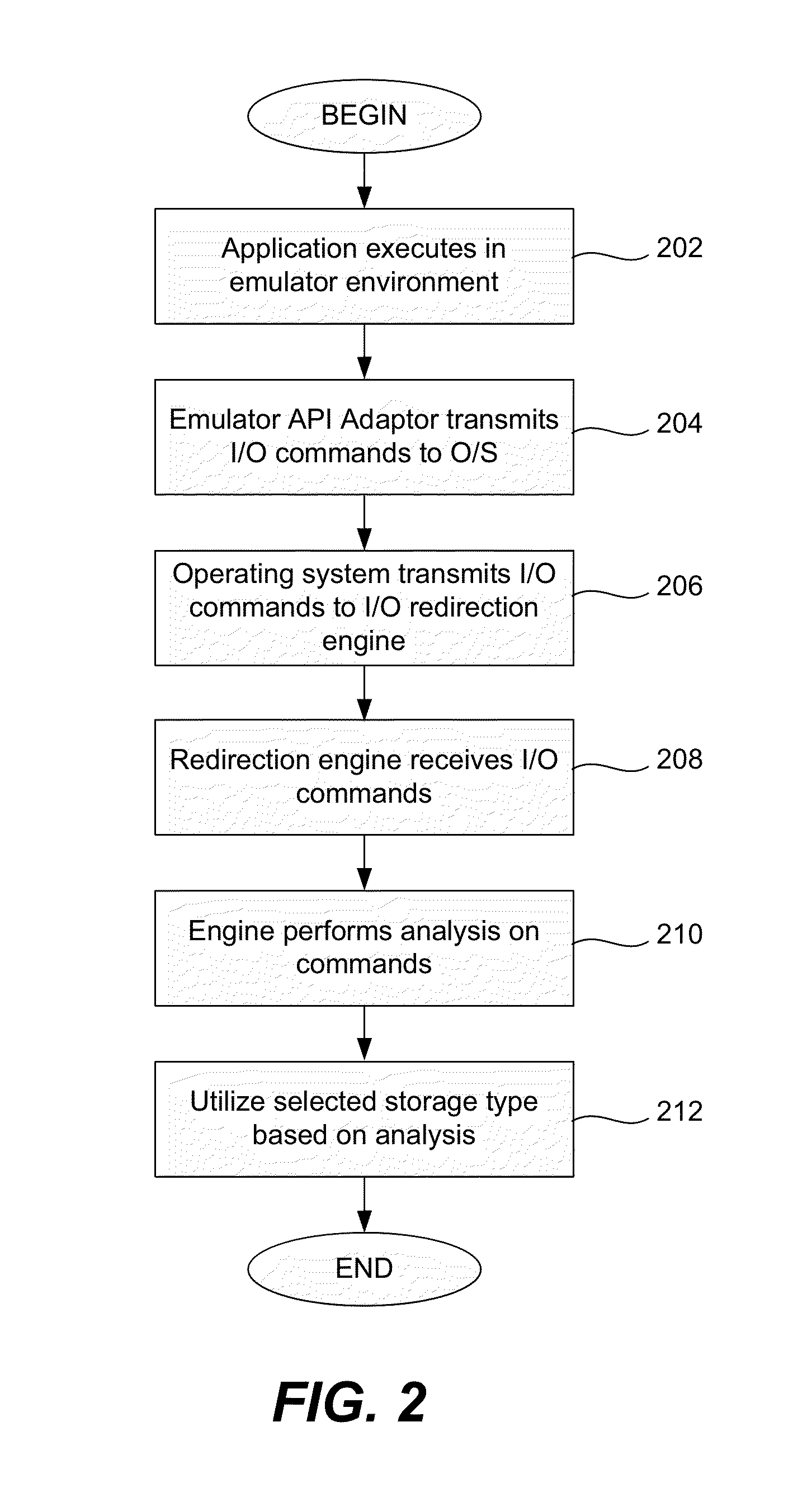
Malware protection using file input/output virtualization
Applications running in an API-proxy-based emulator are prevented from infecting a PC's hard disk when executing file I / O commands. Such commands are redirected to an I / O redirection engine instead of going directly to the PC's normal operating system where it can potentially harm files in on the hard disk. The redirection engine executes the file I / O command using a private storage area in the hard disk that is not accessible by the PC's normal operating system. If a file that is the subject of a file I / O command from an emulated application is not in the private storage area, a copy is made from the original that is presumed to exist in the public storage area. This copy is then acted on by the command and is stored in the private storage area, which can be described as a controlled, quarantined storage space on the hard disk. In this manner the PC's (or any computing device's) hard disk is defended from potential malware that may originate from applications running in emulated environments.
Owner:TREND MICRO INC
Apparatus and method for data virtualization in a storage processing device
ActiveUS7353305B2Provide flexibilityProvides managementMultiplex system selection arrangementsInput/output to record carriersWire speedMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
Apparatus and system for providing software service using software virtualization and method thereof
InactiveUS20140143305A1Easy to manageMaximize availabilityMultiple digital computer combinationsProgram controlGraphicsCommunication unit
Provided are an apparatus and a system for providing a software service, using software virtualization, and a method thereof. The apparatus for providing a software service, using software virtualization, includes: an input unit receiving information according to operation of a menu or keys from a user; a communication unit interlocking to a service server implemented to execute software in a virtual execution environment in accordance with the received information; a control unit receiving graphic data of the software executed in the interlocking service server, performing rendering on the received graphic data with its own graphic processing unit, and generating a video as the result of rendering; and a display unit displaying the generated video.
Owner:ELECTRONICS & TELECOMM RES INST
Database virtualization
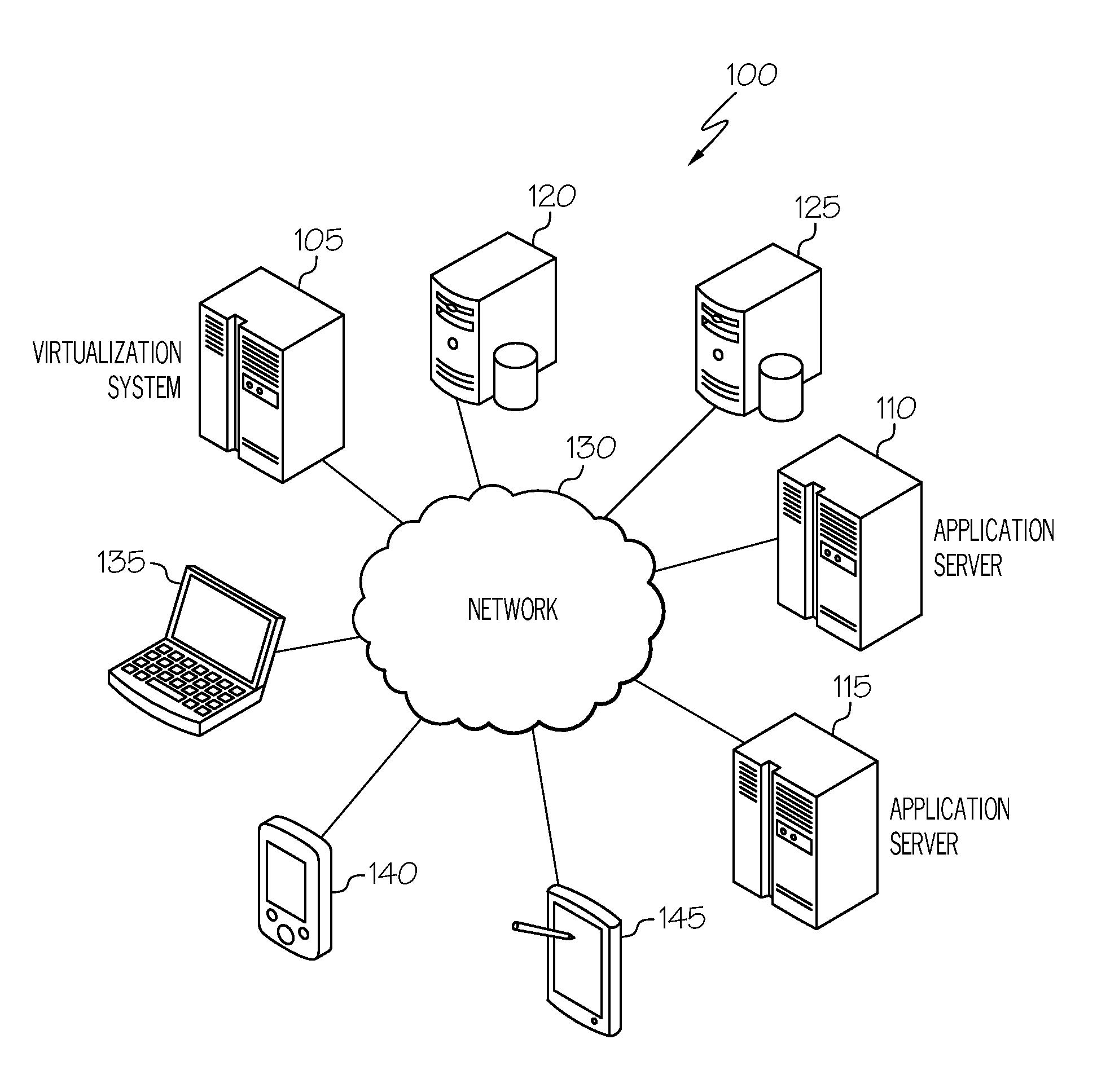
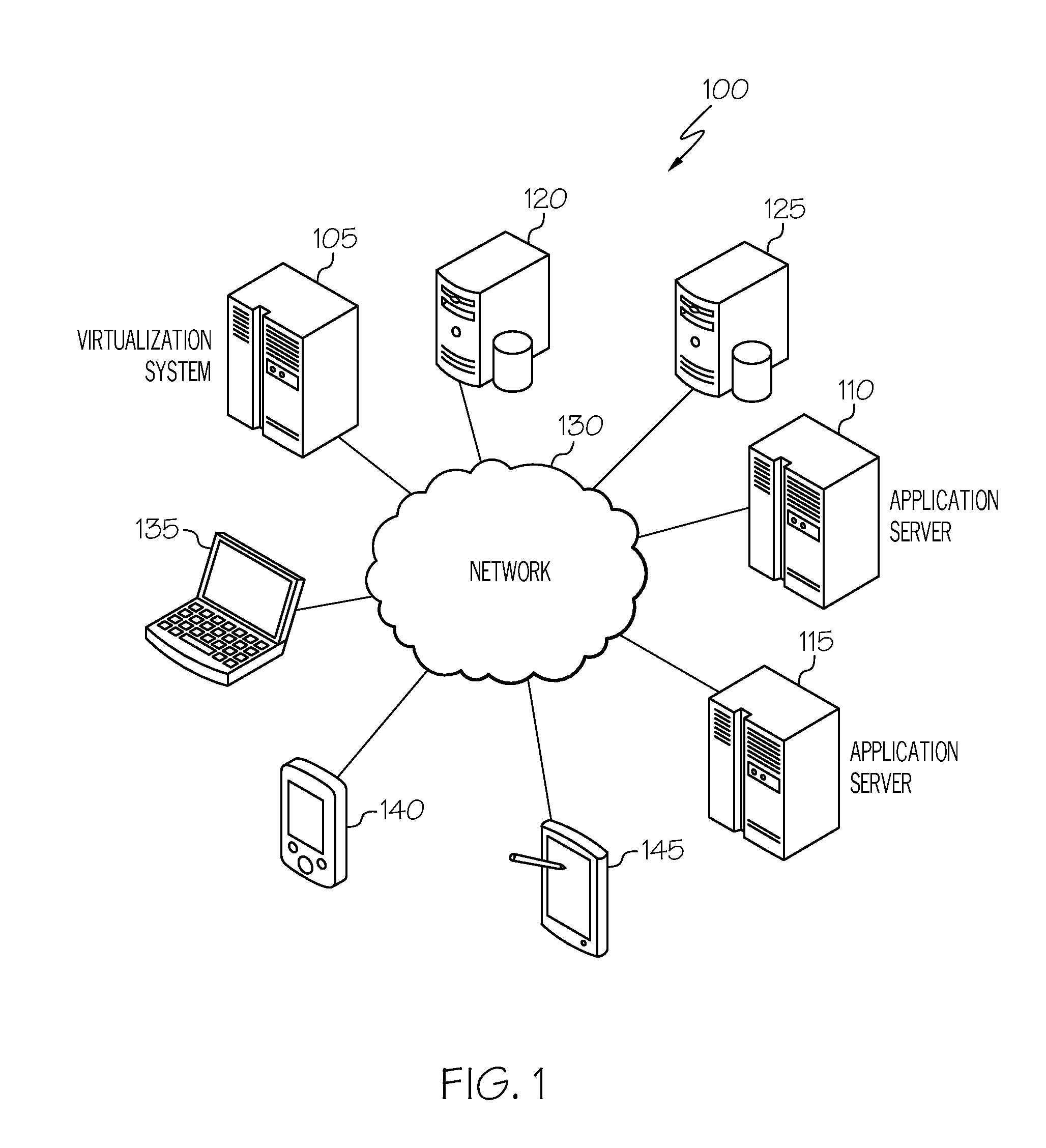
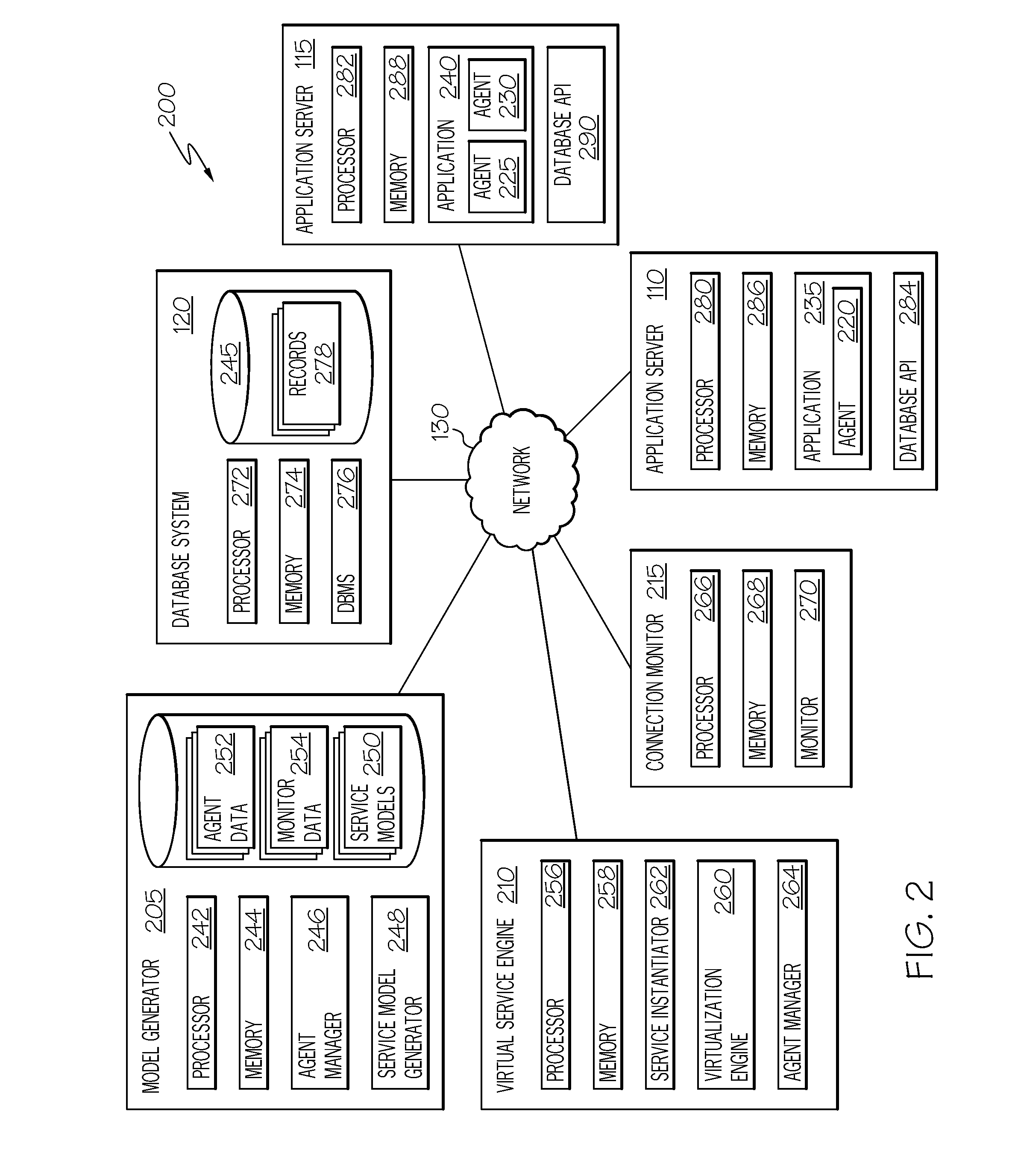
InactiveUS20160217159A1Special data processing applicationsDatabase design/maintainanceService modelData description
Agents monitoring data exchanged between a software component and a database access component provide first, second, third, and fourth data. First data describes a detected first request from the software component to the database access component corresponding to an attempt to open a connection with a database the software component interfaces with using the database access component. Second data describes a detected connection object provided to the software component using the database access component and corresponding to a connection with the database. Third data describes a detected second request from the software component to the database access component corresponding to a query of the database by the software component. Fourth data describes a result set from the database responsive to the query. At least a portion of a service model is generated using the first, second, third, and fourth data to at least model opening the connection and the query.
Owner:CA TECH INC
Multi-root sharing of single-root input/output virtualization
In a first embodiment of the present invention, a method for multi-root sharing of a plurality of single root input / output virtualization (SR-IOV) endpoints is provided, the method comprising: CSR redirection to a management processor which either acts as a proxy to execute the CSR request on behalf of the host or filters it and performs an alternate action, downstream routing of memory mapped I / O request packets through the switch in the host's address space and address translation with VF BAR granularity, upstream routing of requests originated by I / O devices by table lookup indexed by Requester ID, and requester ID translation using a fixed local-global RID offset.
Owner:AVAGO TECH INT SALES PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com