Patents
Literature
323results about How to "Prevent malicious attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
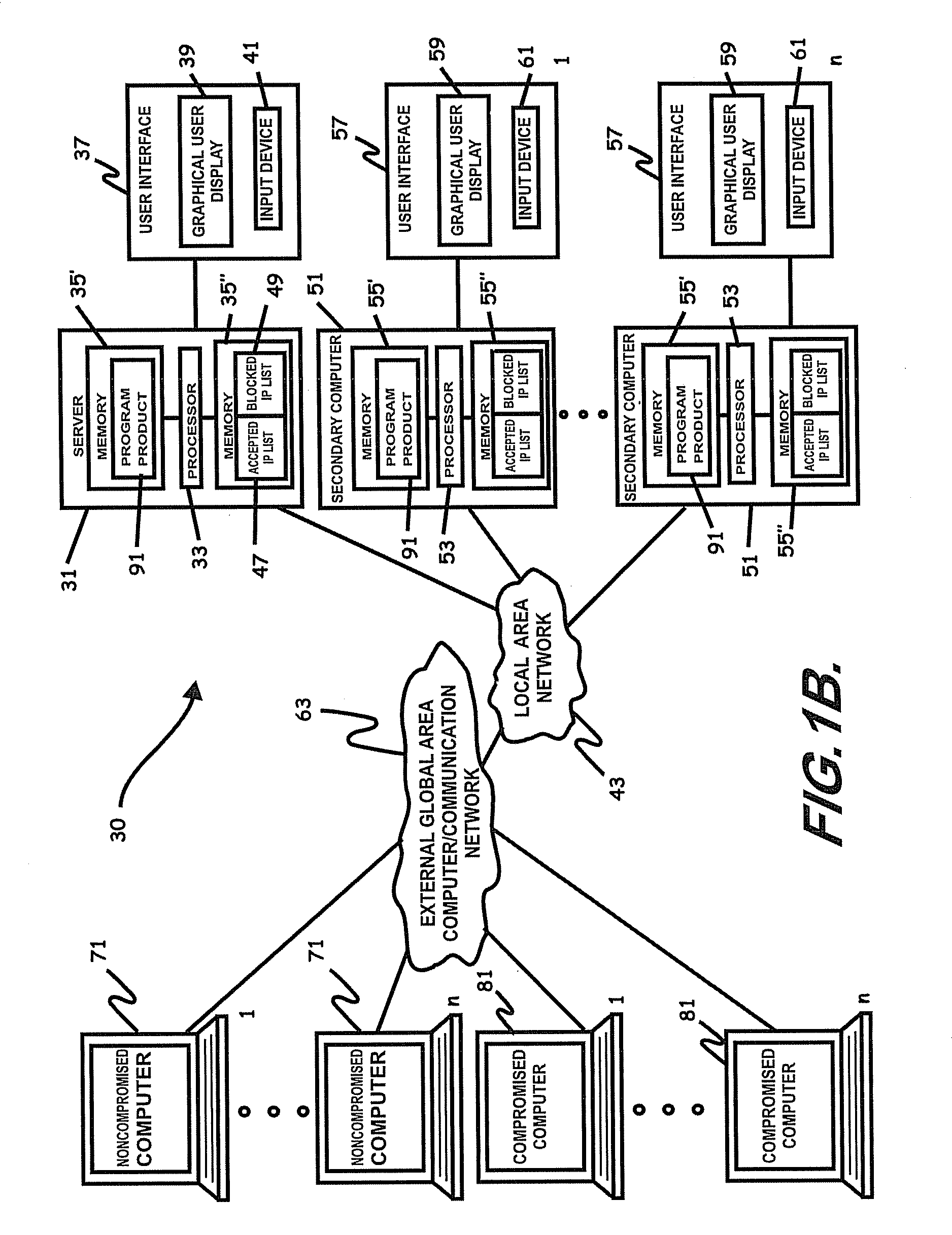
Internet security dynamics assessment system, program product, and related methods
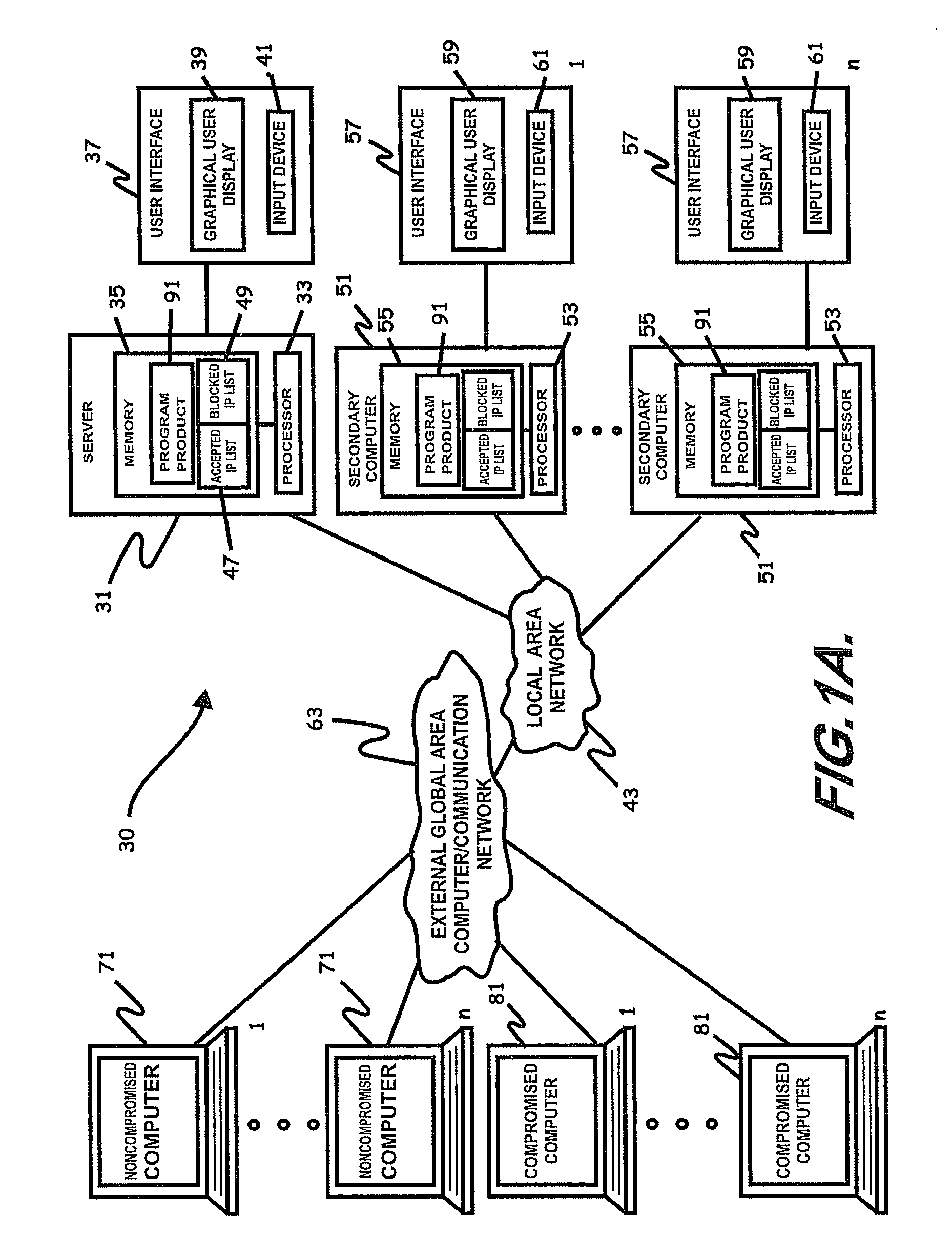
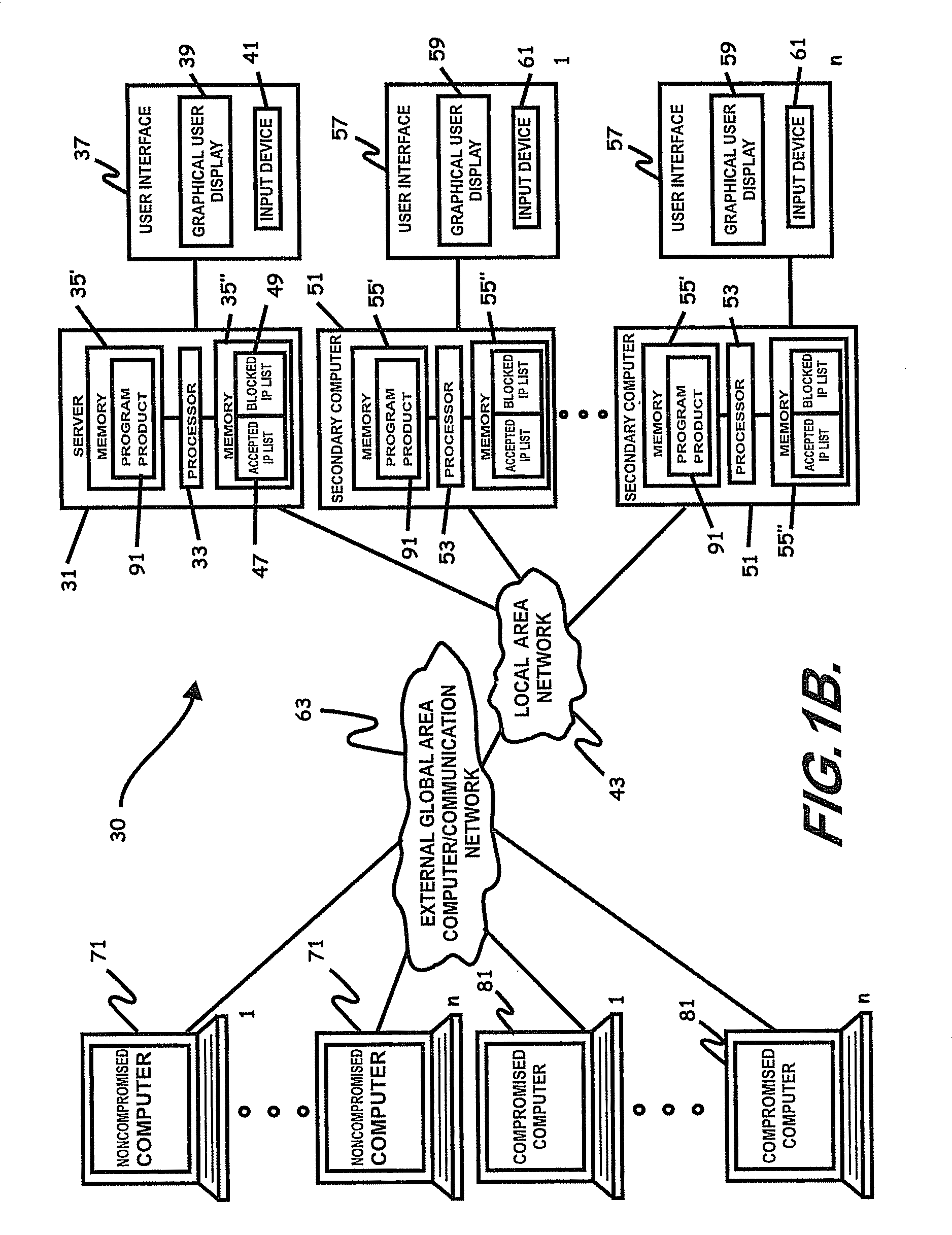
ActiveUS8069471B2Prevent malicious attacksLimited accessMemory loss protectionDigital data processing detailsIp addressThe Internet
Owner:LOCKHEED MARTIN CORP
System and method for preventing malicious code spread using web technology
InactiveUS20080127338A1Avoid attackPrevent malicious attacksMemory loss protectionError detection/correctionCode distributionTransmitter
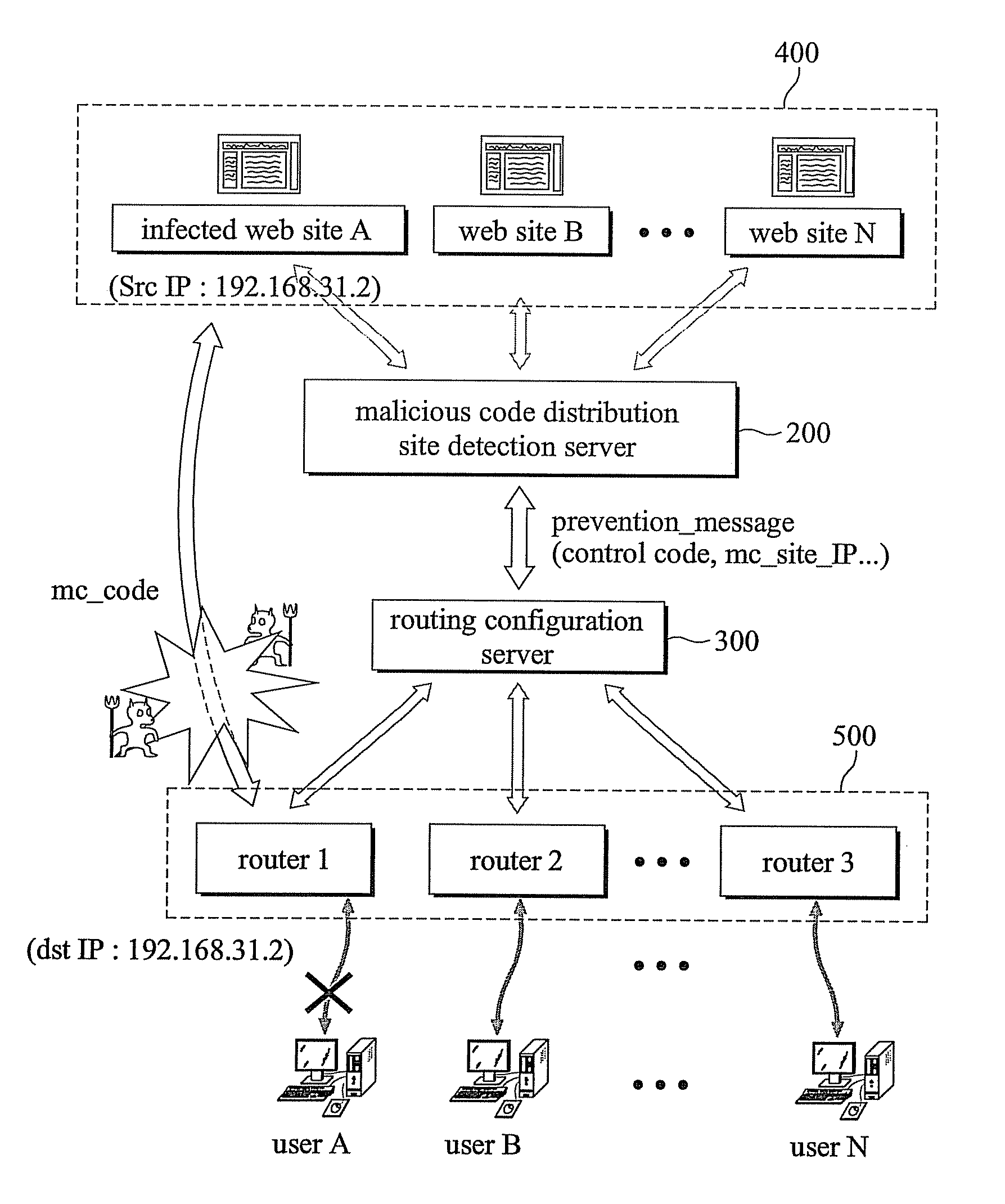
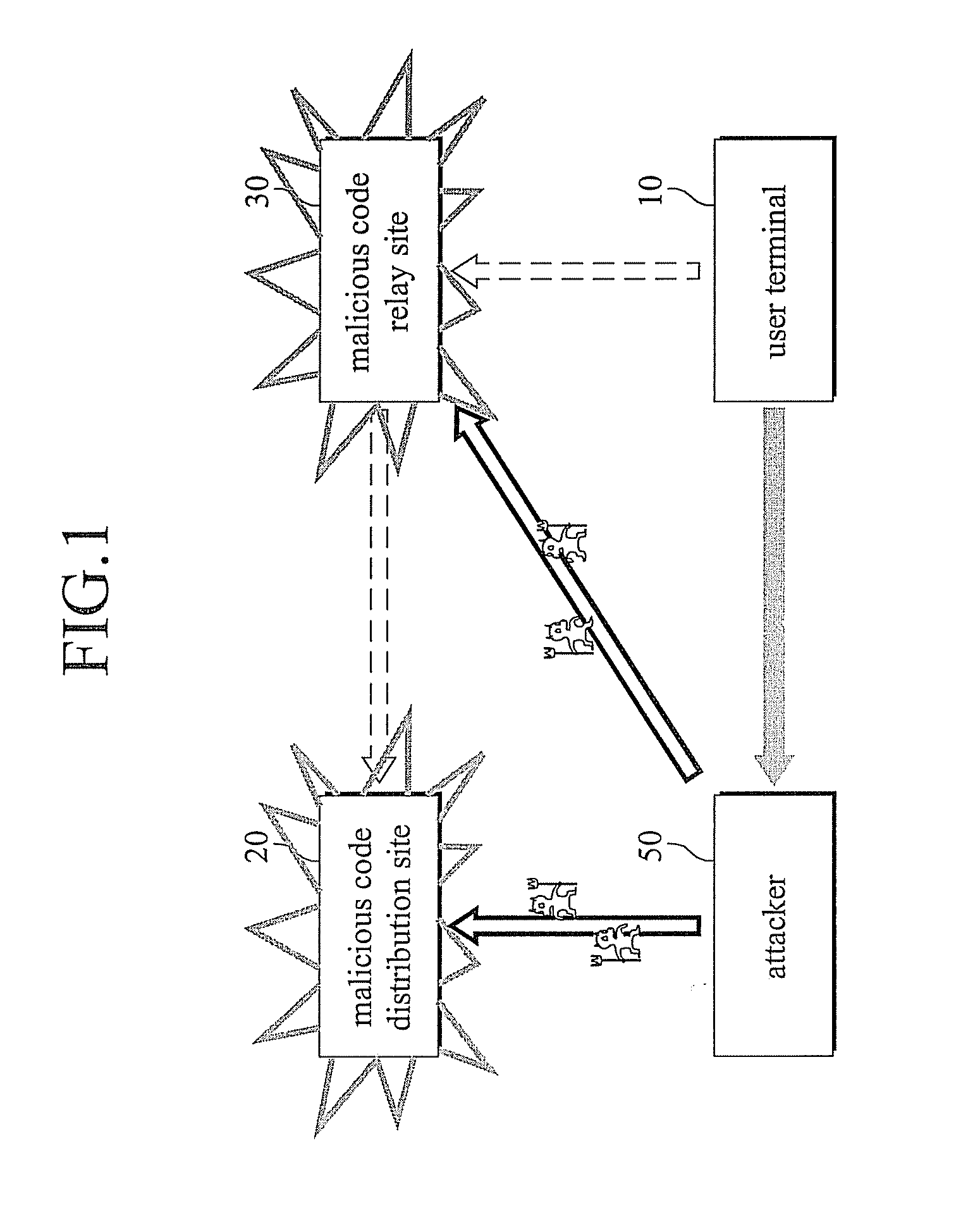
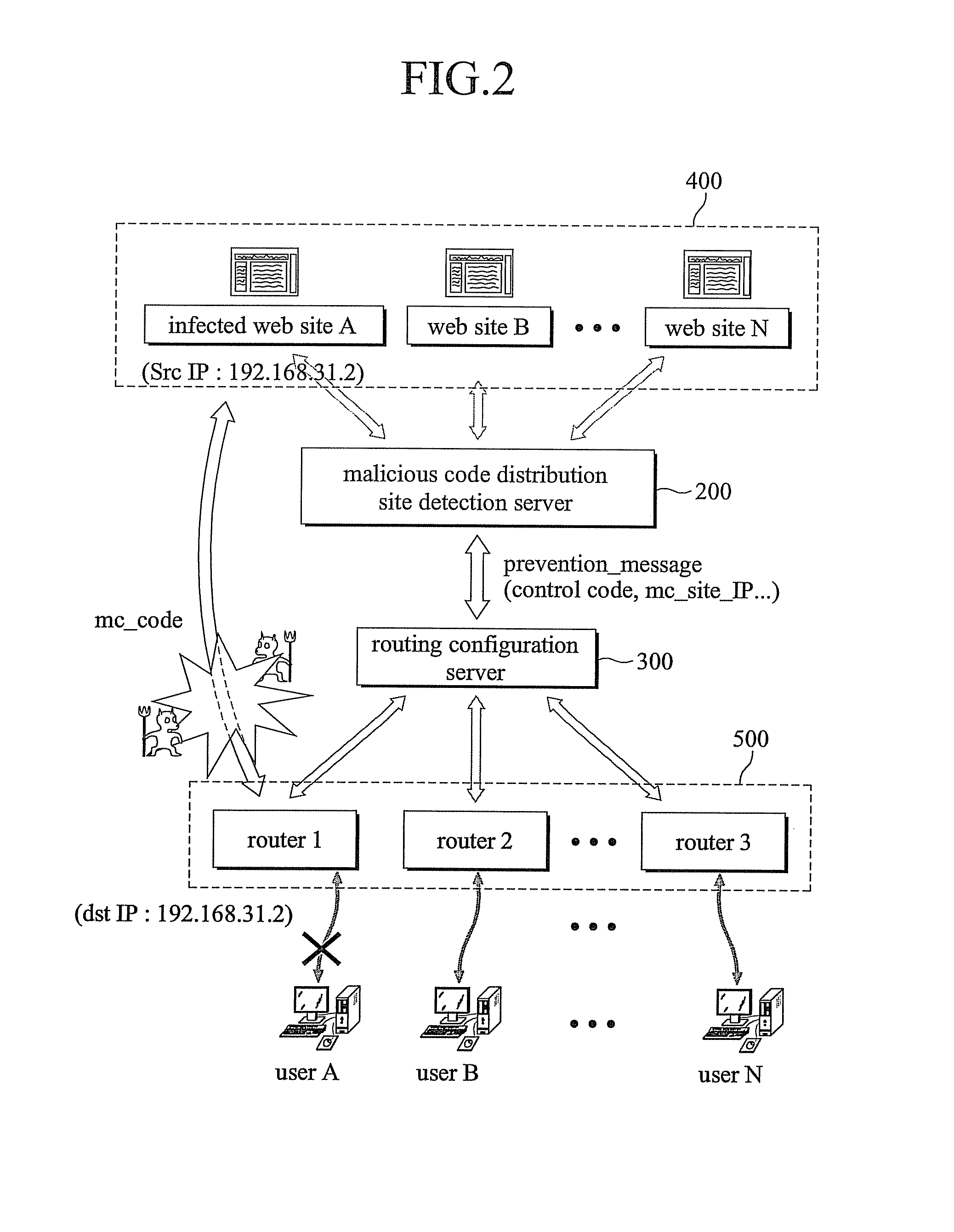
The present invention relates to a system and a method for preventing an attack of a malicious program spread using a web technology comprising a malicious code distribution site detection server comprising a malicious code distribution site detector for detecting a malicious code distribution site, and a prevention message transmitter for transmitting a prevention message to a routing configuration server, wherein the prevention message includes an IP address of the malicious code distribution site detected by the malicious code distribution site detector; a plurality of routers including a virtual IP address; and the routing configuration server for advertising the IP address of the malicious code distribution site such that a routing path of a packet having the IP address of the malicious code distribution site as a target address or an starting address is guided to the virtual IP address according to an reception of the prevention message to block a connection to the malicious code distribution site.
Owner:KOREA INTERNET & SECURITY AGENCY
Internet security dynamics assessment system, program product, and related methods
ActiveUS20100100962A1Prevent malicious attacksLimited accessMemory loss protectionDigital data processing detailsIp addressThe Internet
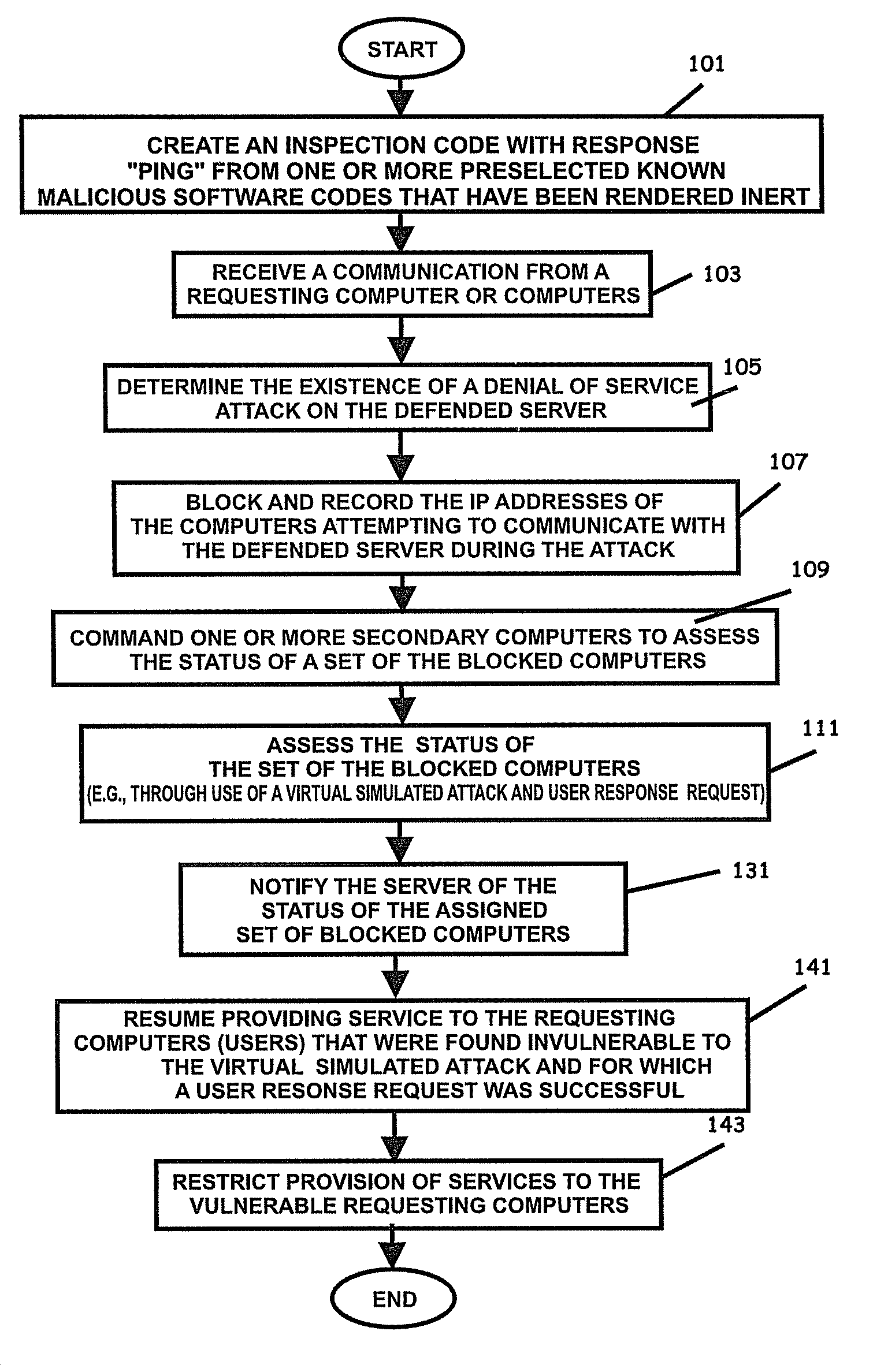
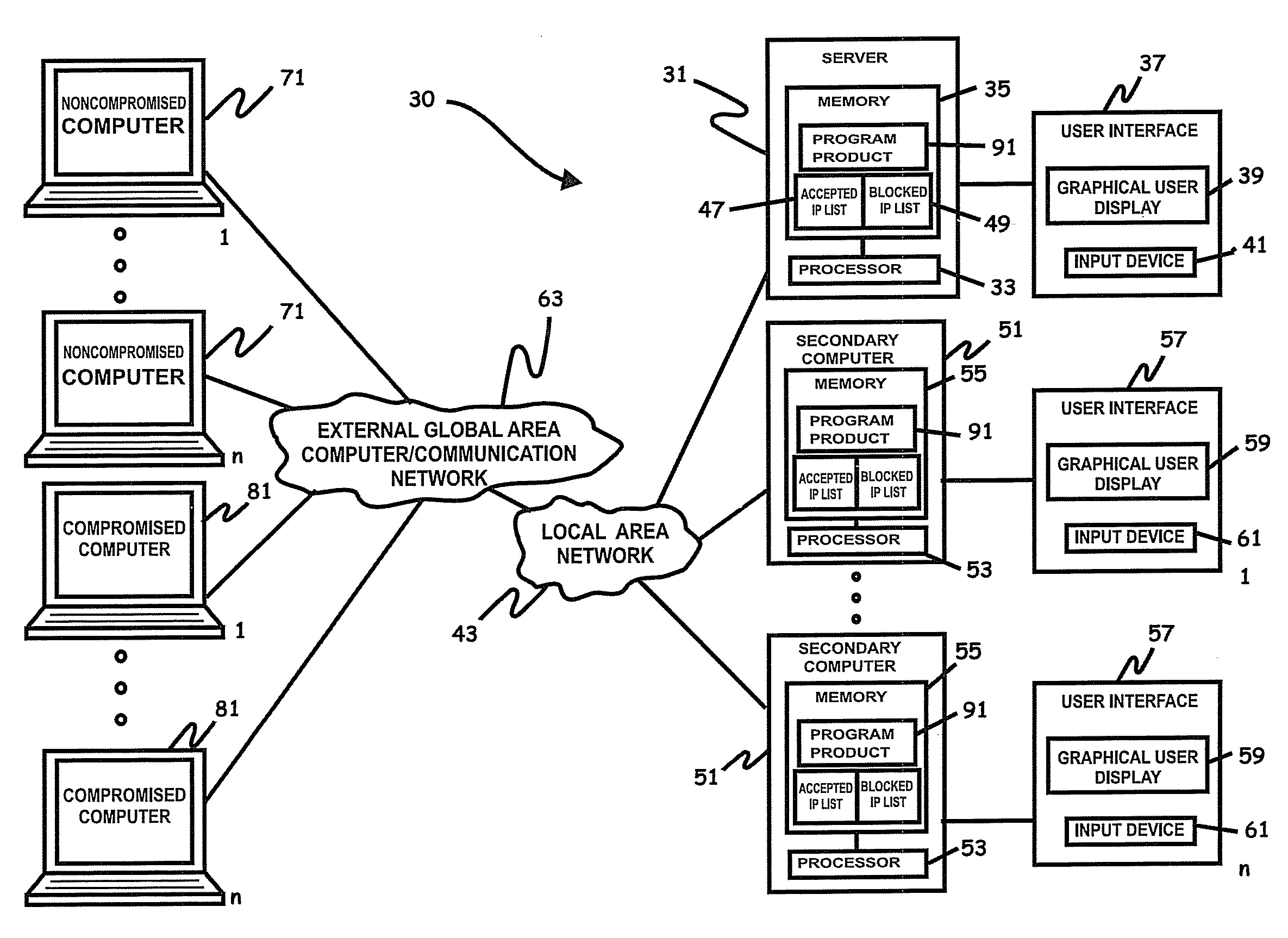
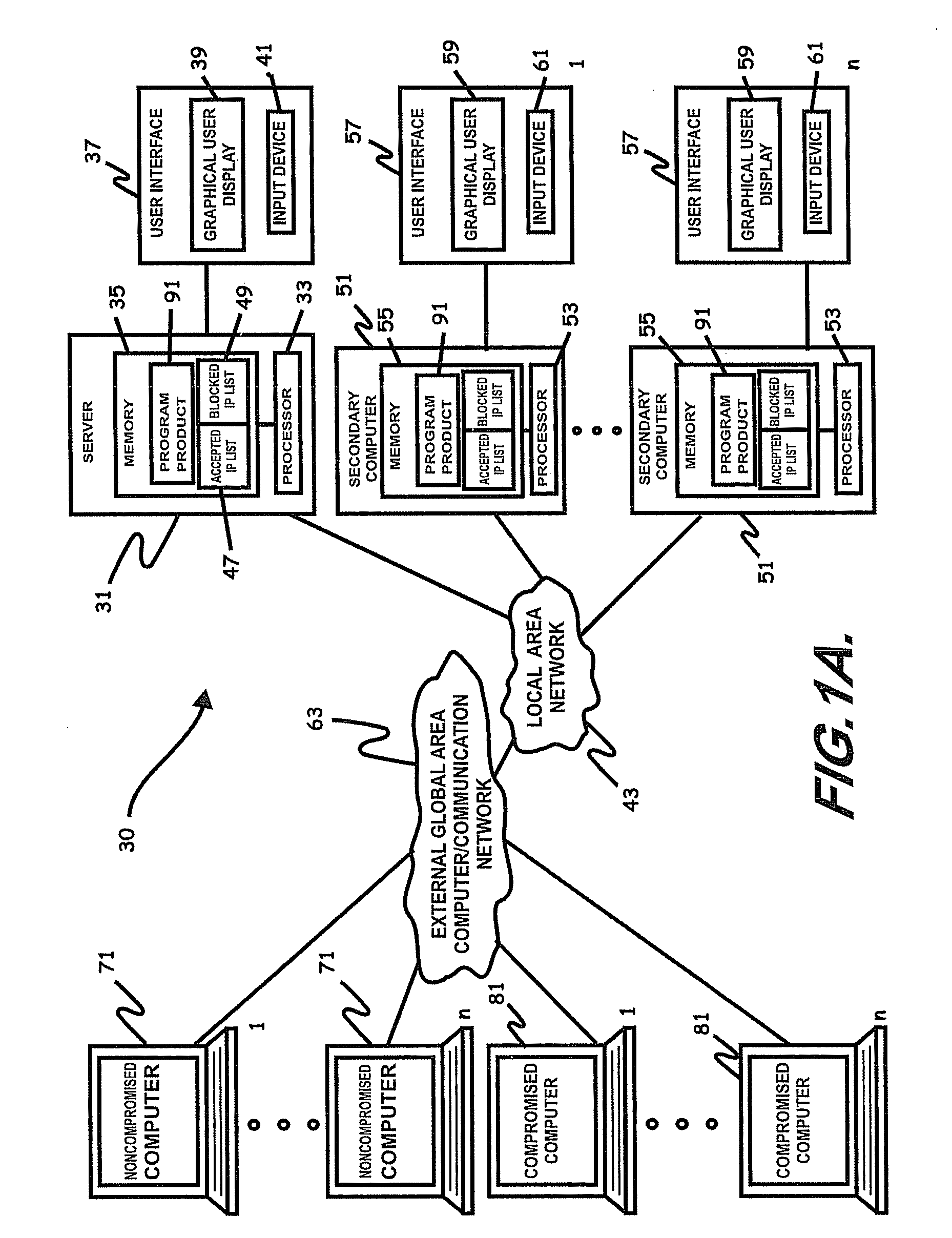
Systems, program product, and methods related to dynamic Internet security and risk assessment and management, are provided. For example, a system, program product, and method of identifying and servicing actual customer requests to a defended or protected computer or server can include the steps / operations of receiving by the defended computer, a service request from each of a plurality of IP addresses associated with a separate one of a plurality of service requesting computers, sending an inspection code adapted to perform a virtual attack on each existing service requesting computers at each respective associated IP address, and restricting provision of services from the defended computer to a subset of the service requesting computers identified for restriction when a security feature of the respective service requesting computer is determined to have been defeated by the virtual attack.
Owner:LOCKHEED MARTIN CORP
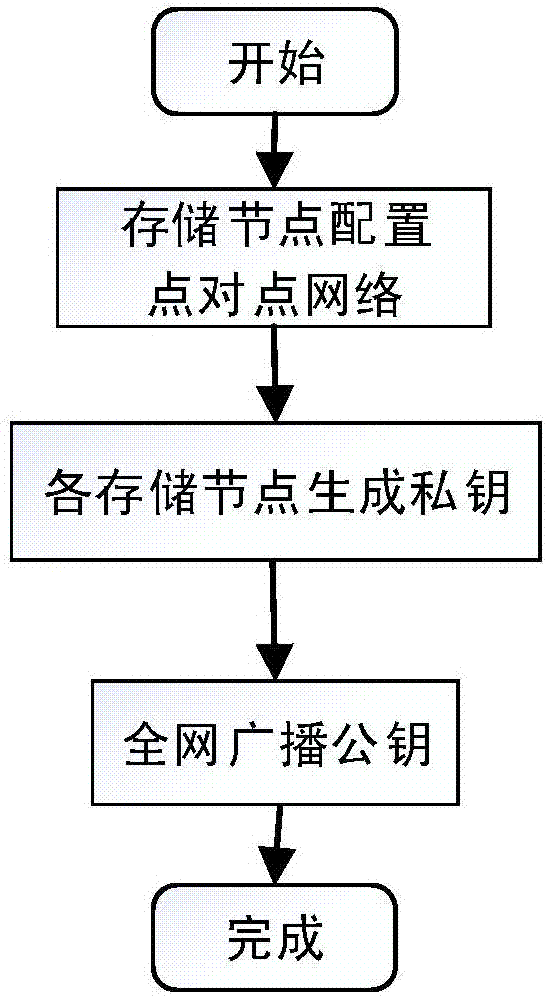
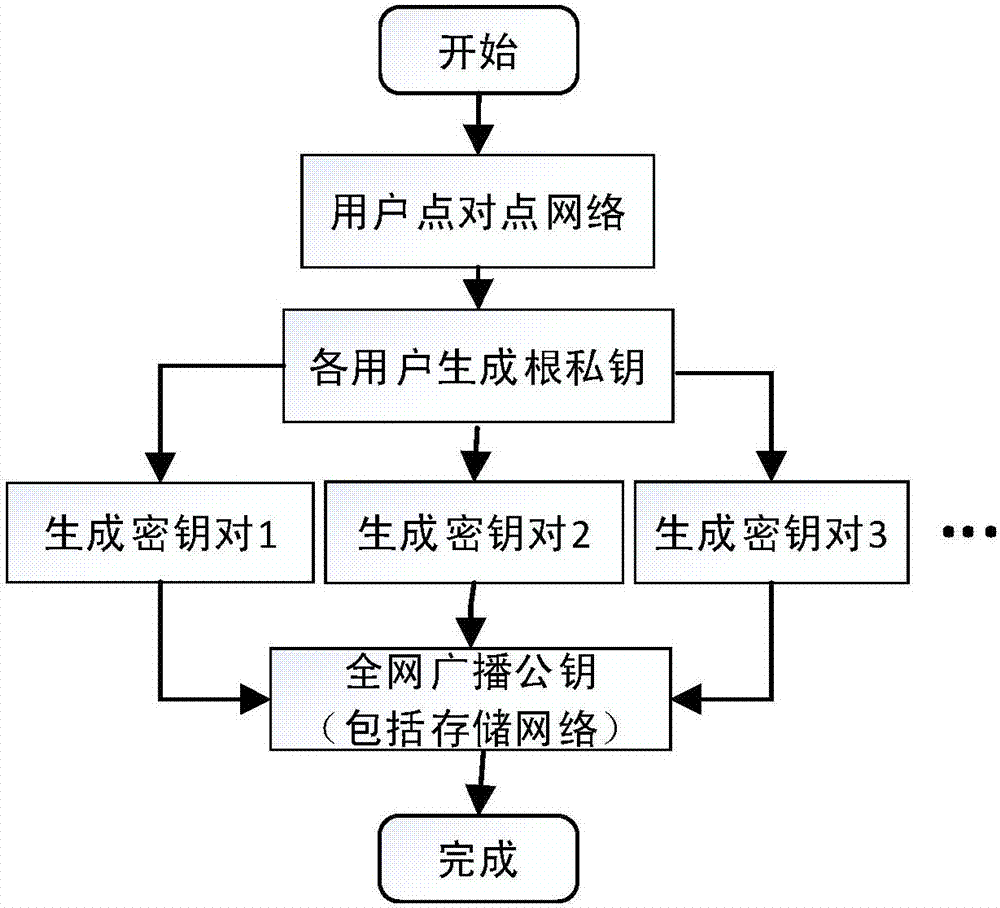
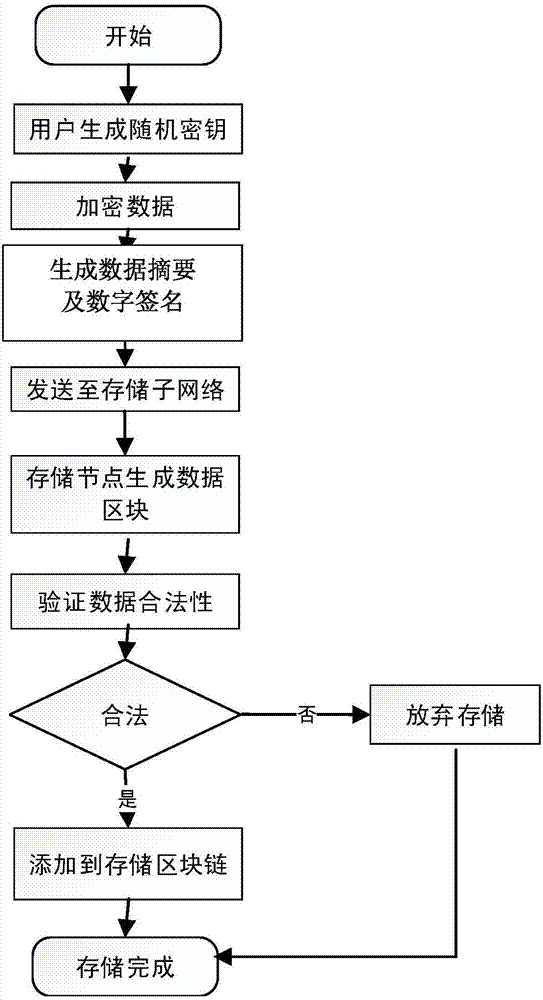
Routing position data secrecy storing and sharing method based on block chain
ActiveCN107181599AGood data protectionSolve workload bottlenecksKey distribution for secure communicationUser identity/authority verificationByzantine fault toleranceOriginal data
Provided is a routing position data secrecy storing and sharing method based on block chains. The routing position data secrecy storing and sharing method includes a data storing method and a data sharing method. The data storing method includes the steps of node configuration, data encryption sending, storage subnetwork verification storing, etc. The data sharing method includes the steps of demand generation, demand response, sharing achievement and the like. The effects of the invention are as follows: through a block chain technology, data sharing is realized through data encryption storage and a decentralized network to solve the problems that data storage parties have no right to use data and users do not have channels to selectively enable personal data to be accessed; local encryption sending is adopted during data storage, service parties store encrypted data, the users themselves save decryption secret keys, and the service parties have no access to original data, so a better data protection effect is achieved; and the block chain technology is adopted during storage, commonly recognized storage is realized through a practical Byzantine fault-tolerant algorithm, workload bottleneck problems of centralized storage are solved, and data is prevented from being tampered.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Chip, data communication method for chip, consumable container and imaging equipment
InactiveCN102231054AImprove reliabilityAvoid crackingElectrographic process apparatusPrintingExternal dataStructure of Management Information
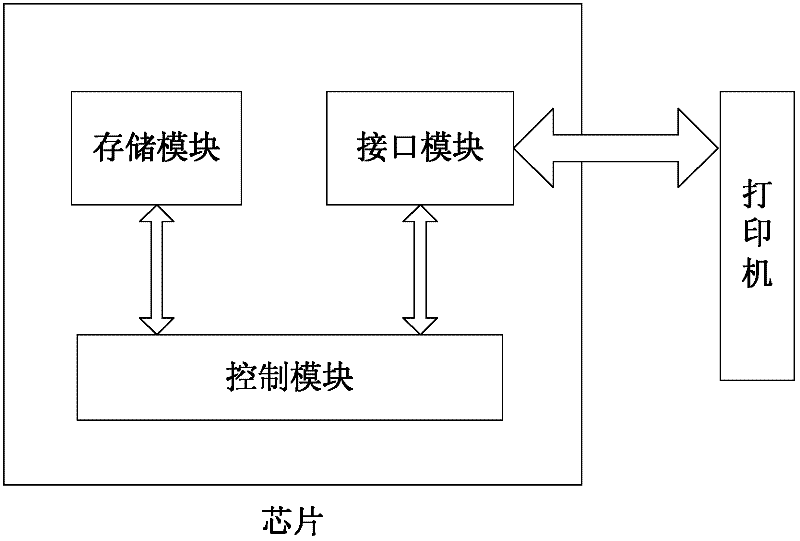
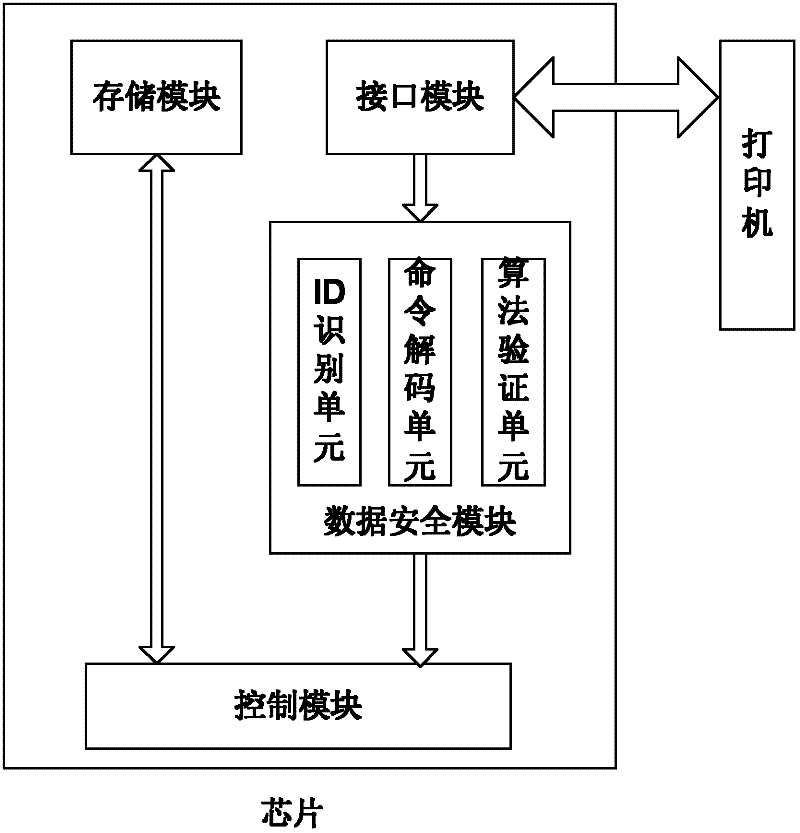
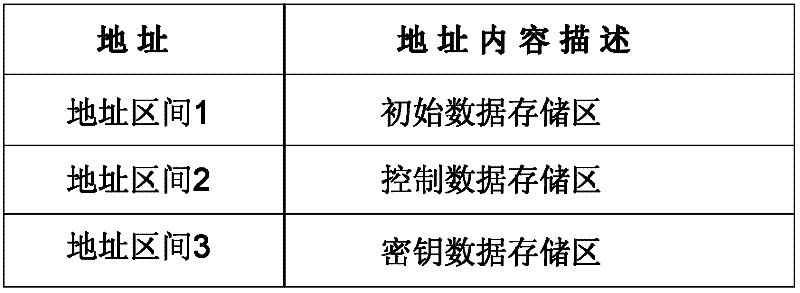
The invention provides a chip of a consumable container, which comprises a storage module, a control module, an interface module and a data safety module. The storage module is used for storing initial data, printing data, control data and key data; the interface module is used for realizing data communication between the storage module and the control module; the data safety module is respectively connected with the interface module and the control module, and is used for identifying a type and a content of data communicated between a printer and the chip, encrypting matched data in a selected safe mode and decrypting the data; the control module is connected with the storage module and is used for controlling data communication between the chip and the printer and the access operation of the data of the storage module and external data and sending a corresponding control command to the chip according to a safety module processing result so as to realize data communication; and the same keys are stored in the printer and the chip. The invention also provides a data communication method for the chip, the consumable container with the chip structure, and imaging equipment with the consumable container. The safety of the communication data of the chip can be protected.
Owner:ZHUHAI TIANWEI TECH DEV CO LTD
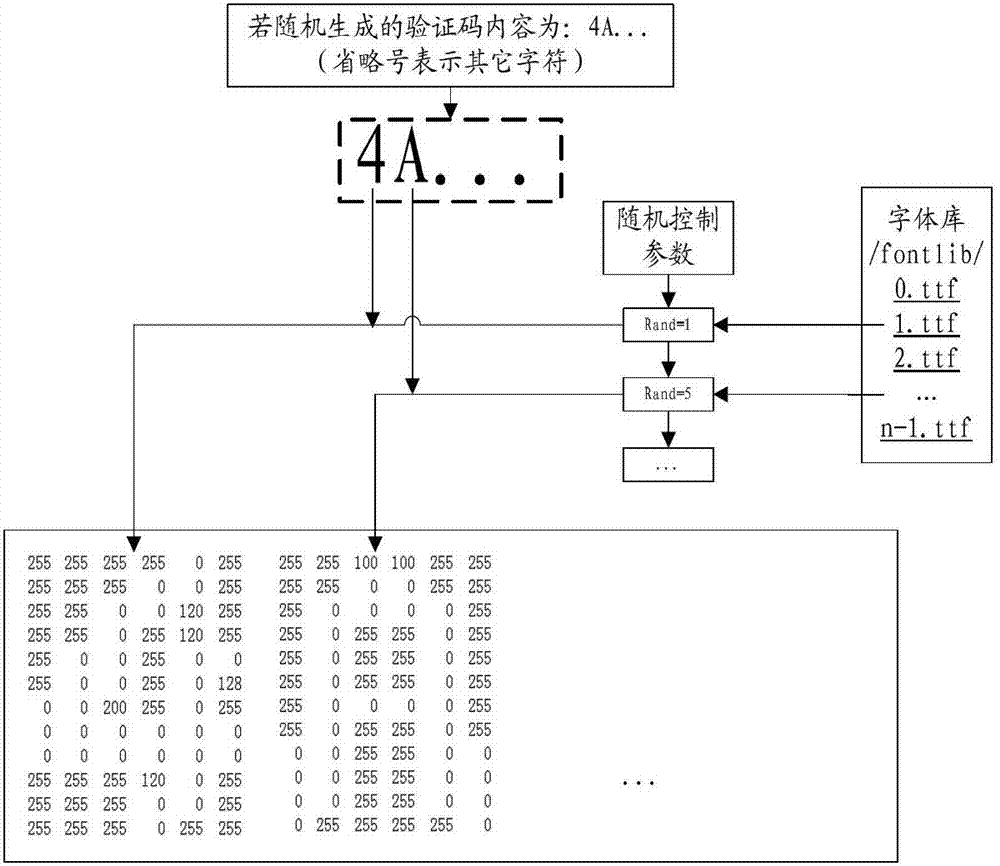
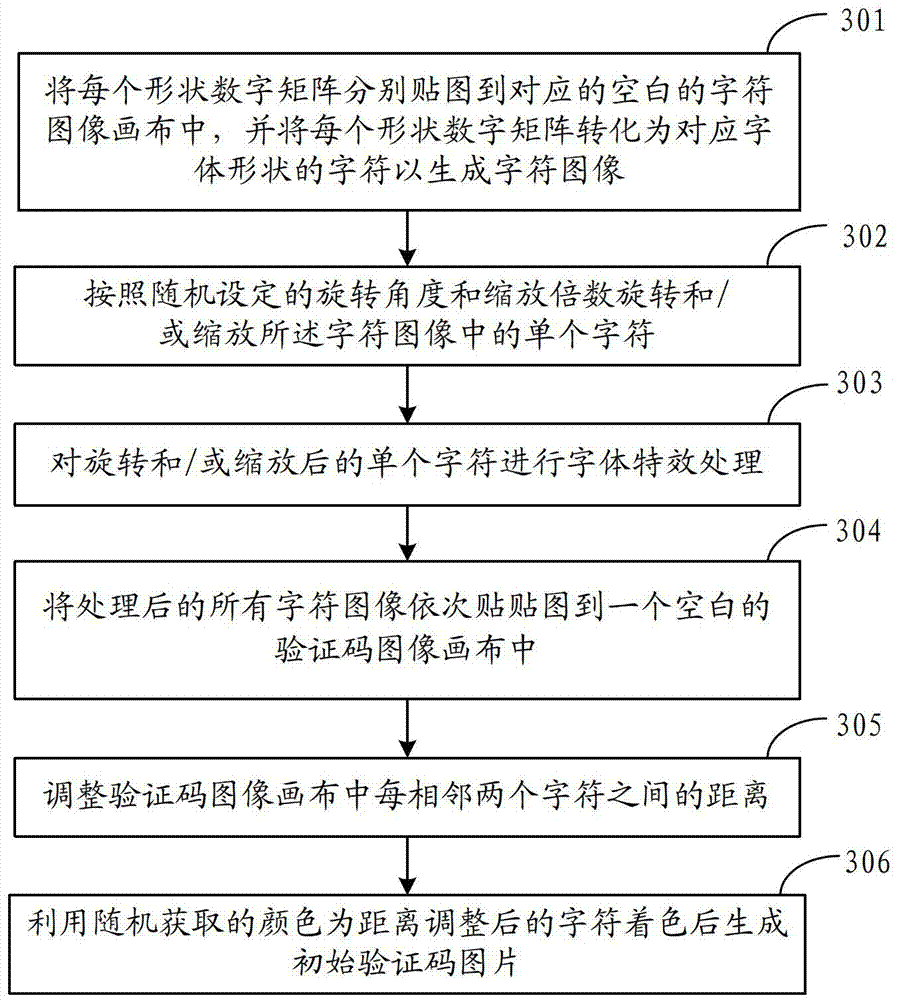
Method and device for implementation of picture verification code
ActiveCN102768754AGood varietyImprove visual experience2D-image generationImage data processing detailsColor changesRandom parameters
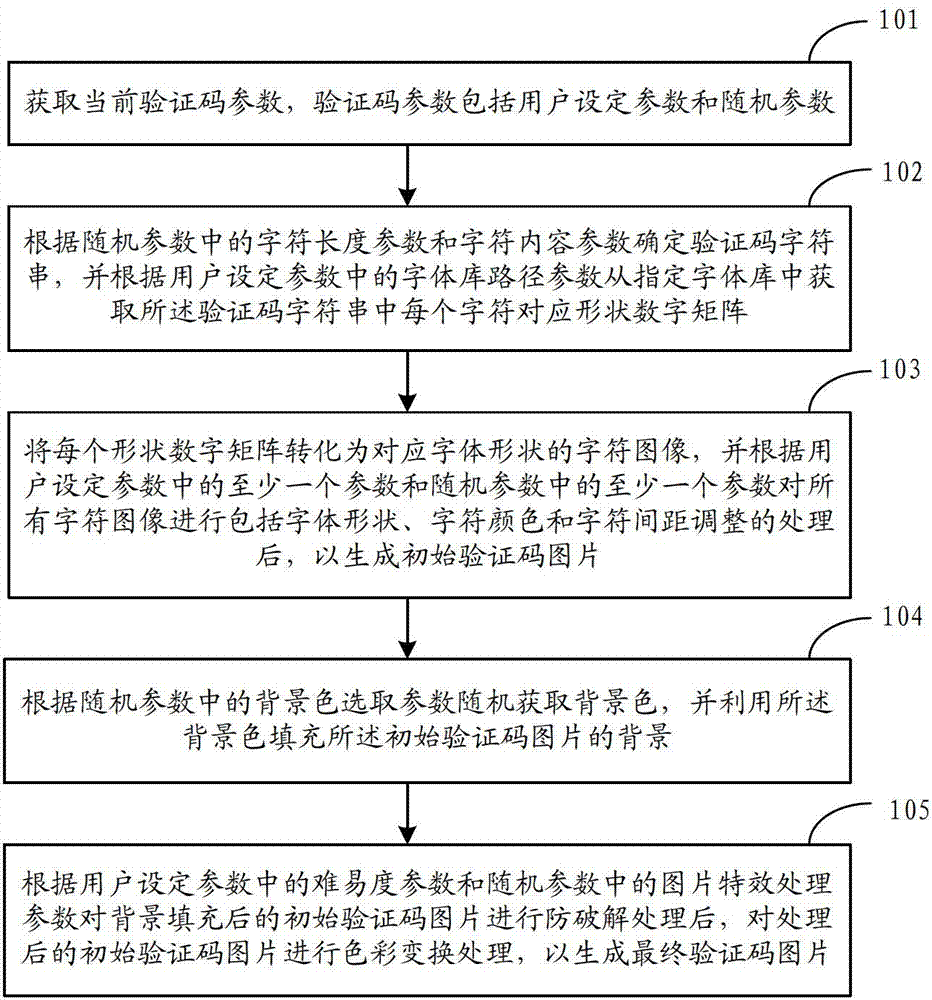
The invention discloses a method for implementation of a picture verification code. The method includes: acquiring current verification code parameters including user setup parameters and random parameters; determining the length and content of a character string of the verification code according to the random parameters, and acquiring a corresponding shape numerical matrix of each character in the character string of the verification code from a designated font object library according to font object library route parameters in the user setup parameters; converting each shape numerical matrix into a character picture of a corresponding character shape, and subjecting all character pictures to character special effect processing according to part of the verification code parameters to generate an initial verification code picture; filling the background of the initial verification code picture with a randomly selected background color; and subjecting the initial verification code picture with the background filled to anti-decoding processing according to difficulty parameters in the user setup parameters and picture special effect processing parameters in the random parameters, and then performing color change processing to generate a final verification code picture. The invention further discloses a device for implementation of the picture verification code.
Owner:杭州网易智企科技有限公司
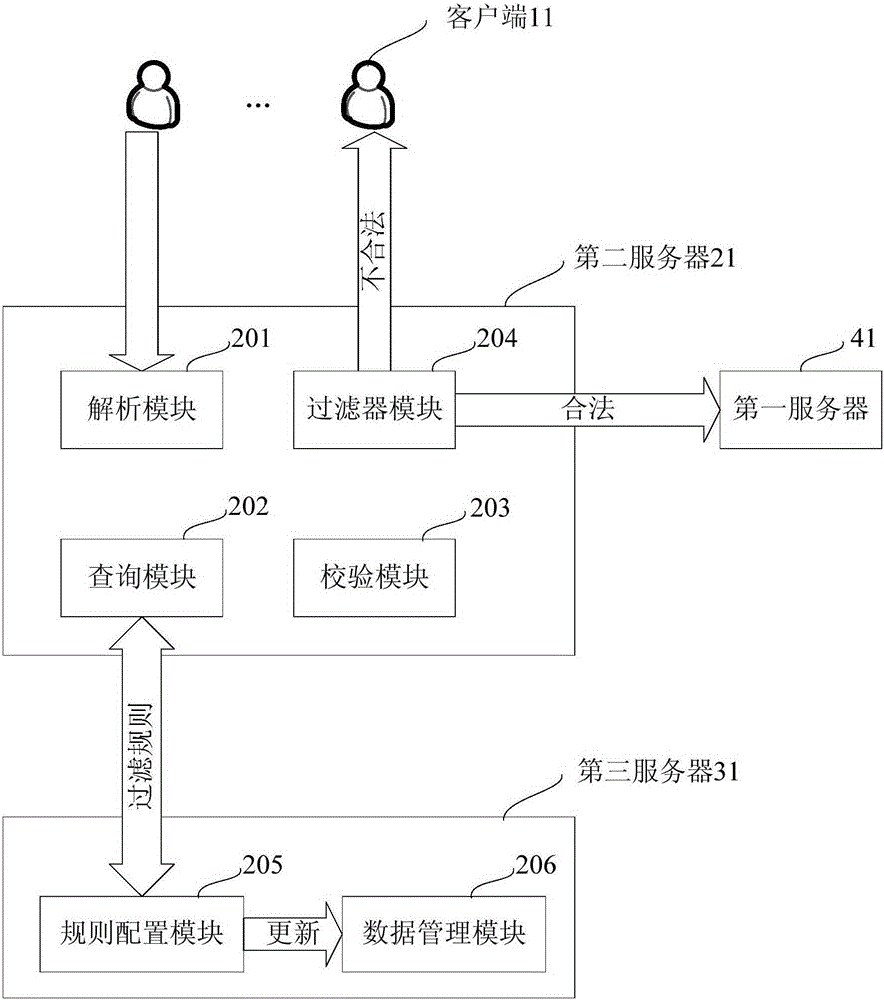
Hostile attack preventing method and network system
InactiveCN105208026AReduce load pressurePrevent malicious attacksTransmissionNetworked systemFiltering rules
The invention discloses a hostile attack preventing method and a network system. The method comprises the steps that a second server receives first data sent by client sides, wherein the first data are connection request data from all the client sides; the second server obtains a filter rule, wherein the filter rule comprises a request address list and a parameter rule; the second server filters the first data through the filter rule, and the first data meeting the filter rule are sent to a first server. The network system comprises at least one client side, the first server and the second server. For illegal requests with request parameter filtering not meeting the rule, error information is directly returned at the second server, the information does not directly enter the first server for parameter legalization verification, the load pressure of the first server can be reduced, and some hostile attacks are prevented.
Owner:NUBIA TECHNOLOGY CO LTD
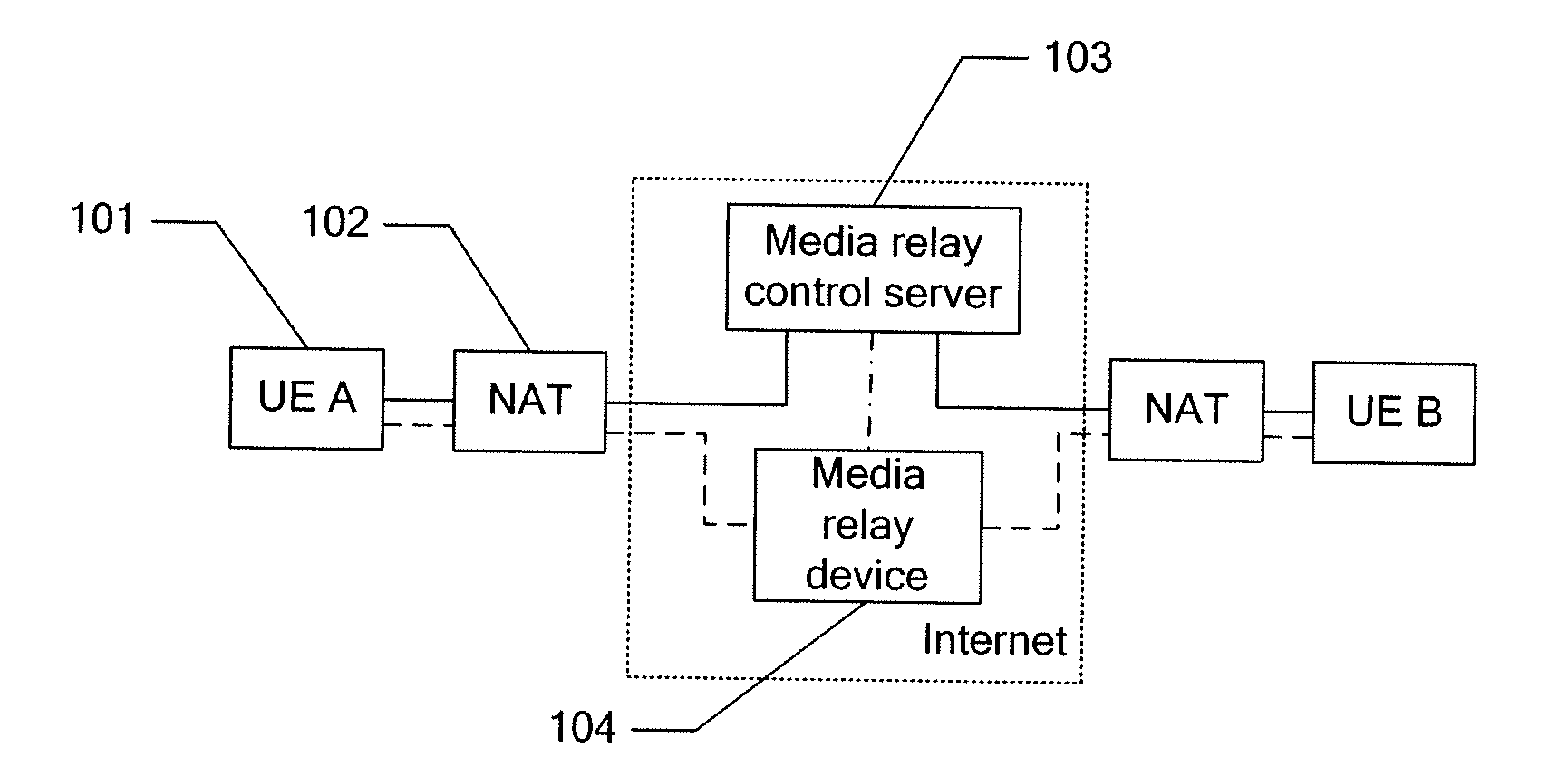
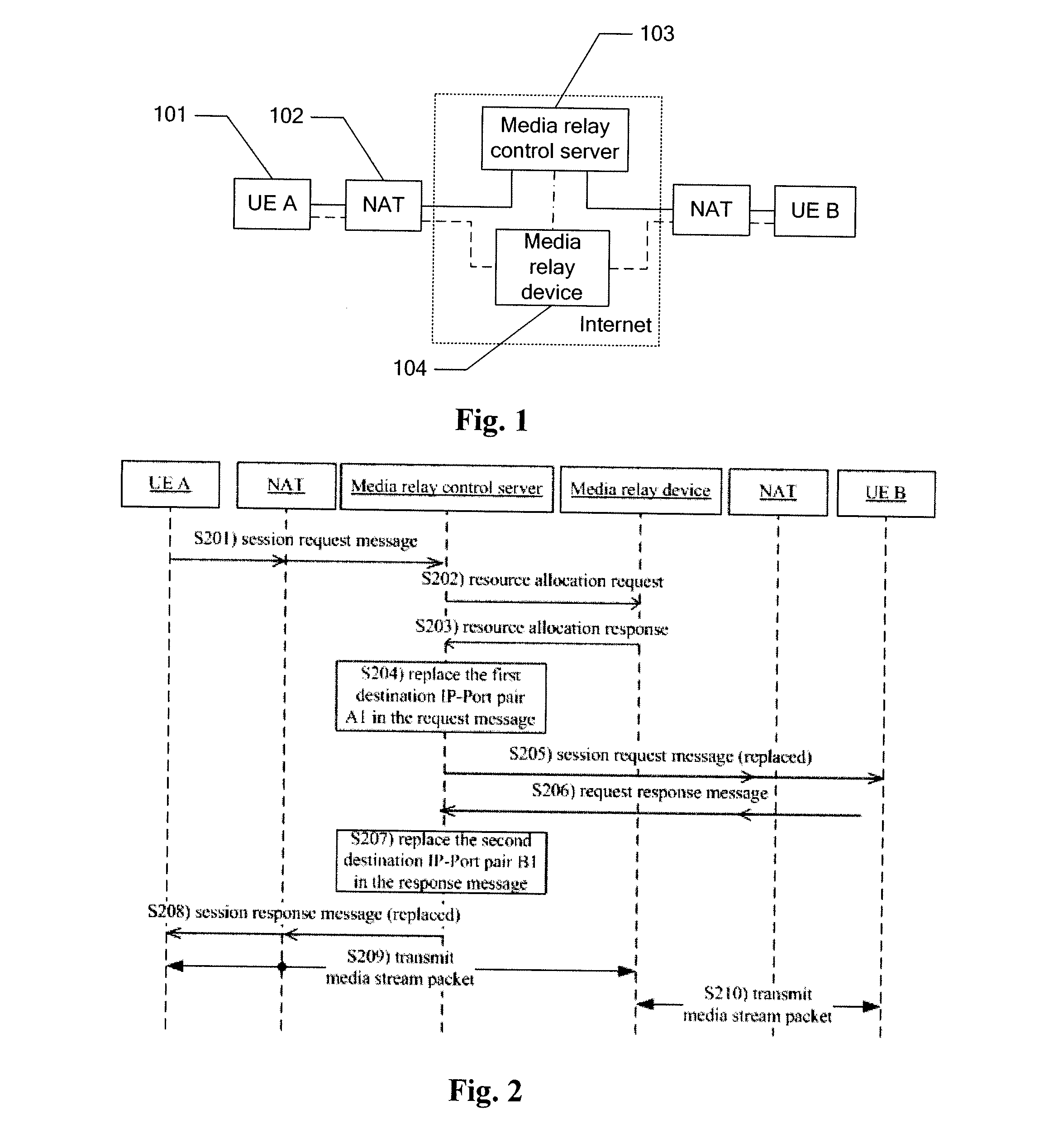
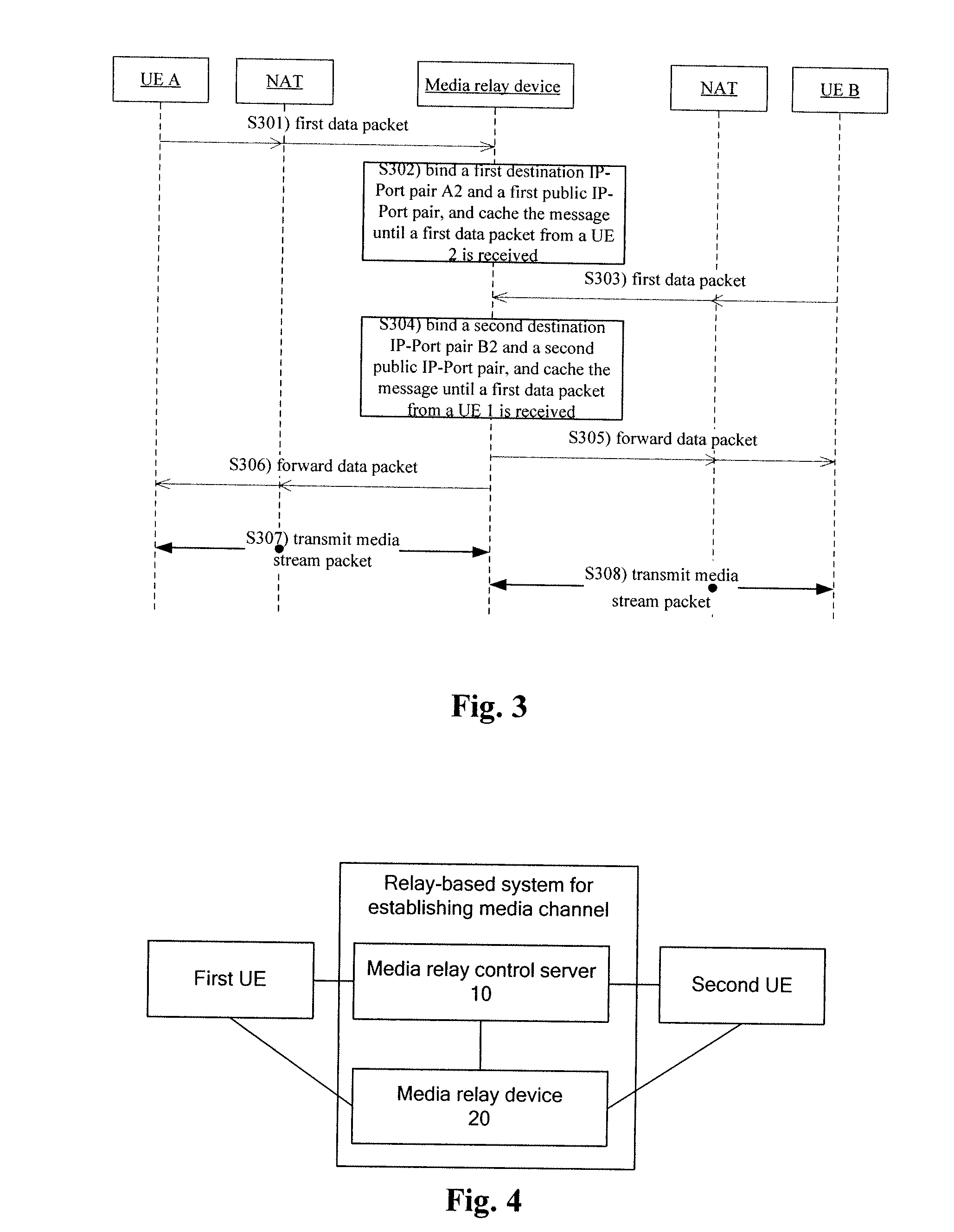
Method and system for establishing media channel based on relay
ActiveUS20130138822A1Prevent malicious attacksConnection securityMultiple digital computer combinationsTransmissionComputer networkServer allocation
The disclosure discloses a method and a system for establishing a media channel based on relay. The method comprises: during a session negotiation process between a first User Equipment (UE) and a second UE, a media relay control server allocating a first service identifier and a second service identifier, transmitting the first service identifier to the first UE, transmitting the second service identifier to the second UE, and transmitting the first service identifier and the second service identifier to a media relay device; the media relay device receiving the service identifiers reported by the first UE and the second UE; the media relay device verifying, according to the first service identifier and the second identifier transmitted by the media relay control server, the service identifiers reported by the first UE and the second UE, and establishing a media channel between the first UE and the second UE if the verification is passed. Through this disclosure, the security of connections between network nodes is improved.
Owner:ZTE CORP
Radio frequency device, radio frequency card reader and related communication system and communication method
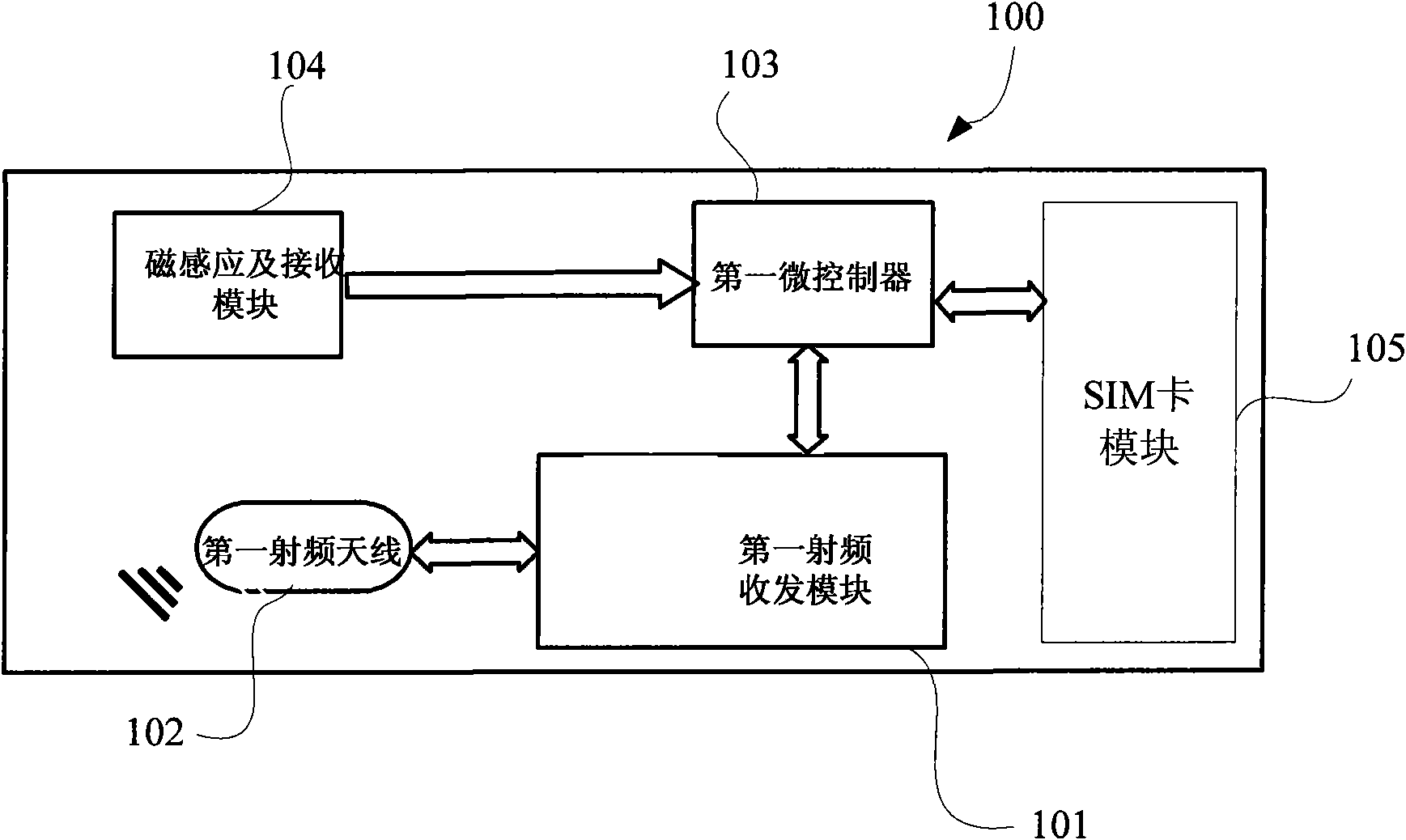
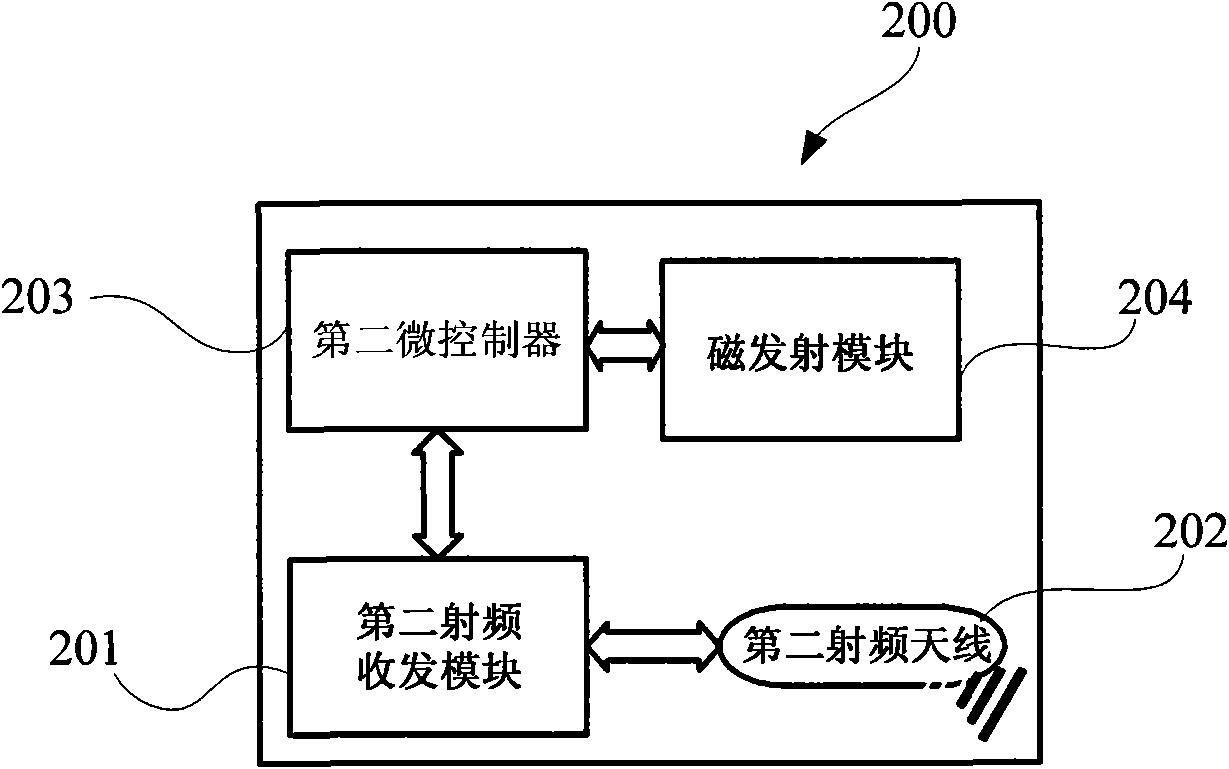
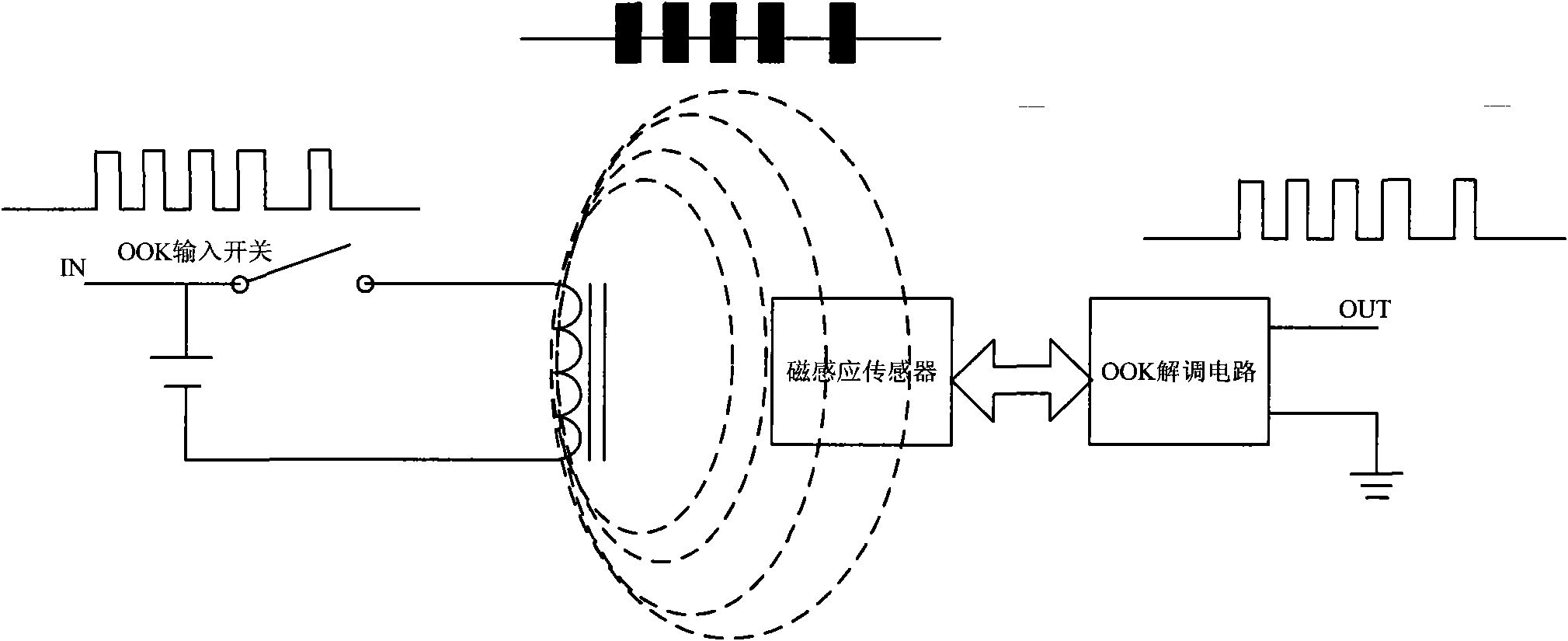
ActiveCN102096836AOvercoming the distance control problemAuthentication is reliableSensing record carriersTransmissionSecure communicationLow speed
The invention relates to the field of radio frequency secure communication and provides a radio frequency device, a radio frequency card reader corresponding to the radio frequency device, and a communication system and a radio frequency secure communication method which use the radio frequency device and the radio frequency card reader. The radio frequency device comprises a radio frequency receiving and transmitting module, a radio frequency antenna and a magnetic induction and receiving module; and the radio frequency card reader comprises a radio frequency receiving and transmitting module, a radio frequency antenna and a magnetic transmitting module. Two communication channels, namely a first low-speed unidirectional communication channel with a stable and controllable distance and asecond high-speed communication channel, with different characteristics are available between the radio frequency device and the radio frequency card reader, wherein the first communication channel is formed by communicating with a magnetic field and is used for transmitting a small data volume of information for identity authentication so as to prevent malicious interference and attack; the second communication channel is formed by using the radio frequency receiving and transmitting module and is used for finishing the identity authentication and a main transaction process; and through the system and the communication method, near field secure communication with a controllable distance can be realized better.
Owner:NATIONZ TECH INC
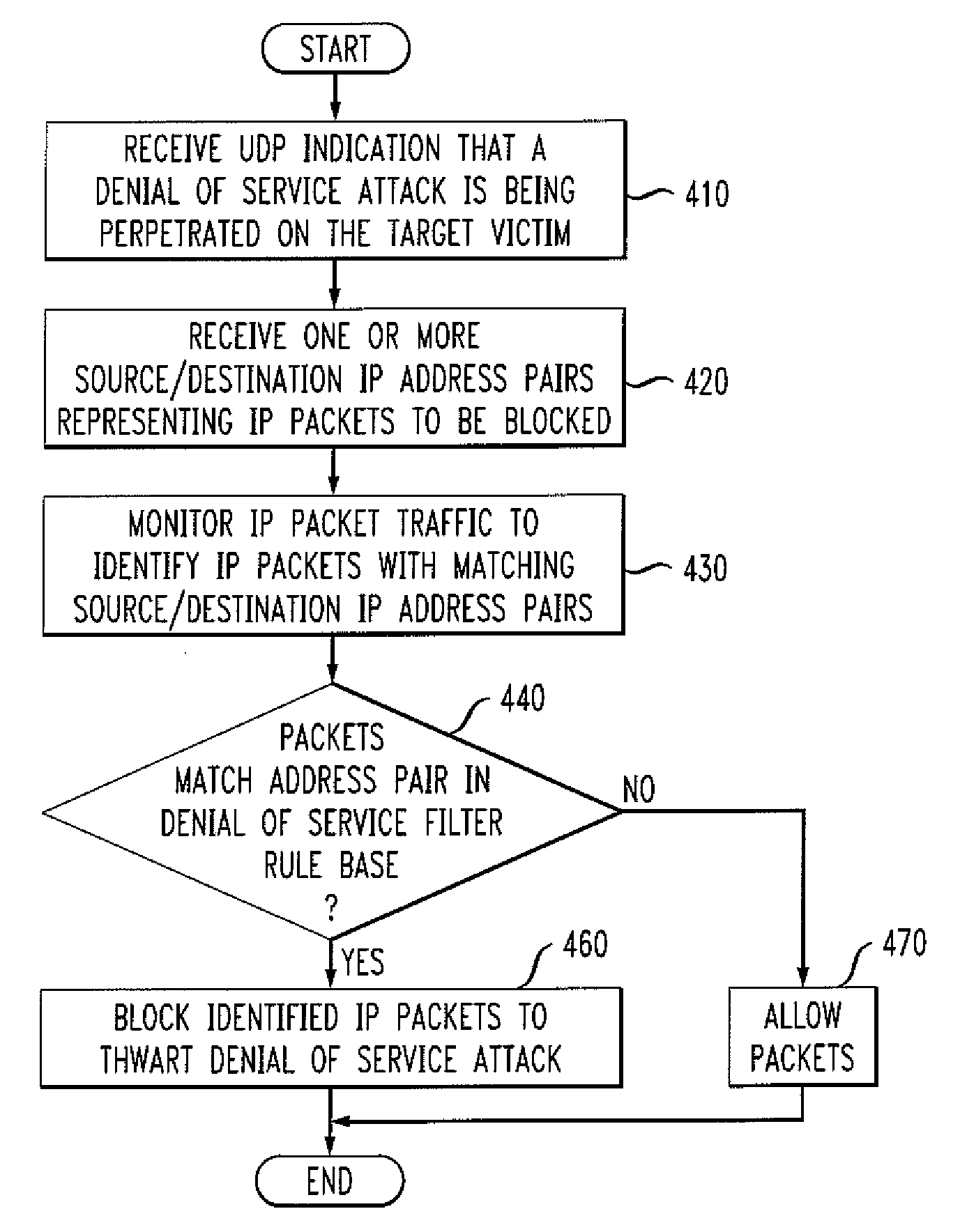
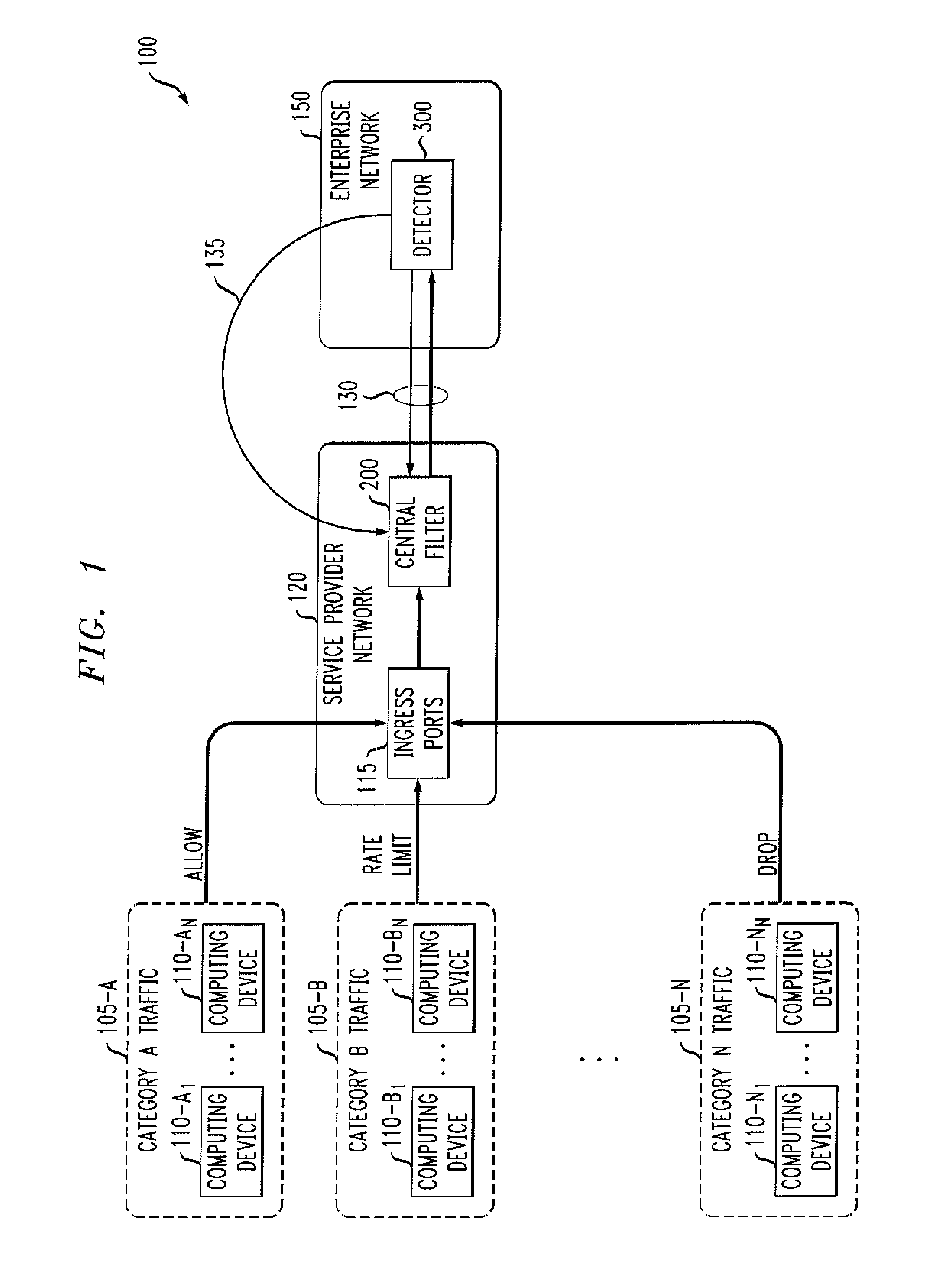
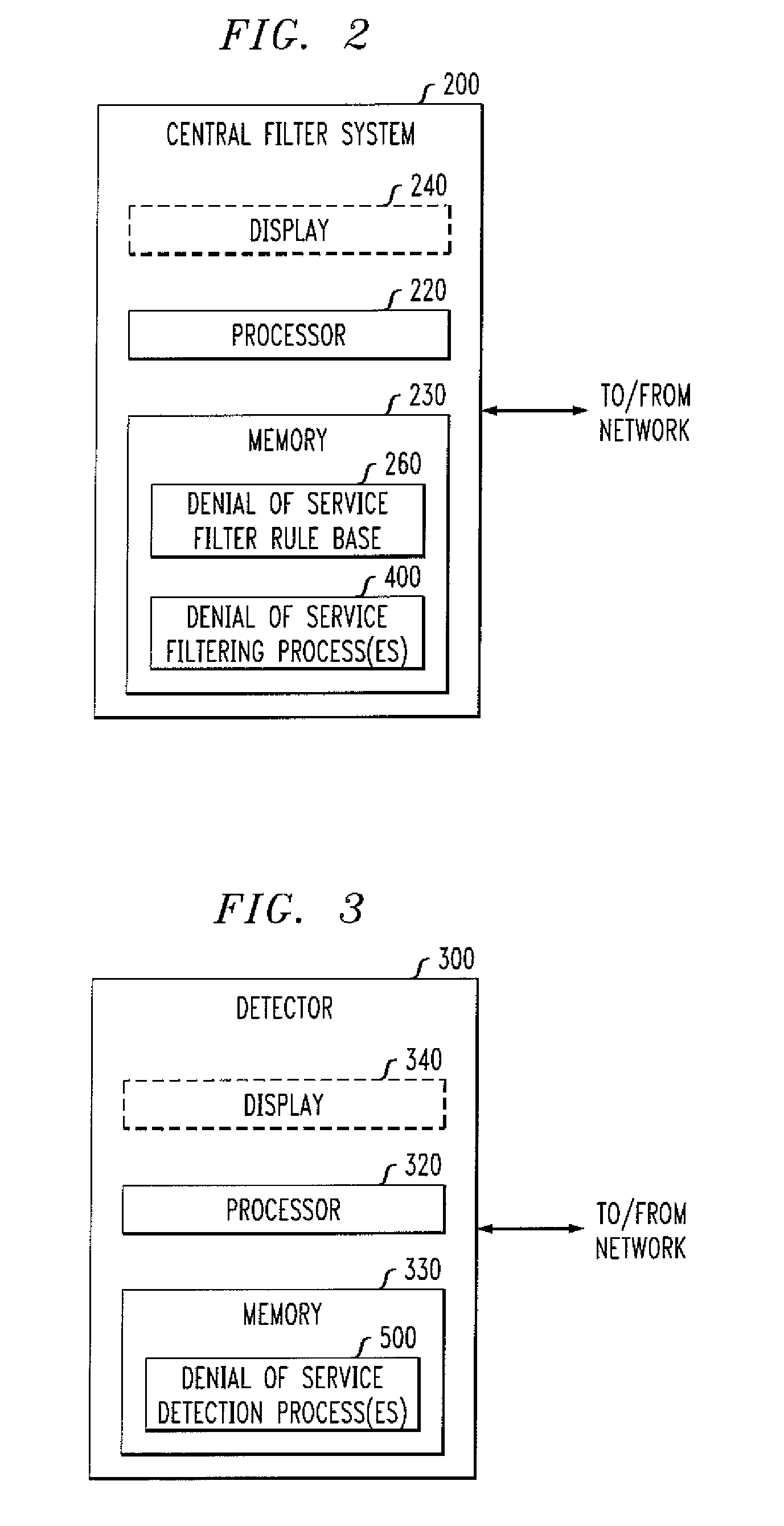
Methods and apparatus for delivering control messages during a malicious attack in one or more packet networks
InactiveUS20080109891A1Prevent malicious attacksData taking preventionMultiple digital computer combinationsIp addressService provision
Methods and apparatus are provided for reliably delivering control messages to a central filter, for example, during a malicious attack, in one or more packet networks without requiring responses or acknowledgements from the central filter to the detector. A detector defends against unwanted traffic by a target victim by determining that unwanted traffic is received by the target victim based on an analysis of packets received from one or more source IP addresses; and transmitting a denunciation message to a central filter associated with a service provider, the denunciation message identifying a source address of at least one source computing device whose transmission of packets to the target victim is to be one or more of limited, dropped or allowed and wherein the denunciation message is transmitted using a Denunciation Protocol that does not require a prompt acknowledgement from the central filter. In addition, the denunciation messages can be sent redundantly to the central filter and are preferably self contained.
Owner:PIECE FUTURE PTE LTD
Dynamic control method for service bandwidth
InactiveCN1842019AImplement dynamic bandwidth controlThe total bandwidth requirement is metData switching networksBroadbandWide band
The invention relates to a business band wide dynamic control method which identifies the business type of the user on the switch device, identifies the data business and the band wide business of the user; it separately identifies the dynamic band wide of the data business and the band wide accession business; when each type business band wide of user or the total business band wide over the allowance threshold value, it controls the band wide of the user. When the business band wide of user or the total business band wide dose not over the allowance threshold value, it can dynamic adjust the band wide allowance of the data business and the accession business.
Owner:HUAWEI TECH CO LTD
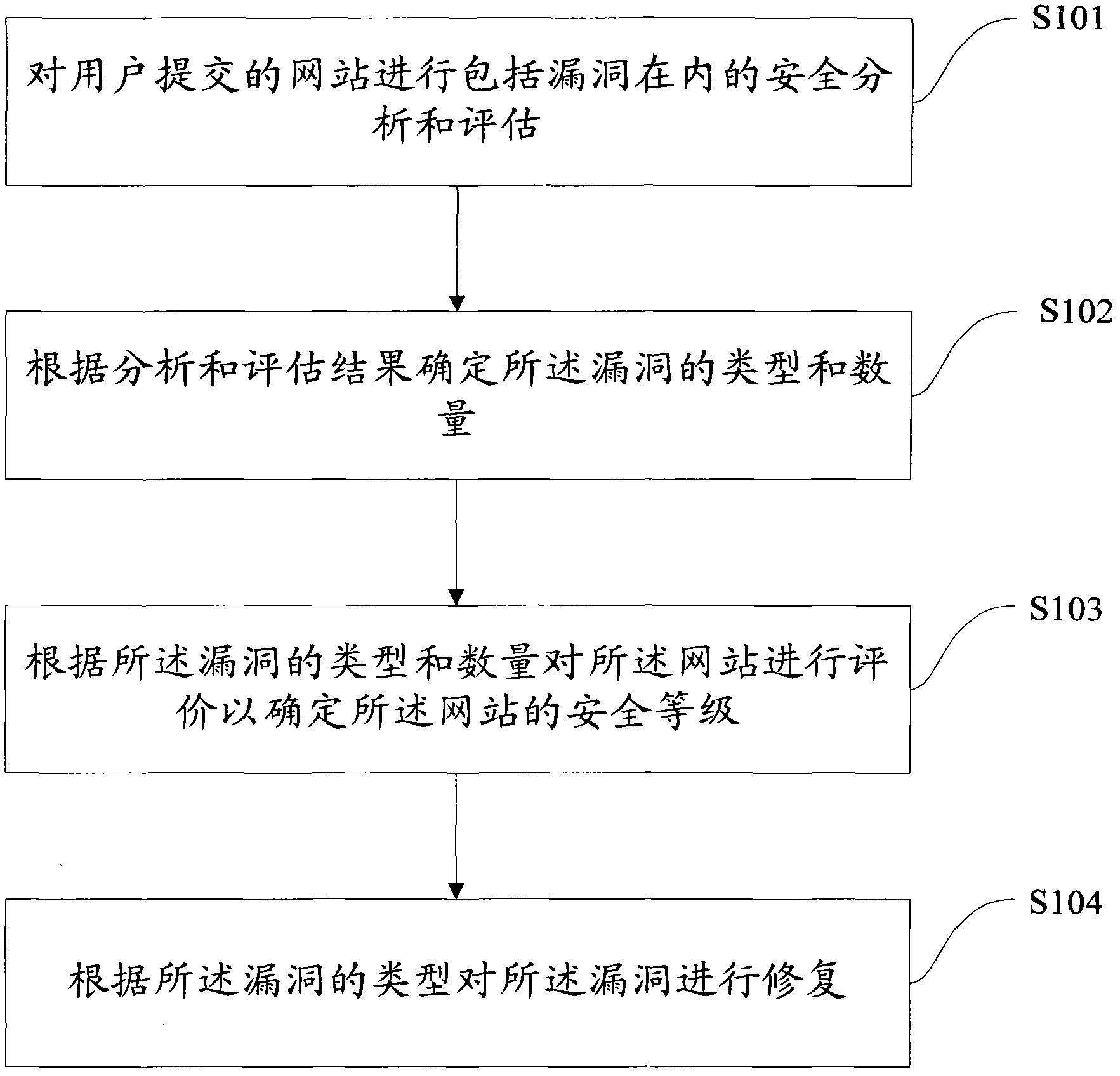
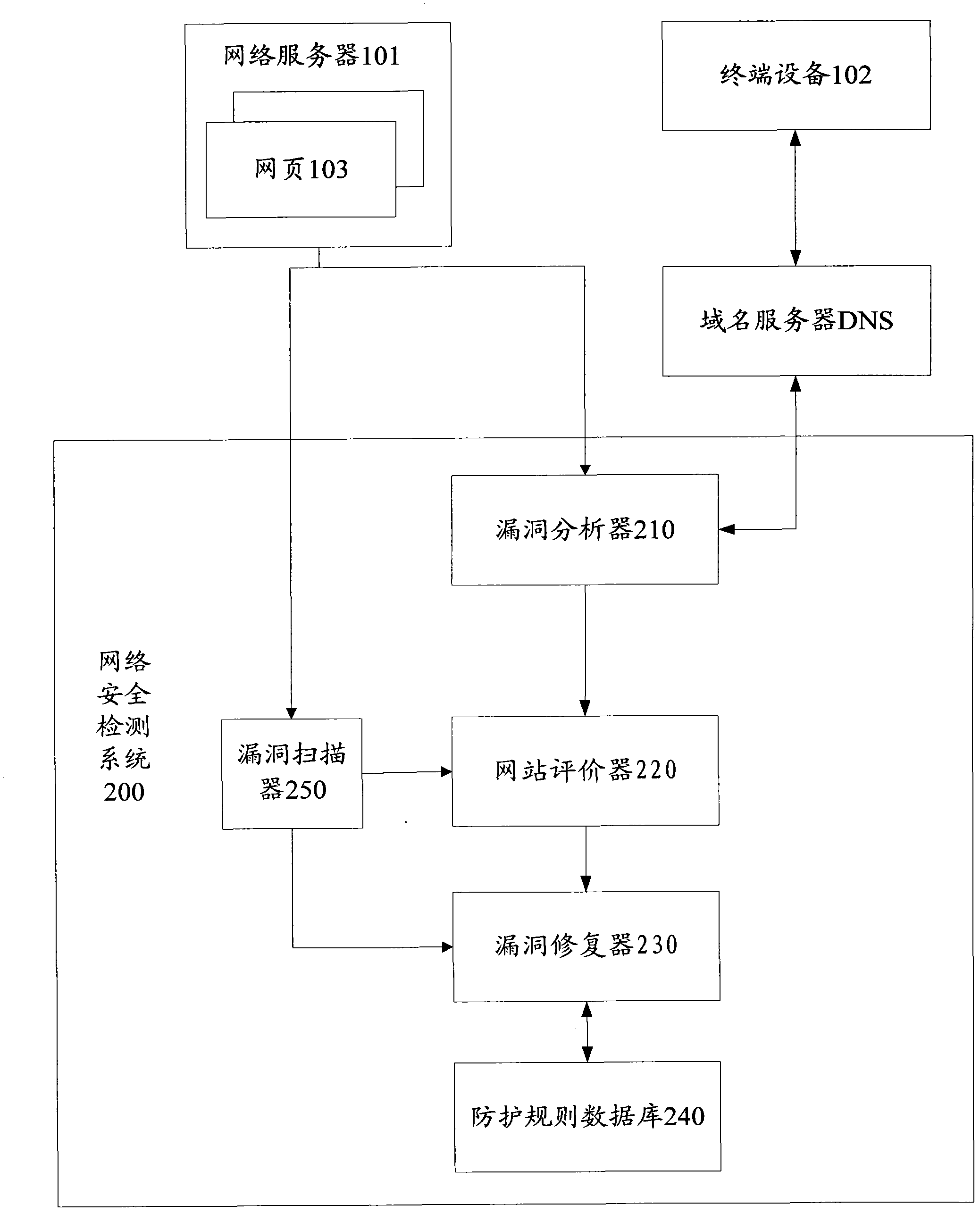
Method and system for detecting network security
InactiveCN102664876AEnsure safetyPrevent malicious attacksData switching networksNetwork security policySecurity analysis
The invention provides a method and a system for detecting network security. The method comprises the following steps: carrying out security analysis and evaluation on a website including the leak, which is submitted by a user; determining the type and quantity of the leak according to the analysis and evaluation results; evaluating the website to determine the security level of the website according to the type and quantity of the leak; and repairing the leak according to the type of the leak. According to the method and the system for detecting the network security, the leak of the website and the security level of the website can be effectively analyzed, and the leak can be repaired online, thereby ensuring the security of the network and avoiding the intrusion of a hacker.
Owner:KUNLUNXIN TECH BEIJING CO LTD
System and Method for Secure Information Handling System Flash Memory Access
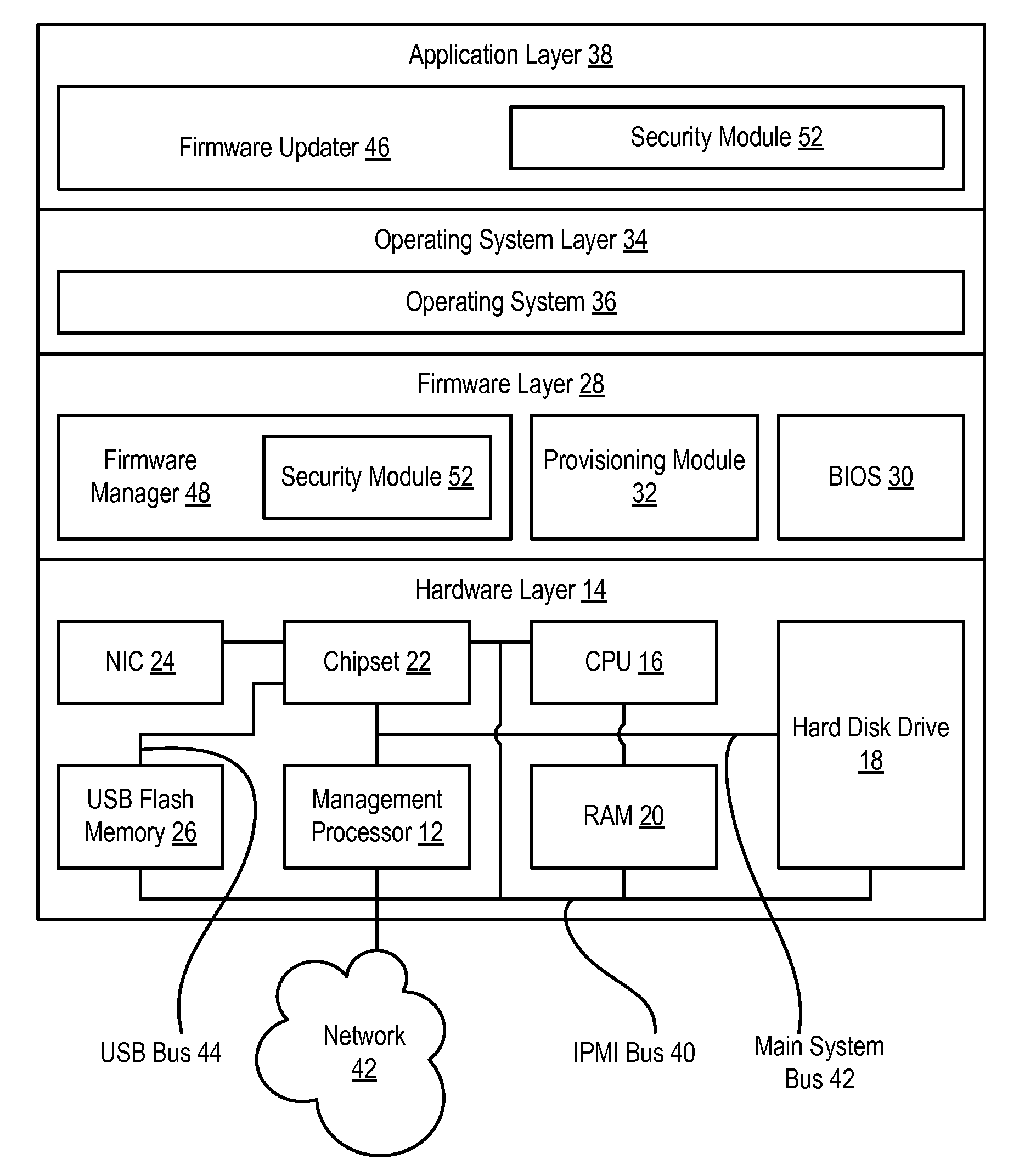
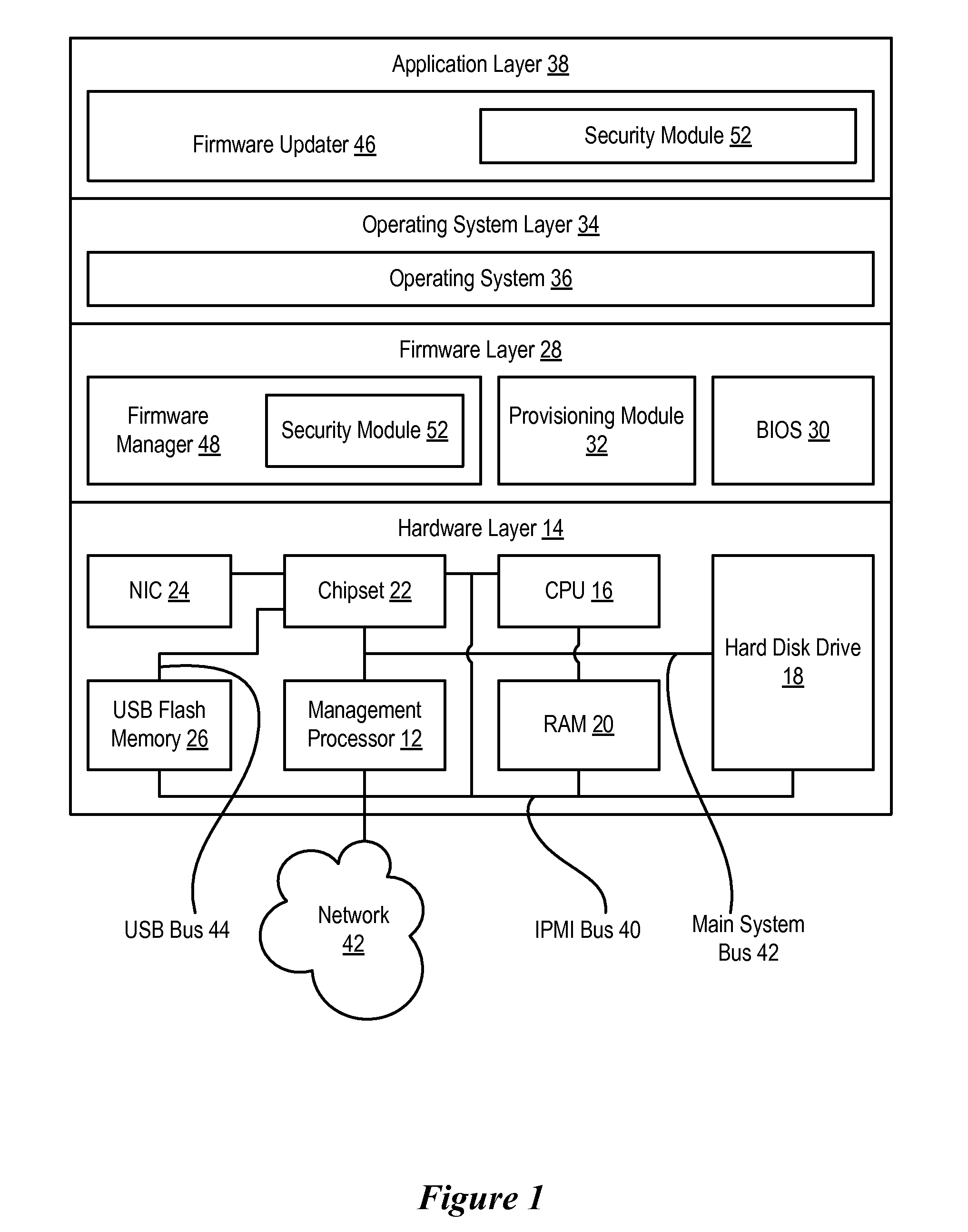
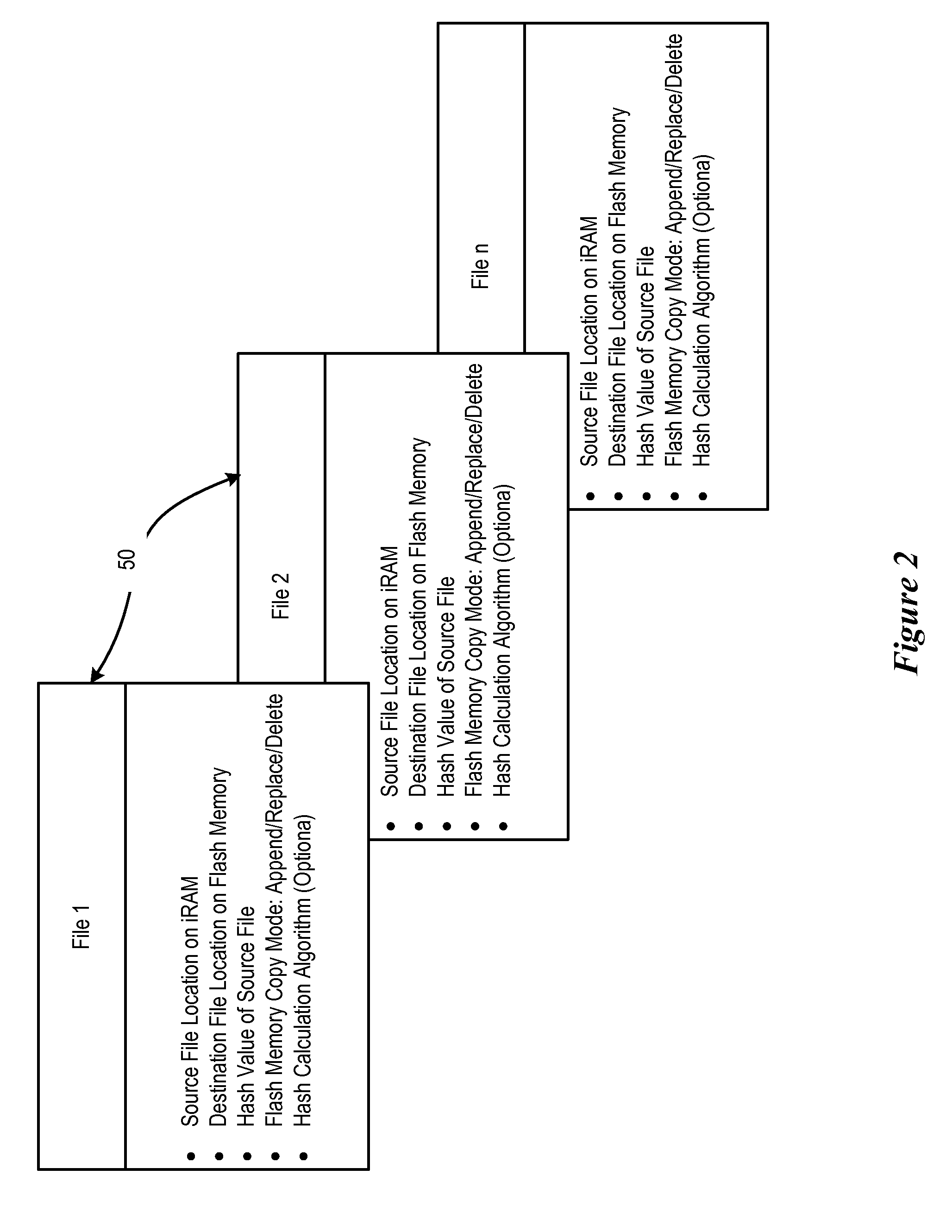
ActiveUS20100058306A1Reduce disadvantagesReduce problemsSoftware engineeringComputer security arrangementsHandling systemApplication software
Firmware updates at an information handling system flash memory device, such as provisioning information stored on a USB device, are securely performed by using a buffer memory and a secured code. An application running on a CPU generates a firmware update and a security code, such as a ciphered hash code based on the firmware update, stores the firmware update and security code in a buffer, and informs a management processor of the update. The management processor analyzes the firmware update to authorize copying of the update from the buffer to the flash memory device. For instance, the management processor creates the security code from the firmware update and compares the created code with the security code stored in the buffer to validate the firmware update.
Owner:DELL PROD LP
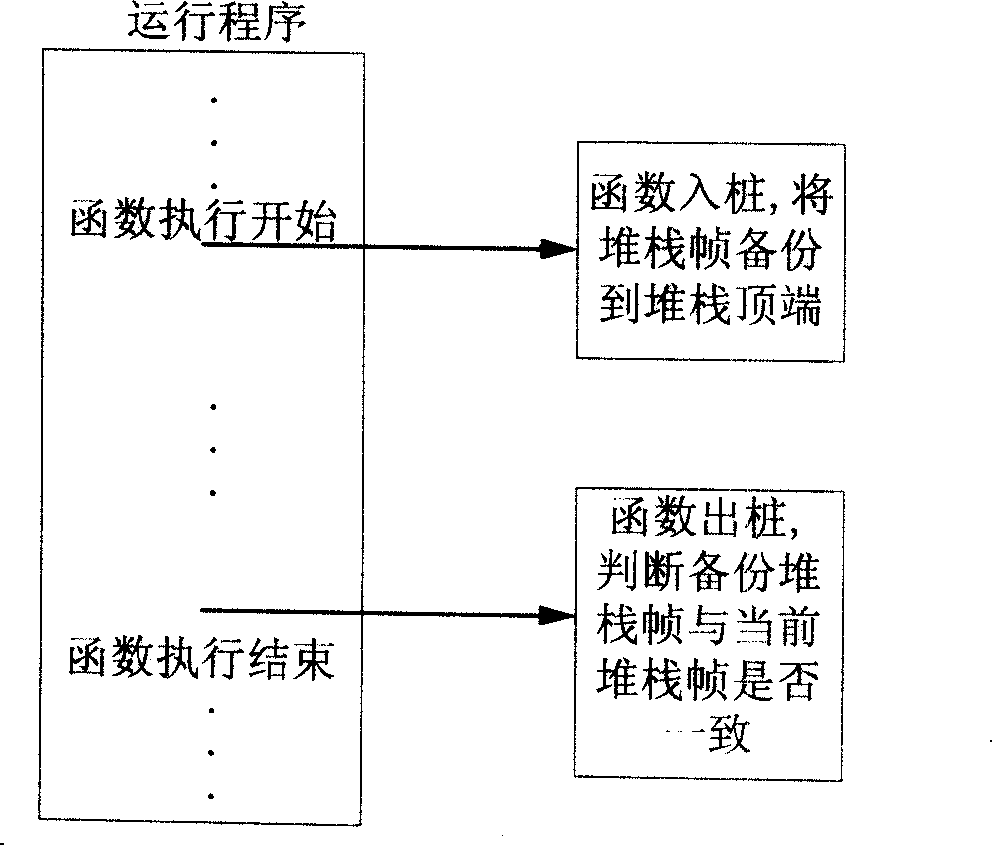
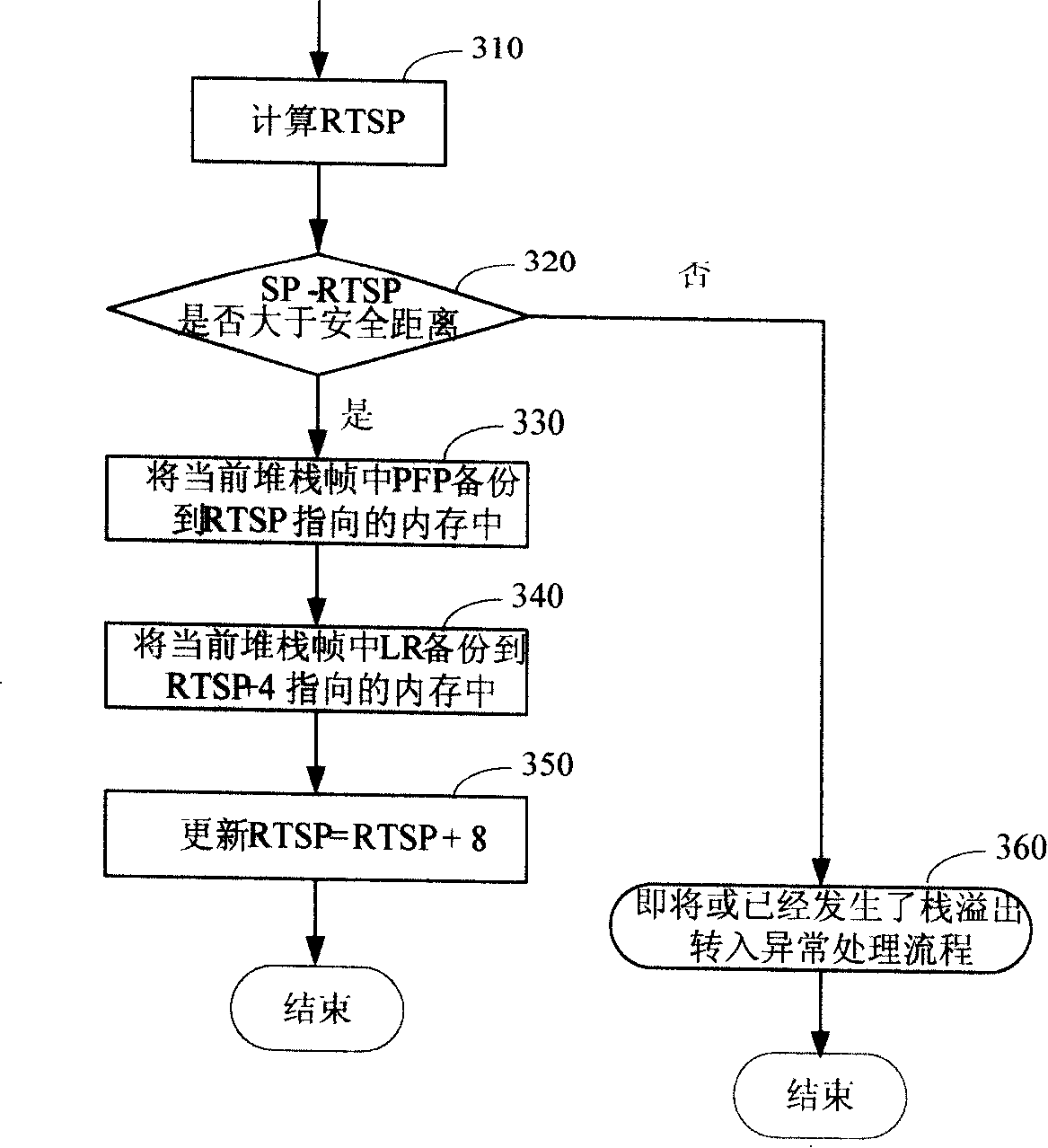
Method for checking stack frame destruction
InactiveCN101241464APrevent malicious attacksAvoid spreadingSoftware testing/debuggingComputer hardware
The present invention provides a method of detecting stack frame damage, when function enters pile, back-up the return address LR, when function exits pile, judging present LR in stack frame whether is identical to the back-up LR, if not identical, the damaged stack frame is detected. The method of the invention can detect damage of stack frame is the first site, and detect program to be or already overflow in the first site.
Owner:STATE GRID BEIJING ELECTRIC POWER +1
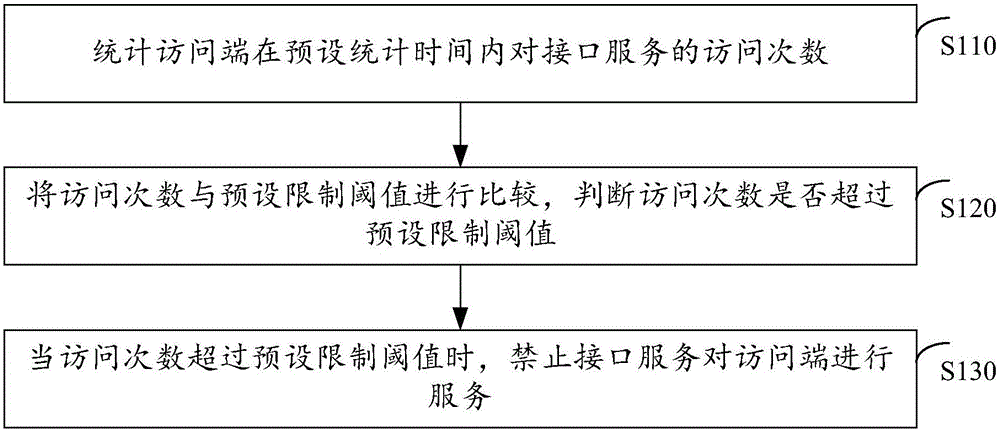
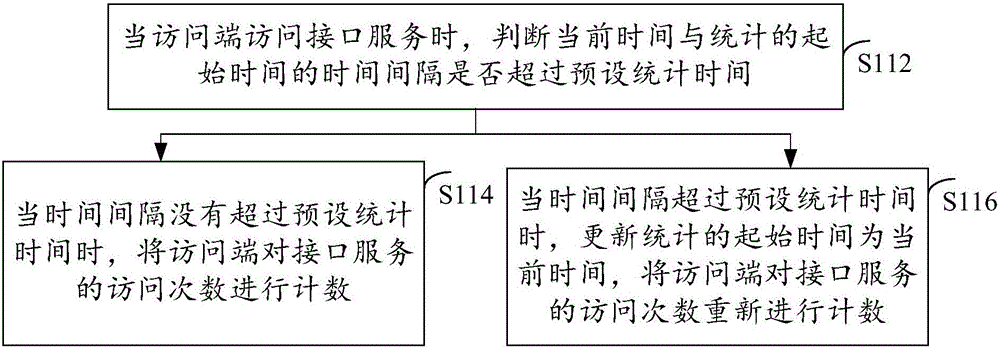
Method and device for preventing malicious attacks to interface service
The invention discloses a method and device for preventing malicious attacks to an interface service. The method comprises the following steps: performing statistics to obtain the access times of an access end accessing the interface service within preset statistics time; comparing the access times with a preset limit threshold, and judging whether or not the access times exceed the preset limit threshold; and when the access times exceed the preset limit threshold, forbidding the interface service to serve for the access end. Through adoption of the method and device, the problem of failure in providing normal services for a user due to interface service paralysis caused by malicious attacks of malicious programs in a network to the interface service is solved. The beneficial effects of detecting the malicious attacks to the interface service and preventing the malicious programs in the network from making malicious attacks to the interface service are achieved.
Owner:BEIJING QIHOO TECH CO LTD +1
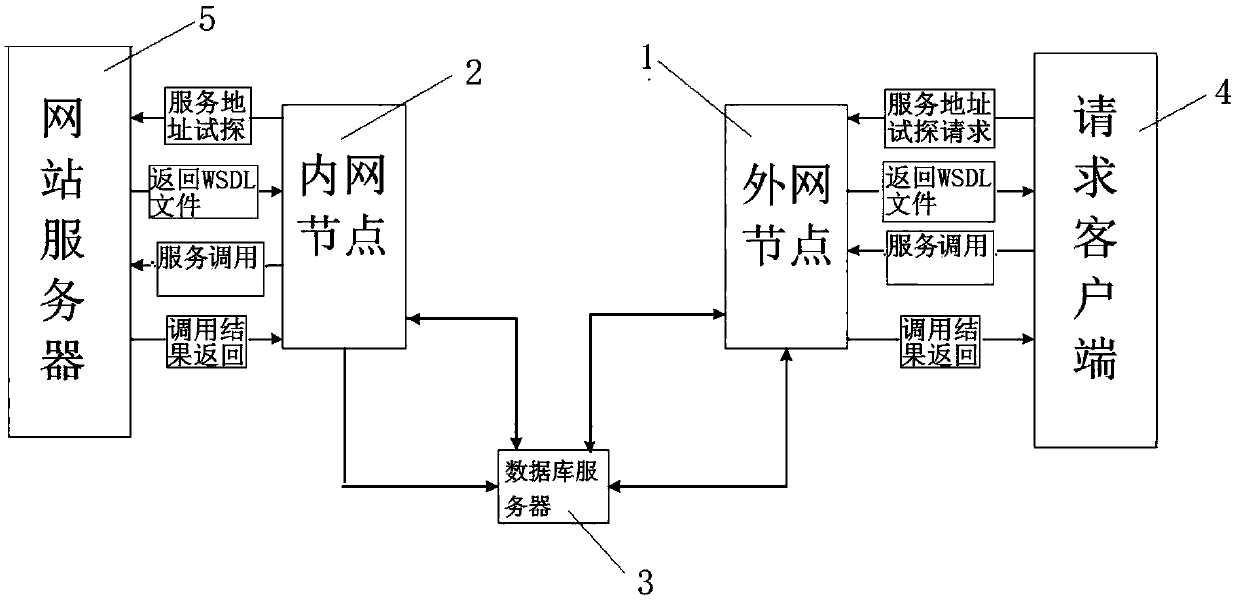
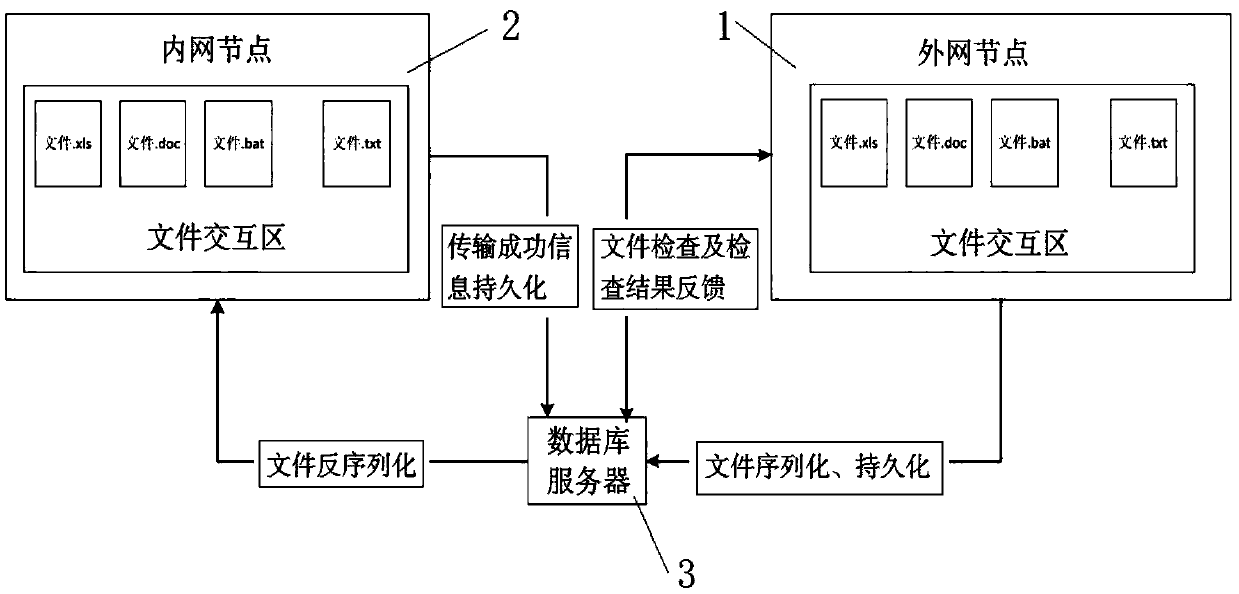
Service interaction platform system based on internal and external network isolation
The invention discloses a service interaction platform system based on internal and external network isolation. The system comprises an external network node and an internal network node, the externalnetwork node and the internal network node are connected with a database server, and the internal network node and the external network node operate a database in the database server for data interaction; the external network node in communication connection with a request client through an information external network, and the internal network node in communication connection with a website server through an information intranet; the request client accesses the website server through adoption of the isolated interaction method; and all the accesses of the request client employ the external network node to receive information, the external network node sends the access information to the internal network node which is used to replace the request client to access the website server and send the return information of the website server to the external network node, and finally, the external network node sends the return information to the terminal. The process can effectively isolate the terminal from the intranet website server for direct access and can perform filter for the access data so as to improve the information safety level.
Owner:DALIAN POWER SUPPLY COMPANY STATE GRID LIAONING ELECTRIC POWER +1
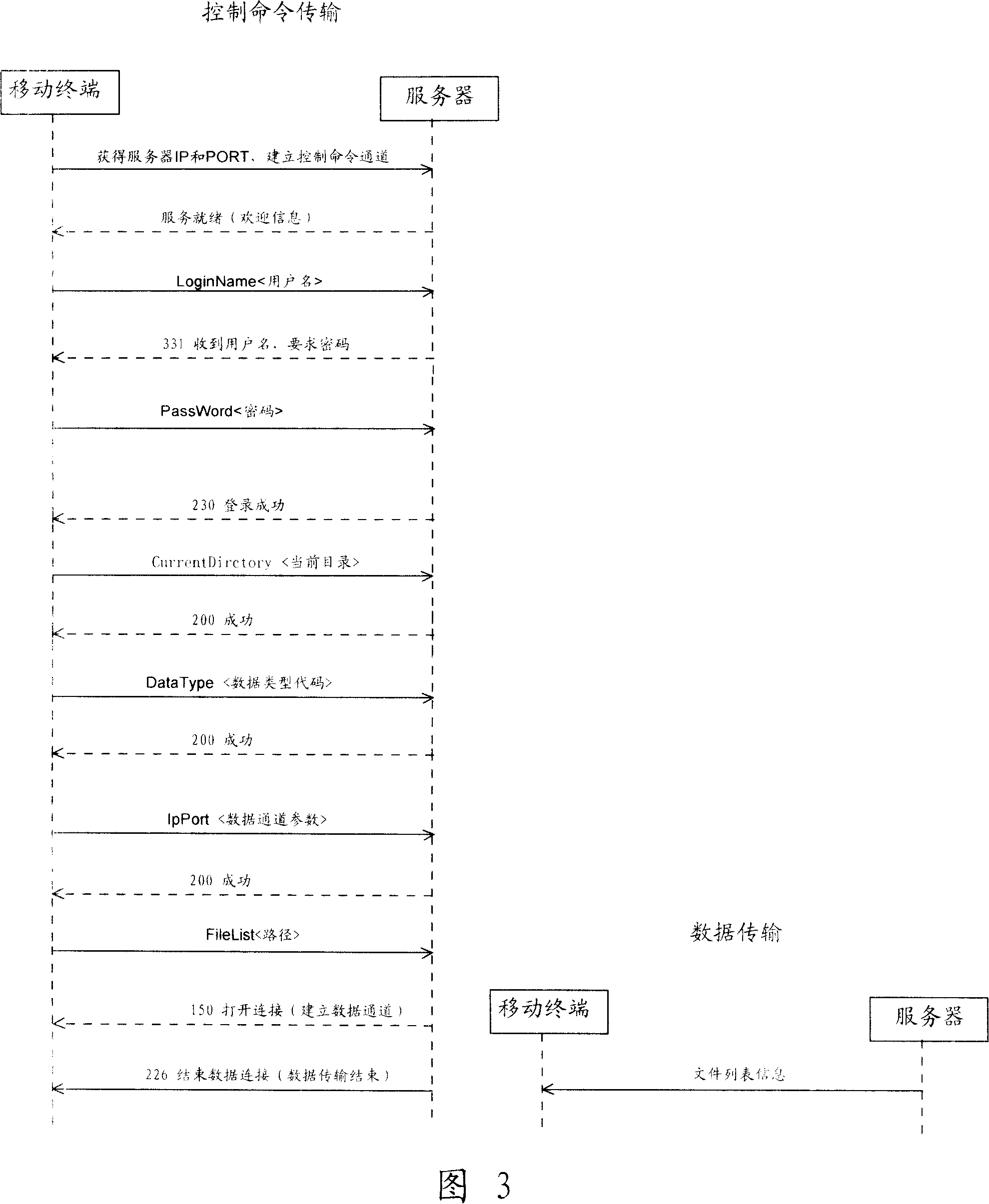
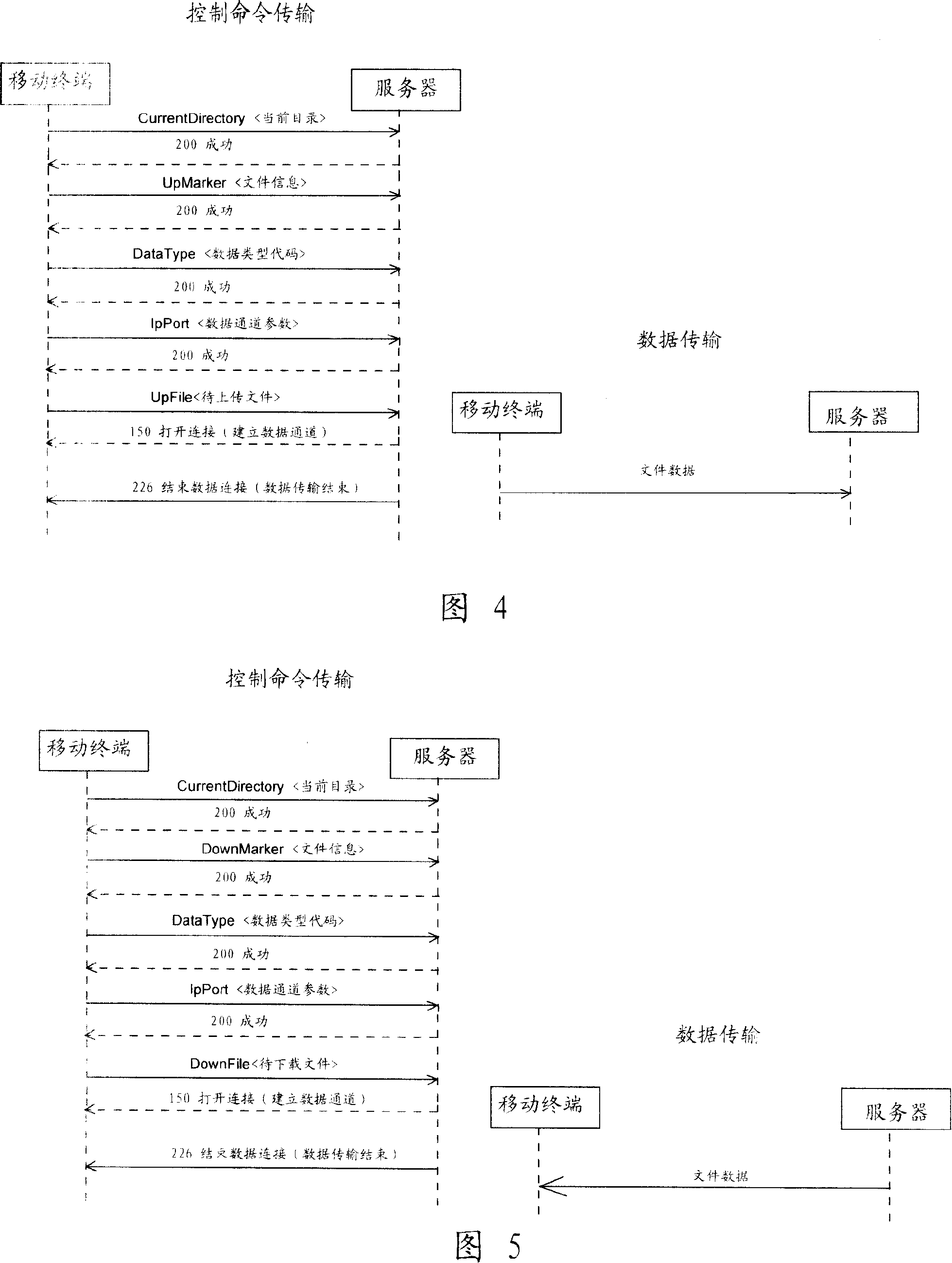
File transferring method for wireless network hard disk system
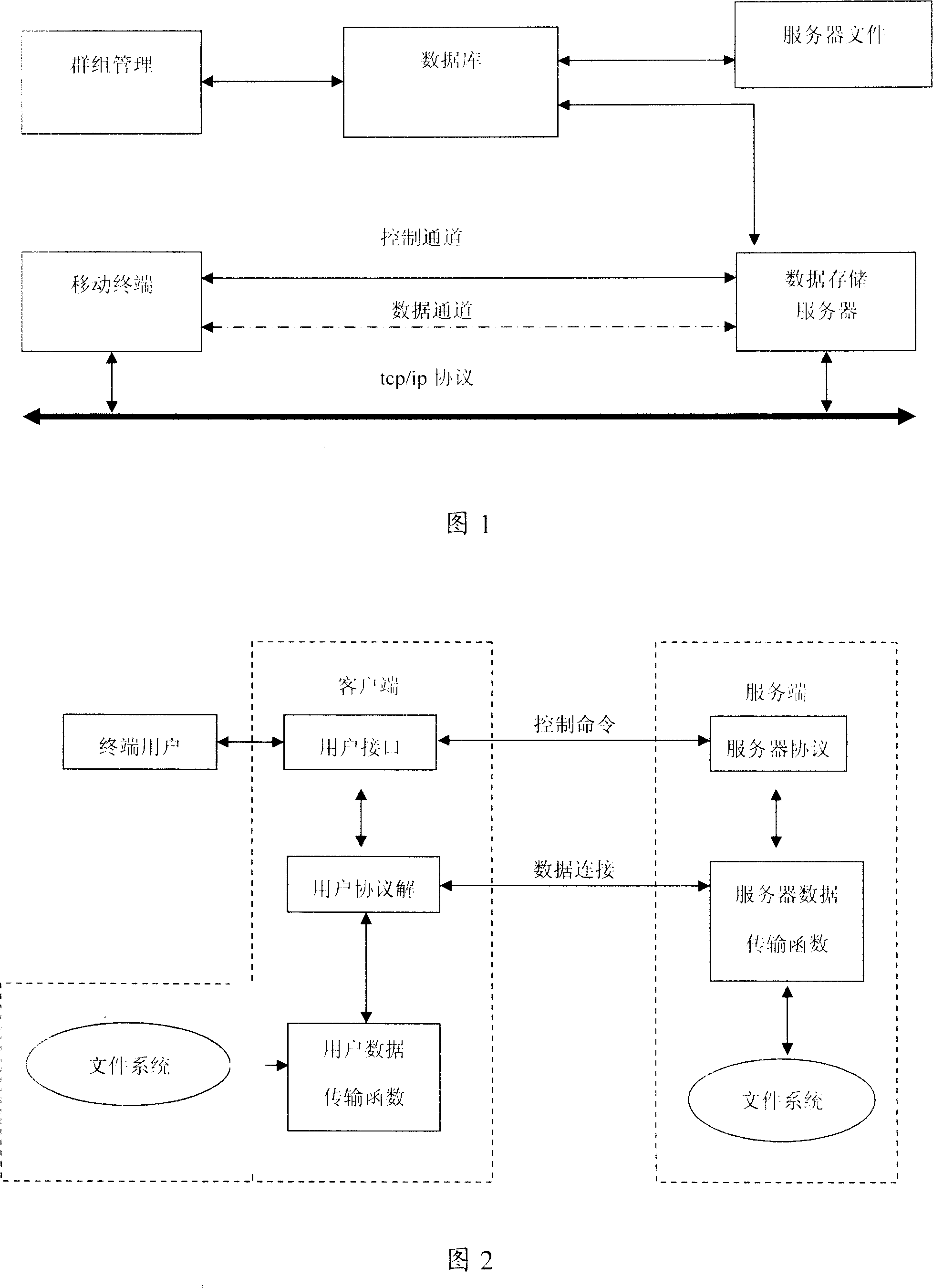
InactiveCN101110656AImplement breakpoint resume functionSave download timeTime-division multiplexRadio/inductive link selection arrangementsPasswordStructure of Management Information
The present invention relates to a file transfer method of a wireless network hard disk system. The wireless network hard disk system comprises a mobile terminal and a data memory server to realize communication with the mobile terminal through a mobile communication network. The file transfer method includes procedures below: A control channel is created between the mobile terminal and the data memory server. The mobile terminal sends a username and a password to the data memory sever to log in the data memory server. Moreover, the mobile terminal or the data memory server sends information of a preset file to a target end and then transfers the preset file in a position corresponding to break-point information returned by the target end. Based on the structure and procedures below, the present invention realizes a function of file transfer resuming at break-points, thus saving file download time, reducing occupied network resource and increasing network communication efficiency.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
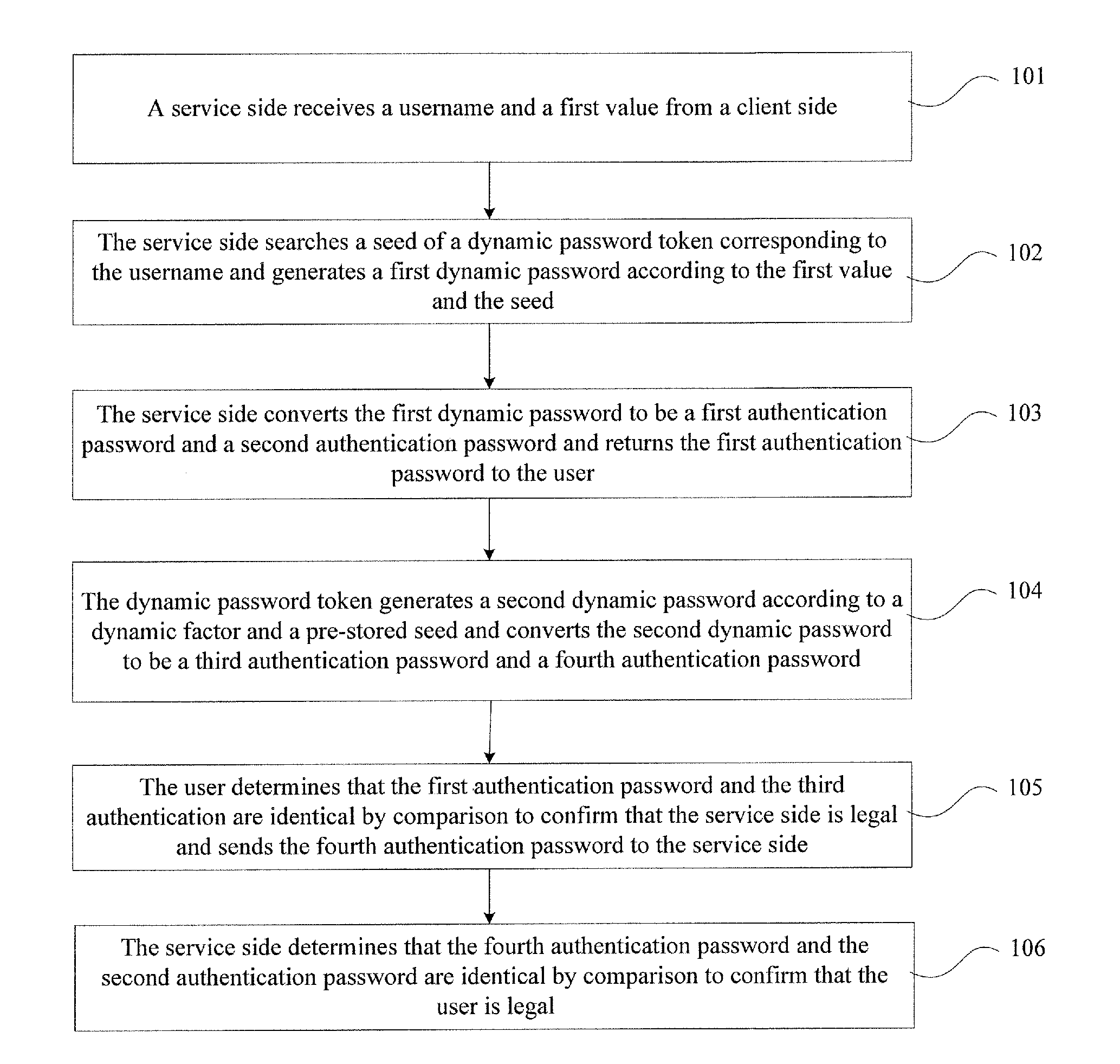
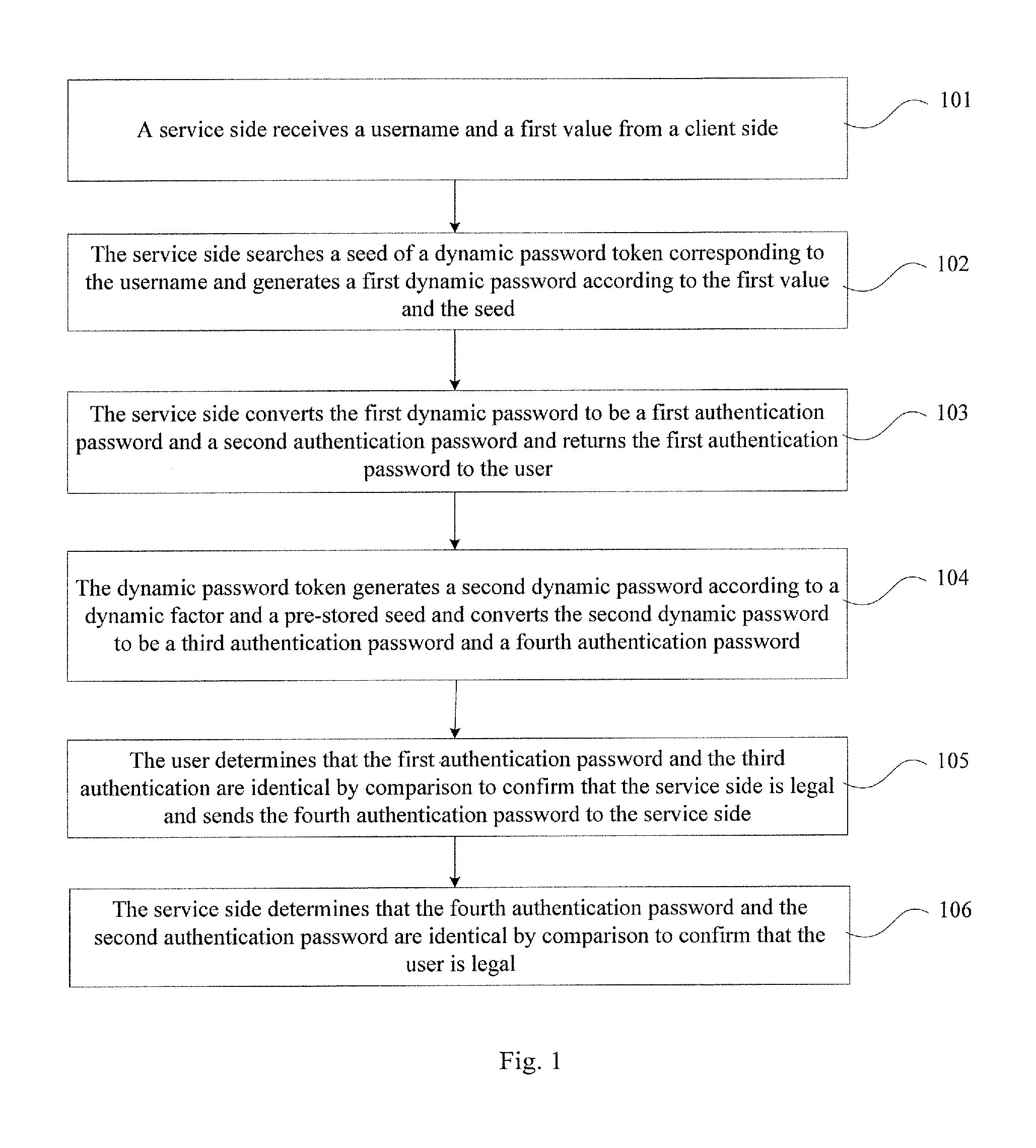
Authentication method, system, and device
ActiveUS20120137131A1Authentication securityAvoid illegal operationDigital data processing detailsUser identity/authority verificationPasswordClient-side
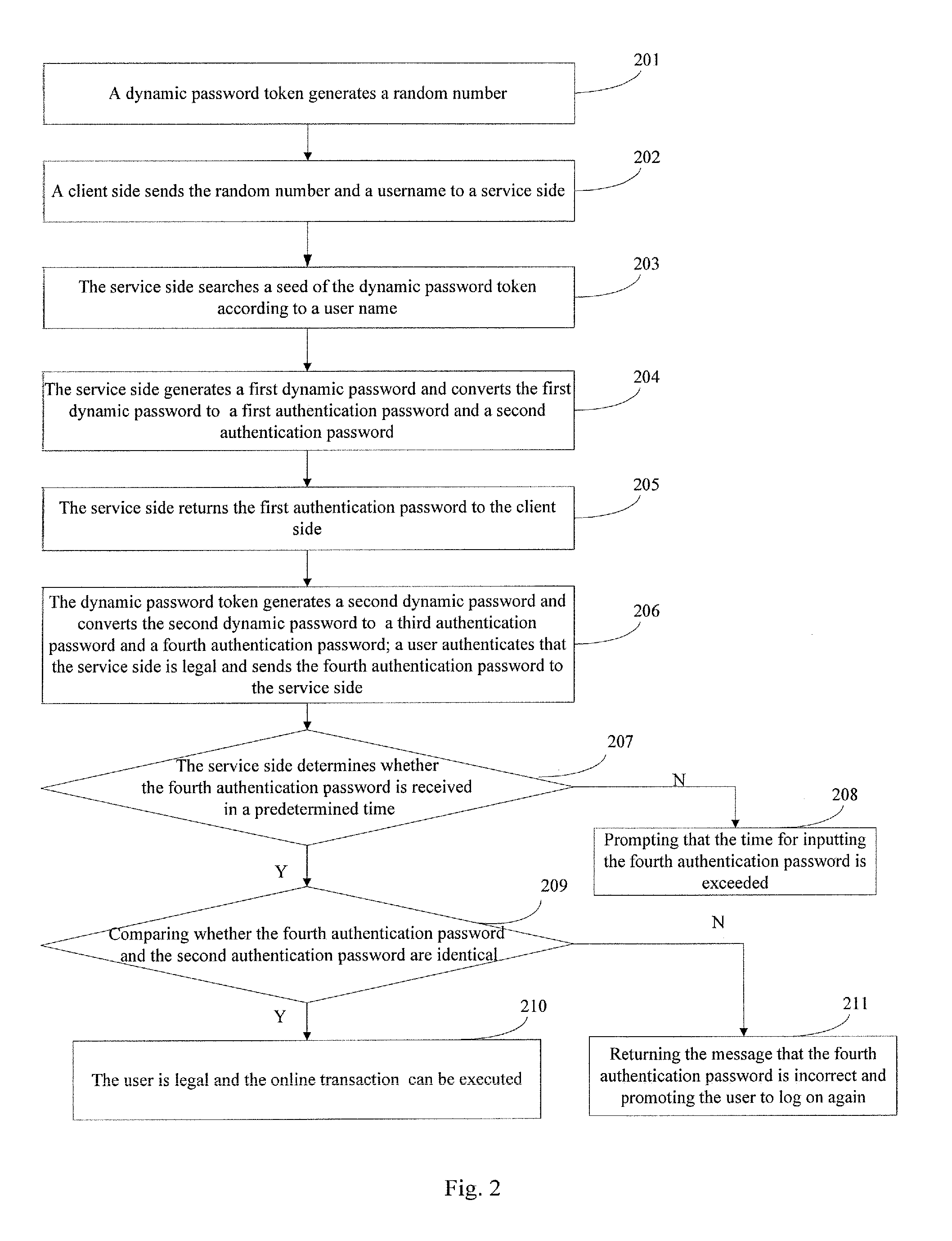
The present invention provides an authentication method, an authentication system, and an authentication device, which is in information security field. The method includes that a service side receives a username and a first value from a client side, searches a seed of a dynamic password token, and generates a first dynamic password according to the first value and the seed, converts the first dynamic password to the first authentication password and the second authentication password, and sends the first authentication password to the user; the dynamic password token generates a second dynamic password and sends the first authentication password to a user; the dynamic password token generates a second dynamic password and converts the second dynamic password to a third authentication password and a fourth authentication password; the user compares the first authentication password and the third authentication password to determine that they are identical, so as to confirm that the user is legal or the transaction is permissible. The invention prevents malicious attack and operation of illegal users, which improves the security of information and property of the users.
Owner:FEITIAN TECHNOLOGIES
Security management method and system for application programming interface
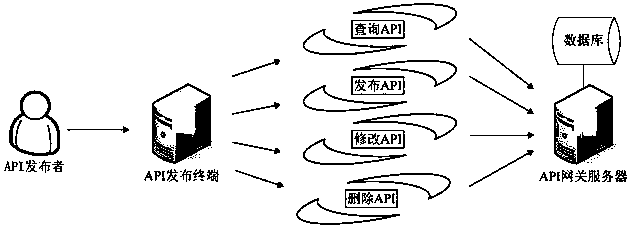
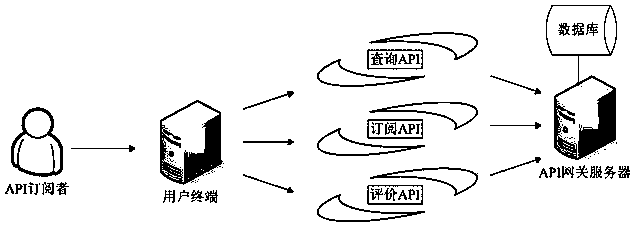
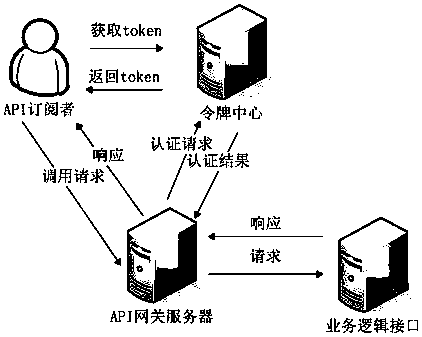
ActiveCN109150805AProtection controllabilityPlay a protective effectUser identity/authority verificationApplication programming interfaceIp address
The application provides a security management method and system for an application programming interface. On a gateway server side, the method includes the following steps that: service logical interface information submitted by a publisher is received; an interface external access address which is published to the outside is generated according to a preset format on the basis of the IP address of the gateway server and a port number allocated to the publisher, an association relationship between the interface external access address and the service logic interface information is established;an interface call request sent by a subscriber is received; and a request token center authenticates the identity of the subscriber that sends the interface call request, if the identity of the subscriber passes the authentication, the interface call request is forwarded to a corresponding service logical interface according to the association relationship between the interface external access address and the service logical interface information, and the execution result of the service logic interface is returned to the subscriber. With the above technical schemes of the invention adopted, the problem that illegal access to service data through an API cannot be blocked in the prior art can be solved.
Owner:亿阳安全技术有限公司
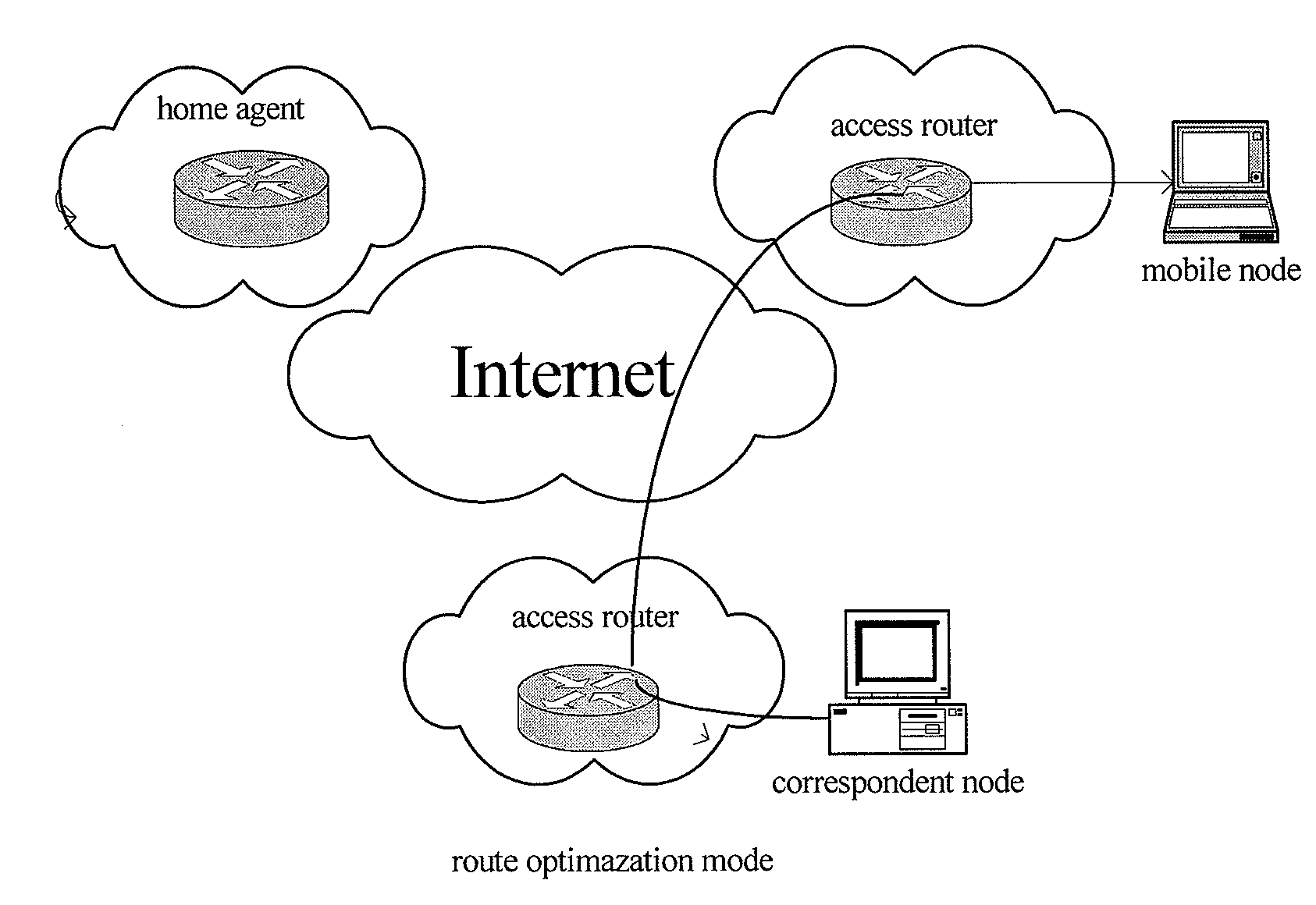
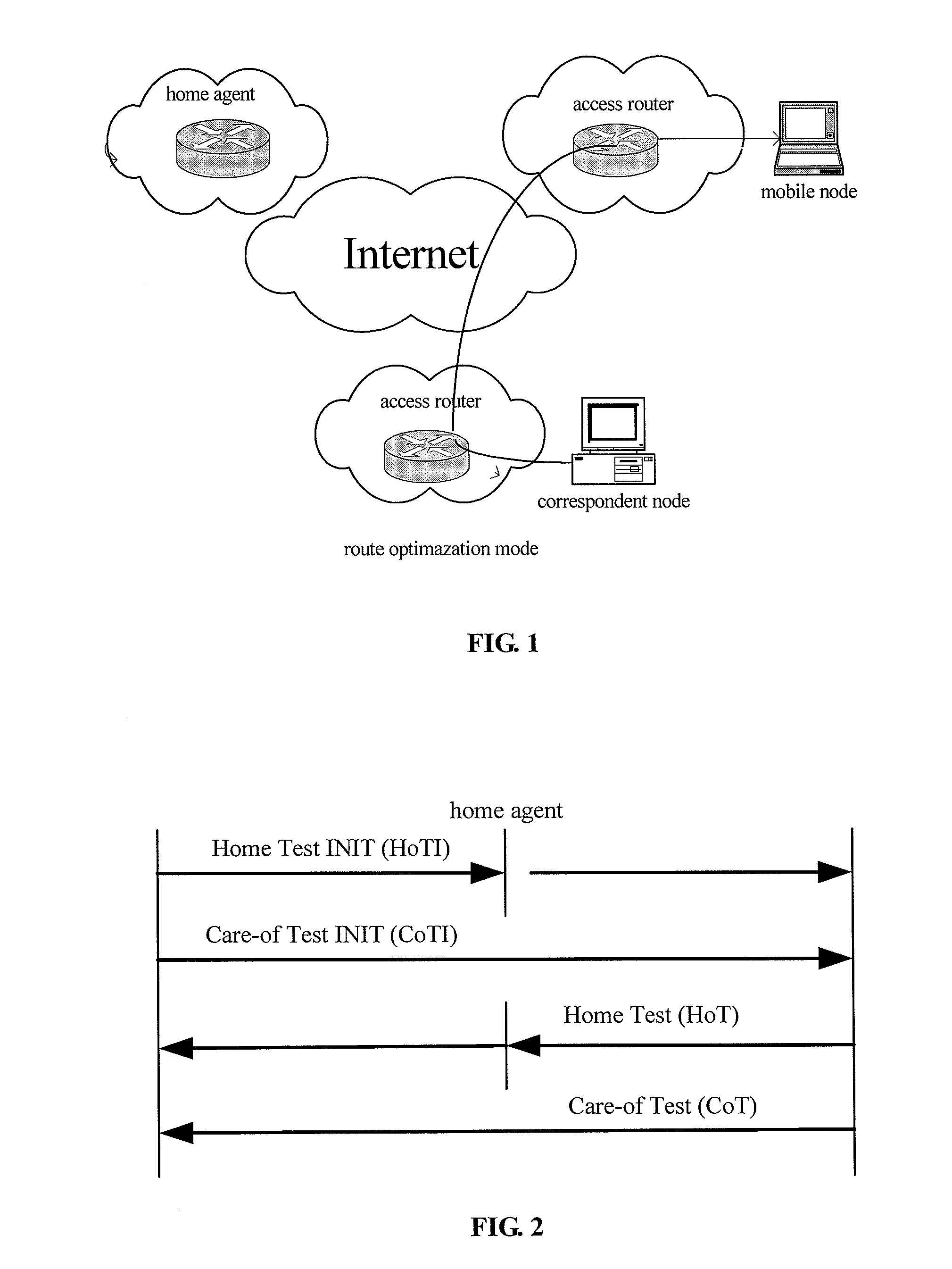
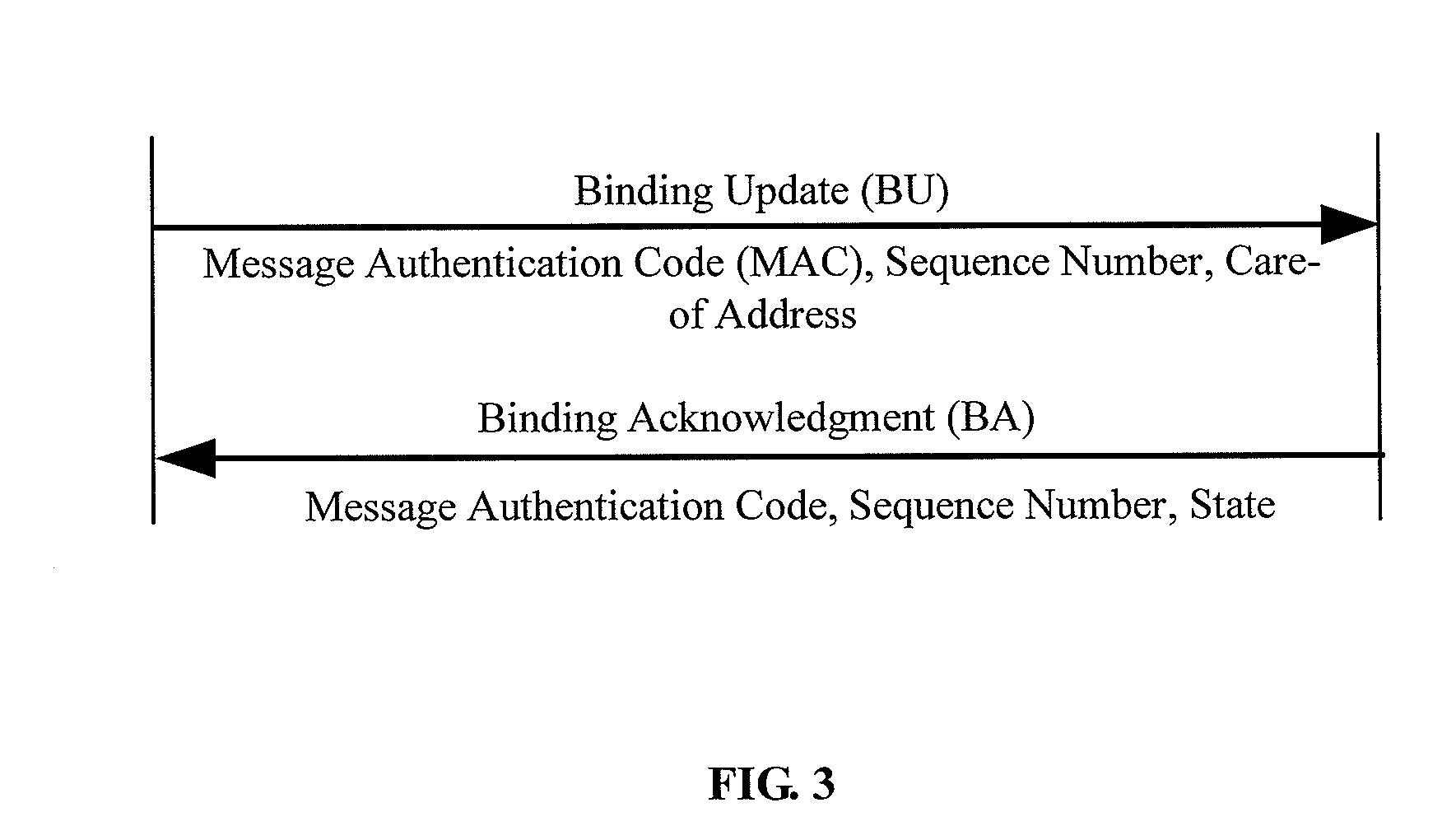
METHOD FOR COMMUNICATION OF MIPv6 MOBILE NODES
InactiveUS20080291885A1Prevent malicious attacksAvoid trackingWireless network protocolsSecret communicationComputer networkIPv6 address
A method for communication of MIPv6 mobile nodes, comprising: the mobile node accesses network at access location and obtains care of address, calculating a privacy identifier PID using the care of address etc. the mobile node replaces its home address by the PID, and sends the PID and the care of address together as binding update message to the home agent and correspondent node, the home agent and correspondent node recover the home address for the mobile node using the PID after they have received the binding update message. The method for communication of MIPv6 mobile nodes according to the present invention uses that a configuring replaced identifier replacing the home address is sent, thereby hiding Ipv6 address. By setting PID and its algorithm, we improve the sequence number in the binding update messages enabling the sequence number has randomness, and prevent the intercepting person continue tracking the mobile node through the home address.
Owner:HUAWEI TECH CO LTD +1
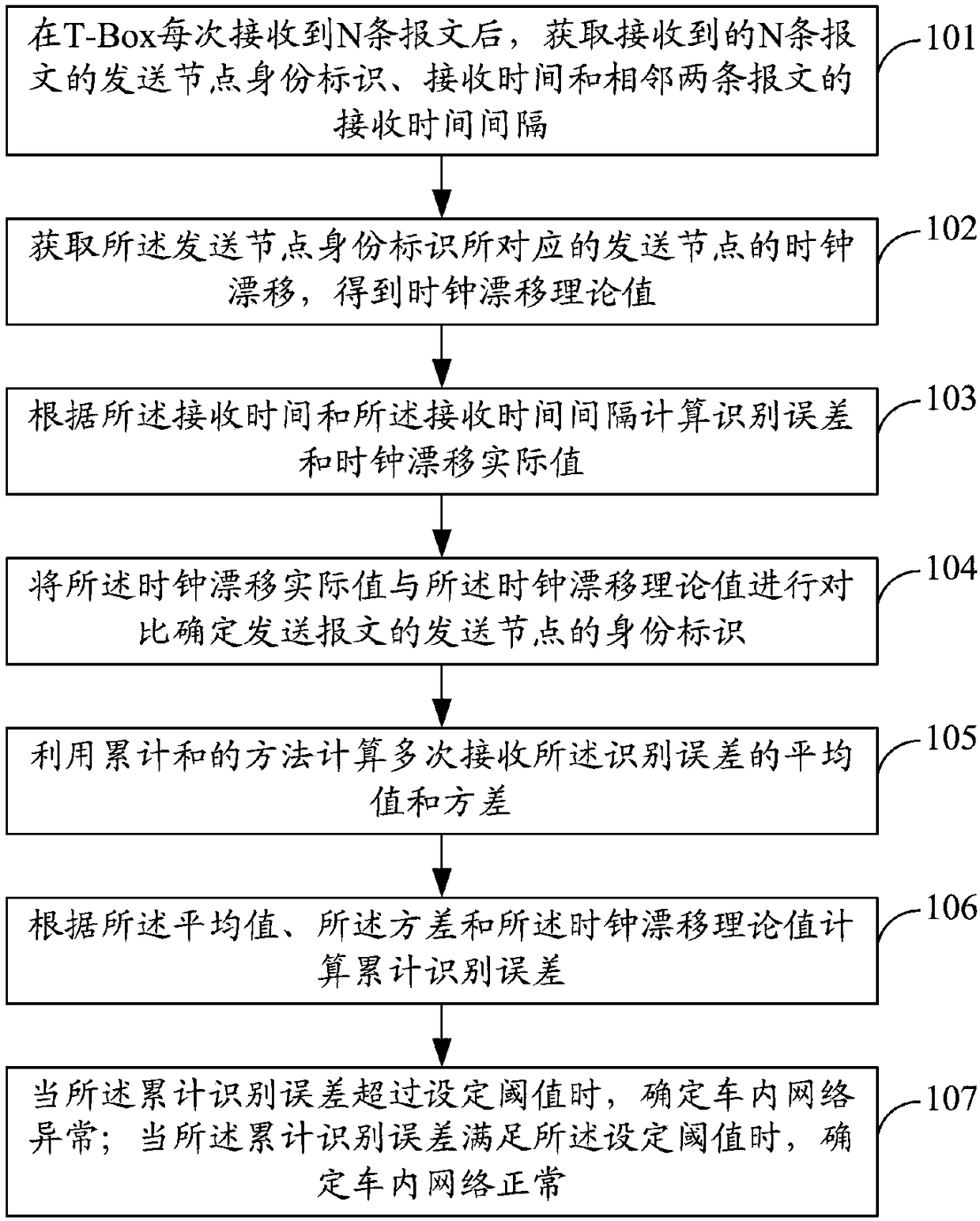
In-vehicle network invasion detection method and system
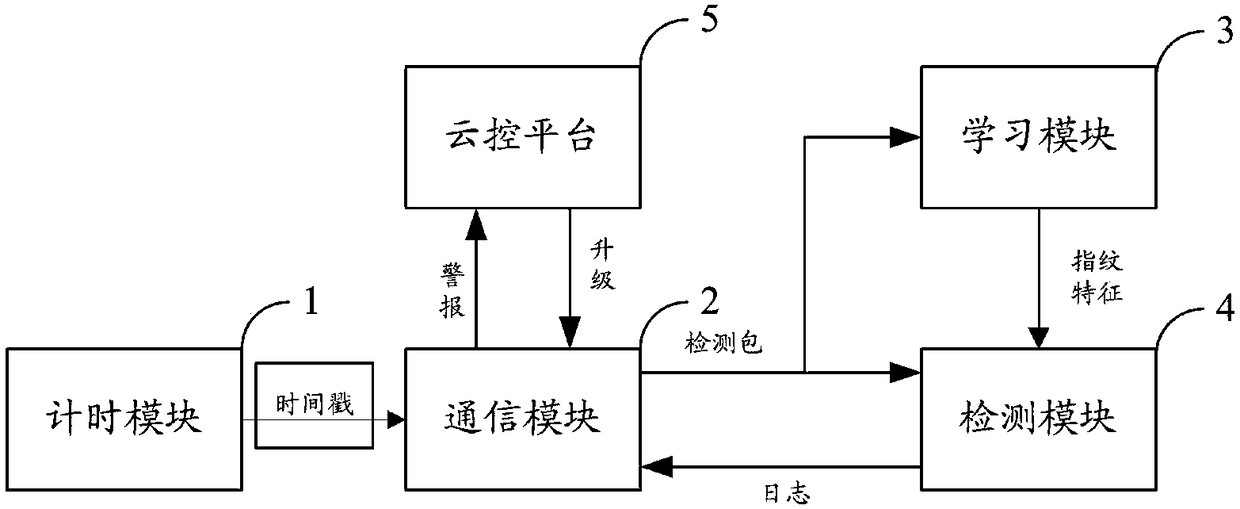
InactiveCN108111510AImprove securityUniversally applicableParticular environment based servicesIn-vehicle communicationTimestampClock drift
The invention discloses an in-vehicle network invasion detection method and system. The system comprises a timing module, a detection module, and a learning module; The timing module is used for transmitting the operation time of the system to the communication module, and the communication module records the timestamp of the receiving time of a received message and the identity label of a messagetransmitting node according to the operation time of the system. The communication module is used for transmitting the identity label and the timestamp of the receiving time to the learning module and the detection module. The learning module is used for determining a clock drift theoretical value of the transmitting node according to the timestamp of the receiving time when a network is normal,and carrying out the binding of the clock drift theoretical value with the identity label of the transmitting node. The detection module is used for determining the deviation of the clock drift of thetransmitting node relative to the clock drift theoretical value according to the timestamp of the receiving time during invasion detection. The system provided by the invention can be directly installed on a T-Box communication module, and the method and system are good in universality, and can guarantee the network safety of most vehicles.
Owner:BEIHANG UNIV
Novel self-defining ethernet out-of-band data packet filtering method and device
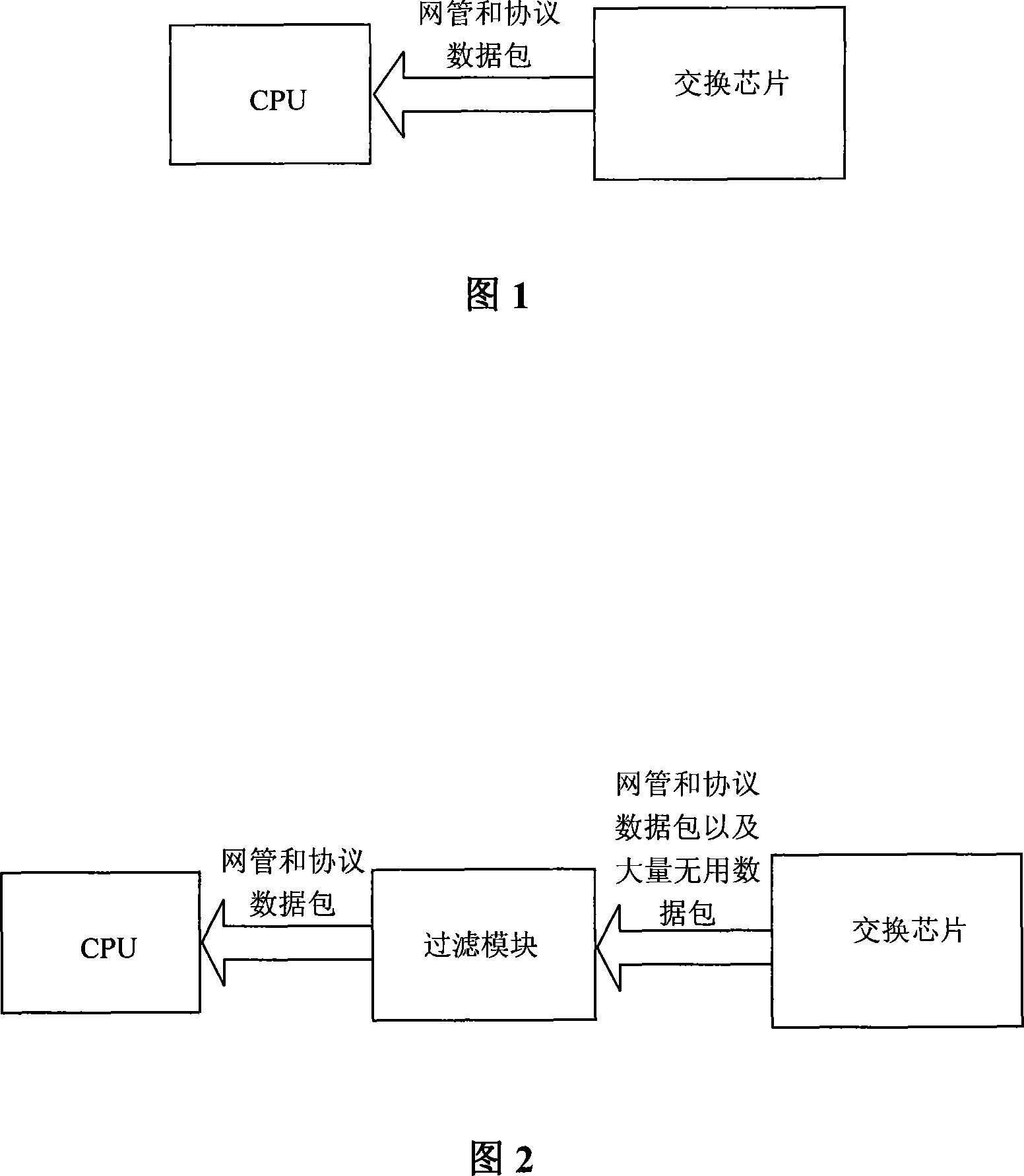
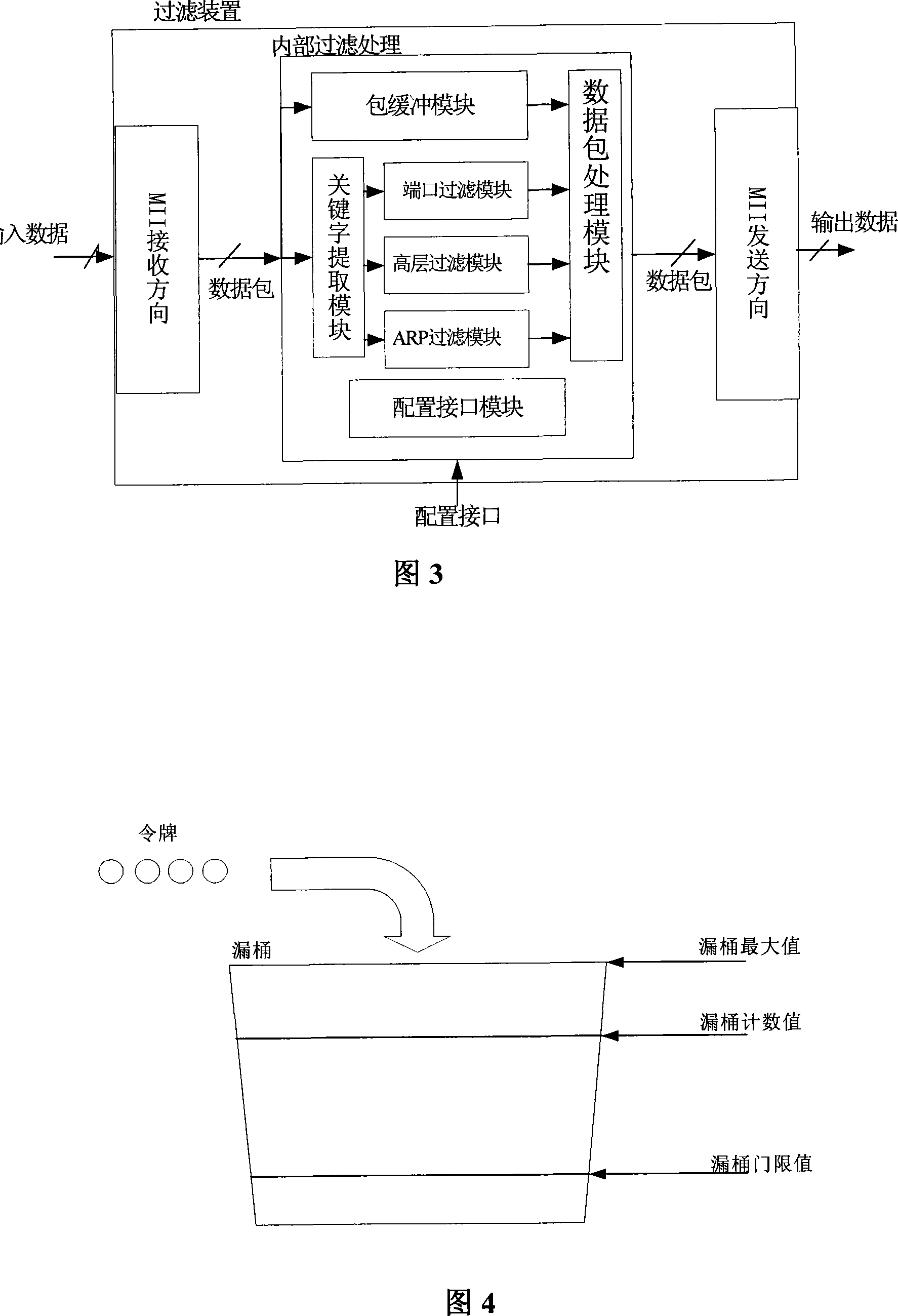
InactiveCN101141390ATroubleshoot issues that don't work properlyImprove reliabilityData switching networksBroadcast packetMulticast packets
The present invention relates to a method and a device for filtering a novel custom Ethernet out-band data packet. The key of the method and the device is that a filter module is additionally arranged between the out-band management interface of the Ethernet switcher and the CPU to extract the keyword of the data packet, to filter the content of the relative data packet, and to operate the discarding or the flow control operation. The method and the device can provide one to seven layers of filtering to the Ethernet out- band data packet, to pre filters the layer 2 or layer 3 or layer 4 data packets used to be processed by the CPU, and the present invention can pre process the special protocol data packets such as an Ethernet broadcast packet, a multicast packet, other Ethernet management protocols, the IP and a high-level IP protocol data packet, an ICMP and an ARP, etc., therefore, the processing efficiency of the CPU is improved, and the overload operation caused by the protocol data packets flooding is avoided, thereby the reliability of the complete Ethernet switcher system is improved.
Owner:WUHAN FIBERHOME NETWORKS
Systems and methods for prevention of json attacks
ActiveUS20110154472A1Avoid problemsReduce probabilityComputer security arrangementsMultiple digital computer combinationsClient-sideData validation
Described herein is a method and system for prevention of personal computing attacks, such as JavaScript Objection Notation (JSON) attacks. An intermediary device is deployed between a plurality of clients and servers. A firewall executes on the intermediary device. A client sends a request to the server and the server sends a response to the request. The intermediary device intercepts the response and identifies that the response may contain possibly harmful content. The application firewall parses the content of the response and determines whether it contains any harmful content. If it does, the application firewall blocks the response from being sent to its destination. Additionally, the method and system can provide other security checks, such as content hijacking protection and data validation.
Owner:CITRIX SYST INC
Content Management System and Method
InactiveUS20080162528A1Prevent malicious attacksBridging language barriersNatural language data processingMetadata still image retrievalRankingCommon word
A system and method for content management is disclosed. Textual content is parsed into forming identified content by excluding common words. The identified content is linked to relevant images. Relevant images are searched and from a number of candidate images suitable to be inserted proximate to the identified content. A relevant image based on a ranking of the images is selected and inserted proximate to the identified content with or without human intervention.
Owner:IBM CORP
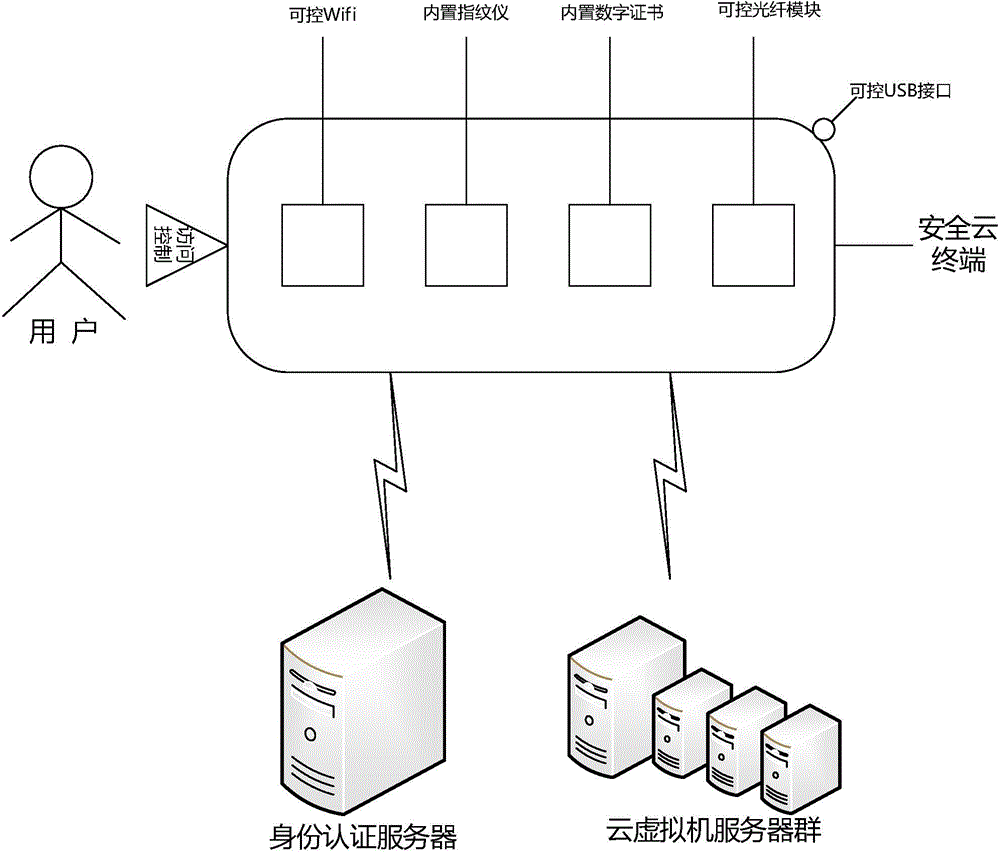
Fusion identify protection system and fusion identify protection method based on cloud computing
ActiveCN104320389APrevent malicious attacksPrevent leakage of user sensitive informationUser identity/authority verificationClient-sideSecurity level
The invention discloses a fusion identify protection system and a fusion identify protection method based on cloud computing and aims at realizing effective protection of network identity security through public cloud and private cloud architectures in a cloud computing environment. According to the fusion identify protection system and the fusion identify protection method based on the cloud computing, infinite existing and unknown strong identity authentication methods are fused together by use of a uniform standard interface based on the special distributed cluster management of the cloud computing, an authentication interface with a single portal is provided for a user and the user can select the authentication methods at different security levels according to own instant requirements. Besides, According to the fusion identify protection system and the fusion identify protection method based on the cloud computing, the biological recognition technology and the digital authentication technology are embedded in a security cloud terminal, and therefore, a cloud computing platform and the desk of a user client can be prevented from the invasion of an illegal control machine.
Owner:NANJING UNIV OF POSTS & TELECOMM
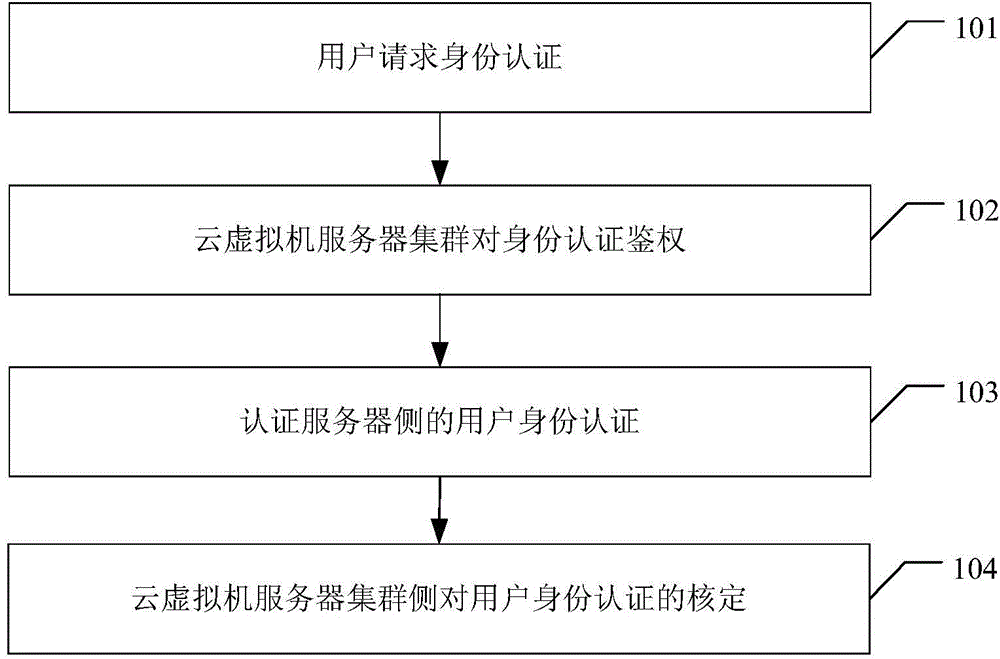
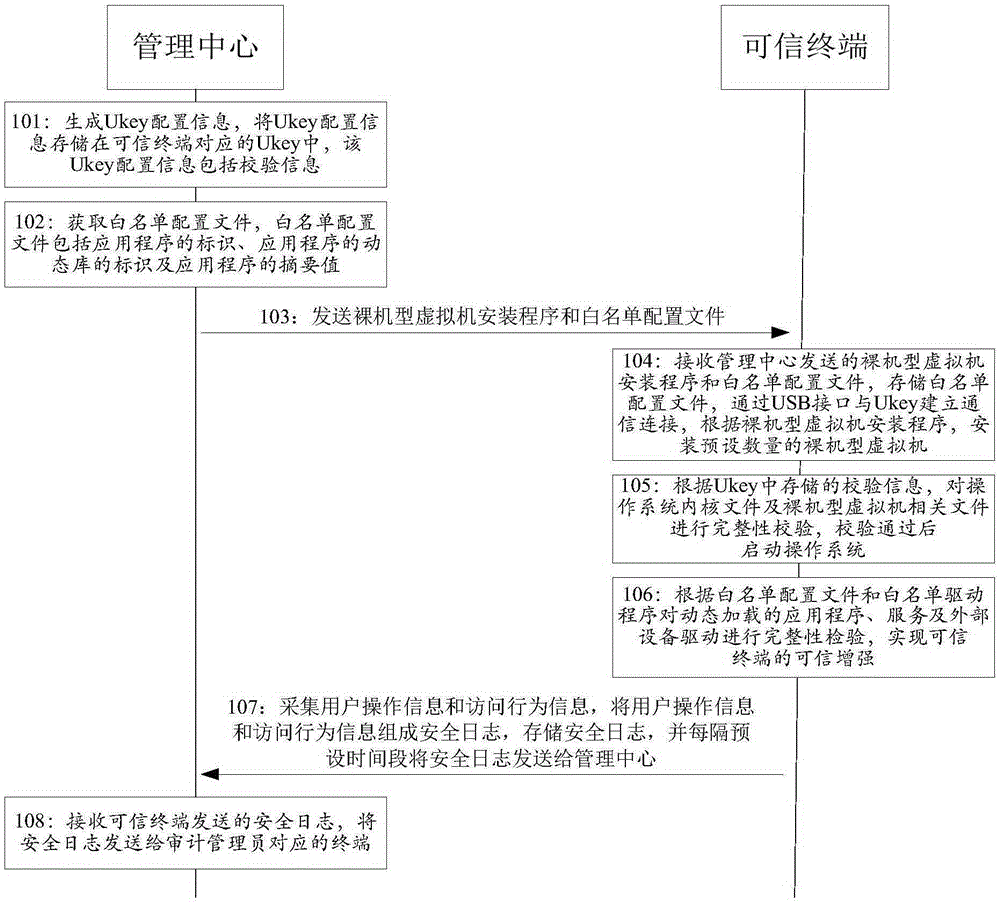
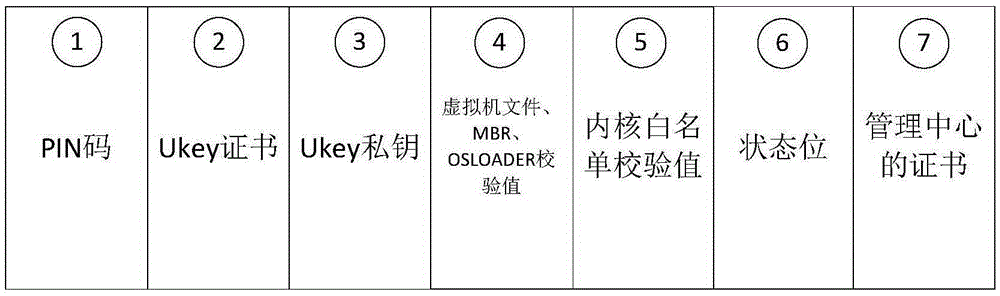
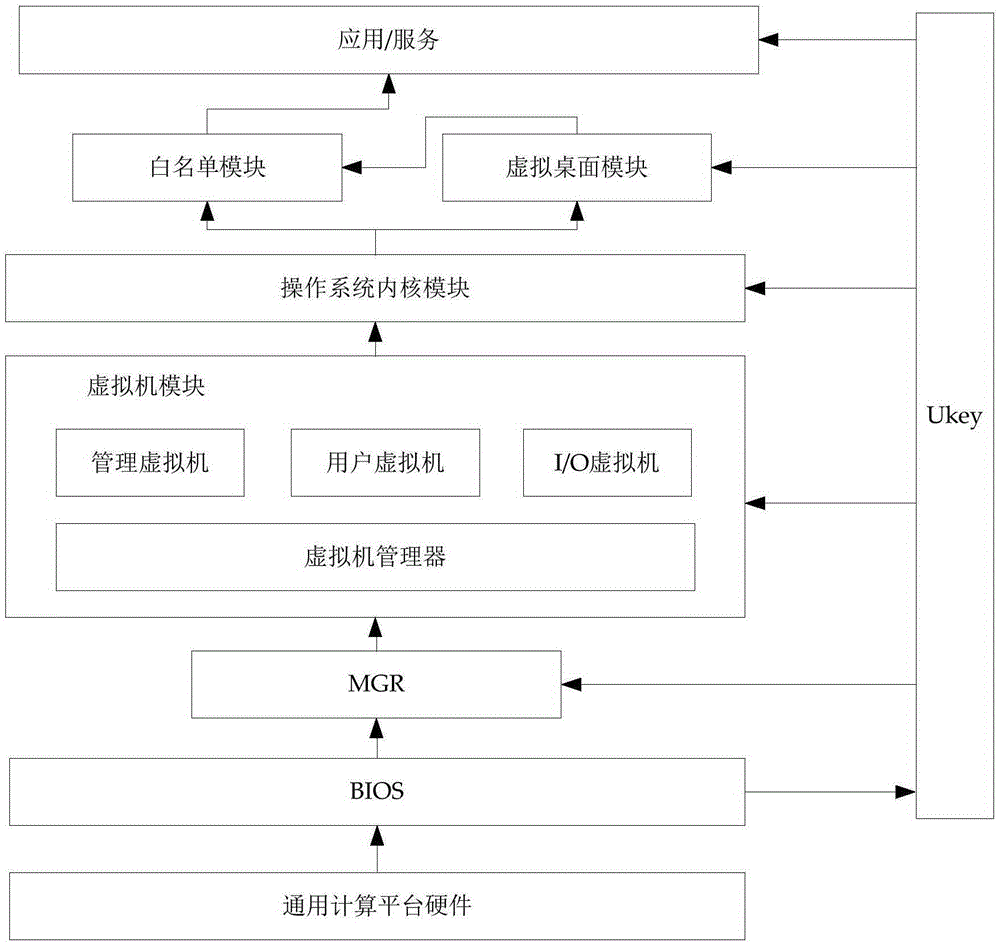
Virtualization technology based terminal trust enhancement method and system
InactiveCN105354493AAchieving Trust EnhancementPrevent leakageDigital data protectionPlatform integrity maintainanceVirtualizationOperational system
The present invention provides a virtualization technology based terminal trust enhancement method and system. The method comprises: a trusted terminal, according to verification information stored in a Ukey, performing completeness verification on an operation system kernel file and a bare-type virtual machine related file, and starting an operation system after verification is passed; and the trusted terminal, according to a whitelist configuration file and a whitelist drive program, performing completeness verification on an application, a service and an external device drive that are loaded dynamically, so as to implement trust enhancement of the trusted terminal. According to the virtualization technology based terminal trust enhancement method and system provided by the present invention, the operation system is started according to verification information stored in the Ukey, a static trust chain is established, and operation system information is prevented from being leaked or tampered from internally; and completeness verification is performed on the loaded application according to the whitelist configuration file, a dynamic trust chain is established, and malicious attacks and unauthorized access are prevented from externally.
Owner:PLA PEOPLES LIBERATION ARMY OF CHINA STRATEGIC SUPPORT FORCE AEROSPACE ENG UNIV +1
A method, system and gateway device for processing packets
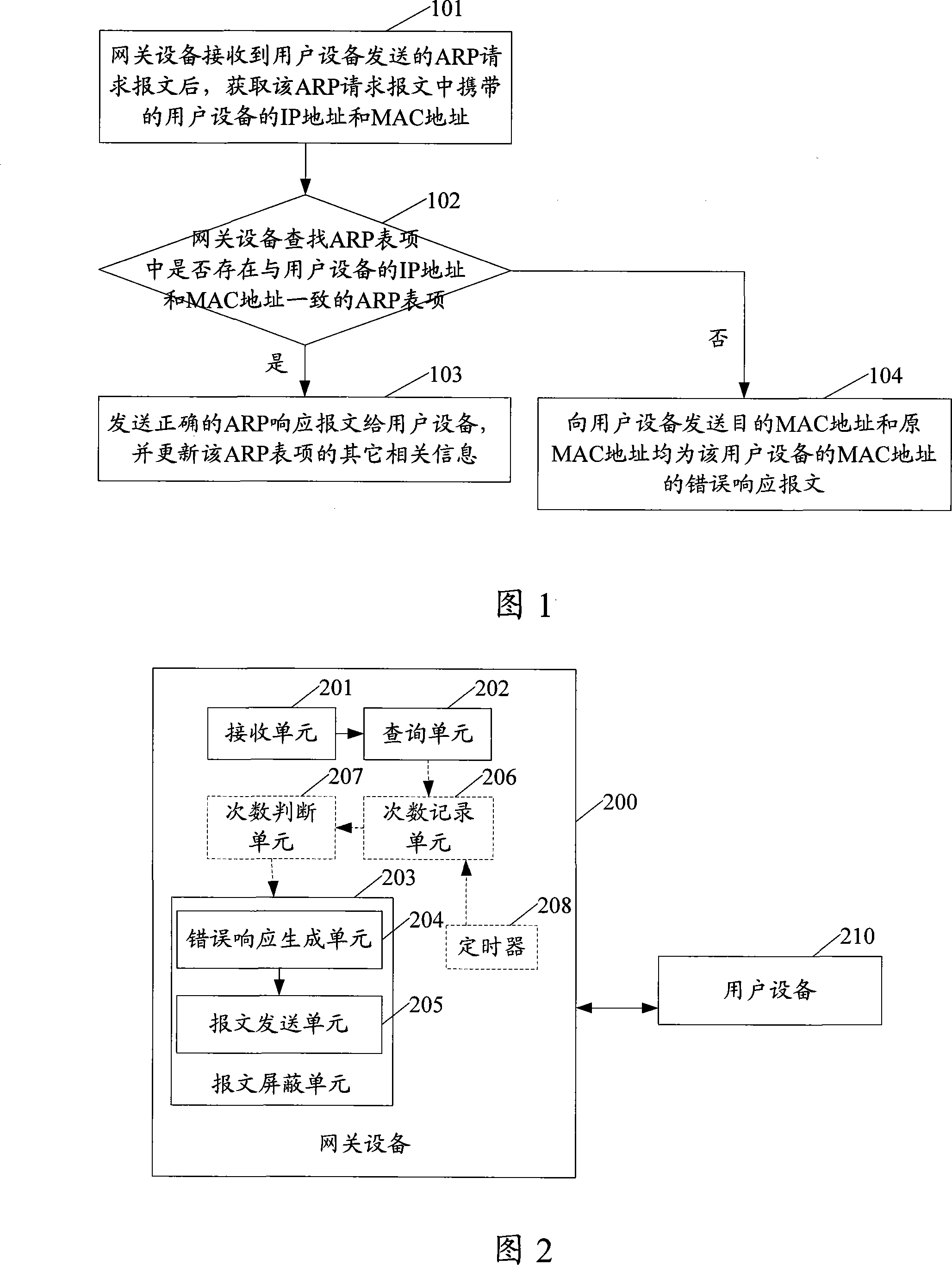
ActiveCN101170515APrevent malicious attacksAvoid repeated executionData switching networksIp addressMedia access control
The invention provides a method, a system and equipment for processing a message, wherein, the method includes that: receiving a media access control (MAC) address request message delivered by user equipment, and then querying about whether an ARP item which is identical with the MAC address and the IP address of the user carried by the MAC address request message exists or not, and if not, screening the message delivered by the user. In this way, after determining the user equipment delivering the MAC address request message is a non-authorized user, the method can be used to screen the MAC address request messages delivered by the user equipment to gateway equipment in a given period, preventing the gateway equipment from repeatedly implementing the message processing, enhancing the processing efficiency of the gateway equipment, and also preventing the malicious attacks from the non-authorized users.
Owner:HUAWEI TECH CO LTD
Mobile phone Bluetooth-based ambient intelligent computer protection device and method
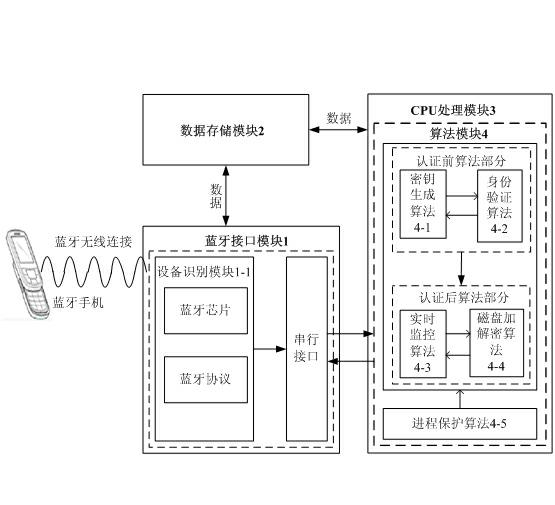
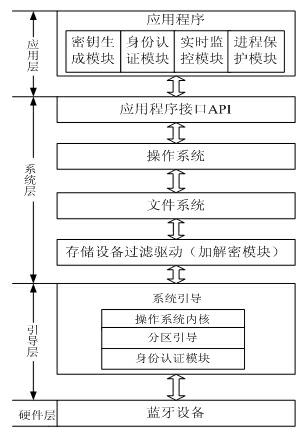
InactiveCN102136048AProtection processPrevent malicious attacksNear-field transmissionInternal/peripheral component protectionMagnetic disksEmbedded system
The invention provides a mobile phone Bluetooth-based ambient intelligent computer protection device and a mobile phone Bluetooth-based ambient intelligent computer protection method. In the device and the method, a Bluetooth mobile phone serving as a user terminal is wirelessly connected with a Bluetooth interface module, and the Bluetooth interface module is connected with a computer by a serial interface. The computer is started by the hardware certification of mobile phone Bluetooth-Bluetooth interface module and user-system authentication. After the computer is started, a system realizesentire disk transparent encryption and decryption by adopting an encryption and decryption algorithm in an advanced encryption standard (AES)-XTS mode; the locking or unlocking of the system is realized by monitoring user behaviors in real time, so the data in a disk is protected. The device mainly comprises the Bluetooth interface module, a data storage module, a central processing unit (CPU) processing module and an algorithm module.
Owner:SOUTHEAST UNIV
Reliable network management method based on TCPA/TCG reliable network connection
ActiveCN101345660AAchieving local trustworthinessActive defense against attacksData switching networksNetwork connectionNetwork management
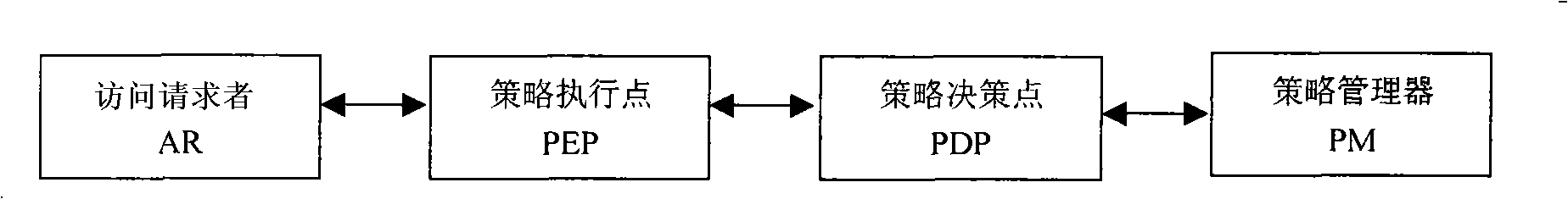
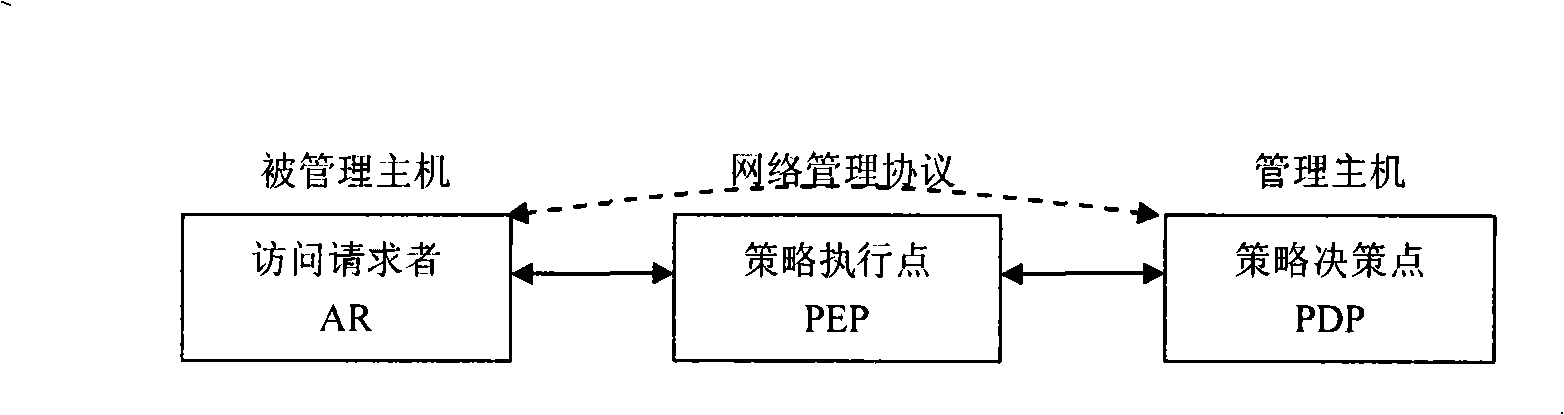
The invention relates to a credible network managing method connected based on TCPA / TGG credible network. An credible managing agent and a credible managing system are respectively mounted and arranged on a managed host computer and a managing host computer and are validated to be locally credible, when the managed host computer and the managing host computer are not connected to a credible network, the computers are connected to the credible network based on a connecting method of TCPA / TGG credible network, then execute discrimination and key negotiating process of the credible managing agent and the credible managing system. When the managed host computer and the managing host computer do not complete user discrimination and the key negotiating process, the computers execute the user discrimination and the key negotiating process, then realize remote confidence of the credible managing agent and the credible managing system, finally execute network management. According to the invention, attack is initiatively defended, safety of a credible network management framework is enhanced, credible network management of distributed control and centralized management is realized.
Owner:CHINA IWNCOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com