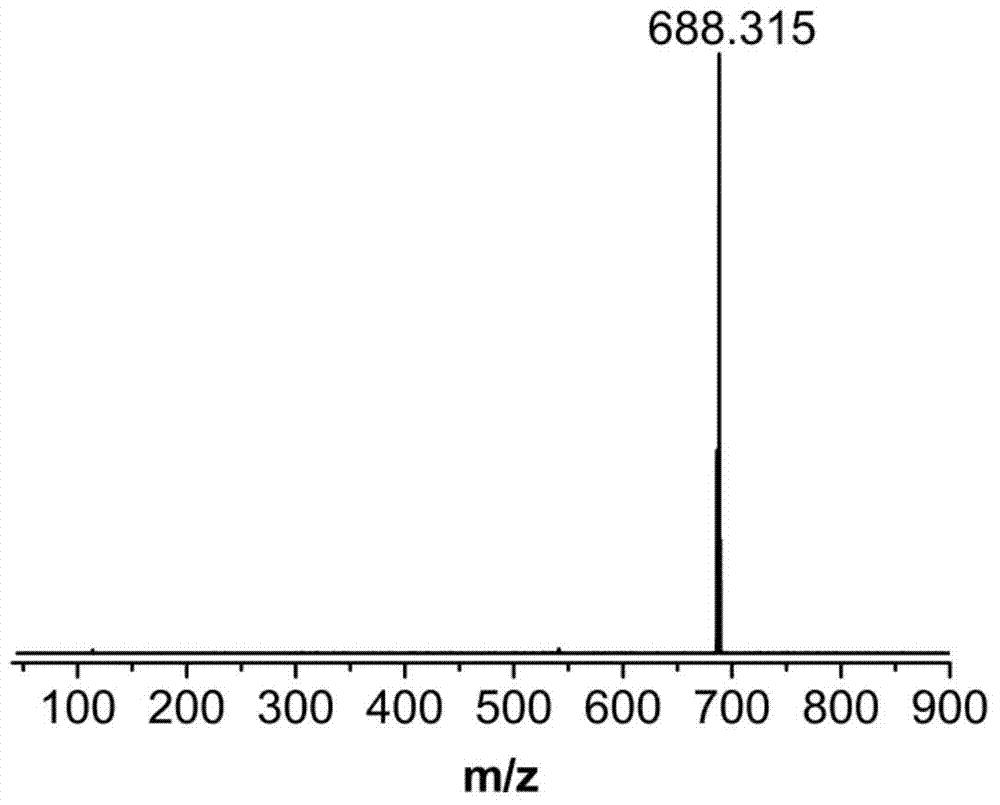
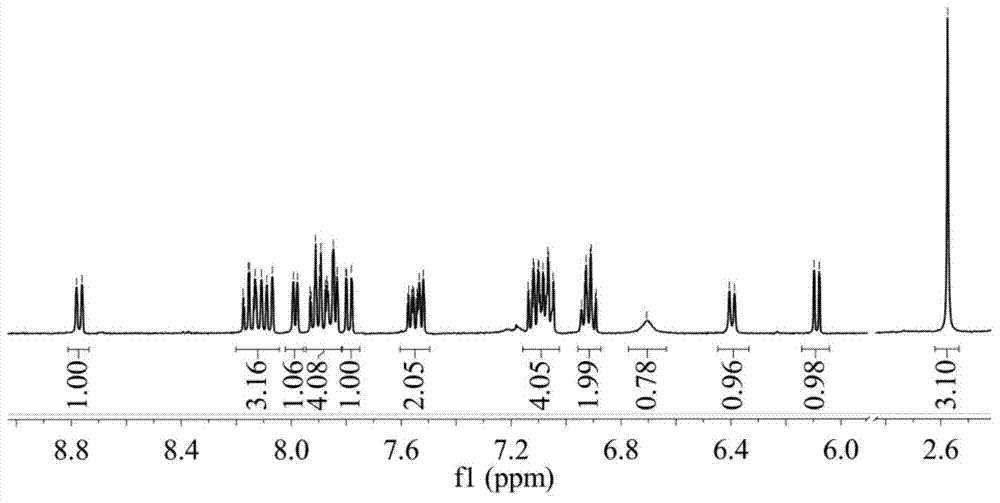
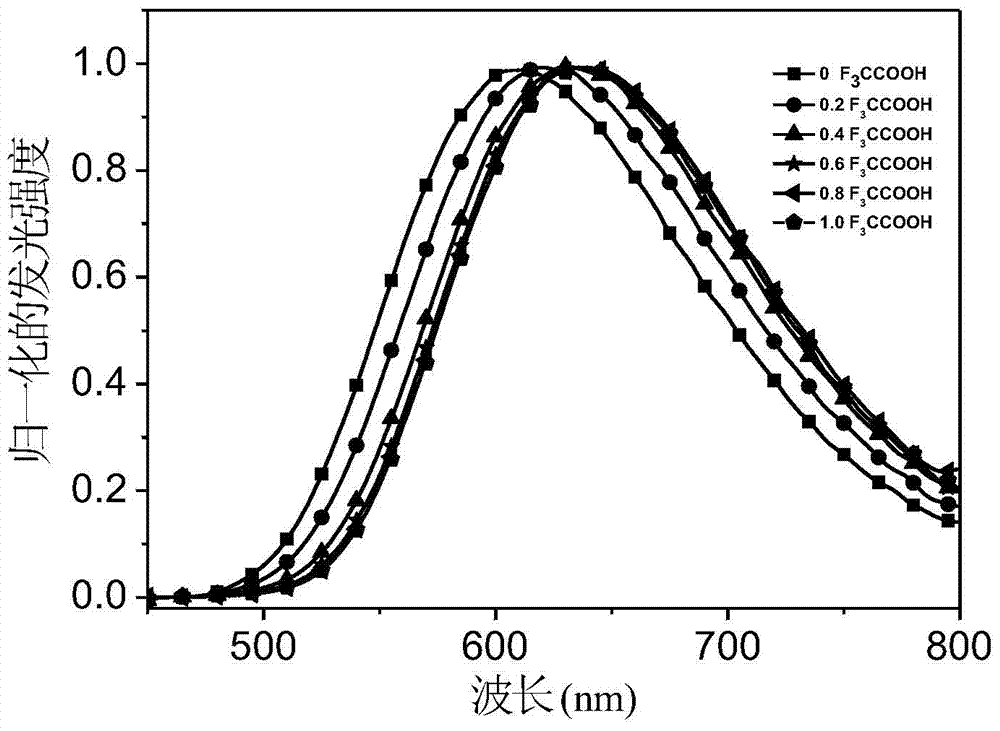
Patents
Literature
51results about How to "Achieve decryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
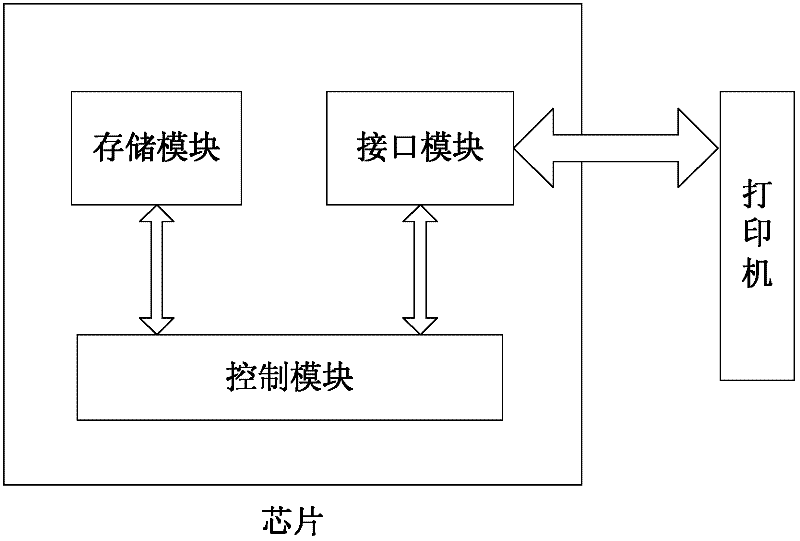
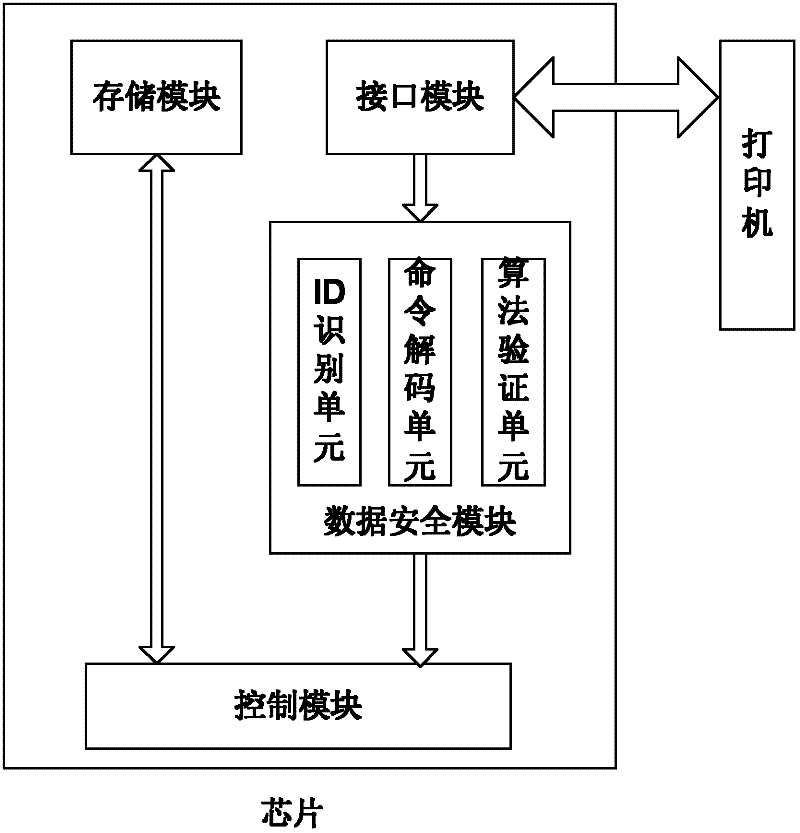
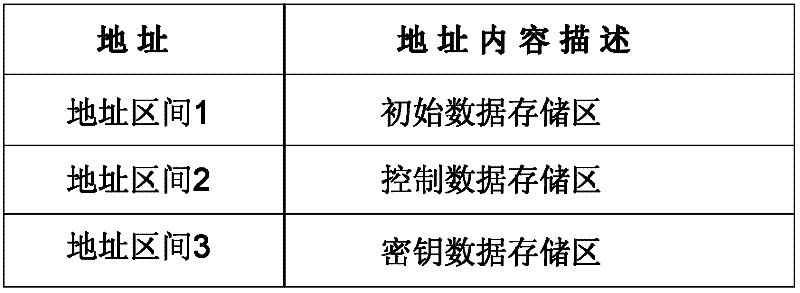
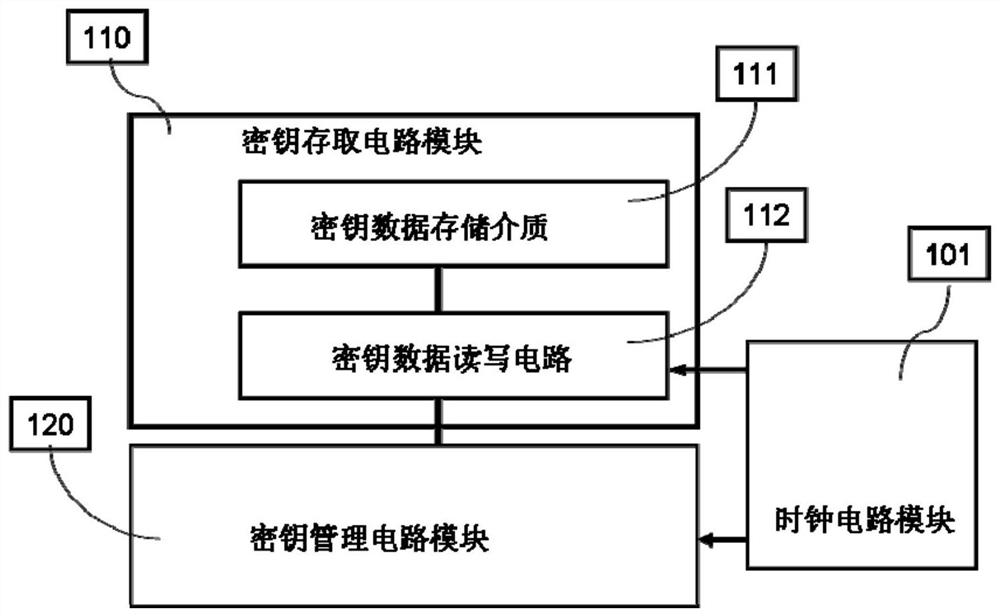
Chip, data communication method for chip, consumable container and imaging equipment
InactiveCN102231054AImprove reliabilityAvoid crackingElectrographic process apparatusPrintingExternal dataStructure of Management Information
The invention provides a chip of a consumable container, which comprises a storage module, a control module, an interface module and a data safety module. The storage module is used for storing initial data, printing data, control data and key data; the interface module is used for realizing data communication between the storage module and the control module; the data safety module is respectively connected with the interface module and the control module, and is used for identifying a type and a content of data communicated between a printer and the chip, encrypting matched data in a selected safe mode and decrypting the data; the control module is connected with the storage module and is used for controlling data communication between the chip and the printer and the access operation of the data of the storage module and external data and sending a corresponding control command to the chip according to a safety module processing result so as to realize data communication; and the same keys are stored in the printer and the chip. The invention also provides a data communication method for the chip, the consumable container with the chip structure, and imaging equipment with the consumable container. The safety of the communication data of the chip can be protected.
Owner:ZHUHAI TIANWEI TECH DEV CO LTD
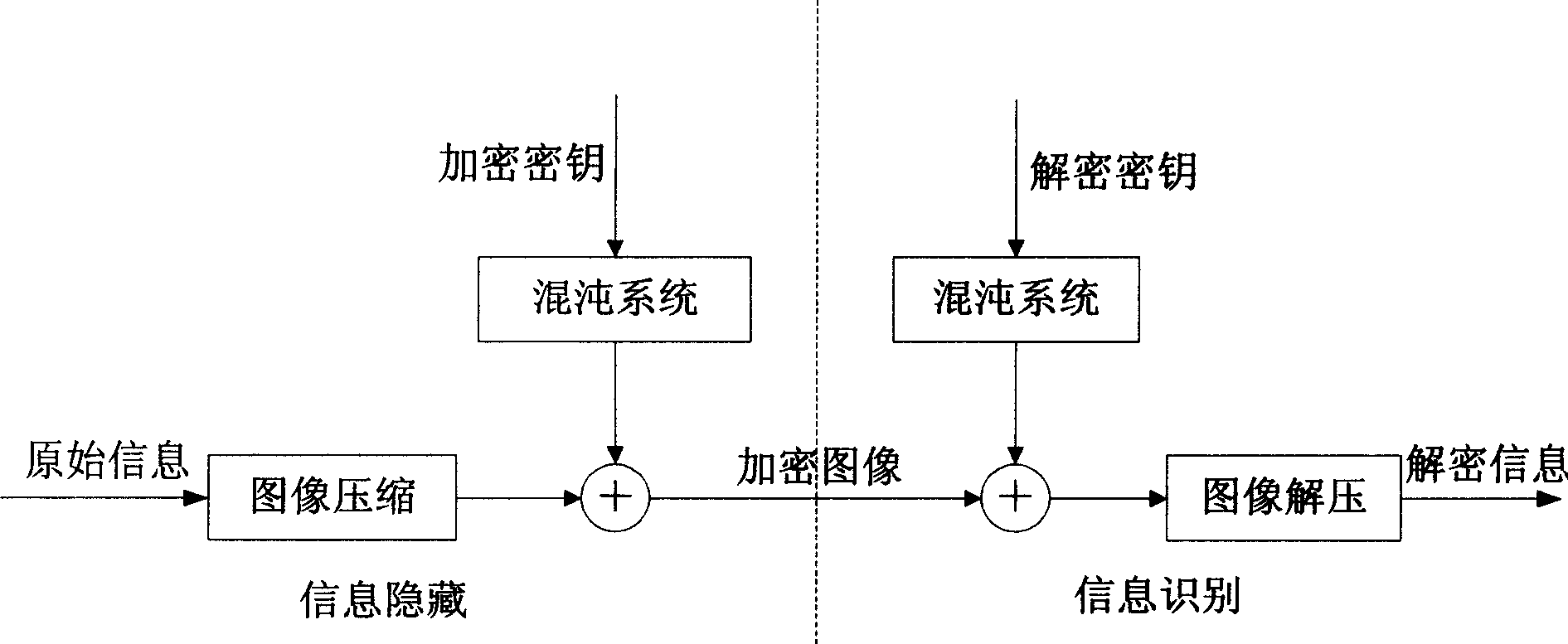
Image false-proof method based on chaotic characteristic
InactiveCN1738235AImplement encryptionAchieve decryptionImage data processing detailsSensing record carriersChaotic systemsImage segmentation
The invention discloses a image counterfeit deterrence method based on the chaotic feature, comprising: first, by the chaotic mapping system, using the information needed keep secret and counterfeit deterrence to generate the chaotic sequence which is used to encode the information, then, printing the encoded information to the two-dimension bar code image according to the PDF417 bar code; collecting the two-dimension bar code image by the scanner, and operating the preprocessing of image segmentation, filtration, geometric correction and stratified on collected image, then decoding the bar code according to the decoding rule of national standard PDF417 bar code to attain the chaotic encoded information carried by bar code image. The invention fully utilizes the features of chaotic system and two-dimension bar code technique which are combined for image counterfeit deterrence. The invention has the characters as strong secret-keeping property and large information carried, while it can recognize automatically.
Owner:XI AN JIAOTONG UNIV
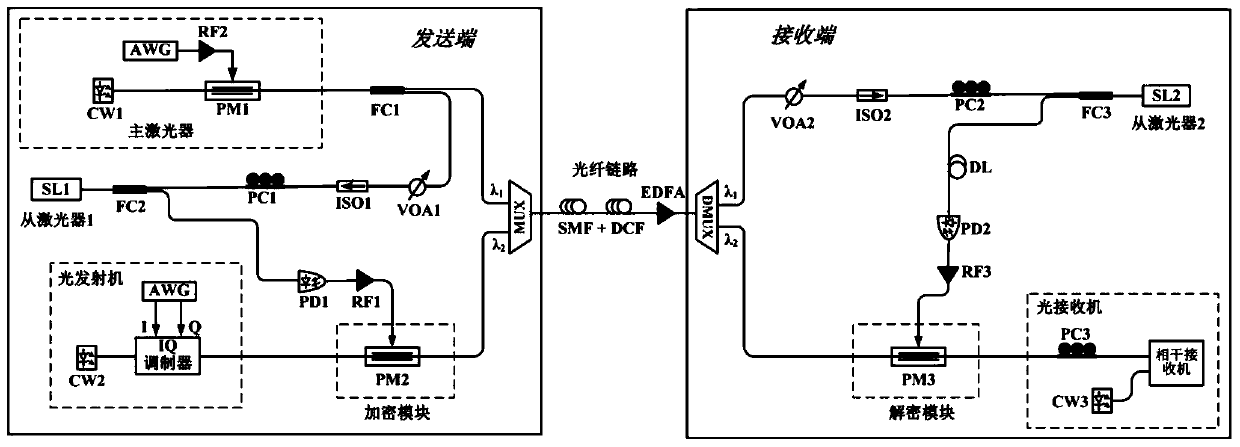
Physical layer secret optical fiber communication system based on chaotic phase encryption
ActiveCN111277337AImplement encryptionAchieve decryptionSecuring communication by chaotic signalsElectromagnetic transmission optical aspectsEngineeringMechanical engineering
The invention discloses a physical layer secret optical fiber communication system based on chaotic phase encryption, and the system comprises the steps: dividing a broadband random light source generated by a main laser into two identical optical signals, and respectively injecting the two optical signals into slave lasers of two communication sides, thereby generating a synchronous chaotic signal; and then the generated synchronous chaotic signal is used as a phase modulator driving signal, and high-speed optical signals generated by high-order modulation are encrypted and decrypted at a sending end and a receiving end.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
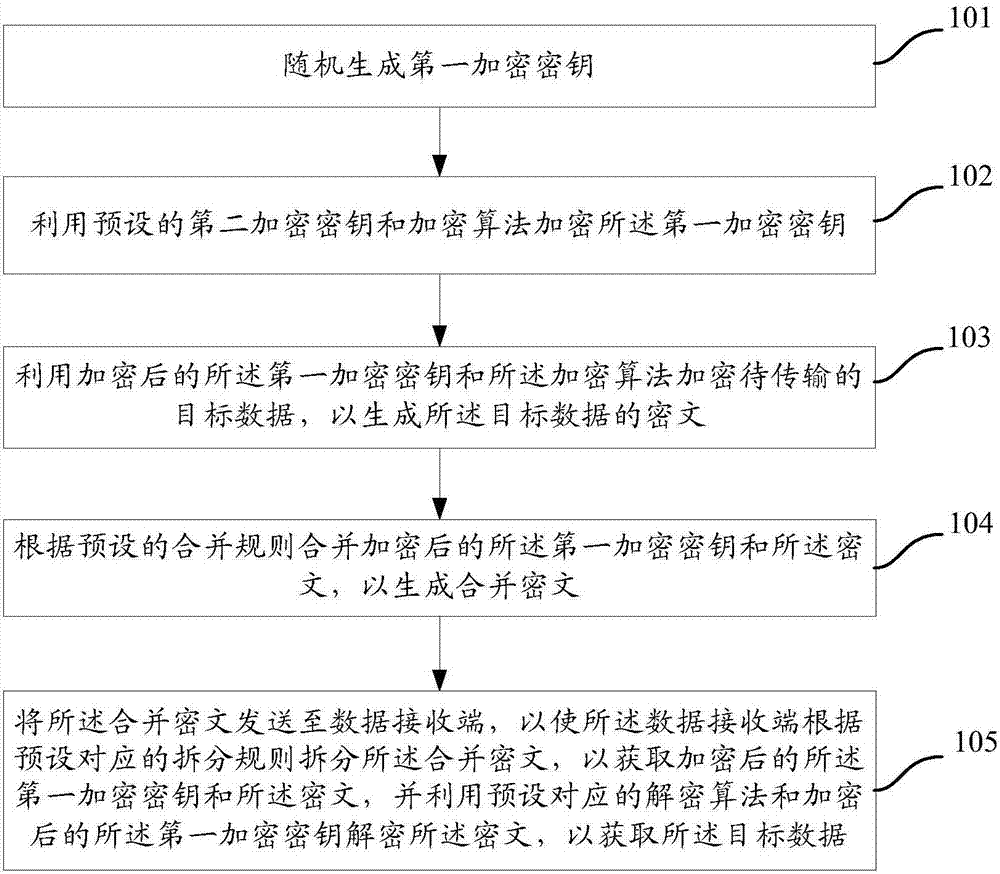
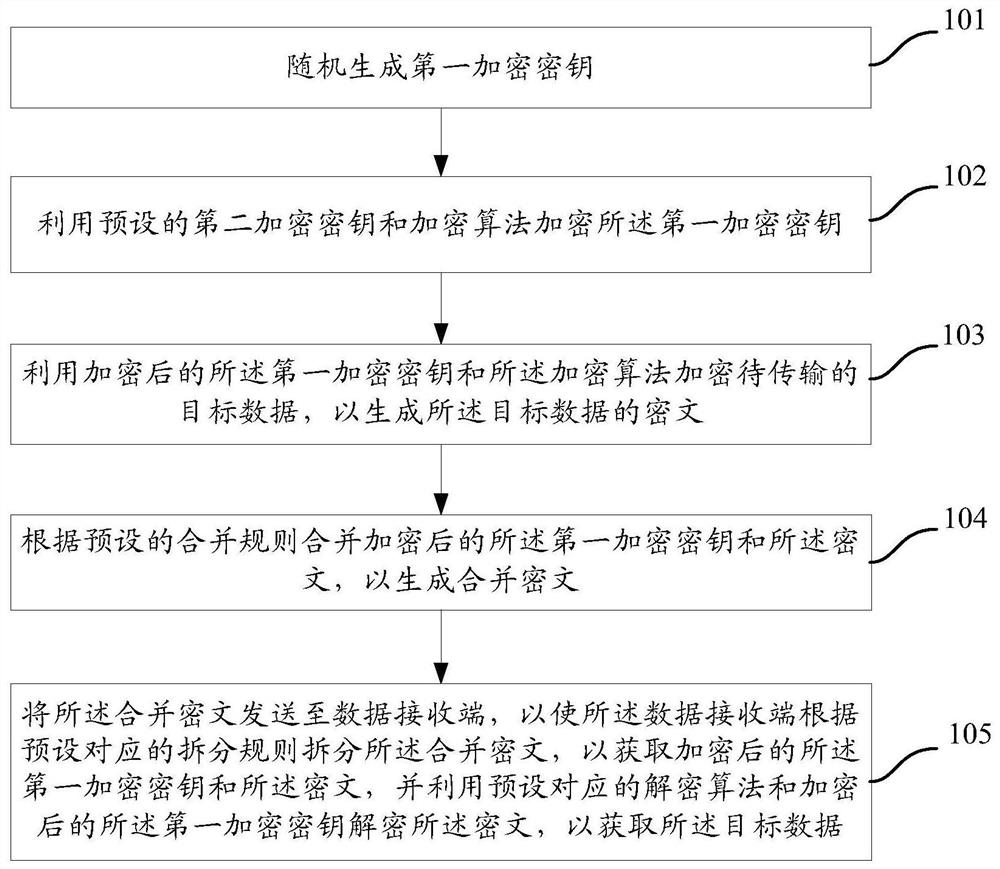
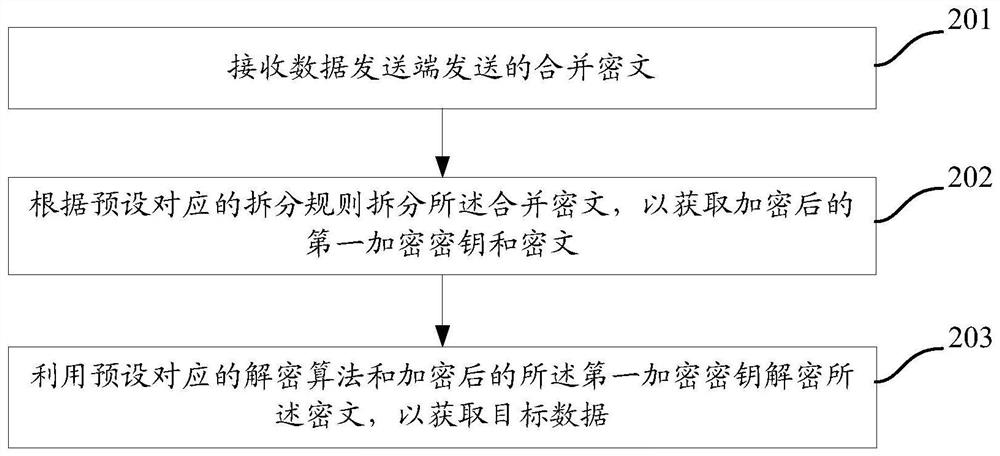
Data transmission method, data transmitting terminal and data receiving terminal
ActiveCN107086915AImprove securityAchieve decryptionKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCiphertext
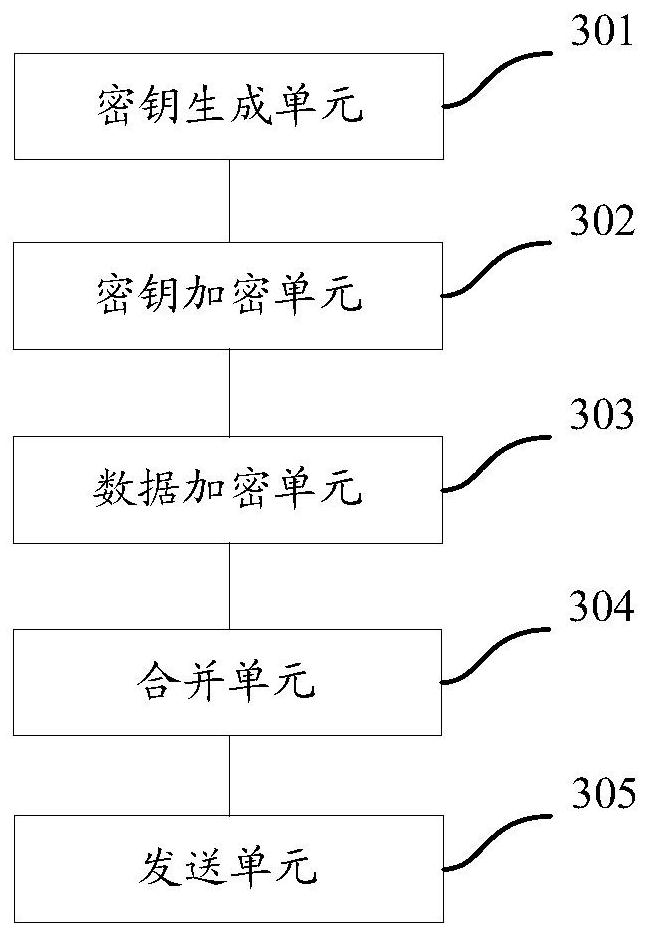
The invention provides a data transmission method, a data transmitting terminal and a data receiving terminal. The method comprises: a first encryption key is generated randomly; the first encryption key is encrypted by using a preset second encryption key based on an encryption algorithm; to-be-transmitted target data are encrypted by using the encrypted first encryption key and the encryption algorithm so as to generate a ciphertext of the target data; according to a preset combination rule, a combined ciphertext is generated by using the encrypted first encryption key and the ciphertext; and the combined ciphertext is sent to the data receiving terminal and thus the data receiving terminal splits the combined ciphertext according to a preset corresponding splitting rule to obtain the encrypted first encryption key and the ciphertext, and the ciphertext is decrypted by using a preset corresponding decryption algorithm and the encrypted first encryption key, so that the target data are obtained. Therefore, security of the data is improved.
Owner:INSPUR SOFTWARE TECH CO LTD
Method for realizing security electronic mail based on digital envelope
ActiveCN105323070AHigh speedImprove securityUser identity/authority verificationData switching networksConfidentialityCiphertext
The invention relates to the technical field of information security, and in particular relates to a method for realizing a security electronic mail based on a digital envelope. According to the invention, on the basis of the digital envelope technology based on PKI symmetric and asymmetric key algorithms, mail encryption and decryption information, user key information, data recovery information, mail ciphertext and other information are assembled into the digital envelope; and thus, encryption, decryption and data recovery of the electronic mail are realized. According to the invention, a session key is encrypted by obtaining all public key certificates of each receiver from a LDAP, such that interconnection and intercommunication of multiple certificates of one person are realized; when a mail blind copying function is started, mail information can be decrypted only by the private key of a blind copying user; therefore, the identity confidentiality of the blind copying user is ensured; in an emergency case that the private key of the user is lost or damaged, mail information can be decrypted without recovering the private key of the user through a KMC; and, by means of a high-grade security protection mechanism that the encrypted private key cannot be derived and a strict service approval signature mechanism, the security of recovered information is ensured from the perspectives of technologies and management.
Owner:BC P INC CHINA NAT PETROLEUM CORP +2
Transparent encryption and decryption method for database based on multi-level view and trigger
InactiveCN102243629AImplement automatic encryptionAchieve decryptionDigital data protectionSpecial data processing applicationsPlaintextRelational database
The invention discloses a transparent encryption and decryption method for a database based on a multi-level view and a trigger, which is used for encrypting and protecting data in a relational database and preventing information from being stolen illegally. Based on the view and the trigger, which are universal to the relational database, an aim of being correspondingly transparent is achieved by implementing automatic encryption and decryption of sensitive data through implementing the multi-level view and using the trigger based on a row identifier, and an application system is not needed to be modified; precise judgment on query actions to the database is implemented through the multi-level view, so that a special ciphertext and plaintext data caching strategy based on an LRU cache management mechanism is established for different types of query actions, a strategy of pre-decrypting the ciphertext data in batches is established, and efficient ciphertext query is implemented.
Owner:BEIJING ANHUA JINHE TECH
Message data encryption method and system, internet of things server and internet of things terminal
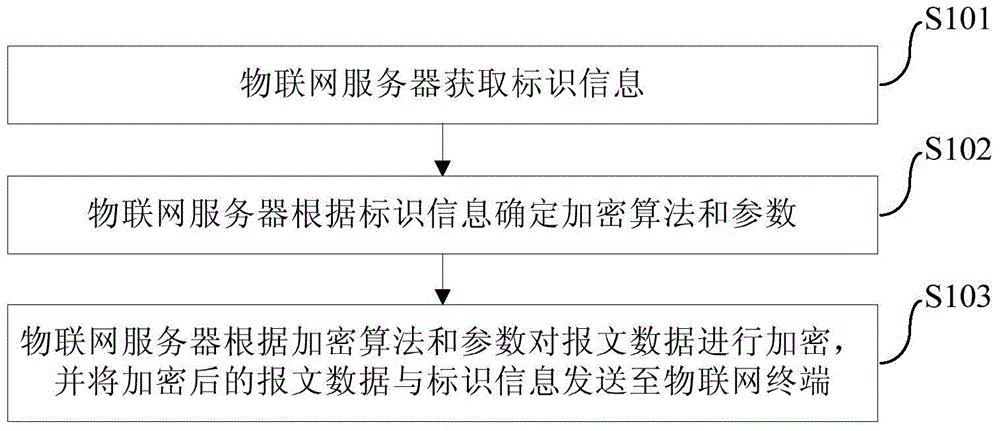
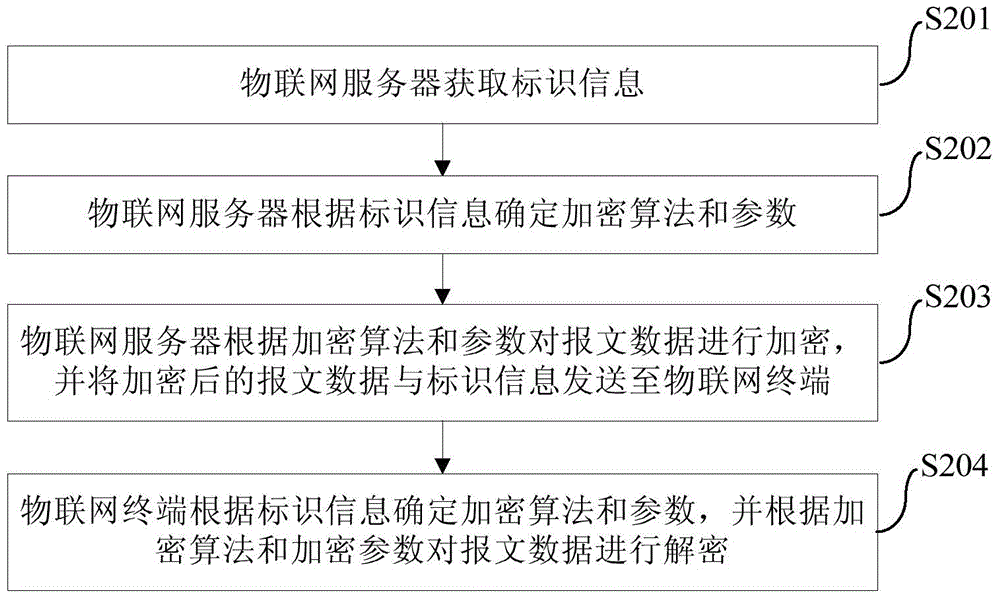
ActiveCN105281904AImprove securityAvoid Privacy LeakageEncryption apparatus with shift registers/memoriesUser identity/authority verificationThe InternetComputer science
The invention provides a message data encryption method and system, an internet of things server and an internet of things terminal. The message data encryption method comprises the steps that the internet of things server acquires identification information; the internet of things server determines an encryption algorithm and parameters according to the identification information; and the internet of things server encrypts message data according to the encryption algorithm and the parameters and transmits the encrypted message data and the identification information to the internet of things terminal. According to the message data encryption method, security of internet of things communication can be enhanced and disclosure of privacy of users can be avoided.
Owner:FOSHAN SHUNDE MIDEA ELECTRICAL HEATING APPLIANCES MFG CO LTD +1
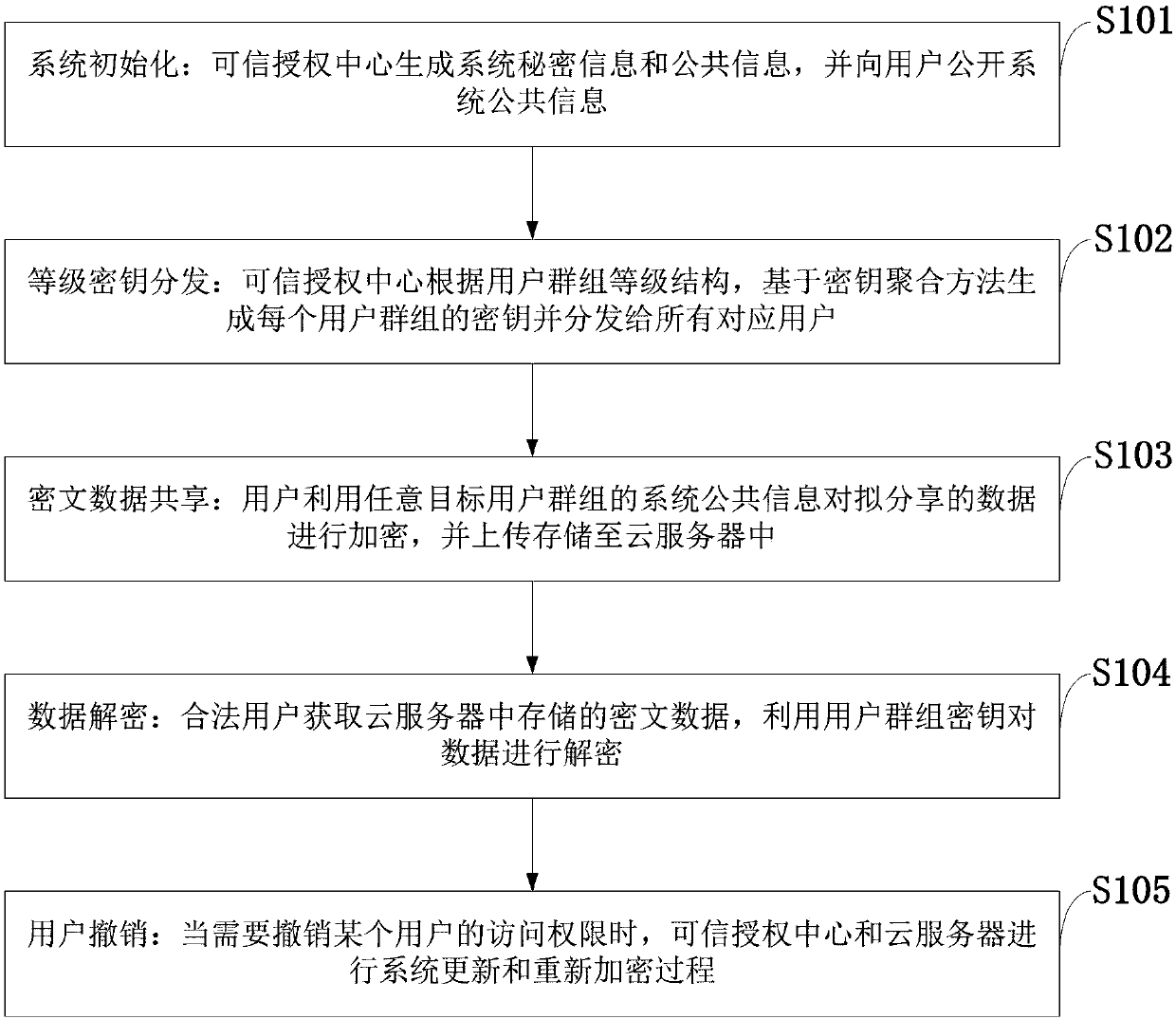
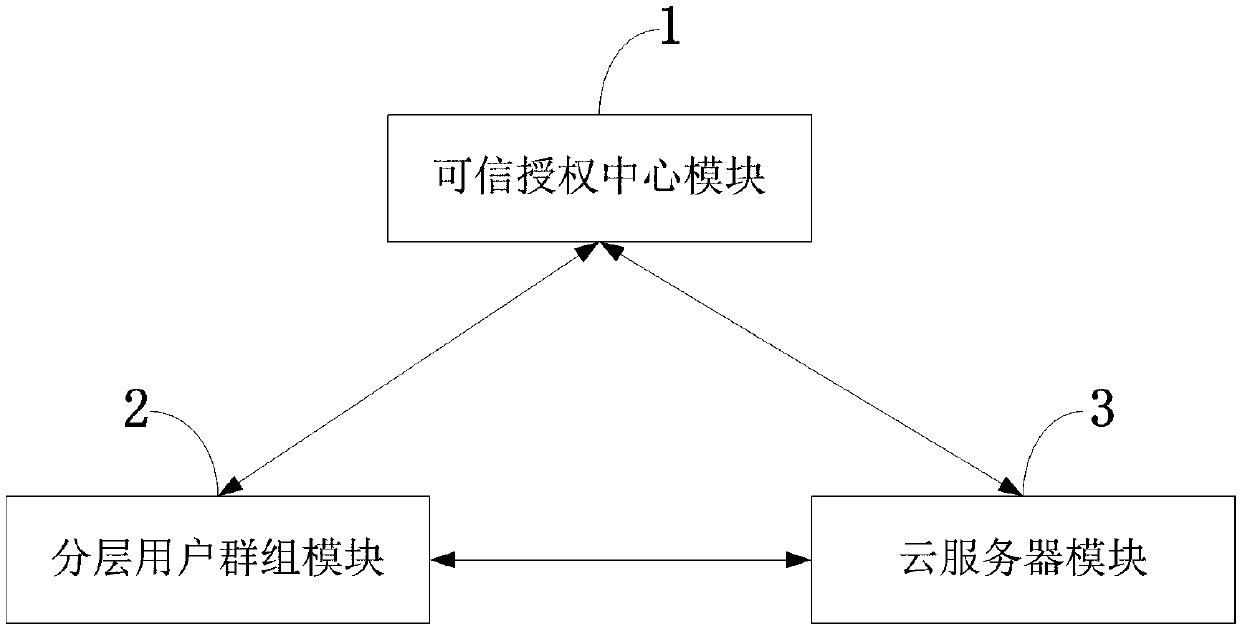
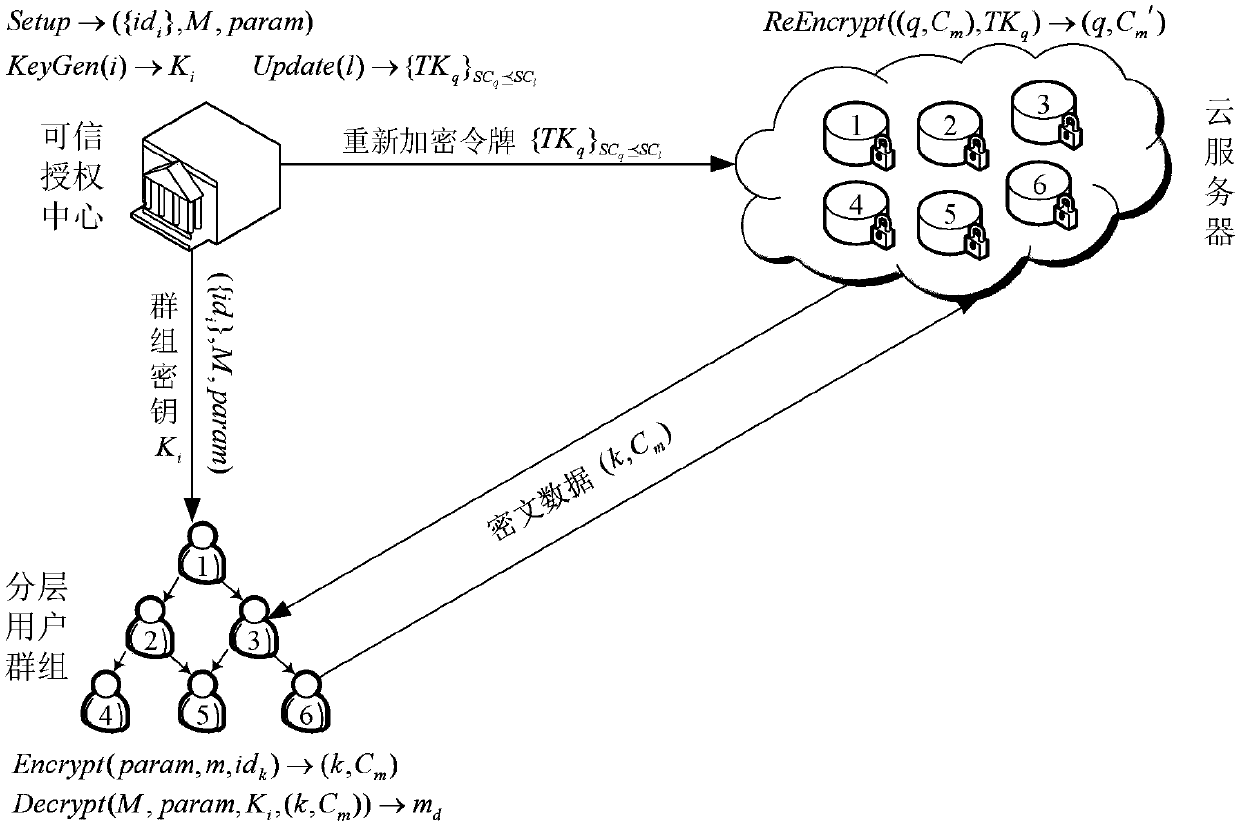
Hierarchical access control system and method for supporting data sharing in cloud storage
The invention belongs to the technical field of protection of data access through a platform, and discloses a hierarchical access control system and method for supporting data sharing in cloud storage. The hierarchical access control method for supporting data sharing in cloud storage comprises: a trusted authorization centre generates system secret information and public information, and opens the system public information to users; according to a user group grade structure, the trusted authorization centre generates the secret key of each user group based on a secret key aggregation method,and distributes secret keys to all the corresponding users; the users encrypt data to be shared by utilizing the system public information of any target user group, and upload and store the data in acloud server; valid users obtain ciphertext data stored in the cloud server, and decrypt the data by utilizing a user group secret key; and, when the access permission of a certain user needs to be repealed, the trusted authorization centre and the cloud server perform a system updating and re-encrypting process. According to the hierarchical access control system and method for supporting data sharing in cloud storage disclosed by the invention, oriented towards a cloud storage environment, hierarchical access control supporting flexible data security sharing and without a secret key deduction process in a public key cryptography system can be realized.
Owner:XIDIAN UNIV
File encrypting and decrypting method and device based on mobile phone
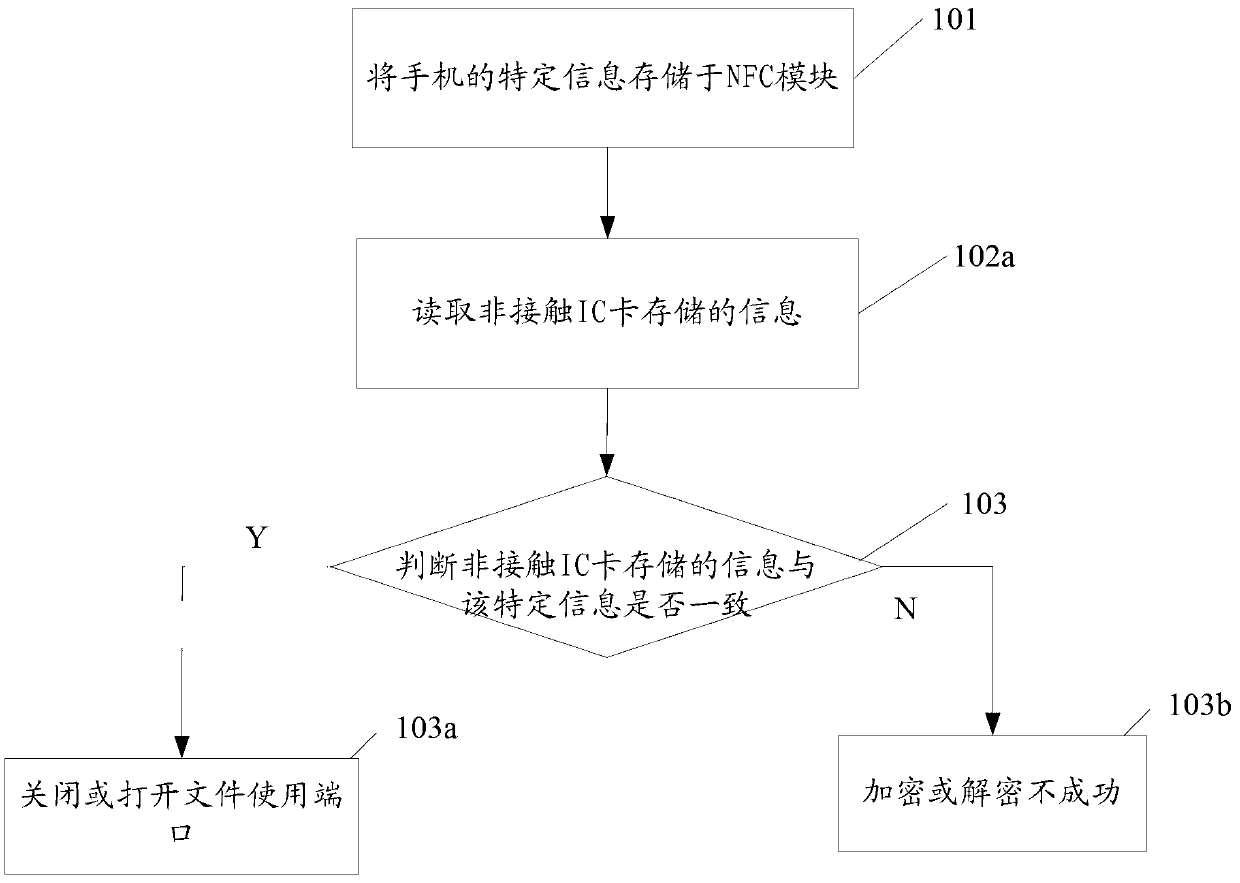
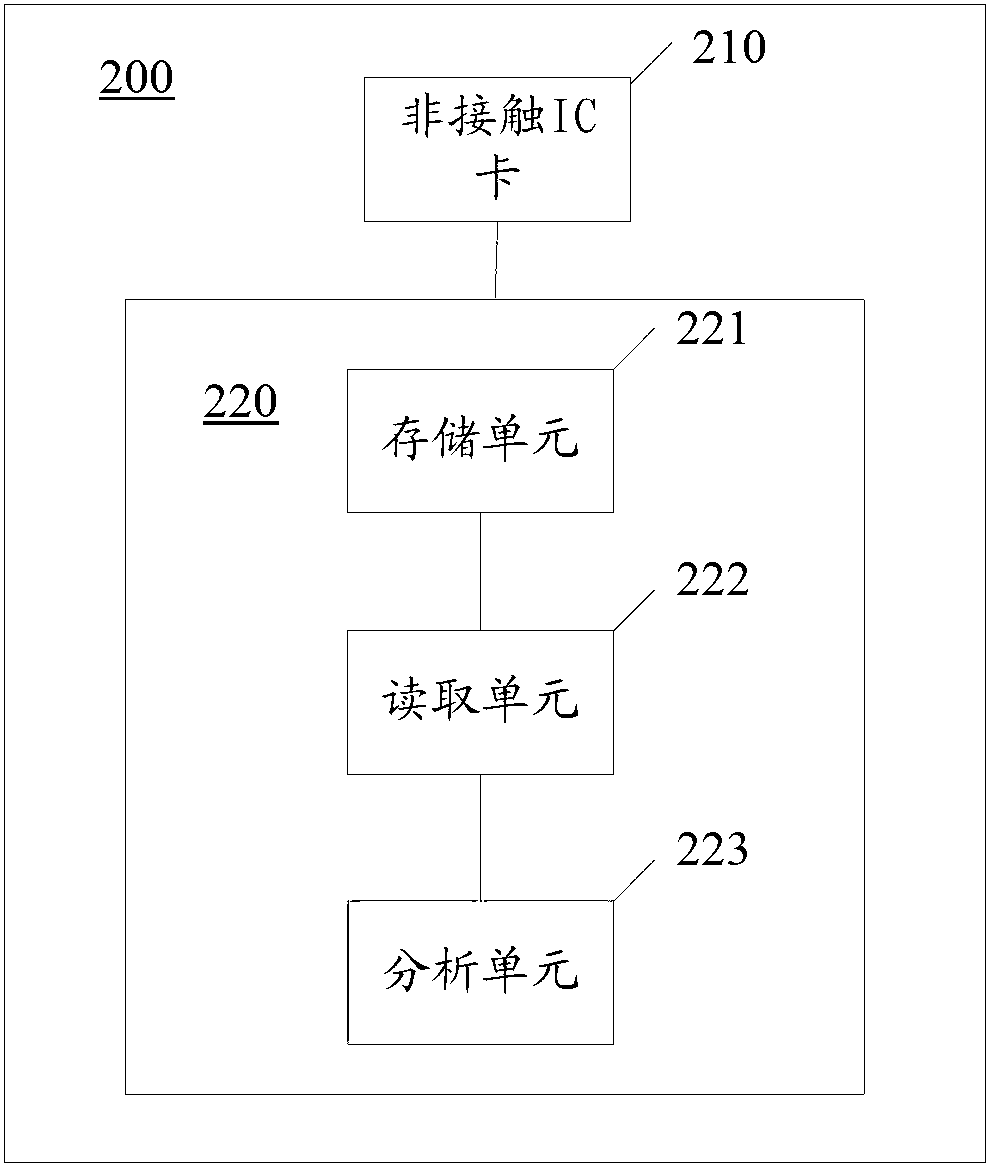
InactiveCN103279692AImplement encryptionAchieve decryptionNear-field transmissionDigital data protectionComputer hardwareMobile phone
The invention discloses a file encrypting and decrypting method based on a mobile phone. The file encrypting and decrypting method based on the mobile phone comprises the steps that specific information of the mobile phone is stored in an NFC module, the NFC module reads the information stored in a non-contact IC card, whether the information stored in the non-contact IC card is conformed with the specific information or not is judged, and a file using port is closed or opened to achieve encryption or decryption if the information stored in the non-contact IC card is conformed with the specific information. The encryption and the decryption of the file encrypting and decrypting method based on the mobile phone are convenient to operate, swift in operation, and high in safety. The invention further discloses a file encrypting and decrypting device.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
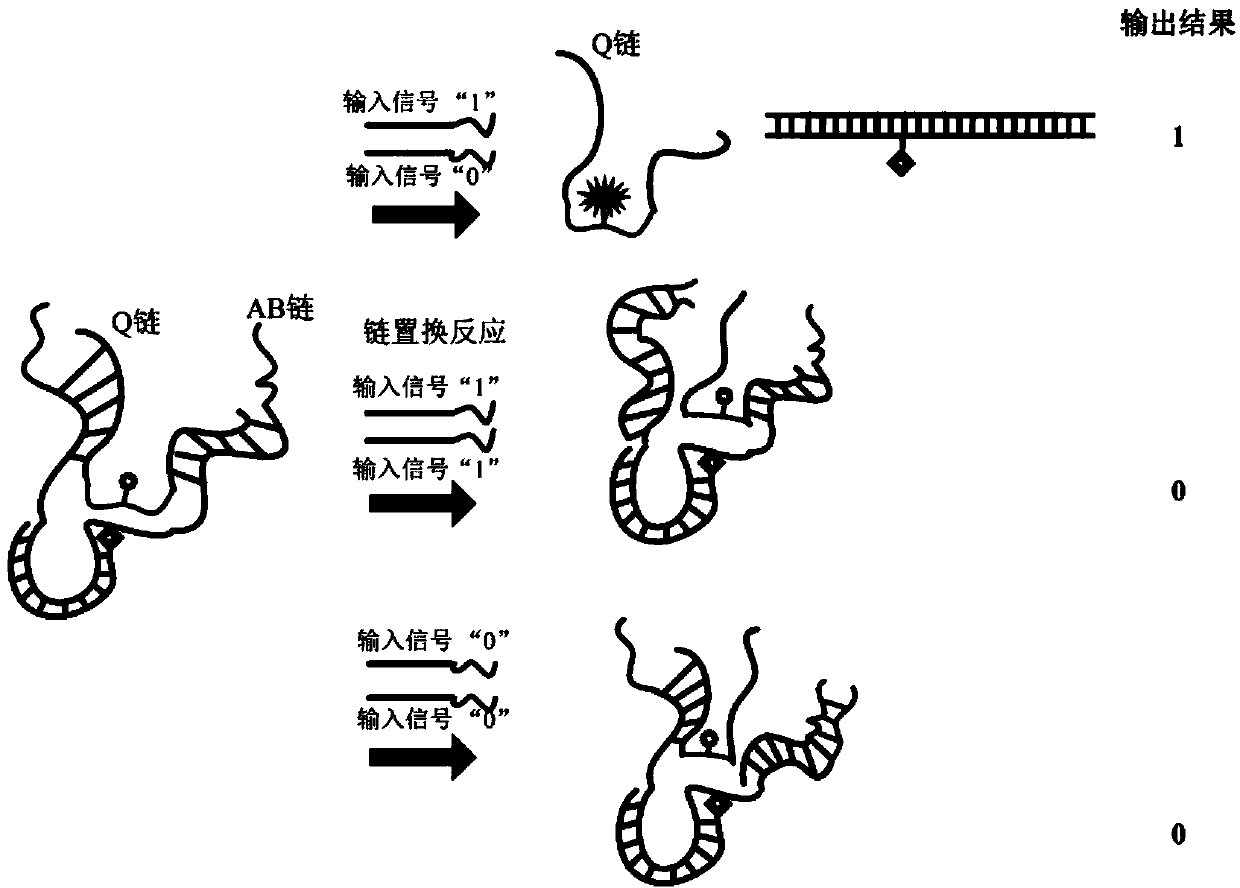
DNA self-assembling structure and symmetrical encryption system based on DNA self-assembling structure
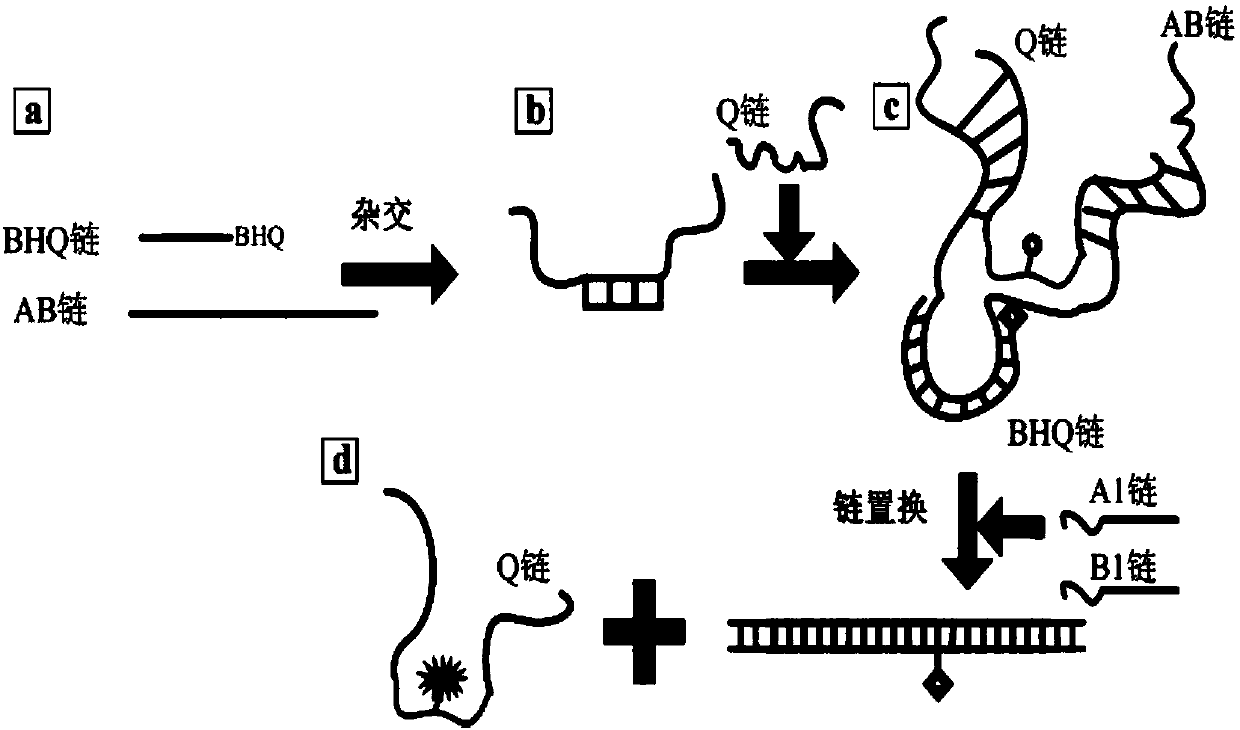
ActiveCN103997404AGuaranteed unhackabilityImplement encryptionEncryption apparatus with shift registers/memoriesNano structuringPassword
The invention relates to a DNA self-assembling structure and a symmetrical encryption system based on the DNA self-assembling structure. The DNA self-assembling structure comprises a bubble structure and is formed by a DNA nano structure and a chain Q through base pairing. The DNA nano structure is formed by a DNA chain AB and a BHQ chain in a hybridization mode. The huge parallelism capacity and the large-scale information searching and single-molecular recognizing capacities of DNA are utilized, inherent advantages of finishing information converting, transmitting and detecting through different detecting methods utilized in the complex biology body are possessed, and then the encryption and decryption in the stream encryption method are achieved based on difficulty of the nano technology in the large scale information searching and the DNA self-assembling structure. According to the symmetrical encryption system, the AB chain specific recognition area and the chain converting technology are adopted, xor operation is achieved, one-time pad information encryption and decryption are achieved, and therefore passwords can be hard to crack, and information storing and conveying safety is improved. The DNA self-assembling structure and the symmetrical encryption system based on the DNA self-assembling structure can be widely applied various password fields.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Safe starting method and device
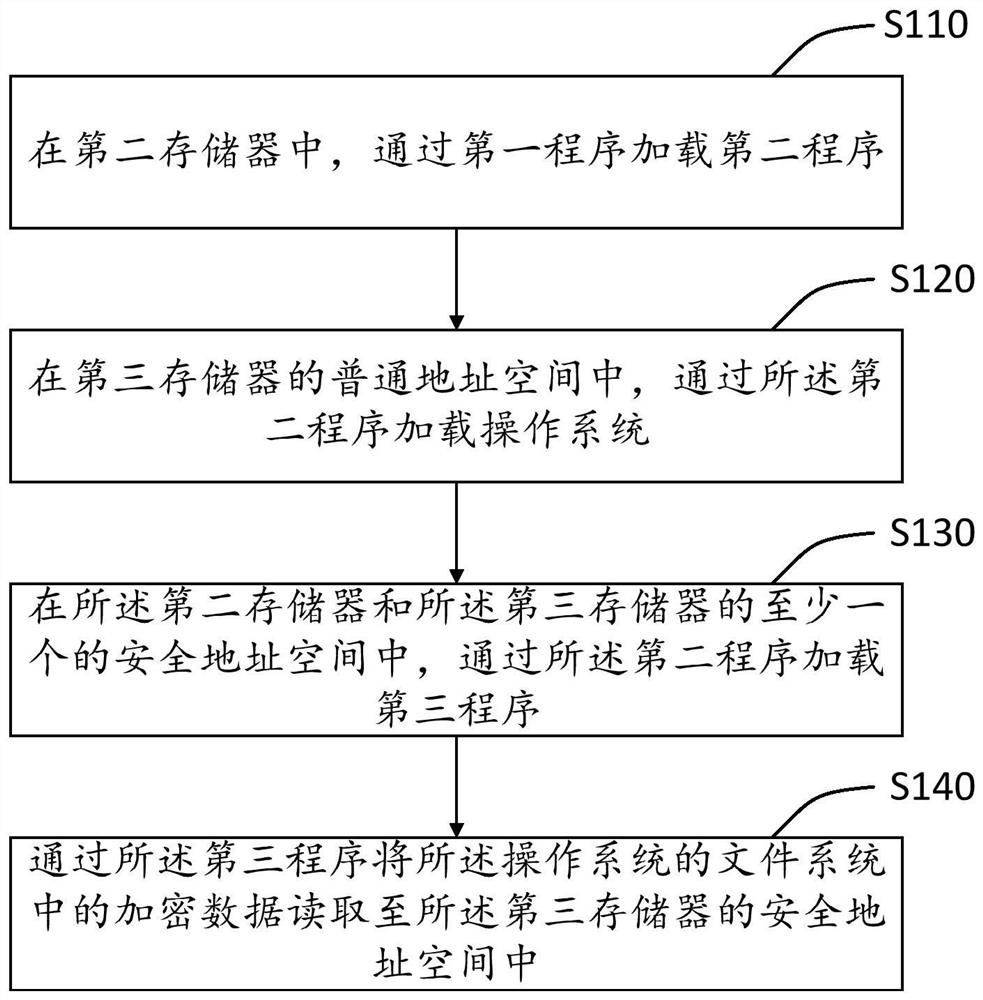
PendingCN112069506AStrong upgradeabilityReduce resource requirementsDigital data protectionPlatform integrity maintainanceOperational systemFile system
The invention discloses a safe starting method and device. The method comprises the steps: in a second memory, loading a second program through a first program, wherein the first program is stored ina safe address space of a first memory; loading an operating system through the second program in a common address space of a third memory; loading a third program through the second program in the safe address space of at least one of the second memory and the third memory; and reading the encrypted data in the file system of the operating system into the safe address space of the third memory through the third program. Loading and decryption of large-scale security data can be realized while hardware resource requirements of an SRAM and the like are reduced, leakage of chip security data isprevented, illegal attacks are avoided, and the security of devices such as a chip and the like is improved while the system cost is reduced.
Owner:HORIZON ROBOTICS SHANGHAI ARTIFICIAL INTELLIGENCE TECH CO LTD
Encryption method and device
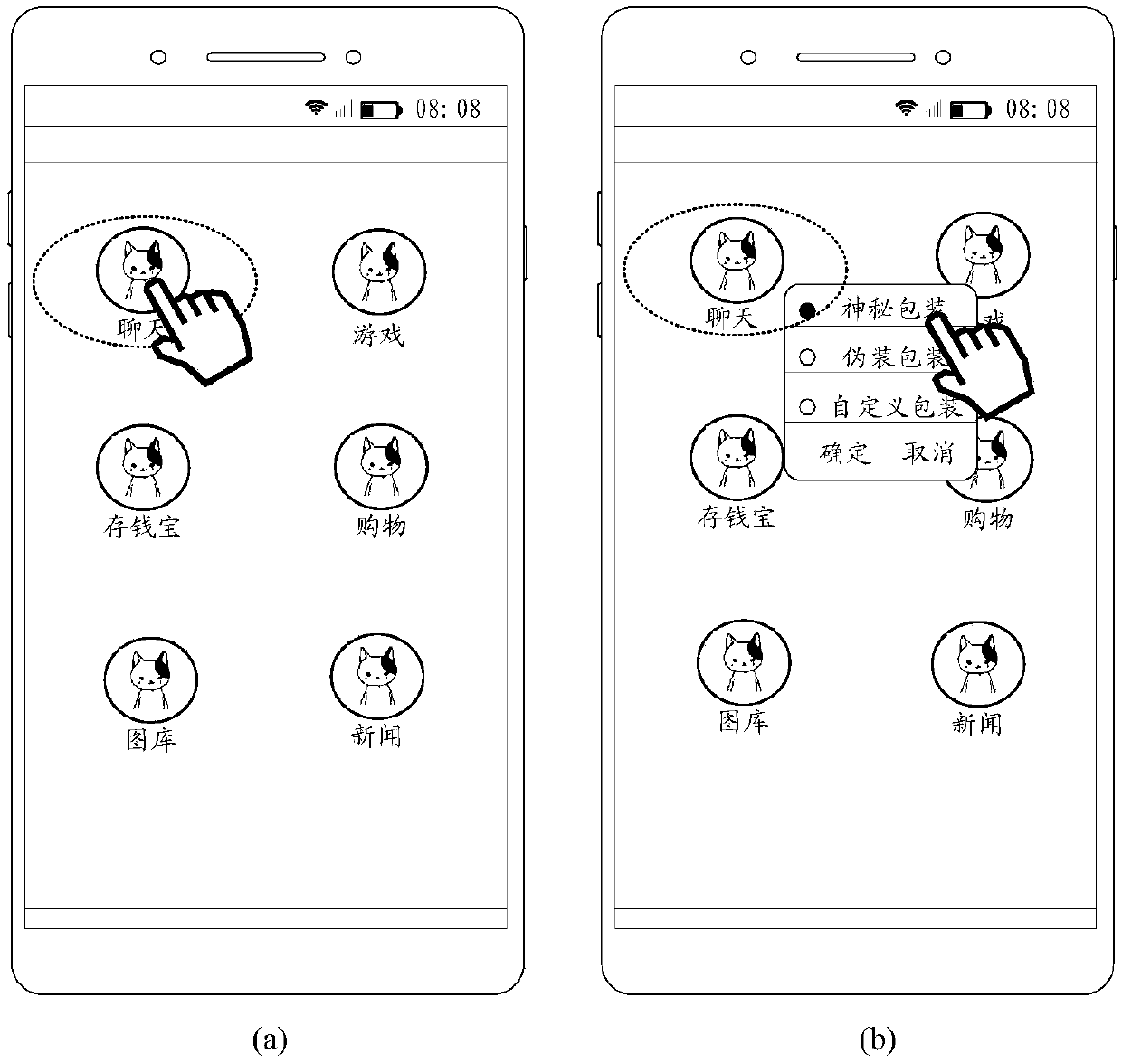
ActiveCN108681664AImprove experienceDifficult to identifyDigital data authenticationInput/output processes for data processingComputer hardwareEncryption
The embodiment of the invention discloses an encryption method and device, relates to the technical field of communication, and aims to solve the problem of limitation and poor flexibility of the existing encryption mode. The encryption method comprises the steps: receiving a first input of a user on a first interface; in response to the first input, displaying a target area corresponding to the first input and prompt information on the first interface, wherein the prompt information is used for reminding the user to select an encryption mode for encrypting a target object which is an object in the target area; receiving a second input of the user on the prompt information; and in response to the second input, encrypting the target object by adopting a first encryption mode selected by theuser. The encryption method can be applied to a scenario of encrypting the content of a terminal.
Owner:VIVO MOBILE COMM CO LTD
Connection device and data transmission method
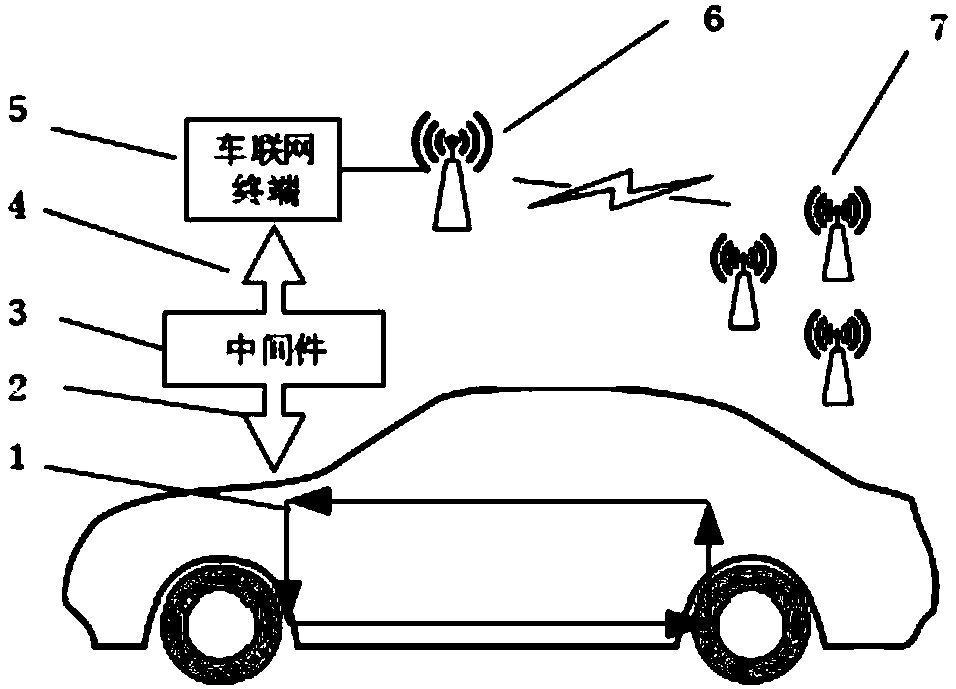
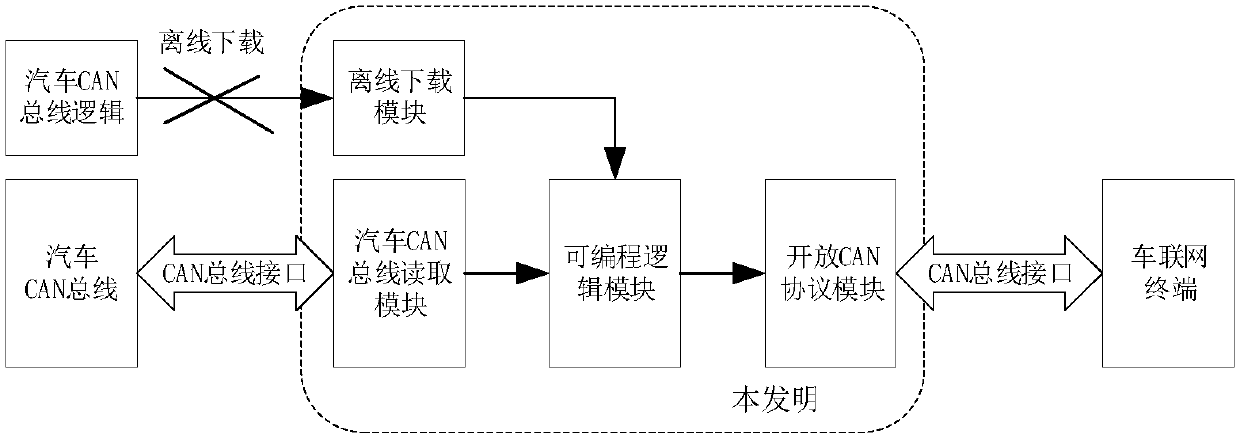
ActiveCN108040082ANot attackedMeet reading needsBus networksProgrammable logic deviceProgrammable logic controller
The invention provides a connection device comprising an offline downloading module, a vehicle CAN bus reading module, a programmable logic module and an open CAN protocol module, wherein the vehicleCAN bus reading module is connected with a vehicle CAN bus and the programmable logic module, the open CAN protocol module is connected with the programmable logic module and an Internet of Vehicles terminal, and the offline downloading module is connected with the programmable logic module. A vehicle-mounted terminal and the vehicle CAN bus physically isolated to overcome the information securityproblem resulting from the fact that the existing Internet of Vehicles terminal directly reads CAN bus messages, and the CAN bus data are isolated and protected while the Internet of Vehicles terminal reads the CAN bus data.
Owner:CHANGAN UNIV
Phosphorescent iridium complex with stimuli responsibility, preparation method and application
InactiveCN103936795AExcellent photophysical propertiesEasy to adjust emission wavelengthGroup 8/9/10/18 element organic compoundsLuminescent compositionsIridiumElectricity
The invention relates to a phosphorescent iridium complex with stimuli responsibility. The phosphorescent iridium complex is composed of a cyclometalated ligand, a metal center and an assistant ligand containing an active function group, and has the structure general formula shown in the specification. The compound disclosed by the invention is capable of causing variation of phosphorescence emission wavelength under stimulation of an acidic or basic reagent; also under electricity stimulation, the compound is capable of causing variation of emission wavelength and also is capable of causing variation of emission lifetime; and based on the electricity stimulation response characteristics and by means of time resolution technology, the phosphorescent iridium complex is applicable to construct memory devices for information recording, encryption and decryption. The phosphorescent iridium complex disclosed by the invention has important application prospect on aspects of information recording, information encryption and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
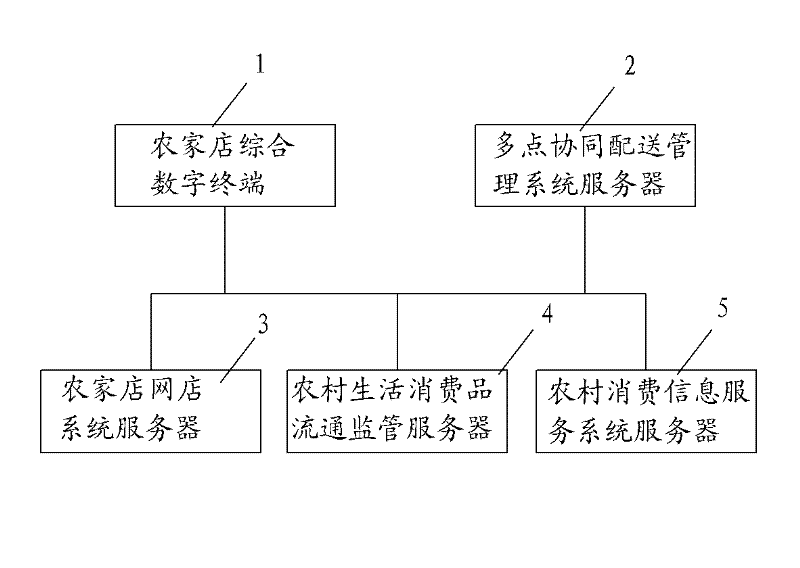
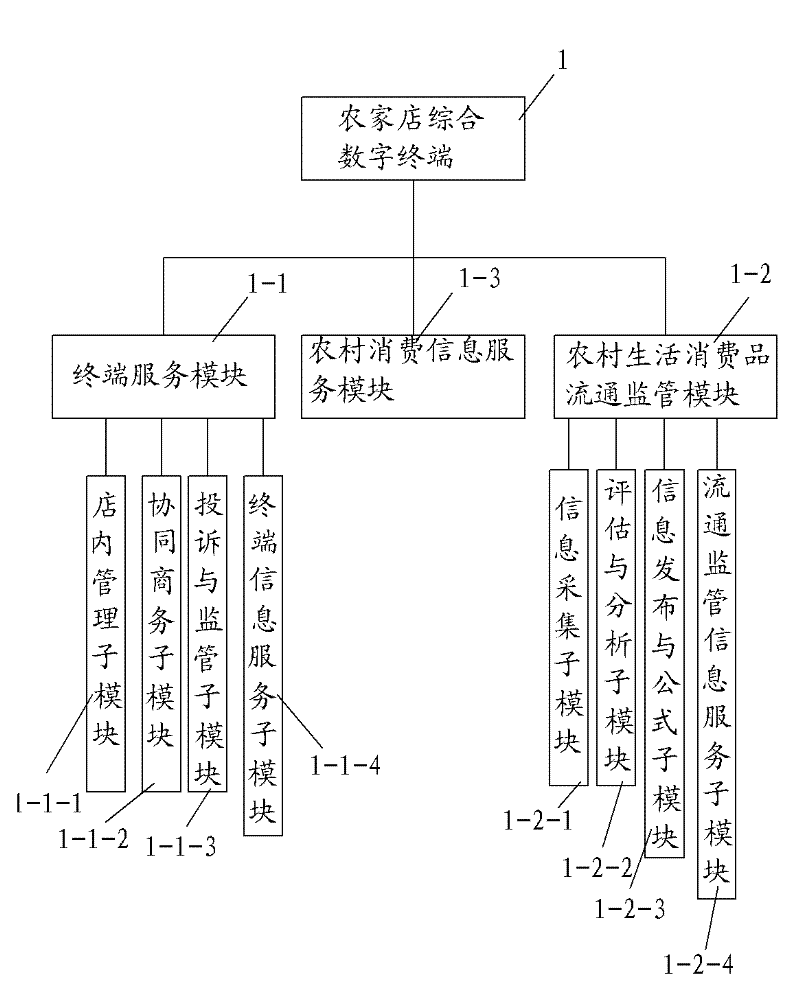
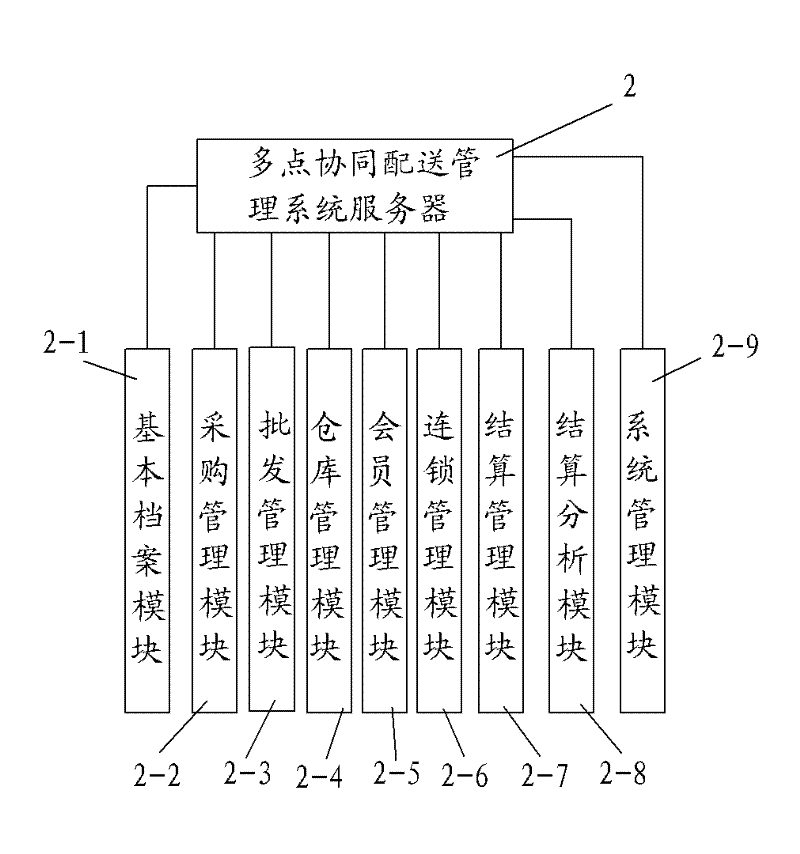
Rural consumer goods circulation application platform
InactiveCN102346875ASimple operation modeRich informationData processing applicationsData acquisitionComputer science
The invention belongs to the goods circulation field, especially relating to a rural consumer goods circulation application platform. The platform comprises a rural store integration digital terminal, a multi-point cooperation dispatching management system server, a rural store network store system server, a rural consumer goods circulation supervision system server, and a rural consumption information service system server which are mutually connected through a network. The platform has the following advantages that: with regards to a rural consumer goods circulation mode, a channel organization with rural stores and consumer goods circulation enterprises as main propulsion power is established, a network has multiple functions, and on the basis of finishing rural store data acquisition, information interaction among a government department, a circulation enterprise, a rural store, and a consumer is realized. Opening a rural store on a network is realized, a rural store operation state is expanded, a capability of rural living article market supervision is reinforced and raised, security and health of rural living articles are ensured, and trust degree of public to quality of domestic rural circulated goods is raised.
Owner:BEIJING ZHONGHE MINBEN TECH
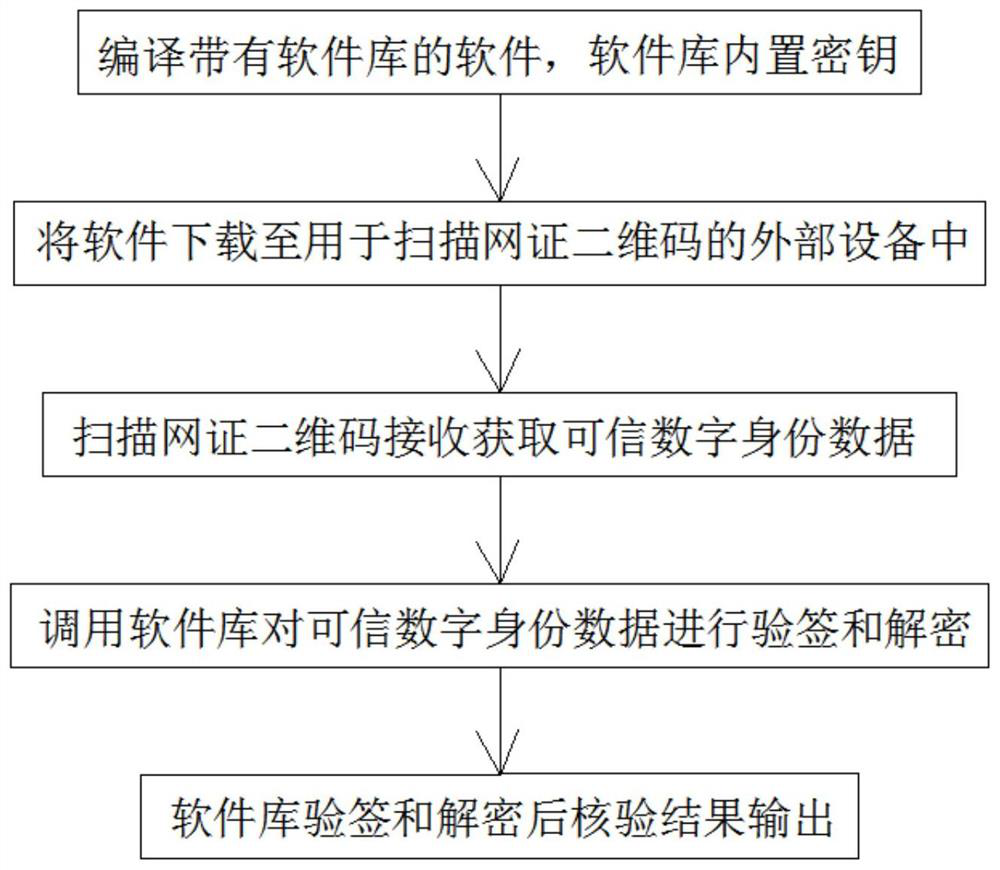
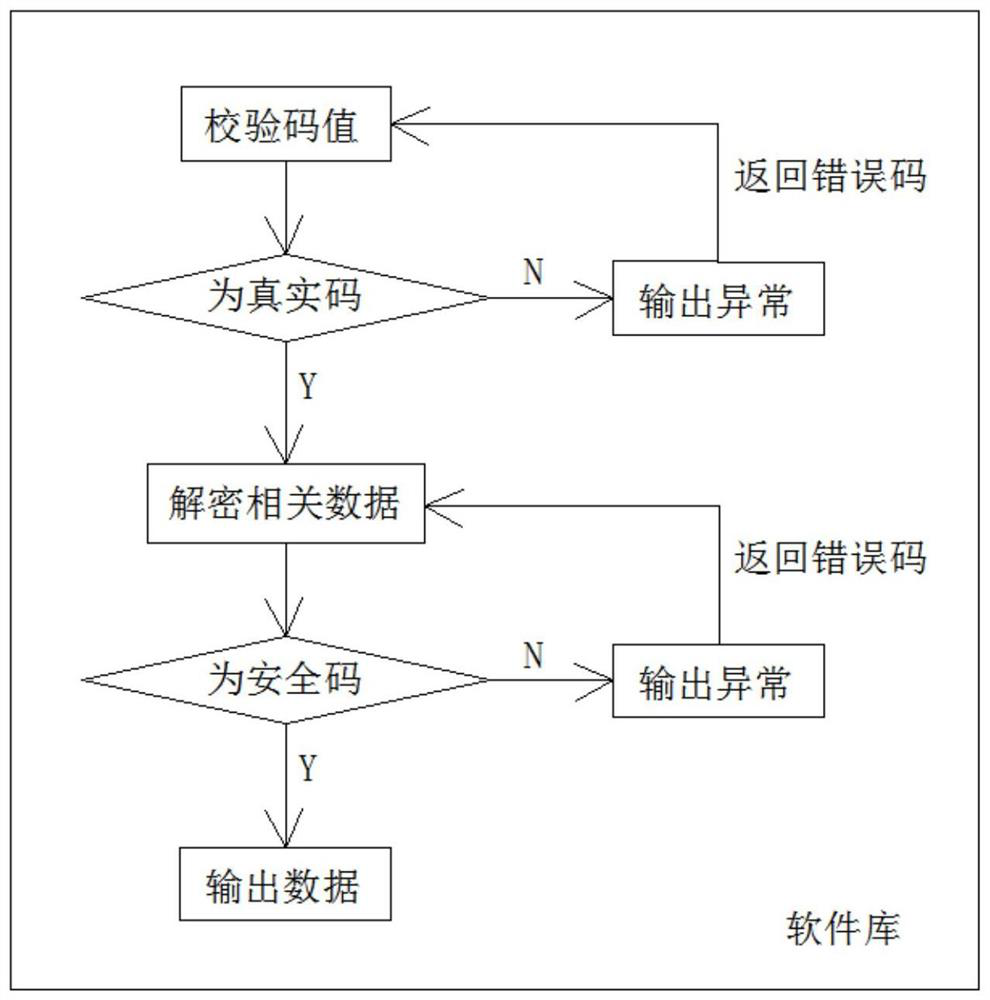
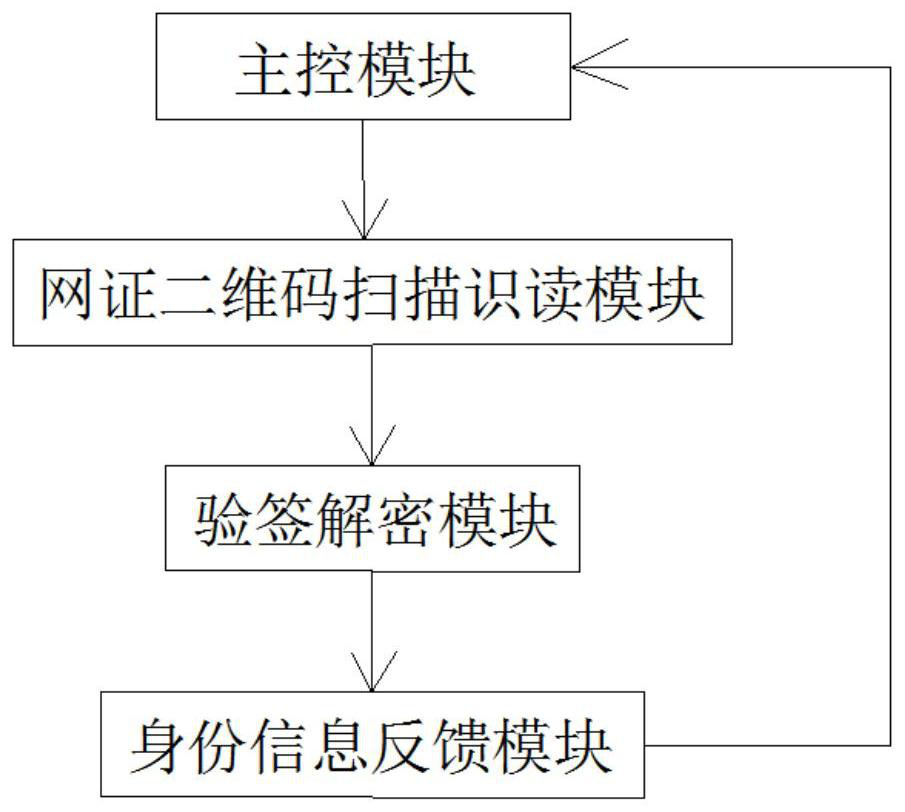
Method, system and device for achieving credible digital identity decryption and signature verification through software library
PendingCN112257046AWith signatureFunctionalCo-operative working arrangementsDigital data protectionDigital identitySoftware engineering
The invention relates to a method for realizing trusted digital identity signature verification and decryption by using a software library and a system and equipment for realizing the method, and themethod comprises the following steps: (1) compiling software with the software library, and setting a secret key required by trusted digital identity reading in the software library, so that the software has signature verification and decryption functions; (2) downloading the software into equipment for scanning the net certificate two-dimensional code, so that the equipment has trusted digital identity verification and decryption functions; (3) the equipment scanning the net certificate two-dimensional code which is issued by the trusted digital identity platform and contains citizen identitydata, and receiving and acquiring the trusted digital identity data; (4) software in the equipment calling a software library to perform signature verification and decryption on the received credibledigital identity data; and (5) after the software library signature verification and decryption operation is finished, returning a verification result to the software and outputting the verificationresult by the equipment.
Owner:新大陆(福建)公共服务有限公司
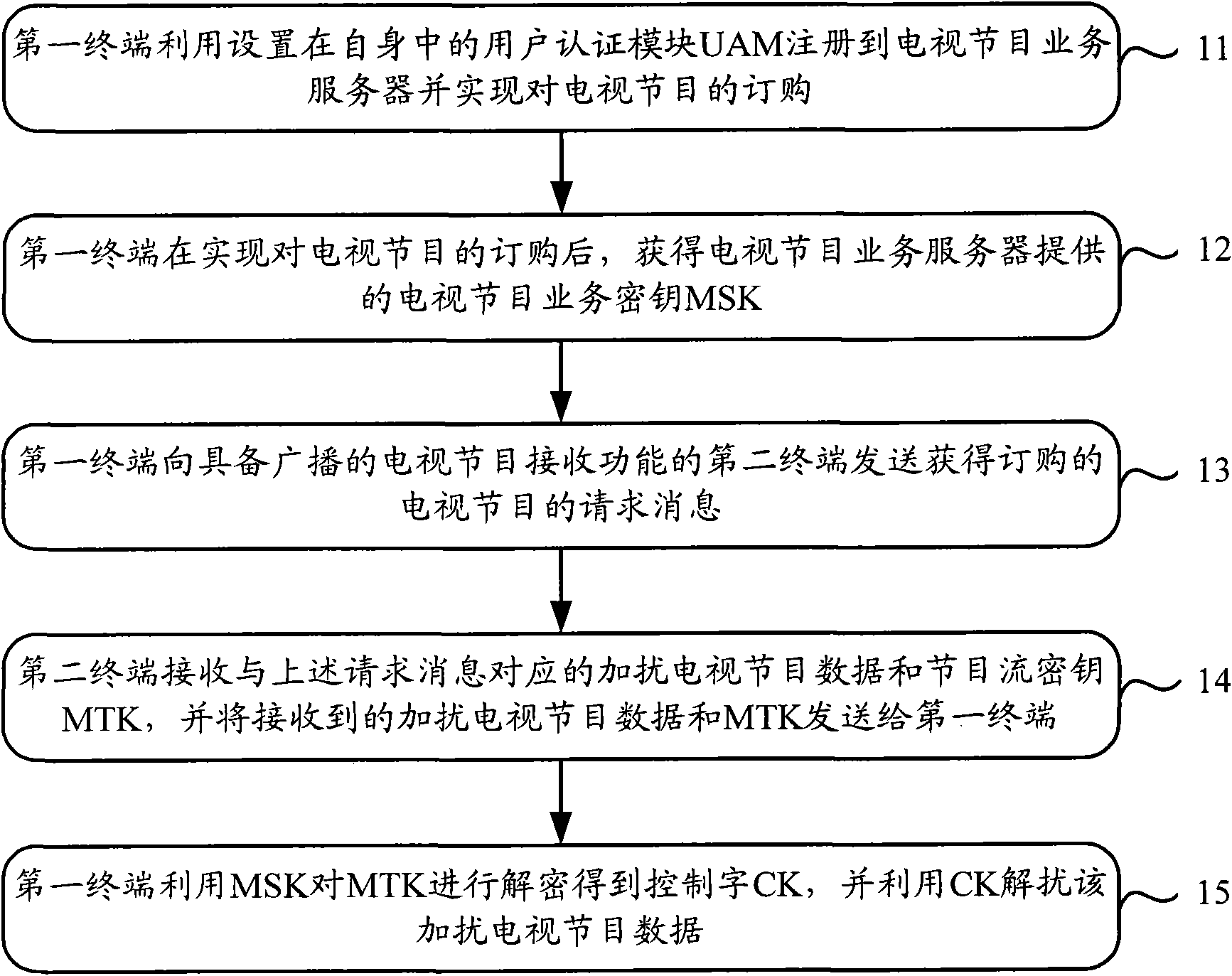
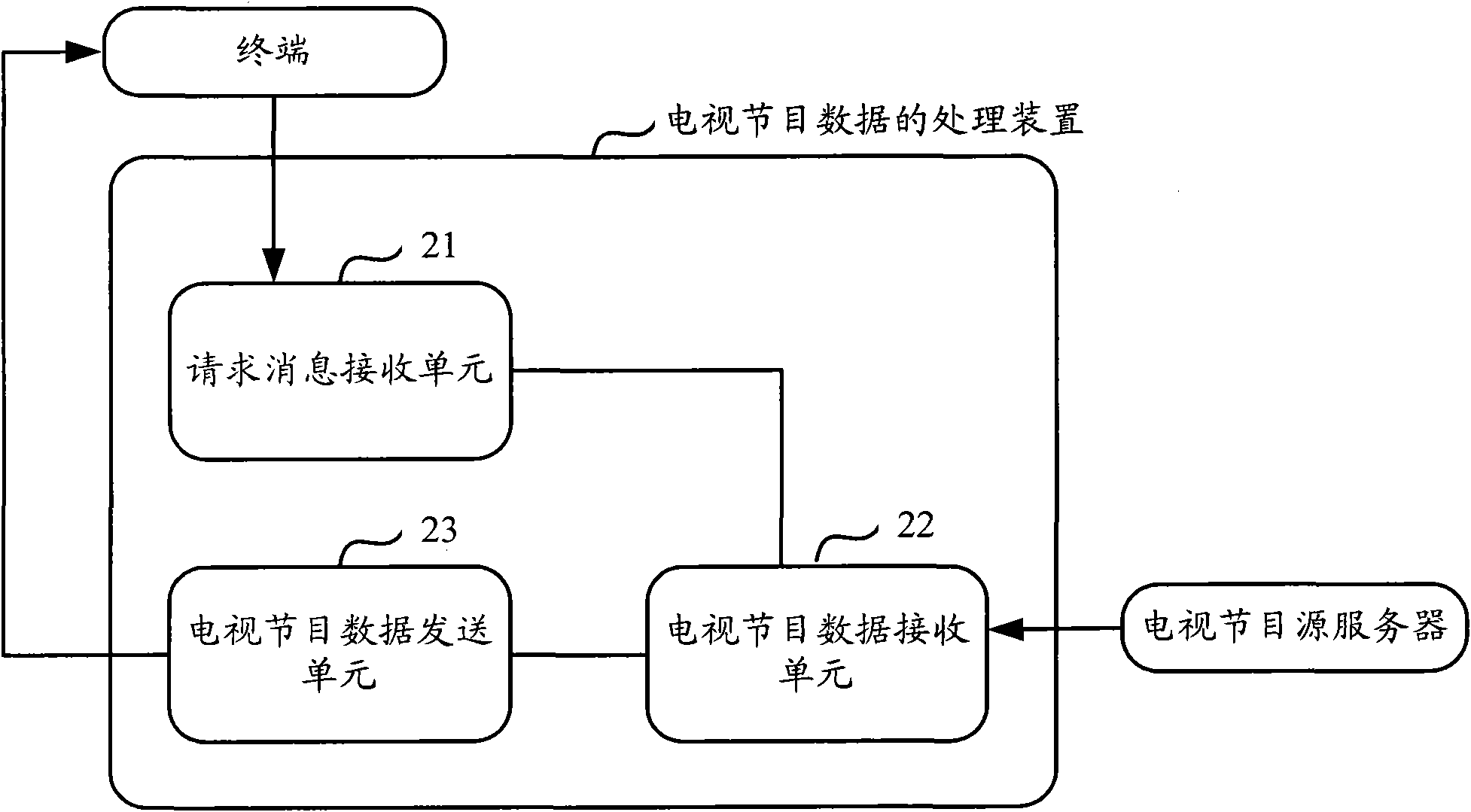
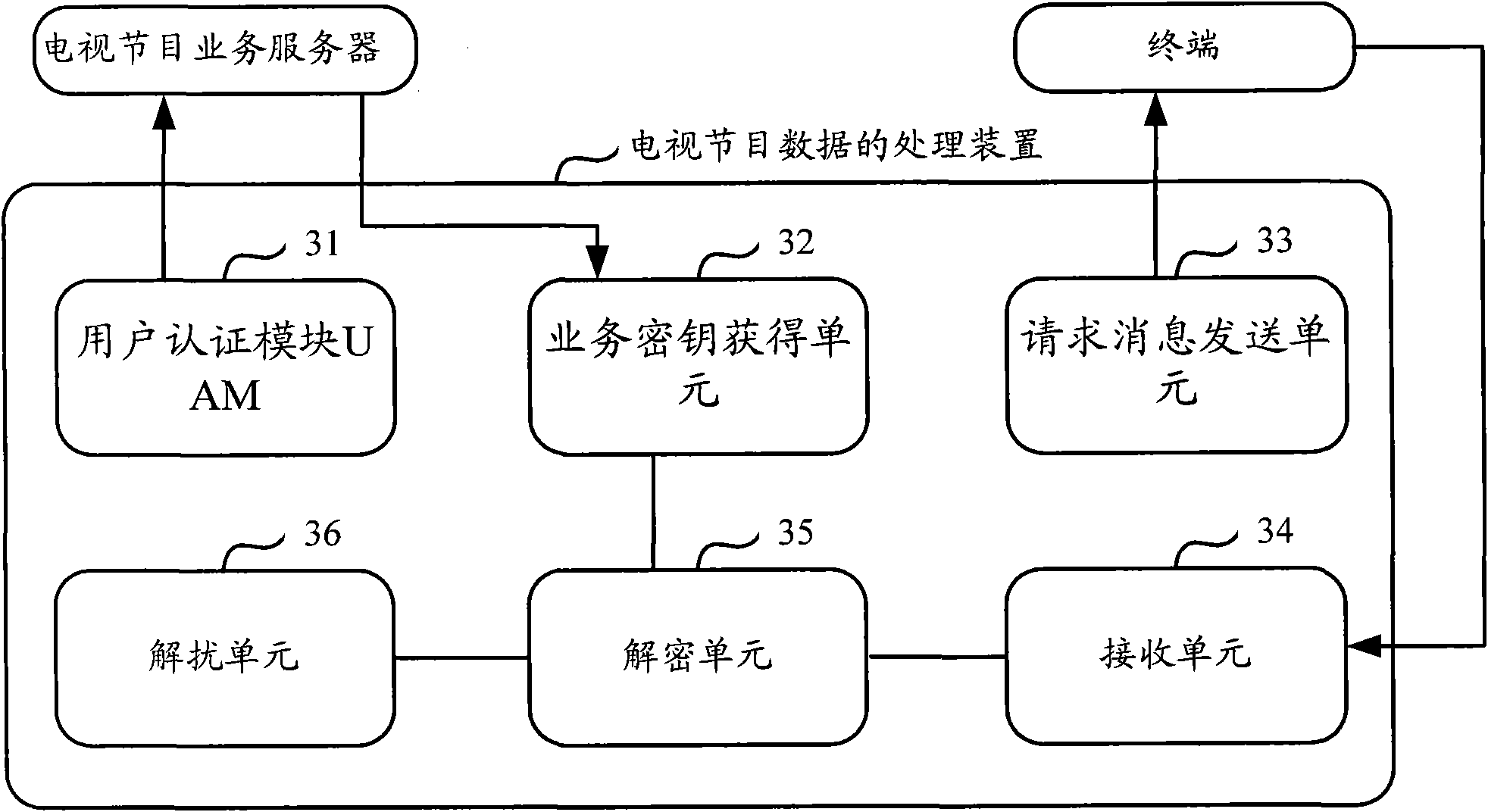
Method and device for processing television program data
InactiveCN102404629AAchieve decryptionAvoid decryptionSelective content distributionComputer hardwareCable television
The invention discloses a method and a device for processing television program data, which are used for solving the problem that in the prior art, when a terminal without a television program data reception function watches television programs with the help of a terminal with the television program data reception function, the former only receives the television program data received by the latter, and the former cannot descramble scrambled television program data. The method comprises the following steps: a first terminal realizes television program subscription through registering into a television program service server by using UAM so as to obtain MSK, and sends a request message of subscribed television programs to a second terminal with the television program reception function; the second terminal receives the scrambled television program data which are broadcasted by a television program source server and corresponding to the request information as well as MTK, and sends the scrambled television program data and MTK to the first terminal; and the first terminal decrypts the MTK by using the MSK so as to obtain a control word CK, and uses CK to descramble the scrambled television program data.
Owner:CHINA MOBILE COMM CO LTD
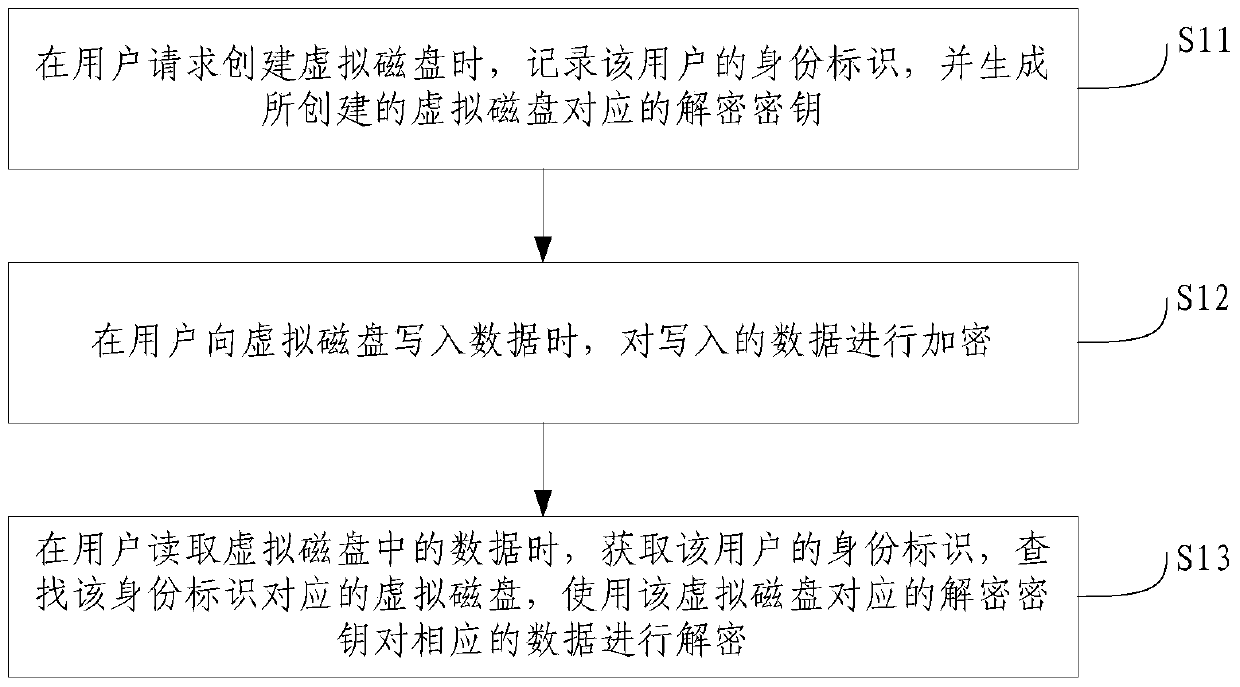
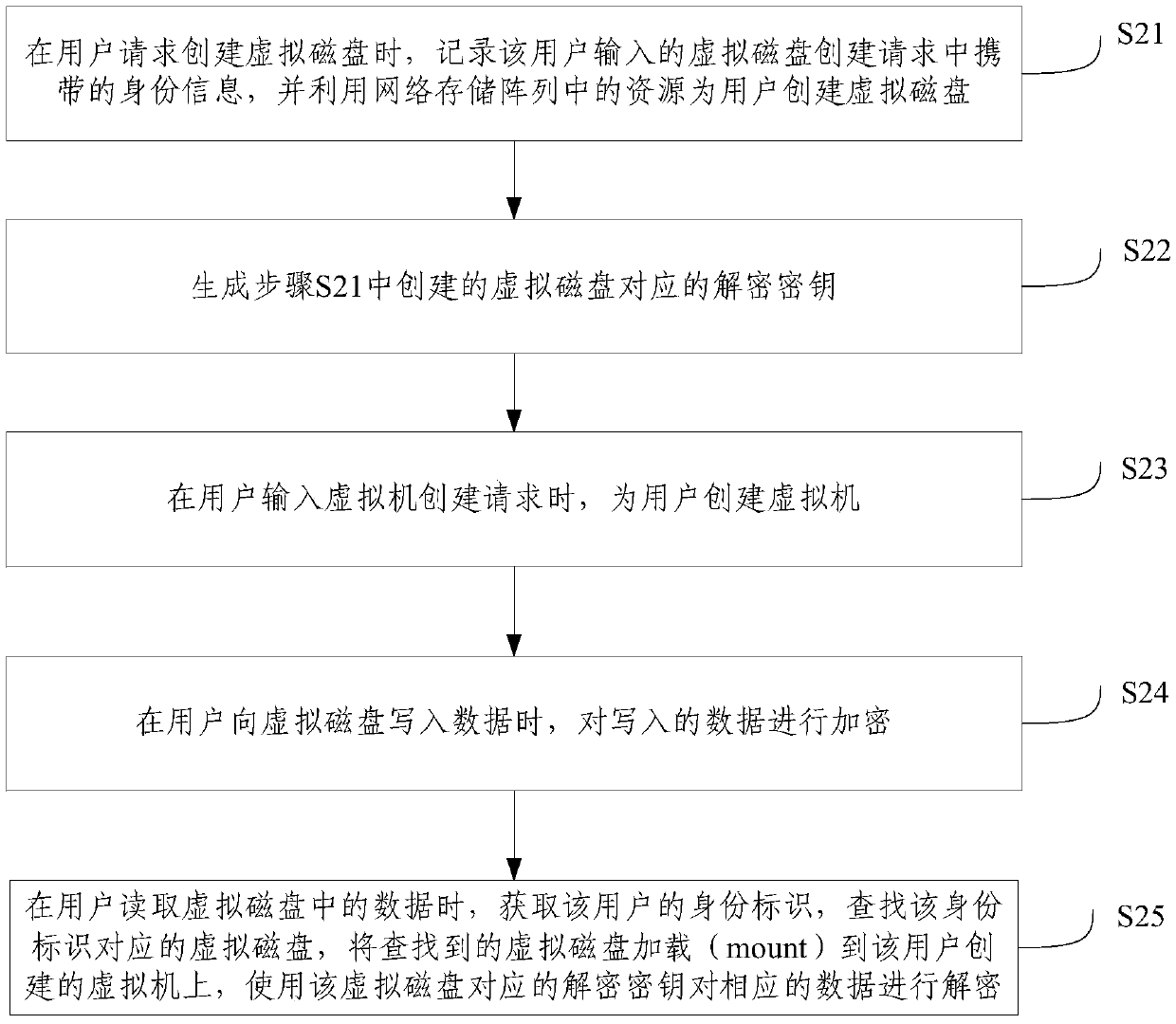
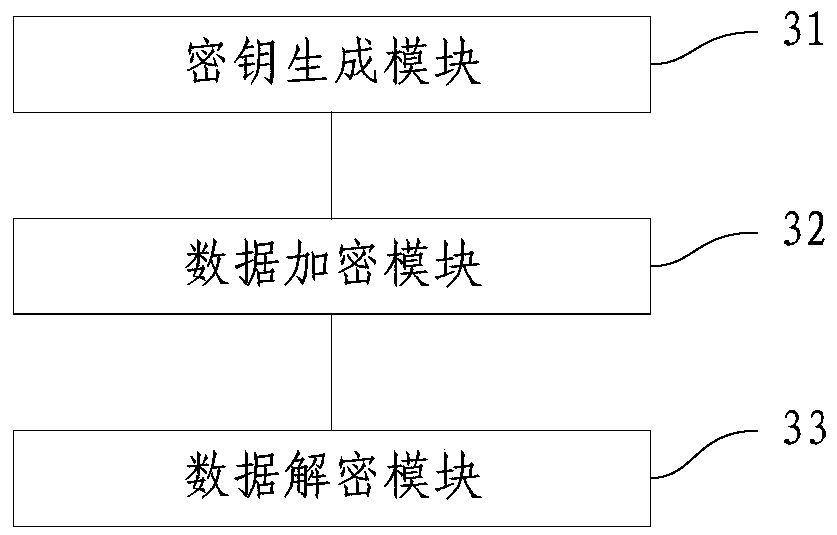
Cloud platform virtual disk encryption method and system
InactiveCN105512575AImplement encryptionAchieve decryptionInternal/peripheral component protectionDigital data authenticationEncryptionDisk encryption
The invention provides a cloud platform virtual disk encryption method. The method comprises the following steps of recording a user identity label when the user requests to create a virtual disk and generating a decoding encryption key corresponding to the created virtual disk, encrypting written data when the user writes data to the virtual data, acquiring the user identity label when the user reads the data in the virtual disk, looking for the virtual disk corresponding to the identity label and decoding the corresponding data via the decoding encryption key corresponding to the virtual disk. By the use of the cloud platform virtual disk encryption method, data in the virtual disk can be encoded and decoded, so safety of the data in the virtual disk can be improved.
Owner:北京汉柏科技有限公司
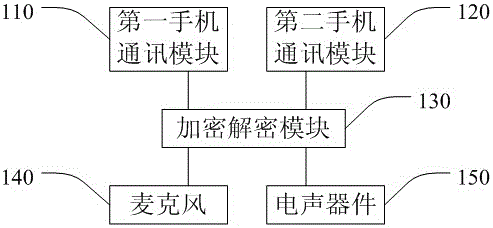
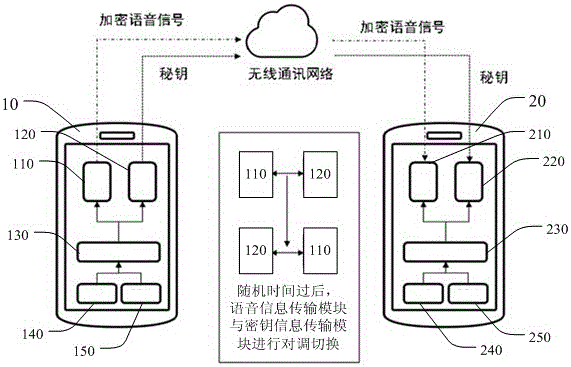
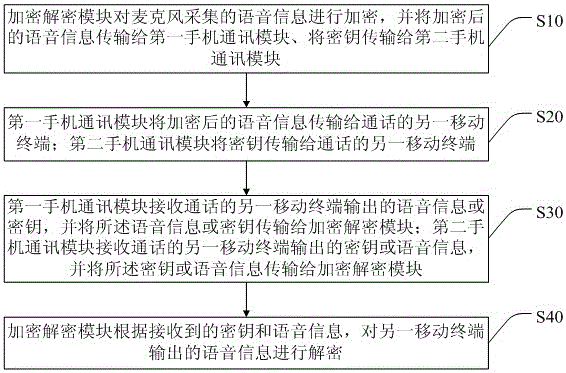
Mobile terminal capable of encrypting voice information and encryption method thereof
InactiveCN105722069AImprove securityAchieve decryptionTransmissionSecurity arrangementMicrophoneMobile phone
The invention discloses a mobile terminal capable of encrypting voice information and an encryption method thereof. The mobile terminal comprises an encryption and decryption module, a first mobile phone communication module and a second mobile phone communication module. In the invention, voice information acquired by a microphone is encrypted through the encryption and decryption module; the encrypted voice information is transmitted to the first mobile phone communication module; the first mobile phone communication module transmits the voice information to another mobile terminal communicating with the mobile terminal; and the encryption and decryption module also transmits a secret key to another mobile terminal through the second mobile phone communication module. According to the invention, separate transmission of secrete keys of the voice information is realized; the encryption security is improved; after the secret key and the voice information output by another mobile terminal are received, the voice information is encrypted through the encryption and decryption module; therefore, decryption of the voice information is realized; even though any channel of two communicating mobile terminals is monitored, a monitor cannot obtain all information; and thus, the encryption security is improved.
Owner:深圳市创百智能科技有限公司 +1
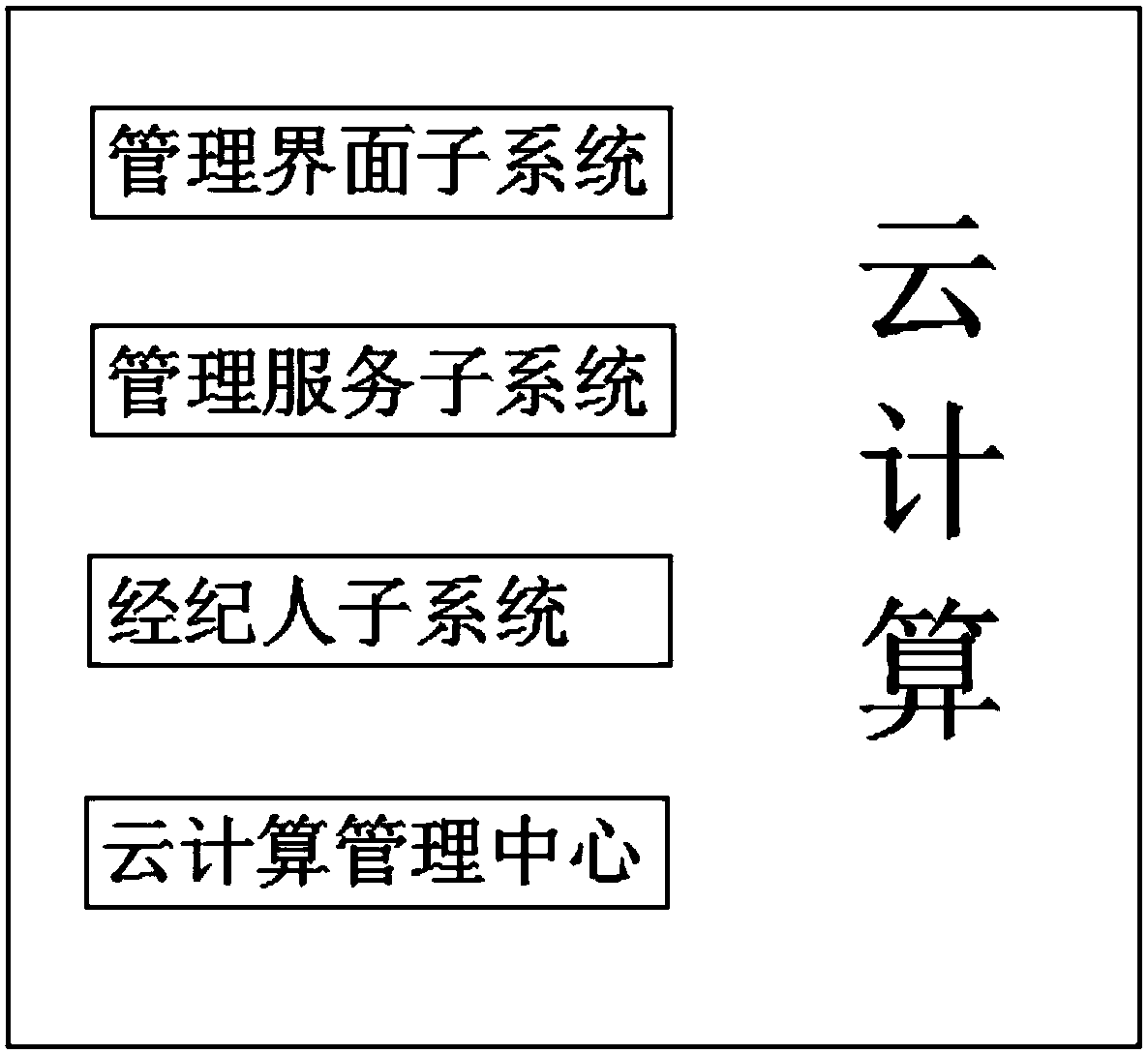
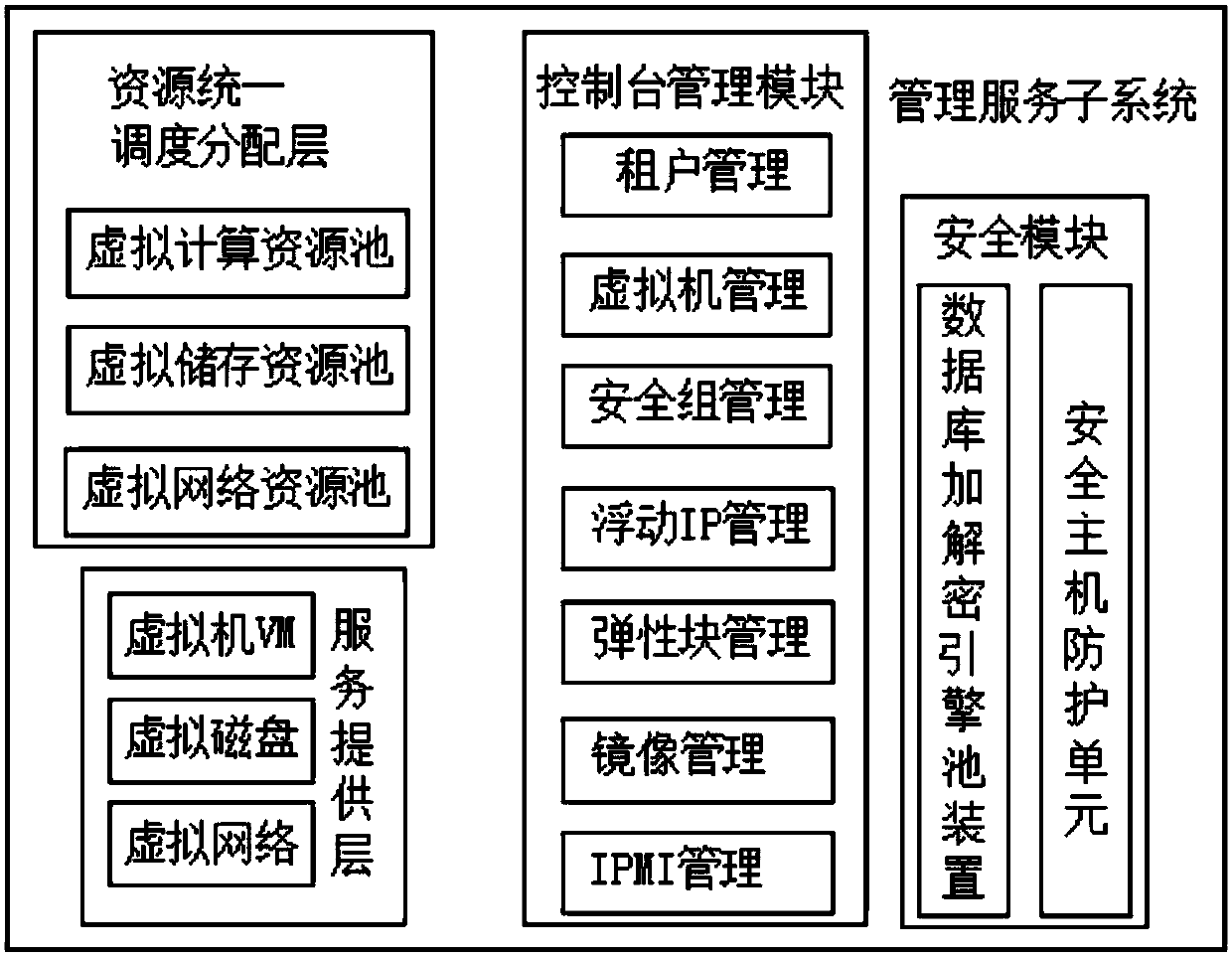
Cloud computing system
InactiveCN107911256AEasy to implementControl and monitor operationsData switching networksComputer terminalComputing systems
The invention discloses a cloud computing system. The cloud computing system comprises a management interface subsystem, a management service subsystem, a broker subsystem and a cloud computing management center. The invention can make full use of the advantages of the cloud computing platform, and facilitate the implementation of cloud computing; through setting a cloud encryption module, the encryption and decryption of the data on a virtual machine is realized, and the security of the data in the cloud computing system is effectively improved; meanwhile, through setting a GUI management interface, the user can control and monitor the operation of the cloud computing system conveniently and intuitively; and a plurality of scheme samples stored in the storage module of the system can be easily invoked by the user, therefore, the use difficulty of the cloud computing system for the general staff is reduced, and it can be ensured that the proxy terminal can continue to use the system mirroring in the local end backup area to call the programs and the data and parameters in the local data area in the cases of communication anomalies or network interruptions, so as to prevent the lossof user data and information in extreme cases.
Owner:李淑芹
Personal privacy protection method in customizable location service
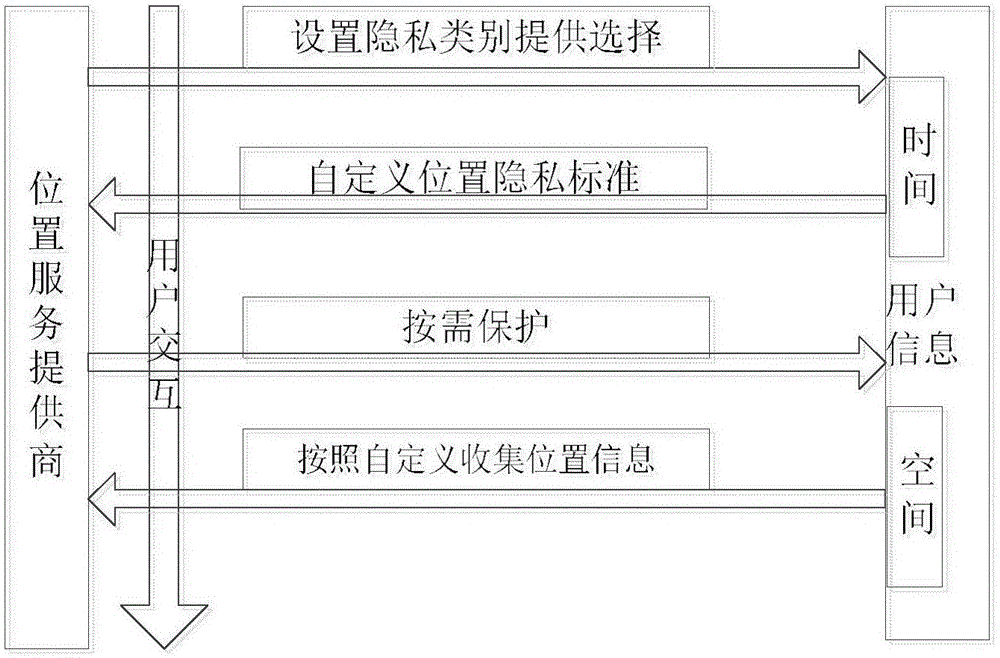
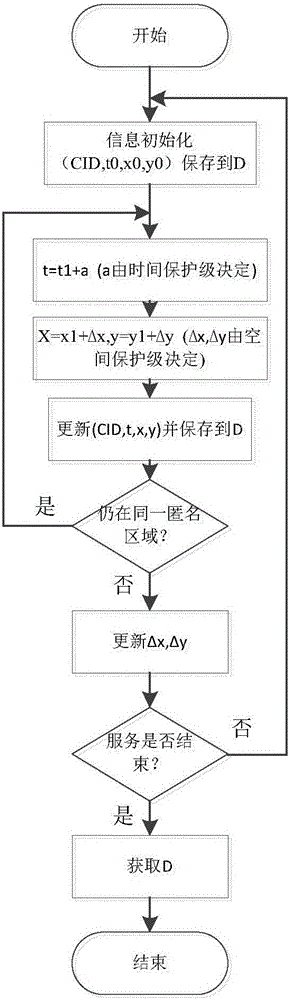
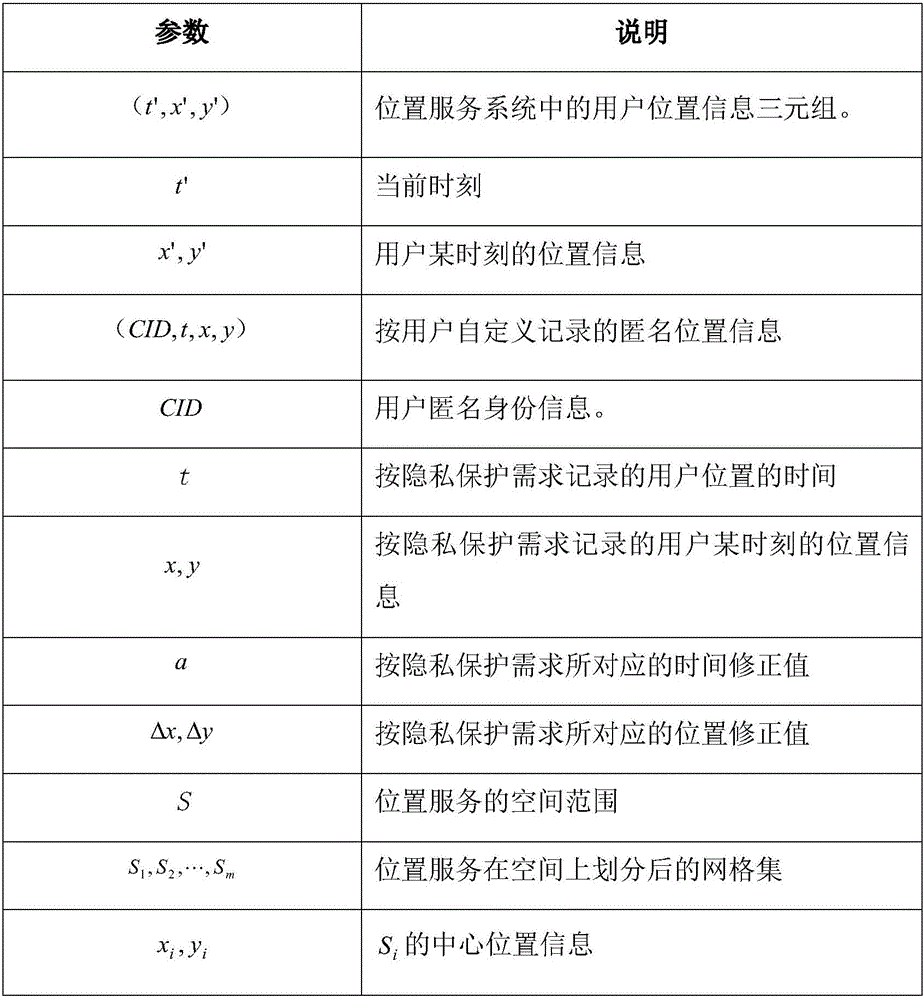
ActiveCN106529337ATo offer comfortAchieve decryptionDigital data protectionSpecial data processing applicationsUser needsUser privacy
The present invention discloses a personal privacy protection method in a customizable location service. The method comprises: classifying personal location information according to the two dimensions of time and space; classifying privacy standards and embedding the privacy standards into a location service system; and applying a personal privacy protection algorithm to protect user privacy on demand, and collecting location information data. According to the method disclosed by the present invention, based on user demand of the location service and different privacy standards of users, the privacy standards are set in the location service system, so as to guarantee that user privacy information of the personal location will not be violated when carrying out latter data collection and release. Thus, location information of users can be protected on demand, so that the problem of privacy leak in the location service is solved; and at the same time, a location service provider can share public location information to better provide the location service, and data decryption is realized to some extent.
Owner:HOHAI UNIV
Data transmission customization system and method
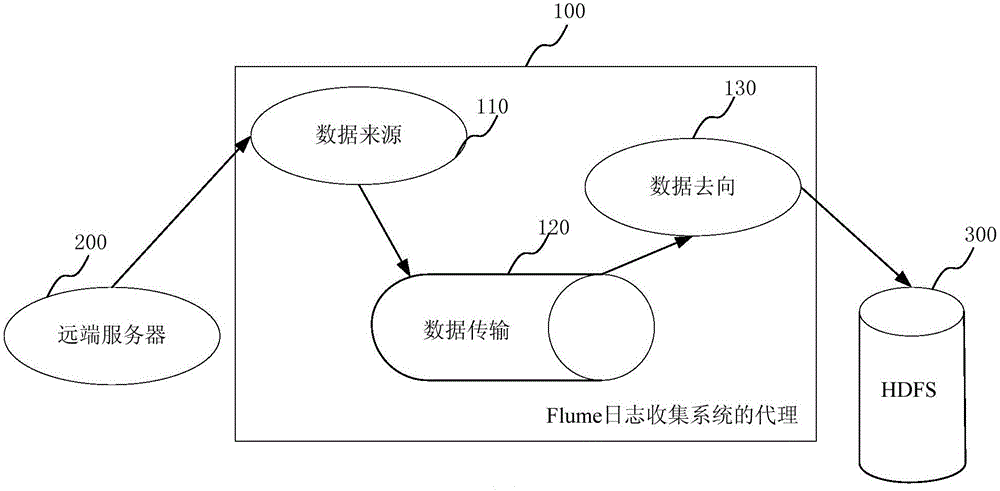
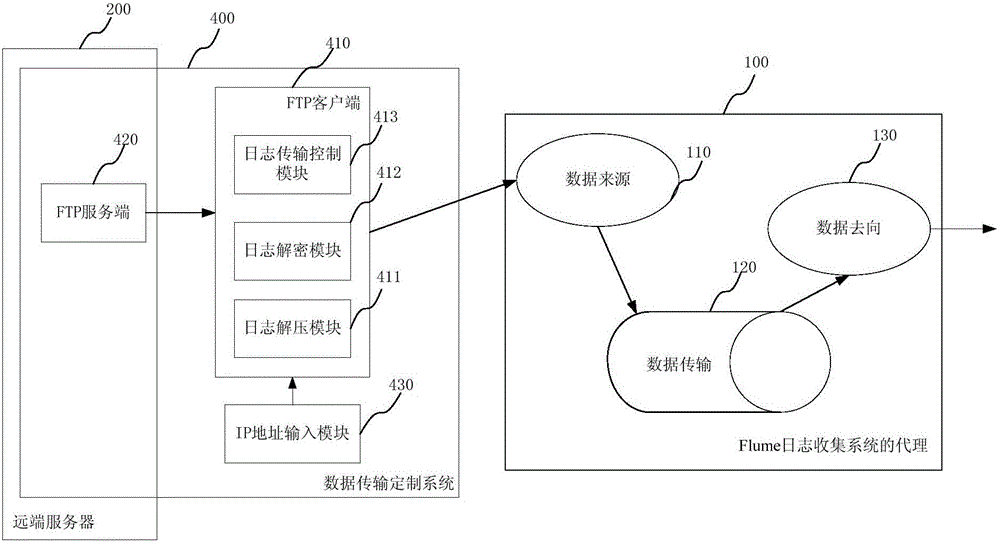
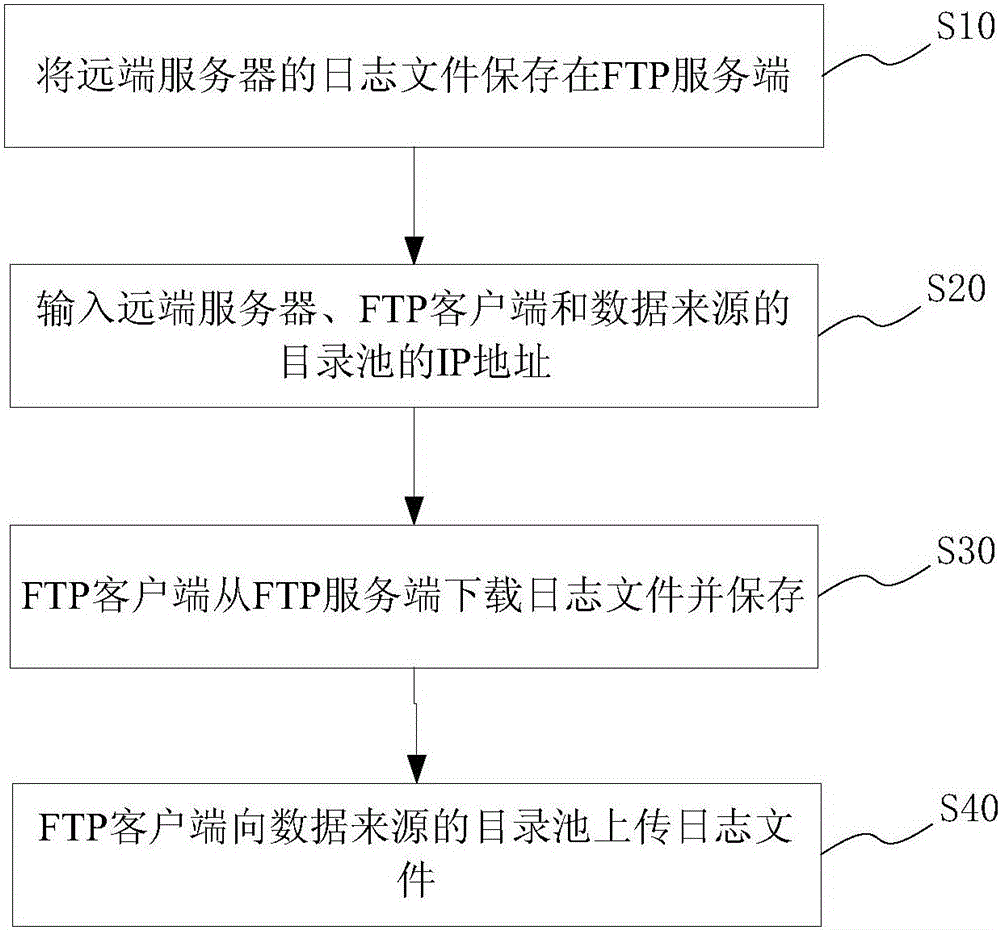
ActiveCN105025090AAddress CustomizabilityImprove collection efficiencyTransmissionCollection systemIp address
The invention provides a data transmission customization system and a method for a Flume event collection system. The data transmission customization system comprises an FTP client, an FTP server and an IP address input module, wherein the FTP server is located at a remote server for storing event files of the remote server; the IP address input module is used for inputting IP addresses of the remote server, the FTP client and a spooling directory of a data source; the FTP client is located between the remote server and the data source for downloading the event file from the FTP server according to the IP address of the remote server; the event file is stored; and according to the IP address of the spooling directory of the data source, the event file is uploaded to the data source. The technical structure of the Flume event collection system is combined, event transmission generality design and development are completed, and the event collection and transmission efficiency is improved.
Owner:好活(重庆)网络科技有限公司
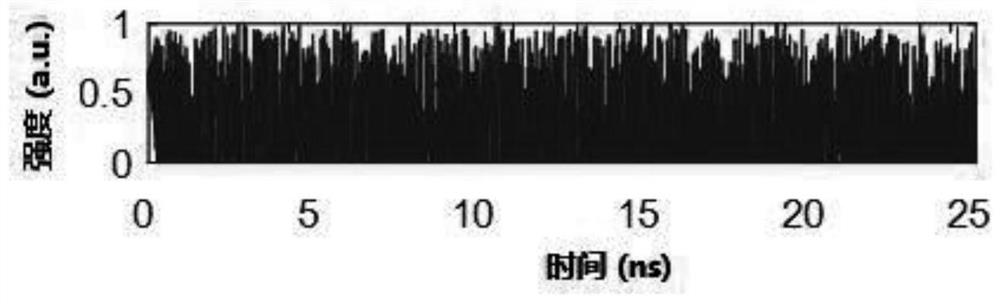
Electro-optic phase mutual modulation chaotic multichannel one-way secret communication system
ActiveCN112713986AAchieve decryptionImprove confidentialityWavelength-division multiplex systemsSecuring communication by chaotic signalsRadio frequencyOptical path
The invention discloses an electro-optic phase mutual modulation chaotic multichannel one-way secret communication system. Four chaotic lasers at a sending end generate four paths of chaotic signals, the chaotic signals are converted into radio-frequency electric signals through a photoelectric detector, and the radio-frequency electric signals are transmitted to corresponding phase modulators to perform phase modulation on optical signals in corresponding optical paths to generate phase chaotic signals. Four paths of phase chaotic signals are converted to different wavelengths through a wavelength converter and are combined into one path through a wavelength division multiplexer to be transmitted to a receiving end, the wavelength division multiplexer at the receiving end divides the signals into four paths, the signals are converted to the same wavelength through the wavelength converter, and the four paths of signals are respectively converted into radio frequency electric signals through corresponding photoelectric detectors, and the optical signals of the corresponding optical paths are subjected to phase modulation through the phase modulator; reverse phase chaos is generated, phase chaos of the optical path signals is counteracted, intensity chaos signals are generated, and the robustness of the intensity chaos is used for decrypting the multiple paths of signals. Multi-channel chaotic synchronous communication is realized, and the confidentiality is high.
Owner:HANGZHOU DIANZI UNIV
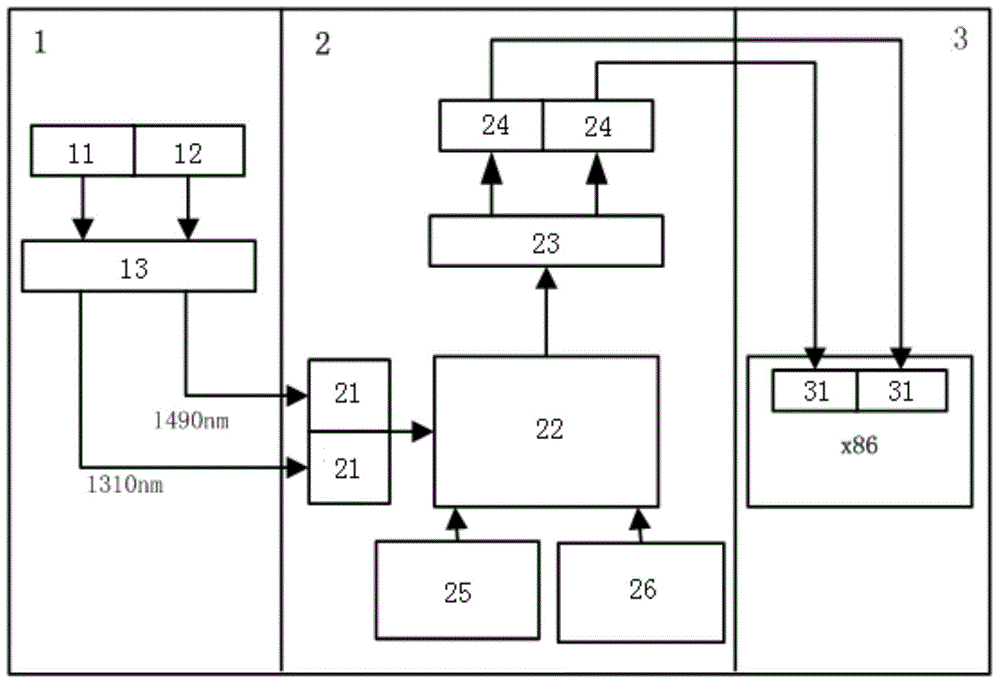
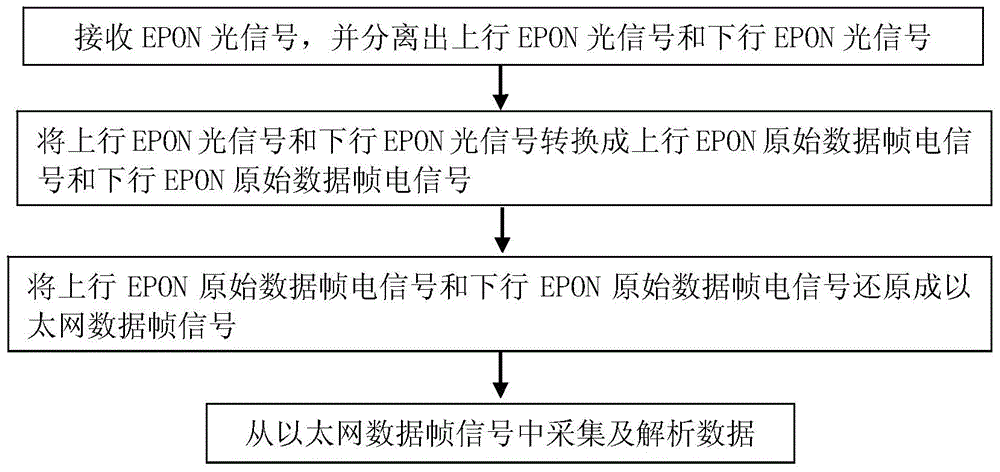
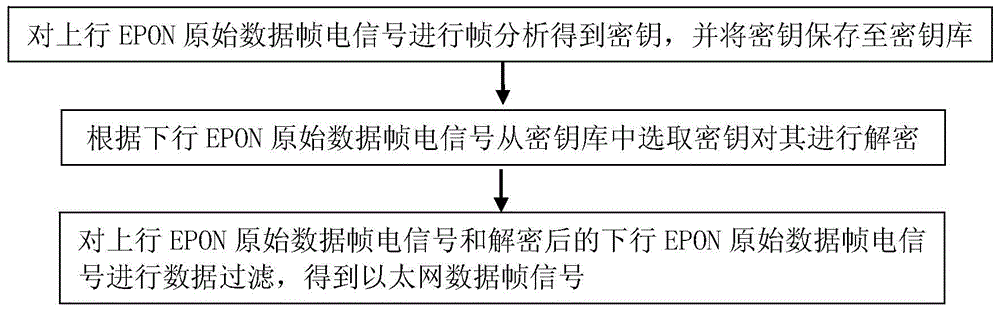
EPON link data collecting and analyzing device and method
InactiveCN104469558ARealize acquisitionEasy to useMultiplex system selection arrangementsData acquisitionLink data
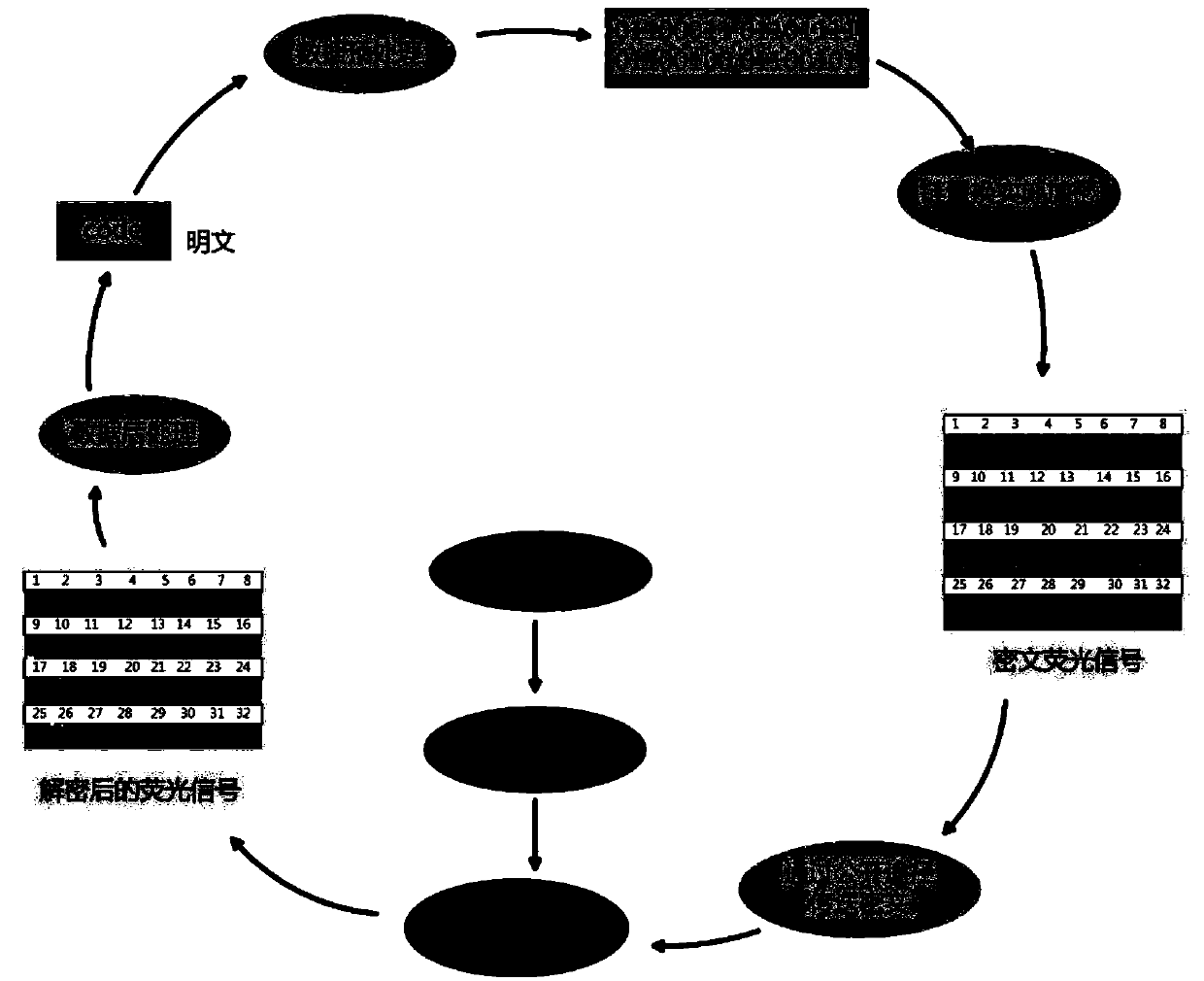
The invention discloses an EPON link data collecting and analyzing device which comprises a link beam split module, a protocol analyzing module and a data analyzing module. The link beam split module is used for receiving EPON light signals and separating uplink EPON light signals and downlink EPON light signals. The protocol analyzing module is connected with the link beam split module and is used for reverting the received uplink EPON light signals and the received downlink EPON light signals into Ethernet data frame signals which are transmitted to the data analyzing module. The data analyzing module is connected with the protocol analyzing module and is used for collecting and analyzing data from the received Ethernet data frame signals. The invention further provides an EPON link data collecting and analyzing method. EPON data collecting and protocol analyzing are achieved, non-object data and useless data filtering is achieved, decryption on collected EPON data is achieved, restoring of the network record of a target user is achieved, user normal use daily service is not affected, and even if equipment power failure happens, all users can work normally.
Owner:SHANGHAI SINO TELECOM TECH
Continuous color-changing fluorescent anti-counterfeiting material as well as preparation method and application thereof
ActiveCN113429963ASolve the single anti-counterfeiting modeOvercome the conditionsInksOrganic dyesOrganic chemistryDye molecule
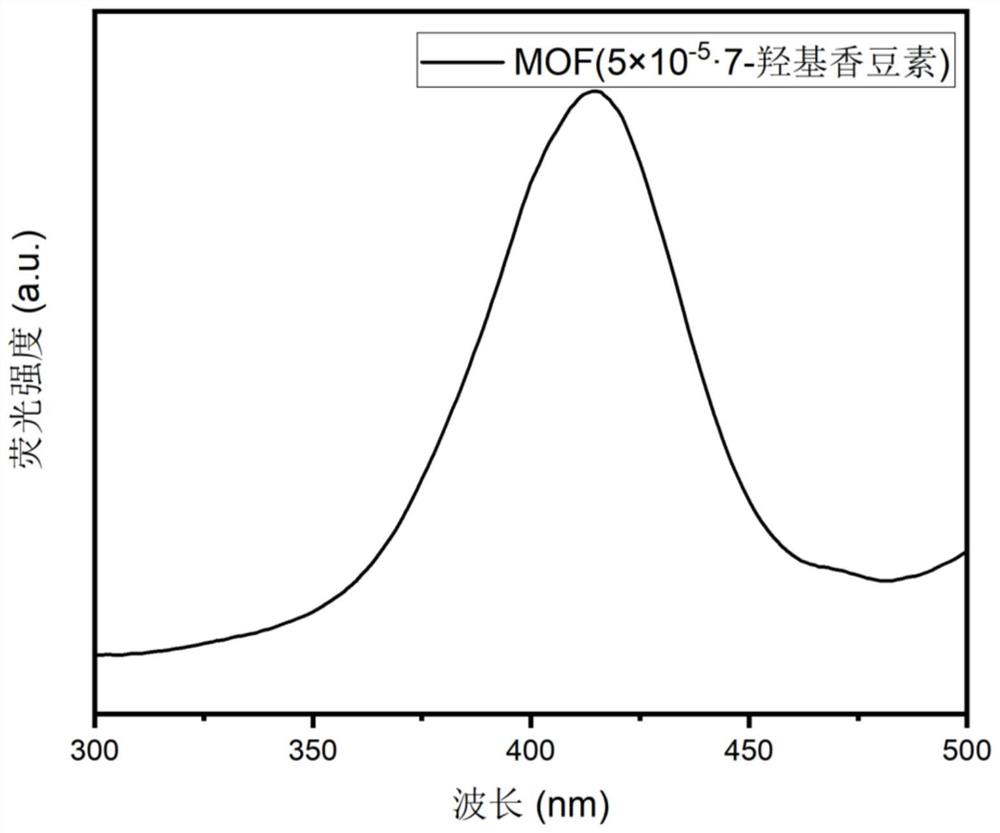
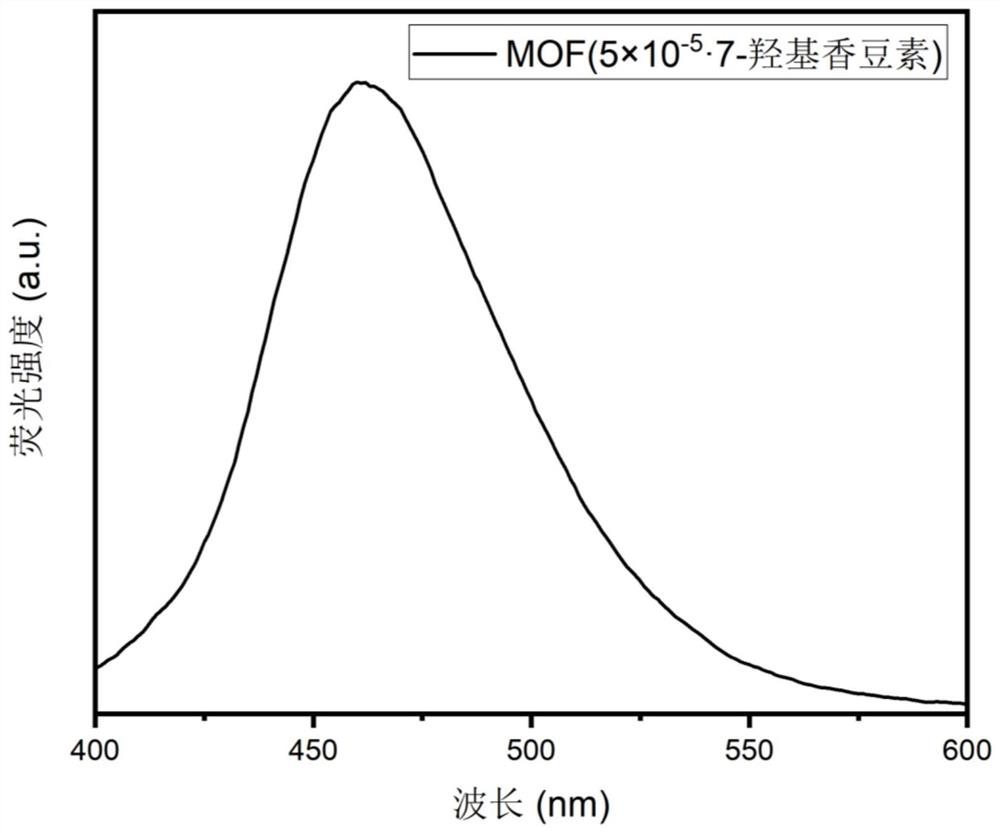
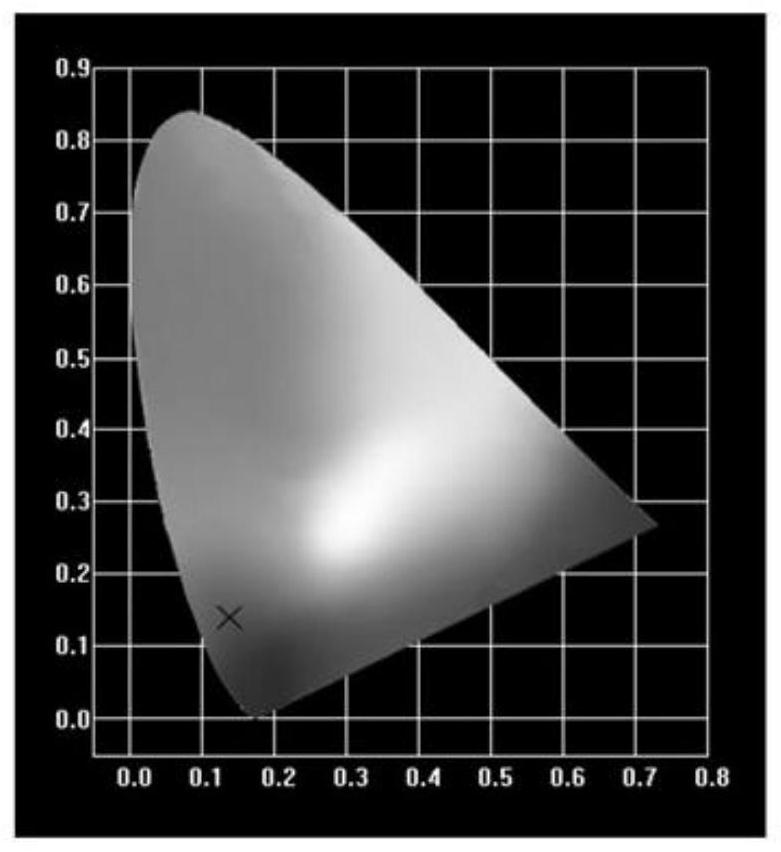
The invention relates to a continuous color-changing fluorescent anti-counterfeiting material as well as a preparation method and application thereof. The material is Ln < 3 + > / MOF. dye, wherein the amount of dye contained in every 2.4000 g of MOF is 5 * 10 <-6 > mol to 1 * 10 <-4 > mol, and the amount of Ln < 3 + > contained in every 2.4000 g of MOF is 0.016 mol to 0.08 mol. The preparation method comprises the following steps: encapsulating dye molecules into a porous material by adopting a hot reflux method to prepare the MOF. dye, and introducing lanthanide ions into the MOF. dye by adopting a post-functionalization synthesis method to synthesize a new substance structure of the Ln < 3 + > / MOF. dye. The obtained material has the advantages of being high in concealment, high in safety performance, low in multi-mode continuous color-changing light-emitting imitability and the like when applied to the fluorescent anti-counterfeiting aspect, the multi-anti-counterfeiting effect is achieved, the potential in the fluorescent anti-counterfeiting aspect is huge, the application value is high, and the wide application prospect is achieved.
Owner:HEBEI UNIV OF TECH
A kind of fluorescent perovskite nanocrystal and its preparation method and application
ActiveCN109423278BStrong fluorescenceEasy to synthesizeLead halidesNanotechnologyFluorescencePerovskite (structure)
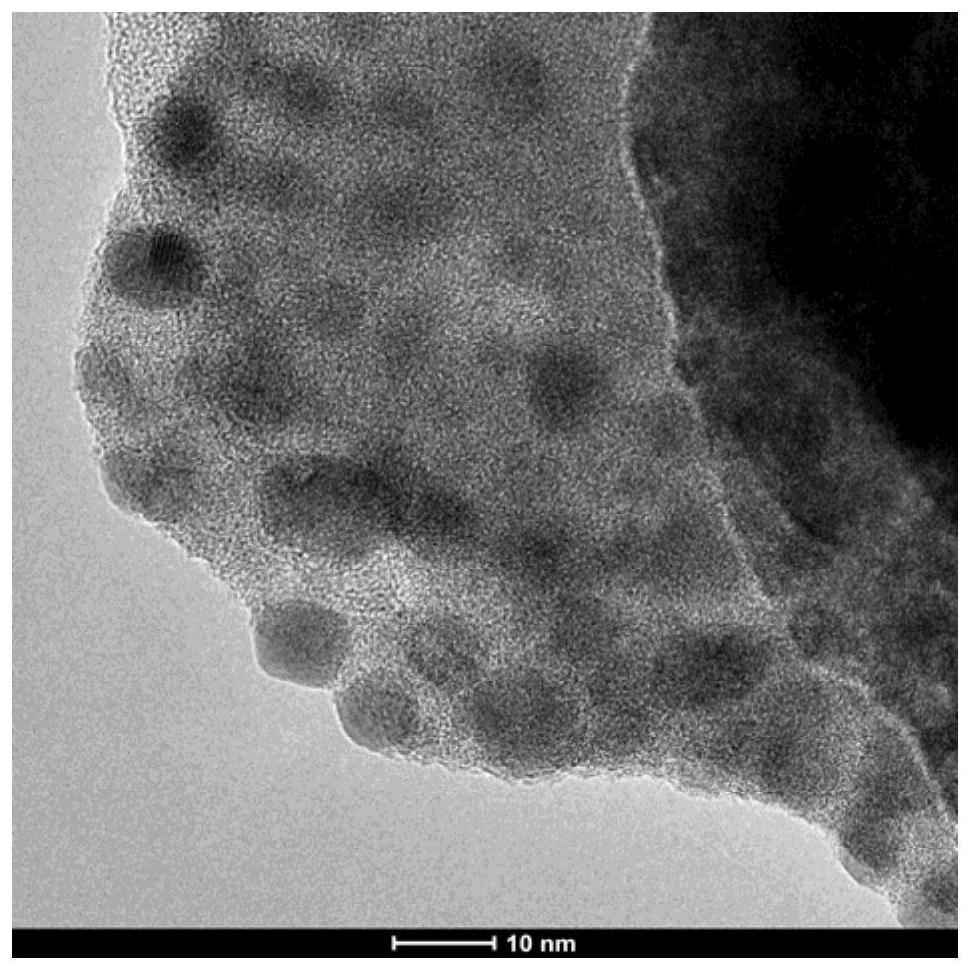
The present invention relates to a kind of fluorescent perovskite nanocrystal and its preparation method and application, and its structure is MOF‑ABX 3 , where MOF and ABX 3 The mass ratio is (1~50):(0.1~5), and the cationic halide salt solution used for perovskite synthesis is added to the metal-organic framework dispersion liquid, and the obtained perovskite nanocrystals are uniformly dispersed in the metal-organic framework crystal, and has good fluorescence properties, and this method is versatile. The synthesis method of the perovskite nanocrystal provided by the invention can be directly used in the storage and protection application of confidential information. Compared with the prior art, the operation process of the present invention is simple and repeatable, the metal-organic framework material and its recorded information are very safe (no absorption and fluorescence characteristics in the visible light range, and cannot be recognized by naked eyes) and the fluorescence characteristics of perovskite nanocrystals Good, so that it can be directly applied in the field of confidential information storage and protection.
Owner:SHANGHAI JIAOTONG UNIV
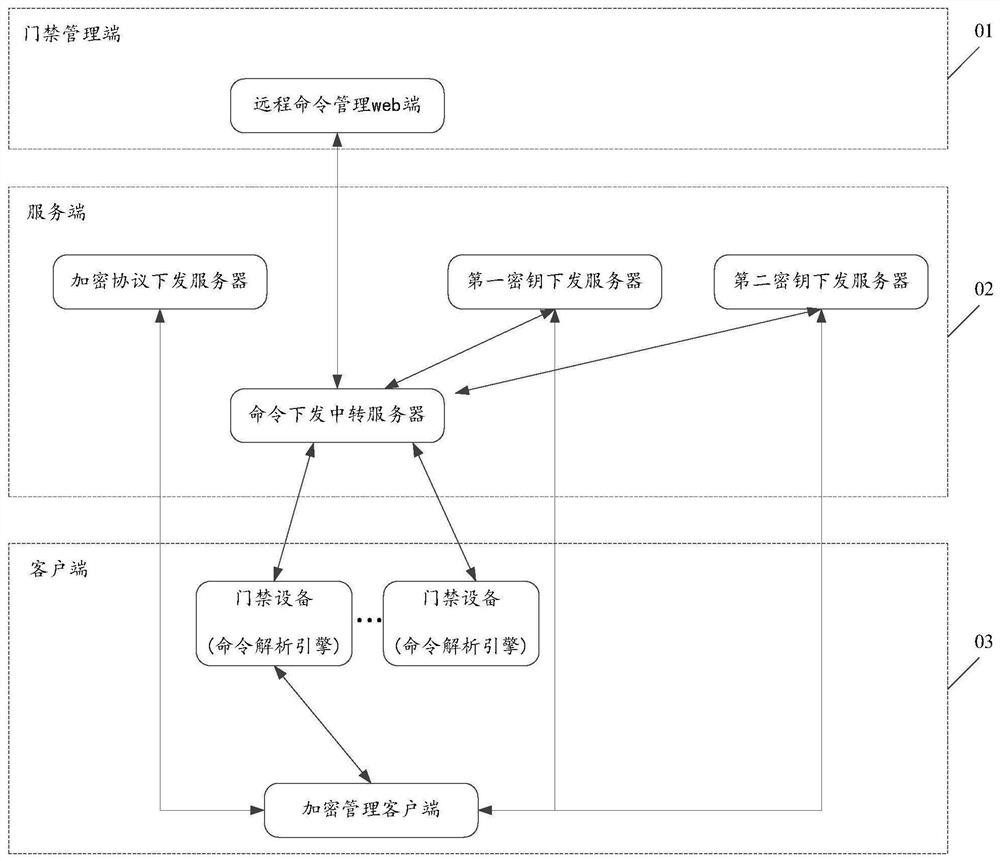
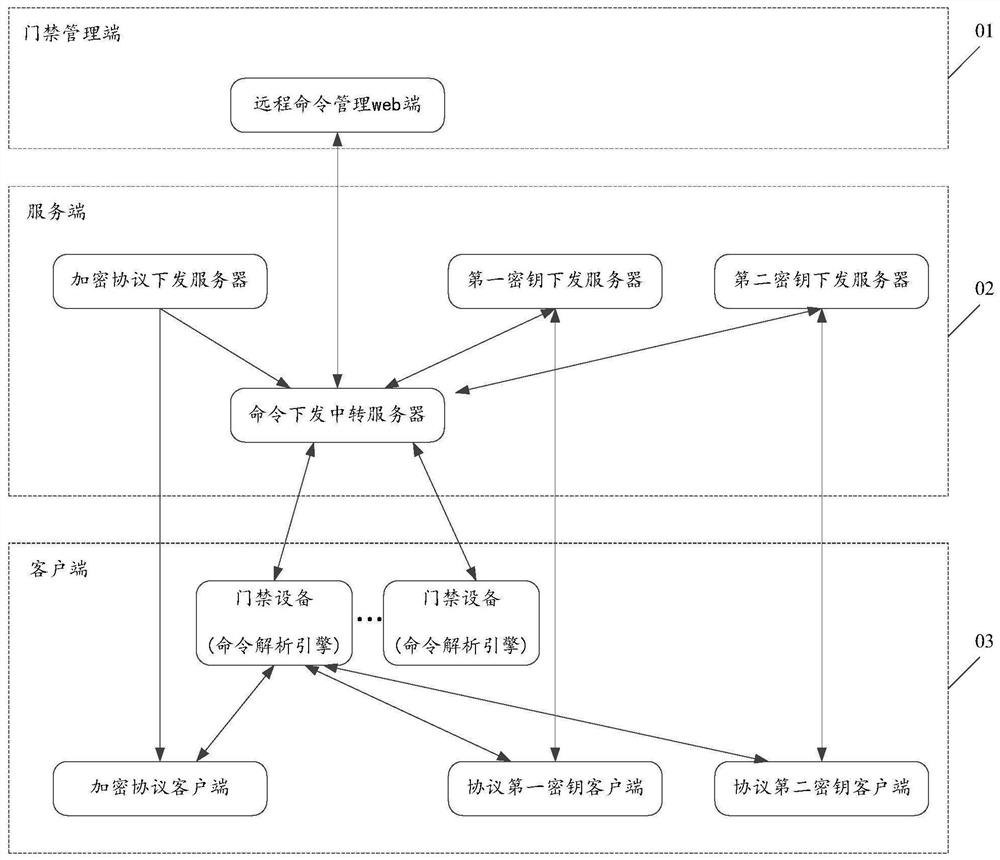
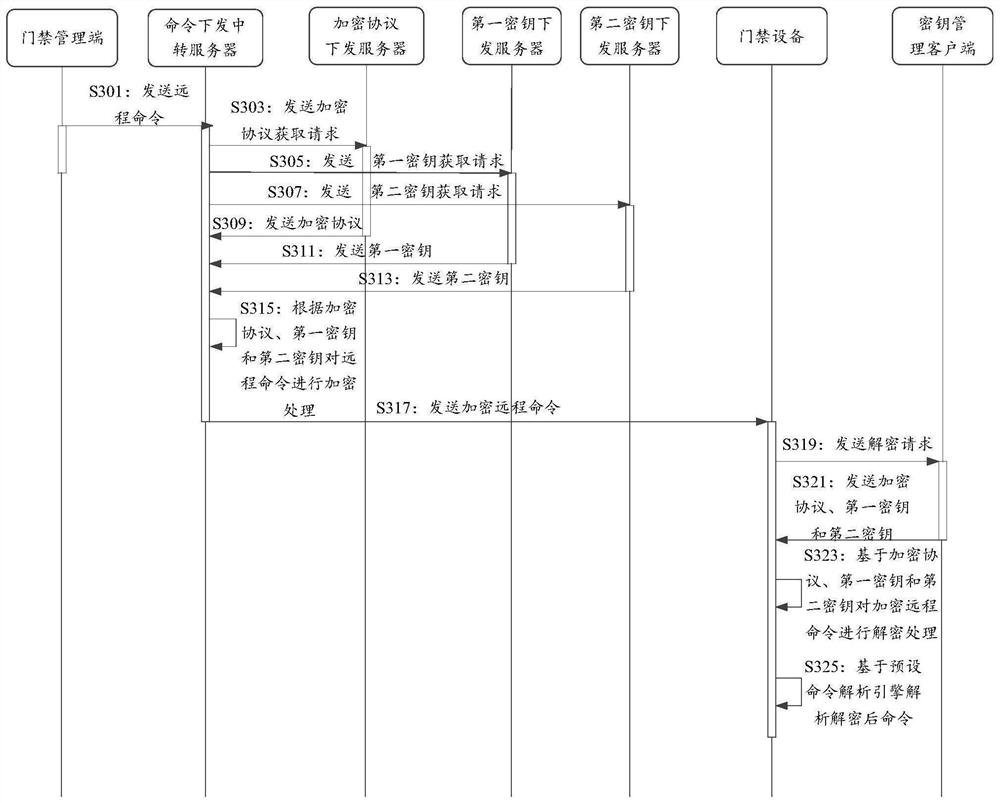
Remote control method and system of access control equipment and storage medium
PendingCN111932752ARich remote control functionsImprove securityIndividual entry/exit registersTransmissionData securityEngineering
The invention discloses a remote control method and system of access control equipment and a storage medium. The method comprises the following steps that an access control management terminal sends aremote command to a command issuing transit server; the command issuing transit server obtains a first secret key, a second secret key and an encryption protocol from a first secret key issuing server, a second secret key issuing server and an encryption protocol issuing server respectively; the command issuing transit server encrypts the remote command according to the encryption protocol, the first secret key and the second secret key to obtain an encrypted remote command, and sends the encrypted remote command to access control equipment; and the access control equipment acquires the encryption protocol, the first secret key and the second secret key from an encryption management client, decrypts the encrypted remote command based on the acquired encryption protocol, the first secret key and the second secret key to obtain a decrypted command, and analyzes the decrypted command based on a preset command analysis engine. By utilizing the technical scheme provided by the invention, the remote control function of the access control equipment can be enriched, and the data security is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
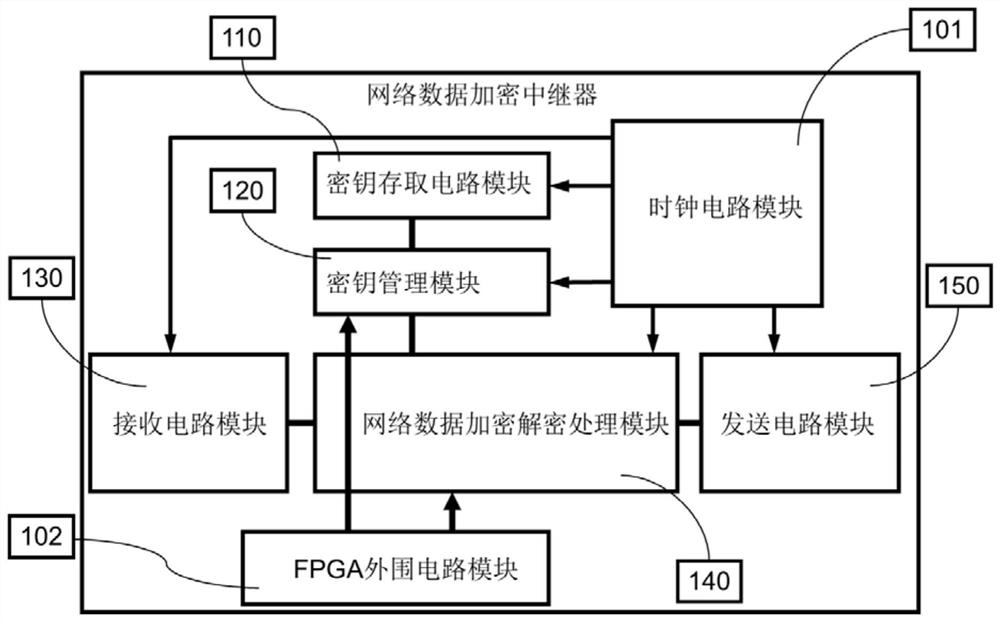
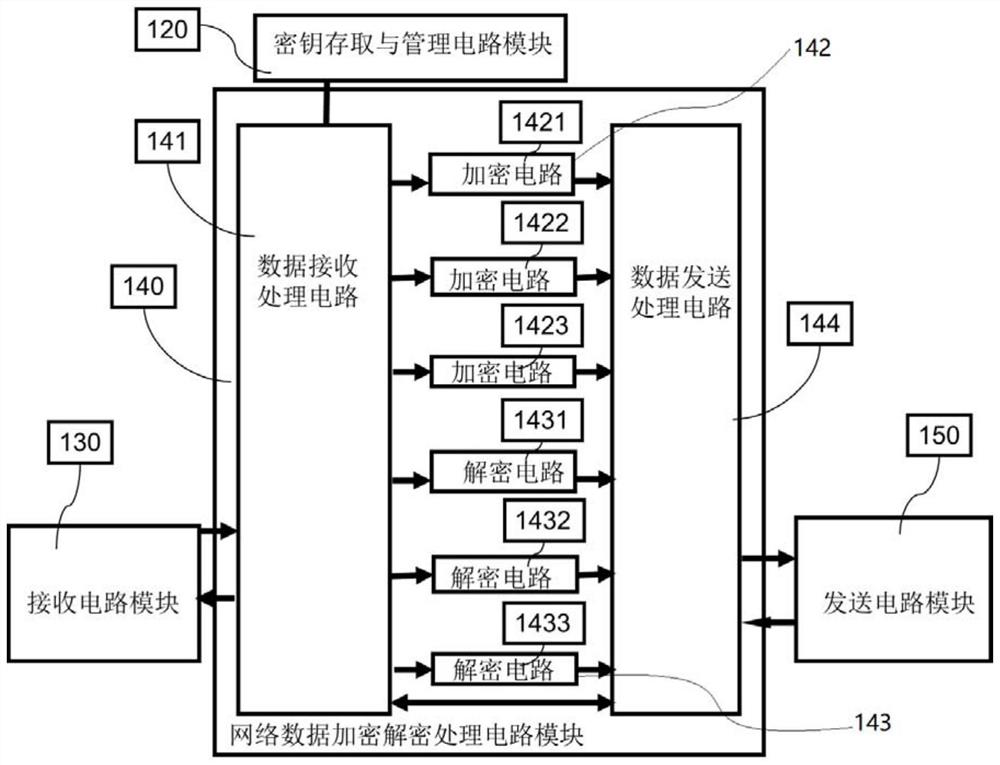
Network data encryption repeater
PendingCN113992321AReal-timeAchieve decryptionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareGigabit
The invention discloses a network data encryption repeater which comprises a key management module, a network data receiving circuit module, a data encryption and decryption processing module and a network data sending circuit module. The output end of the network data receiving circuit module is connected with the input end of the data encryption and decryption processing module, the output end of the data encryption and decryption processing module is connected with the input end of the network data sending circuit module, and the data encryption and decryption processing module is connected with the key management module. The key management module and the network data encryption and decryption processing module are integrated on an FPGA chip. The operation time of an encryption and decryption algorithm is short, the real-time encryption and decryption requirements of high-speed network transmission data are met, real-time encryption and decryption of gigabit network data can be realized, and the security of the system is improved by using the reasonable key management module.
Owner:ANHUI HONGSHI ZIJING PHOTOELECTRIC INST
A data transmission method, a data sending end, and a data receiving end
ActiveCN107086915BImprove securityAchieve decryptionKey distribution for secure communicationMultiple keys/algorithms usageCiphertextEngineering
The invention provides a data transmission method, a data transmitting terminal and a data receiving terminal. The method comprises: a first encryption key is generated randomly; the first encryption key is encrypted by using a preset second encryption key based on an encryption algorithm; to-be-transmitted target data are encrypted by using the encrypted first encryption key and the encryption algorithm so as to generate a ciphertext of the target data; according to a preset combination rule, a combined ciphertext is generated by using the encrypted first encryption key and the ciphertext; and the combined ciphertext is sent to the data receiving terminal and thus the data receiving terminal splits the combined ciphertext according to a preset corresponding splitting rule to obtain the encrypted first encryption key and the ciphertext, and the ciphertext is decrypted by using a preset corresponding decryption algorithm and the encrypted first encryption key, so that the target data are obtained. Therefore, security of the data is improved.
Owner:INSPUR SOFTWARE TECH CO LTD
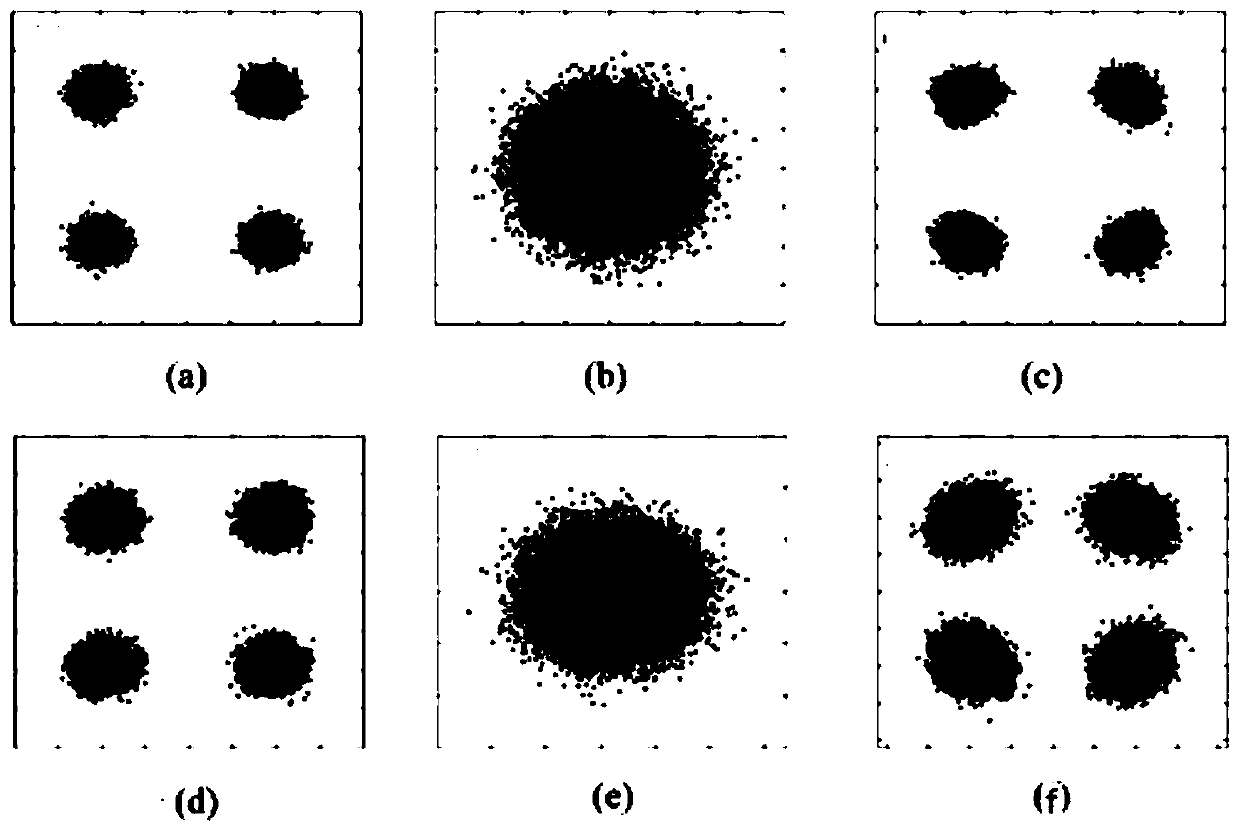
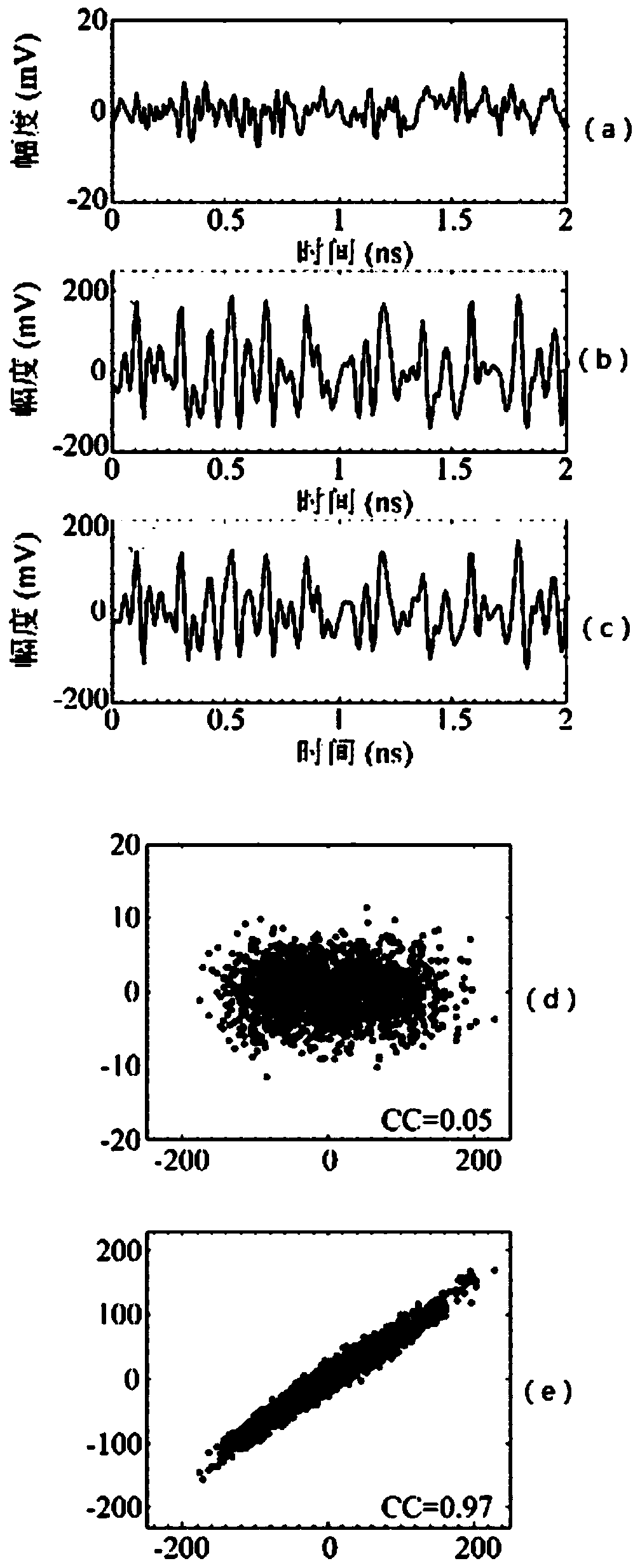
A high-speed chaotic secure transmission method based on coherent detection
ActiveCN112350818BLower requirementAchieve decryptionAmplitude-modulated carrier systemsDistortion/dispersion eliminationDigital signal processingSoftware engineering
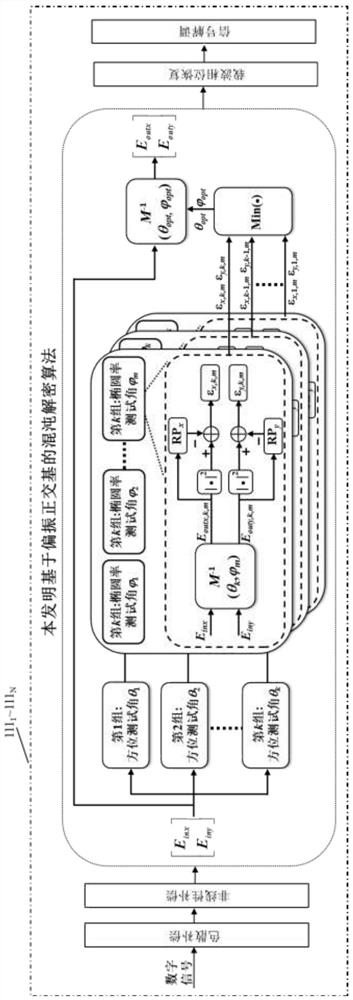
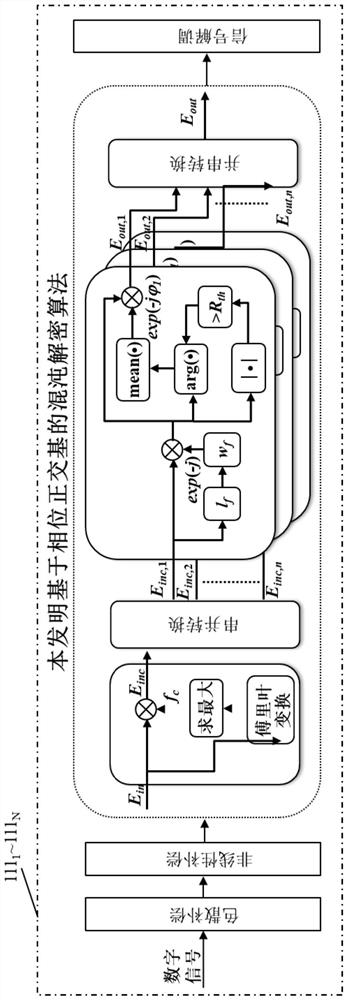
The invention discloses a high-speed chaotic secure transmission method based on coherent detection, specifically: at the transmitting end of the chaotic secure transmission system, the optical chaotic carrier and the transmission information are optically coupled through an orthogonal basis, and through the noise-like characteristics of the chaotic carrier Cover the transmission information to obtain the chaotic cover signal; add phase fast perturbation and polarization fast perturbation, and then enter the optical fiber transmission link for transmission; at the receiving end, use coherent detection technology to obtain the chaotic cover signal, and compensate the linearity by digital signal processing And nonlinear effects, and then through the chaotic decryption algorithm based on the polarization orthogonal basis or the chaotic decryption algorithm based on the phase orthogonal basis, finally realize the separation of the chaotic carrier and signal to complete the decryption operation. The present invention can realize long-distance transmission and decryption of high-speed chaotic secret signal in multiple transmission services, multiple transmission wavelengths, multiple fiber cores, multiple modes, and high-speed secure communication transmission system.
Owner:SOUTHWEST JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com