Safe starting method and device
A technology for secure boot and secure addresses, applied in computer security devices, instruments, platform integrity maintenance, etc., can solve problems such as system security impact, increase system hardware costs, trade secrets and other intellectual property leakage, and achieve improved upgradeability. performance, reducing hardware resource requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Hereinafter, exemplary embodiments according to the present application will be described in detail with reference to the accompanying drawings. Apparently, the described embodiments are only some of the embodiments of the present application, rather than all the embodiments of the present application. It should be understood that the present application is not limited by the exemplary embodiments described here.
[0039] Application overview
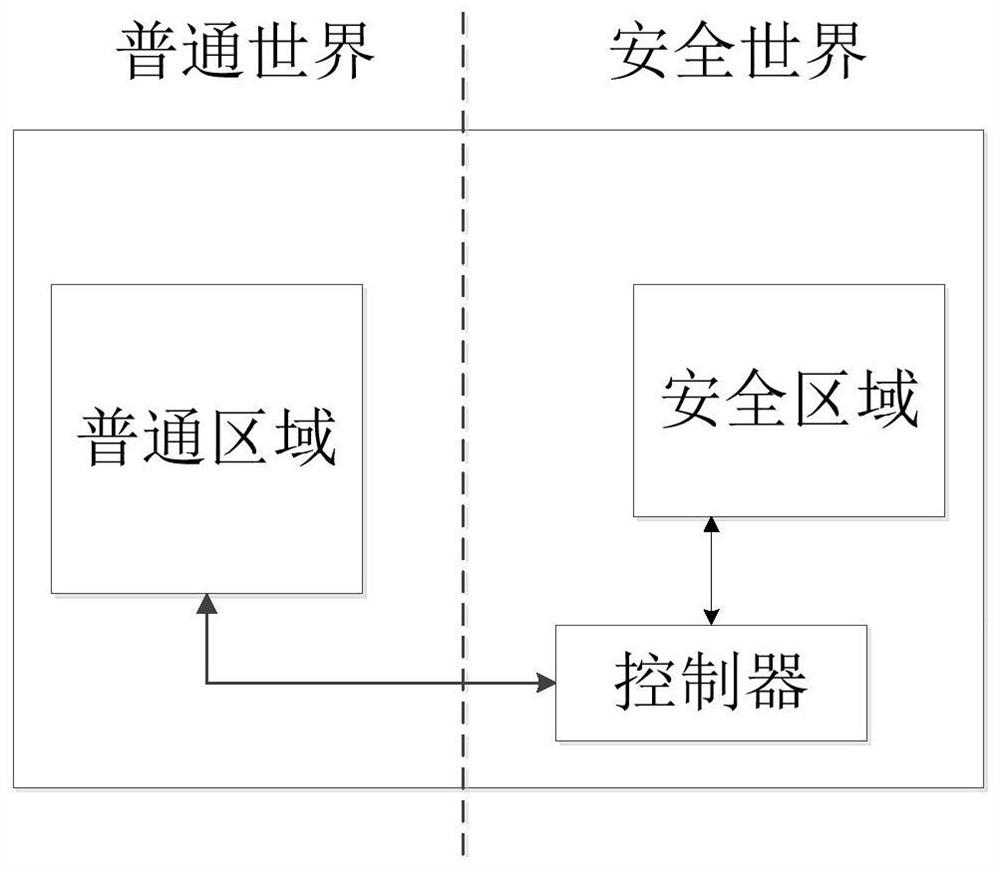
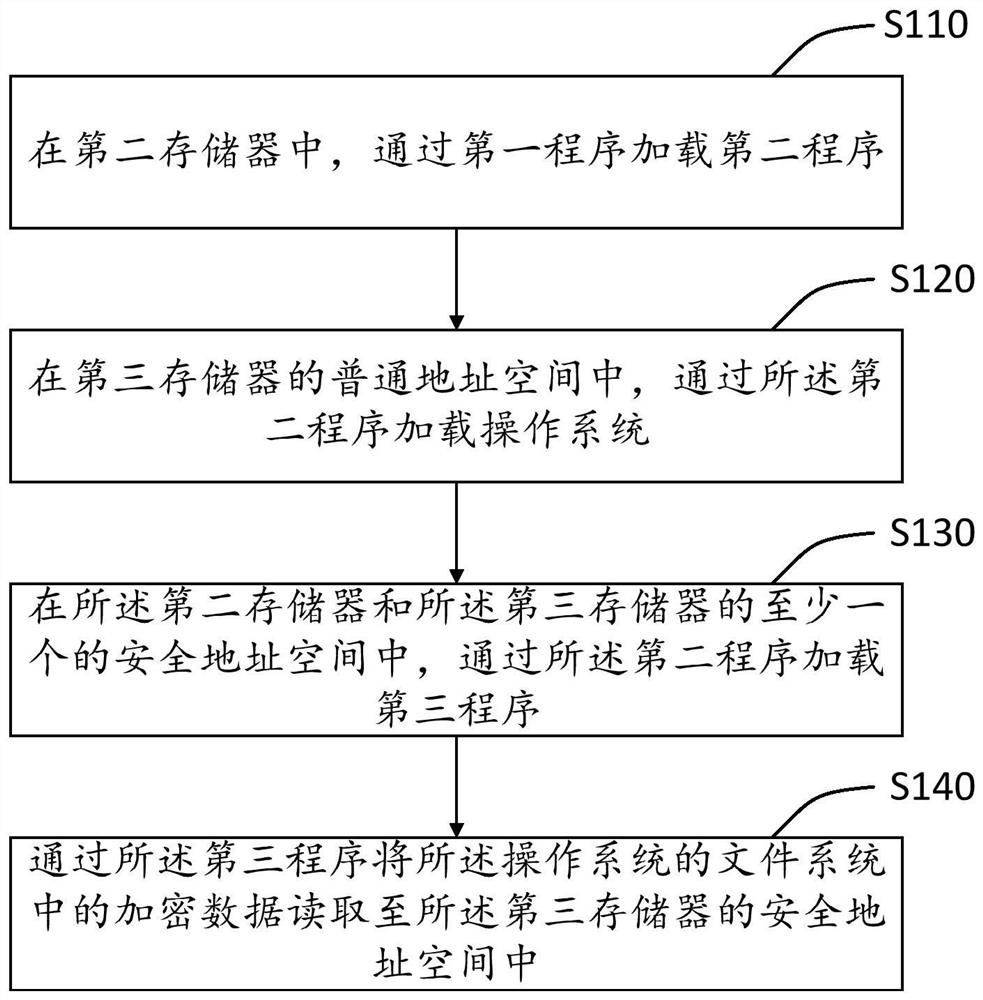
[0040] With the enhancement of chip computing and processing capabilities, embedded devices using SoC systems on chips have become the choice of computer-assisted driving, industrial Internet and other application fields. Embedded devices have the characteristics of convenient mobility, non-modification and strong real-time performance, and can be embedded in existing control systems such as transportation equipment and industrial facilities. On the other hand, due to the continuous expansion of the functions of embedded devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com