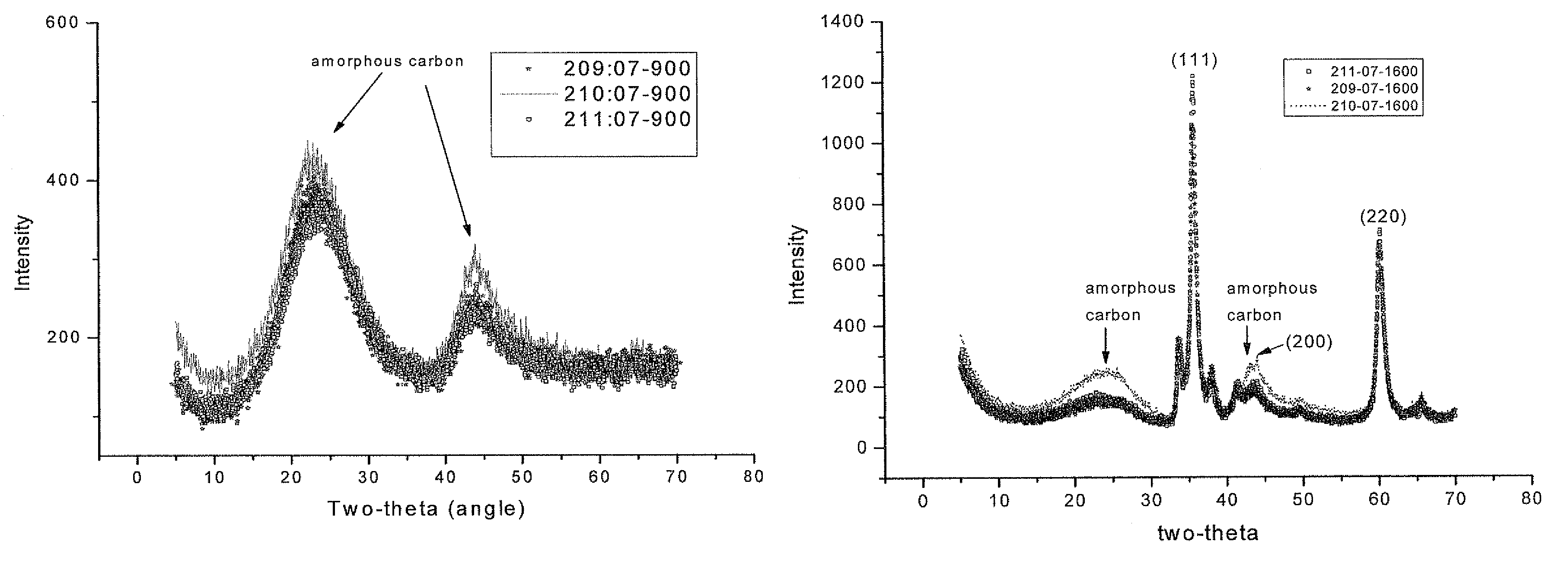
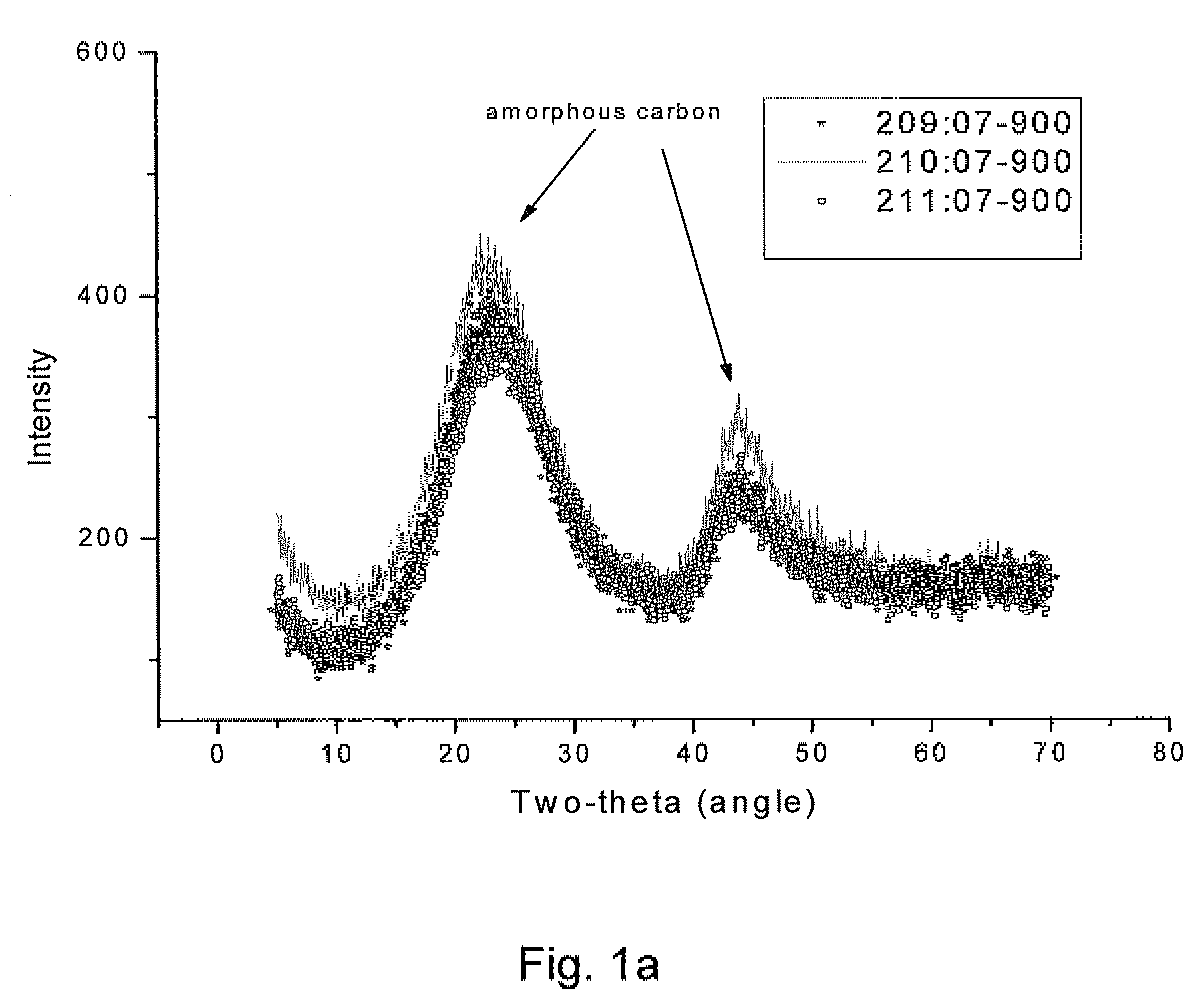
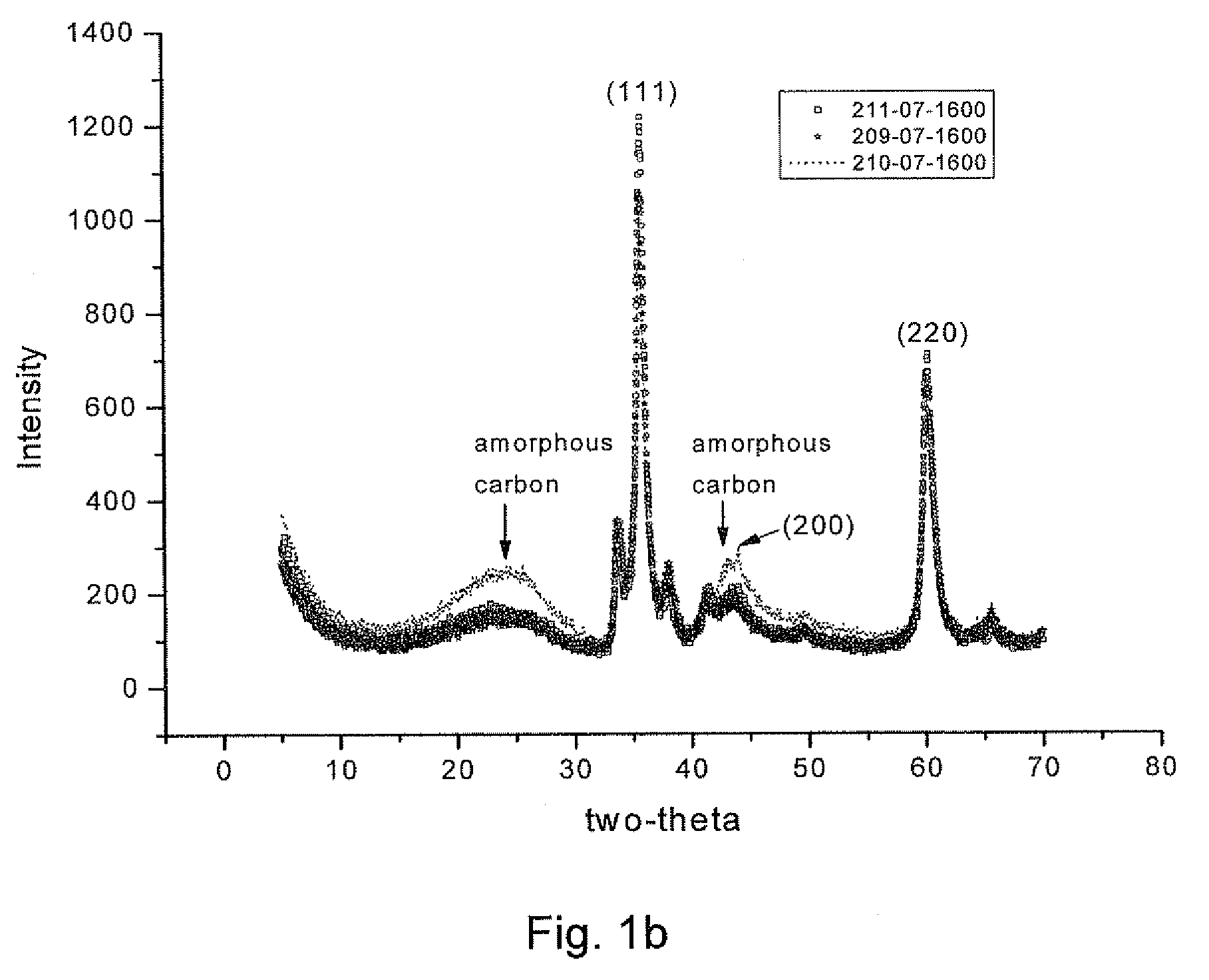
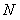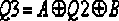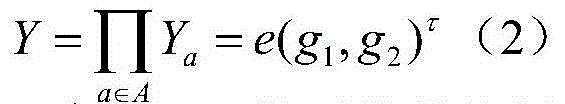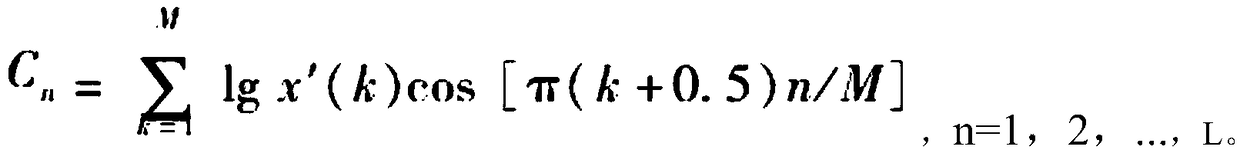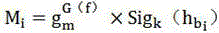Patents
Literature
177results about How to "Strong resistance to attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
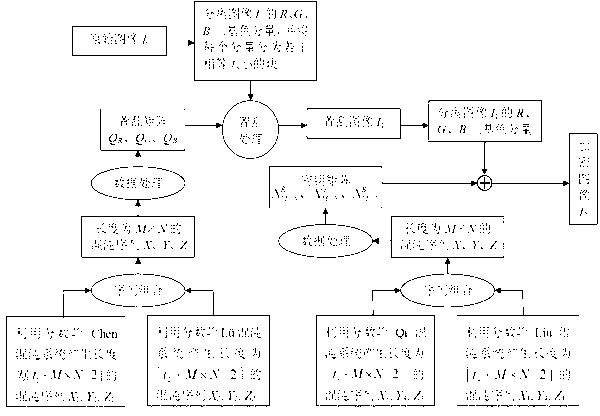
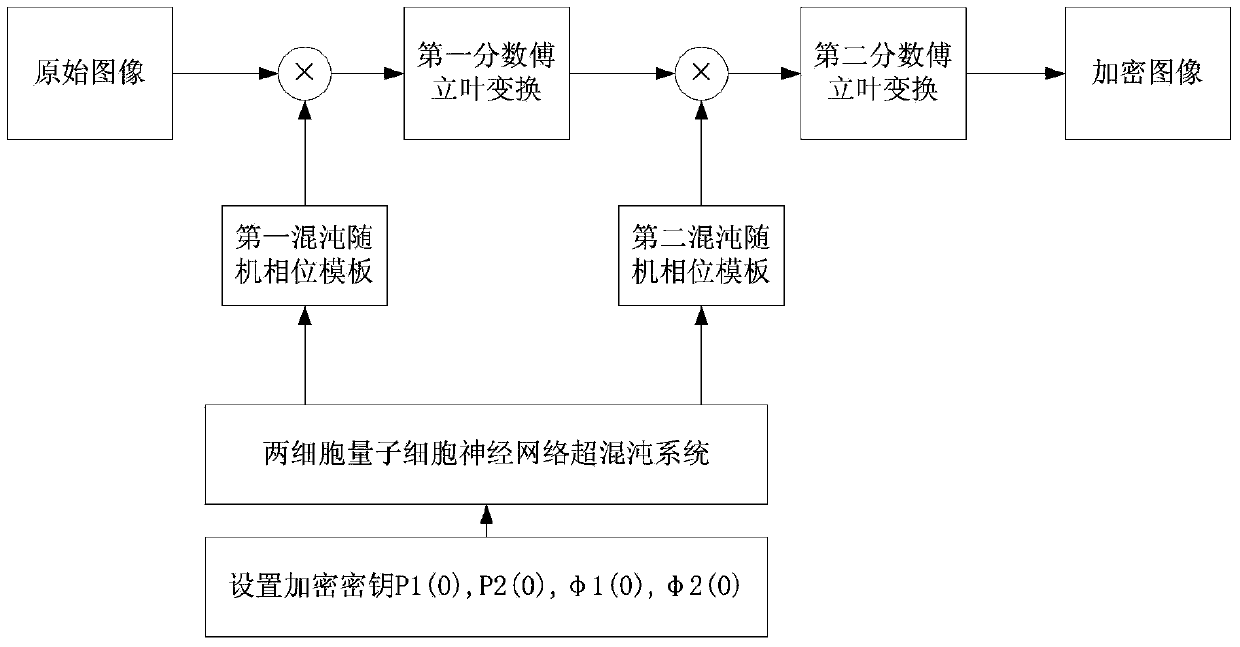
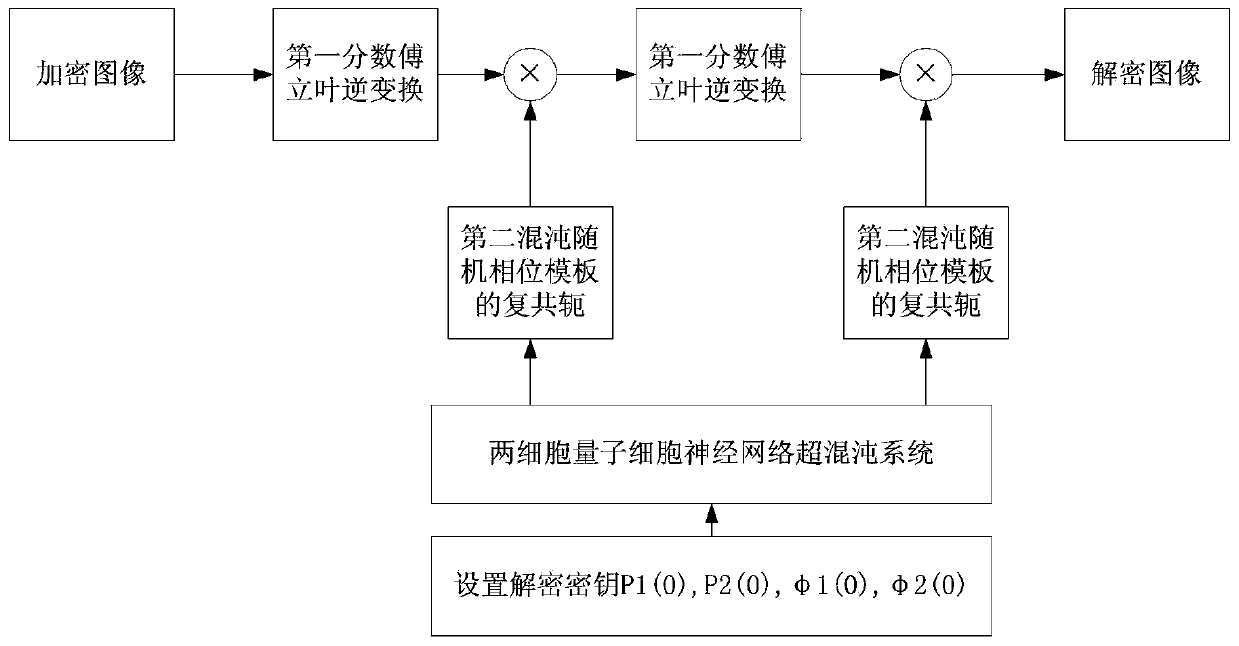
Color image encryption and decryption method based on multiple-fractional-order chaotic systems
ActiveCN102982499ARich Dynamic BehaviorBig Key SensitivityImage data processing detailsKey spaceAlgorithm
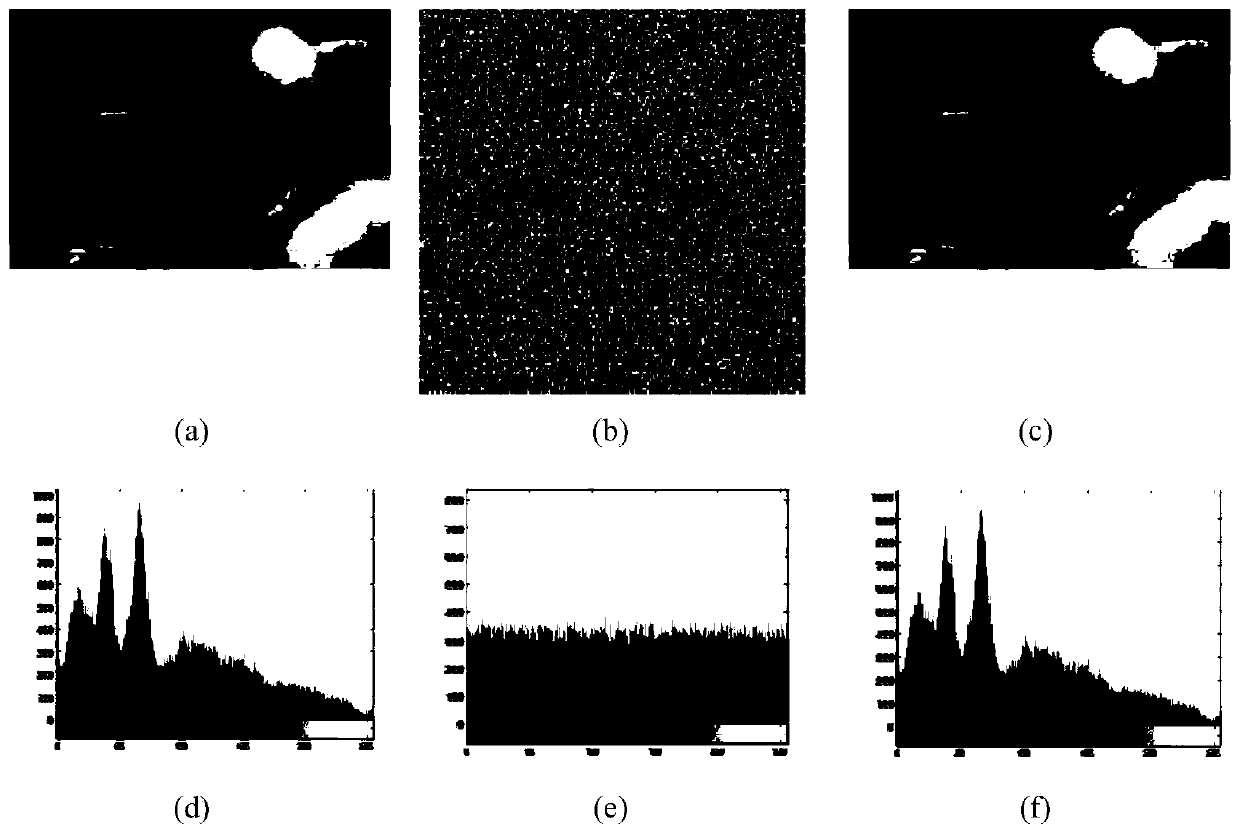
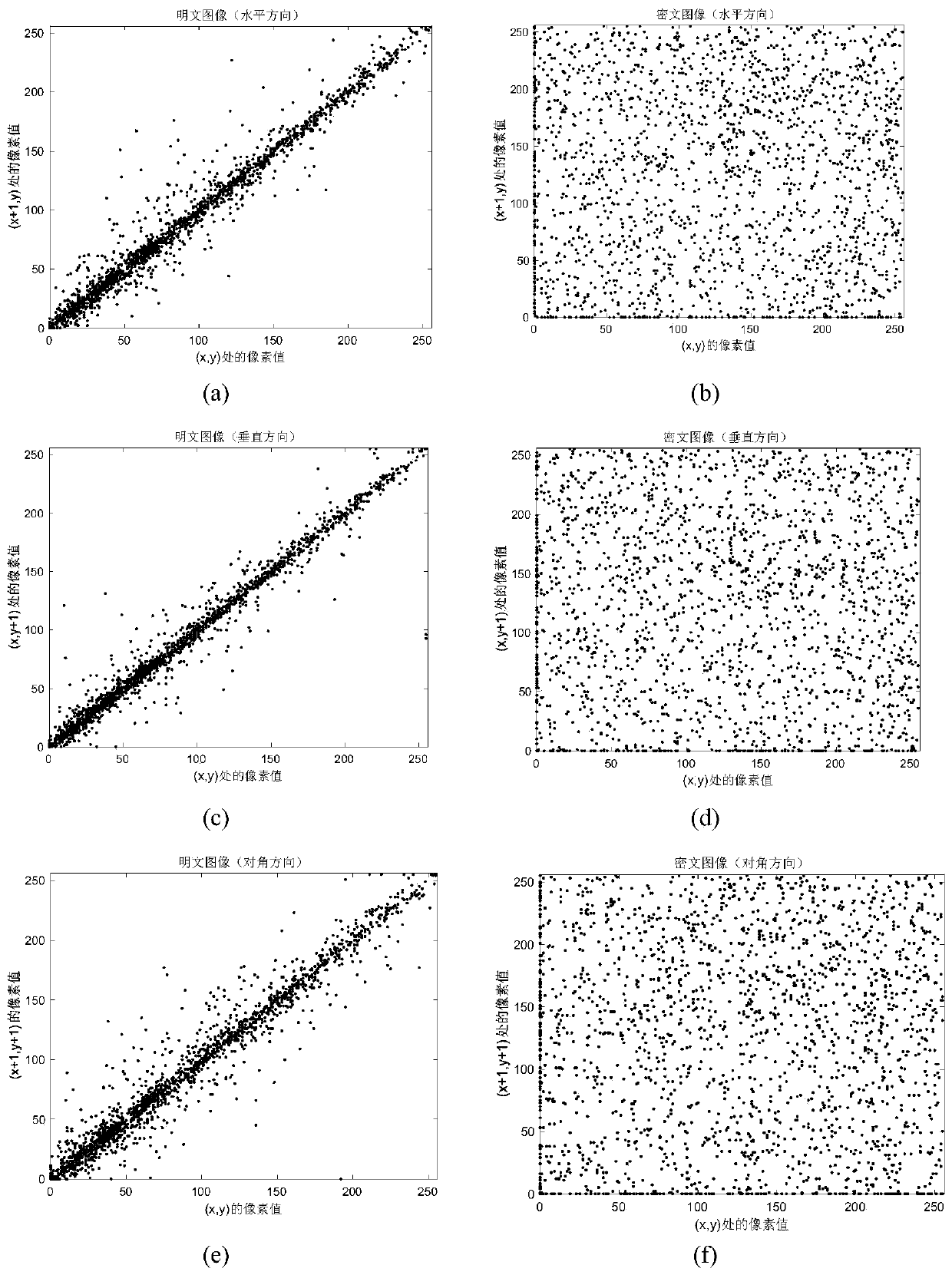
The invention discloses a color image encryption and decryption method based on multiple-fractional-order chaotic systems. An encryption algorithm comprises an original image scrambling stage and a scrambling image encryption stage. Firstly, two different fractional-order chaotic systems are utilize to generate three scrambling arrays and respectively process R, G and B three primary color component arrays of an original color image I0 in a scrambling mode to obtain scrambled image I1. Furthermore, another two different fractional-order chaotic systems are utilize to generate three secret key arrays and carries out exclusive OR operation on elements on the secret key arrays and pixel of the scrambled image I1 one by one to change values of all pixel points of the scrambled image I1 to obtain encrypted image I2, and the image decryption is a reversed process of the encryption. The method uses the multiple-fractional-order chaotic systems so as to greatly enhance safety. Furthermore, the algorithm secret keys are large in space, high in secret key sensitiveness and strong in impact resistance.
Owner:HENAN UNIVERSITY
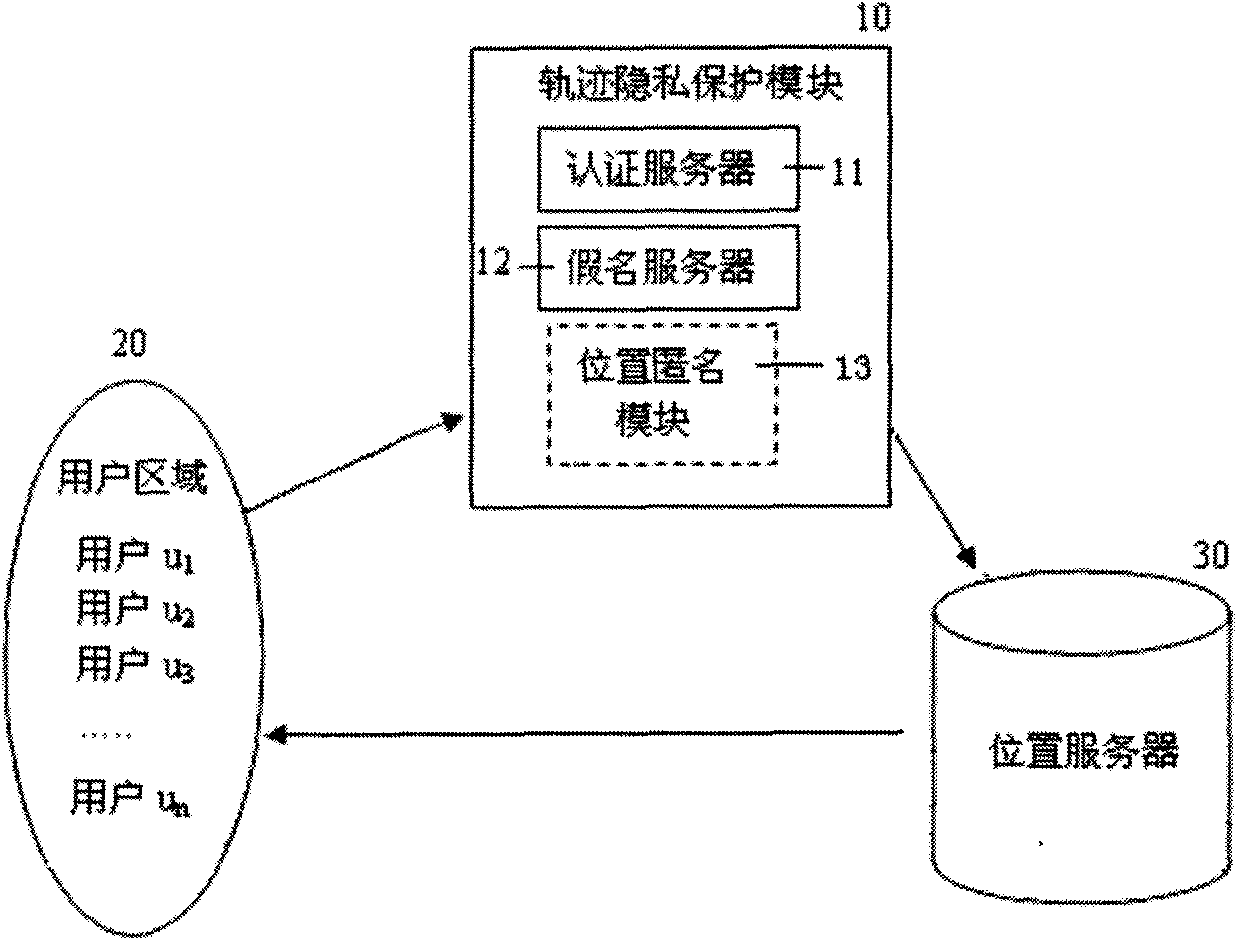
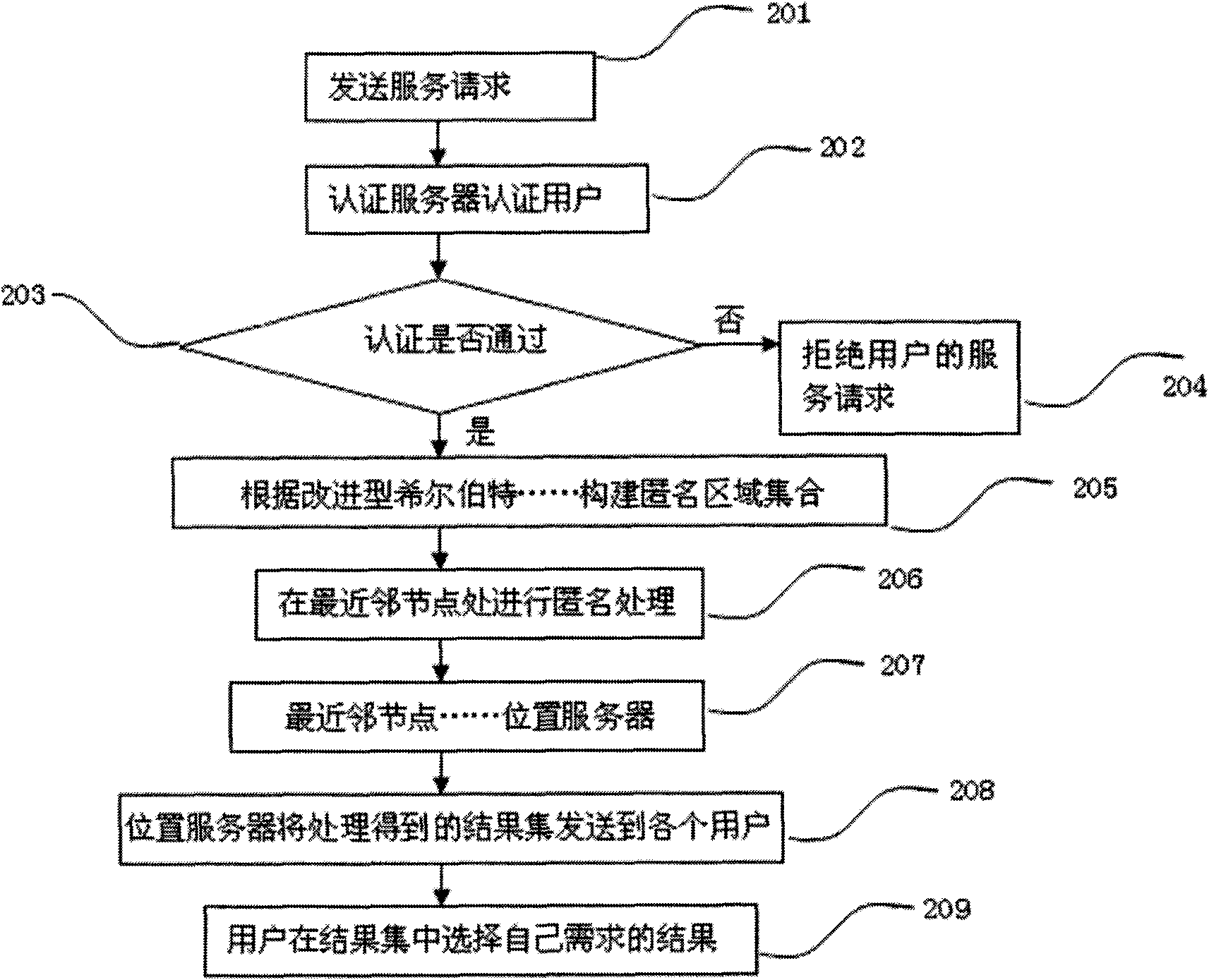
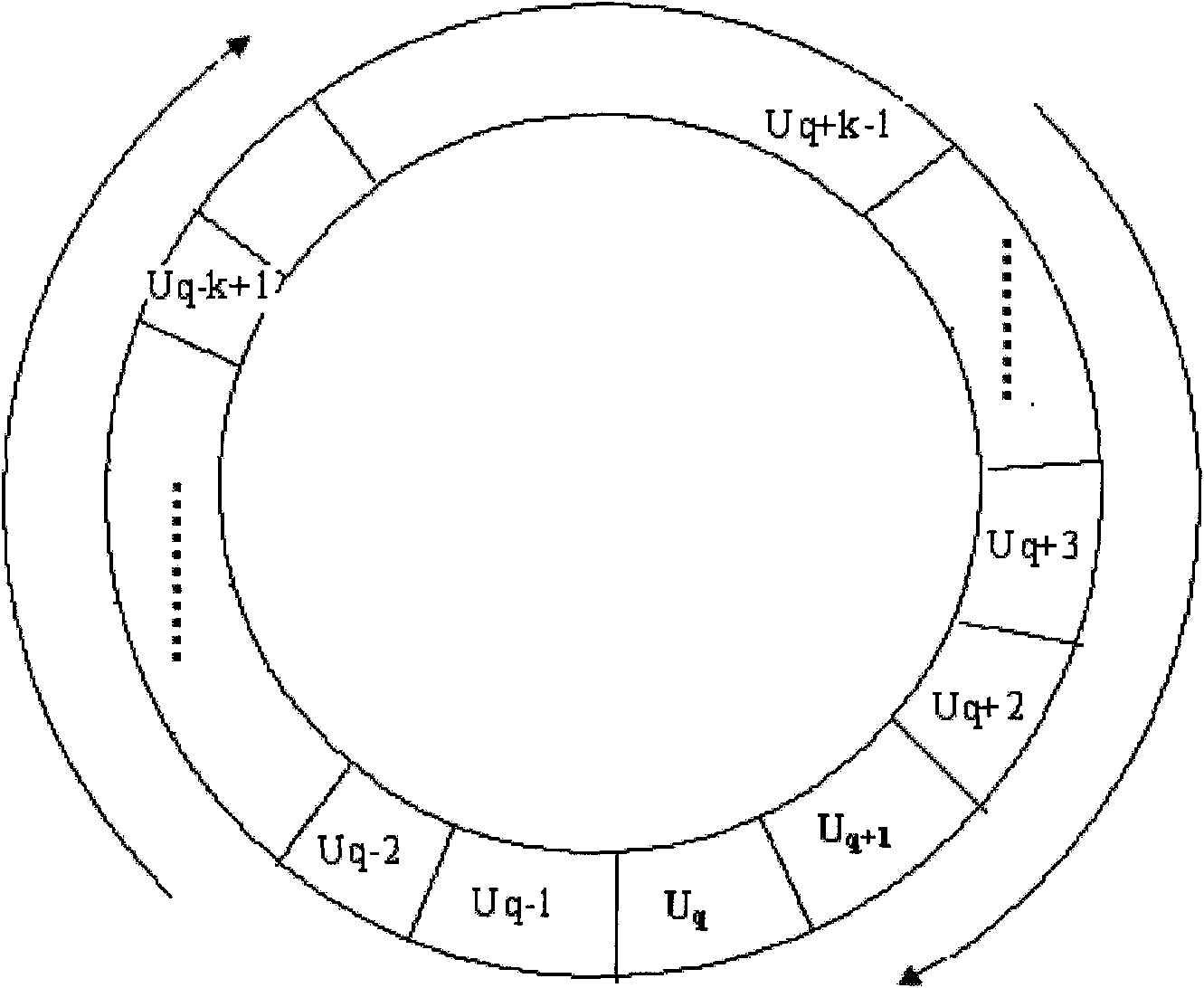
Method for protecting track privacy by forwarding inquiries based on neighboring nodes in location service
InactiveCN101834861AStrong anti-attack abilityEasy to deployTransmissionHilbert spacePrivacy protection
The invention discloses a method for protecting track privacy by forwarding inquiries based on neighboring nodes in a location service and relates to the privacy protection method in the field of information security. The method comprises the following steps of: (1) sending a location service request by an authorized creditable user u by using an anonym; (2) mapping the two-dimensional coordinates of the user to a one-dimensional space by using the Hilbert space filling curve to form an ordered Hilbert sequence and finding out the nearest neighboring node uN of the inquiry user according to the Hilbert value, wherein the node is taken as a node for forwarding an inquiry request; and (3) selecting k-1 users having the Hilbert values more than or less than that of the uN at the uN to form a k anonym group with u and a set of anonym requests after finishing the location anonym at the uN. The method can better reduce the association among the location information and securely and effectively protect the location privacy and track privacy of the user and is easy to implement.
Owner:HUAZHONG NORMAL UNIV
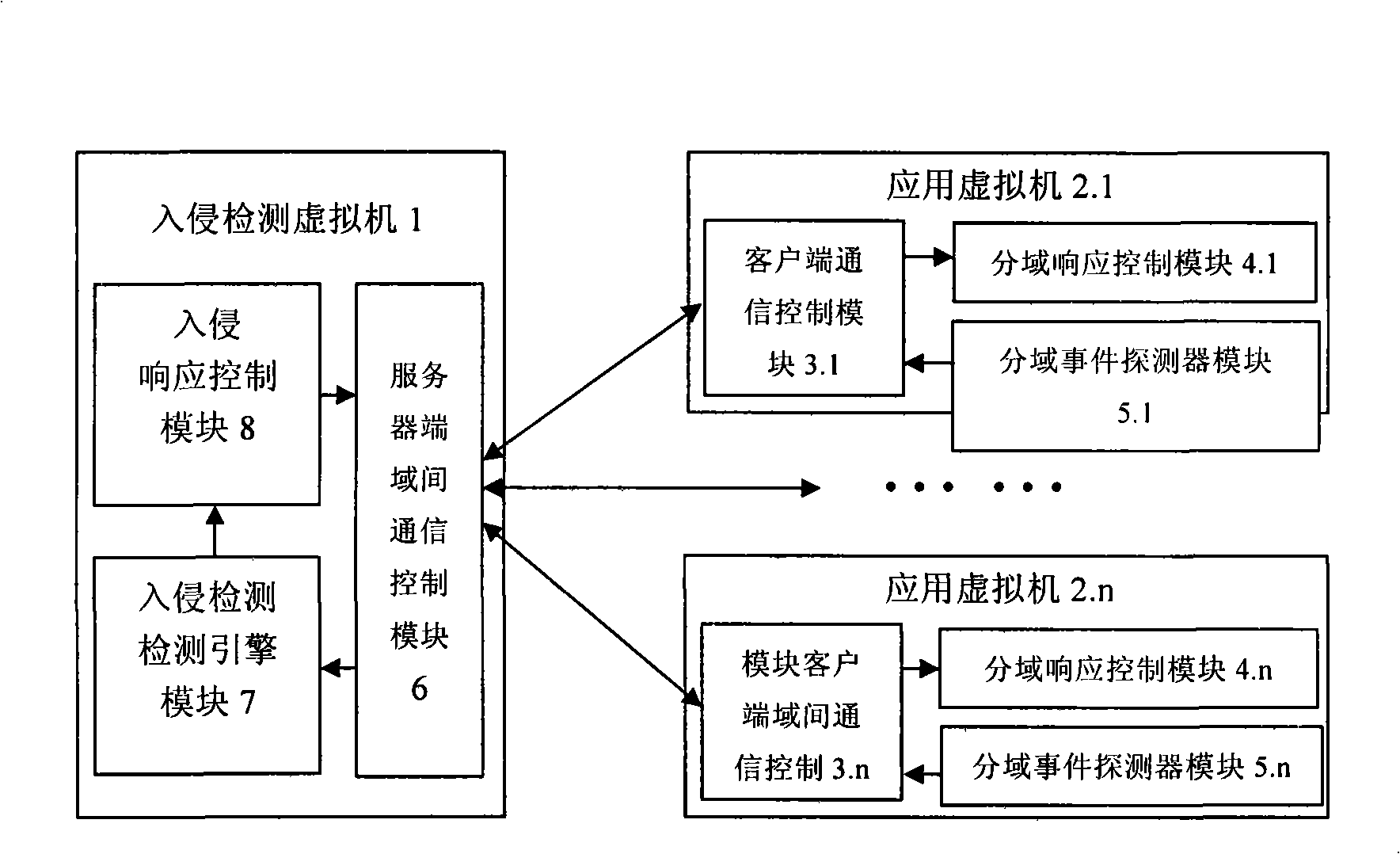
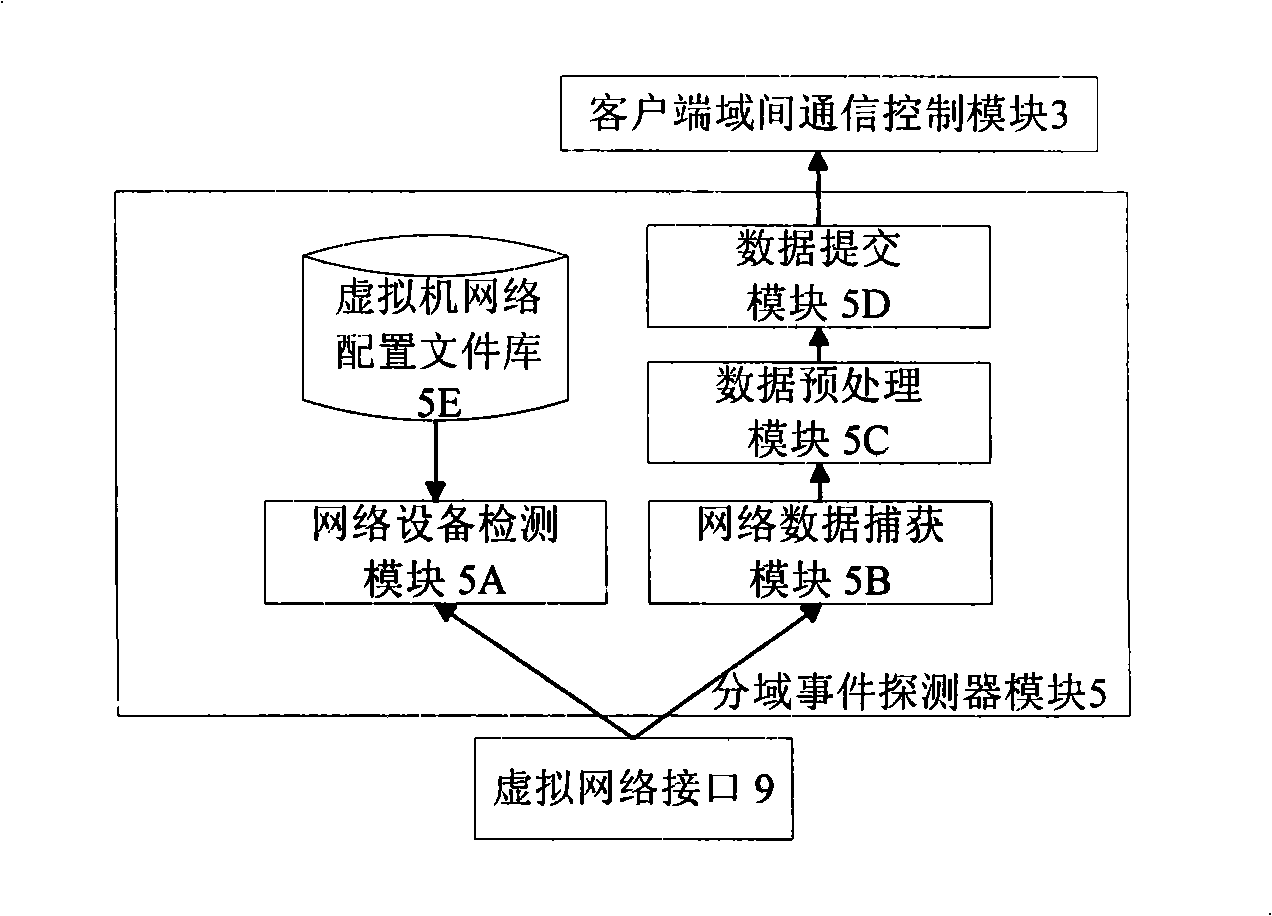
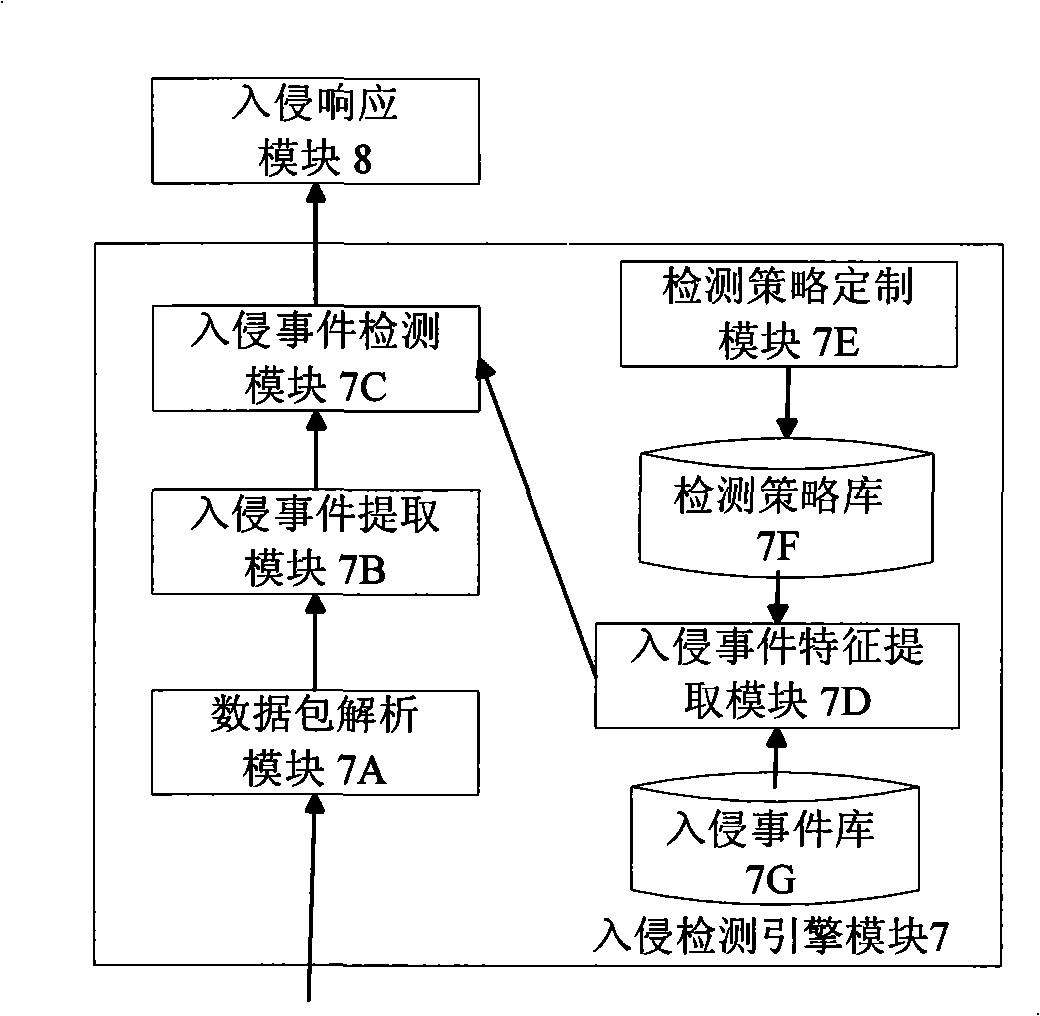
Security network invasion detection system suitable for virtual machine environment
InactiveCN101309180AGuaranteed security featuresCentralized control of intrusion detection rulesData switching networksCommunication controlA domain
The invention discloses a safe network intrusion detection system which is applicable to the virtual machine environment and includes a server inter-domain communication control module, an intrusion detection engine module, an intrusion response control module in the intrusion detection virtual machine, a client inter-domain communication control module, a domain spilt event detector module and a domain split response control module in the detected application virtual machines. According to the problem that the safety of the virtual machine system of the virtual machine needs to be improved; the current intrusion detection system cannot realize the purpose, the safe network intrusion detection system considers the layering structure of the virtual machine network sufficiently and realizes the intrusion detection protection of the virtual machine system in the internal network based on the virtual machine; the safety of the virtual machine applied in the production practice activities is improved; meanwhile, the separation of the intrusion detection system and the protected system is realized based on the separation safety property of the virtual machine; compared with the traditional network intrusion detection system, the safe network intrusion detection system has better safety and reliability.
Owner:HUAZHONG UNIV OF SCI & TECH
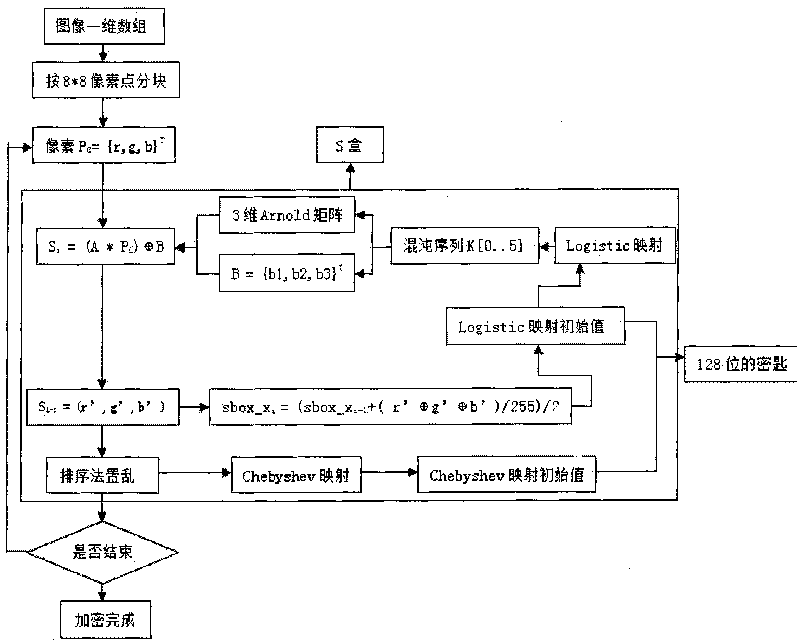
Three-dimensional Arnold mapping-based image grouping encryption method
InactiveCN101739695AIncreased sensitivityHigh sensitivityImage codingChaos modelsGraphicsChebyshev map
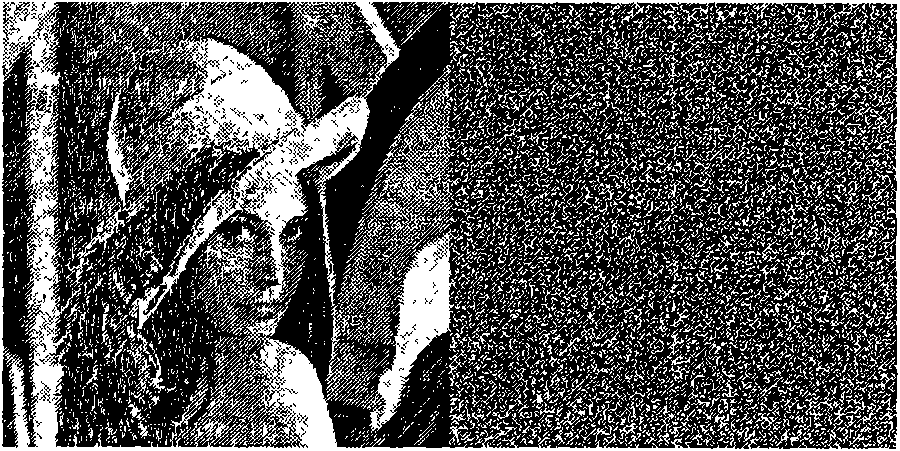
The invention relates to a three-dimensional Arnold mapping-based image grouping encryption method, which is characterized by comprising the following steps: firstly, adopting an Amold mapping extended to three dimensions to construct an S box; then, performing sorting scrambling on a chaotic sequence generated by a Chebyshev mapping; and finishing the encryption operation through multi-iteration. The theoretical analysis and experimental result prove that the three-dimensional Arnold mapping-based image grouping encryption method has the advantages of large key space, high sensitivity, high speed, excellent safety, strong attack resistance, and the like. Compared with other similar methods, the three-dimensional Arnold mapping-based image grouping encryption method guarantees the safety and has higher speed, and is more applicable for graphic data encryption. The main superiority of the method is that: the method has enough key space to resist an exhaustive attack, and the change of a key at any bit can completely change an initial value and the parameters of the chaotic sequence. Therefore, the sensitivity of the key is greatly improved; any useful information cannot be exposed by the statistical property; and the relativity of adjacent pixels of an intensity diagram is small and the attack resistance is strong.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
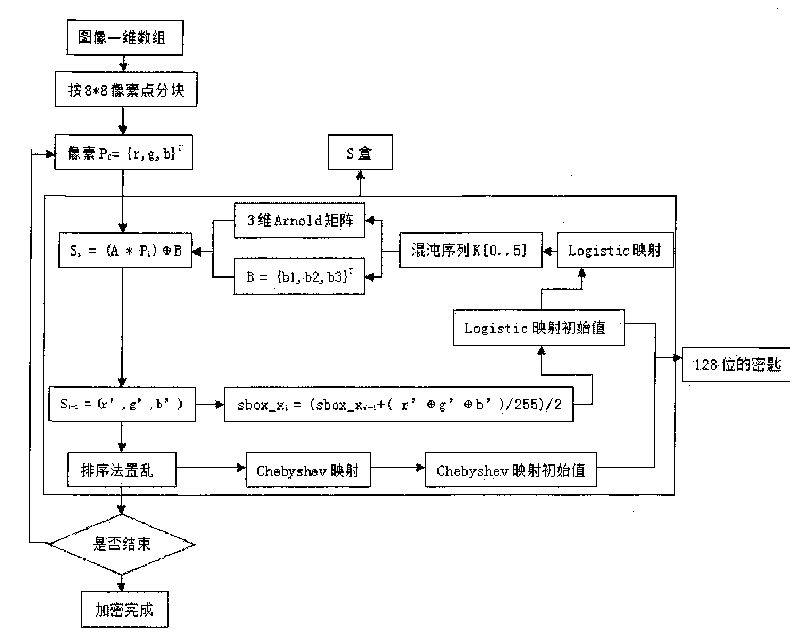
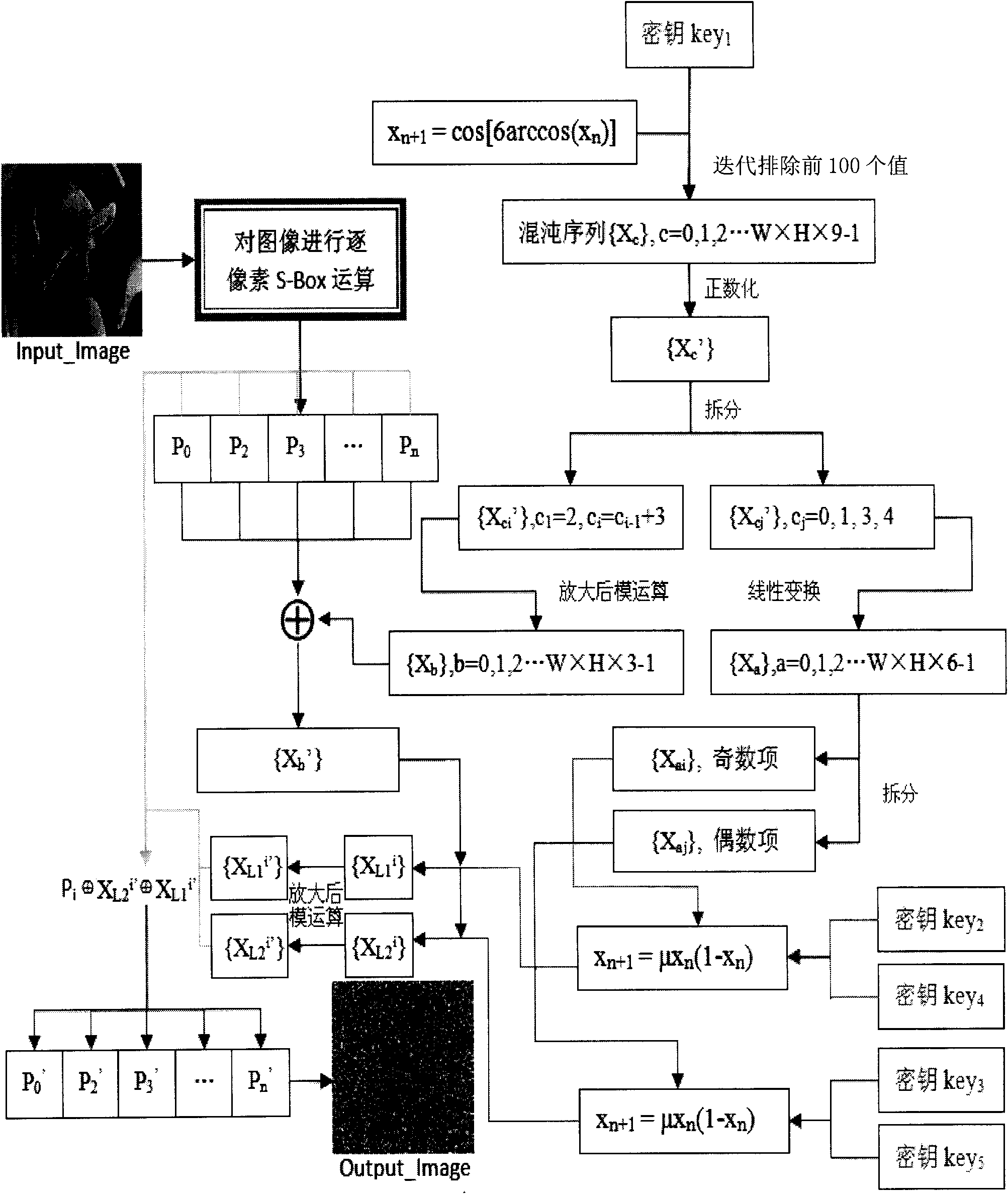
Color image encrypting method based on multi-chaos system
InactiveCN101604439AResist attackLarge key spaceImage data processing detailsArray data structureChaotic systems
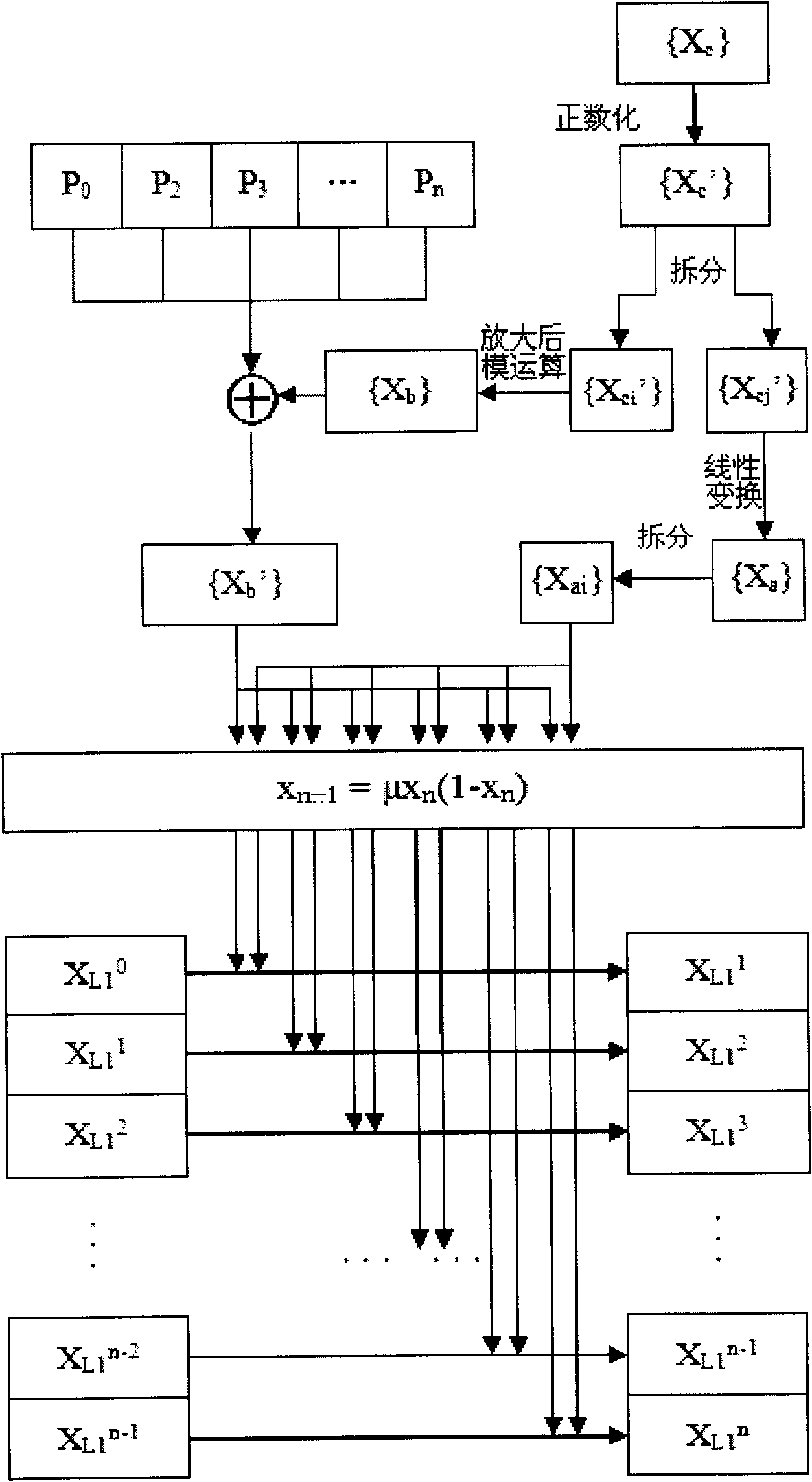
The invention relates to a color image encrypting method based on a multi-chaos system, which is technically characterized in that the gray value of each pixel of an Input-image is recorded as a two-dimensional matrix P(x,y), S box transformation is performed to the P(x,y), and a transformation result is transformed into a pile of pixel groups P(h*x+y), i.e. P0, P1, P2, P3, to Pn, and the pixel groups are recorded as a sequence Pi; XOR operation is performed to each value of {XL1'} and {XL2'} and each pixel in Pi, i.e. Pi'=Pi +XL2'+XL1', thereby finishing the encrypting process. The invention has the advantages of large key space, high key sensitivity, good security and strong anti-attack ability. The security of the method can be completely independent of the attribute of an image and is especially suitable for the condition with higher security requirement.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Image encryption method based on Feistel network and dynamic DNA encoding
ActiveCN108365947AStrong randomnessStrong resistance to attackKey distribution for secure communicationSecuring communication by chaotic signalsPlaintextCiphertext
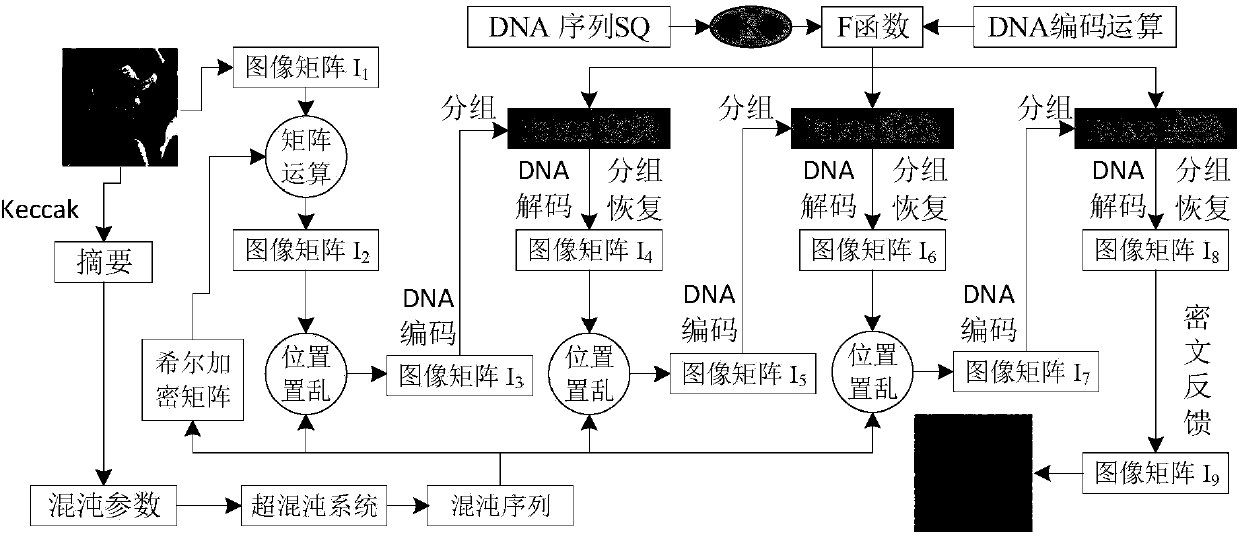
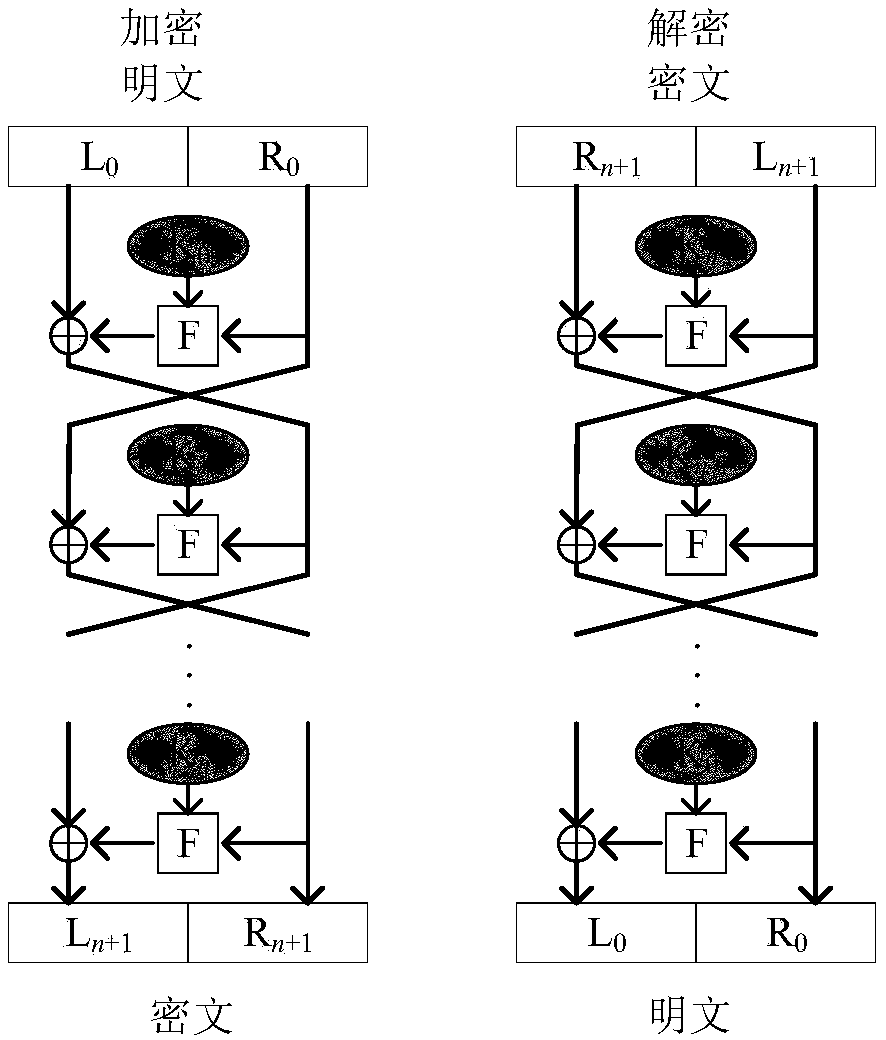
The invention provides an image encryption method based on a Feistel network and dynamic DNA encoding. The method comprises the following steps: computing a Hash value of an original plaintext image by using a Keccak algorithm, and taking the Hash value as an initial value of a hyper-chaotic Chen system, generating a Hill encryption matrix by using a chaotic sequence generated by the hyper-chaoticChen system so as to replace pixels of an original image; realizing image pixel value diffusion by using the DNA encoding operation as a F function of the Feistel network, and a DNA sequence base asa key of the Feistel network; and performing further diffusion through ciphertext feedback. Through three turns of chaotic scrambling-DNA encoding-Feistel conversion-DNA decoding, the ciphertext randomness and attack resistance are stronger, the scrambling conversion of the image pixel location and the diffusion of the pixel value are realized, and the encryption turn is reduced due to repeated scrambling and DNA encoding and decoding. Through the image encryption method provided by the invention, the image can be effectively encrypted, the plaintext sensitivity is strong, the plaintext attack, the differential attack and the statistical attack can be effectively resisted
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Image false-proof method based on chaotic characteristic
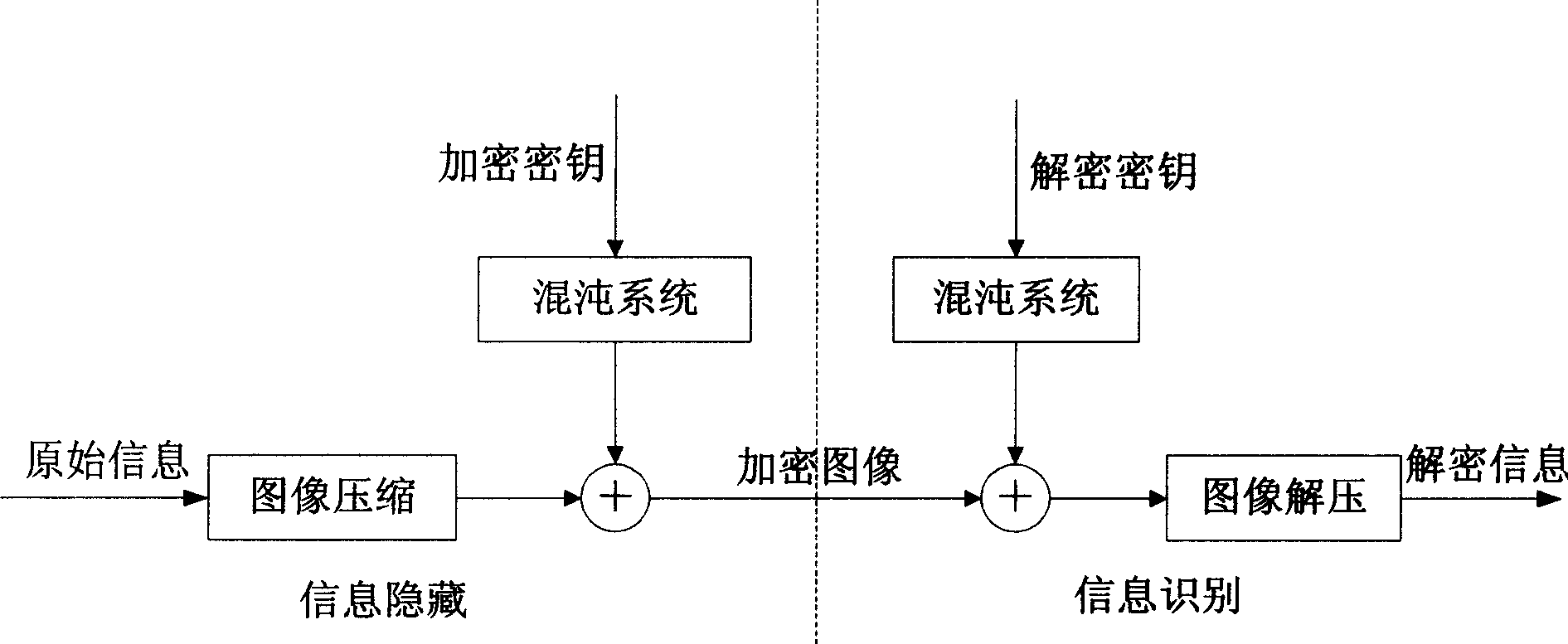
InactiveCN1738235AImplement encryptionAchieve decryptionImage data processing detailsSensing record carriersChaotic systemsImage segmentation
The invention discloses a image counterfeit deterrence method based on the chaotic feature, comprising: first, by the chaotic mapping system, using the information needed keep secret and counterfeit deterrence to generate the chaotic sequence which is used to encode the information, then, printing the encoded information to the two-dimension bar code image according to the PDF417 bar code; collecting the two-dimension bar code image by the scanner, and operating the preprocessing of image segmentation, filtration, geometric correction and stratified on collected image, then decoding the bar code according to the decoding rule of national standard PDF417 bar code to attain the chaotic encoded information carried by bar code image. The invention fully utilizes the features of chaotic system and two-dimension bar code technique which are combined for image counterfeit deterrence. The invention has the characters as strong secret-keeping property and large information carried, while it can recognize automatically.
Owner:XI AN JIAOTONG UNIV
Image encryption method combining three-dimensional Arnold transformation with chaotic sequence
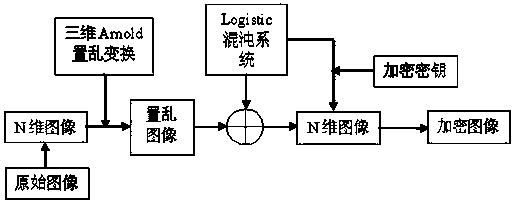
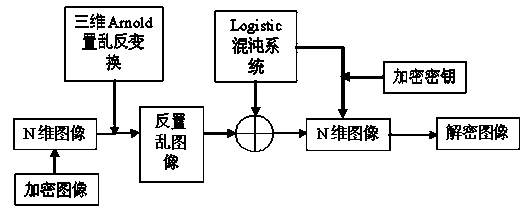
InactiveCN103455971AHigh degree of scramblingImprove securityImage data processing detailsPattern recognitionArnold transformation
The invention relates to an image encryption method combining three-dimensional Arnold transformation with a chaotic sequence. The method includes the steps that firstly, images are processed and converted into multi-dimensional images, pixel value data matrixes of the images are acquired, multiple times of three-dimensional Arnold scrambling transformation is conducted, and then the Logistic chaotic sequence is utilized to conduct bitwise exclusive-or operation with the images to change pixel values of the images. The three-dimensional Arnold transformation is utilized to conduct pixel position scrambling on processed multi-dimensional image data, compared with an ordinary two-dimensional scrambling technology, the scrambling degree of three-dimensional Arnold transformation is higher, then, the chaotic sequence is utilized to change the pixel values, encryption is completed, and the image encryption method has the advantages of being good in safety and high in secret key sensitivity and anti-attack capacity.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
A lightweight secure authentication and key exchange method for narrowband Internet of things
ActiveCN108989318AAvoid risk of leakageReduce Interaction ComplexityTransmissionKey exchangeThe Internet
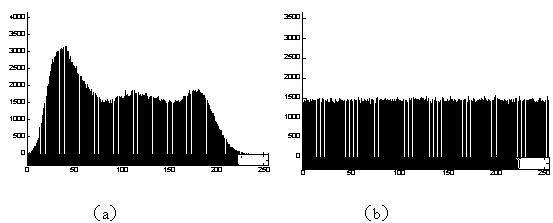
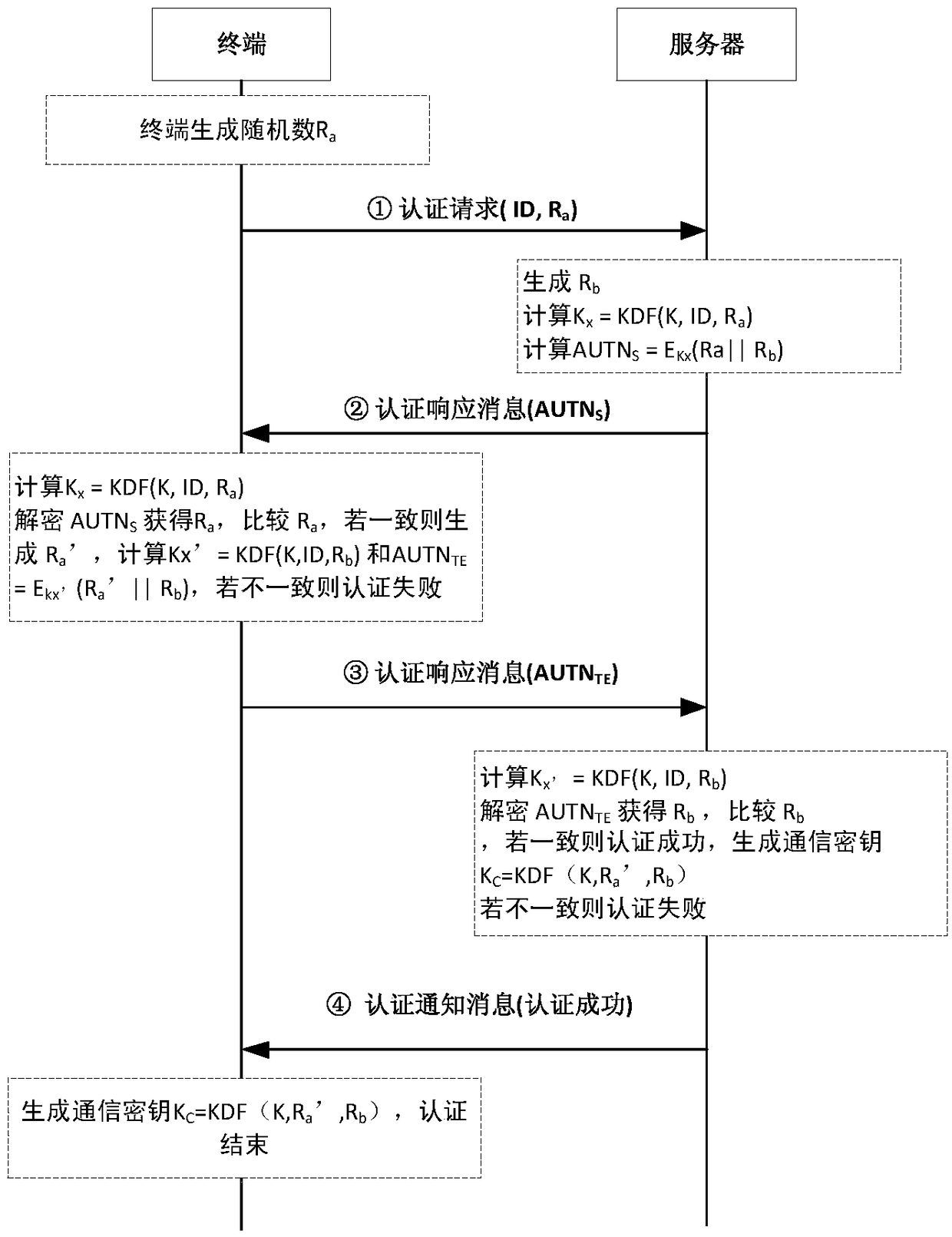
The invention discloses a lightweight security authentication and key exchange method for narrow-band internet of things. The communication main body comprises a terminal and a server. Before the communication is established, the root key is shared between the terminal and the server, and the two-way authentication is realized by adopting a challenge-response interaction mechanism based on a symmetric cryptosystem. The present invention mainly solves the problem of the two-way identity authentication and key exchange between the terminal and server in the Internet of Things application systembased on NB-IoT and other narrow-band Internet of Things connection technologies, can realize lightweight security authentication algorithm, protocol and key agreement mechanism, and meet the design requirements of low power consumption, low bandwidth consumption, low interaction frequency and high security.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Image encryption method based on Arnold transformations and Henon chaotic system
InactiveCN103442157AHigh degree of scramblingImprove securitySecuring communicationPictoral communicationPattern recognitionPlaintext
The invention relates to an image encryption method based on Arnold transformations and a Henon chaotic system. Firstly, a plurality of Arnold scrambling transformations are carried out on images, then scrambling is carried out for a second time on the images through use of a Henon chaotic sequence and then the Henon chaotic sequence is used to carry out a bit-by-bit XOR operation with images to change pixel values of the images. The two technologies are adopted to carry out pixel-value position scrambling twice so that the scrambling degree of the images is higher compared with a single scrambling technology and then the chaotic sequence is adopted to change the pixel values so that any information related to plaintext is completely hidden in the encrypted images. Therefore, the method has the advantages of being great in safety and high in anti-attack ability and the like.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Cipher key negotiating method, enciphering/deciphering method and signature/verification method
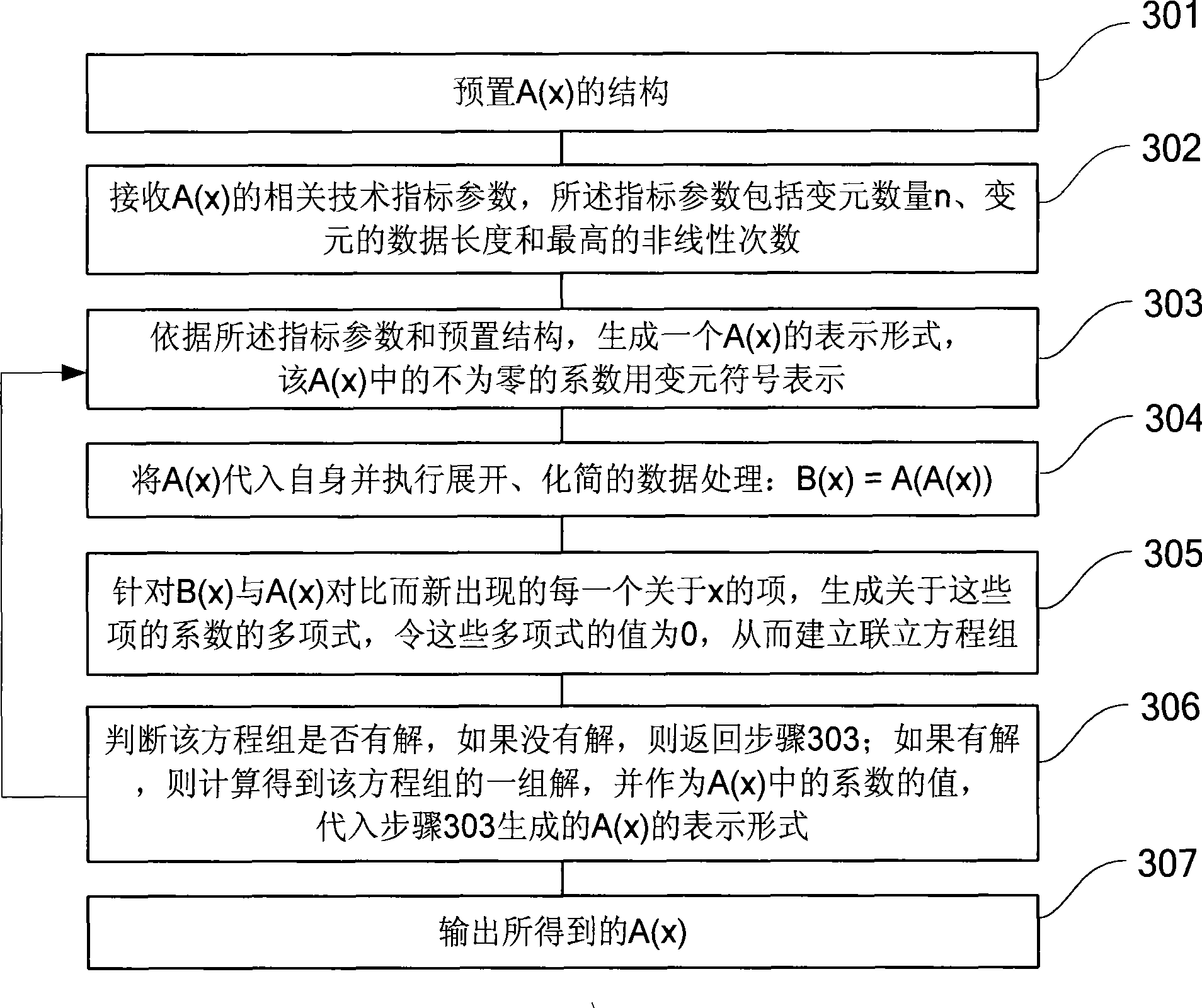
InactiveCN101374043AScale upIncreased complexityKey distribution for secure communicationPublic key for secure communicationAlgorithmFunction group
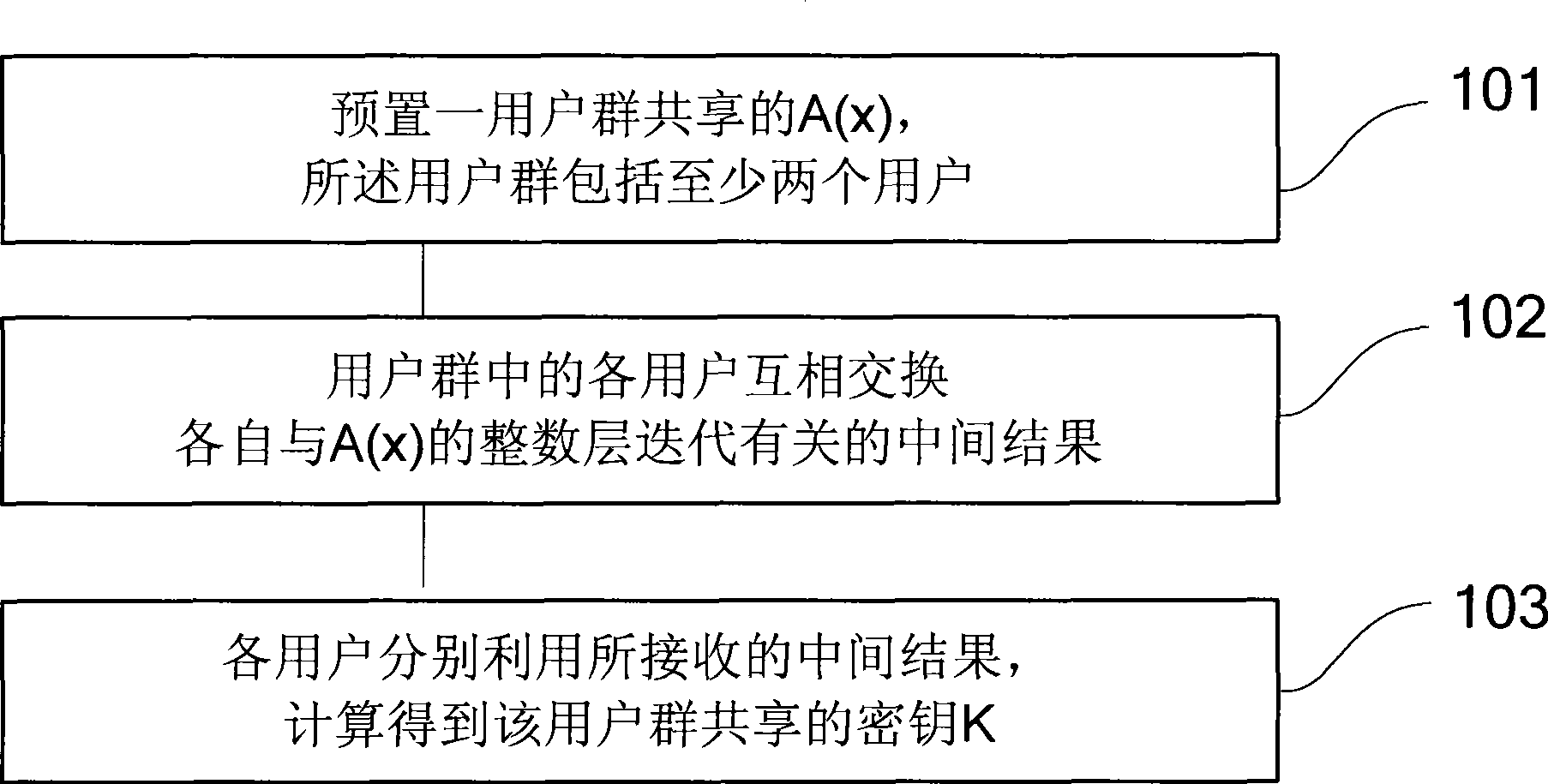
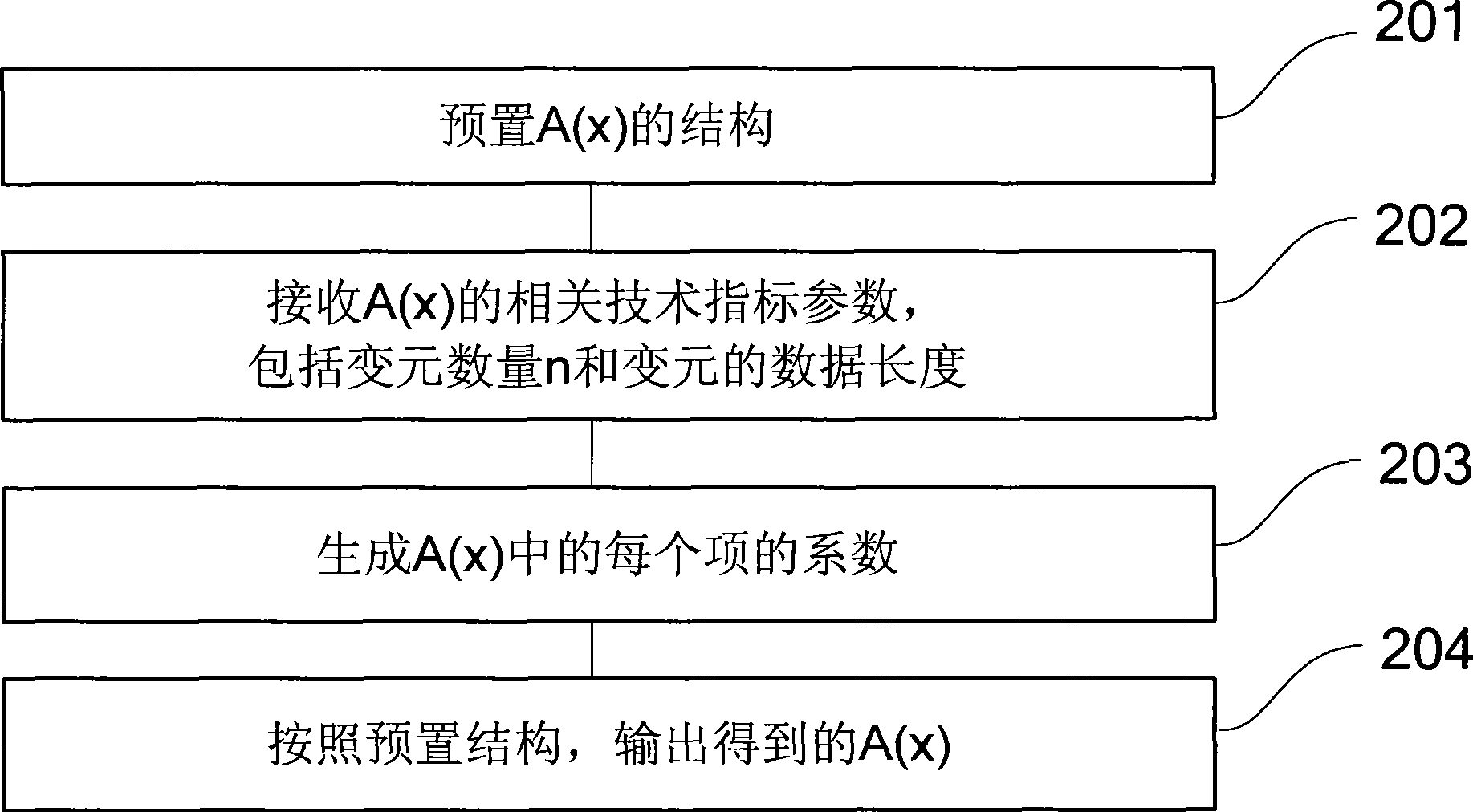
The invention provides a key agreement method and an encryption / decryption method and a signature / verification method. The key agreement method comprises the following steps: step 1. an A(x) shared by a user group is prearranged, wherein the user group comprises at least two users; the A(x) is a nonlinear function group from n vector x to n vector y=(y1,ellipsis, yn)=A(x)=(A1(x1,ellipsis,xn),ellipsis, An(x1,ellipsis,xn), wherein n is more than 1; and the A(x) meets the conditions that when the s layer iterative A<(s)>(x) of the A(x) is compared with the A(x), the number and type of the subsections with non-zero x coefficient are kept unchanged, and s is an integer; if B(x) is equal to A(A(x)), A(B(x)) is equal to B(A(x)); step 2: the users in the user group exchange the intermediate results related to the integer layer iteratives of the A(x); and the step 3: the users respectively adopt the received intermediate results to calculate the key K which is shared by the user group. The method has the advantages of unique coding style, strong attack resistance, enhanced scale and complexity of the cryptographic algorithm, and improved space and safety of the algorithm.
Owner:管海明 +1
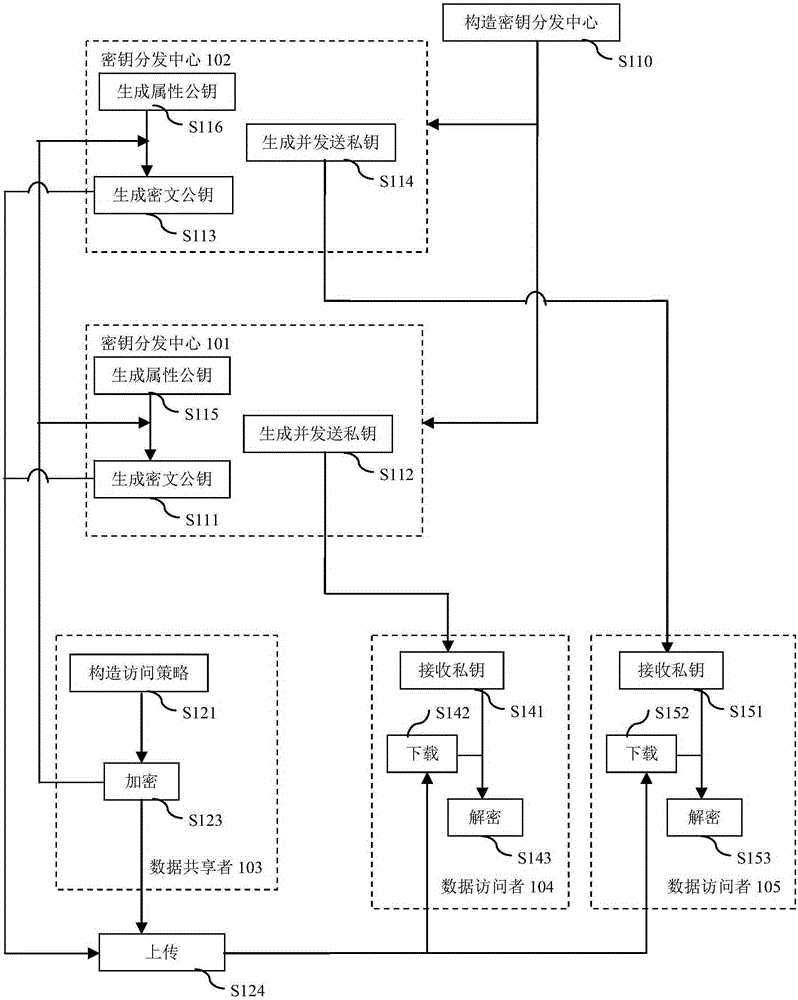
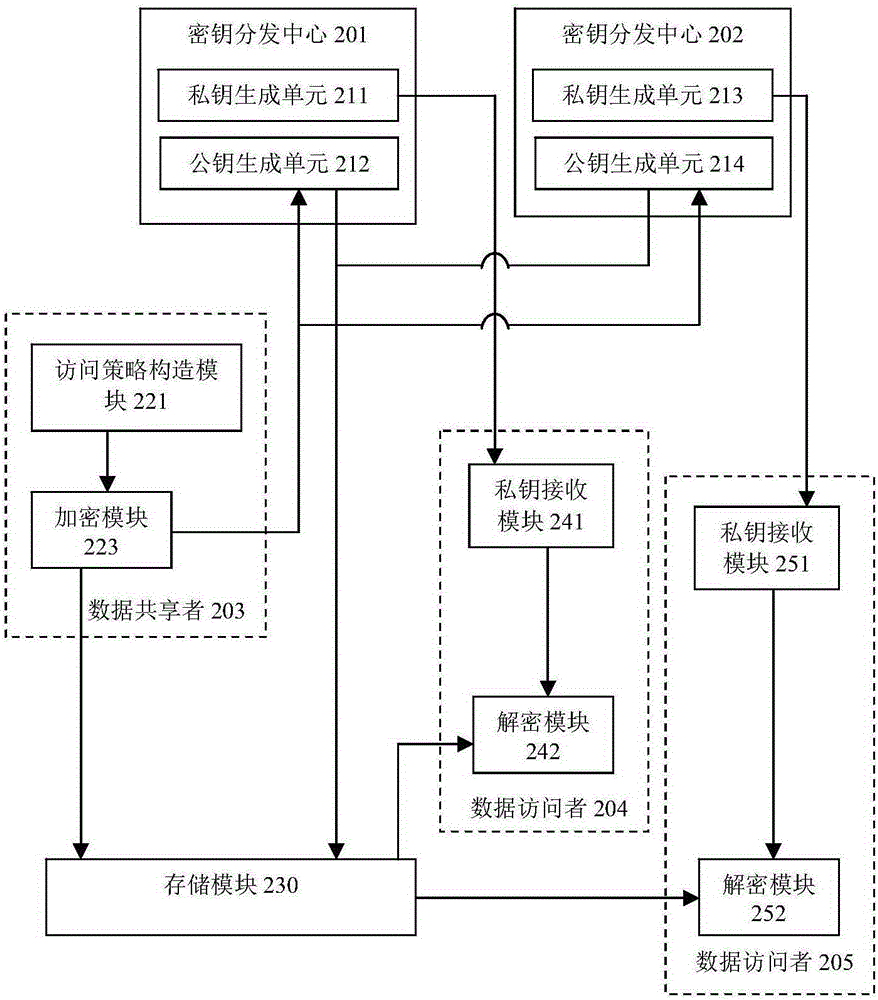
Data sharing system
The invention discloses a data sharing method and system. The method comprises the following steps that: a plurality of secret key distribution center is constructed by using a unified common parameter; on the basis of the common parameter, each secret key distribution center generates an attribute public key corresponding to an attribute of a user; a corresponding secret key is generated based on a user attribute of a data visitor; a data sharer constructs an access strategy according to an access limit demand of shared data; encryption is carried out on the shared data by using an encryption secret key to generate a ciphertext; on the basis of the access strategy and the corresponding attribute public key, the encryption secret key is encrypted to generate a ciphertext public key; and the ciphertext is decrypted according to the ciphertext public key and a private key of the data visitor meeting the access strategy. Compared with the prior art, the safety performance of the system can be substantially improved with the method; and on the premise that safety is not reduced, the computational work of the method can be substantially reduced.
Owner:CHINA STANDARD SOFTWARE
Device for establishing network isolated channel and method thereof
InactiveCN102316108AHighlight substantive featuresSignificant progressInternal/peripheral component protectionSecuring communicationThird partyVirtual network
The invention relates to a device for establishing a network isolated channel and a method thereof. A safe communication channel is established between two or multiple network devices through a network channel isolating device. The network channel isolating device is provided with an internal network interface and an external network interface. The internal network interface is connected with an internal network device. The external network interface is connected with an external network device. The network device which is connected with the internal network interface is protected by the network channel isolating device. A set of network devices protected by the network channel isolating device is called as a network channel isolating device protection domain. Host computers in different domains can communicate safely. By establishing a virtual network isolated channel through a public network among different geographic locations and by adopting an encryption algorithm recommended by the State Secrecy Bureau to conduct high-strength encryption to communication data, any third party cannot effectively decrypt the encrypted data and the communication data cannot be falsified; and the problem that different departments of small and medium enterprises cannot communicate safely through the public network is solved.
Owner:周伯生
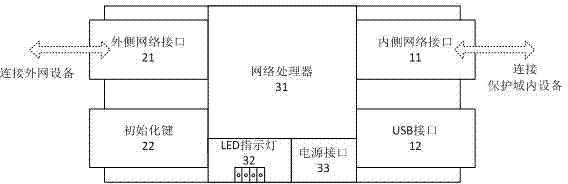
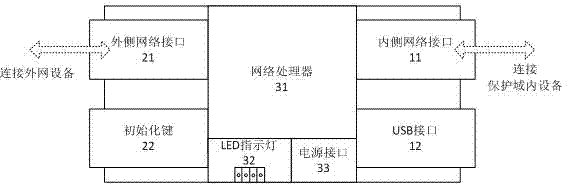
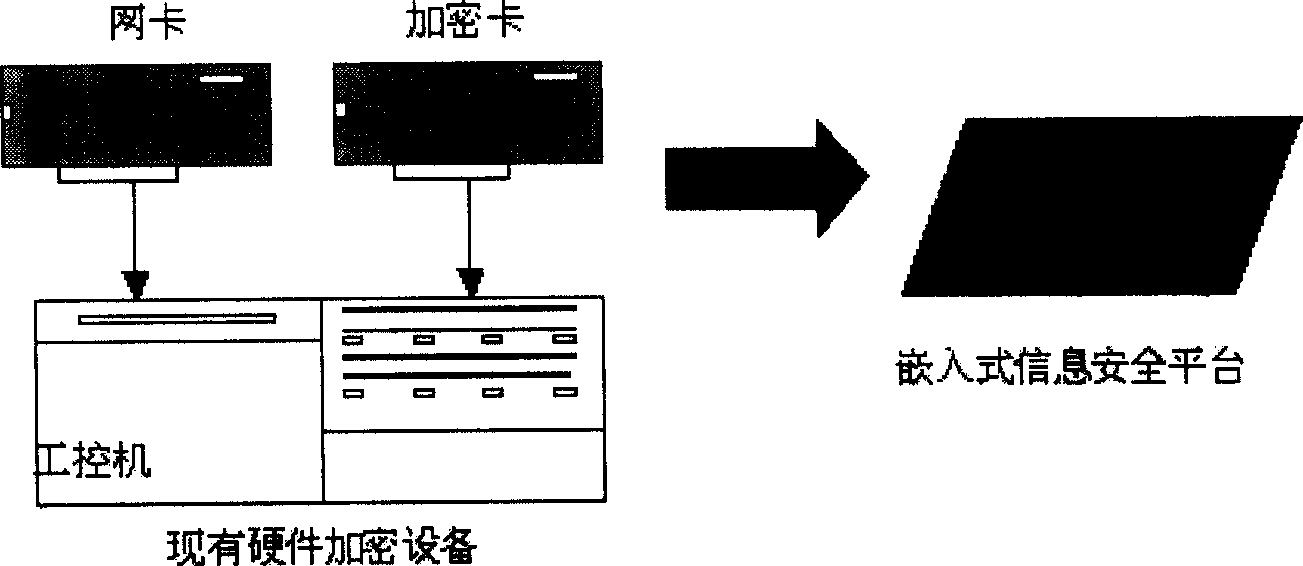
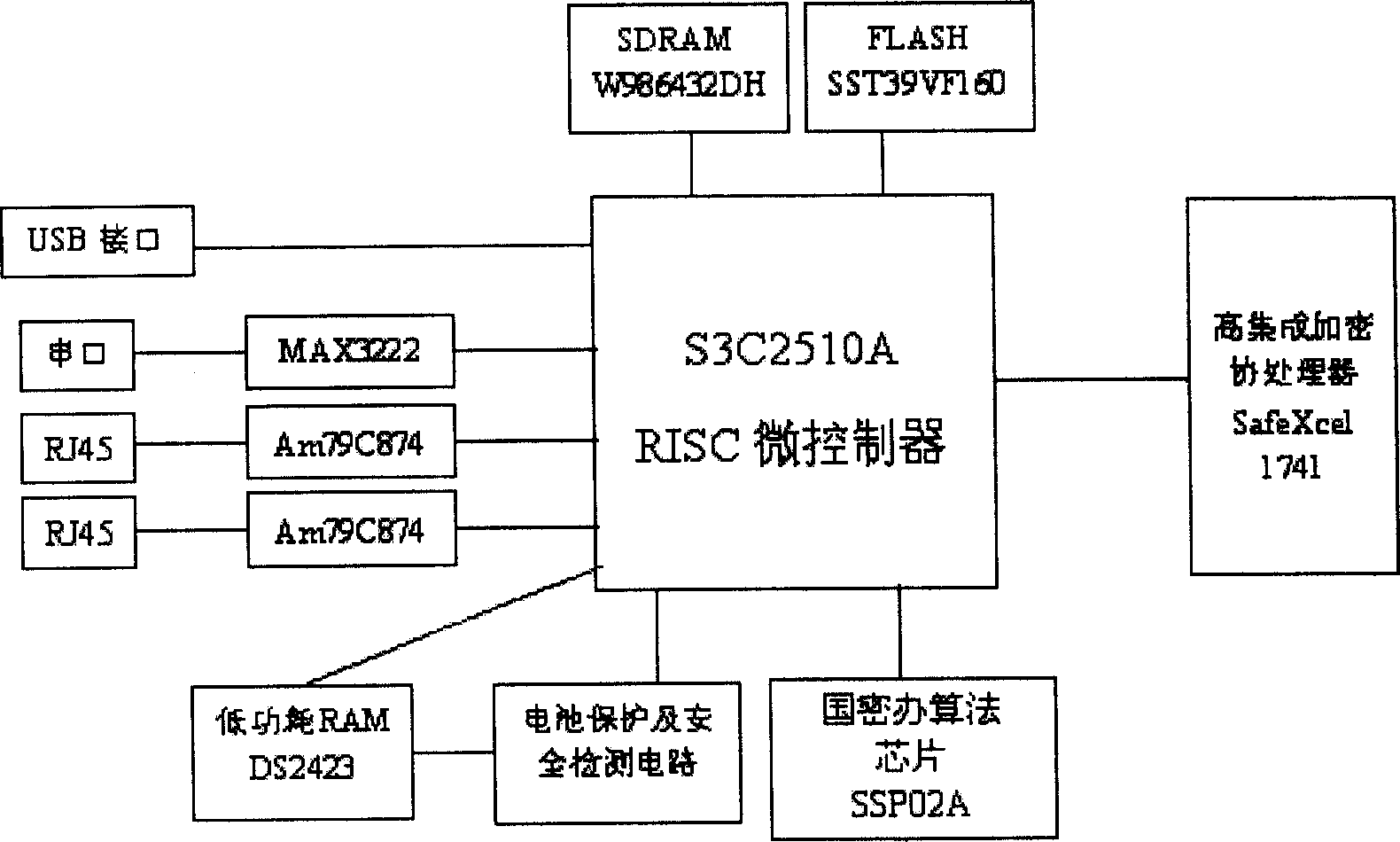
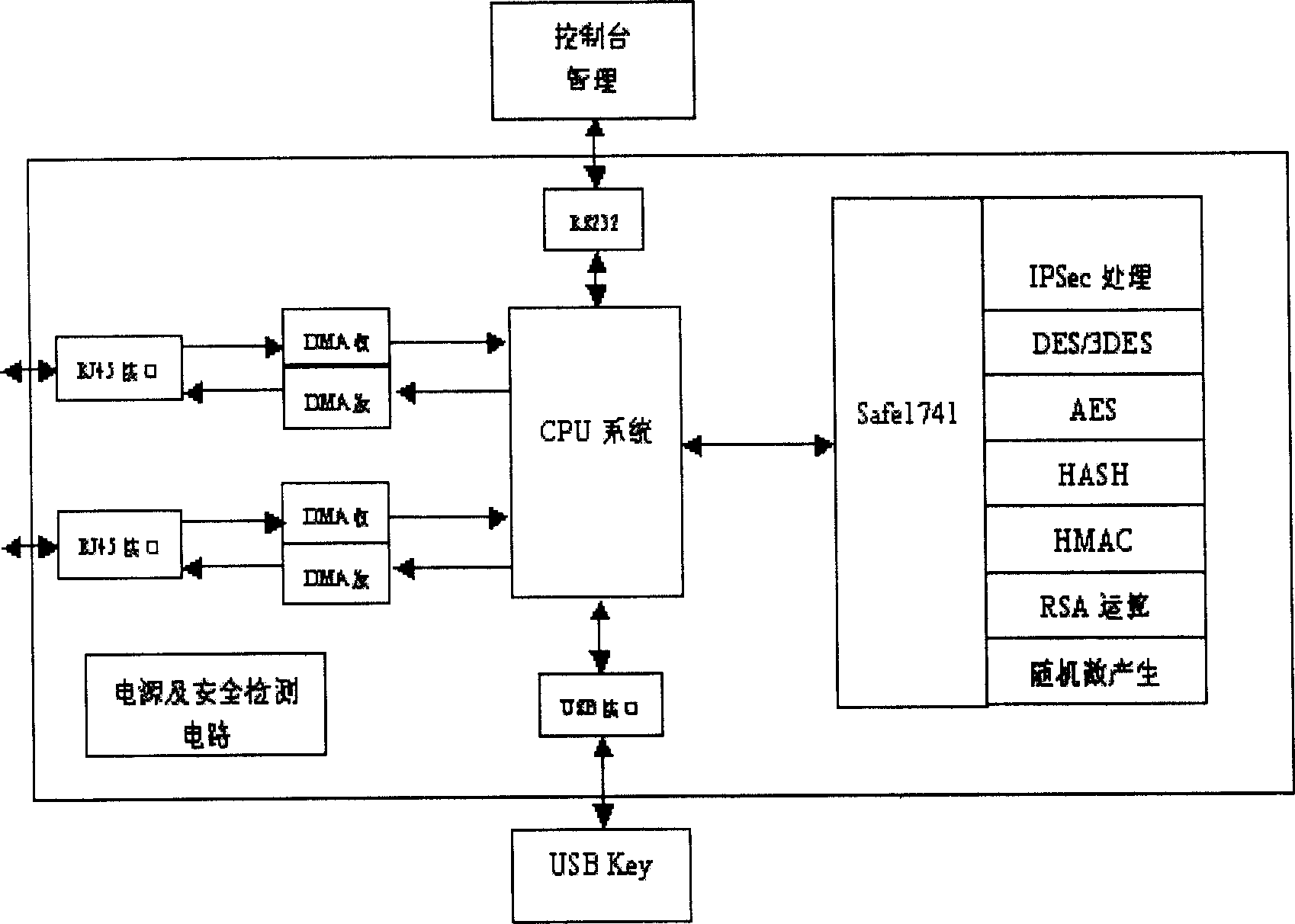
An embedded information security platform
InactiveCN1622517ALow costStrong securityData switching networksSecuring communicationSerial digital interfaceApplication Context
The embedded information safety platform features the CPU micro controller as one network processing chip with ARM940T kernel containing real-time embedded operation system; enciphering and deciphering hardware chip comprising IPSec algorithm chip and symmetric algorithm chip; I / O interface including two 10 / 100 M adaptive Ethernet interfaces, one USB main control interface and one serial interface. The present invention is one opening hardware safety platform enclosed inside one casing and with relaxed application environment, powerful attack resistance and high reliability. The present invention has several enciphered algorithms, supports several kinds of application service, has high versatility, and may be used also in ciphering server, VPN ciphering gateway, SSL safety gateway, safety router, hardware fire wall and other safety devices.
Owner:上海极毅信息科技有限公司
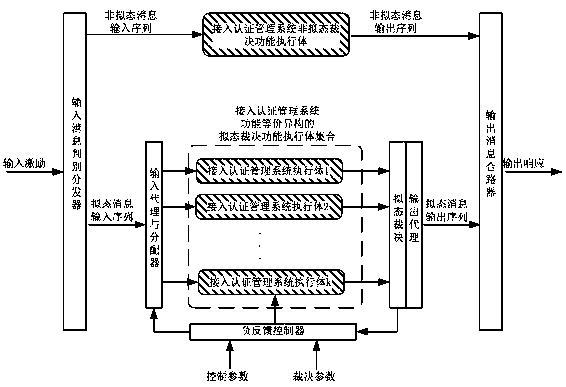
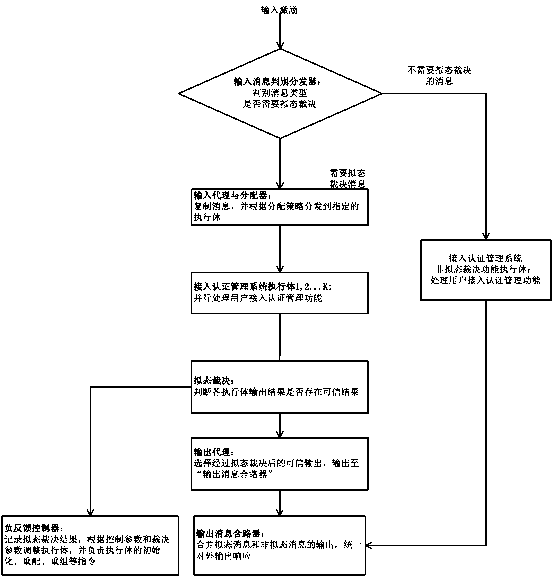
Endogenous safe user access authentication management system and method
ActiveCN110691107AReduce Cybersecurity RisksReduce security risksTransmissionMessage typeParallel processing
The invention discloses an endogenous safe user access authentication management system and method. The method comprises the following steps: an input message discrimination distributor discriminatesthe message type of input excitation information to determine whether mimicry decision needs to be carried out or not, directly sends the input excitation information to a non-mimicry decision function executor to be processed when mimicry decision does not need to be carried out, and sends the input excitation information to a mimicry input agent and a distributor when mimicry decision needs to be carried out; the mimicry input agent and the distributor are copied and distributed to a specified access authentication management system executor according to the distribution strategy; the specified execution body executes parallel processing operation and outputs an execution result to the mimicry decision module; the mimicry decision module operates a credible result discrimination algorithm to calculate credible output according to each execution result and sends the credible output to the mimicry output agent module; and the output message combiner is used for receiving the trusted output sent by the mimicry output agent module or the output of the non-mimicry judgment function execution body and carrying out external output response.
Owner:NANJING REDMATRIX NETWORK SECURITY TECH R & D INST
Synthesis of ordered mesoporous carbon-silicon nanocomposites
InactiveUS7910082B2Large specific surface areaImproved and economical synthesisNanotechPhysical/chemical process catalystsCarbide siliconActive agent
A method for preparing ordered mesoporous silicon carbide (OMSiC) nanocomposites uses an evaporation-induced self-assembly of a precursor composition that preferably includes a phenolic resin, pre-hydrolyzed tetraethyl orthosilicate, a surfactant, and butanol. The precursor mixture is dried, cross-linked and heated to form ordered mesoporous silicon carbide material having discrete domains of ordered, mesoscale pores.
Owner:CORNING INC
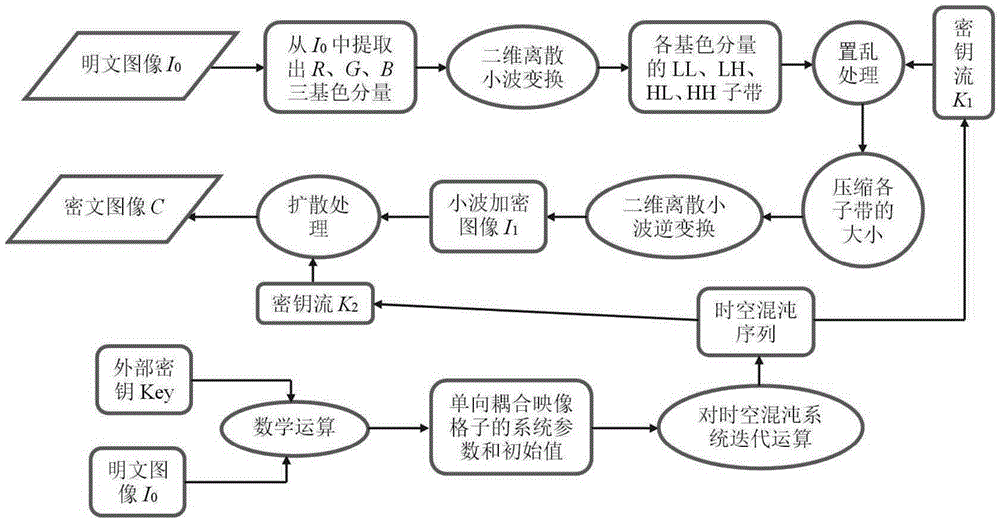
Color image lossless encryption method on basis of two-dimensional discrete wavelet transform and spatiotemporal chaos
The invention relates to a color image lossless encryption method on the basis of two-dimensional discrete wavelet transform and spatiotemporal chaos. The color image lossless encryption method comprises the following steps: separating three primary color components of a color plaintext image to obtain matrices IR0, IG0 and IB0; by utilizing an external key and combining the plaintext image, generating spatiotemporal chaos system parameters and initial values and carrying out iterative operation on a spatiotemporal chaos system to obtain key streams K1 and K2; carrying out two-dimensional discrete wavelet transform on the components IR0, IG0 and IB0 to obtain three groups of sub-bands; utilizing the key stream K1 to respectively carry out disorder processing on the three groups of sub-bands and compressing the sub-bands; respectively carrying out two-dimensional discrete wavelet transform on each group of processed sub-bands to obtain a wavelet encrypted image I1; utilizing the key stream K2 to carry out diffusion treatment on the image I1 to obtain a final ciphertext image C. Compared with an existing image encryption method, the color image lossless encryption method provided by the invention has the advantages of high safety, good encryption effect, lossless information, high encryption speed, high attack resistance and the like and can be widely applied to the fields of medicine, biological gene, military and the like.
Owner:HENAN UNIVERSITY
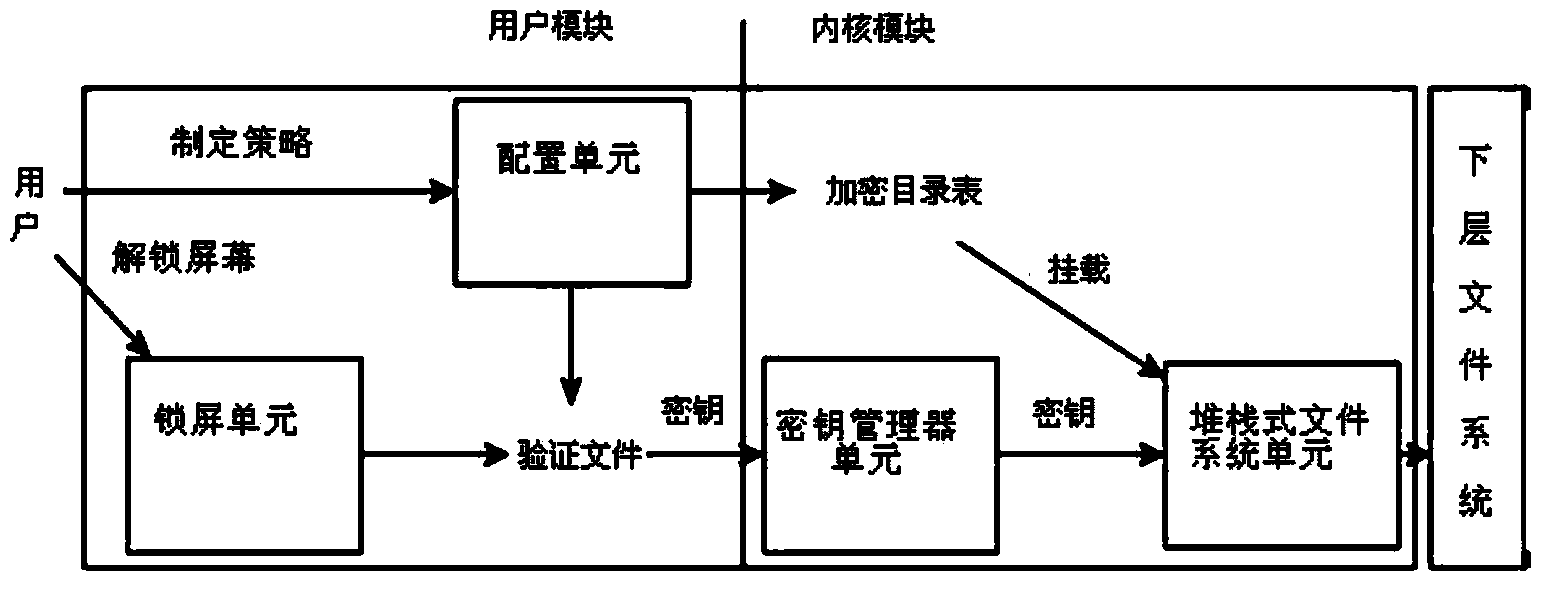
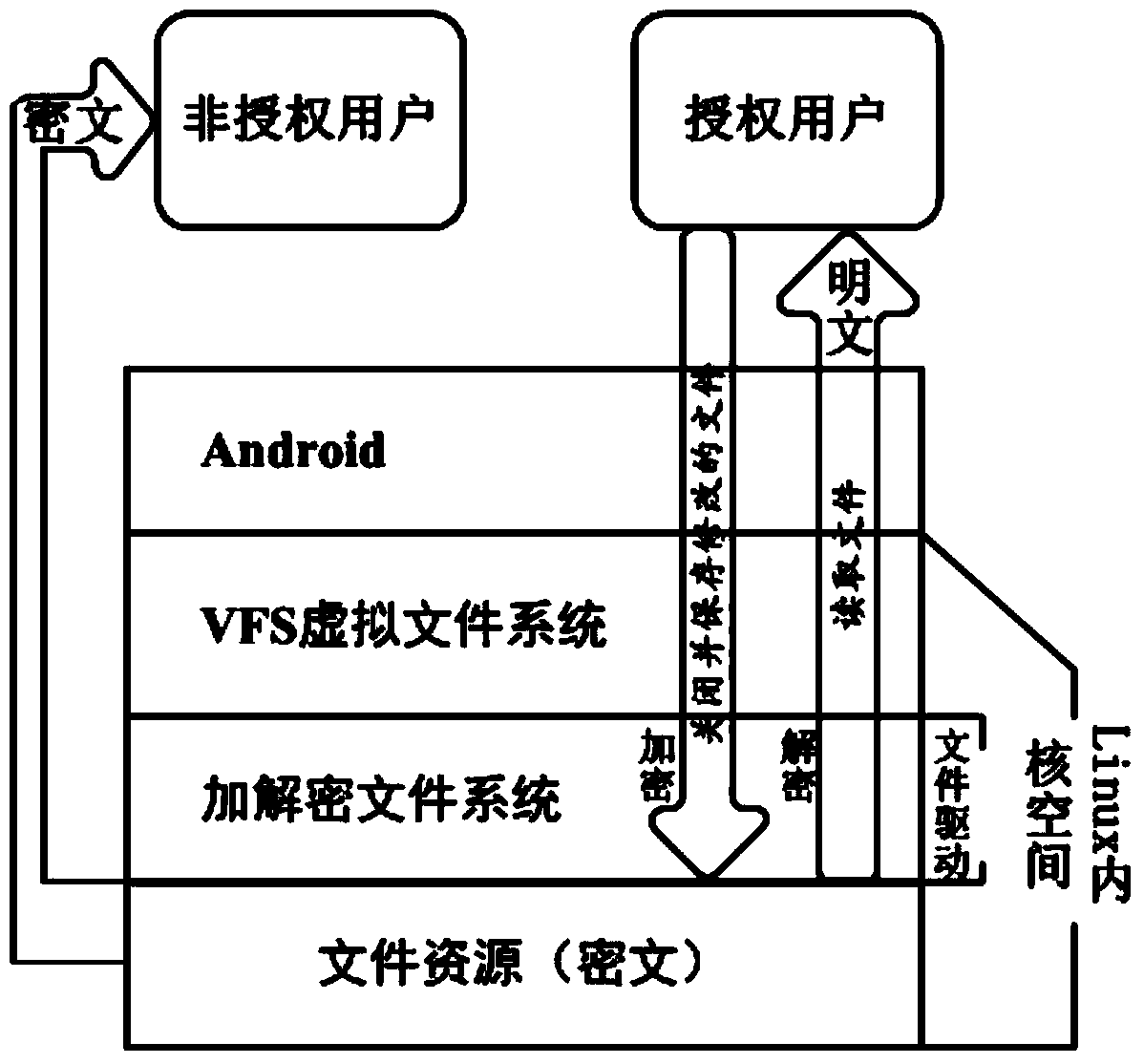
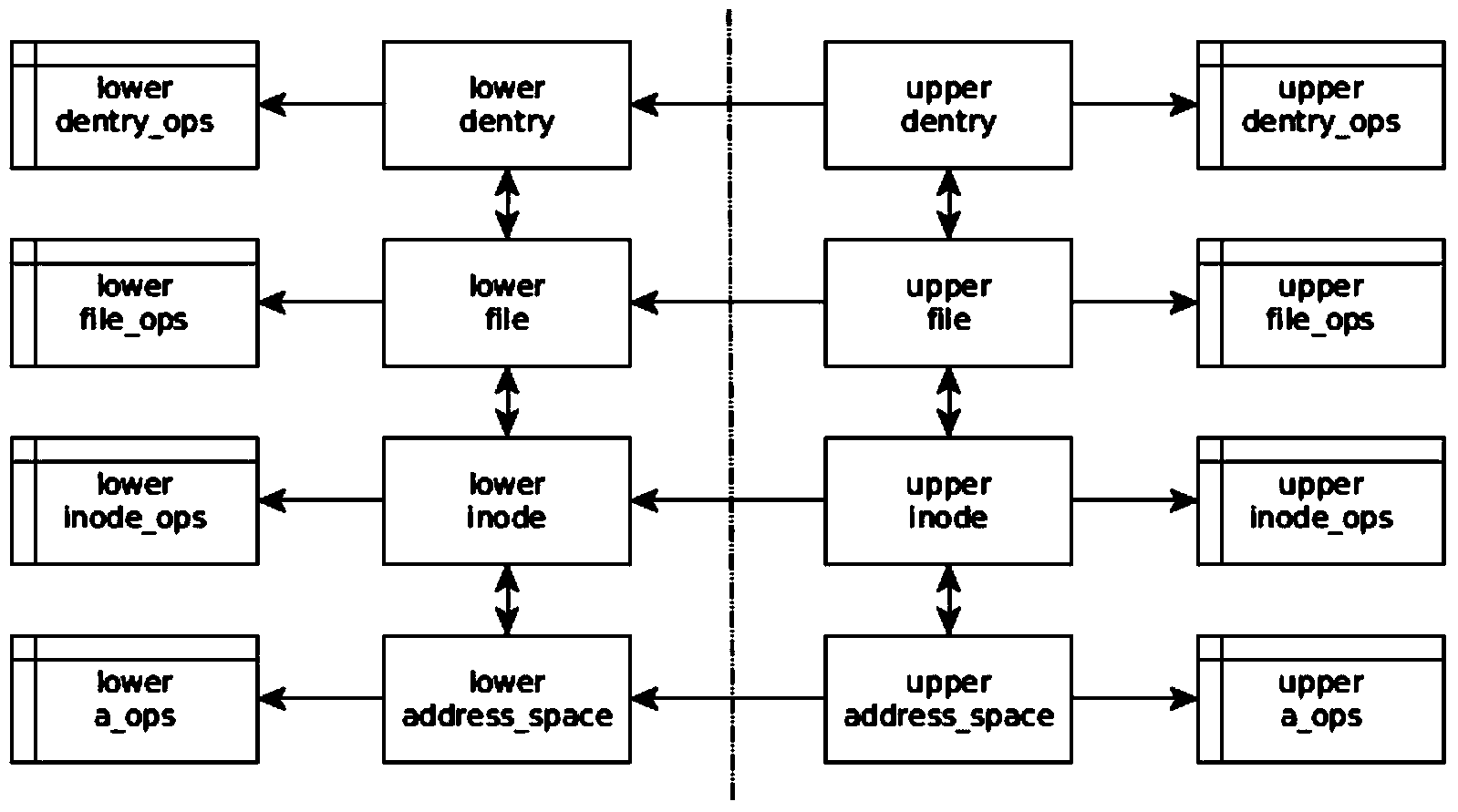
Method and system for file transparent encryption and decryption of Android platform
ActiveCN104252605ADo not change operating habitsDoes not affect experienceDigital data protectionDigital data authenticationPassphraseOperational system
The invention discloses a method for file transparent encryption and decryption of the Android platform. The method includes the steps: selecting a route of a folder where a file needed to be protected is positioned, and setting passwords; respectively generating an encrypted route dictionary list and an authentication file according to the route and the passwords input by a user; scanning the encrypted route dictionary list, if an operating system is started for the first time, subjecting the protected file to first-time initialization encryption according to list items, and then carrying out the next step; when the user triggers a screen unlocking event, receiving a passphrase input by the user, comparing the passphrase subjected to hash algorithm with the authentication file generated at the step two, and if the passphrase is not matched with the authentication file, judging that unlocking fails; if the passphrase is matched with the authentication file, subjecting the passphrase to sha 1 algorithm to generate a secret key, and storing the secret key; calling the secret key for encryption and decryption of the file. The invention further discloses a system for file transparent encryption and decryption of the Android platform. File protection is realized on the premise of small interferences to user operations.
Owner:SUQIAN XINCHAO INFORMATION TECH CO LTD
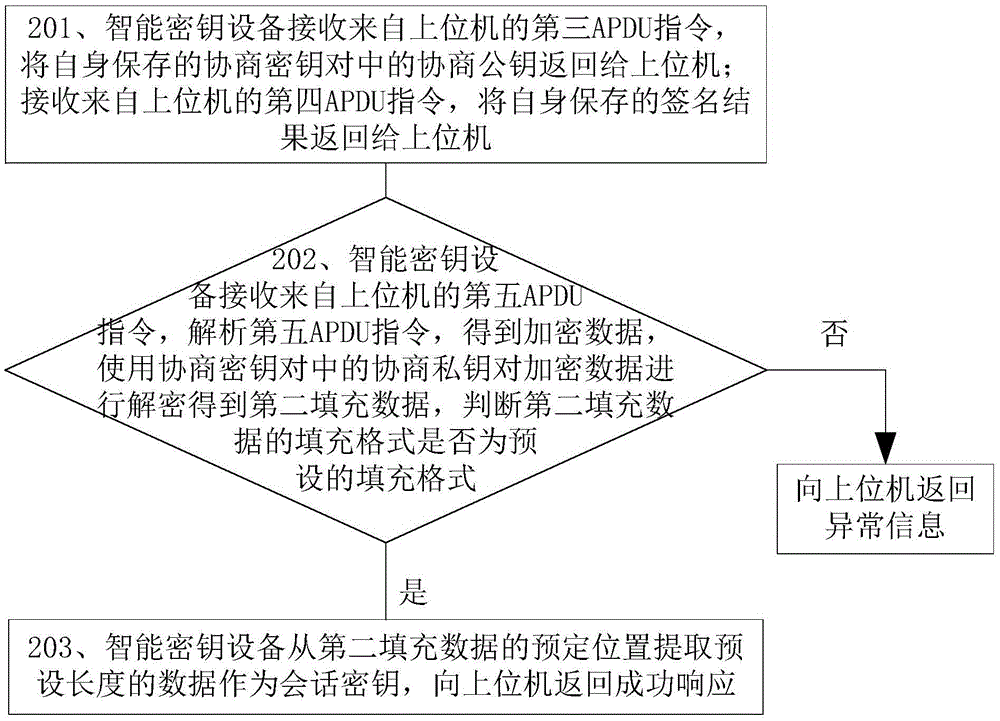
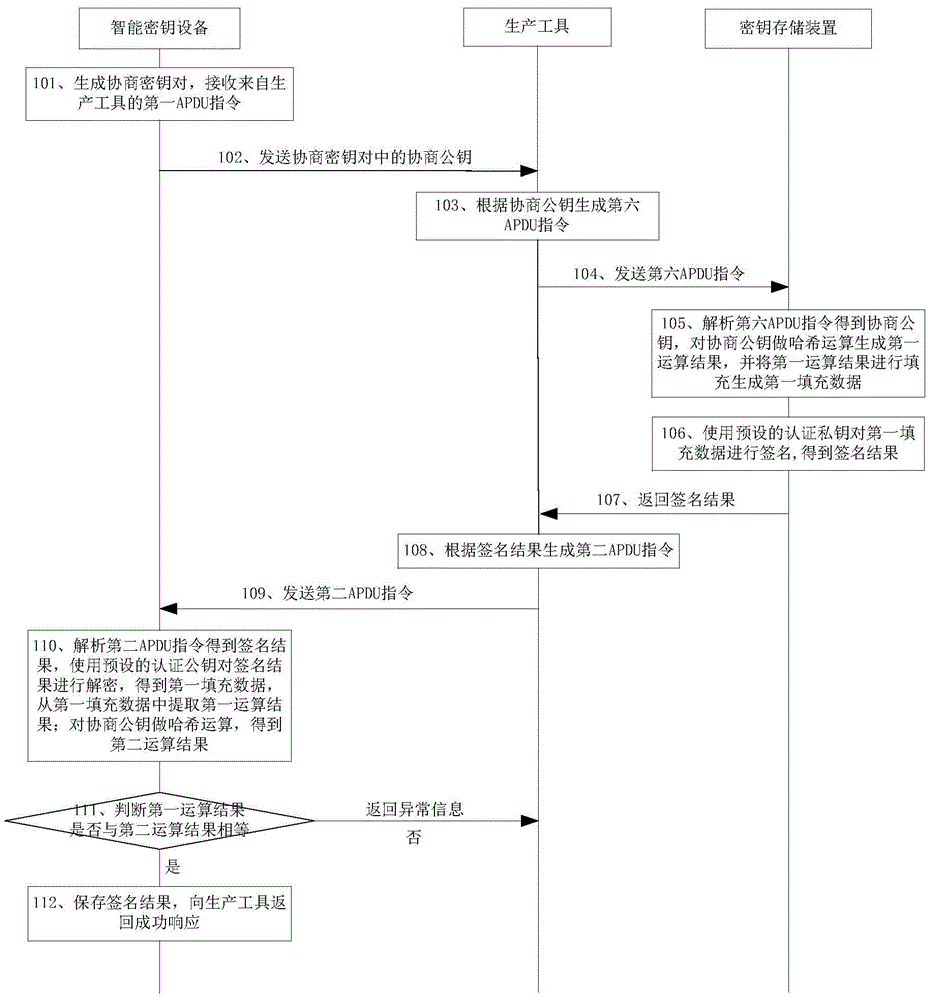
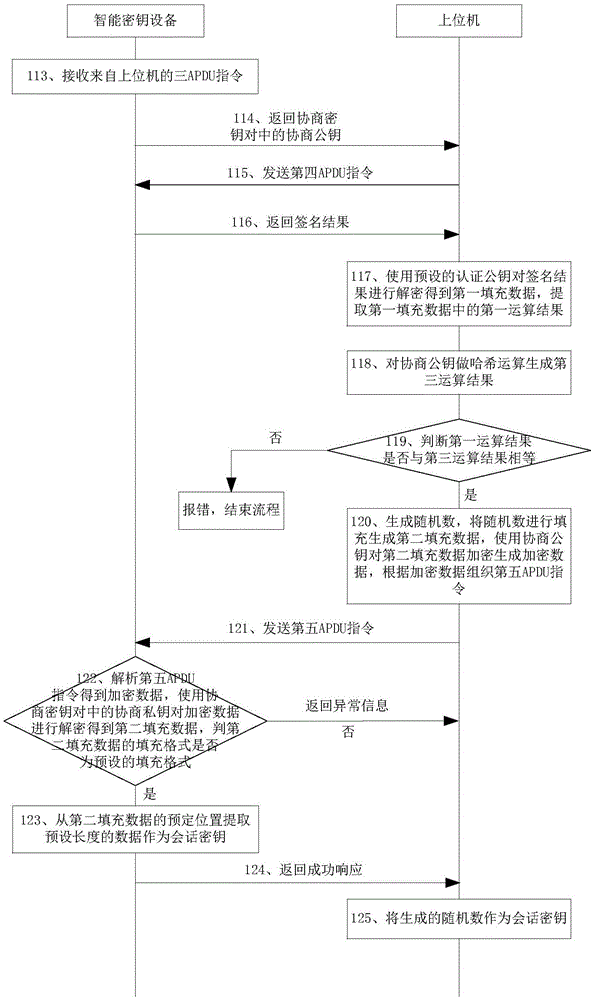
Session key negotiation method and intelligent secret key device
ActiveCN105634742AImprove confidentialityAvoid crackingKey distribution for secure communicationUser identity/authority verificationComputer hardwareSession key
The invention discloses a session secret key negotiation method and an intelligent secret key device, and belongs to the information security field. The method includes the steps of: receiving a third APDU instruction from a host computer by the intelligent secret key device and returning negotiation public key to the host computer; receiving a fourth APDU instruction from the host computer, and returning a signature result to the host computer; receiving fifth APDU instruction from the host computer by the intelligent secret key device, analyzing the fifth APDU instruction to obtain encryption data, using negotiation private key to decrypt the encryption data, and obtaining second filling data; judging whether a filling format of the second filling data is a pre-set filling format, if so, extracting the data with the pre-set length from a pre-set position of the second filling data as a session secret key, and returning the successful response to the host computer, otherwise returning abnormal information to the host computer. The session secret key generated by the method has strong anti-attack capability. After the information transmitted between the host computer and the intelligent secret key device is encrypted by the session secret key, the information is difficult to be intercepted by malicious programs.
Owner:FEITIAN TECHNOLOGIES
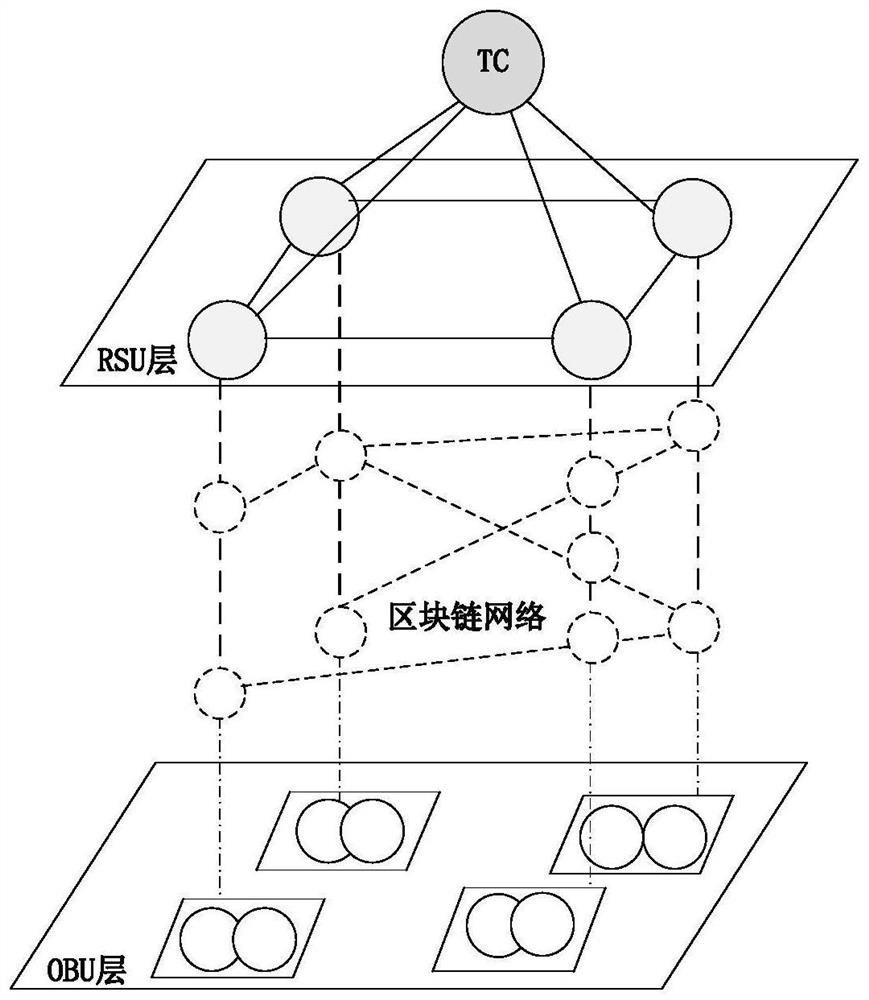
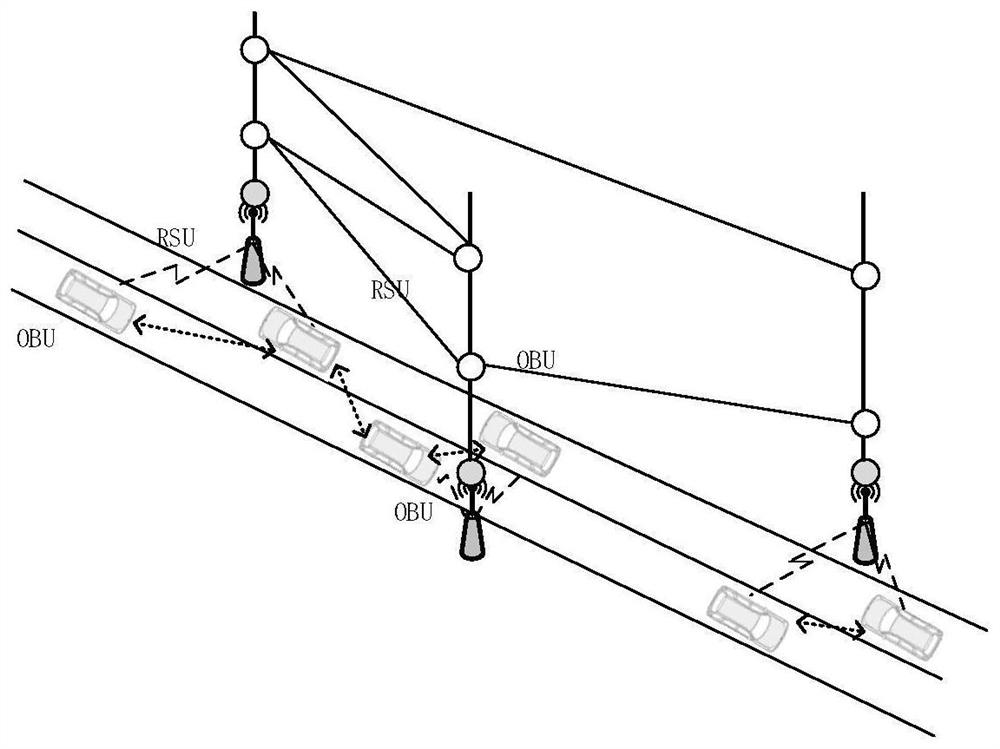
Internet of Vehicles distributed trust system based on HashGraph and trust value calculation method
PendingCN111988381AMeet real-time requirementsGuaranteed unforgeableKey distribution for secure communicationPublic key for secure communicationAccess networkThe Internet
The invention provides an Internet of Vehicles distributed trust system based on HashGraph and a trust value calculation method, and the system comprises an OBU layer which is used for achieving the sensing, collection, calculation and communication functions of a vehicle node for information; a RSU layer which is a network layer formed by the drive test units, serves as a fixed communication node, provides service for wireless access of the vehicle nodes, and forwards the road condition information; a background trusted center (TC) which is used for distributing a secret key to the nodes in the access network and completing registration, revocation or authentication of node identities; and HashGraph block chain nodes, wherein the HashGraph block chain nodes are arranged on Internet of Vehicles nodes, and a plurality of HashGraph block chain nodes form the HashGraph block chain network. The invention discloses the Internet of Vehicles distributed trust system based on HashGraph and thetrust value calculation method. A block chain 3.0 technology-HashGraph is applied to research of the Internet of Vehicles trust mechanism, the problem of centralized single-point failure of a traditional Internet of Vehicles trust mechanism is solved, 103-104 transactions can be processed in parallel by the HashGraph, and the real-time requirement of the Internet of Vehicles is met.
Owner:NANTONG UNIVERSITY +1
Synthesis Of Ordered Mesoporous Carbon-Silicon Nanocomposites
InactiveUS20100040834A1Improve thermal stabilityLarge specific surface areaNanotechPhysical/chemical process catalystsCross-linkEvaporation
A method for preparing ordered mesoporous silicon carbide (OMSiC) nanocomposites uses an evaporation-induced self-assembly of a precursor composition that preferably includes a phenolic resin, pre-hydrolyzed tetraethyl orthosilicate, a surfactant, and butanol. The precursor mixture is dried, cross-linked and heated to form ordered mesoporous silicon carbide material having discrete domains of ordered, mesoscale pores.
Owner:CORNING INC
Multifunctional audio protection method with digital copyright protection and content authentication
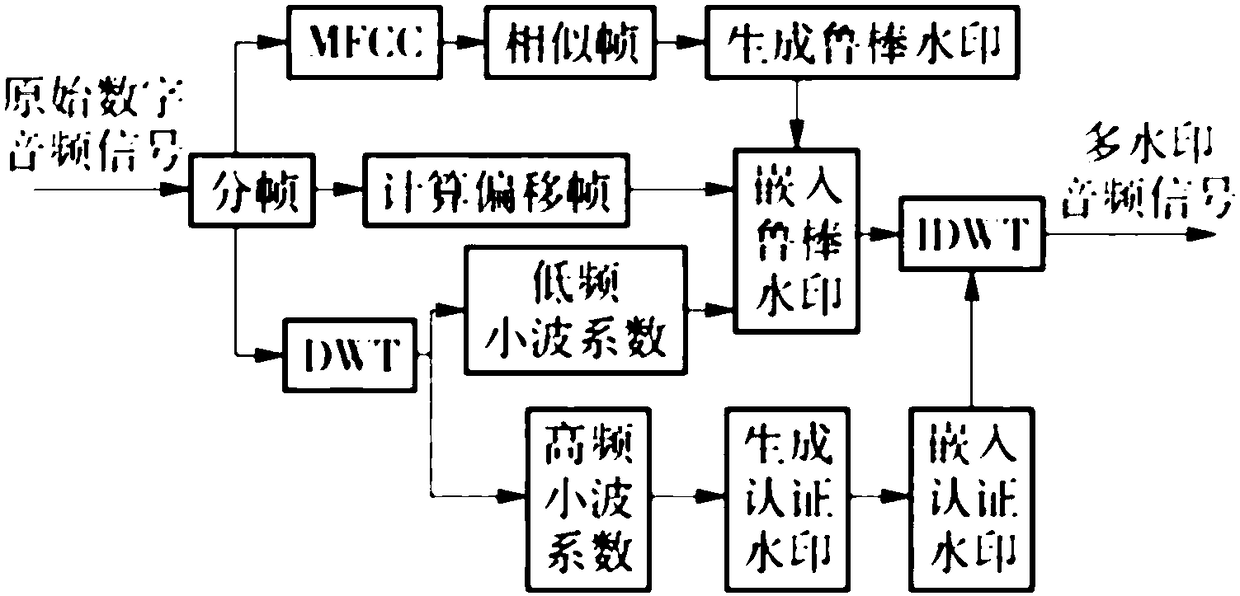
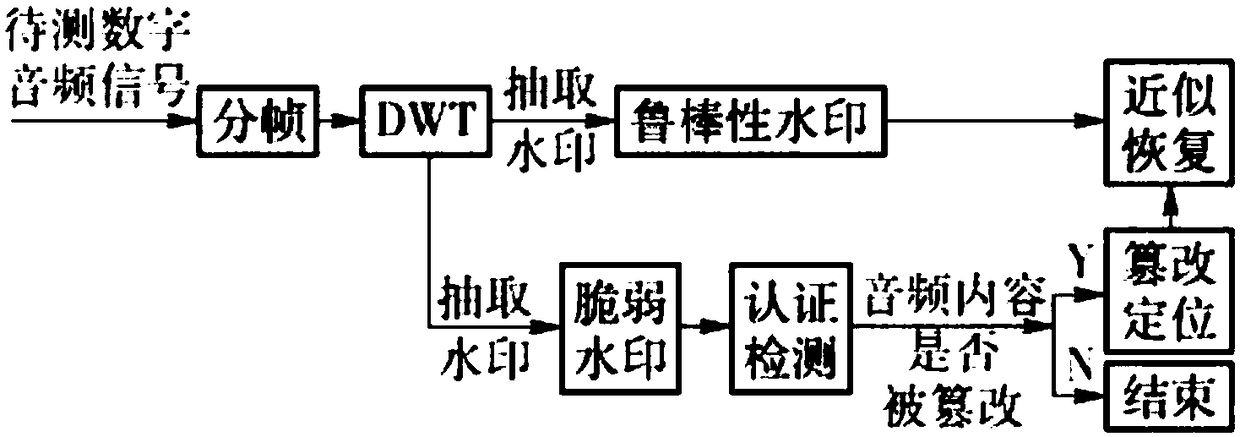
InactiveCN108198563AStrong resistance to attackPrecise location of tamperingSpeech analysisPattern recognitionSimilarity computing
The invention discloses a multifunctional audio protection method with digital copyright protection and content authentication. The method is characterized in that similarity computing is used on distance of MFCC characteristic coefficients of different audio frames to obtain a similar frame of each frame, then the similar frame is utilized to restore an audio frame subjected to tampering, and thespecific steps of calculating the similar frame are as follows: (1) framing is performed an original audio signal X with N points to obtain M frames of data F<1>, F<2>,..., F<M>; (2)MFCCf of eachframe is calculated, wherein i=1, 2,..., M; and (3) similarity S<ij>=VV<j>(||V||||V<j>||) between adjacent frames is calculated, 1<=i<=M, and 1<=j<=M, V and V<j> represent MFCC characteristicvectors corresponding to the ith frame and the jth frame, S<ij> is ranked from big to small, and Frame F<m> corresponding to a maximum distance d<m>(1<=m<=M) is determined to be the similar frame ofF. The method provided by the invention can achieve the purpose of positioning or restoring tampered audio.
Owner:ANHUI XINHUA MEDIA
Storage data integrity verification and recovery method
InactiveCN106611135AReduce overheadReduce storage overheadDigital data protectionRedundant operation error correctionRecovery methodData integrity
The invention provides a storage data integrity verification and recovery method. The storage data integrity verification and recovery method comprises the following steps of: firstly, partitioning information data, and generating data evidence; then, mapping the data evidence onto a server node, performing secondary pseudo-random placement of the data evidence, after verification applied by a user is passed, returning a stored data block and a corresponding evidence label to the user, and calculating and comparing the consistency of information through a private key and an evidence key, so that verification is realized; and, if data is attacked or tampered, when node failure in a system is detected, returning the position of an error node by the system, performing linear processing of a data block, which is smaller than a source file, according to secondary pseudo-random placement storage and a regeneration code, performing iterative operation of an effective node, and precisely recovering data. By means of the storage data integrity verification and recovery method provided by the invention, whether data is integrated, attacked and tampered or not can be checked by using a small amount of resources; due to secondary pseudo-random placement storage of the data, data can be recovered through undamaged data blocks; and furthermore, by means of the method, the storage overhead and the communication overhead are relatively low and high in anti-attacking property.
Owner:SICHUAN YONGLIAN INFORMATION TECH CO LTD
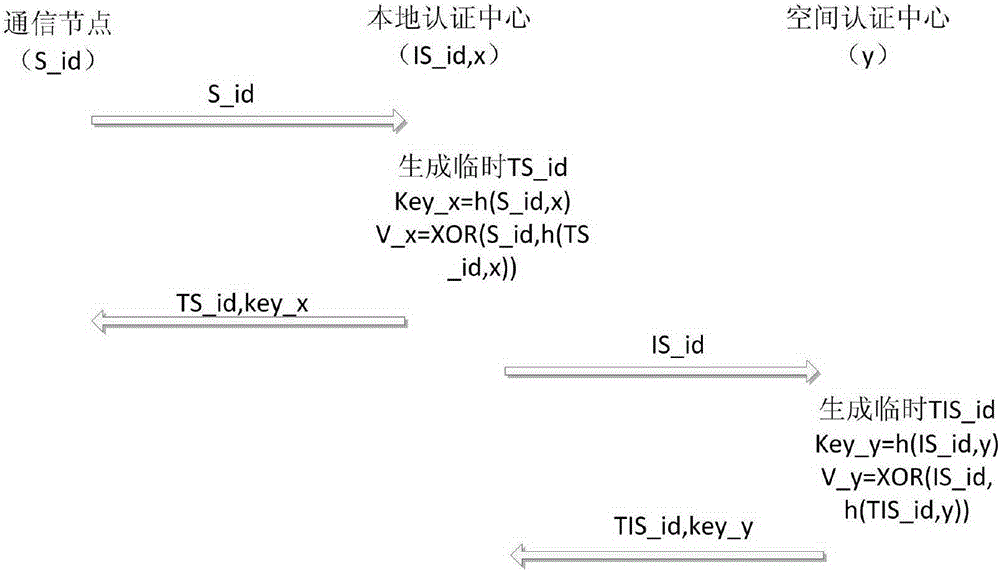
Space network cross-domain anonymous identity authentication method based on hyper-chaos encryption
ActiveCN105262593AStrong randomnessIncreased complexityUser identity/authority verificationQuantum cellular automatonInformation networks
The invention provides a space network cross-domain anonymous identity authentication method based on hyper-chaos encryption, relates to the technology of space information network, and solves the problem that the security mechanism applied in the conventional network cannot be directly applied to space network, and space cross-domain identity authentication cannot be realized. Provided is a space network cross-domain anonymous identity authentication method based on hyper-chaos encryption. The method includes two parts: a register stage and an authentication stage, a chaos algorithm is sensitive to initial conditions and control parameters, the structure is complex, prediction and analysis are difficult, and pseudo random sequences with good randomness and complexity are provided so that the chaos is applicable to encryption. A quantum cellular neural network is a cellular neural network structure coupling via quantum cellular neural network automata, complex linear dynamic features are obtained from the polarizability and quantum phase of each quantum cellular automaton, a nano-scale hyper-chaos oscillator can be constructed, the power consumption is low, the integration level is high, and the application requirement of space network satellite nodes can be better met.
Owner:CHANGCHUN UNIV OF SCI & TECH
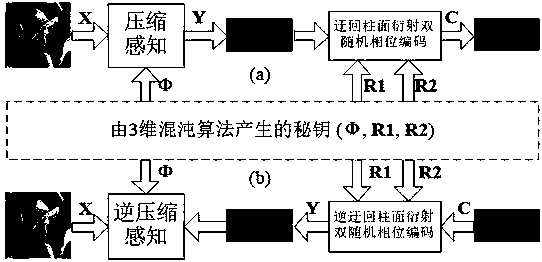
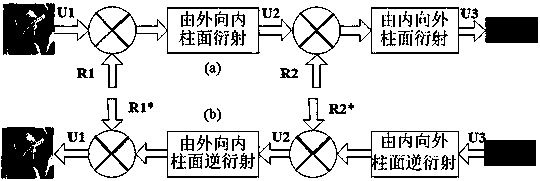
Optical image encryption method based on circuitous cylindrical diffraction and compressive sensing
ActiveCN108596989AStrong resistance to attackManyImage codingDigital data protectionComputer hardwareCiphertext-only attack
The invention provides an optical image encryption method based on circuitous cylindrical diffraction and compressive sensing. According to the method, a simple improvement on a classical first-compressive sensing and second-double random phase encoding encryption technique is performed, a cylindrical phase plate is used to replace a plane phase plate, and two reflection relay cylindrical diffraction processes are used to replace two continuous relay plane diffraction processes. By using the asymmetry between the two reflection relay cylindrical diffraction processes and a reverse process, thesecurity of the encryption method can be greatly improved, particularly, known plaintext attacks, ciphertext-only attacks and phase recovery attacks can be effectively resisted, keys are large in number and strong in sensitivity, a large key space can be realized, and good security can be ensured.
Owner:SICHUAN UNIV
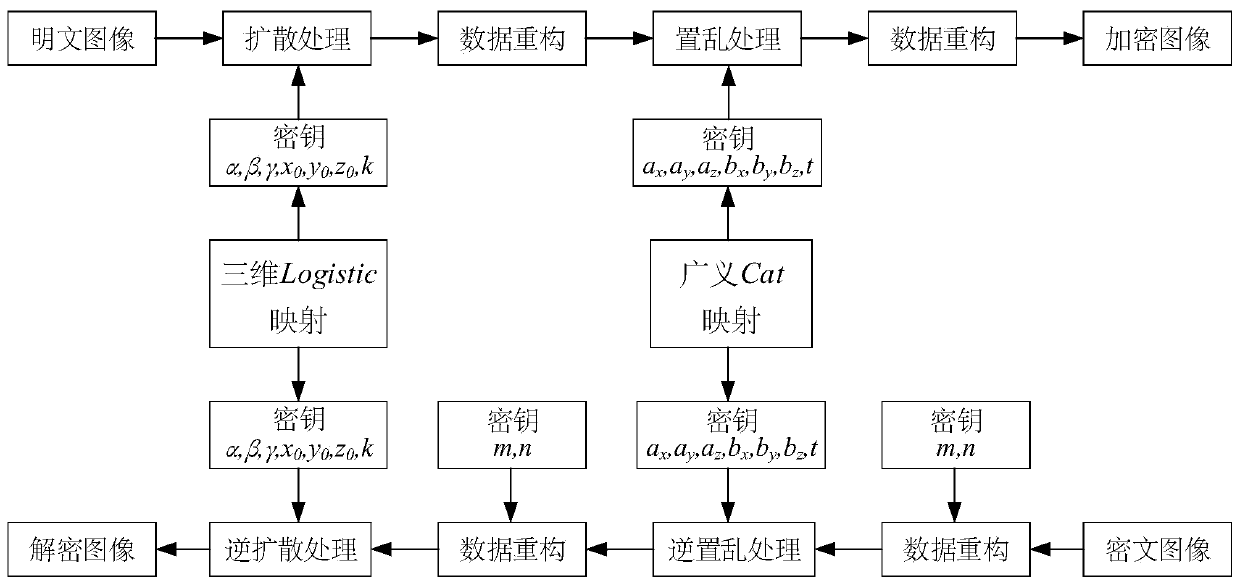
Color image encryption method based on three-dimensional Logistic mapping and generalized Cat mapping
The invention provides a color image encryption method based on three-dimensional Logistic mapping and generalized Cat mapping, which comprises the following steps: reading an original color image toobtain two-dimensional pixel matrixes corresponding to R, G and B components, and straightening the two-dimensional pixel matrixes to obtain three pixel sequences; three groups of chaotic sequences are generated through three-dimensional Logistic mapping iteration, and subjecting the three groups of chaotic sequences and the three pixel sequences to XOR operation to realize diffusion processing; carrying out data reconstruction on the chaotic sequence obtained after diffusion processing and expanding the chaotic sequence into a three-dimensional cube; performing position scrambling processingon the three-dimensional cube through generalized Cat mapping; and converting the three-dimensional cube with the scrambled position into a cuboid which is a ciphertext image. According to the method,parameters and initial values of three-dimensional Logistic mapping and generalized Cat mapping and the plaintext image size are used as keys, the key space is increased. Encryption safety is improved, and the method has the advantages of being high in key sensitivity, high in anti-attack capability and the like.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Digital watermark encryption realization method
InactiveCN103020496ALarge key spaceIncreased sensitivityImage data processing detailsProgram/content distribution protectionChaos theoryPredictability
The invention provides a digital watermark encryption realization method. On the basis of the research of a digital watermark embedding algorithm in a wavelet domain, the chaos theory is introduced into the establishment of the digital watermark; the algorithm that a chaos sequence which is generated by Logistic mapping is embedded into a wavelet domain digital watermark is proposed and realized; and the algorithm has the characteristics of secret key uniqueness, irreversibility, invisibility and robustness according to the specific unpredictability of the chaos sequence. An experiment proves that the algorithm has a good visual effect and is a practical and feasible digital watermark encryption algorithm.
Owner:王少夫
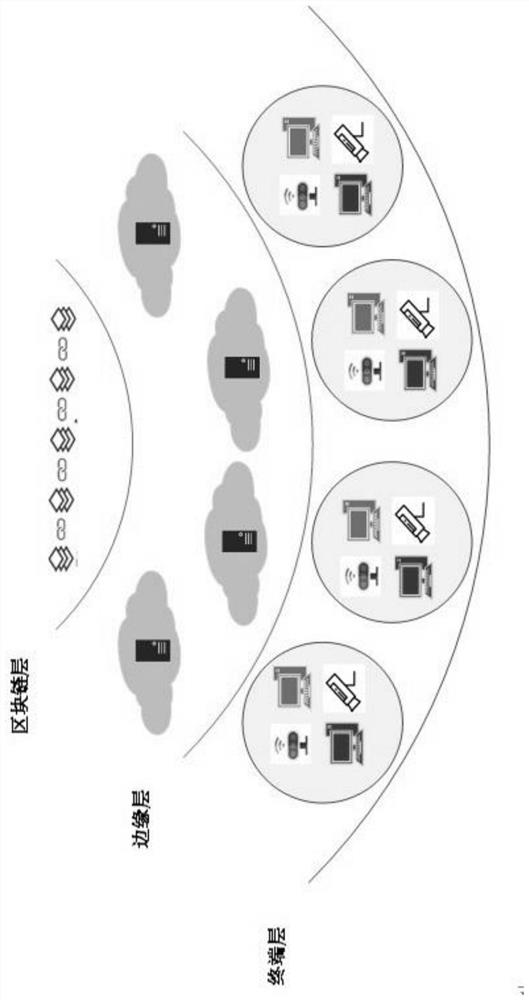
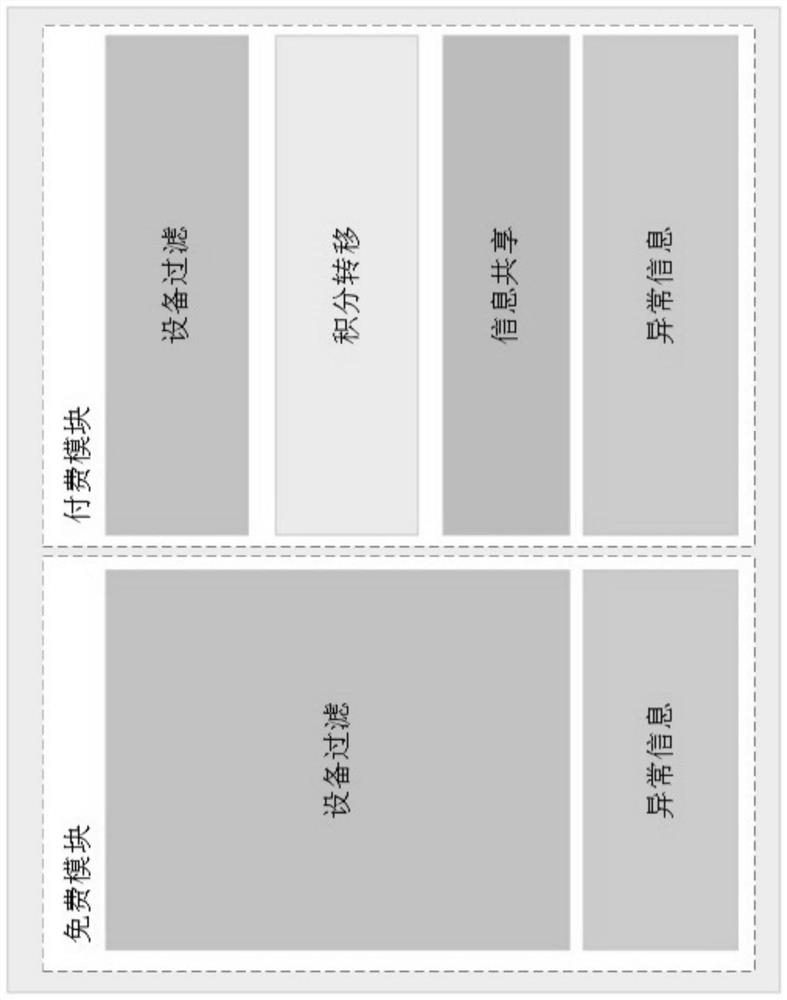
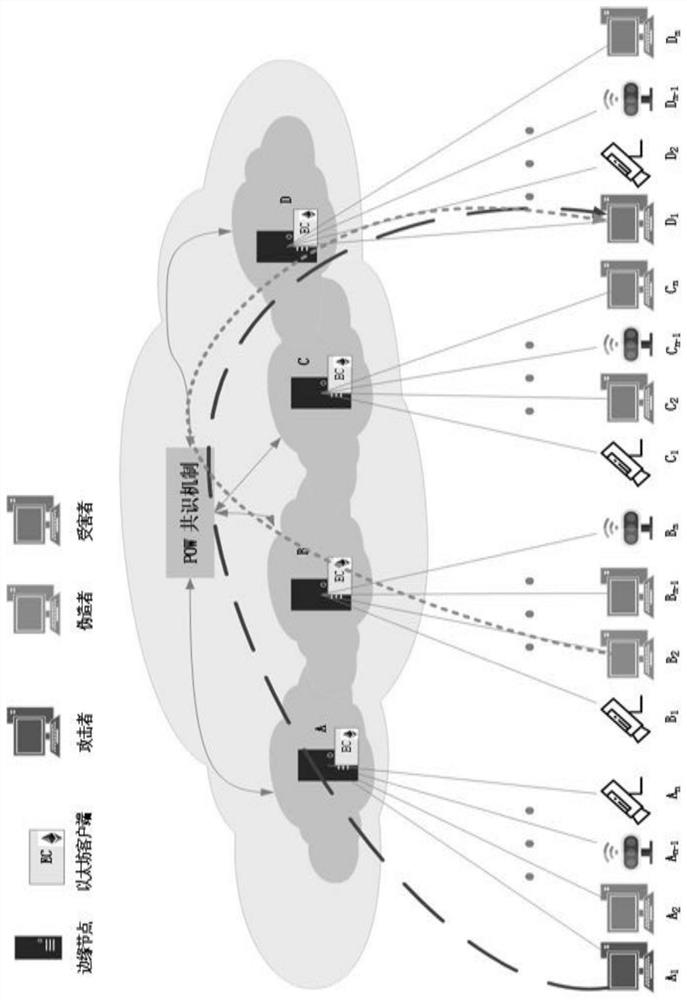
DDoS attack joint defense system and method based on blockchain
ActiveCN112491823AEliminate the risk of a single point of attackSimplify information sharing methodsTransmissionInformation sharingAttack
The invention discloses a DDoS attack joint defense system and method based on blockchain, belongs to the technical field of DDoS attack defense, and aims to solve the technical problem of how to defend DDoS attacks safely, quickly and effectively. The system comprises at least one terminal device; at least one piece of edge equipment which is provided with an Ethereum client; a blockchain which is provided with a device information sharing smart contract and a device filtering smart contract, wherein the blockchain is used for realizing information sharing among the edge nodes based on a blockchain consensus mechanism, and the edge equipment is used for carrying out DDoS anomaly detection to obtain DDoS anomaly traffic information, storing the DDoS anomaly traffic information through local data, and uploading the DDoS anomaly traffic information to the blockchain based on the device information sharing smart contract.
Owner:QILU UNIV OF TECH
Optical image encryption method based on quantum cell nerve network hyperchaotic system
InactiveCN104092530AMake up linear featuresHighly integratedKey distribution for secure communicationQuantum cellular automatonNerve network
The invention relates to the technical field of information security, and discloses an optical image encryption method based on a quantum cell nerve network hyperchaotic system, for solving the defect of insufficient non-linear degree of a conventional optical encryption system. According to the invention, an optical image is encrypted and decrypted by use of the quantum cell nerve network hyperchaotic system, due to the hyperchaonic characteristic of a quantum cell nerve network, the linearity characteristic of a conventional double-random phase coding optical encryption technology is made up for, and the optical image encryption method has the security characteristics of large secret key space and high anti-attack capability. Besides, since a quantum dot and a quantum cell automatic machine are novel nanometer-level electronic devices which transmit information through coulomb interaction, compared to the prior art, the quantum cell automatic machine has the advantages of super-high integration, super-low power consumption, lead-free integration and the like.
Owner:CHANGCHUN UNIV OF SCI & TECH
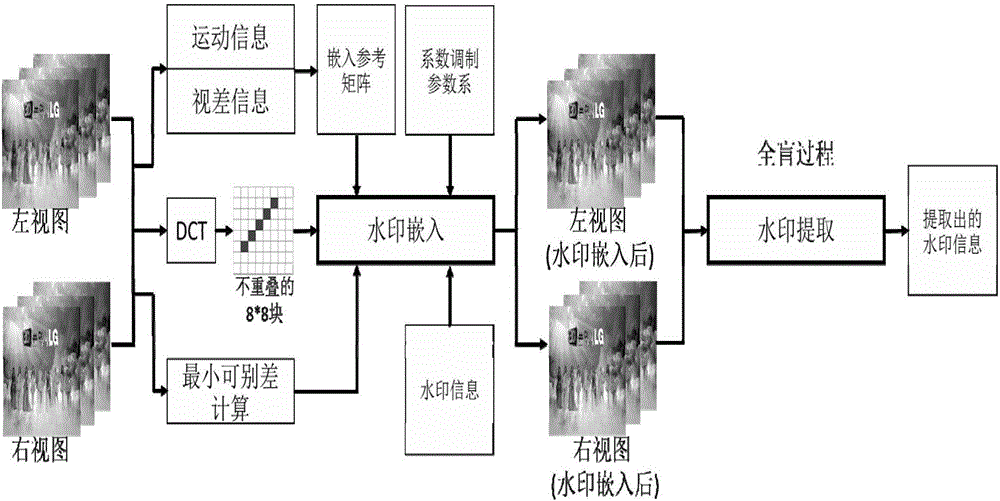
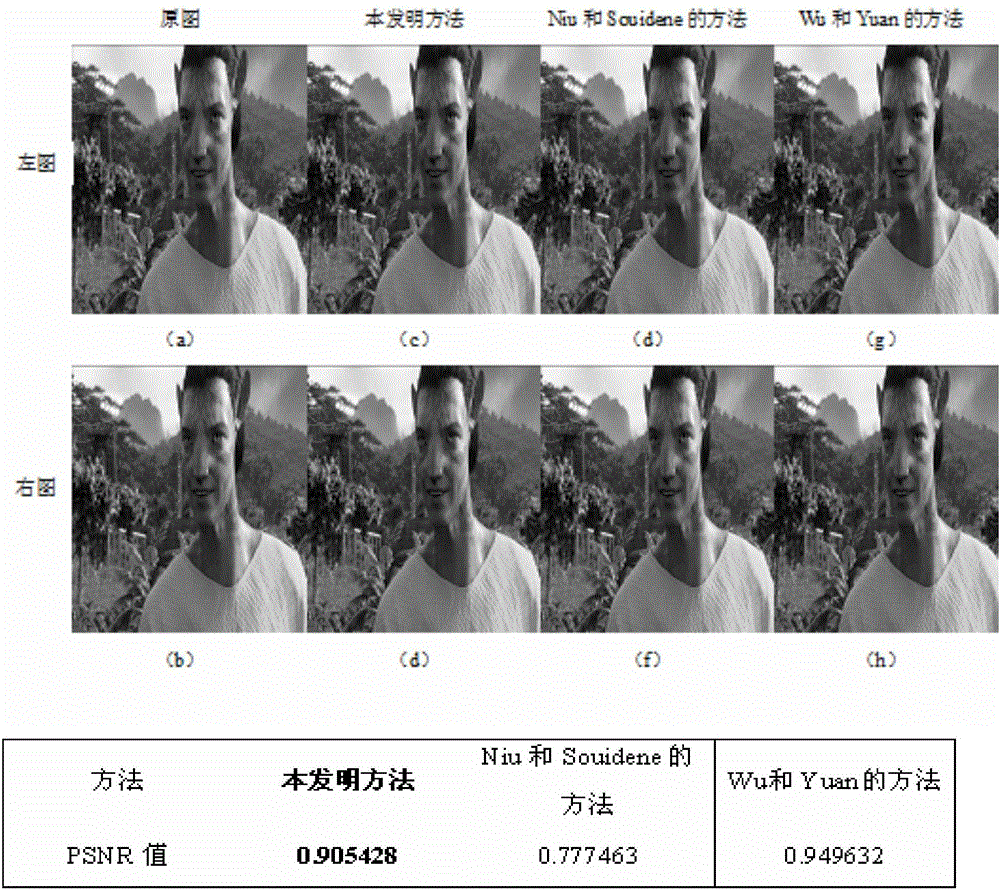
Robust hidden watermark embedding and extracting method for 3D high definition digital videos
ActiveCN106131711AReduce complexityEasy extractionDigital video signal modificationSelective content distributionHigh definitionDct coefficient
The invention provides a robust hidden watermark embedding and extracting method for 3D high definition digital videos, and belongs to the crossing field of image processing, etc. A user inputs a segment of 3D video, and an algorithm divides the 3D video into sequence frames according to a frame rate thereof and carries out an embedding operation on each frame in the sequence frames. On each frame, the algorithm separately carries out DCT conversion on left and right views with 8 * 8 pixel blocks a unit at first. Each bit in a watermark is sequentially embedded on a pair of 8 * 8 DCT coefficient blocks at the same positions in the left and right channel views. A watermark algorithm selects intermediate frequency areas in the DCT coefficient blocks for embedding and introduces three coefficient limit mechanisms to effectively limit the embedding strength, which are respectively a least identifiable difference perception model, a fine grain modulation parameter and an embedding reference matrix. According to the robust hidden watermark embedding and extracting method provided by the invention, the overall complexity is simplified on the theoretical foundation of the study of the watermarking technology based on single channel video, intensive tasks can be processed and calculated in parallel, the processing speed of the high definition 3D videos is accelerated, and the imperceptibility and the robustness are guaranteed on the premise of achieving the above effects.
Owner:BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com