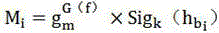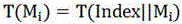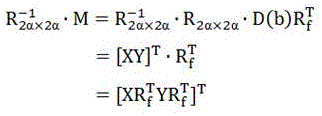Storage data integrity verification and recovery method
A technology of integrity verification and recovery method, which is applied in the field of data integrity verification, can solve problems such as reducing user data reading performance, and achieve the effect of low storage and communication overhead and strong attack resistance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the object, technical solution and advantages of the present invention more clear, the following will describe in detail in conjunction with the algorithm flow chart.
[0020] 1. Basic idea of algorithm
[0021] First, the information is divided into data blocks according to the minimum storage scheme of the regeneration code, and then the data blocks are hashed (MD5 algorithm, the hash described later is not specified, and the MD5 rule is used for all) to generate data evidence; then the data The evidence is mapped to the storage server node using a pseudo-random storage algorithm, and the data evidence is pseudo-randomly placed twice and saved in two ciphertext data blocks; the user saves the private key and the evidence key, and when receiving the user authentication request, first Verify the user's authority, and then return the stored data block and the corresponding evidence tag to the user, and calculate the consistency of the comparison inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com