Method and system for file transparent encryption and decryption of Android platform
A transparent encryption and decryption, file technology, applied in the field of information security, can solve the problems such as permissions cannot protect specific directories, system integration is low and vulnerable, and cannot protect SD card files, etc., to enhance encryption and decryption efficiency, and reduce user operation interference. , the effect of enhancing system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
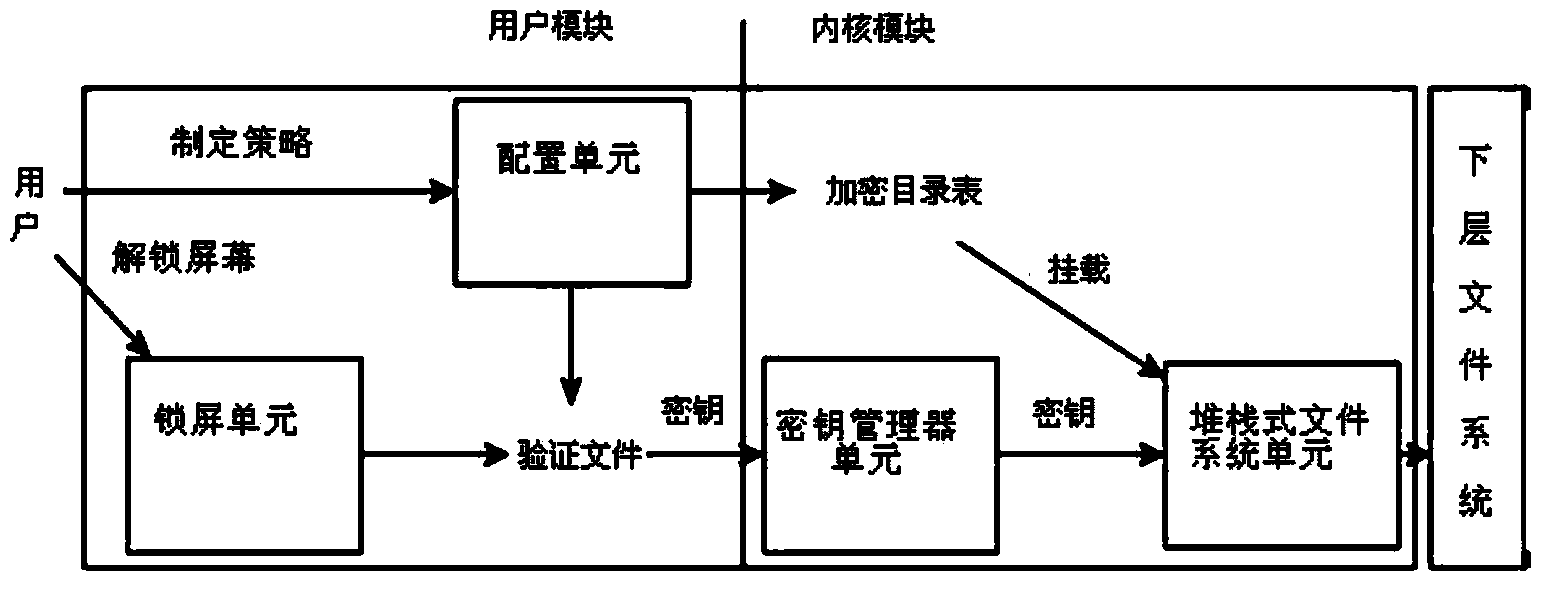
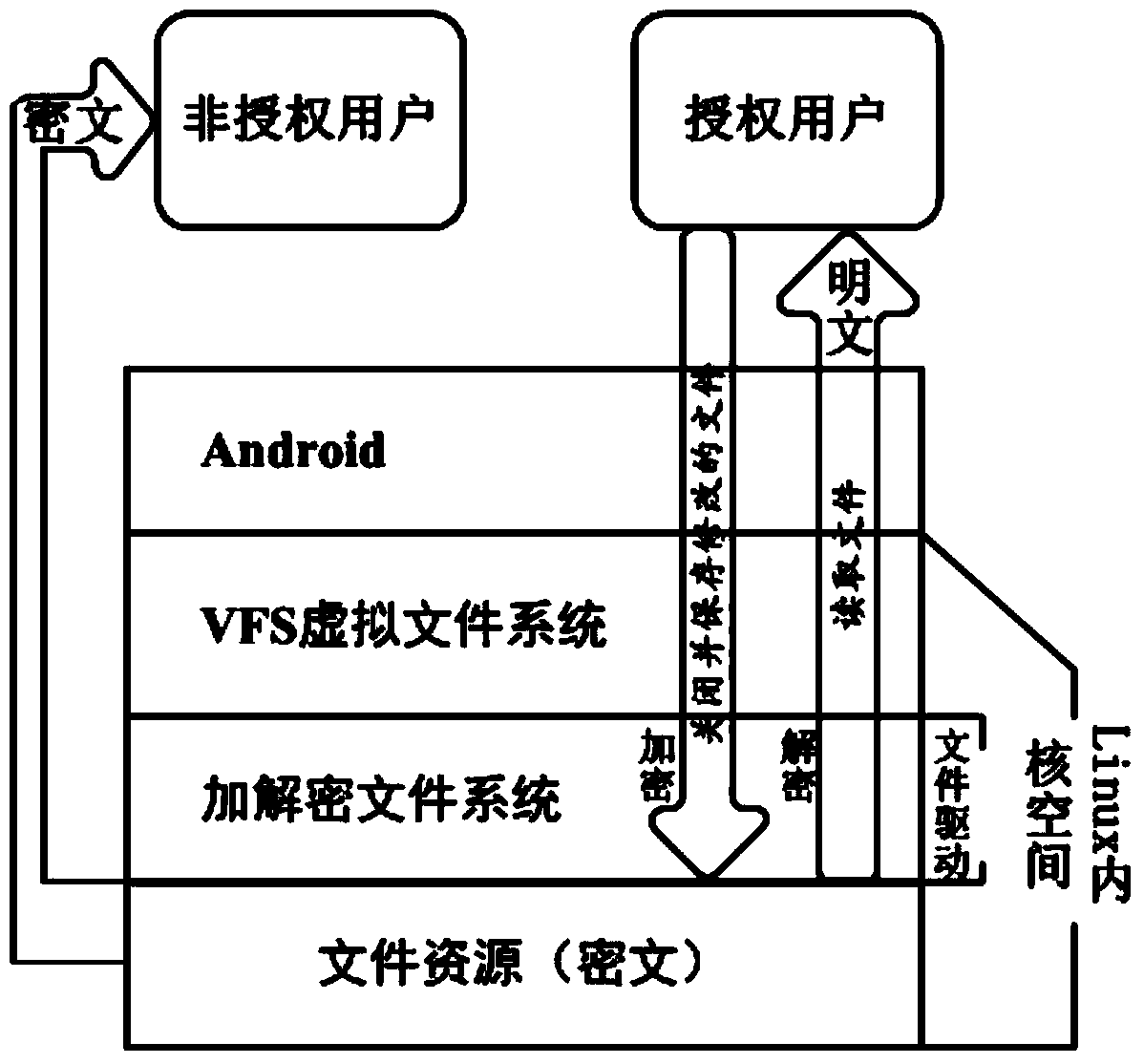
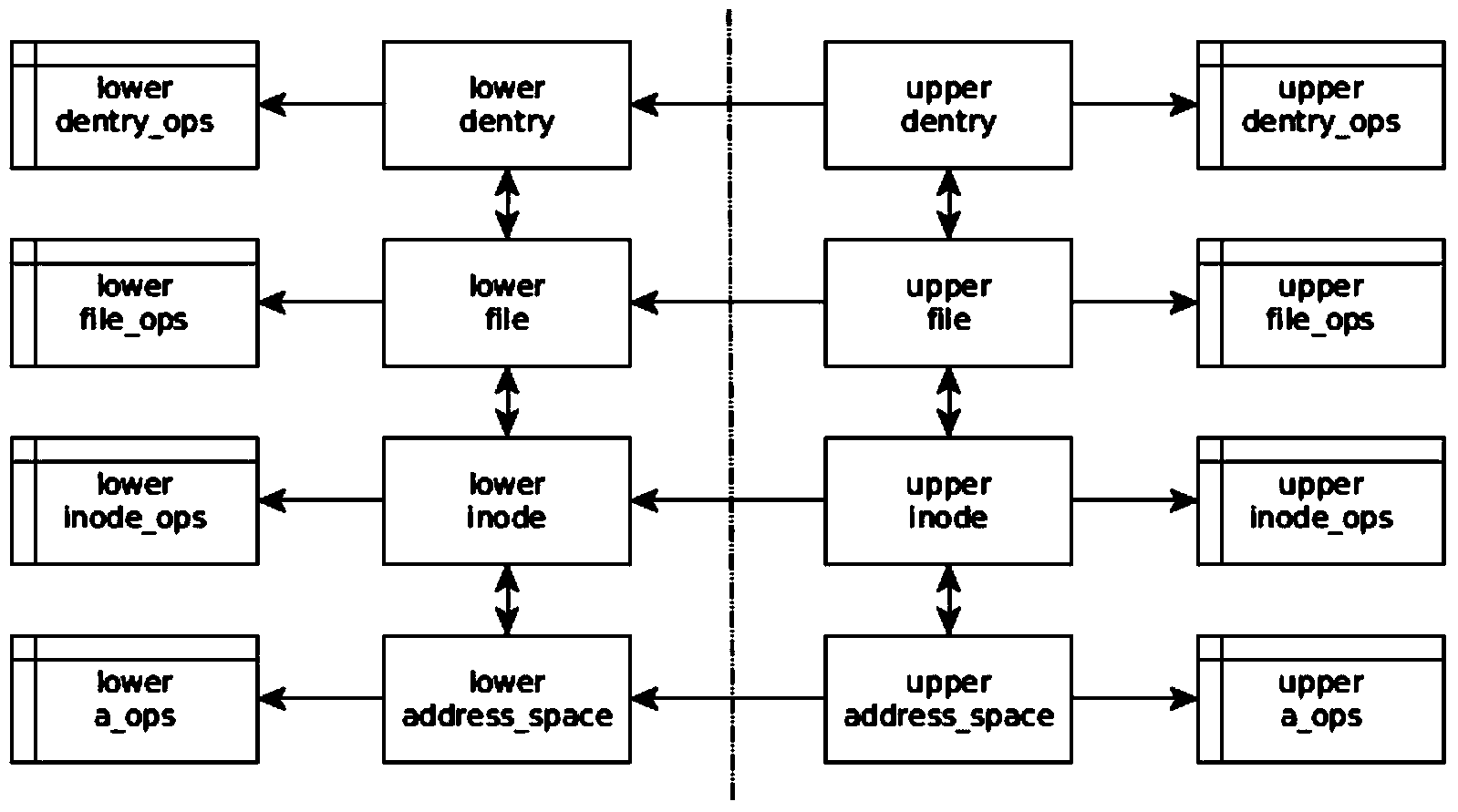
[0029] A method for transparent encryption and decryption of files on an Android platform, comprising the following steps:
[0030] Step 1. Select the path of the folder where the file to be protected is located and set a password;
[0031] Step 2, according to the path and password input by the user, respectively generate an encrypted path directory table and an identity verification file;
[0032] Step 3. Scan the encryption path directory table. If the operating system is started for the first time, the protected file will be initialized and encrypted for the first time according to the table item, and then proceed to the next step;
[0033] Step 4. When the user triggers the unlock screen event, accept the passphrase entered by the user, perform a hash algorithm on the passphrase and compare it with the authentication file generated in step 2:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com