Key protecting method and system in Android environment
A key protection and key technology, which is applied in the field of information security, can solve the problems that permissions cannot protect specific directories, SD card files cannot be protected, and security protection is not comprehensive, so as to achieve enhanced encryption and decryption efficiency, less user operation interference, Ease of deployment and migration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
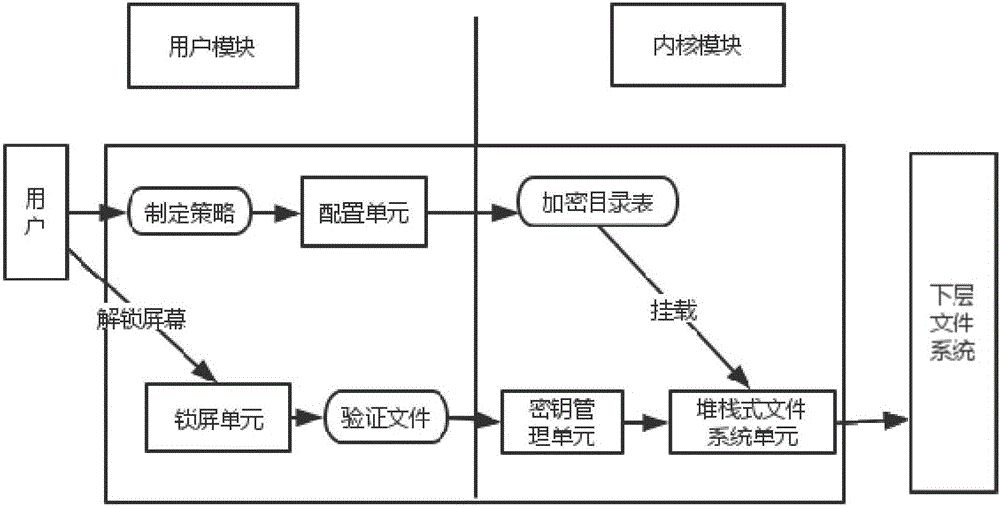
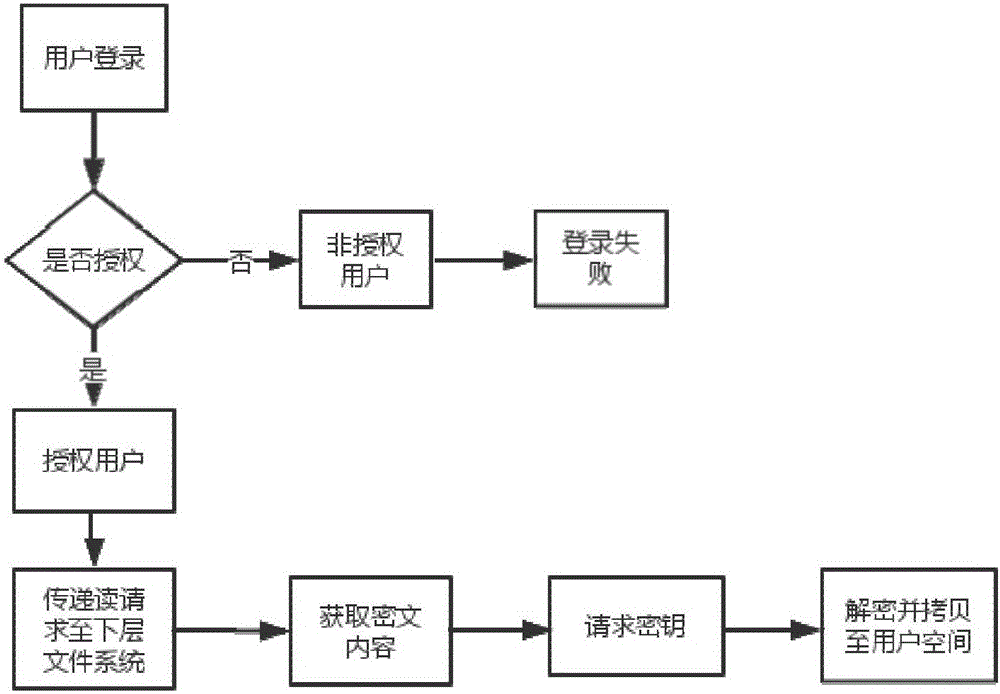
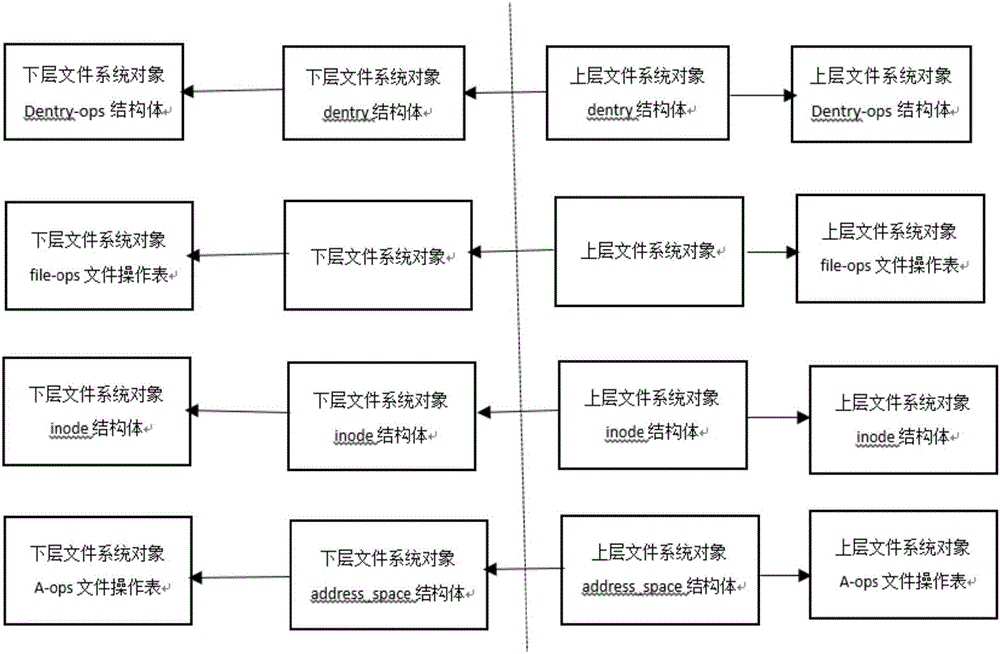
[0043] The present invention provides a key protection method and system in an Android environment, which is implemented by using a stacked file system; the stacked file system is an incremental development mode used to expand the functions of the original key system. This method does not need to modify the code of the original key system, but overwrites it, filters operations such as reading and writing, and adds set processing methods in the process, such as encryption and compression (including white-box encryption algorithm), to enhance the original key system. Has the function of the key system. The present invention adopts the combined lock interface to reduce the impact on user operations as much as possible, closely combines the operating system itself, and realizes key protection that is blo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com