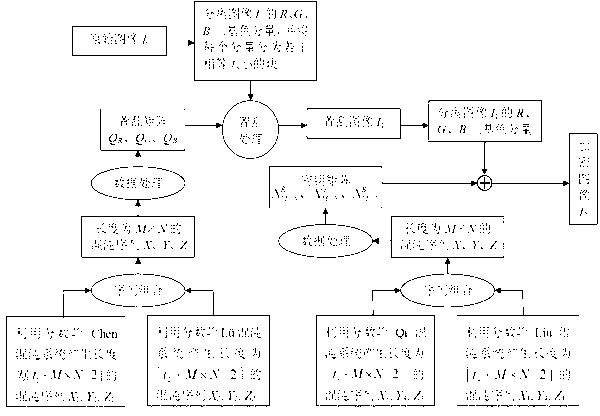
Color image encryption and decryption method based on multiple-fractional-order chaotic systems
A chaotic system and encryption method technology, applied in the field of color image encryption and decryption, can solve the problems of failure of fractional order chaotic system, inability to estimate the fractional order of fractional order chaotic system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0103] Example 1: Assumption It is a matrix with 5 rows and 5 columns as follows:
[0104]
[0105]
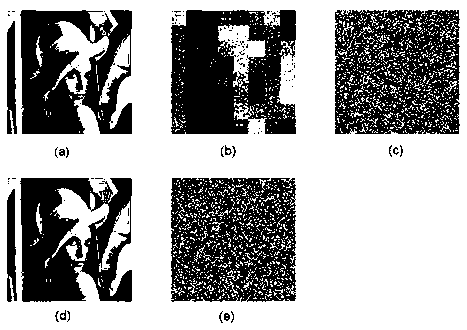
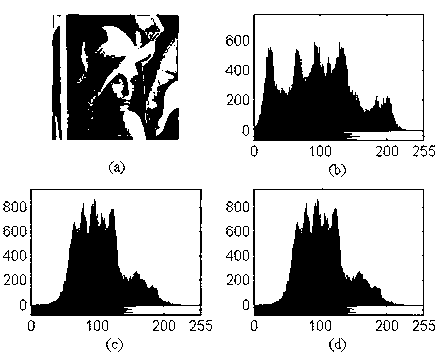
[0106] 3. Using the generated scrambling matrix , with to the original image Scramble block by block to get a scrambled image , see attached figure 2 (b). The program code to realize image scrambling is as follows:
[0107] %% for the original image I 0 Each component of is scrambled block by block %%
[0108] I1_R_block_scrambling = uint8(zeros(32, 32, 64));
[0109] I1_G_block_scrambling = uint8(zeros(32, 32, 64));
[0110] I1_B_block_scrambling = uint8(zeros(32, 32, 64));
[0111] Temp_R_scrambling = uint8(zeros(32, 32));
[0112] Temp_G_scrambling = uint8(zeros(32, 32));
[0113] Temp_B_scrambling = uint8(zeros(32, 32));
[0114] for i = 1 : 64
[0115] Temp_R = I0_R_block( : , : , i);
[0116] Temp_G = I0_G_block( : , : , i);
[0117] Temp_B = I0_B_block( : , : , i);
[0118] for j = 1 : 1024
[0119] Temp_R_scram...
example 2
[0162] Example 2: Assume a sequence of length 16 . Will The data in is rearranged in descending order, giving . Will Replace the position number of each element in The corresponding elements in the sequence can be obtained . Will Each element in is modulo 4 to get the sequence . will sequence Further converted to a 4×4 matrix ,Right now
[0163] .
[0164] 6. Using the key matrix , with Change the scrambled image of each pixel RGB value, to get the encrypted image , see attached figure 2 (c). change scrambled image Each pixel RGB The specific method of the value is: will scramble the image The three primary color component matrix of , with The elements in are respectively related to the key matrix , with Elements in are XORed one by one, that is, , , ,in , .
[0165] For the above encrypted image The method for image decryption is:
[0166] The image decryption process is similar to the encryption process, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com