Color image encrypting method based on multi-chaos system
A color image, encryption method technology, applied in image data processing, image data processing, instruments, etc., can solve problems such as difficulty in resisting known plaintext attacks, and achieve strong anti-attack ability, high key sensitivity, and key space. big effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
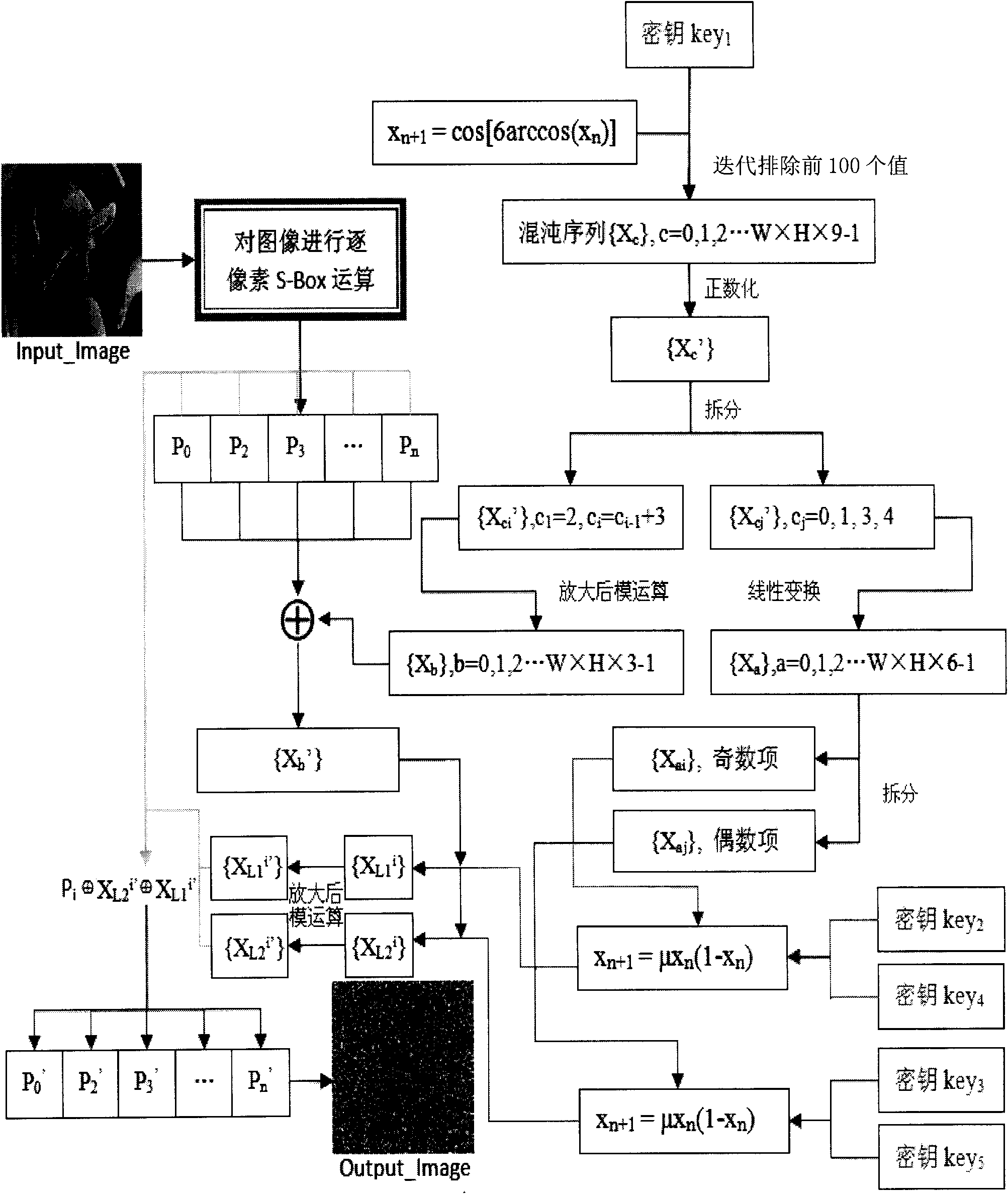
[0029] The present invention will be further described now in conjunction with accompanying drawing:
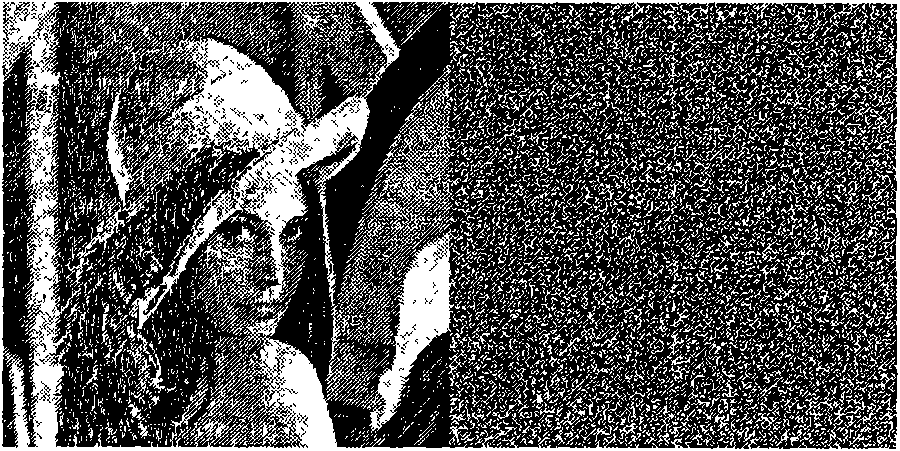
[0030] Digital image Input_image, with M W×H Indicates that w is the width of the image, h is the height of the image, both in pixels, and w×h=n. A pixel P of an image consists of three 8-bit values. The value key of the double type used below 1 key 5 provided by the user.
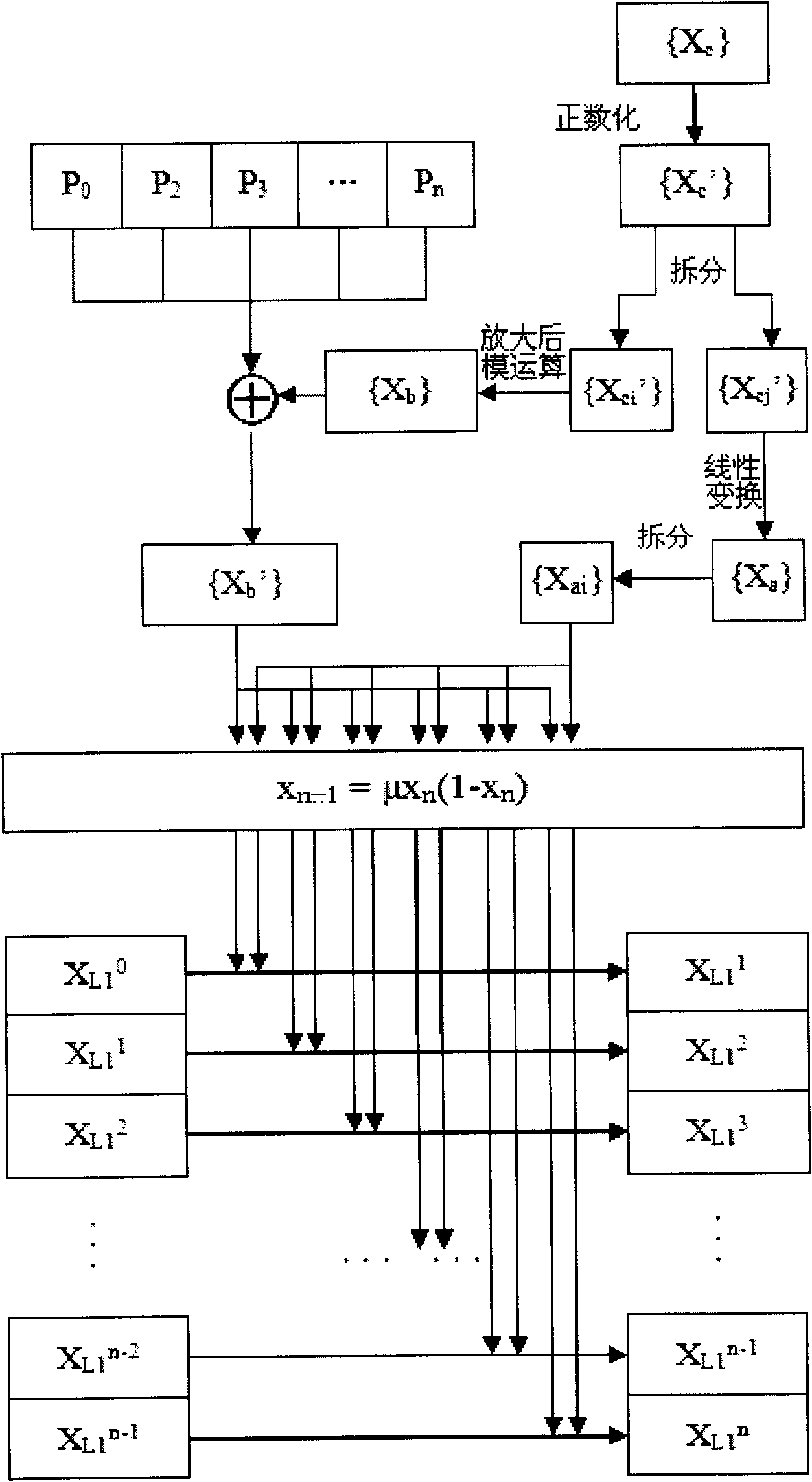
[0031] The specific encryption process is as follows (seefigure 1 , of which steps 7-9 can be referred to at the same time figure 2 ):
[0032] 1. Record the gray value of each pixel of the image Input_image as a two-dimensional matrix P (x,y) , the P (x,y) Perform S box transformation and convert the transformation result into a one-dimensional pixel array P (h×x+y) , namely P 0 , P 1 , P 2 , P 3 ,…P n , denoted as sequence {P i}.
[0033] 2. Use the key key 1 Iterate as the initial value of the Chebychev map, exclude the first 100 values, and take the sequence {X c}, where X c ∈(-1, 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com