Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
A SHA-384, space-time chaos technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of less periodic orbits and small periods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
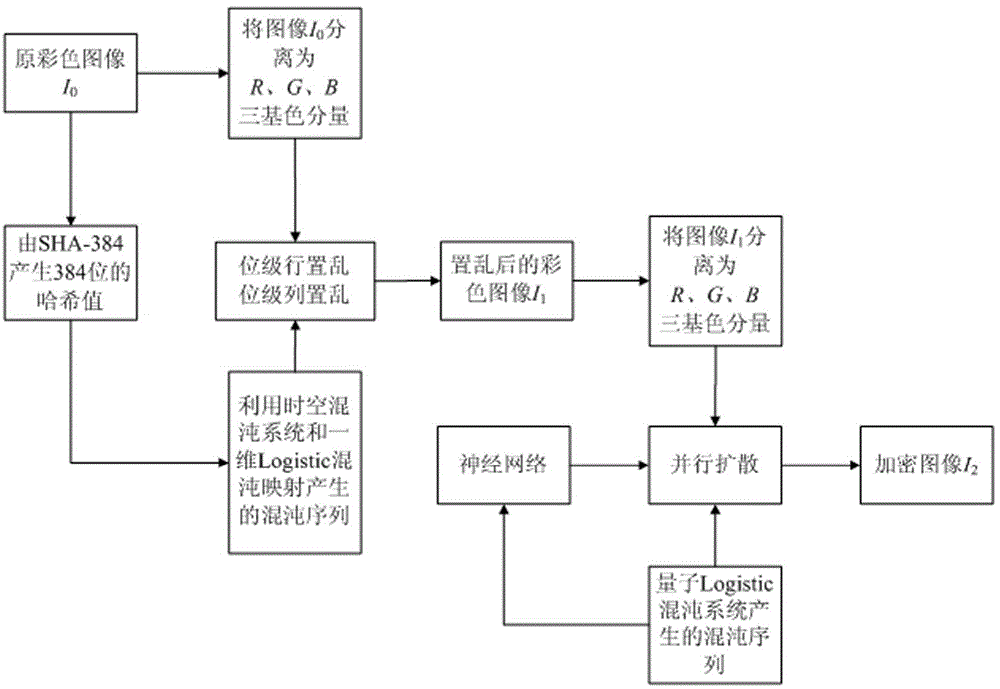
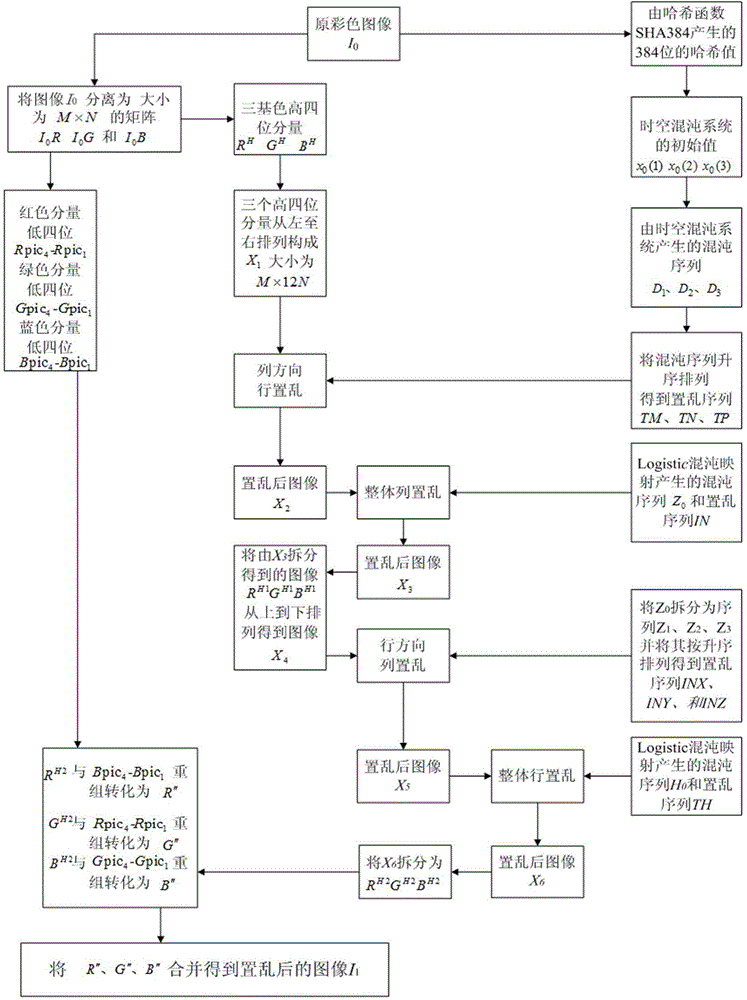
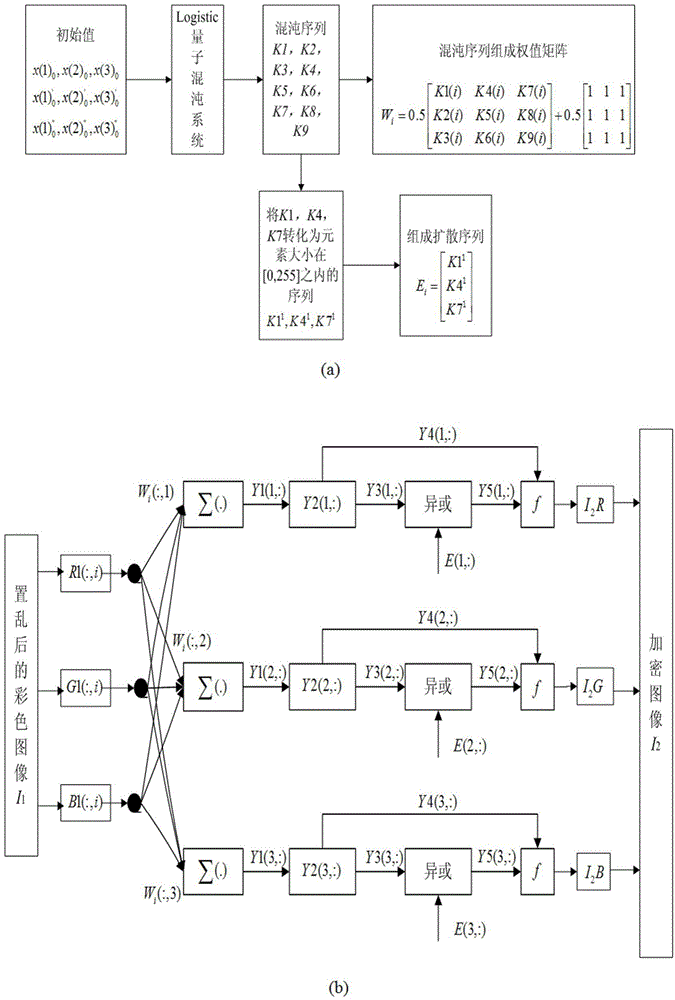
[0078] Embodiment 1: in the present embodiment, the programming software that adopts is Matlab R2009a, selects Figure 4 The LenaRGB standard color image with a size of 512×512 shown in (a) is the experimental object. The specific process of encrypting the LenaRGB color image is as follows:
[0079] 1. Input the original LenaRGB color image, use I 0 =imread('LenaRGB.bmp') reads the image information, and uses the SHA-384 function to process the original color image I 0 Perform calculations to obtain a set of 384-bit hash values as keys, and convert the 384-bit hash values from binary to hexadecimal to obtain 96 hexadecimal numbers, namely B5E9C5E D D3B C800F62C F A894A A B F A D17B29B5D B C7089315438D26728A607F41F7 2B70A7D1133F62B A E427C C E78097029. Divide the hash value into 3 groups on average, each group has 32 hexadecimal numbers, convert each group of elements into decimal numbers, and calculate the sum of each group of elements Sum(j), where j=1,2,3 , calculate ...
Embodiment 2
[0170] Embodiment 2: in the present embodiment, the programming software that adopts is Matlab R2009a, selects the attached Figure 8 The Fruits color image with a size of 480×512 shown in (a) is the experimental object, and the process of encrypting the color image is as follows:
[0171] 1. The input image size is the original color image I of 480×512 0 , with I 0 =imread('Fruits.bmp') read image information. Using the SHA-384 function to the original color image I 0 Perform calculations to obtain a set of 384-bit hash values as keys, convert the 384-bit hash values from binary to hexadecimal, and obtain 96 hexadecimal numbers, namely B C86B B7315F58B6575C E85C C55B3983635F0B B41D0A66088F B4D F9D D8B67D F49E F83B9381441B8B8218E3D A34E D A7677. Divide the hash value into 3 groups on average, each group has 32 hexadecimal numbers, convert each group of elements into decimal numbers, and calculate the sum of each group of elements Sum(j) (j=1,2,3) , calculate x by the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com