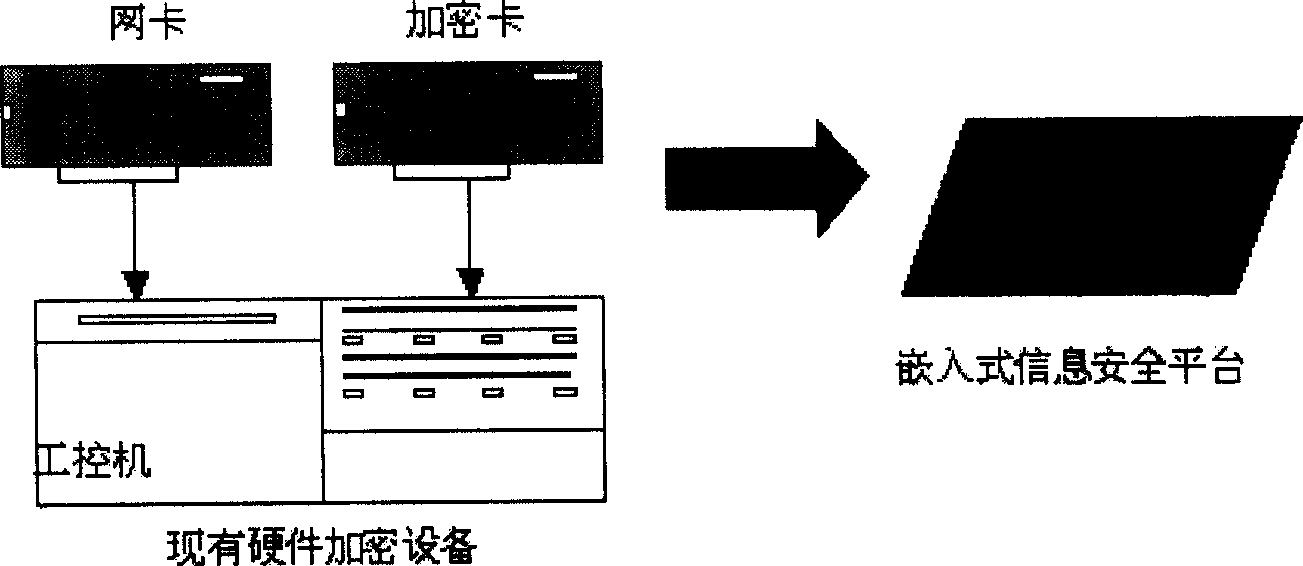
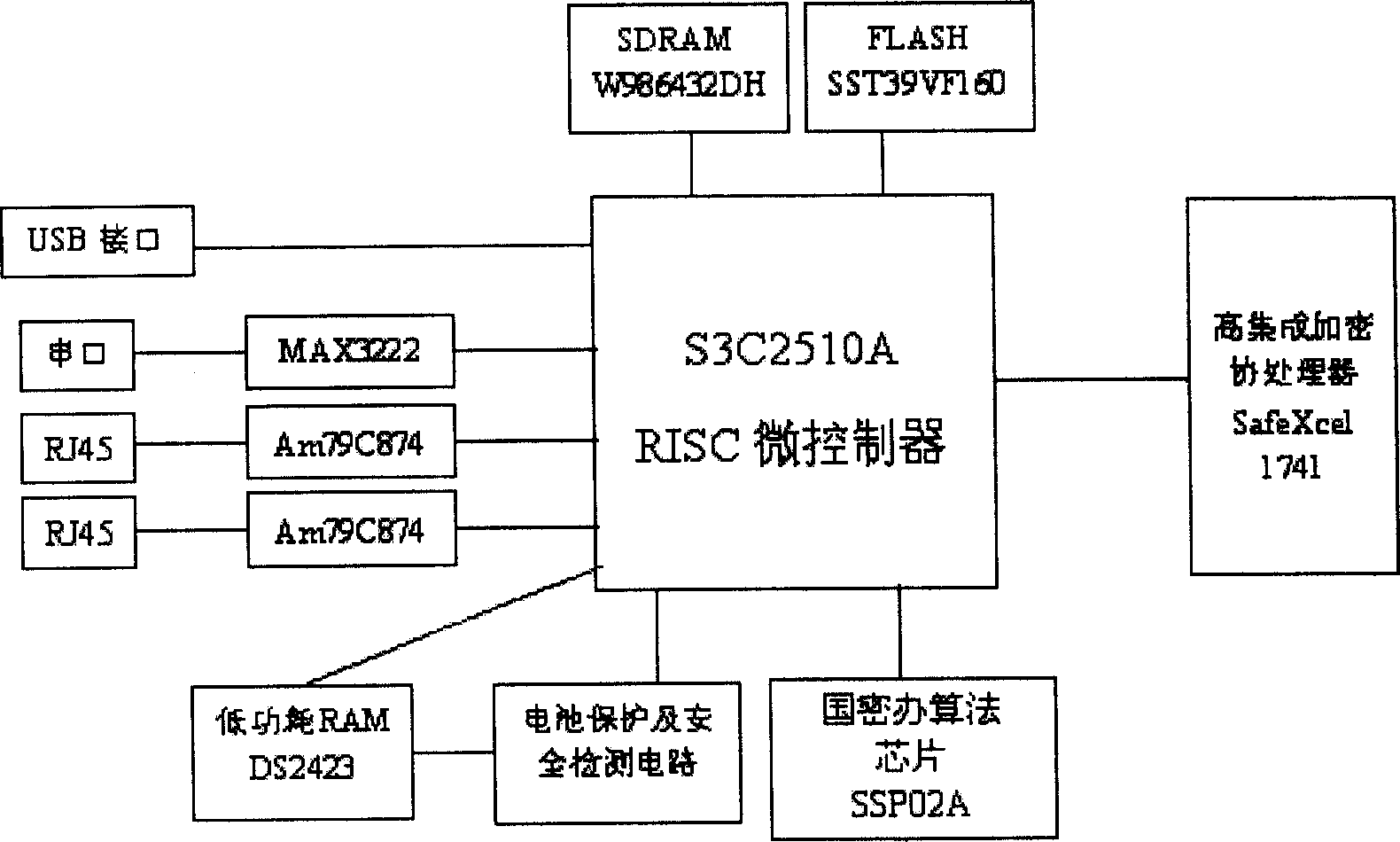
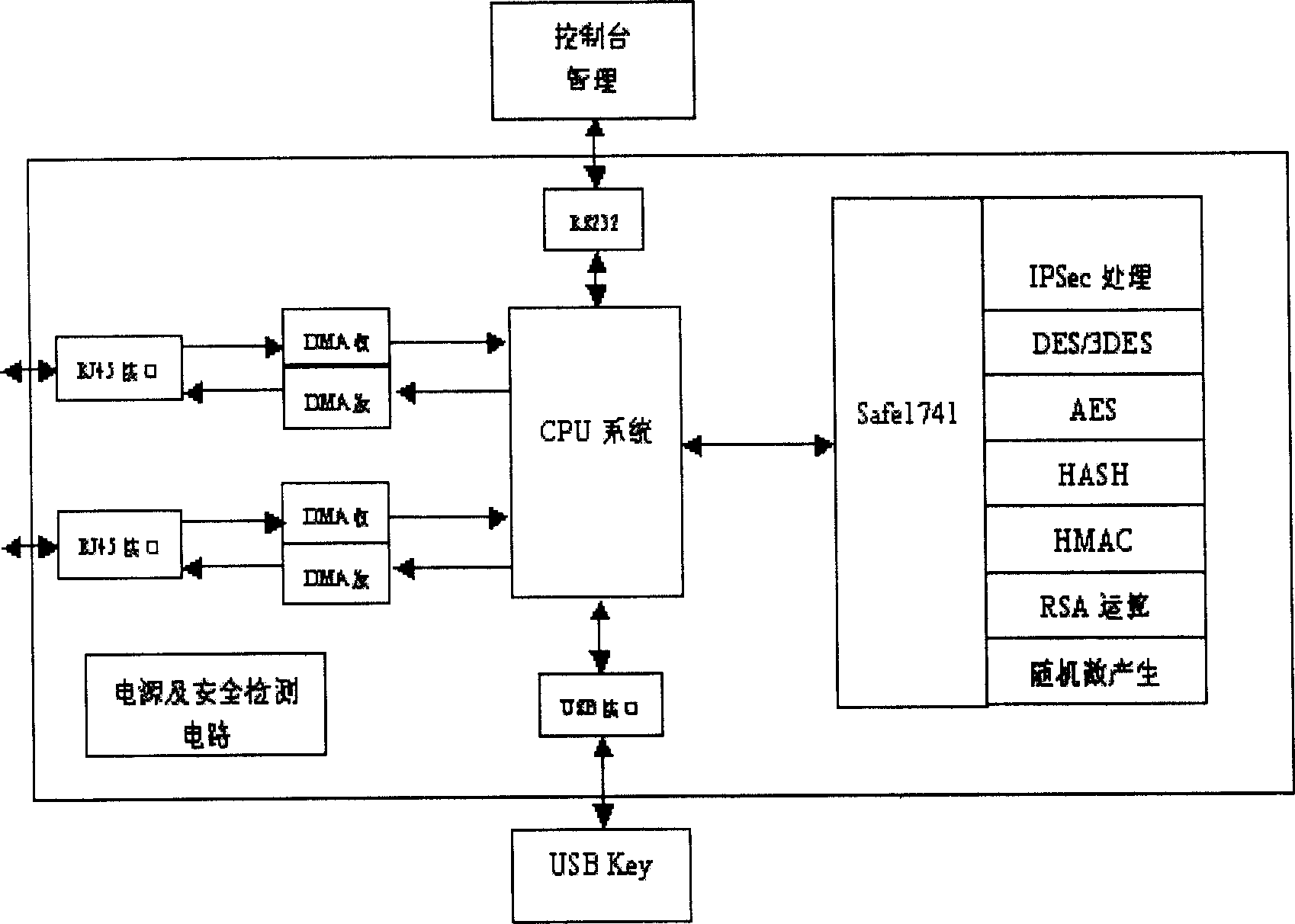
An embedded information security platform
An information security and embedded technology, applied in the field of communication, can solve the problems of unfavorable middle and low-end user promotion, low scalability, high hardware cost, etc., and achieve the effect of strong anti-attack ability, wide applicability and high versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Embodiments of the present invention are described in detail in conjunction with the accompanying drawings.
[0019] Depend on figure 2 As shown, an embedded information security platform is composed of a CPU microcontroller, an encryption and decryption hardware chip, an input and output interface, a power conversion circuit, and a security protection circuit. It is characterized in that the CPU microcontroller is a network processing Chip, select S3C2510A in the present embodiment, on-chip processor is ARM940T core, and an embedded real-time operating system is placed in this core; Encryption and decryption hardware chip is made up of IPSec algorithm chip, symmetric algorithm chip as cryptographic algorithm coprocessor, IPSec algorithm chip is such as figure 2 The one shown above is the highly integrated encryption and decryption coprocessor SafeXcel1741, and the symmetric algorithm chip is the algorithm chip SSP02A of the State Secret Office; the input and output ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com