Method for protecting track privacy by forwarding inquiries based on neighboring nodes in location service
A privacy protection and location service technology, applied in the field of trajectory privacy protection based on neighbor node forwarding query, can solve the problem of not fully protecting user trajectory location privacy, and achieves protection of location privacy and trajectory privacy, strong anti-attack ability, and easy implementation. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
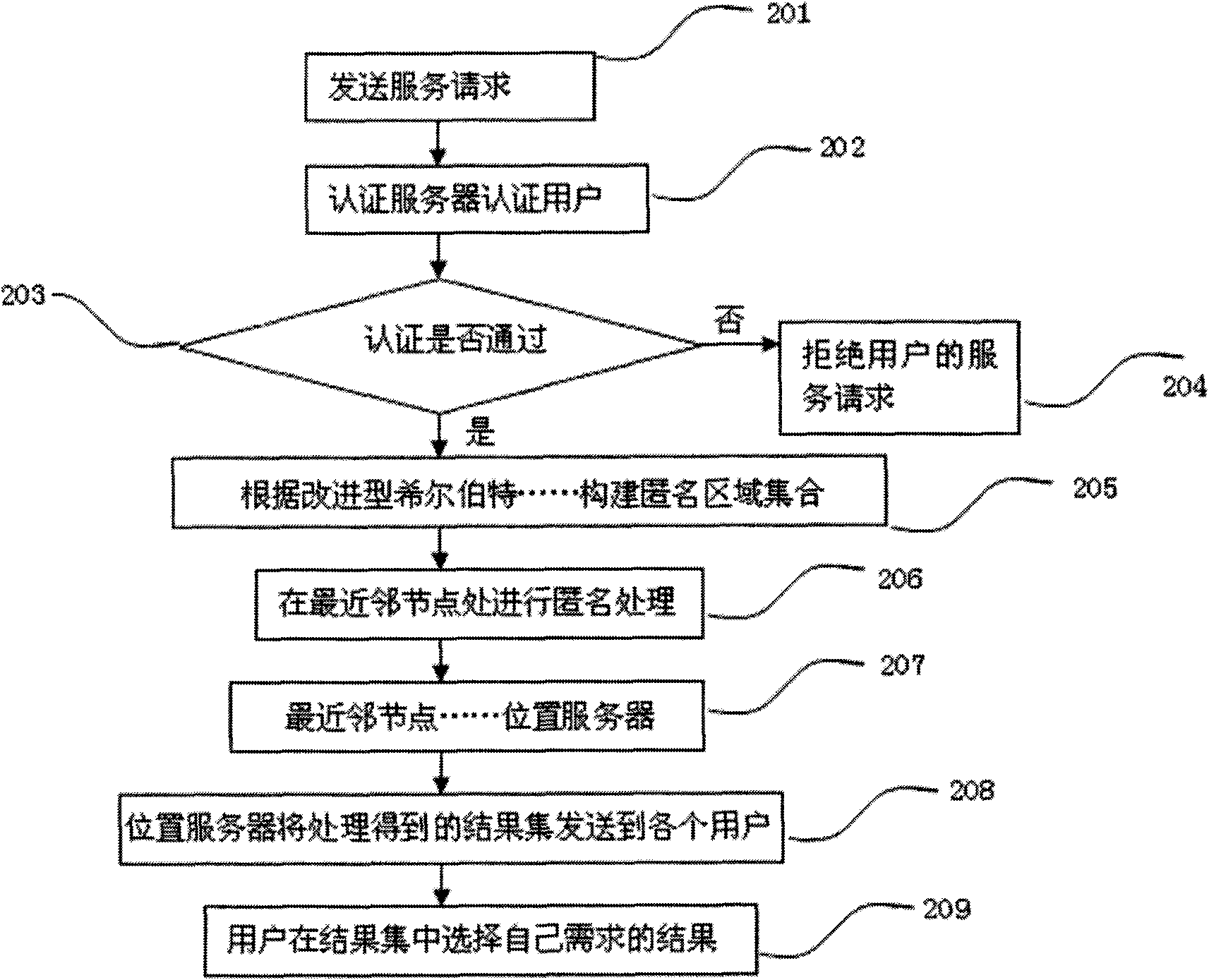
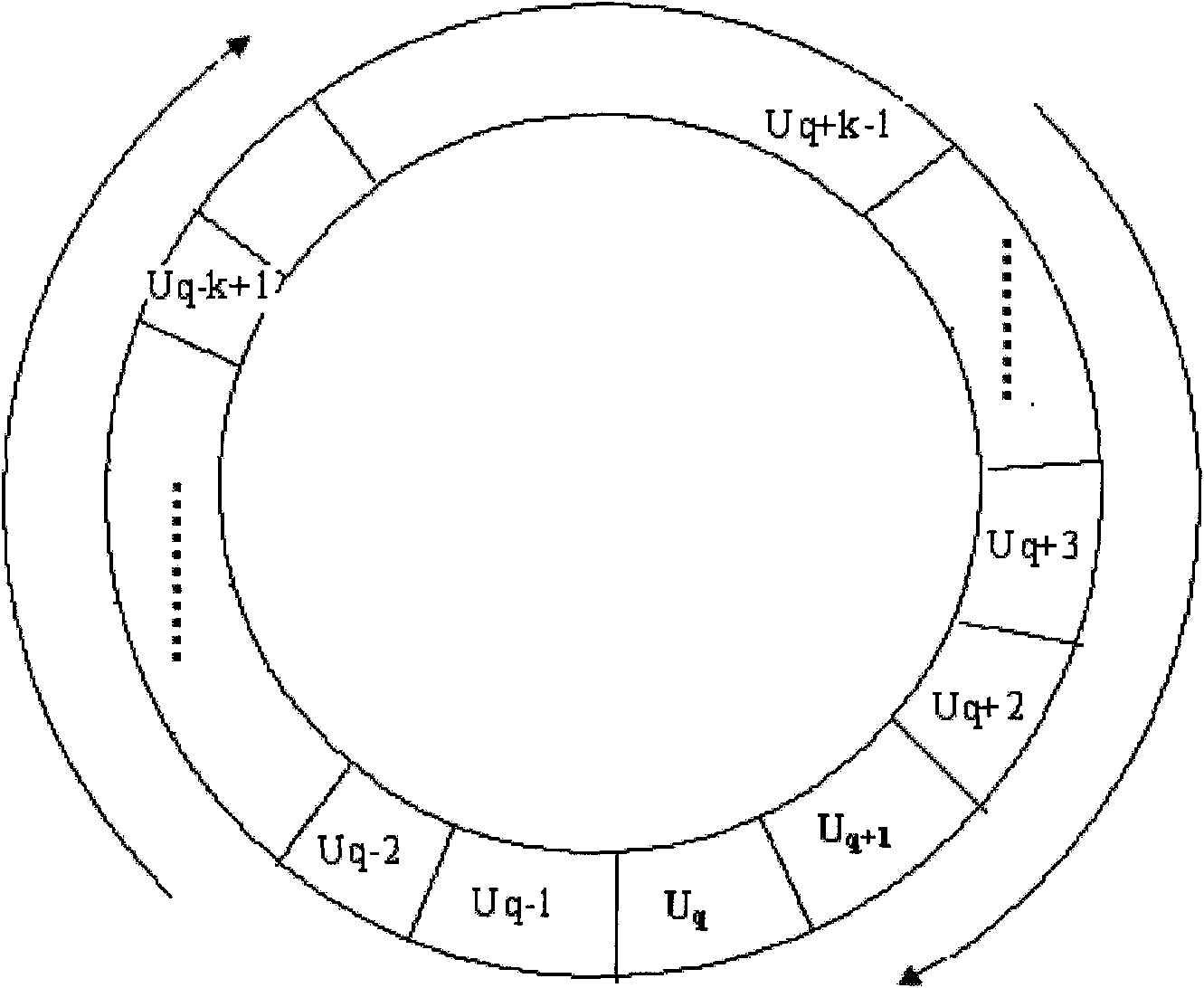
[0032] Below in conjunction with accompanying drawing and embodiment describe in detail:
[0033] 1. Trajectory privacy protection system based on neighbor node forwarding query (referred to as this system)
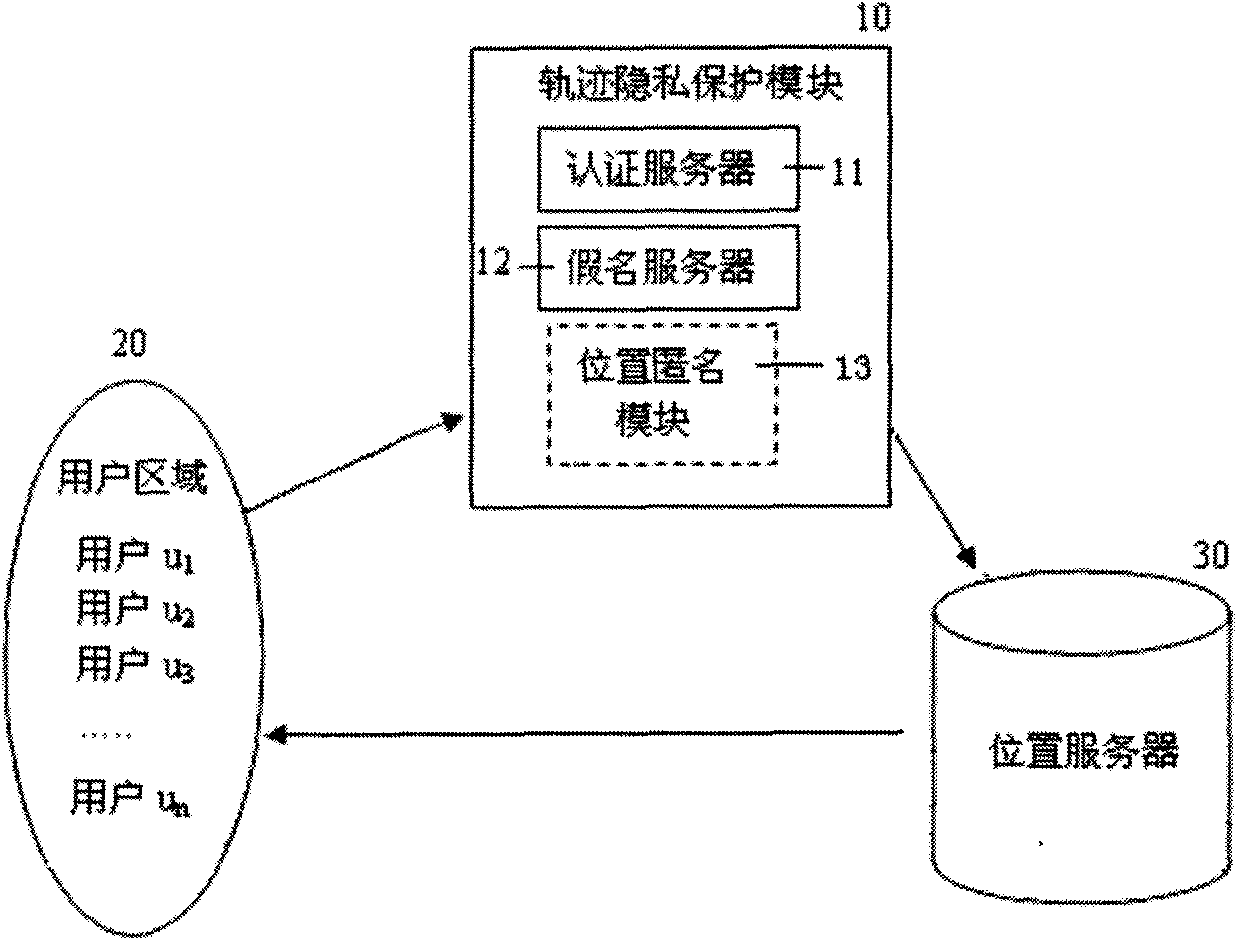
[0034] Such as figure 1 , the system includes a user area 20 and a location server 30, and is provided with a trajectory privacy protection module 10; the user area 20, the trajectory privacy protection module 10 and the location server 30 are connected in sequence;
[0035] Described trajectory privacy protection module 10 comprises authentication server 11, pseudonym server 12 and position anonymous module 13; Its interactive relation is:
[0036] The authentication server 11 verifies the credibility and legitimacy of its identity to the user who makes the request, and ensures that the user who is responsible for forwarding the request can find a credible neighbor node;
[0037] Pseudonym server 12 distributes a pseudonym for each credible user, and user's service req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com