Patents
Literature
152results about How to "Ensure effective implementation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
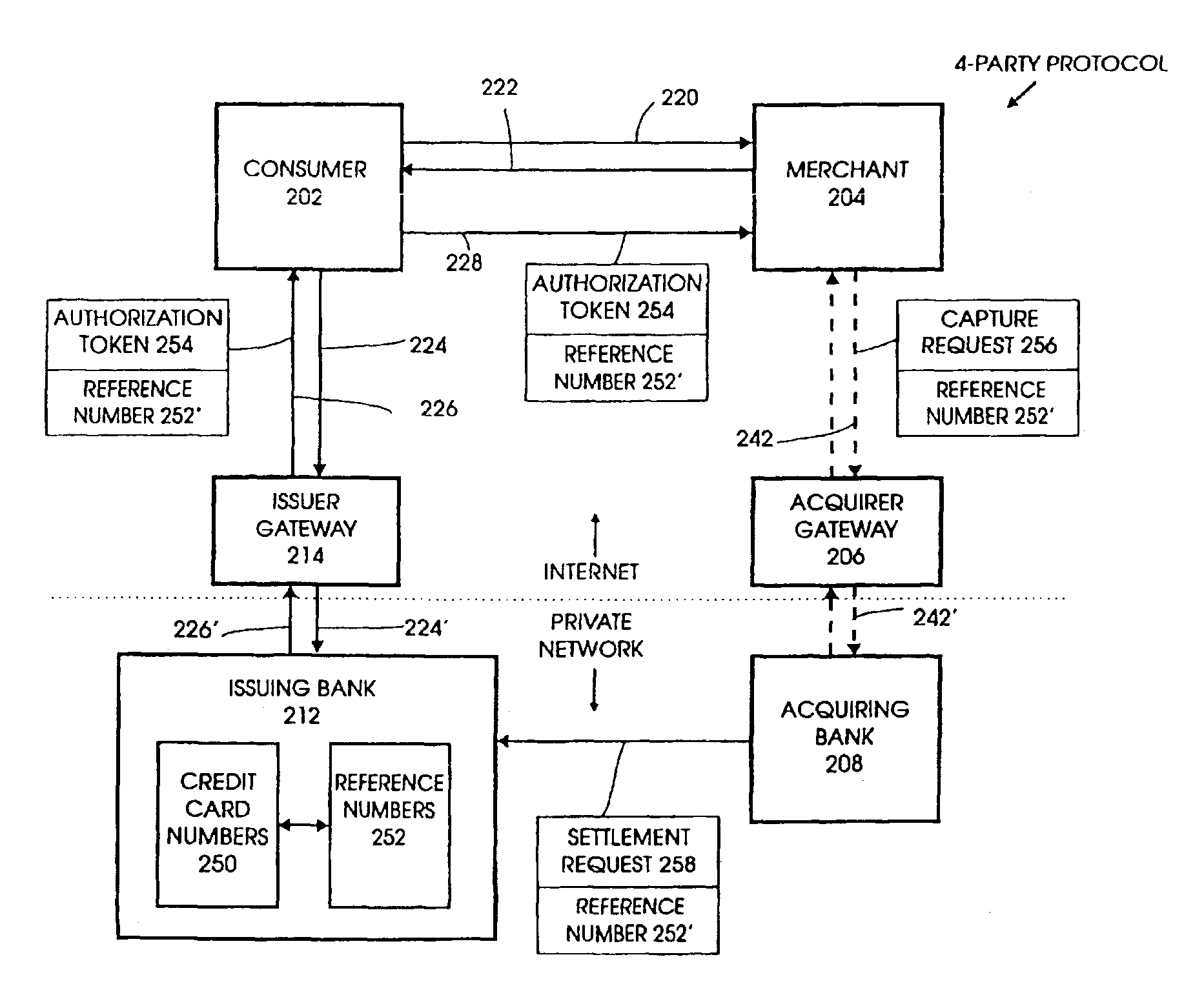
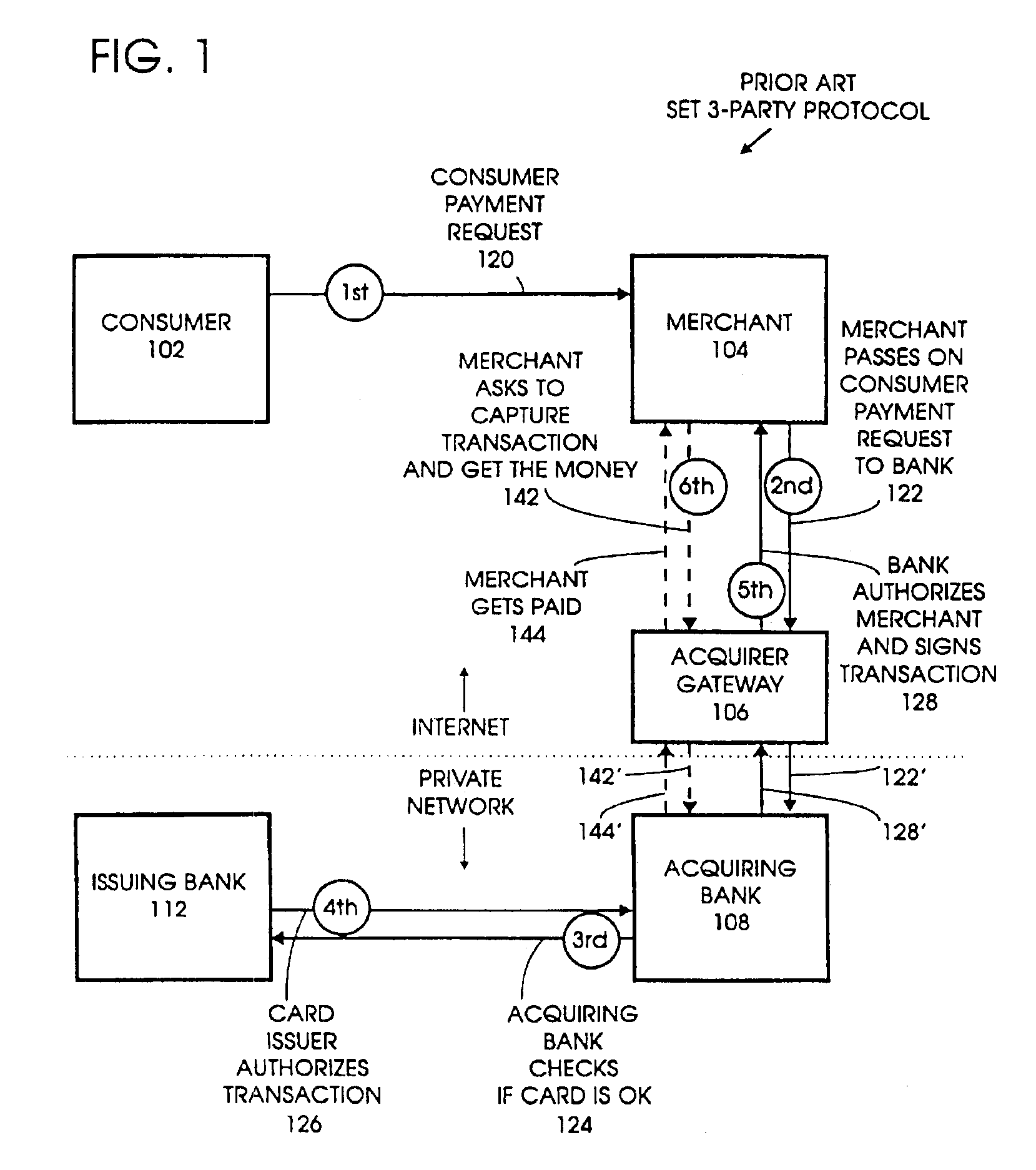
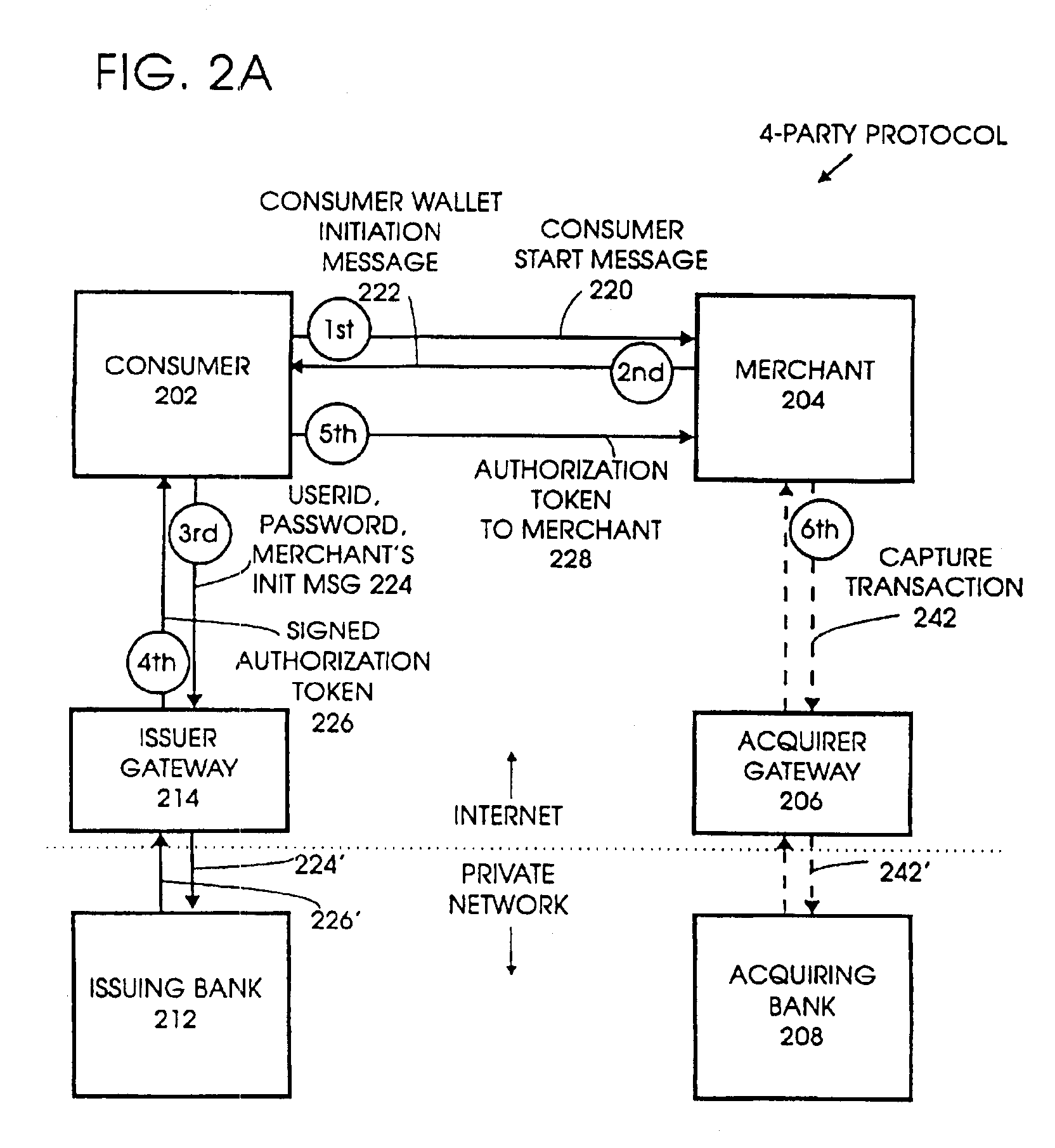
Four-party credit/debit payment protocol
InactiveUSRE40444E1Good effectReduce complexityUser identity/authority verificationSecret communicationE-commerceAuthorization
A method, system, program, and method of doing business are disclosed for electronic commerce that includes the feature of a “thin” consumer's wallet by providing issuers with an active role in each payment. This is achieved by adding an issuer gateway and moving the credit / debit card authorization function from the merchant to the issuer. This enables an issuer to independently choose alternate authentication mechanisms without changing the acquirer gateway. It also results in a significant reduction in complexity, thereby improving the ease of implementation and overall performance.
Owner:PAYPAL INC
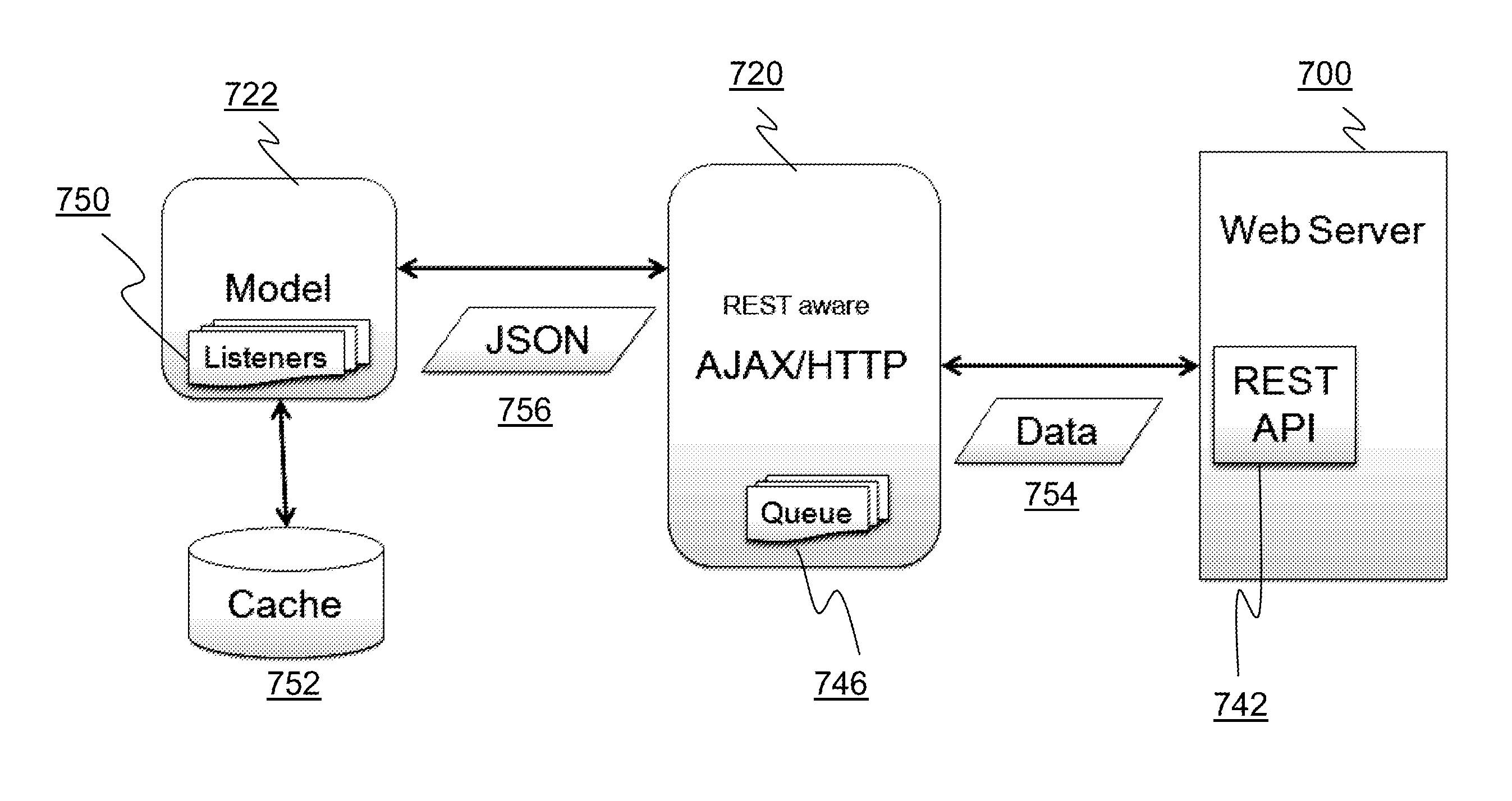
Systems and methods for providing user interfaces for management applications
ActiveUS20130246944A1Attenuation bandwidthReduce consumptionInterprogram communicationTransmissionExtensibilityRepresentational state transfer
The present application is directed towards systems and methods for providing user interfaces for management applications via a definition-based graphical user interface (GUI) framework for developing web based management applications for servers, intermediaries, routers, wide area network (WAN) accelerators, caches, switches, or any other type and form of computing device. The plug-in free framework reduces the server's resource consumption and bandwidth by making a full use of resources available on the client computing device or browser. A complete web application can be developed using JavaScript Object Notation (JSON) definitions along with a representational state transfer (REST) based application programming interface (API) efficiently using the framework, which may comprise light-weight pure JavaScript or similar executable code. In many embodiments, the framework may be layered in a model-view-controller (MVC) architecture easing resource consumption, maintenance and extensibility.
Owner:CITRIX SYST INC
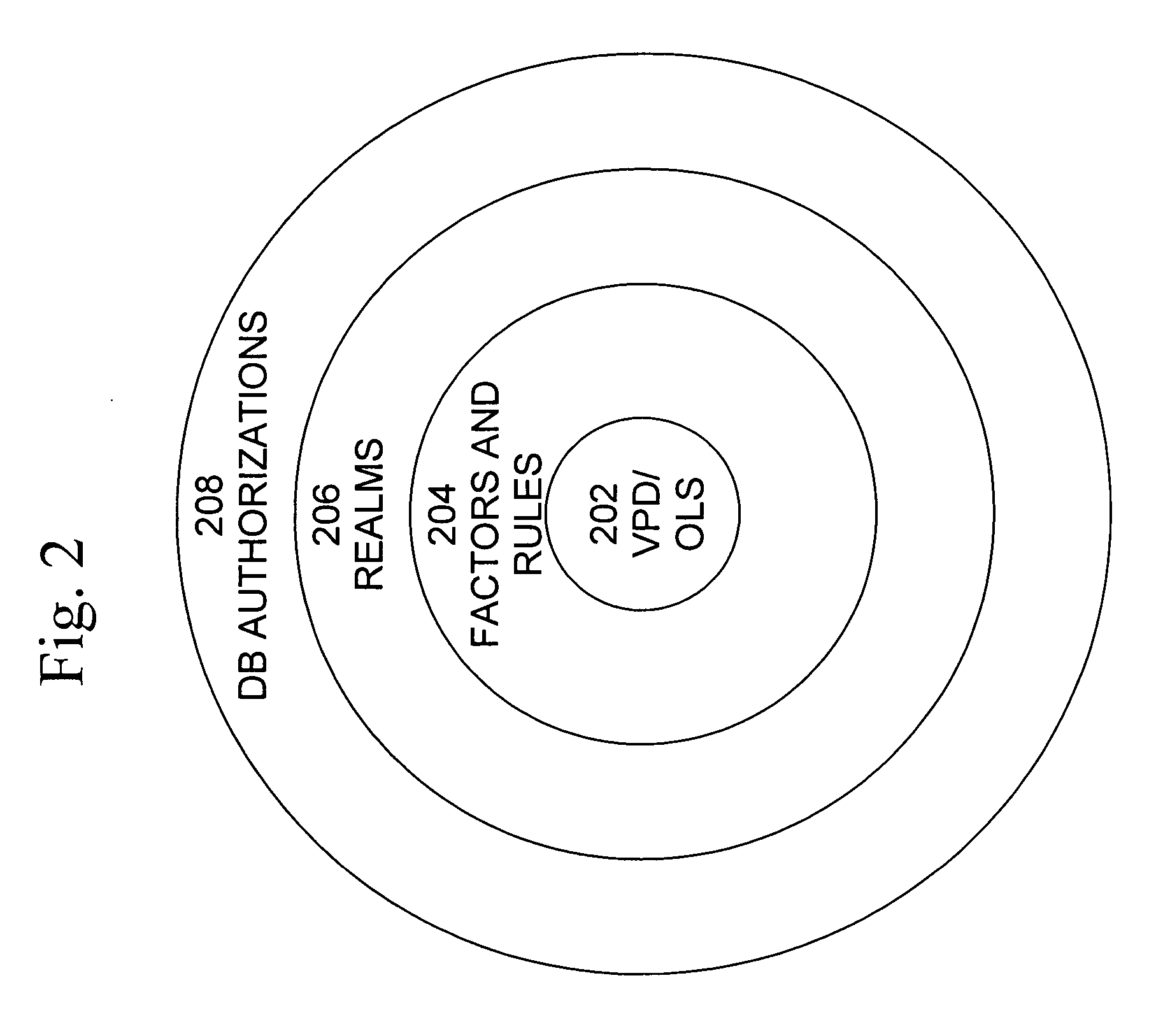
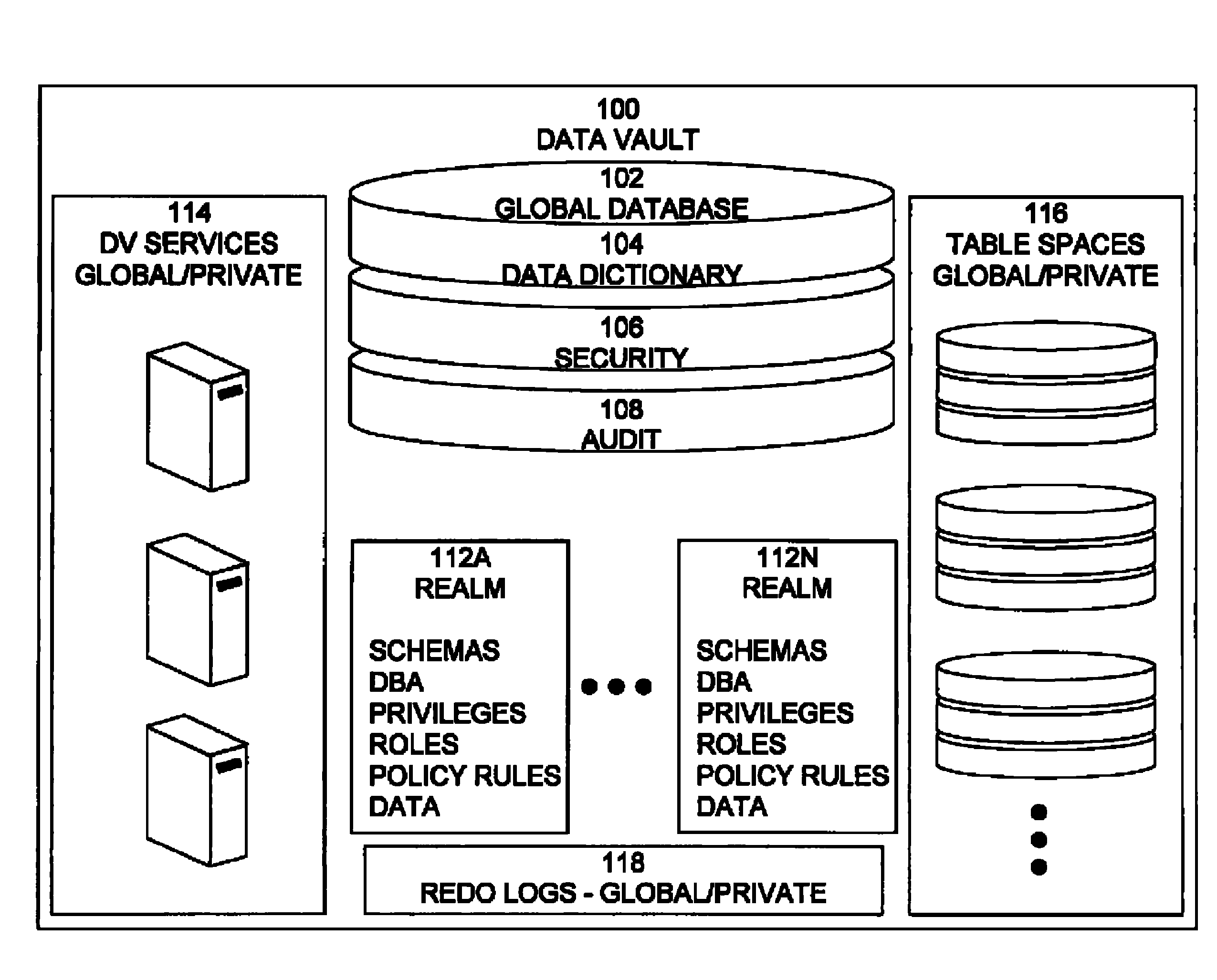
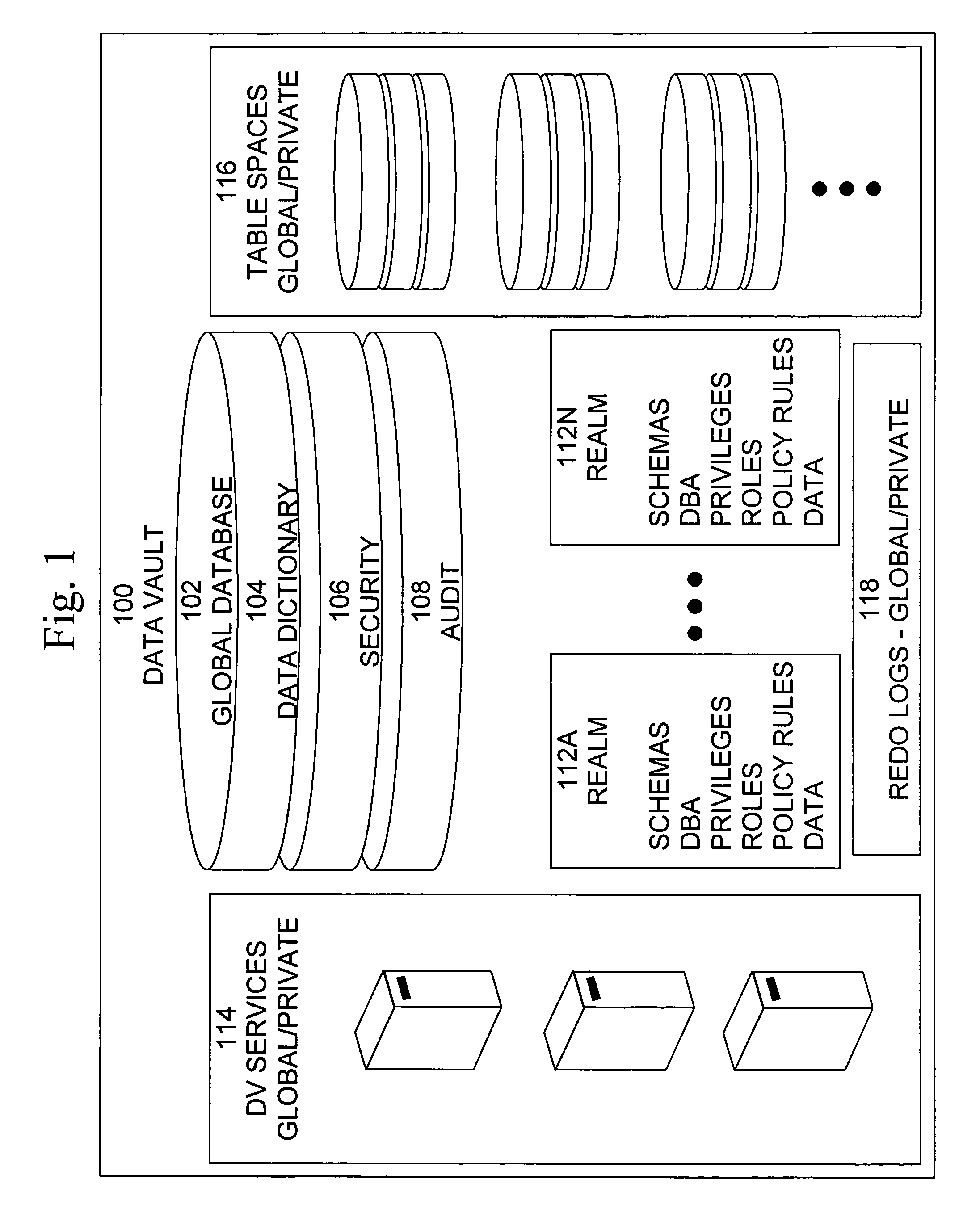
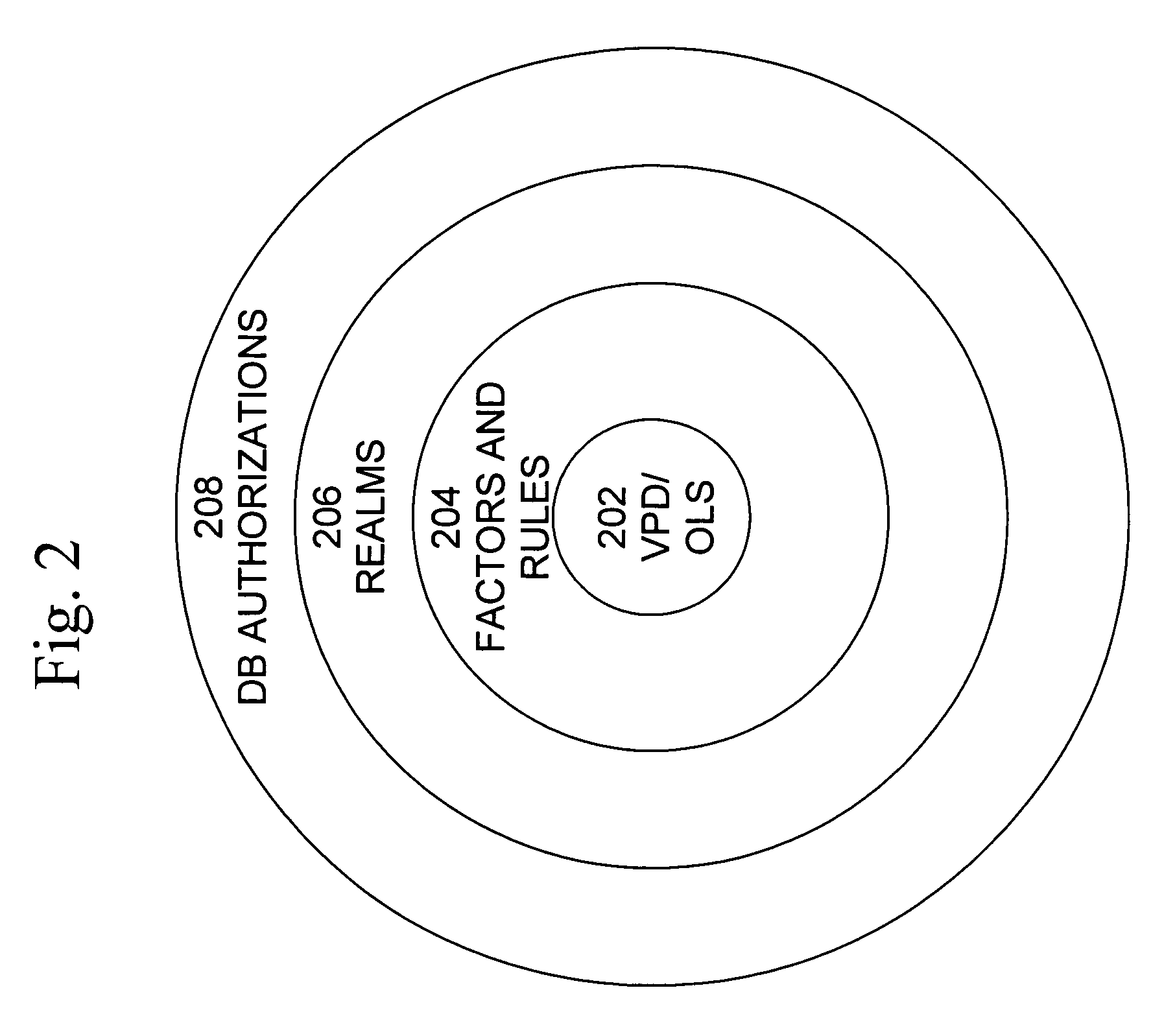
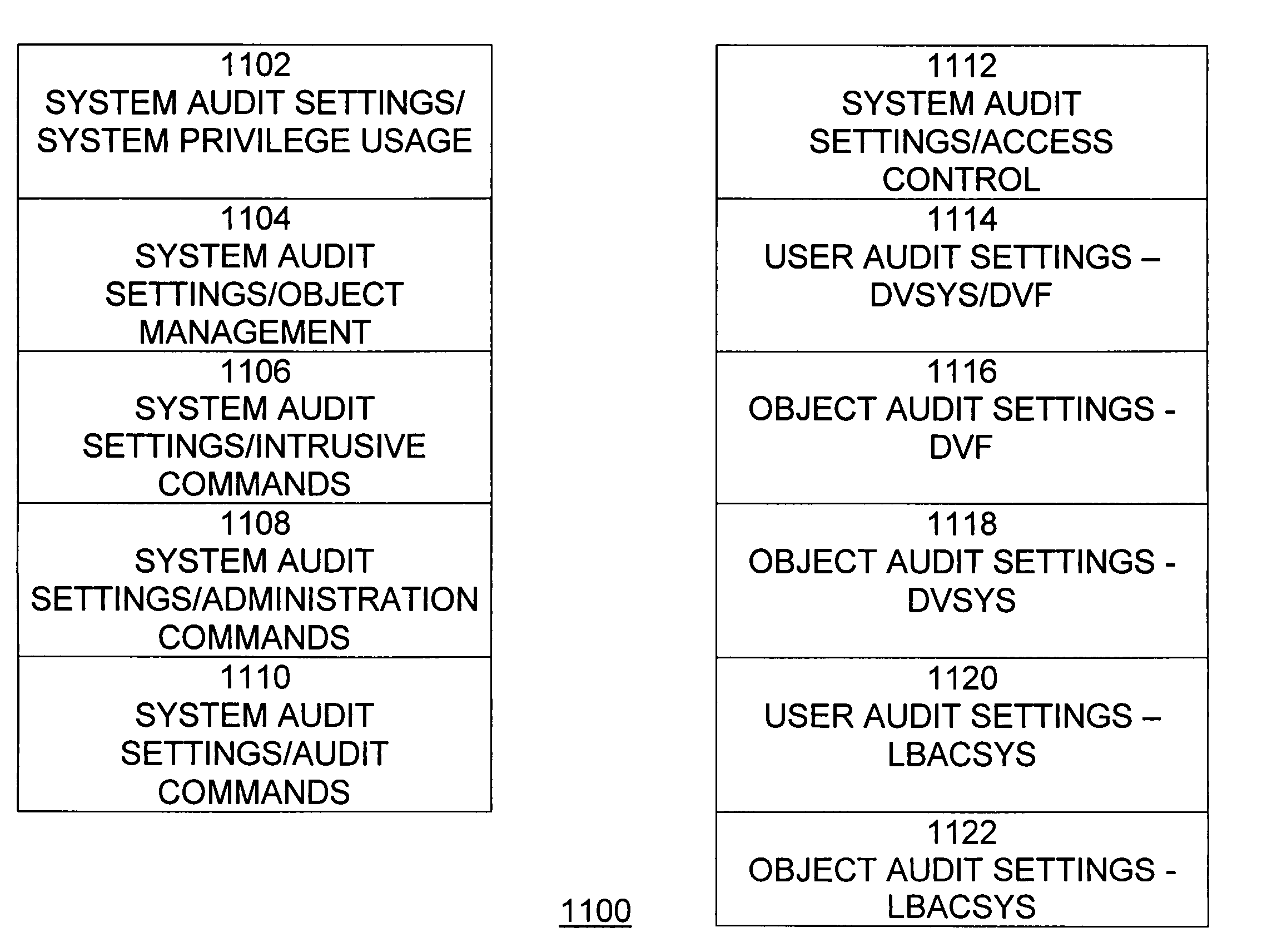
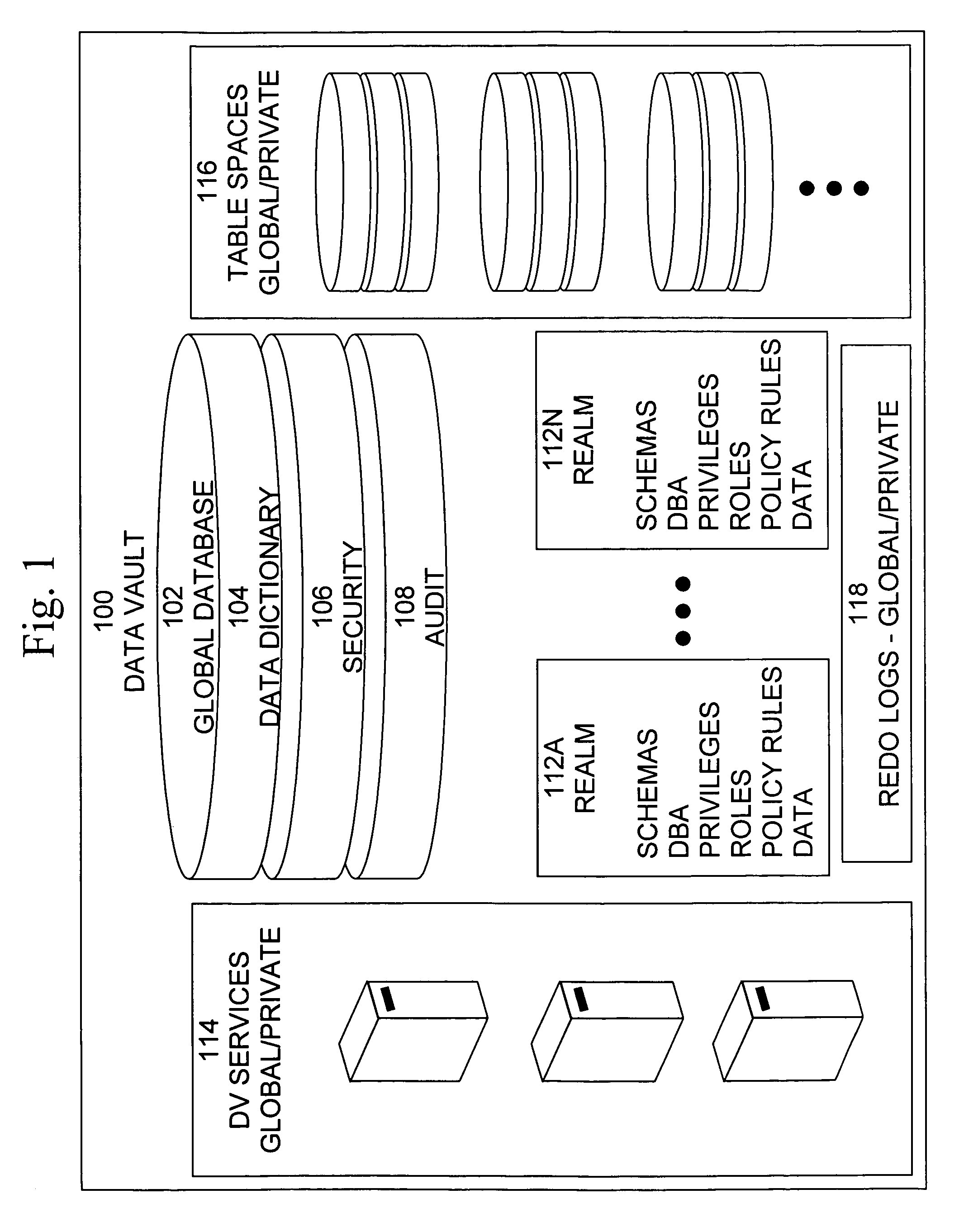
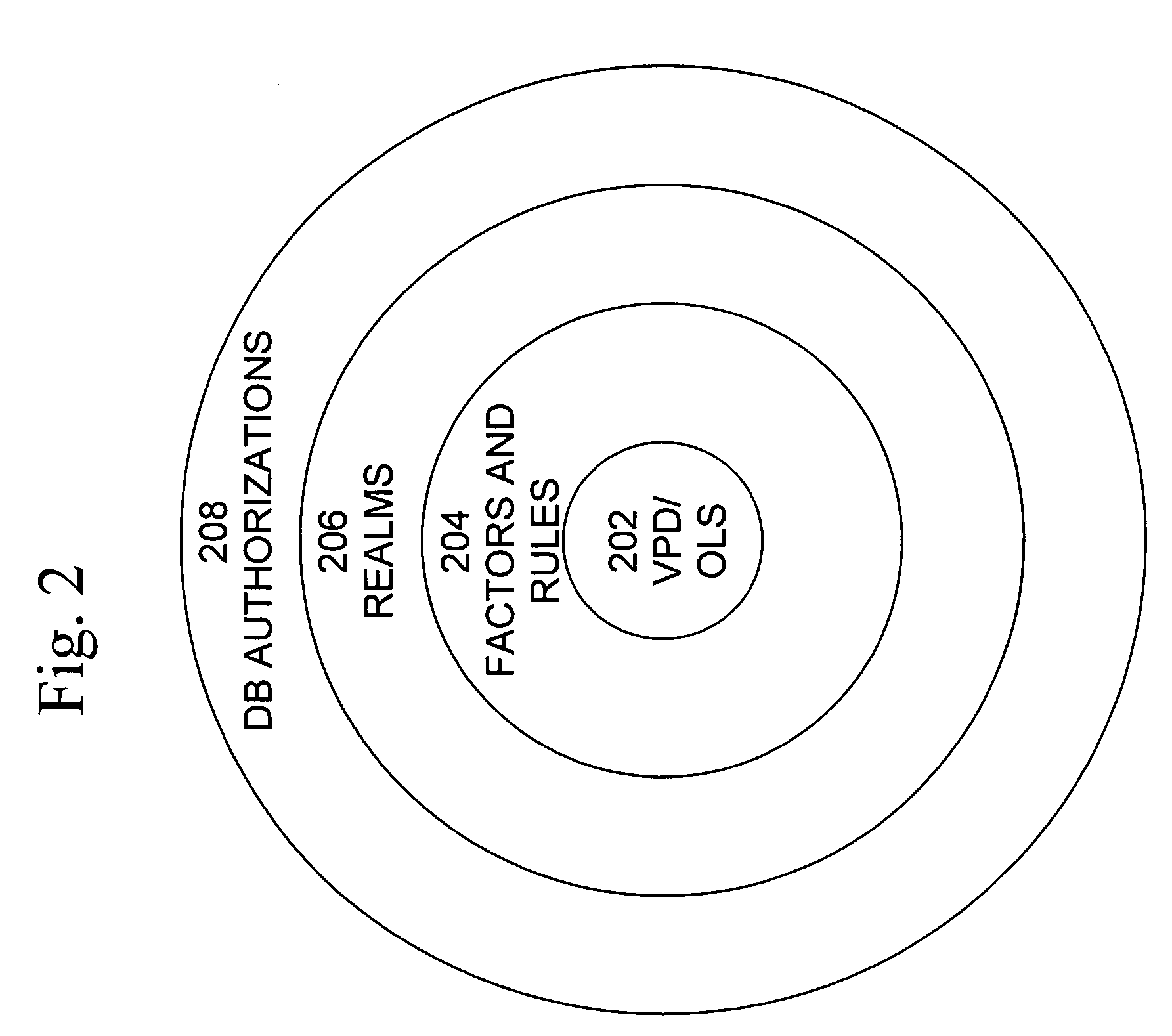
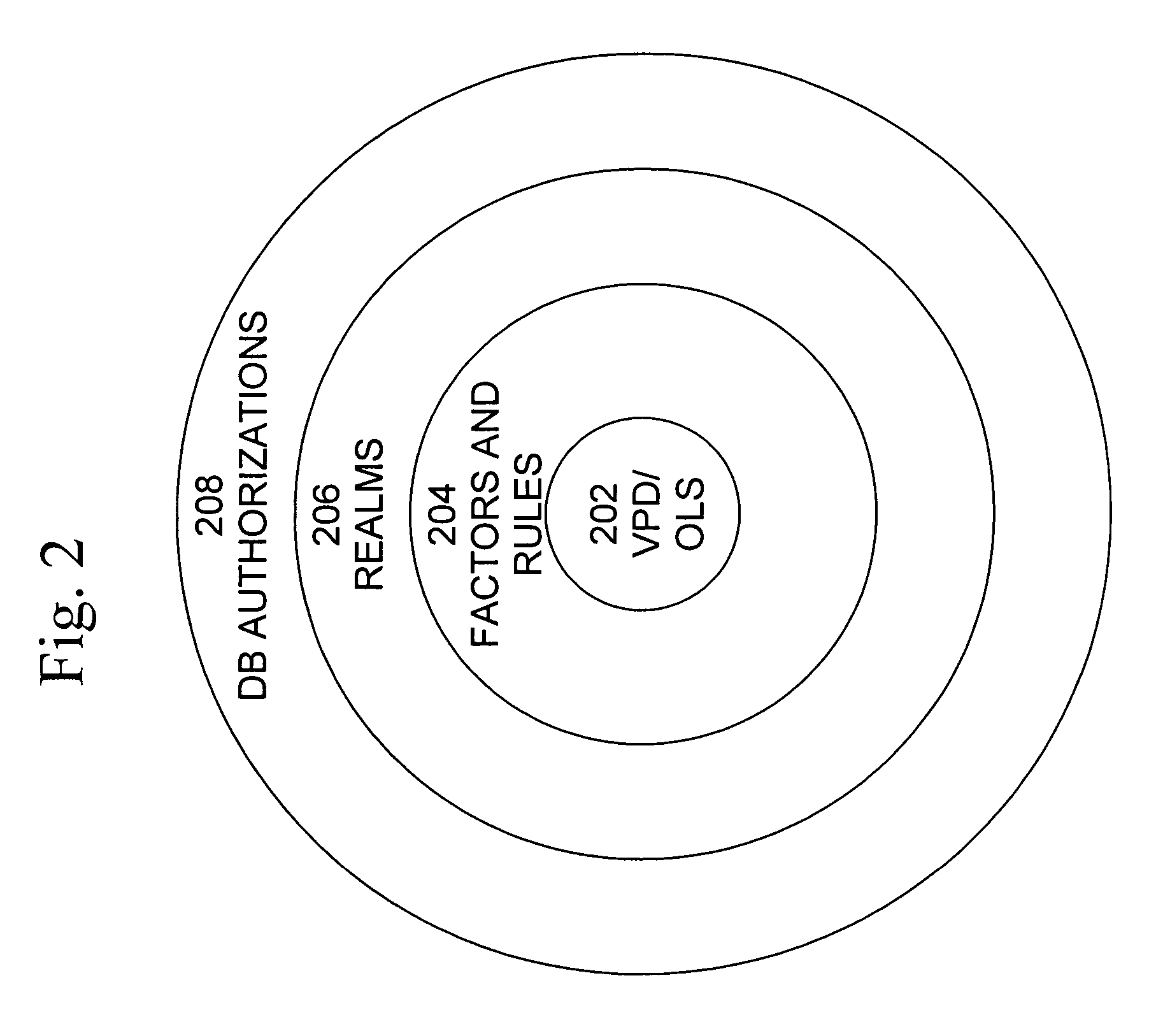
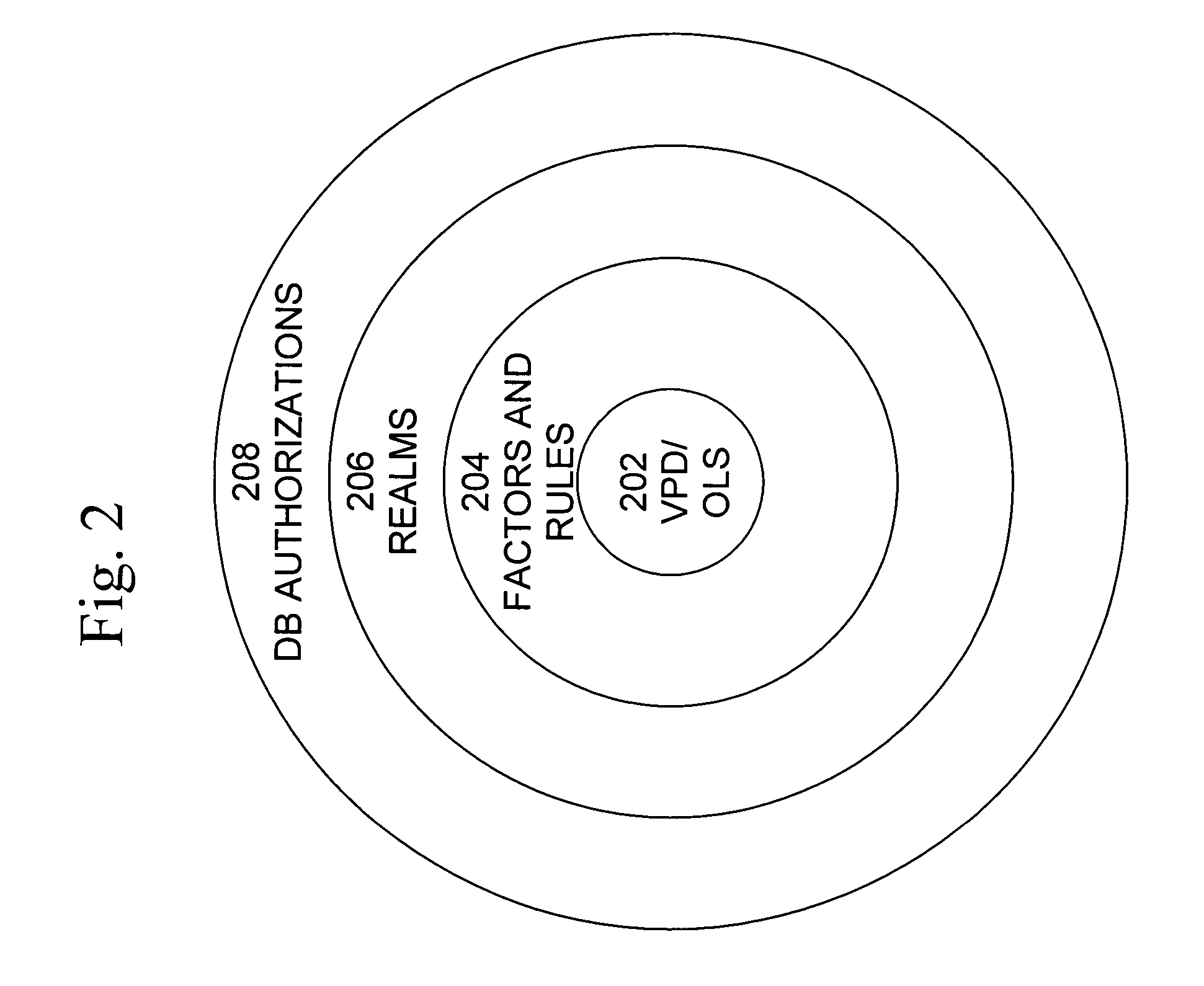
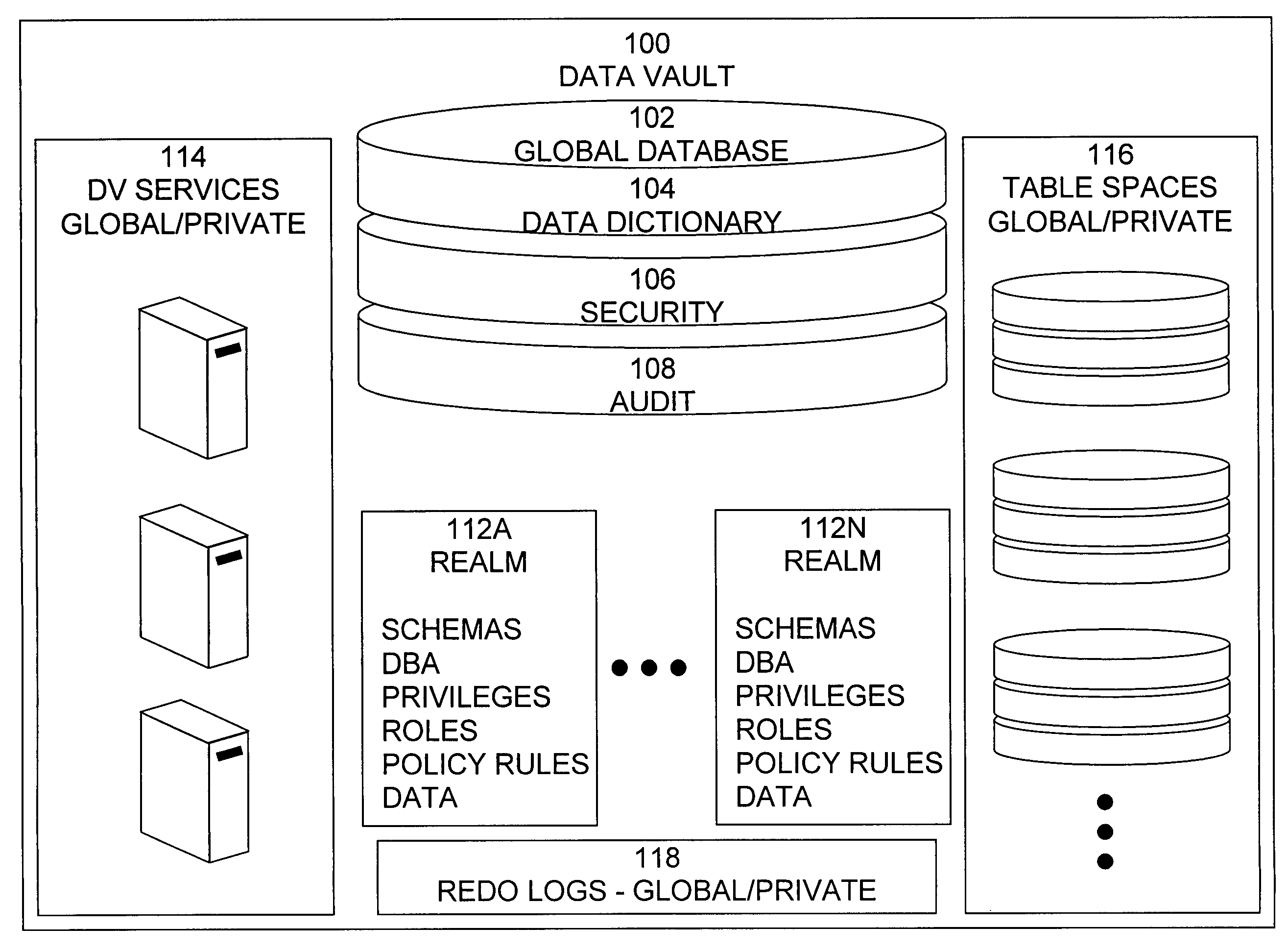
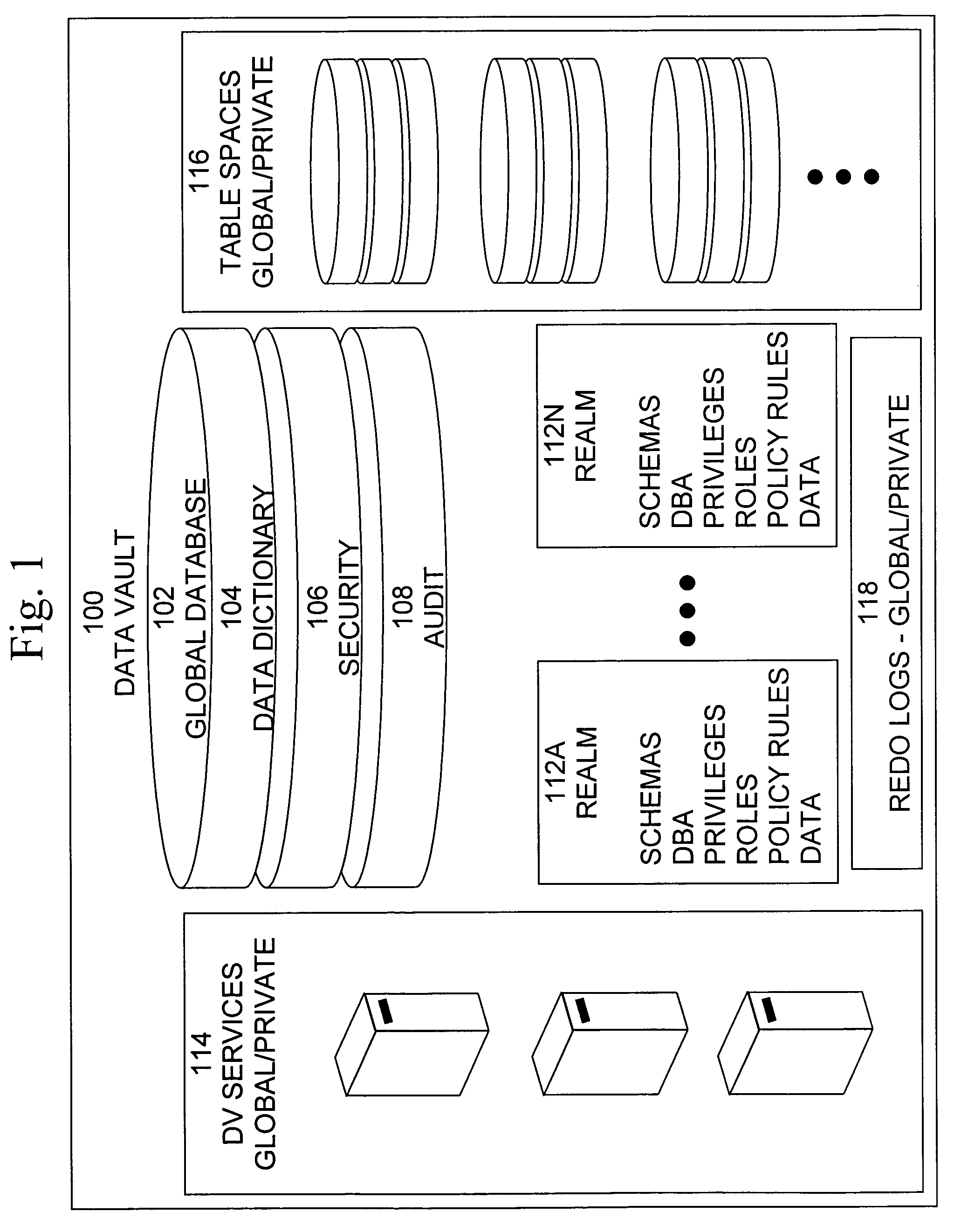
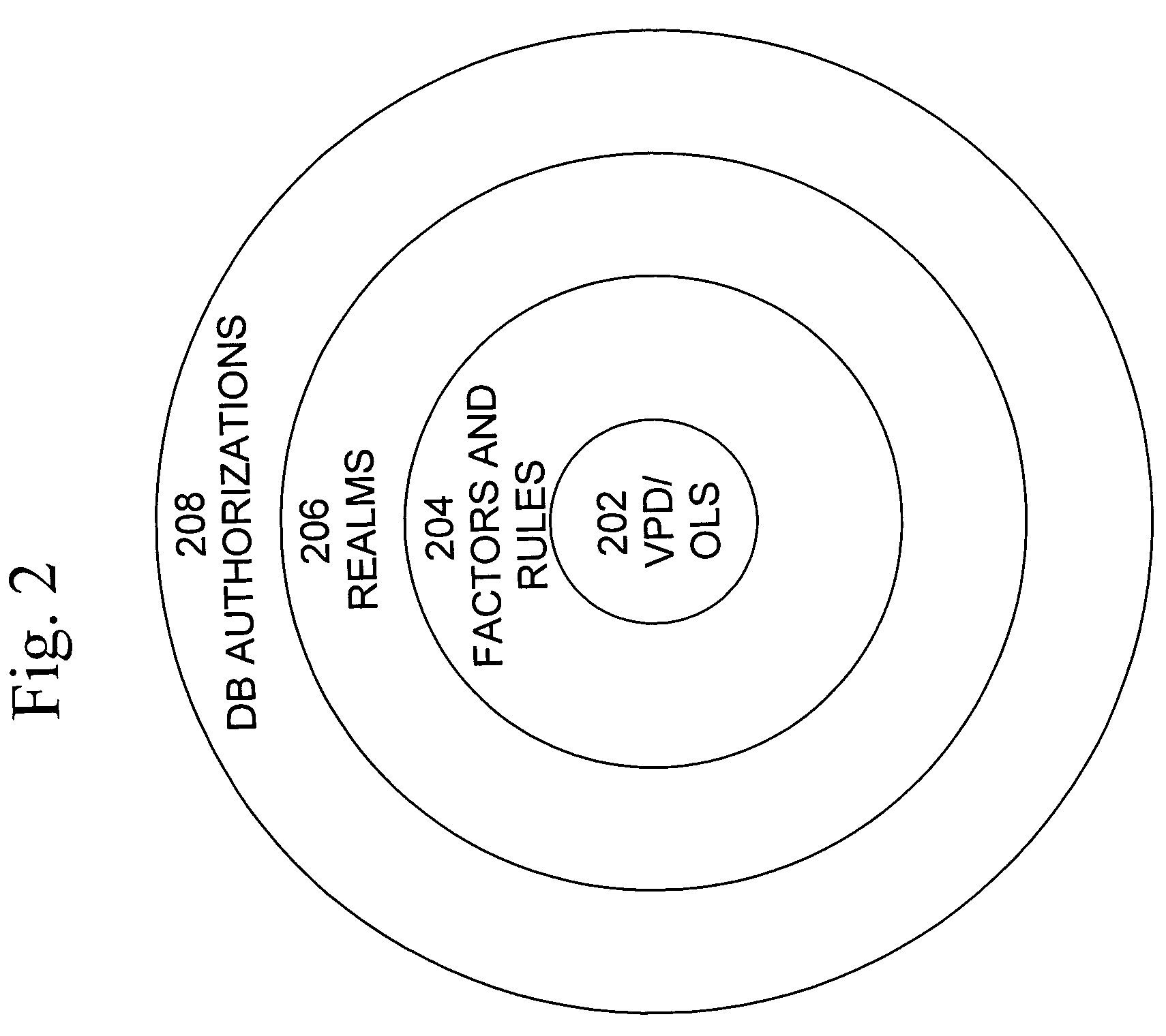
Cross-domain security for data vault
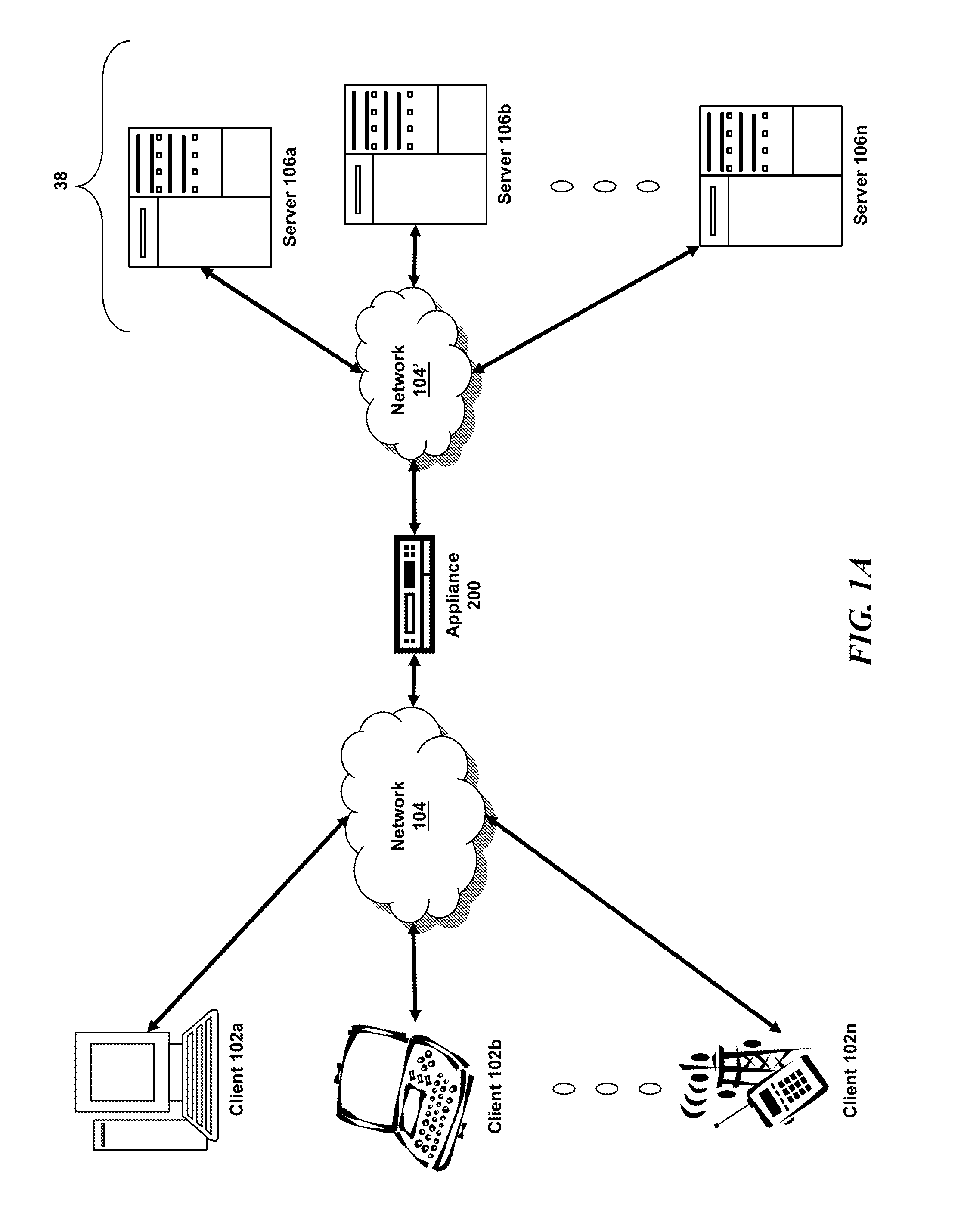
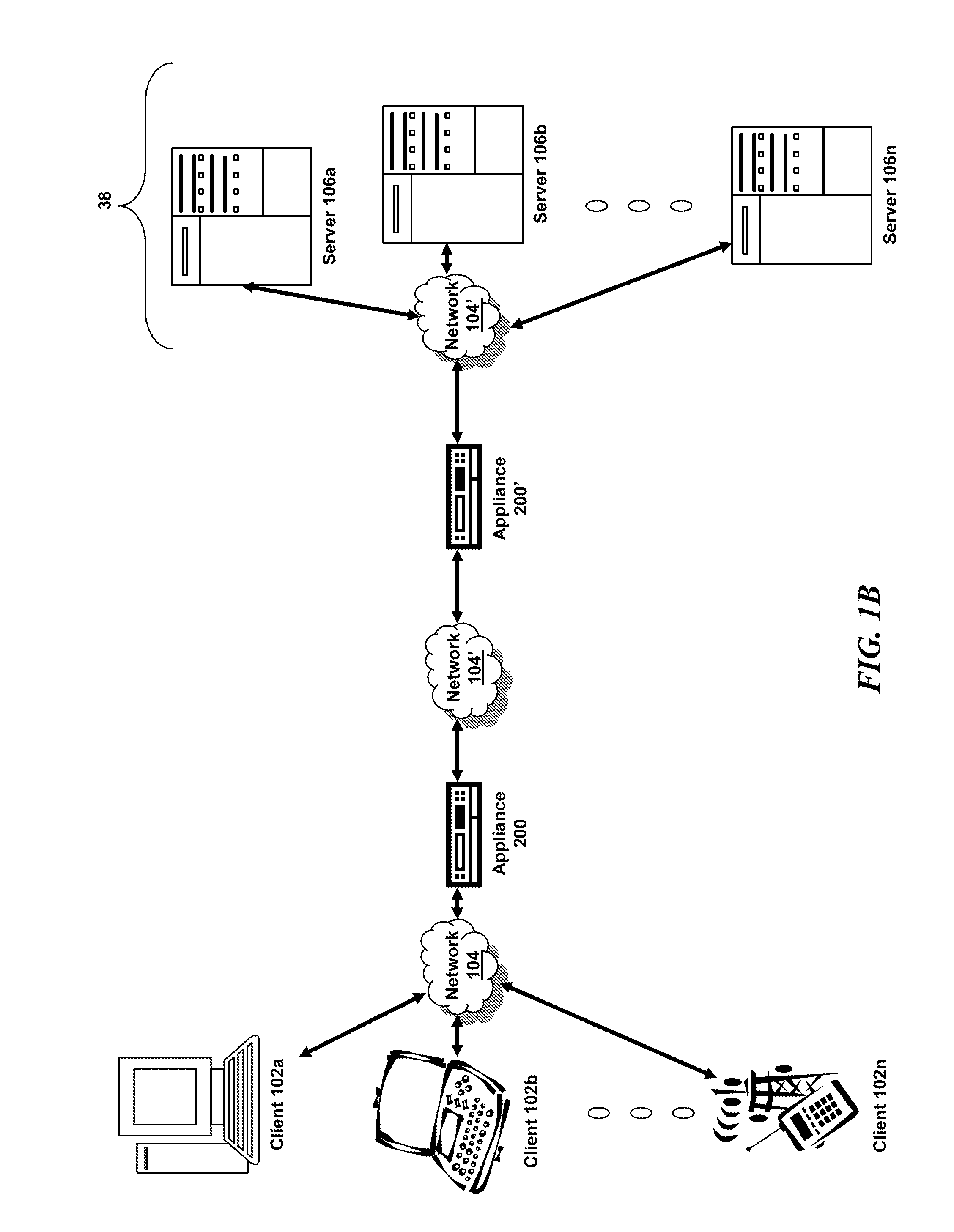
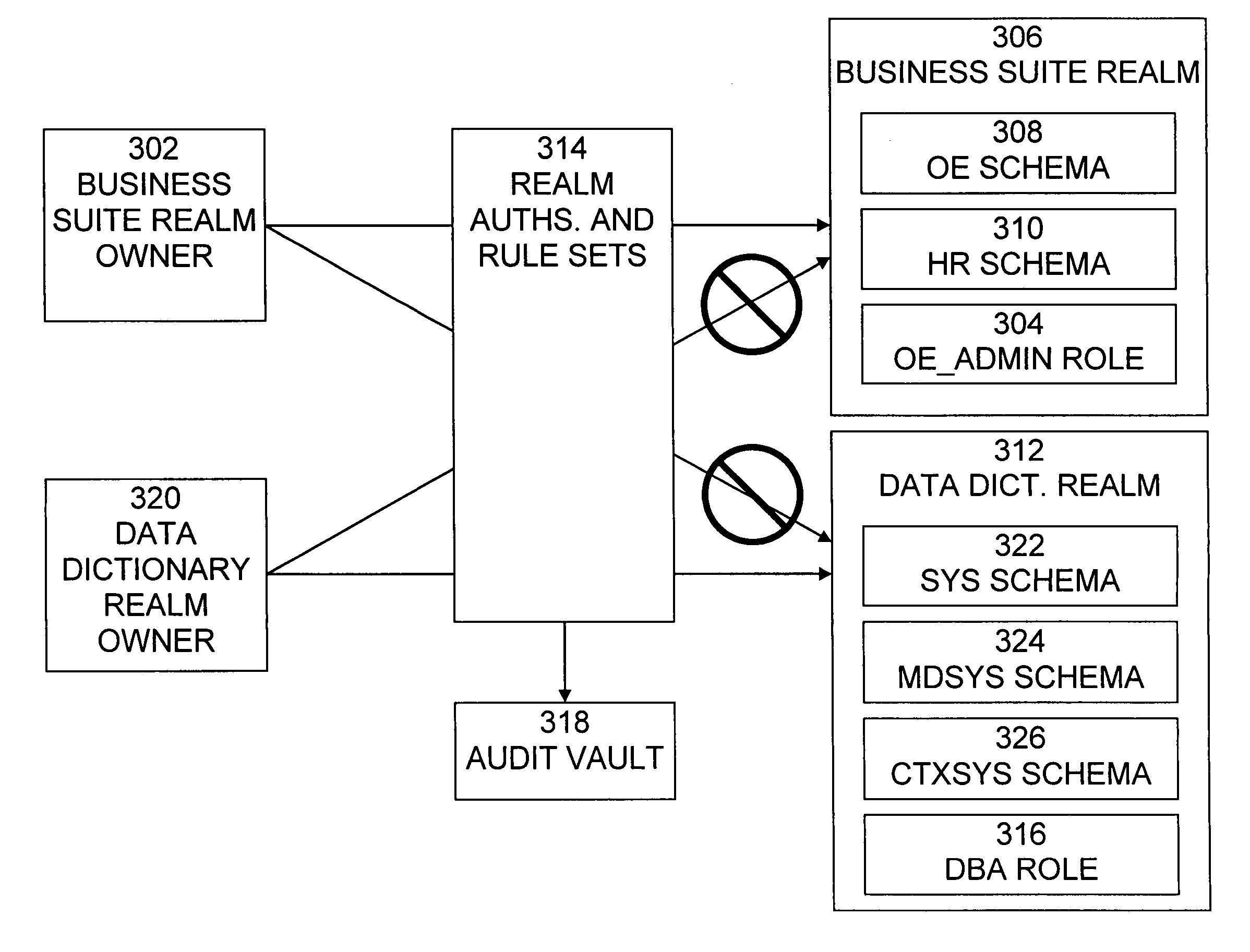
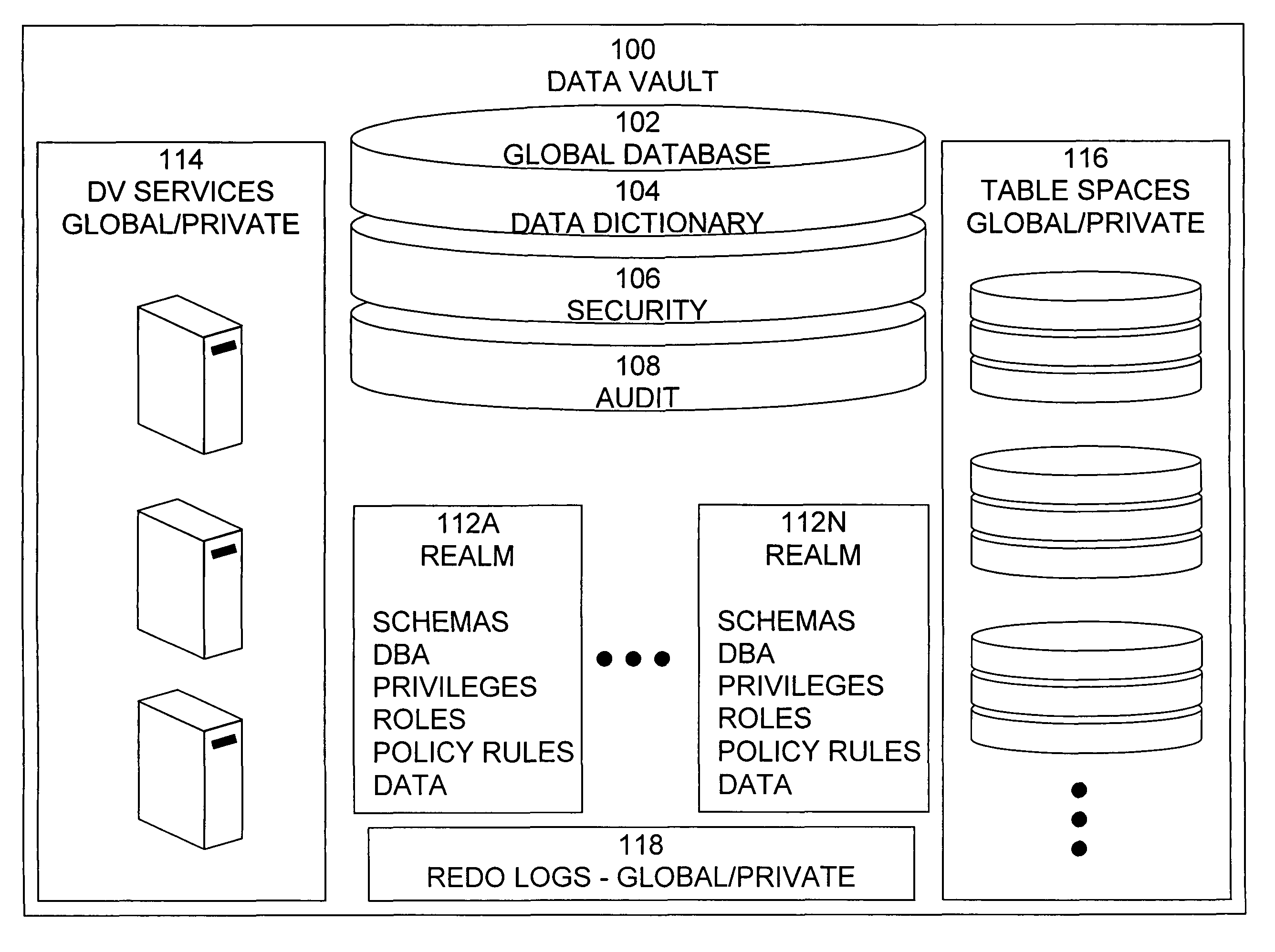
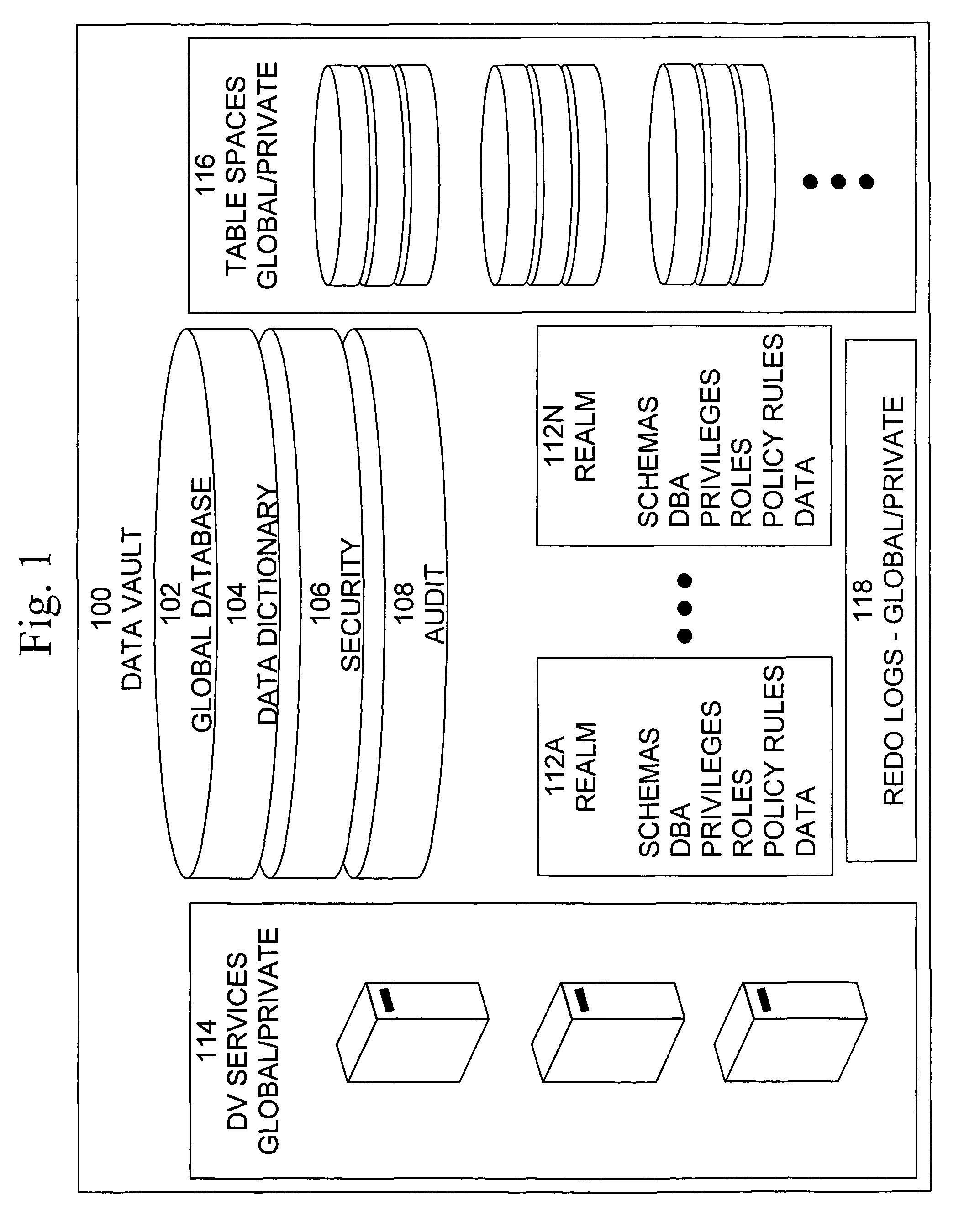
ActiveUS20060248599A1Ease of administrationEnsure effective implementationDigital data processing detailsUser identity/authority verificationDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system communicatively connected to a plurality of network domains, each network domain having a level of security, the database system comprises at least one database accessible from all of the plurality of network domains, the database comprising data, each unit of data having a level of security and access control security operable to provide access to a unit of data in the database to a network domain based on the level of security of the network domain and based on the level of security of the unit of data.
Owner:ORACLE INT CORP
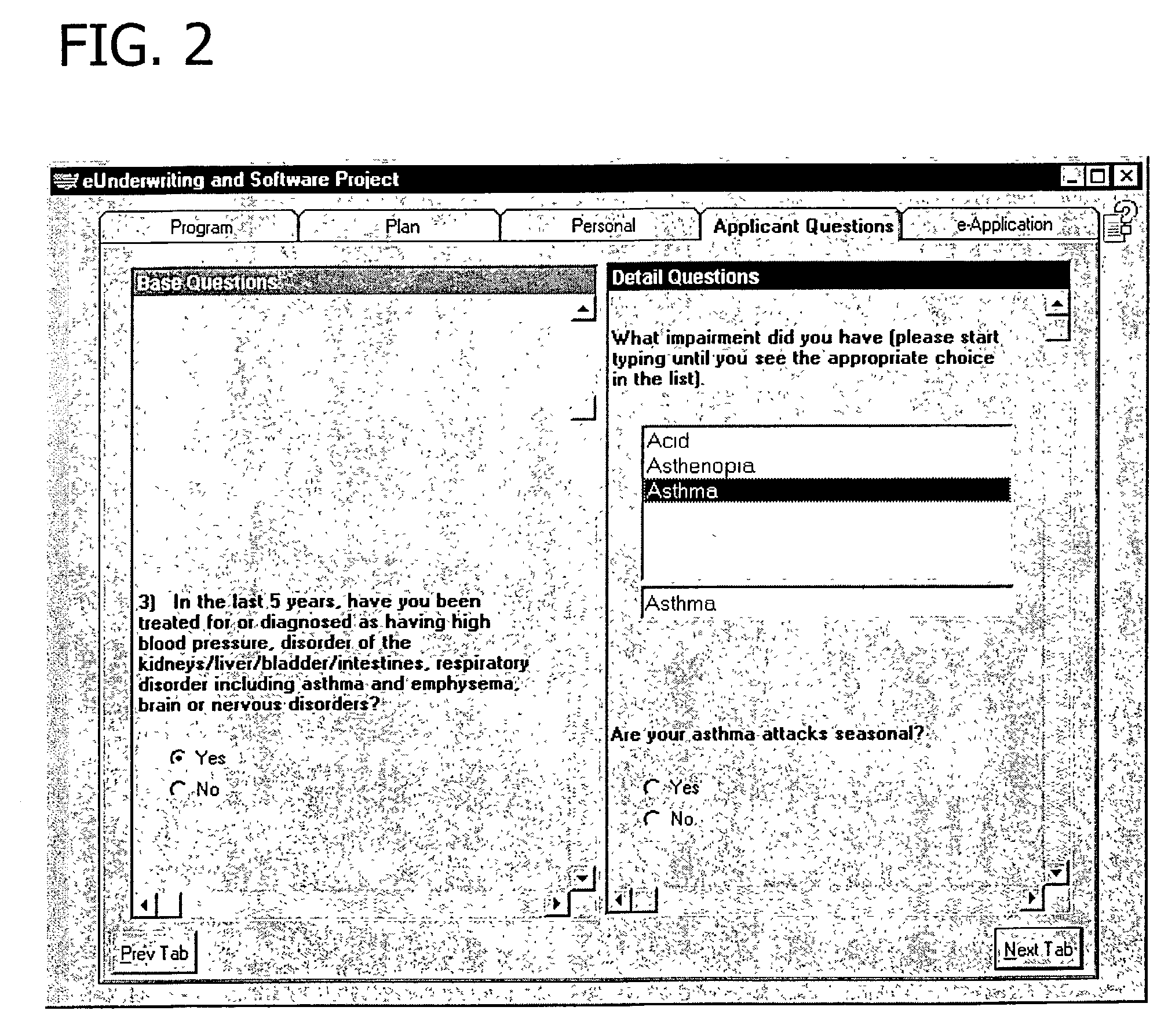
Computerized system and method of performing insurability analysis
InactiveUS20030233260A1Ensure effective implementationQuickly and efficiently handlesFinanceOffice automationComputerized systemClient-side
A method and system for evaluating insurability of an applicant for insurance from a carrier. A server, receiving and responsive to communications from a client computer, renders a contemporaneous insurability decision. The communications from the client computer include responses to an interactive questionnaire presented via a browser. A database associated with the server stores a comprehensive set of questions for collecting underwriting information and the server executes processing rules to determine which questions to present in the questionnaire. The questionnaire includes base questions and detail questions. The detail questions are each related to at least one of the base questions for collecting further information related to the respective base question. The server renders the insurability decision and exports a summary file to the carrier. The summary file includes the questions and responses thereto as well as the insurability decision.
Owner:REINSURANCE GROUP OF AMERICA CORP +1
Method for dynamic management of TCP reassembly buffers
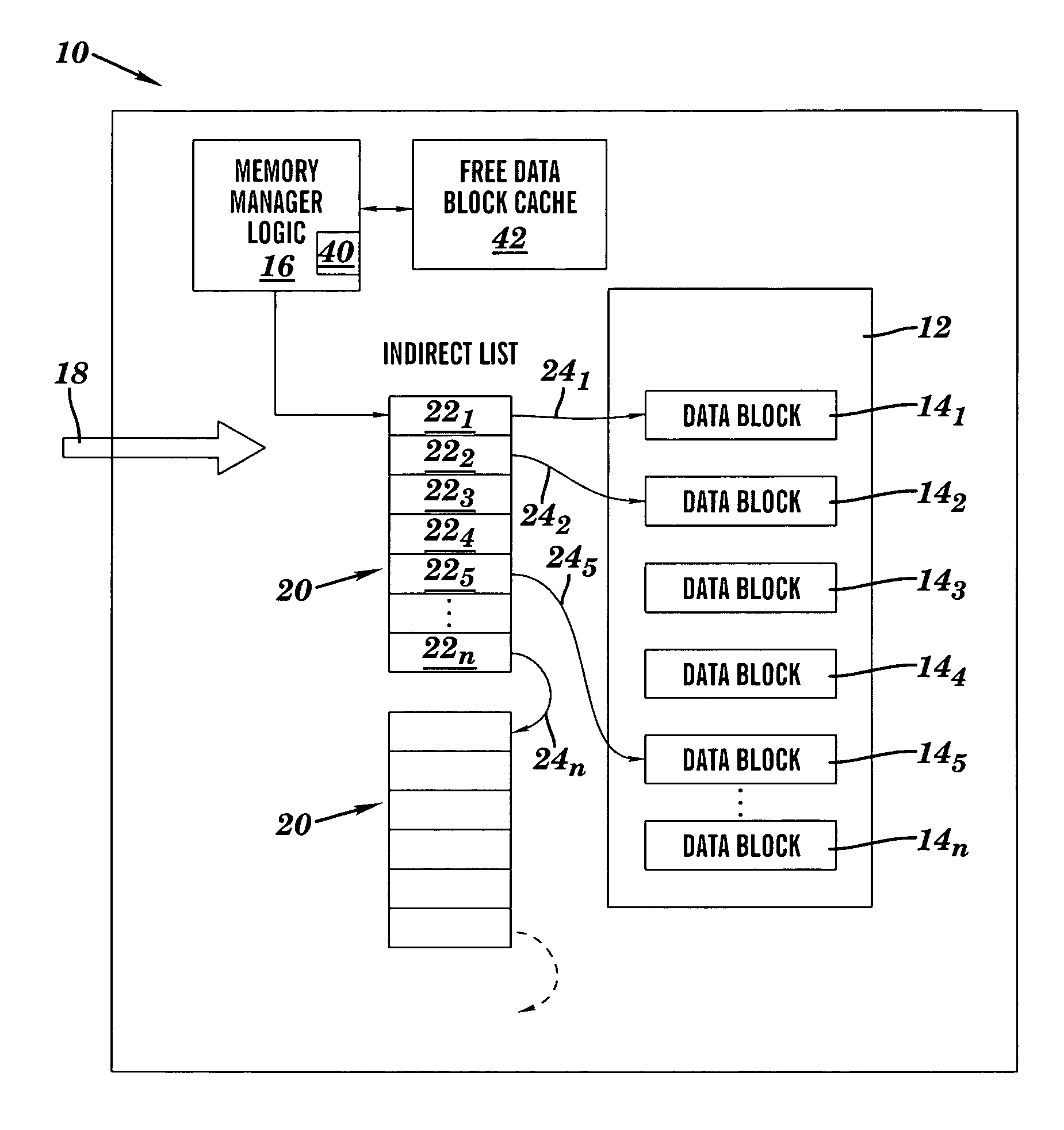
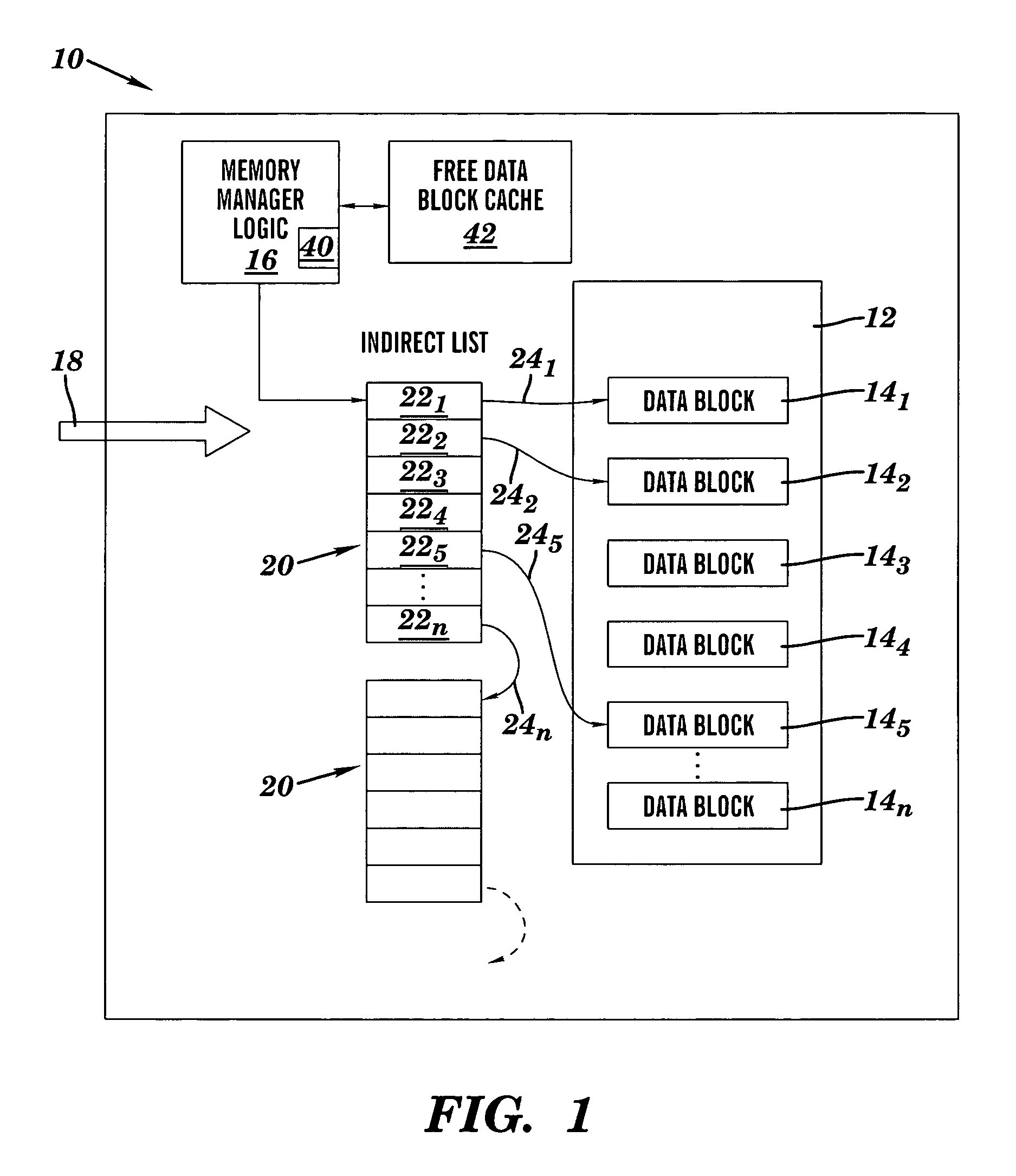
InactiveUS7496108B2Improve flexibility and scalabilityLower performance requirementsError preventionFrequency-division multiplex detailsComputer hardwareDynamic management
A method for dynamic management of Transmission Control Protocol (TCP) reassembly buffers in hardware (e.g., in a TCP / IP offload engine (TOE)). The method comprises: providing a plurality of data blocks and an indirect list; pointing, via entries in the indirect list, to allocated data blocks in the plurality of data blocks that currently store incoming data; if a free data block in the plurality of data blocks is required for the storage of incoming data, allocating the free data block for storing incoming data; and, if an allocated data block in the plurality of data blocks is no longer needed for storing incoming data, deallocating the allocated data block such that the deallocated data block becomes a free data block.
Owner:INT BUSINESS MASCH CORP
Apparatus for estimating delay and jitter between network routers
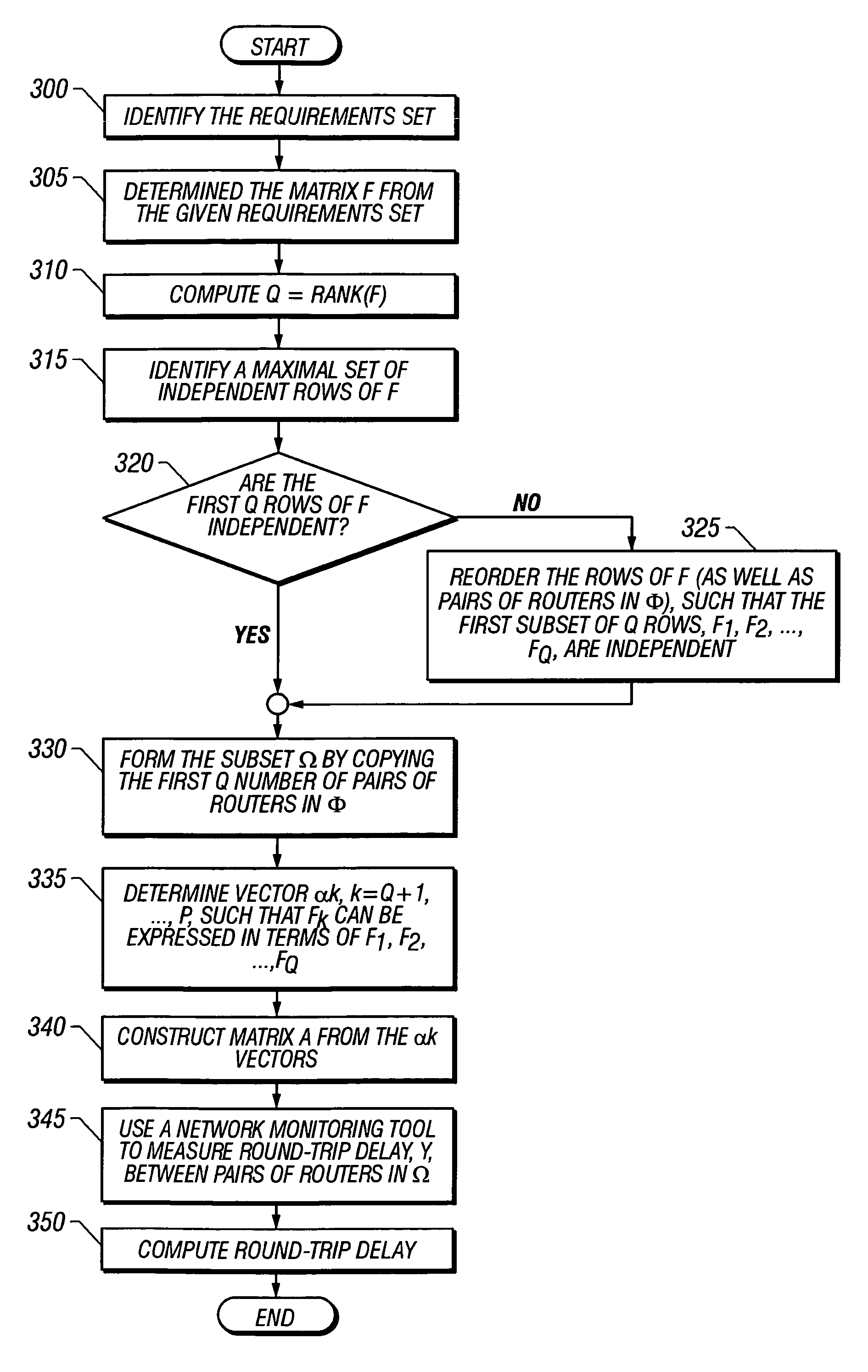
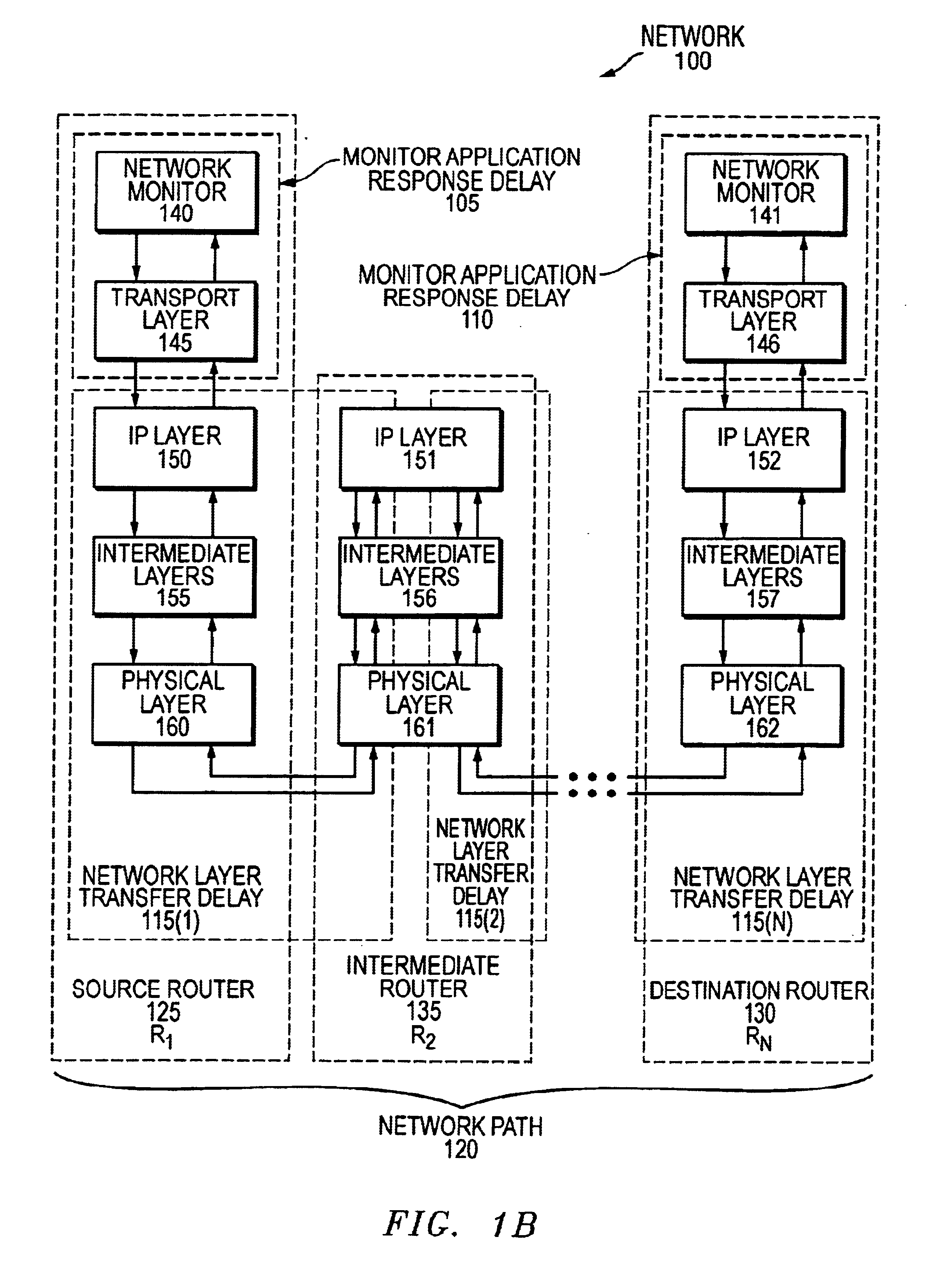
InactiveUS7111073B1Reduce traffic overheadEnsure effective implementationError preventionFrequency-division multiplex detailsDistributed computingNetwork router
A delay measurement technique according to an embodiment according to the present invention is based on the precept, ascertained by the inventors, that a link between network nodes will often contribute to the delay encountered between several different pairs of network nodes. Such a technique identifies the path between each pair of nodes by a list of links that form the path. Paths that are orthogonal are treated as being necessary for describing the delays encountered between nodes, and, once the requisite set of orthogonal paths has been derived, all other paths can be described in terms of one or more of these orthogonal paths. Such a technique also lends itself to matrix representation of the paths, and the use of matrix manipulation techniques in deriving delay and jitter.
Owner:CISCO TECH INC
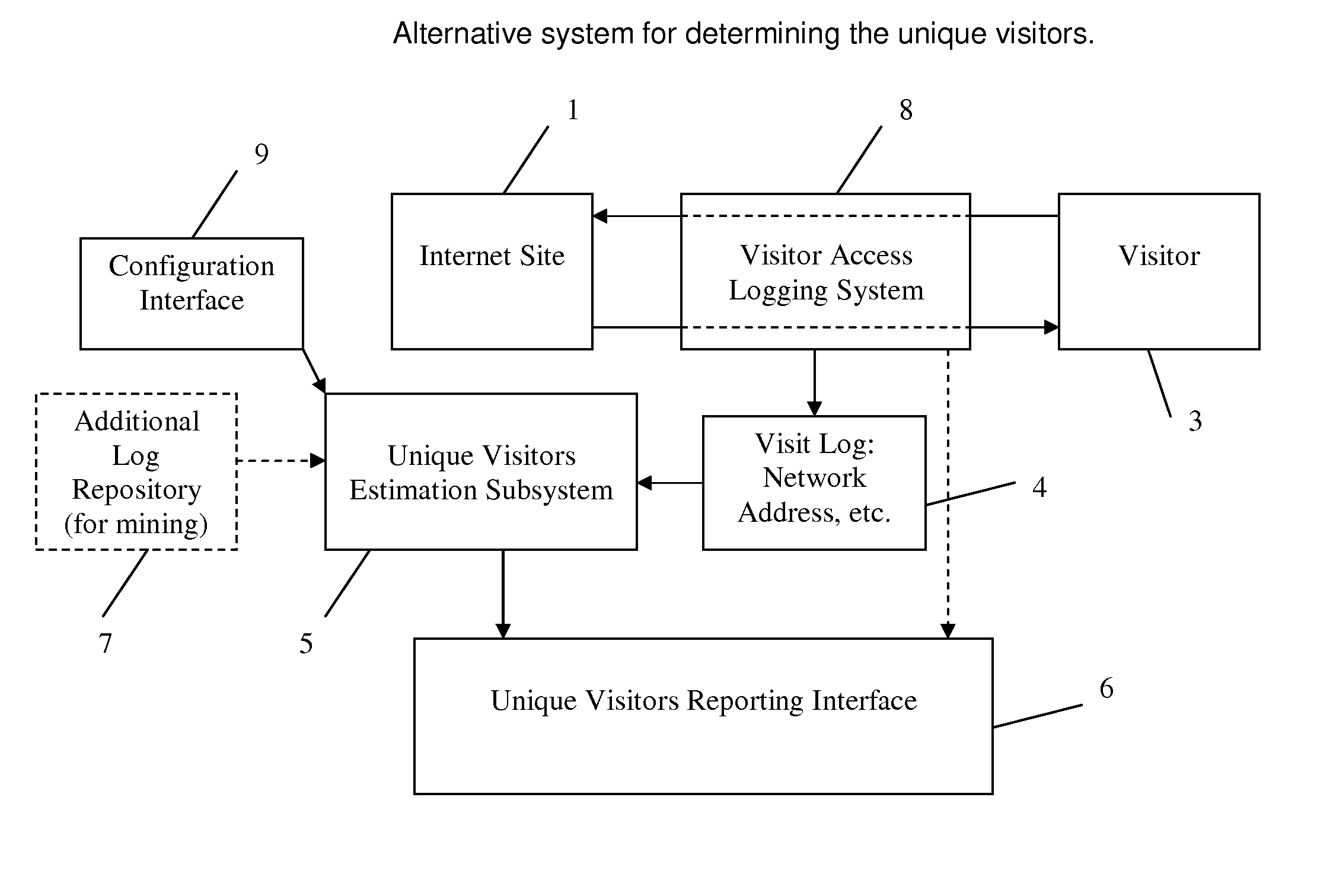
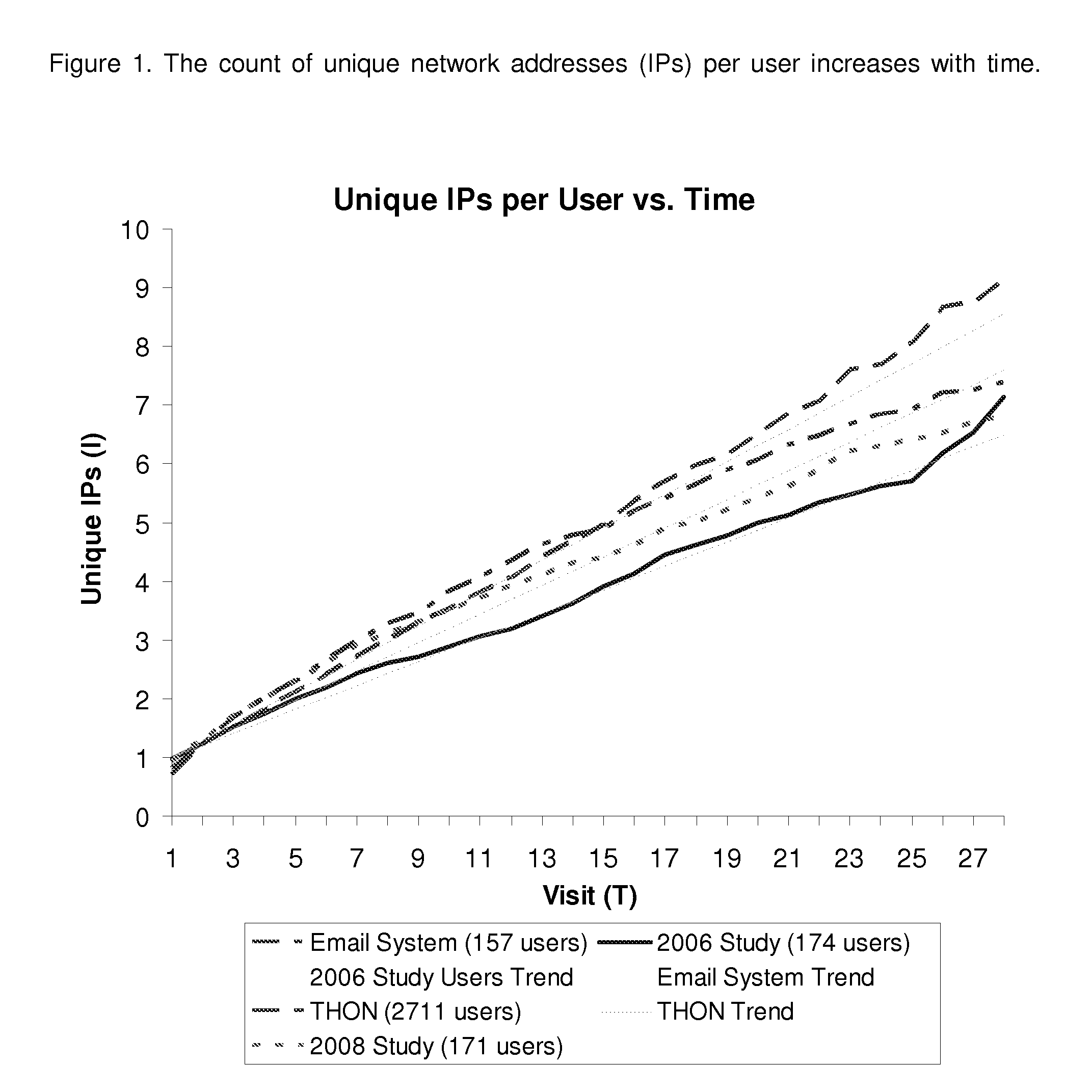
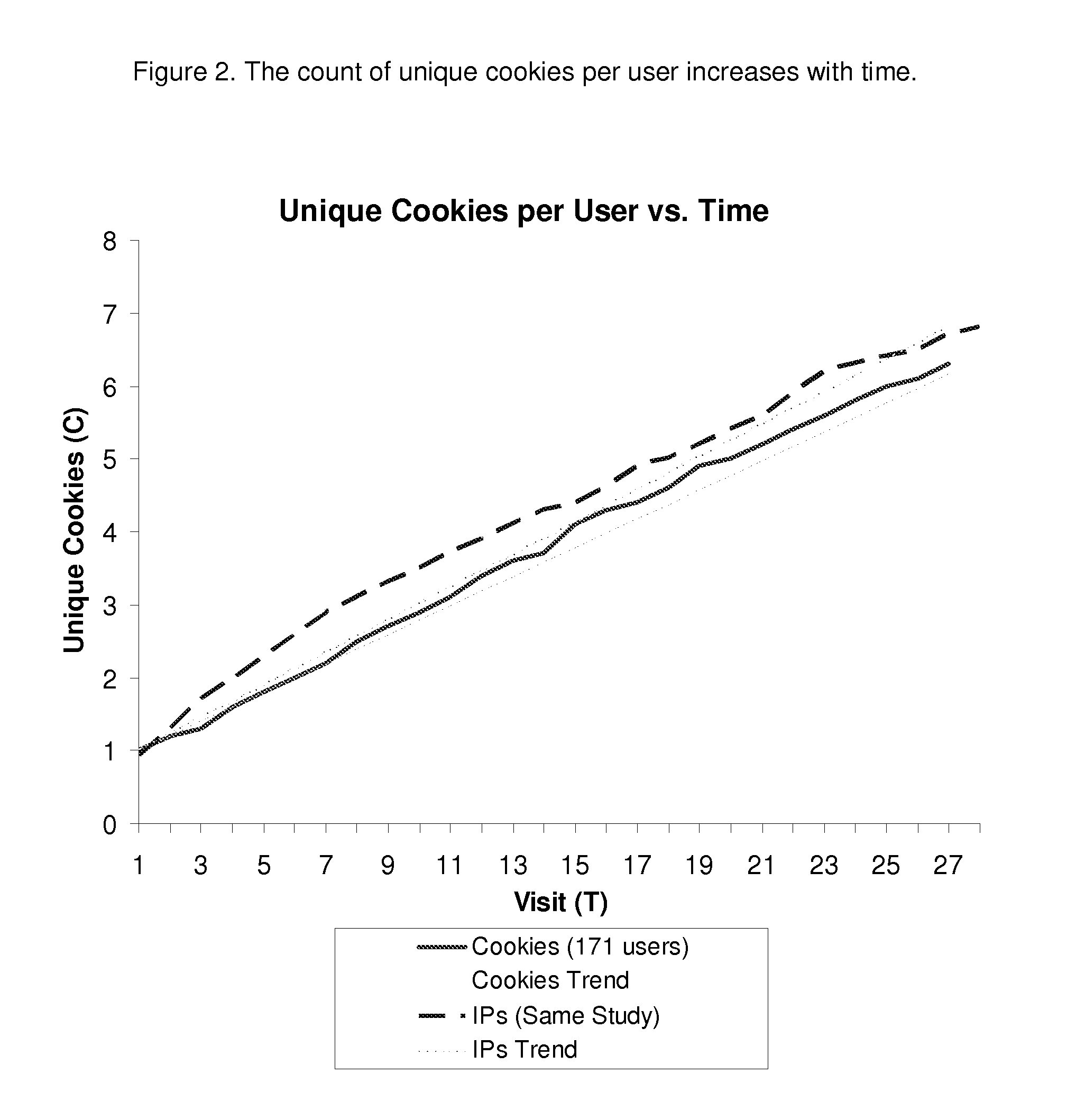
Method and System for Estimating Unique Visitors for Internet Sites
InactiveUS20100228850A1Ensure effective implementationSimplicity easeDigital computer detailsElectric testing/monitoringThird partyNetwork addressing
This invention comprises a method and system for estimating unique visitors for Internet sites that is more accurate than the existing unique cookie / unique address counting methods. The invented method relies on the count of unique user identifiers (such as network addresses or preferably cookies)—I—that can be obtained from an existing cookie tracking / user access logging system. The number of unique visitors U is calculated substantially as a ratio of the count of unique cookies (or unique network addresses) to the number of visits N times the inflation factor X plus constant on that is approximately one (exactly one in the case of cookies). The number of visits is calculated by multiplying the sampling period t to the visitation frequency T1 minus one. The resulting estimate of the unique visitors is stable and does not diverge with sampling time unlike estimates directly obtained from the unique network address or unique cookie counts. The method is also applicable when there are multiple dominant visitation frequencies by accounting to the sum by all significant visitation frequencies. All key parameters of the method can be established before hand by mining a multitude of the site's historical visit logs and / or third party site access logs; the parameters can be corrected / calculated dynamically by mining the site's current access log (or current third party logs) while focusing on unambiguously identified visitors (such as return visitors identified by their login ID or unchanged cookie value).
Owner:FOMITCHEV MAX
Circuits, Architectures, Apparatuses, Systems, and Methods for Merging of Management and Data Signals, and for Recovery of a Management Signal
ActiveUS20120170927A1Low costEasy to manageTransmission monitoringTransmission monitoring/testing/fault-measurement systemsManagement unitTransceiver
An optical and / or optoelectrical transceiver and system are disclosed that enable parallel transmission of data and management signals via an optical fiber without affecting data signal transmissions transmitted on the optical fiber. Furthermore, the present transceiver and system provide a fault diagnosis function for an optical fiber link. The transceiver and system generally comprise an interface, an intersecting transmission management unit, a driver, a management signal driving unit, an optical transmitter, an optical receiver, an amplifier, a management signal recovery unit, a management unit, and optionally, a power supply unit.
Owner:MAGNOLIA SOURCE CAYMAN
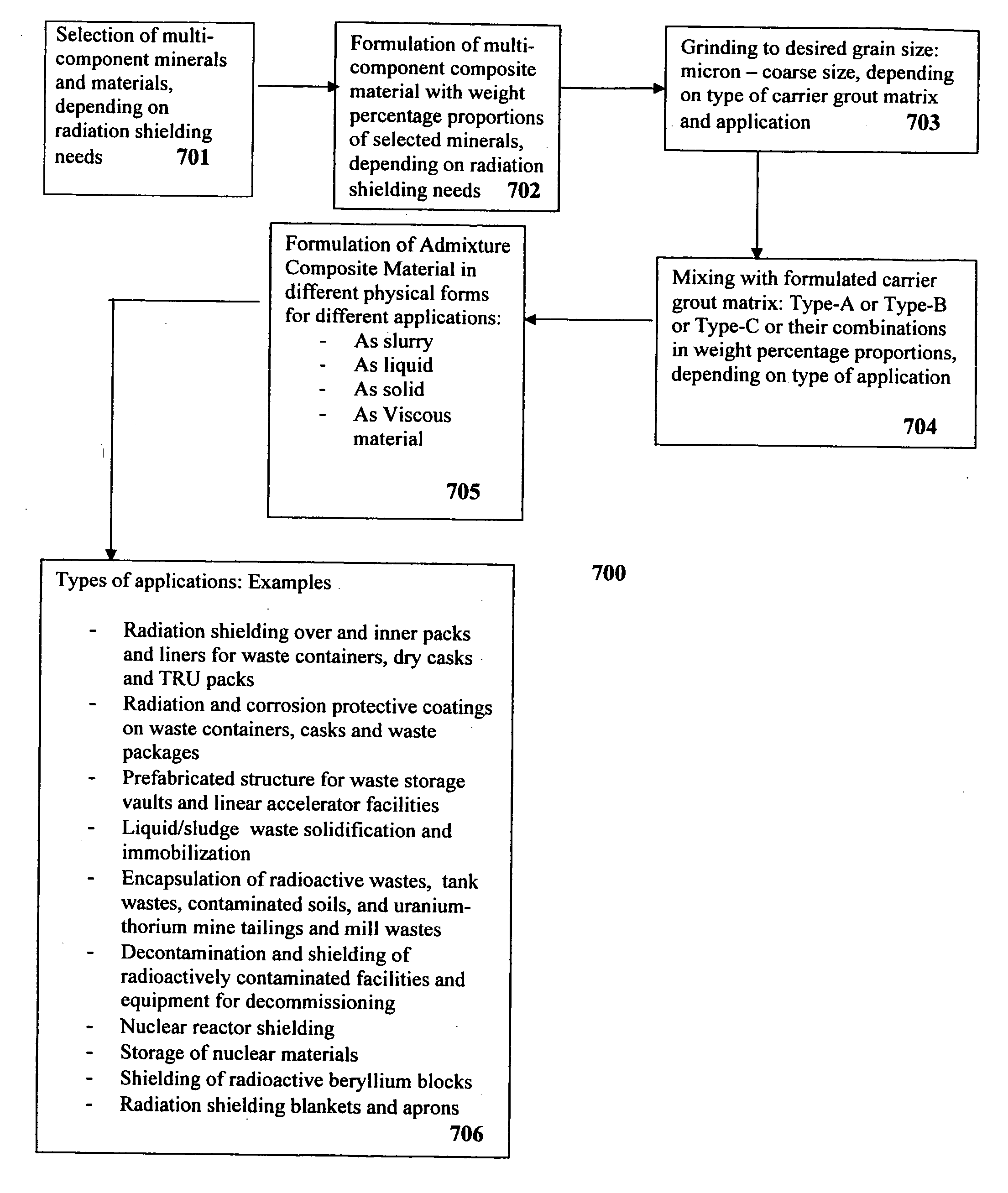
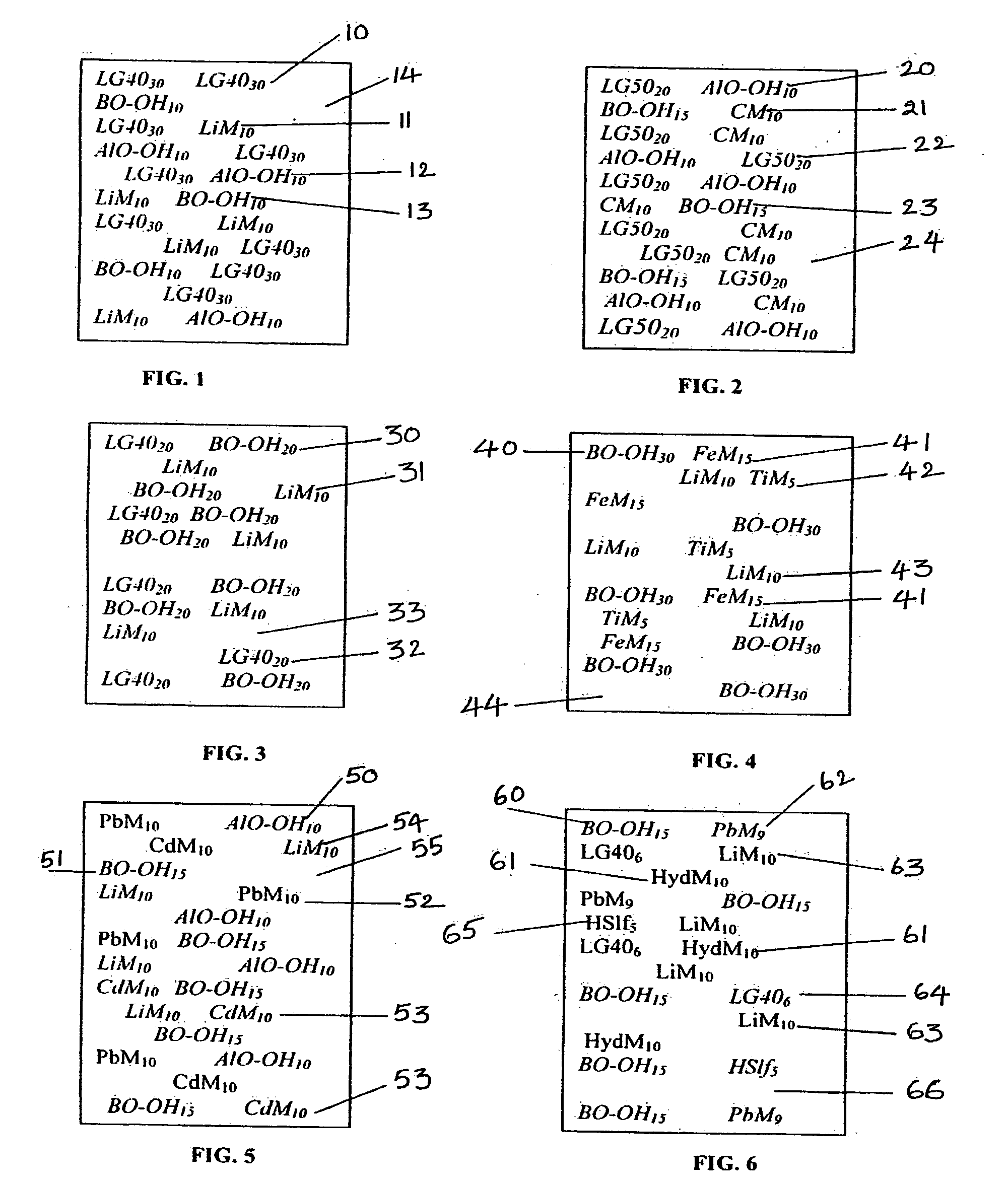
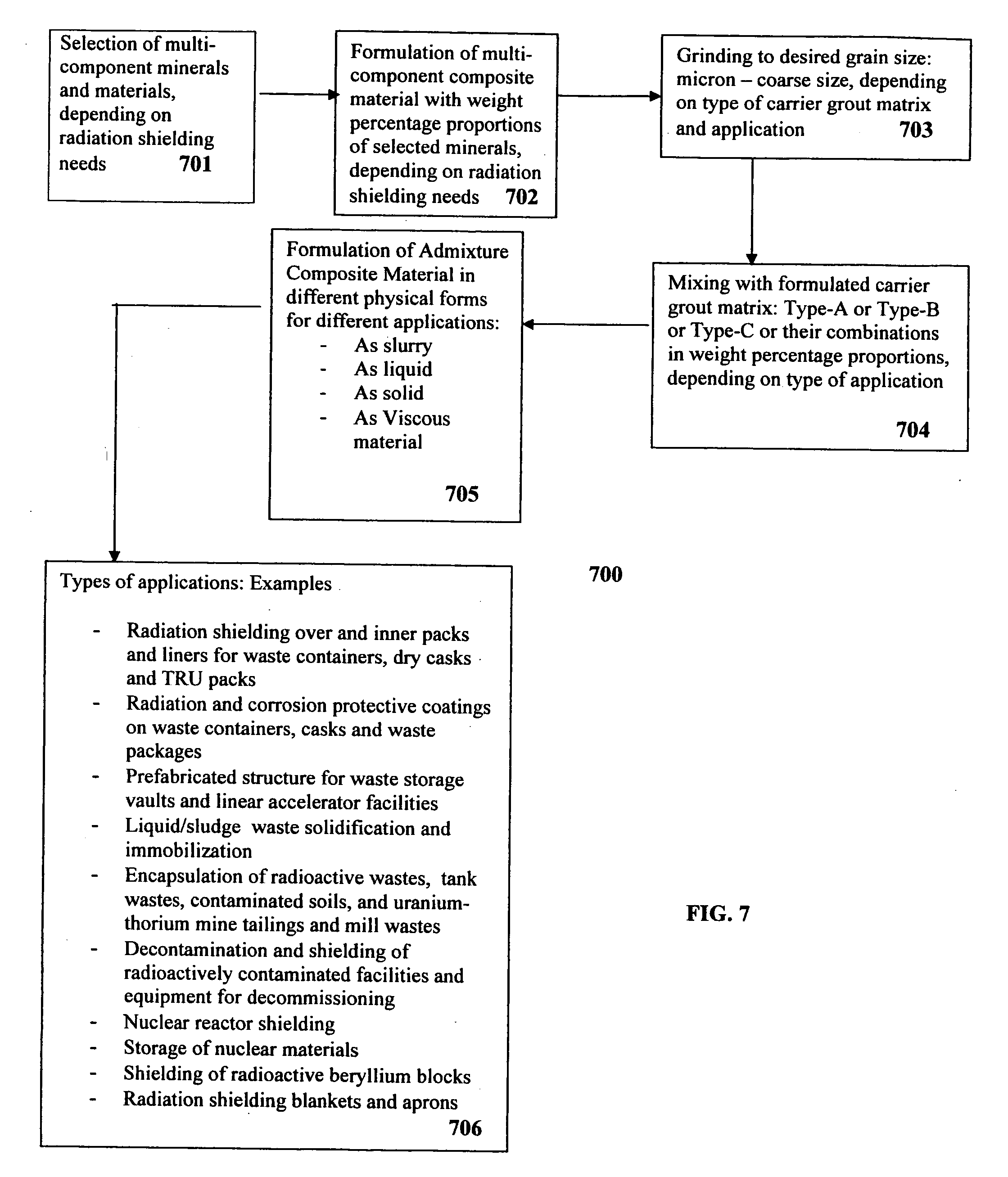
Composite materials and techniques for neutron and gamma radiation shielding
ActiveUS20050258405A1Safe and cost-effective managementIncrease volumeDiffusing elementsNuclear engineering solutionsPolymer modifiedRadioactive waste
This invention deals with multi-component composite materials and techniques for improved shielding of neutron and gamma radiation emitting from transuranic, high-level and low-level radioactive wastes. Selective naturally occurring mineral materials are utilized to formulate, in various proportions, multi-component composite materials. Such materials are enriched with atoms that provide a substantial cumulative absorptive capacity to absorb or shield neutron and gamma radiation of variable fluxes and energies. The use of naturally occurring minerals in synergistic combination with formulated modified cement grout matrix, polymer modified asphaltene and maltene grout matrix, and polymer modified polyurethane foam grout matrix provide the radiation shielding product. These grout matrices are used as carriers for the radiation shielding composite materials and offer desired engineering and thermal attributes for various radiation management applications.
Owner:SAYALA DASHARATHAM
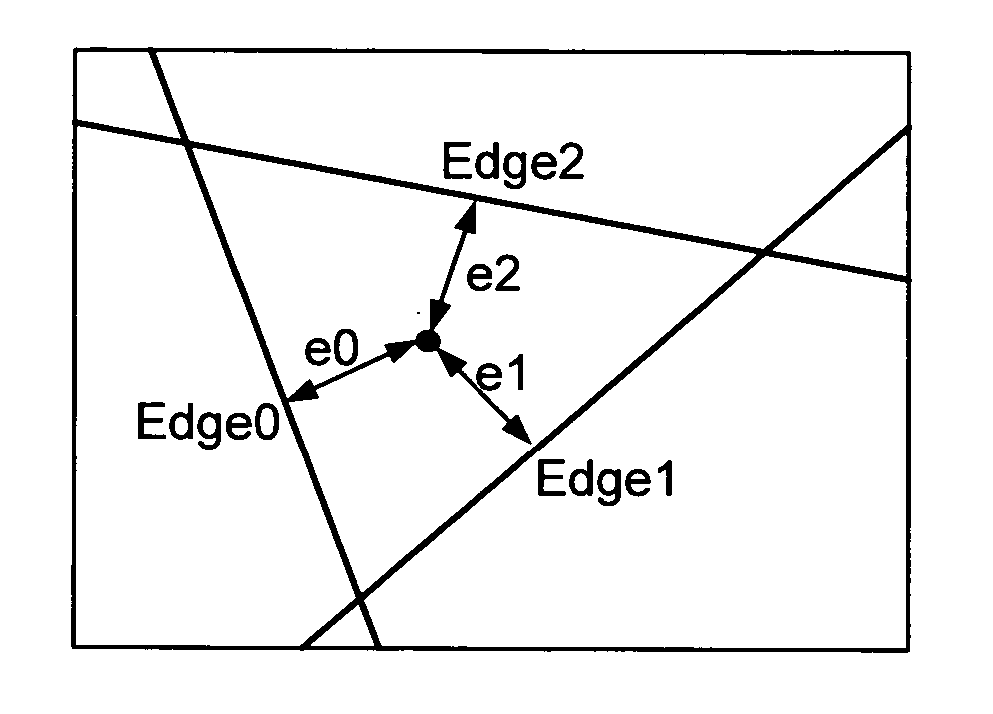
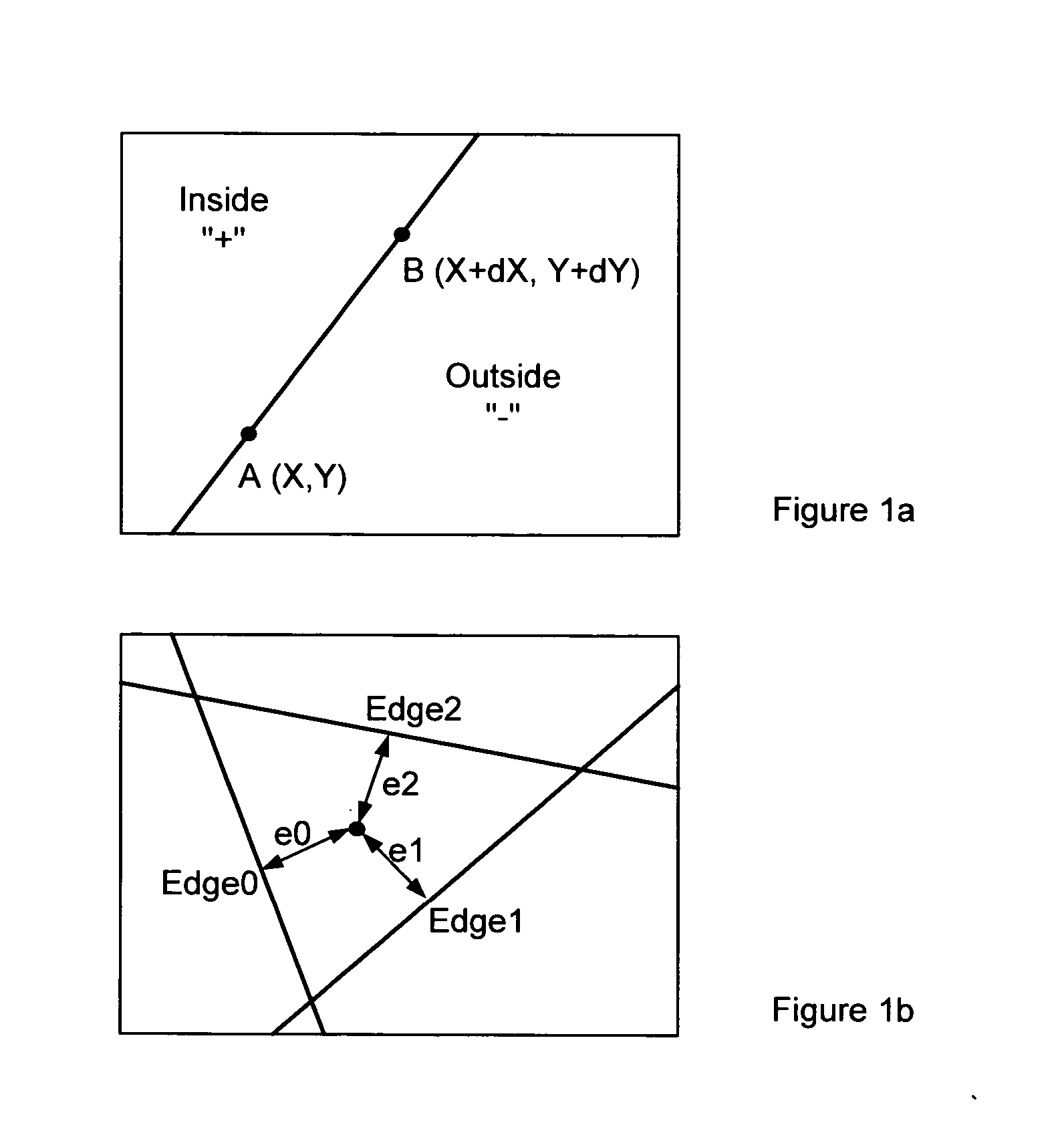
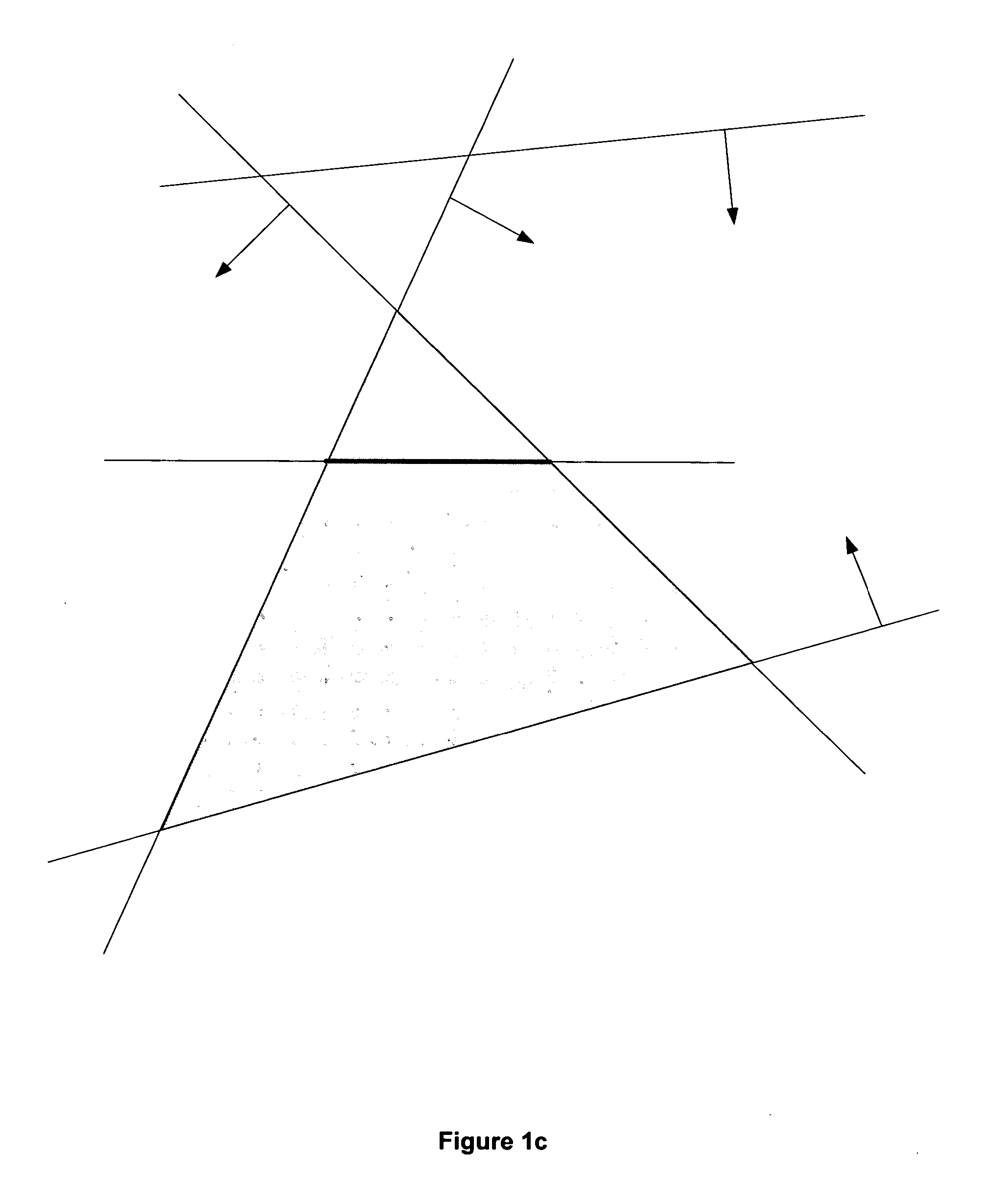
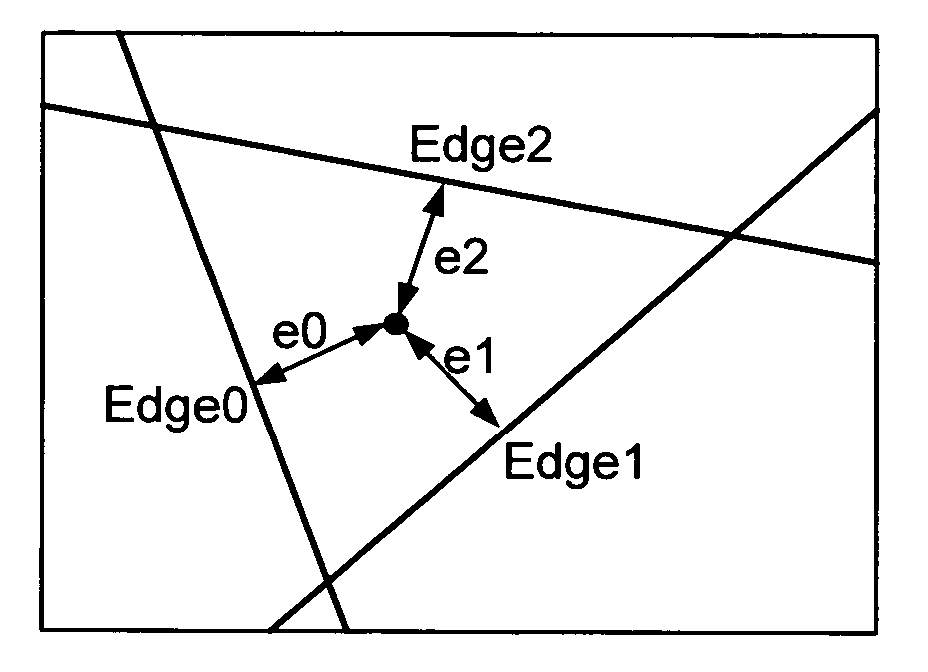
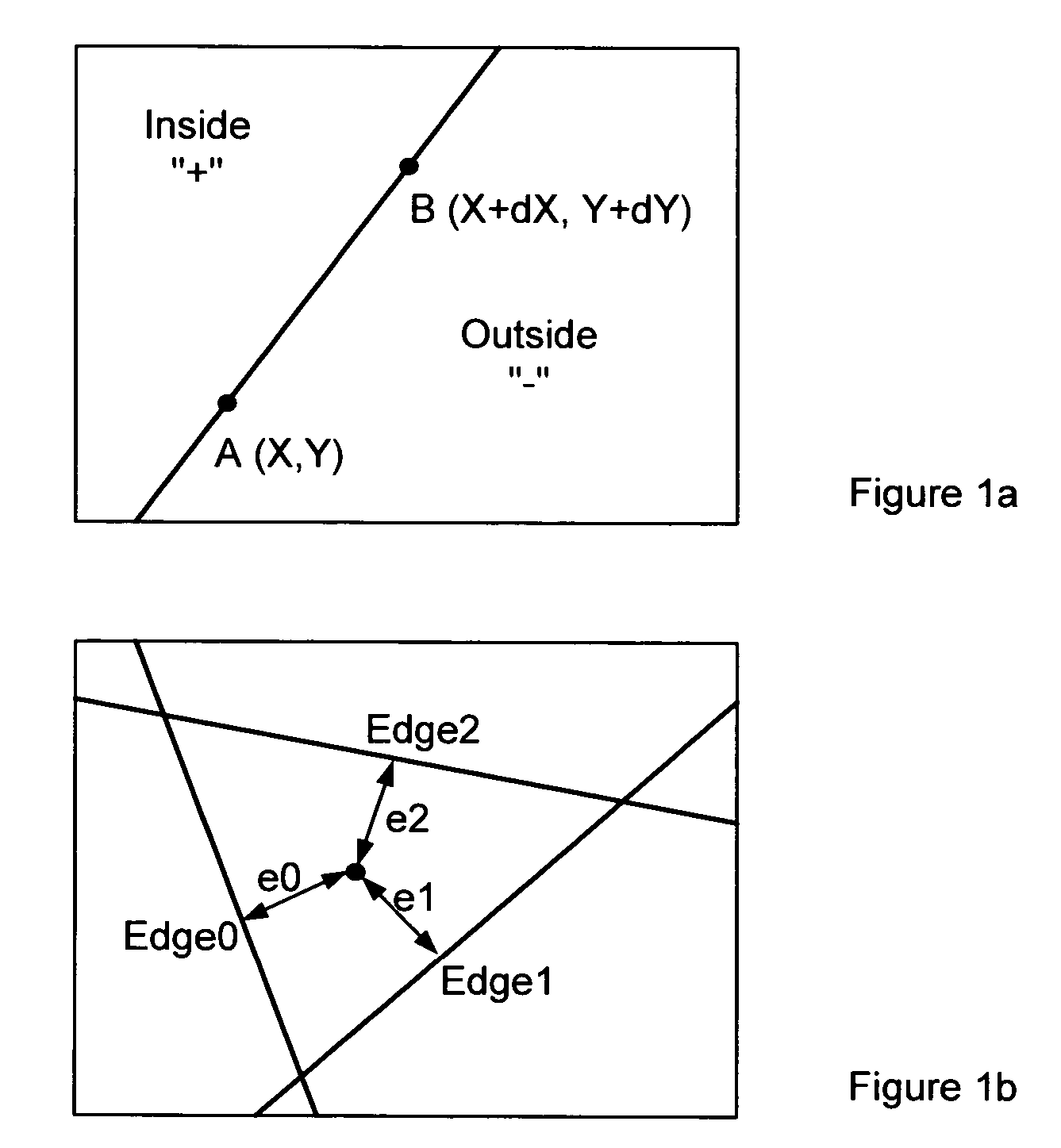
Method and apparatus for triangle rasterization with clipping and wire-frame mode support
ActiveUS20050134603A1Efficient hardware implementationLow-cost high-speedDrawing from basic elementsCathode-ray tube indicatorsHardware implementationsComputer science
A low-cost high-speed programmable rasterizer accepting an input set of functionals representing a triangle, clipping planes and a scissoring box, and producing multiple spans per clock cycle as output. A Loader converts the input set from a general form to a special case form accepted by a set of Edge Generators, the restricted input format accepted by the Edge Generators contributing to their efficient hardware implementation.
Owner:VIA TECH INC
Mandatory access control label security
ActiveUS7831570B2Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsData setData access
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of datasets, each dataset including a plurality of data, and a plurality of database objects, each object having a security label comprising a security classification of the object, at least one database session, the database session having a security label indicating a security classification of the database session, wherein, the database system is operable to allow or deny access to data to a database session based on a security label of a database object and on a security label of the database session.
Owner:ORACLE INT CORP
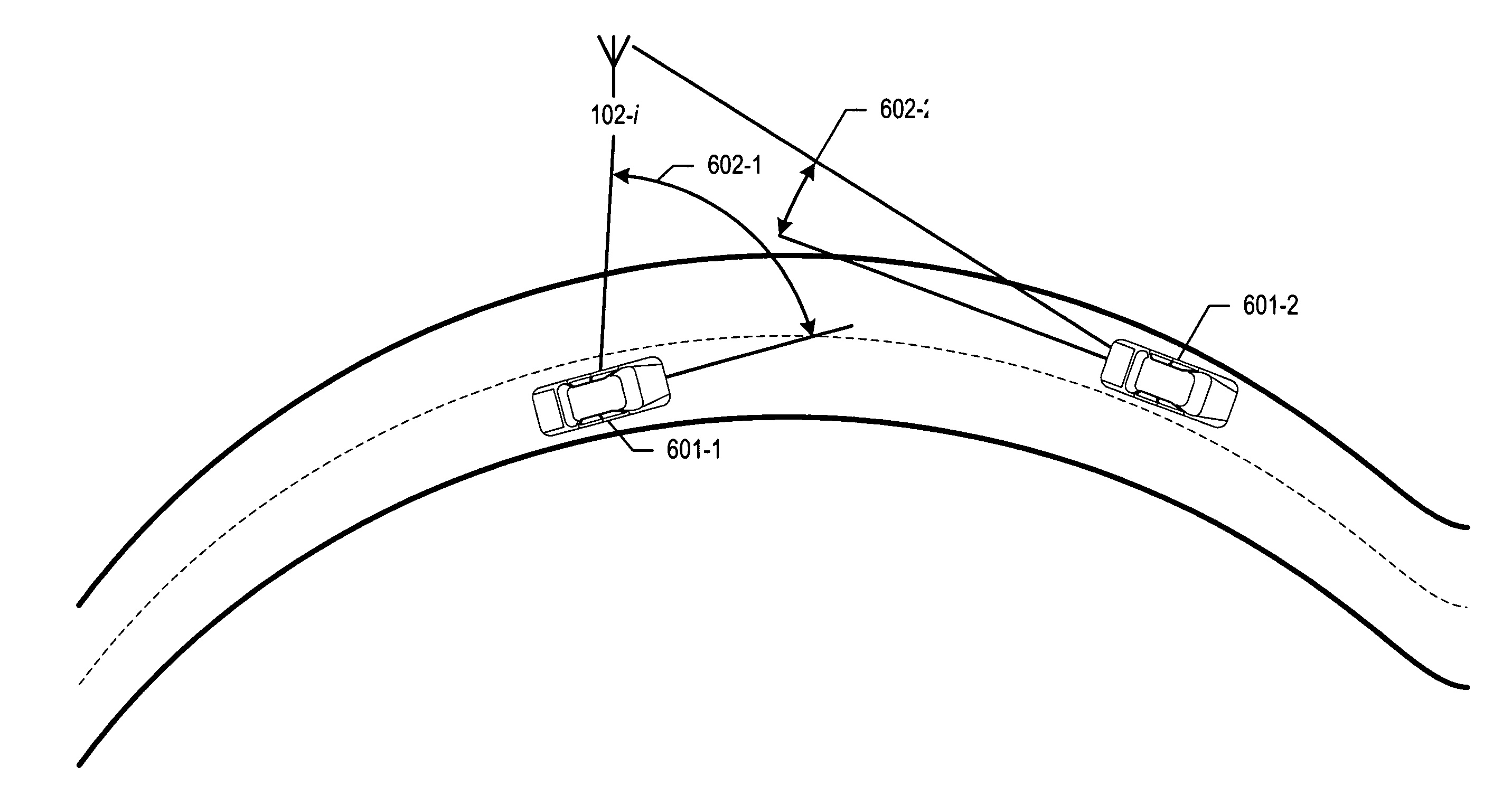
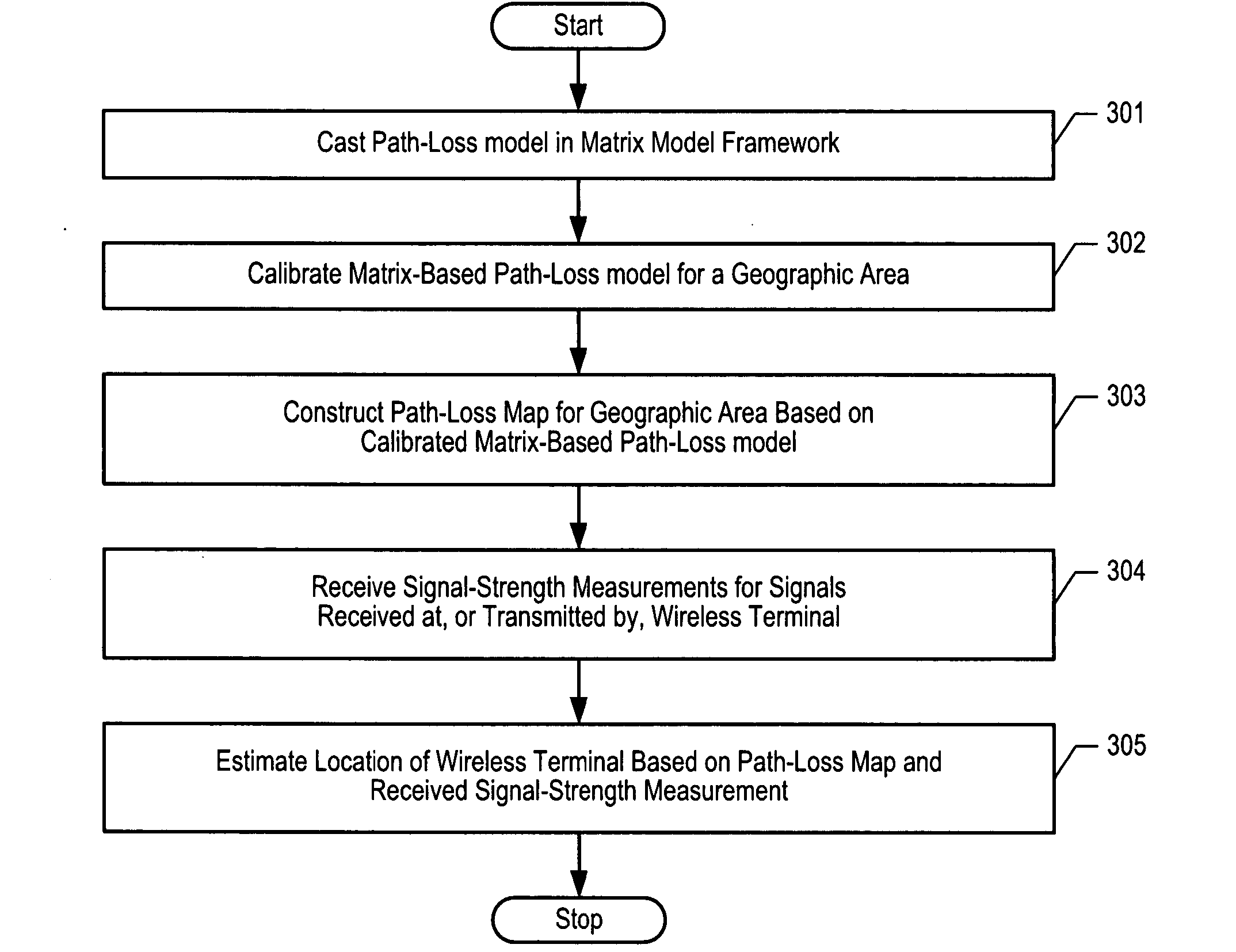
Electro-magnetic propagation modeling
ActiveUS7433652B2Efficient of admissibilityEffective calculationDirection finders using radio wavesTransmission monitoringCommon frameworkData acquisition
A generalized framework is disclosed in which a wide variety of propagation models can be cast in a matrix-based format using arbitrary matrix coefficients. Casting propagation models in the matrix-based framework enables efficient computer implementation and calculation, ease of tuning, admissibility, and aggregating multiple propagation models into a single matrix-based model. Matrix-based propagation models based on transmitter-receiver azimuth orientation, transmitter antenna height, terrain elevation, and clutter are also disclosed. The propagation models can be used in conjunction with automated data acquisition from information sources such as topographic maps, clutter maps, etc.
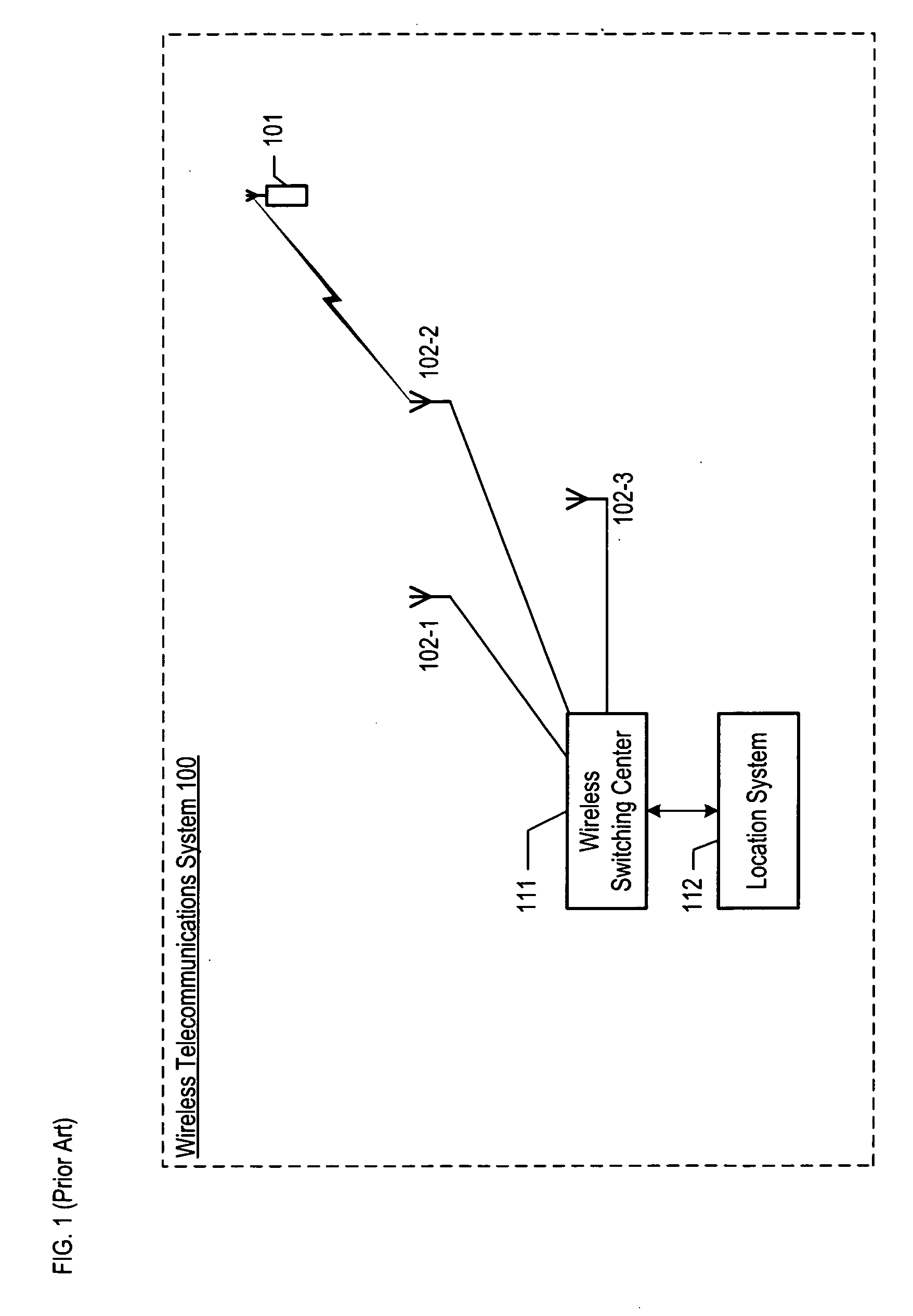
Owner:POLARIS WIRELESS
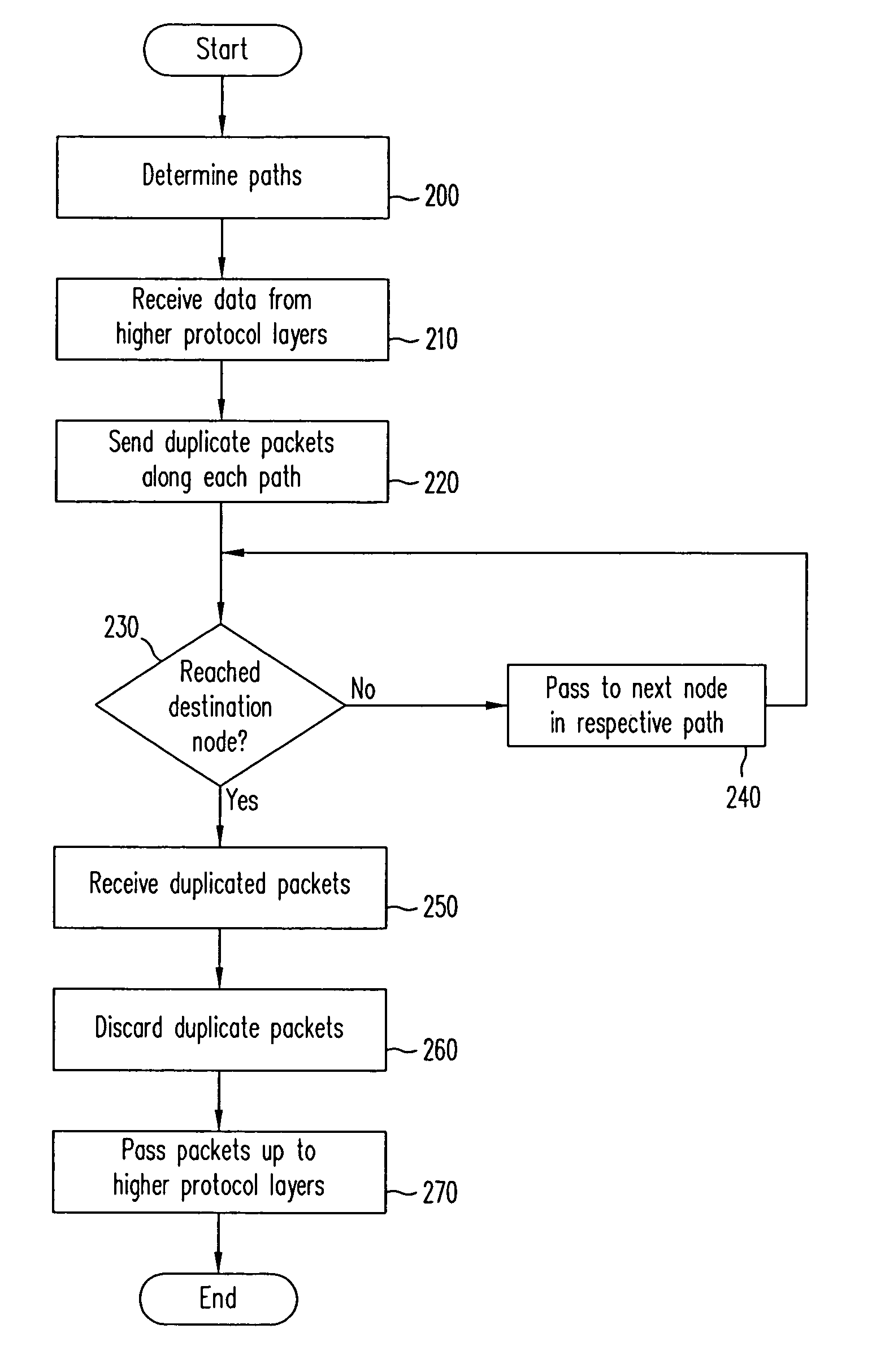
Method and apparatus for uninterrupted packet transfer using replication over disjoint paths
InactiveUS7373543B1Effective maintenanceEnsure effective implementationError preventionTransmission systemsNetwork packetDistributed computing
Owner:CISCO TECH INC
Electro-magnetic propagation modeling
ActiveUS20060199546A1Tuning is slowEfficient of admissibilityDirection finders using radio wavesTransmission monitoringReal arithmeticLinear matrix
A generalized framework is disclosed in which a wide variety of propagation models can be cast in a matrix-based format using arbitrary matrix coefficients (e.g., real numbers, integers, etc.). Casting propagation models in the matrix-based framework enables efficient computer implementation and calculation, ease of tuning, admissibility (i.e., the tuned parameters of a linear matrix model are guaranteed to be the global optimum), and aggregating multiple propagation models into a single matrix-based model. Matrix-based propagation models based on transmitter-receiver azimuth orientation, transmitter antenna height, terrain elevation, and clutter are also disclosed. The propagation models can be used in conjunction with automated data acquisition from information sources such as topographic maps, clutter maps, etc.
Owner:POLARIS WIRELESS
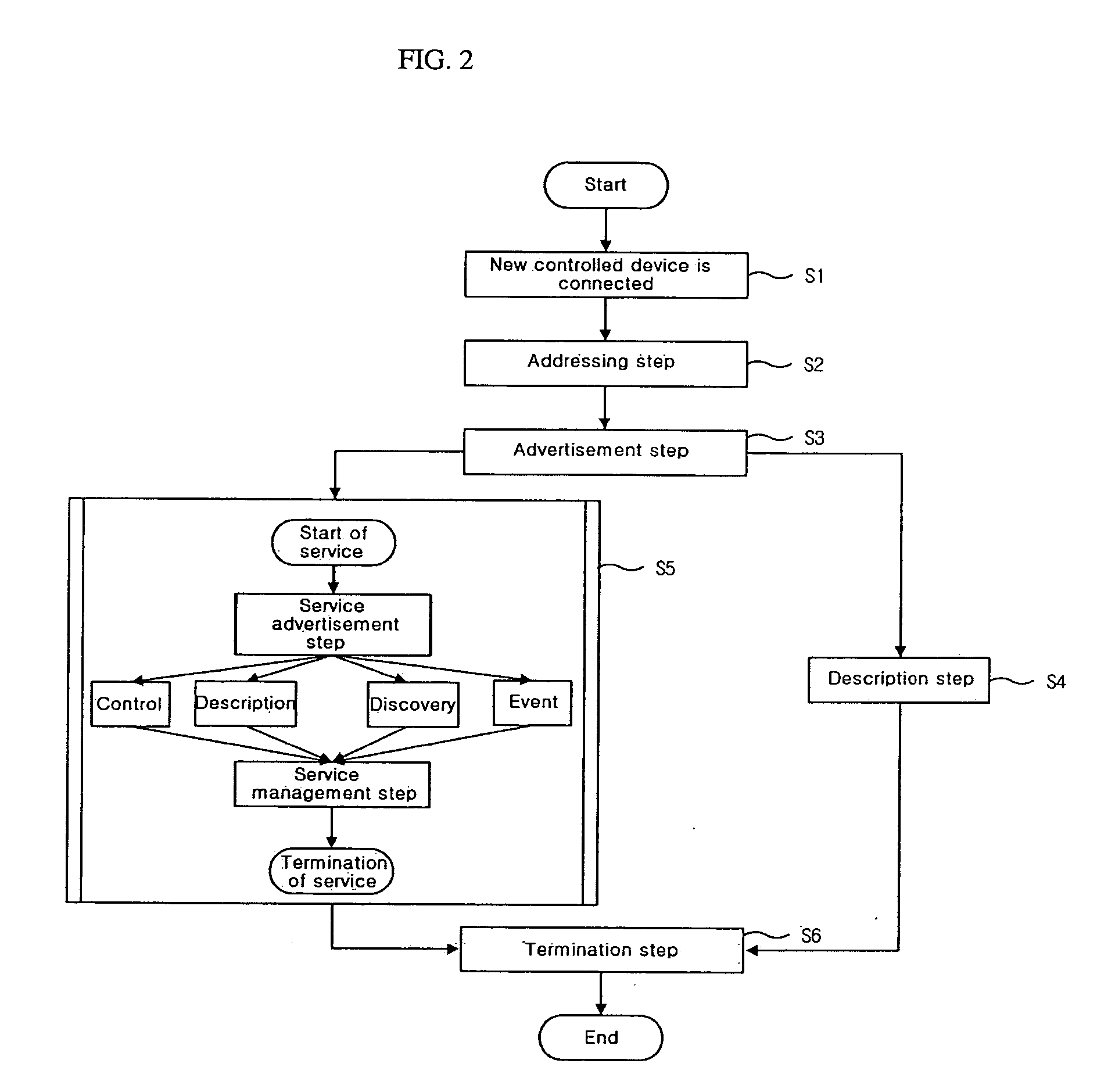
Home network apparatus and system for cooperative work service and method thereof
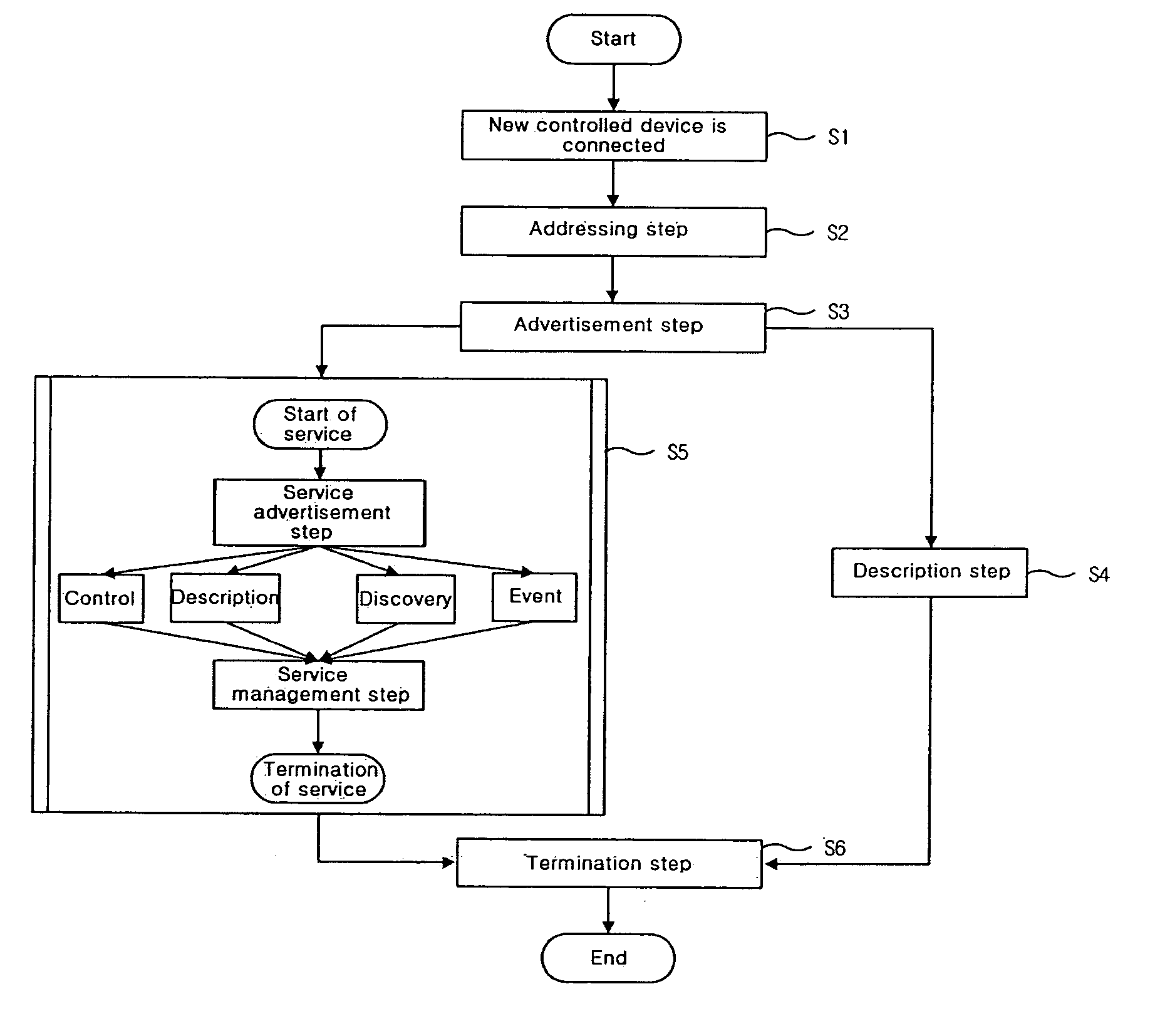
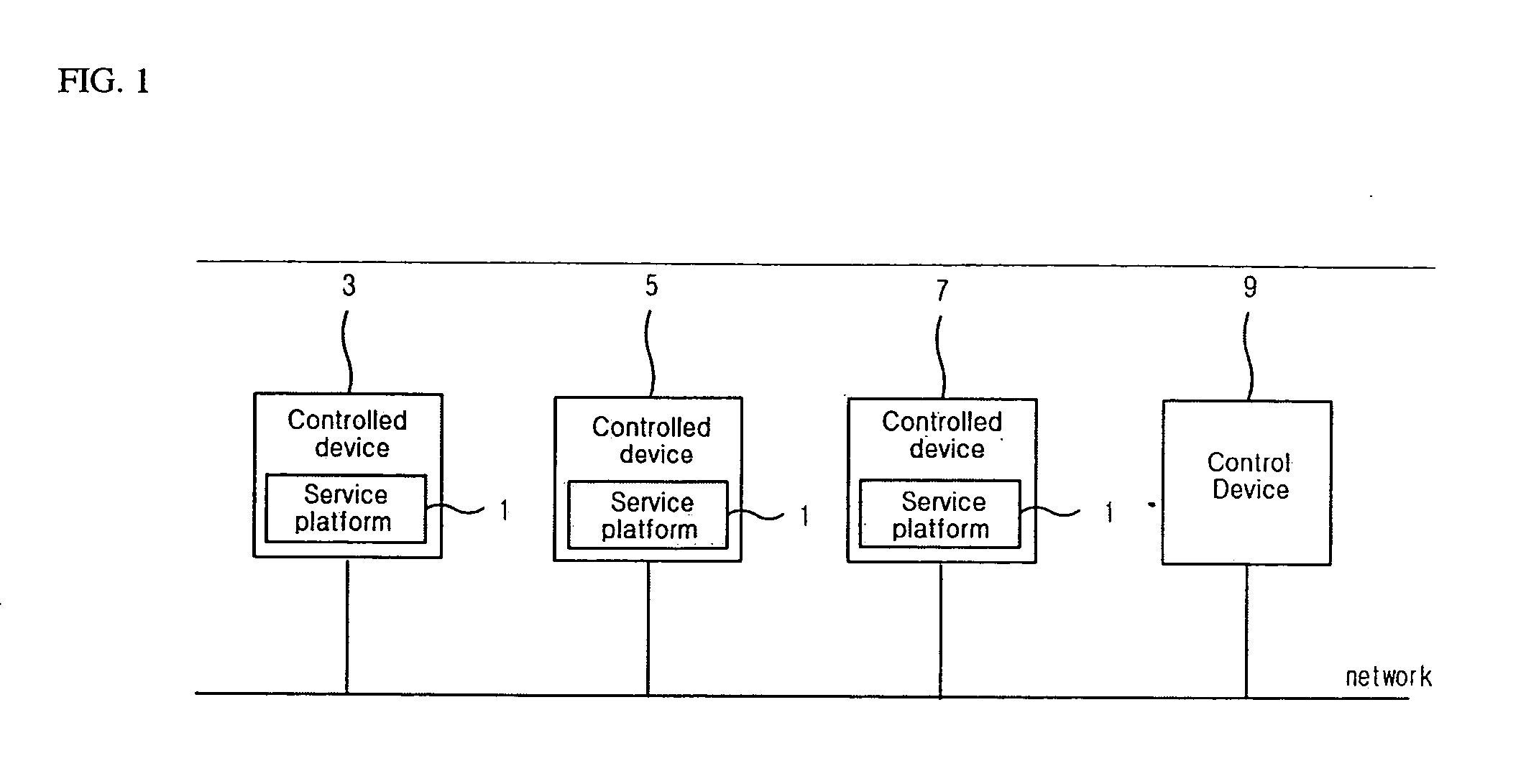
InactiveUS20050021714A1Efficiently defineEnsure effective implementationTelemetry/telecontrol selection arrangementsData processing applicationsCooperative workDirect execution
A home network system and method for providing cooperative work services. The home network system has a plurality of devices connected to a network, a negotiator module connected to the devices for determining cooperative work service roles of the devices by applying device descriptions collected from the devices to a predetermined election algorithm so that the cooperative work service can be performed in consideration of a function of a corresponding device, and a coordinator module for directly performing a control command transmitted from a control device according to the cooperative work service roles determined by the negotiator module.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for triangle rasterization with clipping and wire-frame mode support
ActiveUS7551174B2Ensure effective implementationDrawing from basic elementsCathode-ray tube indicatorsHardware implementationsComputer science
A low-cost high-speed programmable rasterizer accepting an input set of functionals representing a triangle, clipping planes and a scissoring box, and producing multiple spans per clock cycle as output. A Loader converts the input set from a general form to a special case form accepted by a set of Edge Generators, the restricted input format accepted by the Edge Generators contributing to their efficient hardware implementation.
Owner:VIA TECH INC
Mandatory access control base
ActiveUS7593942B2Ease of administrationEnsure effective implementationComputer security arrangementsSpecial data processing applicationsData accessDatabase security
Owner:ORACLE INT CORP
Method and apparatus for estimating delay and jitter between many network routers using measurements between a preferred set of routers
InactiveUS6912203B1Lower requirementReduce traffic overheadError preventionFrequency-division multiplex detailsNetwork routerReal-time computing
A method and apparatus for determining a network performance metric in a network is described. The network includes a number of network elements and a number of links. Each of the network elements is coupled to at least one other of the network elements by at least one of the links. The method includes forming a first set of network element pairs, ordering a first number of network element pairs, forming a second set of network element pairs, measuring a measured network performance metric between a first network element pair and computing a computed network performance metric.
Owner:CISCO TECH INC
Cross-domain security for data vault
ActiveUS8732856B2Ease of administrationEnsure effective implementationDigital data processing detailsAnalogue secracy/subscription systemsDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system communicatively connected to a plurality of network domains, each network domain having a level of security, the database system comprises at least one database accessible from all of the plurality of network domains, the database comprising data, each unit of data having a level of security and access control security operable to provide access to a unit of data in the database to a network domain based on the level of security of the network domain and based on the level of security of the unit of data.
Owner:ORACLE INT CORP
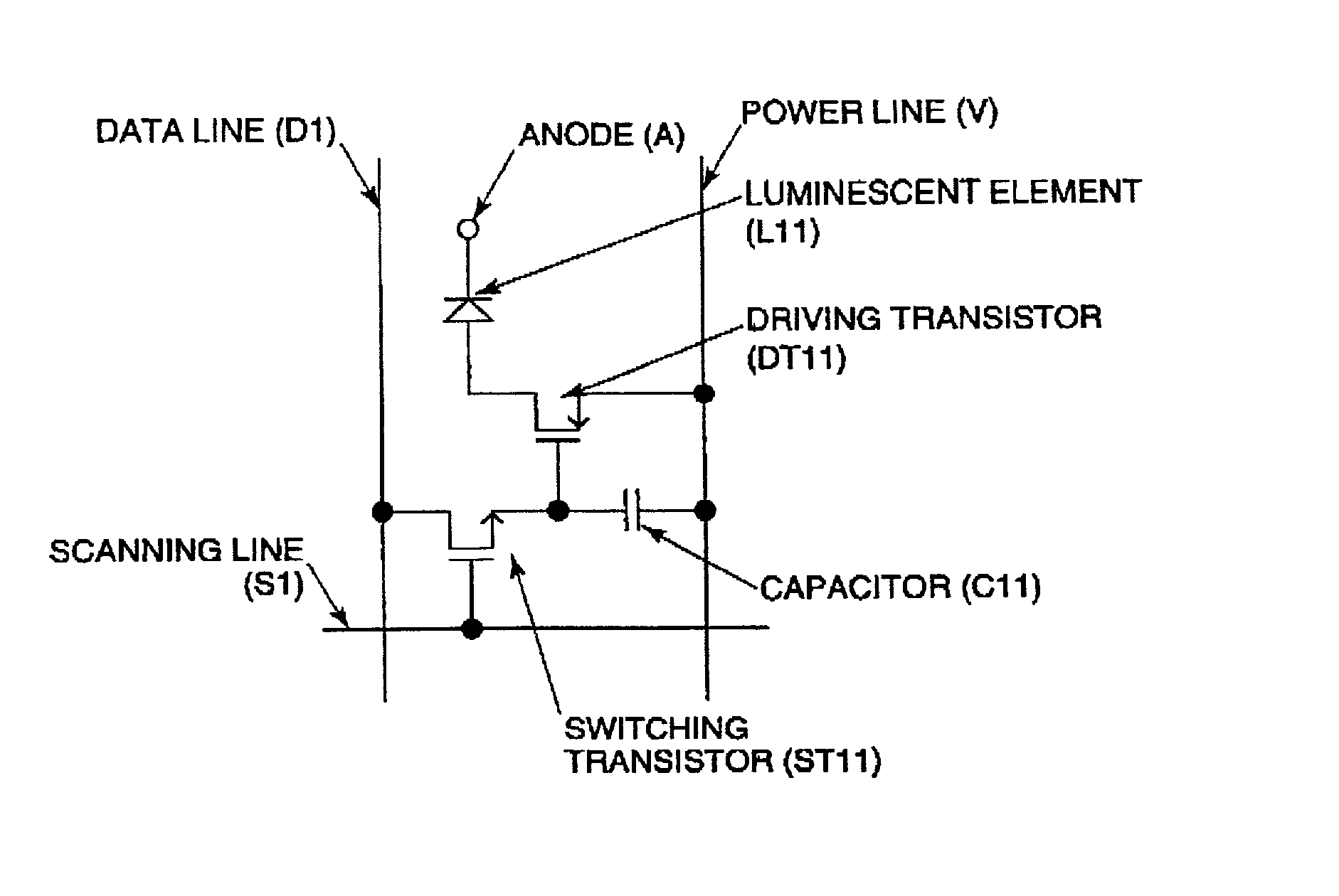
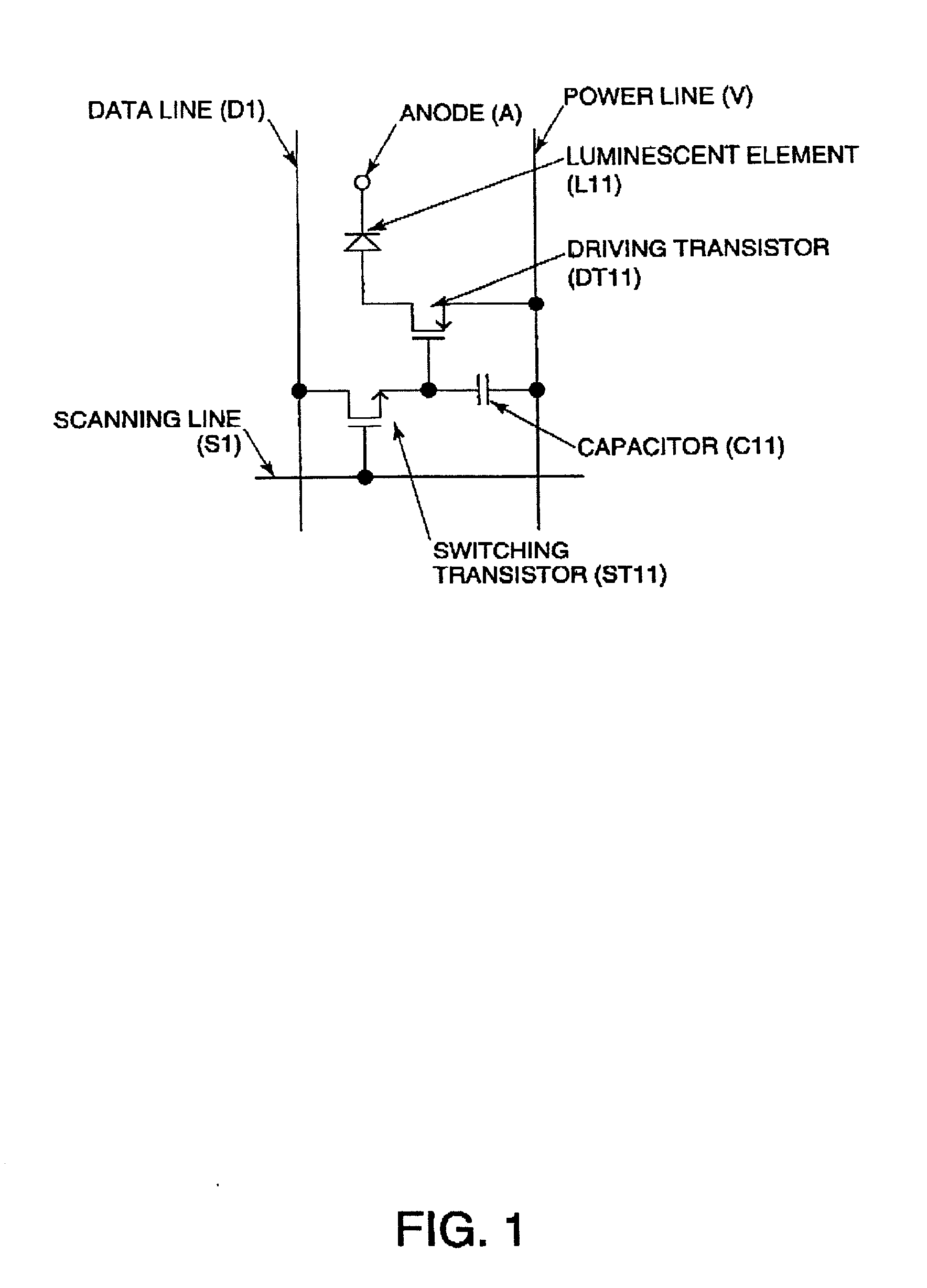
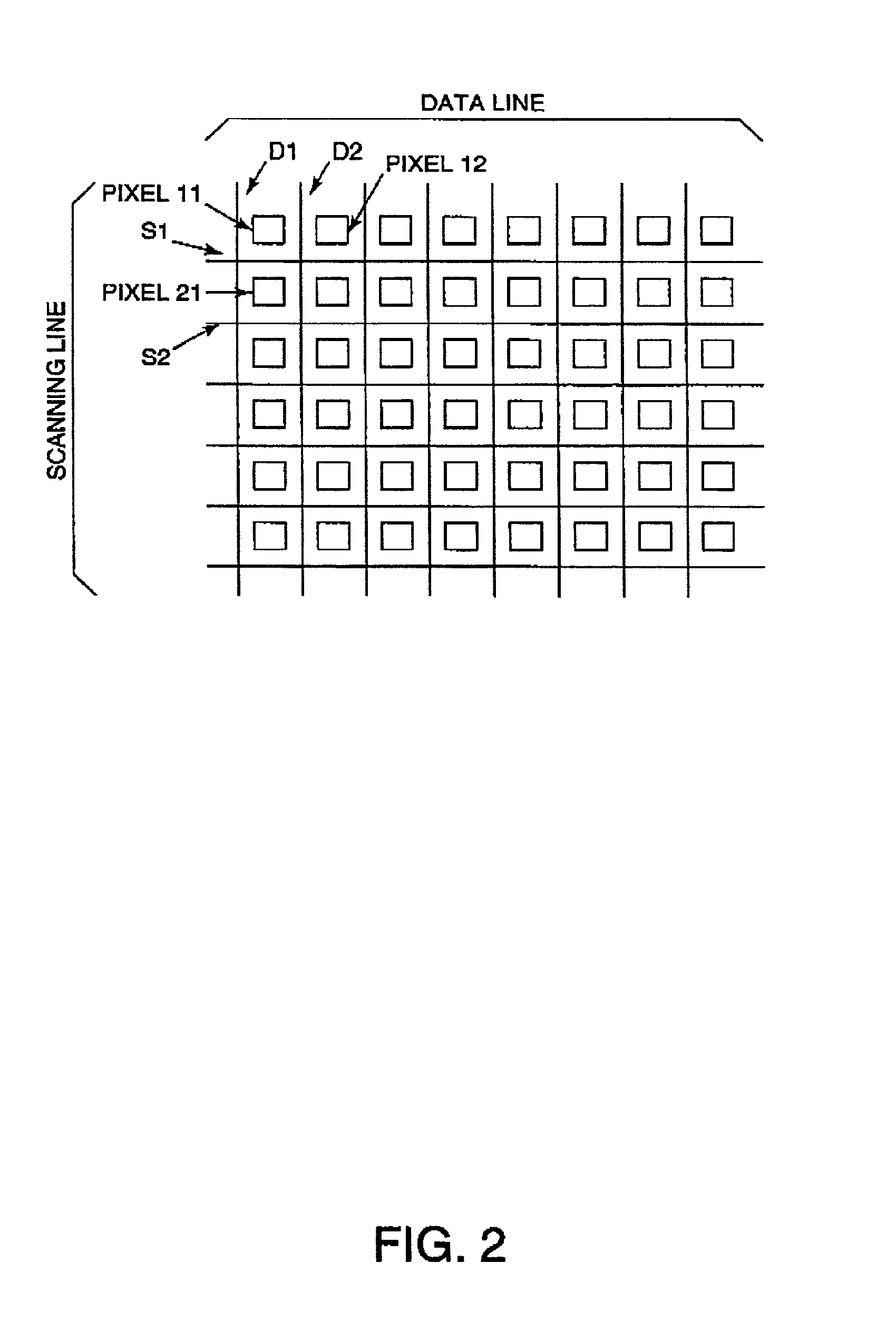
Driving method for electro-optical device, electro-optical device, and electronic apparatus
InactiveUS20020044109A1Ensure effective implementationReduce power consumptionSolid-state devicesCathode-ray tube indicatorsTime ratioTransistor
To provide a method for implementing a multi-level display of an electro-optical device according to a time ratio gray-scale method without providing resetlines. In an electro-optical device comprising, at an intersection of a scanning line and a data line, an electro-optical element, a driving transistor for driving the electro-optical element, and a switching transistor for controlling the driving transistor, a gray-scale is obtained by performing a plurality of set-reset operations, each set-reset operation comprising: a setting step of supplying an on-signal to the switching transistor via the scanning lines, and of supplying a set signal for selecting a conducting state or a non-conducting state of the driving transistor to the driving transistor via the data line and the switching transistor in accordance with the one signal; and a resetting step of supplying an on-signal to the switching transistor via the scanning line, and of supplying a reset signal for selecting the non-conducting state of the driving transistor to the driving transistor via the data line and the switching transistor in accordance with the one signal.
Owner:BOE TECH GRP CO LTD
Damage-tolerance testing method for lower wall panel of airplane outboard wing
InactiveCN101561459AEase of implementationGuarantee authenticityCurrent/voltage measurementTechnical supportAirplane
The invention pertains to airplane fatigue and damage-tolerance testing technologies, and relates to a damage-tolerance testing method for a lower wall panel of an airplane outboard wing. The method comprises the steps of: (I) fabricating a test part, (II) conducting a test and (III) calculating finite element. The method considers test room and technique conditions in the design of the test part and utilizes the test part with simple structure to reflect the complicated structure of the lower wall panel, thereby not only ensuring the realness of a load path and structural characteristics, but also being beneficial to the easy implementation of the test; when cracks are prefabricated, the damage of single part as well as the damage of a plurality of parts are considered, thereby being beneficial to the study of the lower wall panel with widely distributed damage; finite element software is used for conducting comparison analysis and calculating a variation curve with crack propagation of an overall correction factor; comparison analysis is conducted to a convex plate; the method is perfected by combining with testing results; and a correction factor of the finite element method is given, thus providing technical support for the damage tolerance analysis of the part.
Owner:XIAN AIRCRAFT DESIGN INST OF AVIATION IND OF CHINA
Method for discovering congestion points, congestion lines and congestion areas based on composite network
ActiveCN108109382AReduce the amount of calculation dataEasy to handleParticular environment based servicesDetection of traffic movementNetwork structureOperability
The invention belongs to the field of traffic condition prediction, and relates to a method for discovering congestion points, congestion lines and congestion areas based on a composite network. The composite network in the method is composed of two or more sub networks and connecting edges between the sub networks. The sub networks are independent networks constituting the composite network. Thecomposite network includes an intersection network and a sensor network. The sensor network takes traffic sensors at intersections as nodes, and the sensors are related by connecting edges. The intersection network takes intersections as nodes, and connecting edges are established according to whether the intersections can be connected. On the basis of the intersection network, the definitions ofa congestion index, a congestion point, a congestion line and a congestion area are given. Calculation is carried out based on the network structure. The method specifically comprises the steps as follows: first, defining a congestion index Ti, a congestion point, a congestion line and a congestion area; then, quantifying the congestion level; and finally, analyzing and calculating congestion points, congestion lines and congestion areas. The method is designed ingeniously, has good operability and practicability, and has a wide market prospect.
Owner:QINGDAO UNIV
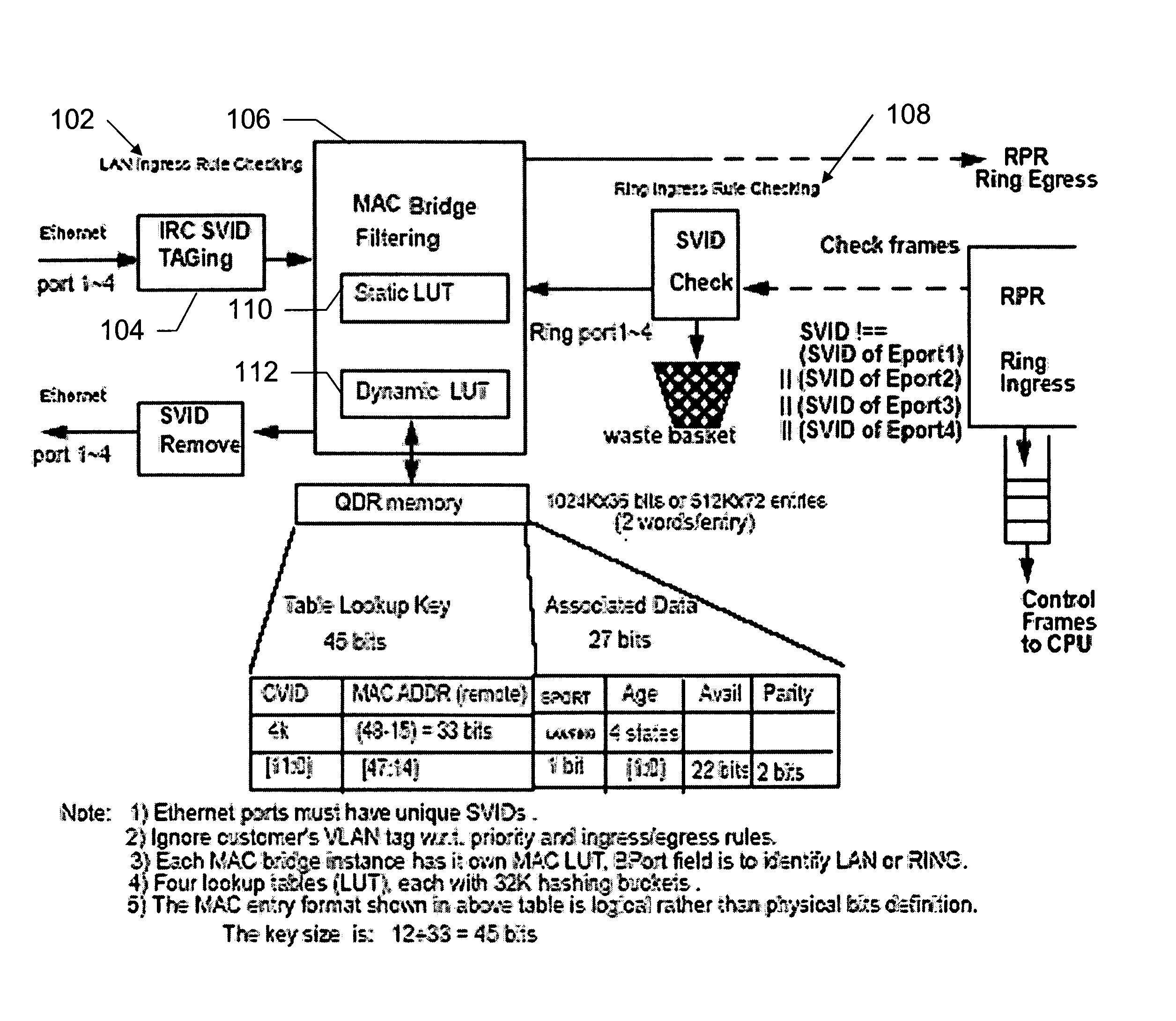
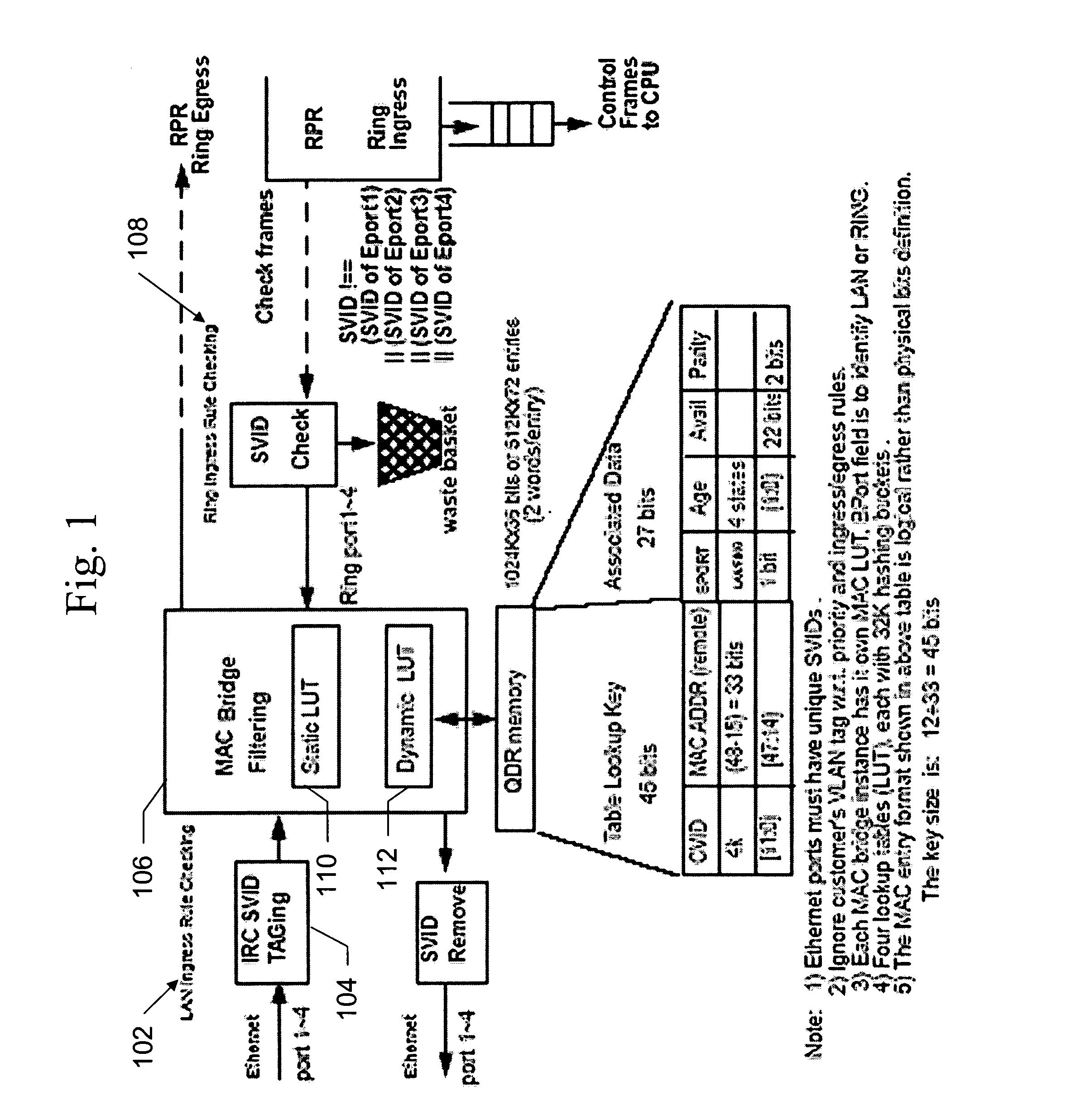
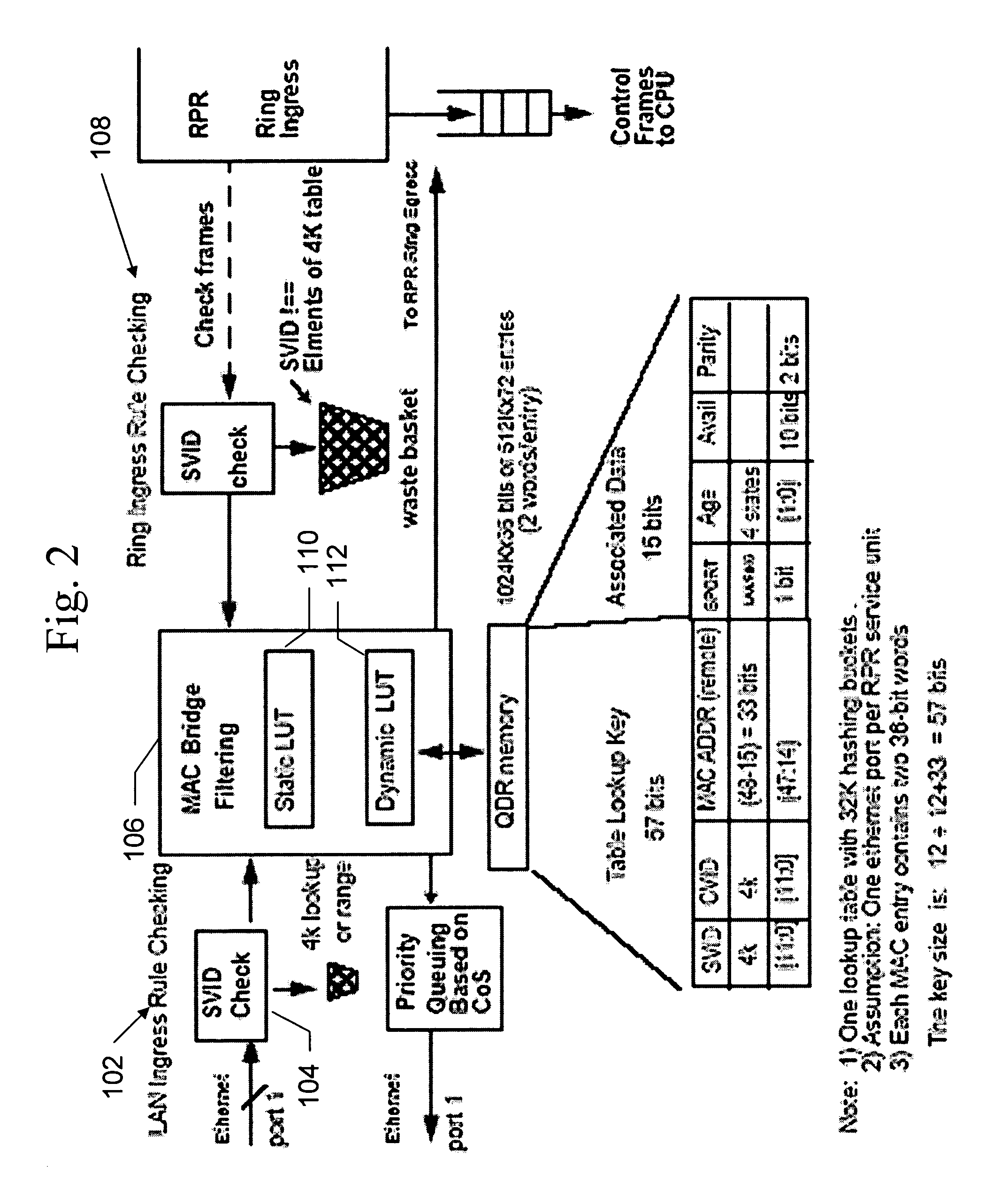
Using CRC-15 as hash function for MAC bridge filter design
InactiveUS20070071015A1Reduce overflowReduce equipment costsData switching by path configurationComputer hardwareHash function
A hash function for a MAC bridge filter that improves bridge performance by reducing overflow of the MAC bridge database and which reduces cost of the device by using relatively few hardware resources. A CRC hash function is used to randomize the search string in the MAC bridge filter so that a consistent bridge performance is achieved regardless of where the bridge is used. Using the CRC as a hash function also results in efficient hardware implementation. In addition, the present invention may be generalized to use a CRC-M as hash function for any bridge filter design.
Owner:FUJITSU LTD
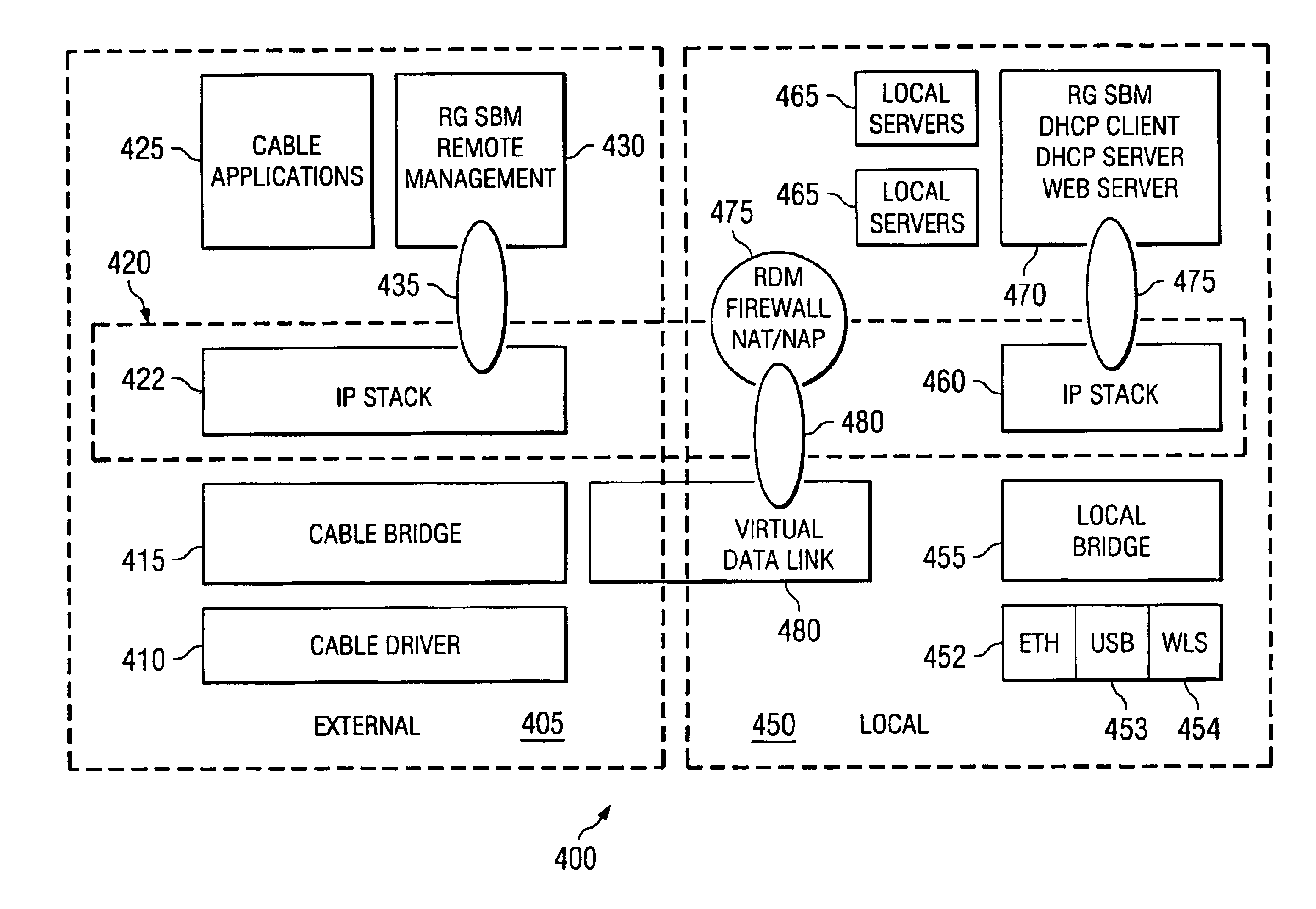
System and method for efficiently processing broadband network traffic
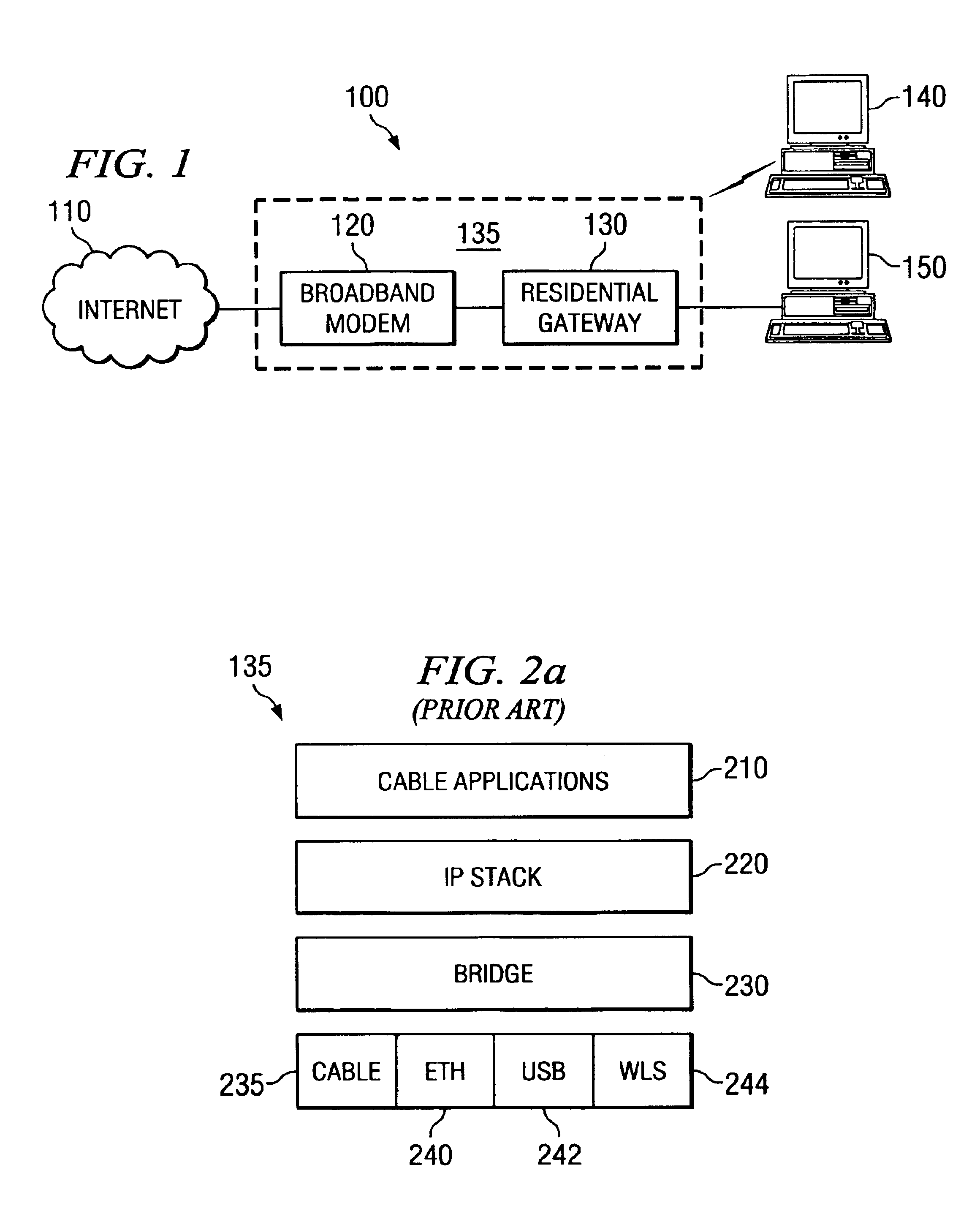
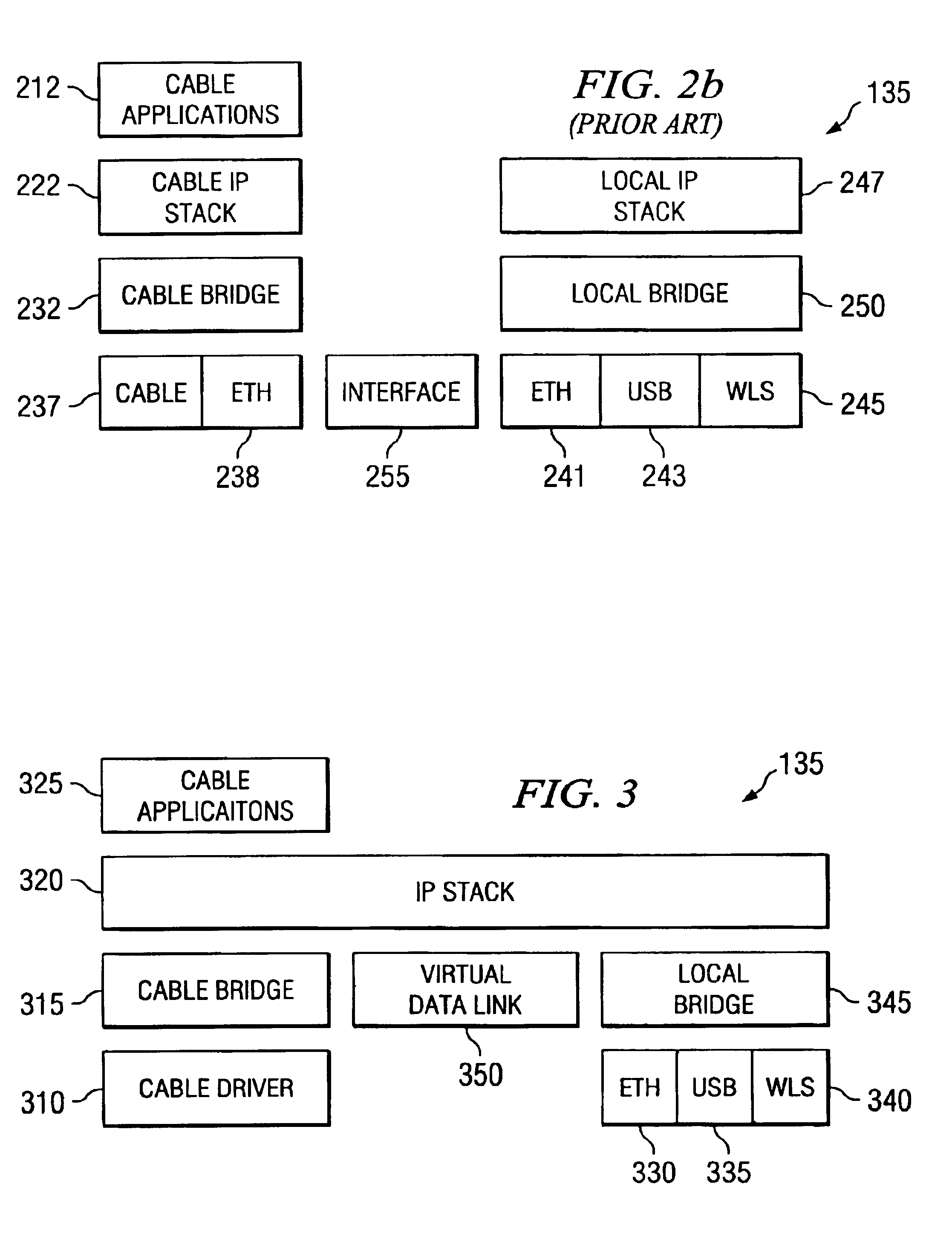
ActiveUS6944706B2Simplifies jobSimple designBroadband local area networksMultiple digital computer combinationsTraffic volumeBroadband networks
A broadband gateway 135 that combines a broadband modem 120 and a residential gateway 130 in a single unit. The single unit features a unique dual bridge, shared module architecture that reduces redundancy in the broadband gateway 135 at the same time it minimizes interactions between modules in the broadband gateway 135. This minimized interaction permits the broadband gateway 135 to operate at peak efficiency and allows for continued development of portions of the broadband gateway 135 without necessarily incurring compliance testing for the broadband portion of the broadband gateway 135.
Owner:TEXAS INSTR INC
Dynamic auditing
ActiveUS7814075B2Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of database objects, each database object having a level of security, a plurality of factors, each factor representing a characteristic of a user of the database system, at least one database session of the user in the database, the database session having a level of security, the user connected to the database with a network domain, each network domain having a level of security, wherein the database system is operable to grant or deny access to the data to a user based on the factors associated with the user, based on the level of security of the data, based on the level of security of the database session, and based on the level of security of the network domain.
Owner:ORACLE INT CORP
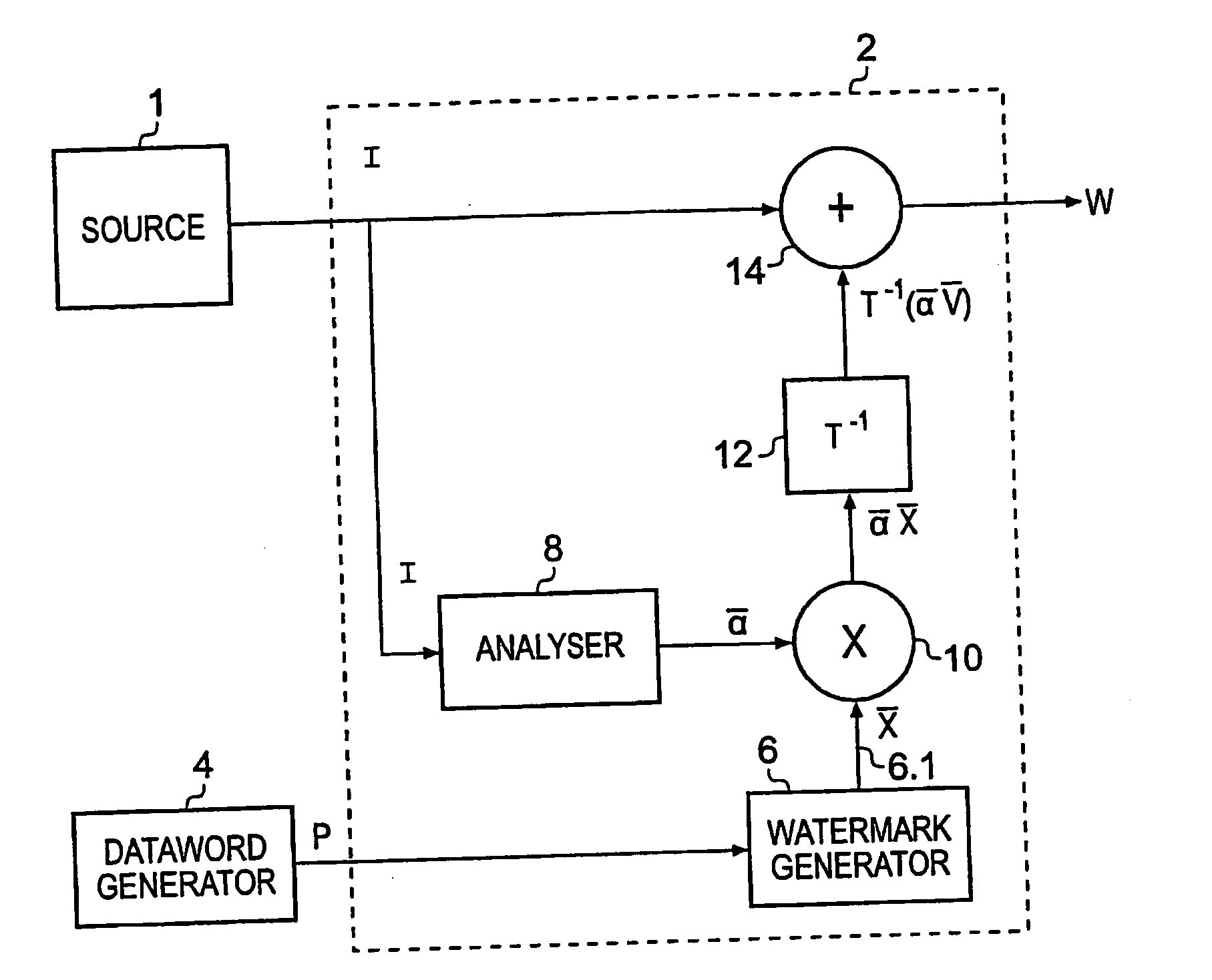
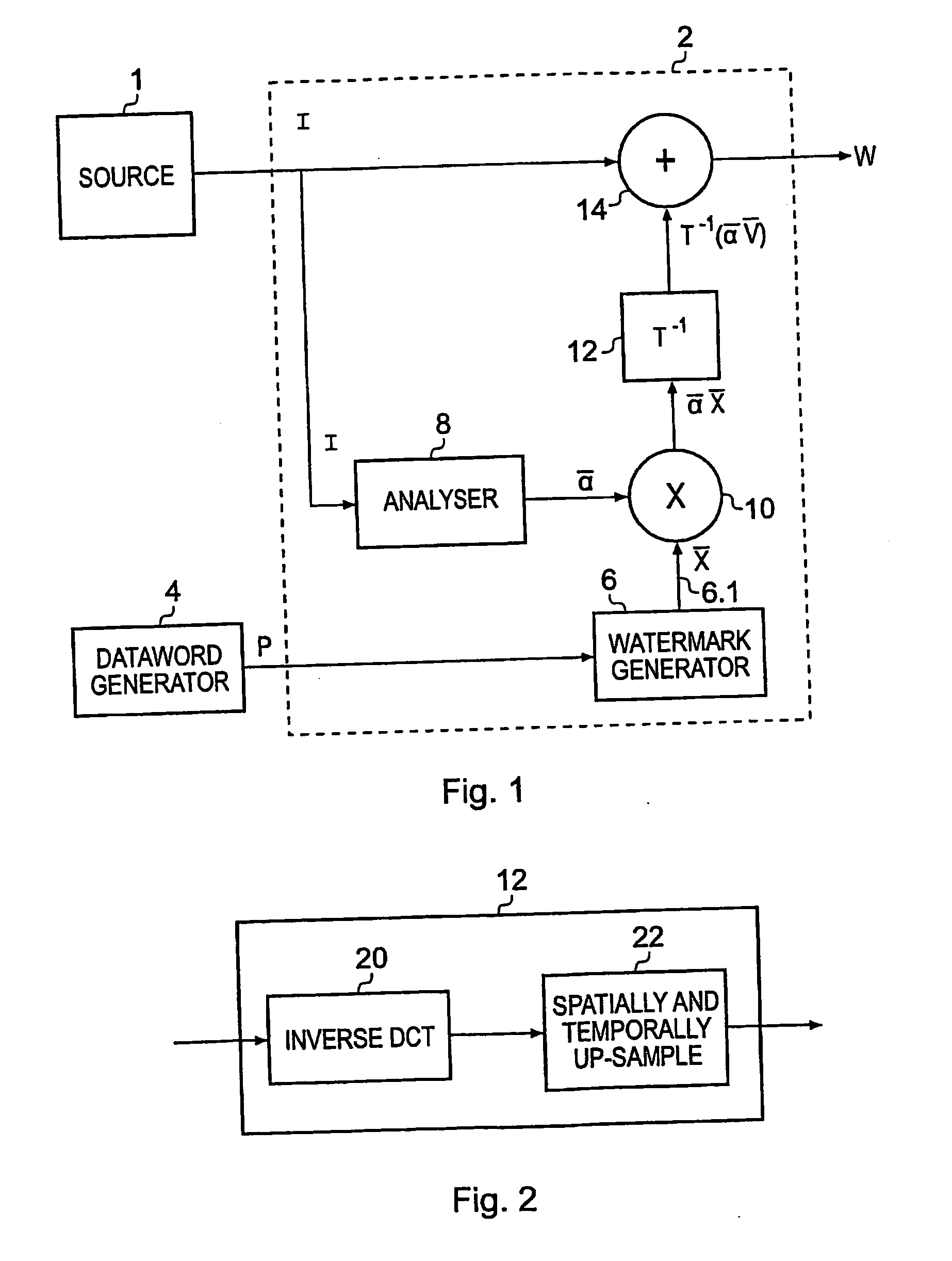
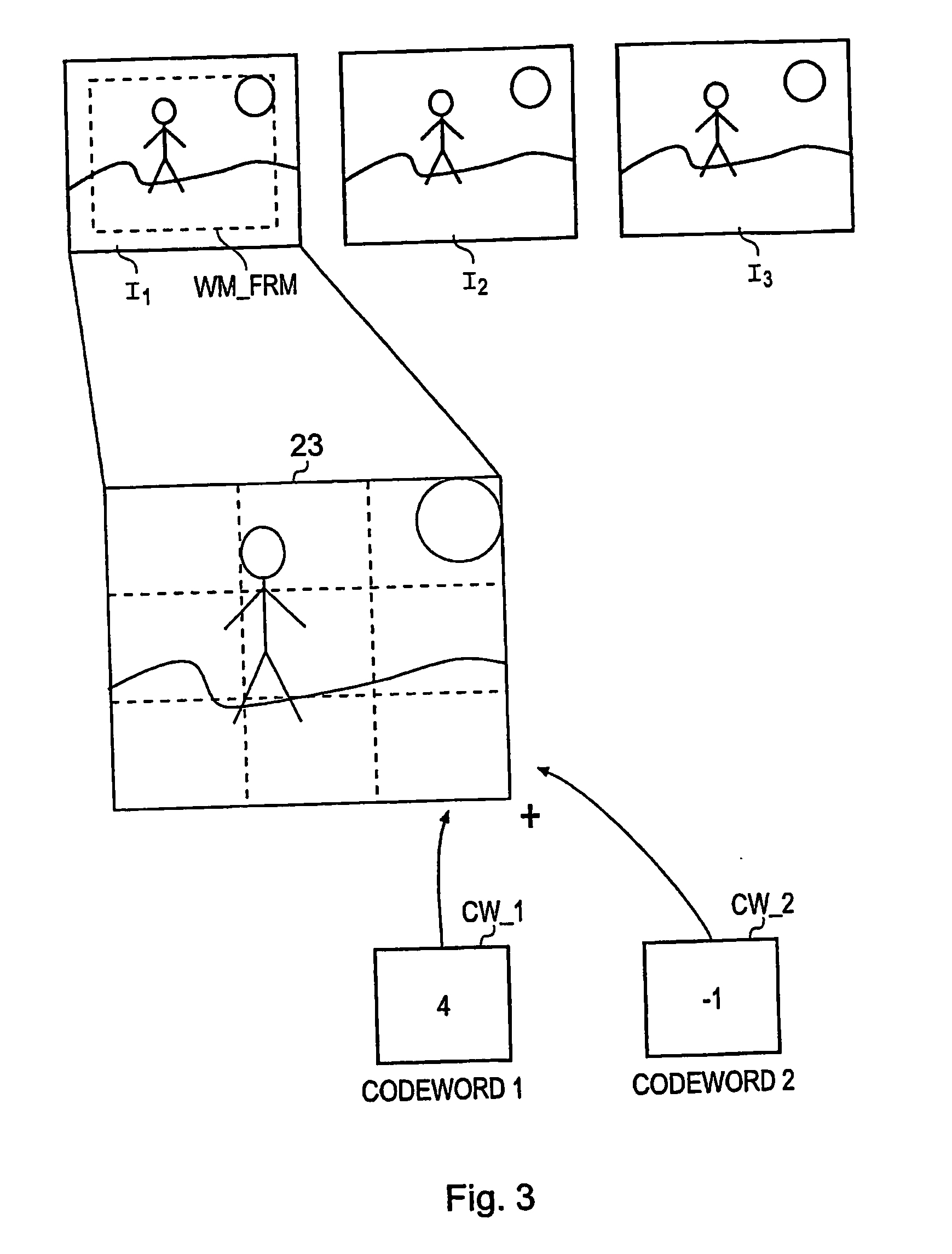
Block-based watermarking
InactiveUS20090290750A1Raise the possibilityEfficient implementationUser identity/authority verificationCharacter and pattern recognitionBlock matchComputer science
A water marking system generates a water marked image frame for conveying a payload data word by combining at least one image frame with a two-dimensional water mark pattern. The water mark pattern includes plural regions each associated with one of symbols of the payload data word. Each region includes a two dimensional water mark block selected from a predetermined set of possible water mark blocks to represent the value of the payload data symbol associated with that region. A detecting data processing apparatus detects the payload data from a received water marked image frame, which has been encoded by utilizing a block match prior probability calculator operable to correlate each region of the water marked image frame with each of the water mark blocks from the set of water marked blocks) to form for each region a set of probability surfaces.
Owner:SONY UK LTD
H.264 based flexible video coding method
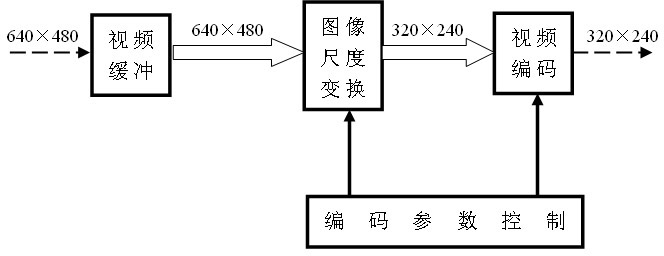
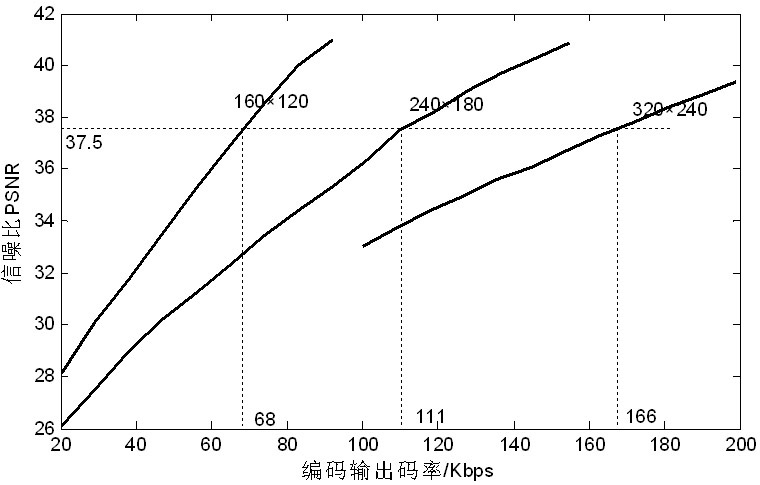
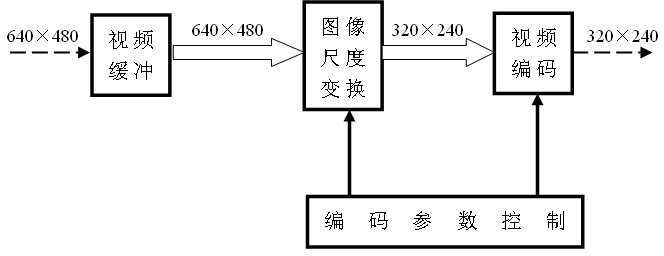
ActiveCN102065302AQuality improvementImprove scalabilityTelevision systemsDigital video signal modificationLoop filterComputer architecture
The invention belongs to the technical field of video coding and decoding, in particular to an H.264 based flexible video coding method which realizes that coded video can be output or transmitted in various code rates through realizing that the resolution ratio, the frame sequence length and the quantitative parameter are adjustable in real time in a process of coding the video based on the H.264 standard. The method also realizes that the relevant parameters of loop filter and dynamic prediction are adjustable in a coding process and the coding complexity in the coding process is controlled, thereby reasonably utilizing system resources. The coding method has the characteristics of high efficiency and easiness of implementation, and can be applied to multiple network video transmission and multiple processor systems.
Owner:FUDAN UNIV
Method for discovering congestion time period based on composite network
ActiveCN108320506AReduce the amount of calculation dataEasy to handleDetection of traffic movementTraffic networkPeriod Analysis
The invention belongs to the field of traffic condition prediction, and relates to a method for discovering a congestion time period based on a composite network. According to the method, a compositenetwork of an intersection network and a sensor network is constructed based on a complex network theory, and a congestion time period in the traffic network can be accurately judged. The method is implemented specifically according to the following steps: firstly, a congestion index Ti, a congestion time period and congestion level quantization are defined, then the congestion time period is calculated through establishing a mapping relation between the intersection network and the sensor network and performing congestion time period analysis, and finally frequent congestion time period analysis is performed. The model established according to the method is simple, the calculation data amount is small, the processing process is concise and clear, the operability and the practicability aregood, and effective implementation is facilitated. Meanwhile, the overall design is ingenious in conception, the required infrastructure are easy to obtain, the prediction process is simple, the application environment is friendly, and the market prospect is broad.
Owner:QINGDAO UNIV
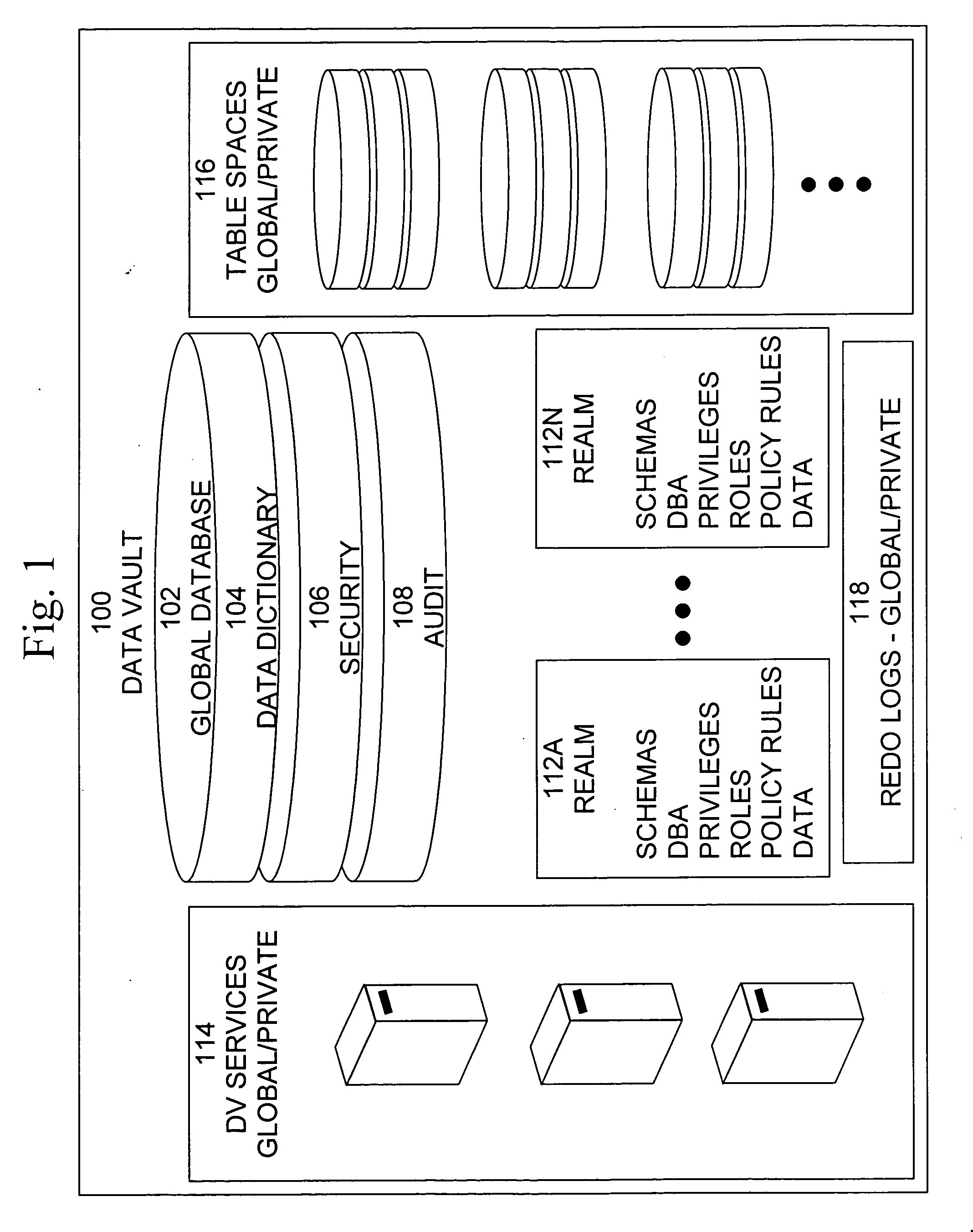
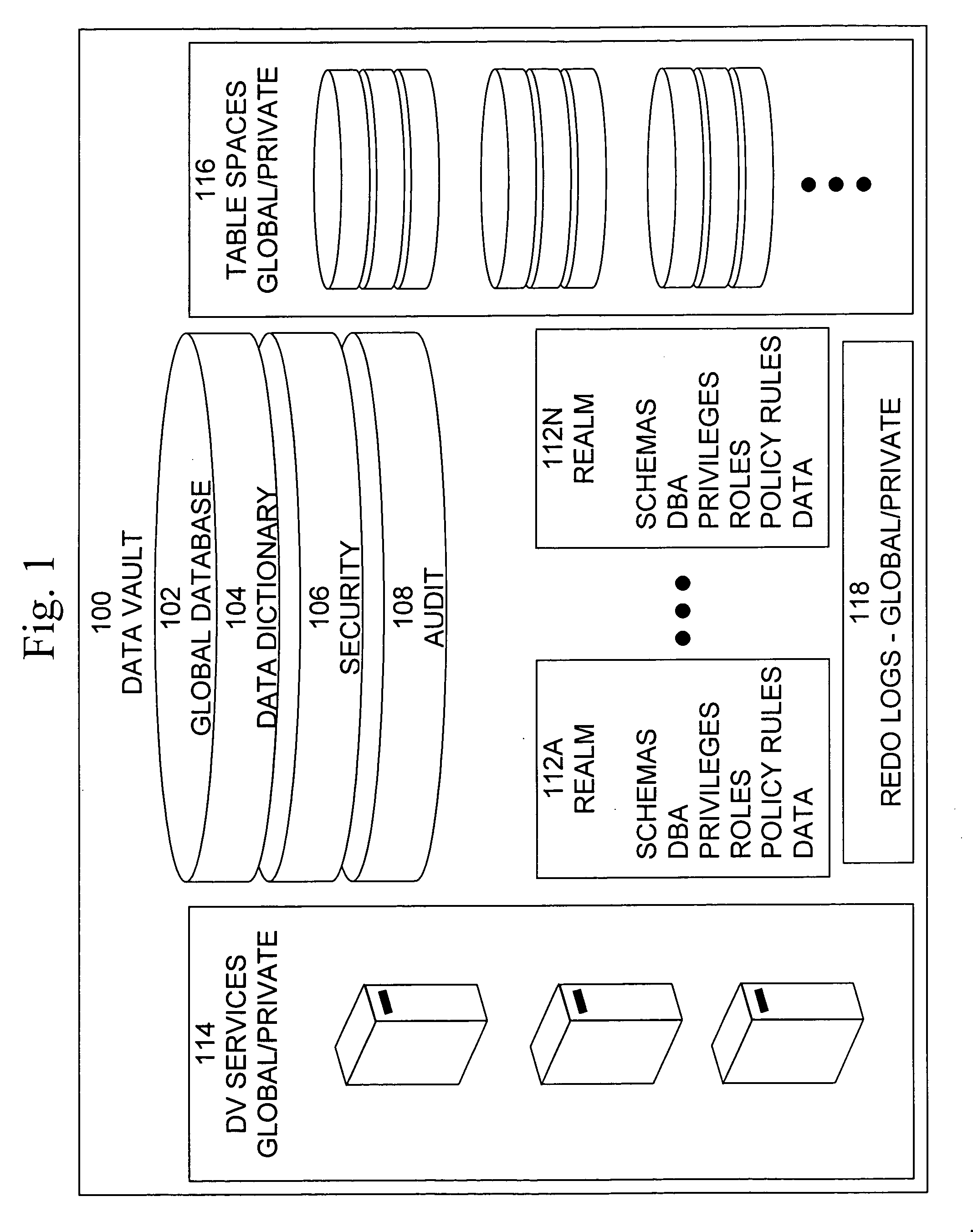
Data vault
ActiveUS7814076B2Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework providing consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of database objects, each database object having a level of security, a plurality of factors, each factor representing a characteristic of a user of the database system, at least one database session of the user in the database, the database session having a level of security, the user connected to the database with a network domain, each network domain having a level of security, wherein the database system is operable to grant or deny access to the data to a user based on the factors associated with the user, based on the level of security of the data, based on the level of security of the database session, and based on the level of security of the network domain.
Owner:ORACLE INT CORP
High voltage power battery with controllable volume of injected liquid and preparation method thereof
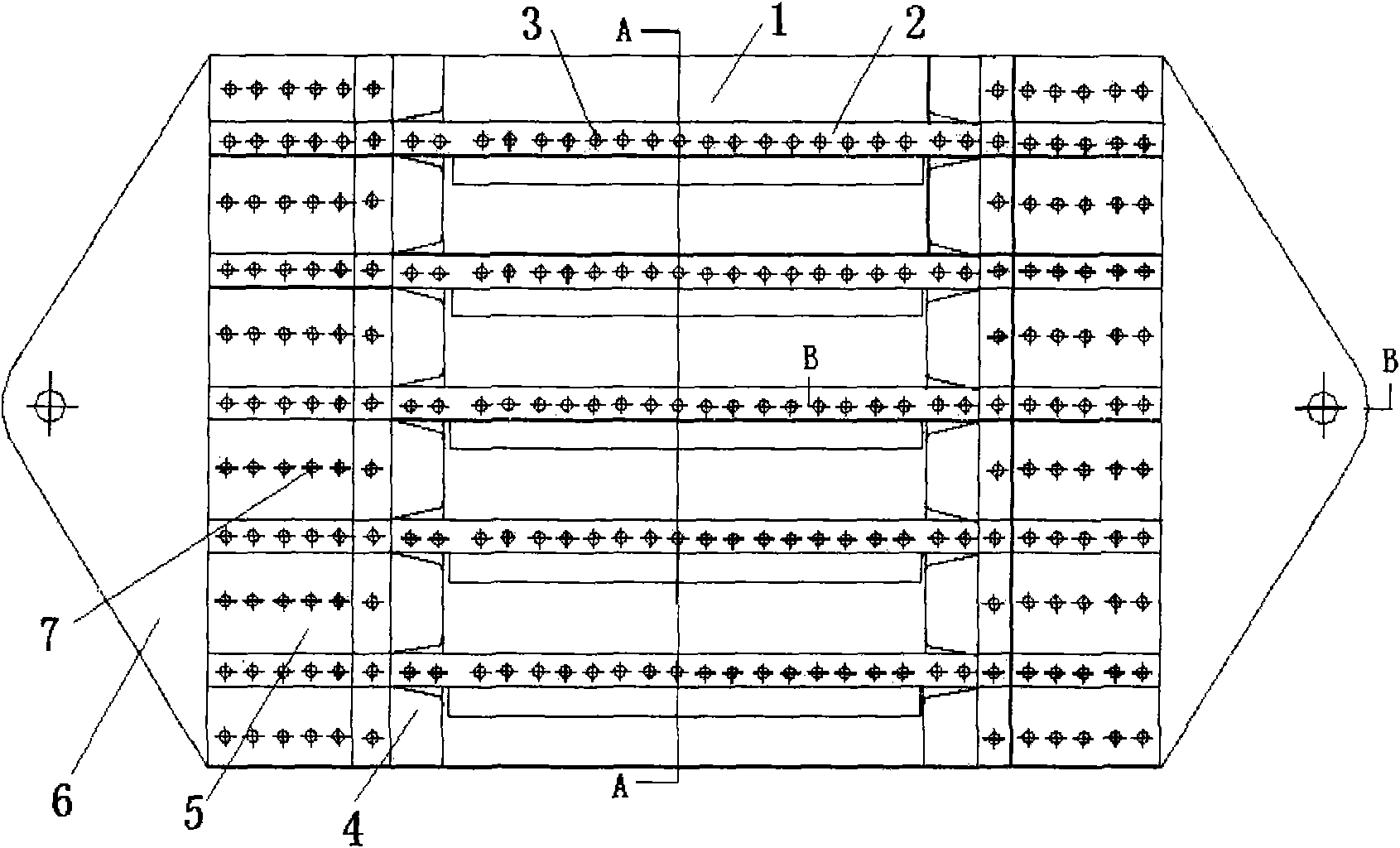
ActiveCN106033823AControl the amount of electrolyteAchieve uniformityElectrolyte moving arrangementsCell seperators/membranes/diaphragms/spacersPower batteryBattery cell
The invention provides an inner laminated type high voltage power battery with a controllable volume of injected liquid and a preparation method thereof. By applying a pressure on the surface of the battery core and controlling the thickness of a partition layer after compression according to the thickness difference between an annular sealing ring and a bipolar electrode sheet, the electrolyte in the partition layer is extruded into the electrode coating; on one aspect, the amount of electrolyte absorbed by the partition layer can be effectively controlled, liquid can be uniformly and consistently injected into each battery cell; on the other aspect, the electrolyte extruded from the partition layer can be uniformly infiltrated into the micro holes of anode coating and cathode coating, the elastic partition layer is tightly contacted with the neighbored cathode coating and anode coating through a long-lasting pressing force, the mechanical consistency of each battery cell in the battery can be effectively improved, the invention further provides a manufacturing method of the high voltage power battery, the operation is simple and effective, and the manufacturing efficiency is high.
Owner:BEIJING HAWAGA POWER STORAGE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com