Session key negotiation method and intelligent secret key device
A technology of intelligent key device and session key, which is applied in the field of information security and can solve the problems of leakage of authentication private key and reduction of session key security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
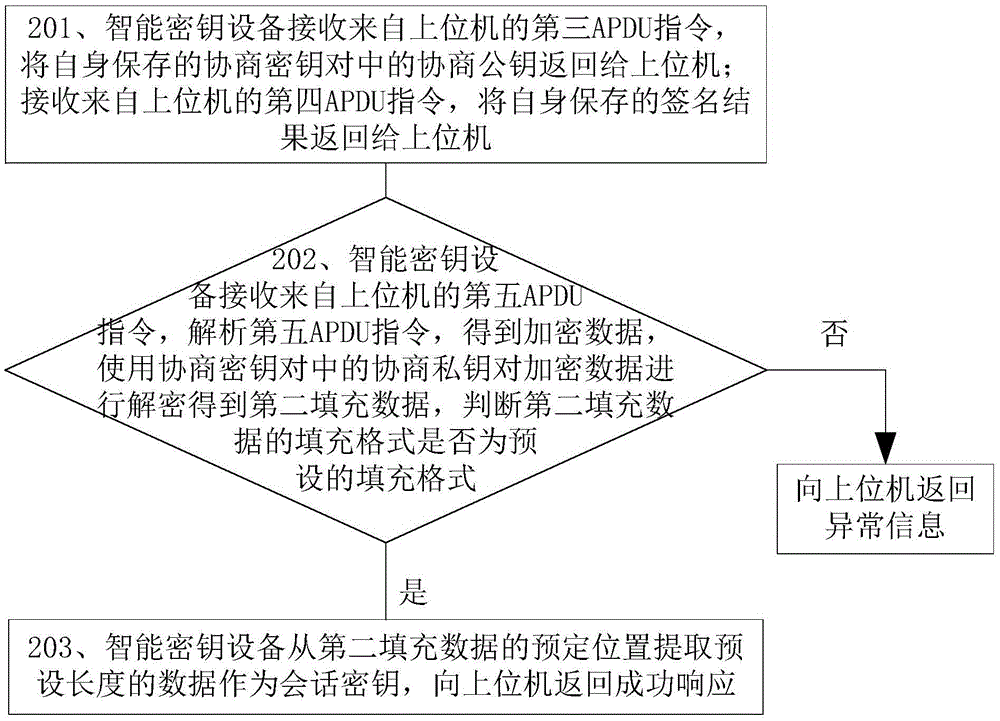
[0081] This embodiment provides a method for negotiating a session key, which is introduced with the smart key device as the main body of the operation, such as figure 1 shown, including the following steps:
[0082] Step 201: The smart key device receives the third APDU instruction from the upper computer, returns the negotiation public key in the negotiation key pair saved by itself to the upper computer; receives the fourth APDU instruction from the upper computer, and sends the signature saved by itself to the upper computer. The result is returned to the host computer.
[0083] Optionally, step 201 can also be: the smart key device first receives the fourth APDU command from the host computer, and returns the signature result saved by itself to the host computer; then receives the third APDU command from the host computer, and saves the signature result by itself. The negotiation public key in the negotiation key pair is returned to the host computer.
[0084] Specifica...
Embodiment 2
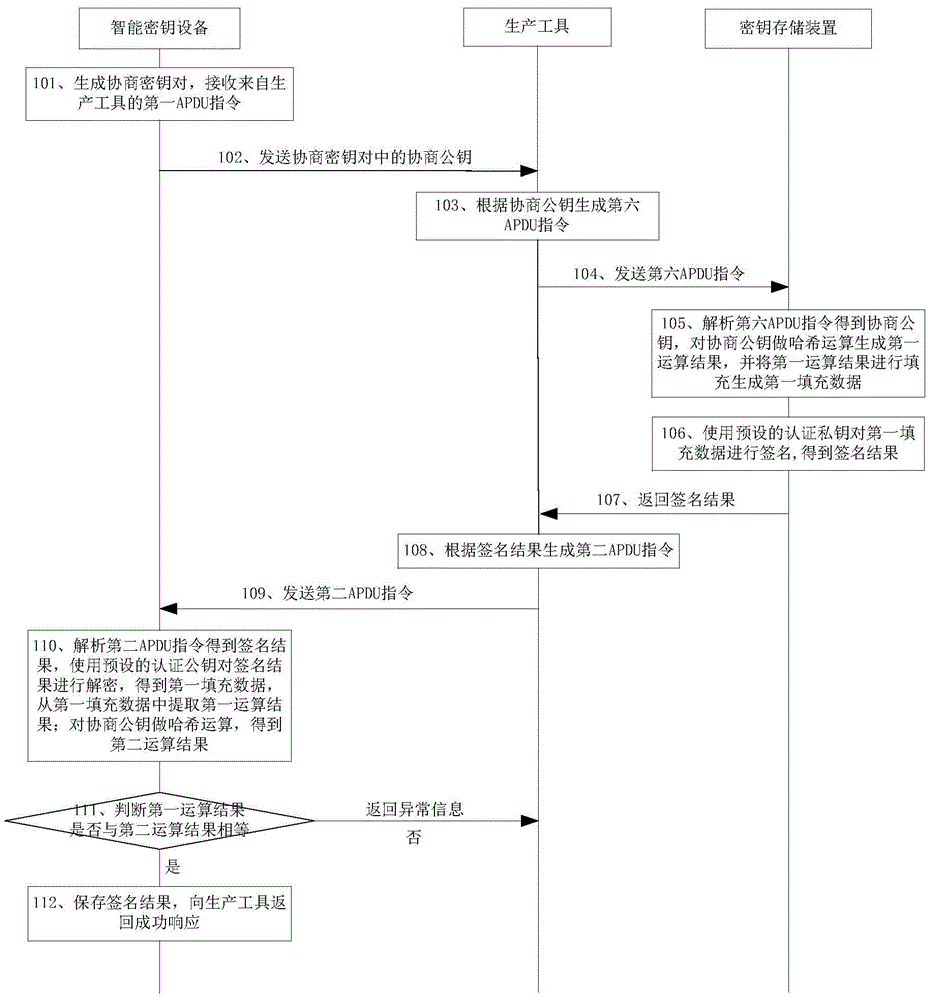
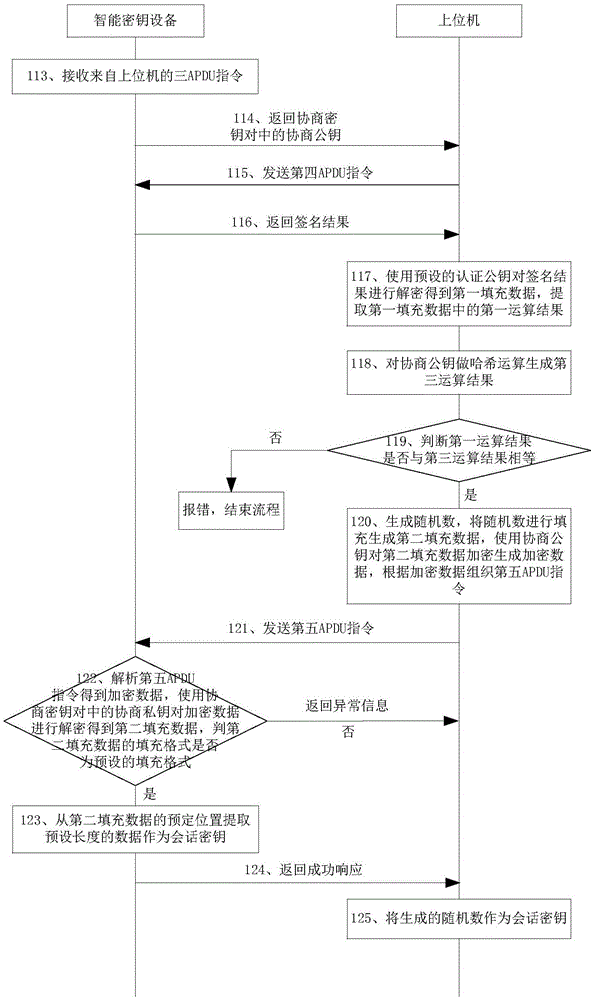
[0165] This embodiment provides a working method for negotiating a session key system, which is applied to a system composed of a host computer, an intelligent key device, a production tool, and a key storage device, such as figure 2 and image 3 shown, including the following steps:
[0166] Step 101: The smart key device generates a negotiated key pair, and receives the first APDU instruction from the production tool.
[0167] In this embodiment, step 101 is specifically: the smart key device automatically generates a negotiated key pair when it is powered on, and receives the first APDU instruction from the production tool;
[0168]Alternatively, the smart key device is powered on, and generates a negotiated key pair after receiving the first APDU instruction from the production tool.
[0169] Specifically, the first APDU instruction is an APDU instruction for reading the negotiated public key.
[0170] For example, the first APDU instruction is specifically:
[0171] ...
Embodiment 3
[0285] This embodiment provides a working method of a negotiation session key system, which is applied to a system composed of a host computer, an intelligent key device, and a production tool.
[0286] In this embodiment, step 103-step 108 in embodiment 2 is changed to step C11-step C12, and other steps are the same as in embodiment 2, that is, the steps before step C11 in this embodiment are the same as the steps in embodiment 2 The steps before step 103 are the same, and the steps after step C12 in this embodiment are the same as the steps after step 108 in embodiment 2, and will not be repeated here.
[0287] Specifically, step C11-step C12 are as follows:
[0288] Step C11: The production tool performs a hash operation on the negotiated public key to generate a first operation result, and fills the first operation result to generate first padding data.
[0289] Specifically: the first operation result is the first hash value.
[0290] For example, the filling format of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com