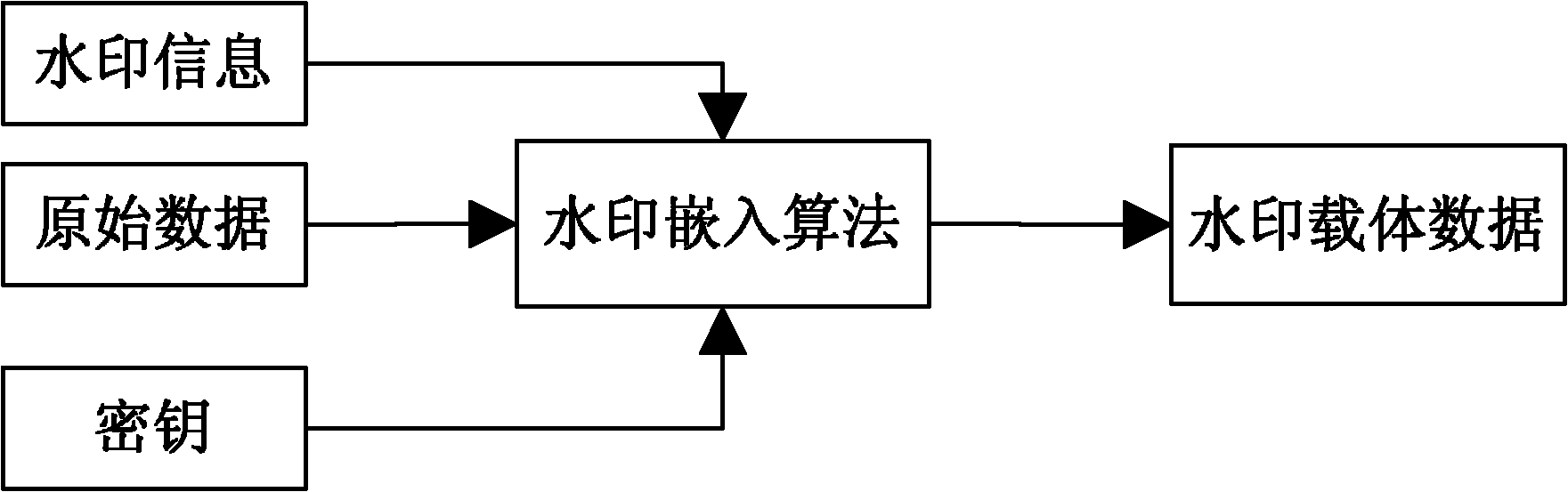
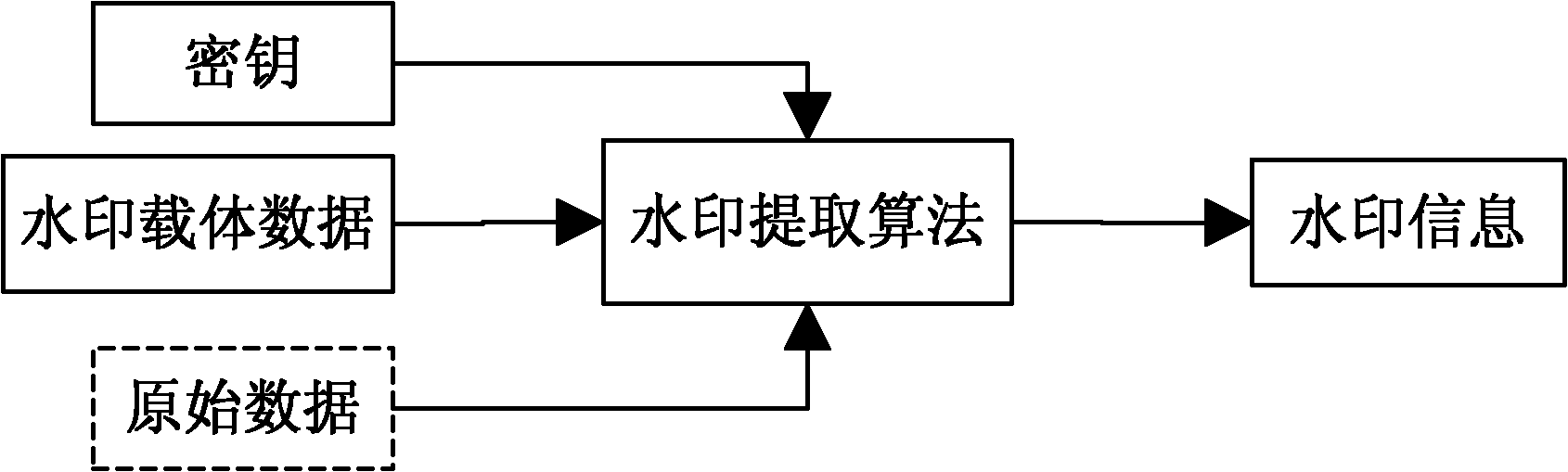
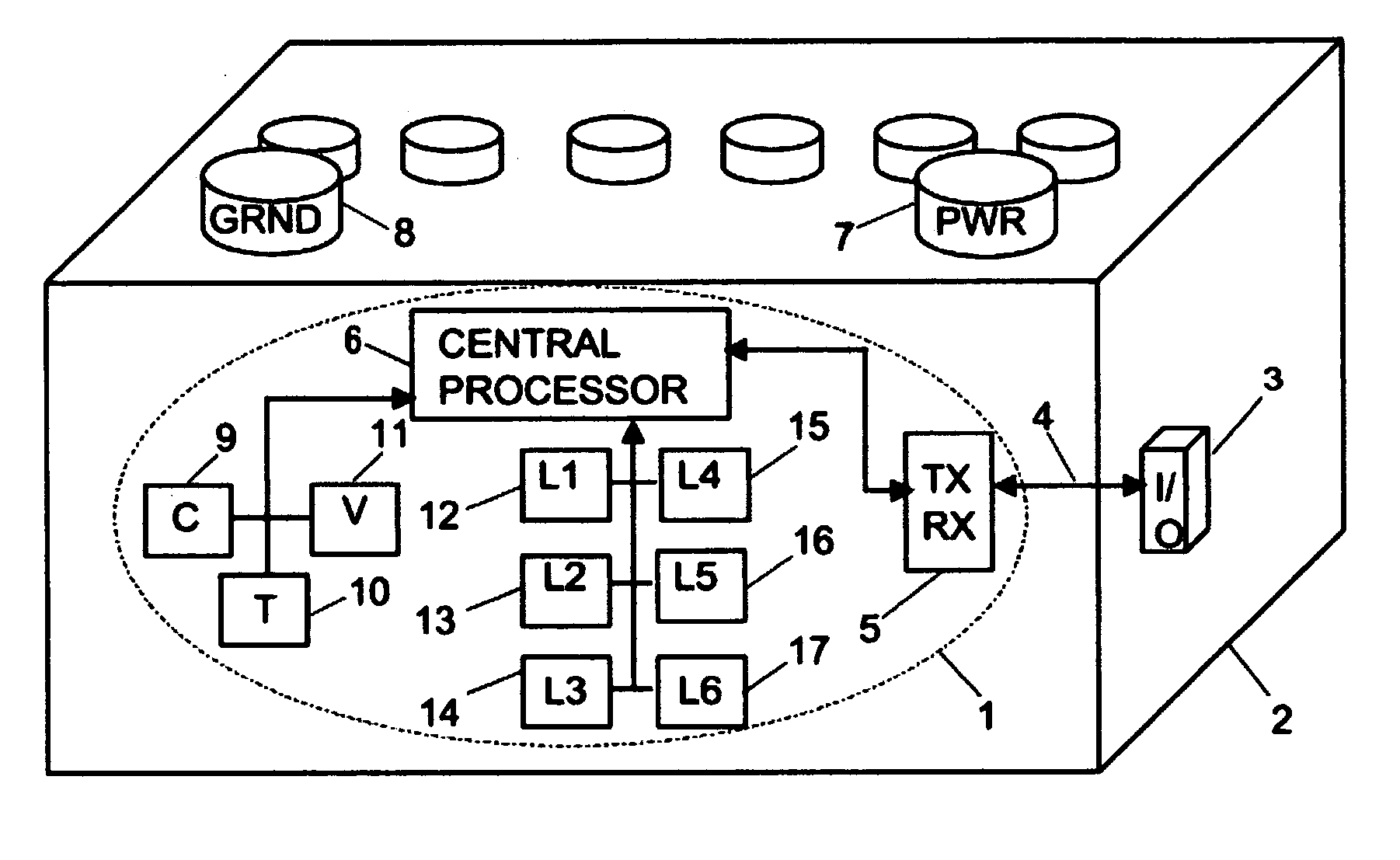
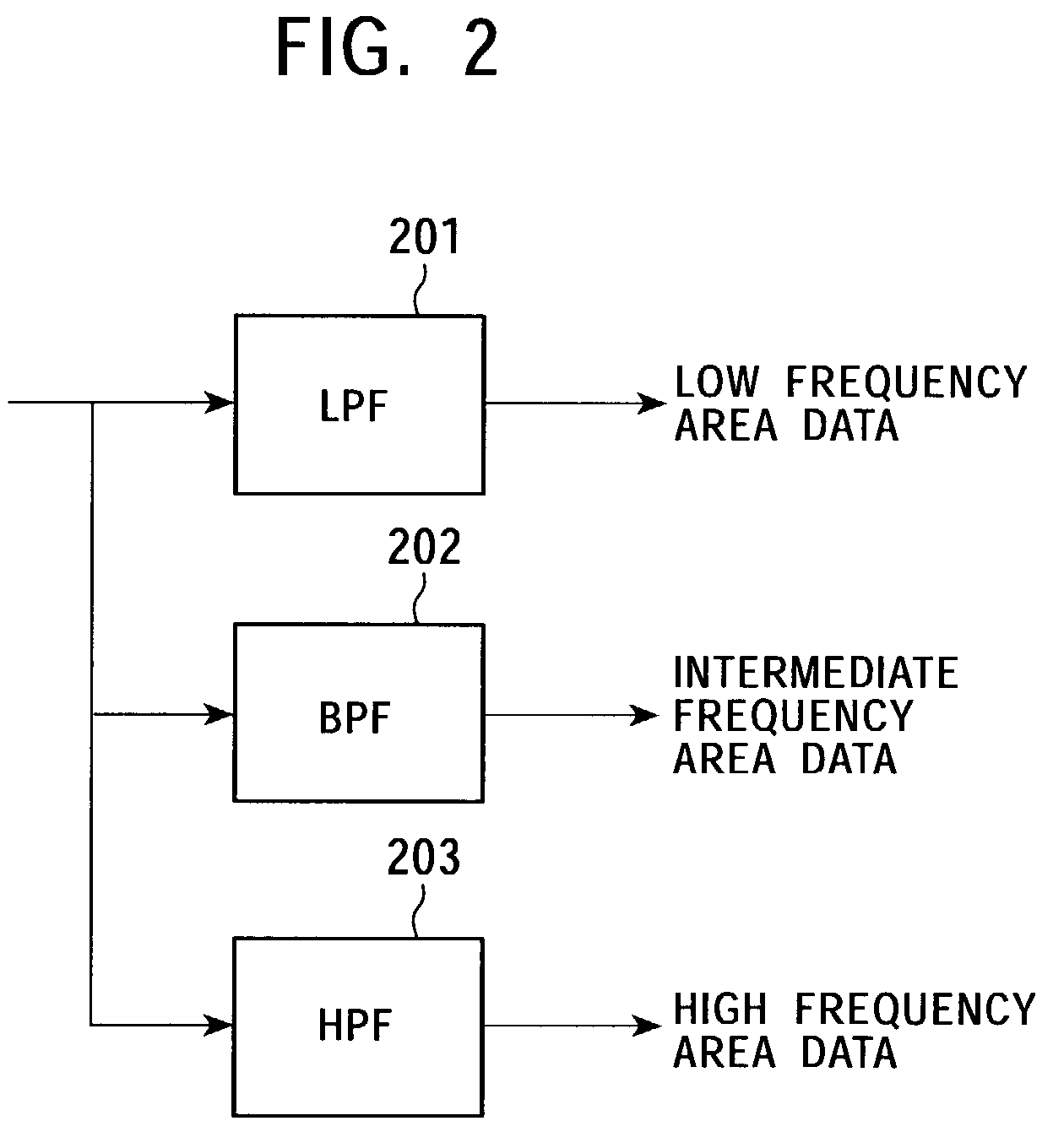
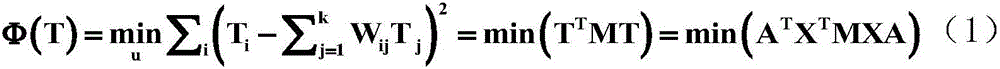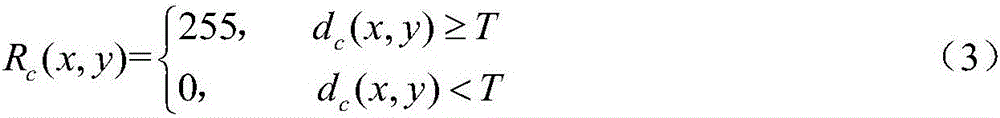Patents
Literature
168 results about "Embedding algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An embedding is 2- cell if each face is equivalent to an open disk. Efficient embedding algorithms for the plane are well-known. By Kuratowski's Theorem, a non-planar graph G contains a subdivision of K 5 or K 3,3 as a subgraph. The objective of this thesis is to devise efficient practical embedding algorithms for the projective plane and torus.
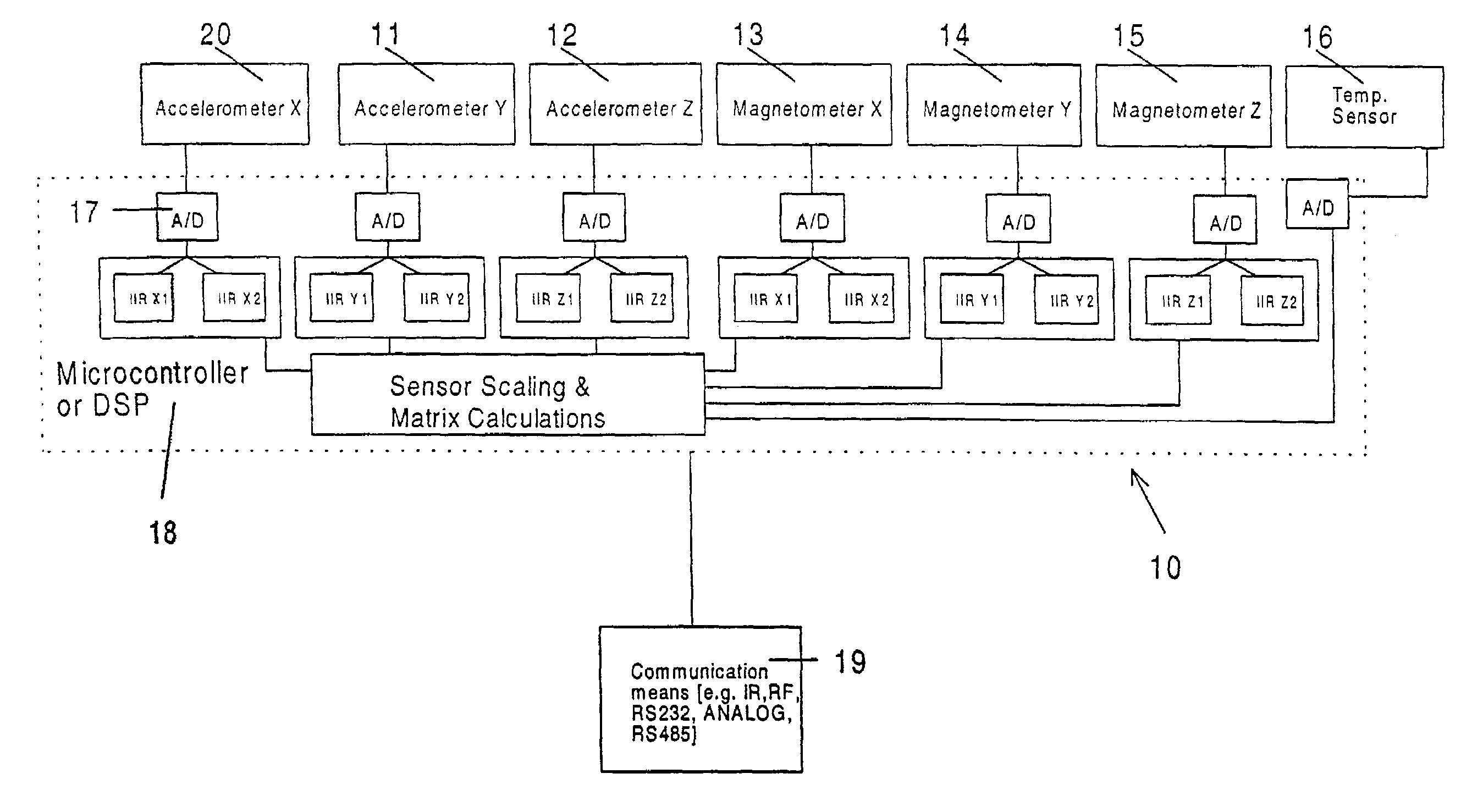
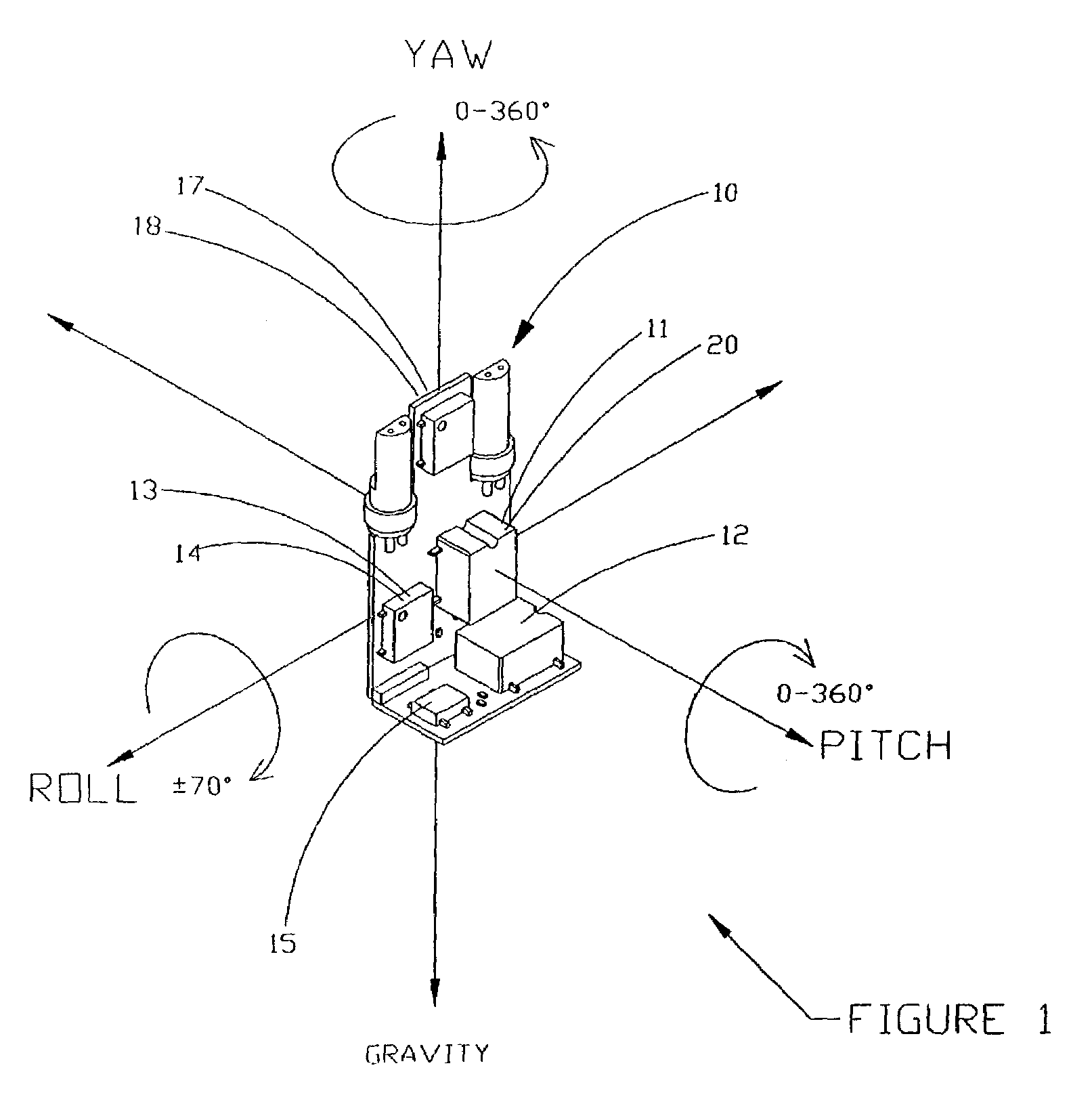
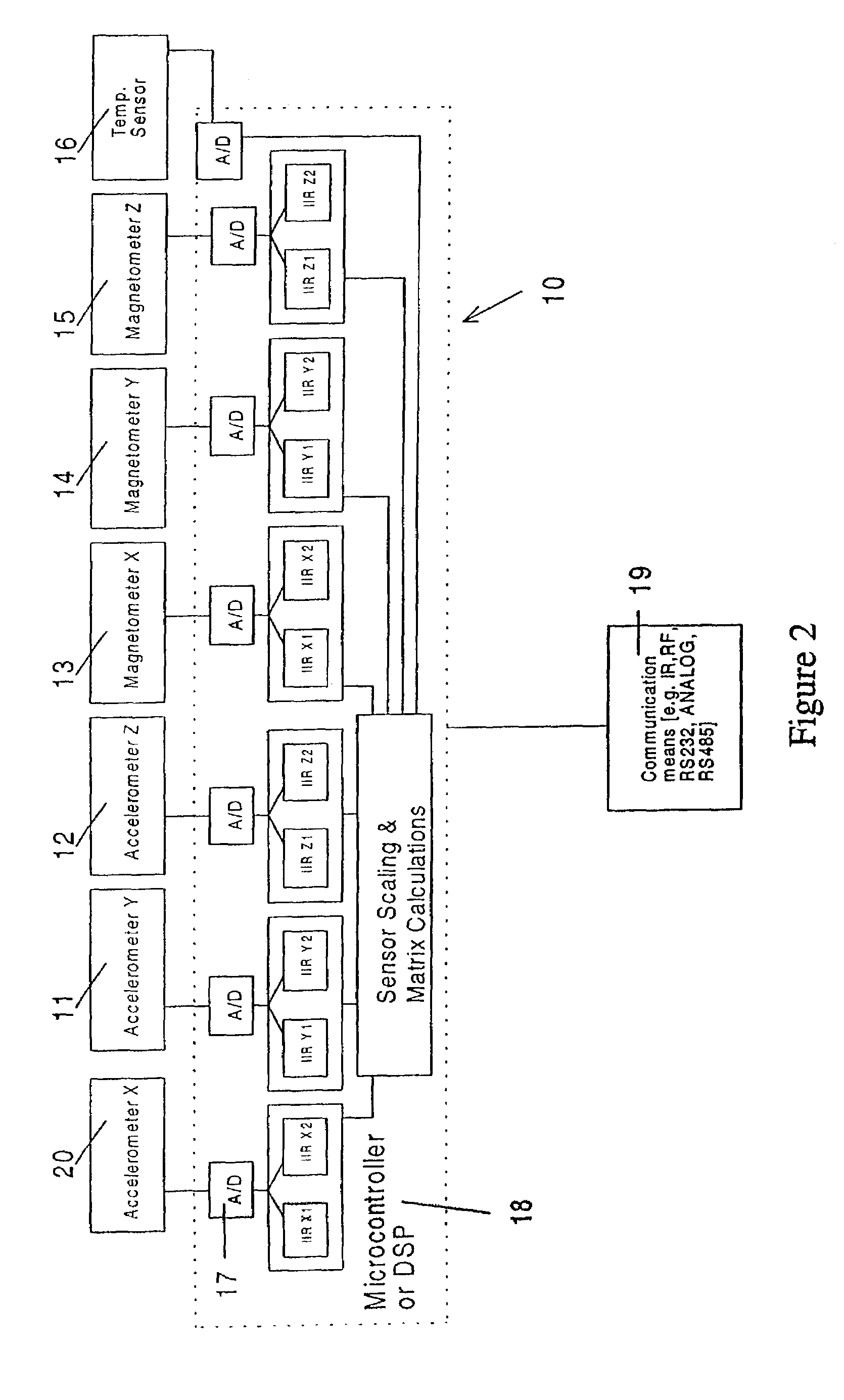
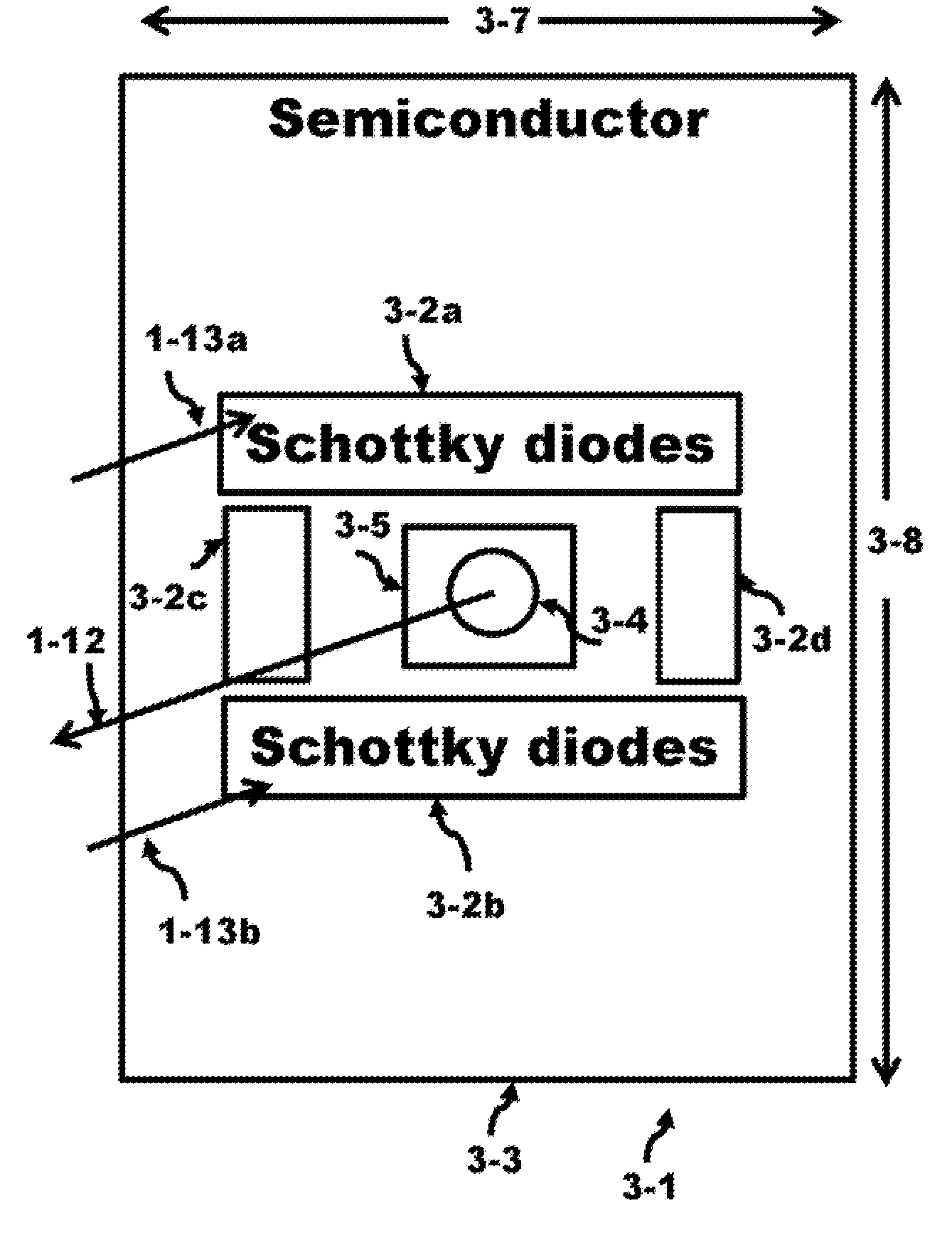
Solid state orientation sensor with 360 degree measurement capability
InactiveUS7143004B2Navigation by terrestrial meansDigital computer detailsRoboticsTriaxial accelerometer
The device is a miniature, self-contained solid state orientation sensor. The unit utilizes three magnetometers and three accelerometers to calculate pitch, roll, and yaw (compass heading) angles relative to the earth's magnetic and gravitational fields. The three orientation angles are output in digital RS232 or optional multi-drop RS485. The device can also be programmed to provide raw accelerometer and magnetometer data in true physical units. The device is capable of measuring angles from 0 to 360 degrees on the yaw axis, 0 to 360 degrees on the pitch axis, and −70 to +70 degrees on the roll axis. The yaw output is compensated for errors due to pitch and roll using embedded algorithms. Applications include fast solid state compassing, robotics, virtual reality, down-hole well drilling, and body position tracking for biomedical and multimedia applications.
Owner:LORD CORP
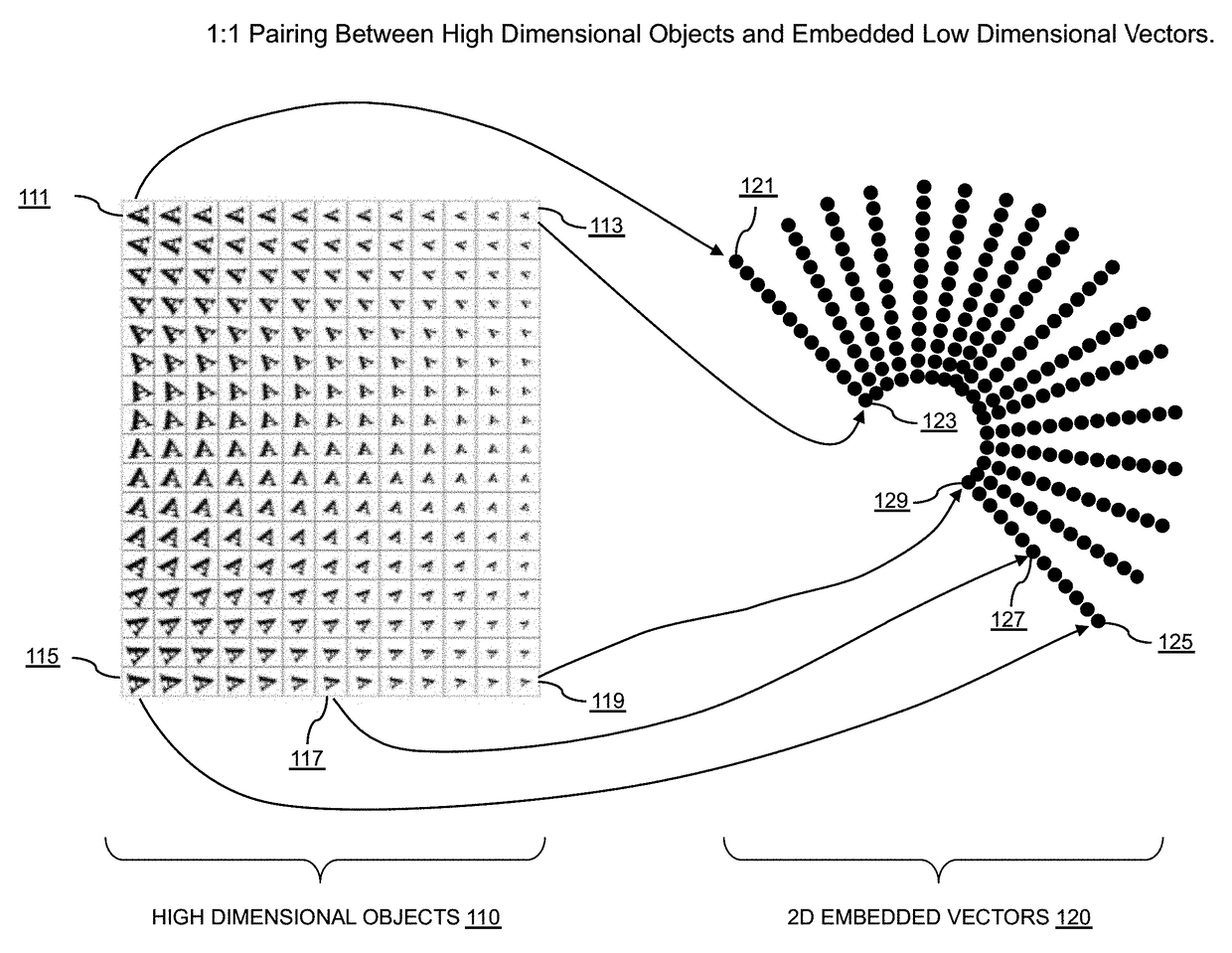
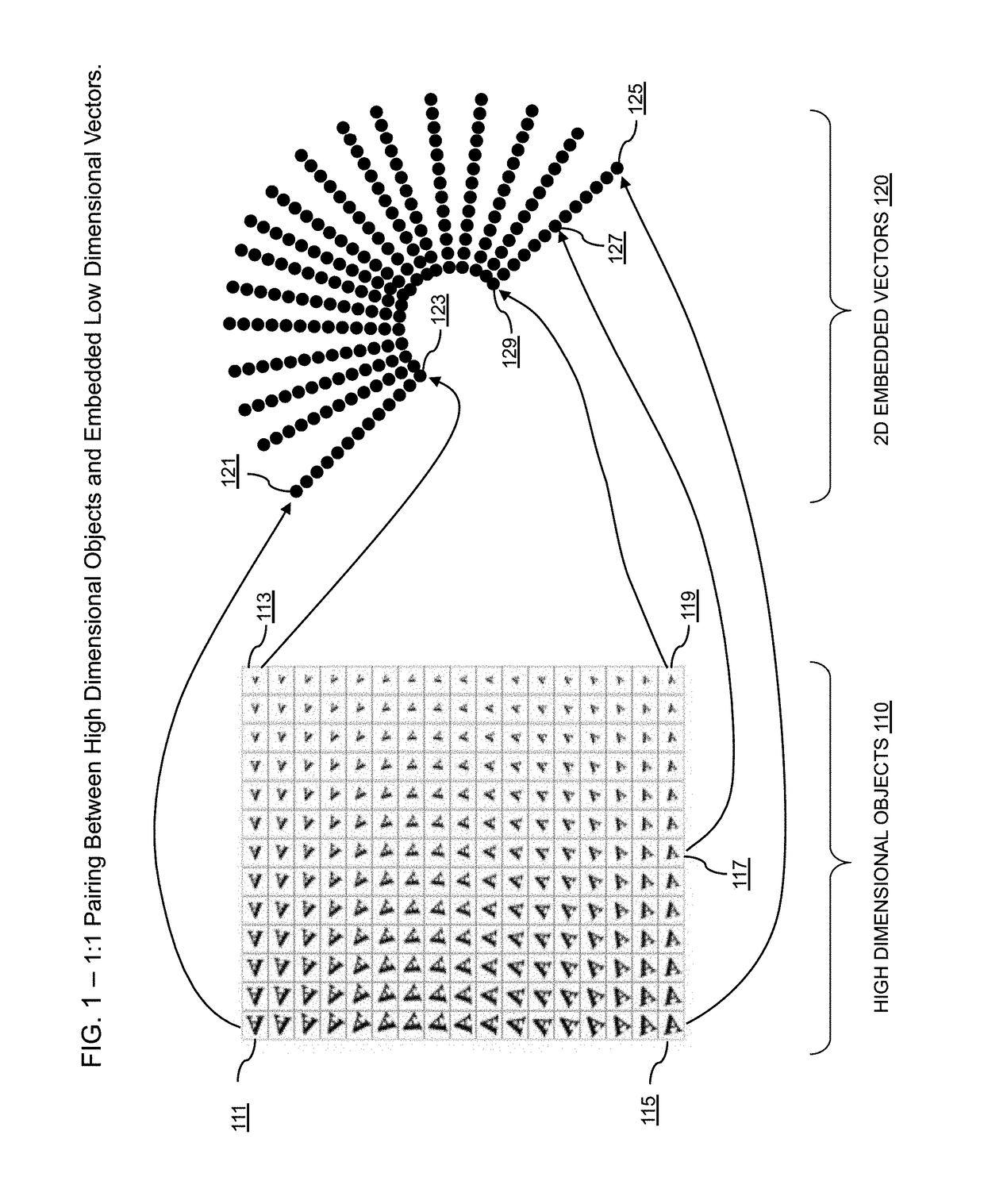
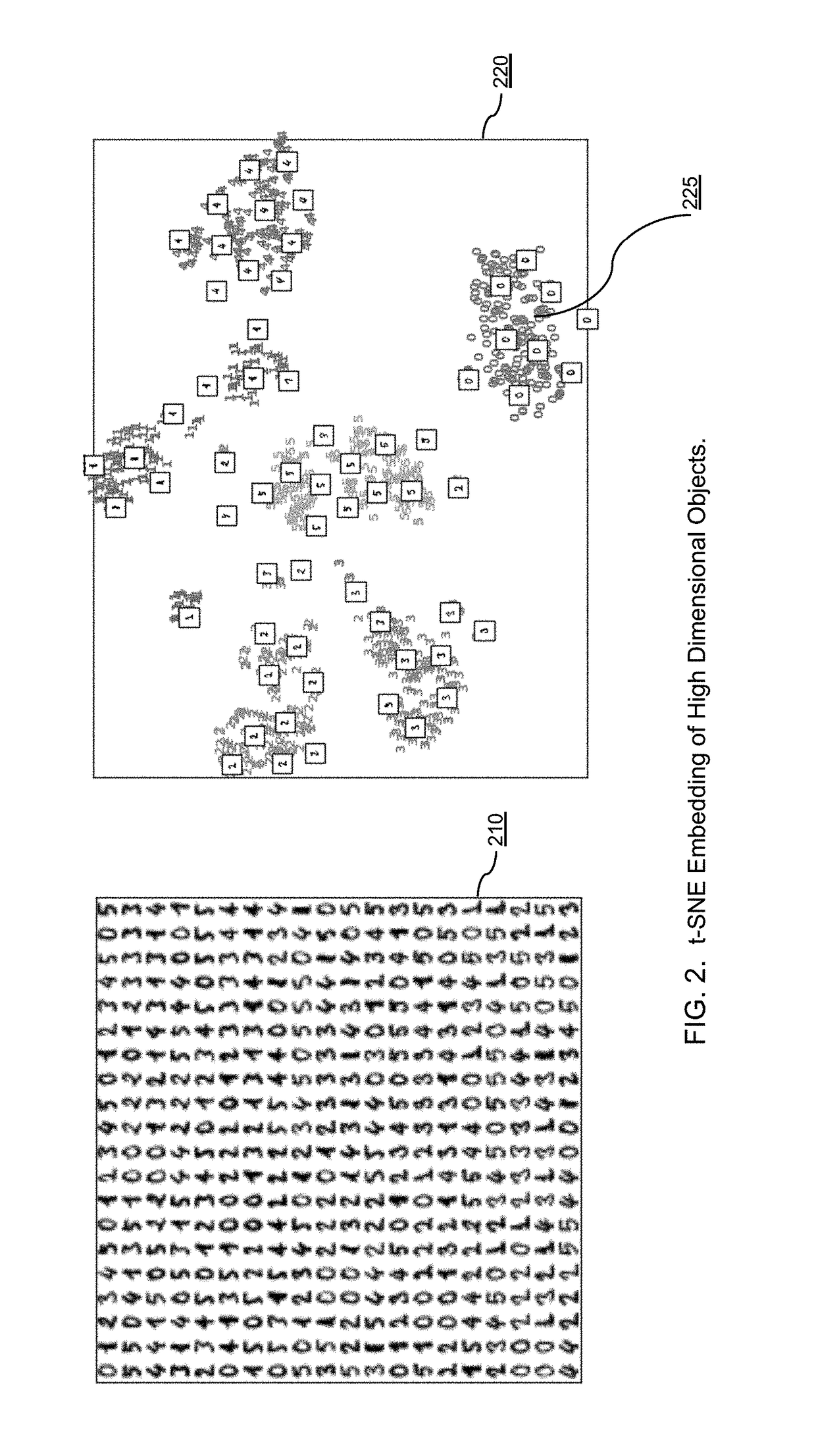
Systems and methods for fast and repeatable embedding of high-dimensional data objects using deep learning with power efficient GPU and FPGA-based processing platforms
ActiveUS9990687B1Reduce total powerShorten the timeCharacter and pattern recognitionImage watermarkingPower efficientAlgorithm
Embodiments of the present invention are directed to providing new systems and methods for using deep learning techniques to generate embeddings for high dimensional data objects that can both simulate prior art embedding algorithms and also provide superior performance compared to the prior art methods. Deep learning techniques used by embodiments of the present invention to embed high dimensional data objects may comprise the following steps: (1) generating an initial formal embedding of selected high-dimensional data objects using any of the traditional formal embedding techniques; (2a) designing a deep embedding architecture, which includes choosing the types and numbers of inputs and outputs, types and number of layers, types of units / nonlinearities, and types of pooling, for example, among other design choices, typically in a convolutional neural network; (2b) designing a training strategy; (2c) tuning the parameters of a deep embedding architecture to reproduce, as reliably as possible, the generated embedding for each training sample; (3) optionally deploying the trained deep embedding architecture to convert new high dimensional data objects into approximately the same embedded space as found in step (1); and optionally (4) feeding the computed embeddings of high dimensional objects to an application in a deployed embodiment.
Owner:GENERAL DYNAMICS MISSION SYST INC
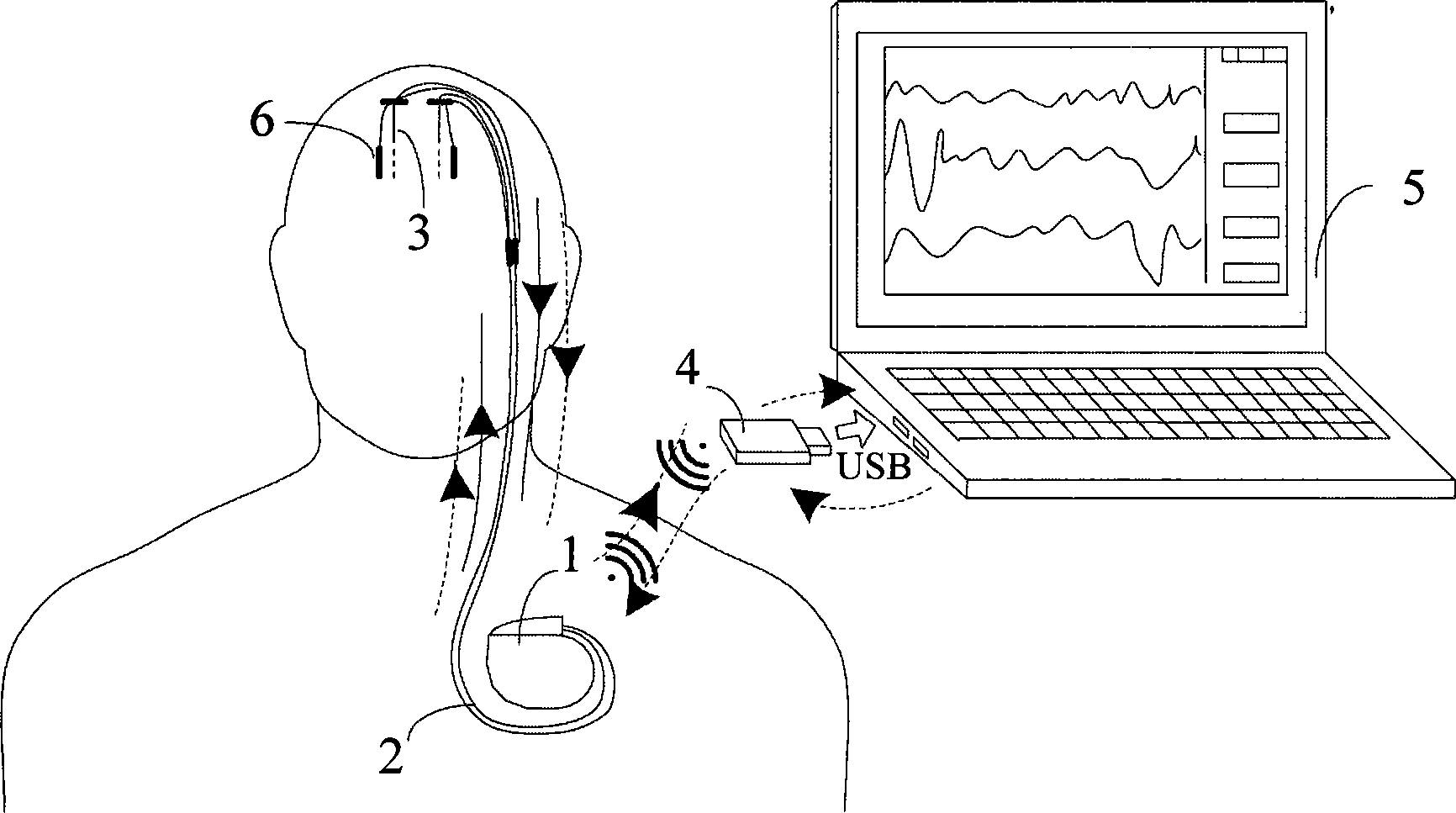
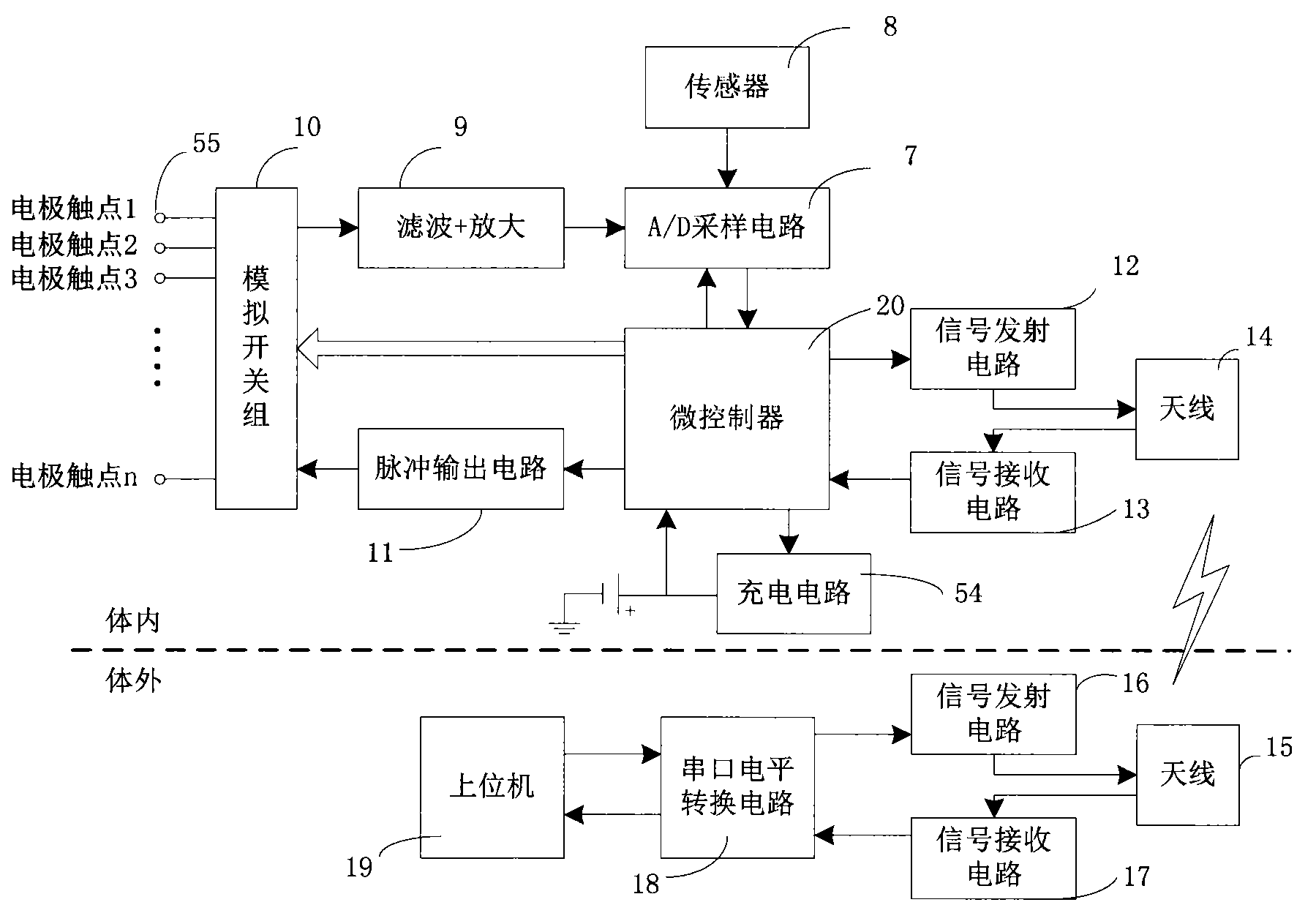
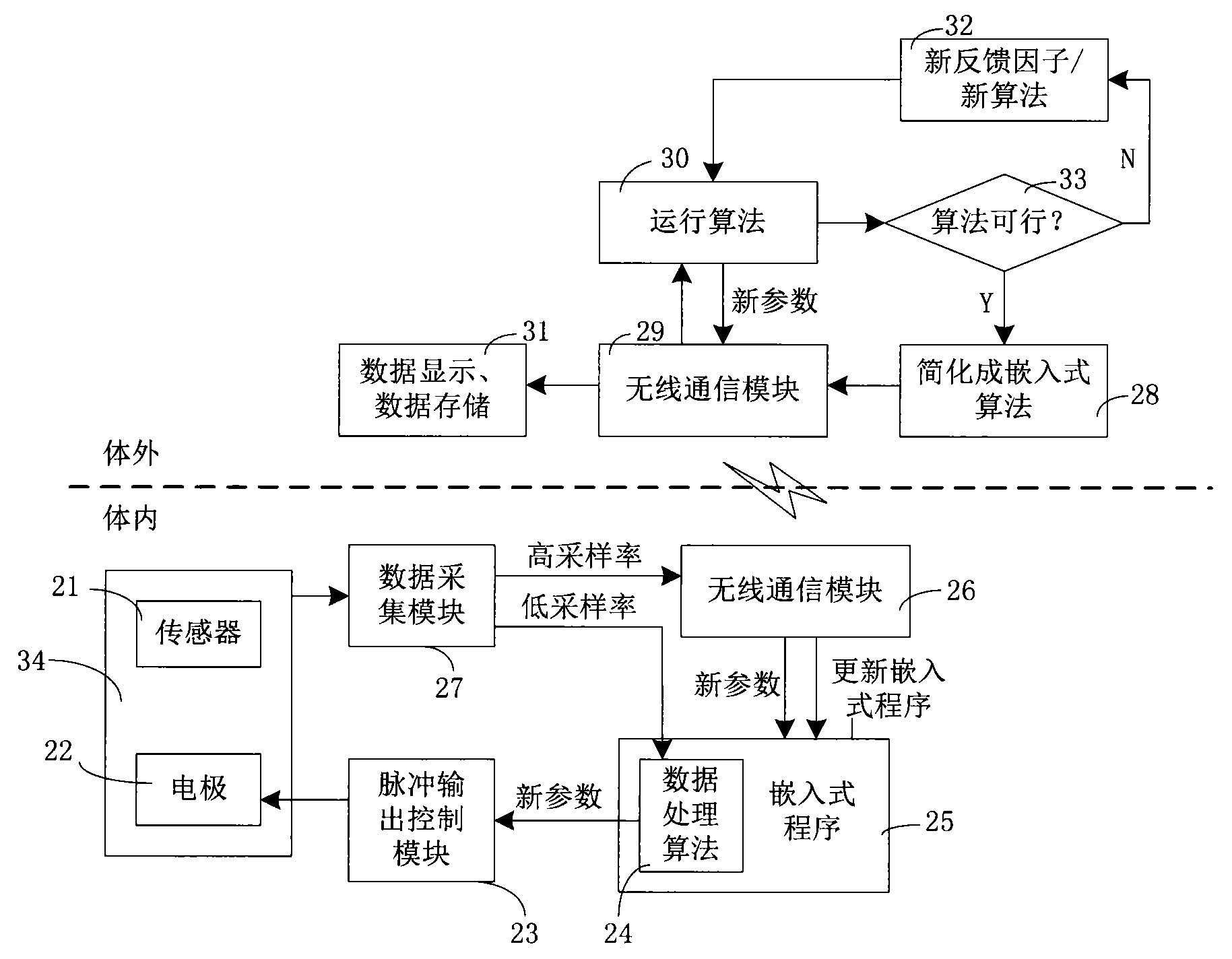
Closed loop nerve stimulation system
The invention belongs to the technical field of implantable medical instruments, and provides a closed loop deep brain stimulation system which can collect physiological signals of patients, adjust pulse stimulation parameters in real time and display data, store the data, design an optimization algorithm and update embedded programs in real time through an upper computer, and particularly relates to a closed loop nerve stimulation system. According to the closed loop nerve stimulation system, two closed loop work modes are provided; in one work mode, an implantable nerve stimulator carries out embedded algorithm data processing to form closed loop control; in the other work mode, the implantable nerve stimulator uploads the collected data to the upper computer through a wireless communication module, and then the upper computer carries out algorithm processing and then controls the stimulation parameters through the wireless communication module to form a closed loop. The closed loop nerve stimulation system can be used for closed loop electrical stimulation treatment of nervous system diseases or clinical research or animal research of a closed loop stimulation method and can provide a good platform for the research of the closed loop stimulation method.
Owner:TSINGHUA UNIV +1
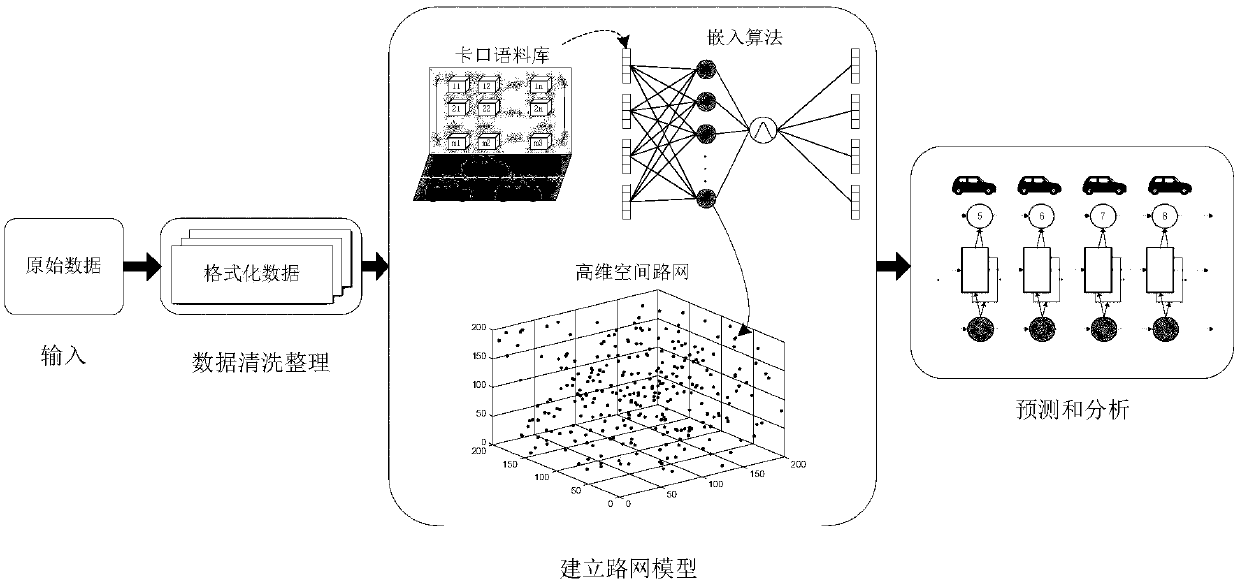
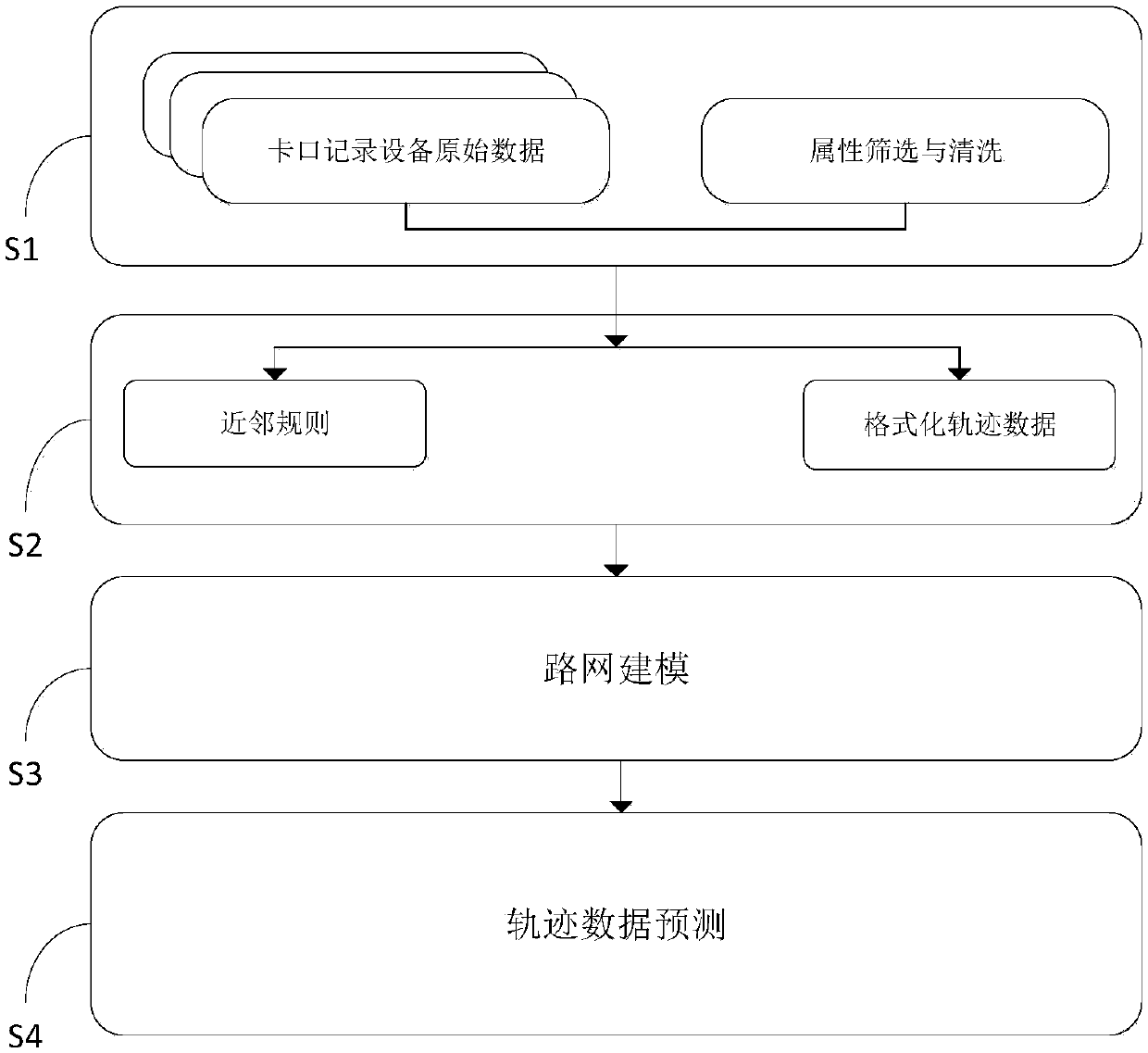
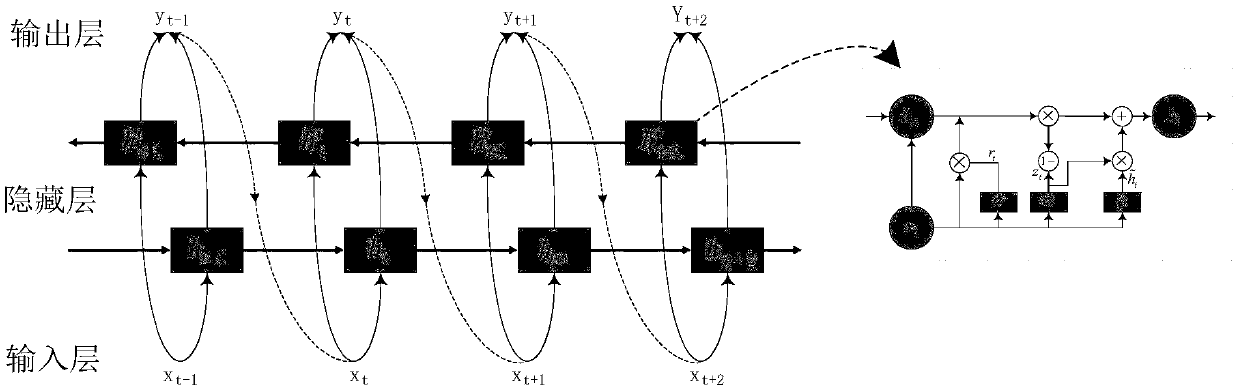
Traffic track prediction method based on high-dimensional road network and circulating neural network
The invention provides a traffic track prediction method based on a high-dimensional road network and a circulating neural network, and belongs to the field of intelligent traffic analysis. The methodcomprises the steps of acquiring a data source, extracting relevant attributes, and screening the track data set according to a vehicle speed threshold value; carrying out secondary screening on track data through a neighbor rule to obtain complete formatted track data; establishing a road network model, extracting the track data set through a time window, obtaining a target bayonet context relation, embedding target bayonet codes into a high-dimensional space through an embedding algorithm, and mapping the two-dimensional plane road network to a high-order spatial road network, wherein complex topological relation is not contained between the bayonets, and the character similarity between the bayonets in the track data can be measured by using the high-dimensional similarity; using a bi-directional cycle neural network for carrying out bidirectional learning and prediction on a track matrix, and carrying out learning and prediction on the track data by combining the forward information and the backward information. The prediction efficiency is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
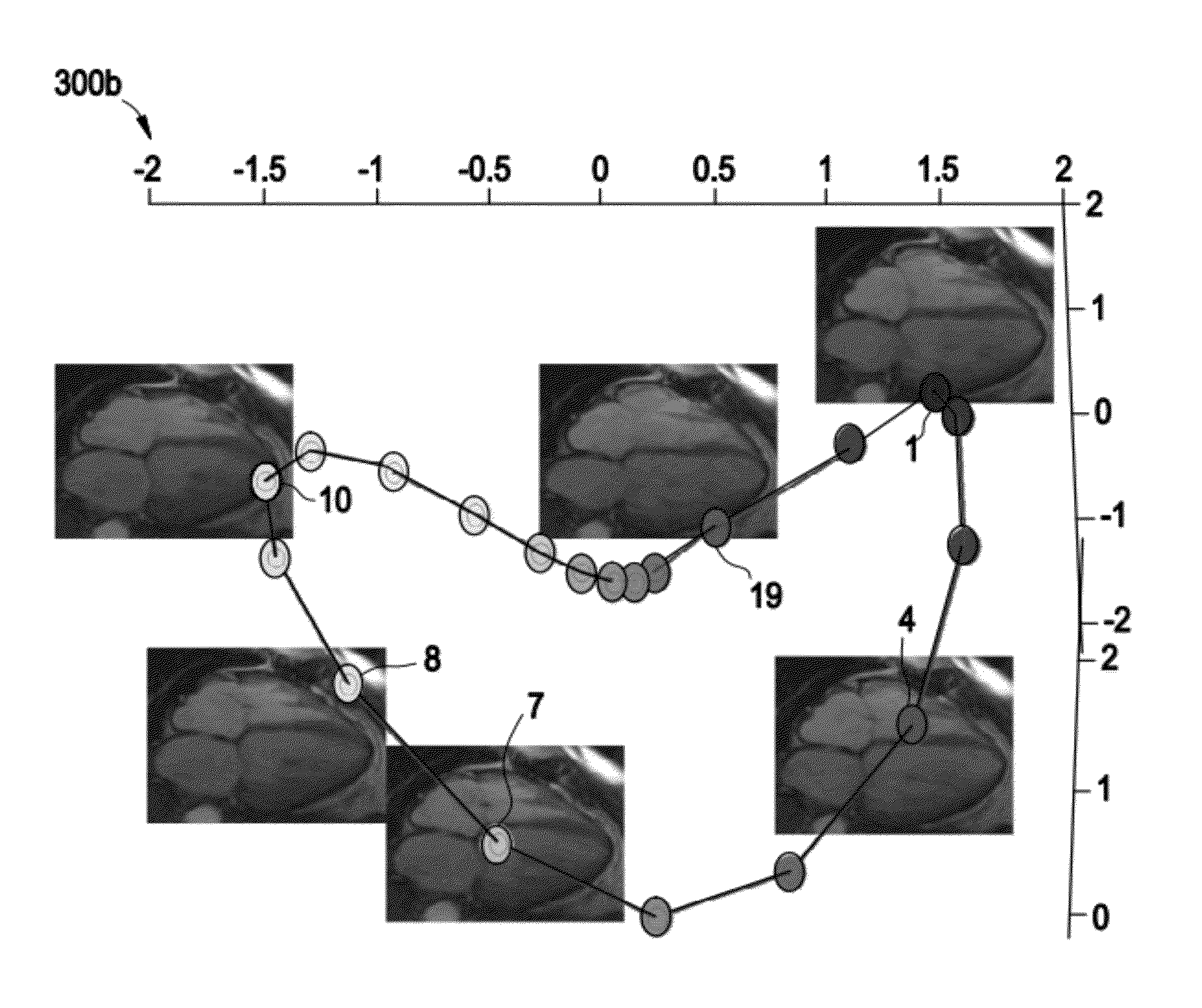
System and method for image based multiple-modality cardiac image alignment
Certain embodiments of the present invention provide a system and method for temporally aligning a plurality of cardiac image sequences. The method includes performing a locally linear embedding algorithm on a first set of cardiac image sequences and on a second set of cardiac image sequences. A graphical representation is created for the first set of cardiac image sequences and the second set of cardiac image sequences. A determination is made whether the first set of cardiac image sequences and the second set of cardiac image sequences were generated from a similar point of view. If a similar point of view is found, the first graphical representation and the second graphical representation are aligned using a minimization function. If a similar point of view is not found, the graphs are aligned with a template and then aligned with each other using the minimization function.
Owner:GENERAL ELECTRIC CO
High-spectral remote-sensing image classification method based on semi-supervision sparse discriminant embedding
InactiveCN103593676ADimension reductionEase the difficulty of choosingCharacter and pattern recognitionClassification methodsProperty value
The invention provides a high-spectral remote-sensing image classification method based on semi-supervision sparse discriminant embedding. The method simplifies the dimension of high-spectral remote-sensing images in a semi-supervision sparse discriminant embedding algorithm, and combines advantages of neighborhood manifold structure and sparsity, wherein the sparse reconstruction relations among samples are reserved, the natural discrimination capability with sparse expression requires no manual selection of neighborhood property values, so that the difficulty in neighborhood parameter selection is reduced to certain extent; and a few of marked training samples and partial unmarked training samples are used to discover intrinsic attributes and low-dimension manifold structure contained in high-dimension data, so that the precision of natural object classification in the high-spectral remote-sensing images can be improved. At the same time, the method of the invention discriminately treat marked data and unmarked data, and the capability of gathering data points of the same natural-object classification is enhanced to the largest degree, thereby further improving the precision of natural object classification in the high-spectral remote-sensing images.
Owner:CHONGQING UNIV
Multiple digital watermarking method for geographic information system (GIS) vector data
InactiveCN101968878AImprove robustnessComputer security arrangementsImage data processing detailsDiscrete cosine transformGeographic information system
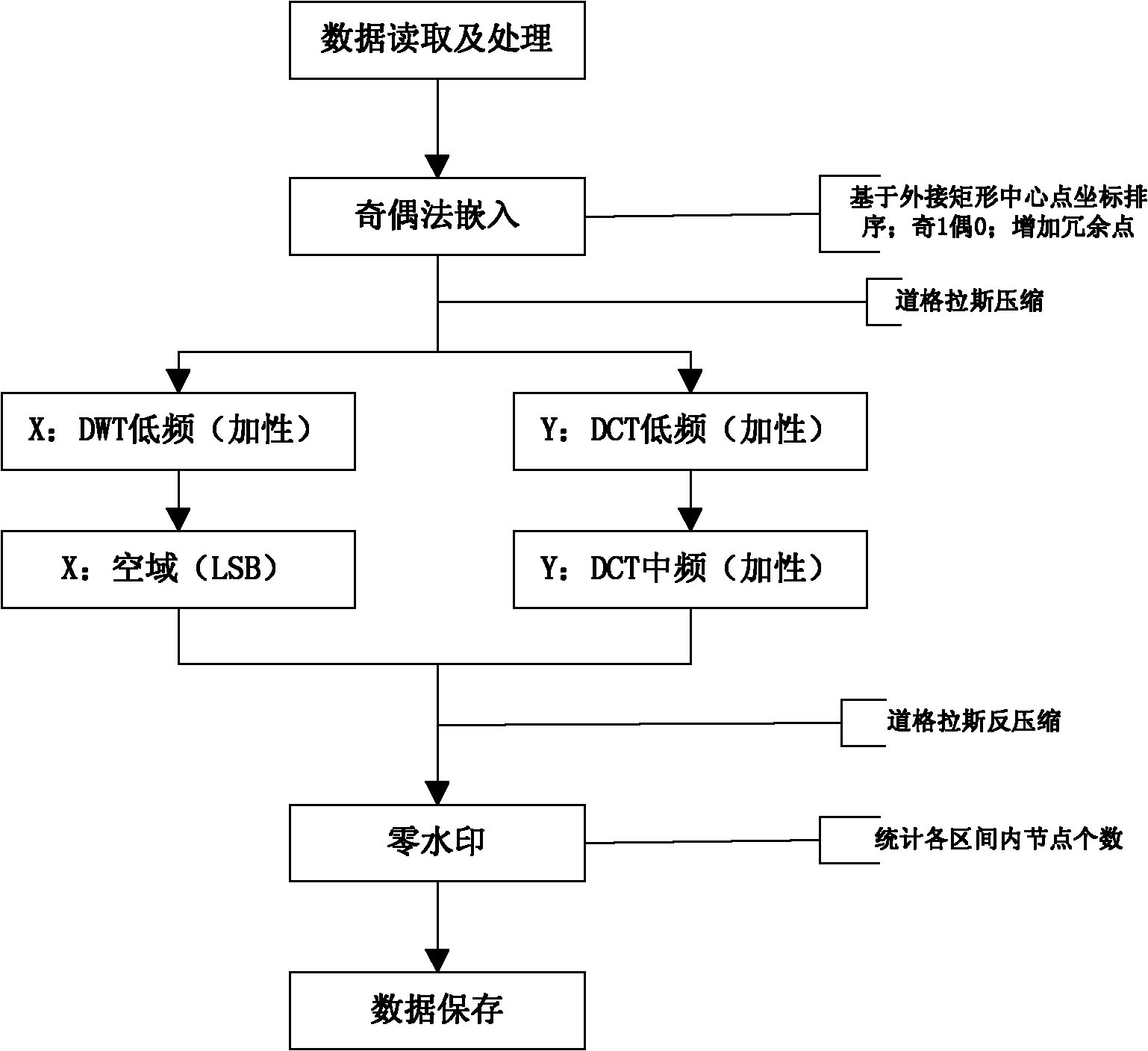
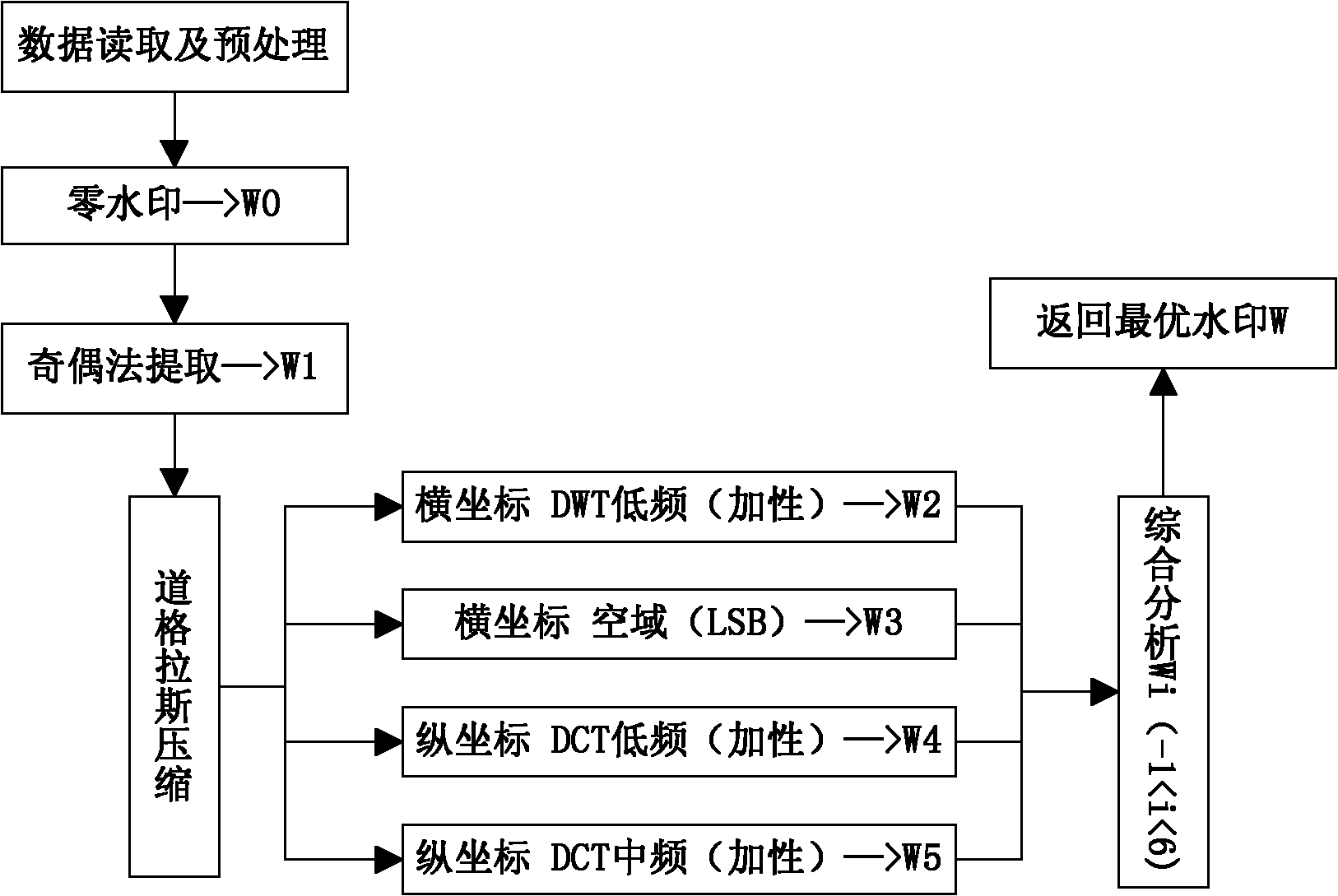
The invention discloses a multiple digital watermarking method for geographic information system (GIS) vector data, and belongs to the field of geographic information copyright protection. The watermark embedding process of the method comprises the following steps of: reading and processing the data; embedding algorithms by an odd-even method; respectively embedding watermarks into a spatial domain, a discrete wavelet transform domain, a discrete cosine transform domain of horizontal coordinates and vertical coordinates by a low-order additive method and a least significant bit substitution method; adopting a zero-watermark algorithm; and storing watermark-containing data. The watermark extraction process of the method is the inverse process of the embedding process. A practical multiple digital watermark protection method is comprehensively integrated aiming at the common attack modes of the GIS vector data and according to the principle and anti-attack performance of each single algorithm. Various embedding modes are adopted and the specific embedding position of each watermark is controlled, so that embedding and extraction are non-interfering, conflicts are avoided, the advantages of each algorithm are exerted and complemented and the anti-attack capability of digital watermarks is greatly improved.
Owner:苏州南师大智慧创意产业有限公司
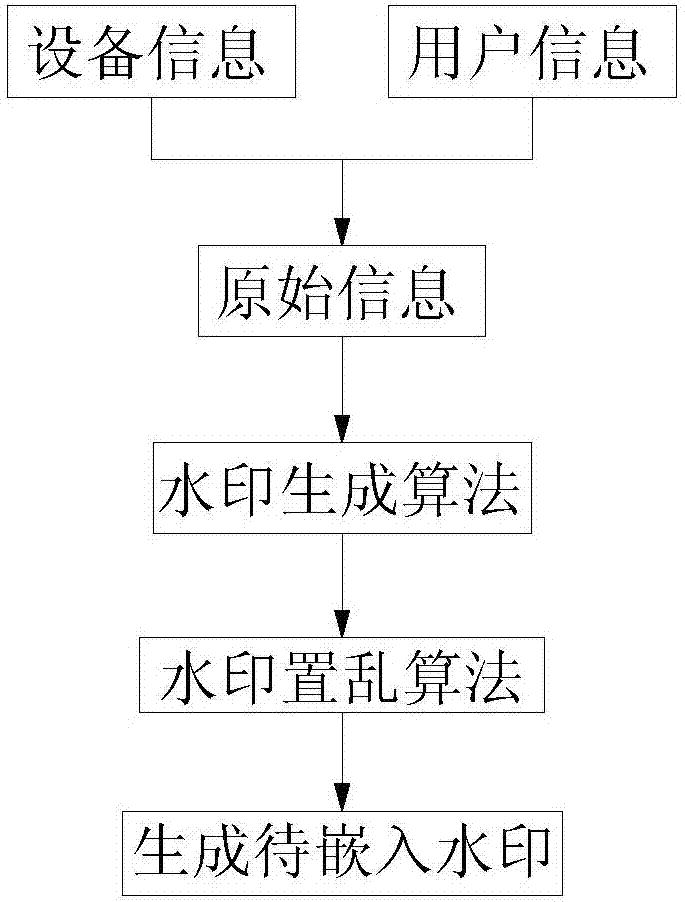
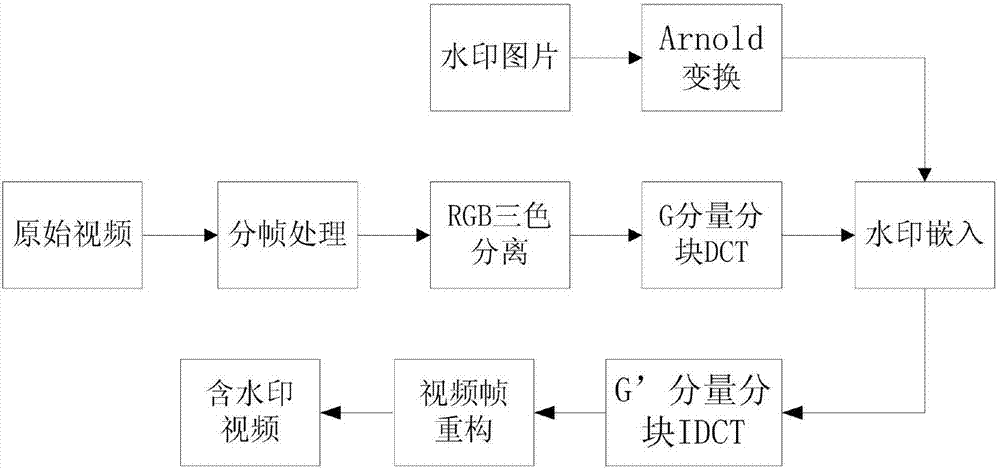
Video source tracing and encryption method based on watermark technology
InactiveCN107027055AAvoid damageGuaranteed video qualityDigital video signal modificationSelective content distributionSource tracingExtraction algorithm
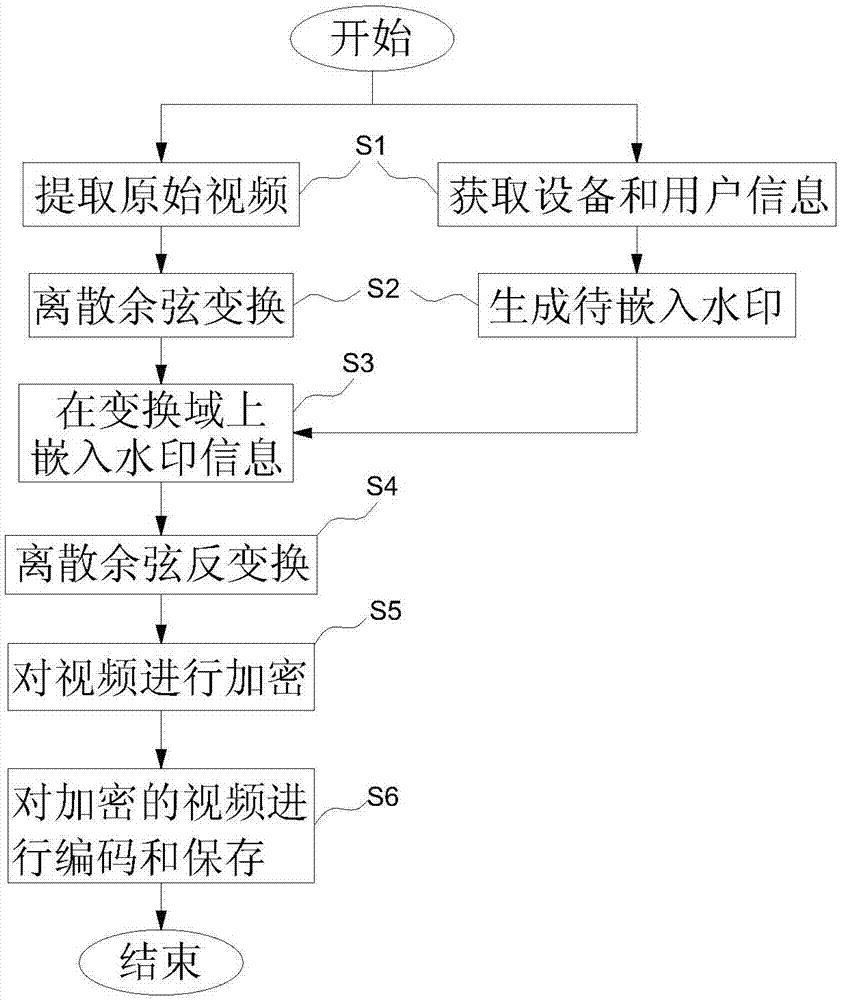
The invention relates to a video source tracing and encryption method based on a watermark technology. The method comprises the steps of extracting an original video and obtaining device information and user information; transforming the original video from a time domain to a frequency domain through adoption of a discrete cosine transform algorithm, and generating a to-be-embedded watermark through adoption of a watermark generation algorithm; embedding the to-be-embedded watermark through adoption of a watermark embedding algorithm, thereby generating the video containing the watermark; generating a time domain video containing the watermark through adoption of an inverse transform algorithm; carrying out encryption through adoption of a key frame extraction algorithm and a video head information encryption algorithm, thereby forming an encrypted video file; and coding and storing the encrypted video file. According to the method, the generated video containing the watermark is good in quality, high in concealment and security and good in video sensuality; the method is good in encryption effect and high in security; relatively good source tracing and encryption effects are achieved; the video sharing security and circulation traceability are realized.
Owner:ANHUI SUN CREATE ELECTRONICS
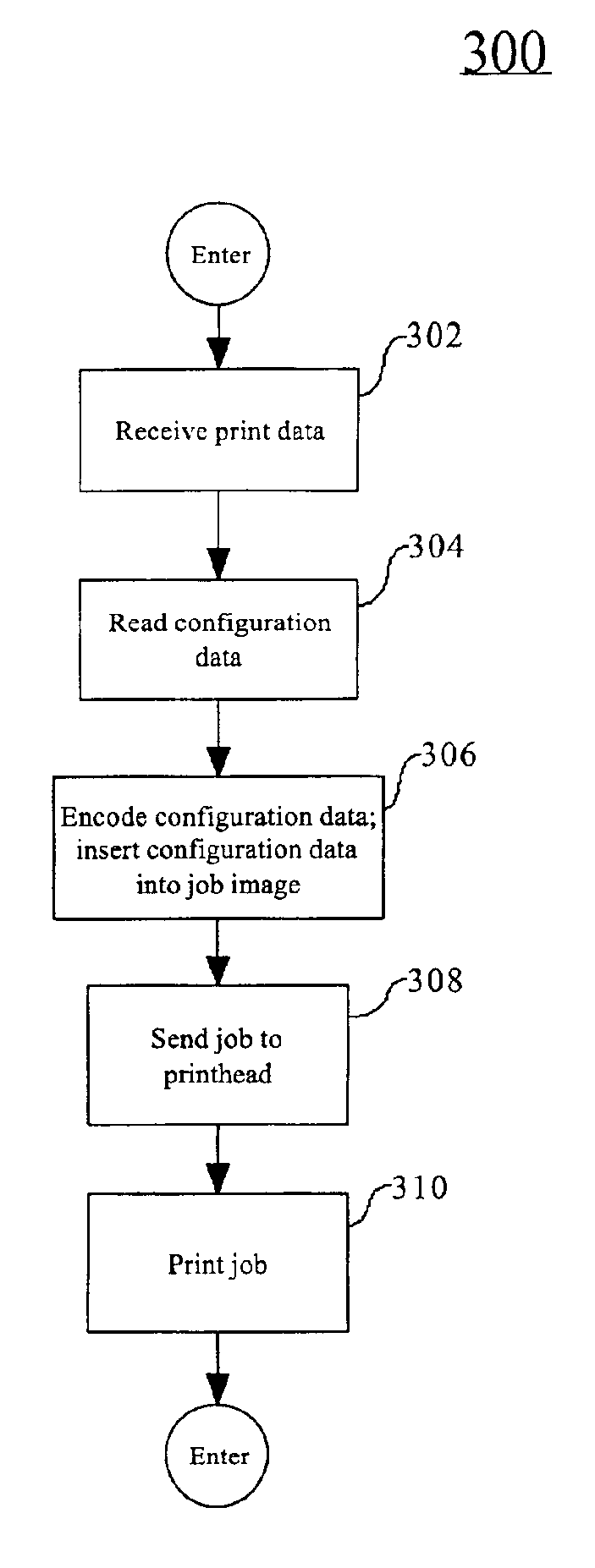
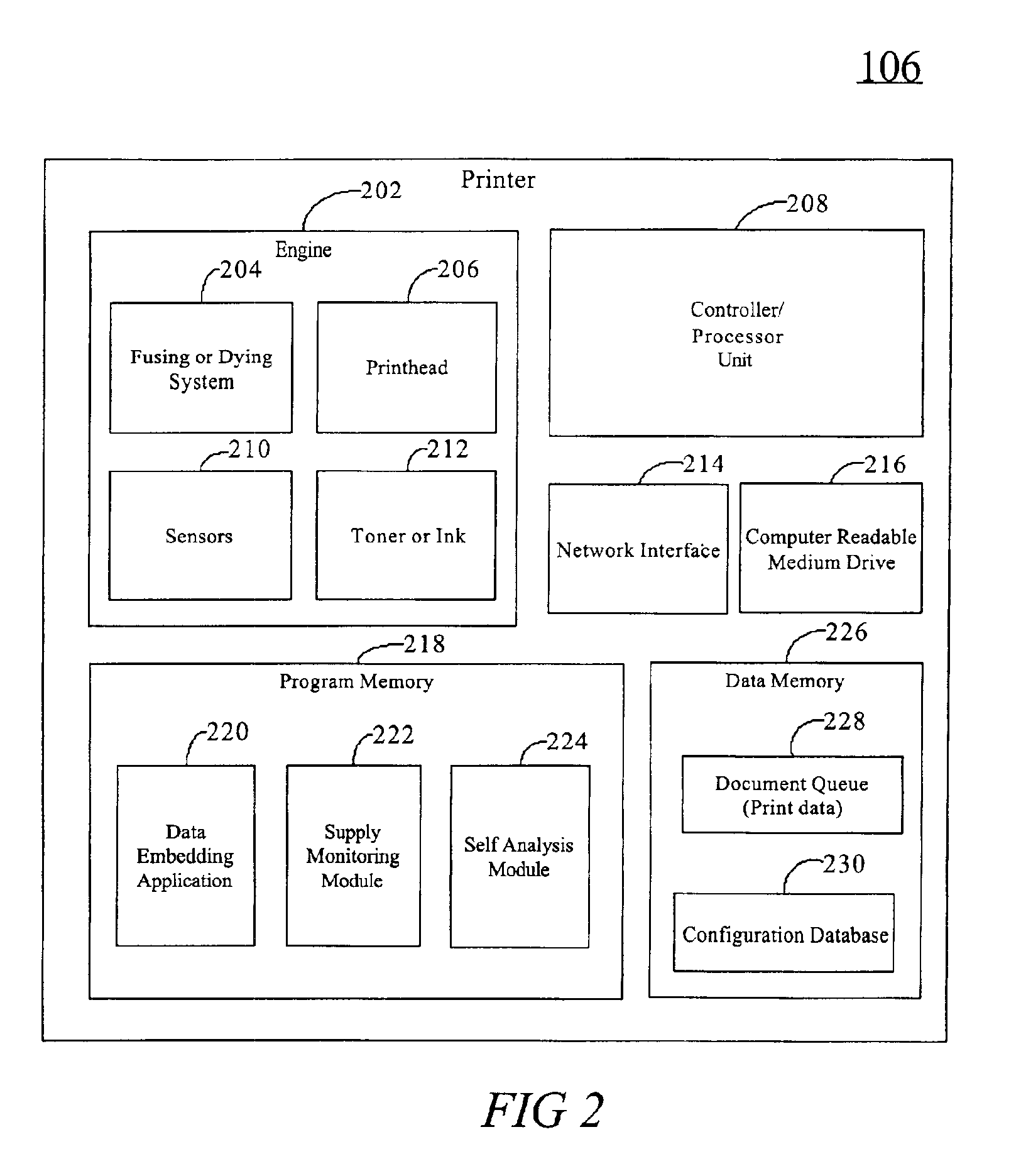
System and method for diagnosing printer problems and notarizing prints by evaluating embedded data
A method triggers a printer (106) to receive a trigger to initiate an embedding algorithm (220), receive the print data (228); read the printer configuration data (230); encode the configuration data (230); insert the configuration data (230) into the print data (228); send the print data (228) to a printhead (206); and print the data. The printed data is then scanned, run through analysis software, and the embedded data is returned. The embedded data can then be used to diagnose printer problems or as a digital notary.
Owner:IBM CORP
Method for detecting unknown malicious code
InactiveCN102142068ADetection speedAccurate divisionPlatform integrity maintainanceFeature vectorAlgorithm
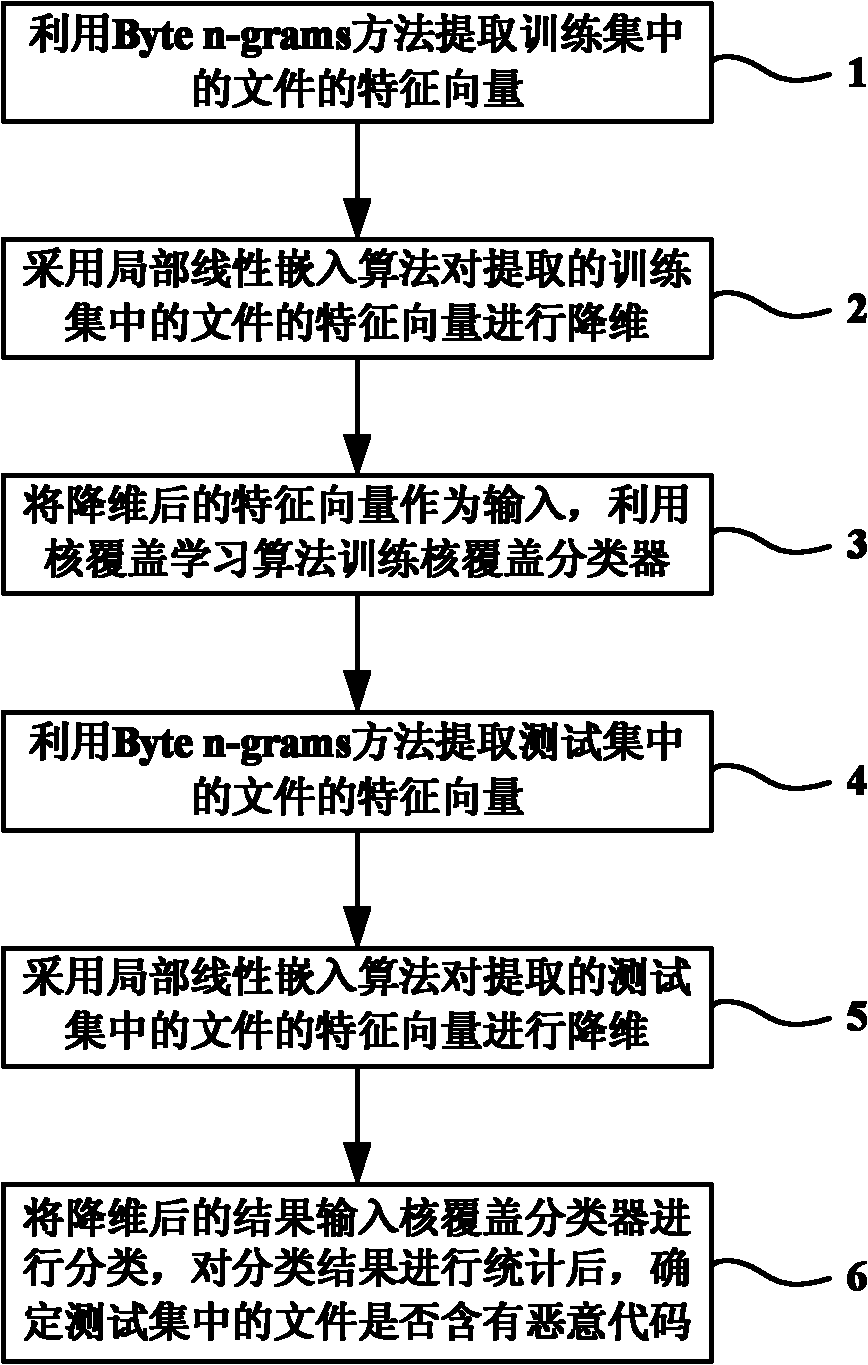
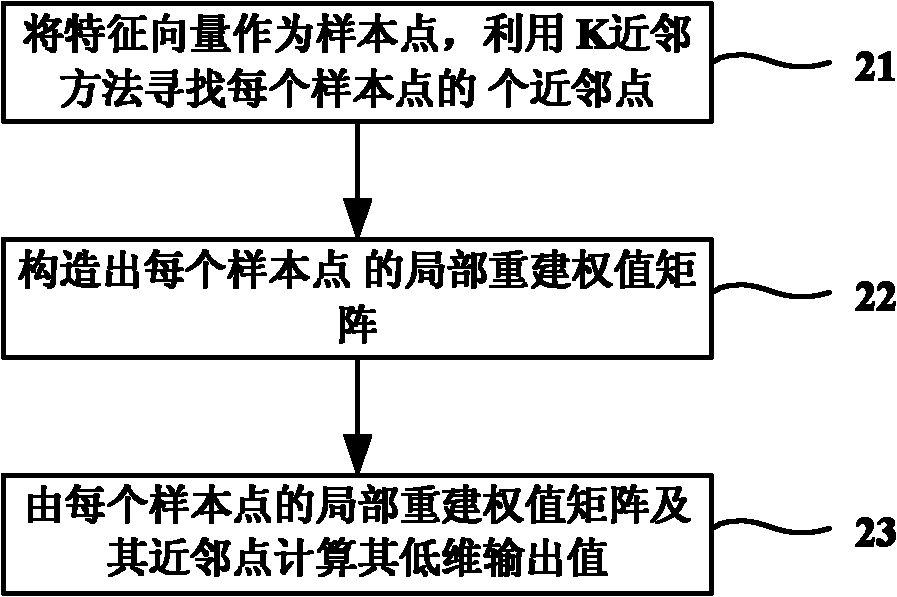
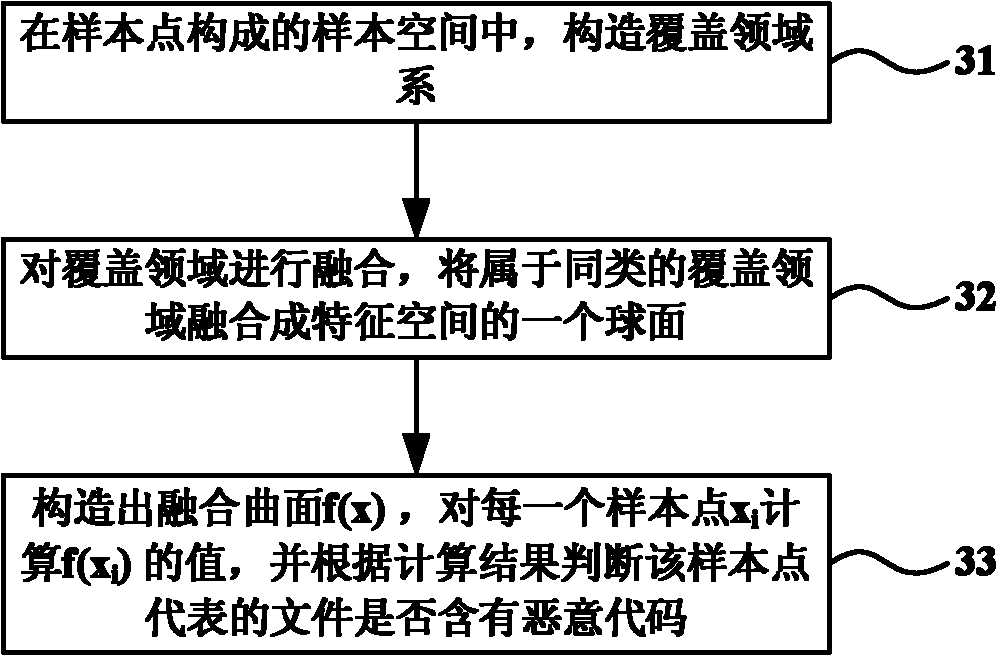
The invention discloses a method for detecting an unknown malicious code in the technical field of information safety, which can detect the malicious code in a file in advance under the situation that a malicious code library is not updated. The method comprises the following steps: extracting the feature vector of a file in a training set by utilizing a Byte n-grams method; carrying out the dimension reduction to the extracted feature vector of the file in the training set by adopting a local linear embedding algorithm; taking the feature vector after being subjected to dimension reduction as input, training a kernel cover classifier by utilizing a kernel cover learning algorithm; extracting the feature vector of the file in a test set by utilizing the Byte n-grams method again; carrying out the dimension reduction to the extracted feature vector of the file in the test set by adopting the local linear embedding algorithm; inputting a result after being subjected to dimension reduction into the kernel cover classifier for classification; and calculating the classification result and determining whether the file in the test set contains the malicious code. With the adoption of the method, the detection speed of the file is improved, and the advanced accuracy detection of the malicious code is realized.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
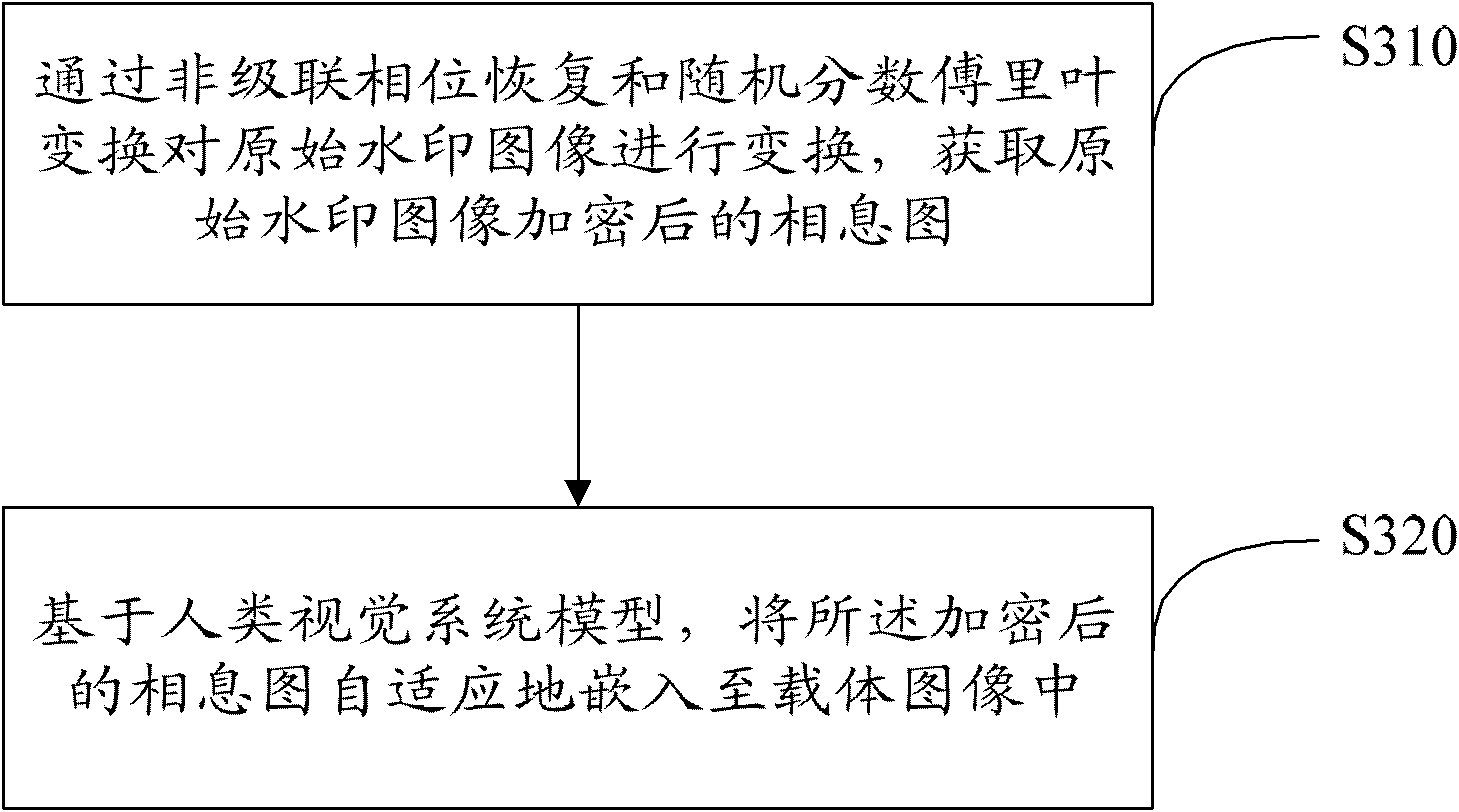
Encrypted kinoform based digital image watermarking embedding and extracting methods and systems
ActiveCN102142131AReduce data volumeGood clipping resistanceImage data processing detailsHuman visual system modelKinoform
The invention discloses encrypted kinoform based digital image watermarking embedding and extracting methods and systems. The digital image watermarking embedding method comprises the following steps of: transforming an original watermarking image through non-cascaded phase recovery and random fractional fourier transform (RFrFT) to acquire an encrypted kinoform of the original watermarking image; and adaptively embedding the encrypted kinoform into a carrier image based on a human visual system (MVS) model. In the invention, the safety of the watermarking of the kinoform is enhanced by using a non-cascaded iterative encryption method; meanwhile, blink watermarking is realized by adopting an adaptive embedding algorithm; and experiments verify that extremely high robustness against various attacks is achieved, and the safety performance is extremely high.
Owner:PEKING UNIV
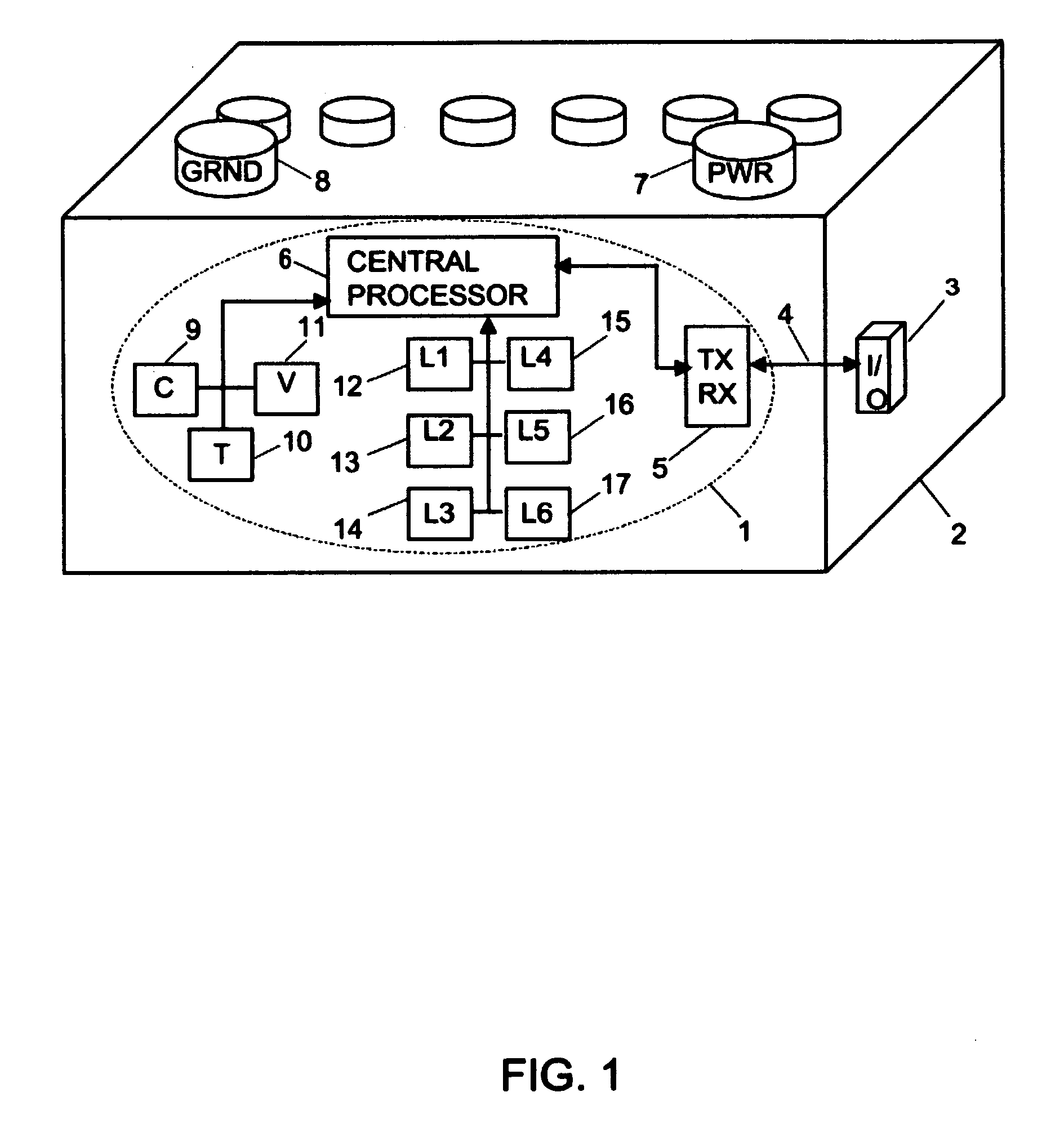
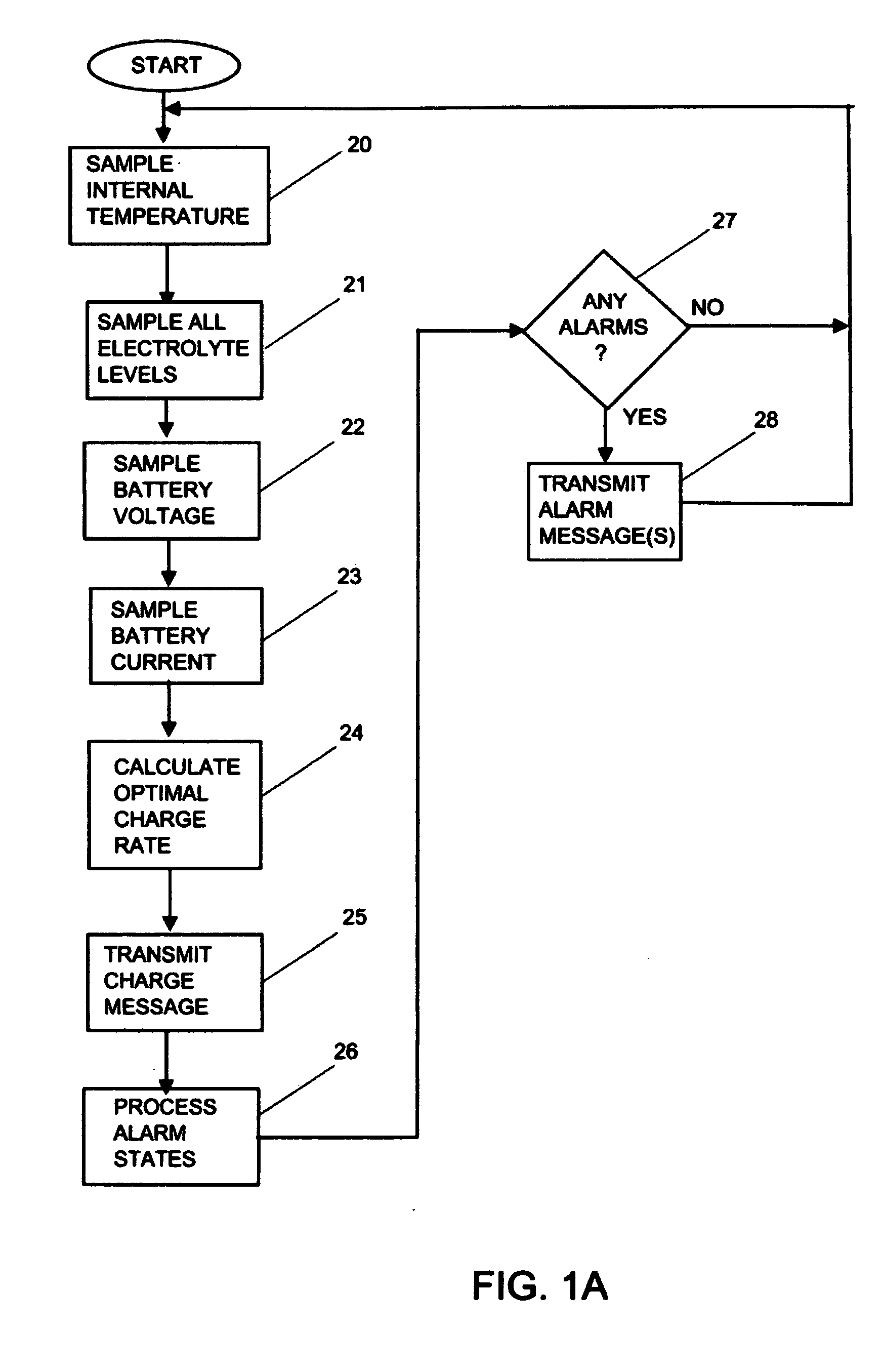
Embedded algorithms for vehicular batteries
InactiveUS20100292942A1Material analysis by electric/magnetic meansElectrical testingComputerized systemCharge rate
Owner:4 PEAKS TECH
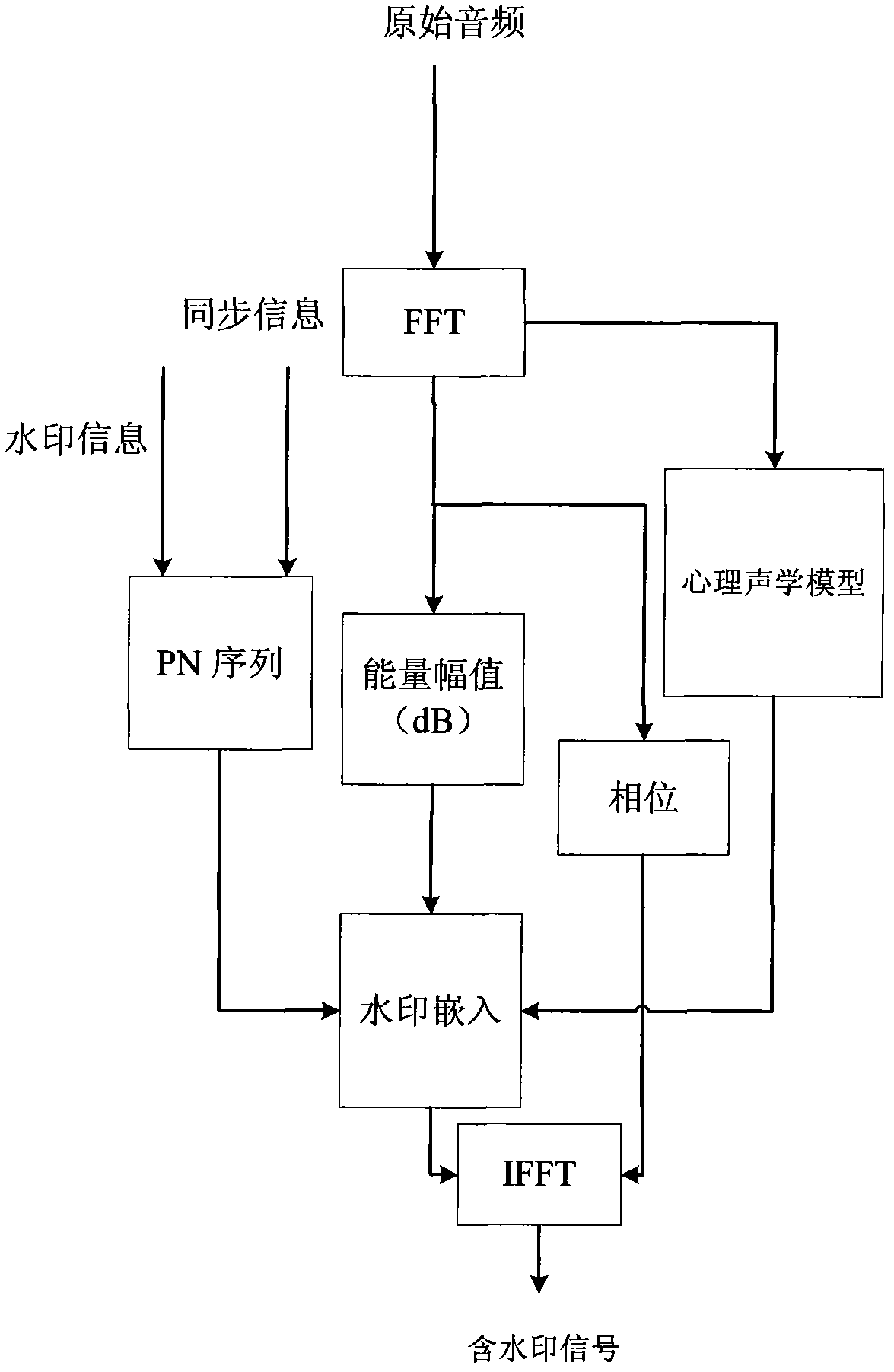
Digital audio watermarking algorithm for copyright management
ActiveCN102074240AGuaranteed imperceptibilityImprove robustnessSpeech analysisPaymentDigital Signature Algorithm
The invention relates to a method for performing copyright management by utilizing digital audio watermarking. The method comprises the following steps: embedding a watermarking signal in a logarithm domain of the audio signal energy so that the decoding is unrelated to the amplitude; reasonably designing the frame structure of the embedded watermarking information so that the timing statistical accuracy of a de-embedded result reaches second, and the decoding time accuracy and decoding accuracy rate are not influenced under the operations of cutting, splicing and inserting other audio signals and the like; encrypting the embedded information by an RSA (Asymmetric Algorithm) digital signature algorithm so that the embedded information has security; and effectively reducing interference of the carrier audio to the watermarking information by the embedding algorithm by using the relativity of the short-time stability of the audio so as to obviously improve the success rate and accuracy rate solved by the watermarking. In the method, a digital watermarking technology is introduced to identify the audio materials in a medium library, and then the broadcast flow or audio file are decoded and analyzed to obtain the service conditions of materials, thereby acquiring copyright payment information.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
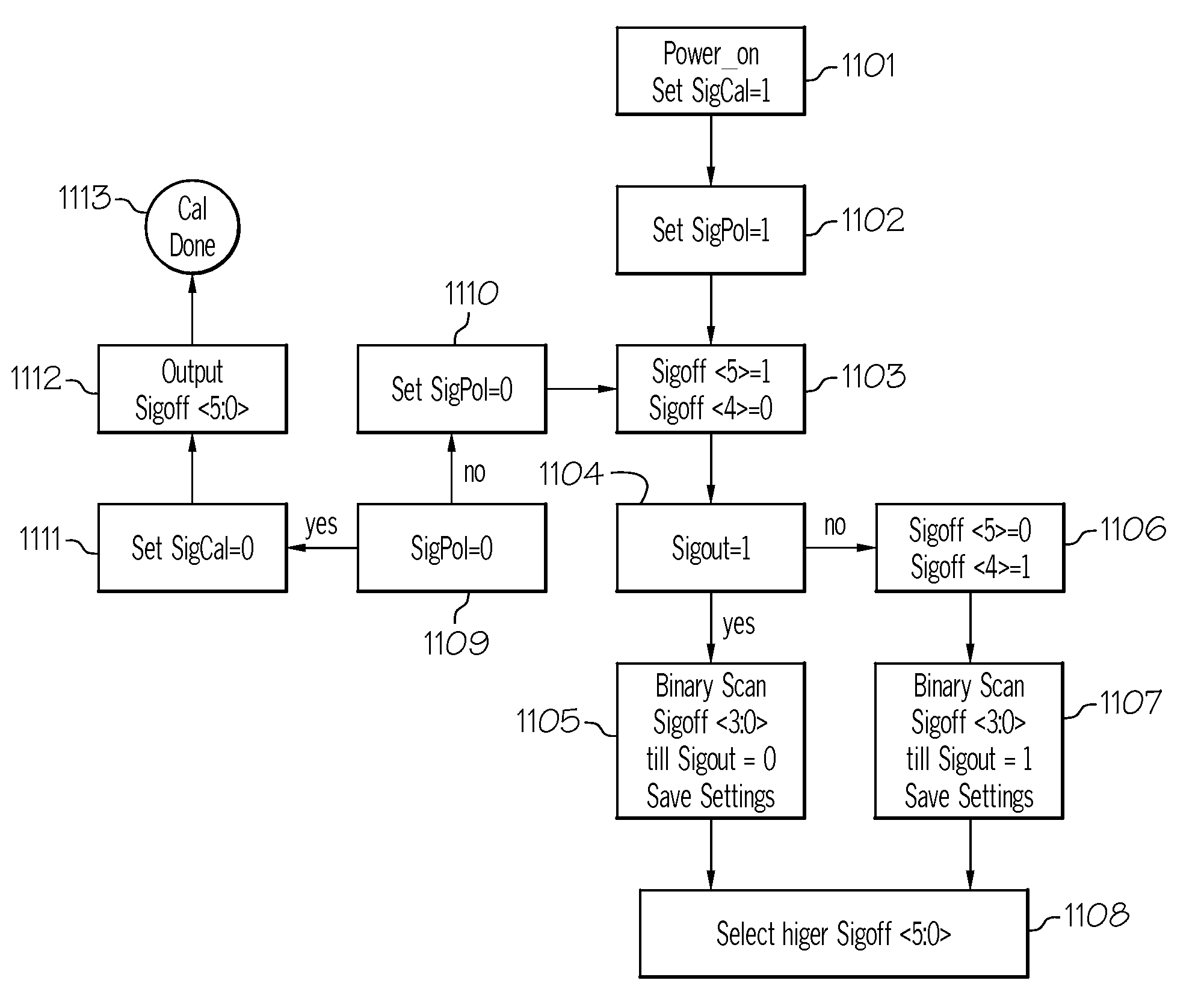
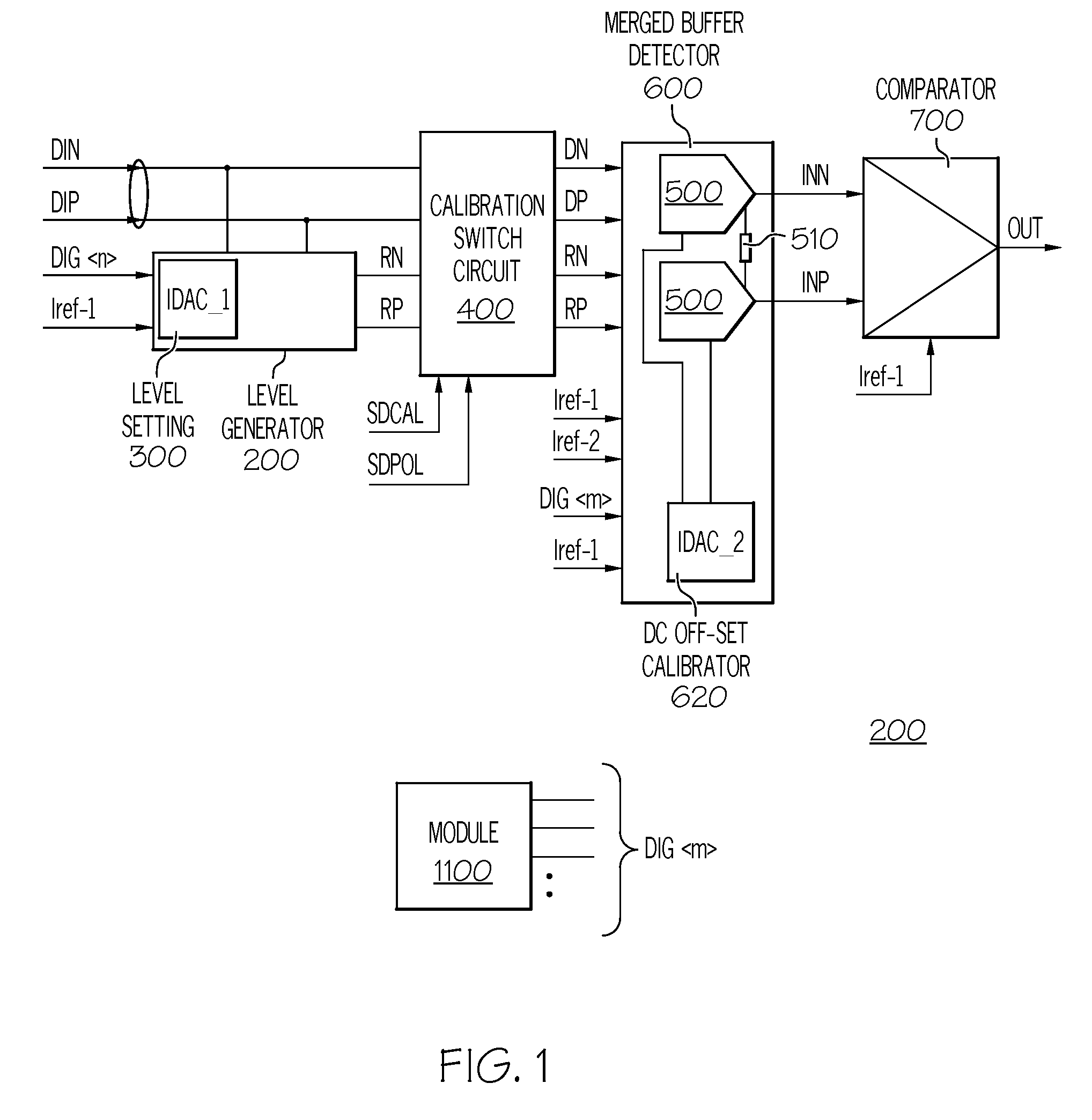
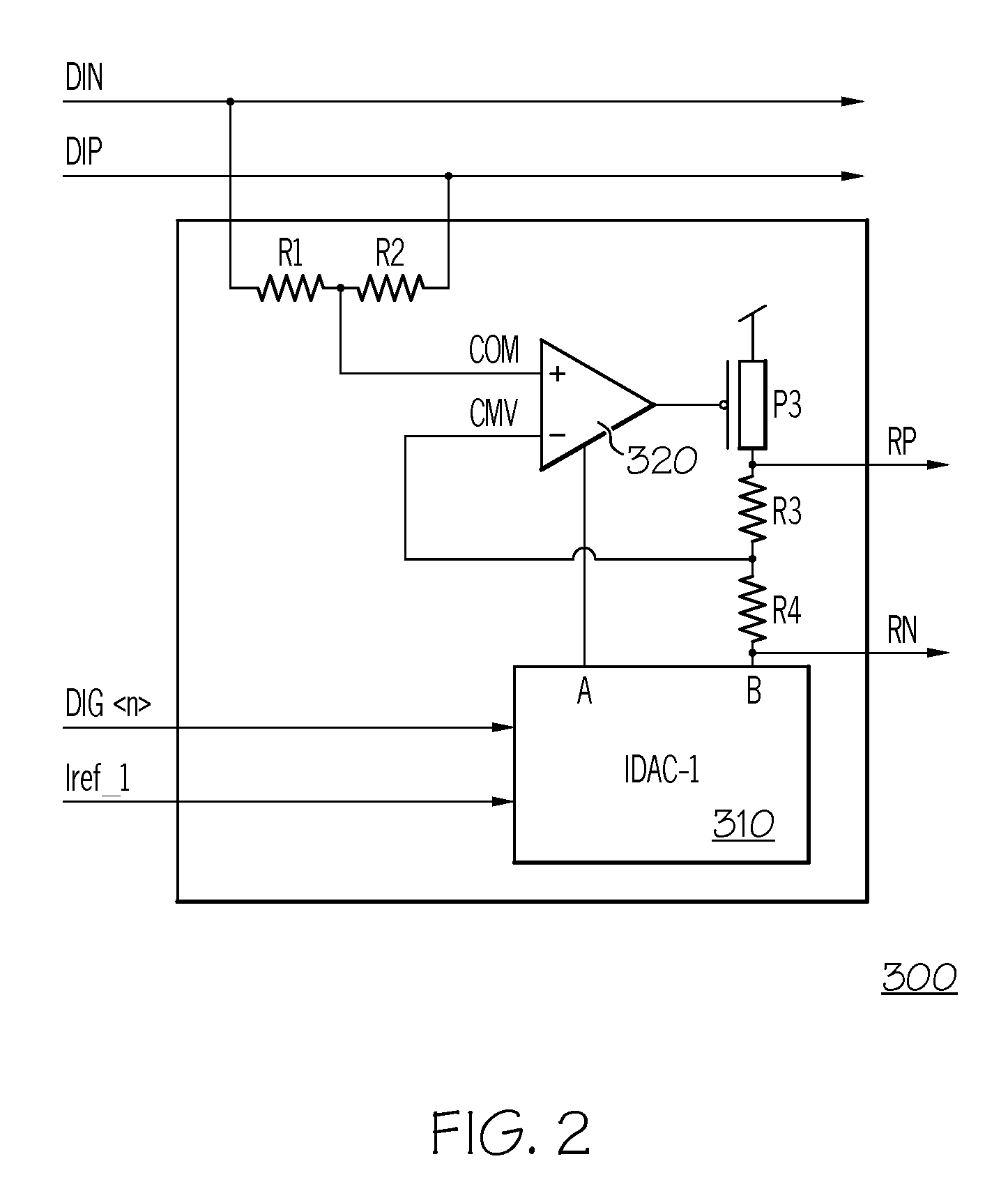
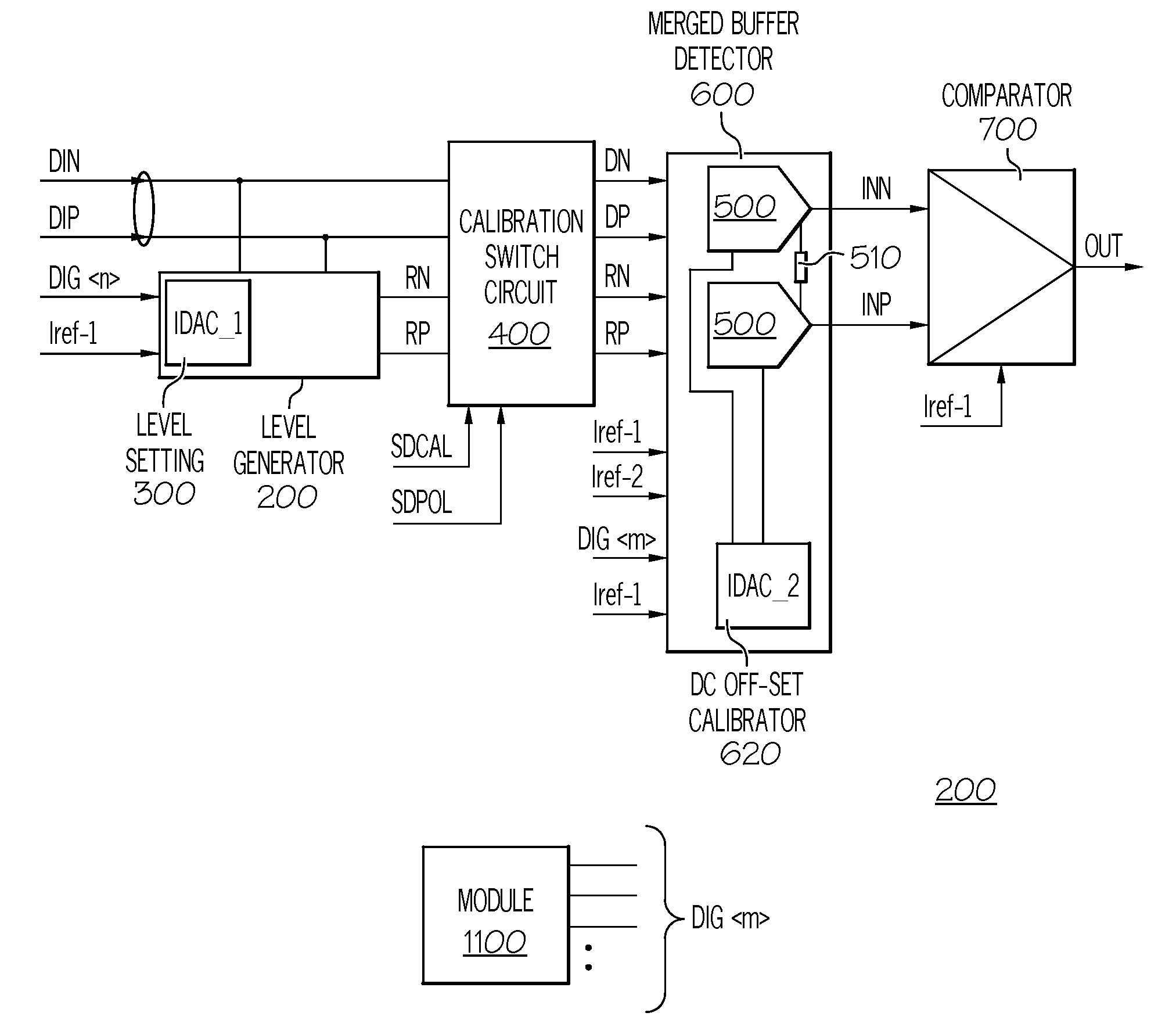
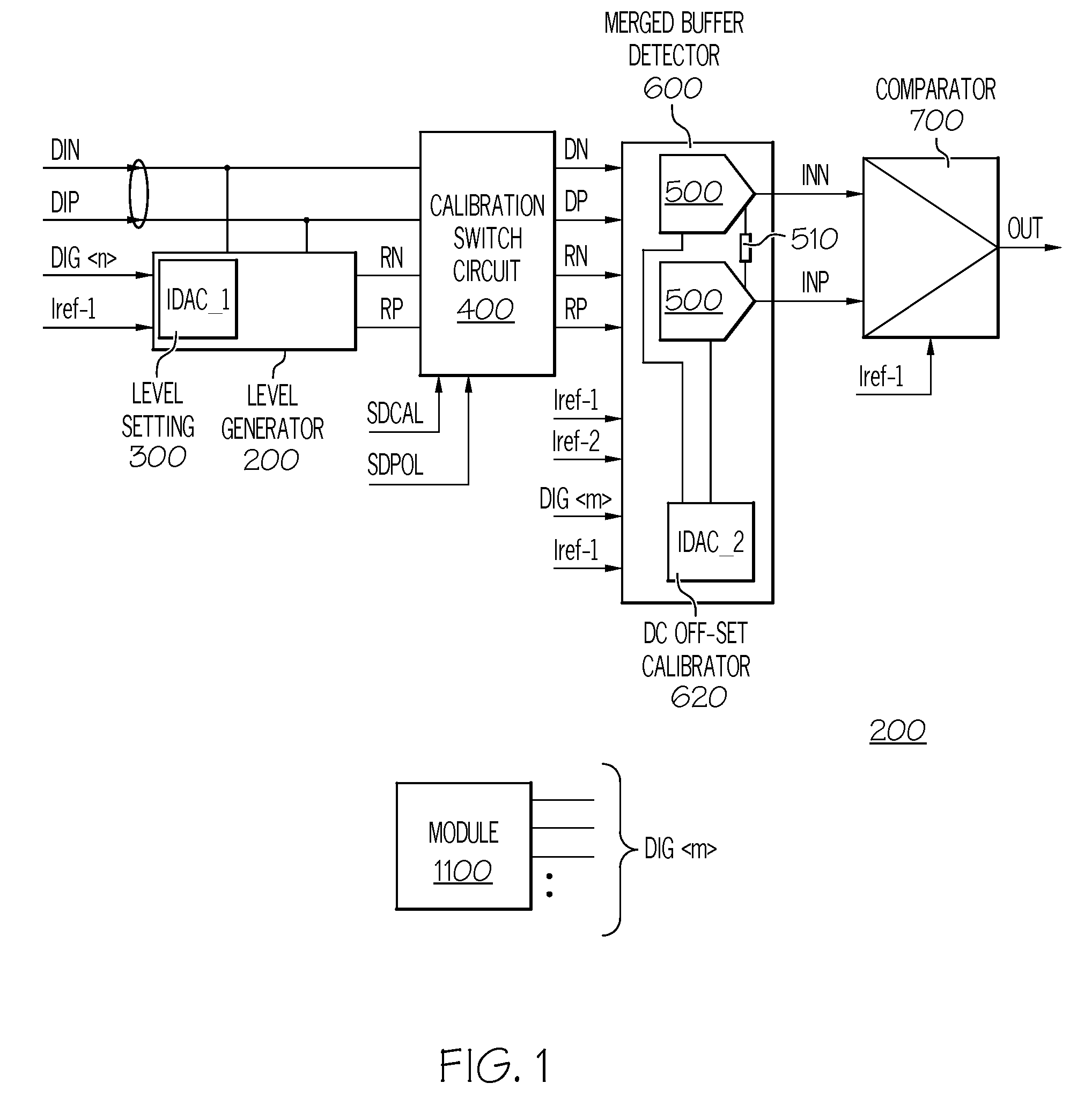
Signal Detector with Calibration Circuit Arrangement
ActiveUS20070271054A1Eliminate inherent differential signal imbalanceEliminate the inherent differential signal imbalanceMultiple input and output pulse circuitsCurrent/voltage measurementDifferential signalingImage resolution
A signal detector and method detect the presence or absence of an incoming differential signal. The method nullifies the DC off-set of the signal detector so that it can detect a signal within a very narrow window. The common mode levels of the signal and reference paths are used for calibration which is done automatically by use of an embedded algorithm residing in a digital block. The calibration range and resolution are predetermined to cope with the technology, modeling, design methodology and human error.
Owner:MARVELL ASIA PTE LTD
Digital image recovering method based on digital water mark technology
InactiveCN1492338AStrong resistanceImprove reconstruction qualityImage enhancementMemory loss protectionImage resolutionDigital image
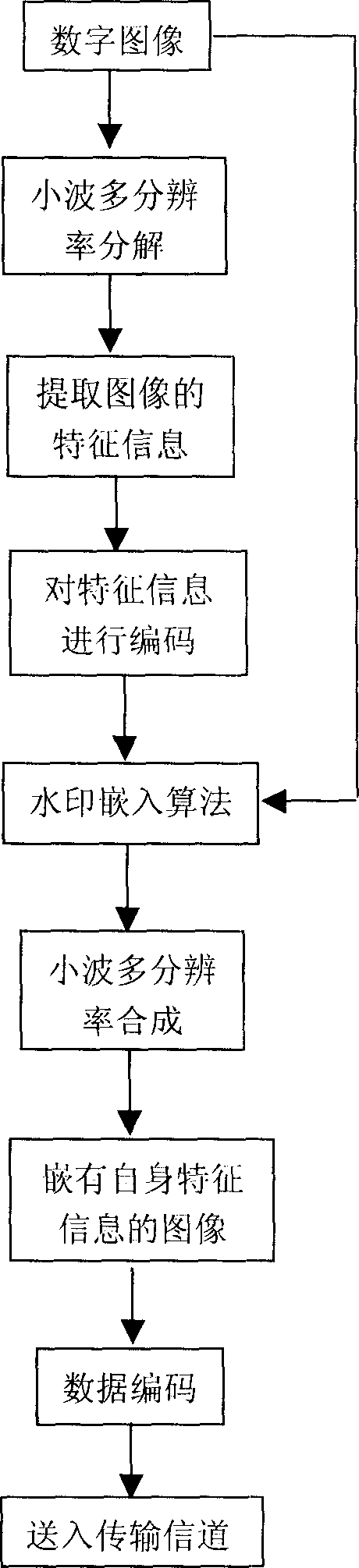
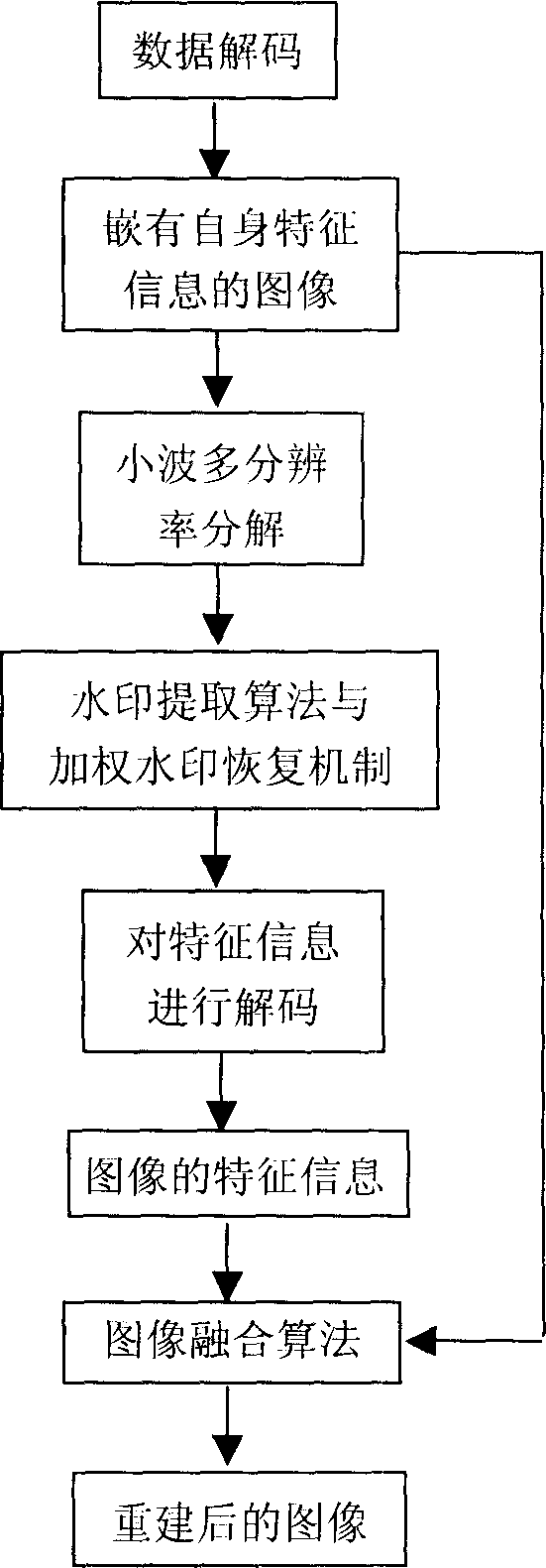
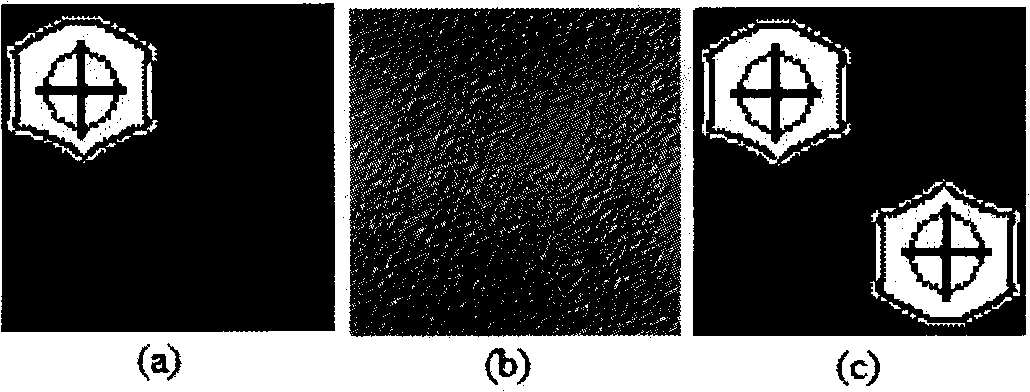
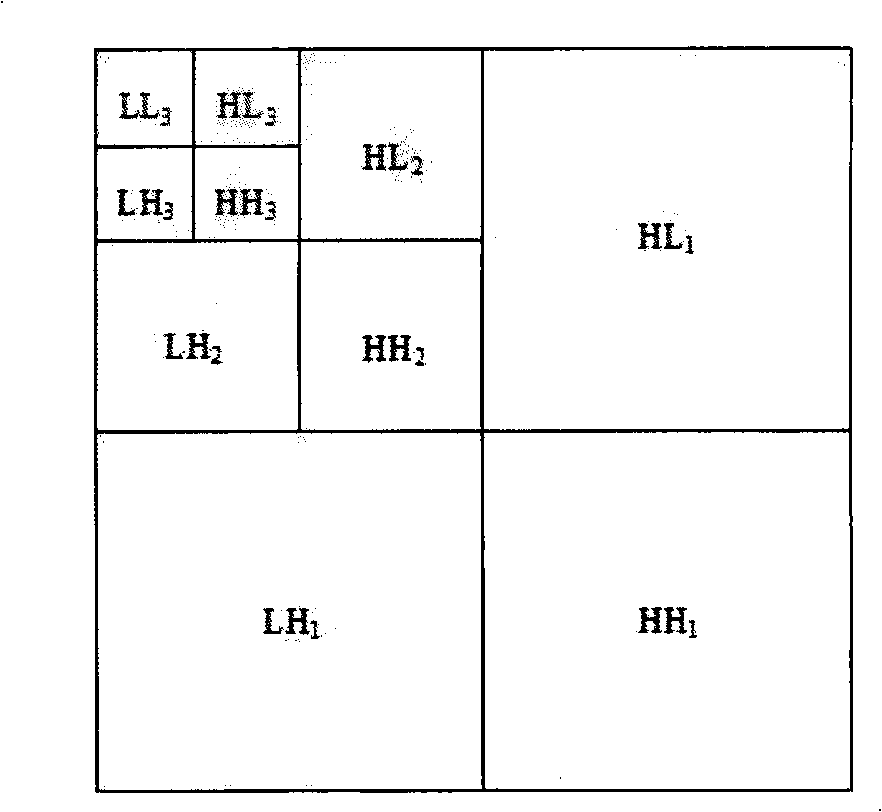
The digital image recovering method based on digital water mark technology processes digital image through quantizing the image characteristic obtained via wavelet multi-resolution disintegration operation into water mark signal through a quantizing and coding process, embedding the water mark into the image itself through water mark embedding algorithm and obtaining digital image with embedded characteristic information through wavelet multi-resolution synthesis. When the digital image via the said processing has some data loss during transmission or owing to the attack of hacker, the digital image may be restored through extracting water mark from the image, restoring the characteristic information of the image via decoding process and image fusion. The present invention can visual quality of digital image transmitted under harsh condition and may be used in protect digital image.
Owner:刘彤
Method for generating hologram digital watermarking by appliance computer
InactiveCN101493929AMany degrees of freedomEliminate strong correlationsImage data processing detailsMultimedia signal processingComputer generation
The invention discloses a digital watermarking method for generating a holographic image by applying a computer, which relates to a multimedia signal processing technology. The digital watermarking method for generating the holographic image by applying the computer has relatively good imperceptibility and strong anti-attack performance and is more flexible in calculating the holograph, low in cost and wide in application scope. The step for generating the holographic image by applying the computer serves as a watermark information sequence to be embedded into a carrier image. The steps for embedding the holographic image into the carrier image adopts a watermark embedding algorithm to embed the generated holographic image into the carrier image as the watermark information sequence of the carrier image, to ensure the robustness to various attacks and imperceptibility of a watermark. The step for a watermark detection algorithm is judging whether an image contains the watermark information; and the step for computer generation of the holographic image is generating the content of the watermark extracted on the computer clearly.
Owner:XIAMEN UNIV
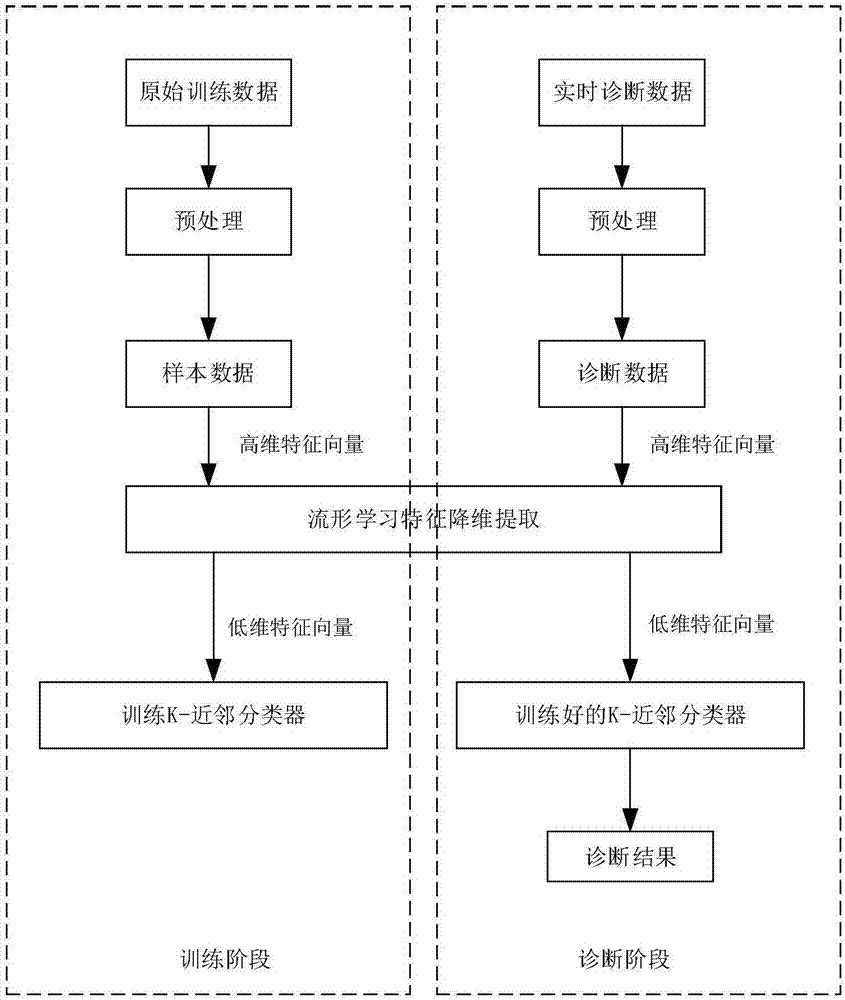
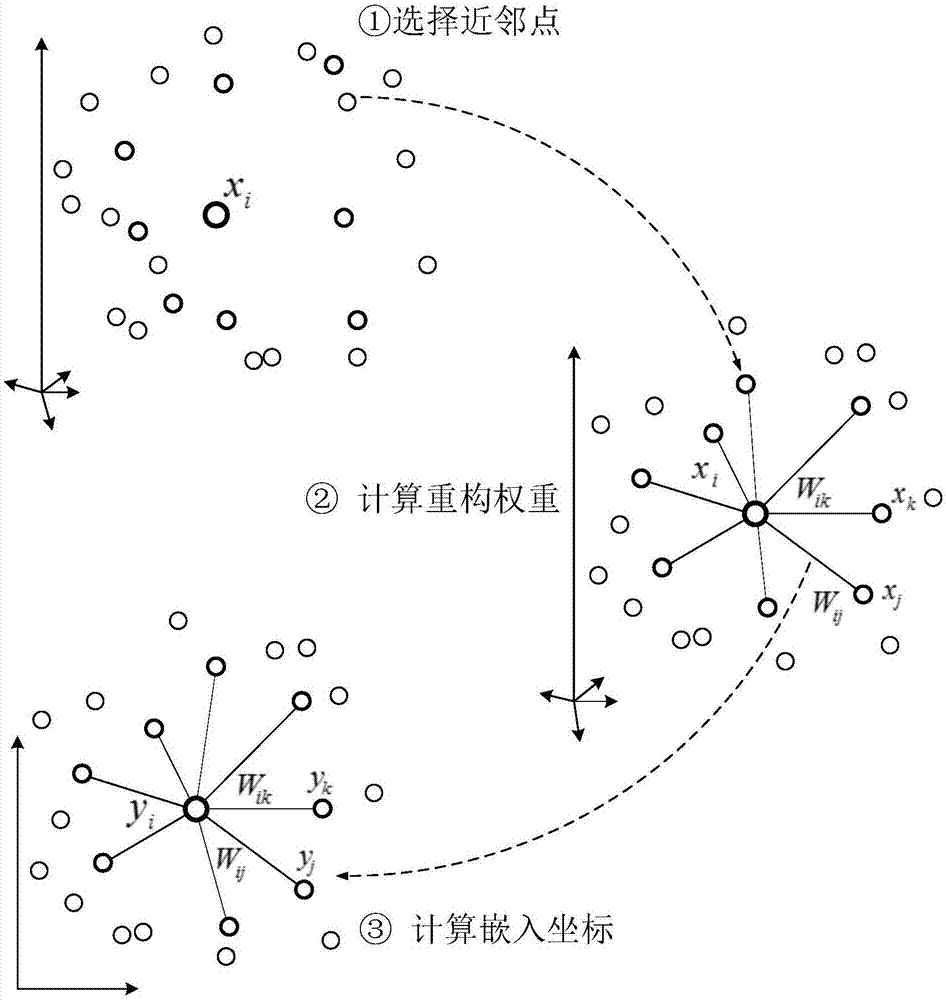
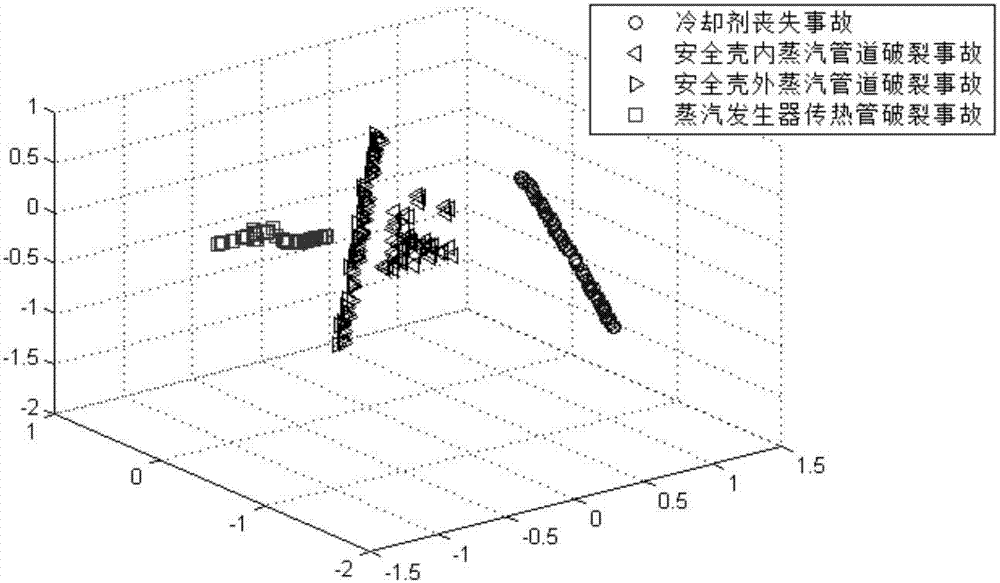
Nuclear power device fault diagnosis method based on local linear embedding and K-nearest neighbor classifier
ActiveCN107316057AEasy extractionEasy to calculateCharacter and pattern recognitionNuclear powerNonlinear manifold
The invention provides a nuclear power device fault diagnosis method based on local linear embedding and a K-nearest neighbor classifier. The method comprises steps of (1) acquiring operation data of a nuclear power device in steady-state operation and typical accident states as training data; (2) using the mean-variance standardization method, carrying out dimensionless standardization processing on the training data to obtain high-dimension sample data; (3) using the local linear embedding algorithm, extracting low-dimension manifold structures of the high-dimension sample data so as to obtain low-dimension characteristic vectors; (4) inputting the low-dimension characteristic vectors into a K-nearest neighbor classifier to carry out classification training; (5), acquiring real-time operation data of the nuclear power device, and repeating the steps of (2) and (3); and (6) using the trained K-nearest neighbor classifier to make decisions for classification of the characteristic vectors. According to the invention, by taking advantages of the nonlinear manifold learning method in the aspects of characteristic dimension reduction extraction, the provided method is suitable for fault diagnosis of nonlinear data high-dimension systems, and has quite high fault diagnosis accuracy.
Owner:HARBIN ENG UNIV
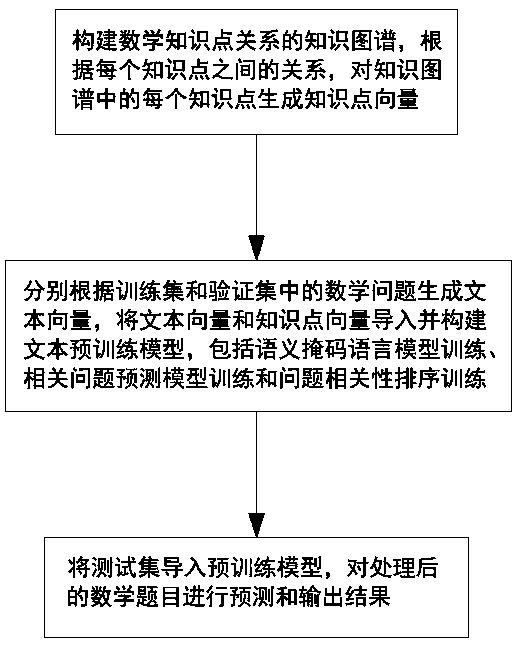
Pre-training model method for mathematical problem classification
PendingCN111563166AEnhanced Knowledge Point RepresentationAccurate predictionForecastingSpecial data processing applicationsAlgorithmInformation embedding
The invention discloses a pre-training model method for mathematic problem classification, and the method comprises the following steps: constructing a knowledge graph of mathematic knowledge point relations, and generating a knowledge point vector for each knowledge point in the knowledge graph according to the relation between the knowledge points; generating text vectors according to mathematical problems in the training set and the verification set, importing the text vectors and knowledge point vectors and creating a text pre-training model, wherein the model comprises semantic mask language model training, related problem prediction model training and problem correlation sorting training; and importing the test set into a pre-training model, predicting the processed mathematical questions, and outputting a result. The knowledge graph is integrated, and a novel masking and prediction strategy is provided to enhance knowledge point representation, so that prediction effect is moreaccurate; the model uses a knowledge embedding algorithm to encode a graph structure of a knowledge graph, and multi-information embedding is used as input of the model, so that the accuracy of pre-training is greatly improved.
Owner:浙江学海教育科技有限公司
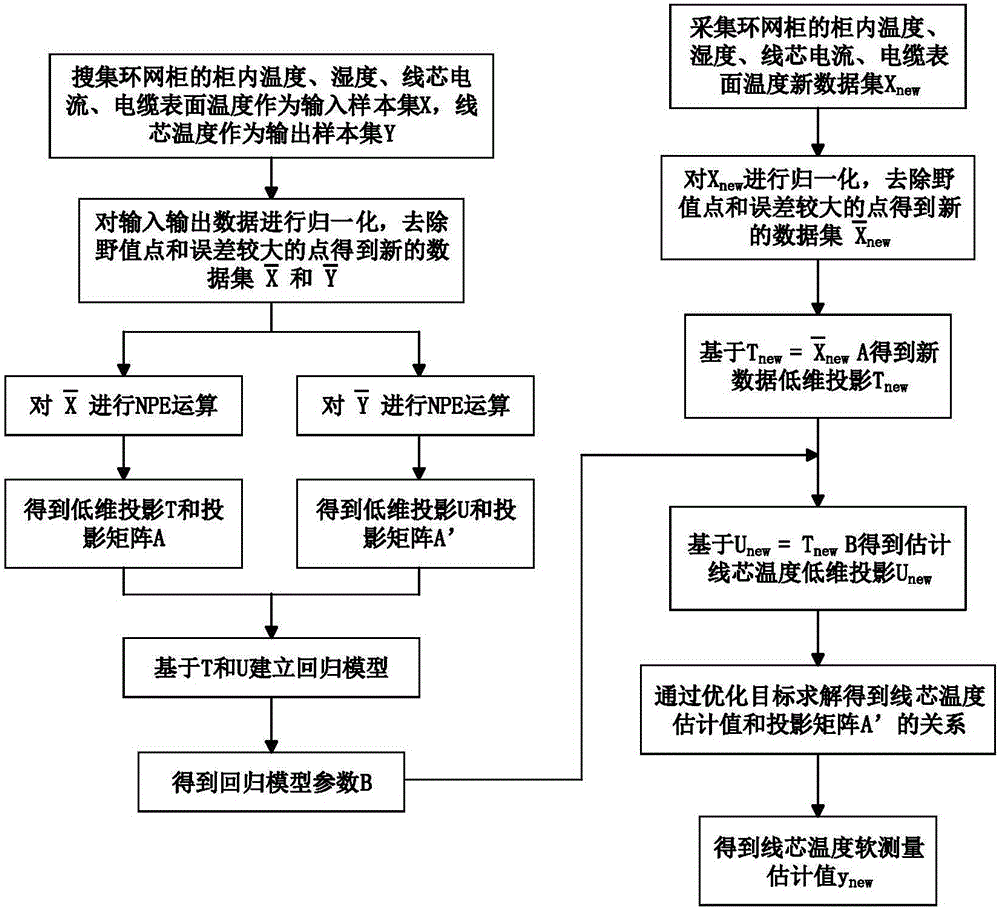
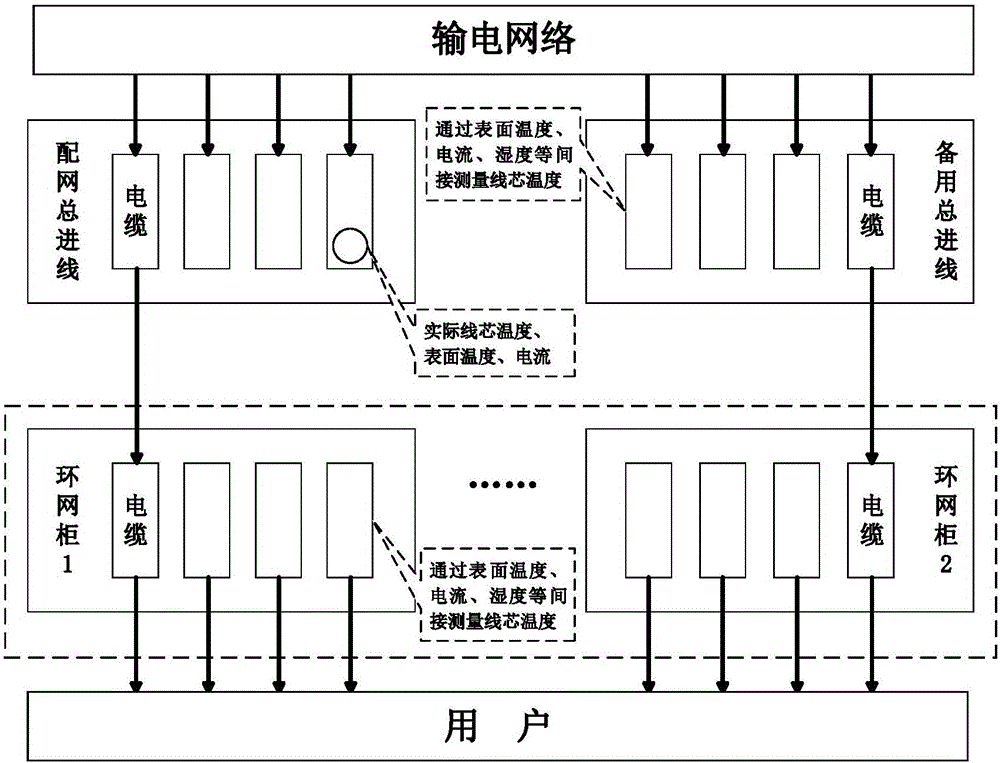
Ring main unit cable core temperature soft measurement method based on neighborhood preserving embedded regression algorithm
ActiveCN106644162ARealize online estimationEasy to measureThermometer applicationsFeature extractionOperability
The invention discloses a ring main unit cable core temperature soft measurement method based on a neighborhood preserving embedded regression algorithm. The ring main unit cable core temperature soft measurement method comprises that firstly, based on the local feature extraction strategy of the neighborhood preserving embedded algorithm, a regression optimization function which takes the internal temperature and the internal humidity of a ring main unit, the cable core current and the cable surface temperature as input, and takes the cable core temperature of a cable in the ring main unit as output is established, local features of input data and output data are reserved, and the maximum relationship between data is obtained; then based on lower-dimension latent variables of data, input and output features which construct data regression are obtained; and a cable core temperature soft measurement model is established. The ring main unit cable core temperature soft measurement method is advantaged in that by means of a data local feature extraction method, a traditional neighborhood preserving embedded algorithm is modified to be a regression model, and key variable information, of the ring main unit, which cannot be measured easily is obtained. According to the invention, the problem that the temperature of the cable core in the ring main unit cannot be measured easily is solved, and the accuracy and operability of on-line monitoring and fault locating of the ring main unit are improved.
Owner:YUNNAN UNIV +1
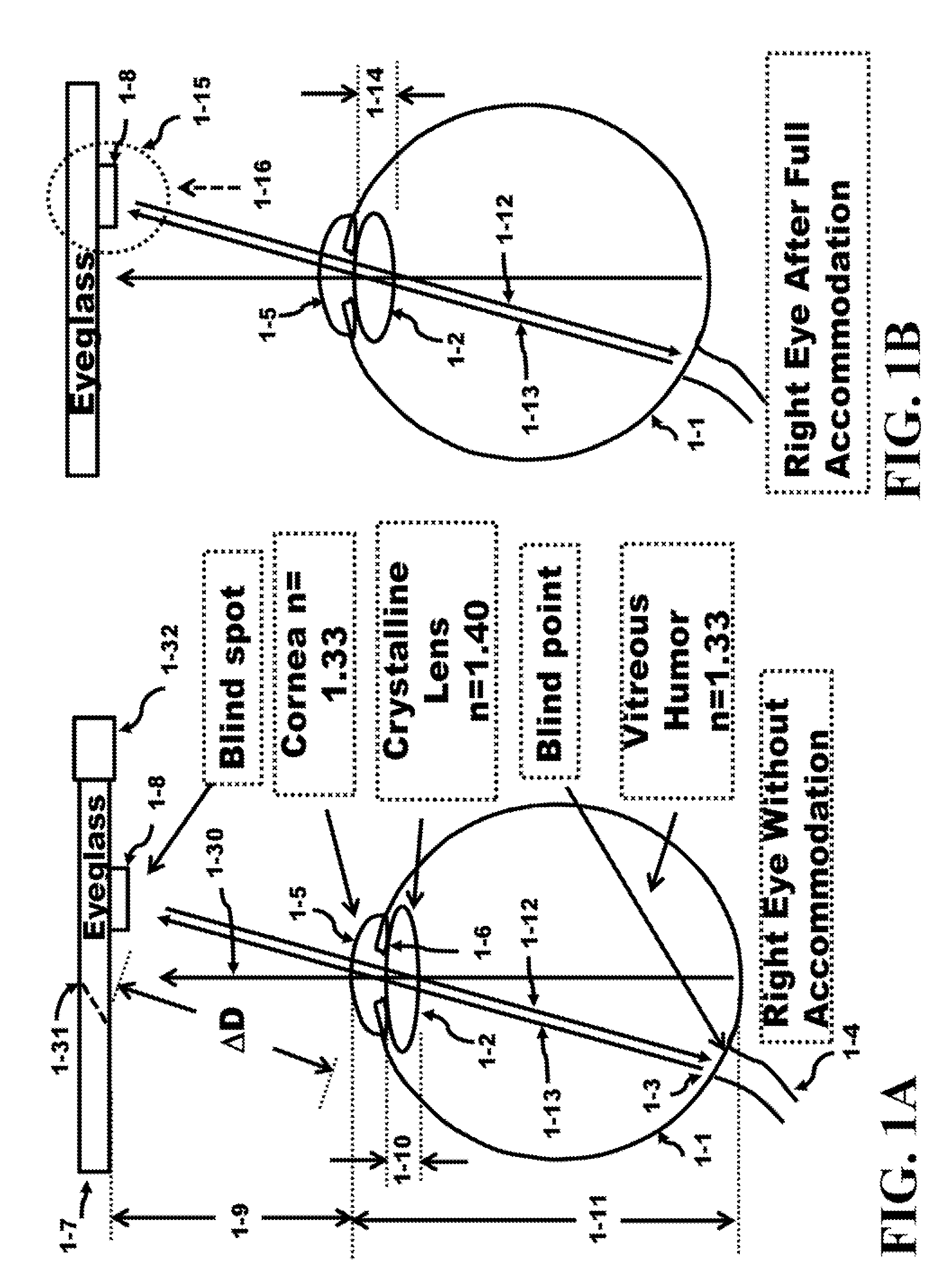
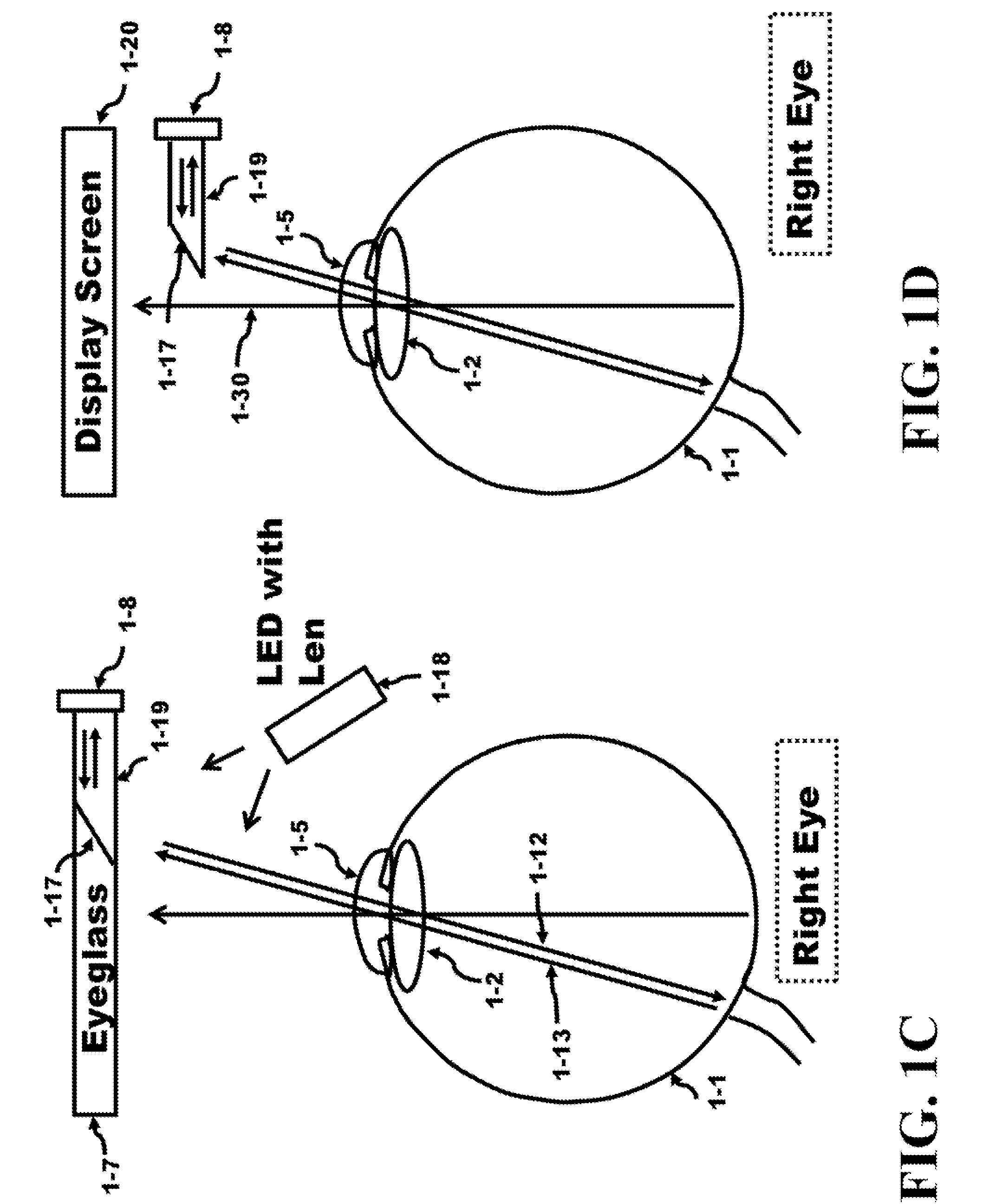
Method and Apparatus for a Self-Focusing Camera and Eyeglass System
ActiveUS20140375788A1Quality improvementBaseline distanceColor television detailsClosed circuit television systemsEyewearDepth plane
An involuntary action adjusted by the accommodation of the crystalline lens of the eye provides the data to the embedded algorithm to get the new image. Instead of the user performing a voluntary action to control the embedded algorithm, an involuntary action by the user is used to control the embedded algorithm allowing the user to automatically adjust the Plane of Depth (POD) for a Light Field Photograph (LFP) image or an eyeglass image. The adjustment of eyeglass image is used by an accommodation system to control the mechanical system of lenses in an eyeglass to automatically focus the glasses over a range of PODs. In addition, a voluntary far / near button can be used manually to adjust the POD for both the LFP image and the eyeglass adjustment. The variation of the crystalline thickness to adjust the focus of nearby and distant objects is called accommodation.
Owner:TRACKTHINGS
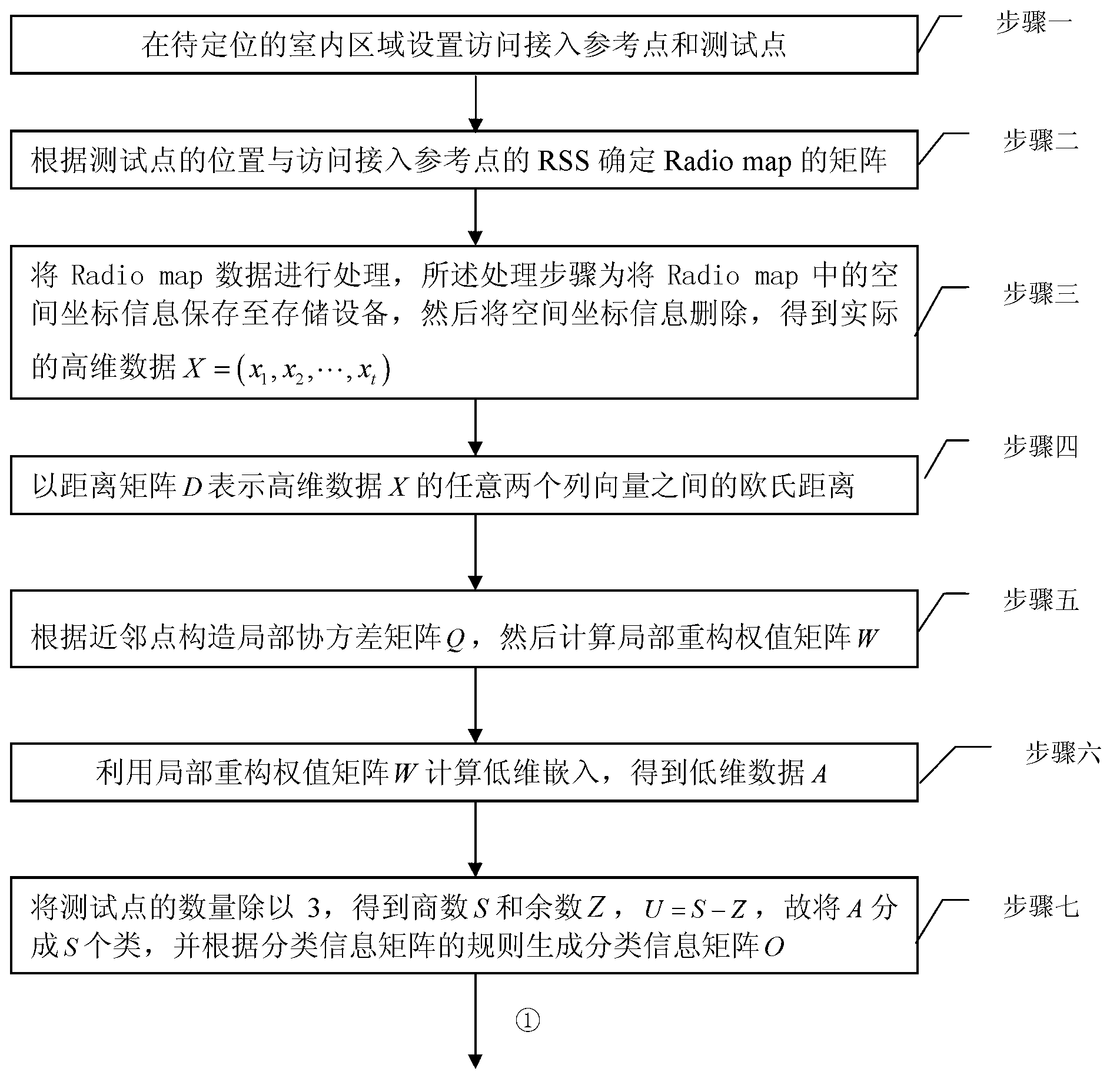
Local linear embedded algorithm based radio frequency map unsupervised classifying method
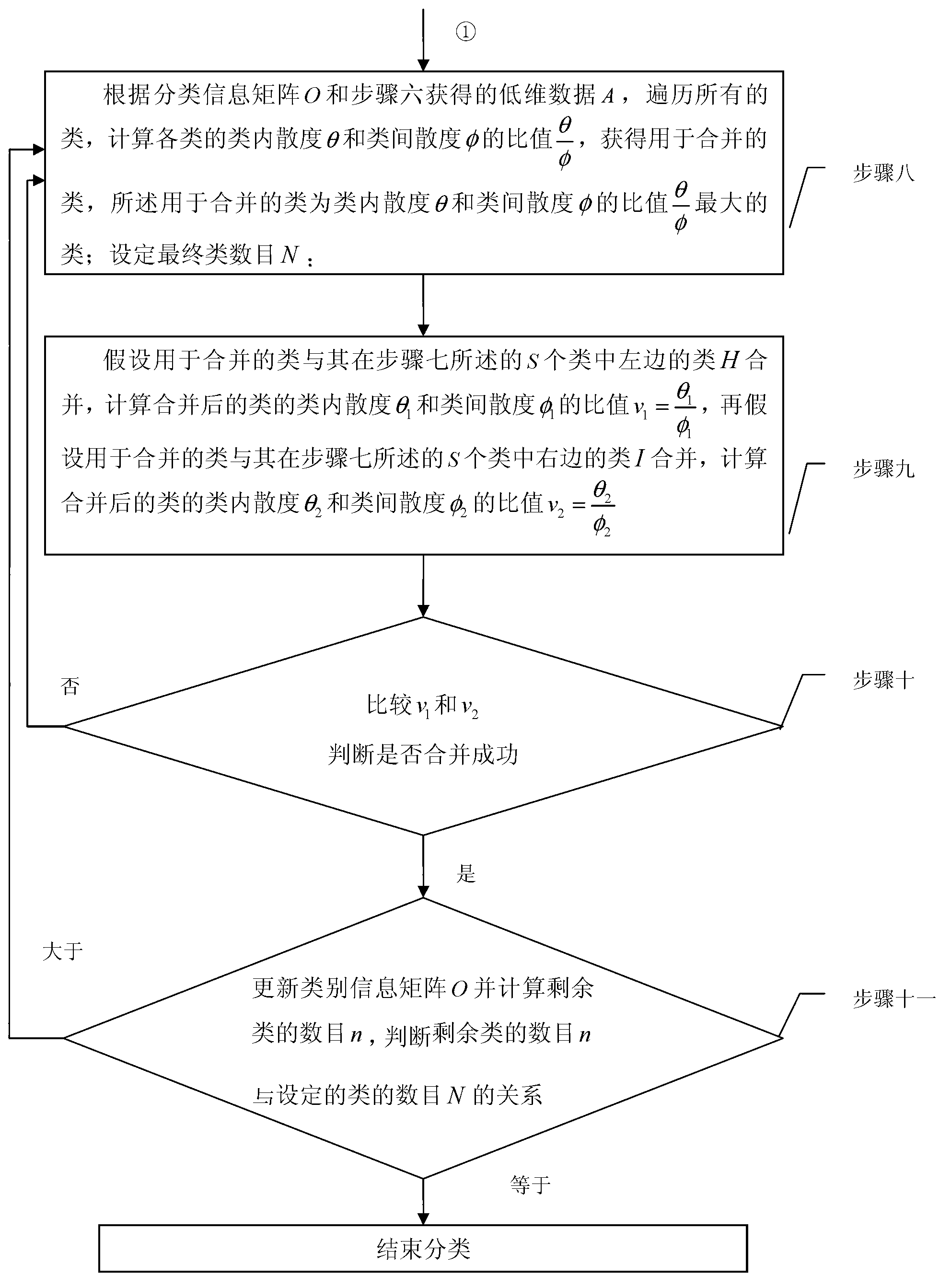
ActiveCN103258001AImprove effectivenessReduce computing costSpecial data processing applicationsClassification methodsRadio map
The invention relates to a local linear embedded algorithm based radio frequency map unsupervised classifying method and aims at solving the problem that existing radio frequency map classifying methods can only depend on space distribution of a to-be-positioned area for classification. The method includes setting an access reference point and a test point in a to-be-positioned indoor area; determining a matrix of a Radio map according to the position of the test point and RSS (radio-frequency signal strength) of the access reference point; processing data of the Radio map, namely, storing space coordinate information in the Radio map into storage equipment, and deleting the space coordinate information to acquire actual high-dimension data X=(x1, x2, ..., xt); and building a local covariance matrix Q according to adjacent points, calculating low-dimension embedding by utilizing a local reconstruction weigh matrix W, dividing low-dimension data into S classes and judging inter-class divergence and in-class divergence, merging the classes according to ratio conditions, and acquiring a final class information matrix. The local linear embedded algorithm based radio frequency map unsupervised classifying method can be widely applied to unsupervised classification of radio frequency maps.
Owner:哈尔滨工业大学高新技术开发总公司
Signal detector with calibration circuit arrangement
ActiveUS7486114B2Eliminate the inherent differential signal imbalanceMultiple input and output pulse circuitsCurrent/voltage measurementImage resolutionSignal detector
A signal detector and method to detect the presence or absence of an incoming differential signal. The method nullifies the DC off-set of the signal detector so that it can detect a signal within a very narrow window. The common mode levels of the signal and reference paths are used for calibration which is done automatically by use of an embedded algorithm residing in a digital block. The calibration range and resolution are predetermined to cope with the technology, modeling, design methodology and human error.
Owner:MARVELL ASIA PTE LTD
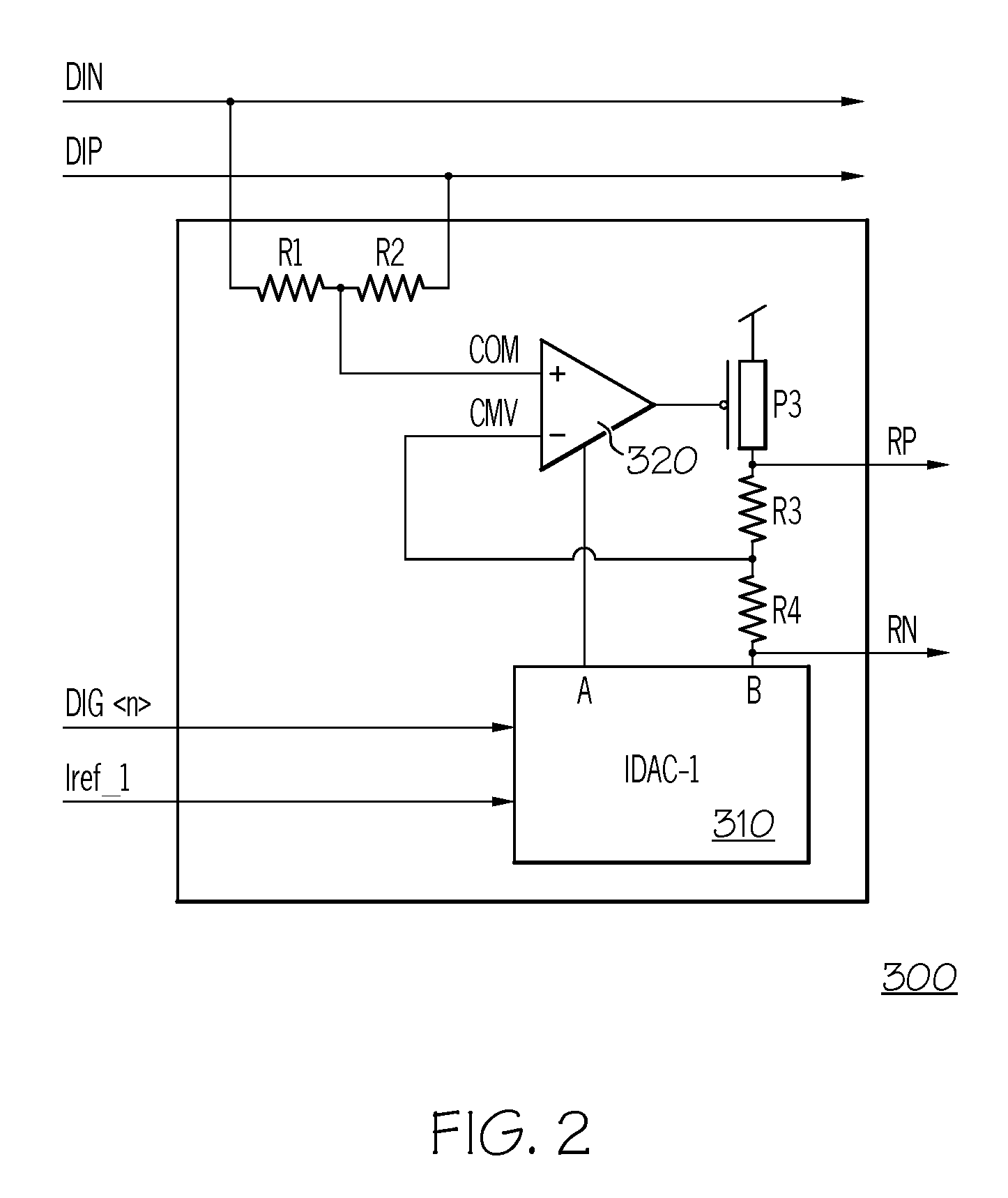
Heart sound signal classification identification method
ActiveCN108470156AAvoid Segmentation PreprocessingImprove processing efficiencyCharacter and pattern recognitionSupport vector machineSignal classification
Owner:NANJING UNIV OF POSTS & TELECOMM
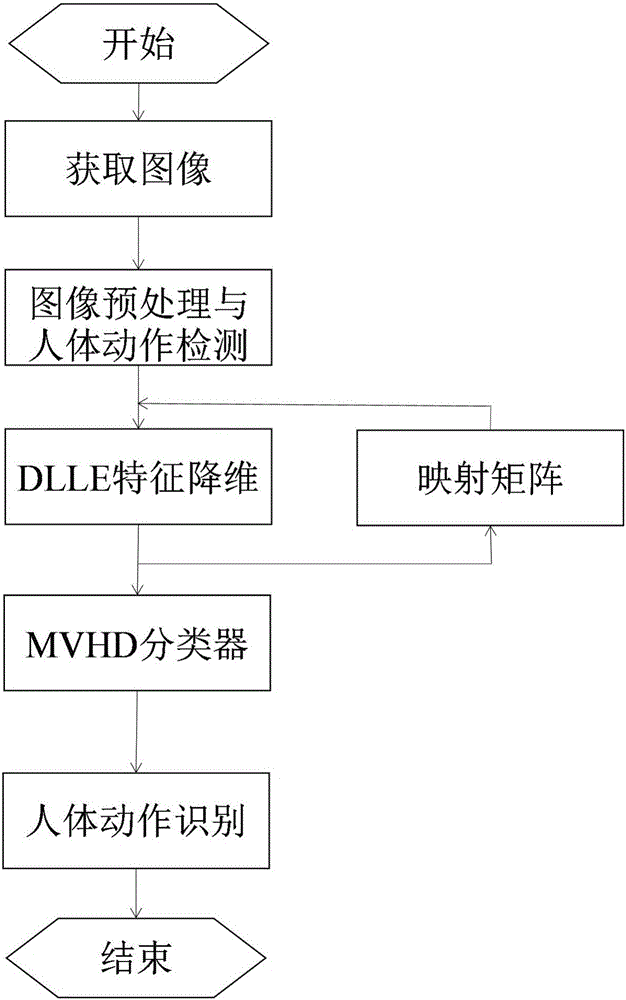
DLLE model-based data dimension reduction and characteristic understanding method
InactiveCN106127112AHigh precisionProof of validityCharacter and pattern recognitionHuman bodyKey frame
The invention discloses a DLLE (Linear Local Embedding of Difference) model-based data dimension reduction and characteristic understanding method, and belongs to the field of computer vision. The method comprises the steps of firstly, obtaining an image sequence through a visual sensor, then analyzing an input motion image sequence, extracting a foreground human body contour region through a background subtraction method, performing binarization, researching a periodic characteristic of a motion, performing key frame extraction on each motion sequence, and extracting a complete motion periodic sequence; performing manifold dimension reduction through a DLLE algorithm to obtain a low-dimensional eigenvector, and storing the low-dimensional eigenvector in a motion database; and performing identification through a nearest neighbor classifier by comparing a mean Hausdorff distance between a test sequence and a motion sequence in a training sample library. According to the method, the application of a differential function and category information-based neighborhood preserving embedding algorithm to human body motion identification is proposed; a DLLE model can not only keep a manifold local geometric structure during dimension reduction but also fully utilize category information of original high-dimensional data; and the extension from unsupervised extension to supervised extension is realized.
Owner:BEIJING UNIV OF TECH
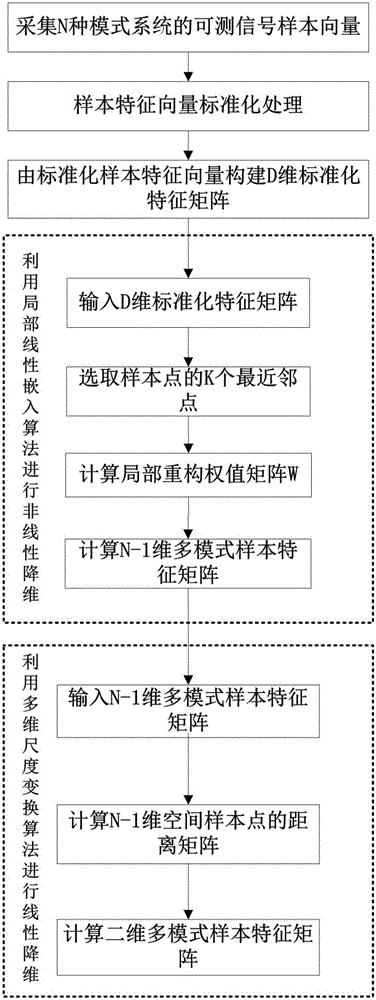
Multimode system feature dimensionality reduction method
ActiveCN106096640ARetain structureMaintain propertiesCharacter and pattern recognitionMultidimensional scalingAlgorithm
The invention relates to a multimode system feature dimensionality reduction method. The method comprises the steps that M sets of sample feature vectors under different operation modes Fn of a multimode system are acquired; the sample feature vectors are successively normalized to acquire normalized sample feature vectors; a multimode sample normalized feature matrix is constructed; a local linear embedding algorithm is used to carry out nonlinear dimensionality reduction on the normalized feature matrix; the most similar N-1 dimensional features of the same mode are selected; a multidimensional scaling algorithm is used to carry out linear dimensionality reduction on the matrix in the step (4); and two-dimensional feature matrixes with the largest difference in modes of different classes are selected. According to the invention, feature extraction technologies of non-linear and linear manifold learning algorithms are integrated; through effective feature dimensionality reduction of high-dimensional data, the difficulty of multimode system mode recognition is reduced; linearity and nonlinearity structures of high-dimensional data are maximally preserved; and domain characteristics and distance similarity of high-dimensional data are maintained.
Owner:HEFEI UNIV OF TECH
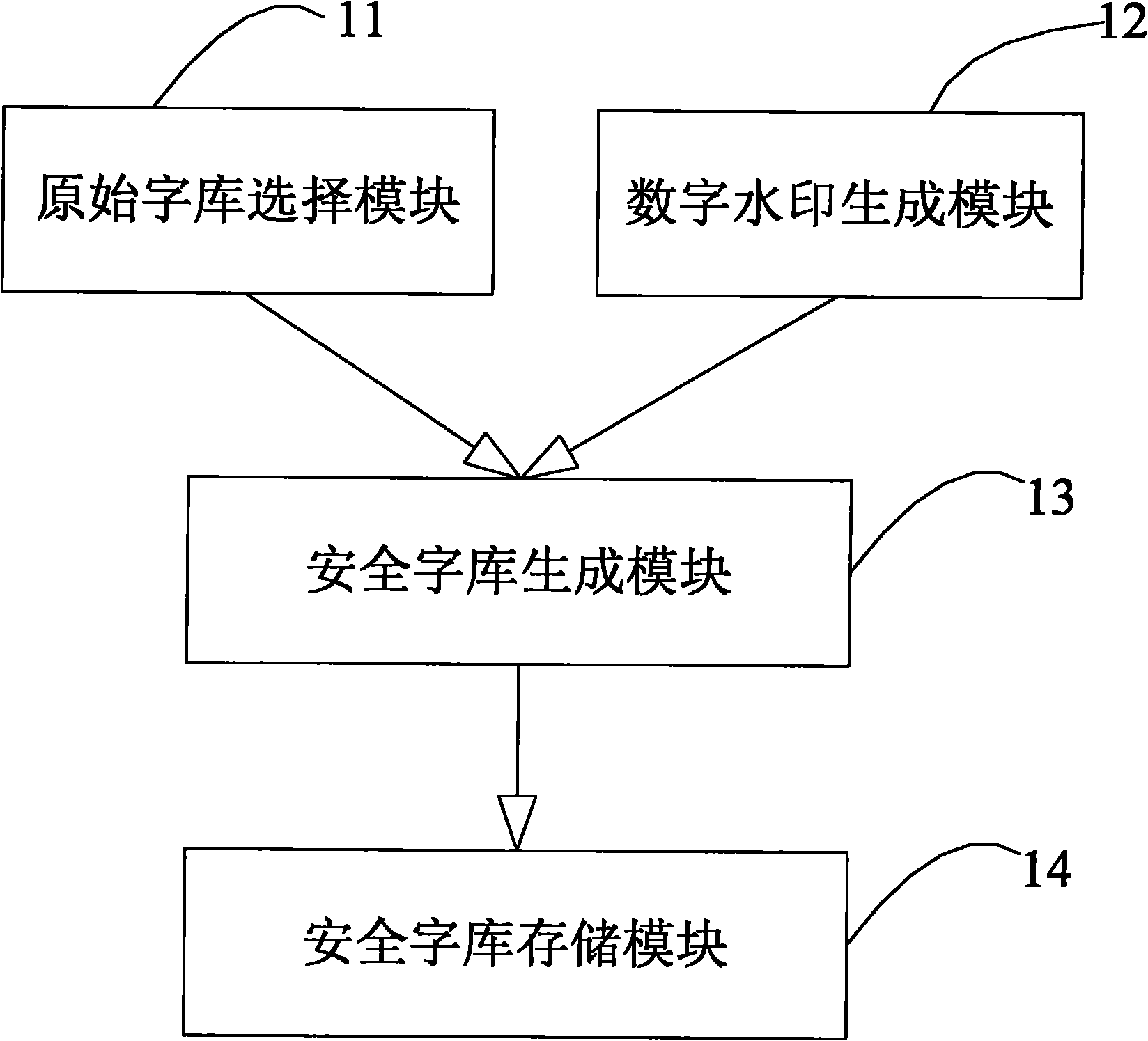
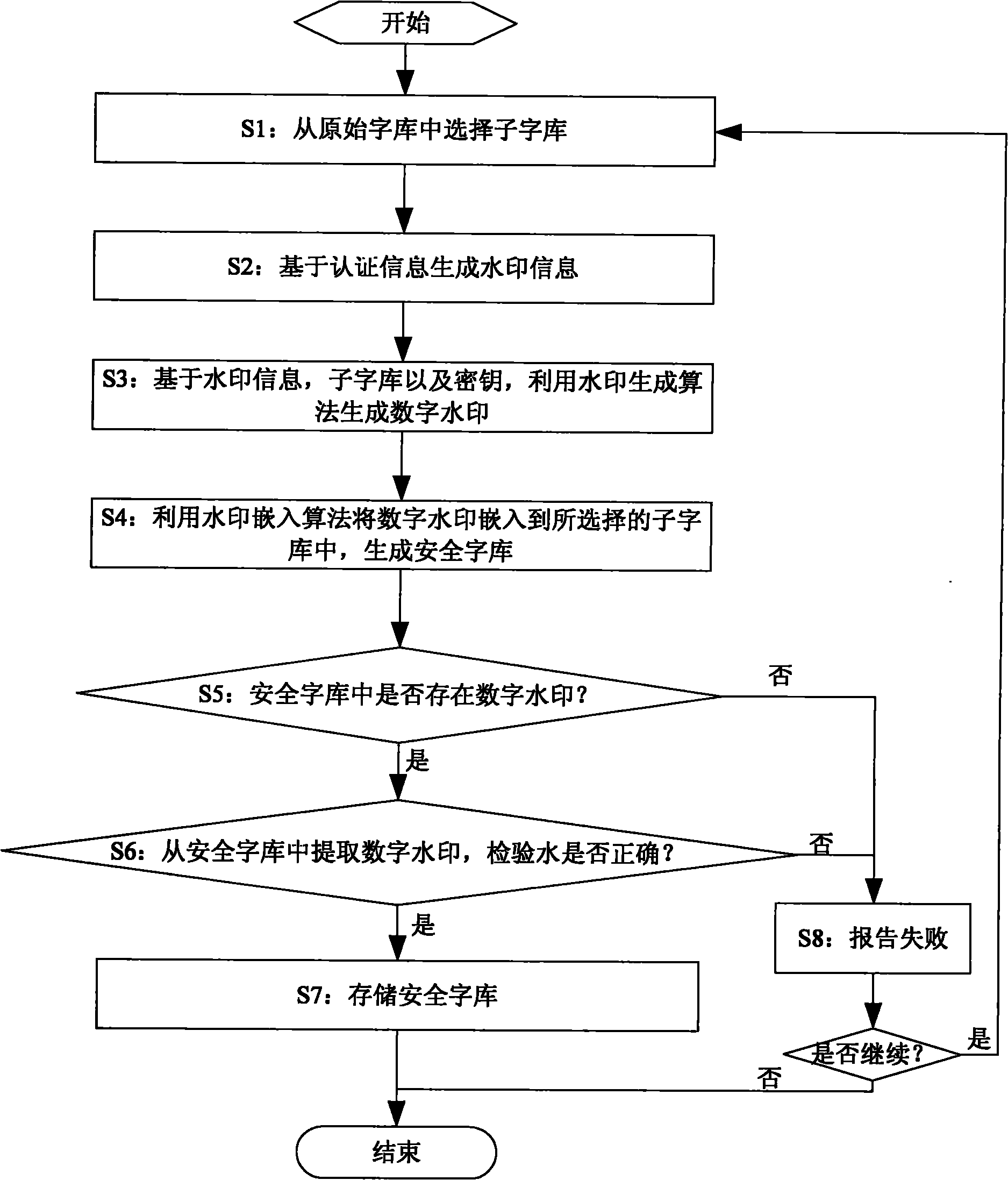
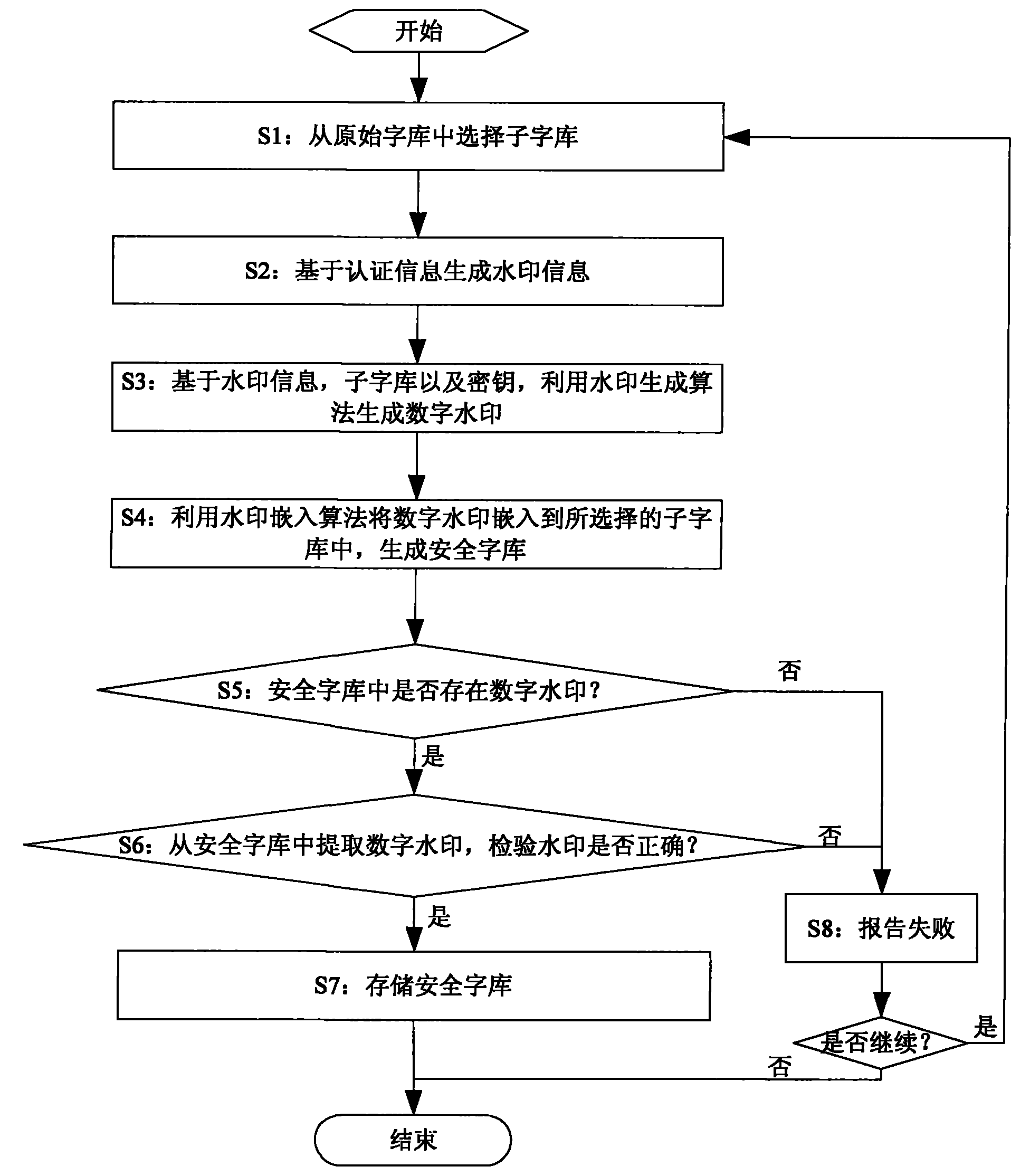
Method and system for generating digital watermark-based safe word stock
InactiveCN101833747AProtected copyImage data processing detailsSpecial data processing applicationsDocument preparationDocumentation
The invention discloses a method and a system for generating a digital watermark-based safe word stock. The safe word stock is used for establishing a user document which exclusively belongs to a user, and the method is characterized by comprising the following steps of: step S1, determining a sub-word stock which needs to be embedded with a digital watermark in an original work stock set according to the requirement of creating a document; step S2, forming watermark information based on authentication information; step S3, generating the digital watermark by using a watermark generation algorithm based on the sub-word stock, the watermark information and a key; and step S4, embedding the digital watermark into the sub-word stock by using the watermark embedding algorithm and generating the safe word stock comprising the digital watermark. The user can input characters by using the unique safe work stock so as to generate the unique document per se; and a watermark signal comprising the specific information of the user is embedded into the documents and can be extracted, so that the documents are protected from being copied illegally.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Digital watermark embedding apparatus and method, and computer program
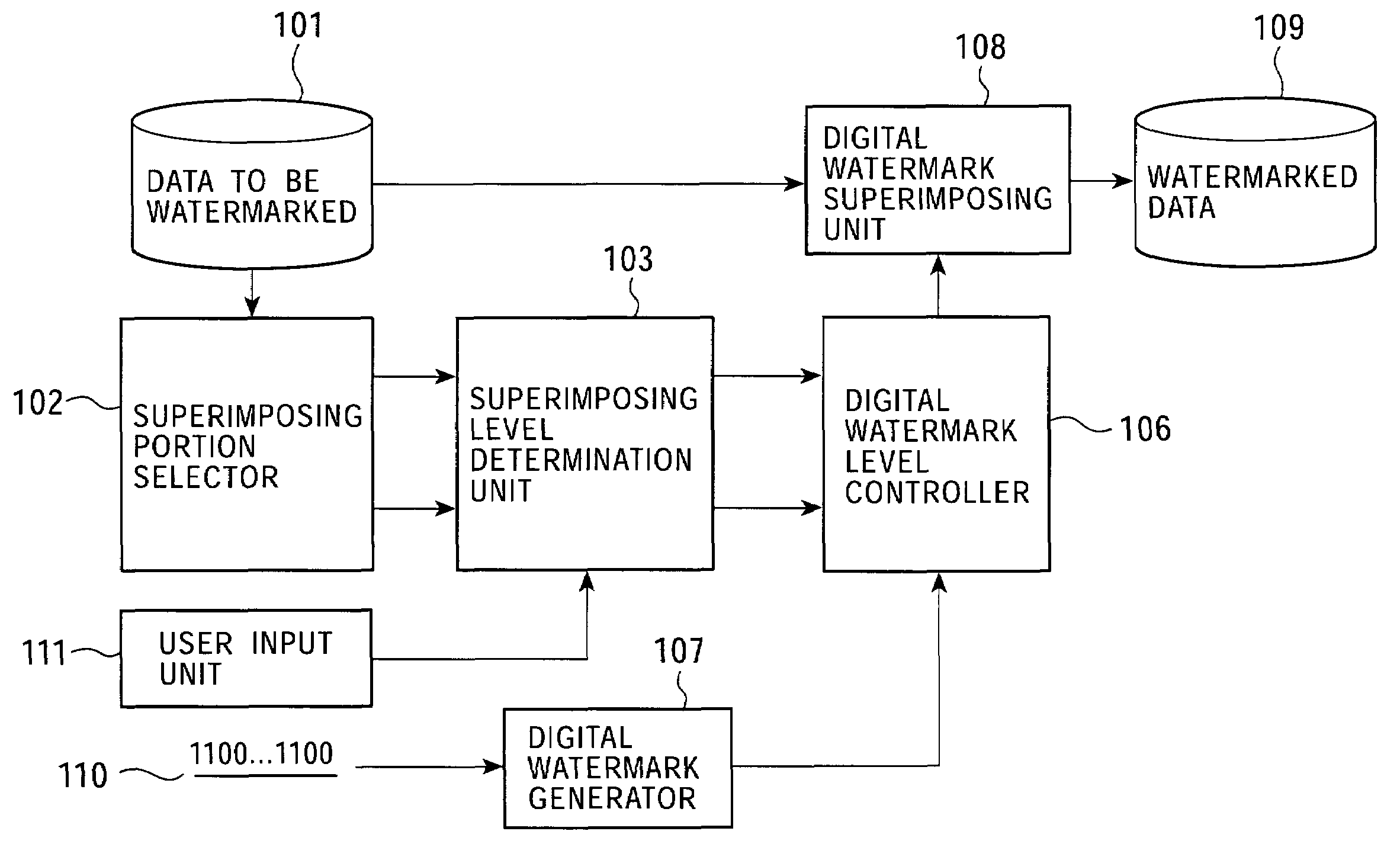
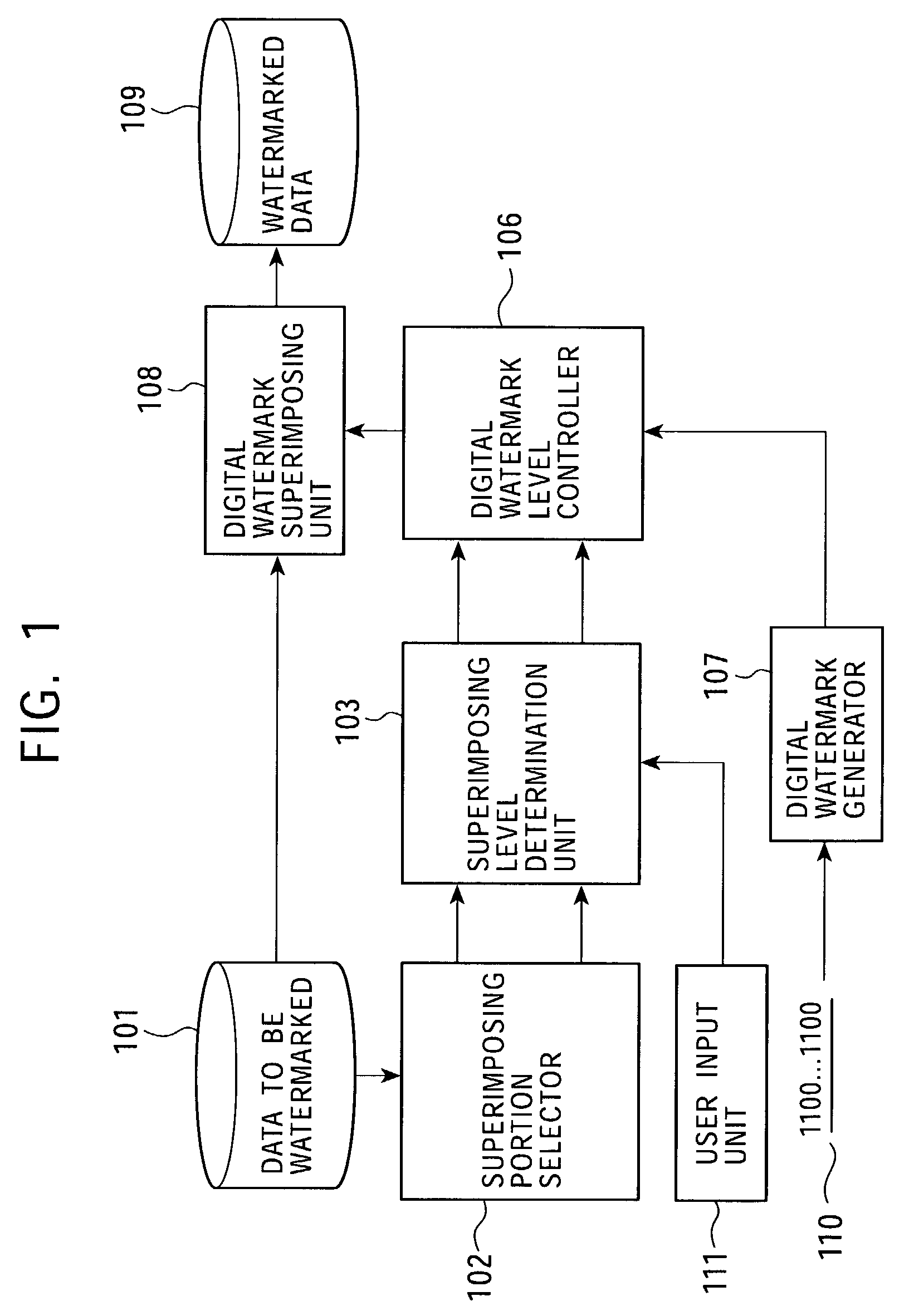
InactiveUS7287163B2Easy to detectData quality can be minimized and preventedOther printing matterUser identity/authority verificationAuditory senseUser input
A digital watermark embedding apparatus divides data to be watermarked into a plurality of data areas on the basis of data characteristics, in time series, or on the basis of user selection and performs digital watermark embedding in which different algorithms are applied to the separate data areas. Unlike schemes that embed digital watermarks using an algorithm that is uniform with all data areas, a digital watermark can be embedded in accordance with each data area of an image. When the algorithm is selected in accordance with user input, the embedding algorithm can be selected in accordance with the characteristics of the human vision or auditory sense. Image / audio quality control and detection performance improvement are thus made possible, and deterioration in data quality can be prevented.
Owner:SONY CORP
Wireless sensor network data security protection method based on digital watermarking
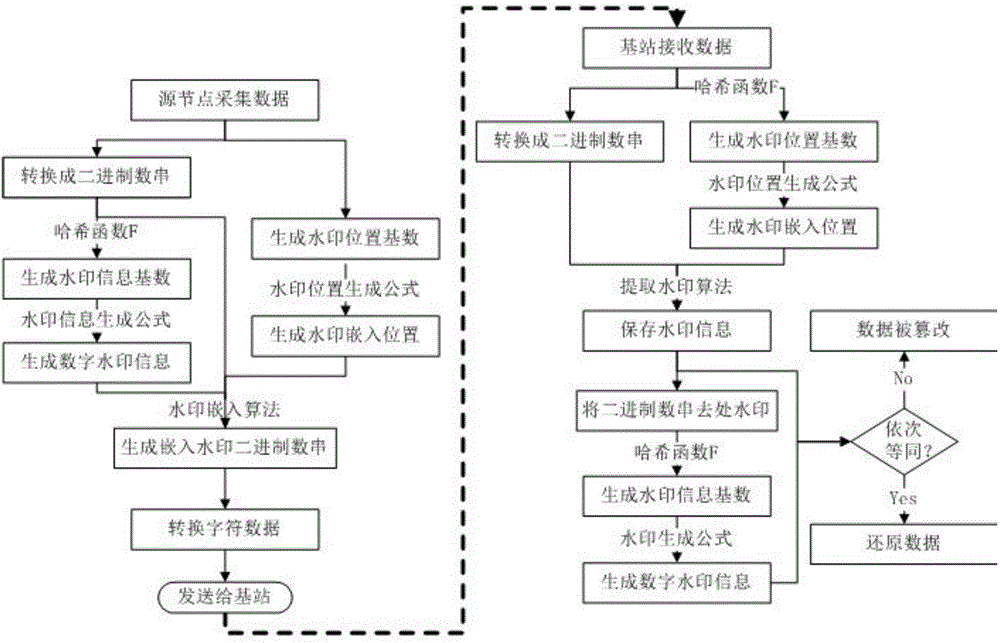
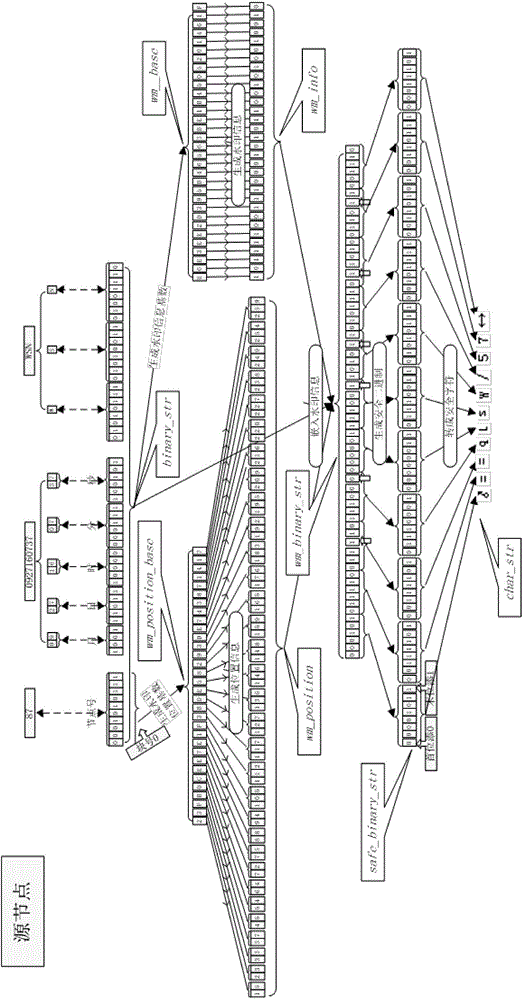
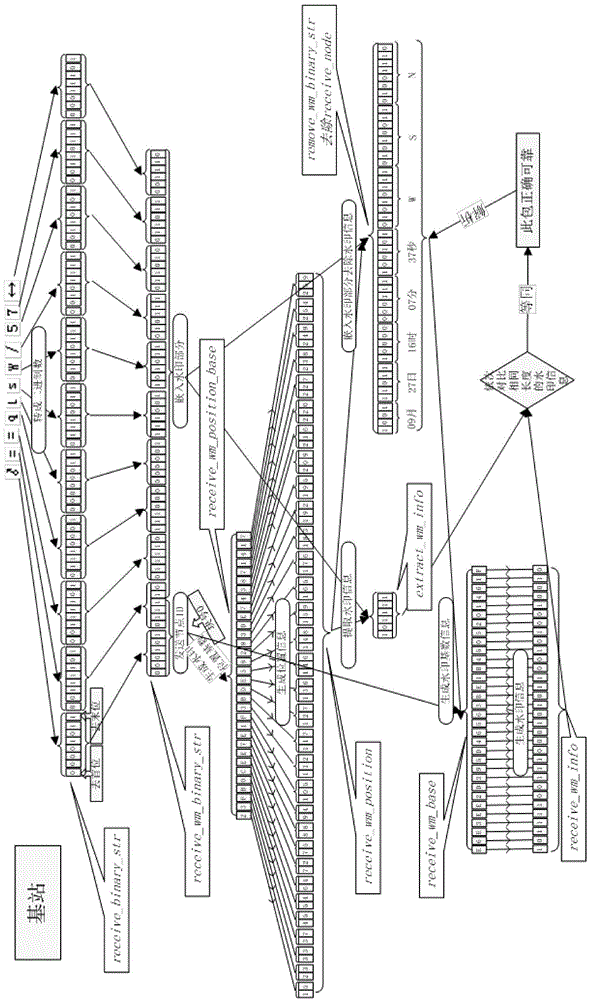
ActiveCN104486304AIntegrity guaranteedImprove integritySecurity arrangementSecuring communicationHash functionOriginal data
The invention discloses a wireless sensor network data security protection method based on digital watermarking. According to the method, data are perceived in source node positions and are converted into binary numbers, and then, processing blocks are divided; a Hash function is utilized for obtaining a watermarking base number, and watermarking information is calculated; the Hash function is utilized for generating a watermarking embedded position base number, and the watermarking storage position is calculated; the embedded watermarking binary numbers are obtained by a watermarking embedded algorithm according to the binary numbers, the watermarking information and the watermarking storage position; character strings are generated through the embedded watermarking binary numbers by using a security character transformation algorithm and are sent. After a base station node receives the data, the original binary numbers and the embedded watermarking information are obtained through a reversion process, then, the watermarking information is calculated, if the watermarking information is sequentially identical to the embedded watermarking, the condition that the original data is correct and complete can be known, and otherwise, the packet is abandoned. The wireless sensor network data security protection method has the advantages that the proper-length watermarking information can be embedded according to the length of the original data, the unnecessary communication volume can be reduced, and the network security is improved through security character transformation.
Owner:陕西雅高科技有限公司
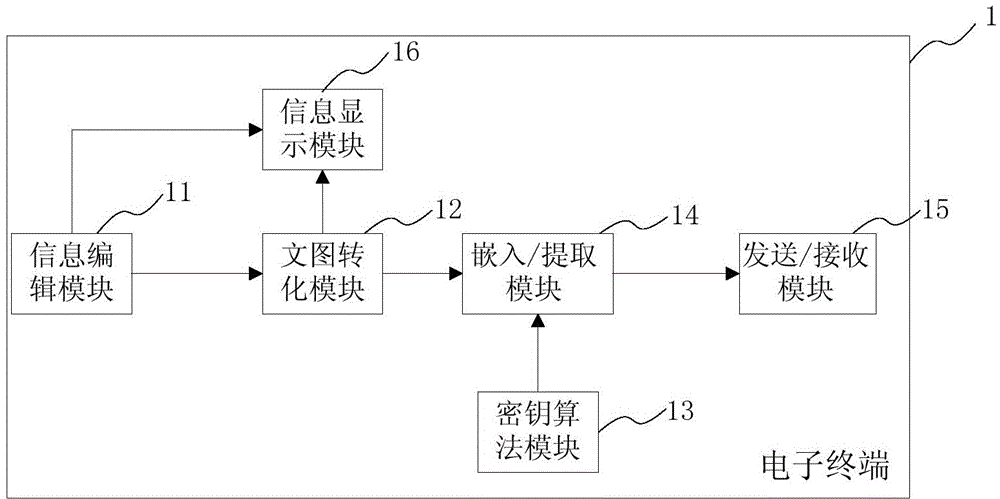
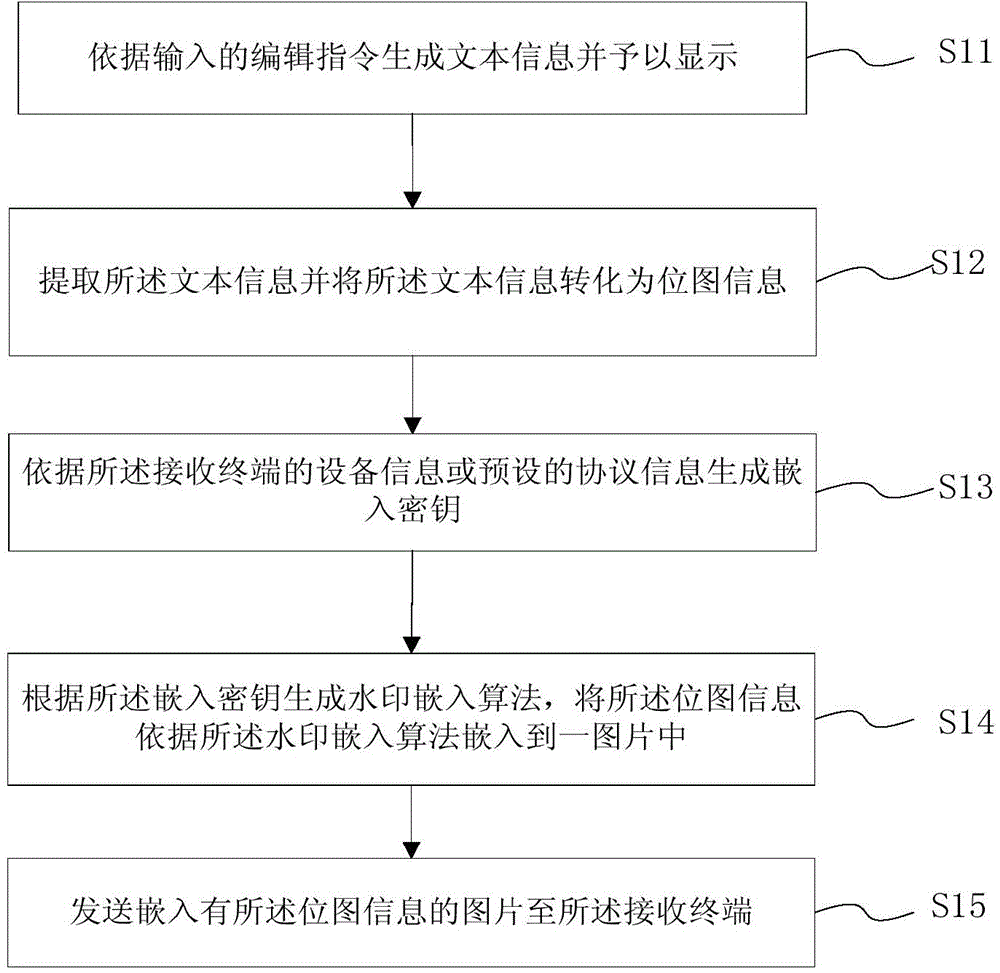
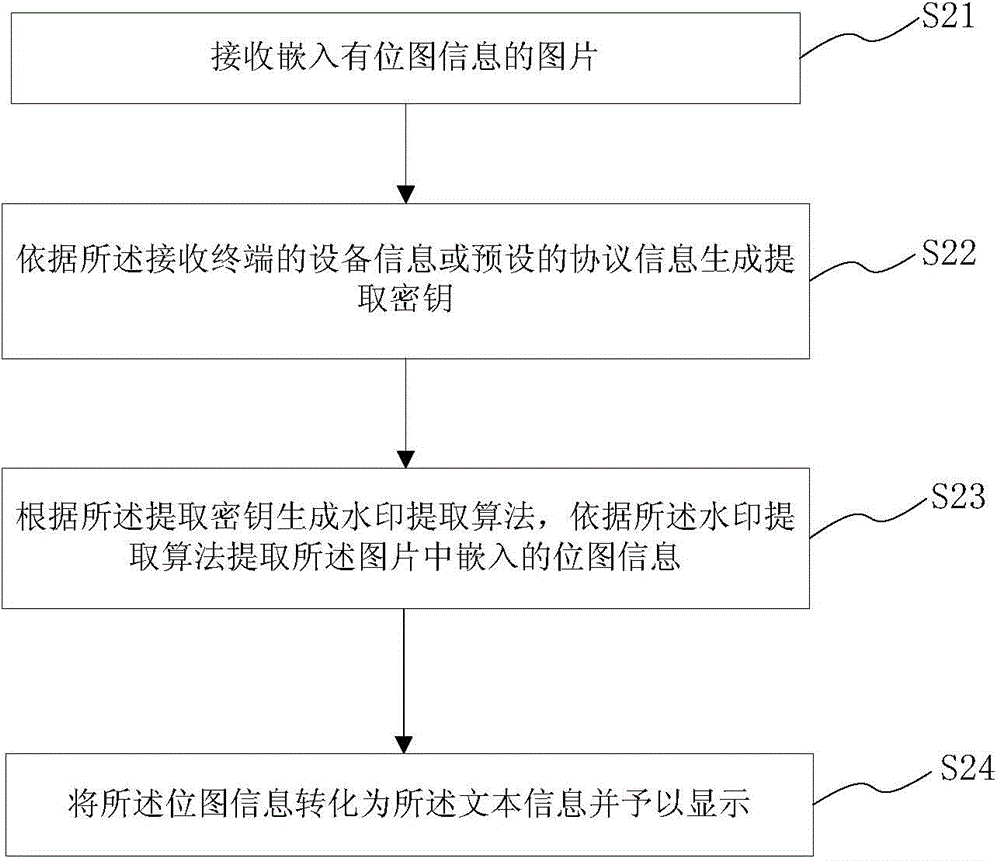
Electronic terminal and short message encrypting and decrypting method thereof
The invention relates to an electronic terminal and a short message encrypting and decrypting method thereof, and is applied to a network system comprising a transmitting terminal and a receiving terminal. The short message encrypting method comprises the following steps: converting inputted text information to bitmap information, generating an embedded secrete key by utilizing equipment information or preset protocol information of the receiving terminal, embedding the bitmap information into a preset or randomly-selected picture according to a watermark embedding algorithm, and receiving the picture with the bitmap information through the receiving terminal. The short message decrypting method comprises the following steps: generating an extracting secrete key according to the equipment information or preset protocol information of the receiving terminal, extracting the bitmap information from the picture by utilizing a watermark extracting algorithm, and converting the bitmap information into corresponding text information to be displayed. The electronic terminal and the short message encrypting and decrypting method are high in security, when the information is intercepted by a third party or the electronic terminal is lost, the security of the information can be guaranteed.
Owner:湖州丰源农业装备制造有限公司
BIM-model-based distribution network and underground cable fault detection method
ActiveCN108614191AAdvantages of detection methodEasy fault detectionFault locationInformation technology support systemData modelingMaintenance management
The invention discloses a BIM-model-based distribution network and underground cable fault detection method comprising steps of building an original BIM model, carrying out normal state data modelingand carrying out online data detection. At the step of building an original BIM model, structural characteristics of distribution network and underground cable distribution are obtained comprehensively; at the step of carrying out normal state data modeling, several kinds of variable process data in a normal stable operation state of a distribution network and underground cable are inputted into the BIM model based on a neighborhood preserving embedding algorithm and a statistic amount and a corresponding statistic threshold are calculated; and at the step of carrying out online data detection, process variable data collected in real time during the operation process of the distribution network and underground cable are projected to the model constructed by normal state data modeling, a statistic amount is calculated; and the statistic amount is compared with the statistic threshold calculated by the normal state data modeling to obtain a detection result. Therefore, BIM-model-based multi-variable distribution network and underground cable fault detection is realized; and the operation and maintenance management safety of the distribution network and underground cable is improved.
Owner:云南电网有限责任公司丽江供电局 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com