Method for detecting unknown malicious code
A malicious code and detection method technology, which is applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of undetectable, continuous update, malicious code damage, etc., and achieve the effect of improving the detection speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The preferred embodiments will be described in detail below in conjunction with the accompanying drawings. It should be emphasized that the following description is only exemplary and not intended to limit the scope of the invention and its application.
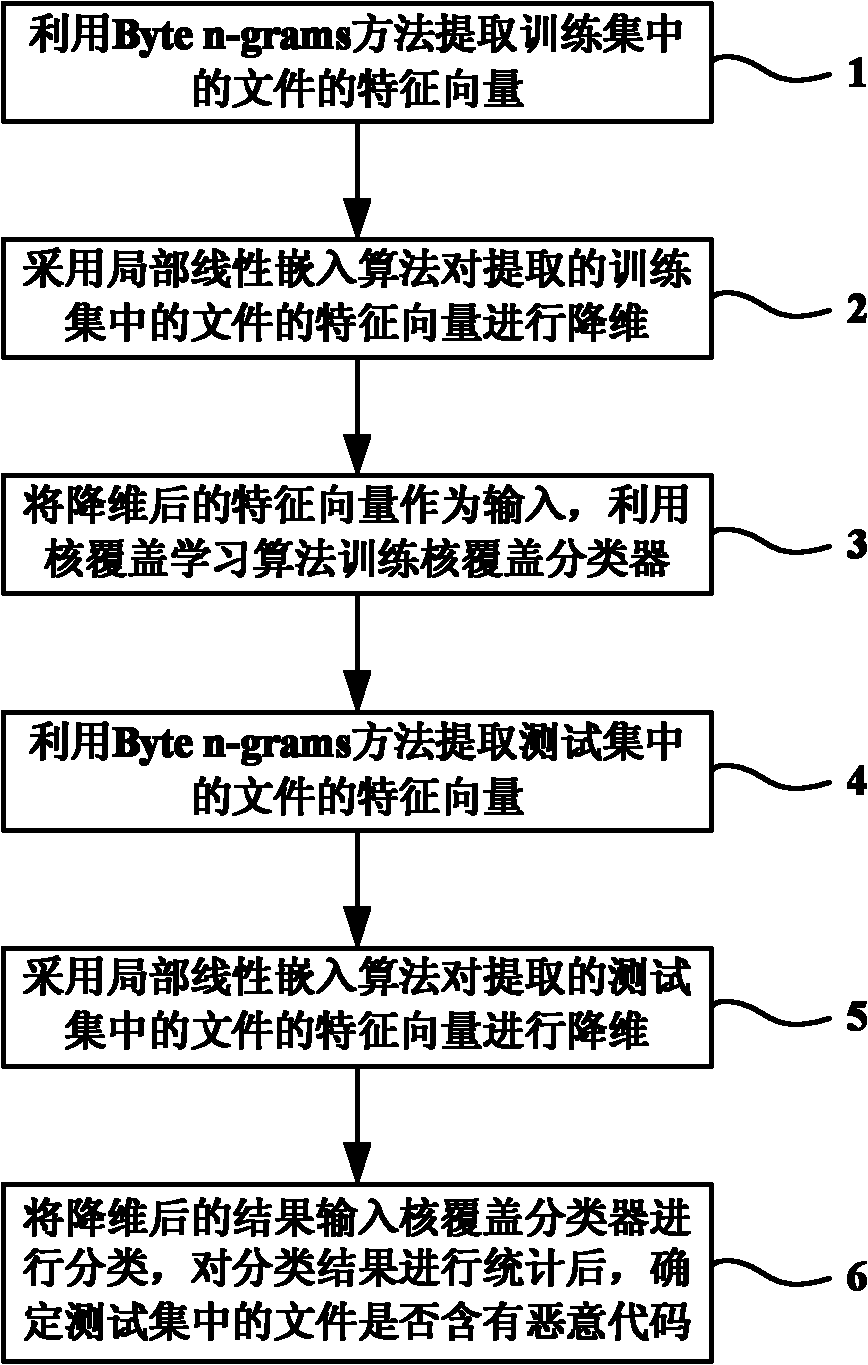
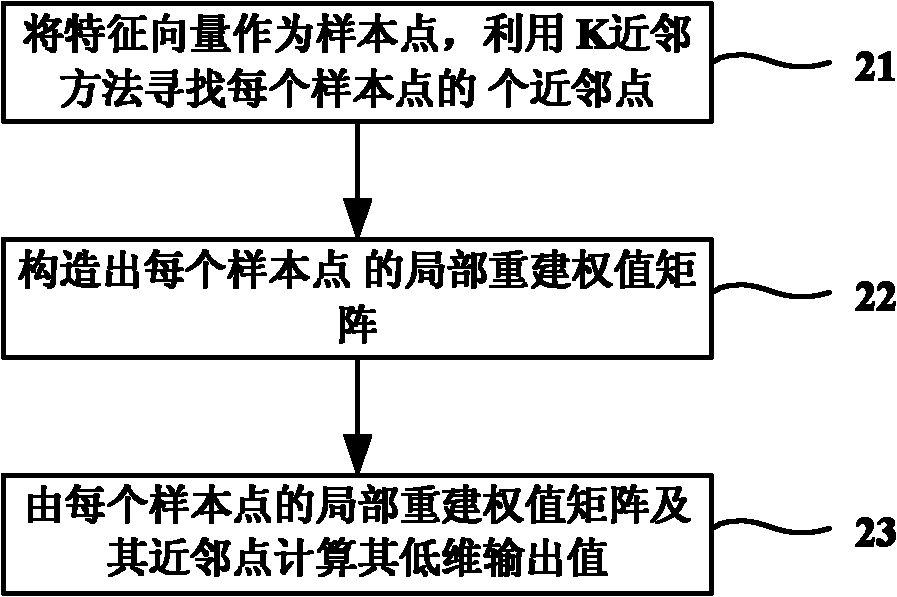
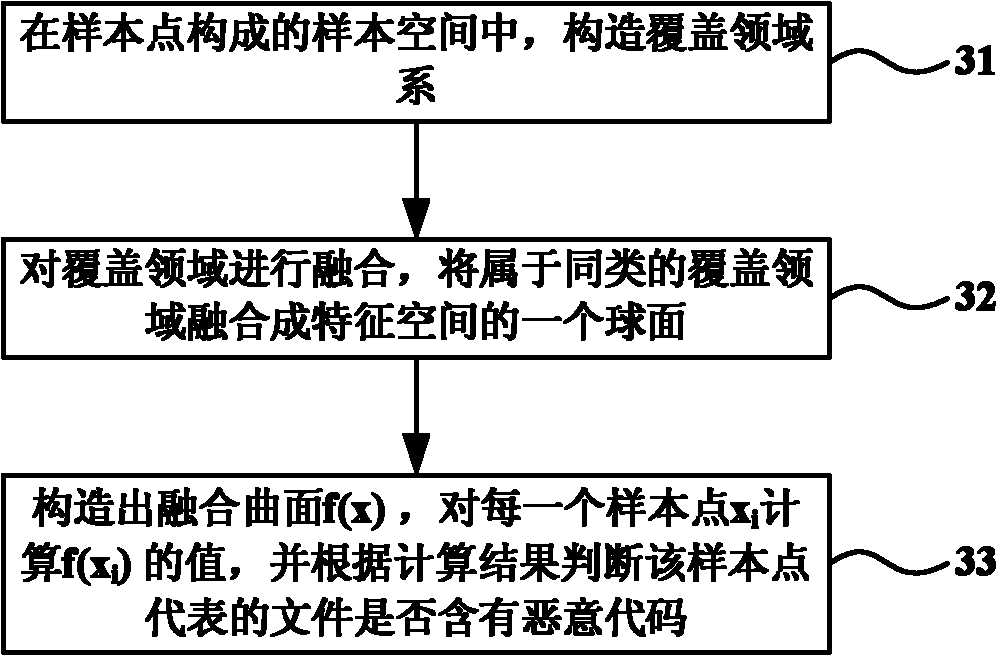
[0027] The idea of solving the problem of the present invention is: take files containing malicious codes and file sets not containing malicious codes as training samples, and use manifold learning algorithm to perform feature selection on the training set files, so that each file corresponds to a feature vector, and the features The vector is used as input to the kernel coverage classification algorithm to train the kernel coverage classifier. Finally, feature selection is performed on the unknown file to generate the corresponding feature vector, which is used as the input of the classifier to classify it, so as to distinguish whether it is a malicious file or a non-malicious file.
[0028] The specific implementa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com