Method, system and device for achieving credible digital identity decryption and signature verification through software library
A digital identity and software library technology, applied in digital data authentication, digital data protection, electronic digital data processing, etc., can solve problems such as not having a dedicated security chip, unable to decrypt data and encrypt part of the data, and restricting digital identity application scenarios. Achieve the effect of expanding the use scenarios and application scope of digital identity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
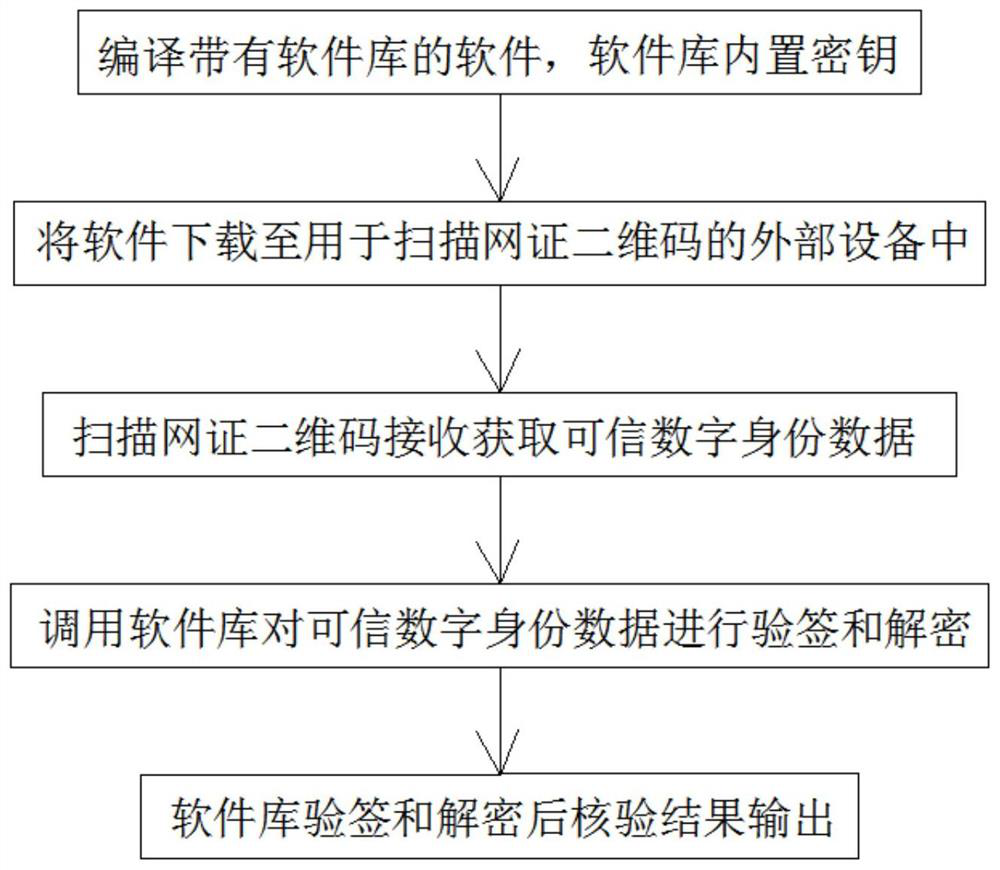
[0025] see figure 1 and figure 2 , a method for realizing trusted digital identity verification and decryption with a software library, comprising the following steps:
[0026] (1) Compile the software with a software library, and the key needed for trusted digital identity reading is built into the software library, so that the software has signature verification and decryption functions;
[0027] (2) Download the software to the device used to scan the QR code of the network certificate, so that the device has its own trusted digital identity verification and decryption functions, even in offline devices without a dedicated security chip installed can also use the built-in The software library executes the program for signature verification and decryption;
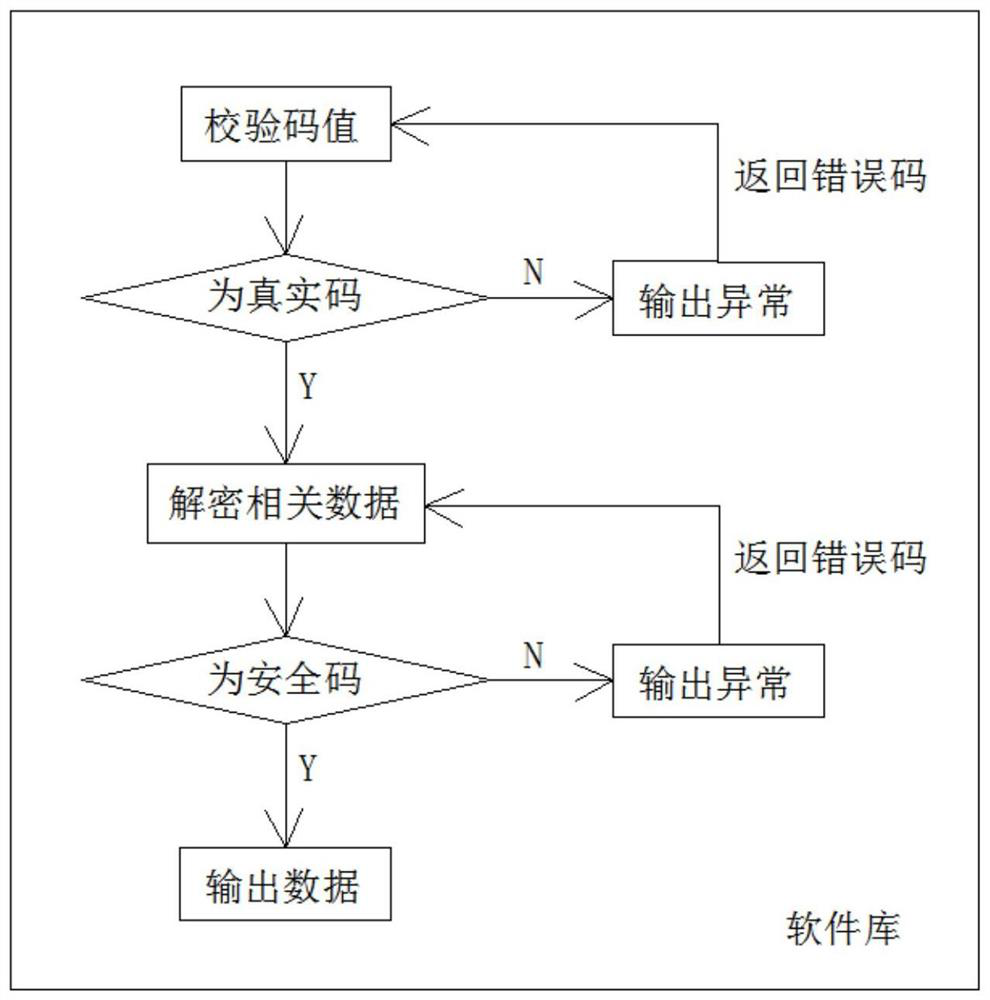
[0028] (3) The device scans the QR code of the network certificate containing the citizen identity data issued by the trusted digital identity platform, and receives and obtains the trusted digital identity data; amon...
Embodiment 2
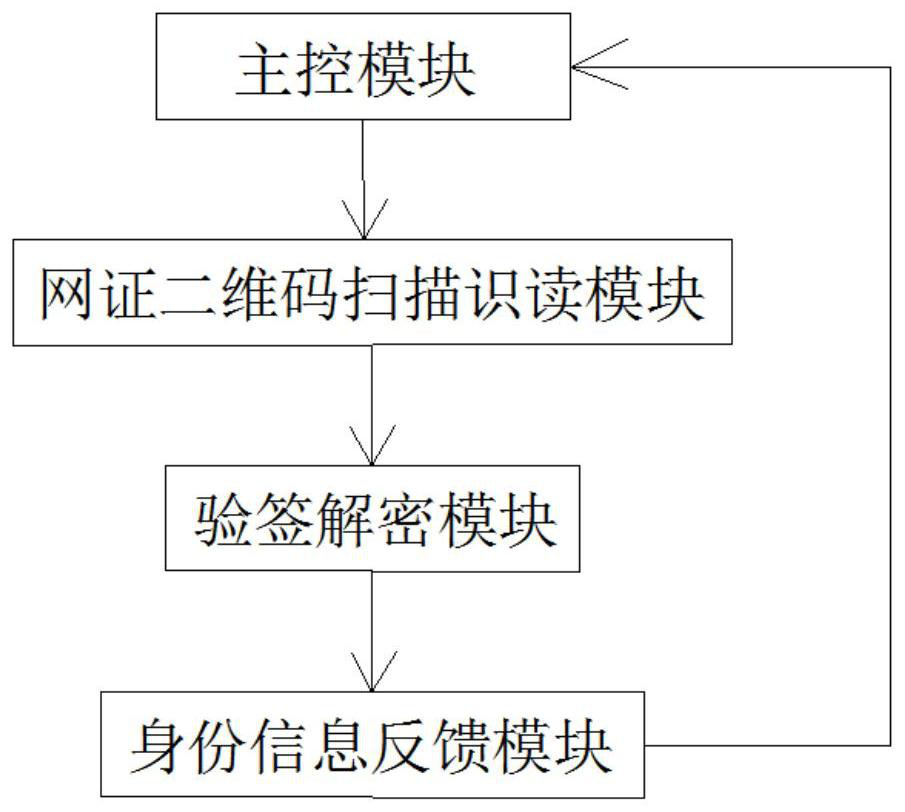
[0035] see image 3 , the invention discloses a system that uses a software library to realize signature verification and decryption of trusted digital identities, including a main control module, a two-dimensional code scanning and reading module for network certificates, a signature verification and decryption module, and an identity information feedback module; the main The control module communicates with the network certificate two-dimensional code scanning and reading module, the network certificate two-dimensional code scanning and reading module connects with the signature verification and decryption module through a function call interface, and the signature verification and decryption module communicates with the identity information feedback module; the main The control module controls the two-dimensional code scanning and reading module of the network certificate to scan the two-dimensional code of the network certificate to obtain credible digital identity data; a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com