DNA self-assembling structure and symmetrical encryption system based on DNA self-assembling structure
A symmetric encryption and self-assembly technology, applied in the field of cryptography research and DNA encryption, it can solve the problems of lack of parallelism, failure of encryption method, interception of ciphertext, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
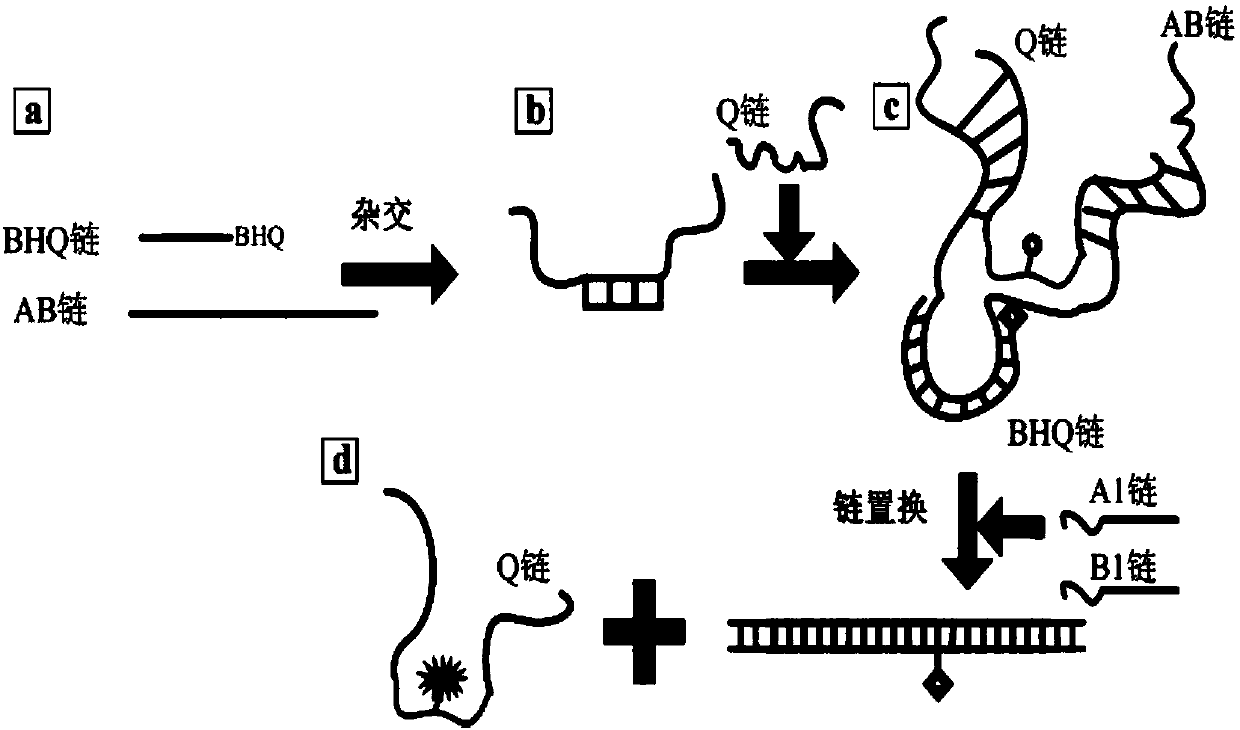
[0030] Example 1: The basic process of forming a DNA self-assembly structure is as follows figure 1 shown.
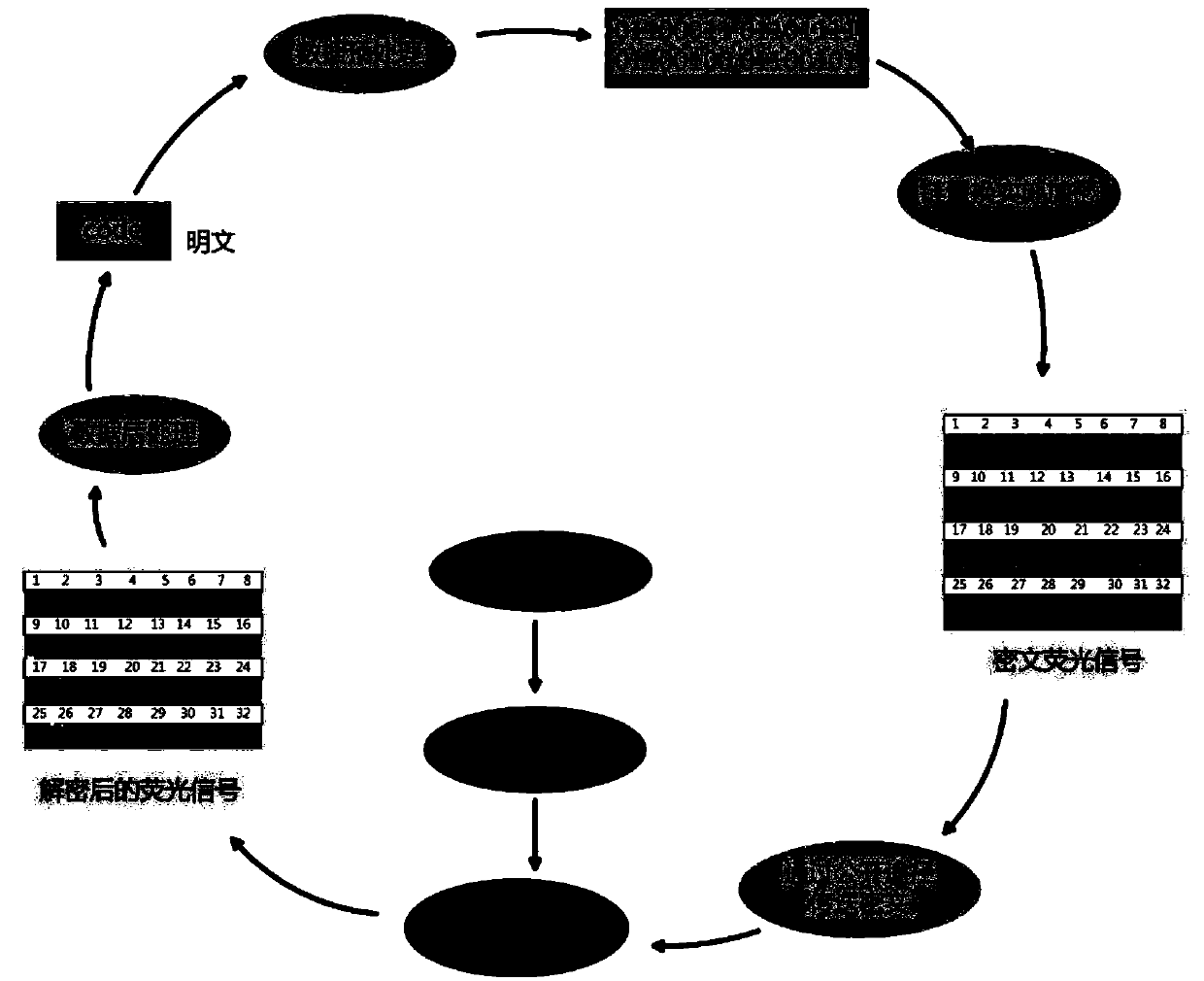
[0031] Based on the DNA self-assembly structure, a symmetric encryption system is constructed. The encryption key used by the sender is named Ka. The sender uses Ka to convert plaintext P into ciphertext C, and sends this ciphertext to a receiver, who has the decryption key Kb. After receiving the ciphertext C, the receiver uses Kb to obtain the plaintext P through the decryption process. This encryption algorithm uses a one-time pad XOR operation. The XOR operation is a logic gate that performs an XOR operation, that is, the output is true (1) when only one input is true (1), and if all inputs are true (1) or the input is false (0) The output is false (0).
[0032] In the present invention, "code" is selected as plaintext for encryption and decryption. According to the ASCII password, this plaintext can be converted into a binary string "01100011 01101111 0110010...
Embodiment 2
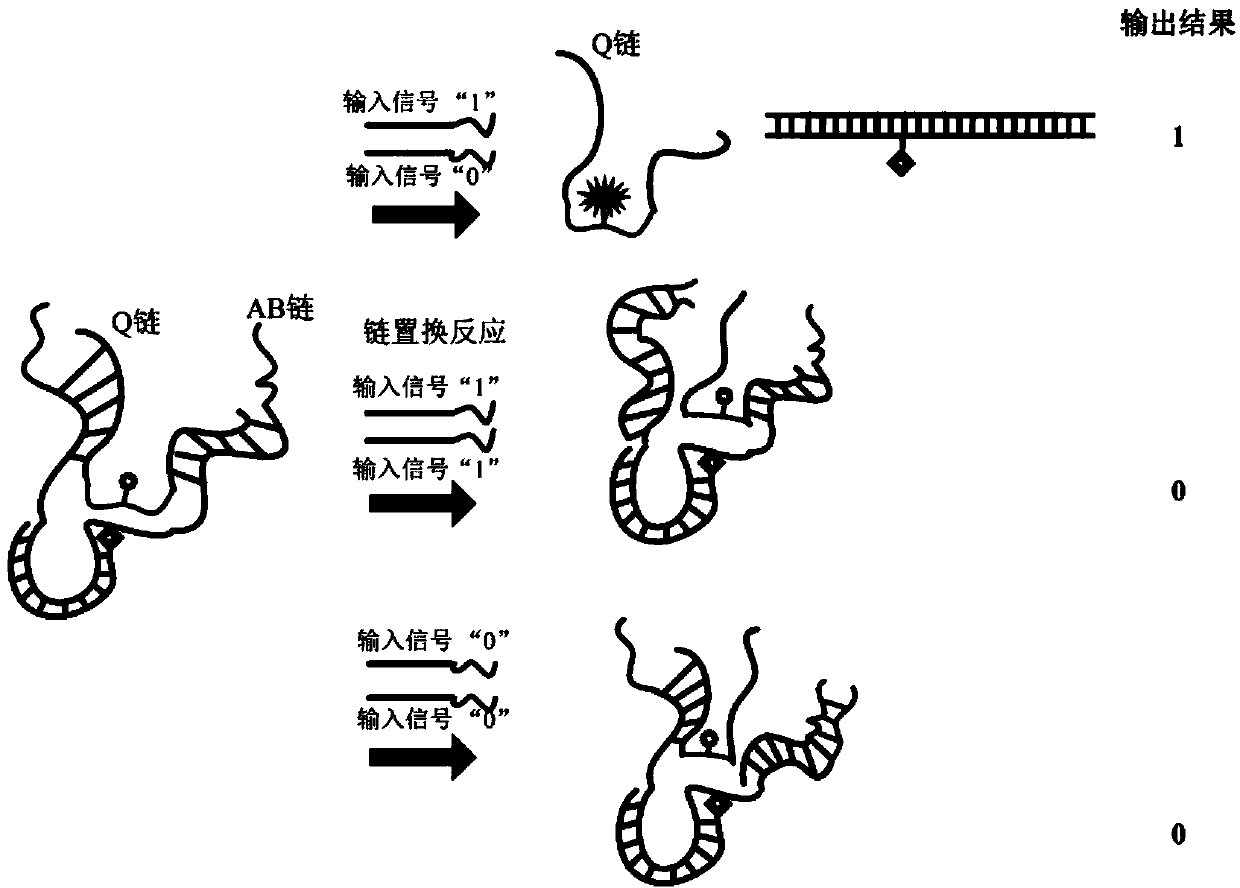
[0039]Example 2: The DNA self-assembly structure is formed by hybridization of several different oligonucleotide single strands, the specific method is as follows: First, through the complementary recognition region, the single strand AB and BHQ hybridize to form a new DNA strand, here During the process, equimolar concentrations of single-chain AB and BHQ were added to the system (final concentration 3.75 pmol / L, TAE / Mg2+ buffer), and the mixture was left at 37°C for 2 hours. Next, add Q chains to the mixture at an equimolar concentration, and place at 37°C for 2 hours. In the experiment, in order to carry out the strand displacement reaction of XOR operation, the input strand (final concentration 3.75pmol / L) was added to the mixture containing DNA self-assembly, and reacted at room temperature for more than 2 hours, then PAGE electrophoresis and fluorescence could be performed. Result detection. For each sample, use a fluorescence detector to record the fluorescence value o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com