P2P storage system coding method based on Reed-Solomon code
A technology of storage system and encoding method, which is applied in the field of peer-to-peer network, can solve problems such as leakage, inability to completely delete data, and failure to protect user data privacy, so as to achieve the effect of ensuring security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in more detail through specific embodiments below in conjunction with the accompanying drawings, but these embodiments should not be construed as limiting the present invention.
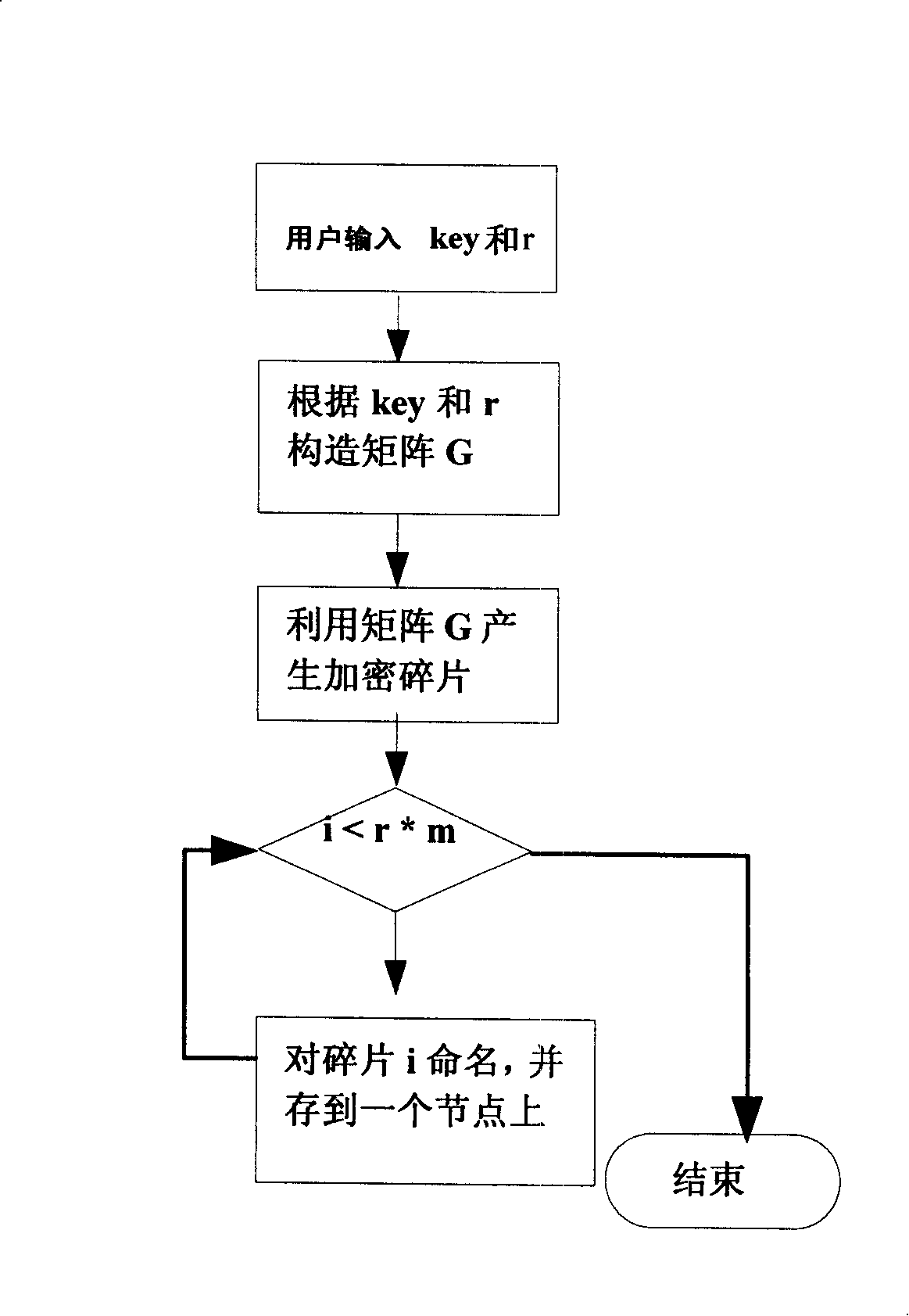
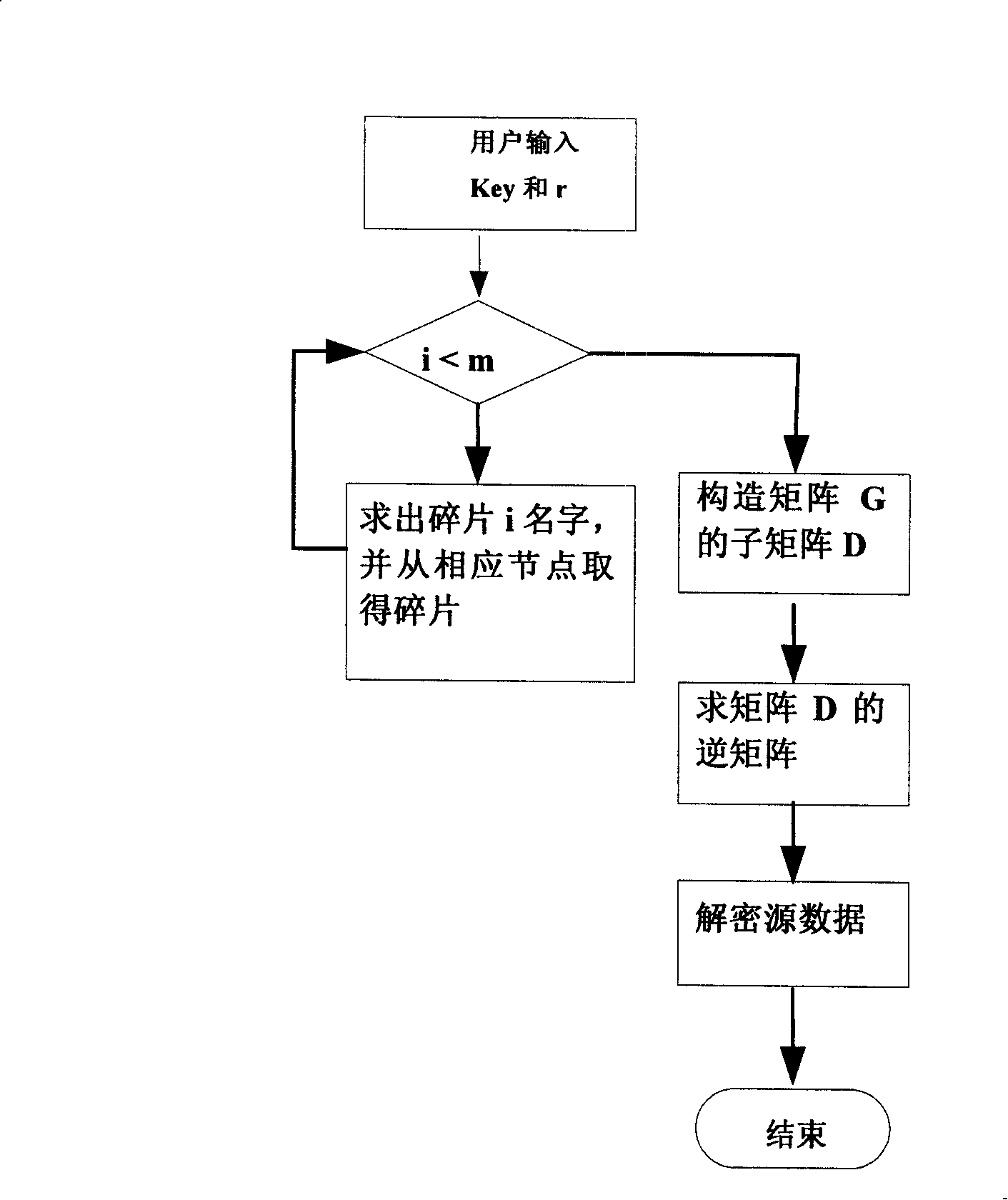
[0035] 1. Generate encryption matrix G
[0036] 1) Galois field:
[0037] In order to prevent the result of the operation from exceeding the range that the computer can express, all our operations are defined on the Galois field, and the addition, subtraction, multiplication, and division on the Galois field are closed, and one has 2 L The Galois field of elements is denoted as GF(2 L ).
[0038] 2) Cauchy matrix:
[0039] In order to enable any m fragments among the redundant r×m fragments to be able to decode the original data, it is necessary to require that the sub-matrix formed by any m rows of the matrix G is linearly independent. The Cauchy matrix satisfies this property, and the definition of the Cauchy matrix is given below:
[0040] {x ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com