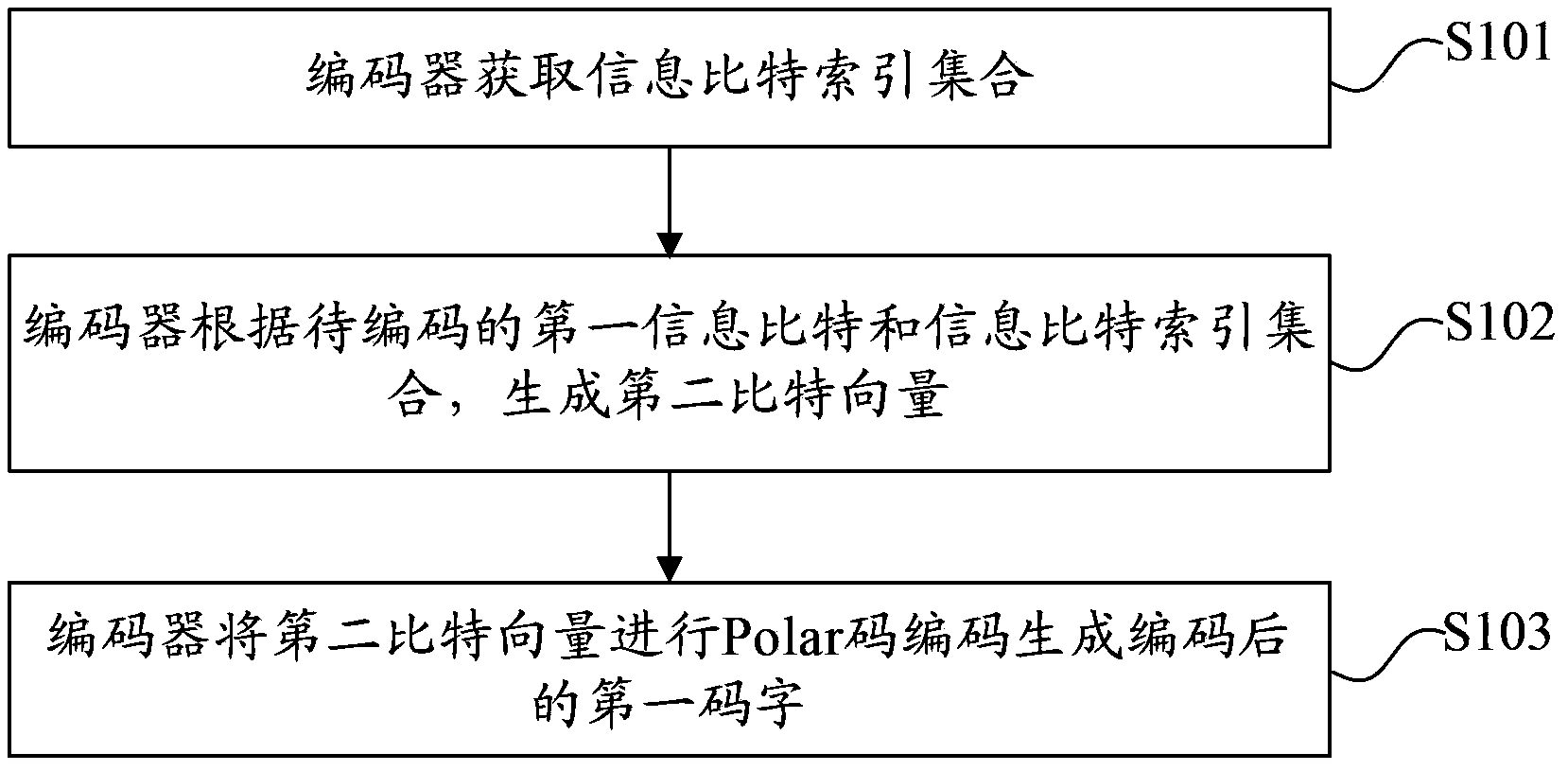
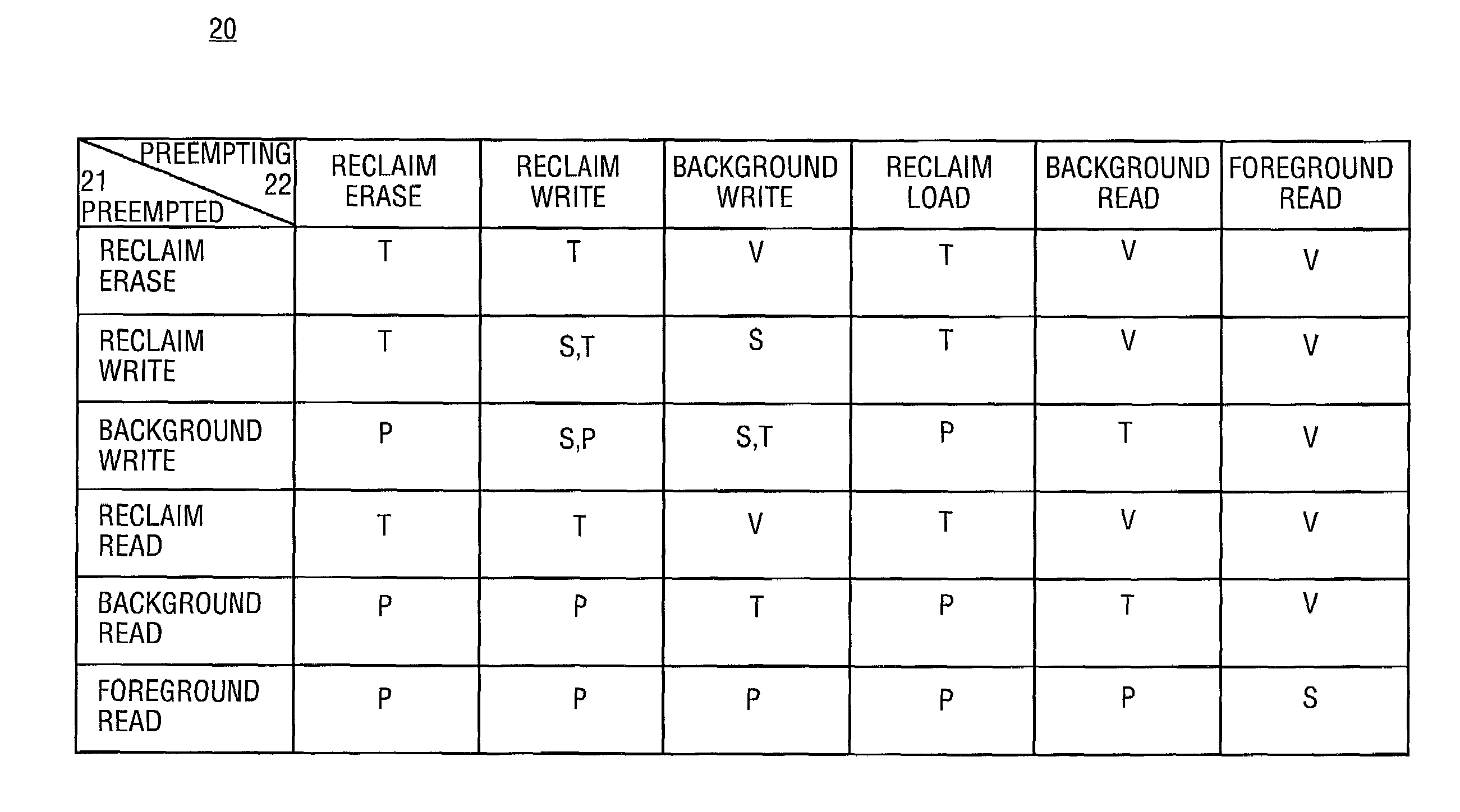
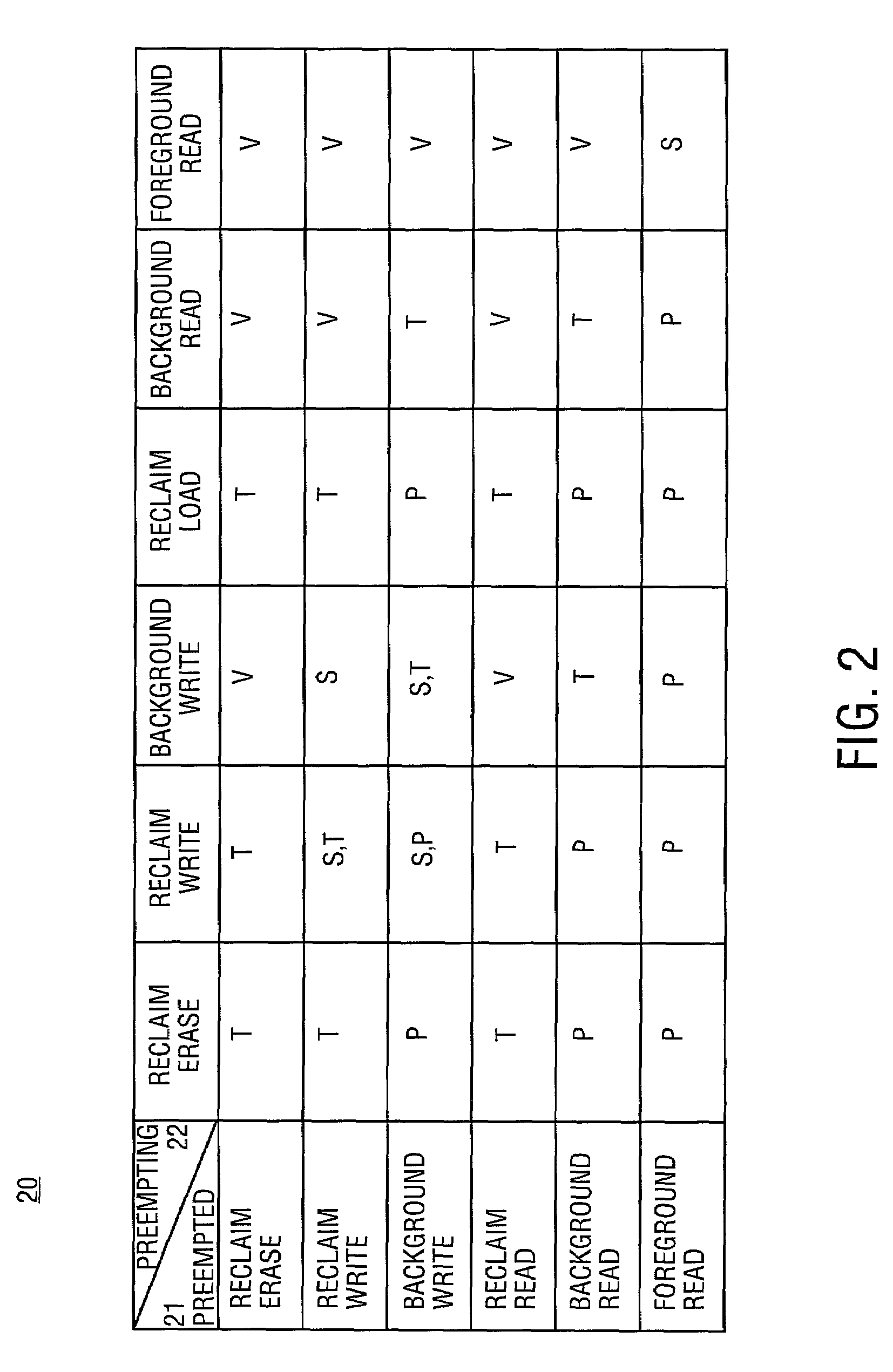
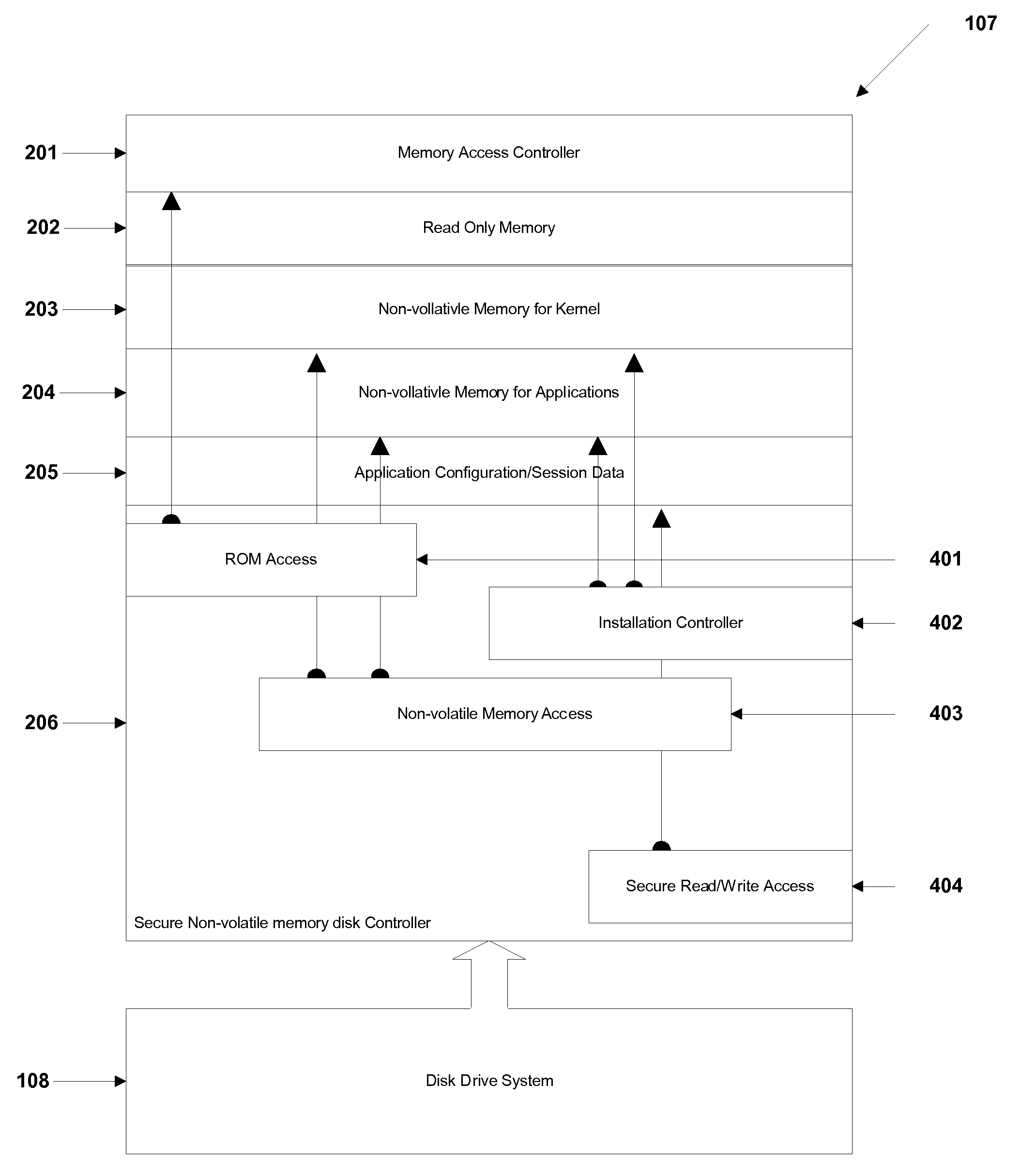
Patents
Literature
646 results about "System code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
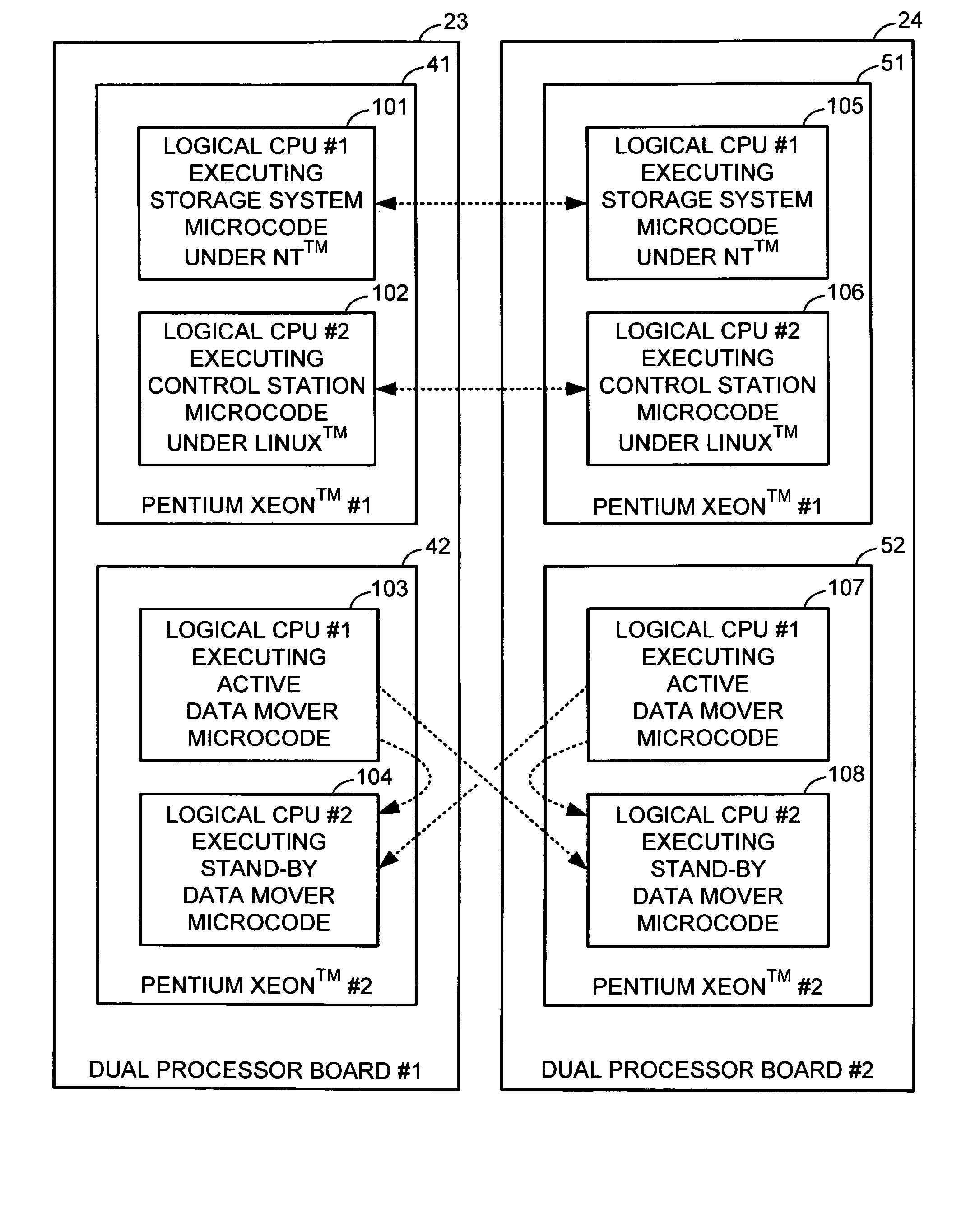
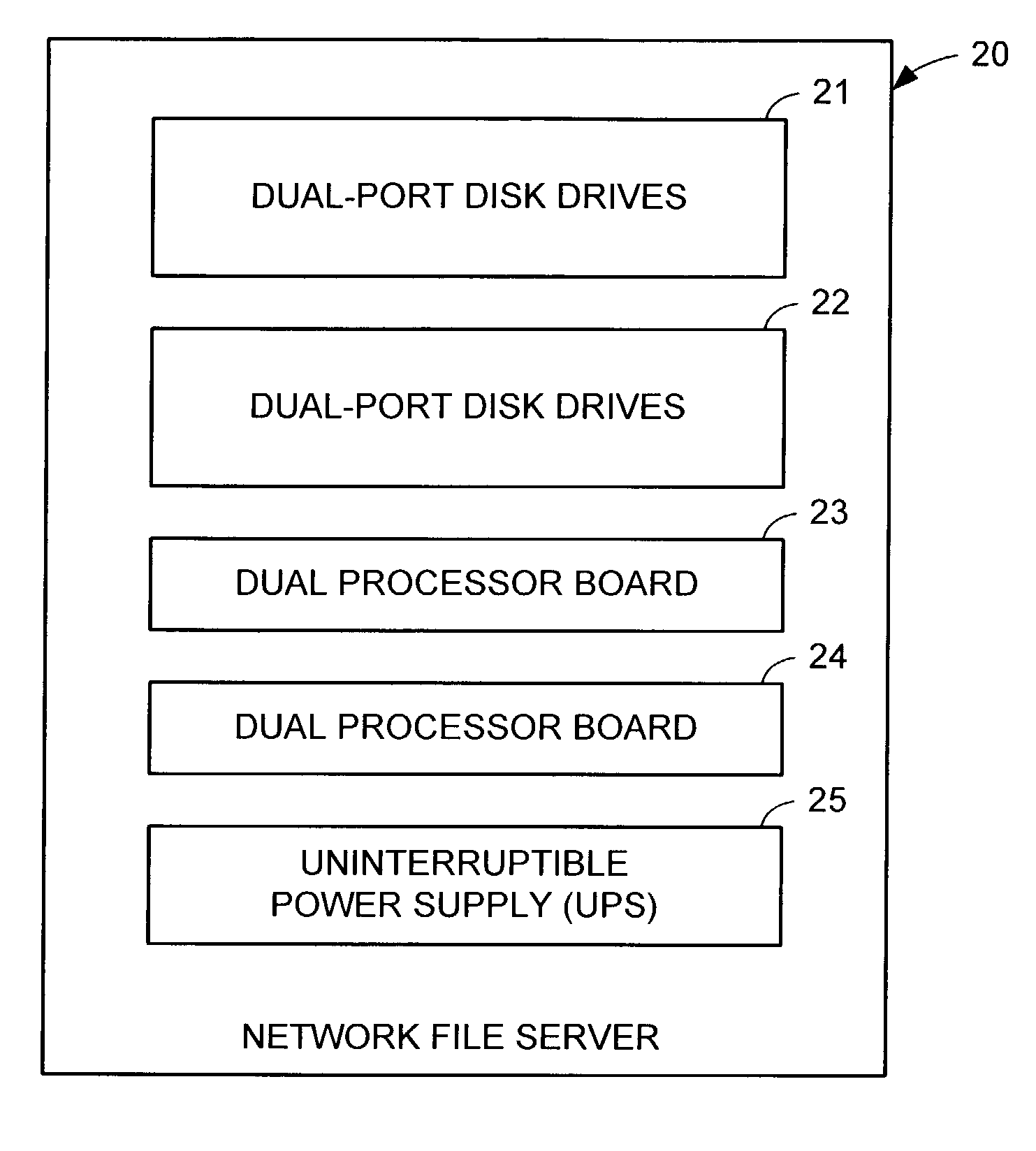
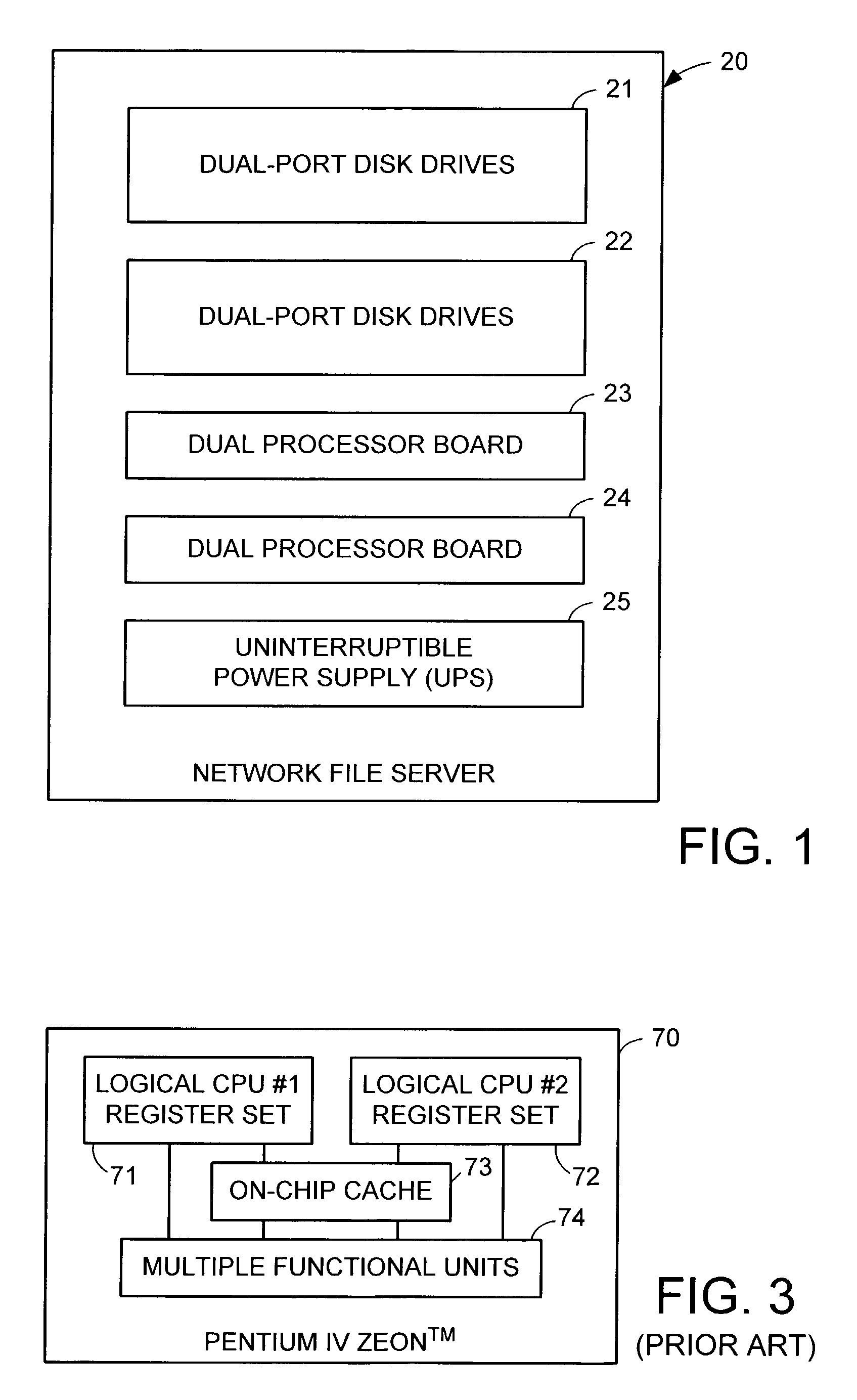
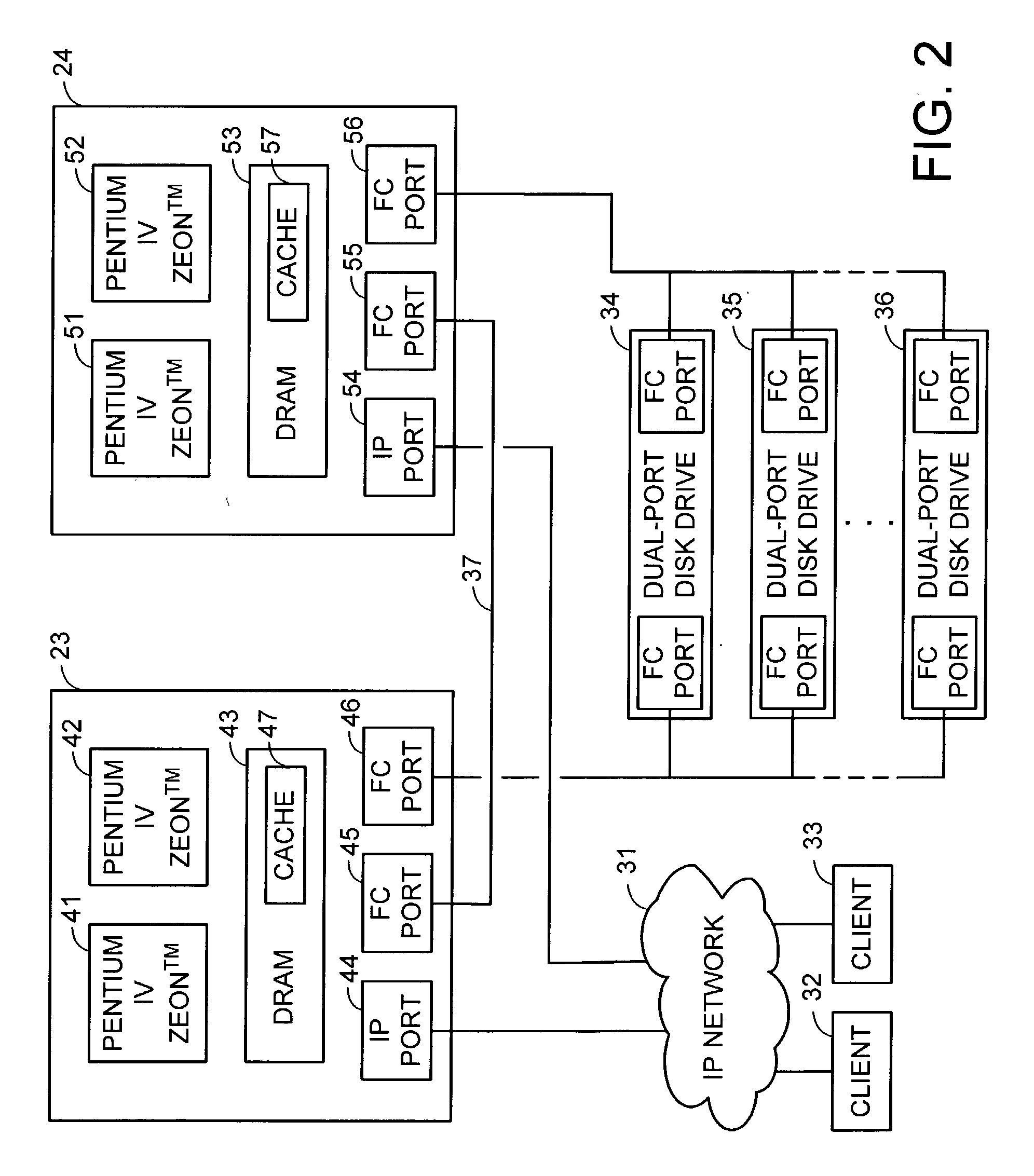
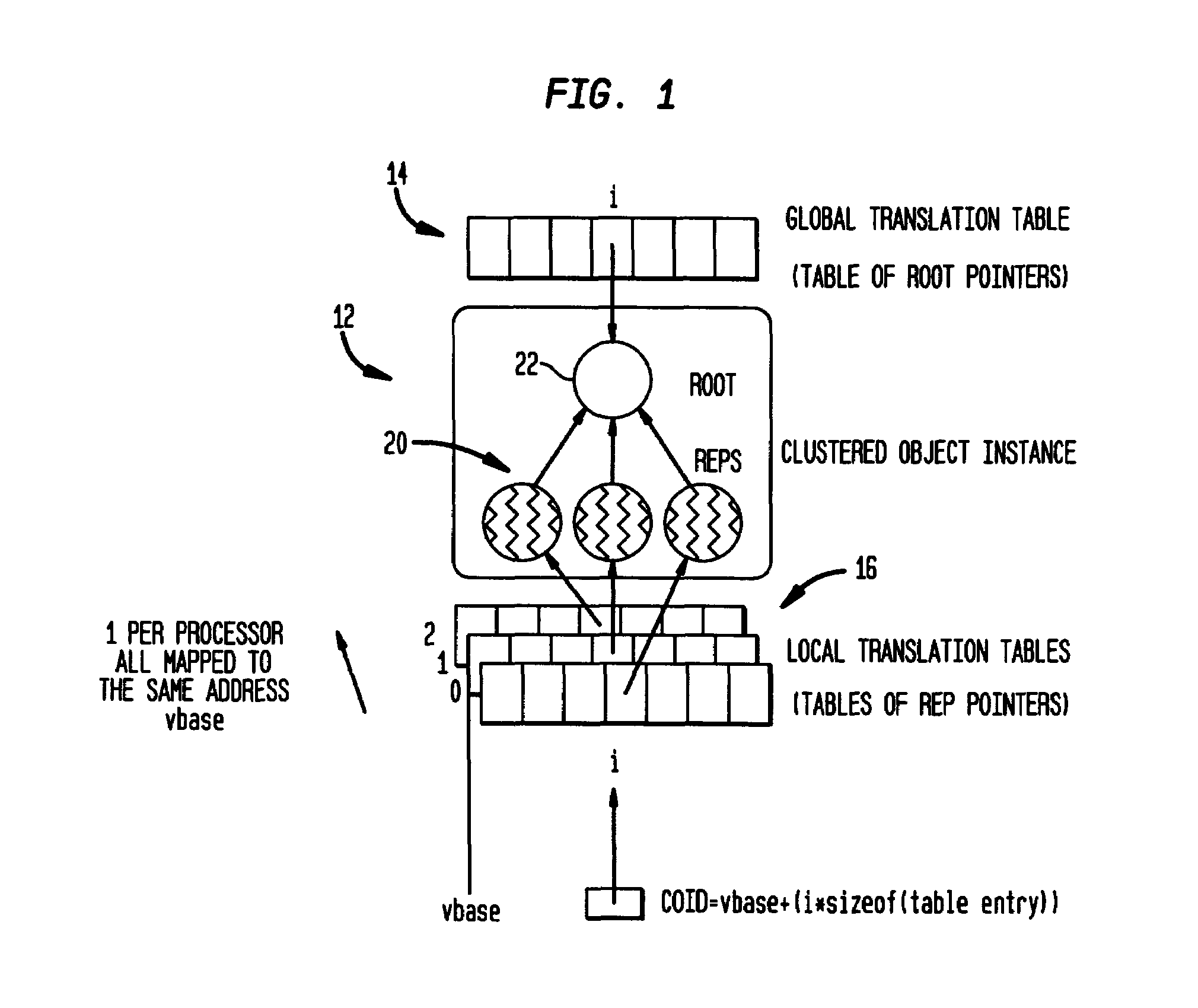
Redundant multi-processor and logical processor configuration for a file server
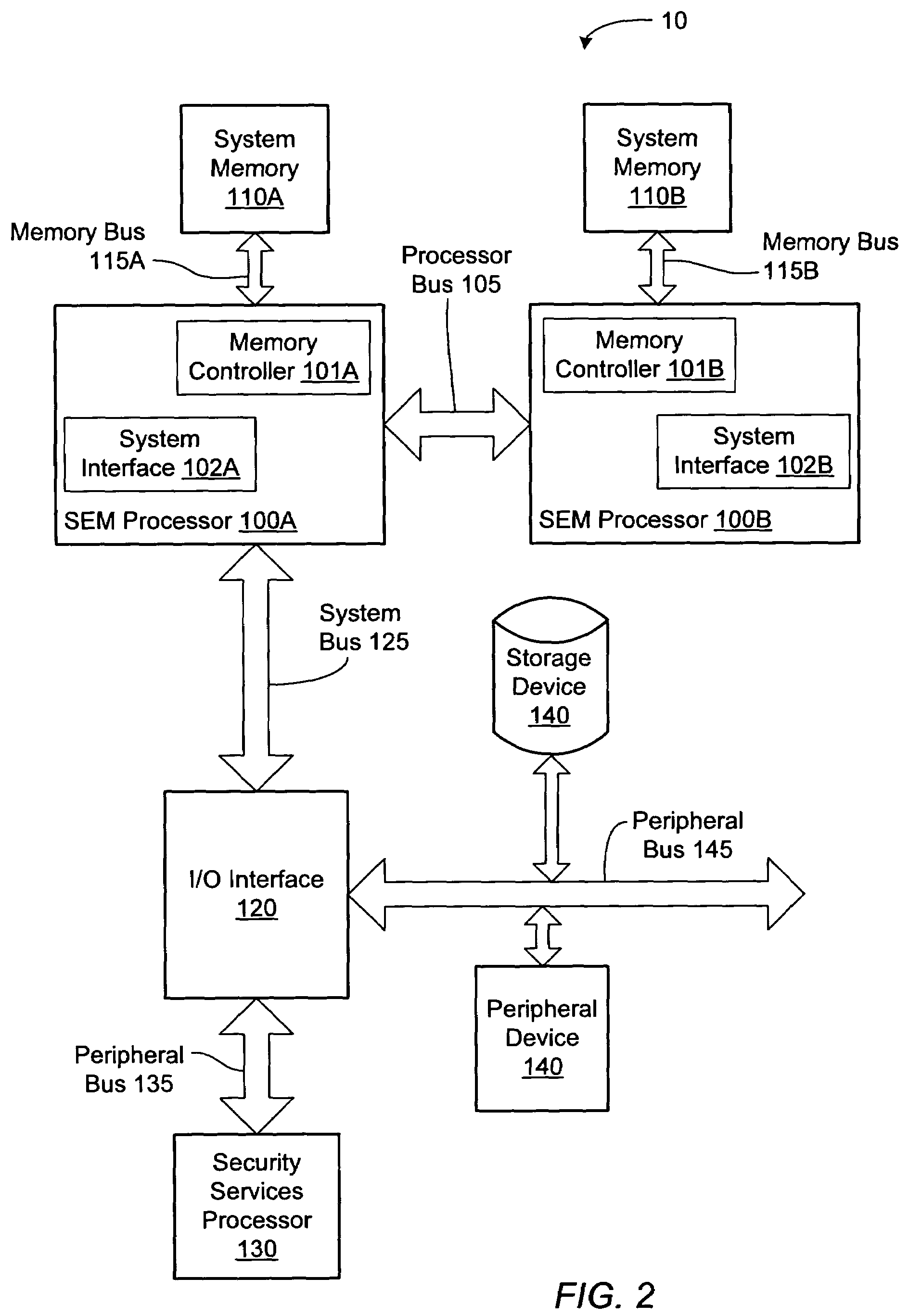
A redundant file server includes at least two dual processor boards. Each physical processor has two logical processors. The first logical processor of the first physical processor of each board executes storage system code under the Microsoft NT™ operating system. The second logical processor of the first physical processor of each board executes control station code under the Linux operating system. The first logical processor of the second physical processor of each board executes data mover code. The second logical processor of the second physical processor of each board is kept in a stand-by mode for assuming data mover functions upon failure of the first logical processor of the second physical processor on the first or second board.
Owner:EMC IP HLDG CO LLC
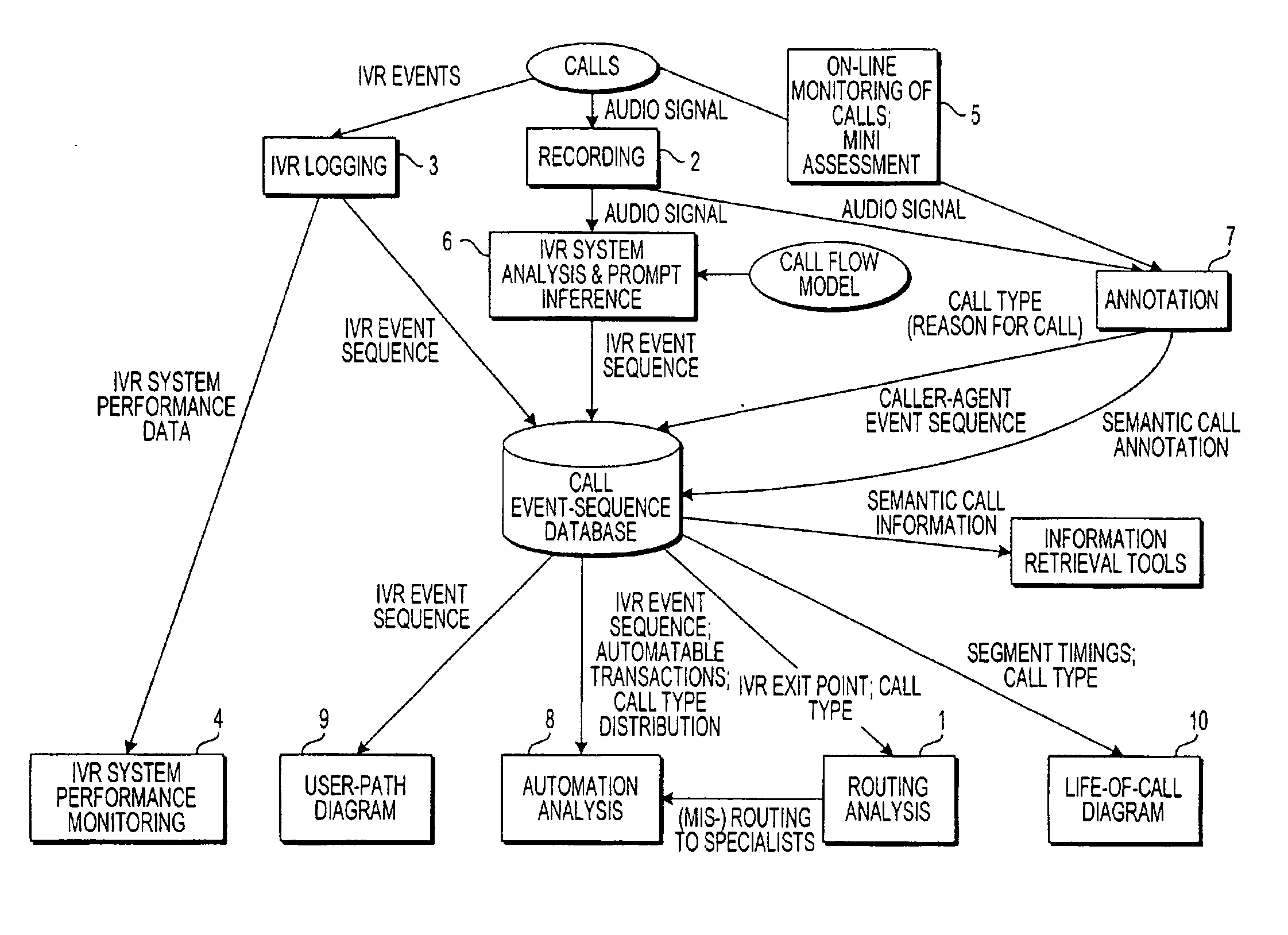
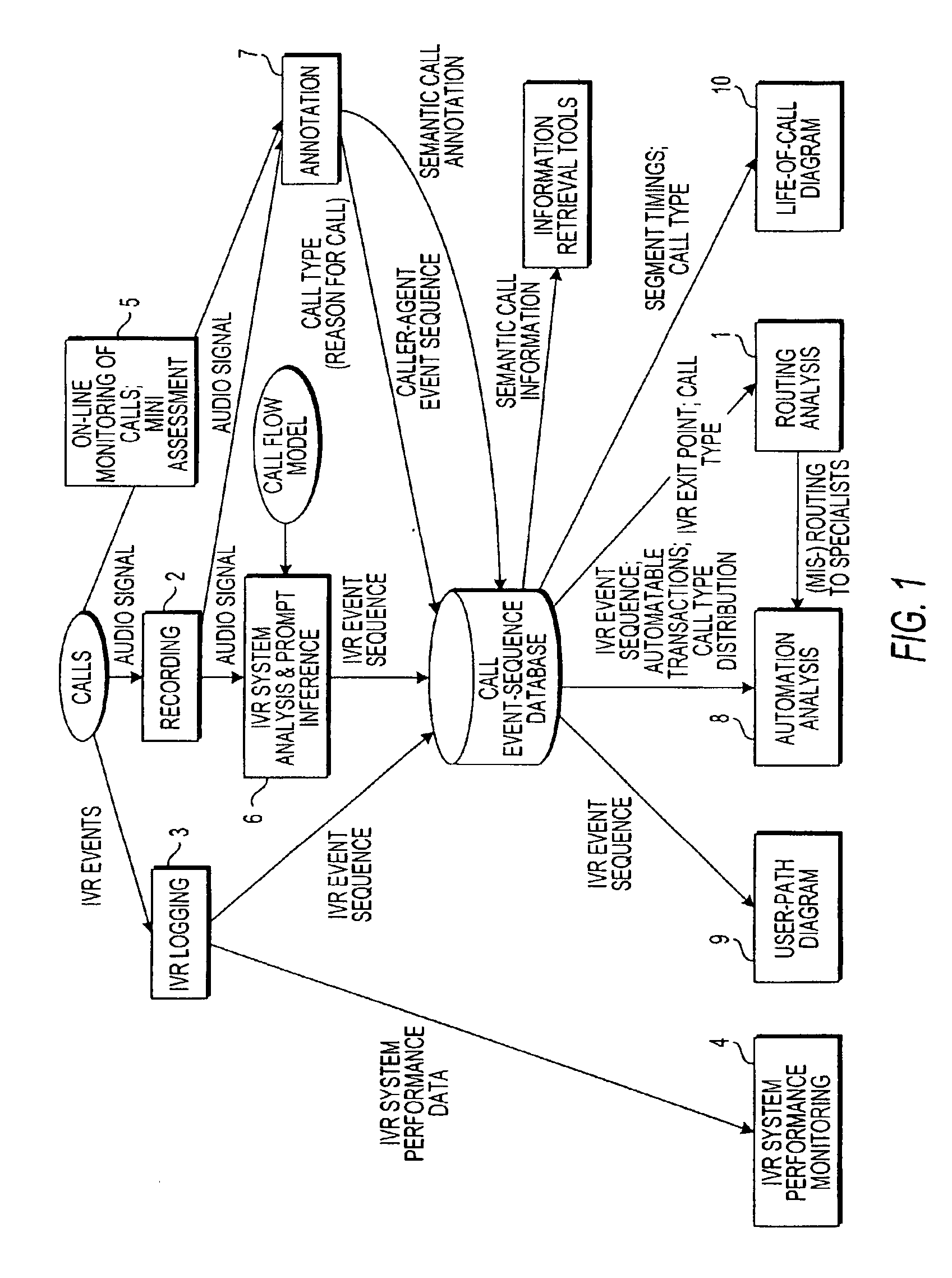
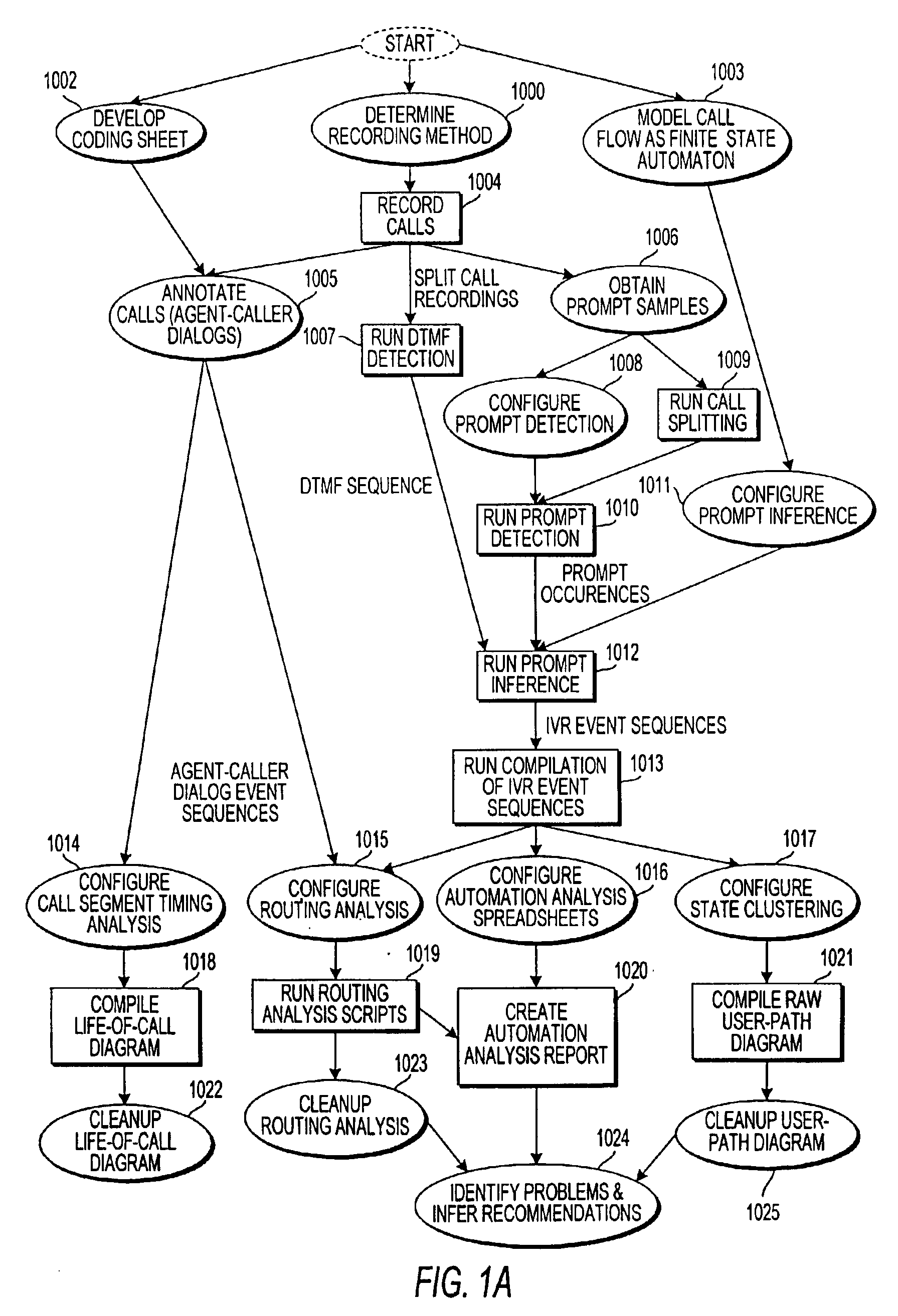
Apparatus and method for analyzing routing of calls in an automated response system
ActiveUS6879685B1Overcome deficienciesAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersSpeech soundCall routing
A system for analyzing the performance of an interactive voice response (IVR) system operates to record from end to end plural calls from callers. For a plurality of calls, the system codes and annotates an agent-caller interaction, including a topic discussed during the interaction; detects a routing operation of the IVR system by detecting a sequence of events in the IVR system, with reference to a call-flow file that summarizes the call-flow model of the IVR system, for each call; and cross-tabulates routing information obtained from the detected sequence of events with results from the coded and annotated agent-caller interactions.
Owner:VERIZON PATENT & LICENSING INC +1
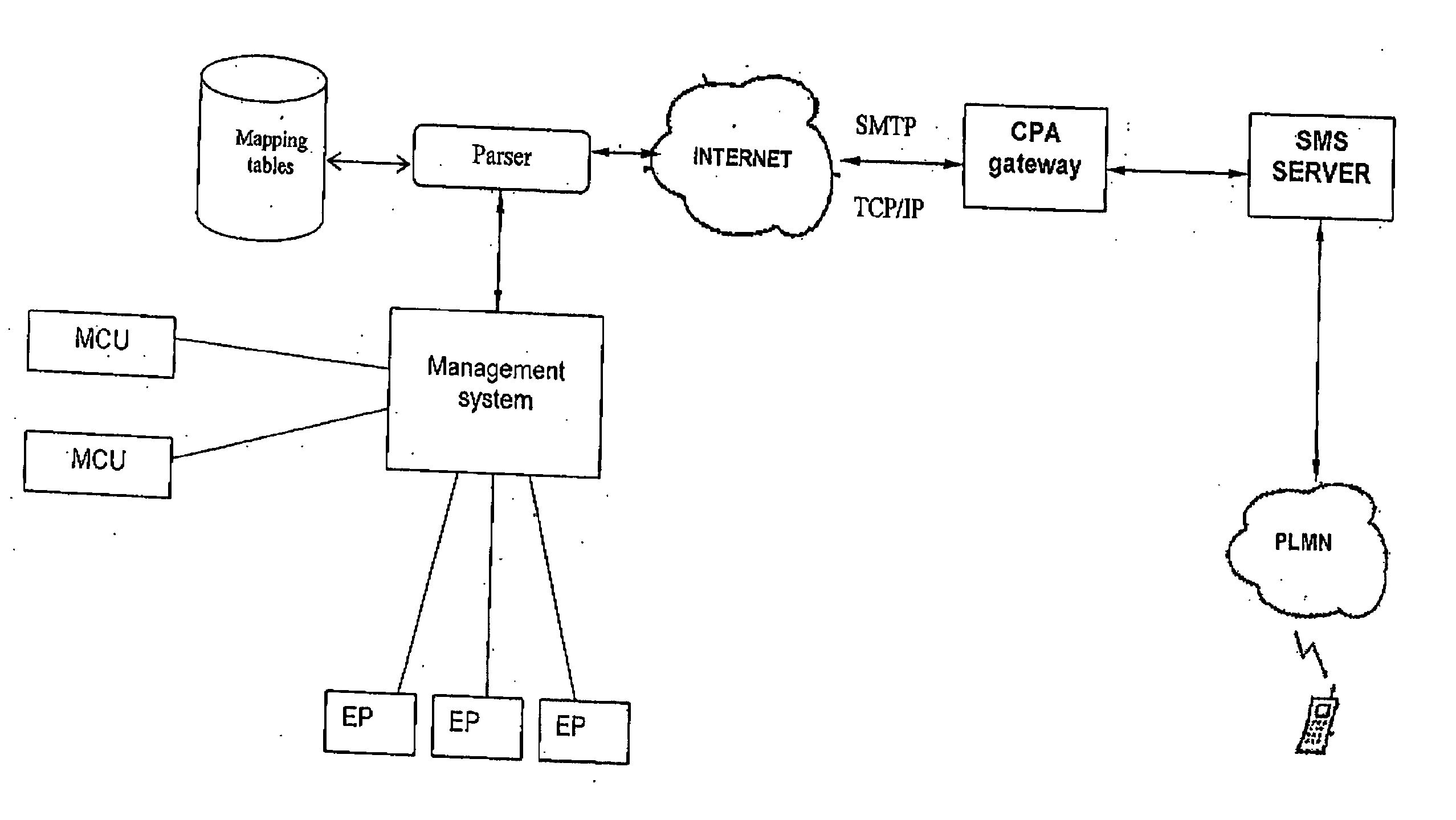
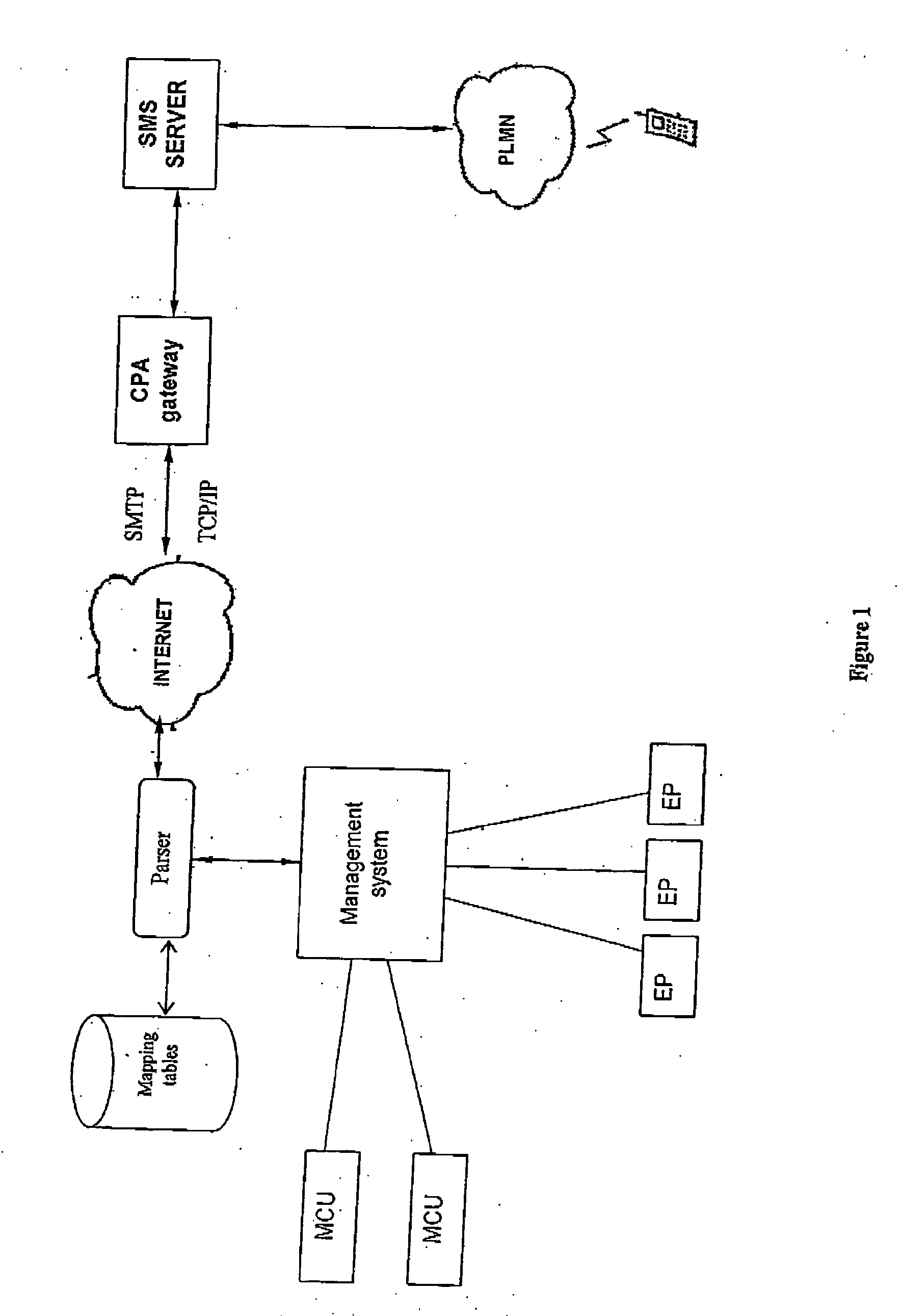
Monitoring and control of administration systems
InactiveUS20060012672A1Avoid problemsTelevision conference systemsTwo-way working systemsConference managementMonitoring and control
The present invention allows administrators of conference equipment, remotely localized from the ordinary managing interface, to execute simple commands for solving a problem that may have occurred during a conference or at conference set up. This is provided by a parser translating user terminal commands transmitted from the user terminal (e.g. a cellular phone) of the system administrator to Conference Management System codes, which are executed on the conference equipment in question from the Conference Management System. The present invention also allows system administrators to be alerted by a message (e.g. SMS) at any errors occurring during a conference or conference set up, and to correct the errors by responding to the alert without the need of addressing the equipment in which the errors occur
Owner:CISCO TECH INC
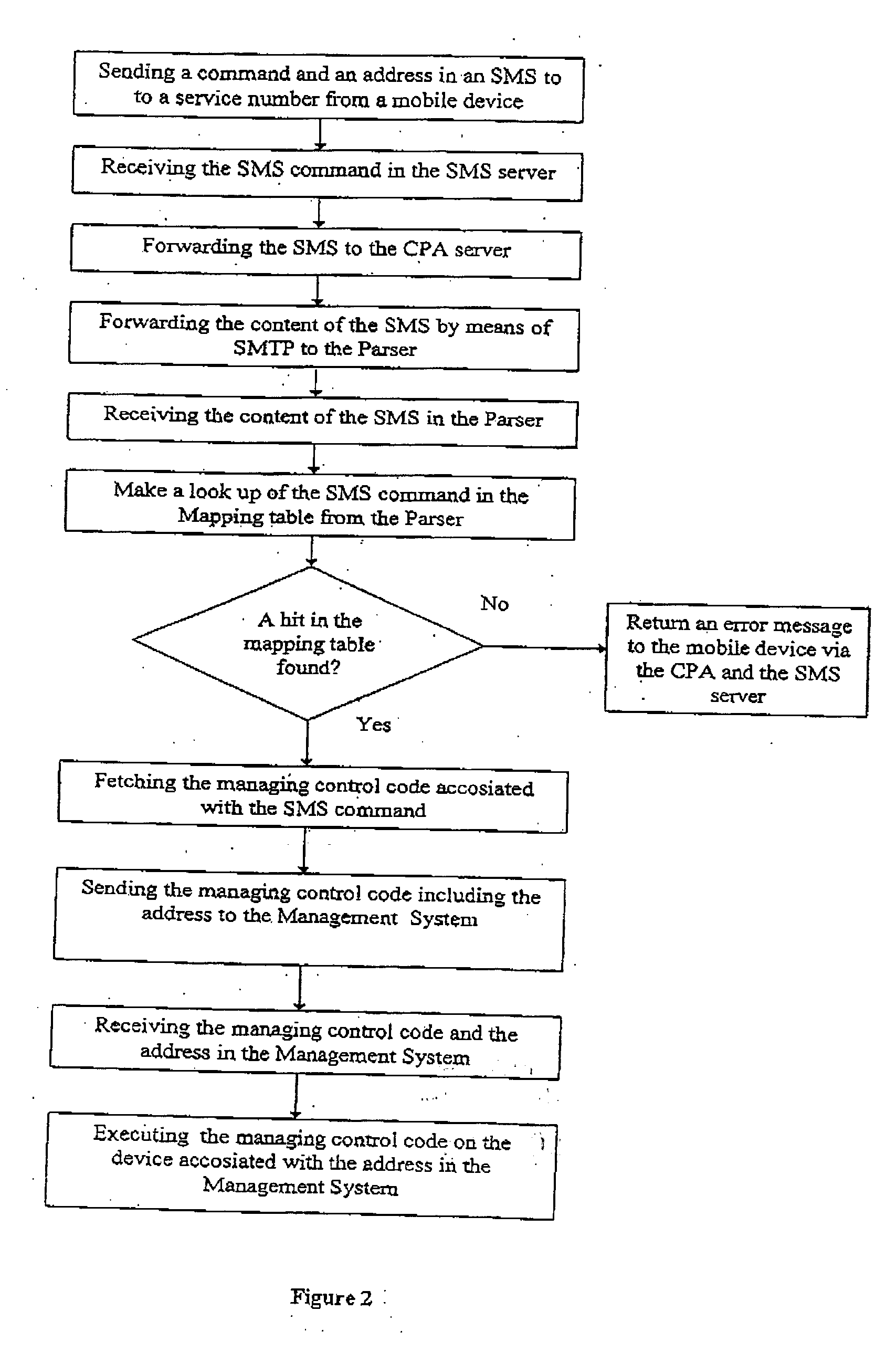
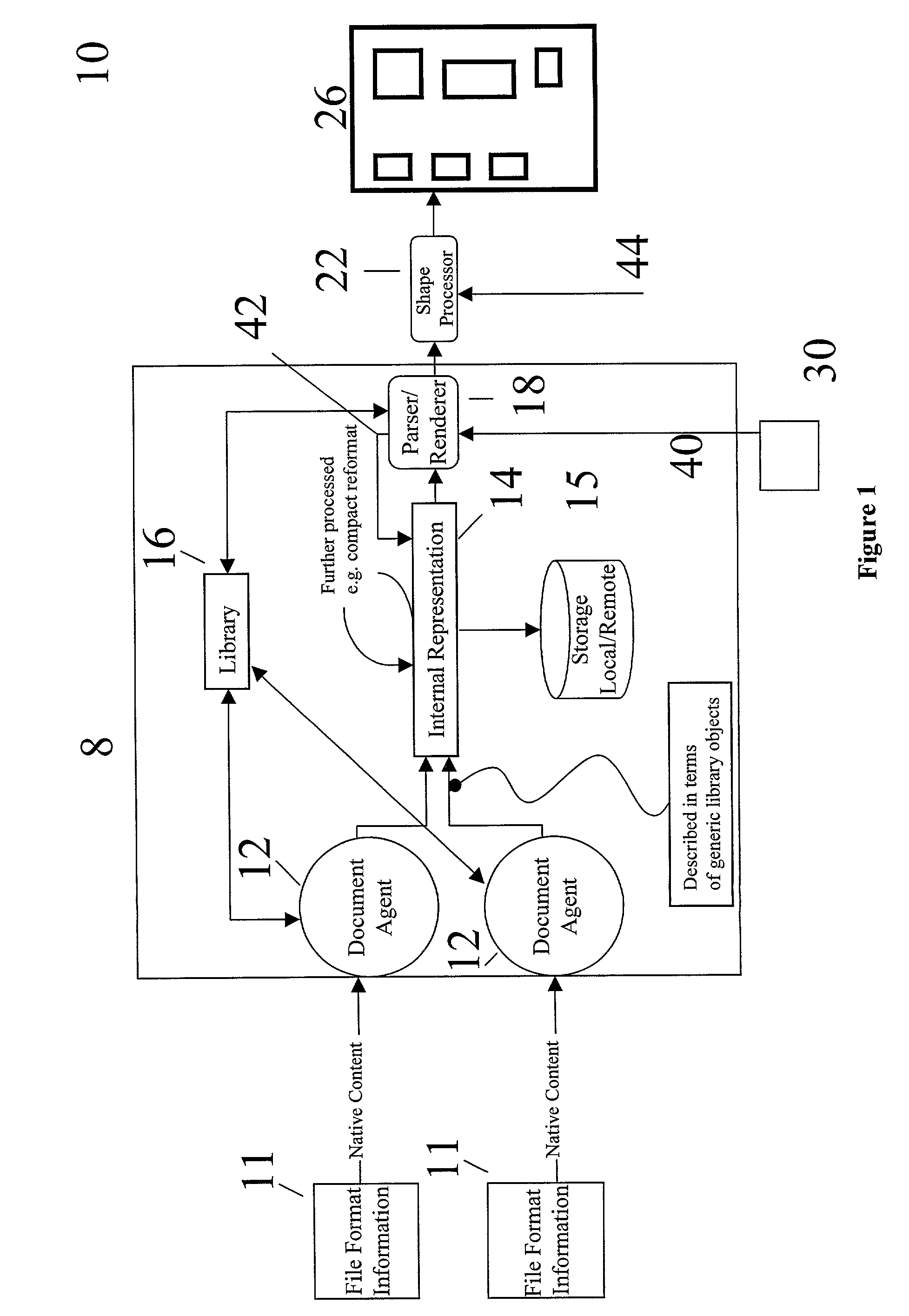
User interface systems and methods for manipulating and viewing digital documents
InactiveUS7450114B2Easily manipulateEasy to viewStatic indicating devicesDigital data processing detailsGraphicsDisplay device
Systems, including handheld computing devices that include system code stored within the memory and adapted to be executed by the processor. The system code can process an input byte stream that is representative of contents to be displayed on the touch sensitive display and can generate a content document file representative of an internal representation of the content. A tool document file may also be stored in the memory and may provide an internal representation of a document providing an image that is representative of a graphical tool. Associated with a tool document can be tool code that is capable of processing the content document file to create an internal representation of the contents that presents the content in a manner that achieves a display effect associated with the tool. The device will also include parsing code that processes the content document file, the tool document file, and the processed internal representation to generate a screen document for display on the touch sensitive display in a manner that portrays the display effect.
Owner:SAMSUNG ELECTRONICS CO LTD
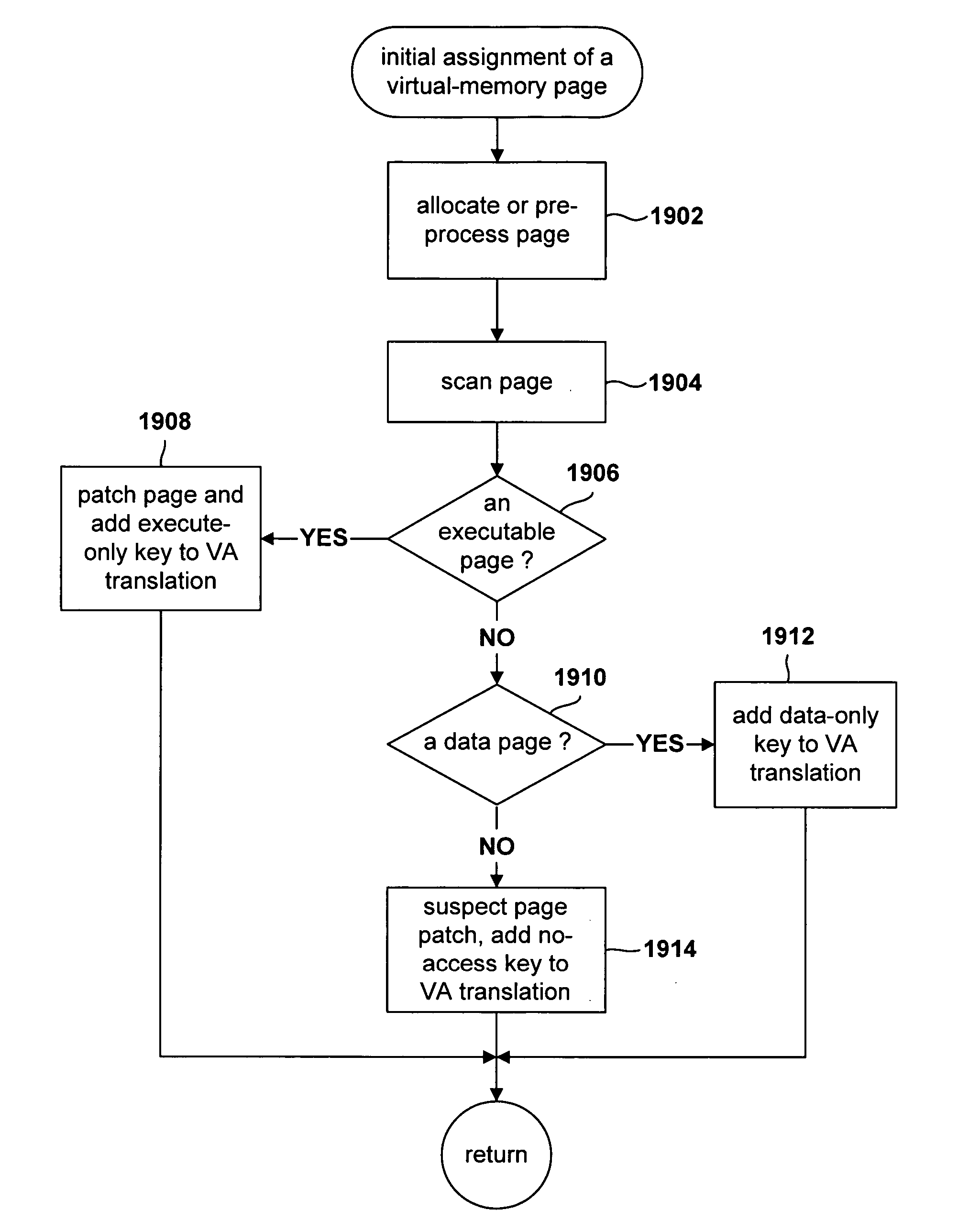
Method for monitoring access to virtual memory pages
InactiveUS20060036830A1Internal/peripheral component protectionMemory systemsVirtual memoryOperational system
Various embodiments of the present invention are directed to efficient methods for virtual-machine monitors to detect, at run time, initial attempts by guest operating systems and other higher-level software to access or execute particular instructions or values corresponding to the particular instructions, that, when accessed for execution, need to be emulated by a virtual-machine monitor, rather than directly accessed by guest operating systems. In certain embodiments of the present invention, the virtual-machine monitor assigns various guest-operating-system-code-containing memory pages to one of a small number of protection-key domains. By doing so, the virtual-machine monitor can arrange for any initial access to the memory pages assigned to the protection-key domains to generate a key-permission fault, after which the key-permission-fault handler of the virtual-machine monitor is invoked to arrange for subsequent, efficient access or emulation of access to the protected pages. In alternative embodiments, protection domains can be implemented by using page-level access rights or translation-lookaside-buffer entry fields.
Owner:HEWLETT PACKARD DEV CO LP
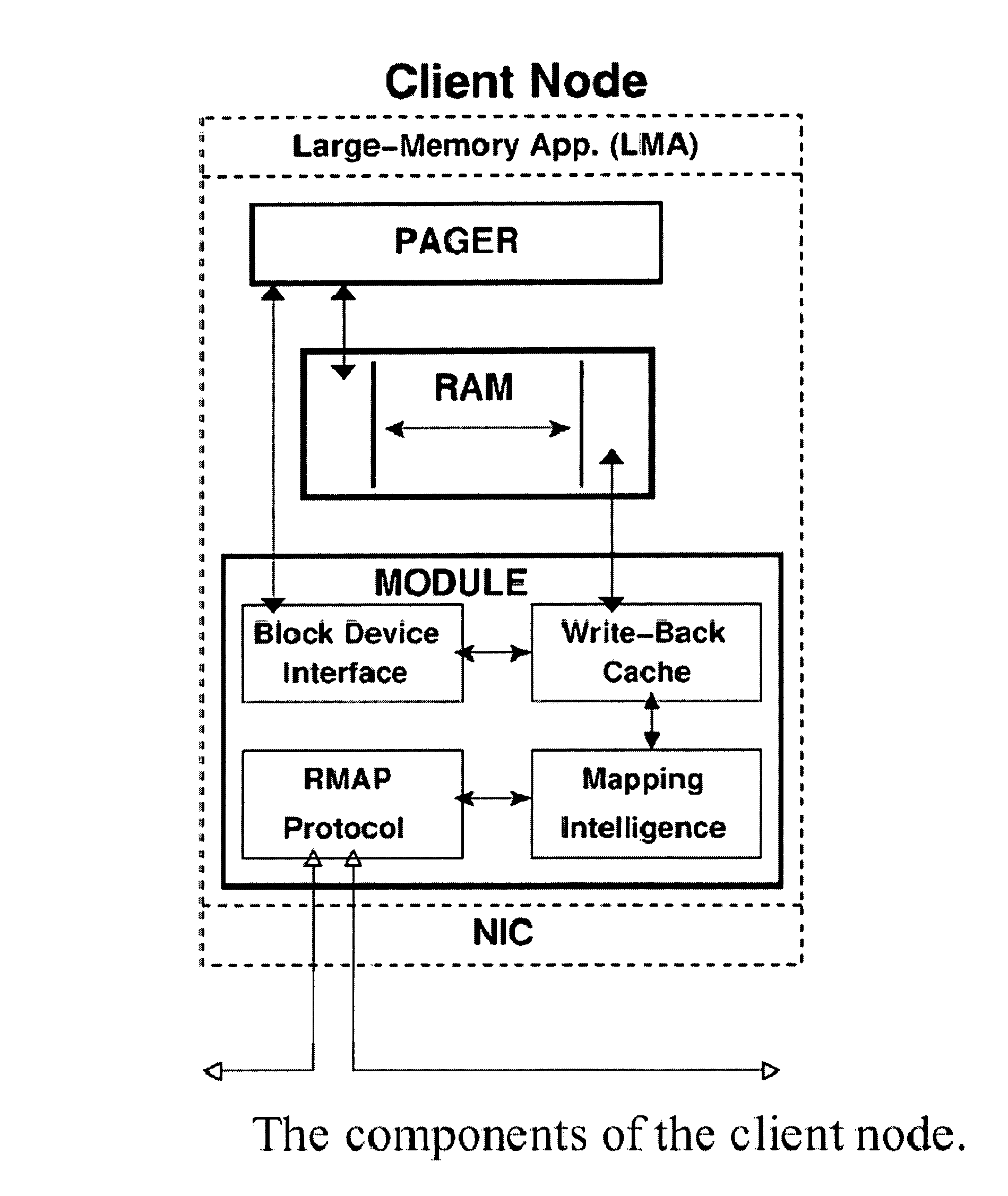
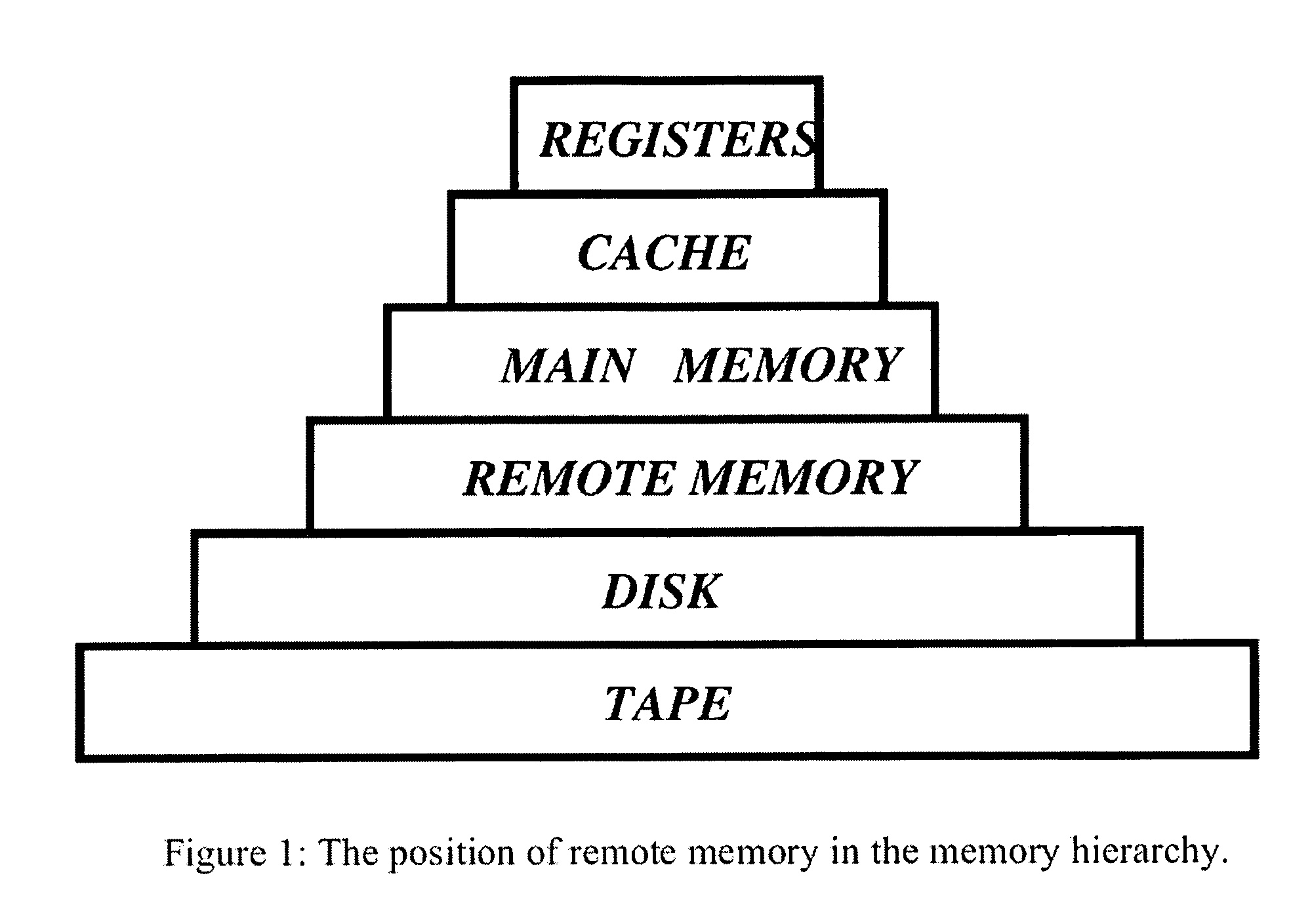
Distributed adaptive network memory engine
ActiveUS7917599B1Processing speedLower latencyMultiple digital computer combinationsTransmissionMass storageOperational system
Memory demands of large-memory applications continue to remain one step ahead of the improvements in DRAM capacities of commodity systems. Performance of such applications degrades rapidly once the system hits the physical memory limit and starts paging to the local disk. A distributed network-based virtual memory scheme is provided which treats remote memory as another level in the memory hierarchy between very fast local memory and very slow local disks. Performance over gigabit Ethernet shows significant performance gains over local disk. Large memory applications may access potentially unlimited network memory resources without requiring any application or operating system code modifications, relinkling or recompilation. A preferred embodiment employs kernel-level driver software.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Redundant multi-processor and logical processor configuration for a file server
A redundant file server includes at least two dual processor boards. Each physical processor has two logical processors. The first logical processor of the first physical processor of each board executes storage system code under the Microsoft NT(TM) operating system. The second logical processor of the first physical processor of each board executes control station code under the Linux operating system. The first logical processor of the second physical processor of each board executes data mover code. The second logical processor of the second physical processor of each board is kept in a stand-by mode for assuming data mover functions upon failure of the first logical processor of the second physical processor on the first or second board.
Owner:EMC IP HLDG CO LLC
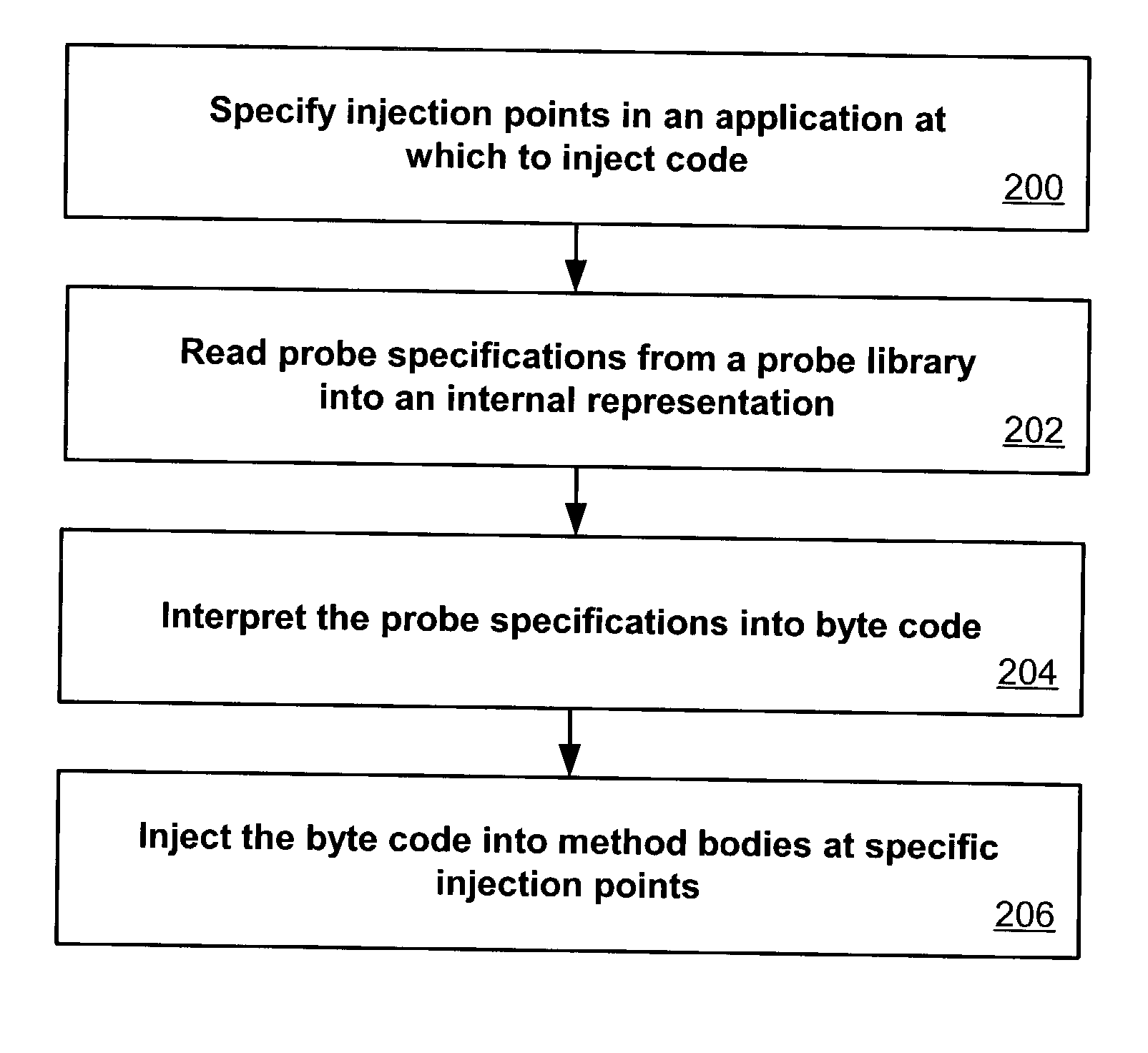
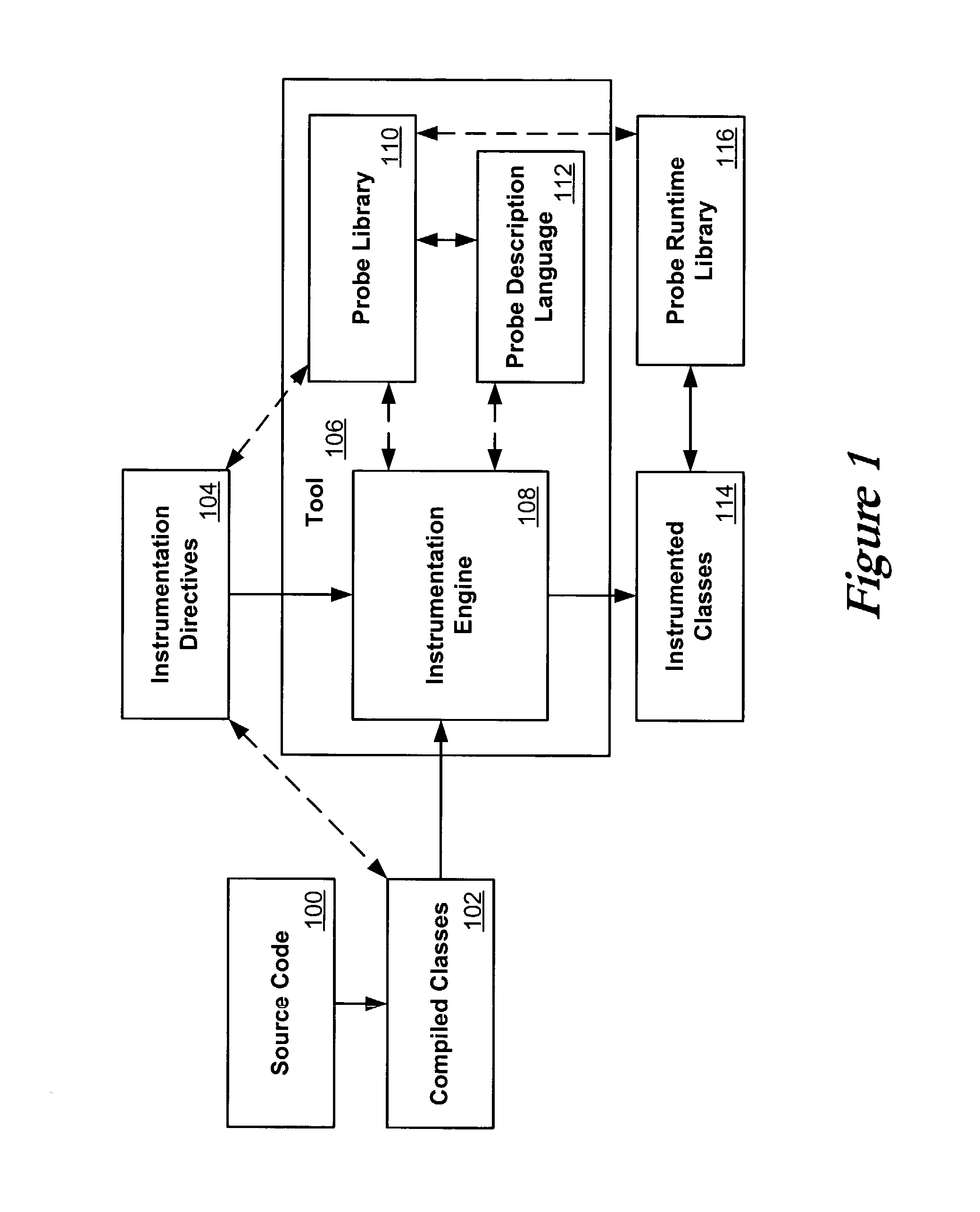
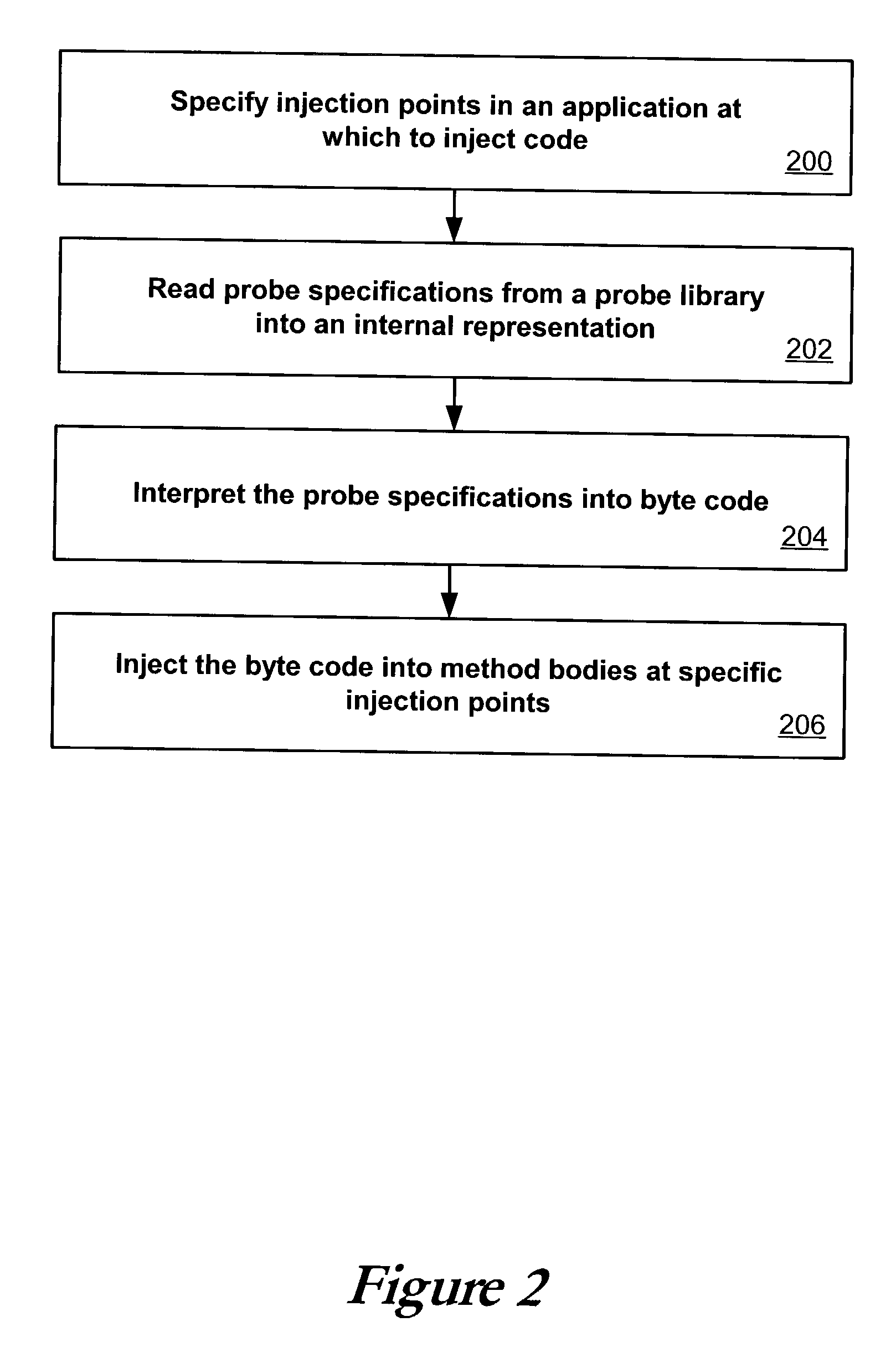
Flexible and extensible java bytecode instrumentation system
ActiveUS20030149960A1Error detection/correctionDigital computer detailsInjection pointCode injection
Code can be injected into a compiled application through the use of probes comprised of instrumentation code. Probes can be implemented in a custom high level language that hides low level instruction details. A directive file contains instructions on injecting a probe into a compiled application. An instrumentation engine reads these instructions and injects the probe into the compiled application at the appropriate injection points. Multiple probes can be used, and can be stored in a probe library. Each probe can inject code into the application at, for example, a package, class, method, or line of the compiled application. Calls can also be made to external runtime libraries. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
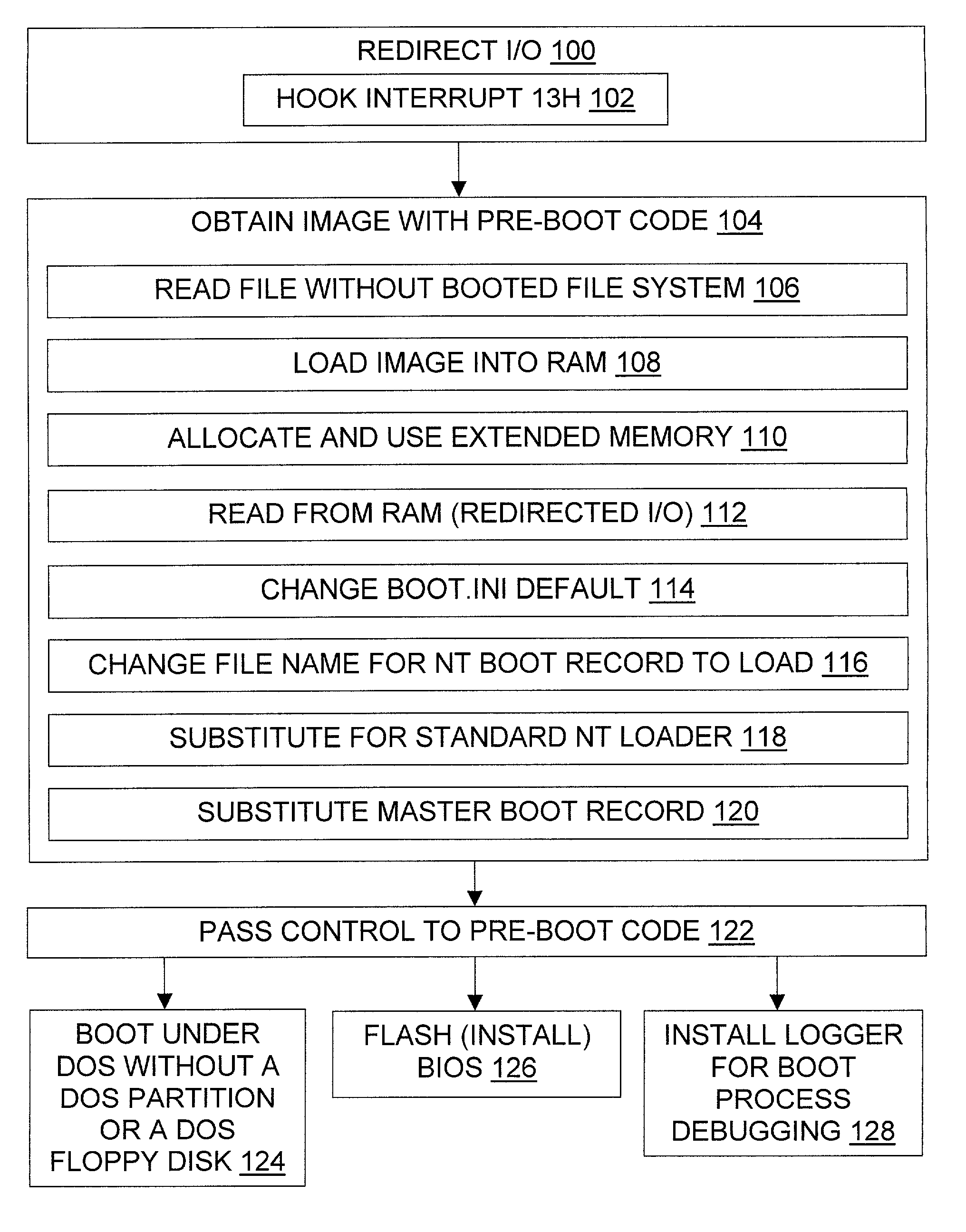
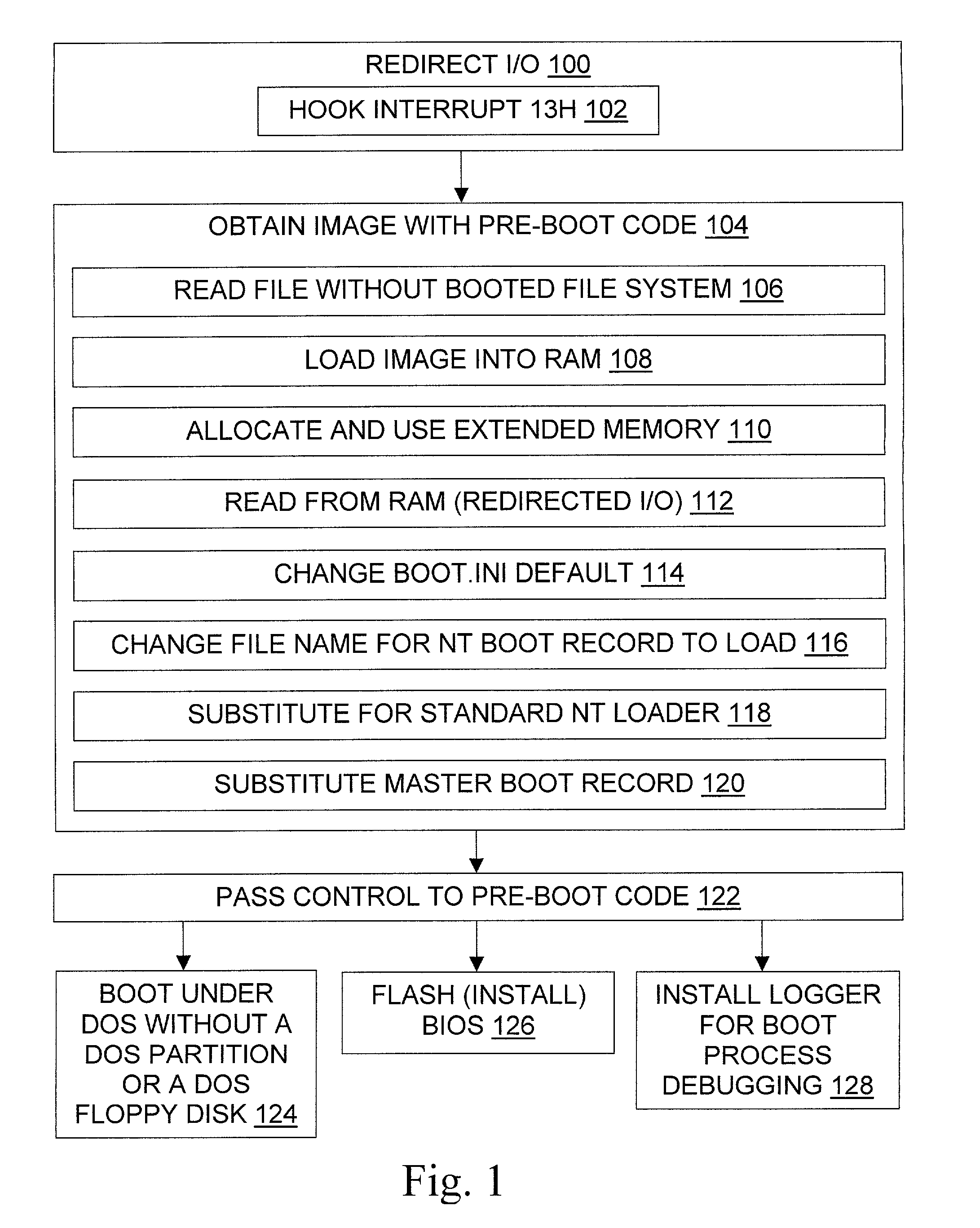
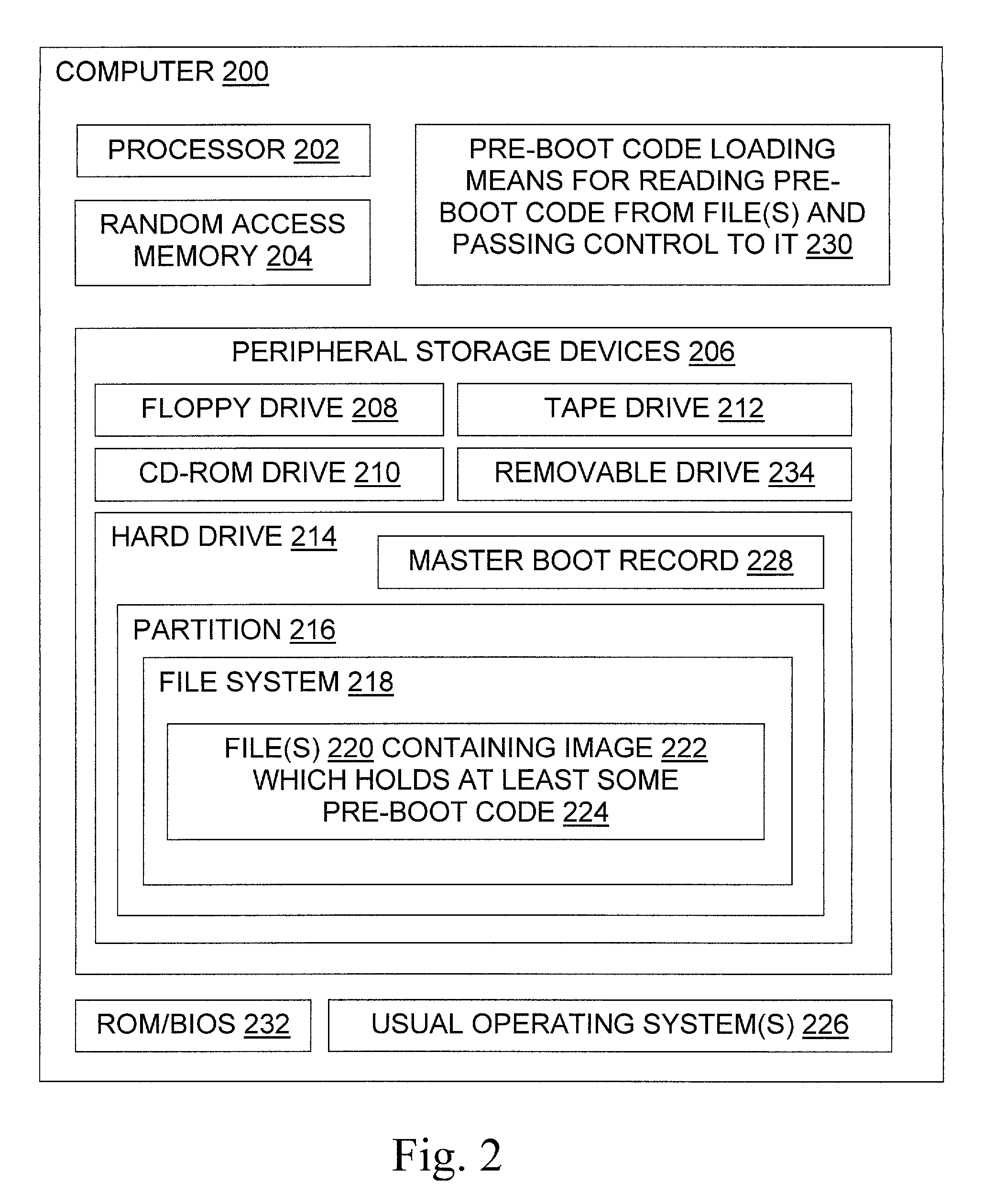
Booting an operating system or running other pre-boot code from a file stored under a different operating system
InactiveUS6996706B1Increase flexibilityWithout usingDigital computer detailsBootstrappingOperational systemFile system
The invention provides tools and techniques for running pre-boot code on a computer from a file stored in a file system on the computer. The pre-boot code may include an operating system which is not otherwise installed on the system. For instance, the pre-boot code may be used to boot a DOS operating system on a computer which lacks a DOS hard disk partition. The pre-boot code may contain code to perform operations that are difficult to perform after the operating system is booted, such as code for monitoring the boot process to help debug it. The pre-boot code is obtained from the file without using booted file system code, and is then executed. The code may be obtained by redirecting floppy drive I / O to read the pre-boot code from a copy in memory, or to read it as needed from one or more files on the hard disk.
Owner:GEN DIGITAL INC
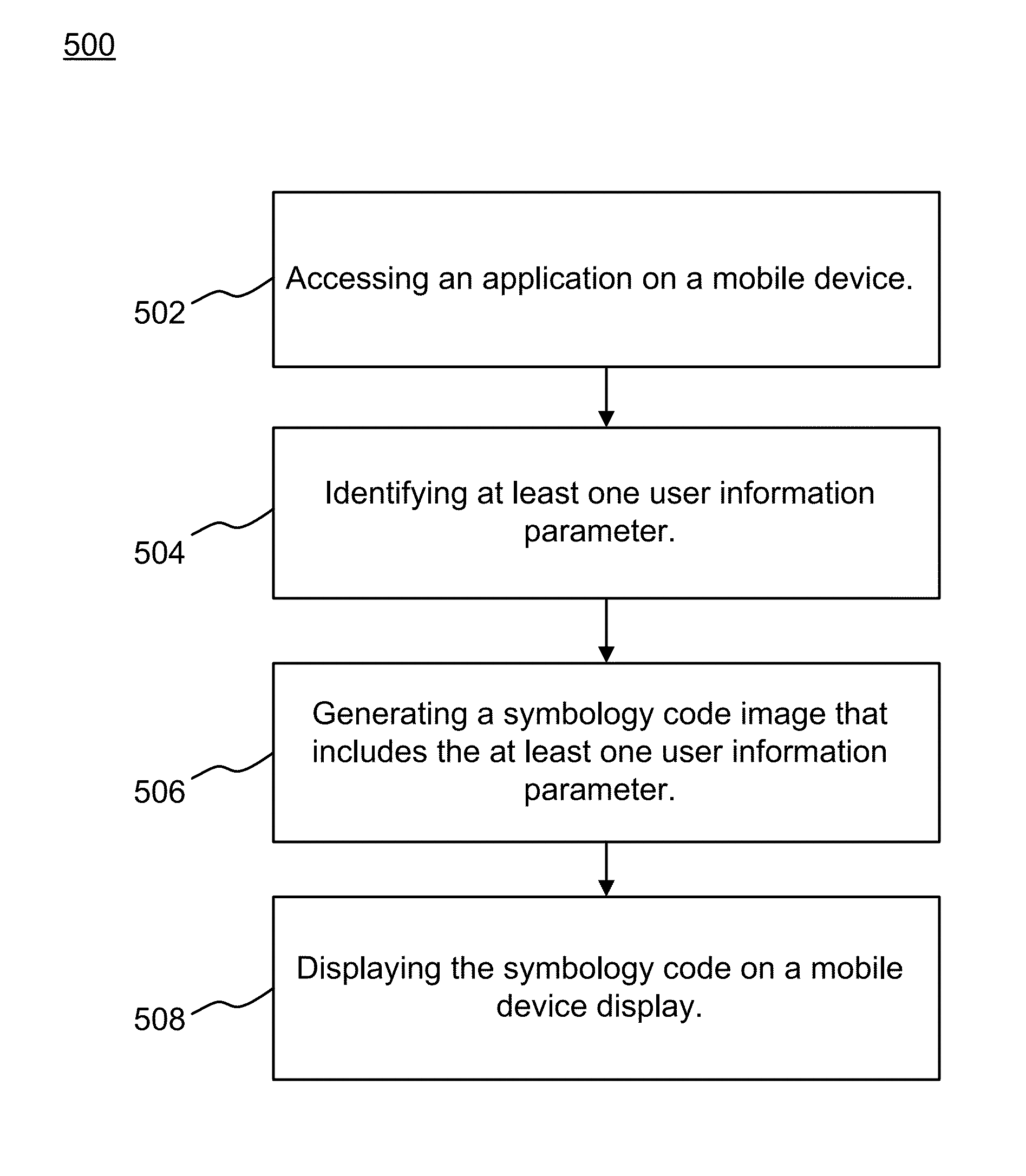
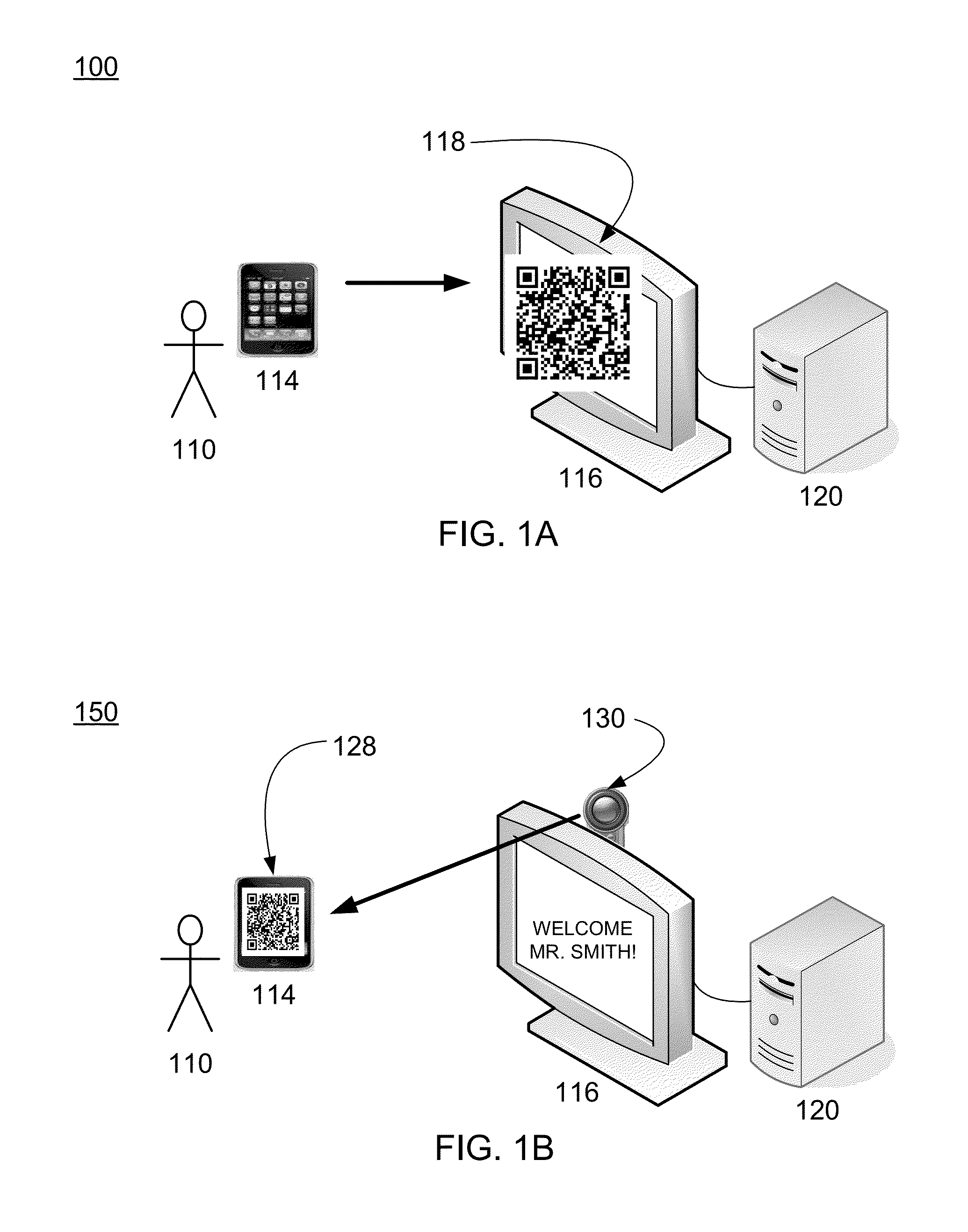
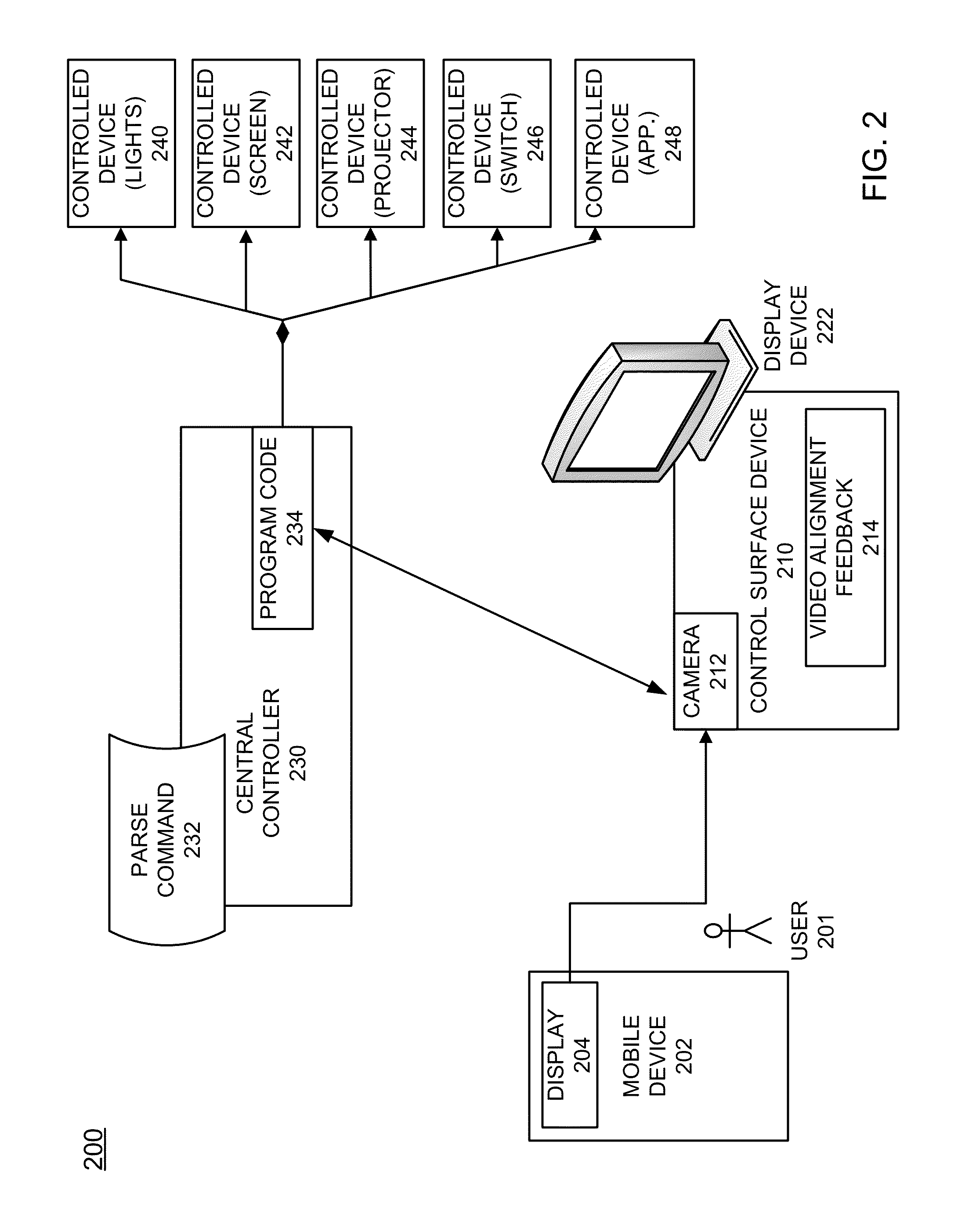
Method and apparatus of processing symbology interactions between mobile stations and a control system
ActiveUS20140001253A1Payment architectureRecord carriers used with machinesSymbolic SystemsControl system
Disclosed are an apparatus and method of creating, displaying and utilizing quick response (QR) codes to perform processing an application on a mobile device and a control system network. One example method of operation may include identifying a user information parameter and generating a symbology code image that includes the user information parameter and displaying the symbology code on a mobile device display.
Owner:HARMAN PROFESSIONAL INC
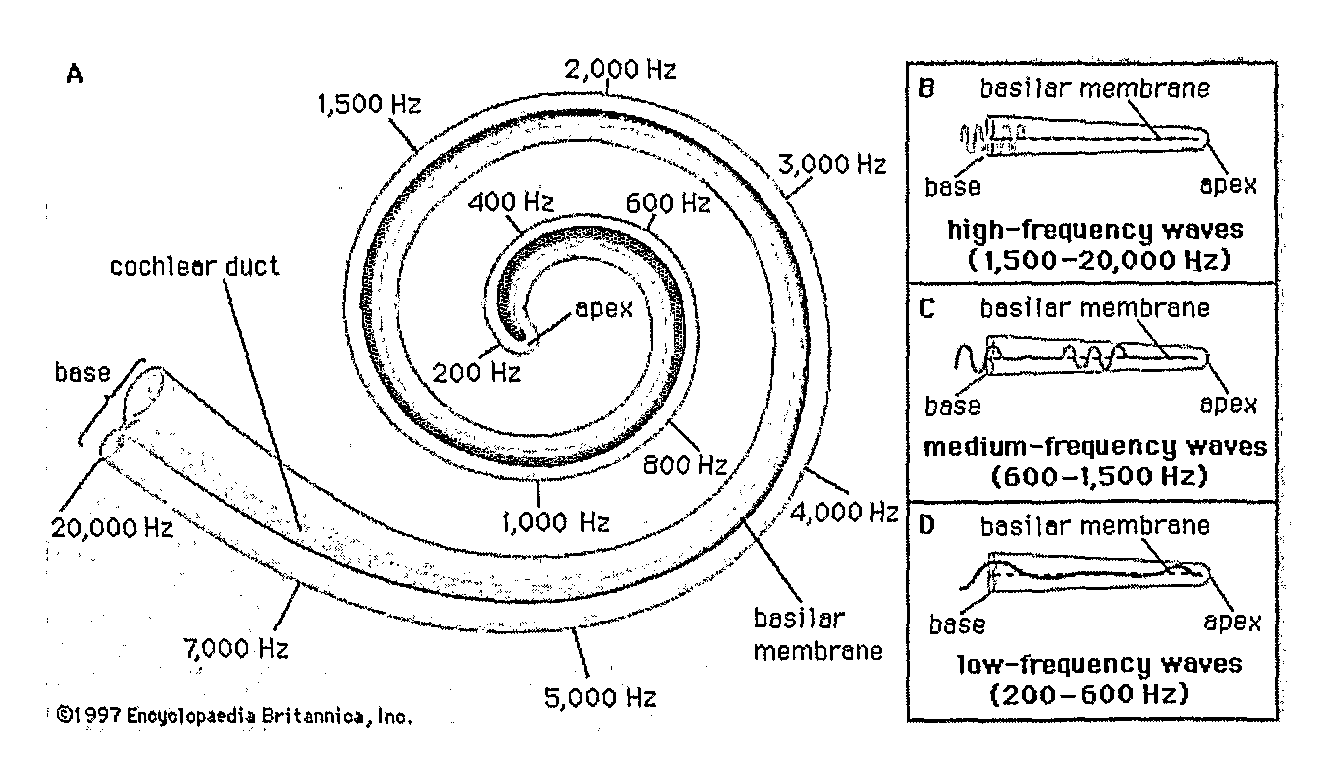
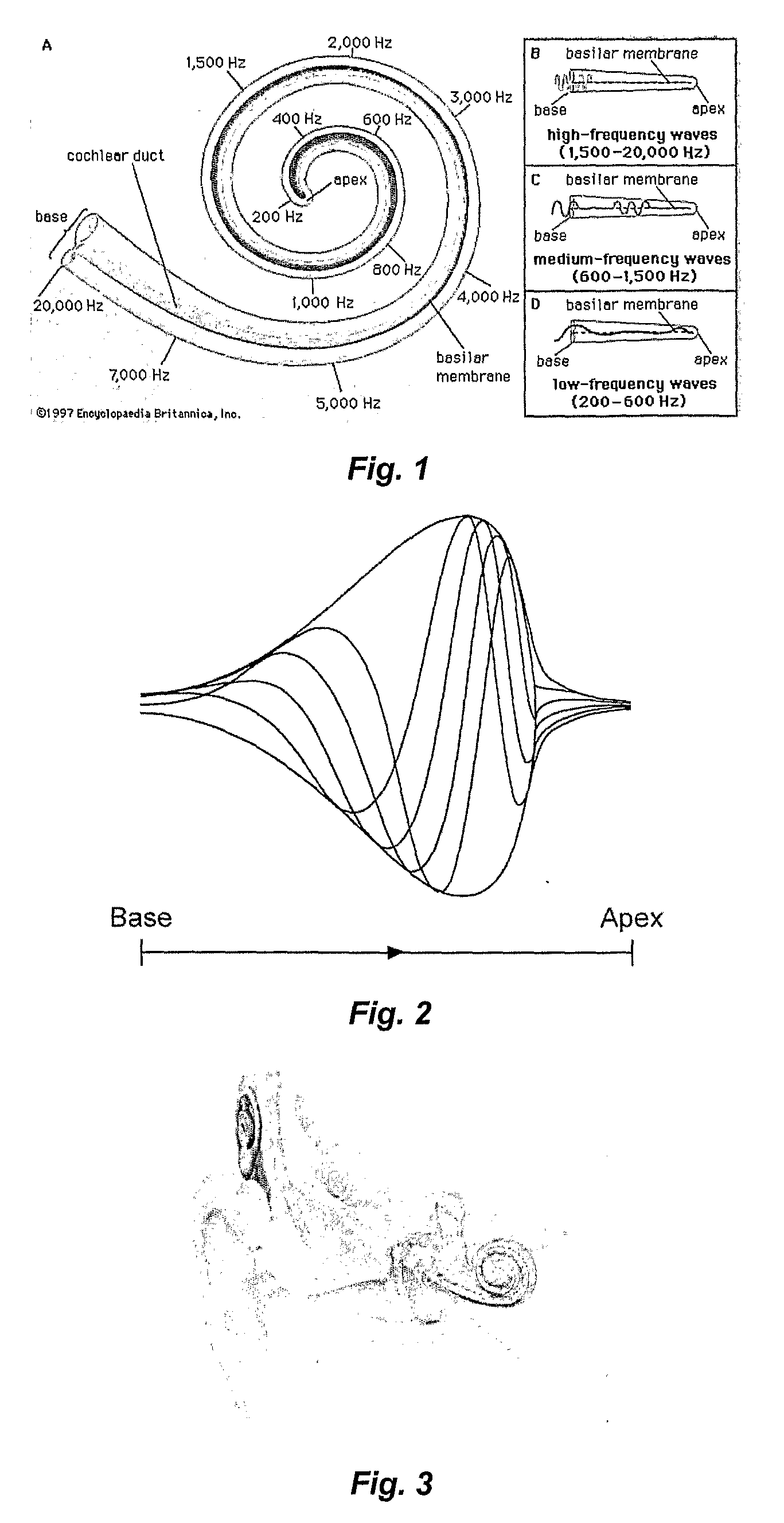
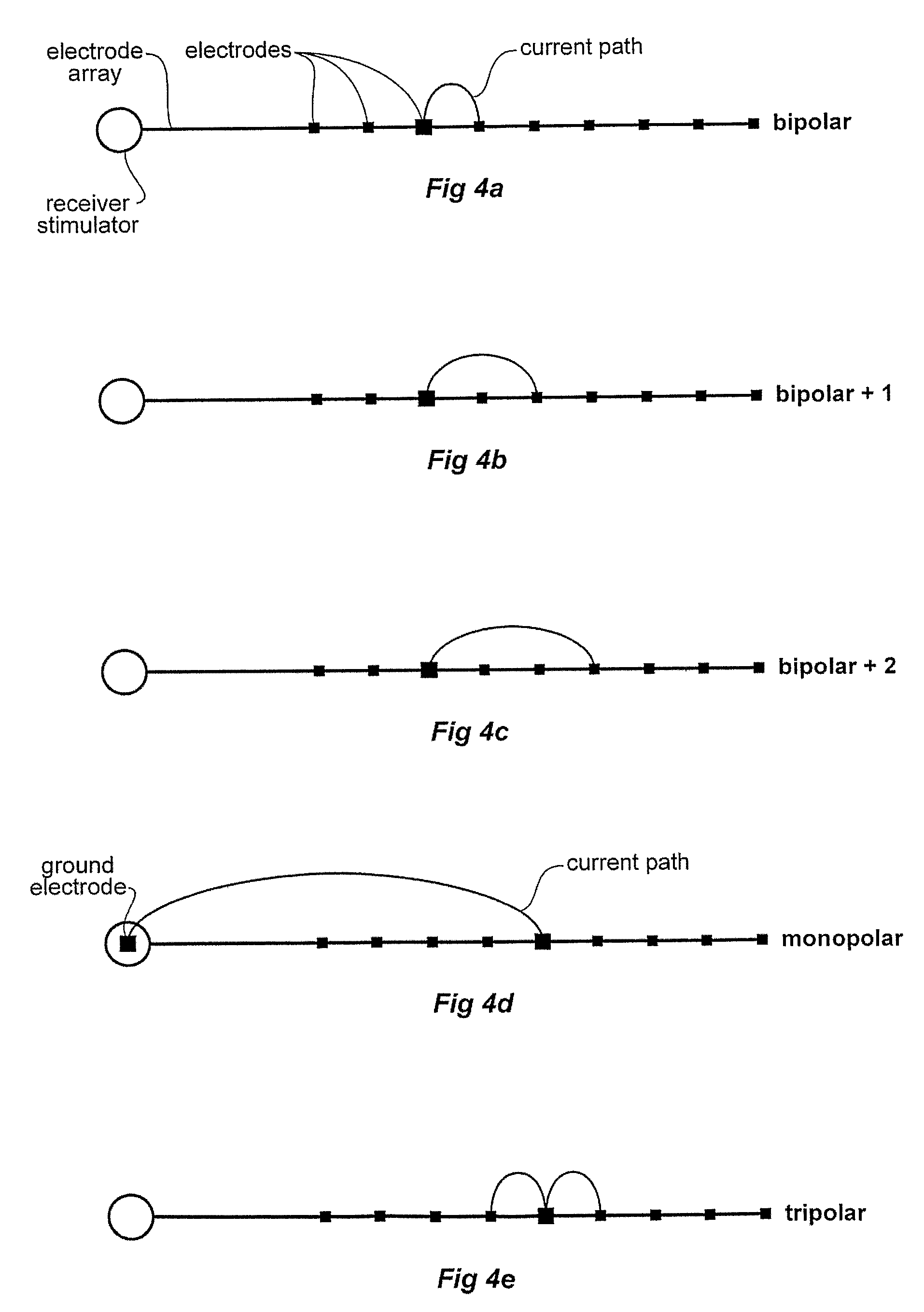
Sound processing method and system
Coding of received audio signals and the resulting application of electrical stimuli applied to electrodes used in a cochlear implant system are disclosed together with a method of fitting this new coding strategy. One of the aims is to place specific stimulation representing pitch by applying near threshold electrical stimuli with limited and focussed excitation fields. A range of stimulation rates and a minimal range of current levels above threshold are used for creation of a dynamic loudness percept for a cochlear implant recipient. Another aim is to disclose a coding scheme based on a model of physiological measures (i.e. refractoriness, adaptation, spread of activation field, spatiotemporal acoustical cochlear activation patterns and spontaneous activity) to estimate the proportions of available excitable auditory neurons close to the electrodes available for stimulation. The spectral bands formed from the pre-processing of incoming audio signals are weighted by these proportions of excitability to control place, timing, rate and current level of electrical stimuli applied to the electrodes available in the array.
Owner:COCHLEAR LIMITED
Code compression algorithms and architectures for embedded systems
InactiveUS7095343B2Increase the compression ratioSimple designCode conversionProbit modelAdaptive coding
Code compression techniques and decompression architectures for embedded systems are disclosed, providing good compression ratio while improving decompression time for VLIW instructions and reducing bus power consumption. The invention includes two fixed-to-variable (F2V) length code compression schemes based on a reduced arithmetic code compression algorithm combining arithmetic coding with probability models; a static probability model using static coding and semi-adaptive coding using a Markov model. Multi-bit decompression methods for the F2V techniques are presented, together with a parallel decompression scheme that tags and divides a compressed block into smaller sub-blocks. The Markov model provides better compression ratio, but the static model has a less complicated decompression unit design. The invention also includes two variable-to-fixed (V2F) length coding algorithms, one based on Tunstall coding and another on arithmetic coding. The V2F algorithms are also combined with a static model and a Markov model.
Owner:THE TRUSTEES FOR PRINCETON UNIV
Channel coding and decoding method and device
ActiveCN104079370AReduce complexityImprove bit error rate performanceError preventionError correction/detection using linear codesChannel encodingBit rate
The embodiment of the invention provides a channel coding and decoding method and device, wherein the channel coding method comprises the steps that: a coder obtains an information bit index set; the coder generates a second bit vector according to a to-be-coded first information bit and the information bit index set; and the coder performs Polar code coding on the second bit vector to generate a coded first codeword. According to the technical scheme provided by the invention, the coder firstly obtains the information bit index set, generates the second bit vector according to the to-be-coded first information bit and the information bit index set, and performs Polar code coding on the second bit vector to generate the coded first codeword, thus the channel coding method can realize that a Polar code is converted into a system code at a lower level of complexity, and can reduce the bit error rate so as to improve the performance of the Polar code.
Owner:HUAWEI TECH CO LTD
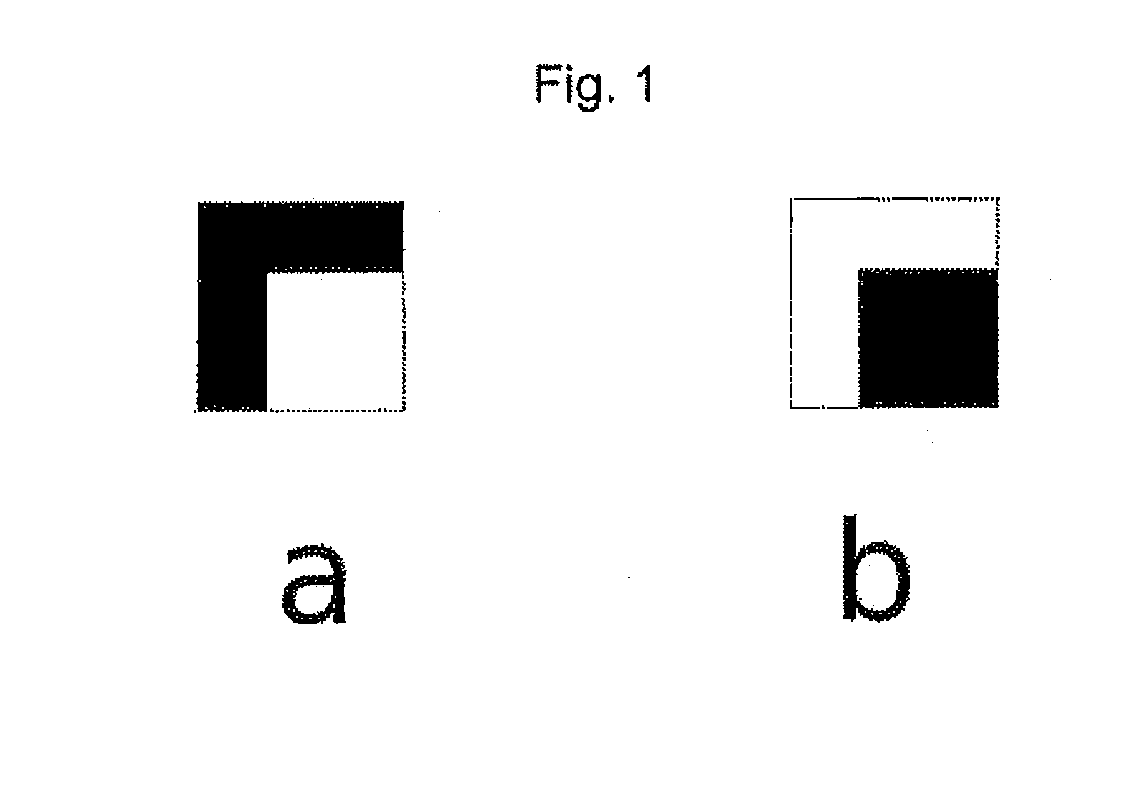
Two-dimensional symbol code and method for reading the symbol code
InactiveUS20120145779A1Shorter clock timeLine area be quicklyCharacter and pattern recognitionRecord carriers used with machinesProgramming languageGraphics
The specification describes a two-dimensional symbol code for representing binary data, which symbol code is constructed from a plurality of graphical symbols arranged next to one another, wherein the symbol code is formed from precisely two different symbols having the same surface area which differ in their areal brightness distribution and each code a value from a binary data word. The symbols have a complementary brightness distribution. In a method for reading this two-dimensional system code, the system code has a filter applied to it which matches the brightness distribution of one of the two complementary symbols, wherein in the event of a match one symbol is recognized and in the event of no match the other symbol is recognized.
Owner:CONTINENTAL TEVES AG & CO OHG
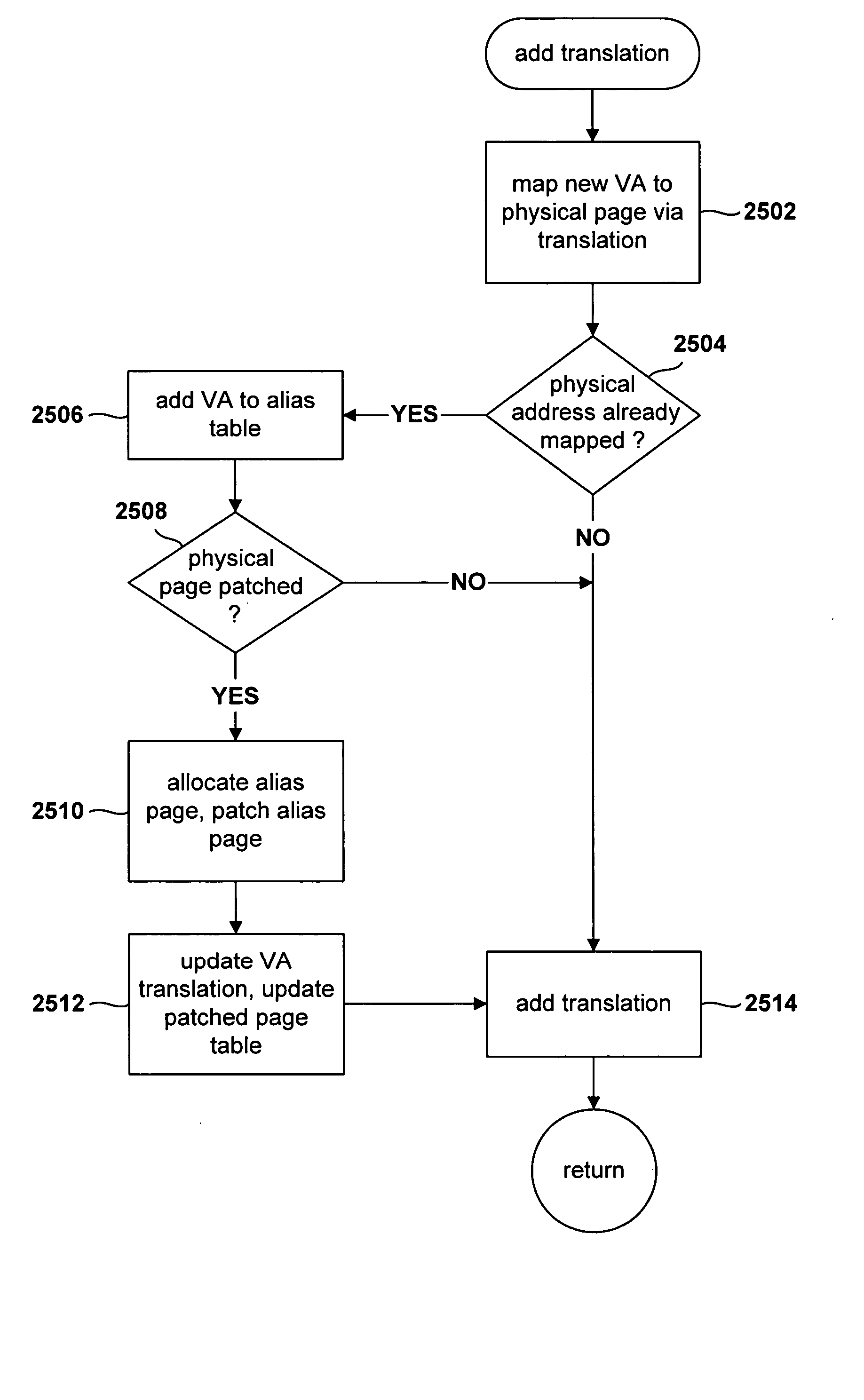
Method for patching virtually aliased pages by a virtual-machine monitor
InactiveUS20060026385A1Memory adressing/allocation/relocationMultiprogramming arrangementsComputer hardwareVirtual memory
Various embodiments of the present invention are directed to methods by which a virtual-machine monitor can introduce branch instructions, in order to emulate privileged and other instructions on behalf of a guest operating system, into guest-operating-system code residing on virtually aliased virtual-memory pages. In a described embodiment of the present invention, the virtual-machine monitor physically aliases each virtual alias for a particular physical memory page by allocating a physical page for the virtual alias, copying the original contents of the physical memory page to the allocated physical page, or physical alias page, and subsequently patching each physical alias page appropriate to the physical address of the physical alias page.
Owner:HEWLETT PACKARD DEV CO LP
Method for constructing checking matrix of LDPC code and coding and decoding apparatus utilizing the method
InactiveUS20110239077A1Improve performanceLess occupiedError preventionCode conversionAlgorithmEngineering
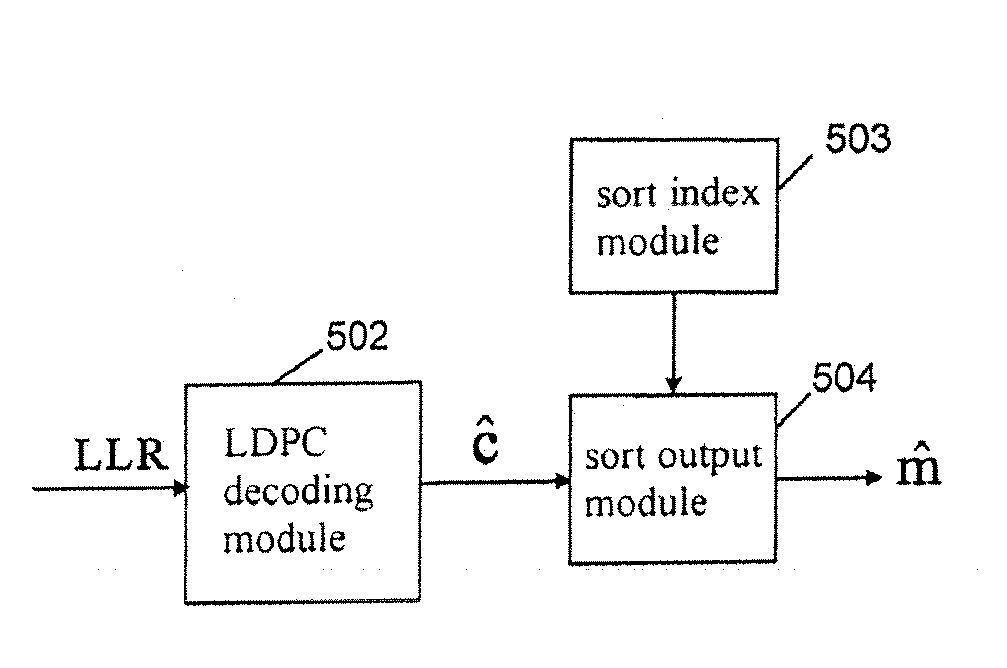
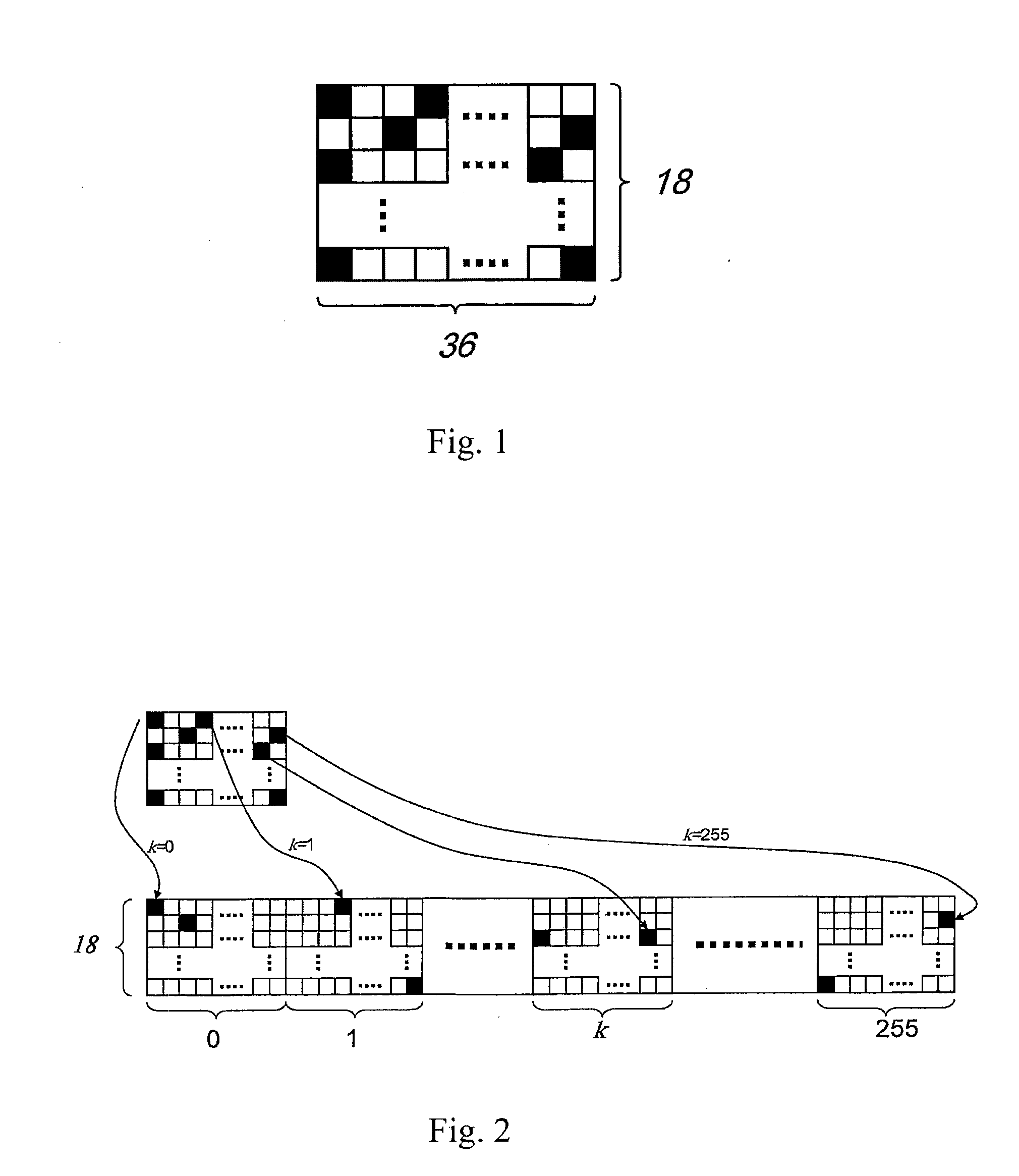
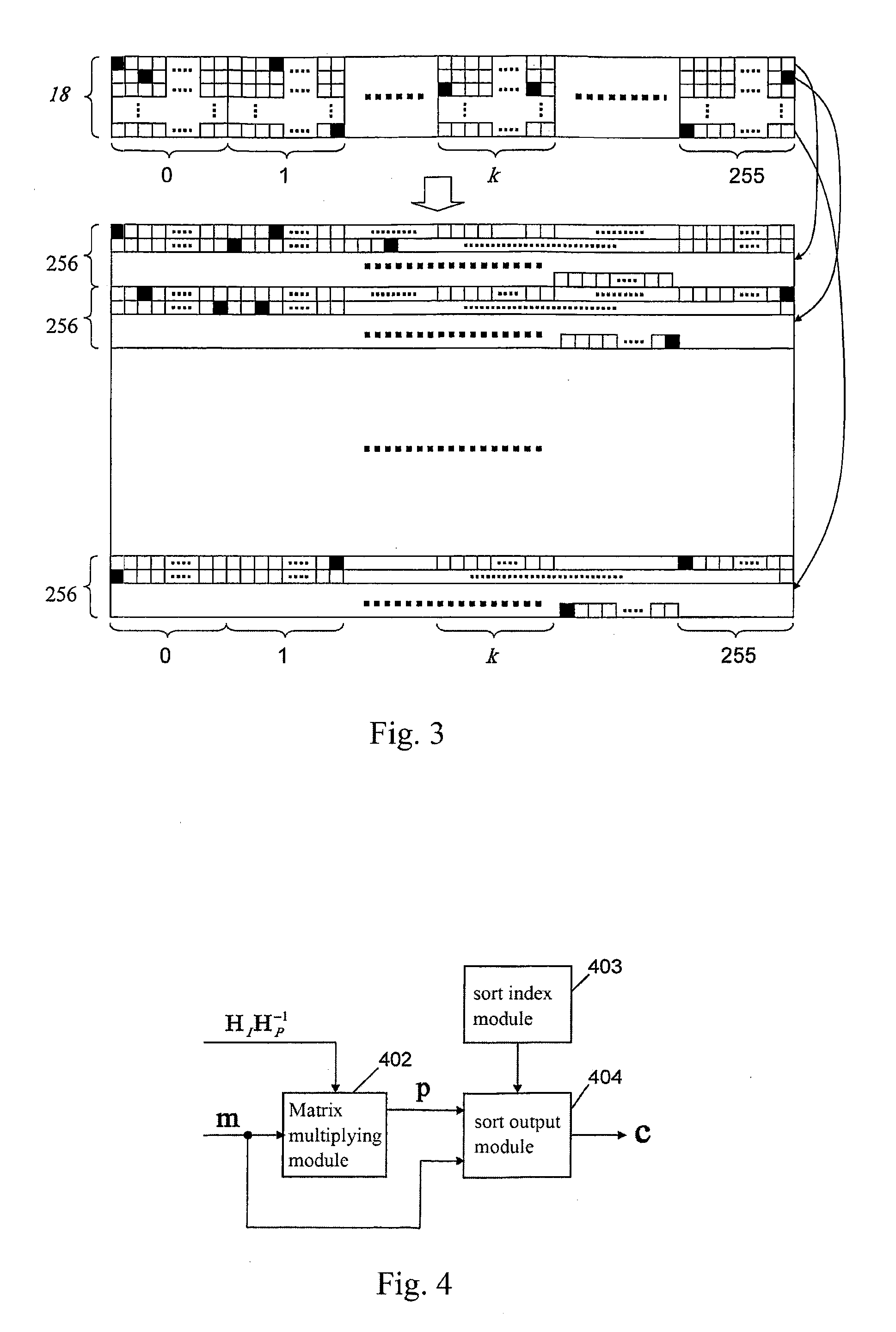
The present invention relates to a method for constructing LPDC code check matrix and encoding and decoding devices using the same. The encoding device encodes the inputted binary information and outputs the encoded system code sequence of position transformation. The encoding device comprises: a matrix multiplication module outputting a check sequence p which is obtained through the binary information sequence m multiplied with a matrix; a sorting index module having N memory units storing index values of a sorting table IDX in turn; and a sorting output module for sorting the m and p and outputting a code word c based on the index value stored in the sorting index table. The present invention constructs the LDPC code check matrix using an algebraic structure, obtaining the LDPC code with stable performance. In addition, the encoding and decoding devices of the present invention occupy less memory, which is preferable for optimization of the devices.
Owner:TIMI TECH
Implementing a dual partition flash with suspend/resume capabilities
A method of performing multiple operations on a flash memory device is described. This is made possible through the implementation of multiple partitions within the flash memory. The partitions are used to store data, application code, and system code. Low level functions within the system code process the data and handle preemption functions within the flash memory.
Owner:INTEL CORP
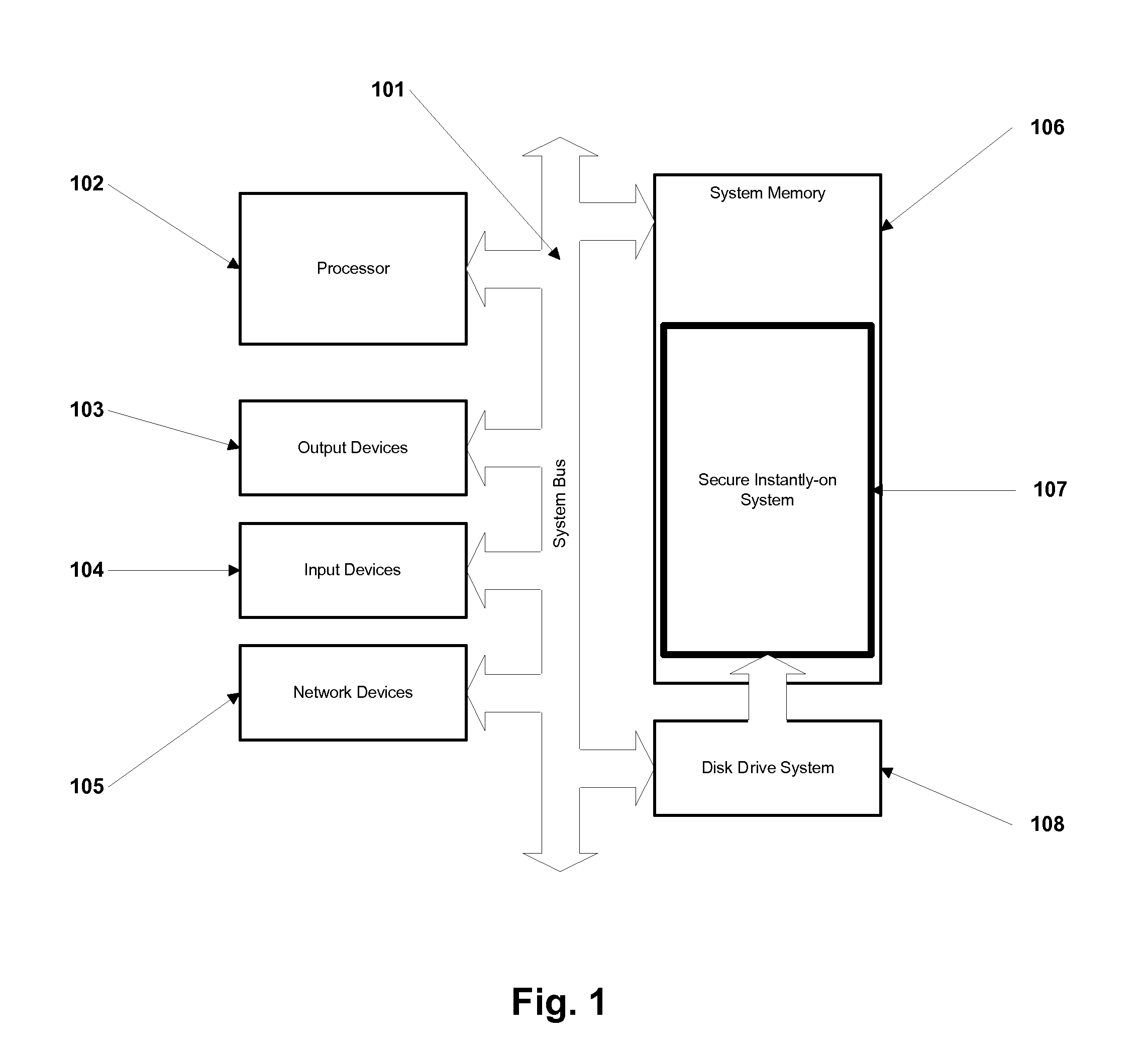
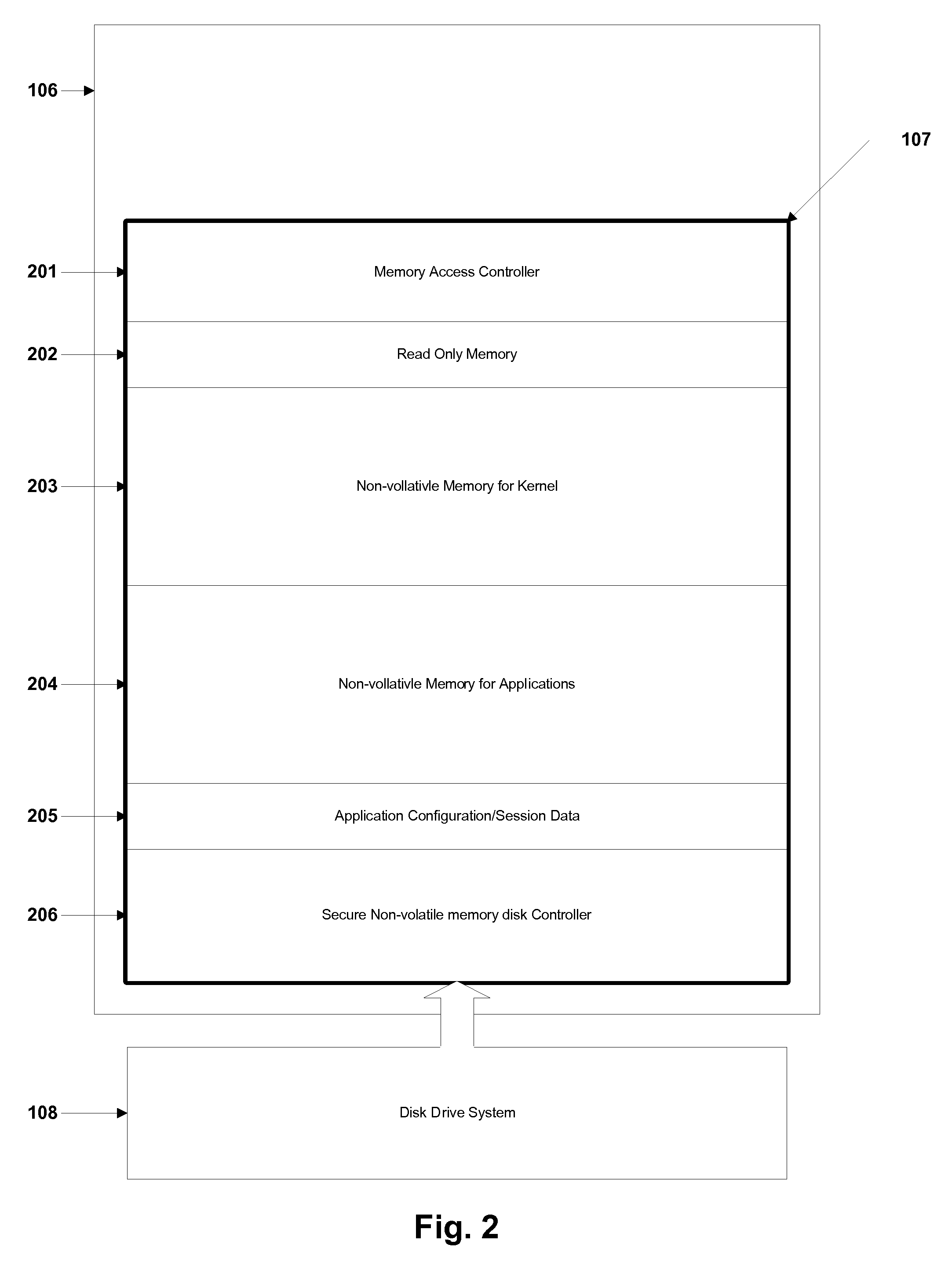
Method and Apparatus for Secure Instantly-On Computer System
ActiveUS20100058041A1Memory architecture accessing/allocationMultiple keys/algorithms usageOperational systemComputerized system
A method and apparatus for an instantly-on computer system is presented. A computer that incorporates fast non-volatile primary memory for storing the operating system, resulting in an instant-on or instant-booting of the computer. Large parts of the operating system code and application code are stored in non-volatile write-protectable areas that cannot be modified by malicious sources, resulting in a secure computer. It solves the problem from typical computers having to load the operating system and applications from a slow device such as the hard disk to the main memory. This loading is avoided by permanently housing the operating system in a non-volatile main memory. The system also solves the problem of corruption of operating system areas from malicious sources. The memory contains writeable and write-protected areas and a memory controller controls the access to the various regions of the memory.
Owner:CEREMORPHIC INC
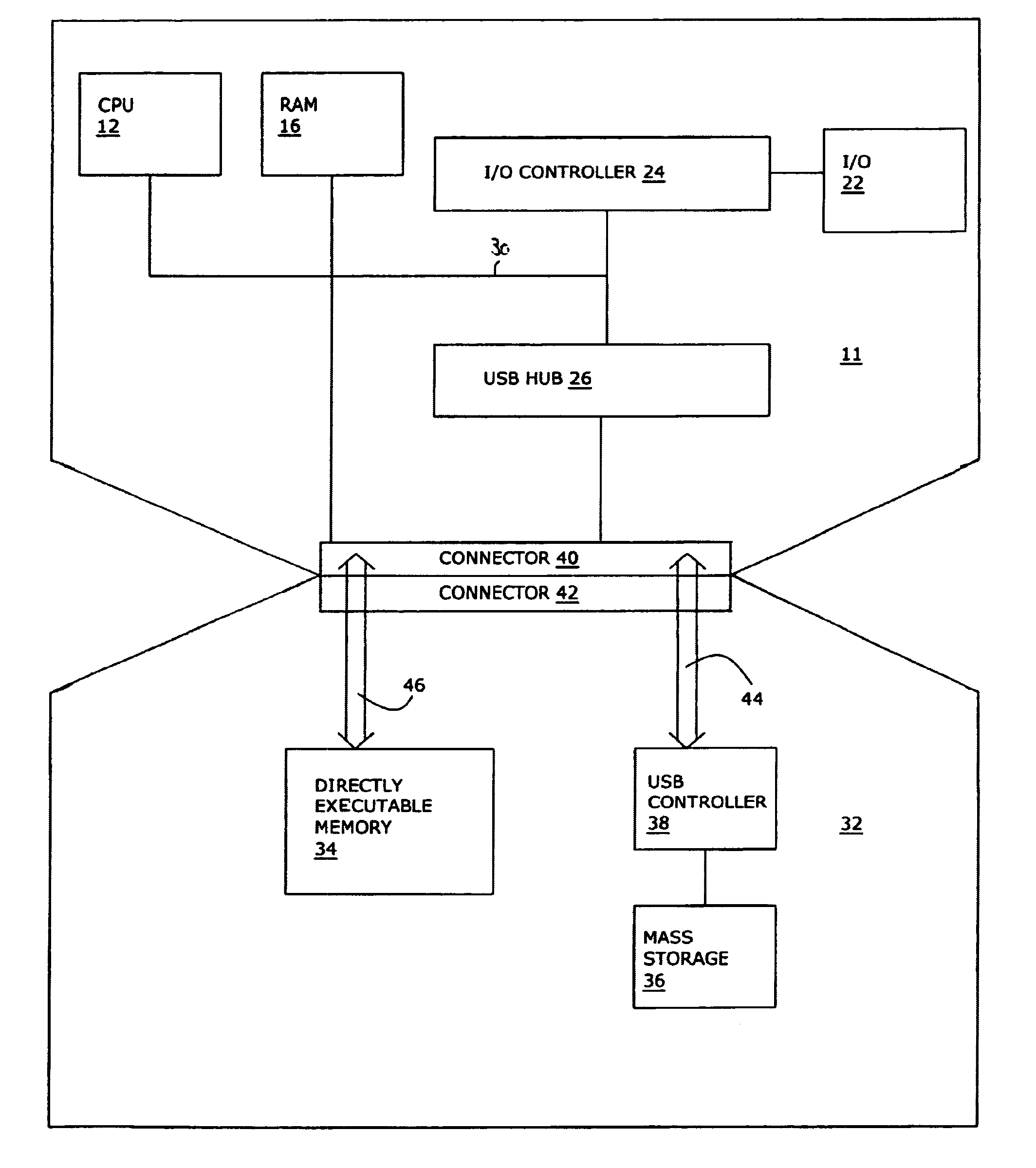
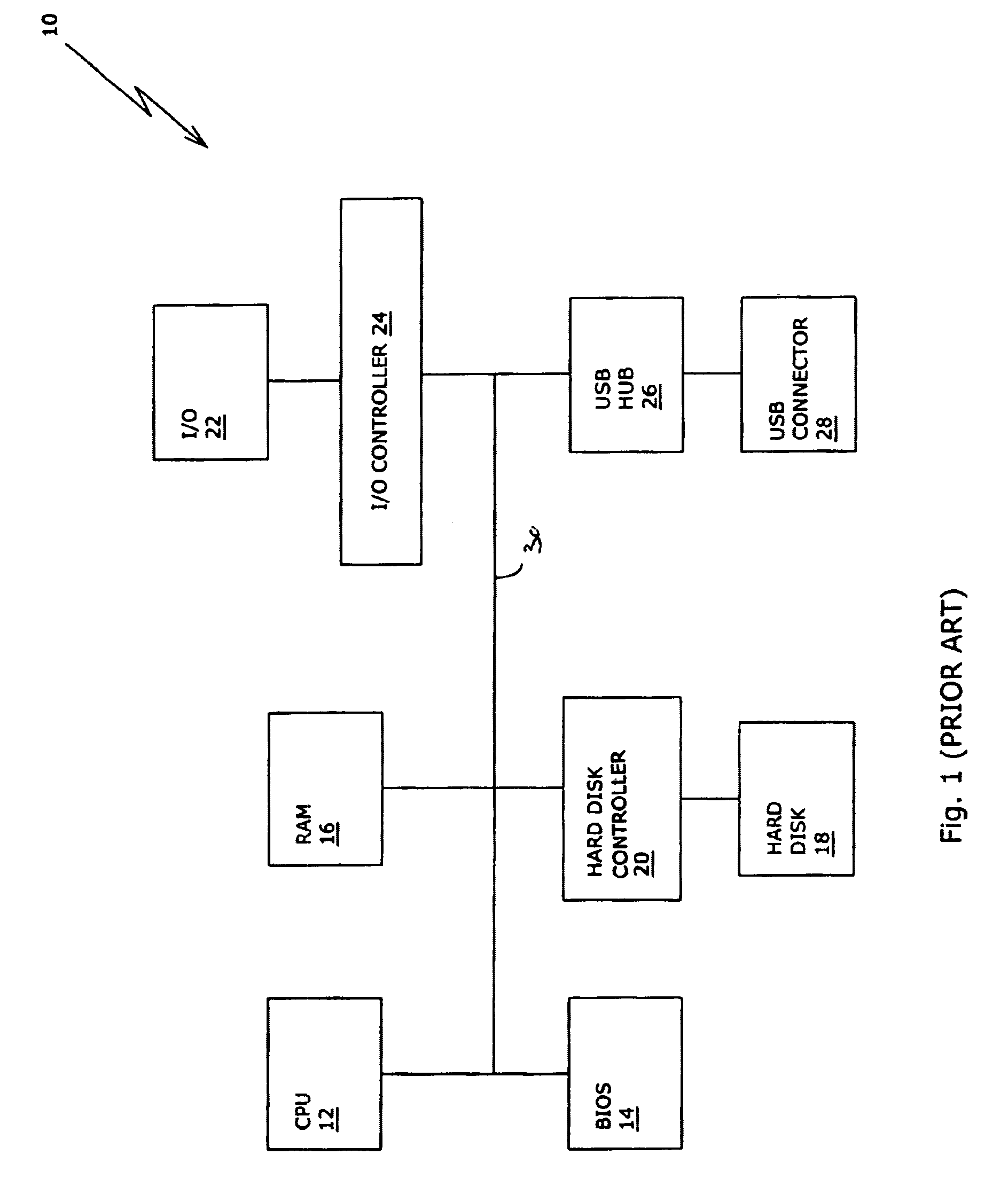
Mass storage device with boot code
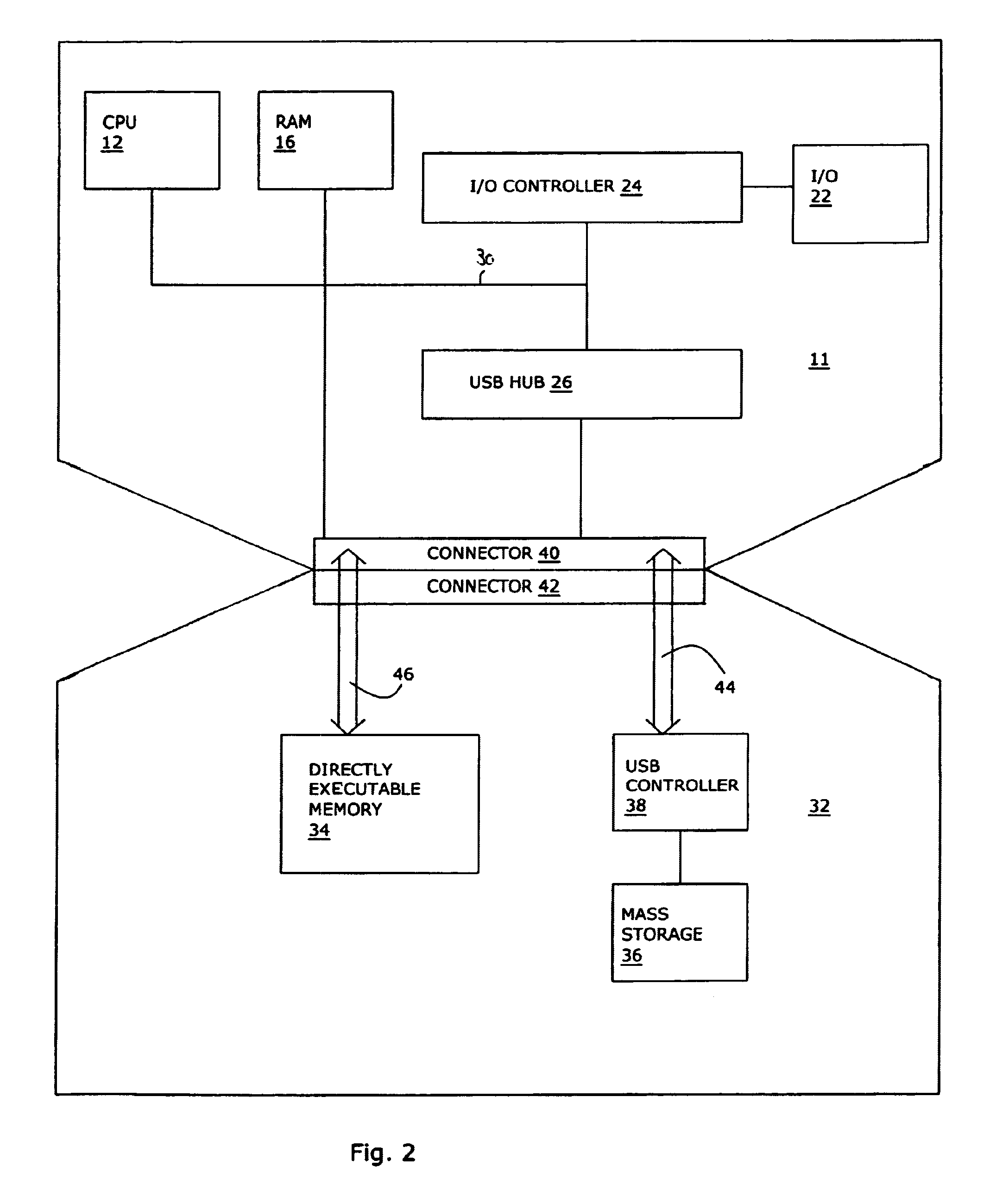
ActiveUS7073013B2Digital computer detailsComputer security arrangementsMass storageOperational system
A memory device includes a first, directly executable memory with boot code, a second memory with operating system code, and a common connector. When the device is connected to a computer that lacks a BIOS of its own, the computer boots from the first memory and downloads the operating system from the second memory. A user of a system that includes a plurality of the memory devices and a computer that lacks a BIOS selects an operating system by reversibly connecting the appropriate memory device to the computer. The memory device also serves as a security key for a computer that lacks a BIOS.
Owner:WESTERN DIGITAL ISRAEL LTD
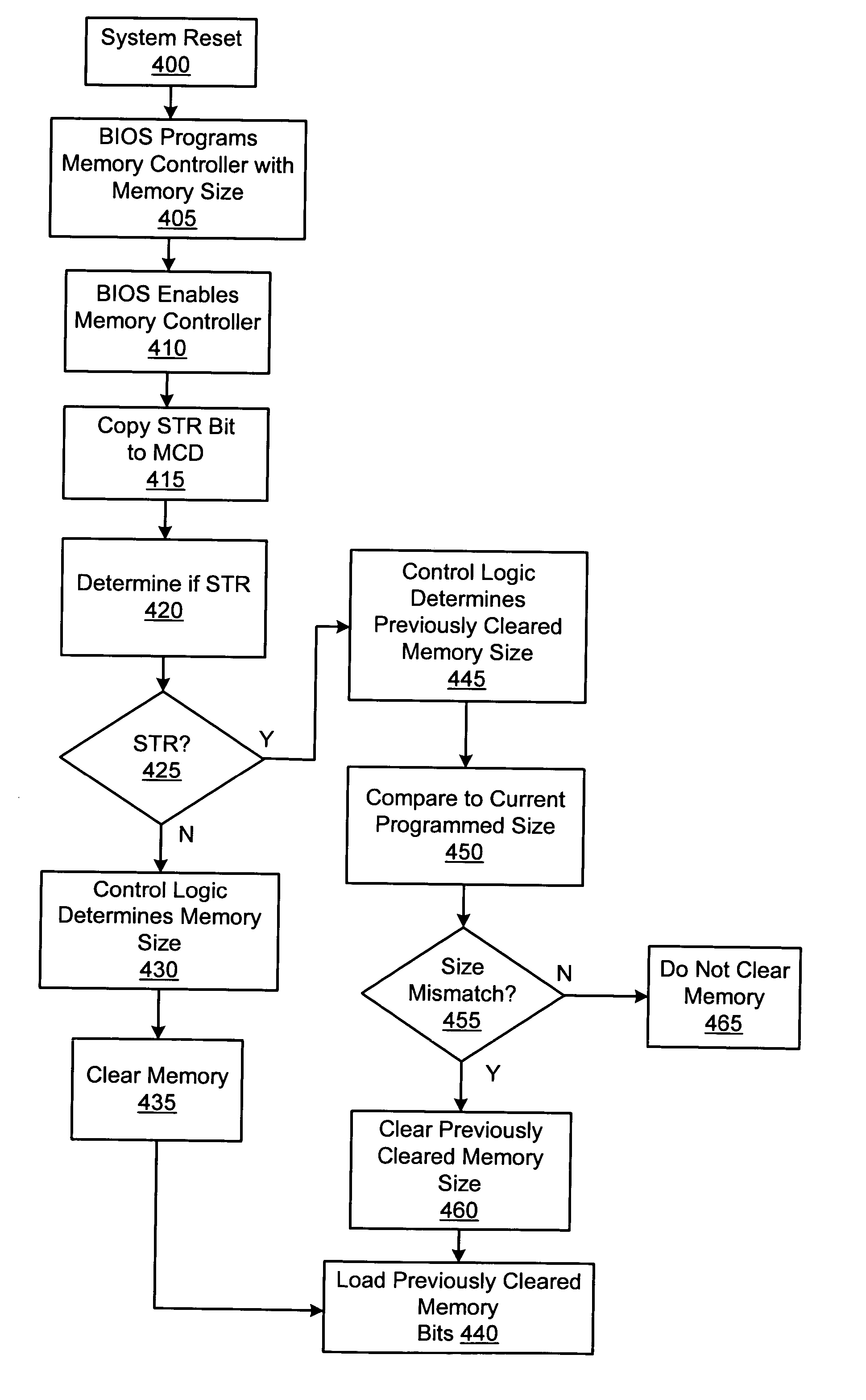
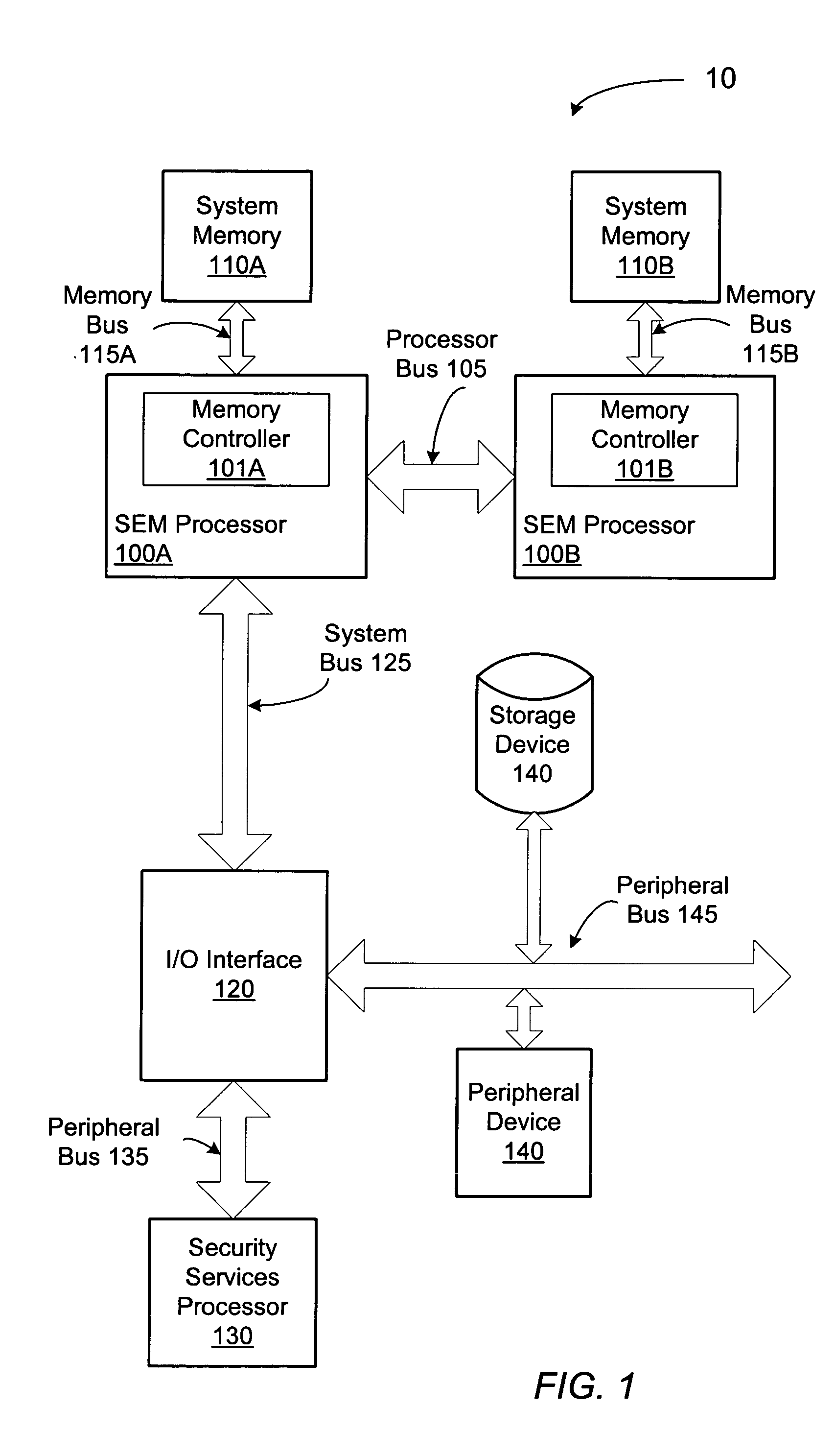
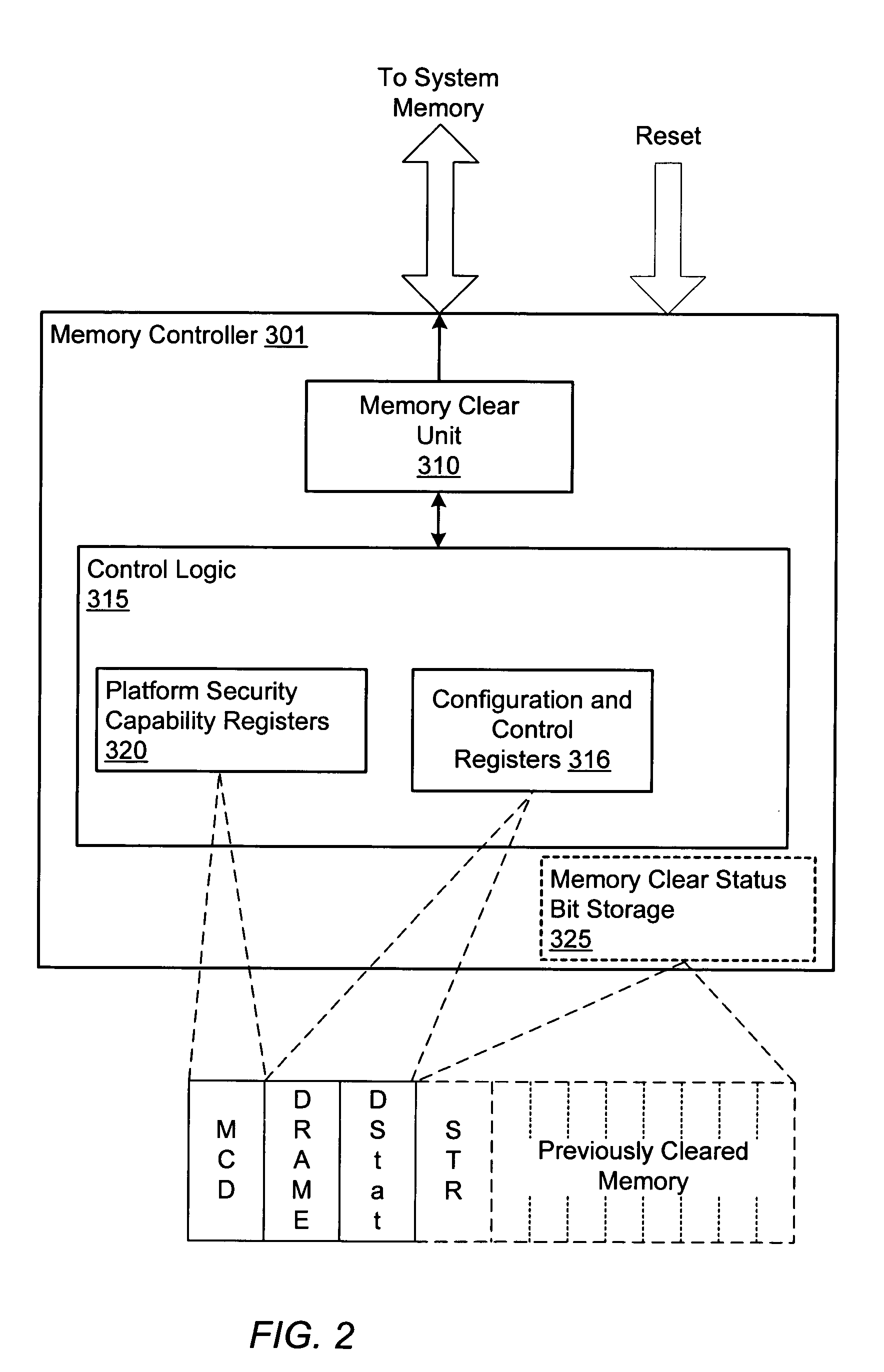
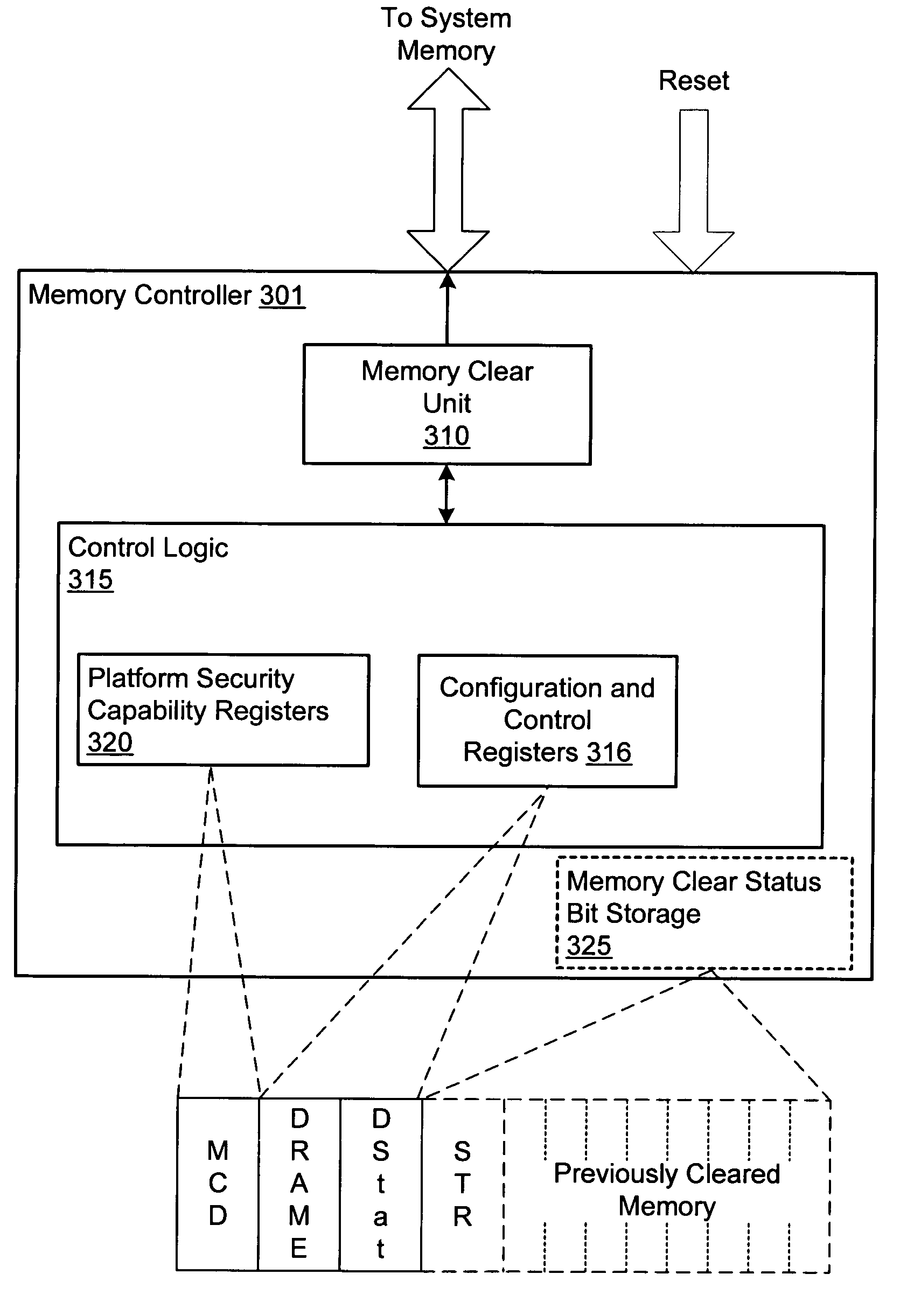
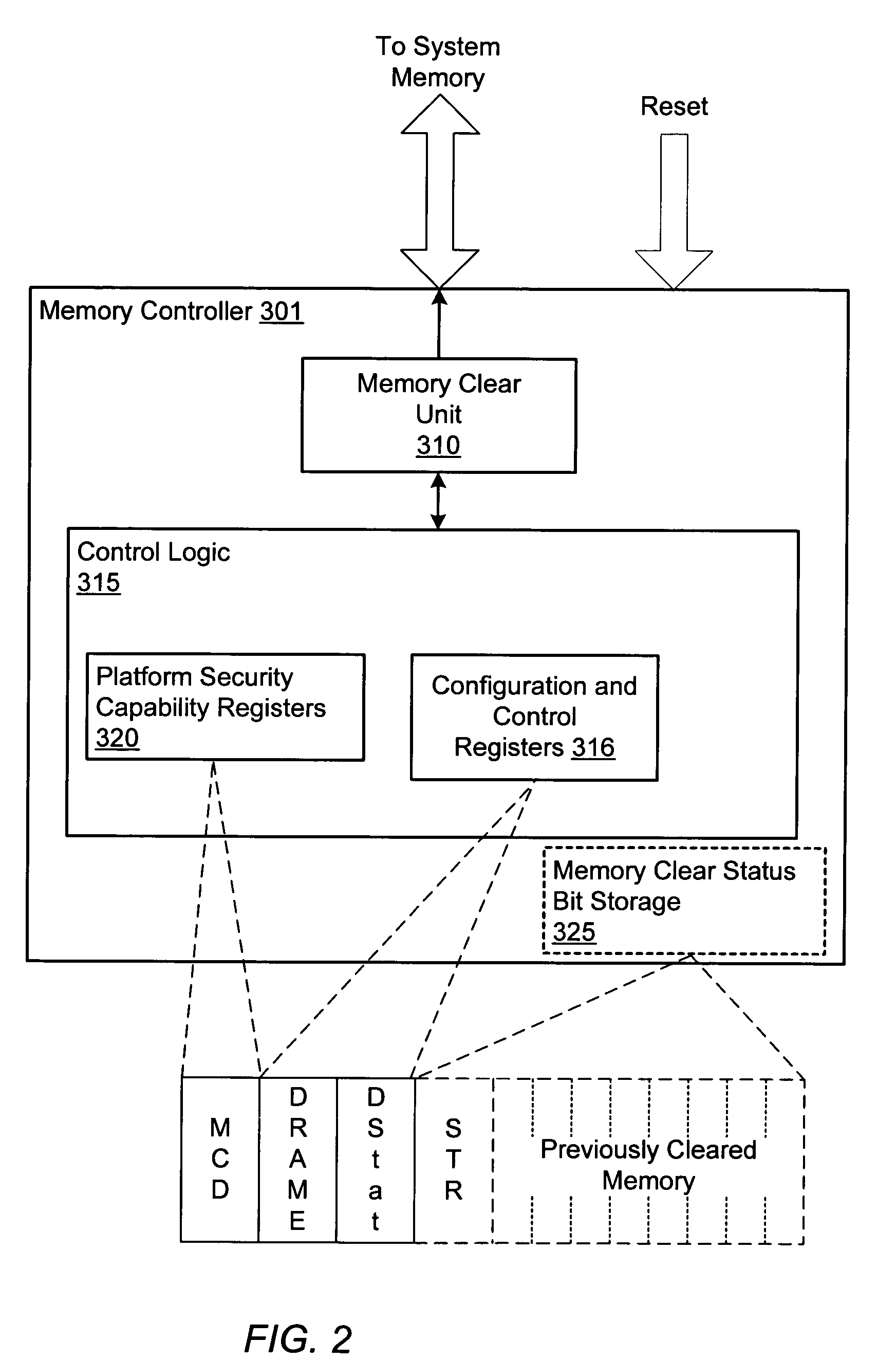
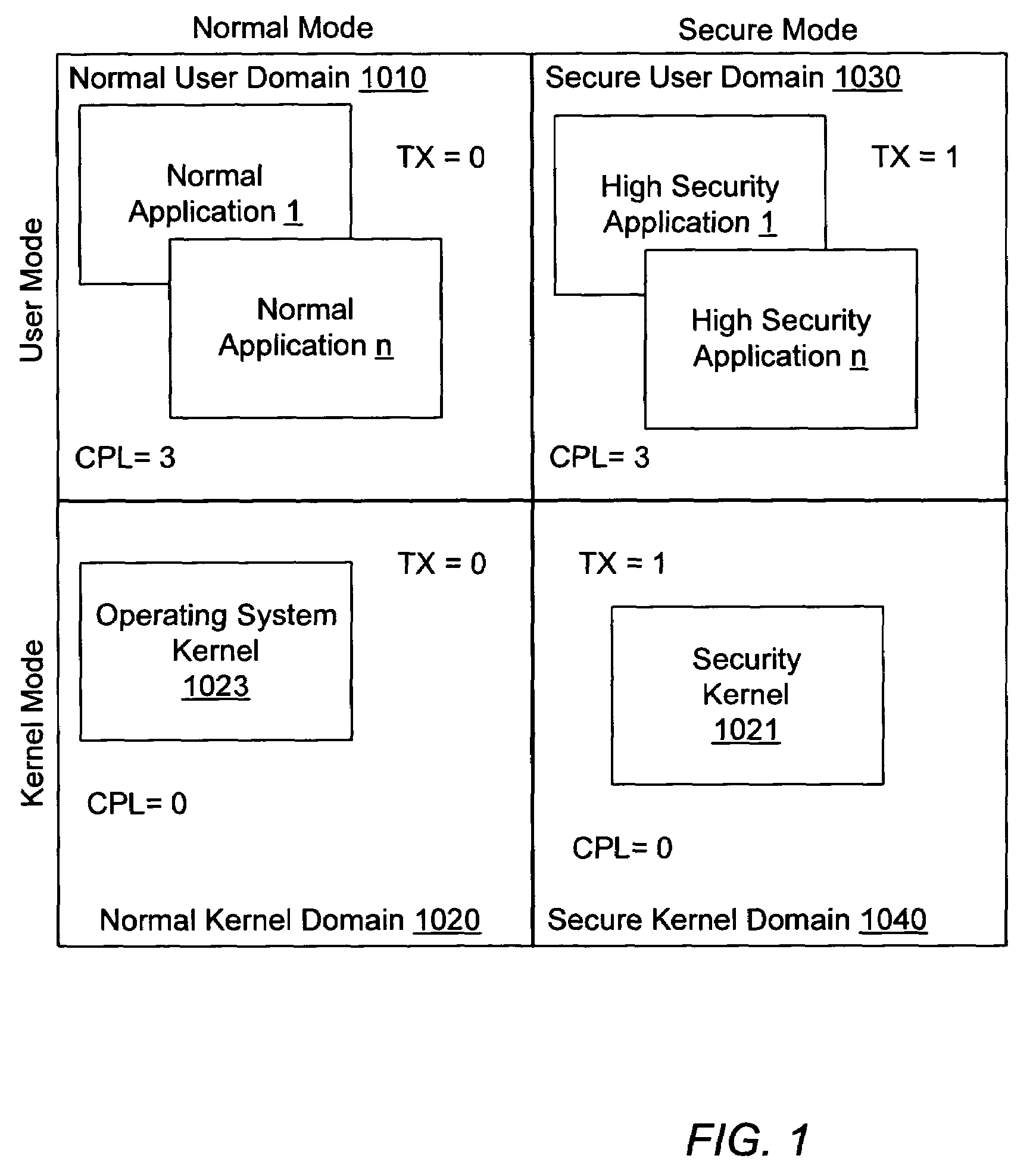
Computer system employing a trusted execution environment including a memory controller configured to clear memory
A computer system includes a processor which may initialize a secure execution mode by executing a security initialization instruction. Further, the processor may operate in the secure execution mode by executing a secure operating system code segment. The computer system also includes a system memory configured to store data in a plurality of locations. The computer system also includes a memory controller which may selectively clear the data from a programmed range of the memory locations of the system memory when enabled in response to a reset of the processor.
Owner:ADVANCED MICRO DEVICES INC
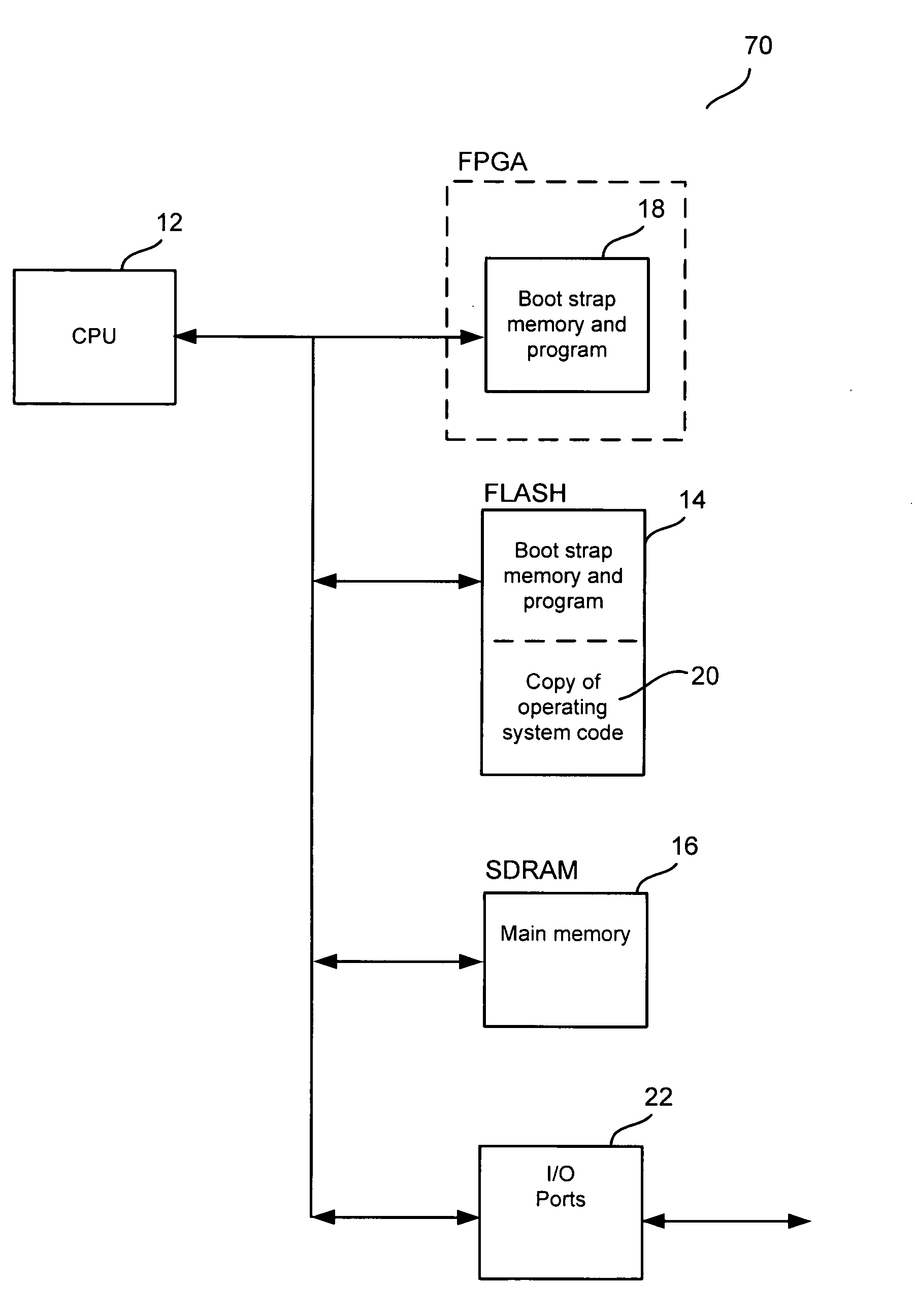
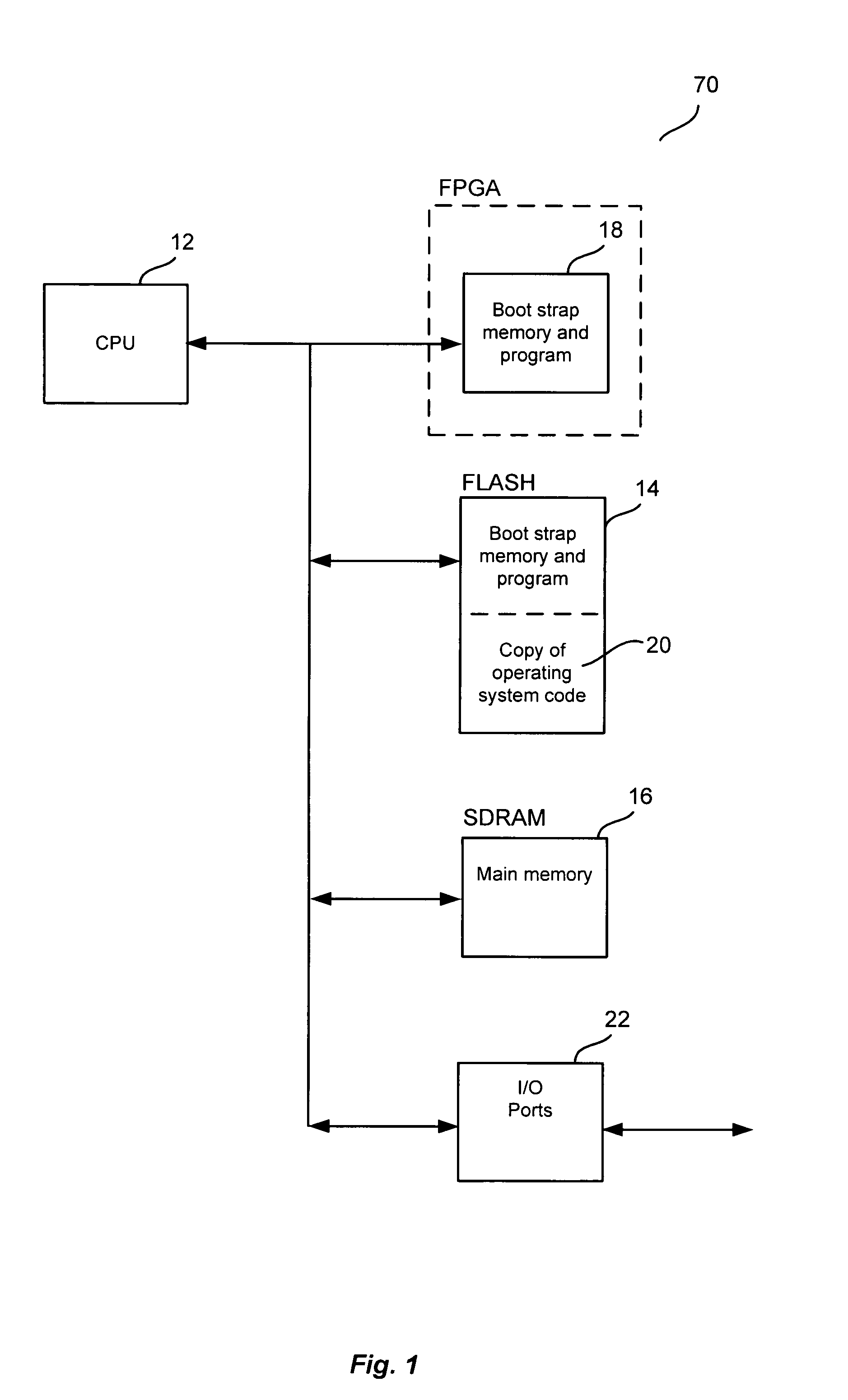
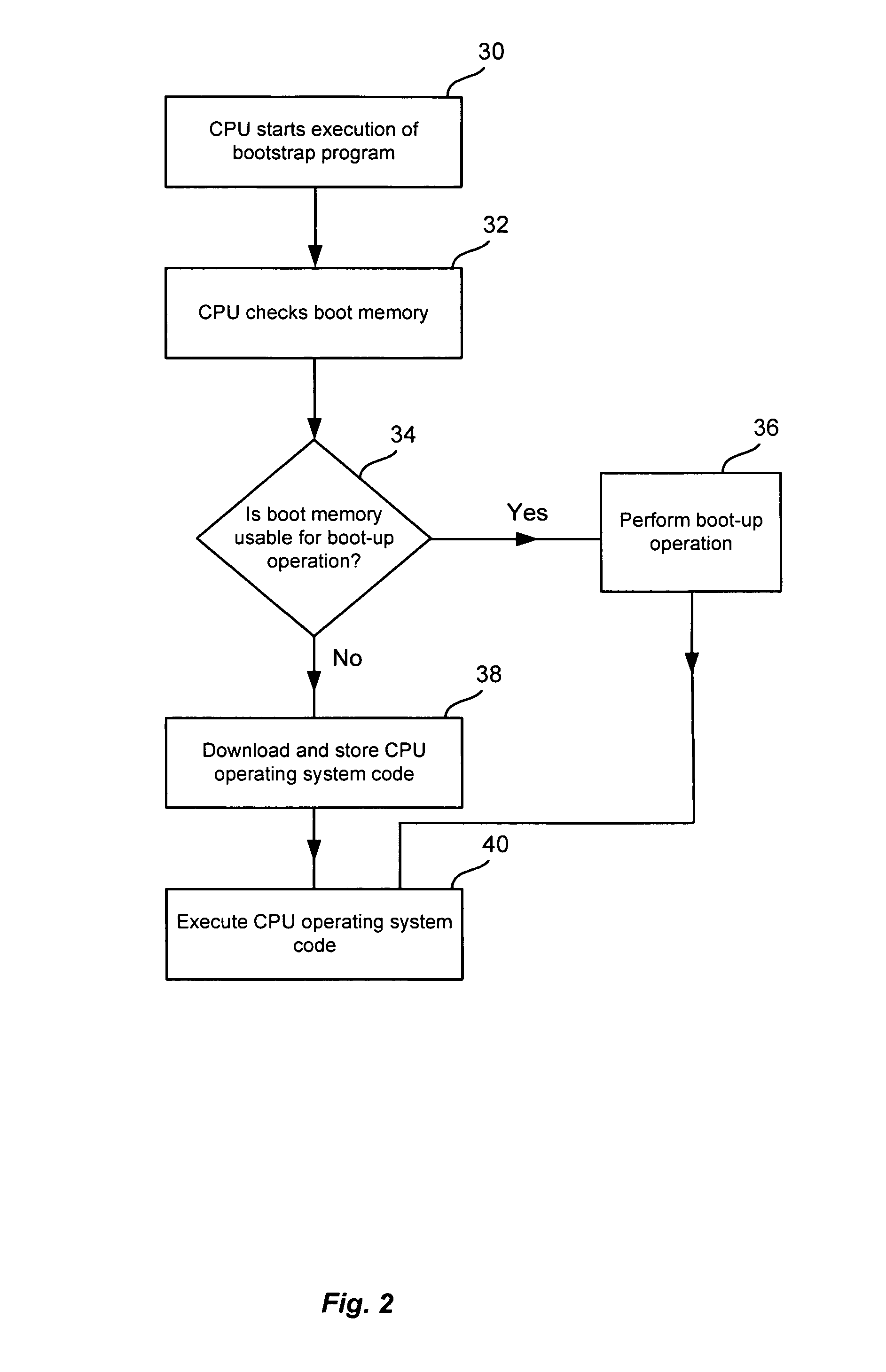
Method and system to provide first boot to a CPU system
ActiveUS7017038B1Minimizes problemError detection/correctionDigital computer detailsOperational systemSystematic code
A boot-up operation system is provided. In one exemplary embodiment, the system includes a CPU, a bootstrap memory, a boot memory, a main memory, an I / O port and CPU operating system code. When the system is turned on, the CPU executes the bootstrap program which directs it to determine whether the boot memory contains the necessary code to perform the boot-up operation. If the boot memory contents are usable for boot-up operation, the CPU starts executing a boot program that is stored in the boot memory. If the boot memory contents are not usable for boot-up operation, the bootstrap program directs the CPU to download a copy of the CPU operating system code from outside the system using the I / O port. After the download, the CPU stores a copy of the downloaded operating system code and the boot program into the boot memory for future use.
Owner:RIBBON COMM OPERATING CO INC
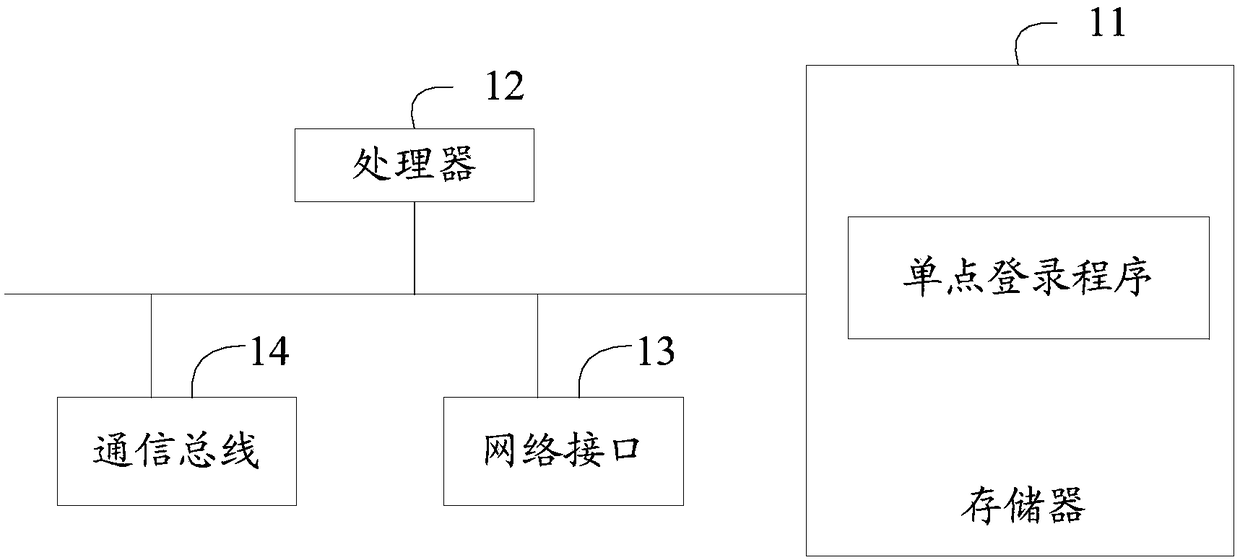
Single sign-on server, single sign-on method and computer readable storage medium
The invention discloses a single sign-on server. The single sign-on server comprises a memory and a processor; a single sign-on program which can be run in the processor is stored in the memory. Whenthe program is carried out by the processor, steps below are realized: obtaining a sign-on request sent from a client to the server based on a reorientation information sent by a service system; obtaining account information from the sign-on request, obtaining a system identifier of the service system and an associated white list from the reorientation information and judging whether account information exists in the white list; if so, verifying the account information and a password in the sign-on request; if the verification passes, returning token information to the client for storage and storing the token information after the token information is associated with the account information of the client. The invention also provides a single sign-on method and a computer readable storage medium. According to the single sign-on server, the single sign-on method and the computer readable storage medium, a system code amount is reduced, the system reusability is improved, and centralizedmanagement of each service system authority in the single sign-on system is realized.
Owner:重庆金融资产交易所有限责任公司
Method and Apparatus for Secure Instantly-Available Applications in a Computer System
ActiveUS20100058046A1Memory architecture accessing/allocationMultiple keys/algorithms usageOperational systemComputerized system
A method and apparatus for instantly-available applications in a computer system is presented. A computer that incorporates fast non-volatile primary memory for storing the application software and / or operating system, resulting in an instant-on computer is presented. Large parts of the application code and / or operating system code are stored in non-volatile write-protectable areas of the memory that cannot be modified by malicious sources, resulting in a secure computer. It solves the problem of typical computers having to load the applications from a slow device such as the hard disk to the main memory. This loading is avoided by permanently housing the applications in a non-volatile main memory. The system also solves the problem of corruption of application software areas from malicious sources. The memory system contains writeable and write-protected areas and a memory controller that controls the access to the various regions of the memory.
Owner:CEREMORPHIC INC
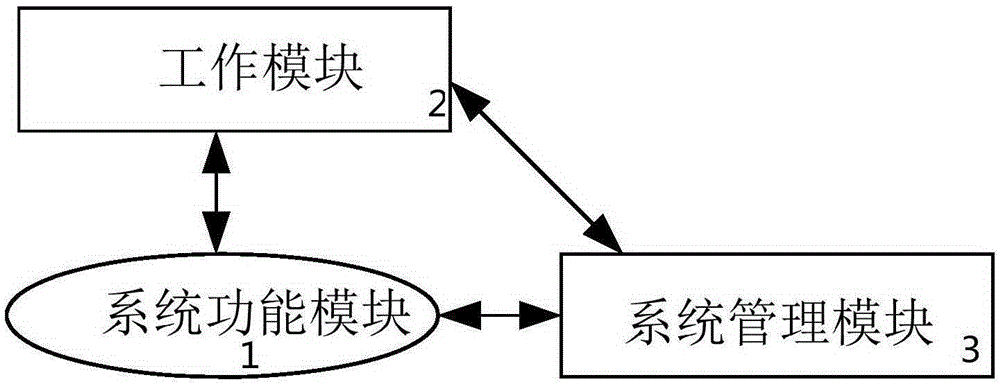
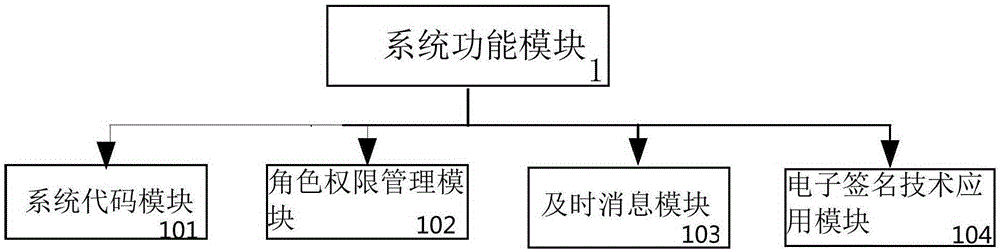
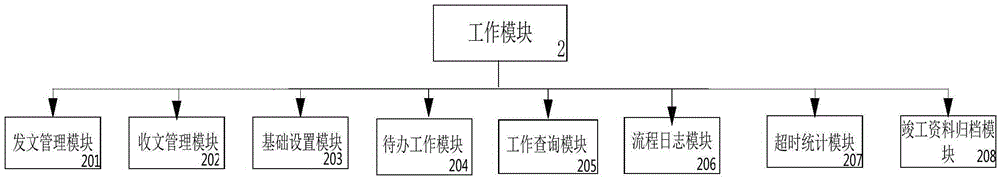
OA intelligent office system and management method thereof
InactiveCN105260858ARealize Signing OpinionsRealize functionResourcesSystems managementProject completion
The invention relates to an OA intelligent office system and a management method thereof. The system comprises a system function module responsible for the system code settlement, the role authorization management service and the message notification service, a working module responsible for the outgoing message management, the incoming massage management, the basic settlement, the to-be-done job settlement, the job inquiry, the process log, the overtime statistics and the project completion data filing, and a system management module responsible for the administrative office settlement, the information exchange settlement, the timed task management, the workflow settlement and the organization mechanism settlement. The working module acquires the usage authorization information, the login information and the message reminding of a user by means of the system function module. The system management module acquires the data of the system authorization management, the settlement data of the workflow, the settlement data of roles in the company of the above user and the settlement data of document templates by means of the system function module. The working module acquires the operating authorization of incoming massages and outgoing messages, the job inquiry authorization and the division basic data of project completion items by means of the system management module. According to the invention, the electronic signature technology, the project management service management and the OA office flow function are integrated.
Owner:苏州天地微易智能科技有限公司
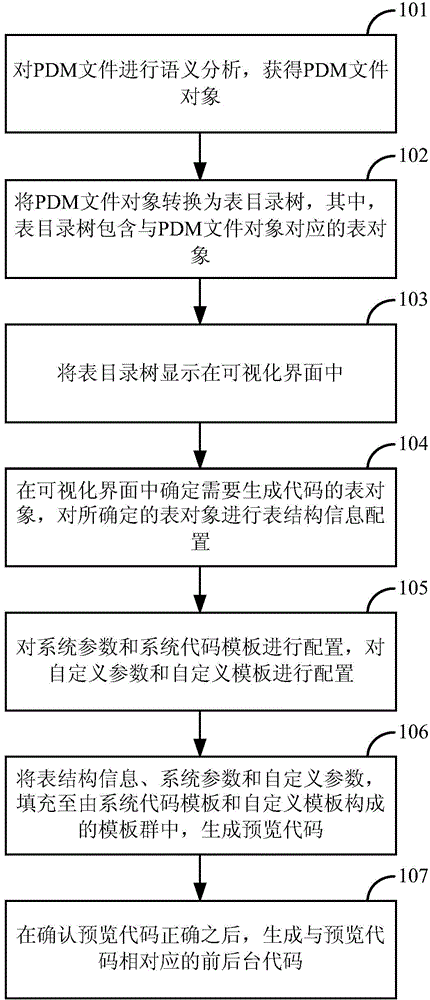
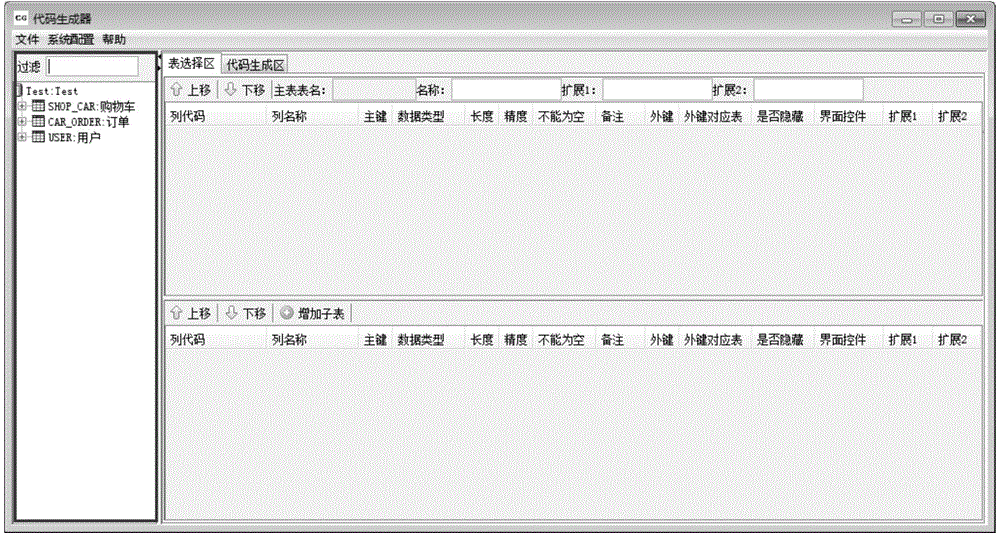
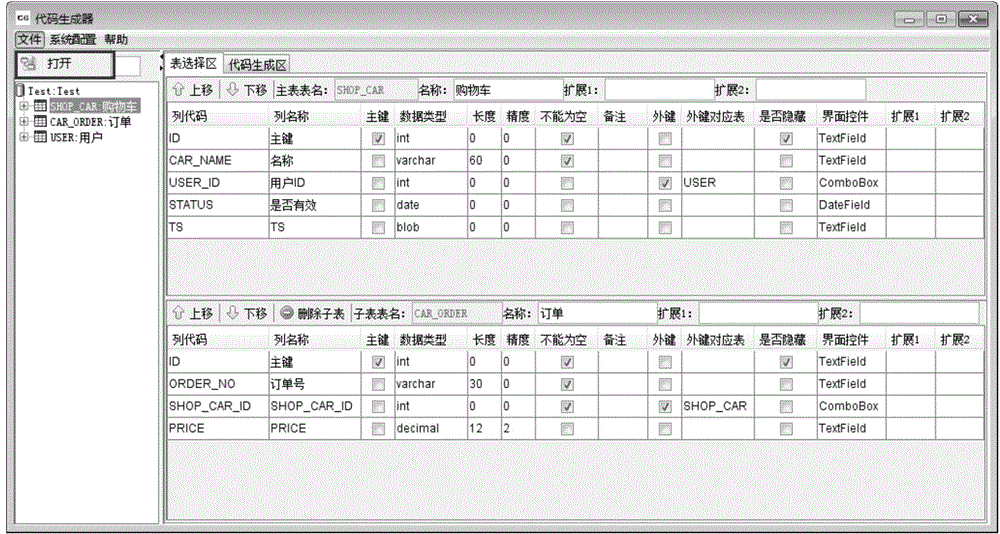
Code generation method and apparatus
InactiveCN106293664AAddressing the lack of versatilitySolve the problem that the generation process cannot be visualizedSpecific program execution arrangementsSystematic codeSystem parameters
The invention discloses a code generation method and apparatus. The method comprises the steps of performing semantic analysis on a physical data model (PDM) file to obtain a PDM file object; converting the PDM file object into a table directory tree, wherein the table directory tree comprises a table object corresponding to the PDM file object; displaying the table directory tree in a visual interface; determining a table object needed to be subjected to code generation in the visual interface, and performing table structure information configuration on the determined table object; configuring system parameters and system code templates, and configuring self-defined parameters and self-defined templates; filling a template group composed of the system code templates and the self-defined templates with the table structure information, the system parameters and the self-defined parameters to generate a preview code; and after the preview code is confirmed to be correct, generating foreground and background codes corresponding to the preview code. According to the code generation method and apparatus, the software program development efficiency can be improved, the development cost can be reduced, and the development cycle can be shortened.
Owner:BANK OF COMMUNICATIONS
Method and system for recognizing instructions and instruction blocks in computer code
InactiveUS20060026387A1Efficient and robustGeneral purpose stored program computerProgram controlOperational systemVirtual machine
Various embodiments of the present invention are directed to efficient and robust methods by which virtual-machine monitors can recognize individual instructions and blocks of instructions within guest-operating-system code. In a described embodiment of the present invention, the guest operating system recognizes the instructions by recognizing an overall form, or pattern, for the instruction as well as the values of various fields within the instruction that may change with re-compilations and / or re-linking of guest operating system code.
Owner:HEWLETT PACKARD DEV CO LP
Computer system employing a trusted execution environment including a memory controller configured to clear memory
ActiveUS7210009B2Memory loss protectionMemory adressing/allocation/relocationOperational systemComputerized system
A computer system includes a processor which may initialize a secure execution mode by executing a security initialization instruction. Further, the processor may operate in the secure execution mode by executing a secure operating system code segment. The computer system also includes a system memory configured to store data in a plurality of locations. The computer system also includes a memory controller which may selectively clear the data from a programmed range of the memory locations of the system memory when enabled in response to a reset of the processor.
Owner:ADVANCED MICRO DEVICES INC
Multi-dimensional symbologies and related methods
ActiveUS20080035730A1Increasing data bitImprove abilitiesTransmission systemsSensing detailsMulti dimensionalData mining
Multi-dimensional symbology codes that use plural characteristic features encoded in a data cell and related methods. Such methods include methods of encoding, methods of creating and methods of reading multi-dimensional symbology codes that use such plural characteristic features. The features, for example, include colors, grey scale levels, cell shape, patterns within a cell or any grouping discernable by an area array camera or similar device.
Owner:VERITEC INCORPORATED
Achieving autonomic behavior in an operating system via a hot-swapping mechanism
Systems, especially operating systems, are becoming more complex to the point where maintaining them by humans is becoming nearly impossible. Many corporations have recognized this trend and have begun investing in autonomic technology. Autonomic technology allows a piece of software to monitor, diagnose, and repair itself. This can be used for improved performance, reliability, maintainability, security, etc. Disclosed herein is a mechanism to allow operating systems to hot swap a piece of operating system code, while continuing to offer to the user the service which that code is providing. This can be used, for examples, to increase the performance of an application or to fix a detected security hole live without bringing the machine down. Some autonomic ability will be mandatory in next generation operating system for without it they will collapse under their own complexity. The invention offers a key component of being able to achieve autonomic computing.
Owner:IBM CORP
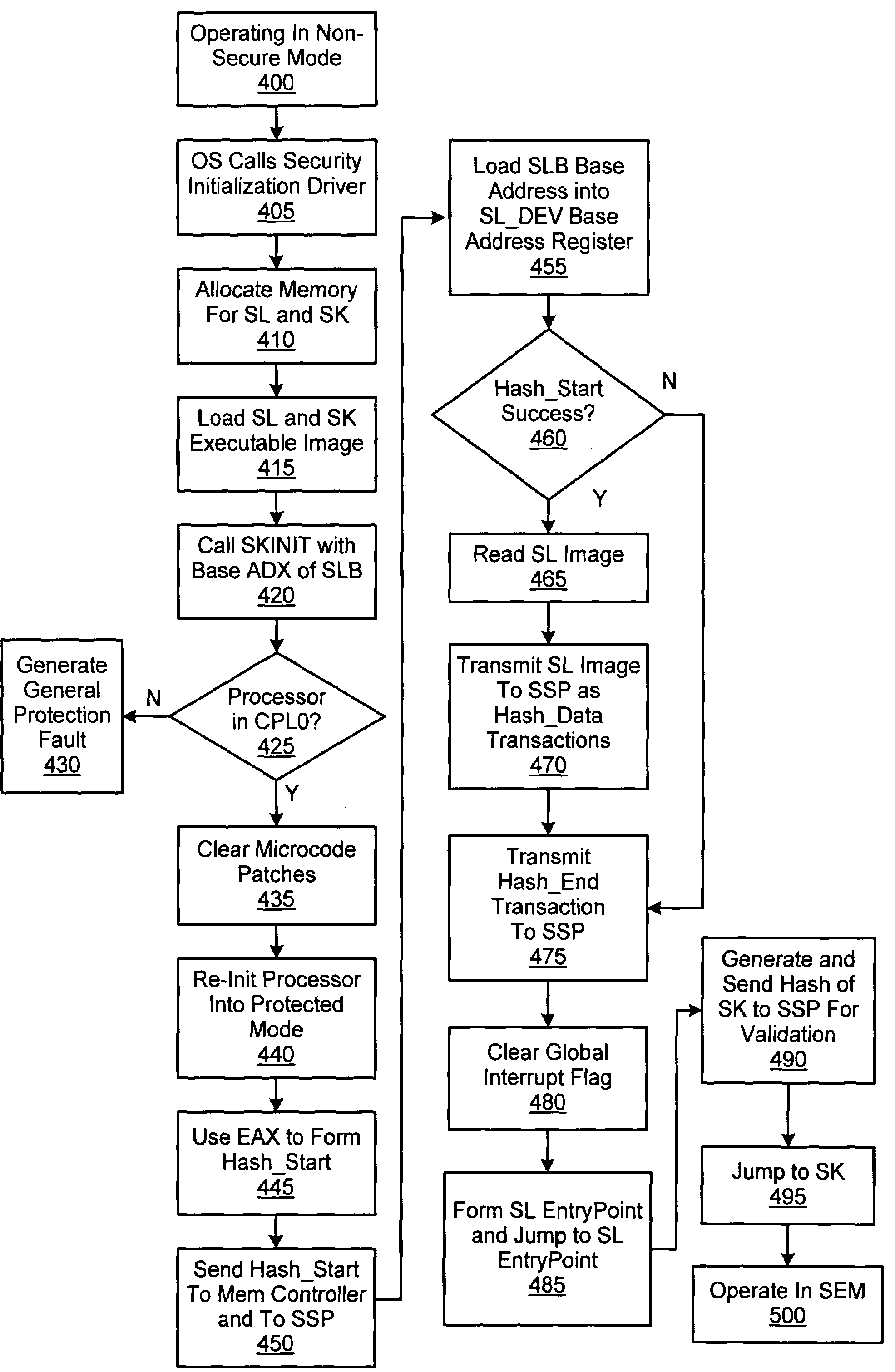
Initialization of a computer system including a secure execution mode-capable processor
InactiveUS7603551B2Avoid accessUnauthorized memory use protectionHardware monitoringOperational systemComputerized system
The initialization of a computer system including a secure execution mode-capable processor includes storing a secure operating system code segment loader to a plurality of locations corresponding to a particular range of addresses within a system memory. The method also includes executing a security initialization instruction. Executing the security initialization instruction may cause several operations to be performed including transmitting a start transaction including a base address of the particular range of addresses. In addition, executing the security instruction may also cause another operation to be performed including retrieving the secure operating system code segment loader from the system memory and transmitting the secure operating system code segment loader for validation as a plurality of data transactions.
Owner:ADVANCED SILICON TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com