Hostile attack preventing method and network system
A malicious attack and network system technology, applied in the field of network communication, can solve problems such as aggravating the business processing capacity of business servers and the failure of websites to operate normally, and achieve the effect of reducing load pressure and preventing malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to have a clearer understanding of the technical features, purposes and effects of the present invention, the specific implementation manners of the present invention will now be described in detail with reference to the accompanying drawings.
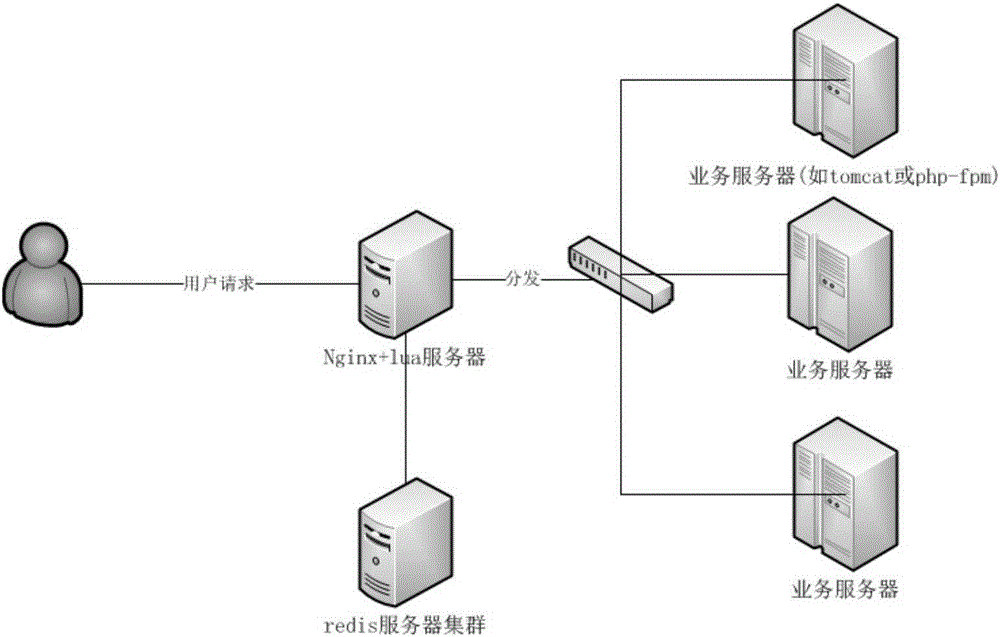
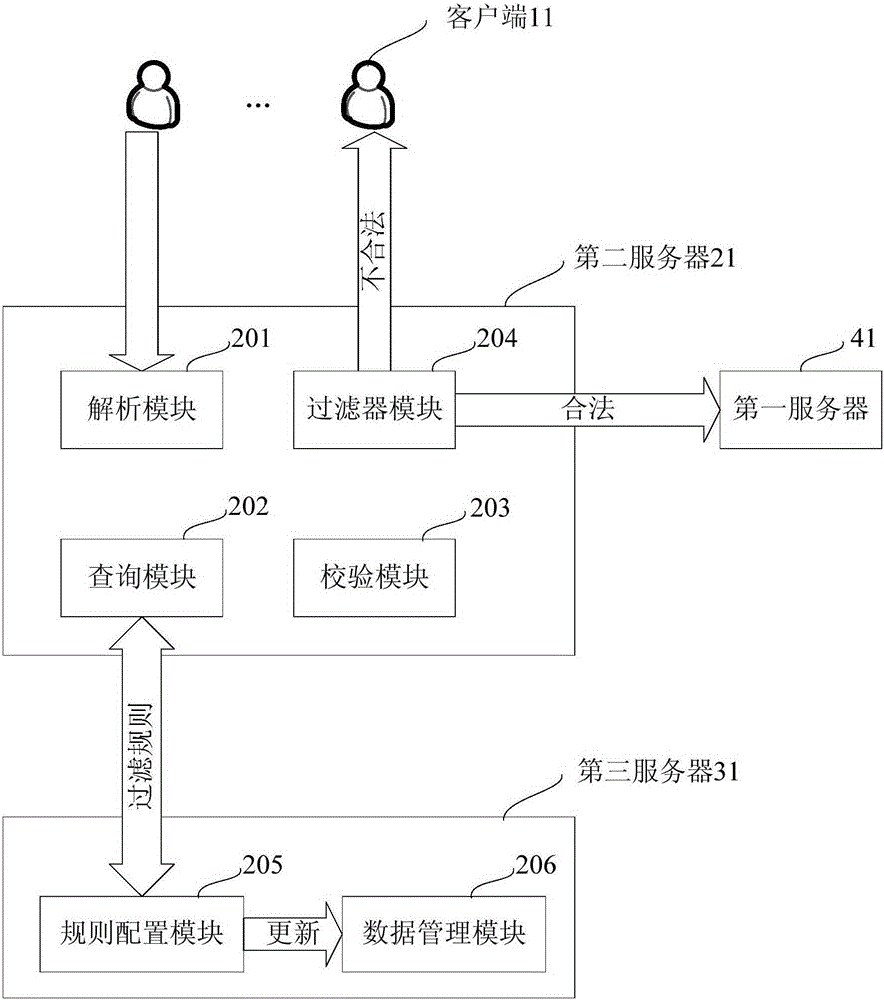
[0042] In a communication network, an address is an identifier assigned to each device on the network. As applied to the Internet, a device's address is often referred to as its "Internet Protocol address" (IP address), which is a numerical representation of a device's virtual location on the Internet. If the device hosts a website, the host device's IP address is used to locate the host device and provide access to content from the website. For example, the web domain name google.com actually represents a numerical IP address, which may be, for example, 73.14.213.99. When a web client types a domain name into its web browser, the downstream DNS system matches or routes the entered domain name to an IP address, which i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com