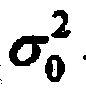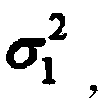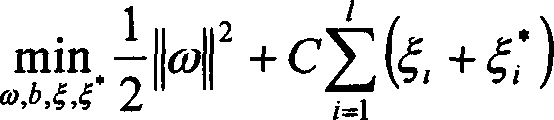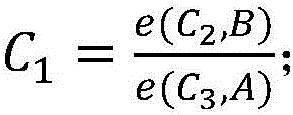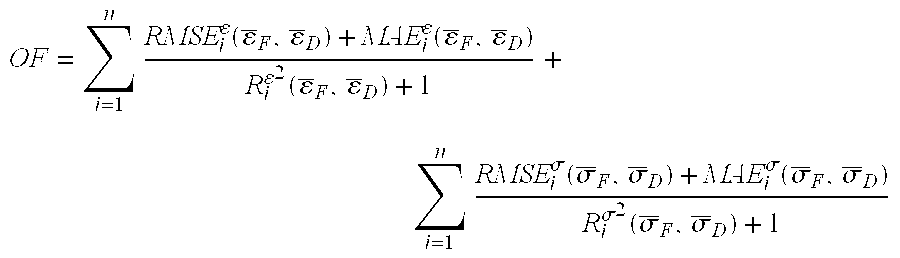Patents
Literature
229 results about "Random parameters" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The random parameters model is defined in terms of the density of the observed random variable and the structural parameters in the model: where b(i) and c(i) are parameter vectors and x(i,t) is a set of covariates observed at observation t.
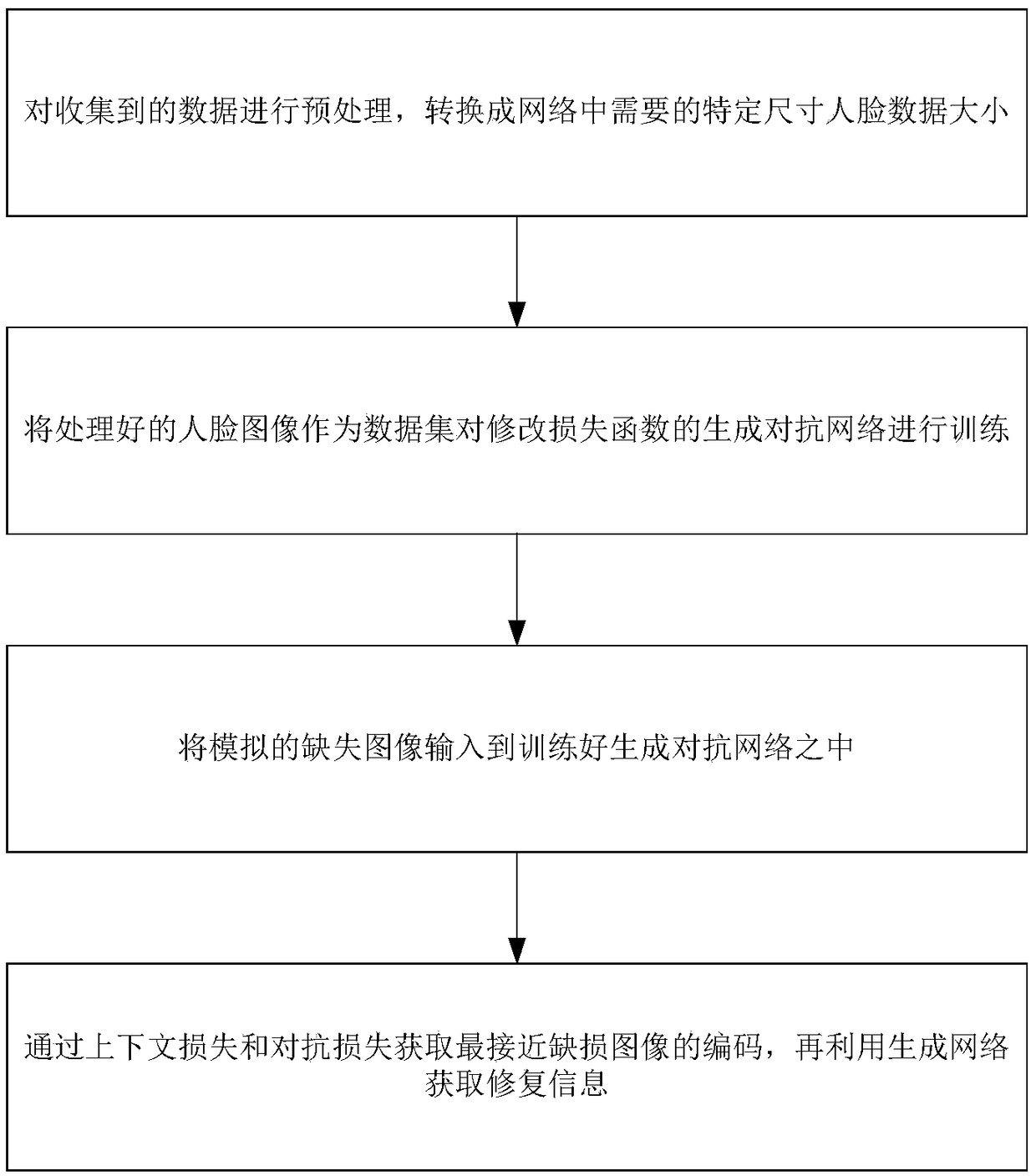
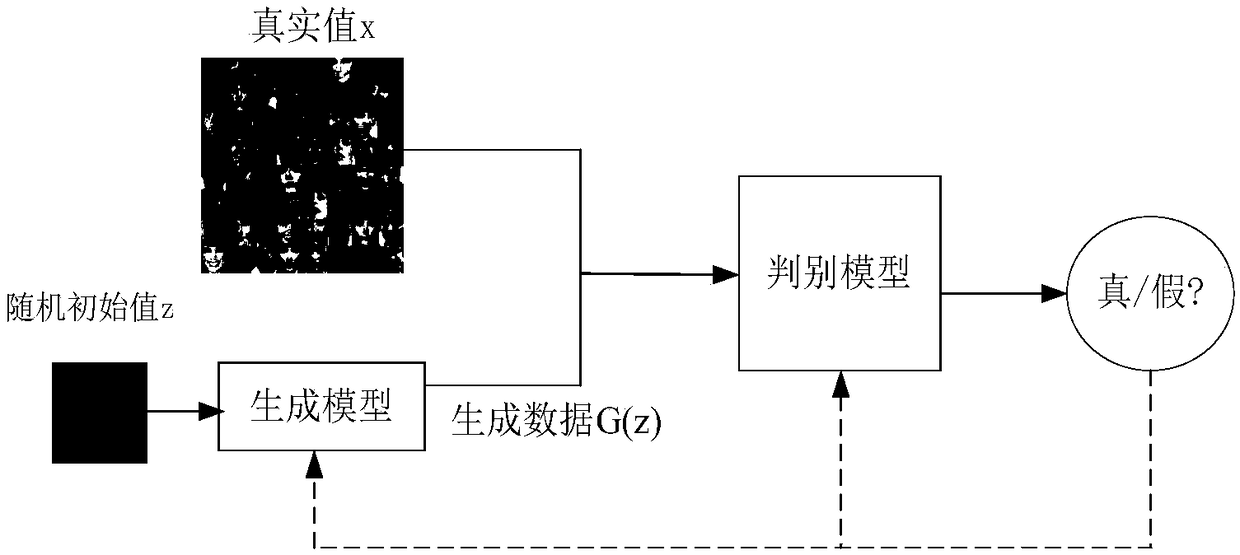
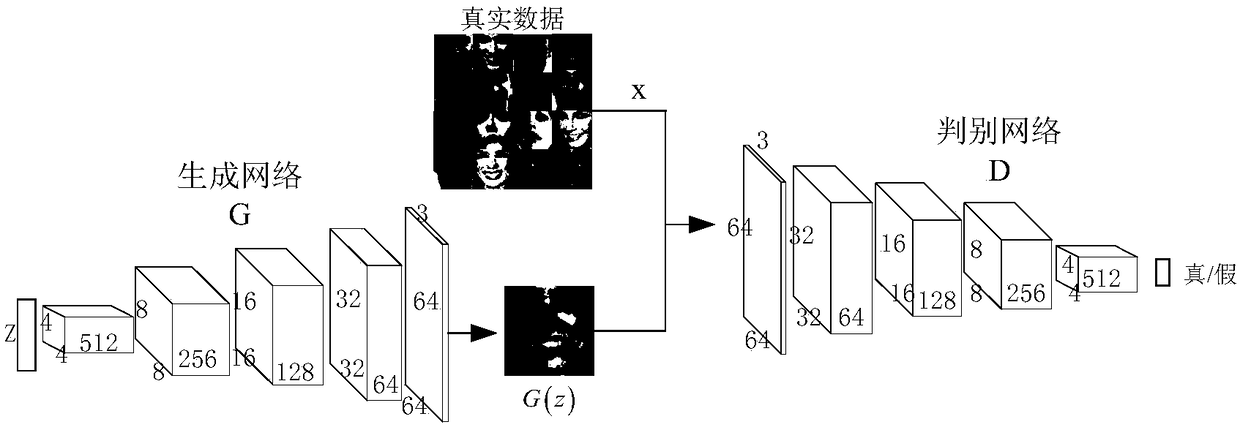
A face image restoration method based on a generation antagonism network
ActiveCN109377448AImprove stabilityGuarantee authenticityImage enhancementImage analysisData setTraining phase
The invention discloses a face image restoration method based on a generation antagonism network. The method comprises the following steps: a face data set is preprocessed, and a face image with a specific size is obtained by face recognition of the collected image; In the training phase, the collected face images are used as dataset to train the generating network and discriminant network, aimingat obtaining more realistic images through the generating network. In order to solve the problems of instability of training and mode collapse in the network, the least square loss is used as the loss function of discriminant network. In the repairing phase, a special mask is automatically added to the original image to simulate the real missing area, and the masked face image is input into the optimized depth convolution to generate an antagonistic network. The relevant random parameters are obtained through context loss and two antagonistic losses, and the repairing information is obtainedthrough the generated network. The invention can not only solve the face image repairing with serious defective information, but also generate a face repairing image which is more consistent with visual cognition.
Owner:BEIJING UNIV OF TECH
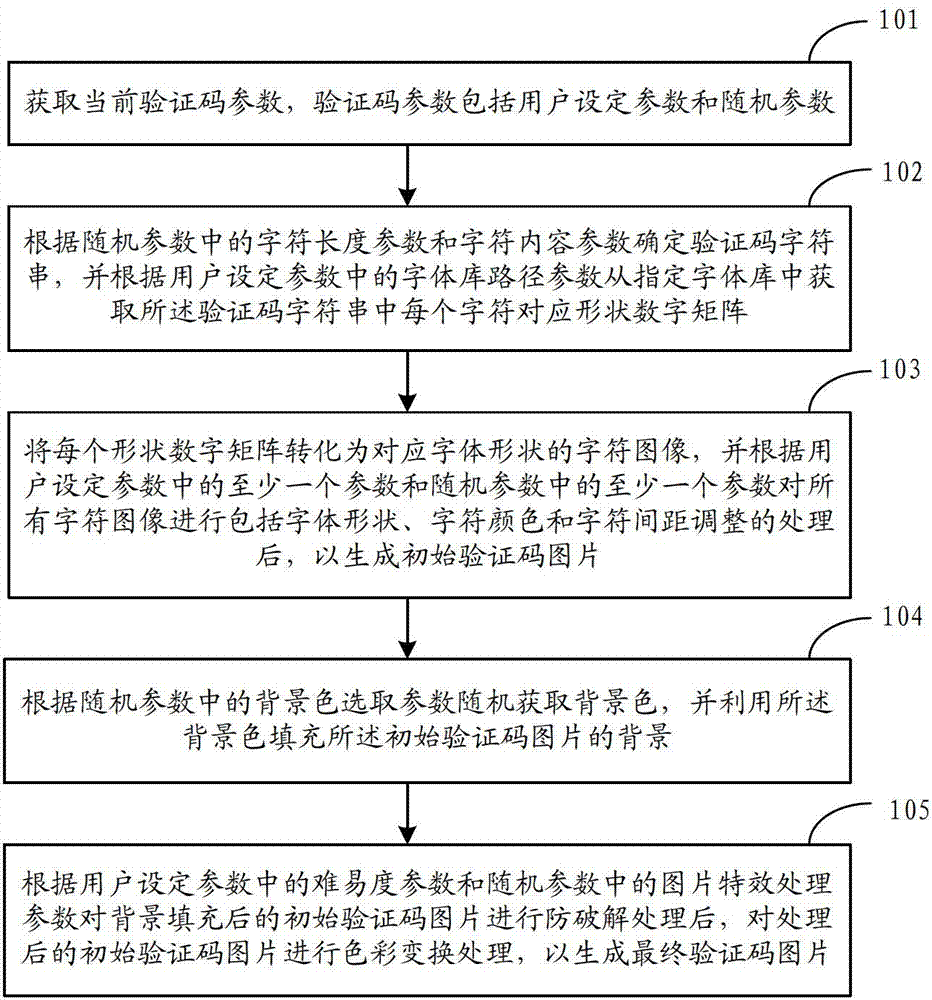
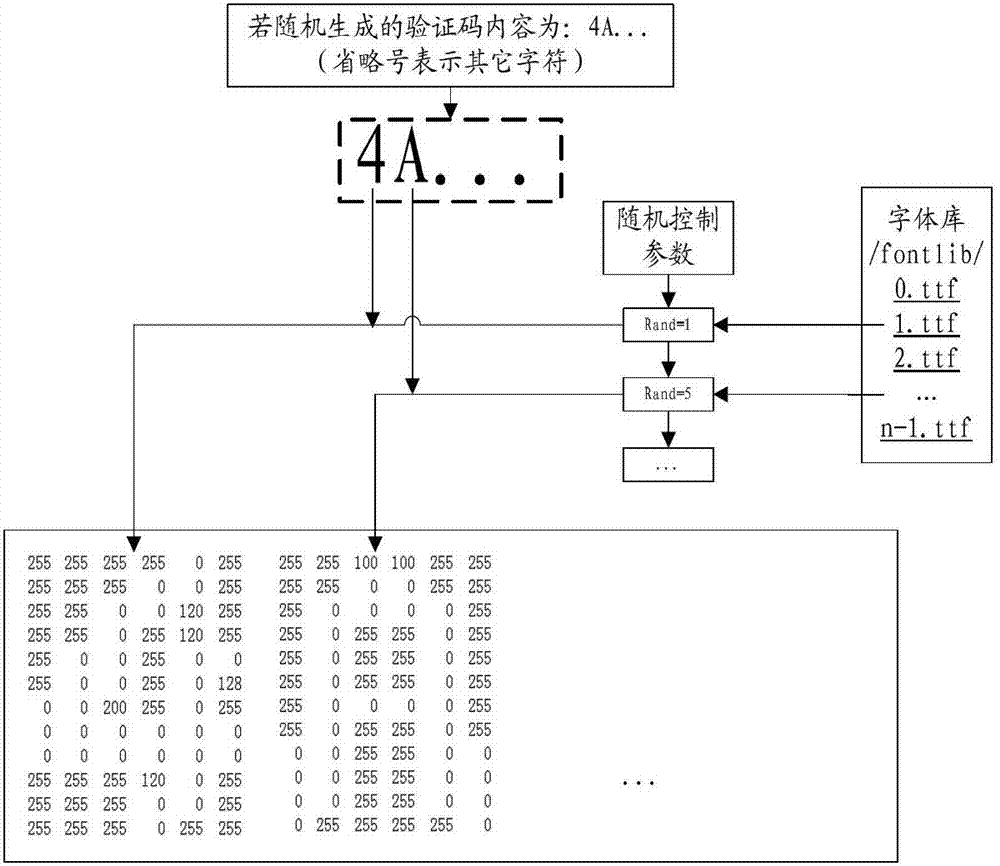
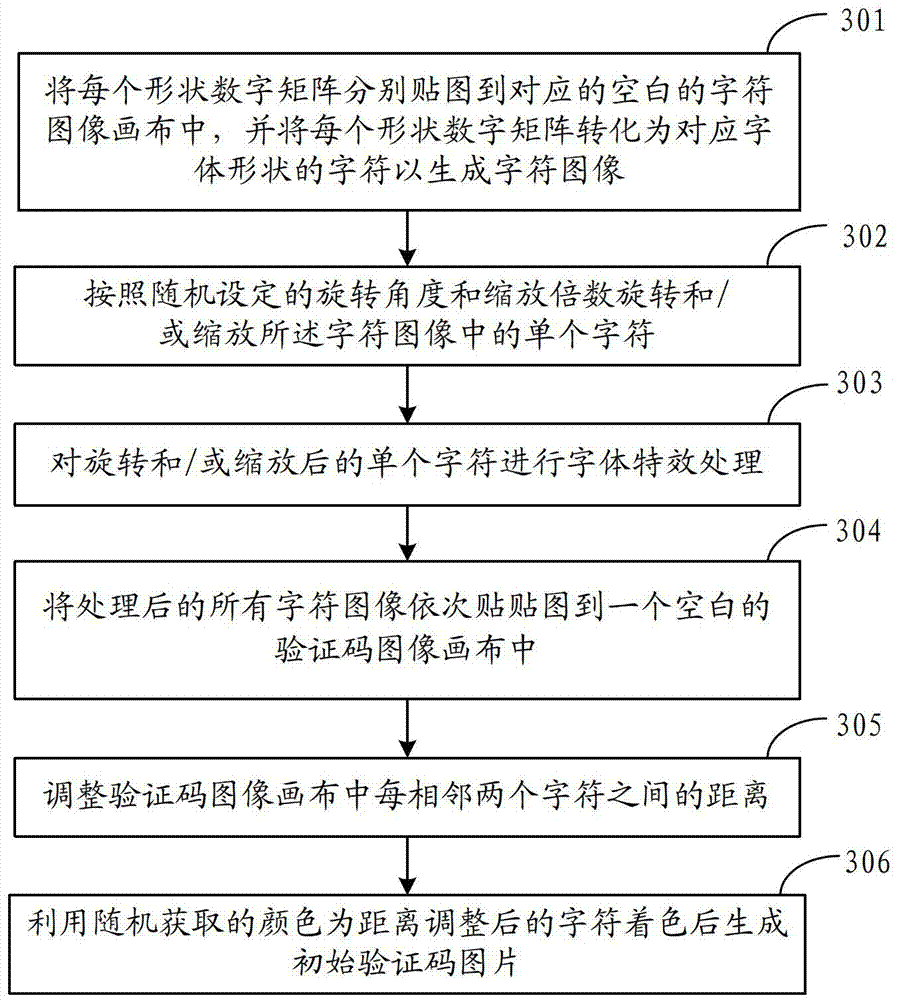
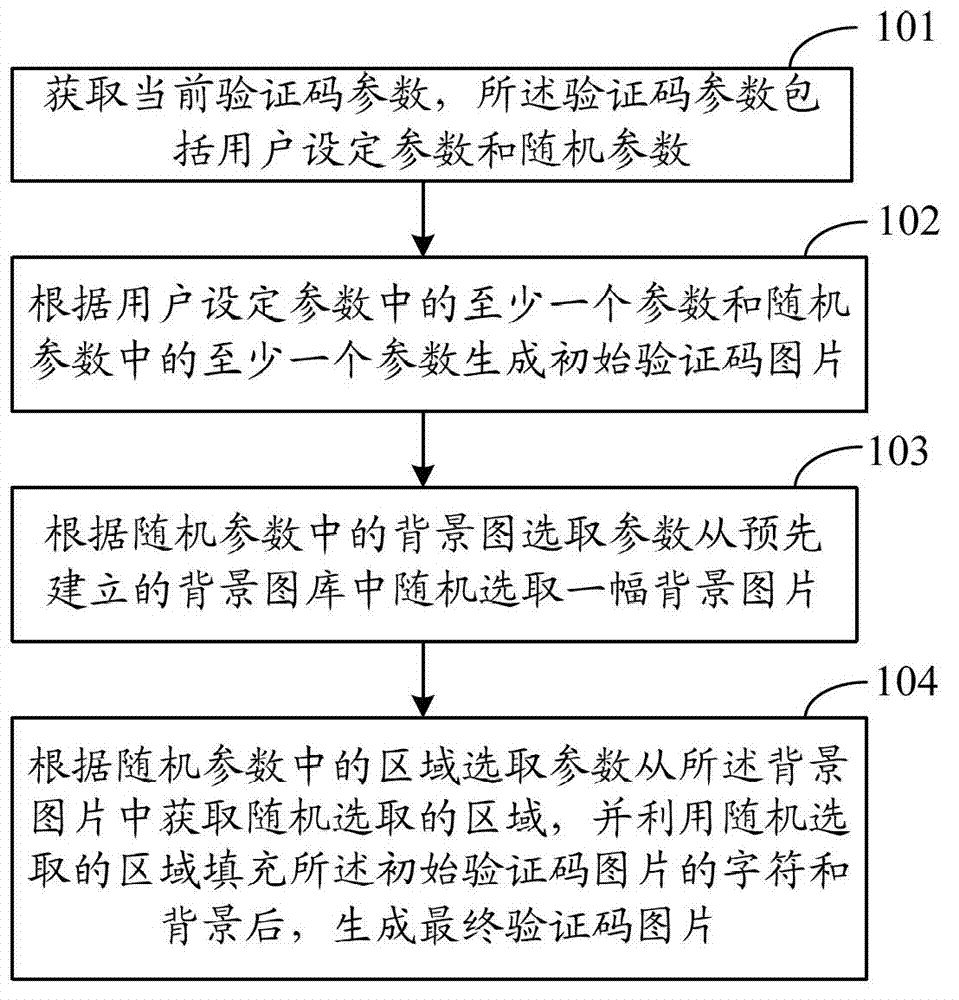
Method and device for implementation of picture verification code
ActiveCN102768754AGood varietyImprove visual experience2D-image generationImage data processing detailsColor changesRandom parameters
The invention discloses a method for implementation of a picture verification code. The method includes: acquiring current verification code parameters including user setup parameters and random parameters; determining the length and content of a character string of the verification code according to the random parameters, and acquiring a corresponding shape numerical matrix of each character in the character string of the verification code from a designated font object library according to font object library route parameters in the user setup parameters; converting each shape numerical matrix into a character picture of a corresponding character shape, and subjecting all character pictures to character special effect processing according to part of the verification code parameters to generate an initial verification code picture; filling the background of the initial verification code picture with a randomly selected background color; and subjecting the initial verification code picture with the background filled to anti-decoding processing according to difficulty parameters in the user setup parameters and picture special effect processing parameters in the random parameters, and then performing color change processing to generate a final verification code picture. The invention further discloses a device for implementation of the picture verification code.
Owner:杭州网易智企科技有限公司
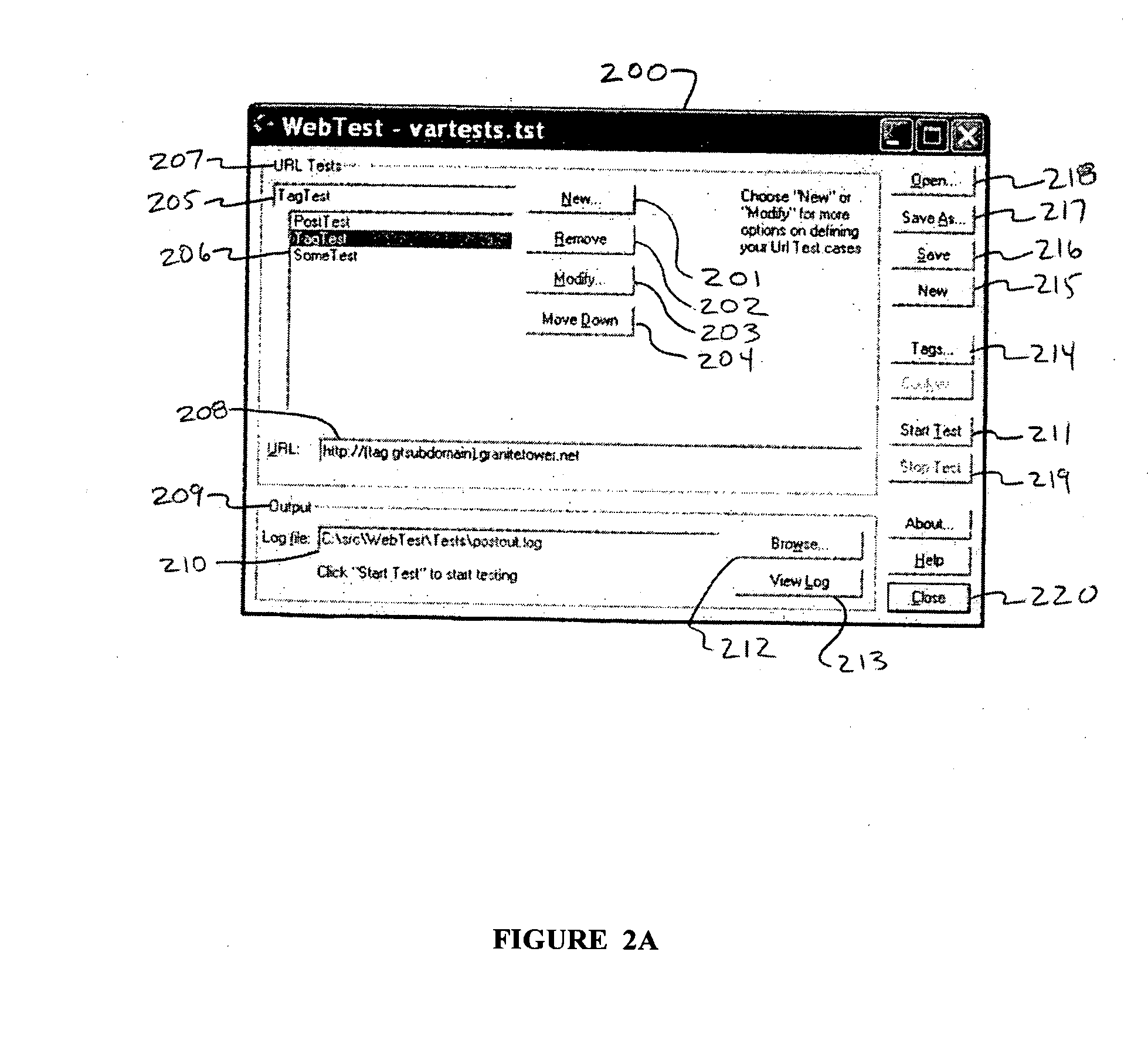
System and method for load testing a web-based application
A computer-based method for load testing a web application. The computer-based method comprises selecting one or more uniform resource locator (URL) parameters, identifying the selected parameters by parameter type, and loading the web application with URLs created by randomly generating the selected URL parameters. An electronic system adapted to load test a web application utilizing random parameter generation.
Owner:HEIN HENRI
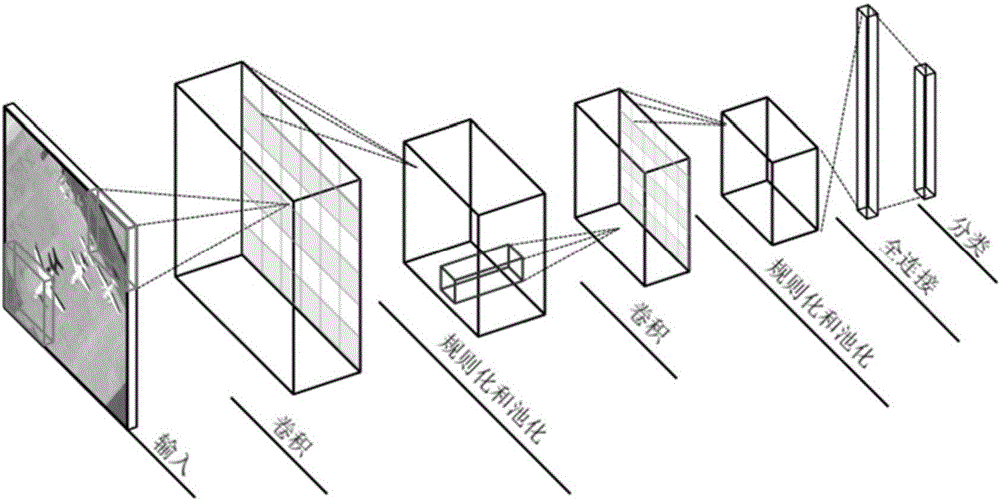
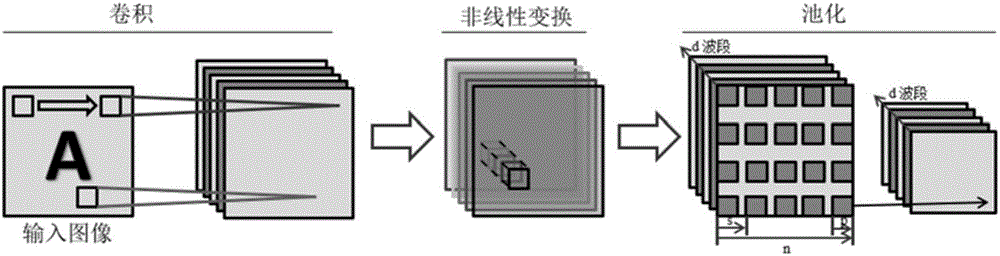
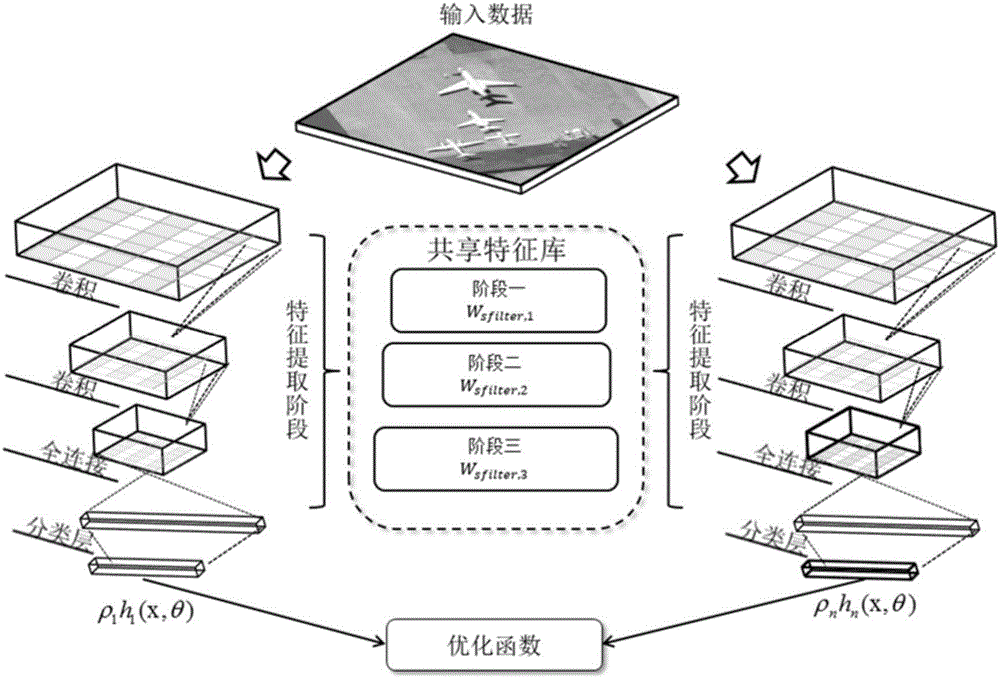
Random convolutional neural network-based high-resolution image scene classification method
InactiveCN106250931AImprove generalization abilityImprove training efficiencyCharacter and pattern recognitionNerve networkAlgorithm
The invention discloses a random convolutional neural network-based high-resolution image scene classification method. The method comprises the steps of performing data mean removal, and obtaining a to-be-classified image set and a training image set; randomly initializing a parameter library of model sharing; calculating negative gradient directions of the to-be-classified image set and the training image set; training a basic convolutional neural network model, and training a weight of the basic convolutional neural network model; predicting an updating function, and obtaining an addition model; and when an iteration reaches a maximum training frequency, identifying the to-be-classified image set by utilizing the addition model. According to the method, features are hierarchically learned by using a deep convolutional network, and model aggregation learning is carried out by utilizing a gradient upgrading method, so that the problem that a single model easily falls into a local optimal solution is solved and the network generalization capability is improved; and in a model training process, a random parameter sharing mechanism is added, so that the model training efficiency is improved, the features can be hierarchically learned with reasonable time cost, and the learned features have better robustness in scene identification.
Owner:WUHAN UNIV
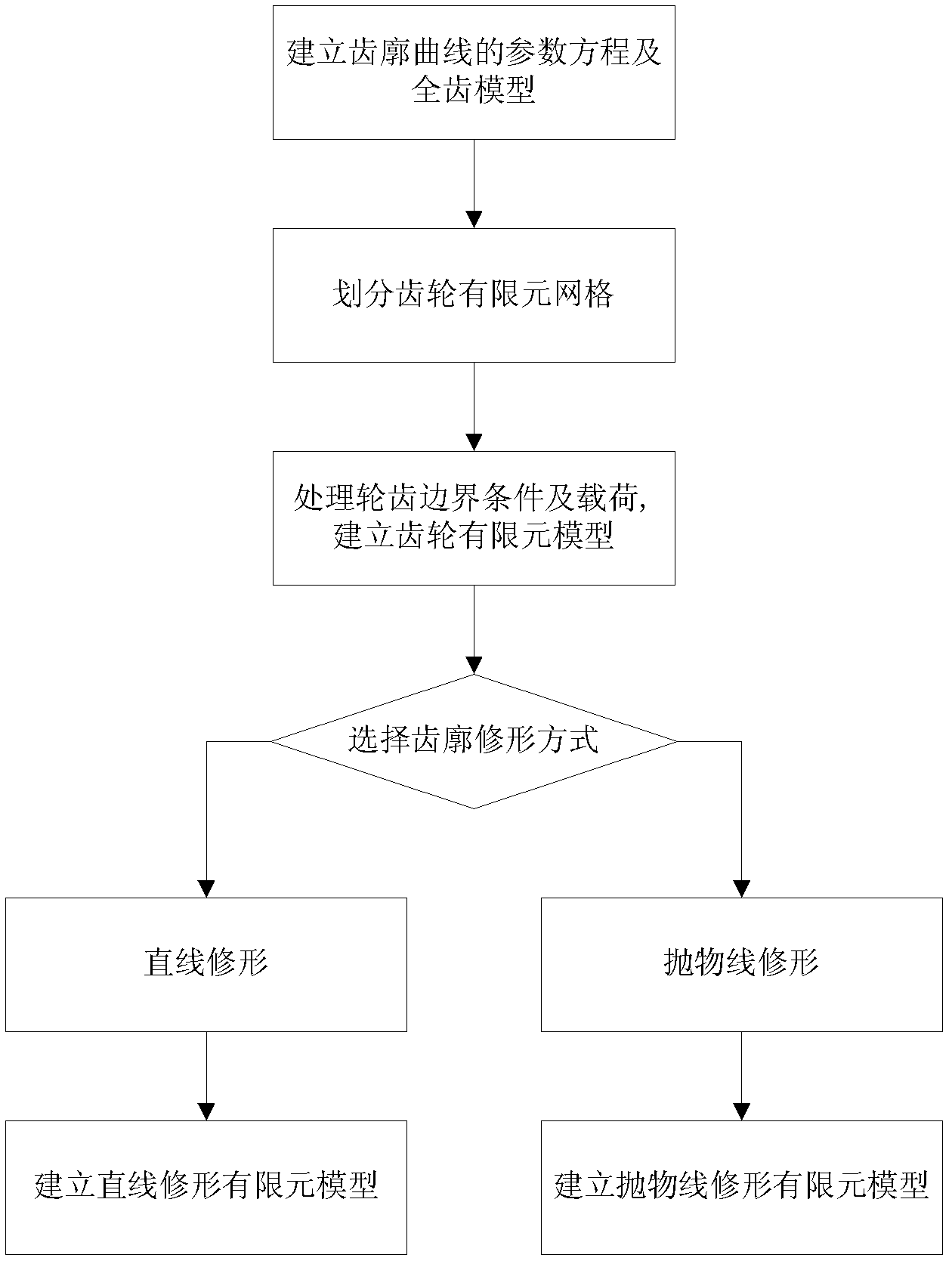
Gear profile modification method based on vibration reliability and genetic algorithm
InactiveCN102314534AImprove transmission error reliabilityEliminate shockSpecial data processing applicationsGear systemGenetic algorithm
The invention discloses a gear profile modification method based on vibration reliability and a genetic algorithm, belonging to the technical field of reliability designs. The gear profile modification method can not only reduce meshing impact due to elastic deformation and manufacturing errors, but also reduce the meshing excitation of a gear so that a gear system has smooth transmission, the vibration and the noises are reduced, and the reliability and service life of the gear system can be improved. The gear profile modification method comprises the following steps of: (1), establishing an elastic modification virtual prototype for meshing between a gear and a modifying gear; (2) carrying out dynamic simulation on gear transmission errors in the process of an involute profile and the profile modification; (3) analyzing the reliability sensitivity of the transmission errors at the time of gear pair random parameter meshing; (4) determining optimal parameters of the gear profile modification by utilizing the genetic algorithm; and (5) verifying the correctness of the parameters.
Owner:NORTHEASTERN UNIV LIAONING +1
Car networking authentication and key agreement method based on certificateless aggregation signature
ActiveCN108471351ATroubleshoot hosting issuesEliminate administrative overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRandom parametersComputer science
The invention discloses a car networking authentication and key agreement method based on certificateless aggregation signature. The method mainly comprises the following steps: A, establishing a key:a public-private key pair of a vehicle is bound to a real identity, and even if the temporary identity changes, the vehicle public-private key pair is not updated; B, registration and authorization:a random number for vehicle application and the real identity of the vehicle are stored in a constructed temporary identity index database; C, authentication and key negotiation: by introducing a random parameter, the vehicle reconstructs a secret pre-signature issued by a registration tracking center for the vehicle temporary identity in the authorization issuance stage, and a roadside facility (RSU) aggregates and forwards the signature information of the vehicle; and the method has conditional anonymity, can resist temporary private key compromise attacks and is high in security, high in authentication efficiency and low in system overhead.
Owner:蓝马舱行智能科技(上海)有限公司
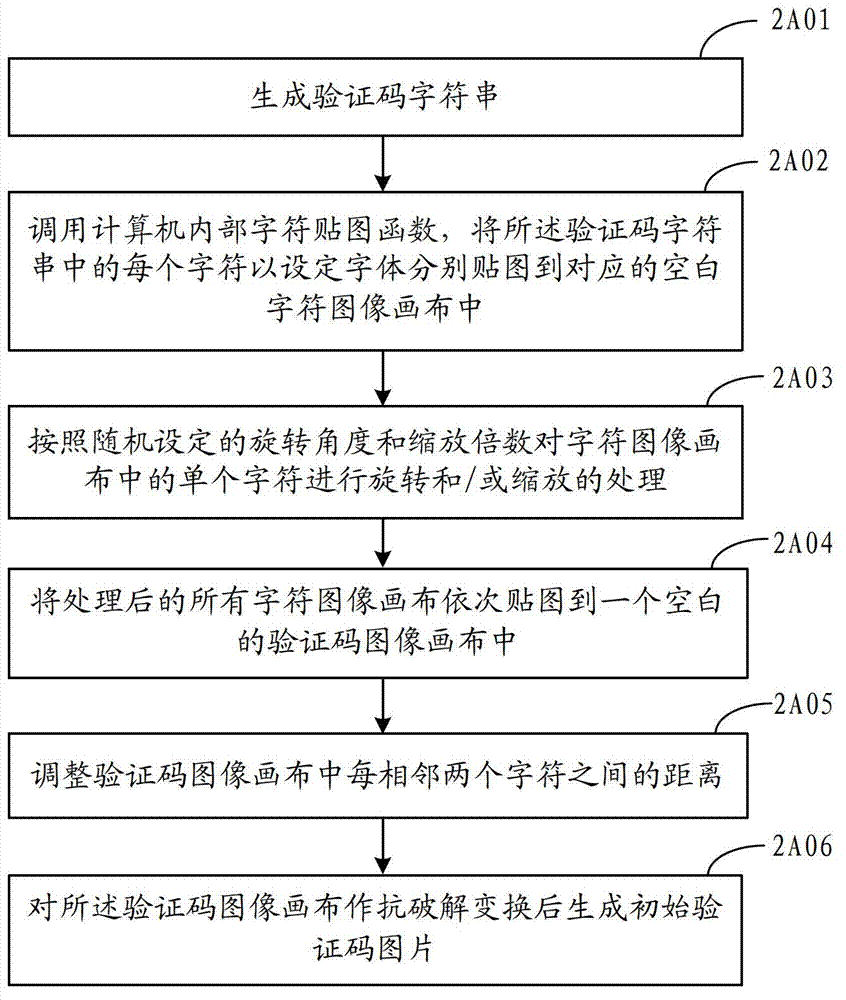
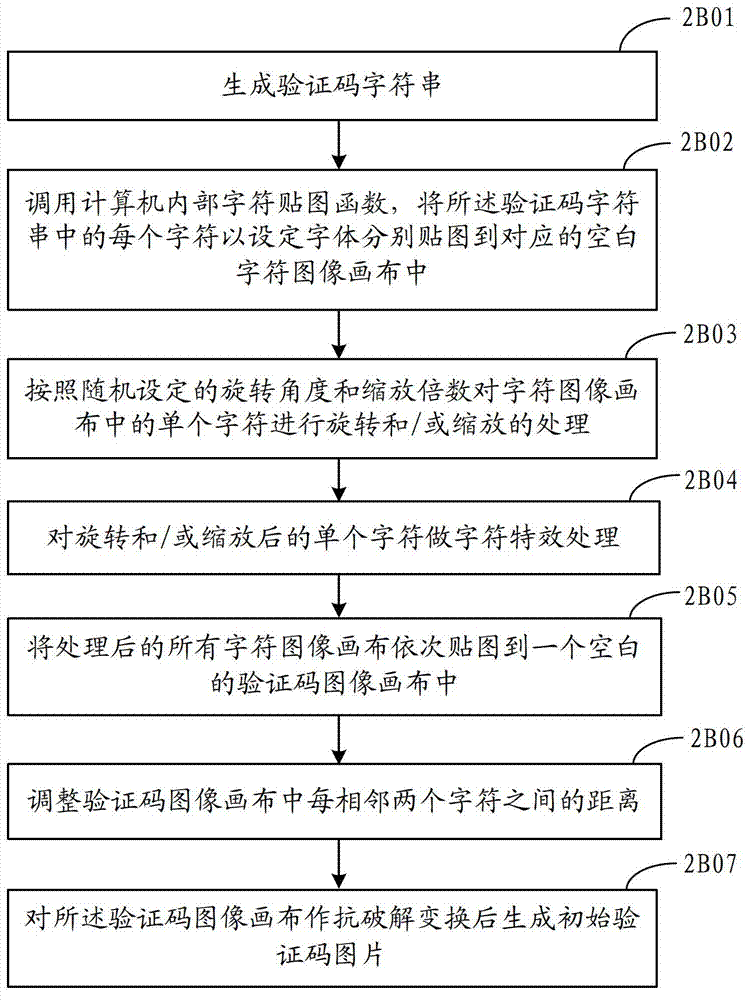
Method and device for generating verification code picture
ActiveCN102831568AHigh anti-cracking abilityImprove securityImage data processing detailsTheoretical computer scienceRandom parameters
The invention discloses a method for generating a verification code picture. The method comprises the following steps of: acquiring current verification code parameters including user set parameters and random parameters; generating an initial verification code picture according to at least one of the user set parameters and at least one of the random parameters; selecting a background picture at random from a pre-built background picture storage according to background picture selection parameters in the random parameters; acquiring a random selection area from the background pictures according to area selection parameters in the random parameters; and filling characters and backgrounds of the initial verification code pictures by using the random selection area to generate a final verification code picture. The invention also discloses a device for generating the verification code picture.
Owner:杭州网易智企科技有限公司
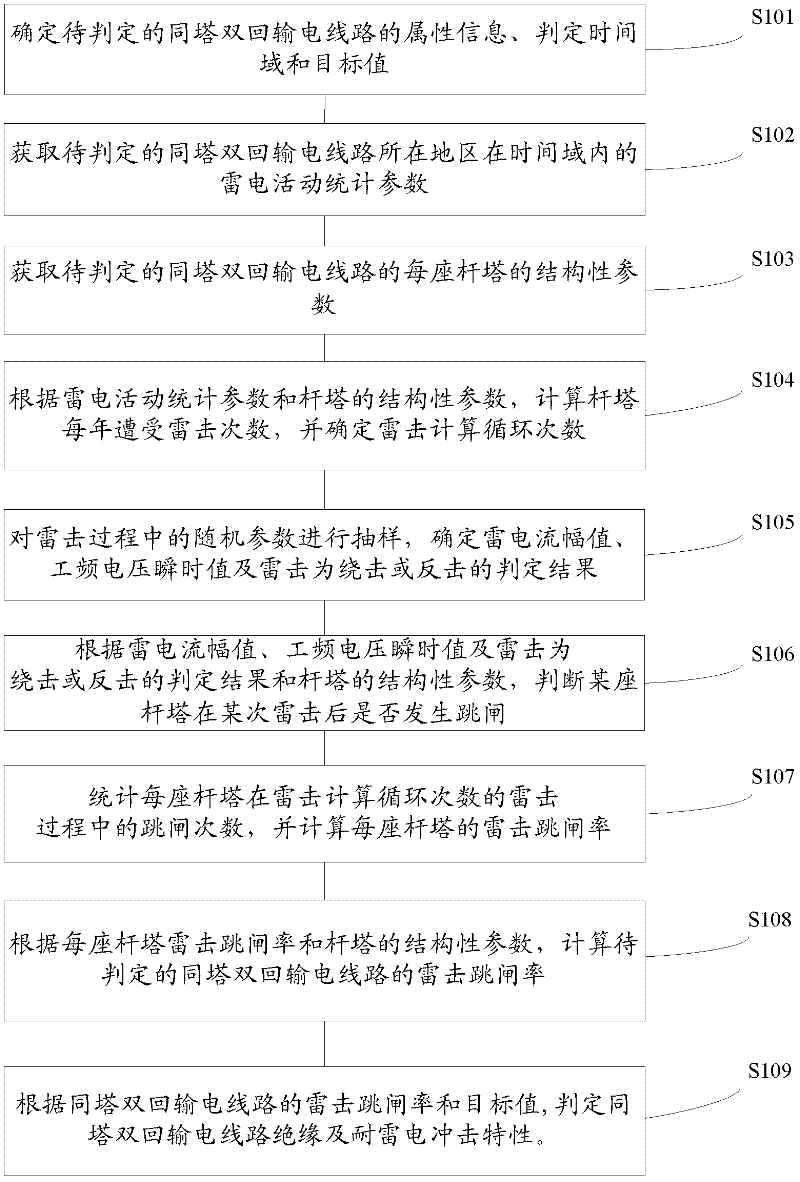
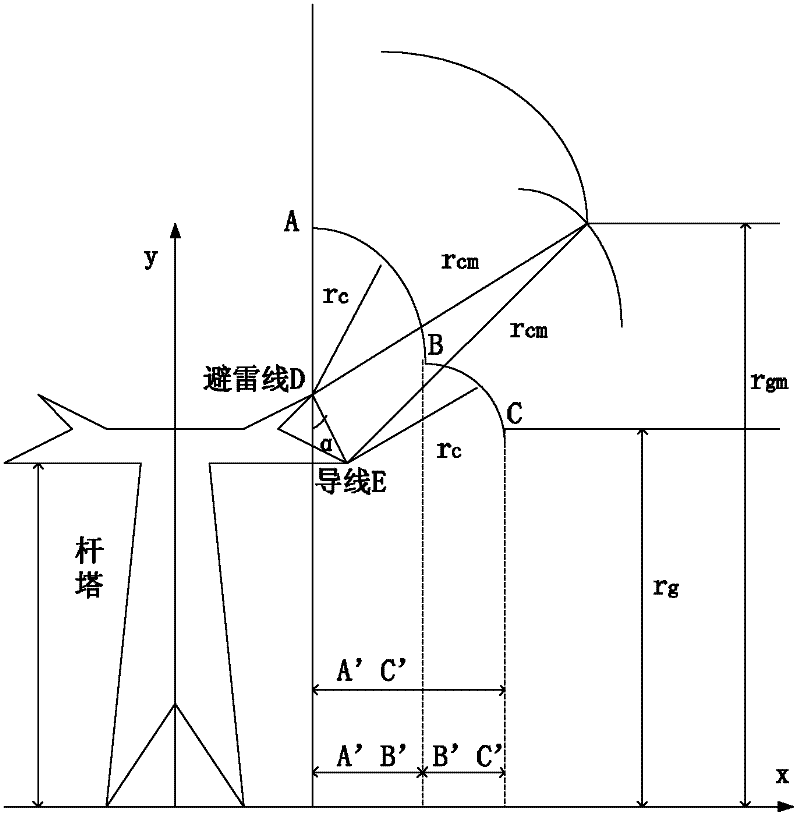
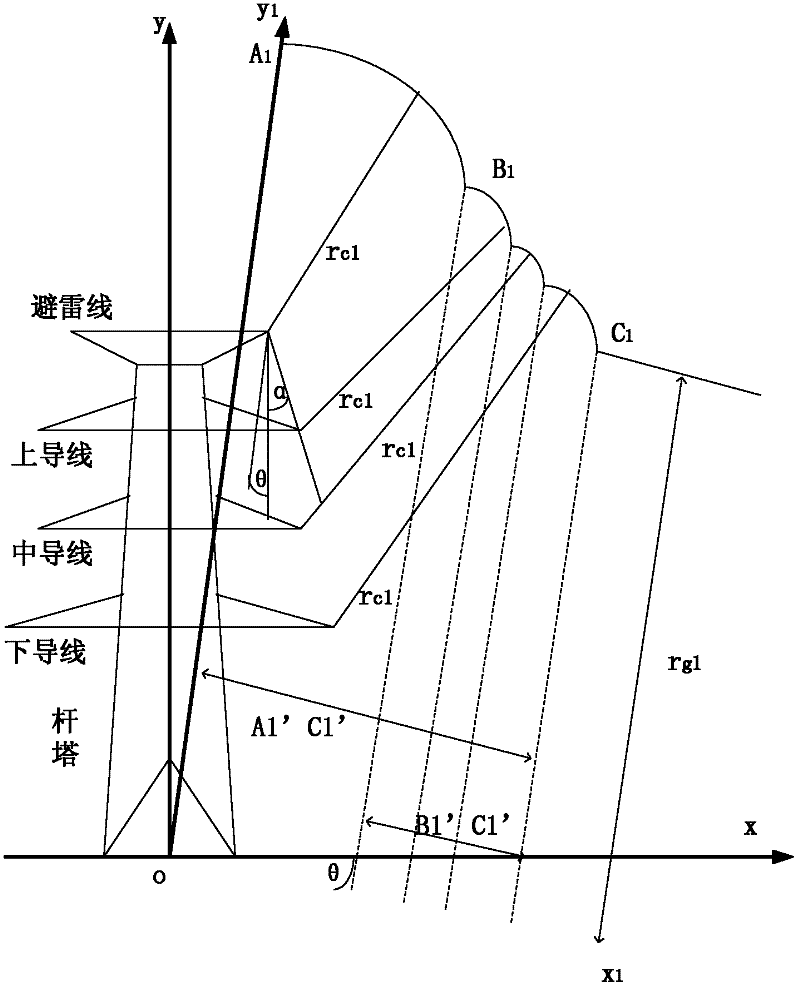
Method for determining insulation and lightning impulse withstanding properties of same-tower double-loop power transmission line
InactiveCN102435921ATargetedScientificTesting dielectric strengthLightning impulse voltageLightning strike
The invention provides a method for determining insulation and lightning impulse withstanding properties of a same-tower double-loop power transmission line. The method comprises the following steps: determining the same-tower double-loop power transmission line to be determined, acquiring statistical parameters of lightning activities in an area in which the power transmission line is located and structural parameters of each pole tower and determining a lightning strike calculation cycle number Nl; sampling random parameters during a lightning strike process and determining lightning current amplitude, transient power frequency voltage and determination result that the lightning strike is shielding failure or back striking; judging whether tripping occurs in the pole tower after the certain lightning strike or not and carrying out statistics on the tripping times during the Nl lightning strikes according to the lightning current amplitude, the transient power frequency voltage and the shielding failure or back striking determination result, as well as the structural parameters of the pole tower, and calculating the lightning strike tripping rate; and determining the insulation and the lightning impulse withstanding properties of the power transmission line according to the lightning strike tripping rate and a target value. The determination method provided by the invention is small in error, high in precision and specific; and by adopting the determination method, design, operation and improvement of lightning protection measures of the same-tower double-loop power transmission line of an electric power department can be scientifically guided.
Owner:XINZHOU POWER SUPPLY COMPANY STATE GRID SHANXI ELECTRIC POWER +1
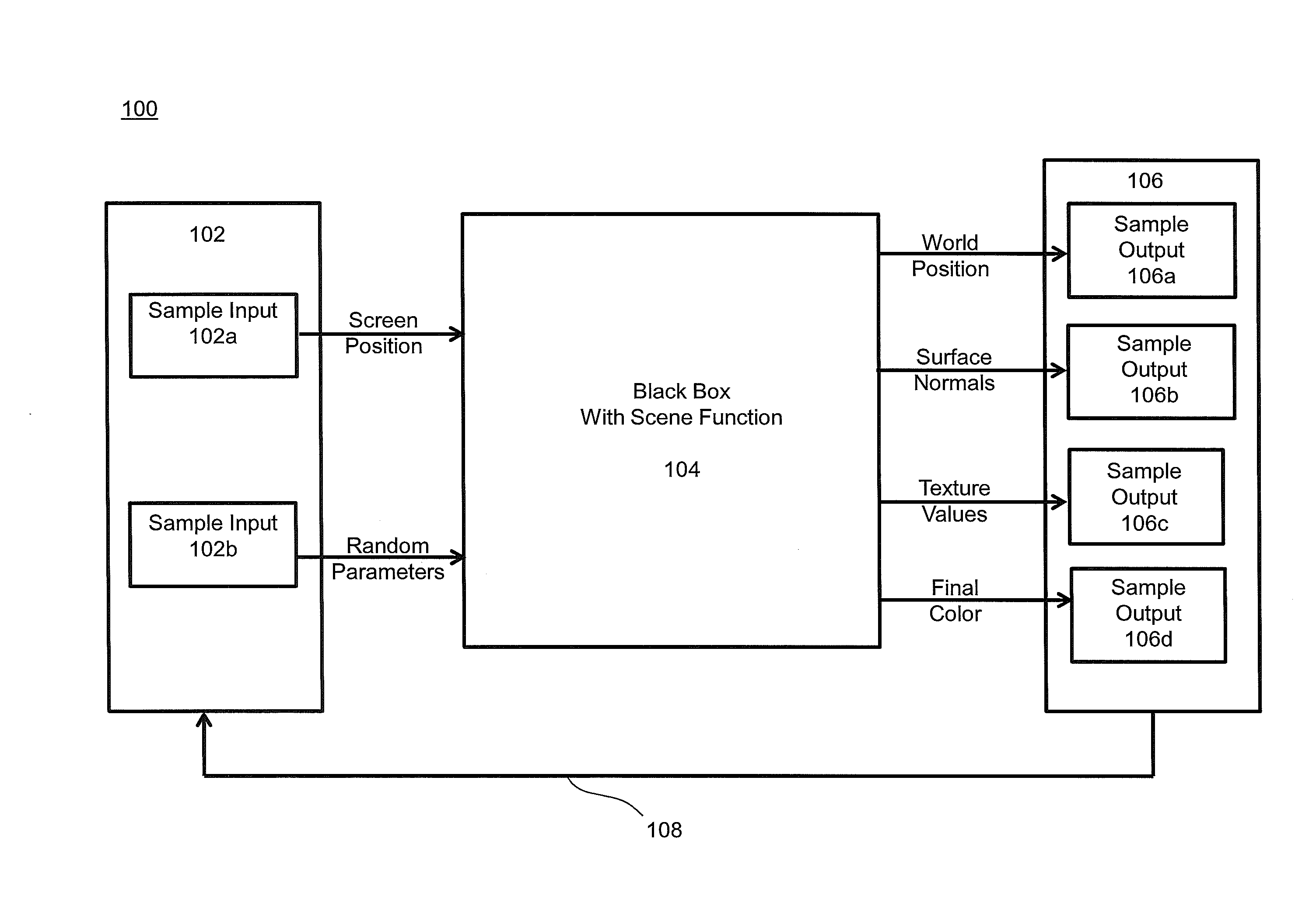
System and methods for random parameter filtering
ActiveUS20140029849A1Cancel noiseWide rangeImage enhancementDetails involving antialiasingBilateral filterMutual information
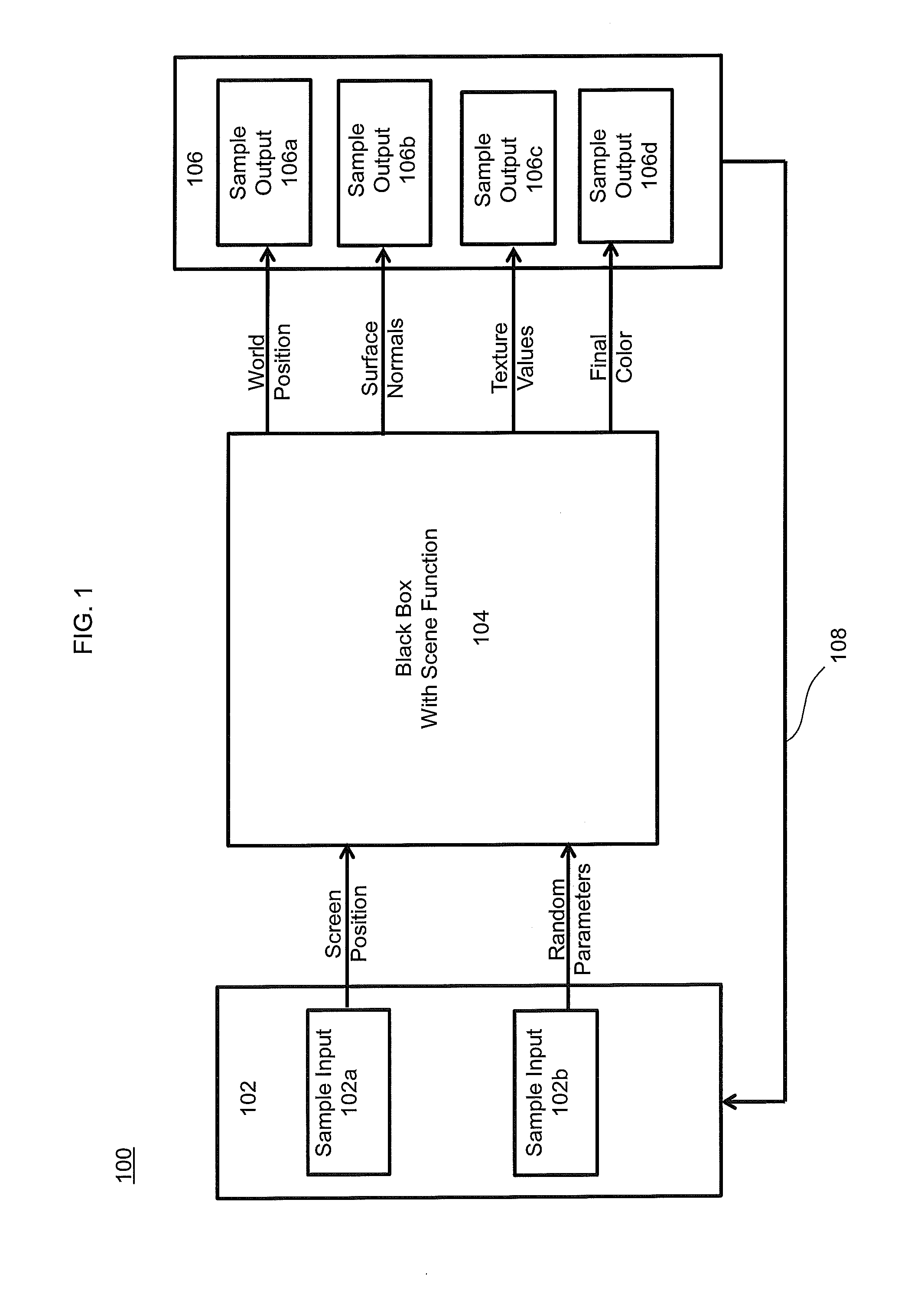
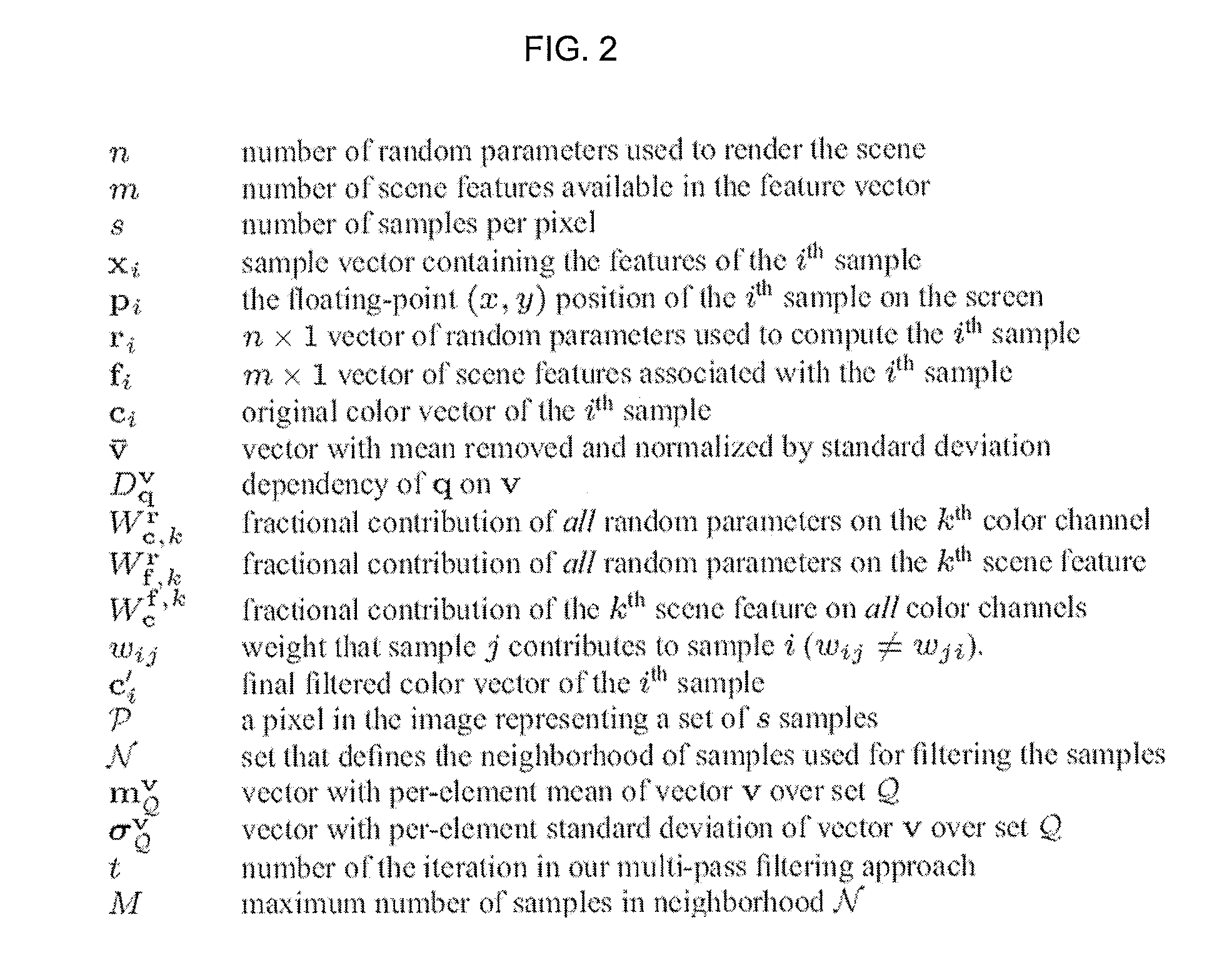
The invention produces a higher quality image from a rendering system based on a relationship between the output of a rendering system and the parameters used to compute them. Specifically, noise is removed in rendering by estimating the functional dependency between sample features and the random inputs to the system. Mutual information is applied to a local neighborhood of samples in each part of the image. This dependency is then used to reduce the importance of certain scene features in a cross-bilateral filter, which preserves scene detail. The results produced by the invention are computed in a few minutes thereby making it reasonably robust for use in production environments.
Owner:STC UNM
Random testing method based on Android
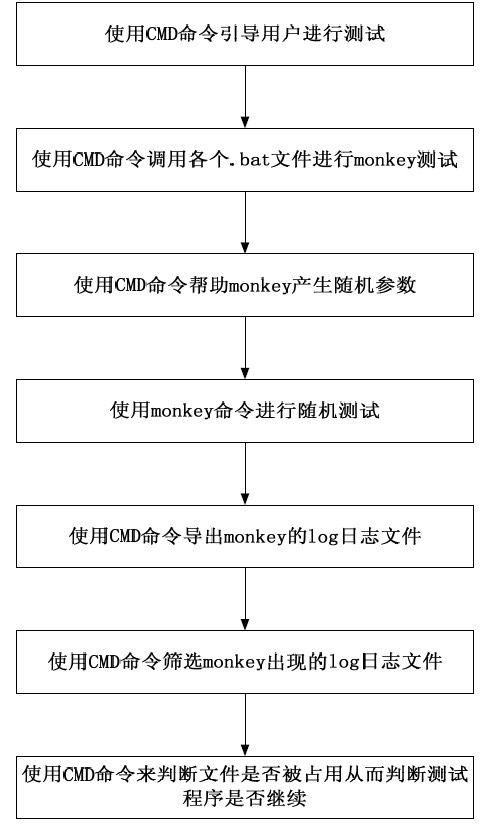
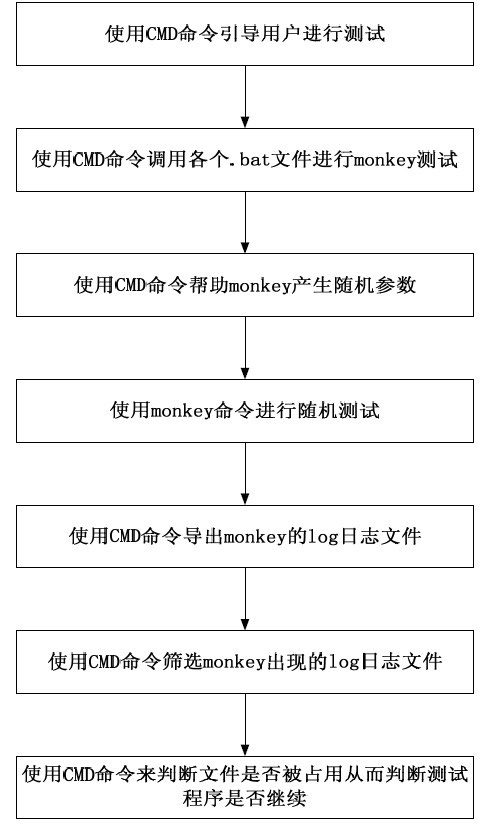
ActiveCN102110053AEasy to testImprove test efficiencySoftware testing/debuggingTest efficiencyMicrochiroptera
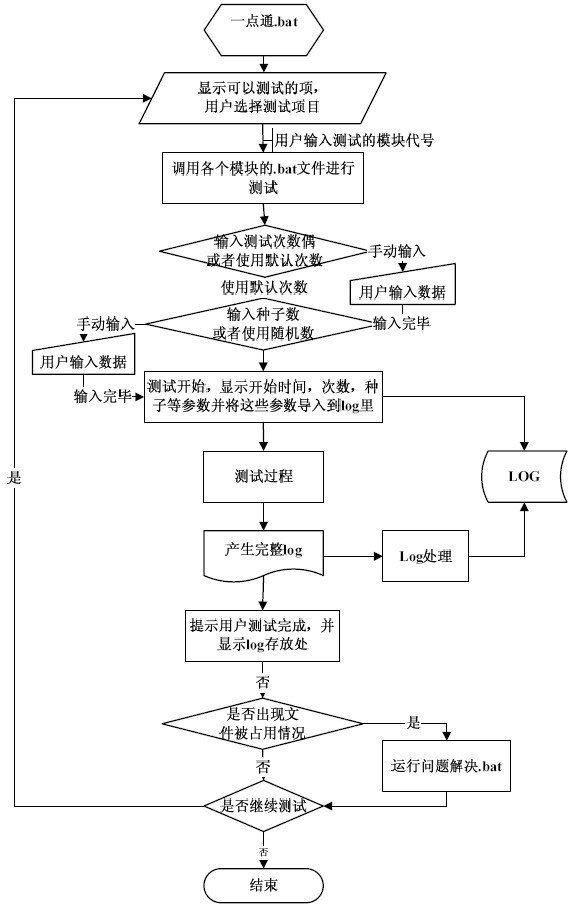
A random testing method based on Android comprises the following steps: (1) using a Windows CMD (command) to guide a user to conduct testing; (2) calling each.bat file by use of the CMD to carry out monkey testing; (3) using the CMD to help monkey generate a random parameter; (4) using the monkey command to conduct random testing; (5) using the CMD to export a log file of monkey; (6) using the CMD to screen the existing log file of monkey; and (7) using the CMD to determine whether the file is occupied so as to determine whether to continue the testing program or not. By integrating the CMD of the Windows with the Monkey command of Android, the method can simplify the software testing of mobile phones, improve the testing efficiency and lower the use threshold.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Information processing apparatus, server-client system, and computer program product
InactiveUS20120023156A1Accurately reflectMultiple digital computer combinationsTransmissionInformation processingRandom parameters
In a server-client system, a server provides a Web site and a function to record access logs using Web beacon technology, and a client terminal communicatable with the server includes a browser to execute JavaScript by dynamically embedding a 1-pixel image file that is dynamically added with a random parameter to a source of a <img> tag element in a <div> tag element. The random parameter may include at least current time data acquired in the client terminal. The server may read the requested 1-pixel image file from the Web site, and transfer the 1-pixel image file in HTML to the client terminal, and concurrently record a log including the random parameter in addition to information recordable by the Web beacon technology.
Owner:EMPIRE TECH DEV LLC
Probabilistic power flow data acquisition method based on renewable energy uncertainty
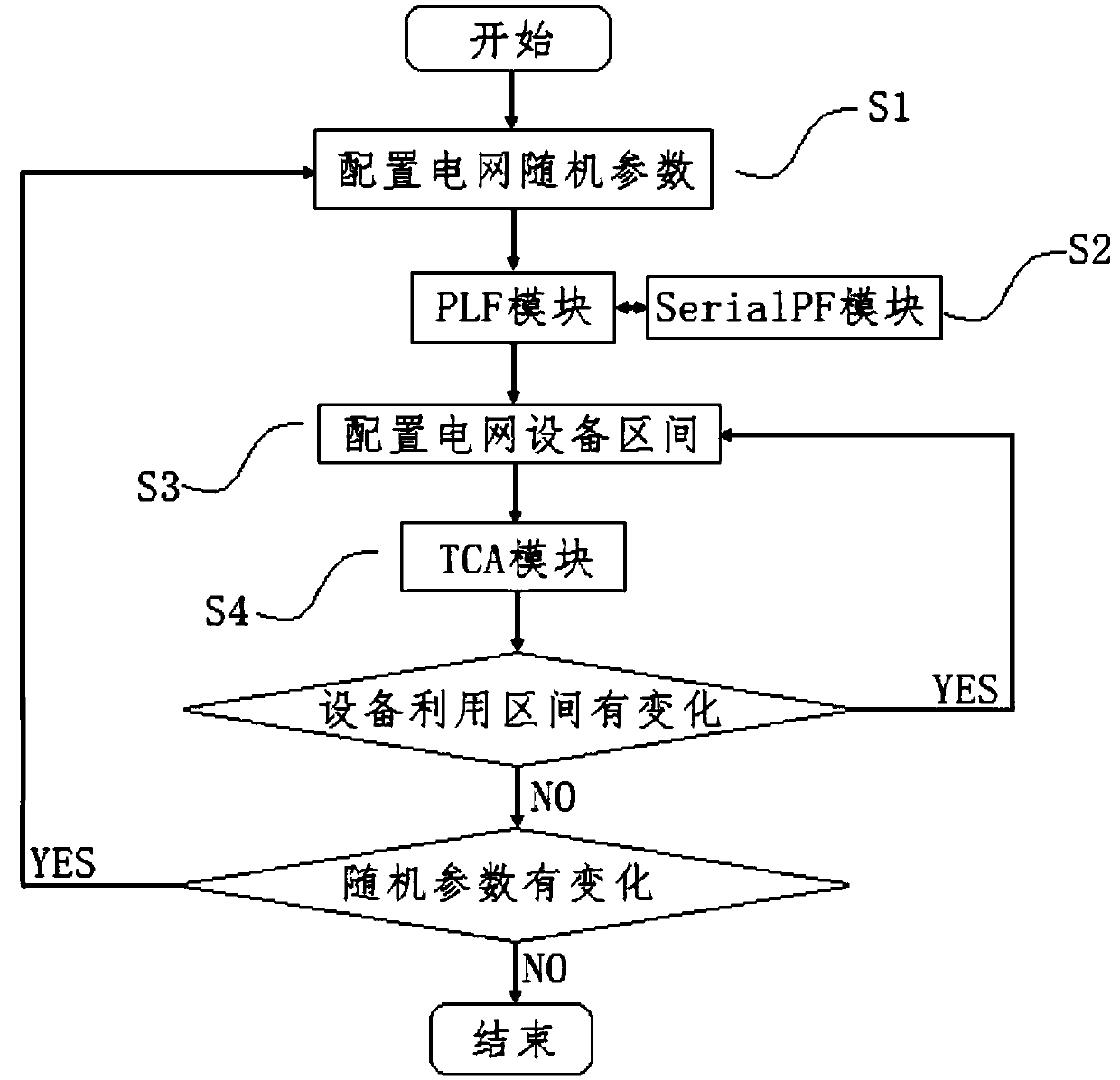
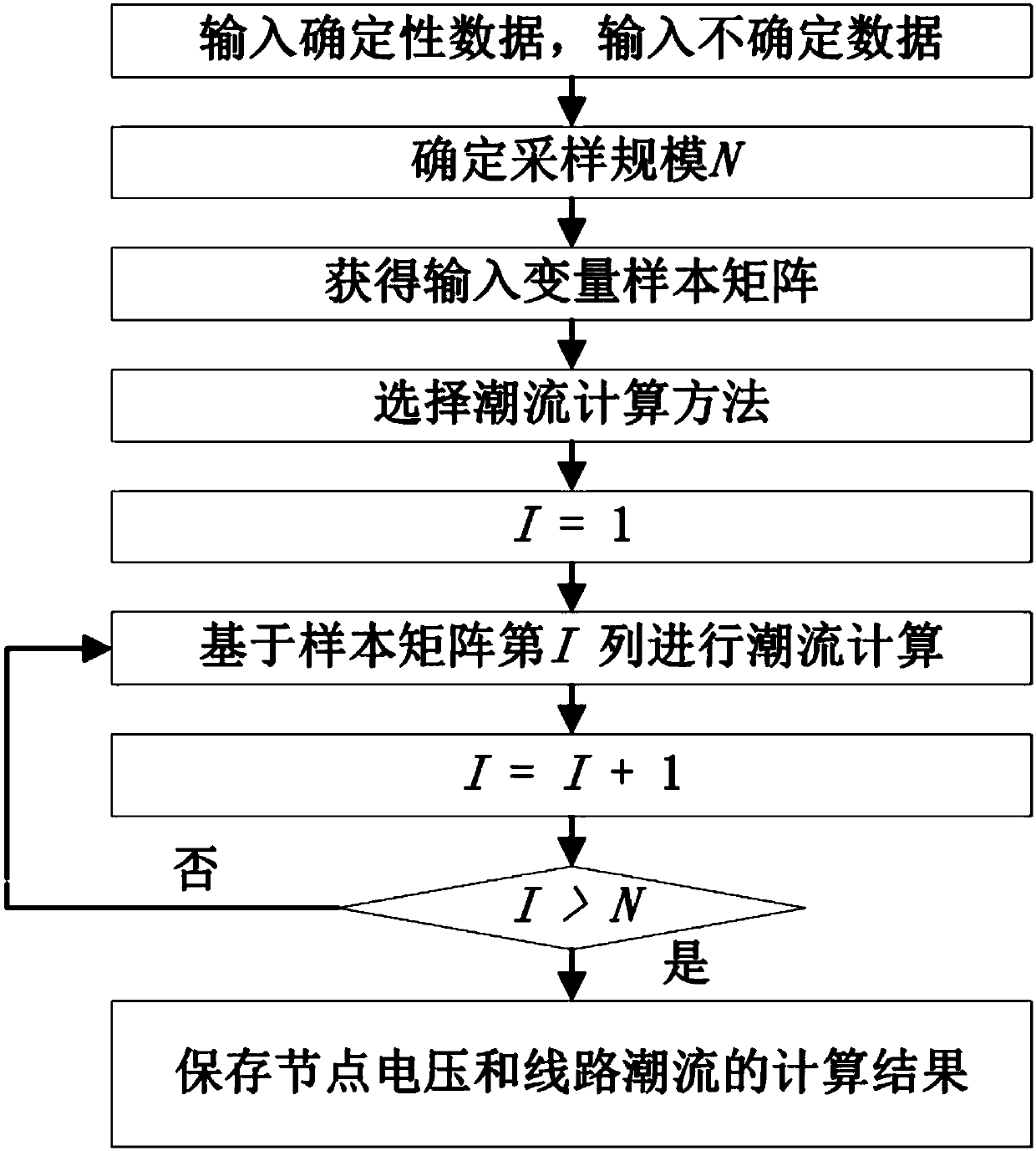
The invention discloses a probabilistic power flow data acquisition method based on renewable energy uncertainty. The method comprises steps of S1 inputting a data file of electric parameters of a power grid and configuring random parameters of the power grid; S2, carrying out AC power flow calculation and probabilistic power flow calculation, and outputting MCS sampling scale, bus independent variable parameters and line independent variable parameters; S3, configuring a network equipment interval, including a bus voltage amplitude interval, a line load rate interval, and a transformer load rate interval; S4, utilizing the kernel density estimation to obtain the evaluation result of the utilization ratio of the electrical equipment; The invention can fully consider a plurality of uncertain factors of a power network, establishes a calculation program for estimating a power network power flow based on a probabilistic power flow method of Monte Carlo simulation, applies the program to apractical transmission system, analyzes a power network capacity level and a load rate, etc., and better guides the planning and evaluation of the power network.
Owner:WUHU POWER SUPPLY COMPANY OF STATE GRID ANHUI ELECTRIC POWER +1
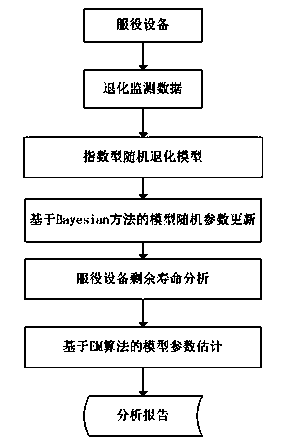
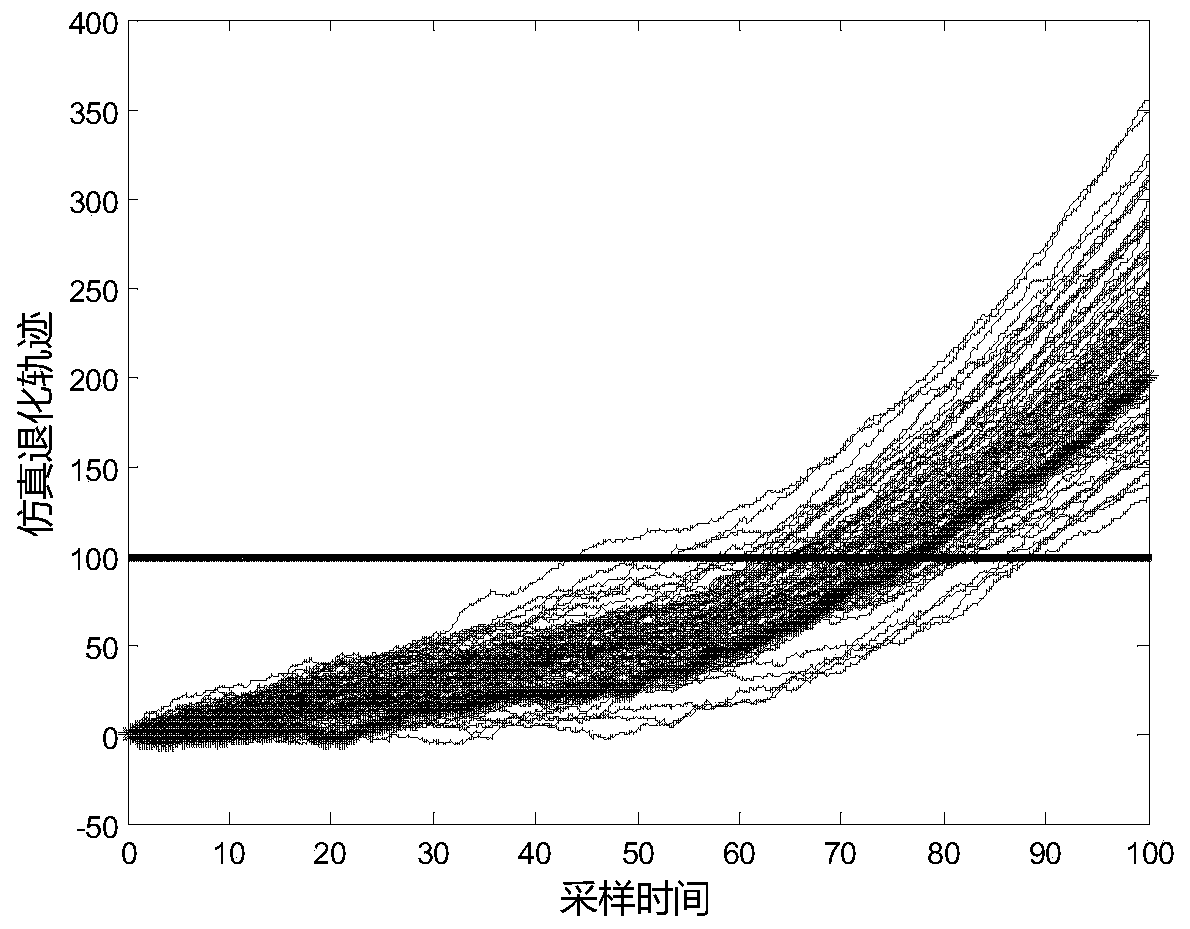
Adaptive prediction method of residual service life of service equipment modeled based on degradation data
The invention discloses an adaptive prediction method of residual service life of service equipment modeled based on degradation data. Degradation modeling and residual service life prediction of the service equipment are realized by a Bayesian method and an EM algorithm, and the method comprises the following steps of (1) randomly degrading and modeling; (2) updating random model parameters based on the Bayesian method; (3) predicting the residual service life; and (4) establishing model parameters based on the EM algorithm. An adaptive parameter updating mechanism based on the EM algorithm is introduced into a method for establishing a random index degradation model for predicting residual service life of service equipment, so that all parameters of the random index degradation model are continuously updated when the real-time data of the service equipment are accumulated, and thus the actual operation condition of the equipment can be reflected by predicted results, and the purpose of minimizing uncertainty prediction is achieved. According to the adaptive prediction method, historical data of multiple similar equipment are not required to initialize the degradation model, namely model parameters and residual service life distribution can be adaptively updated.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
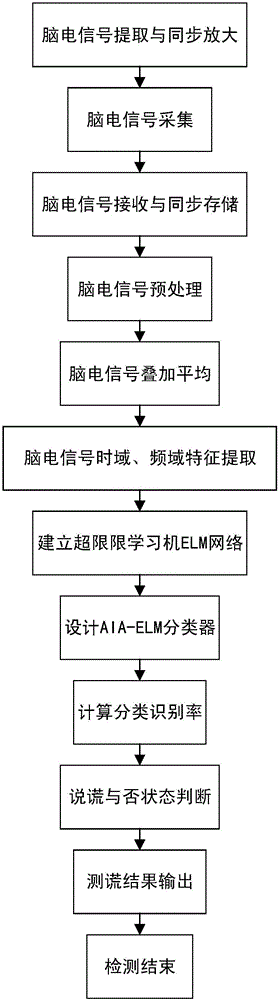
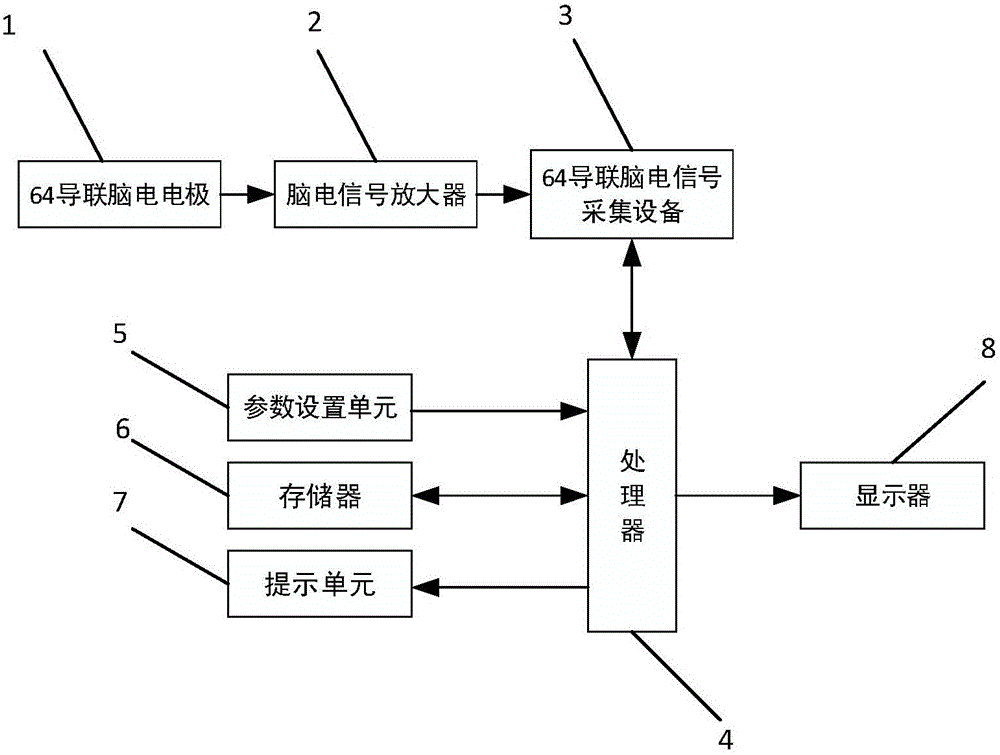
N400 evoked potential lie detection method based on improved extreme learning machine
ActiveCN105852885AStable lie recognition accuracyImprove classification recognition rateSensorsPsychotechnic devicesGeometric propertyTime domain
The invention provides an N400 evoked potential lie detection method based on an improved extreme learning machine; random parameters of the extreme learning machine are optimized on the basis of an artificial immune algorithm, and the electroencephalogram lie detection method based on an N400 evoked potential and the improved extreme learning machine is proposed; by virtue of the improved extreme learning machine, classification recognition rates of crime group subjects and control group subjects to detection stimulation and unassociated stimulation are calculated, and the classification recognition rates of the two groups of subjects are calculated and analyzed, so that a threshold parameter for distinguishing whether a subject lies or not is found out; and detection stimulation and unassociated stimulation time domain and frequency domain characteristics of 40 channel N400 induced electroencephalogram signals are extracted, so that the extracted electroencephalogram signal characteristics are more comprehensive; therefore, shortcomings in the prior art which conducts lie detection and judgment on the basis of a few of channels and by taking induced potential waveform geometric properties as characteristic parameter are overcome; and the lie detection method disclosed by the invention has the advantage that a stable lie identification right rate is effectively guaranteed.
Owner:SHAANXI NORMAL UNIV
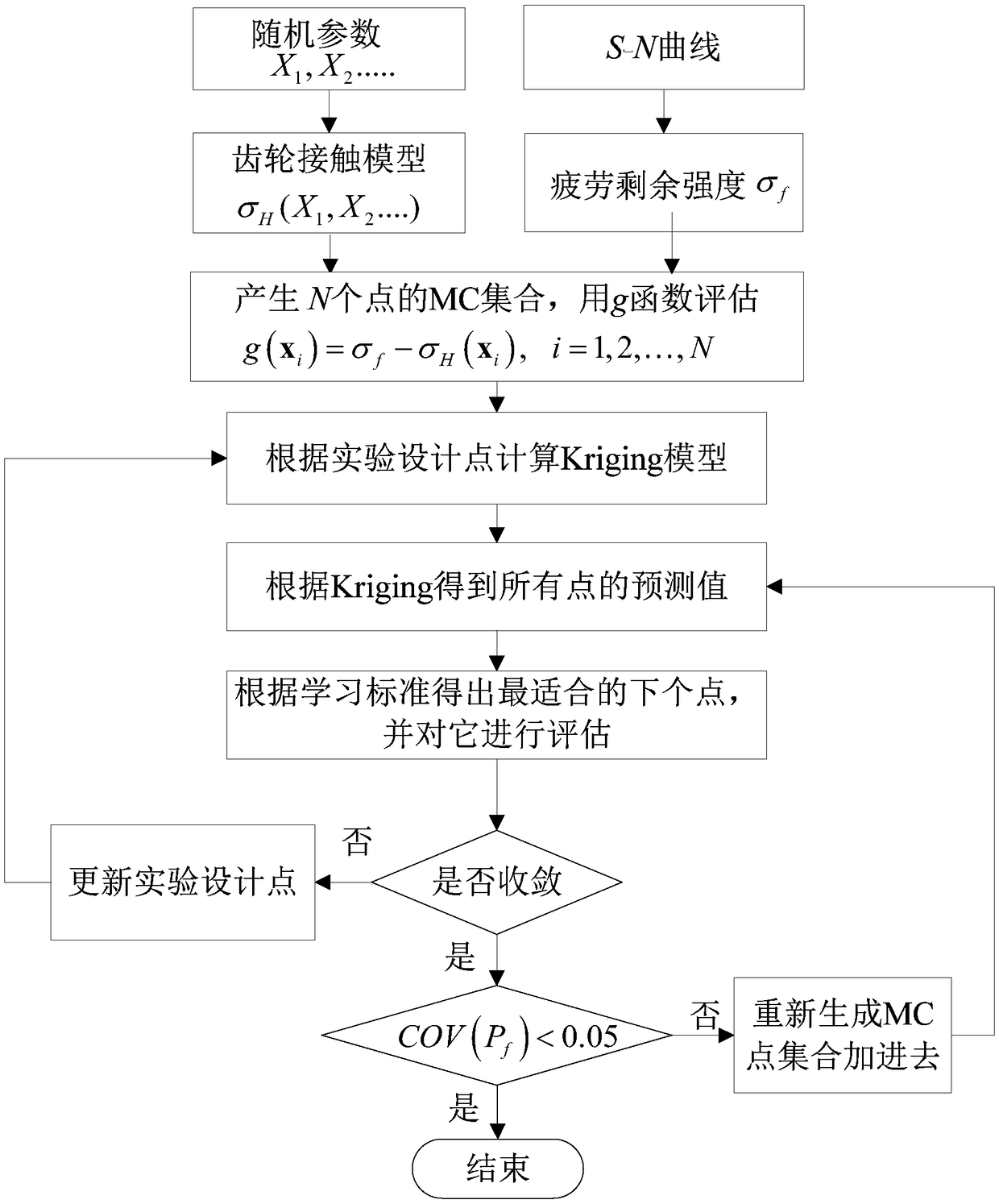
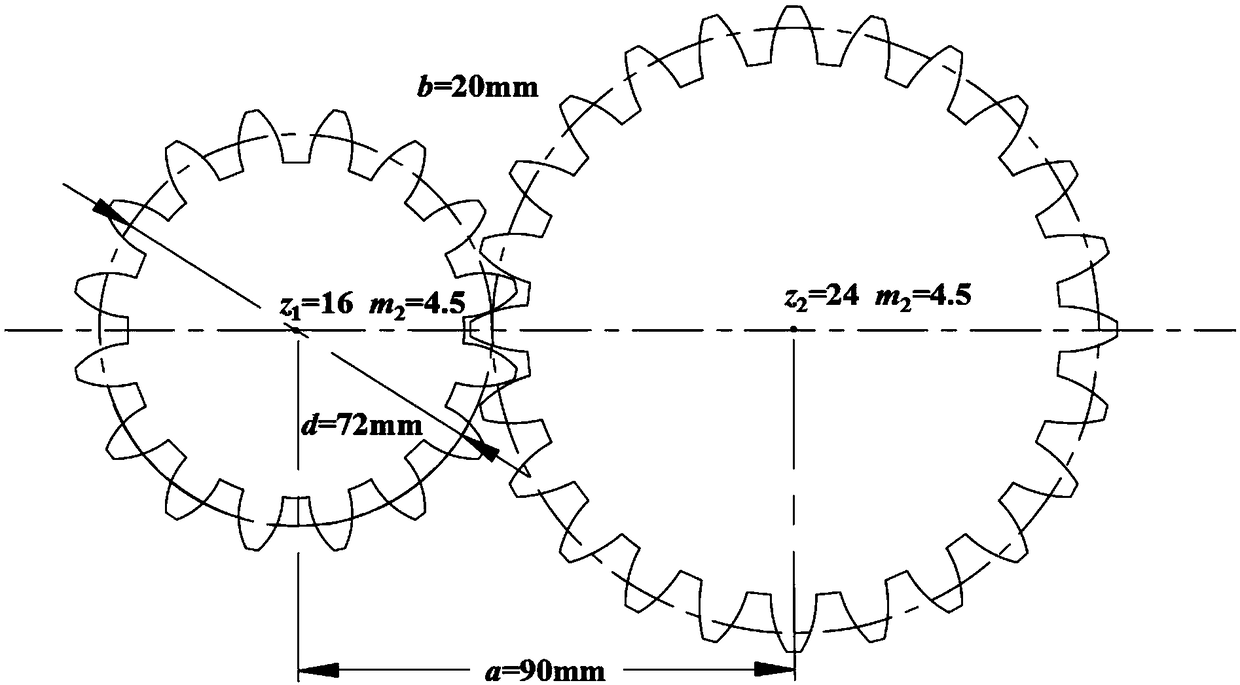
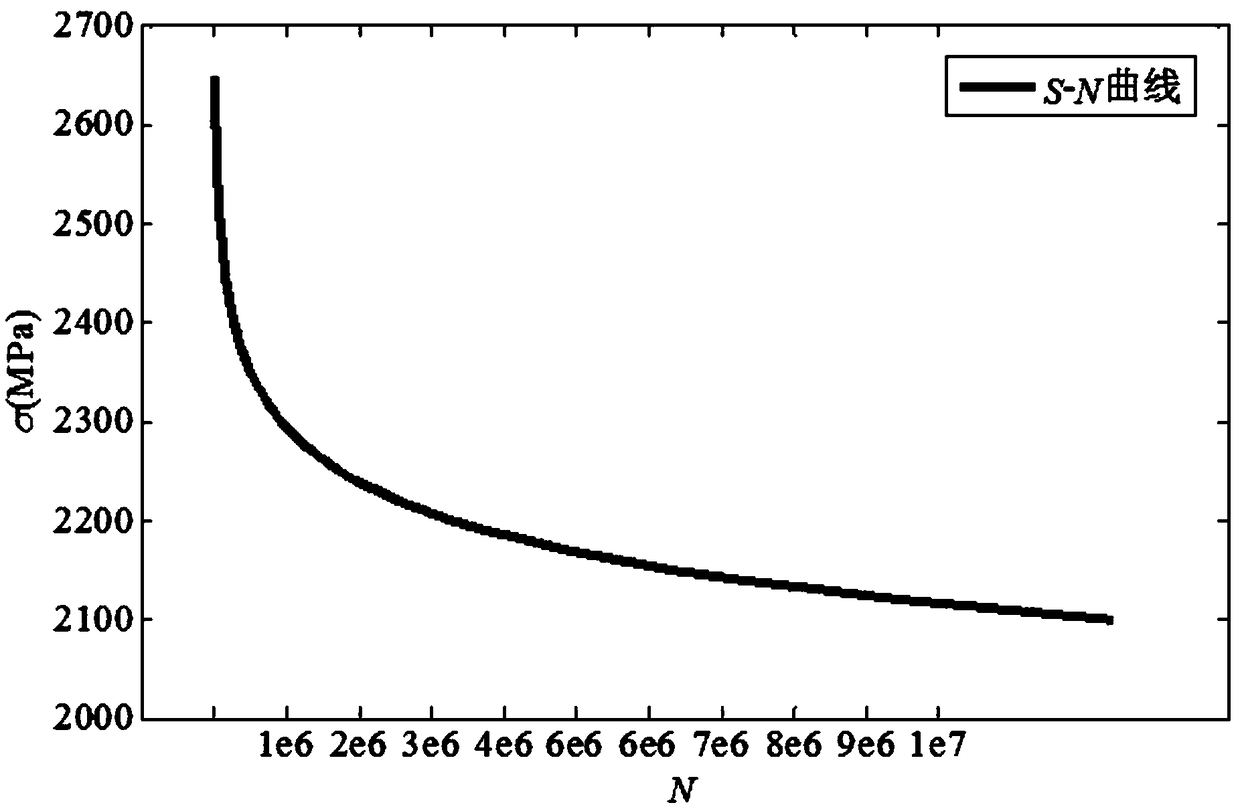
A gear contact fatigue reliability analysis method
ActiveCN109165425AAccurate and reliableGuaranteed reliabilityDesign optimisation/simulationSpecial data processing applicationsDistribution characteristicEngineering
The invention discloses a gear contact fatigue reliability analysis method. Firstly, the contact stress model of gear is established, the residual fatigue strength after a certain cycle is obtained onthe basis of a fatigue S-N curve, and then the function of gear contact fatigue failure is constructed. Then, according to the distribution characteristics of the random parameters, the Monte Carlo method is used to generate point set, the initial Kriging model is constructed by randomly selecting N points as the experimental design points, and then the sample points which are closest to the limit state surface or have the largest error are obtained by active learning strategy, and the sample points are added to the original experimental design points as the best sample points, and the Kriging model is updated until convergence. According to the convergent Kriging model, the approximate value of the function corresponding to all the sample points is obtained, and the failure probability is calculated by Monte Carlo method. Finally, an example is given to verify the feasibility of the proposed method. The gear contact fatigue reliability analysis method of the invention is more efficient and practical.
Owner:HUNAN UNIV
Aero-engine reliability monitoring method based on mixed weibull distribution
InactiveCN103020438ARealize performance degradation value monitoringReal-time dynamic grasp of reliability levelSpecial data processing applicationsAviationLower limit
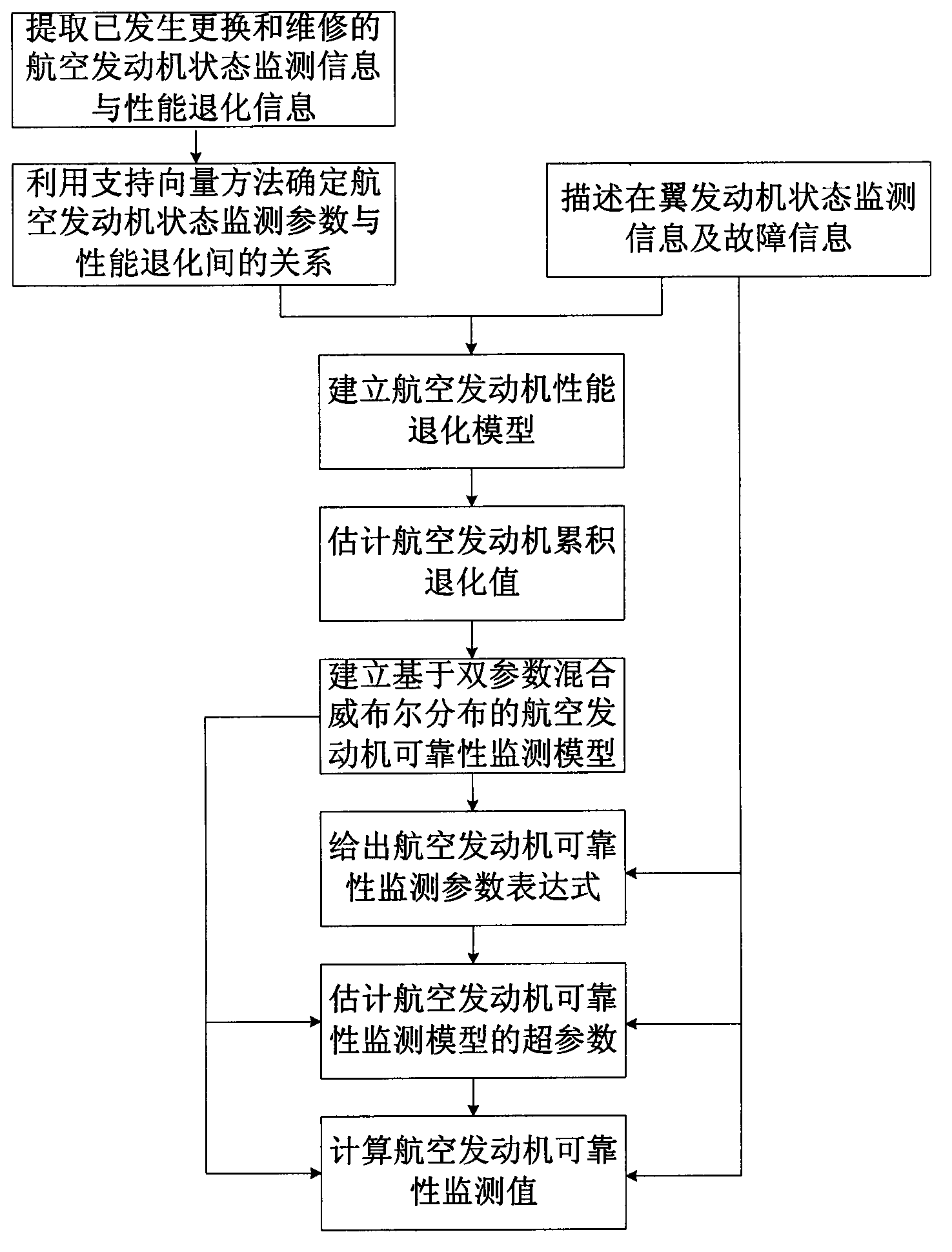
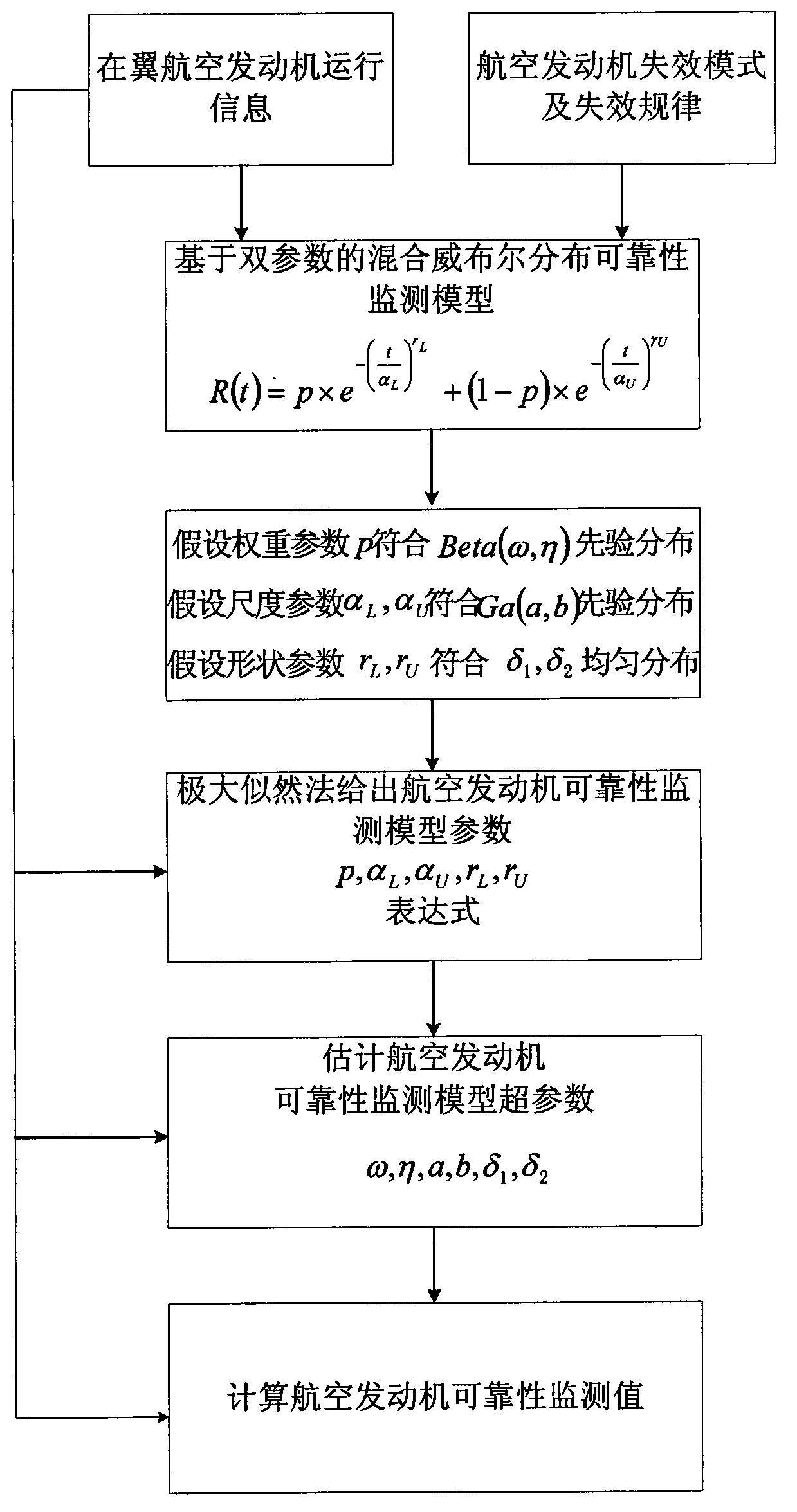
The invention relates to an aero-engine reliability monitoring method based on mixed weibull distribution, and the method comprises the following steps of extracting state monitoring information and performance degradation information of an aero-engine which is already replaced and repaired; extracting a relation between each monitoring parameter and the performance degradation of the aero-engine by utilizing a support vector method, and realizing the monitoring of the performance degradation value of a wing engine; utilizing a degradation model to describe the accumulated degradation volume of the aero-engine on the basis of the monitoring result of the real-time degradation value of the wing aero-engine; estimating a random parameter in a linear degradation model of the aero-engine, and determining the variation of the random parameter and the upper limit and the lower limit of the accumulated performance degradation volume of the aero-engine; establishing an aero-engine reliability monitoring model based on the dual-parameter mixed weibull distribution; utilizing a maximal likelihood method to give an expression of each parameter in the aero-engine reliability monitoring module; estimating hyper-parameters of the aero-engine reliability monitoring module based on the dual-parameter mixed weibull distribution; and calculating the reliability monitoring value of the aero-engine, and realizing the real-time and precise reliability monitoring of the aero-engine.
Owner:PEOPLES LIBERATION ARMY ORDNANCE ENG COLLEGE
Check Matrix Generating Apparatus and Communication Apparatus
InactiveUS20080184084A1Promote generationStable characteristicsElectronic circuit testingChecking code calculationsAlgorithmLow-density parity-check code
A check matrix generating apparatus calculates a parameter for pseudo-random-number permutation matrices using a predetermined information length, a coding rate, and a maximum column degree, generates the pseudo-random-number permutation matrices from the calculated parameter for the pseudo-random-number permutation matrices by using a pseudo-random-number sequence and a Latin square matrix, determines, as a parameter, a combination of degree distributions which can be adopted for optimization of a degree distribution of generation of a check matrix which can be formed with the pseudo-random-number permutation matrices, using the predetermined information length, coding rate, and maximum column degree, optimizes the degree distribution of generation of a check matrix under a restriction condition based on the determined combination of degree distributions which can be adopted, and arranges the generated pseudo-random-number permutation matrices according to the optimized degree distribution of generation of the check matrix so as to generate the check matrix for low-density parity-check codes.
Owner:MITSUBISHI ELECTRIC CORP
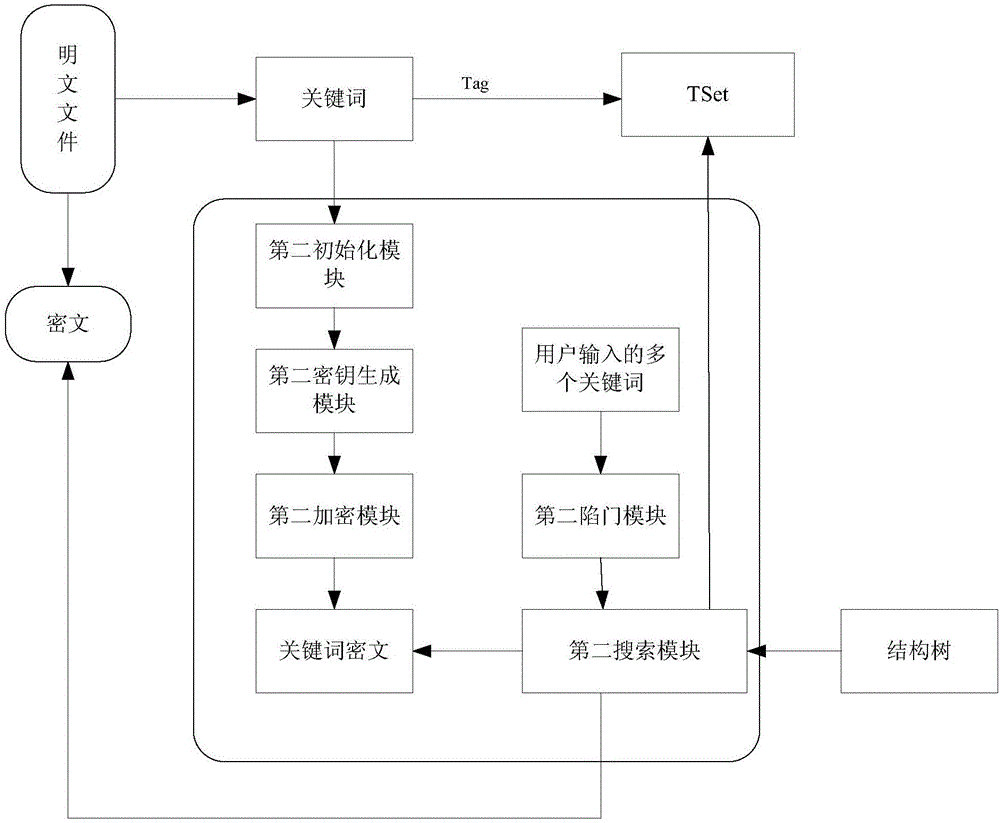
Keyword or multi-keyword based searchable encryption method and system
ActiveCN106407822AImprove securityReduce computational overheadDigital data protectionTransmissionUser inputCiphertext
The invention discloses a keyword or multi-keyword based searchable encryption method and system. The keyword based searchable encryption method comprises the following steps: generating a public key in an encryption process according to a random parameter and a system public coefficient, then encrypting a keyword in a file through the public key and a private key to obtain a keyword ciphertext, and searching the keyword ciphertext according to a keyword input by a user to obtain a ciphertext required by the user. The keyword based searchable encryption method has the advantages of low computing expense, simple algorithm, high speed and suitability for multiple user models. The multi-keyword based searchable encryption method comprises the following steps: storing all keywords of each file through a structural tree, generating the public key according to the random parameter and the system public coefficient, establishing relations between all the keywords in the file and ciphertexts of the keywords through a hidden part of the structural tree according to the public key, and encrypting to obtain all keyword ciphertexts in the file, wherein for a plurality of keywords input by the user, a cloud ciphertext required by the user can be searched only if the ciphertexts of all the keywords are searched. The multi-keyword based searchable encryption method has the advantage of higher safety.
Owner:SOUTH CHINA UNIV OF TECH
Method for Identifying Stochastic Information of Heterogeneous Materials
InactiveUS20150057988A1Minimize objective functionComputation using non-denominational number representationDesign optimisation/simulationRandom materialsElement analysis
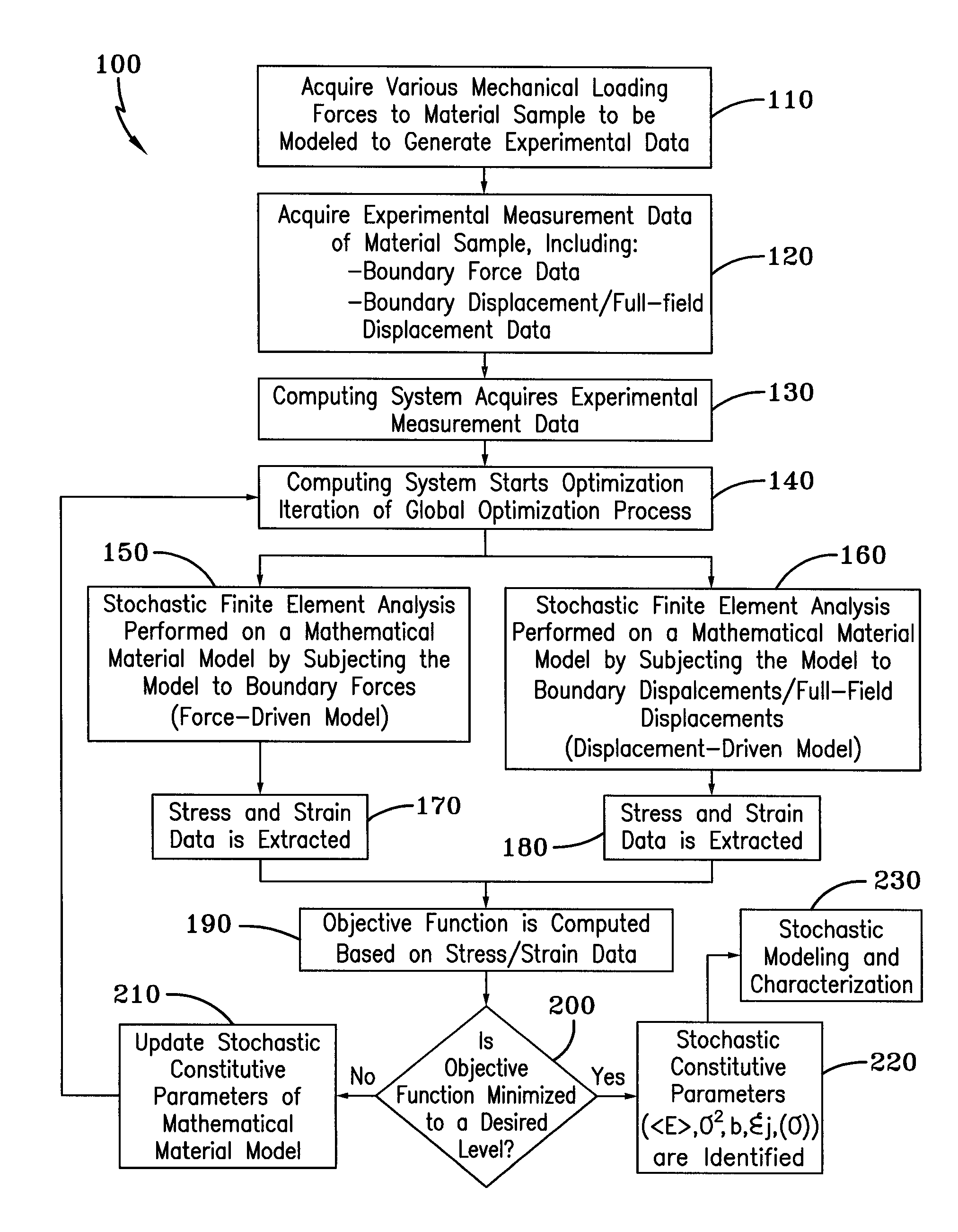
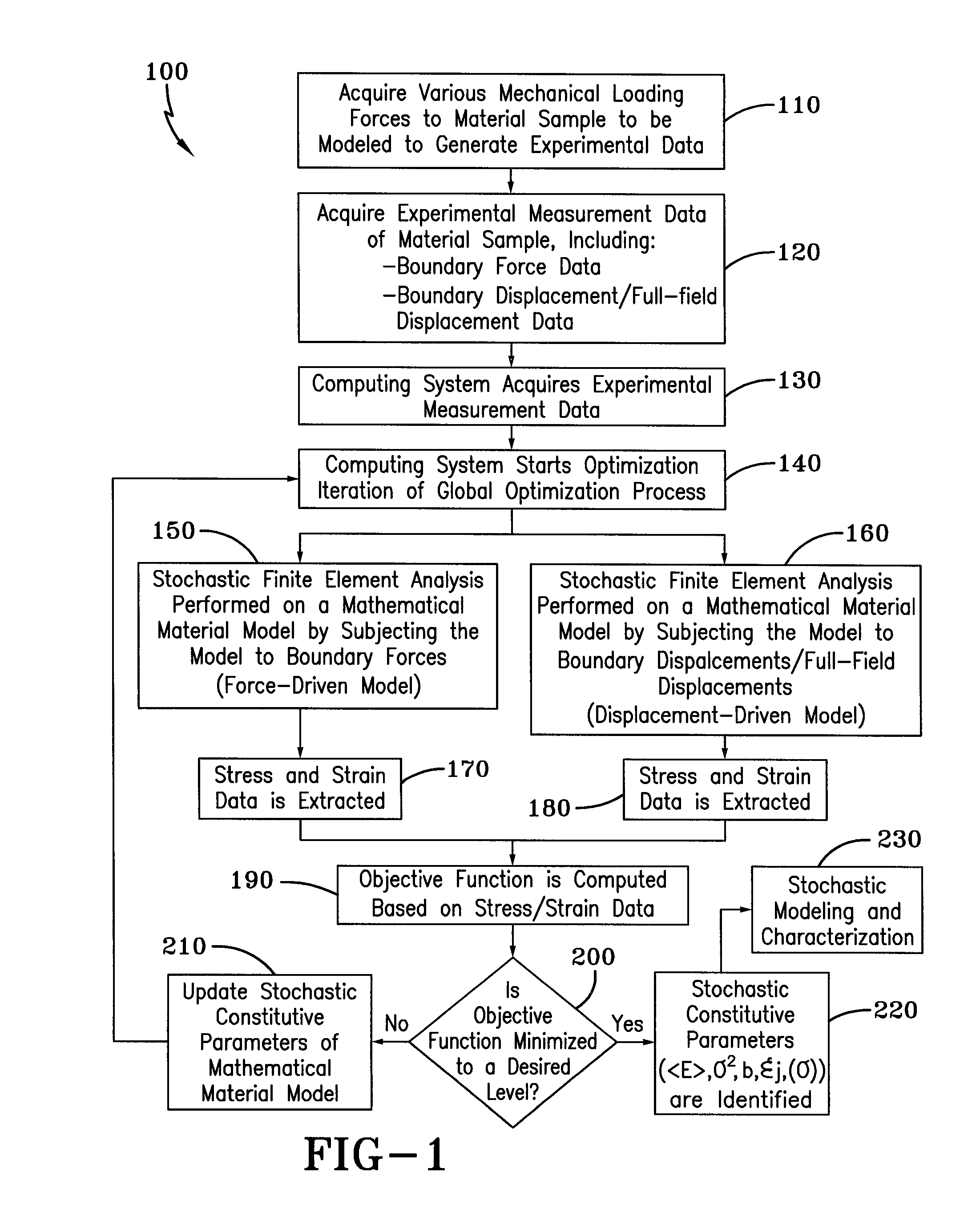
A method for identifying stochastic information of a heterogeneous material utilizes physical loading measurements that are input into a global optimization process. The optimization process executes, in parallel, a force-driven non-linear finite element simulation and a displacement-driven finite element simulation of a constitutive model of the heterogeneous material. The constitutive models model the spatially varying random material properties (i.e. stochastic properties) using the Karhunen-Loeve expansion, thereby introducing the stochastic parameters, including spatial mean, spatial variance, and correlation length for example into the models. Stress and strain values for both the force-driven and displacement driven finite element analyses are input into an objective function, whereupon the finite element simulations are updated after each iteration of the optimization process is performed until the objective function is minimized to a desired level. This results in the identification of optimized stochastic parameters associated with the heterogeneous material under investigation.
Owner:THE UNIVERSITY OF AKRON
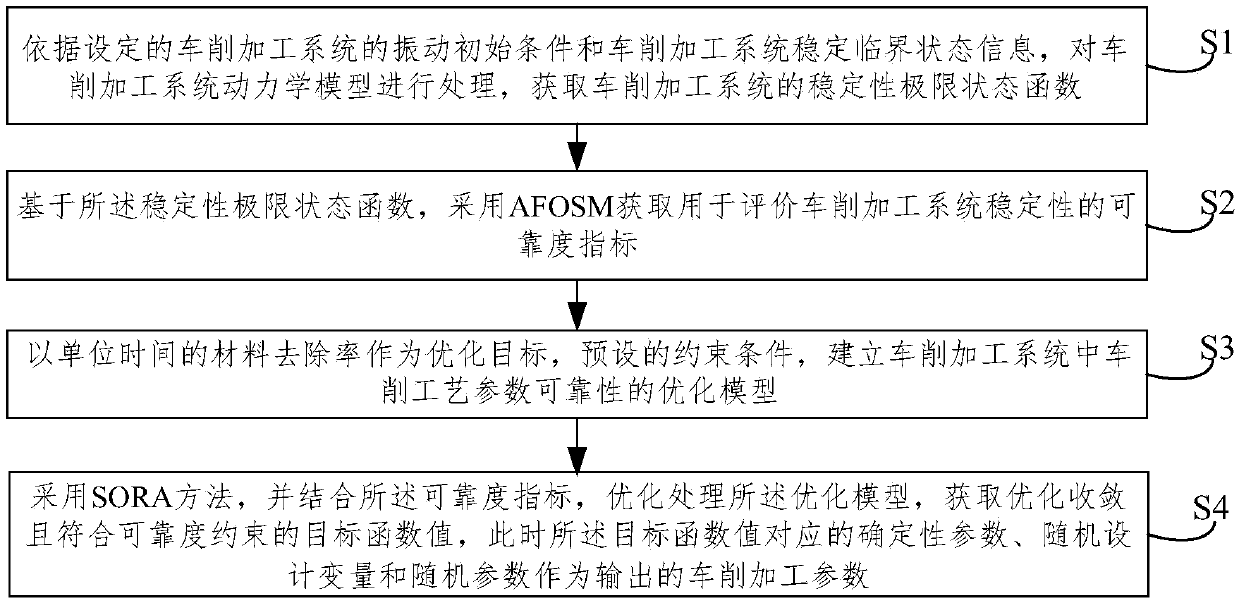
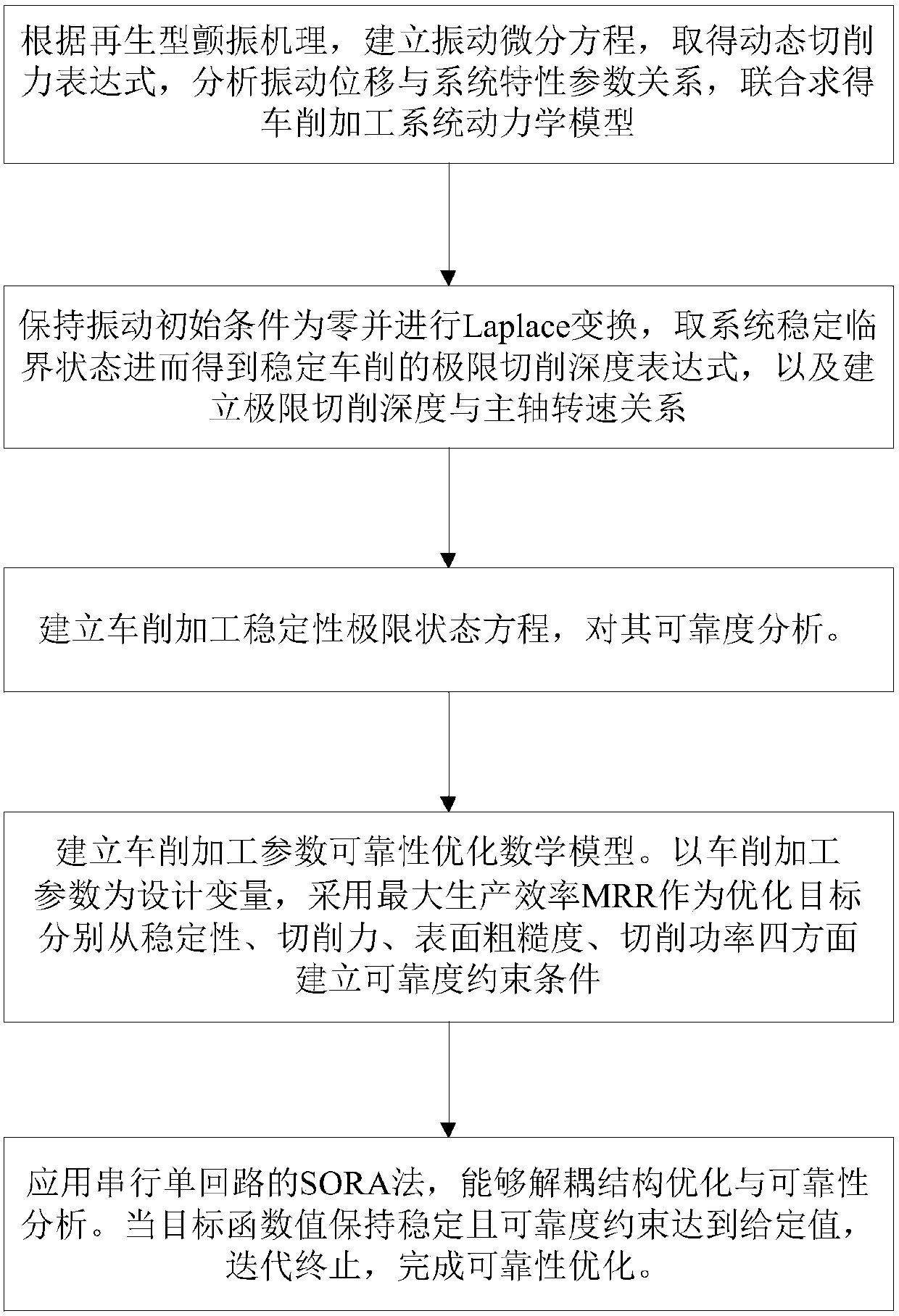
Turning machining parameter optimization method considering uncertain parameters,
InactiveCN107480354AGood turning parametersDesign optimisation/simulationSpecial data processing applicationsSystem stabilityDependability
The invention provides a turning machining parameter optimization method considering uncertain parameters. The method comprises the steps of obtaining a stability limit-state function according to preset initial vibration conditions and stability critical-state information of a turning machining system; adopting an AFOSM to obtain reliability indexes for evaluating the stability of the system; with MRR as preset constraint conditions of an optimization target, ,establishing an optimization model of the reliability of turning process parameters in the system, wherein the constraint conditions comprise reliability constraint conditions and stochastic design variable boundary constraint conditions; optimizing and processing the optimization model, and obtaining a target function value which is optimized and converged and meets the reliability constraint conditions, wherein certainty parameters, stochastic design variables and stochastic parameters which correspond to the target function value serve as output turning machining parameters. According to the method, the reliability can serve as an evaluation index and optimization condition, and the influences of uncertain factors on the turning process are analyzed in order to obtain the best turning machining parameters.
Owner:NORTHEASTERN UNIV
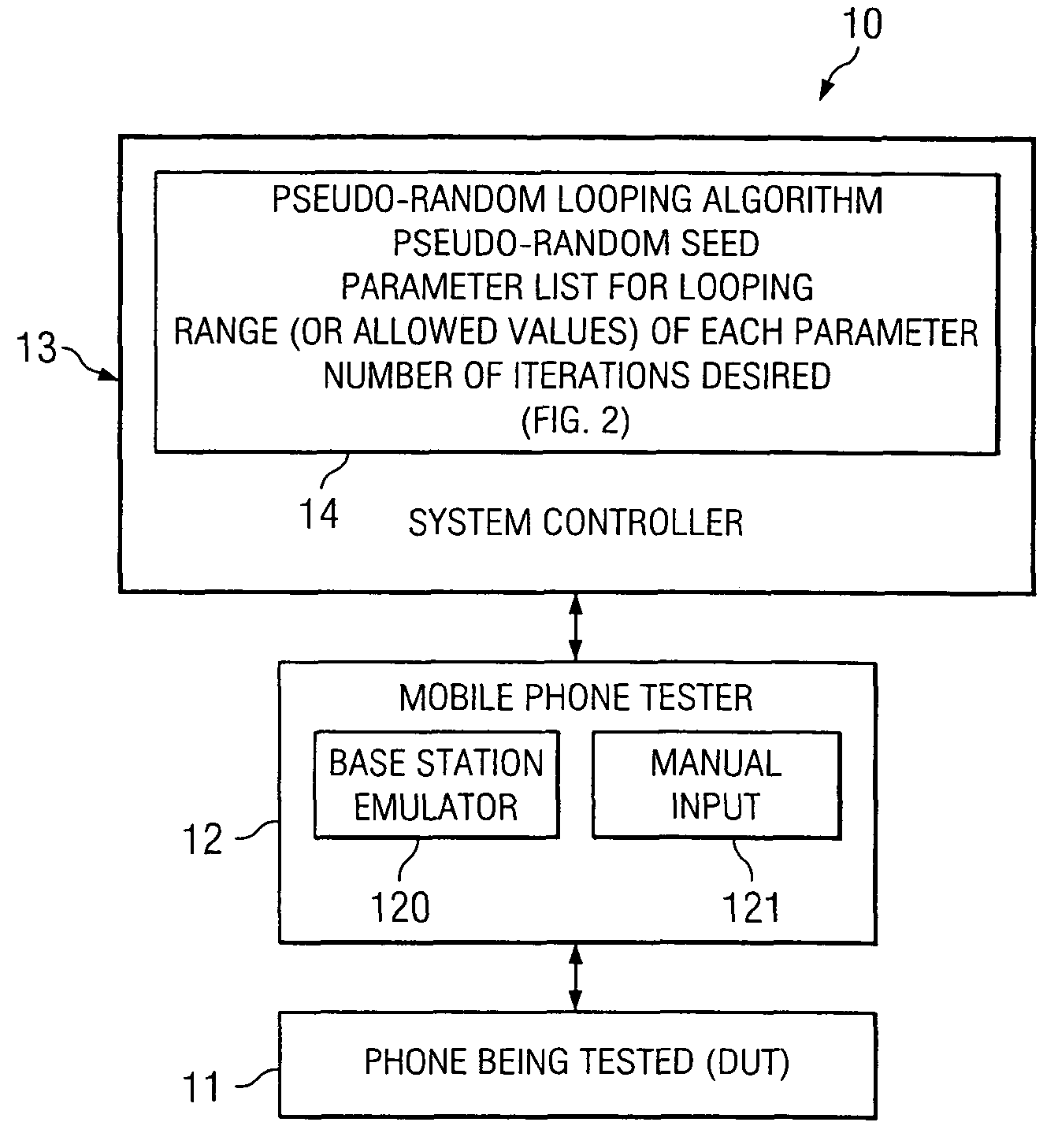
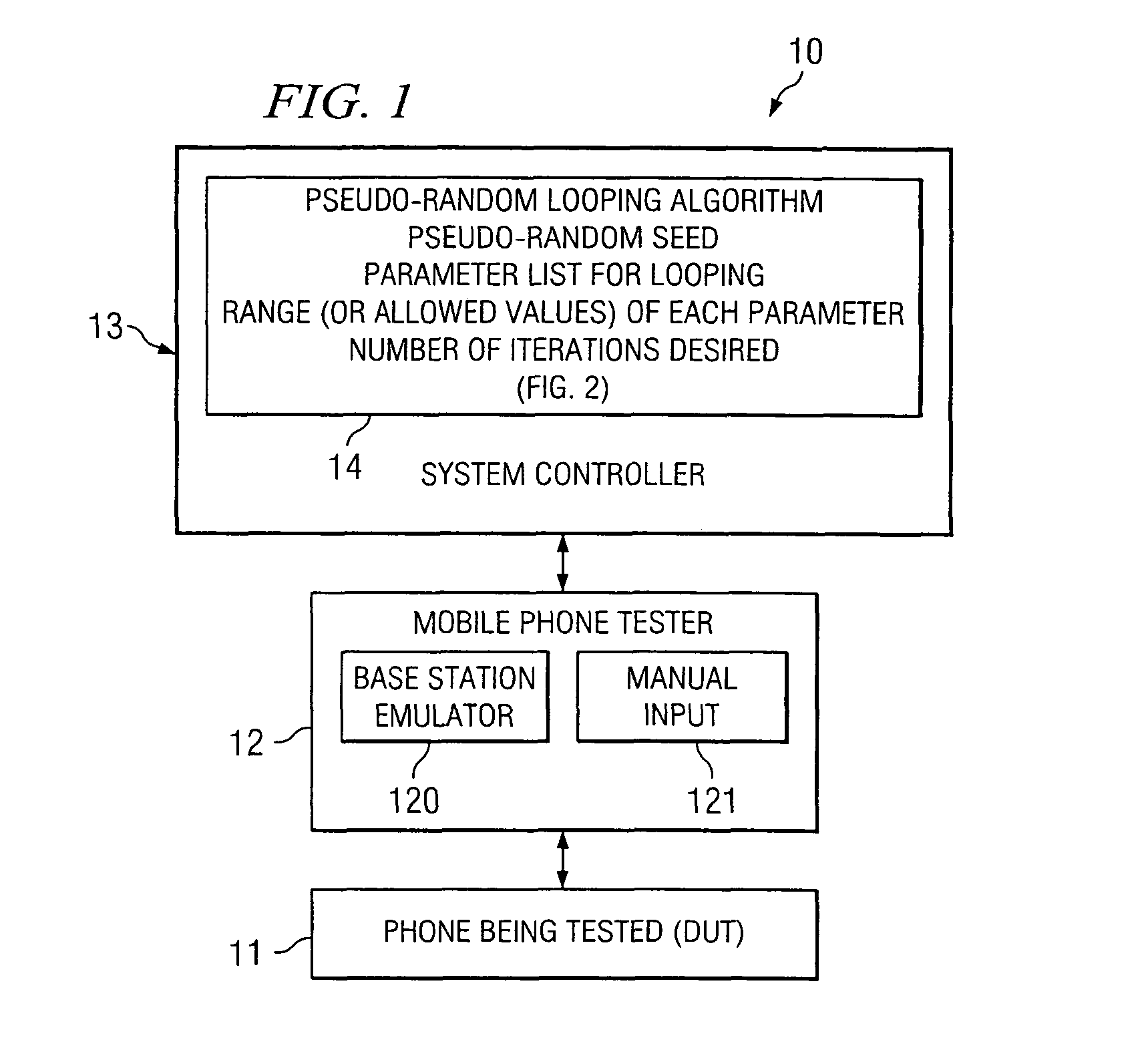
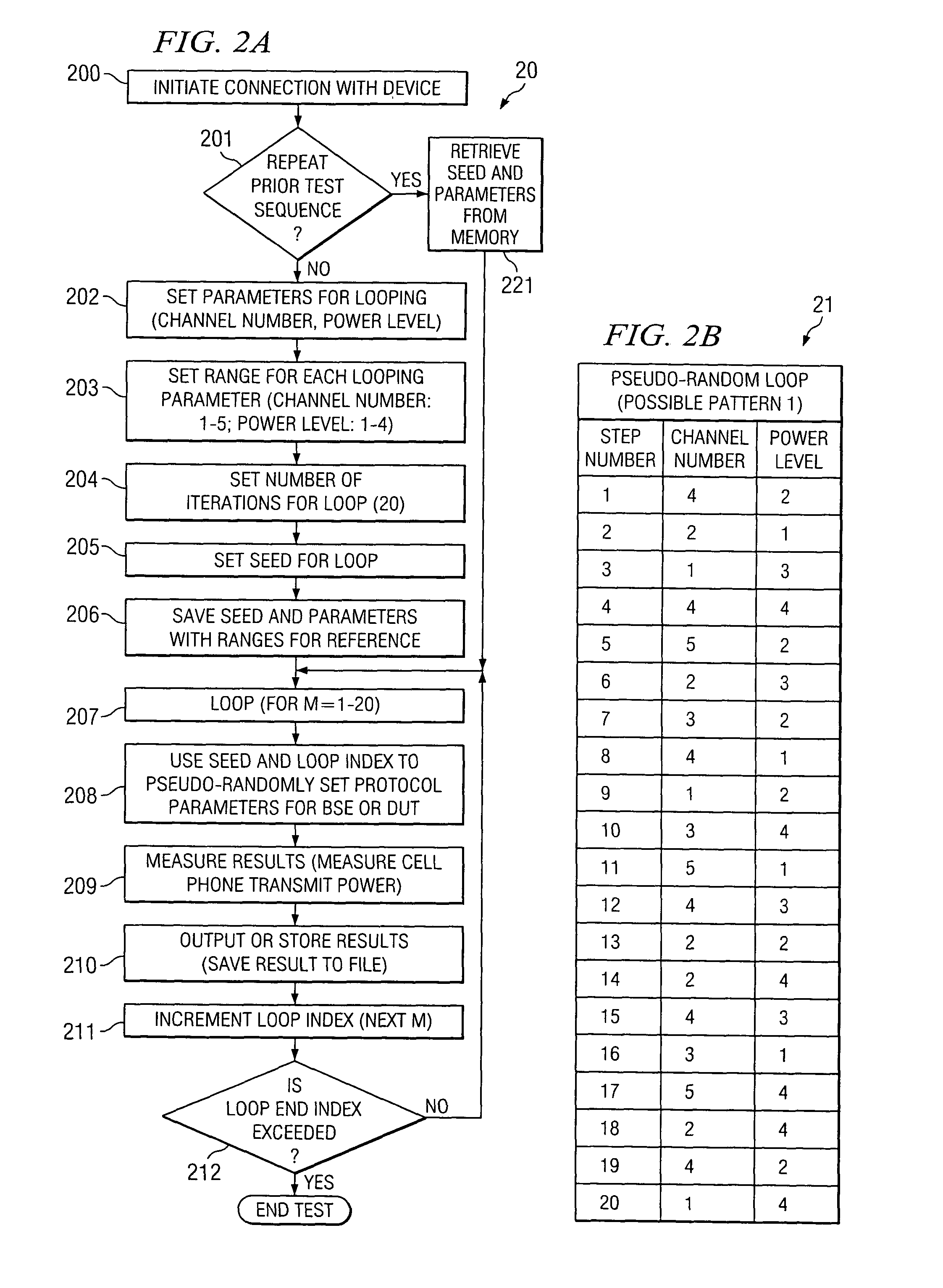
System and method for electronic device testing using random parameter looping
InactiveUS7363567B2Electronic circuit testingError detection/correctionComputer hardwareEquipment under test
Disclosed is a system and method for testing electronic devices which uses a random pattern for testing electronic devices. In one embodiment there is communicated to a device under test (DUT) a test sequence causing the DUT to exercise certain parameters in a controlled pattern of operation. The test sequence is randomly created. In one embodiment this random creation is controlled by a random looping algorithm which controls both the order of and the magnitude of each parameter. Included, if desired, is the ability to selectively retransmit previously communicated test sequences.
Owner:AGILENT TECH INC
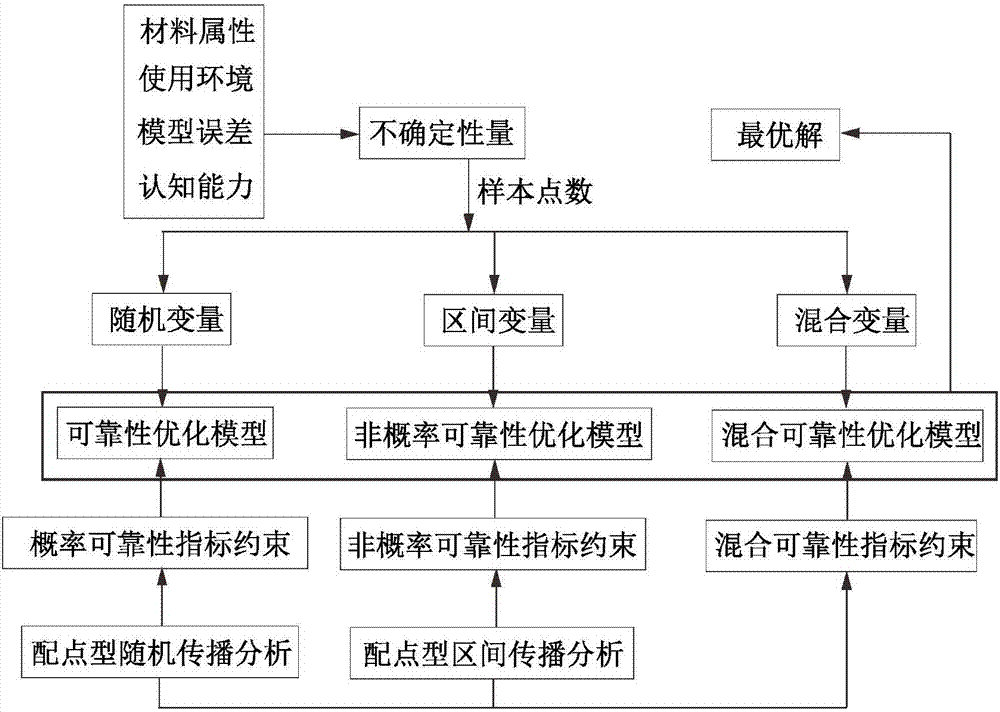
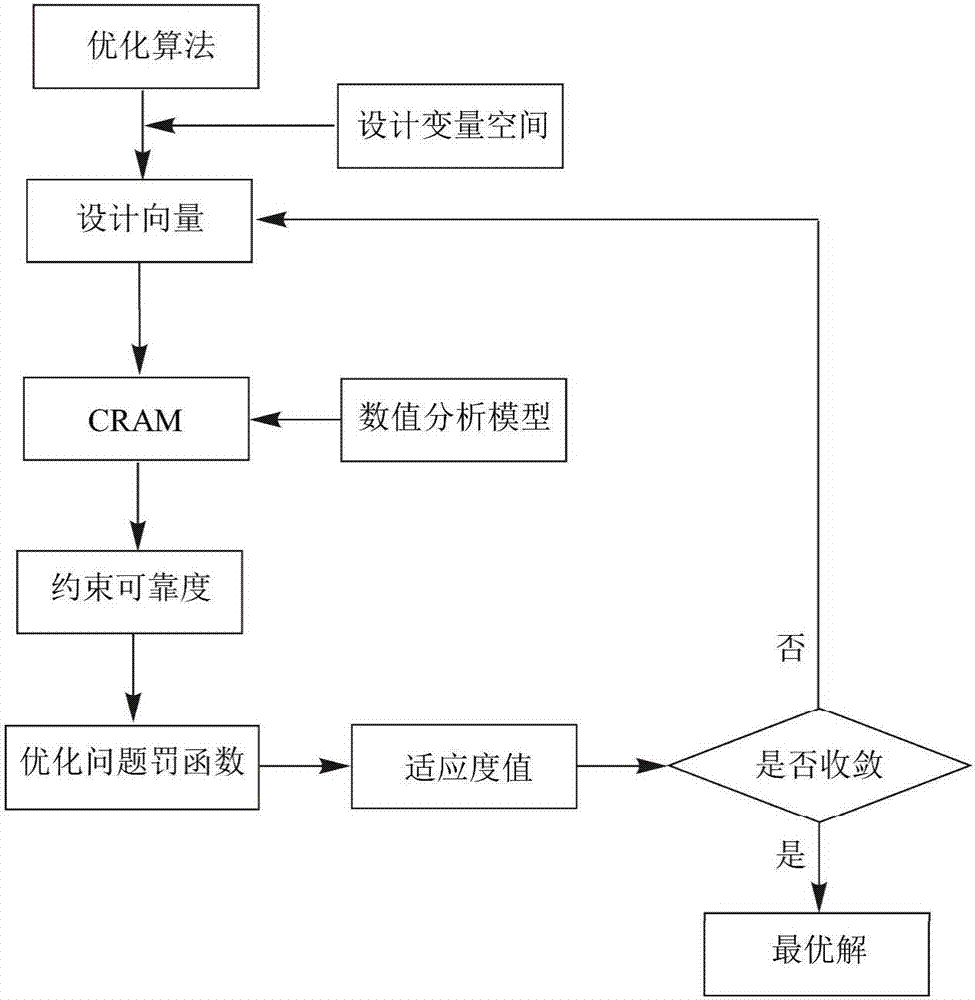
Engineering structure optimization design method used in uncertain environment
InactiveCN106909718AAvoid nested optimization problemsGeometric CADDesign optimisation/simulationInterval propagationStructural reliability
The invention provides an engineering structure optimization design method used in an uncertain environment, and relates to the technical field of engineering structure reliability optimization. According to the method, an uncertain engineering structure optimization design problem is defined first, an engineering structure and uncertain information in the use environment are described as random variables, interval variables or combinations of the random variables and the interval variables according to existing samples, corresponding optimization models are established according to different types of uncertain variables, reliability indexes in the optimization models are calculated on the basis of the point collocation random / interval propagation analysis method, and finally different optimization solvers are selected according to actual problems for outer layer optimization. Reliability indexes of an inner layer failure function are obtained through efficient uncertain propagation analysis, and formation of the nested optimization problem is avoided; hybrid uncertainty models including random parameters and interval parameters in the same problem are considered, and the method has a practical engineering significance in interval parameter optimization problem under random process stimulation.
Owner:SHENYANG AEROSPACE UNIVERSITY +1
Identification circuit and method for generating an identification bit using physical unclonable functions
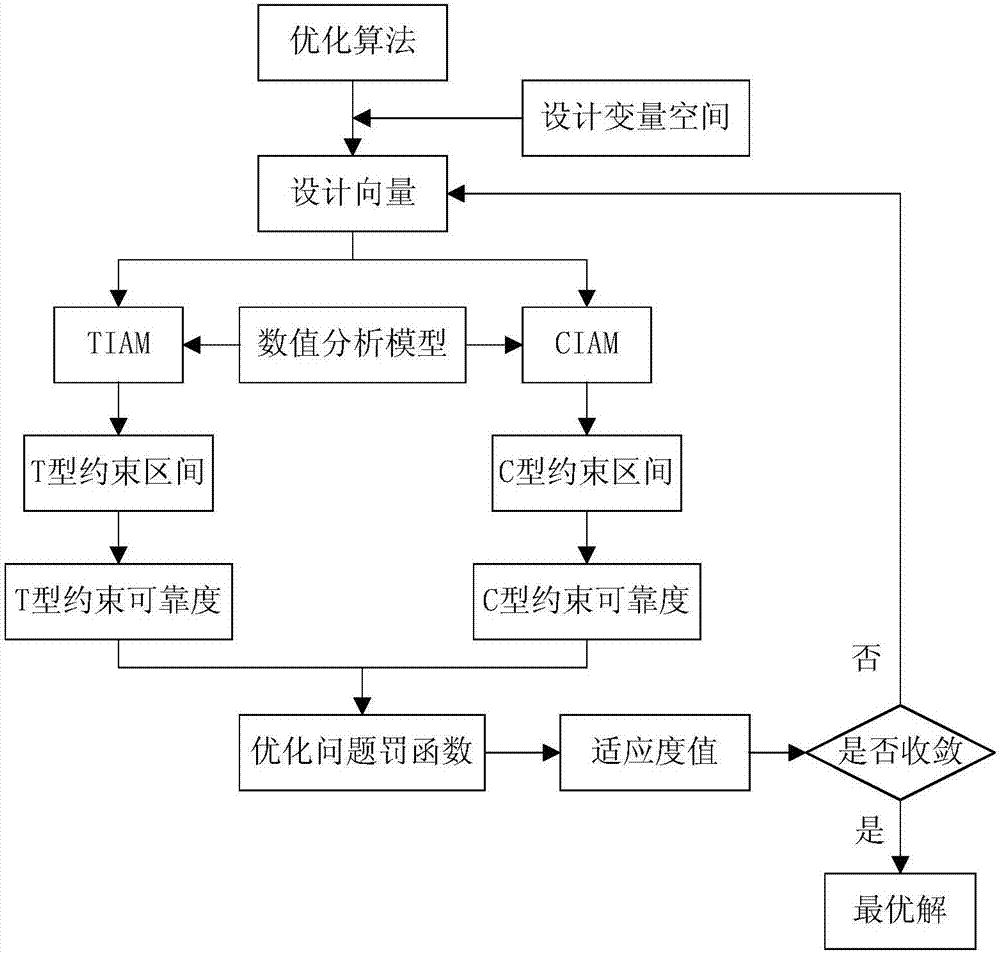
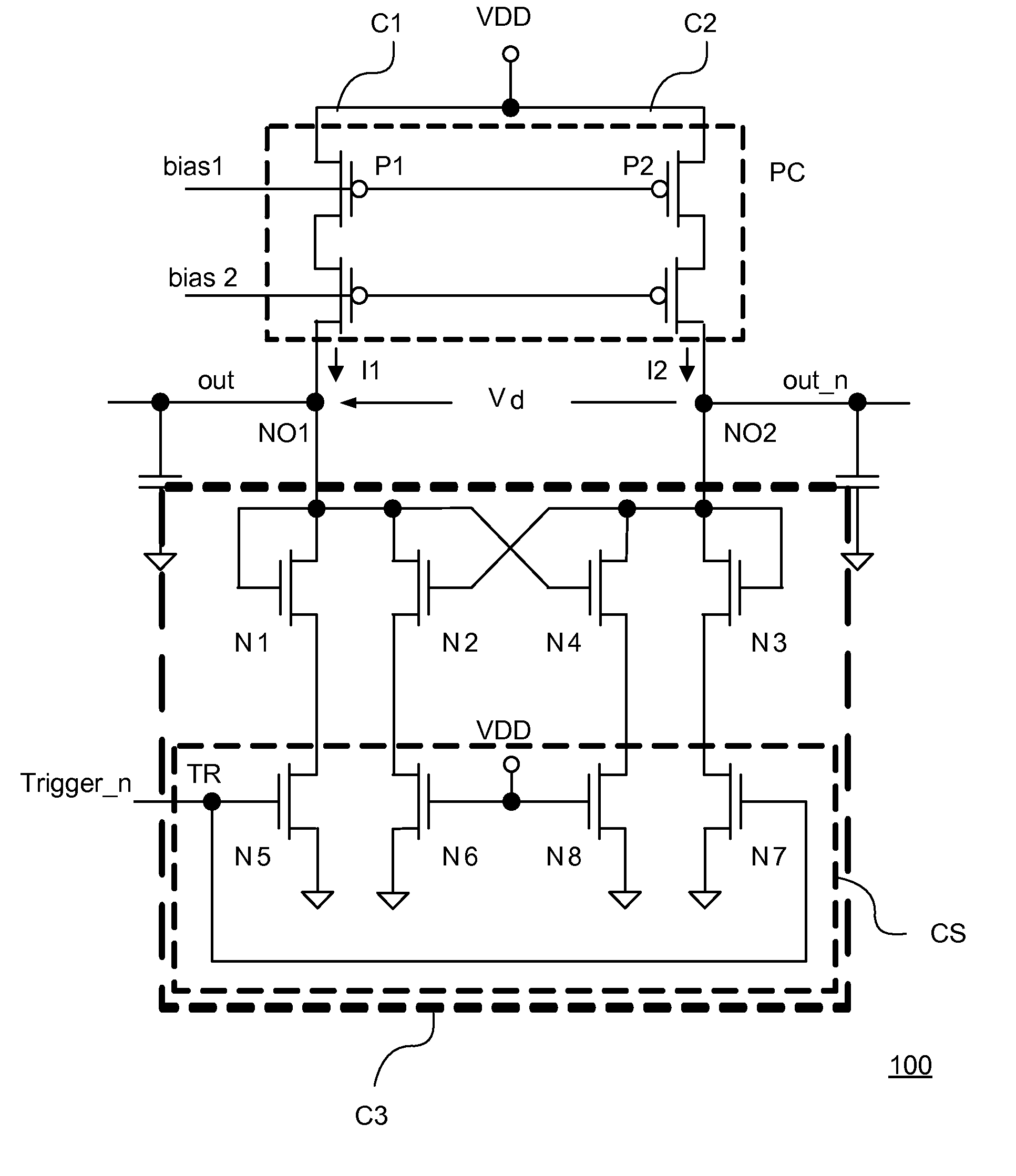
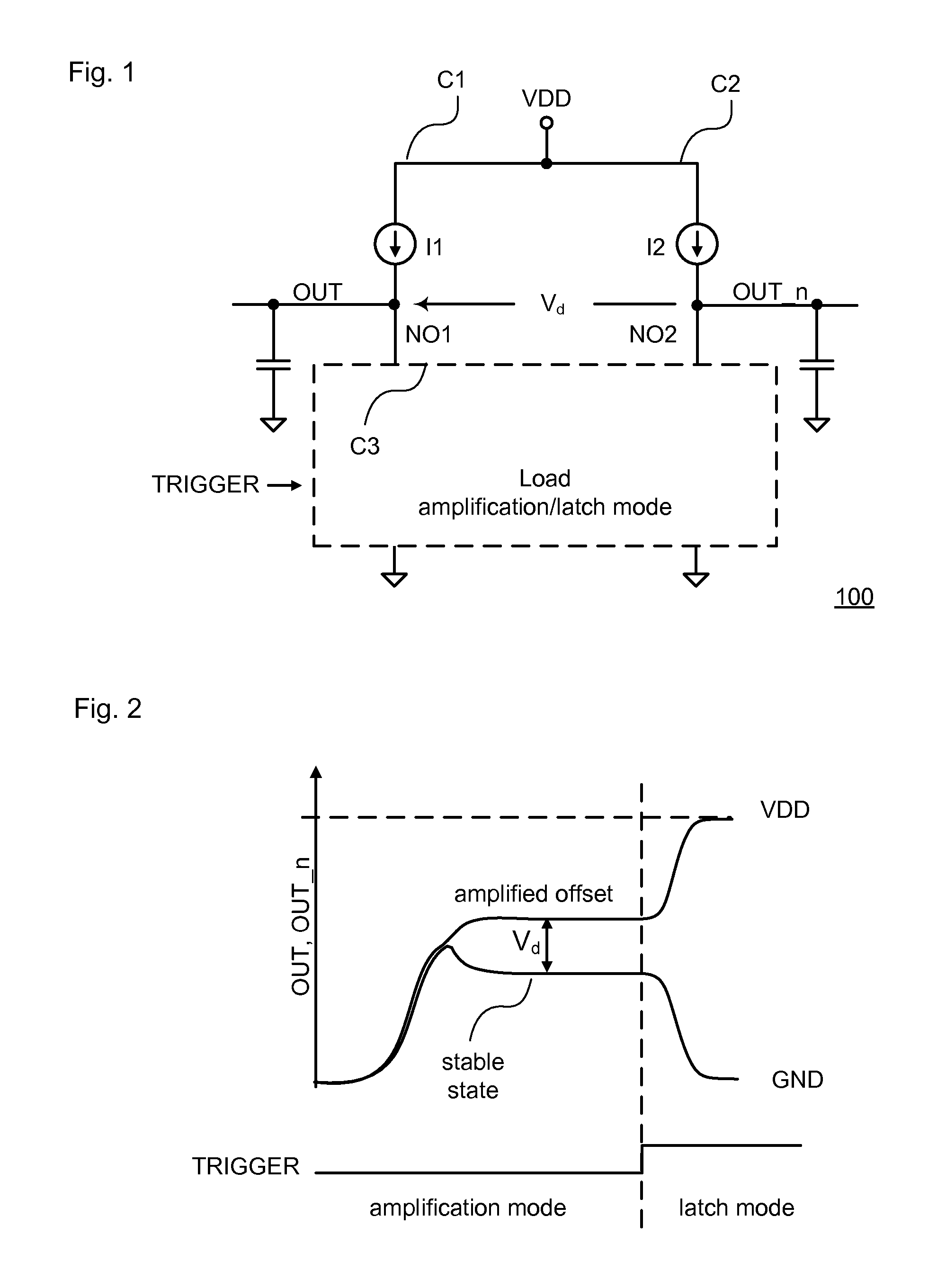
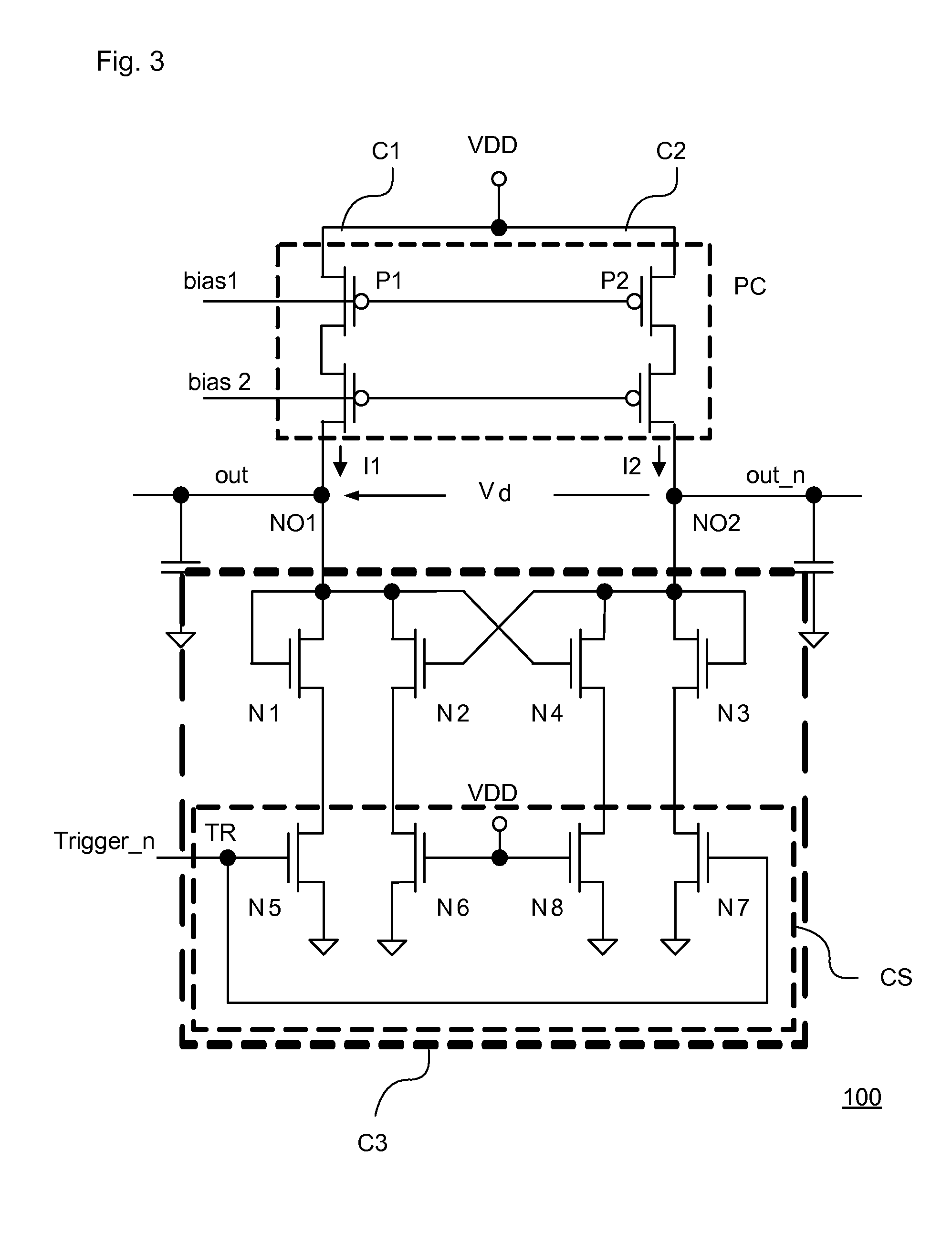
ActiveUS20120072476A1Reliability increasing modificationsSemiconductor/solid-state device detailsPhysical unclonable functionRandom parameters
An embodiment of the present invention is an identification circuit installed on an integrated circuit for generating an identification bit, comprising a first circuit to generate a first output signal that is based on random parametric variations in said first circuit, a second circuit to generate a second output signal that is based on random parametric variations in said second circuit, a third circuit capable to be operated in an amplification mode and in a latch mode, wherein in said amplification mode the difference between the first output signal and the second output signal is amplified to an amplified value and, wherein in said latch mode said amplified value is converted into a digital signal.
Owner:INFINEON TECH AG
Method, device and terminal for card personalization over the air
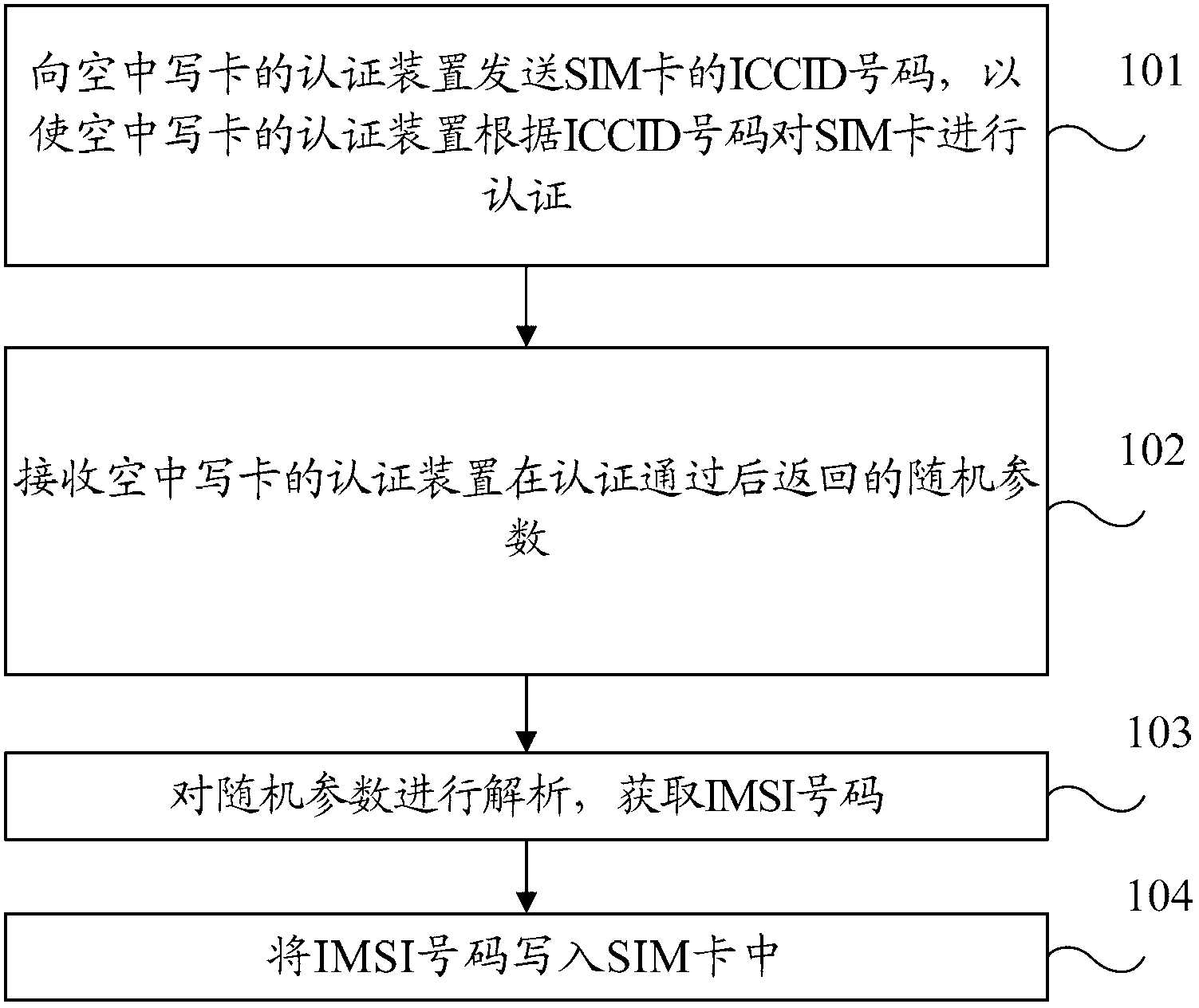
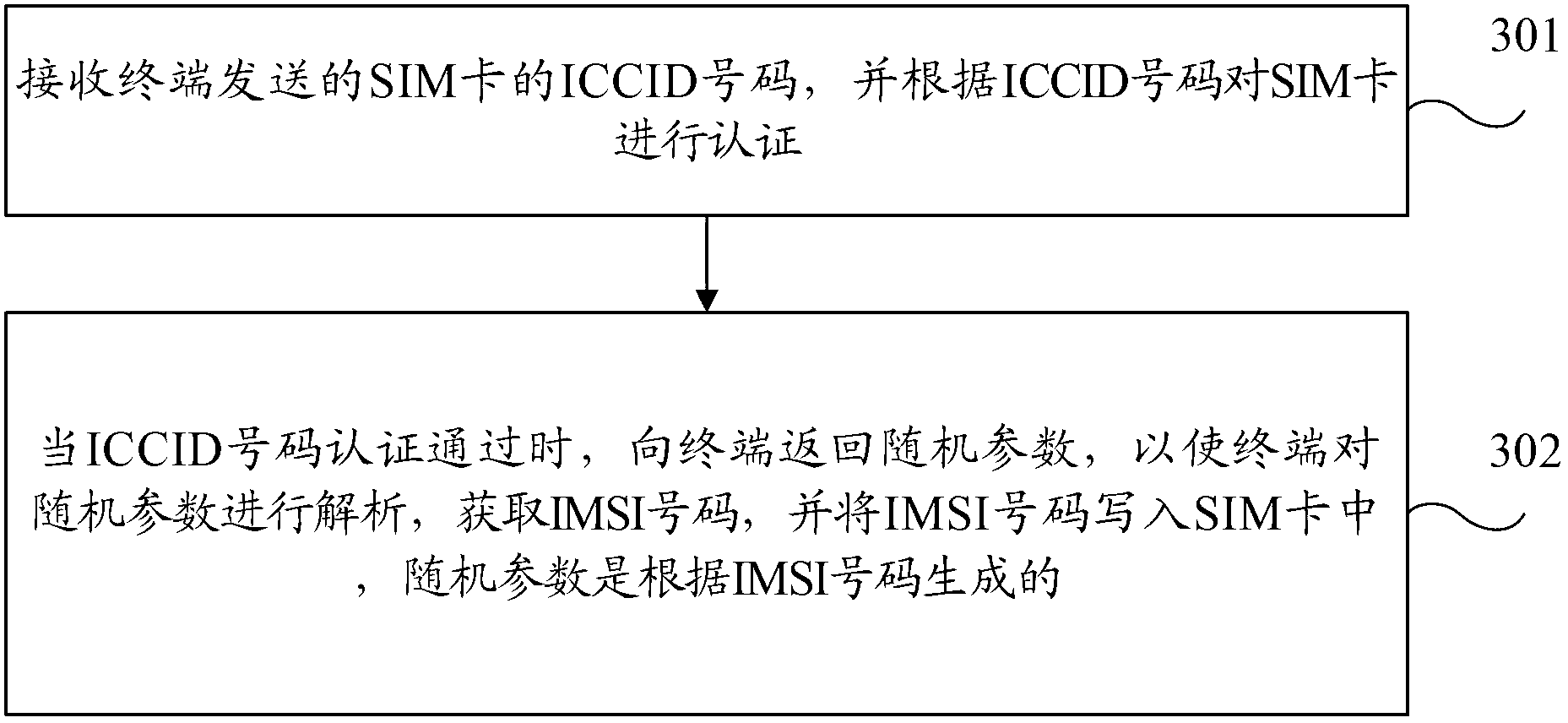
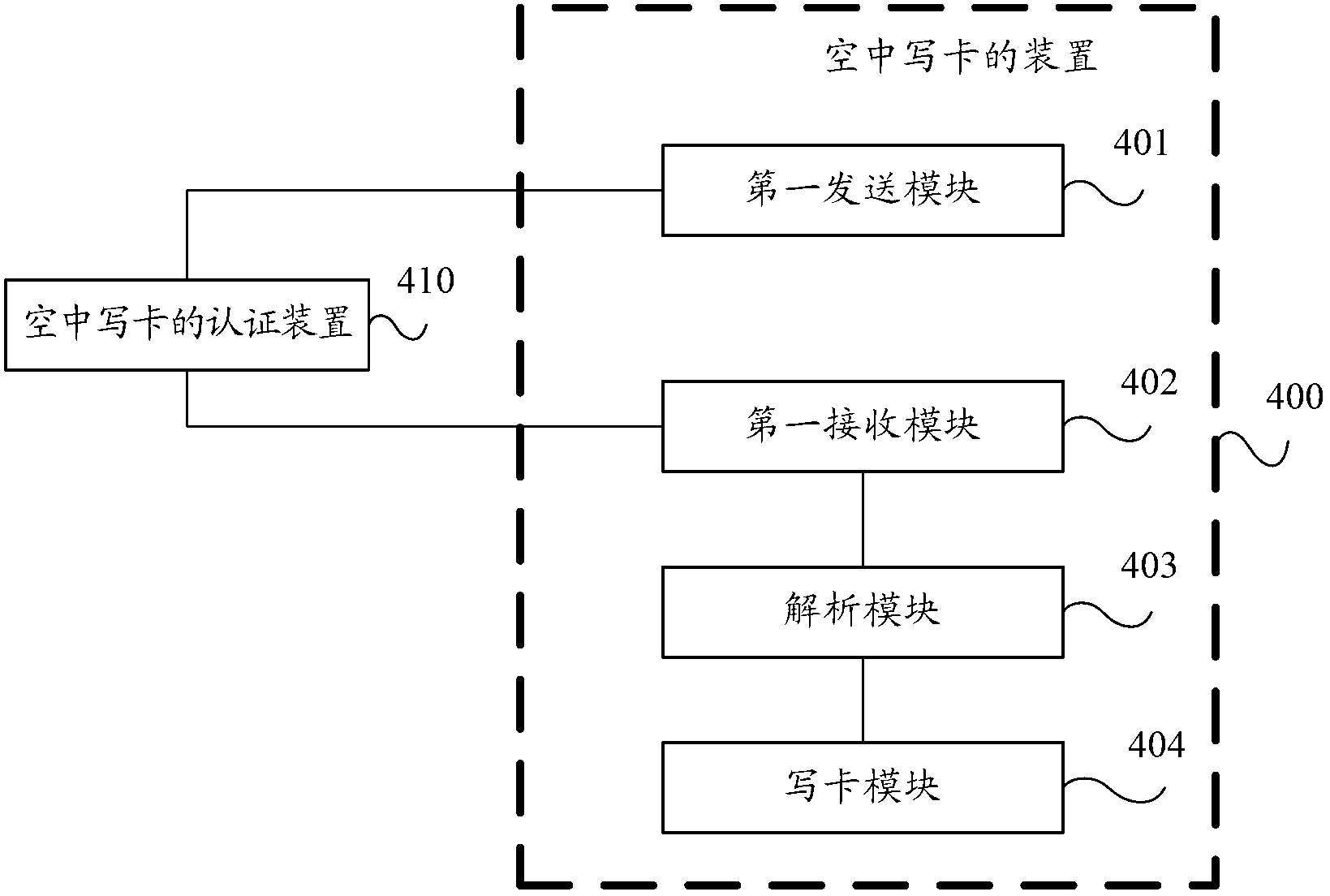
ActiveCN102711096AAvoid occupyingAvoid the phenomenon of wasting IMSI number resourcesSecurity arrangementNetwork data managementPersonalizationRandom parameters
The invention provides a method, a device and a terminal for card personalization over the air. The method comprises the following steps of: transmitting an integrated circuit card identity (ICCID) of a subscriber identity module (SIM) card to an authentication device for the card personalization over the air, so that the authentication device for the card personalization over the air authenticates the SIM card according to the ICCID; receiving a random parameter from the authentication device for the card personalization over the air after the SIM card passes the authentication, wherein the random parameter is generated according to an international mobile subscriber identification (IMSI) number; resolving the random parameter, and acquiring the IMSI number; and writing the IMSI number into the SIM card. According to the method, the device and the terminal for the card personalization over the air, the waste of IMSI number resources can be avoided.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Reliability robust design method for multi-failure mode of superdeep well lifting container
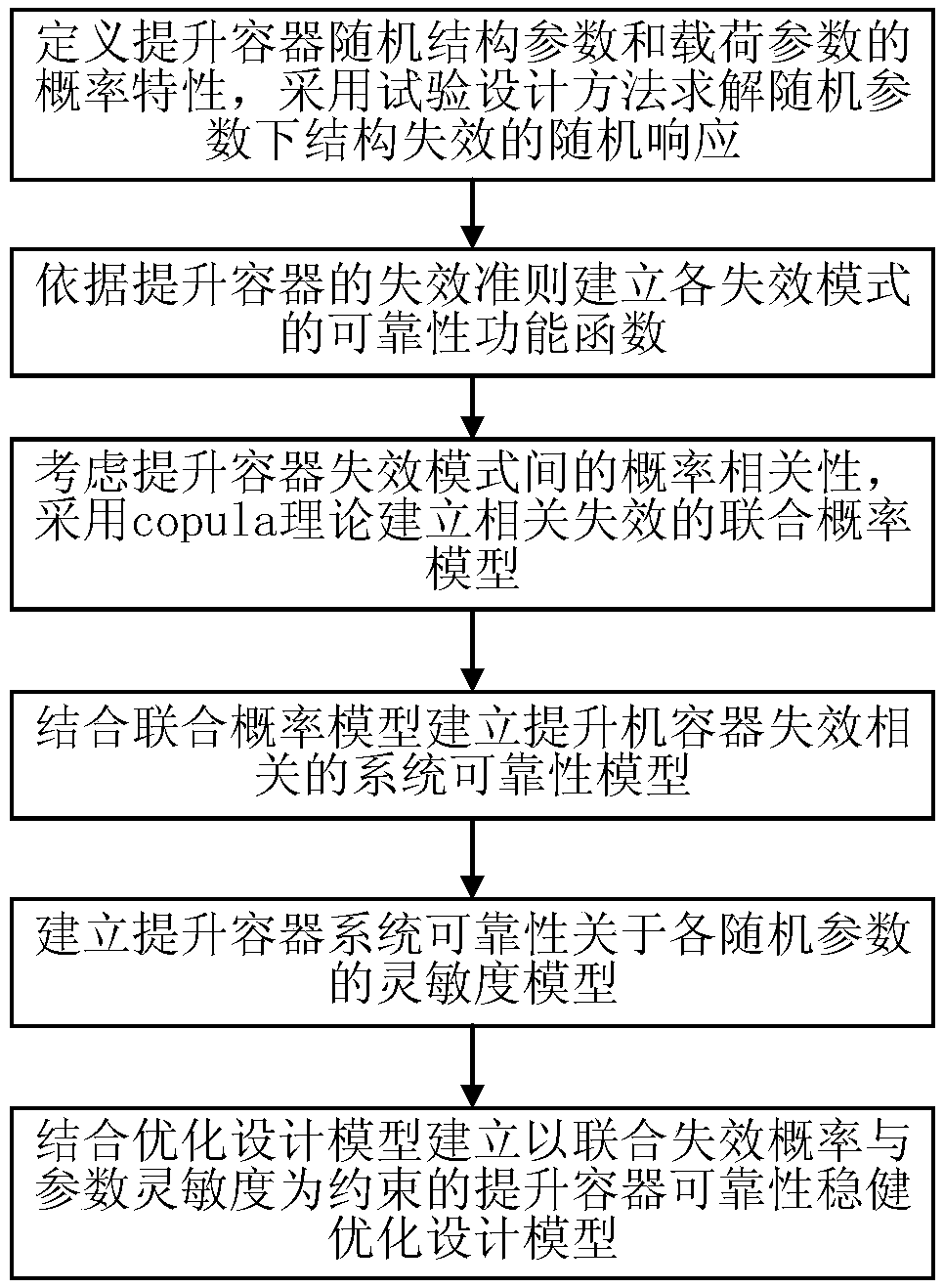
PendingCN107832511AImprove modeling efficiencyImprove calculation accuracyGeometric CADDesign optimisation/simulationPerformance functionDependability
The invention discloses a reliability robust design method for a multi-failure mode of a superdeep well lifting container. The method includes the following steps of (1) determining structural parameters, material properties and dynamic load randomness of the lifting container, and adopting an experiment design method for figuring out a random response to a structure failure under random parameters; (2) according to a failure criterion of the lifting container, creating a reliability performance function under each failure mode; (3) taking the probability correlation among the failure modes into account, and adopting a copula theory for creating a combined probability model of correlative failures; (4) creating a system reliability model correlative with failures of the lifting container under the combination of the combined probability model; (5) creating a sensitivity model of the system reliability of the lifting container for each random parameter; (6) under the combination of an optimization design model, creating a lifting container reliability robust optimization design model with the combined failure probability and parameter sensitivity as constrains.
Owner:CHINA UNIV OF MINING & TECH
Authentication method used for open interface calling
ActiveCN105634743AAvoid the risk of being intercepted and maliciously misappropriatedImprove securityUser identity/authority verificationAuthentication serverRandom parameters
The invention provides an authentication method used for open interface calling. The method comprises the steps that an application operating on a user terminal performs initial registration operation on an open interface service operation platform before initiation of a calling request for the first time so as to acquire an ID and a key; the application dynamically creates a token based on random parameters when the calling request is initiated and constructs the calling request through combination of the created token and the ID and the key and then transmits the calling request to an open interface provider server; and the open interface provider server receives the calling request and then transmits the calling request to an authentication server to perform authentication of the calling request and provides an open interface required by the calling request to the application under the condition that the authentication server transmits back a message indicating success of authentication. The method has high security and is convenient to operate.
Owner:CHINA UNIONPAY
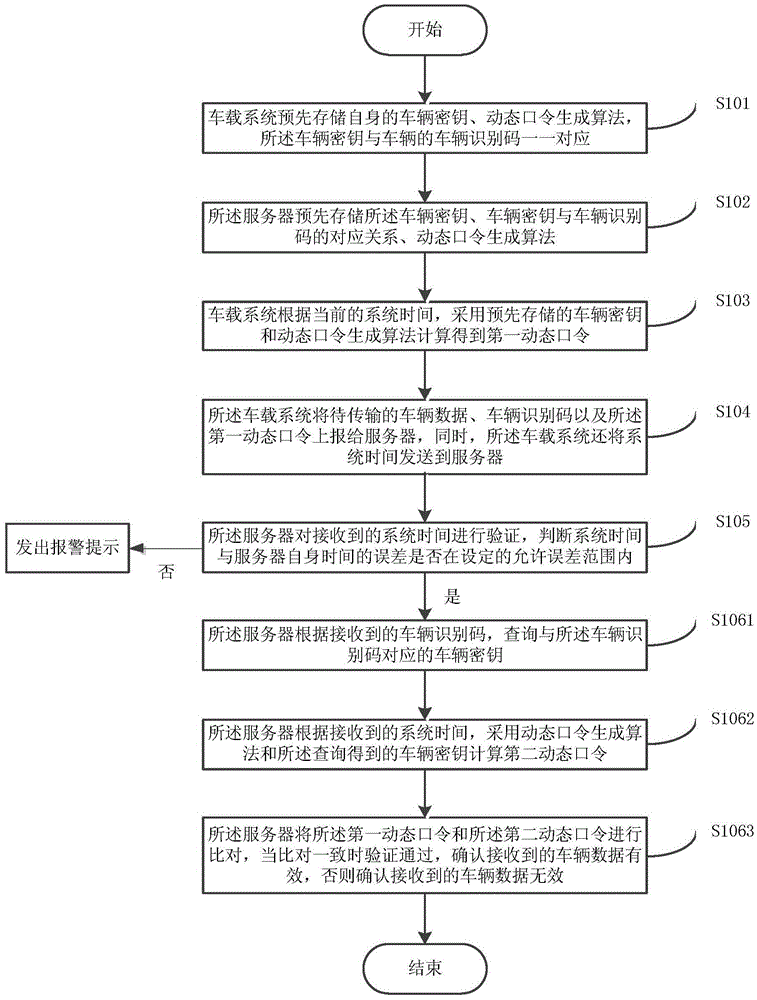
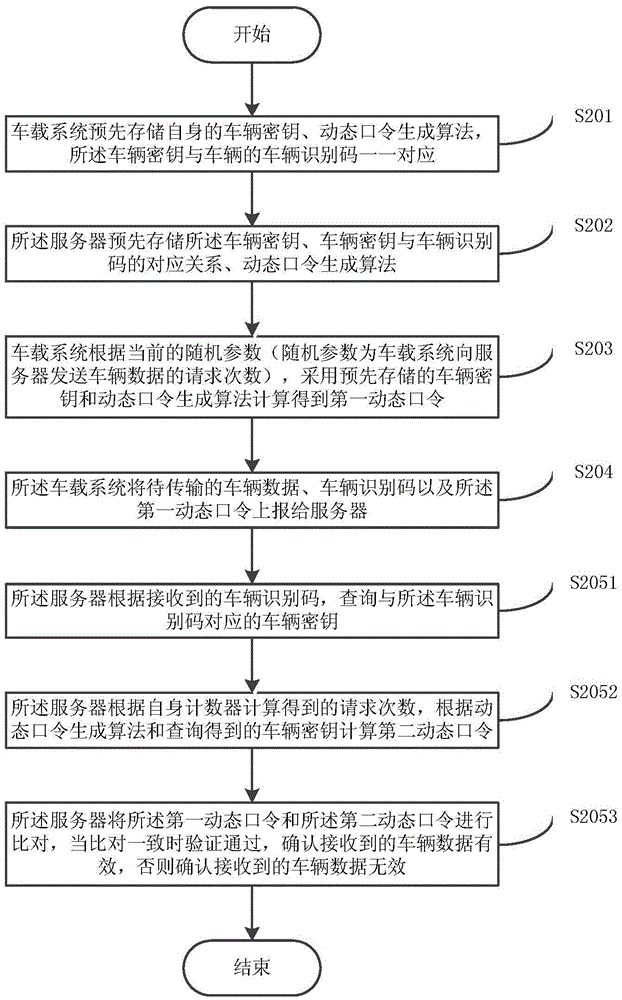
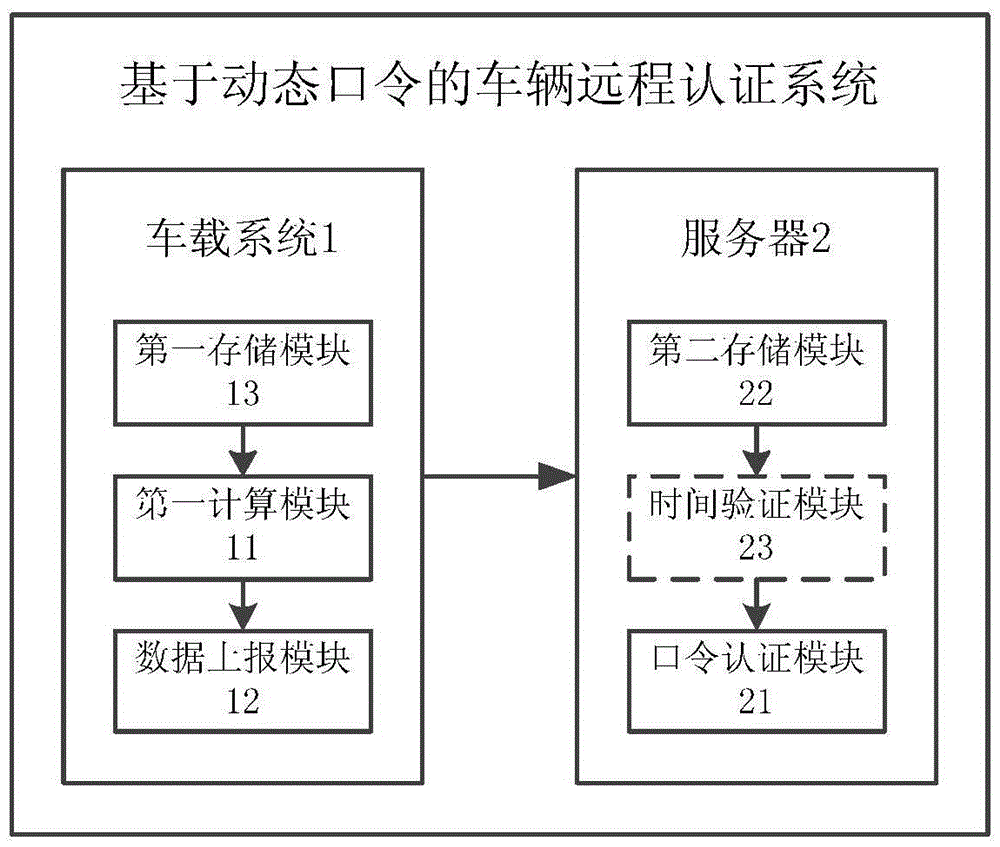
Vehicle remote authentication method based on dynamic password and vehicle remote authentication system thereof
InactiveCN105916143AGuaranteed unpredictabilityEnsure safetyNetwork topologiesTransmissionPasswordRandom parameters
The invention discloses a vehicle remote authentication method based on a dynamic password and a vehicle remote authentication system thereof. The method comprises the steps that step A: a vehicle-mounted system obtains a first dynamic password through calculation by adopting a pre-stored vehicle secret key and a dynamic password generation algorithm according to current random parameters; step B: the vehicle-mounted system reports vehicle data to be transmitted, a vehicle identification code and the first dynamic password to a server; and step C: the server verifies the first dynamic password, and the received vehicle data are determined to be effective if verification is passed, or the received vehicle data are determined to be ineffective. According to the vehicle remote authentication method based on the dynamic password and the vehicle remote authentication system thereof, the dynamic password generated each time is different due to difference of the random parameters in each time of authentication. Unpredictability of the password each time is guaranteed by the randomness of the parameters in each time of calculation so that the security of the system is guaranteed in the basic link of password authentication.
Owner:LE SHI ZHI ZIN ELECTRONIC TECHNOLOGY (TIANJIN) LTD
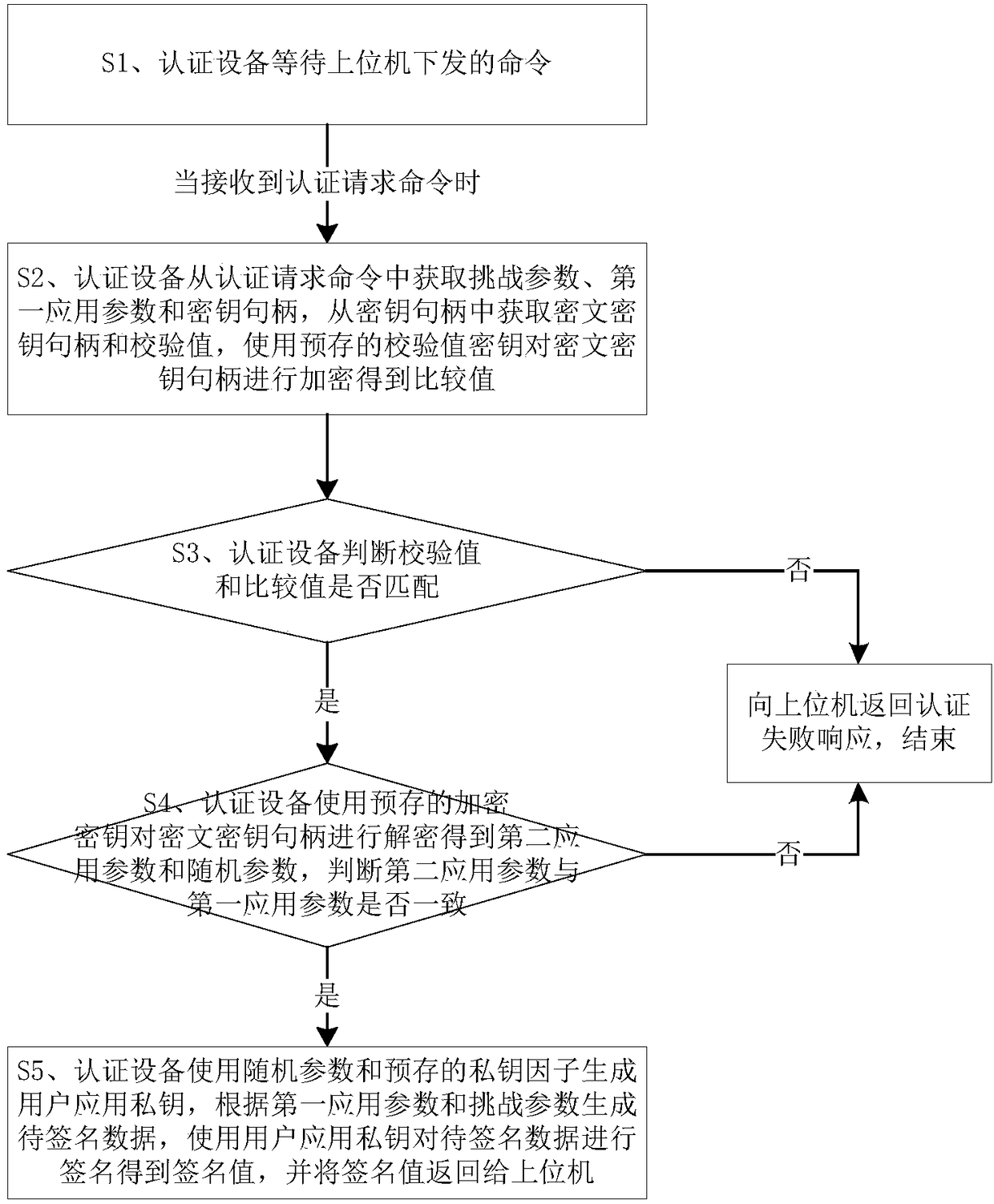
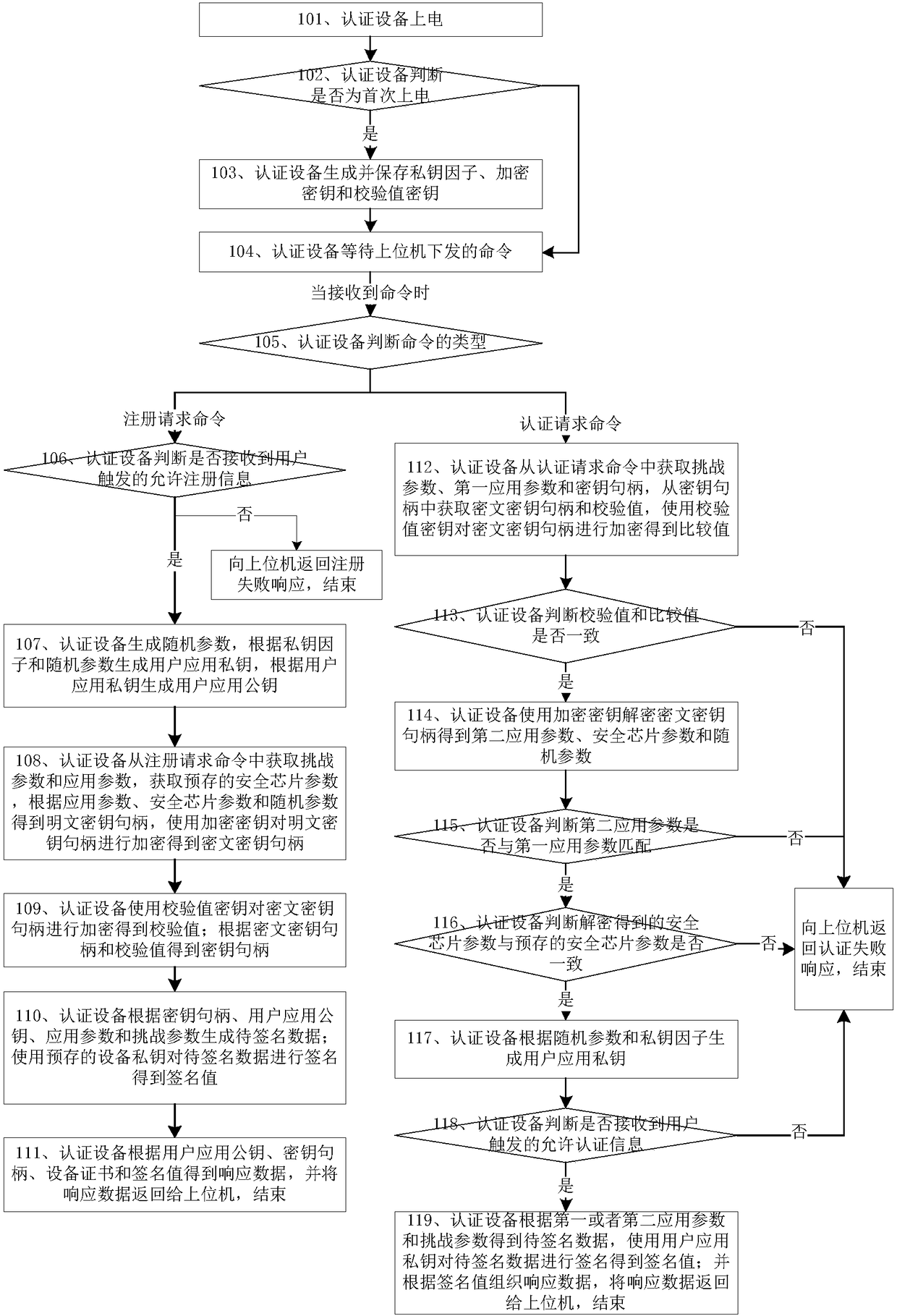
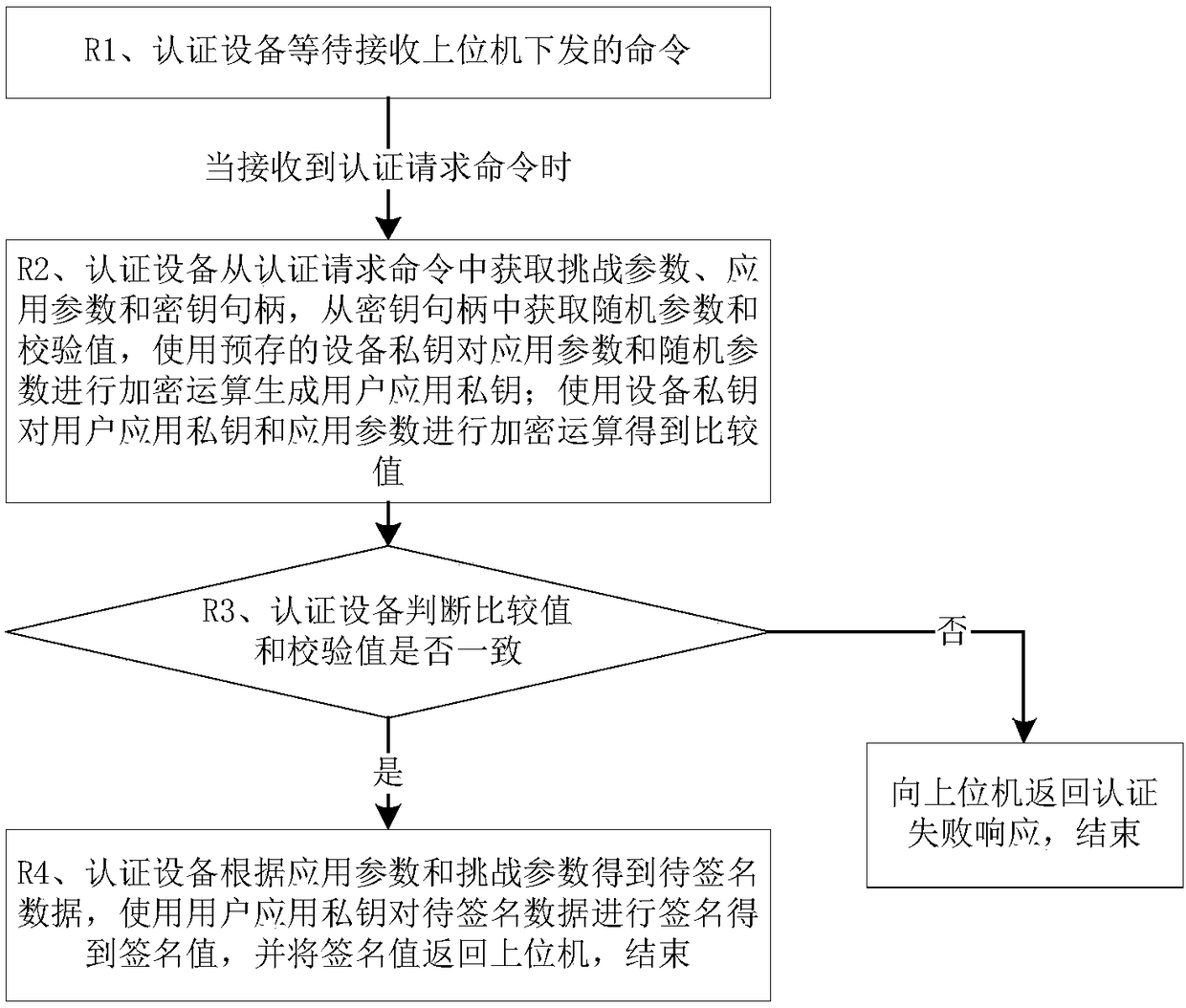
Authentication equipment and working method thereof
The invention relates to the communication field, in particular to authentication equipment and a working method thereof. The method comprises the steps that when the authentication equipment receivesan authentication request command, the authentication equipment acquires a challenge parameter, a first application parameter and a key handle from the authentication request command, acquires a ciphertext key handle and a verification value from the key handle and encrypts the ciphertext key handle by using a pre-stored verification value key to obtain a comparison value; whether or not the verification value and the comparison value are matched is judged; if the verification value and the comparison value are matched, the ciphertext key handle is decrypted by using a pre-stored encryption key to obtain a second application parameter and a random parameter, and whether or not the second application parameter is consistent with the first application parameter is judged; when the second application parameter is consistent with the first application parameter, a user application private key is generated by using the random parameter and a pre-stored private key factor, to-be-signatureddata is generated according to the first application parameter and the challenge parameter and signatured by using the user application private key to obtain a signature value, and the signature valueis returned to an upper computer. The method is small in occupied memory, more safe and more reliable.
Owner:FEITIAN TECHNOLOGIES
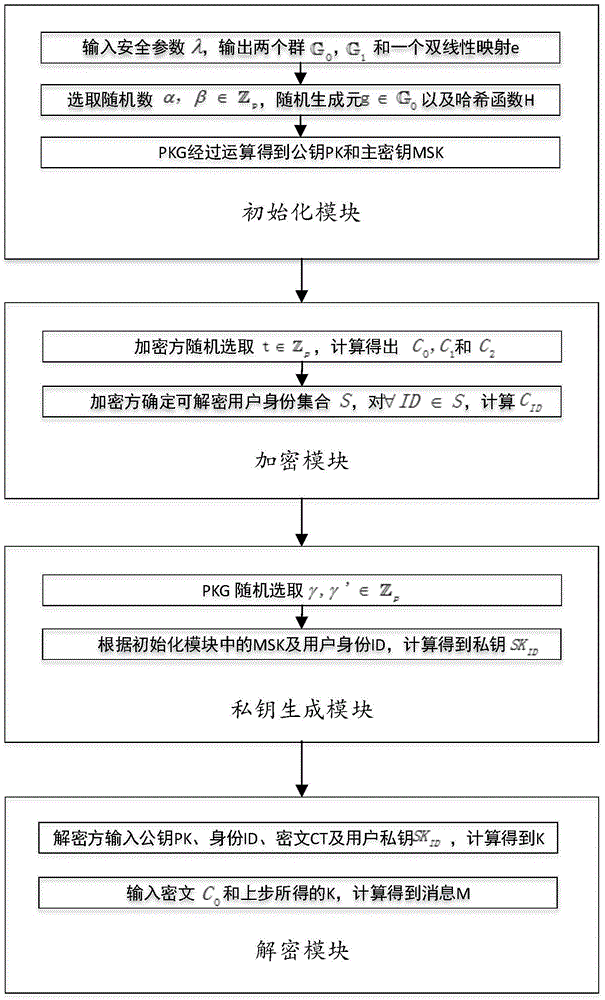
A method for realizing identity-based broadcast encryption by ciphertext-policy attribute-based encryption
ActiveCN104135473AShorten the development cycleReduce system loadPublic key for secure communicationPlaintextAttribute-based encryption
There is provided a method for realizing identity-based broadcast encryption by ciphertext-policy attribute-based encryption. The steps of the method are as follows: in step 1, a PKG (Private Key Generator) inputs a safety coefficient of a system to output an initialization parameter; in step 2, the PKG runs a random number generation algorithm to choose a random number required for the system; in step 3, the PKG executes operation to obtain a public key and a master secret key; in step 4, an encrypting party chooses the random number and completes operation to output a part of ciphertext; in step 5, the encrypting party executes calculation according to a set of identities of decrypting users to obtain the remaining part of the ciphertext; in step 6, the PKG runs a random number generation algorithm to obtain a random parameter; in step 7, the PKG executes calculation according to the master secret key and the identity of the user to obtain a private key SKID; in step 8, a decrypting party conforming to requirement is able to execute calculation according to the private key and the ciphertext to obtain K; and in step 9, the decrypting user is able to output correct plaintext by executing calculation according to the K. According to the invention, a development cycle and system load are reduced greatly, and chosen ciphertext attack can be resisted, which ensures safety and effectiveness of the scheme.
Owner:BEIHANG UNIV
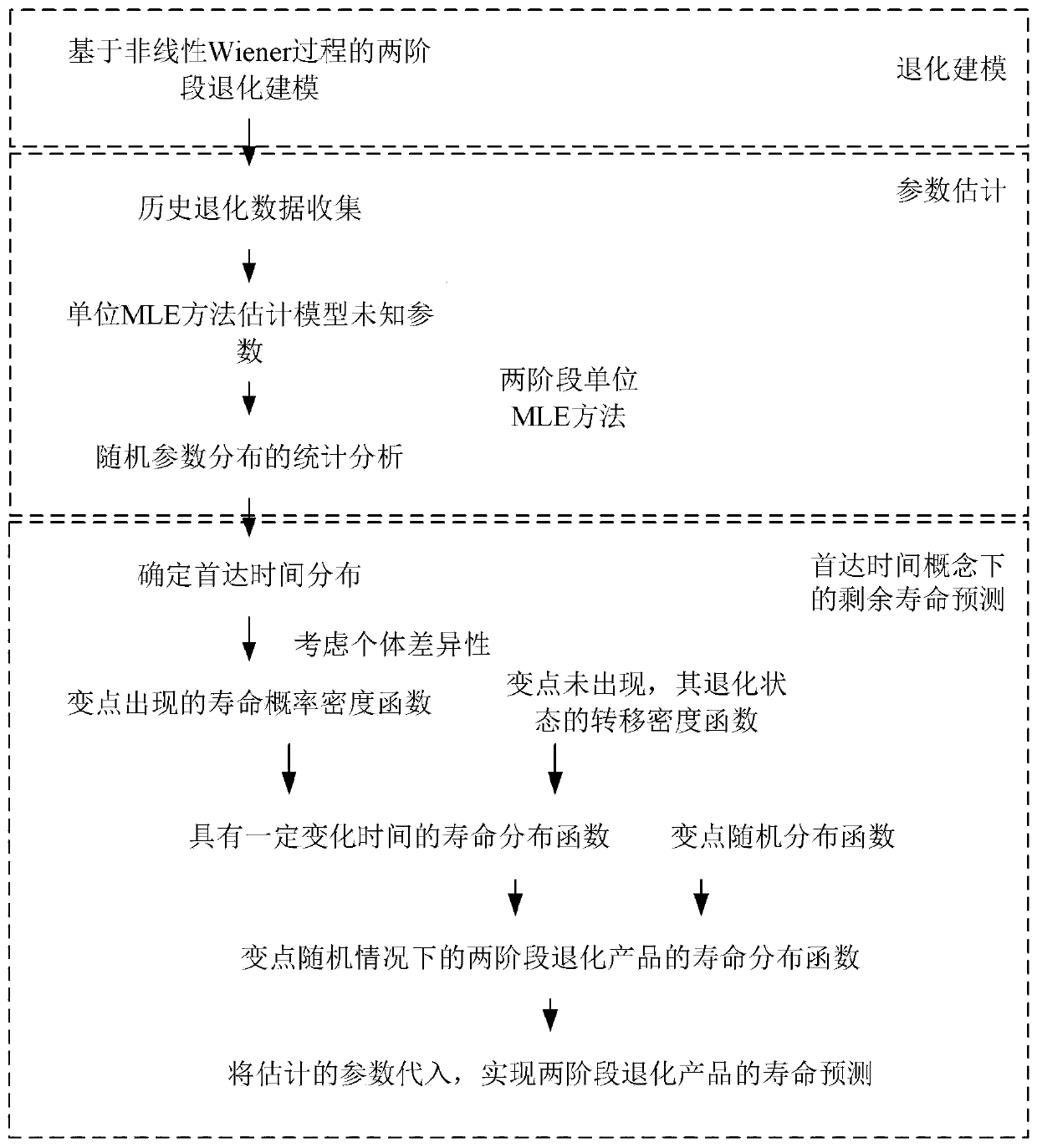
Residual life prediction method for two-stage degraded product
PendingCN111046564AIndicates lifeEffective estimateForecastingDesign optimisation/simulationStatistical analysisEstimation methods
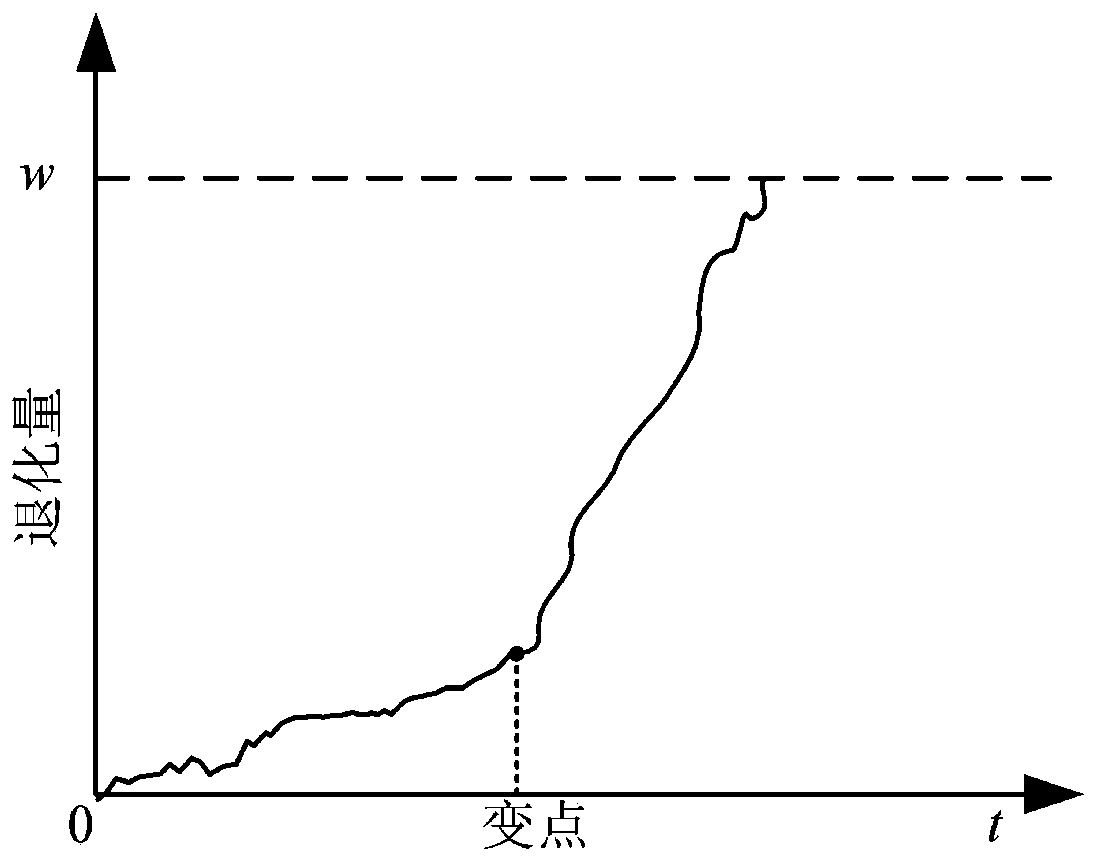
The invention discloses a residual life prediction method for a two-stage degraded product, which belongs to the field of residual life prediction in prediction and health management, and mainly comprises the steps of degradation process modeling, model parameter estimation and residual life prediction, wherein the degradation process modeling is to establish a two-stage degradation model by usinga nonlinear Wiener process; the model parameter estimation comprises the following steps: collecting historical degradation data; estimating model parameters based on a unit maximum likelihood estimation method; statistical analysis of random parameter distribution; the residual life prediction comprises the following steps: obtaining first arrival time distribution; deriving a state transition probability function; and predicting the residual life of the product based on the estimated parameters. The residual life of the two-stage degraded product can be effectively predicted, the operationreliability of the product is ensured, the maintenance cost is reduced, and safety accidents are avoided.
Owner:CHONGQING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com