Authentication equipment and working method thereof
A technology for authenticating equipment and authentication requests, which is applied in the field of communication, can solve the problem of large memory usage, and achieve the effect of small memory usage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
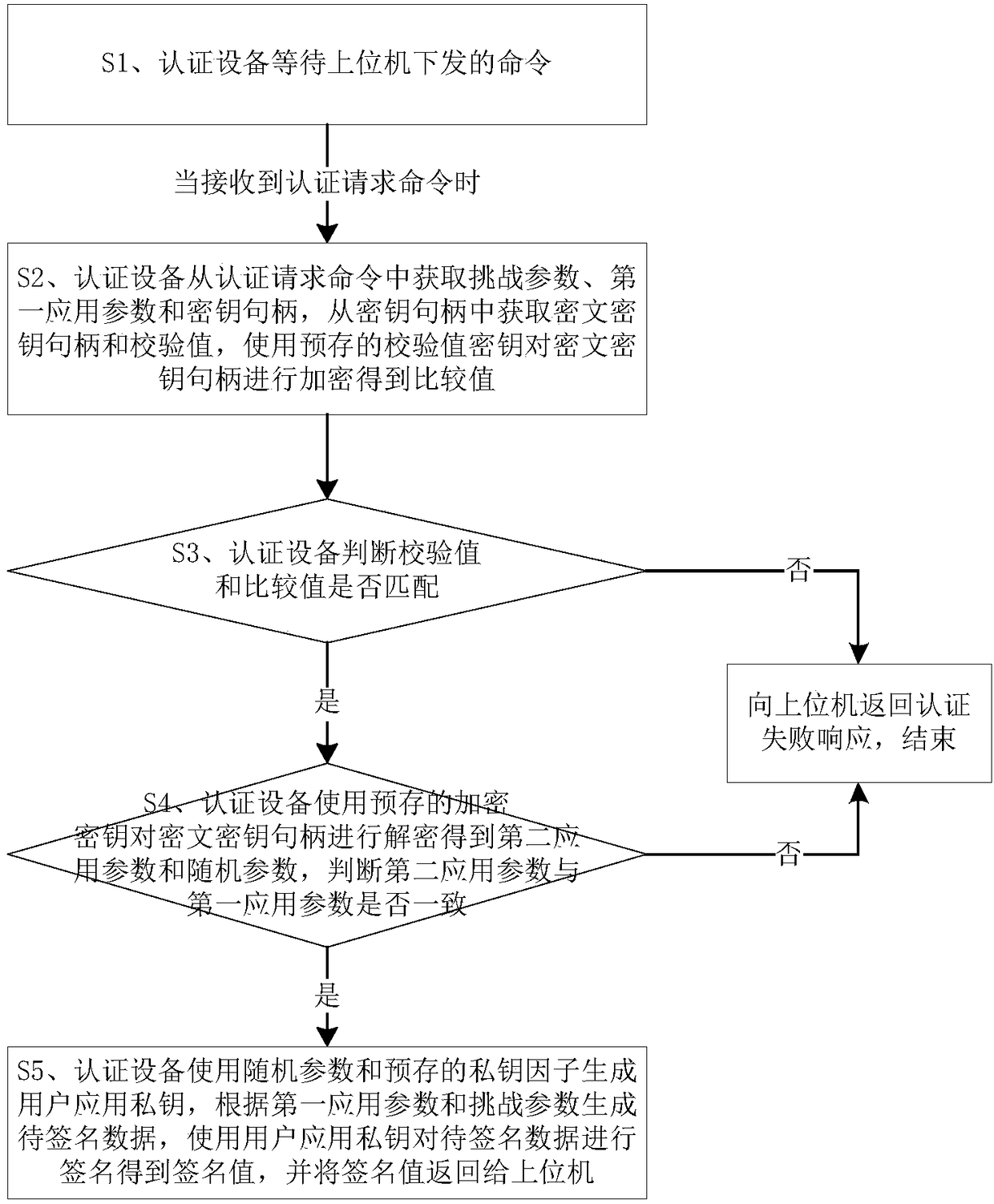
[0046] This embodiment provides a working method for authenticating equipment, such as figure 1 shown, including:
[0047] Step S1, the authentication device waits for the command issued by the host computer, and executes step S2 when receiving the authentication request command;
[0048] Step S2, the authentication device obtains the challenge parameter, the first application parameter and the key handle from the authentication request command, obtains the ciphertext key handle and the check value from the key handle, and uses the pre-stored check value key to pair the ciphertext The key handle is encrypted to obtain the comparison value;
[0049] Step S3, the authentication device judges whether the verification value matches the comparison value, if yes, execute step S4, otherwise, return an authentication failure response to the host computer, and end;
[0050] Step S4, the authentication device uses the pre-stored encryption key to decrypt the ciphertext key handle to o...
Embodiment 2
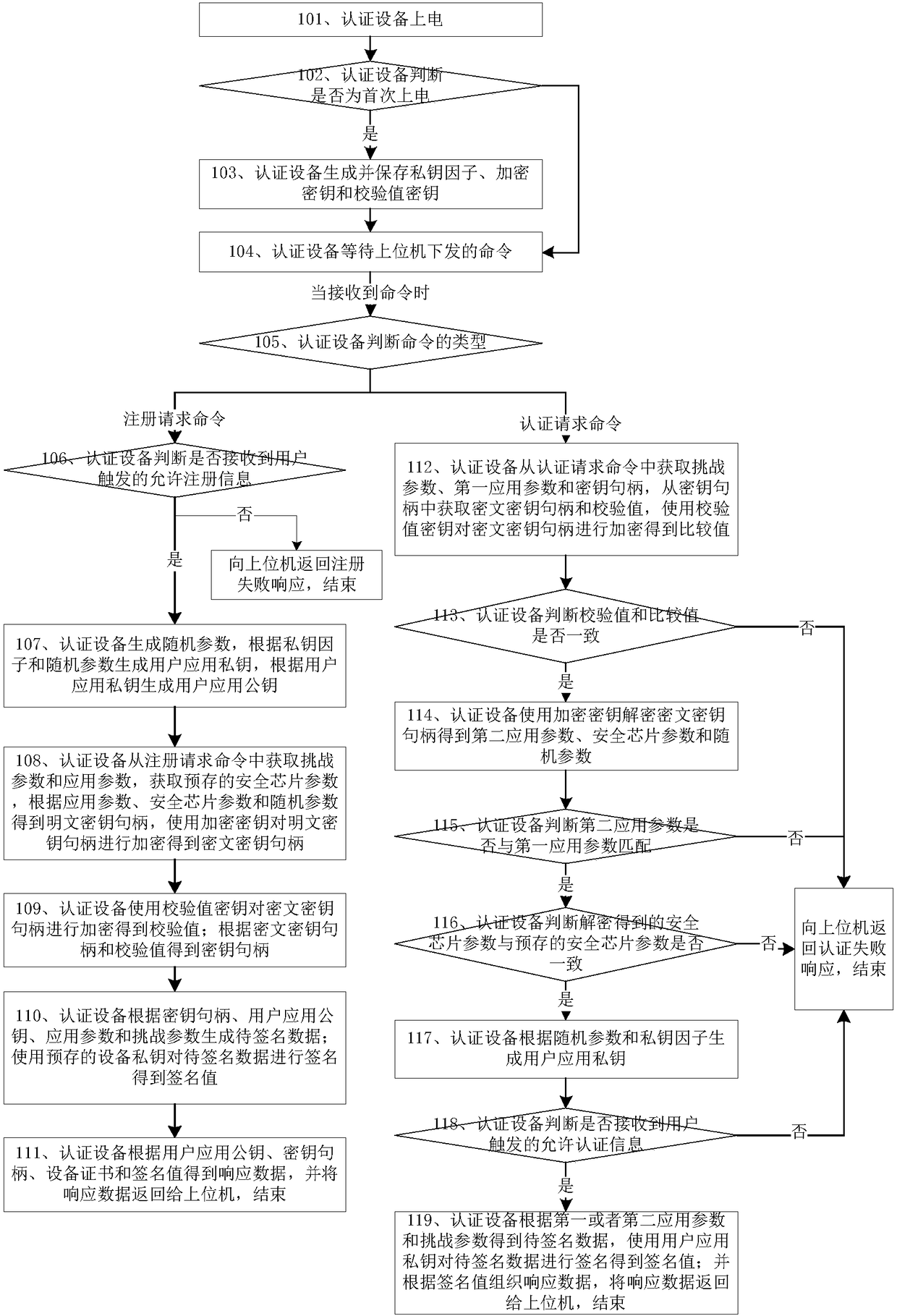
[0064] This embodiment provides a working method for authenticating equipment, such as figure 2 shown, including:
[0065] Step 101, power on the authentication device;
[0066] Step 102, the authentication device judges whether it is powered on for the first time, if yes, execute step 103, otherwise execute step 104;
[0067] Preferably, the authentication device judges whether it is the first power-on according to the power-on flag, if the power-on flag is not set, it is the first power-on, the power-on flag is set, and step 103 is executed, otherwise step 104 is executed;
[0068] Step 103, the authentication device generates and saves the private key factor, the encryption key and the check value key, and executes step 104.
[0069] Step 104, the authentication device waits for the command issued by the host computer; when receiving the command, execute step 105;
[0070] Step 105, the authentication device judges the type of the command, if it is a registration reques...
Embodiment 3
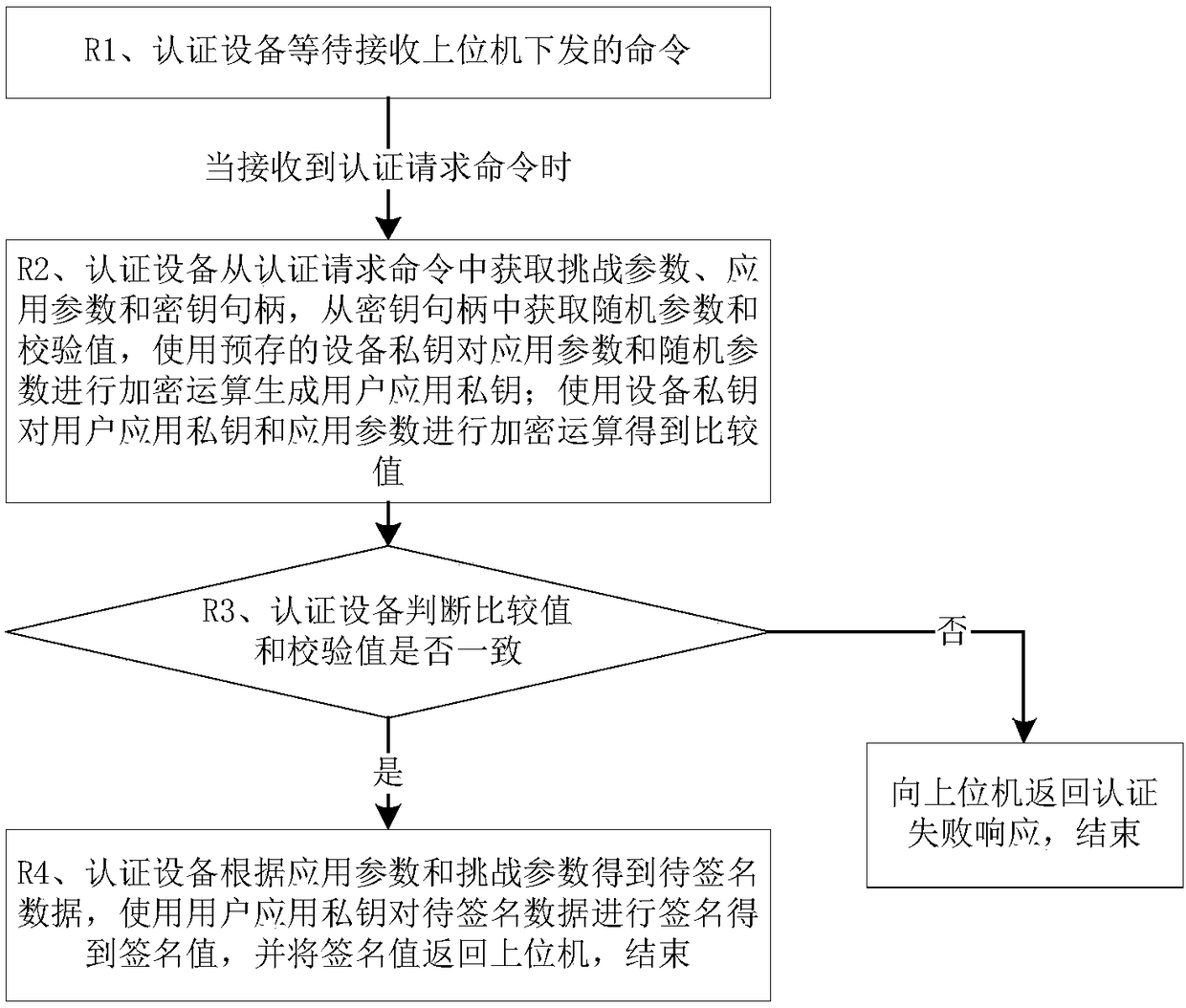
[0125] This embodiment provides a working method for authenticating equipment, such as image 3 shown, including:
[0126] Step R1, the authentication device waits to receive the command issued by the host computer, and when receiving the authentication request command, execute step R2;
[0127] Step R2, the authentication device obtains the challenge parameter, application parameter and key handle from the authentication request command, obtains the random parameter and check value from the key handle, and uses the pre-stored device private key to encrypt the application parameter and random parameter to generate The user application private key; use the device private key to encrypt the user application private key and application parameters to obtain the comparison value;
[0128] Step R3, the authentication device judges whether the comparison value is consistent with the verification value, if yes, execute step R4, otherwise, return an authentication failure response to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com