Keyword or multi-keyword based searchable encryption method and system
An encryption method and keyword technology, applied in the field of information security, can solve problems such as difficult implementation, slow encryption and decryption speed, and complex algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
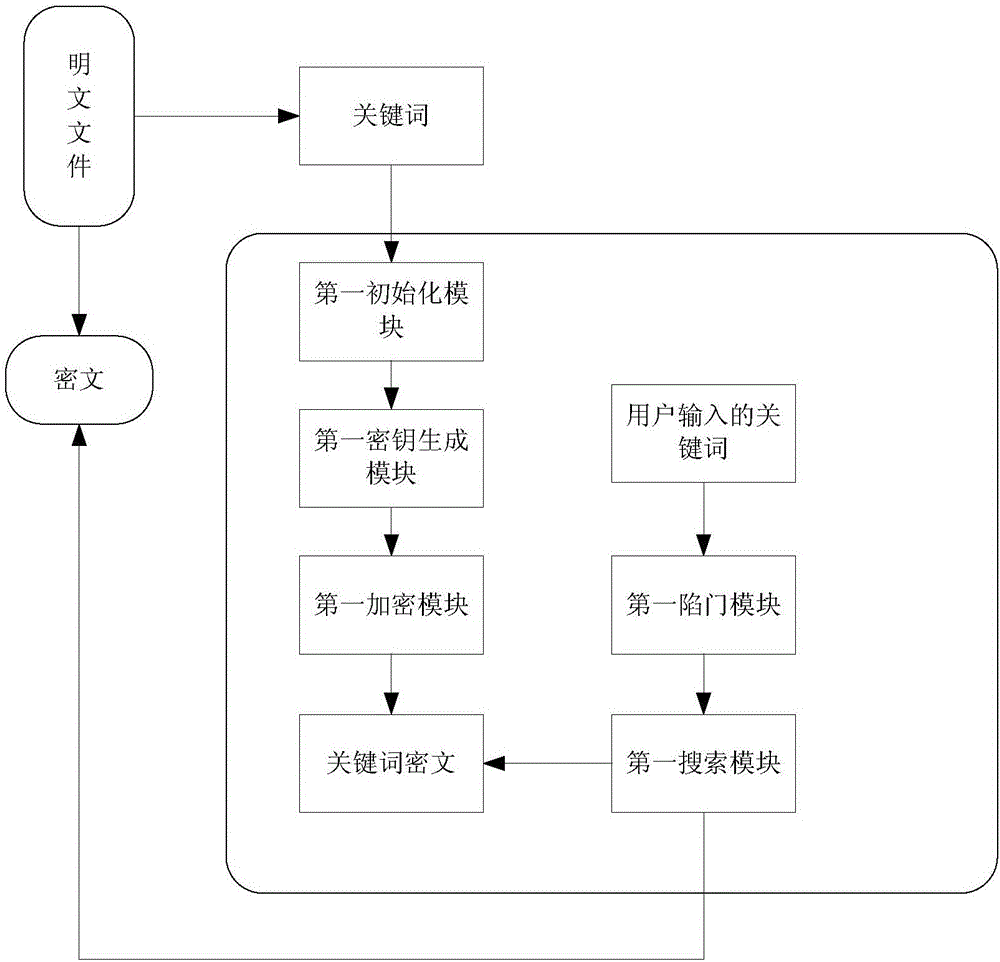
[0070] This embodiment discloses a keyword searchable encryption method, the steps are as follows:
[0071] S1. System initialization, generating system disclosure coefficients under input-based security parameters. The details are as follows: the system publicity coefficient is generated under the input-based security parameter k, where the system publicity coefficient includes the multiplicative group G, the multiplicative group generator g and the bilinear map e:G×G→G T .
[0072] S2. Generate the user's public key and private key according to the first parameter randomly selected by the user and the system disclosure coefficient. The specific process is as follows:
[0073] First calculate X and Y according to the first parameters x and y randomly selected by the user, where x, y ∈ Z p ,Z p is a prime number order group, calculated to get X=g x , Y=e(g,g) y ; Then generate the user's public key PK = (X, Y), private key sk = (x, y).
[0074] S3. Encrypt the keywords ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com